-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 32ee46c5:dde81be9
2024-09-27 03:39:34
@ 32ee46c5:dde81be9
2024-09-27 03:39:34As I travel around the United States, one of the things that always jumps out to me is just how beautiful this country is. The seashores and the rivers, the mountains and canyons, the farmlands and forests, the deserts and plains are spectacular, for sure, but so are the cities. A week or so ago, as I... This is a preview of my post. Join my community and get access to this and more of my work.
https://highlighter.com/npub1xthyd3ttv467g65ff6rpvz6qdvm9zpmf3j35svrc8wuumh0gr05sgx8evy
-
 @ a012dc82:6458a70d
2024-09-27 00:48:50
@ a012dc82:6458a70d
2024-09-27 00:48:50Table Of Content
-
Educational Initiatives Promoting Blockchain and Cryptocurrency Awareness
-
Supportive Government Policies and Regulatory Frameworks
-
Growing Cryptocurrency Mining Industry
-
Increased Adoption by Businesses and Consumers
-
Establishment of Cryptocurrency Exchanges and Digital Asset Marketplaces
-
Collaboration with Neighboring Countries
-
Conclusion
-
FAQ
In recent years, Thailand has emerged as a hub for blockchain technology and cryptocurrency adoption. The country has shown an eagerness to embrace the Bitcoin revolution, with significant developments in areas such as education, mining, and regulatory frameworks. This article explores the key factors that have contributed to Thailand's growing prominence in the global Bitcoin landscape
Educational Initiatives Promoting Blockchain and Cryptocurrency Awareness
Thailand has recognized the importance of education in fostering a strong foundation for the growth of blockchain technology and cryptocurrency adoption. As a result, numerous universities and educational institutions now offer courses and degree programs in the field. This has created a talented pool of blockchain experts and enthusiasts who are driving the growth of the industry in the country.
Supportive Government Policies and Regulatory Frameworks
The Thai government has adopted a proactive approach towards the regulation and growth of the cryptocurrency market. In recent years, the country has established clear legal frameworks and guidelines for digital asset businesses, which has encouraged both local and international players to invest in Thailand's burgeoning cryptocurrency sector.
Growing Cryptocurrency Mining Industry
Thailand has become an attractive destination for cryptocurrency mining, thanks to its affordable electricity rates and well-developed infrastructure. The country has seen an influx of mining companies, which have set up large-scale mining operations to capitalize on the favorable conditions. This has not only created jobs but also contributed to the growth of the local economy.
Increased Adoption by Businesses and Consumers
In Thailand, both businesses and consumers are embracing the Bitcoin revolution. A growing number of merchants accept Bitcoin and other cryptocurrencies as a form of payment, while consumers are increasingly adopting digital wallets for everyday transactions. This widespread adoption has facilitated the growth of a vibrant cryptocurrency ecosystem in the country.
Establishment of Cryptocurrency Exchanges and Digital Asset Marketplaces
Thailand's supportive regulatory environment has paved the way for the establishment of numerous cryptocurrency exchanges and digital asset marketplaces. These platforms have facilitated easy access to cryptocurrencies for Thai citizens, further boosting the adoption and use of digital assets in the country.
Collaboration with Neighboring Countries
Thailand has actively engaged with neighboring countries in the Southeast Asian region to develop cross-border initiatives and partnerships in the blockchain and cryptocurrency space. These collaborative efforts have helped to create a strong regional network that supports the growth of the industry in Thailand and beyond.
Conclusion
Thailand's rapid embrace of the Bitcoin revolution is a testament to the country's forward-thinking approach towards technology and innovation. By fostering education, supportive regulation, and collaboration, Thailand has positioned itself as a leading player in the global blockchain and cryptocurrency landscape. This has not only benefited the Thai economy but also contributed to the worldwide adoption of cryptocurrencies and blockchain technology.
FAQ
How has Thailand embraced the Bitcoin revolution in education? Thailand has incorporated blockchain and cryptocurrency courses into university curriculums, creating a talented pool of experts and enthusiasts who contribute to the growth of the industry.
What role does the Thai government play in supporting the Bitcoin revolution? The government has established clear legal frameworks and guidelines for digital asset businesses, encouraging both local and international players to invest in the cryptocurrency sector.
Why is Thailand becoming a popular destination for cryptocurrency mining? The country offers affordable electricity rates and well-developed infrastructure, attracting mining companies to set up large-scale operations and contributing to the local economy.
How have Thai businesses and consumers adopted cryptocurrencies? A growing number of merchants accept cryptocurrencies as payment, and consumers increasingly use digital wallets for everyday transactions, fostering a vibrant cryptocurrency ecosystem in the country.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 912212cc:672aac36
2024-09-26 20:35:38
@ 912212cc:672aac36
2024-09-26 20:35:38O Tsathoggua negro se moldou de uma gárgula semelhante a um sapo para uma linha sinuosa com centenas de pés rudimentares. Como um deus, Tsathoggua pode alterar sua forma para se adaptar melhor a qualquer ambiente em que você esteja. O que você acha dos vídeos sobre os mitos de Cthulhu?
https://video.nostr.build/394067118f64907e9034190f715da078c7c73c07c65b526fe91f683115fff5c5.mp4
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ e83b66a8:b0526c2b
2024-09-26 19:29:43
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357%
Over a year, your chances increase to: 0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to: 0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ c99e3a74:57eb85c1
2024-09-26 18:34:45
@ c99e3a74:57eb85c1
2024-09-26 18:34:45Livro I
Capítulo I
\ Aristóteles abre sua obra constatando o fato de que toda arte ou investigação, são realizadas em vistas a algum bem. Sendo, portanto, o bem aquilo a que todas as ações tendem. Porém, se bem é aquilo ao qual todas as coisas tendem, surge o seguinte dilema: como pode, então, algumas atividades serem o fim de si mesmas, e outras atividades terem por fim a realização de uma outra coisa? Por exemplo, a realização da construção naval é a produção de um navio, porém a realização da dança se dá no próprio ato de dançar. Assim, há uma diferença entre a natureza dos fins: alguns fins são atividades, enquanto outros são produtos de determinada atividade. Observação: No caso dos fins que são a produção de algo a partir de uma atividade, naturalmente o fim produzido(por exemplo, a saúde para a medicina) é mais perfeito do que a atividade. \ A partir desta constatação, pode-se pensar que, por haver muitas atividades, há também muitos fins. Cita-se o exemplo de que a finalidade da arte médica é a saúde, da construção naval é um navio, da economia é a riqueza e etc. Porém, observa-se que algumas artes subordinam-se a outras, tendo outras por finalidade. Por exemplo, a arte de produzir um bisturi é uma arte sujeita à arte da medicina, que por sua vez tem por finalidade a saúde. Neste sentido, deriva-se que a finalidade da arte mais fundamental, é superior aos da arte subordinadas a ela(no exemplo, a saúde é uma finalidade superior à produção de um bisturi).
Capítulo II
-
 @ 01d0bbf9:91130d4c
2024-09-26 17:58:10
@ 01d0bbf9:91130d4c
2024-09-26 17:58:10Chef's notes
Amazingly tangy, firey hot, but still mellow and bright.
I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee!
Don't forget to use up those delicious chilis and garlic, they are so good!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 1-2 weeks
- 🍽️ Servings: (12x) 8oz jars
Ingredients
- 16oz fresh chili peppers
- 8oz red onion
- 8oz garlic
- 96oz honey
- Fresh thyme
Directions
- Thinly slice peppers, garlic, shallots and fresh thyme
- Add chopped ingredients to the honey
- Leave to ferment (loosely covered) for 1-2 weeks
- Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 3ad01248:962d8a07
2024-09-26 17:39:34
@ 3ad01248:962d8a07
2024-09-26 17:39:34https://image.nostr.build/c7e3732889827ab0a8e2064de5fa6992e37e035347b0c91d249cb8f312b47087.jpg I love Bitcoin. Let me get that out there first of all. I sincerely believe that Bitcoin has the power to change the way the world functions if we can grow adoption to a global scale. This obviously will take time as the gears of economic change grinds slowly. As of right now, people in the western countries don't really see the need for a sovereign politically neutral money that can't be inflated away. They simply don't have to deal with inflation on a regular basis like the rest of the world.
Citizens in western countries got a small taste of what real inflation looks like and guess what? They didn't like it one bit. Overall the last three and a half years you saw countless news stories about how bad inflation and how its making life for the average American or European more difficult.
Yes inflation does suck but look at countries like Argentina, Turkey, Zimbabwe or Venezuela. The people in these countries are suffering from excessive inflation on a regular basis! According to recent economic data Turkey experienced a decline in inflation from 61 percent to 51 percent in August. This is seen as a win in their book! Can you imagine this level of inflation in America? There would be riots in the streets!
Argentina's inflation rate is an astounding 236 percent over the last 12 months! As Bitcoiners we understand that the problem is the money itself. As long as governments have the ability to manipulate the money supply, they will. This is human nature at its finest. When you give a select few that kind of power it becomes irresistible and becomes a tool to control the masses. This shouldn't be a surprise to anyone to be honest.
What I find shocking is with all of this inflation globally no one is really looking around asking questions to why this is happening and looking for a way to escape this system. Are people really this lazy? Not to be mean but cmon. It seems to me that most people are perfectly fine bitching online about how hard it is to make ends meet or supporting their favored political party and wanting them to fix the problem they created. Newsflash to all the normies out there, its the GD political parties that caused inflation in the first place.
We literally have a solution that is staring them in the face, ready to go to replace the current debt based system that we are currently suffering through and no one wants to take the time to research it? Am I black pilled? No, am I realist, very much so. If 236 percent inflation in Argentina can't get them on a Bitcoin Standard immediately, we as a community have a long road ahead of us. Hyperbitcoinization isn't coming in 5 years. It isn't coming in 10 years. Hell it might not even happen in our lifetimes and we have to be ok with that.
So what is the best way to get more Bitcoin into the hands of the people, so they can see the true value of the digital monetary revolution that is Bitcoin. We need a trojan horse and that trojan horse is nostr.
Enter The Nostr Trojan Horse
https://image.nostr.build/5ffee418133ac80ba14b30abf0d5390b878f676cbf6332d67639f9384764da4c.jpg
It should be plain to see by now that the inflation or the number go up narrative alone isn't going to drive Bitcoin adoption. The reason for that is because people don't see the utility of Bitcoin. They see it as some esoteric digital funny money that drug dealers and terrorist use to do bad things.
The average Joe doesn't see how Bitcoin is helping dissidents on foreign countries fund their activism, escape oppressive regimes or simply earn a living. These stories are never told in the mainstream media because they don't want to highlight the fact that a non-state money can circumvent the status quo.
The best way to highlight these stories is to share it on social media, which again is controlled by mainstream gatekeeper such as Meta, Google and X. It is in their best interest to censor these stories or memory hole them out of existence which I suspect happens quite a bit without us even knowing. But the thing about censorship is that it slowly impacts everyone one by one until no one is allowed to say anything without the fear of being put in jail.
Think this can't happen in western democracies? It's happening already my friend! Take a look at the UK or Australia. Citizens their are being arrested over post made to social media. I sincerely believe that these two countries should be a proving ground for showing the value of nostr and Bitcoin.
Introducing the concept of a censorship resistant messaging protocol to them will go over well and once it is understood will grow like a wildfire because people innately understand that censorship is bad and will see the utility value of having the ability to speak freely again.
It is only a matter of time until they realize that they can monetize their speech and build a life using zaps aka Bitcoin.
Until people see the utility in the tools that lie before them, they will never pick them up and use them. It is really that simple. At the end of the day we are still kind of like cavemen. We only use tools when it makes life easier. Man made the wheel. We use it everyday because it has utility.
Bitcoin in the end will be the same way. Utility first, then mass adoption. Nostr is what will help people see the utility Bitcoin and from there sky is the limit. The best thing we can do as Bitcoiners is to encourage people to learn about nostr and show them how easy it is to use and to switch clients that suit their needs instead of being shoved into a one-size fits all solution on centralized platforms.
People like choices, and nostr is all about choice. The interoperability and thelack of need to give personal information to create an account are HUGE selling points that can be touched on. Go out and spread the good word about nostr!
Bitcoin #Nostr
-
 @ 3ad01248:962d8a07
2024-09-26 17:31:27
@ 3ad01248:962d8a07
2024-09-26 17:31:27test poasting
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ dc652bee:6154e7d0
2024-09-26 16:06:14
@ dc652bee:6154e7d0
2024-09-26 16:06:14NEW UPDATE TELEGRAM AIRDROP BOT
📢Exciting news! 🚀 Our new update bot is here to make your Telegram experience even better. Get ready for the ultimate airdrop! Don't miss out!
https://t.me/Dogiators_bot/game?startapp=F80aAU4OlGJX61YK
https://t.me/tonton_intract_bot/start?startapp=eyJyZWZlcnJhbENvZGUiOiJGOER6dDAiLCJyZWZlcnJhbFNvdXJjZSI6IlRFTEVHUkFNX01JTklfQVBQIiwicmVmZXJyYWxMaW5rIjoiaHR0cHM6Ly93d3cuaW50cmFjdC5pby90bWEvcmV3YXJkcyJ9
https://t.me/gamee/start?startapp=ref_730909086
https://t.me/Bcoin2048bot/app?startapp=ref_pCGwqQ15aSZUFYa9ZEys8qRH
https://t.me/realgoats_bot/run?startapp=c127fadc-579e-485a-a68f-f901cd4e64e6
https://t.me/OwlMini_bot/app?startapp=730909086
https://t.me/bluefarming_bot/play?startapp=c8a58023
https://t.me/BitsTonboxBot/BitsAirdrops?startapp=M9Ek3ygSFAJTZ5Y4PS2aoq
https://t.me/digibuy_bot/digiverse/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
http://t.me/foxs_HouseBot?start=730909086
https://t.me/Agent301Bot/app?startapp=onetime730909086
t.me/RealCowsHouse_bot/cowshouse?startapp=kentId730909086
http://t.me/token1win_bot/start?startapp=refId730909086
https://t.me/MemesLabBot?start=PNT7D8
https://t.me/major/start?startapp=730909086
https://t.me/uptonfi_bot/UpTonGames?startapp=ByKBX2QurGdYa
https://t.me/catizenbot/gameapp?startapp=r_1938_7836673
https://t.me/memefi_coin_bot/main?startapp=r_27d6952978
https://t.me/whitebunnywtf_bot?start=ref666953186736f7f2eff6261f
https://t.me/pixelversexyzbot?start=730909086
https://t.me/tapswap_mirror_2_bot?start=r_730909086
https://t.me/hamster_kombaT_bot/start?startapp=kentId730909086
https://t.me/IcebergAppBot?start=referral_730909086
https://t.me/gemsee_bot?start=ref_100a006b
https://t.me/GoodRides_bot?start=NzMwOTA5MDg2
https://t.me/lost_dogs_bot/lodoapp?startapp=ref-u_730909086
https://t.me/gemzcoin_bOt/tap?startapp=nSoqE-UNEtgNUcRp5luy0w
https://t.me/QappiMinerBot?start=730909086
https://t.me/Snakelite_official_bot/Snakelite?startapp=nOuSbPc0
https://t.me/squid_squad_bot/squid?startapp=link_730909086
https://t.me/lovetap_bot?start=ref_120218
https://t.me/BIRDTonBot/app?startapp=730909086
https://t.me/LovelyLegends_bot/start?startapp=kentId730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/pehekingdom_bot/open?startapp=iAzmZVumOr
https://t.me/loody_farming_bot/LOODY/?startapp=inviter_id_40937
https://t.me/Tomarket_ai_bot/app?startapp=0000bDIo
https://t.me/CoinCryptoGameBot?start=r_JSGDH54A
https://t.me/Xyzmercoin_bot/play?startapp=BZI2CZ
https://t.me/dragonz_land_bot/app?startapp=ref-668302fc033aa4721ab5d1ea
https://t.me/BullishFarmBot/start?startapp=r_730909086
https://dashboard.wormfare.com/referral/0DC0D761
https://t.me/betfury_social_bot/app?startapp=tgReLe1ec7c70
https://t.me/PipeFlareBot/pipeflare_app?startapp=730909086
https://t.me/TimeFarmCryptoBot?start=x3jKZG0eoJa58ayY
https://t.me/MatchQuestBot/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
https://t.me/DiamoreCryptoBot/app?startapp=730909086
https://t.me/money_dogs_bot/money_dogs?startapp=3eAlu89K
https://t.me/ZARGatesBot/?start=2307731133
https://t.me/taptapcore_bot/Earn?startapp=b1720f3afcf04e5cb76418c267c4559e
https://t.me/Mimiland_appbot/app?startapp=ref_eyJwIjoiIiwiZiI6InJlZiIsInIiOiI3MzA5MDkwODYiLCJtIjoiNjZkNWZmMWJkNTE3MGU1M2ZiYmMwZmNiIn0=
https://t.me/CyberFinanceBot/game?startapp=cj1CRjNxRE5WbmhNQlomdT1yZWY=
https://t.me/BBQcoin_bot/BBQcoin?startapp=rp_9004676_730909086
https://t.me/PonchKick_bot/ponchiqs?startapp=730909086
https://t.me/potusclick_bot/app?startapp=r730909086
https://t.me/chickcoopofficial_bot/chickcoop?startapp=ref_730909086
https://t.me/ArtiTapBot/start?startapp=referrerId730909086
https://t.me/Frogs_HouseBot?start=730909086
https://t.me/tomo_cat_bot?start=r-cofuLtoo
https://t.me/Boom/LoudCoins?startapp=F5iKvP2LEVi9g4hFkGdpya
https://t.me/The_Rocket_bot?start=r_730909086
https://t.me/monkeycost_bot/app?startapp=r_730909086
https://t.me/tapcoinsbot/app?startapp=ref_TxCe4a
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/flarexgamebot?start=66743fede9b04d43fd21fe9e
https://t.me/grandcombat_bot/start?startapp=TFqI0dXjLc
https://t.me/fishing_bowl_bot/fish?startapp=EQANA57LP2PPLgBIwbnWMpHD4708uGKu7YipzvELhOt6fdnA
https://t.me/GametyPlatform_bot?start=NzMwOTA5MDg2XzA
https://t.me/HUNDTAPbot?start=r_730909086
https://t.me/BabyDogePAWS_Bot?start=r_730909086
https://t.me/BillyBobRobot/GAME?startapp=730909086
https://t.me/wcoin_tapbot?start=NzMwOTA5MDg2
https://t.me/cherrygame_io_bot/game?startapp=r_730909086
https://t.me/pirate_frenzy_bot/piratefrenzy?startapp=i7z37hc2G6
https://t.me/MMproBump_bot?start=ref_730909086
https://t.me/theHoldCoinBot/app?startapp=ref_NRPViKZ4
https://t.me/not_panda_bot/not_panda_app?startapp=9j3938HJeb
https://t.me/gmdotaibot/Airdrop?startapp=ovyova
https://t.me/GoldVerseBot/app?startapp=ref_zzT4iN
https://t.me/herewalletbot/grafun?startapp=TewJ6VV5SA2CrVidvyILAXC8diL
https://gra.fun/?ref=TewJ6VV5SA2CrVidvyILAXC8diL
https://t.me/owlsonton_bot?start=730909086
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/cedex_tap_bot?start=1725744305355276
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/BYIN_official_bot/BYIN_Launchpad_Beta?startapp=q3lj8O41
https://t.me/ARIXcoin_bot?start=ref_730909086
https://t.me/sunkongmyth_bot/sunkong_miniapp?startapp=E987837FE
https://t.me/boolfamily_bot/join?startapp=8T1X0
https://t.me/tonstationgames_bot/app?startapp=ref_aysq8p4swodmv4ex6c7e4y
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/GalaCoin_bot/app?startapp=ref_KFfSylID
https://t.me/Yaytsogram_bot?start=invite4546481
https://t.me/battle_games_com_bot/start?startapp=frndId730909086
https://t.me/PinEye_Bot/pineye?startapp=r_730909086
https://t.me/pocketfi_bot/Mining?startapp=730909086
https://t.me/SatoshiMiner_Hq_Bot?start=730909086
https://t.me/sidekick_fans_bot?start=730909086
https://t.me/bums/app?startapp=ref_rgws9zFi
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/head_coin_bot/start?startapp=bonusId730909086
https://t.me/onus_tap_tap_tap_bot/join?startapp=1722155904792
https://t.me/Atleta_tap_bot/tap?startapp=a89197f4-6ef7-4925-a38d-cbe0cc71aa34
https://t.me/SecretPadBot/app?startapp=r730909086
https://t.me/Binance_Moonbix_bot/start?startApp=ref_730909086&startapp=ref_730909086&utm_medium=web_share_copy
https://t.me/catsdogs_game_bot/join?startapp=730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/playpenchobot/play?startapp=ZF6EG6NCVC
https://t.me/nodgoin_bot/?start=ref_309eb495-9c18-4c3b-8177-297b89ac8911
https://t.me/Loodygame_bot/loodydev/?startapp=inviter_id_40937
https://t.me/CrashinoCasinoBot/?start=EjtAhLG5X
https://t.me/BybitCoinsweeper_Bot?start=referredBy=730909086
http://t.me/CamelsHouseBot/House?startapp=66f428b404d8bde3bbb68790
https://t.me/forge_game_bot/start?startapp=NzMwOTA5MDg2
https://t.me/boinker_bot/boinkapp?startapp=boink730909086
🆘Several projects are coming to the listing soon, some have already been released, start today it's completely free.⛏️
-
 @ d6affa19:9110b177
2024-09-26 15:44:34
@ d6affa19:9110b177
2024-09-26 15:44:34it's a sunny afternoon at a shopping center. i open the car door for Her. we head into the bookstore. the aroma is rich, thick. i buy us coffee.
we then browse around. but beneath my calm surface, a quiet longing stirs—a deep yearning for Her.
Her touch. Her love.
i still feel the echoes of Her words—a sweet torment that rests in my mind. i've felt it all day. it's nearly maddening.
and yet i maintain my composure as i follow along to the next store.
She turns. i spot a brief smirk.
my breath catches. She knows... i can't hide from Her.
a simple brush of Her hand. it sends jolts. a reminder of the pleasure She wields.
"Are you okay?" Her voice sweet, yet probing.
"Yes, my Queen." i answer in an even tone, managing the storm underneath.
"Good," She nods.
"Let's go, sweet boy." Her command lingers gracefully in the air.
"Help me try on some shoes."
the thought of helping Her... it sends a thrill through me.
i nod, taking another sip of coffee.
it burns, still hot. my hands feel clammy against the cup, heart racing.
the anticipation is electric...
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ dc652bee:6154e7d0
2024-09-26 15:40:20
@ dc652bee:6154e7d0
2024-09-26 15:40:20Embracing the power of positivity and prosperity! 💵✨ Let's make every dollar count and spread good vibes all around. #GoodDollar 🌐https://n9.cl/gooddolars
-
 @ e97aaffa:2ebd765d
2024-09-26 14:57:00
@ e97aaffa:2ebd765d
2024-09-26 14:57:00Claro que não, o Bitcoin não é uma solução mas sim uma reação à inação dos governos.
O sistema FIAT está numa situação tão crítica, não existe uma solução boa para o problema da dívida soberana, terá que se optar pela menos má. Como resolver o problema das dívidas futuras, dos fundos de pensões? As dívidas do passado tem que ser pagas, mas como? As dívidas não são apenas números no excel, são pessoas que estão por detrás desses números, não podem ser apagadas, simplesmente.
Uma solução seria uma mudança drástica nas políticas, com uma forte redução de custos do estado e muita austeridade, gerando uma queda do padrão de vida dos cidadãos. Só que isto seria extremamente impopular, nenhum político tem coragem de o fazer, quem tentar vai acabar por perder na próxima eleição.
Assim, a única maneira que resta para os políticos, é fazê-lo pela calada, através da desvalorização da moeda. A inflação permite destruir as dívidas do passado e consequentemente a poupança e a qualidade de vida dos cidadãos. É isto que temos visto nos últimos anos e vai agravar-se no futuro. Só que os atuais níveis de expansão monetária, não foram suficientes para resolver o problema, apenas permite ao governo estar à tona da água, procrastinar o problema.
Um bom exemplo é na UE, onde existe uma regra que permite um défice até 3% do PIB por ano, que muitas vezes nem é cumprida, isto é uma situação insustentável. A regra deveria ser o oposto, obrigar um superávit mínimo de 2% ao ano, só assim será possivel reduzir a dívida.
A expansão monetária e política monetária está a ser utilizada como uma arma contra os cidadãos, é um imposto totalmente cego, muito penalizador para os mais pobres e os governos têm abusado desse poder. A moeda é o sangue de uma economia, os políticos ao diluí-la estão a envenenar a economia. O Bitcoin é a única moeda que não pode ser diluída.
Os políticos reconhecem que existe um problema mas todas as soluções são extremamente impopulares, e como eles são os principais beneficiados do sistema FIAT, dificilmente haverá uma mudança.
Bi-monetário
Como nenhum político terá coragem de mudar, essa mudança tem de partir dos cidadãos, voluntariamente, ou seja, com a adoção do Bitcoin.
Todos os bitcoiners gostariam de assistir a uma mudança rápida do padrão FIAT para o padrão Bitcoin, mas não é possível. É necessário ter noção como o mundo real é, uma mudança rápida entre os padrões seria desastrosa para toda a humanidade, esse processo terá que ser gradual, para não existir uma ruptura entre gerações e entre estratos sociais.
Com a criação do Bitcoin, o paradigma mudou, passou a existir um sistema bi-monetário, com a moeda FIAT e o Bitcoin em circulação simultânea. O FIAT como unidade de conta e o Bitcoin como reserva de valor e as duas como meio de troca.
Hoje, a alocação em Bitcoin ainda é muito baixa. Em média a nível mundial está 99.2% em FIAT e 0.8% em Bitcoin. Mas chegará o dia, atingirá os 50-50%, em alguns países possivelmente será ainda maior.
Será uma adoção completamente voluntária, não será pelos governos, mas sim, pelos cidadãos, de baixo para cima. No início, a adoção será lenta, mas quanto maior for a alocação em Bitcoin, mais acelerada será a adoção.
A dupla circulação de moeda, vai obrigar os governos a fazer uma melhor gestão, vai limitar indiretamente a impressão de dinheiro. Se os governos abusarem desse poder, as pessoas vão se proteger ainda mais no Bitcoin, diminuindo a alocação em FIAT, por sua vez a moeda fica mais fraca e o governo também. Vai obrigar um maior rigor na política monetária.
O Bitcoin será uma proteção contra o abuso dos governos, vai obrigar uma mudança, um maior rigor na sua gestão, possibilitando a redução da dívida a longo prazo.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ a012dc82:6458a70d
2024-09-26 12:16:02
@ a012dc82:6458a70d
2024-09-26 12:16:02Table Of Content
-
A Brief Overview of Bitcoin Mining
-
The Rails Programming Tool: A Game Changer for Bitcoin Miners
-
Customization and Scalability
-
Enhancing Security and Compliance
-
Conclusion
-
FAQ
The world of cryptocurrency is ever-evolving, and as the demand for Bitcoin mining solutions grows, so does the need for innovative and efficient tools. Lincoln Technologies, a leading name in the field of blockchain technology, has introduced a groundbreaking Rails Programming Tool that aims to revolutionize the Bitcoin mining landscape. This article will explore the features and benefits of this powerful new tool and how it can help you unlock the full potential of Bitcoin mining.
A Brief Overview of Bitcoin Mining
Before delving into the details of the Rails Programming Tool, it is essential to understand the concept of Bitcoin mining. Mining is the process of validating and adding new transactions to the blockchain, which ensures the security and integrity of the cryptocurrency network. In return for their efforts, miners are rewarded with newly minted bitcoins and transaction fees. As the mining process becomes increasingly competitive, miners require sophisticated tools to stay ahead of the game.
The Rails Programming Tool: A Game Changer for Bitcoin Miners
Lincoln Technologies' Rails Programming Tool is a cutting-edge solution designed specifically for Bitcoin mining. This powerful software offers a range of features to streamline the mining process, reduce energy consumption, and optimize mining efficiency. Some of the key features include:
User-friendly interface: The Rails Programming Tool boasts a clean and intuitive interface that is easy to navigate even for beginners, reducing the learning curve for new miners.
Advanced mining algorithms: The tool is equipped with the latest mining algorithms to maximize the mining output and increase the chances of earning rewards.
Energy-efficient operations: Energy consumption is a significant concern for Bitcoin miners. The Rails Programming Tool optimizes mining efficiency and reduces energy consumption, lowering the overall costs and environmental impact of mining.
Customization and Scalability
One of the standout features of the Rails Programming Tool is its adaptability. The tool can be customized to suit the specific needs of individual miners, allowing them to create a tailored solution that works best for their mining setup. Additionally, the Rails Programming Tool is designed to grow with the ever-changing world of cryptocurrency, ensuring that users can continue to benefit from its features as the mining landscape evolves.
Enhancing Security and Compliance
Security is of the utmost importance in the world of cryptocurrency, and Lincoln Technologies has taken steps to ensure that the Rails Programming Tool meets the highest security standards. The software employs advanced encryption protocols to protect sensitive data and maintain compliance with industry regulations. By using the Rails Programming Tool, miners can have peace of mind knowing that their operations are secure and compliant.
Conclusion
The Rails Programming Tool from Lincoln Technologies is poised to revolutionize the way Bitcoin miners operate. By harnessing the power of this innovative software, miners can unlock new levels of efficiency, profitability, and sustainability in their mining efforts. As cryptocurrency continues to gain mainstream acceptance, the Rails Programming Tool is a valuable asset for those looking to capitalize on the growing demand for Bitcoin mining solutions.
FAQ
What is the Rails Programming Tool by Lincoln Technologies? The Rails Programming Tool is an innovative software solution designed to streamline and optimize the Bitcoin mining process, reduce energy consumption, and enhance security and compliance.
How does the Rails Programming Tool improve mining efficiency? The Rails Programming Tool uses advanced mining algorithms to maximize mining output, optimizes energy consumption, and offers customization and scalability features that help miners tailor the tool to their specific needs.
Is the Rails Programming Tool suitable for beginners? Yes, the Rails Programming Tool features a user-friendly interface, making it easy to navigate and learn for both beginners and experienced miners alike.
Can the Rails Programming Tool adapt to the changing cryptocurrency landscape? Yes, the Rails Programming Tool is designed for scalability, allowing it to grow and adapt to the ever-evolving world of cryptocurrency and Bitcoin mining.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a58a2663:87bb2918
2024-09-26 11:14:34
@ a58a2663:87bb2918
2024-09-26 11:14:34Quem sabe – quem sabe! – você se interesse em saber como andam as minhas pesquisas sobre o “projeto humanista” em “A alegoria do mundo: o mago, o filólogo e o colonizador”, módulo atual de Convivium – Seminário Permanente de Humanidades.
Na semana passada fiz uma transmissão de áudio no grupo do Telegram dos participantes. Entre outros temas abordados, pude falar da interpretação que Edgar Wind faz do quadro “Primavera”, de Botticelli, como uma explicitação do tipo de alegoria platonizante que dominaria a mente de humanistas da Renascença.
https://image.nostr.build/6e1ee79986d3d4c929609fdf037a3e1e6ee399559fb7e2b5d8c02ad0b9b188ad.jpg
A alegoria é o modo mental, defende E. H. Gombrich, pelo qual uma tese é proposta antes que as causas e analogias que a embasam sejam estabelecidas, de modo que o processo associativo irá apenas justificar a posteriori o que se quis desde logo comunicar. Imagine George Orwell postado às suas costas enquanto você lê 1984. A todo momento, ele irá cutucar o seu ombro e dizer: “Está vendo? Aqui está o que eu quis dizer com a fala desse personagem nesse trecho”. O texto é apenas pretexto para uma mensagem, e é a mensagem que se ergue com claro perfil discursivo diante do leitor. A ficção começa a ceder espaço para o palanque.
Defendo que a alegoria é a mãe das mitologias abstratas, do romance de tese e da experiência de avatar que caracteriza o mundo digital. E seus princípios de analogia arbitrária, que datam do fim da Idade Média, ganham exemplificação máxima nas obras Da magia e Dos vínculos, de Giordano Bruno, que discutirei numa aula ao vivo hoje (26), às 20h30. Na atuação de Bruno se nota como a magia foi cada vez mais percebida de maneira imaterial, abstrata, psicologizante (e dessa sua concepção nos vêm os primeiros prenúncios do inconsciente), ao mesmo tempo que sua primeira ocupação com o mundo material foi aos poucos transferida para as ciências que tendiam a ignorar o elemento humano que manipula esse mesmo mundo material.
Se por um lado, portanto, começa a triunfar uma cosmovisão que supõe um ser humano quase sobrenatural em seus poderes psíquicos (segundo a nova ideia de magia como manipulação da memória), por outro lado começa a se difundir uma cosmovisão que supõe um mundo subtraído de todo elemento humano, uma espécie de cosmos impessoal, aquele que hoje se encontra nos livros de física. Penso que essa como que esquizofrenia reflete a dinâmica de exaltação e depressão do erudito que comentei durante a leitura do Fausto de Goethe realizada no primeiro módulo de Convivium: o herói do poema ora se sente um deus ora se sente um verme, tal como hoje é muito comum nos sentirmos.
Na aula de hoje irei lidar com aquele primeiro aspecto da analogia como arma de um ego entronado, ao passo que na primeira semana de outubro irei disponibilizar aos alunos o texto “Máquina e segredo”, acompanhado de vídeo com comentários complementares. Nesse escrito tratarei, por exemplo, de como os inventos de Giambattista della Porta (1535-1615), especialmente na área da criptografia, assinalam não só um novo estágio na história da tecnologia, como também um novo estágio da disposição dos estudiosos para com o conhecimento, uma disposição típica do que venho chamando de “nova aposta de Pascal”, conceito que terei a oportunidade de rever.
“Máquina e segredo” será o primeiro excerto que colocarei em discussão do ensaio O destino do humanismo, que talvez acabe recebendo o título de A alegoria do mundo, como o atual e terceiro módulo de Convivium; a ver.
Para comemorar este momento importante das pesquisas que venho fazendo a respeito do “projeto humanista” (iniciadas em 2020, privadamente, e continuadas algo publicamente a partir de 2022), resolvi dar 25% de desconto na inscrição de Convivium para quem optar por pagar em bitcoin. Algumas pessoas já chegaram a Convivium por meio do Nostr, e é minha intenção trazer ainda mais gente. Em vez de pagar R$ 449, pague agora R$ 336,75 para ter acesso a:
- O destino do humanismo: uma leitura do Fausto de Goethe, com 12 aulas, materiais complementares e aulas bônus (mais de 20 horas de vídeo);
- Os livros da vida: Abelardo, Dante, Cardano, Santa Teresa, com mais 12 aulas, textos e materiais auxiliares (mais de 20 horas de vídeo idem);
- A alegoria do mundo: o mago, o filólogo e o colonizador, módulo em andamento e com aulas mensais até abril de 2025. Até o momento tivemos 4 aulas ao vivo, 3 vídeos pré-gravados e 3 transmissões de áudio, além de comentários esparsos pelo grupo do Telegram.
Caso queira se inscrever pagando em bitcoin, mande-me uma mensagem privada ou e-mail para camoensiii57@protonmail.com
-
 @ 8f69ac99:4f92f5fd
2024-09-26 11:08:21
@ 8f69ac99:4f92f5fd
2024-09-26 11:08:21As revoluções muitas vezes começam com os membros mais jovens da sociedade—adolescentes, idealistas e cheios de energia, ansiosos por causar mudanças. No entanto, no mundo de hoje, a noção de revolução foi sequestrada por forças que procuram controlar e manipular, em vez de empoderar os indivíduos. A chamada "revolução woke" é um exemplo claro, impulsionada por uma agenda que polariza a sociedade ao longo das linhas da política identitária. Esta distracção desvia a atenção dos verdadeiros problemas: a desigualdade económica e o autoritarismo. Mas há uma alternativa melhor, uma que prioriza a liberdade e a soberania em vez da divisão e do controlo—Bitcoin.
A "Revolução Woke" Globalista e a Agenda da Polarização
Uma das tácticas mais insidiosas da "revolução woke" é a polarização deliberada da sociedade. Ao criar narrativas que colocam as pessoas umas contra as outras com base em raça, género, religião e política, aqueles no poder mantêm o controlo e desviam a atenção dos problemas mais profundos que realmente importam. Esta estratégia é orwelliana: ao criar uma mentalidade de "nós contra eles", fabricam uma cultura de conflito perpétuo.
Em vez de promover uma mudança significativa, a "revolução woke" prende as pessoas num ciclo de indignação e divisão, distraindo-as de enfrentar as verdadeiras estruturas de poder—como a desigualdade económica e o excesso de controlo estatal. Esta fragmentação enfraquece os laços entre as pessoas, tornando a sociedade mais vulnerável à manipulação pelas autoridades centralizadas.
Esta polarização serve os interesses daqueles que estão no poder. Quando as pessoas estão demasiado ocupadas a lutar entre si, são menos propensas a questionar os sistemas que realmente as controlam. A "revolução woke" torna-se menos uma questão de progresso genuíno e mais uma forma de manter o status quo através da divisão e da distracção.
Por Que a Polarização é Incentivada
A polarização não é acidental—é uma estratégia calculada com o objectivo de controlar. Dividindo as pessoas em campos opostos, a sociedade fragmenta-se, tornando mais difícil para os indivíduos unirem-se contra adversários comuns ou combaterem políticas que beneficiam as elites.
Esta divisão serve também como uma distracção poderosa. Enquanto as pessoas estão consumidas por batalhas ideológicas, os sistemas financeiros centralizados e o controlo governamental expandem-se silenciosamente. Os meios de comunicação, muitas vezes controlados pelos mesmos poderes, alimentam estas divisões, mantendo as pessoas focadas em conflitos internos enquanto ocultam as verdadeiras ameaças à liberdade.
A polarização também corrói as liberdades individuais. Quando as pessoas estão envolvidas em batalhas ideológicas intermináveis, são menos propensas a notar a erosão gradual dos seus direitos. Isto é precisamente o que os poderes estabelecidos desejam—uma população distraída e dividida, demasiado ocupada para desafiar o desmantelamento lento das suas liberdades pessoais.
O Resultado da Polarização
O resultado desta polarização deliberada é uma sociedade mais preocupada com a pureza ideológica do que com a garantia das suas verdadeiras liberdades. As pessoas ficam presas na política identitária, priorizando a lealdade ao grupo em detrimento da autonomia individual. Isto promove uma mentalidade de "pensamento de grupo", onde questionar a narrativa dominante é desencorajado.
Entretanto, a desigualdade económica aprofunda-se à medida que os poderes centralizados continuam a consolidar o controlo. Os sistemas que deveriam promover equidade tornam-se cada vez mais manipulados, beneficiando os poucos em detrimento dos muitos. A verdadeira liberdade—especialmente a liberdade financeira—torna-se mais difícil de alcançar, com os indivíduos presos em sistemas concebidos para beneficiar uma minoria poderosa.
No final, a "revolução woke" apenas reforça as mesmas estruturas que afirma combater. Ao dividir as pessoas e distraí-las dos verdadeiros problemas, os poderes estabelecidos mantêm o seu controlo, enquanto as liberdades pessoais e financeiras da maioria continuam a ser corroídas.
Bitcoin: A Verdadeira Revolução
Em contraste com a "revolução woke", que divide, Bitcoin oferece uma verdadeira revolução—uma que empodera os indivíduos em vez de os separar. Bitcoin proporciona soberania financeira, retirando poder dos governos autoritários e das instituições centralizadas.
Bitcoin permite que os indivíduos controlem a sua própria riqueza, eliminando a necessidade de intermediários como bancos ou governos. As pessoas já não estão sujeitas a entidades que restringem a sua liberdade financeira. Com Bitcoin, podem criar, armazenar e transferir valor de forma segura, transparente e acessível.
Isto não se trata apenas de economia—é sobre recuperar a liberdade. A natureza descentralizada do Bitcoin permite que as pessoas tomem decisões financeiras sem interferência do estado ou de entidades corporativas.
Porque é Que o Bitcoin é Revolucionário
A verdadeira natureza revolucionária do Bitcoin reside no seu design e princípios, que rompem com os sistemas de controlo enraizados. Eis algumas razões pelas quais o Bitcoin é transformador:
-
Aberto e Sem Fronteiras: O Bitcoin transcende fronteiras, permitindo que pessoas de todo o mundo participem igualmente no sistema financeiro. Quebra barreiras baseadas em nacionalidade ou geografia, permitindo uma participação económica global.
-
Resistente à Censura: Nenhum governo ou empresa pode parar uma transacção em Bitcoin, dando às pessoas a liberdade de transferir valor sem medo de interferências ou retaliações. Esta é a forma definitiva de autonomia financeira.
-
Sem Permissão: O Bitcoin não requer aprovação de nenhuma autoridade. Ao contrário dos sistemas financeiros tradicionais, não há porteiros a controlar quem pode participar, tornando o Bitcoin uma ferramenta para a verdadeira auto-soberania financeira.
-
Neutro: O Bitcoin é imparcial. Não se importa com raça, género, religião ou política. Num mundo onde a política identitária é usada para dividir, o Bitcoin trata todos de forma igual, oferecendo um sistema financeiro inclusivo que transcende essas divisões.
Bitcoin como o Antídoto para a Polarização
O Bitcoin oferece uma solução para a divisão criada pela polarização. Transcende a política identitária ao tratar todos de forma igual, independentemente da sua origem ou crenças. A neutralidade do Bitcoin garante que nenhum grupo ou facção pode manipulá-lo para impor as suas visões sobre os outros.
Bitcoin permite que os indivíduos se libertem das narrativas divisivas e tomem controlo dos seus destinos financeiros. Promove a cooperação em vez do conflito, capacitando as pessoas a focarem-se em objectivos comuns, em vez de batalhas ideológicas.
O Bitcoin não é apenas uma moeda—é uma força unificadora, oferecendo esperança àqueles que estão cansados da divisão e das lutas pelo poder. Representa uma mudança para práticas financeiras inclusivas que priorizam a autonomia individual em detrimento do controlo centralizado.
Um Apelo à Acção
Para os jovens que sonham em criar uma mudança real: se querem liderar uma revolução que verdadeiramente empodere os indivíduos e quebre as cadeias do controlo centralizado, então é hora de abraçar o Bitcoin.
Esta revolução não é sobre seguir uma agenda predefinida ou alinhar-se com ideologias divisivas. Trata-se de criar um futuro de sistemas financeiros abertos, onde todos têm a liberdade de participar igualmente.
A cor desta revolução é laranja, simbolizando o logótipo do Bitcoin e o movimento em direcção à liberdade financeira. Representa a esperança para aqueles que querem escapar das restrições dos sistemas tradicionais e criar um mundo descentralizado e empoderado.
Conclusão
Estamos à beira de uma revolução financeira. A juventude tem uma escolha: seguir as narrativas pré-definidas dos sistemas ultrapassados ou tomar controlo dos seus próprios destinos através de redes financeiras descentralizadas e abertas.
O Bitcoin é a verdadeira revolução. É um movimento impulsionado pelo desejo de liberdade, autonomia e inclusão. Juntem-se à revolução, sejam parte de algo maior, e ajudem a construir um mundo onde o poder é descentralizado, as oportunidades são iguais e o futuro é brilhante e laranja—a cor da liberdade financeira.
Photo by Tarik Haiga on Unsplash
-
-
 @ a9434ee1:d5c885be
2024-09-26 10:42:52
@ a9434ee1:d5c885be
2024-09-26 10:42:521. Relay = Community?
If spinning up a relay is getting easier and cheaper by the day, why can't the relays literally be the group/community?
Then: * Any relay is by default a public community. The more restricted read- or write-access is, the more it becomes a private group. * Any publication targeted at (h-tag) and stored, and thus accepted, by a relay can be seen as a publication in that community. * All-in-1 hosting solutions (integrated blossom servers, lightning nodes, ...) are made easier.
2. Why invent new kinds?
Why can't Kind 1 posts that are targeted and accepted by a relay (i.e. community) just be the forum-posts of that community? Why create new kinds for this? And even weirder, why create a new kind with that exclusively serves as a reply to that new kind? Why not just use generic replies (kind 1111) and take the #otherstuff (event kinds and apps) as an opportunity to introduce those?
For chat messages, however, I get it. You need a kind + reply-kind for those.
3. Community VS Private group
It seems like the only distinction you really need, both for the user and the apps implementing all this, is:
1. Public Community: anyone can read and follow this community but for writing the admins can set limits (pricing, white listings, ...) 2. Private group: only the profiles that even know this relay (i.e. group) exists can interact with it. Read-access has to be granted (invite, pricing, ...) and admins can set limits for writing too. Beyond this distinction it's a bit naive to try to categorize them. Open vs Closed doesn't really mean much for example, since technically all groups/communities set limits and are thus closed. It's more interesting to look the ways in which they can be closed and build on the simplest distinctions you can make there.The difference between Public communities and private groups is the most important one because they both have very different UX and specification requirements:
Memberlist
Communities: None existent
Anyone can read and follow. It just has limits on who can publish what, when. So the most interesting thing to surface is probable something like a list of most active members or a highlighted set of profiles that have special characteristics within this community (top supporter, god-mode, resident artist, ...).
Private Groups: Necessary for it's existence
The whitelisted npubs for read-access are the members.Moderation actions
Both types of groups need a way for the admin(s) to:
* Block/remove users * Remove events * Edit metadata (name, description, guidelines...) * Specify who can write publish what, under what conditionOnly private groups need a way for the admin(s) to:
* Add/approve new members → specify who has read-access, under what conditionGeneralizing too many actions like
add member,join request, etc... that are only applicable to one of these categories just creates bad UX for the other one. You don't "add a member" to a public community. People can follow it without asking anyone's permission (ok yes, some will AUTH for reading but that's besides the point). Some of its followers will then just choose to publish something there and the admin either allows them or not.Having a common protocol for specifying the conditions for this write-access interoperably (as mentioned above) is what I would like to see instead: * Both Communities and Private groups need it anyway * You have to assume admins need granularity in the conditions they set for publishing in their group/community: Who, what, under what condition, ... * You don't want to link out to custom websites (or similar) explaining their allowance schemes
Sidenote: we need a similar kind of spec for the services that allow you to spin up your hosting solution (relay, server, node, ...) so that, when you click "Create new community" in an app, those services can be surfaced. With their business models (including options to self-host parts of it) just there, in the app, without linking out. Same for the lines of communication and payments that are needed to make those business models work from within any app.
Publication and Discovery
Only Communities allow for the exciting possibility of publishing something in multiple overlapping communities at once. Someone writing about how Bees are Capitalists can target their article at the communities that most overlap with its content (and with the author's means and write-access of course). Members of a community around beekeeping can organically discover content and communities on Austrian economics relevant to them.
With Private groups publication happens only in the group and discovery is blocked on purpose.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ 104f6f7d:220bf499
2024-09-26 05:01:05
@ 104f6f7d:220bf499
2024-09-26 05:01:05“He is free to make the wrong choice, but not free to succeed with it. He is free to evade reality, he is free to unfocus his mind and stumble blindly down any road he pleases, but not free to avoid the abyss he refuses to see.” - Ayn Rand
-
 @ a6e6a54b:8aca70c6
2024-09-26 04:41:21
@ a6e6a54b:8aca70c6
2024-09-26 04:41:21Outline
- Introduction.
- Setting the Ground with Definitions: UFO, UAP and The Phenomenon.
- About the Author: Luis Elizondo.
- Skeptical Approach.
- Non-Skeptical Approach.
- Spiritual-Metaphysical Component of UAP.
- Worldview Frameworks.
- Making Sense of UAP.
- The Stickiness of The Phenomenon.
- Possibilities for UAP.
- Spiritual-Metaphysical Beings.
- Human Nature.
- UAP Intentions.
- Psyop Hypothesis.
- Conclusions.
- References.
From Lights in the Sky to the Fallen
Expanding the Conversation from Imminent by Luis Elizondo
### 1. Introduction
Man’s mind, once stretched by a new idea, never regains its original dimensions. -Oliver Wendell Holmes.
During the past few years, there has been a resurgence of interest in the UFO-UAP topic. If you have been paying attention, you know by now that the phenomenon is real: there has been an acknowledgment of what people have been saying for years. However, if you are not aware of the current state of affairs, you might need to catch up. Imminent by Luis Elizondo [1] summarizes the latest events and his role in them. I think this book is not for UAP beginners, and I still consider myself as one. For this reason, it was not the book I was expecting, but it was the book I needed to challenge my approach to this topic. I had to make a mental shift in order to think about this issue more broadly. I will elaborate more on the challenges I faced later.
Luis “Lue” Elizondo explains his role as the Head of AATIP (Advanced Aerospace Threat Identification Program) run by the Pentagon and why he resigned due to the secrecy. As you can imagine, it is very difficult to make sense of someone else’s experiences, especially when they also involve the phenomenon. From my perspective, the book brings to the forefront yet another layer of this mystery —the spiritual and metaphysical component of UAP—, which is hard to process (it certainly was for me). I initially planned to write a review of the book, but I have decided instead that I will continue the conversation that Lue started, specifically about this aspect of UAP.
Keep in mind that whether you believe they live among us or think it is all nonsense, you may already have a strong bias that confirms your beliefs and dismisses any new information. This is part of what makes this topic so strange—most people seem to fall into one of two categories: either fully invested or completely indifferent. In my experience, the most common nuanced opinion among those who have not delved deeply into the subject but still want to appear open-minded is: “Of course, there are aliens somewhere in the universe, but it is ridiculous to think they have already visited us.” However, if you look closely at the discussions over the past few years, people are not necessarily talking about aliens visiting Earth—that is just one possibility being considered. I think claiming that aliens exist somewhere but have not shown up yet, and probably never will, is a comfort zone stance.
Furthermore, I am not inclined to convince anyone that this topic is relevant. But, if you already think that transparency is worth your time, then let’s think about the puzzle together!
Notes: 1. I think you should read the book, but if you prefer a summary and review of the key points made by Lue, I recommend watching Richard Dolan’s video: https://www.youtube.com/watch?v=uazfN6CqUeQ. 2. I have been careful with the quotes I am sharing here. Having listened to several hours of Lue’s interviews and podcasts, I have only included quotes he has publicly discussed. 3.
2. Setting the Ground with Definitions: UFO, UAP and The Phenomenon
I want clarify the meanings of UFO, UAP and the phenomenon, as I understand them:
- UFO: Unidentified Flying Object. This is a well-known acronym, often associated with flying saucers. It carries a lot of stigma, taboo, and conspiracy theories. Because of the recent surge of interest in the topic, the term "UFO" is not as commonly used anymore; instead, most people now refer to UAP. Additionally, the term UFO does not encompass the full range of the phenomenon.
-
UAP: Unidentified Anomalous Phenomena[^1]. It was previously defined as Unidentified Aerial Phenomena, but the phenomenon is not only aerial; it is transmedium (moving through air, space, and water—USO refers to Unidentified Submerged Object), and possibly transdimensional. Therefore, “anomalous” is a more accurate word, as it better captures the broader nature of the phenomenon.
-
The Phenomenon: This is the core of the issue and what we are trying to understand. The way that I see it, the phenomenon involves the interaction[^2] between humans and a non-human intelligence, which may be more advanced than us. The elements of interaction include:
Objects: These are observed in the sky, in the ocean, or coming from outer space. Objects can also be inserted into the human body. Examples include crafts, lights, and drone-like objects. These objects may appear tangible or not.
Entities or Beings: These are sometimes seen near or inside the objects, or on their own. They may communicate messages through unusual means. Their origin is uncertain—whether material or metaphysical in nature.
To summarize:
From a human perspective, the interaction with the phenomenon can be both material—occurring through devices, human senses, and visible changes in the body with biological effects—and psychological. Even more puzzling is that the phenomenon may enclose what some refer to as paranormal activity[^3].
Whatever the phenomenon is, it seems to have both material and non-material components. So, when we talk about evidence (photos, videos, vehicles, etc.) we might only be seeing one side of the coin, not the whole picture. I am being very deliberate in using the terms material and non-material because I am referring to the materialistic interpretation of the universe. I will expand more about this later.
[^1]: As for the word "phenomena," I do not think it is necessary to use "UAPs" to refer to the plural form. However, it is very common to see “UAPs” used everywhere. I will just stick with "UAP" in this discussion. [^2]: If they are seen or detected, that counts as interaction. When I mentioned earlier that some people say that “life exists somewhere else in the universe”, they are missing the point. The life forms that might exist elsewhere, which we do not yet know about, are not interacting with humans. [^3]: Some suggest that a subset of what we call paranormal activity can be caused or related to the phenomenon. Therefore, in the end, certain instances of paranormal activity could have a material explanation.
3. About the Author: Luis Elizondo
Luis Elizondo was recruited as a senior intelligence officer to help establish counterintelligence and security for the Advanced Aerospace Weapons System Applications Program (AAWSAP), which later became the Advanced Aerospace Threat Identification Program (AATIP). This program was focused on “unconventional technologies” (p. 6), “unusual phenomena” and investigated unidentified aircraft, specifically ones that seem to display beyond-next-generation technology and capabilities—what we now call unidentified anomalous phenomena, or UAP, or what were long referred to as UFOs (p. 8).
Some interesting details discussed at the podcast Theories of Everything with Curt Jaimungal [2] include: * Lue still keeps his security clearance. * Lue’s book went through a year-long review process by the Pentagon, resulting in certain parts being redacted.
Due to these factors, some speculate that he could be a disinformation agent. However, I do not agree with this notion, as other whistleblowers[^4] have come forward and support some of Lue’s claims. Additionally, Lue’s coming out appears to have caused an internal struggle within the Pentagon. It is very confusing to say the least.
[^4]: Lue does not view himself as a whistleblower but rather as a “patriot”. The fact that he retains his security clearance and continues to work as a government consultant makes people wonder who is really behind this disclosure movement. He has stated that: I would never in a million years violate my security oath. The damage inflicted by people such as Bradley (now Chelsea) Manning and, later, Edward Snowden arguably did more harm than good. Yes, the truth got out, but people lost their lives, and intelligence was compromised in the process (p. 193).
In my opinion, the most important claim made by Lue is the following: Unidentified craft with beyond-next-generation technology—including the ability to move in ways that defy our knowledge of physics and to do so within air, water, and space—have been operating with complete impunity all over the world since at least World War II. These crafts are not made by humans. Humanity is in fact not the only intelligent life in the universe, and not the alpha species… While there are valid reasons for secrecy around some aspects of UAP, I do not think humanity should be kept in the dark about the fundamental fact that we are not the only intelligent life in the universe. The United States government and other major governments have decided its citizens do not have a right to know, but I could not disagree more. You might be thinking this all sounds crazy. I’m not saying it doesn’t sound crazy, I’m saying that it’s real (pp. 1-2).
4. Skeptical Approach
In seeking truth you have to get both sides of a story. -Walter Cronkite.
Before sharing my opinions, assuming that the claims made by Lue and others are true, I need to outline some of the reasons for skepticism about the information being presented (in his book and in general during this disclosure process):
-
Lack of evidence: Lue has not provided concrete evidence, only his personal testimony. The Pentagon denies his claims.
-
Quality of evidence: The evidence that is presented is often of poor quality: blurry pictures and out of context videos that could be anything.
- Lue Elizondo’s Credentials: Right after the release of the book, there was considerable debate on #UFOTwitter regarding his position at AATIP.
- Government secrecy: Many think that it is impossible for a government to keep a big secret like this one from the public for so many years. They argue that the cover-up and secrecy are just conspiracy theories.
- Persistent Claims of Imminent Disclosure: Ufologists keep claiming, for decades, that disclosure is just about to happen any day now.
- Questionable Sources: A lot of the reported encounters come from people who might be unstable, seeking attention, or trying to scam others. Even those who seem genuine might be misinterpreting what they experienced.
5. Non-Skeptical Approach
The eye sees only what the mind is prepared to comprehend. -Henri Bergson.
The goal here is not to focus on the skeptic view. I am well aware that one can just say “Show me the evidence”, and move on if no one points to anything convincing and irrefutable. Also, given the fact that there are many other relevant issues affecting our daily life—like inflation, climate change, geopolitical instability, wars, and surveillance— dedicating mental energy to the UAP issue seems like a waste of time. It is totally reasonable to set this discussion aside due to other priorities.
However, I think it is unfair to dismiss the UAP issue as unscientific, nonsense and full of fraudsters (and there are definitely some of those) without spending a decent amount of time trying to understand what it is really about before criticizing it. Ridiculing a subject you do not know much about and do not understand is not scientific. In my opinion, one of the best critics in this area is Dr. Michael Shermer^5. He is a well-known skeptic with a deep knowledge of various UFO cases, has read a vast amount of information and talked to experiencers and witnesses. I recommend following his work.
In the previous section, I mentioned that some people think it is impossible for a government to keep a big secret[^6] like this for so long. I agree with that perspective and it seems that whistleblowers are starting to come forward. Not just one, but several whistleblowers with military backgrounds have been sharing their stories. It is up for you to decide how trustworthy you think they are. They have appeared in interviews, podcasts and some have even testified before the US Congress. While it is possible that they could all be lying or working together, I am going to assume for now that this is not the case so I can focus on the information they are providing.
[^6]: Some people believe that if there was anything significant to the UAP issue, we would have seen it revealed in Wikileaks by now. Interestingly, the “Podesta emails” include exchanges between Tom DeLonge and John Podesta, both of whom are mentioned in the book because of their interest in the topic.
Sometimes it is important to state the obvious: if something is engaging humanity, we do not need any government to tell us whether it is real or not. As Dr. Avi Loeb^7, Head of the Galileo Project^8, puts it: The sky and oceans are not classified and we can survey them ourselves [3]. People all around the world have been sharing their experiences on this topic for years. Sure, some of these people might be fraudsters, attention seekers, or simply confused, but others might be recounting genuine experiences of events that truly happened to them (even if we do not agree on their nature). That is why the testimonies of whistleblowers who have encountered unusual phenomena during their military service are very significant. Their credibility and training to identify anomalies while staying objective make their accounts worth considering.
There are also people who have had more intriguing encounters with the phenomenon, often referred to as experiencers[^9]. If you’re a good listener, you might have heard some unusual stories from people you know, and you might even know someone who falls into this category. For those who might be unaware, experiencers do exist, and many of them choose to stay quiet. As Dr. Garry Nolan^10, Executive Director of the Sol Foundation^11, points out: I think that what [ridiculing] does is a disservice to people who come forward with stories because they have a double trauma, they have the trauma of seeing something they do not understand and doesn’t fit with their worldview, and then they have the trauma of everyone making fun of them [4]. [^9]: I think this term was originally reserved for abductees, but recently, I have heard it used more broadly to refer to anyone who has had an experience related to the phenomenon. So, I’ll use “experiencers” in this broader context.
6. Spiritual-Metaphysical Component of UAP
It is not the answer that enlightens but the question. -Eugène Ionesco.
Worldview Frameworks
To ensure we are all on the same page, let’s take a moment to discuss Materialism, which is the predominant worldview among scientists and philosophers for explaining the nature of reality.
Materialism holds that the universe is entirely physical and governed by the laws of physics.
Reductive Materialism refers to the notion that all mental states—such as emotions, beliefs, perceptions, desires—can be reduced to physical phenomena, hence, mental states correspond to physical states. Most Materialists identify with Reductive Materialism.
Eliminative Materialism takes a step further by suggesting that mental phenomena do not exist at all.
Mental phenomena is an interesting case of study because it seems to be something different. However, most scientists argue that mental states can be explained through materialistic means, suggesting, there is no need to postulate another substance[^12] or property. Nevertheless, consciousness does not seem to be reconciled in a materialistic way due to its subjective nature and we still lack a clear definition of it. This is one of science's greatest mysteries, sparking extensive debate among philosophers, psychologists, and neurologists. In recent decades, computer scientists have also joined the conversation, due to the advances in Artificial Intelligence. I mention this because, as we explore the unknown characteristics of the phenomenon later, some have proposed that moving beyond a materialistic interpretation might be necessary, especially since the phenomenon seems to interact directly with human consciousness.
[^12]: Cartesian dualism divides the world in two parts: the physical and the mental, leading us to the mind-body problem—how does the interaction occur? We have shifted toward a form of monism, assuming that the world is only made of physical stuff (materialism), thus dismissing the mind-body problem, by claiming that the mind is material (reductionism). However, phenomenal consciousness—the realm of subjective experiences or qualia—seems to escape materialism, drawing us back to reconsider dualism and other flavors of it. This scientific challenge has been famously formulated as the Hard Problem of Consciousness by the philosopher Dr. David Chalmers.
Professor Dr. Mark Harris, physicist and theologian, in his essay Faith and physics states that: Physics is widely said to have a unique ability to shine light on physical reality at its most fundamental level. But in order to do so, physicists must make many assumptions. Indeed, the widespread assumption that physics is the most fundamental of the natural sciences, and that all others relate to it, is a consequence of reductionism, a metaphysical belief which can’t itself be established empirically in any direct way. Moreover, whether theorists or experimentalists, most physicists assume a form of realism –in spite of the fact that quantum physics has led to various anti-realist challenges– and a strong belief in the uniformity of nature, that physical reality is systematic, regular and patterned everywhere, and that these patterns may be understood rationally (the idea that is often expressed as the ‘laws of nature/physics’). This requires reliance on physical models to explain or summarise observations. A model is effectively a scientific metaphor, or an analogy, a way of explaining something we don’t understand in terms of something we do… The next assumption is that the uniform patterns we think we see in nature, which we try to describe using models, are universal. This means that we can eliminate local variables. For instance, in an experiment we discard the vast array of data we observe which are not universally systematic in favour of those (usually much sparser) data that are. Note that this means that we inevitably bring theoretical expectations to the lab: we can’t perform an experiment without having a pre-conceived theoretical framework already in place. This is often summarised by the famous phrase of N. R. Hanson that, ‘All data are theory-laden’. In other words, our observations come with theoretical baggage which already goes some way towards interpreting them [5].
Hence, the scientific lenses through which we understand reality are also grounded in suppositions or metaphysical beliefs because we cannot prove: materialism, realism (reality exists independent of the observer), determinism and reductionism, and that all reality can be understood by rational means. These notions certainly help us effectively interpret, understand and predict the physical world we are familiar with. There is a common belief that if something appears to be outside this worldview, it is either because: 1) We have not yet discovered the scientific explanation for it, or 2) It simply does not exist. I find the first possibility compelling, as we should indeed strive to understand the world around us. However, if we encounter phenomena that truly[^13]defy scientific explanation and challenge our established notions of reality (such as the concept of God), dismissing them as non-existent might reflect a personal bias or attachment to a specific worldview rather than an objective search for truth. I do not think that we should just abandon ourselves to all possible explanations every chance we get, but if after a thorough examination of the issue following the scientific method we remain puzzled, maybe, it is time to consider alternative perspectives.
[^13]: We cannot be sure about this.
Making Sense of UAP
Once you find true knowledge, ignorance is no longer an option. And if the knowledge you find is unusual then strange becomes a way of life. -Thomas Campbell.
The UAP issue challenges our scientific understanding in two significant ways:
1. Behavior of UAP: The behavior of UAP do not align with our current understanding of physics. This discrepancy leads many to speculate that we might be encountering intelligence and technology far more advanced than our own. This idea often implies that these phenomena could originate from a more technologically advanced civilization, potentially from somewhere else in the universe. In this regard, Lue mentions the 6 observables that should be explained (p. 156): * Instantaneous acceleration. * Hypersonic velocity. * Low observability. * Transmedium travel. * Antigravity. * Biological effects. *
2. Interaction with Humans: The way experiencers describe their interactions with UAP could challenge our materialistic worldview. This aspect introduces what I refer to as the spiritual-metaphysical component.
When I used to think about the UAP issue, I never felt the need to consider anything beyond science. I was comfortable sticking to a materialistic interpretation of the world (although I do not subscribe to it as the ultimate explanation of reality), and this was reflected in my approach to the phenomenon—I would just ignore anything metaphysical. I was aware of some of the claims but they seemed too overwhelming to process. I also thought that once we understood ‘the observables’, we would be able to explain the rest. While I have not completely changed my perspective on how to study this topic, I am now open to the idea that we need to explore the spiritual-metaphysical side in parallel.
As I was reading and Lue mentioned Robert Bigelow^14 in the first few pages, I thought to myself “Oh no, please don’t go there…” But sure enough, he did touch on the paranormal aspects later in the book. I was disappointed and felt he might be making a mistake: if he wanted to draw attention to this topic from a broader audience, focusing only on concrete data—such as sensor readings, the capabilities of the crafts, and how they seem to defy our understanding of physics—would be more effective. Introducing the more unusual aspects of the topic might turn off physicists and the scientific community, potentially leading them to dismiss the discussion.
To be fair, Lue does not imply that the phenomenon cannot be explained materialistically and it is spiritual in nature. In fact, he references Arthur C. Clarke’s idea that “any sufficiently advanced technology is indistinguishable from magic”, and he appears frustrated with the attitude of some Christian fundamentalists in government regarding this topic. But I will address this in more detail later.
I believe that Lue is intentional with his choice of words and the information he presents as he retains his security clearance. Early in the book, he mentions: Over time, my colleagues and I gained insight into how these mysterious UAP operate (p. 2). From this, I concluded: * He is signaling to a certain group. The book is not meant for beginners looking for a general overview of the UAP issue. * The spiritual-metaphysical aspect of the phenomenon is so significant that it cannot be ignored. * He may be an experiencer himself (he refers to personal experiences), and by acknowledging them, he is validating others, encouraging them to come forward.
Now that the spiritual-metaphysical part of this issue was brought front and center, I had to confront it as well, even though I had been mentally resisting it.
Remote Viewing and Orbs
Lue dedicates a whole chapter to remote viewing: Recruits were trained to spy upon enemies, but not in the usual way. Stargate trained “supersoldiers” to spy on hard targets using their psychic gifts. No, I am not kidding, this was an official US government program. They called the highly controversial technique “remote viewing.” The program, pioneered at Stanford University in the late 1960s, was led by none other than Hal Puthoff, whom I met at the dinner meeting I described earlier. Hal had been a Stanford University researcher and an employee of the NSA when he and his colleague Russell Targ were approached by the CIA and told that Russia had a remote-viewing program. The US needed to catch up and beat their efforts. That’s how it all started. Extrasensory perception had won over supporters in government who were initially dubious, then shocked that the technique worked. No one understood the mechanism. The CIA didn’t care why it worked; the only thing that mattered was that it did (p. 33). This whole story is really captivating but I was under the impression that it was unnecessary for the reader who is only interested to learn about UAP.
It turns out that Lue connects his involvement in AATIP to some unusual incidents that were occurring to him, his family and colleagues. He explains that they started seeing orbs in their homes: I was shocked to find that a lot of my colleagues and I began experiencing firsthand some of these orbs at our homes...The object behaved as if guided by some intelligence. It parked itself in the air, then drifted off down the hall before disappearing entirely (p. 68).
For those of you who do not know about orbs this is how he describes them: One of the most common types of UAP that are often reported is what we call orbs, which are small, luminous balls of light or, in some cases, smooth and metallic spheres. This is nothing new. In World War II, orbs were reported regularly in and around Allied and Axis aircraft, so much so that they were nicknamed “foo fighters” (p. 67). The orbs have been reported: by commercial pilots or military pilots or by eyewitnesses on the ground, particularly around military test ranges and sensitive US military facilities. This is not just a military phenomenon. Now, with the pervasiveness of home security systems and advancements in cell phone cameras, private civilians are capturing these orbs, just like the military is (p. 67). At this point, I was quite surprised because I remembered being part of a conversation with some colleagues in an academic setting where they expressed how much they would like to study orbs. I had no idea what orbs were, and I had never heard about them before, let alone their potential connection to UAP. Reading that chapter made a lot of things from that old conversation click into place. I wish I could go back and ask more questions about orbs, but they sounded too esoteric for my taste back then, and I was not in the right mindset to show genuine curiosity.
There is another interesting point he makes about orbs: The classification of these orbs really varies quite a bit. There are different colors and sizes; some of the colors reported were white, yellow, blue, red, and green. Reports I have seen suggested the blue orbs in particular had a very negative biological consequence, meaning if you got close to one of these, you could expect to be injured (p. 67). This example highlights that the phenomenon is not entirely harmless.
The way I see it, the connection between remote viewing and orbs in the book (not that these two are necessarily related) is that they might both be some kind of surveillance mechanism and ways to collect intel (this much information we have with remote viewing in a military context). This raises interesting questions about the nature of both remote viewing and orbs, as we venture into the blurry area between physics and metaphysics. I was under the impression that remote viewing was debunked, but Lue says that it works and is still used by the CIA, which does not care why it works but just that it does. What is going on here?
Stickiness of The Phenomenon
At the beginning of Lue’s involvement in UAP related work, he was warned that: “You should be prepared for the possibility that some of that strangeness will impact your personal life. These portfolios are sticky” (p. 12). Later, he linked this initial warning to his experience with orbs. I had heard about the Hitchhiker^15 effect but it took me a while to make the connection.
In a particularly eye-opening section of the conversation about Imminent in the podcast hosted by Post Disclosure World, the guests Christopher Sharp and James Iandoli, clearly highlight the concept of stickiness: If you engage with the phenomenon the phenomenon engages back. They raise an intriguing argument against widespread disclosure or confirmation of UAPs: There is this idea that we should not disclose because if we disclose that’s going to open a door for the phenomena to start engaging us in a much more proactive and unambiguous way. Do we want to all wake up at 3 am and see green orbs in our bedroom like Lue Elizondo and his family experience?[6]. Isn’t this a fascinating question?
There does seem to be a reactive aspect to the phenomenon. Personally, I lean towards the idea of transparency. After all, many of us have wondered whether we are alone in the universe and if human intelligence is the highest form. While the stickiness of the phenomenon might be a consequence of this new knowledge, we would eventually learn how to manage it. However, it is easier said than done. No one wants to live in fear, and this reactive part of the phenomenon appears to exacerbate that emotion. Additionally, in times of collective anxiety, there is always the risk of powers emerging “for our protection”—as Winston Churchill famously said, “Never let a good crisis go to waste.”
On the other hand, how deeply do you need to engage with the topic for it to become sticky? I am not sure. I have not had any experience myself.
I have noticed a common pattern among those who have opened up to me about their experiences: they often express confusion, shame, and fear. Many of them wish to forget what happened to them entirely. None of the experiences shared so far have been described as positive or exciting. But I recognize I cannot draw broad conclusions.
Possibilities for UAP
We sometimes get all the information but we refuse to get the message. -Cullen Hightower.
This classification is where things start to get even stranger. Physicist Dr. Harold Puthoff (mentioned several times by Lue), in his paper titled “Ultraterrestrial Models”, published in the Journal of Cosmology, states: It is currently unknown whether the phenomenon is exclusively extraterrestrial, extradimensional, crypto-terrestrial, demonic/djinn, proto/ancient human, time-travelers, etc., or some combination or mutation of any or all of these. However, it appears highly likely that the phenomenon per se is not constituted exclusively of members of the current human population [7]. At this point, I do not even want to speculate on what we are dealing with. The current information available to the public makes it almost impossible to even guess.
Professor Dr. Kevin Knuth[^16], physicist and member of the Advisory Board of the Sol Foundation, in his podcast appearance with the Scientific Coalition for UAP studies shares his thoughts to the very interesting question: How do you empirically study something where the very definition of just kind of a question mark, we don’t know what it is, it’s a phenomenon, it’s a thing, it's an object in the traditional sense at all? [Answer]: The first thing we need to do is to develop some kind of taxonomy. We need to come up with a way to classify things whether it's based on appearance, behavior and situation… We are faced with the difficulty in that there is a stigma attached to one of the hypotheses of what some of these things might be: the extraterrestrial hypothesis, which to me I don’t actually see very unlikely anymore, I think that’s actually very probable. But once you develop some kind of taxonomy then you can start to tease apart what you’re looking at and what you’re trying to study. These things aren’t clearly not all alien spacecraft: some of them are weather balloons, atmospheric phenomena that we don’t know anything about, pictures of birds…. It’s a very interesting and complicated problem, there is a lot to be discovered here. They are not just one thing… I’ll sometimes joke, I’m only interested in the ones that are craft, you cannot always tell which ones are craft and which ones aren’t, it’s not that simple…. We’re in a position where we really don’t know much at all and it really is smart to keep all the hypotheses on the table: the natural phenomena, the craft phenomena, the extraterrestrial hypothesis, the ultraterrestrial hypothesis, time travelers (from the past and future). There’s a lot of possibilities and there could be several of these hypotheses being true, which can be confounding and it'll be difficult to sort things out [8].
[^16]: https://www.albany.edu/physics/faculty/kevin-knuth https://thesolfoundation.org/people/
I know I mentioned things were getting weird, but now they are about to get even weirder. Lue recounts a conversation that left him stunned: “Lue, you know we already know what these things are, right?” …“It’s demonic,” he said to me. “There is no reason we should be looking into this. We already know what they are and where they come from. They are deceivers. Demons.” I couldn’t believe what I was hearing. This was a senior intelligence official putting his religious beliefs ahead of national security. (p. 84, 85). I guess you are not disappointed by how bizarre things have become with this twist.
I was not entirely surprised by this interpretation. I agree with Lue that a senior officer’s religious beliefs should not be more important than national security. The real question is whether this officer arrived at this conclusion purely based on his religious beliefs, or if there is additional information that is being withheld from the public and from special agents like Lue, who were investigating this topic from within the government.
Spiritual-Metaphysical Beings
Believe those who are seeking truth. Doubt those who find it. -André Gide.
Tucker Carlson shared his views, and it is worth noting his perspective because of his significant influence on public discourse. In this conversation he appears with another important public figure, Joe Rogan. Also, what Carlson says is how I expect many people to react and interpret the nature of the entities associated with the phenomenon.
Carlson says: They are spiritual beings, it’s a binary, they are either team good or team bad… The template that you’re using to understand this is, science fiction or an advanced race of beings from somewhere else but the template that every other society before us has used is the spiritual one. There is a whole world that we can’t see that acts on people, the supernatural world, it’s acting on us all the time for good and bad. Every society has thought this before ours, in fact, every society in all recorded history has thought that until, I'll be specific, August 1945 when we dropped the atom bombs in Hiroshima and Nagasaki, and all of the sudden the West is just officially secular, we’re God, there is no God but and that’s the world we have grown up. But, that’s an anomaly, no one else has ever thought that… Once you discard your very recent assumptions about how the world works, well, that kind of seems like the obvious explanation [9]. I applaud Carlson for openly talking about this, especially bringing up the spiritual beings interpretation. However, amidst the confusion, we should apply caution when listening to people who emphatically tell us with certainty what they are.
On the other hand, Dr. Avi Loeb expresses his stance on this discussion: Shawn asked whether I believe that UAPs have a spiritual component. I explained that spirituality or consciousness are likely an emergent phenomenon of complex systems, like the human brain and advanced AI systems. Their behavior is difficult to predict because they have a large number of degrees of freedom and are influenced by input from uncontrolled environments. Whether there are intelligent UAPs remains to be documented by the Galileo Project. If such UAPs exist, I would add psychologists to our research team, because they are trained to deal with intelligent systems [3].
We can analyze the nature of these beings from different angles: 1. Non-Materialistic Point of View: I have not gone into a deep level of study of the UAP beings —commonly known as aliens—but I have heard people talk about these entities. They seem to be embodied although their appearances vary. When they interact with humans, some people report both physical and psychological effects, such as body marks, paralysis, telepathic communication, missing time, memory loss, and fear. This does not suggest they are intrinsically spiritual beings, such as angels and demons (the fallen ones) from the Bible. These entities seem to have a dual nature. But one could argue that angels and demons are spiritual in essence and they also have the ability to materialize, and this observation would lead us into theological territory. This shows how easy things get messy when trying to relate something unknown with something else that we think we know. 2. Materialistic Point of View: Let’s forget all the spiritual stuff and demons, nothing of that exists, and even if it does, these entities could just be material. In this case I would say pretty much what Lue keeps repeating “any sufficiently advanced technology is indistinguishable from magic”. Maybe these creatures have learned how to access our consciousness in a way that we do not even think it is possible.
In my opinion, we are dealing with a mix of different types of entities although I cannot say anything about their ontology. I would not rule out the spiritual beings, demons, or dual nature entities interpretation. For those who have experienced encounters with these beings, sharing their experiences is crucial so we can gather enough data to better understand and categorize them[^17]. But unfortunately, there is always the fear of ridicule. We need to understand what is and isn’t part of the phenomenon. I would also like to hear what other religions and traditions think.
[^17]: Esoteric groups have already developed some taxonomy, but the information they have gathered falls into the category of revelation (by the beings themselves) rather than an accumulation of data.
Reality is merely an illusion, albeit a very persistent one. -Albert Einstein.
For example, Dr. John E. Mack^18, a renowned psychiatrist from Harvard who tragically passed away in a car accident in 2004, made significant contributions to the field. I first encountered his work through a documentary about the Ariel School UFO landing. Dr. Mack was deeply interested in speaking with the children who witnessed this traumatic event and sought to understand it. His book, Abduction, explores UFO abductions and encounters with these beings. It is important to point out that he was also a well-regarded expert on nightmares.
In an interview, journalist Ralph Blumenthal^19, who wrote a biography about Dr. Mack titled The Believer, noted that Dr. Mack's research highlighted fundamental differences between experiences of the "old hag syndrome" and UFO abductions. The former often involves reports of an evil presence that sits on the bed and causes suffocation, while abductees typically describe being given information telepathically and undergoing medical procedures.
Although these accounts are disturbing, they provide valuable insights by helping us distinguish between similar but distinct experiences. However, the question of the ontology of these beings and their origins still remains unresolved. Blumenthal adds: What are we to draw from this? Well, first of all, there is a whole kind of anomalous experiences that seem to operate in a world that we do not recognize, another reality, that penetrates our world, as John Mack said, somehow, in ways we can’t explain, we have a clear idea of reality, we think we do; reality is what you can see, smell, taste, and touch, knock on the table, feel it... So maybe there are other dimensions, aspects to the universe that we don’t understand” [10]. In addition, Professor Dr. Garry Nolan, whom I mentioned earlier, says the following: It’s interesting, religions have been dealing with extra dimensions and non-human intelligences for centuries: angels and demons, the spirits of the forest, the jinn of the Quran, etc. Where is heaven and hell? It’s another dimension. Are heaven and hell even in the same dimension? Are they different places altogether? Religion struggled with these ideas and the human mind can already encompass the possibility that they exist and had done so since the most primitive of men. That’s amazing to me [4].
This naturally leads us to ask: Are these realities and dimensions “real”? And more importantly, What do we understand by “real”?
About experiencers, Lue expresses that: In the end, abductees report feeling that these beings did not care one way or another if they lived or died. Many experiencers reported feeling completely vulnerable, helpless, and afraid. As a former special agent, if a witness reported being whisked away against their will, I would consider that an act of kidnapping, a federal crime. And if the witness said they were touched against their will, I would consider that assault, yet another crime in human terms (p. 173). I totally agree with Lue on his opinion right here.
I now think it is a mistake to rely solely on physicists, astronomers, and engineers for answers, yet that is where most people tend to focus. The phenomenon we are dealing with is not just about lights in the sky, mysterious crafts, or extraterrestrial beings. The problem is far more complex, and narrowing the scope to only the physical aspects limits our understanding. To fully grasp what is happening, we need insights from a much broader range of perspectives—psychologists, psychiatrists, philosophers, theologians, heads of different religions, anthropologists, and historians. Each of these fields offers a piece of the puzzle, whether it is understanding human consciousness, exploring ancient interpretations of similar phenomena, or delving into the spiritual implications. It is only by bringing together all of these viewpoints that we can begin to form a more complete picture of the UAP phenomenon.
Human Nature
When the student is ready, the teacher will appear. Ancient Buddhist proverb.
I also believe that we need to start looking inwards and understand our true nature—what makes us humans.
- *Materialistic Point of View: We have the poetic words of the physicist Sean Carroll, PhD: I want to argue that, though we are part of a universe that runs according to impersonal underlying laws, we nevertheless matter. This isn’t a scientific question — there isn’t data we can collect by doing experiments that could possibly measure the extent to which a life matters. It is at heart a philosophical problem, one that demands that we discard the way that we’ve been thinking about our lives and their meaning for thousands of years. By the old way of thinking, human life couldn’t possibly be meaningful if we are “just” collections of atoms moving around in accordance with the laws of physics. That’s exactly what we are, but it is not the only way of thinking about what we are. We are collections of atoms, operating independently of any immaterial spirits or influences, and we are thinking and feeling people who bring meaning into existence by the way we live our lives* [11].
- Non-Materialistic Point of View: Professor Mattias Desmet, PhD, expert on the Theory of Mass Formation expresses that: Young science, too, starts from a belief that the object being studied can be fully understood by means of logical reasoning. Facts are logical—how could they not be? However, the further the logical analysis of the phenomenon under investigation is carried, the more clearly one sees the emergence of a core that is intrinsically illogical and inaccessible to the human mind. And just like with a child, that moment gives rise to an awareness of the relativity of all logic as well as a heightened sensitivity to forms of language that don’t aim to be logically understood but lead to a more direct affinity, to resonance with the object (poetry, mysticism, etc.). In the same way, man also has to come to know himself as a psychological being, as a confluence of subjective experiences, thoughts, feelings, especially as they arise in relations with others. The ability to sense one’s own experience and to put it into words and to express it in relation to another is what constitutes the core of our existence as human beings… we exist as human beings when we can give something of our individuality to another through full speech—a kind of speaking in which something of the human being we are vibrates and resonates. It is through the art of full speech—which is the art learned, for example, in psychoanalytic therapy—that we are able to realize a real connection with others and the world around us (without thereby losing ourselves) [12].
If we truly understand who we are and how it feels to relate to each other in our human form, I think that we would be able to recognize what is not us and perhaps discern what kind of entity or intelligence is trying to engage with us. However, if we do not fully grasp our own humanity and the ways in which we are interconnected, how can we even begin to comprehend a non-human intelligence that might be more advanced than we are?
One of the most intriguing insights we have so far about the phenomenon is the possibility that this intelligence is reactive. This is one of the reasons why we need to start talking about our experiences with it. We may be part of a transformational process without even realizing it, and I also believe that this intelligence is being affected by our interaction—it is a two-way street. This is, of course, speculation.
For example, in the Christian worldview, Jesus was a non-human intelligence that transfigured His divinity when He adopted human form, altering His essence through His humanity and interactions with people. He is now both God and human. So, how are we planning to influence this other intelligence?
This process of understanding who we are and our purpose in the universe is entirely subjective, and/or revealed. This is a different kind of knowledge, —more like wisdom—, and, in my opinion, it cannot come from science. How could it? This is why I am now more inclined to consider the phenomenon from perspectives beyond the scientific. The wisdom and knowledge humanity has acquired over thousands of years will be crucial when addressing this subject.
7. UAP Intentions
Lue begins his book by discussing the Colares UAP case in Brazil during the 1970s. If you research about what happened you will see that the phenomenon engaged with humans in a very harmful way. This contradicts the belief held by some in the UFO community that these entities are here to help humanity. This belief is often linked to numerous reports of sightings near nuclear weapon sites and facilities, with the suggestion that they are trying to warn us about the dangers of nuclear technology. Moreover, Lue also talks about a case in 1982 in Ukraine: UAP flew over Byelo Air Base in the former Ukrainian Soviet Socialist Republic. Seconds later, the launch sequence for the base’s missiles switched on without any human ever entering the launch codes. Operators frantically rushed to shut the system down but could not. When the launch sequence reached its very last rung, it shut down of its own accord (p. 54). Moreover, he says that: “Adults taking matches out of the hands of children,” some say. That’s a nice hopeful thought, but reality has proven us incorrect. At no time have UAP stopped our nuclear ambitions. As examples: They did not stop us from dropping atomic bombs on Japan. UAP did not stop us from making the leap from atomic to nuclear weapons. UAP did not stop the disasters at Three Mile Island, Chernobyl, or Fukushima. UAP did not stop the proliferation of nuclear technology from getting into the hands of more nations. Most recently, UAP have not interfered with North Korean, Indian, or Pakistani nuclear testing. And switching on nuclear missiles? That is not so benevolent (pp. 54-55).
Also, Lue on multiple occasions throughout the book expresses his concerns about national security: Humanity acts as if no one else is watching us, like we are alone. But a more advanced intelligent life is likely observing us. Humanity needs to become more aware of our place in the universe and the potential consequences of our actions. Regardless of their motivation, if this tech is cracked by another nation-state with bad intentions it will be an existential threat to our nation and the planet as a whole. Those are the urgent national security concerns and urgent concerns for humanity at large (pp. 168-169).
Regarding national security, I do not believe we have enough information to assign benevolent or malevolent intentions to UAP yet. Additionally, if this is a non-human intelligence, we cannot necessarily think about it in terms of human-like intentions or motivations aimed at accomplishing a specific purpose.
That being said, I appreciate the fact that someone who was in charge of studying UAP from a national security perspective, shares his concerns and makes evaluations based on his background and experience. UAP should be closely monitored. I believe that the US Congress has already briefed on this matter specifically, and they are requesting yearly reports.
8. Psyop Hypothesis
To test a first-rate intelligence is the ability to hold two opposed ideas in the mind at the same time, and still retain the ability to function. F. Scott Fitzgerald.
We are facing a trust crisis.
A frequent argument among UAP skeptics is that the recent surge of interest in this topic could be part of a psyop (psychological operation), with the ultimate goal of instilling fear in the population to justify increased surveillance and control. This is a valid point, I have been thinking about this a lot. While I personally believe that the phenomenon is real and engaging with humans, I could also see a scenario where the phenomenon could be exploited—weaponized, even—with half-truths to serve nefarious purposes.
The pressing question then becomes: How can we discern what is real from manipulation?
After reflecting on the book, now I believe that bringing up the spiritual-metaphysical component of the phenomenon was a clever move. At the beginning I thought it was a total mistake, but I have changed my mind. If the phenomenon is used by a government or an elite group for control and manipulation, they would need a common narrative that influences people’s behavior and convinces them that they know and possess ‘the truth’. This approach might work for the material component of the phenomenon but clearly not for the spiritual-metaphysical side. What could be more diverse than people’s spiritual and metaphysical beliefs (and non-beliefs)?
If we start talking to one another about the strange experiences related to UAP, asking for opinions about their meaning and nature, and even disagreeing on interpretations, then two things could happen: 1) Through the process of open discourse, we are more likely to approach the truth, and 2) It becomes much harder for a powerful group to control the narrative. Even if such a group possesses hard evidence and attempts to use certain elements of truth to steer the public toward a specific outcome, open discussion could counteract that influence.
Regarding evidence, there is always an element of trust involved. Imagine that we are finally shown, by “official channels”, a vehicle displaying non-human capabilities: What would convince you that it is “real” and not fabricated to provoke a reaction? Who would need to validate the evidence for you to believe it? The government? Which government (don’t they all have secret programs)? Independent scientists? Scientists affiliated with institutions or organizations? And what kind of institutions or organizations are truly trustworthy?
I believe that a government or elite group can never have control of what is most intimate to a human: their subjective experiences and the meaning they attach to them which is an individual process. This is why we should not allow a particular faith, tradition, or worldview to dominate or lead the discourse related to the spiritual-metaphysical aspects of the phenomenon. Even if you believe there is no such component, you should still have a voice. This is what we, the people, can control—because we are not the ones trying to reverse-engineer retrieved craft in our backyard, but we may have an intuition about the kind of intelligence we might be dealing with. Therefore, we need to start having these conversations, open to all hypotheses, so when disclosure happens (if it does), whether real or fake, it will not catch us off guard.
9. Conclusions
The opposite of a correct statement is a false statement. The opposite of a profound truth may well be another profound truth. -Niels Bohr.
Lue was a human who found himself in a very strange position. His decision to come forward has been complicated to digest because he is not the usual whistleblower we are used to seeing. Unlike many, he still retains his security clearance and speaks carefully, only about what is not classified. This unique position makes Lue different from typical whistleblowers. Even for those who are not interested in the UAP topic, Lue argues that it is still worth considering how taxpayer money is being used and whether resources are being properly allocated to investigate these sightings and encounters. Whether or not you are personally invested in this subject, the implications for national security and public accountability are real concerns that deserve attention. By coming forward, Lue has opened up a wide range of discussions, not only about the nature of the UAP phenomenon itself but also about the role of transparency in government and the public’s right to know.
Personally I find this topic fascinating. There are many angles to explore and here I chose to focus on the dual nature of the phenomenon, with special attention to the spiritual-metaphysical component. I understand this can also be frightening given all the possibilities we are faced with when considering the phenomenon’s nature. I have faith in humanity, and whatever we find on the other side, I am sure we can handle it. Moreover, during this time of many questions and very few answers, we should learn to embrace the discomfort of not knowing.
Despite the fear of the unknown, there is also the potential for great discoveries. If we are to fully engage with the phenomenon, we have to address not just the external mystery, but also the internal one: it seems like the phenomenon interacts with us on a deeply personal and psychological level, challenging our established ideas about the nature of reality. Understanding ourselves might be a crucial step toward understanding whatever this phenomenon represents because we are the ones extracting meaning. Maybe it is not just about figuring out what the phenomenon is, but why it engages us in the way it does—and that starts with a deeper exploration of our own human experience.
If this topic resonates with you, there are many ways to keep the conversation going: ask others for their thoughts, share your own experiences, and explore the multiple perspectives surrounding the issue. The more we talk openly about UAPs, the harder it will be for any narrative—governmental or otherwise—to control our reactions. This is not just about the phenomenon; it is about our collective right to transparency, understanding, and the courage to face the unknown together as a species.
There are many topics I would have liked to cover, and I know I am only scratching the surface of what has been discussed for years—but at last, I have arrived.
10. References
[1] Elizondo, Luis. Imminent: Inside the Pentagon's Hunt for UFOs: the Former Head of the Program Responsible for Investigating UAPs Reveals Profound Secrets (p. 19). HarperCollins. Kindle Edition.
[2] Pentagon’s UFO investigator breaks two year silence:
[3] For the Love of the Unfamiliar by Avi Loeb: https://avi-loeb.medium.com/for-the-love-of-the-unfamiliar-9d9a7612bd8e
[4] Garry Nolan on UFOs, Neil deGrasse Tyson, and Eric Weinstein:
[5] Pritchard, Duncan; Harris, Mark. Philosophy, Science and Religion for Everyone (pp. 17-18). Taylor and Francis. Kindle Edition.
[6] Elizondo’s Imminent Round Table:
[7] Ultraterrestrial Models by H. E. Puthoff, Ph.D.: https://thejournalofcosmology.com/Puthoff.pdf
[8] Kevin Knuth on Studying Scientific Anomalies, Simulating Star Systems, & Possible UAP Origins:
[9] When Tucker Carlson Changed His Mind on Aliens:
[10]: The Harvard Psychiatrist Obsessed with Alien Abduction:
[11]Existential Therapy from the Universe: Physicist Sean Carroll on How Poetic Naturalism Illuminates Our Human Search for Meaning: https://www.themarginalian.org/2016/05/31/sean-carroll-the-big-picture/
[12] Desmet, Mattias. The Psychology of Totalitarianism (p. 223, pp. 225-226). Chelsea Green Publishing. Kindle Edition.
-
 @ df478568:2a951e67
2024-09-26 02:11:59
@ df478568:2a951e67
2024-09-26 02:11:59One way to mitigate the risk of a Password breach is to stop using passwords and start using randomly generated passphrases. A passphrase is a combination of words. A good example can be found on the EFF dice words website. For most applications, they suggest using 6 words randomly chosen by rolling 5 dice. Each word has a corresponding combination of 5 numbers from. 1-6. In other words, they are generated by dice(That's D6 dice for all the nerds out there)Here is an example of a strong passphrase that is easy to memorize.
pacifist-area-unfiled-demeaning-rundown-oblivion
It would take a computer about 200 ocrodecillion years to brute force this passphrase so it is highly unlikely to get cracked before the sun goes all supernova.
Here's how it works: - Step 1: roll 5 dice
- Step 2: Find the coresponding word: In this example, our dice rolls are 2-6-1-3-1
- Step 3: Find the coresponding word in the eff dice roll list:
- Repeat this 6 times.
- Step 4: Write this down on paper. I like waterproof paper made by Rite in the Rain. This is not an affiliate link. I don't make any money off of them. I just like them because they are waterproof and easy to hide. You can also etch the password on military grade steel.
- Step 5: Use this password password for your passphrase manager like Vaultwarden.
Each character is really a binary number so your passphrase is just a big random number to the computer. This number is hashed with SHA256 or something. If you're really smart, you can calculate this with a pencil and paper, but I use computers and calculators. Xorbin is one of the easier tools, but this can be done in bash using the hash library too. Be aware, typing an actual passphrase you use into any website might be a phishing scam. Don't try to use this for anything you are worried about losing.
Here is the hash we get from the 6 words above:
a41c5312e2957462f9f81597088c1c943c11e864b462cddf49dc55145707b69a
Sweet, Sweet Salt
. If you don't want to hassle with running your own server, bitwarden does the same thing. Last I checked, they only charged $10.00 a year for the premium plan, but it might have changed. They both allow you to: - Create passwords and passphrases. - Add special characters, numbers and capital letters. - Check if your password was pwned.
For example, "password1" was breached 3,339,722 times. If this is your password, you might want to change it.
"Blink-182" was breached 1,810 times. This password would meet most policies. It has a capital letter, special character and a 3 numbers. Where did we go wrong? Blink 182 is a popular punk band. Of course 1,810 people and one hacker thought of this. Think your safe if you change a number? Think again. "Blink-183" was pwned 16 times. Changing the numbers are also not a good idea due to possible dictionary attacks.
I run my VaultWarden using Start9 and it is also available on Umbrel and Yunohost
Let's try our six word passphrase we created earlier.
"pacifist-area-unfiled-demeaning-rundown-oblivion"
This password was not found in any breaches. It should be safe to use. Well...except I put it on the clear net, but you get the idea.
Other Risks
Okay, we have a strong password, but that's not the only threat. A bad guy could trick us with a spear phishing attack or someone installs a keylogger onto our computer. Now what do we do? Be prepared like a boyscout. This is where it's a good idea to use 2fa or two-factor authentication. I like Aegis There are others like Google Authenticator or physical devices like YubiKeys, but I like Aegis becauseyou can create backups. YubiKeys were cool, but this happened and I'm not sure if that's been resolved yet.
Securing your login with 2fa means one password us an insufficient amount of information to gain access to your account. The attacker would need to pwn the password and your phone to gain access. While not impossible, this is much more difficult.
Here's a Dad joke created by the Duck Duck Go's free AI chatbot.
`Why did the password go to therapy?
Because it was feeling a little "insecure".`
✌️ https://marcleon.work/pgp
862,887
-
 @ 502ab02a:a2860397
2024-09-26 00:11:24
@ 502ab02a:a2860397
2024-09-26 00:11:24
เมื่อกรดซิตริก (citric acid) ที่จริงแล้วไม่ได้ทำมาจากผลไม้
เราเรียนรู้กันมาเราค้นกูเกิลกันมา ว่ากรดซิตริกนั้นเป็นกรดธรรมชาติ มีอยู่ในผลไม้รสเปรี้ยวต่างๆ แล้วมันก็ถูกนำมาใช้เป็นสารป้องกันการบูดเน่าจากธรรมชาติ โดยกรดซีตริกเกิดขึ้นครั้งแรกนั้นคือเมื่อปีค.ศ. 1784 โดยแยกออกมาจากน้ำมะนาว แต่ในปัจจุบัน กรดซิตริกไม่ใช่สูตรนี้ครับ
ที่ผมมีข้อมูลอยู่นั้น สามารถให้คำตอบได้ว่า
นั่นเพราะว่าราวๆปี 1917 บริษัท Pfizer ได้จ้างนักเคมีอาหารชื่อ เจมส์ เคอรี่ James Currie ที่มีแนวคิดฉีกทุกกรอบว่า จะทำการผลิตกรดซิตริก โดยไม่ใช้มะนาวแม้แต่ลูกเดียว คุณเคอรี่ ค้นพบว่าเชื้อราสีดำที่ชื่อว่า Aspergillus niger สามารถเปลี่ยนน้ำตาล ให้เป็นกรดซิตริกได้ ทำให้ Pfizer ออกจำหน่ายสินค้าตัวนี้ในปี 1919 เป็นต้นมา
ในปัจจุบัน กว่า 99% ของกรดซิตริกที่มีขายนั้นเราเรียกว่า manufactured citric acid (MCA) นั่นคือ มันไม่ใช่ของธรรมชาตินั่นเองครับ คุ้นๆไหม ที่ผมเคยบอกเรื่องสารให้ความหวาน ไม่ว่าจะ อิริททริทอล แอลลูโลส สารพัดโอสๆ และอื่นๆอีกมากมาย เราจะได้รับการขายของว่า มีอยู่ในธรรมชาติ บลา บลา บลา โดยที่จริงแล้วที่เราได้มาเป็นกระสอบนั้นไม่ได้มาจากธรรมชาติ แต่มาจากการเร่งให้เกิดปริมาณมากๆเพื่อเอามาขาย ซึ่งไม่เป็นธรรมชาติโดยสิ้นเชิง
MCA นี่ก็เช่นกันครับ เชื้อรา Aspergillus niger ซึ่งส่วนใหญ่ผลิตจากเชื้อราสายพันธุ์ที่ผ่านการดัดแปลงพันธุกรรม (GMO) เอาไปหมักน้ำตาล โดยทั่วไปจะเลี้ยงมันด้วย high fructose corn syrup ที่มีอยู่มากมายและราคาถูกๆ
ก็แน่นอนครับว่าเวลาเราเห็นคำว่ากรดซิตริก เราก็จะนึกถึงรสเปรี้ยวๆ รูปมะนาวสวยๆ cute cute แต่จริงๆแล้วในโรงงานผลิตมันตรงกันข้ามเลยครับ ในการผลิตเราจะได้เห็น ของเหลวหนืดๆเหนียวๆ มีตะกอนสีเข้มๆ ที่เกิดจากการหมักในถังสเตนเลส ข้างในนั้นเป็นส่วนผสมของ เชื้อรา น้ำตาลอุตสาหกรรมโคตรๆ( hyper-refined sugars) บางครั้งก็มีการยิงรังสีแม่เหล็กไฟฟ้าเพื่อให้ความร้อนด้วย
ได้รับการรับรองว่าเป็นออแกนิก ???
และเชื่อหรือไม่ว่า มันได้รับการรับรองว่าเป็นออแกนิก แม้กรดซิตริกจะไม่ได้มาจากแหล่งธรรมชาติแท้จริงเพราะผลิตผ่านกระบวนการหมักที่ใช้เชื้อราดำ GMO (Aspergillus niger GMO) ซึ่งมักใช้ข้าวโพดที่ผ่านการดัดแปลงพันธุกรรม (GMO) เป็นวัตถุดิบในการผลิต ด้วยเหตุผล 2 ข้อคือ
- มาตรฐานการรับรองที่แตกต่างกัน: องค์กรรับรองออร์แกนิกทั่วโลกมีหลายพันองค์กร แต่ละองค์กรมีเกณฑ์ที่แตกต่างกันในเรื่องคุณภาพและความเข้มงวดในการตรวจสอบแหล่งที่มาของวัตถุดิบ โดยบางแห่งอาจใช้แบบสอบถาม ถามผู้ผลิตว่าใช้กรดซิตริกที่มีส่วนผสมของ GMO หรือไม่
- การจัดประเภทว่าเป็น Non-GMO: ผู้ผลิตกรดซิตริกจากเชื้อราดำมักจะระบุว่ากรดซิตริกที่ผลิตได้นั้นเป็น Non-GMO เนื่องจากผลผลิตสุดท้ายไม่มีสารพันธุกรรมจาก GMO ที่สามารถตรวจพบได้ ถึงแม้ว่ากระบวนการผลิตจะเริ่มจากวัตถุดิบที่มาจากข้าวโพด GMO หรือเชื้อราที่ถูกดัดแปลงพันธุกรรมโดยการใช้รังสีความร้อน (thermo-radiation) หรือการดัดแปลง DNA ของเชื้อรานั้นก็ตาม
ถึงกระบวนการผลิตกรดซิตริกนี้จะไม่เป็นธรรมชาติและใช้วัตถุดิบที่เกี่ยวข้องกับ GMO แต่มันสามารถได้รับการรับรองออร์แกนิกได้ เนื่องจากไม่มีการตรวจพบสารพันธุกรรมจาก GMO ในผลิตภัณฑ์สุดท้ายที่จะจำหน่าย ทำให้กรดซิตริกนี้สามารถเข้าสู่ตลาดอาหารออร์แกนิกได้โดยไม่ผิดกฎ และหน่วยงานที่ให้การรับรองใบเซอร์ ออแกนิก เจ้าไหนที่ต้องการให้ใช้ MCA ได้นี่ก็เพียงระบุคำว่า "ไม่สามารถตรวจจับ DNA ที่มีแหล่งกำเนิดจาก GMO ได้" ไว้ในเอกสารก็จะทำให้แบรนด์สินค้าได้รับการรับรอง ออแกนิกได้สบายๆ
ได้รับสถานะ GRAS??
เนื่องจากกรดซิตริกมีการผลิตขึ้นมาใช้ก่อนที่สำนักงานคณะกรรมการอาหารและยา (FDA) จะจัดตั้งขึ้น กรดซิตริกจึงได้รับสถานะ GRAS (หมวด “โดยทั่วไปถือว่าปลอดภัย”) แม้ว่าจะยังไม่มีการทดสอบทางวิทยาศาสตร์ใดๆ เกี่ยวกับการบริโภคในมนุษย์ในระยะยาวก็ตาม เจ๋งเนอะ
ผลข้างเคียงจากรา Aspergillus niger
ในปี ค.ศ. 2016 มีการผลิต MCA จำนวน 2.3 ล้านตัน โดยส่วนใหญ่ผลิตในประเทศจีน และประมาณ 70% ใช้เป็นสารเติมแต่งอาหารหรือเครื่องดื่ม ยังไม่มีการศึกษาวิจัยทางวิทยาศาสตร์ใดๆ ที่ดำเนินการเพื่อประเมินความปลอดภัยของ MCA เมื่อรับประทานเข้าไปในปริมาณมากและเป็นเวลานาน (อีกแล้ว เหมือนเดิมเป๊ะ)
เชื้อรา Aspergillus nigerเกี่ยวข้องกับปัญหาการอักเสบของระบบต่างๆ รวมถึงระบบทางเดินหายใจ ระบบทางเดินอาหาร ระบบประสาท และกล้ามเนื้อและโครงกระดูก ดังนั้นหาก เชื้อรา Aspergillus niger เกิดมีเศษเล็กเศษน้อย ดันแทรกซึมเข้าไปในผลิตภัณฑ์กรดซิตริกสำเร็จรูป ผู้บริโภคผลิตภัณฑ์ที่มีกรดซิตริกนี้อาจกินสารพิษที่ก่อให้เกิดการอักเสบนี้เข้าไป แม้จะผ่านกระบวนการฆ่าเชื้อด้วยความร้อนสูงแล้วก็ตาม
นี่เป็นอีกเหตุผลที่แยม Passion of Orange ที่ผมทำนั้นไม่ใส่ citric acid ครับ
แหม่ยังมีอีกหลายเรื่องนะที่จะเล่าให้ฟังเกี่ยวกับอุตสาหกรรมอาหาร อย่างที่บอกนะครับ อะไรที่มั่นใจในวันนี้ อย่าเพิ่งมั่นใจ อาจจะจริงเราเห็นอยู่ เผื่อใจไว้ที่ยังไม่เห็น
PirateKeto #กูต้องรู้มั๊ย #ฉลาก3รู้ #siamstr
-
 @ a03b38f8:2c7ce1f0
2024-09-25 23:36:29
@ a03b38f8:2c7ce1f0
2024-09-25 23:36:29FINANCIAL PRIVACY: Card Transactions, Cash, Monero, Sending Bitcoin Privately
Privacy is foundational for protecting freedom. Abuses to human rights and efforts to control people often depend on governments knowing details of a person’s life, this is why financial privacy is so important. Financial activity reveals details about a person’s relationships, profession, religion, political beliefs, geo location, and lots more.
Much has been said about data privacy concerns around social media, but financial data is also detrimental when abused or in the hands of the wrong persons.
A Person can speak about their humble life in a small town but their Financial data from the banks would reveal that they are actually a Billionaire.
Financial data reveals many areas of a person’s life, so it’s more likely to reveal who someone truly is, even if an individual does not want those details revealed to others.
From where you travel to, what you donate to, financial activity can paint a detailed picture of a person’s life, ensuring financial privacy means being able to have control over who gets to see that picture and purposes. You may not have something to hide but remember privacy is really about having control over your life.
Governments around the World Use Financial data to control people and activities within its jurisdiction. This is where financial privacy can act as a limit on governmental power. Where a lack of privacy is likely to lead to an abuse of that power.
Government policy on financial privacy is complex and often demands access to personal data for law enforcement and National Security purposes. Although often we see governments use that same financial data to hunt and halt activities that do not align with the policies of its agenda.
We believe any access at all should be reasonable and in accordance with privacy and human rights.
Almost all financial institution privacy standards prohibit the disclosure of client information to third parties without consent or an accepted criminal complaint, it is a conditional agreement because it has some limitations; this limitation or restriction in most cases is not clearly explained to clients but it is an ambiguous statement that further explains the limits of the financial institution, meaning the Central Bank which controls a country’s entire financial activities of all Financial institutions in a country does have the power to access all financial data as it demands, thereby limiting privacy.
CARD TRANSACIONS
Data Security and privacy are crucial in payment transactions in the digital era, protecting personal and financial information not only stops unlawful access but also increases customer trust and confidence.
Card transactions comes with a lot of risk and dangers such as Identity theft, cyber criminals use stolen data from digital payment platforms to impersonate individuals and access their financial accounts, make unauthorized purchases, or setup new accounts in order to illegally transfer funds or perform fraudulent financial transactions without owners consent.
Identity theft can have lasting effects on a victim’s financial health and credit status. Additionally phishing attacks are prevalent. Hackers use this technique to deceive users into providing their personal and payment information (Data) under the guise of legitimate request.
It is advisable for cards that you choose to carry around on your person be held in a RFID blocking wallet. Beyond physical security any cards that you use online or in stores should have spending limits and have no access to large amounts of funds you may have to prevent or limit the impact of fraud. For privacy protections consider virtual privacy cards or reloadable debit cards.
Lastly, do not use PayPal. They are a privacy nightmare and there is an entire cottage industry on the dark web selling stolen accounts.
CASH TRANSACTIONS
Cash is king. For a long time cash has been used as the primary form of payment and cash transactions have excellent privacy properties and it is widely accepted in most countries.
Cash transactions provides a high degree of privacy in payments, it also slows the growing information asymmetry between consumers and companies as well as between citizens and public authorities.
Bank notes and coins reduce your digital footprints compared to an electronic payment. Cash remains one of the most effective tools for financial privacy in a world increasingly dominated by digital payments. It offers true anonymity, leaving no digital trail or record of the transaction, making it impossible for third parties—such as governments, corporations, or hackers—to track your spending habits. Unlike card payments or online transfers, cash transactions don't reveal your identity, location, or spending patterns, providing a level of confidentiality that digital methods simply cannot match.
Physical cash works without registers of cash holders and transaction, when paying with bank notes and coins, it is only the buyer and seller who are aware of this: What is bought, how much, when, when by whom and at what.
While cash has its limitations in today’s digital society, it remains a valuable option for those who prioritize privacy. By using cash whenever possible, especially for sensitive or personal purchases, The use of cash gives room for maintenance and control over your financial data, it also help protect from unwanted surveillance, and safeguard your financial autonomy. Ultimately, cash is still king when it comes to preserving your financial privacy.
MONERO (XMR)
Monero is a decentralized cryptocurrency designed with a strong emphasis on privacy, security, stealth address and unlinkability, it is abbreviated XMR.
Monero’s transactions are completely anonymous and confidential by default making it one of the most privacy centric digital currencies available today.
Key features of Monero
·Untraceable Transactions: Monero uses advanced cryptographic techniques, such as Ring Signatures, which combine your transaction with others, making it impossible to identify the actual sender. This feature ensures that transactions cannot be traced back to any single individual.
·StealthAddresses: When you send Monero, the recipient’s address is never publicly recorded on the blockchain. Instead, a one-time address is generated for each transaction, ensuring the recipient's identity remains private.
·ConfidentialTransactions: Monero employs Ring Confidential Transactions (Ring CT) to hide the amount of XMR being transferred. This means the transaction amounts are kept entirely private, further enhancing confidentiality.
·Fungibility: Because Monero transactions are private, every XMR coin is indistinguishable from another. This makes Monero a truly fungible currency, meaning no coin carries a traceable history or stigma, unlike Bitcoin, where some coins can be "tainted" based on their transaction history.
Despite Monero’s popularity as a primary focused cryptocurrency, Monero faces criticism and challenges. The Monero community development team frequently updates the protocol to improve privacy and resist surveillance attempts, this is beneficial for security, meaning users and miners must regularly update software, this can be inconvenient and lead to potential forks if consensus is not reached within the community.
Many governments and financial institutions view Monero as a threat because of its untraceable nature, as a result this has posed some challenges making exchanges to delisted Monero in order to comply with anti-money laundering and know your customer (KYC) regulations.
SENDING BITCOIN PRIVATELY:
Bitcoin is often perceived as an anonymous payment network but in reality Bitcoin is the most transparent payment network in the world. At the same time, Bitcoin can provide acceptable levels of privacy when used correctly. All bitcoin transactions are public, traceable and permanently stored on the Bitcoin network, Bitcoin addresses are the only information used to define its allocations and history.
In ensuring privacy while Bitcoin transactions are performed it is advisable to generate a new address each time a payment is received. The incomplete privacy on transactions will lead to the Fungibility of the scripts, which could affect the stability of Bitcoin as a long-lived currency system, Bitcoin system addresses privacy by hiding the address of transactions via hash functions but the hash value is obviously unique, If the addresses and traders are bounded unconsciously through activities by attackers, the anonymity of the entire system will disappear.
Suppose that the Bitcoin system is connected to the payment of an e-commerce platform, the strong computing power can search the complete data of your incomes and outcomes, which makes everything about money exposed to the public.
Let’s say; You are paid salary via bitcoins and you spend those coins in the supermarket, the plaintext of the account of your income and outcome will inevitably be utilized by businesses to access the benefits like charge you higher prices or target you with advertisement.
-
 @ ae1008d2:a166d760
2024-09-25 21:52:49
@ ae1008d2:a166d760
2024-09-25 21:52:49I wanted to share this PDF on Nostr. Original post: Block ~862,844 September 25th, 2024 Original link Original PDF 👇Click the link below to view as original PDF on YakiHonne or Satellite.Earth👇
-
 @ eac63075:b4988b48
2024-09-25 20:28:17
@ eac63075:b4988b48
2024-09-25 20:28:17🤖 Baseado na explicação de Gerard Aithen para o Morning Crypto
Nos últimos anos, o Bitcoin se consolidou como a criptomoeda de referência, trazendo inovação e mudança para o cenário econômico global. Apesar de sua notoriedade, a tecnologia por trás do Bitcoin, especialmente em termos de escalabilidade e eficiência, ainda é um campo em constante evolução. Recentemente, um novo avanço tem gerado bastante discussão entre os entusiastas do mundo cripto: a BitVM2. Desenvolvida por Robin Linus, essa inovação promete transformar a maneira como as transações são processadas e verificadas no ecossistema do Bitcoin.
A BitVM2 está sendo apontada como uma revolução na forma como programas inteiros podem ser verificados dentro da blockchain, facilitando e tornando mais acessível a participação nas transações. Mas o que exatamente é essa nova tecnologia? Como ela funciona? E, acima de tudo, por que ela é tão importante para o futuro do Bitcoin?
Neste artigo, vamos explorar a BitVM2 em profundidade, analisando seu funcionamento, os benefícios que ela traz e suas implicações para o futuro da rede Bitcoin.
O Que é a BitVM2?
Imagine que a primeira versão da BitVM era como um quebra-cabeça gigante, onde cada peça precisava ser ajustada meticulosamente para que a transação fosse validada. Essa estrutura exigia muitas etapas e transações para garantir que tudo funcionasse corretamente, o que, claro, consumia tempo e recursos. A BitVM2 vem para mudar completamente esse cenário.
Com a BitVM2, todo esse processo se torna muito mais rápido e acessível. Agora, é como se um GPS eficiente tivesse sido instalado no lugar do velho mapa. O caminho está traçado, e tudo o que você precisa fazer é seguir as direções. A nova estrutura da BitVM2 utiliza criptografia avançada para transformar programas complexos em fragmentos menores, que podem ser verificados diretamente nas transações do Bitcoin. Em outras palavras, ela permite que contratos inteligentes e programas complexos rodem dentro da blockchain do Bitcoin, sem comprometer a segurança ou eficiência.
O principal benefício? Antes, um processo que exigia mais de 70 transações agora pode ser verificado com apenas três. Isso não apenas economiza tempo e recursos, mas também abre as portas para que mais pessoas possam participar e monitorar essas transações.
A Importância da Descentralização na BitVM2
Um dos pontos mais revolucionários da BitVM2 é que ela é completamente permissionless, ou seja, não precisa de permissão. Isso significa que qualquer pessoa pode verificar ou contestar uma transação. Antes, essa era uma tarefa restrita a operadores específicos dentro da rede. Agora, a verificação e contestação de transações suspeitas podem ser feitas por qualquer um, tornando o sistema mais democrático e transparente.
Essa descentralização aumenta a segurança da rede. Em vez de depender de um grupo centralizado de validadores, o sistema se torna autossustentável. A comunidade como um todo pode vigiar e garantir a integridade das transações, o que dificulta tentativas de fraudes ou manipulações.
Além disso, o novo design da BitVM2 foi pensado para ser compatível com a estrutura atual do Bitcoin, ou seja, não foi necessário fazer alterações no código base da criptomoeda. Isso garante que o Bitcoin continue funcionando como sempre, enquanto permite a introdução de novas funcionalidades. É como construir um novo andar em um prédio sem precisar mexer na estrutura do alicerce.
Rollups e a Eficiência das Transações no Bitcoin
Um dos temas mais discutidos na comunidade de criptomoedas nos últimos anos é a questão da escalabilidade. Conforme o Bitcoin ganha mais adoção, a rede fica mais sobrecarregada, o que pode aumentar o tempo e o custo das transações. A BitVM2 pode ajudar a resolver esse problema, especialmente quando falamos de rollups.
Rollups são soluções que permitem processar transações fora da blockchain principal, para depois consolidá-las em um único registro na blockchain do Bitcoin. Isso torna as transações mais rápidas e baratas, sem comprometer a segurança. A BitVM2 pode ser vista como uma espécie de ponte entre o Bitcoin e essa nova era de rollups, permitindo uma maior eficiência e abrindo espaço para que o Bitcoin continue evoluindo.
De forma simples, a BitVM2 garante que transações complexas possam ser processadas sem sobrecarregar a blockchain principal. Com isso, ela ajuda a diminuir as taxas e a aumentar a velocidade das transações, um avanço crucial para o futuro da criptomoeda.
O Papel dos Covenants no Bitcoin
Outro conceito-chave no desenvolvimento da BitVM2 é o uso dos Covenants. Para quem não está familiarizado, os Covenants são como pequenas promessas que os Bitcoins "fazem" durante as transações. Eles colocam condições específicas sobre como e onde os Bitcoins podem ser gastos. Isso adiciona uma camada extra de segurança e funcionalidade às transações, permitindo que os Bitcoins sejam gastos apenas sob determinadas circunstâncias.
Por exemplo, um Covenant pode especificar que os Bitcoins só podem ser transferidos para certos endereços ou que só podem ser liberados após determinado período de tempo. Esses contratos inteligentes tornam o Bitcoin ainda mais flexível e permitem a criação de soluções inovadoras dentro da rede.
Na BitVM2, os Covenants desempenham um papel importante na verificação das transações, garantindo que todas as regras sejam seguidas e que não haja brechas para fraudes ou manipulações. Isso amplia as possibilidades de uso do Bitcoin, permitindo que ele seja utilizado de formas que antes eram impensáveis.
BitVM2 e a Manipulação de Opinião Pública
Outro ponto que não podemos ignorar ao discutir as inovações tecnológicas no mundo das criptomoedas é a questão da manipulação de opinião pública. Bilionários e grandes empresas têm se posicionado como grandes influenciadores no cenário das criptomoedas. O caso de Elon Musk é um exemplo clássico, onde tweets e posicionamentos podem mudar drasticamente o valor de uma criptomoeda em questão de horas.
Com a BitVM2, no entanto, o poder de manipulação pode ser mitigado, uma vez que o sistema se torna mais descentralizado e aberto à participação de todos. A liberdade de contestar transações e a democratização do processo ajudam a garantir que o Bitcoin continue sendo uma moeda de todos, sem a influência de poucos.
Conclusão: Um Futuro Promissor para o Bitcoin
O lançamento da BitVM2 representa um salto importante para o futuro do Bitcoin. A capacidade de verificar transações complexas de forma rápida e acessível, aliada à descentralização e à possibilidade de uso dos rollups, promete tornar o Bitcoin mais eficiente e acessível para todos.
Mais do que uma simples atualização tecnológica, a BitVM2 traz à tona a discussão sobre liberdade digital, transparência e o papel das criptomoedas no futuro. É um avanço que, sem dúvida, será observado de perto pelos entusiastas e críticos da criptoeconomia.
O Bitcoin sempre foi visto como uma alternativa descentralizada ao sistema financeiro tradicional, e a BitVM2 parece reforçar essa visão. À medida que mais pessoas se envolvem e a tecnologia avança, o futuro das transações digitais parece mais promissor do que nunca. Vamos ficar de olho no que essa nova fase nos reserva e nas novas possibilidades que ela pode abrir.
***
-
 @ 44dc1c2d:31c74f0b
2024-09-25 20:15:13
@ 44dc1c2d:31c74f0b
2024-09-25 20:15:13Chef's notes
Last time I made this I subbed the tomato puréed with some blistered cherry tomatoes. Don't think I'll be using the purée going forward.
I prefer thighs so that's what I use for this but use whatever you want.
Adjust spices based on the size of your onions. If all you have is two massive onions maybe use one and a half onion or just up the amount of spices a little.
Details
- ⏲️ Prep time: ~10 min
- 🍳 Cook time: ~40 ish min
- 🍽️ Servings: 4
Ingredients
- 2 Onions
- 2 tbsp tomato purée
- 1/3 cup cashews
- 1.5 tsp Garam Masala
- 2 ish cloves of crushed garlic
- 1 tsp chili powder
- 1 tbsp lemon juice
- 1/4 tsb ground turmeric
- 1 tsb salt
- 1 tbsp plain yogurt
- 2 tbsp of your cooking oil or fat
- 1 tbsp Coriander (Cilantro) plus extra for garnish
- 1 tbsp sultanas (golden raisins)
- 1 lb of chicken cubed
- 6 oz of white button mushrooms
Directions
- Quarter the onions and put them in a food possessor for about a minute
- Add the tomatoes, nuts, garlic, Garam masala, chili powder, lemon juice, turmeric, salt, yogurt and blend for another minute tell its well mixed in.
- In a wok or a large pan heat your cooking oil and add the onion and spice mix in. Fry gently for around 2-ish minutes, stir frequently.
- Add the chicken, coriander, and raisins to the pan. Stir-fry for another minute or so.
- Add mushrooms and water. Bring to simmer and cover the pan cook for 10 min or until the chicken is 100% cooked through.
- Serve with plain rice and enjoy!
-
 @ 9262b5a5:2a89f8de
2024-09-25 19:30:54
@ 9262b5a5:2a89f8de
2024-09-25 19:30:54testing
-
 @ 9262b5a5:2a89f8de
2024-09-25 19:03:12
@ 9262b5a5:2a89f8de
2024-09-25 19:03:12https://image.nostr.build/c7e3732889827ab0a8e2064de5fa6992e37e035347b0c91d249cb8f312b47087.jpg I love Bitcoin. Let me get that out there first of all. I sincerely believe that Bitcoin has the power to change the way the world functions if we can grow adoption to a global scale. This obviously will take time as the gears of economic change grinds slowly. As of right now, people in the western countries don't really see the need for a sovereign politically neutral money that can't be inflated away. They simply don't have to deal with inflation on a regular basis like the rest of the world.
Citizens in western countries got a small taste of what real inflation looks like and guess what? They didn't like it one bit. Overall the last three and a half years you saw countless news stories about how bad inflation and how its making life for the average American or European more difficult.
Yes inflation does suck but look at countries like Argentina, Turkey, Zimbabwe or Venezuela. The people in these countries are suffering from excessive inflation on a regular basis! According to recent economic data Turkey experienced a decline in inflation from 61 percent to 51 percent in August. This is seen as a win in their book! Can you imagine this level of inflation in America? There would be riots in the streets!
Argentina's inflation rate is an astounding 236 percent over the last 12 months! As Bitcoiners we understand that the problem is the money itself. As long as governments have the ability to manipulate the money supply, they will. This is human nature at its finest. When you give a select few that kind of power it becomes irresistible and becomes a tool to control the masses. This shouldn't be a surprise to anyone to be honest.
What I find shocking is with all of this inflation globally no one is really looking around asking questions to why this is happening and looking for a way to escape this system. Are people really this lazy? Not to be mean but cmon. It seems to me that most people are perfectly fine bitching online about how hard it is to make ends meet or supporting their favored political party and wanting them to fix the problem they created. Newsflash to all the normies out there, its the GD political parties that caused inflation in the first place.
We literally have a solution that is staring them in the face, ready to go to replace the current debt based system that we are currently suffering through and no one wants to take the time to research it? Am I black pilled? No, am I realist, very much so. If 236 percent inflation in Argentina can't get them on a Bitcoin Standard immediately, we as a community have a long road ahead of us. Hyperbitcoinization isn't coming in 5 years. It isn't coming in 10 years. Hell it might not even happen in our lifetimes and we have to be ok with that.
So what is the best way to get more Bitcoin into the hands of the people, so they can see the true value of the digital monetary revolution that is Bitcoin. We need a trojan horse and that trojan horse is nostr.
Enter The Nostr Trojan Horse
https://image.nostr.build/5ffee418133ac80ba14b30abf0d5390b878f676cbf6332d67639f9384764da4c.jpg
It should be plain to see by now that the inflation or the number go up narrative alone isn't going to drive Bitcoin adoption. The reason for that is because people don't see the utility of Bitcoin. They see it as some esoteric digital funny money that drug dealers and terrorist use to do bad things.
The average Joe doesn't see how Bitcoin is helping dissidents on foreign countries fund their activism, escape oppressive regimes or simply earn a living. These stories are never told in the mainstream media because they don't want to highlight the fact that a non-state money can circumvent the status quo.
The best way to highlight these stories is to share it on social media, which again is controlled by mainstream gatekeeper such as Meta, Google and X. It is in their best interest to censor these stories or memory hole them out of existence which I suspect happens quite a bit without us even knowing. But the thing about censorship is that it slowly impacts everyone one by one until no one is allowed to say anything without the fear of being put in jail.
Think this can't happen in western democracies? It's happening already my friend! Take a look at the UK or Australia. Citizens their are being arrested over post made to social media. I sincerely believe that these two countries should be a proving ground for showing the value of nostr and Bitcoin.
Introducing the concept of a censorship resistant messaging protocol to them will go over well and once it is understood will grow like a wildfire because people innately understand that censorship is bad and will see the utility value of having the ability to speak freely again.
It is only a matter of time until they realize that they can monetize their speech and build a life using zaps aka Bitcoin.
Until people see the utility in the tools that lie before them, they will never pick them up and use them. It is really that simple. At the end of the day we are still kind of like cavemen. We only use tools when it makes life easier. Man made the wheel. We use it everyday because it has utility.
Bitcoin in the end will be the same way. Utility first, then mass adoption. Nostr is what will help people see the utility Bitcoin and from there sky is the limit. The best thing we can do as Bitcoiners is to encourage people to learn about nostr and show them how easy it is to use and to switch clients that suit their needs instead of being shoved into a one-size fits all solution on centralized platforms.
People like choices, and nostr is all about choice. The interoperability and thelack of need to give personal information to create an account are HUGE selling points that can be touched on. Go out and spread the good word about nostr!
Bitcoin #Nostr
-
 @ 6bae33c8:607272e8
2024-09-25 16:35:54
@ 6bae33c8:607272e8
2024-09-25 16:35:54I went 2-3 again last week to push the season record to 5-10, nearly drawing dead in the Circa Millions (though you can still win relatively big prizes for winning four-week stretches.)
I didn’t look at the lines yet, only my feel about the teams through three weeks.
Cowboys at Giants — seems like a get well game for Dallas. Probably win by 7-10, won’t be favored by nearly that much. Only chance for the Giants is to get those rushers after Prescott, but more likely the Dallas rush will crush a skittish Danny Dimes.
Saints at Falcons — I like the Falcons at -2.5 or better. Last week’s game was annoying though.
Bengals at Panthers — Get well game for Cincy. Good sell high on Panthers, but Dalton is not bad, and the Bengals defense is. Probably staying away.
Rams at Bears — Two shit teams. Probably Bears -2.5. Stay away. If anything leaning Rams.
Vikings at Packers — If Jordan Love is playing, Packers -2.5. Have to treat the Vikings as a serious contender now.
Jaguars at Texans — Jaguars are broken probably getting seven. Texans looked bad last week too. Both teams desperate in their own ways. Stay away.
Steelers at Colts — Anthony Richardson looks off, and this is not the get-well opponent. Steelers -3, stay away. If anything taking the ugly Colts.
Broncos at Jets — Jets by 7.5, think last week’s Broncos win was a fluke.
Eagles at Buccaneers — I’ll say pick ‘em. Leaning Bucs as buy-low.
Team at Cardinals — Jayden Daniels looked great, but I’m taking Cardinals up to 5.5
Patriots at 49ers — Probably 49ers -13 for me, real line maybe 10? Can’t play hide the QB forever, and this would be a tough assignment if Drake Maye plays.
Chiefs at Chargers — Depends on Herbert’s status. Can’t say. Chiefs are unwatchable with the dink, dunk and penalties in their favor.
Browns at Raiders — Two teams desperate to bounce back. I instinctively like the Raiders here, but feels like the Browns are the sharper side for some nagging reason.
Bills at Ravens — Imagine this line will be 2.5 or so. I’ll probably go with the Ravens who need it much more.
Titans at Dolphins — Two bad teams, no idea who will play QB for the Dolphins. Pass.
Seahawks at Lions — Imagine this line will be about 3.5. Probably lay the wood if I had to, but would be my fifth out of five if I use it.
-
 @ a03b38f8:2c7ce1f0
2024-09-25 16:11:17
@ a03b38f8:2c7ce1f0
2024-09-25 16:11:17PROTECT YOUR HOME (NETWORK)
This is actually a rather large topic depending on your needs and how far you are willing to go. I will most likely have to put out several posts on this topic. For today we will start at the very beginning and build from there.
This is going to be more of a beginners guide but that doesn't make it any less important. First you must get your home in order before you can do anything else. If bad actors get access to your network then they can use it for illegal things that will be tied to your IP address, use it to launch a bot for a DDoS attack, gain access to any of your home devices, or just hangout and watch you log into bank accounts or whatever.
I will be blunt, your home network sucks. It's slow and unsecure but we will be fixing that.
I. EVERYONE
- WHAT DO YOU HAVE?
Somewhere in your house you have either a phone cord or a cable coming out of the wall running to a box. Go find it. This is your modem, it "translates" the internet signal from your ISP to your house so you can use the internet.
Found it? Good. Now is there a cable coming from the modem to another box or do you just have one? This other box is your router, it is pretty common now that you will have a all in one modem, router, WIFI, etc. That's fine. Write down the model number of the router or all in one. Also there should be a sticker on the side with the administrator password (sometimes listed as access code) and maybe the WIFI password. Also look if the IP address is listed as well. You will need these for the next step.
- LOG IN
Go to your computer and fire up a web browser. Enter your routers IP address if it was listed, otherwise we are going to have to find your router's IP address.
In widows and Mac you can look under Network & Internet, scroll down to your internet connection and look for details or properties. Inside properties you are looking for something listed as default or gateway or IPv4 DNS Server. It will be a 192.168.X.X number.
Or you can open a command prompt and type: ipconfig /all
Or you can just do a internet search for your router model number IP.
You will know when you get the right one because a control screen for your router will pop up in the browser.
- UPDATE
First thing first check if there is any available updates. This could be it's own tab or listed under device or in diagnostics. If it asks you for a password use the one that was written on the side of the router. Install any available updates. Honestly they rarely update these things so if there is one then it must have been pretty needed.
- CHANGE THE LOCKS
You have to realize that this device is the front door between every internet device in your home and the outside wild internet. You are probably blasting WIFI signal all the way to the street. All someone has to do is connect to your WIFI and then they will have access to your router as well. The default administrator password for these mass produced ISP devices are not exactly secret. You can even find lists of them by brand. It is like locking your front door but leaving the key under the mat, not very secure.
Look in the settings and change the administrator password. Use your password manager to generate a 10 word passphrase. Change it to that and SAVE it in your password manager.
- RENAME AND CHANGE WIFI PASSWORD
In the settings change the default name of your network to something memorable. Do NOT use anything personal like your name, address, or router brand (Netgear or whatever). If you want to be cute you can use: Not Available, or Network Error or something like that.
Now change the WIFI password. Again use your password manager to generate a passphrase. You can cut it down to 6 words since you will probably be entering this one much more often. Be sure to SAVE it in your password manager.
- ADD A GUEST NETWORK
You don't just give your WIFI password to all the kids in the neighborhood that swing by to play with your kids or to your friends visiting do you? If so, STOP it. Setup a guest network. A guest network allows people to have WIFI access at your house without giving them access to the router. Yes I know we put a strong password on the router but it doesn't matter.
Setup a guest network with a easy password. If you have given this out to several people already that are coming back often you can name the guest network the old default name and use that default WIFI password. When friends and family come over their devices will have that name already saved and will connect automatically. This way you don't have to do the whole song and dance everytime someone comes over.
- CHANGE YOUR DNS SERVER
DNS is the Domain Name System. Remember the IP address we found earlier for the router? Every device connect to the internet has a unique IP address. Every server hosting a website, etc but luckily you don't have to remember 142.250.188.14, you can just go to Google.com
This works because behind the scenes your computer is checking with a DNS server to provide a human readable address instead of a bunch of numbers. The equivalent would be a phone book that gives you John Smith and not just a address somewhere.
There is a little bit more to it than that but you don't need to know all that in order to grasp the concept.
The default DNS in your router is probably the one provided by your ISP. Your ISP can see everything that pings against that DNS server and probably uses it to feed you ads. The DNS server provider impacts how a lot of your data is handled. It's speed, it's security, how it's logged, shared, and sold.
So change your DNS server. The default one your ISP gave you is shit. It will improve your speed and security but just remember that privacy and security are not the same thing. The Google Public DNS (8.8.8.8) is very secure and a good choice but as you can imagine the privacy is not really great. But not to worry, all the data they are collecting is anonymized ; )
Your best bet is to use your own DNS server with something like Pi Hole or Adguard home. Setting that up is a little bit beyond the scope of this article so I will cover it in greater detail in a future one. Until then Cloudflare (1.1.1.1) is probably your best choice until you run your own.
Now you have probably better privacy and security than most people with only these simple changes. Next steps would be to upgrade your hardware for faster internet, better firewall, more control, etc. Will detail in future drops.
Always Forward, GHOST
-
 @ 8d34bd24:414be32b
2024-09-25 14:41:11
@ 8d34bd24:414be32b
2024-09-25 14:41:11Also posted on substack
1 Thessalonians 5:17 tells us “pray without ceasing;”
You may be thinking, “I have responsibilities. How can I pray without ceasing? I can’t be on my knees praying without stopping. This can’t be what the Bible expects from us.”
Don’t worry, prayer doesn’t have to be a burden. It doesn’t have to be locking yourself in a room alone for hours on you knees on a cold, hard stone floor like the monks of the middle ages. Prayer is just what you need to help you on your next step to growing closer to Jesus.
Analogy of old married couple and believer with God
As believers, our prayer relationship with God should be like the way an old, loving couple talks. They don’t talk without stopping to do other things, but they are always talking and keeping the other person included in what they do and what they care about.
They also have lots of different kinds of conversation. Some are deep conversations that take an extended period of time. Some are brief comments about what is going on in their life. Some are pointing out something interesting or asking for help. Sometimes the words are just an acknowledgement of the other’s presence. Sometimes communications may be no more than a glance or a grunt, but it conveys so much because of how close they are.
Scheduled time
Just like the old married couple schedules a date night or other time together, there are times that we want to schedule time with God. It might be a group prayer meeting. It might be a time alone to discuss particular worries with God. This is usually an extended time to pray about something in particular. It may be scheduled regularly. It may be scheduled specifically based on circumstances.
To many people, this is what they think of when they think about being a prayer warrior, but the truth is, at least for most of us, this is the smallest portion of our prayer life.
Regular time
Just like an old married couple has times that they are regularly together and talking, such as first thing in the morning when they awake and say “Good morning!” or just talk about their plans for the day. Most couples regularly talk during meals together. These discussions might be about how the day is going or about plans for the future or about various common interests. Most couples also talk at least briefly at bed time. They know that almost every day they will talk during these periods.
In the same way, believers should have regular times that they talk to God. I think upon waking, at meals, and at bedtime are good times to pray regularly. That doesn’t mean that you always have to pray for extended periods . Most of these will probably be fairly short and the time allowed may vary from day to day.
Praying at these 5 times is handy because you wake up and go to bed every day and most people eat breakfast, lunch, and dinner every day. These events are reminders to pray. You may have other times like when you pick kids up at school, when you get in your car to drive, or nightly devotions before putting kids to bed. You might have other times that work for you because everyone’s life is a little different. Some of these may be solitary prayers, while others might include someone else, especially family members. Whatever the case, these are times that you usually pray every day. They are guaranteed times with God. They are times God can count on you and you can count on God.
With others
An old married couple usually doesn’t hang out only with each other. They also hang out and talk with friends and family. They will get together with some friends/family on regular occasions. They will get together with others on special occasions. This is a nice time of jointly conversing and helping each other.
Believers also are called to pray together.
They were continually devoting themselves to the apostles’ teaching and to fellowship, to the breaking of bread and to prayer. (Acts 2:42) {emphasis mine}
We may pray with a person or group. We may pray at church, a Bible study, or a prayer meeting. We may regularly meet with one or more people just to pray for our church, our country, and each other.
For 2-3 years I had a friend I would pray with once a week for about an hour. We were both very busy. We both homeschooled kids and had other responsibilities. We didn’t live near each other, so we prayed together on the phone. We made prayer together work, even when it wasn’t convenient, because it was important to us.
Depending on our life circumstances, we may pray with others more or less. (Singles usually have less opportunities to pray with others, while families always have each other to pray with.) Whether or not it happens every day, we are called to pray to God with other believers and for other believers.
Random discussion (Thanks, interests, & Concerns)
Random discussion normally should be the largest component of communications between a couple and between believers and God. These prayers are not planned or organized. They are a sign that we are including another in our daily lives because they are important to us.
Sometimes these prayers are a quick comment on what is happening in our lives. Sometimes these prayers are about a worry or concern. They can be a mention of something we find interesting or something we find beautiful. It may be a comment on something we learned or about us finally understanding something. Frequently they are prayers to say a quick “help” or “thank you.”
These little brief prayers shot up to God, usually while doing the normal activities of life, are just a sign that we find God important and want Him in our life. You may say, “Wow! That is a great view! You made beautiful mountains.” You may say, “I’m really struggling with this. Please help me do better.” You may say, “What is happening in the world is scary. Please help me to know what to do and help me to trust you in all things.” You might ask, “What am I supposed to say to this unbeliever to draw them to you?” or “How do I speak wisely to this person who is hurting?” We are including God in our lives and listening to Him because we want His opinion and guidance.
We may speak out loud or we may think our prayers silently where only God hears. We usually aren’t kneeling. We usually don’t have our hands folded, nor do we have our eyes closed.
If we are truly depending on God to guide our lives, these prayers should be a huge part of our lives. They should be sprinkled consistently through our day.
Cries for help
Part of the joy of a long and loving marriage is having someone to depend on when we are in need, whether sick, or tired, or sad, or frustrated, or physically unable to do something ourselves. We always have that other person to depend on and lean on.
And if one can overpower him who is alone, two can resist him. A cord of three strands is not quickly torn apart. (Ecclesiastes 4:12)
In the same way believers should lean on God to support them throughout their lives. I’ll admit that I used to only “bother God” with my really big concerns. I wasn’t comfortable asking Him for help with my little, day-to-day concerns, but that was pushing God away.
Unlike with a person who has a limited amount of time and energy, God can see and hear all prayers throughout all of history at the same time and not even break a sweat. We aren’t bothering God with our requests. We are honoring Him with our requests. He wants to be not only a part of our lives, but the leading part of our lives. When we ask for His help, His wisdom, His guidance, and His power, we are doing exactly what we should and we are growing our relationship with Him.
It is good to continually ask God for help, but that doesn’t mean we should ask for every petty desire. Our prayers shouldn’t be filled with requests for wealth, fame, and power. All prayers should include the same qualifier (even if not stated explicitly) Jesus used right before going to the cross, saying, “… yet not My will, but Yours be done.” (Luke 22:42b) We should be praying our problems and leaving the solution to Him. He frequently will answer in ways we never imagined (and frequently would never choose for ourselves), but these answers are always for our good.1
Conclusion
As you can see, praying continually is just a lifestyle. It is a way of including God in our lives. It is a way of showing we trust God fully. It is a way of serving God and being used by God.
In reality, praying continually isn’t as hard as it sounds. Like all habits, it just takes a little time to build the habit. Once prayer becomes a part of your life, it doesn’t feel like work, it just happens. It is as natural as talking to your best friend or spouse or parents or kids. You can’t imagine not talking to God continually.
I’ll end with these lyrics:
What a friend we have in Jesus\ All our sins and grieves to bear\ What a privilege it is to carry\ Everything to God in prayer
Have we trials and temptations\ Is there trouble anywhere\ Our precious Savior\ He is still our refuge\ Take it to the Lord in prayer
When we're weak and heavy laden\ Cumbered with a load of care\ We should never be discouraged\ When we take it to the Lord in prayer
Oh what peace we often forfeit\ Oh what needless pain we bear\ We should never be discouraged when we\ Take it to the Lord in prayer
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
FYI, If you are wondering what to say, this acrostic (ACTS) is a handy for outline for prayer:
-
A = Adoration -Praise God for who He is
-
C = Confession - Admit our sins and His righteous lordship
-
T = Thanks - Thank God for all He has done for us including our salvation
-
S = Supplication - Make requests from God for help and to supply our needs.
For more articles and to see all of my posts check out my Trust Jesus Substack and consider subscribing to avoid missing any posts.
-
-
 @ dc652bee:6154e7d0
2024-09-25 11:28:17
@ dc652bee:6154e7d0
2024-09-25 11:28:17🆘📢Exciting news for our community! We are thrilled to announce the Bybit bot airdrop, designed to enhance your trading experience. Don't miss out on this opportunity to elevate your game! 🚀💰 #BybitAirdrop 🌐 http://surgishop.lnkiy.in/Bybit_bot👈
-
 @ 13e63e99:25525c6a
2024-09-25 10:43:42
@ 13e63e99:25525c6a
2024-09-25 10:43:42
The Federal Reserve has announced a 50-basis-point reduction in the benchmark interest rate, officially initiating the first easing cycle in U.S. monetary policy since March 2020. This move aims to address potential weaknesses in the U.S. economy and labor market while further reducing inflation. Fed Chair Jerome Powell emphasized that current economic conditions are strong, and the rate cut is designed to sustain this momentum and enable a flexible response to changing conditions.
 Fed officials expect additional rate reductions for the remainder of the year, gradually lowering rates over the next few years. This easing cycle is anticipated to have significant implications for the future of the U.S. economy, influencing the rates at which banks extend loans to both individuals and businesses. As a result, borrowing costs for consumers—such as home mortgages and credit card debt—are likely to decrease.
Fed officials expect additional rate reductions for the remainder of the year, gradually lowering rates over the next few years. This easing cycle is anticipated to have significant implications for the future of the U.S. economy, influencing the rates at which banks extend loans to both individuals and businesses. As a result, borrowing costs for consumers—such as home mortgages and credit card debt—are likely to decrease.The news supported bitcoin prices, with bitcoin recently near $63,000. Bitcoin prices tend to rise on signs of monetary easing, as they are broadly seen as risk-on assets even as some investors tout their use as safe havens.
In the long run, increased borrowing and spending can lead to stronger economic growth, which may further enhance liquidity in the system. However, while liquidity may initially increase, prolonged low rates can also lead to potential risks, such as asset bubbles and excessive debt levels. Monitoring these factors is essential to maintain financial stability.
Reference: Trading Economics, Reuters
 The Nostr ecosystem is known for its decentralization and focus on sovereign identity, offering a unique advantage for users. With more than 100 applications across social media, entertainment, marketplace and more, Nostr's key strengths include:
The Nostr ecosystem is known for its decentralization and focus on sovereign identity, offering a unique advantage for users. With more than 100 applications across social media, entertainment, marketplace and more, Nostr's key strengths include:-
Decentralization and Sovereignty: Protects users' privacy from censorship.
-
Integration with payment system: Enhances features like zapping and streaming.
While these aspects attract Bitcoin enthusiasts, broader user adoption will require more sustainable and diverse features. Over the next few years, various opportunities and challenges may arise.
Social Media
Nostr represents a significant opportunity in decentralized social media, giving users control over their data and promoting free speech. Users can zap each other’s content through the Bitcoin Lightning Network. Nostr’s interoperability allows users to share posts across platforms, enabling a more integrated experience. Unlike traditional social media, where data is siloed, Nostr fosters collaboration among apps, allowing users to switch easily based on their needs. Over the next few years, we can expect a thriving ecosystem.
Identification and Login
Nostr's decentralized identity system relies on public and private keys, making it a fundamental feature. While no standalone disruptive applications are expected, this identification functionality can enhance social media and wallet apps by integrating features that improve competitiveness.
Decentralized Marketplace
Nostr's secure communication framework can facilitate decentralized marketplaces, enabling direct buyer-seller interactions while enhancing privacy. These marketplaces could extend beyond traditional goods to include music, writing, and services.
Regulation in the Nostr Ecosystem
As a censorship-resistant platform, Nostr might faces unique regulatory challenges. The protocol itself is neutral, but how developers manage relays will determine oversight levels. Proper regulation might prevent illegal activities and enhance the credibility of apps, helping Nostr grow without stifling its decentralized spirit. Developers focusing on decentralization may find opportunities in regulatory advising, ensuring that Nostr apps adhere to principles of decentralization while fostering healthy growth.
 ## MicroStrategy Raises $1.01 Billion in Convertible Notes to Fuel Bitcoin Acquisitions
## MicroStrategy Raises $1.01 Billion in Convertible Notes to Fuel Bitcoin AcquisitionsMicroStrategy has completed a $1.01 billion offering of 0.625% convertible senior notes due in 2028, with plans to acquire Bitcoin using part of the proceeds. The private offering, finalized on Sept. 19, targeted institutional investors and allows conversion into cash or MicroStrategy stock. The company will also redeem $500 million in senior secured notes, releasing collateral that includes 69,080 Bitcoin. Between Sept. 13 and 19, MicroStrategy purchased approximately 7,420 Bitcoin for about $458.2 million, averaging $61,750 per Bitcoin.
 > Reference: Microstrategy, Cointelegraph
> Reference: Microstrategy, CointelegraphBhutan Revealed as Major Bitcoin Holder with 13,093 BTC
Bhutan, the Buddhist kingdom in the eastern Himalayas, has emerged as a significant Bitcoin holder, owning 13,093 BTC valued at approximately $830.789 million, according to Arkham Intelligence. This is the first public disclosure of Bhutan's Bitcoin addresses.
 Mining is conducted by the country's investment arm, Druk Holdings, which has established facilities at various sites, including the defunct Education City project. In May 2023, Bitdeer partnered with Druk Holding & Investments to develop a 100% carbon-free Bitcoin mining operation in Bhutan. Earlier reports indicated plans to expand mining capacity from 100 to 600 megawatts, leveraging the country's abundant hydropower resources for eco-friendly operations.
Mining is conducted by the country's investment arm, Druk Holdings, which has established facilities at various sites, including the defunct Education City project. In May 2023, Bitdeer partnered with Druk Holding & Investments to develop a 100% carbon-free Bitcoin mining operation in Bhutan. Earlier reports indicated plans to expand mining capacity from 100 to 600 megawatts, leveraging the country's abundant hydropower resources for eco-friendly operations.Reference: Arkham, Bitcoin Magazine
Donald Trump Makes History with Bitcoin Payment
Republican Party presidential nominee Donald Trump made history as the first former U.S. president to complete a Bitcoin payment at PubKey, a Bitcoin-themed bar in Greenwich Village, NYC, during National Cheeseburger Day.
He described the payment as “easy” and said it went through “quickly and beautifully.”
After the transaction, Trump, accompanied by bar owner Thomas Pacchia, greeted attendees. “This was one of the most important Bitcoin transactions of all time,” said Pacchia. “President Trump came to connect with and support the Bitcoin community. We are very excited he was here.”
 > Reference: Yahoo Finance, Cointelegraph
> Reference: Yahoo Finance, Cointelegraph ## We are Hiring: Entrepreneur In Residence
## We are Hiring: Entrepreneur In ResidenceAs an Entrepreneur In Residence with HCM, you will lead and drive innovative projects related to building Bitcoin ecosystem. Leveraging your extensive background in business, technology, product development, marketing, and/or operations management, you will drive projects from the seed stage through capital market financing and growth, along with our resource supports. We seek leaders with a good understanding of the Bitcoin who can achieve breakthroughs in the international market.
Please send your resume to: account_admin@hcm.capital/yake@hcm.capital\ For more information, please check out bitcoinerjobs.com
 ## Lifpay is sponsoring Max & Stacy Invitational at EL Encanto Golf Tournament in January 2025, El Salvador
## Lifpay is sponsoring Max & Stacy Invitational at EL Encanto Golf Tournament in January 2025, El Salvador > Reference: X.com
> Reference: X.comUnchained and University Impact Launch Bitcoin-Native Donor-Advised Funds to Streamline Charitable Donations and Maximize Tax Efficiency
 > Reference: X.com
> Reference: X.com -
-
 @ c278022e:b37d01a2
2024-09-25 05:58:25
@ c278022e:b37d01a2
2024-09-25 05:58:25Abstract
This paper proposes a comprehensive system design for a decentralized prediction market and a game-theoretic stablecoin built entirely on Bitcoin's Lightning Network. Leveraging Discreet Log Contracts (DLCs) and off-chain transactions, the system enables leveraged trading, liquidity provision, and stablecoin creation without relying on alternative cryptocurrencies or tokens. We address potential flaws and criticisms, demonstrating that Bitcoin alone provides a secure, scalable, and efficient platform for advanced financial applications.
truthserum@iris.to
Introduction
Motivation
Bitcoin, as the original and most secure cryptocurrency, offers a stable and decentralized platform for financial innovation. While alternative platforms like Ethereum have introduced smart contracts and decentralized finance (DeFi) applications, they often suffer from network congestion, high fees, and centralization risks. This paper aims to demonstrate that Bitcoin's Lightning Network can support complex financial instruments, including a decentralized prediction market and a game-theoretic stablecoin, without the need for alternative cryptocurrencies.
Overview
We propose a system that:
- Utilizes Bitcoin's Lightning Network for scalability and low fees.
- Employs Discreet Log Contracts (DLCs) for secure, private smart contracts.
- Creates a decentralized prediction market with leveraged trading.
- Introduces a synthetic stablecoin based on the net positions of long and short traders.
- Addresses potential flaws and criticisms, ensuring robustness and security.
Background
Bitcoin and the Lightning Network
Bitcoin is a decentralized digital currency that operates on a peer-to-peer network, using proof-of-work consensus for security. The Lightning Network is a layer-two protocol that enables fast, off-chain transactions between participants, enhancing Bitcoin's scalability.
Discreet Log Contracts (DLCs)
DLCs are a type of smart contract that allows two parties to make a conditional payment based on the outcome of a future event, with privacy and security ensured by cryptographic techniques.
Prediction Markets and Stablecoins
Prediction markets allow participants to speculate on the outcome of future events, while stablecoins are cryptocurrencies designed to maintain a stable value relative to a target asset or basket of assets.
System Design
Key Components
- Liquidity Providers (LPs): Users who provide Bitcoin as collateral to the liquidity pool.
- Traders: Users who take leveraged long or short positions on asset prices.
- Oracles: Entities that provide reliable price feeds for asset settlement.
- Stablecoin: A synthetic stablecoin derived from the net positions of traders, backed by Bitcoin collateral.
Core Features
- Decentralized Prediction Market: Facilitates leveraged trading on asset prices.
- Game-Theoretic Stablecoin: Maintains stability through the balance of longs and shorts.
- Yield Generation: LPs earn yields from trading fees, funding rates, and liquidation penalties.
- Bitcoin-Only: Built entirely on Bitcoin's network without alternative tokens.
Technical Implementation
Leveraged Trading via Discreet Log Contracts
Contract Setup
Two parties, a trader and an LP, agree on contract terms:
- Asset: Bitcoin/USD price.
- Leverage: Multiplier on the trader's collateral.
- Collateral: Bitcoin amount provided by the trader.
- Duration: Contract length.
- Oracle: Selected to provide the settlement price.
Funding the Contract
- Trader: Locks collateral C_T in a multi-signature address.
- LP: Locks collateral C_LP to cover potential payouts.
Execution and Settlement
- At maturity, the oracle provides a signature of the final price P_f.
- The DLC allows funds to be distributed based on P_f and the contract terms.
Synthetic Stablecoin Creation
Mechanism
- Stablecoins are minted when traders open positions.
- Backed by Bitcoin collateral from LPs and traders.
- Stability maintained through balanced market positions and funding rates.
Funding Rates and Market Balance
Purpose
To incentivize traders to balance long and short positions, maintaining system stability.
Implementation
- Funding Rate: Funding Rate = k * (Net Position / Total Open Interest)
- Payments: Traders on the dominant side pay funding fees to the opposite side.
Risk Management and Liquidations
- Margin Requirements: Minimum collateral ratios for traders.
- Liquidation Thresholds: Positions are liquidated if collateral falls below maintenance margin.
- Automatic Liquidations: Enforced by smart contracts without human intervention.
Mathematical Foundations
Payout Calculation
Position Size
Position Size = C_T * L
Profit/Loss (P/L)
P/L = Position Size * ((P_f - P_0) / P_0)
Return on Investment (ROI)
ROI = (P/L / C_T) * 100%
Liquidation Price Calculation
For a long position:
P_liquidation = P_0 - ((C_T / Position Size) * P_0)
Game Theory and Incentive Alignment
Traders
- Incentive: Profit from accurate market predictions.
- Behavior: Manage risk to avoid liquidation.
Liquidity Providers
- Incentive: Earn yields from fees and funding rates.
- Risk: Exposure to traders' net P/L.
Oracles
- Incentive: Earn fees for accurate data provision.
- Behavior: Maintain reliability to secure future earnings.
Potential Flaws and Criticisms Addressed
Oracle Trustworthiness
Criticism
Relying on oracles introduces a single point of failure and potential for data manipulation.
Solution
- Decentralized Oracles: Use multiple oracles and aggregate data.
- Threshold Signatures: Require consensus among oracles.
- Incentive Alignment: Oracles are incentivized to provide accurate data through fees and reputation.
Liquidity Risks
Criticism
Insufficient liquidity may prevent covering traders' profits, especially during high volatility.
Solution
- Dynamic Leverage Limits: Adjust leverage based on liquidity.
- Risk Management Protocols: Implement strict margin requirements.
- Incentivizing LPs: Offer competitive yields to attract liquidity.
Price Volatility and Market Manipulation
Criticism
Extreme market movements could lead to rapid liquidations and instability.
Solution
- Anti-Manipulation Measures: Use time-weighted average prices (TWAP).
- Circuit Breakers: Temporarily halt trading during extreme volatility.
- Robust Liquidation Mechanisms: Ensure smooth liquidations without market disruption.
Technical Complexity
Criticism
Implementing DLCs and managing Lightning Network channels require advanced expertise.
Solution
- User-Friendly Interfaces: Develop intuitive platforms.
- Educational Resources: Provide guides and support.
- Community Development: Encourage collaboration and open-source contributions.
Regulatory Compliance
Criticism
Operating a leveraged trading platform may raise regulatory concerns.
Solution
- Decentralization: Structure the platform to minimize central control.
- Legal Consultation: Engage experts to navigate regulations.
- KYC/AML Policies: Implement where necessary without compromising privacy.
Network Limitations
Criticism
The Lightning Network may face limitations in liquidity and channel capacity.
Solution
- Channel Management Strategies: Utilize multi-path payments and channel factories.
- Liquidity Hubs: Establish well-funded nodes.
- Ongoing Development: Contribute to scalability improvements.
Conclusion
By leveraging Bitcoin's Lightning Network and Discreet Log Contracts, we can build a decentralized prediction market and a game-theoretic stablecoin without relying on alternative cryptocurrencies. This system addresses potential flaws and demonstrates that Bitcoin alone provides a secure, scalable, and efficient platform for advanced financial applications.
Future Work
- Prototype Development: Create a working model of the proposed system.
- Security Audits: Conduct thorough assessments to ensure robustness.
- Community Engagement: Involve developers and users in refining the system.
- Regulatory Navigation: Work with legal experts to ensure compliance.
Acknowledgments
We thank the Bitcoin and Lightning Network communities for their ongoing contributions to decentralized finance and open-source development.
References
- Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System, 2008.
- Joseph Poon and Thaddeus Dryja, The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments, 2016.
- Tadge Dryja, Discreet Log Contracts, 2017.
- GMX, Decentralized Perpetual Exchange, https://gmx.io/, Accessed 2023.
- BIP 0341, Taproot: SegWit Version 1 Spending Rules, 2020.
- Rusty Russell, Generic Smart Contracts Over Lightning, 2019.
-
 @ 472f440f:5669301e
2024-09-25 04:12:35
@ 472f440f:5669301e
2024-09-25 04:12:35Last night I had the pleasure of sitting down with Caitlin Long, Founder and CEO of Custodia - a fully reserved bank providing banking services to bitcoin companies, to discuss an affidavit written by Elaine Hetrick of Silvergate Bank. Elaine is the Chief Administrative Officer of Silvergate and wrote an affidavit, a sworn testimony subject to perjury, in which she detailed the events that led to Silvergate voluntarily winding down their business and returning deposits to their customers.
This affidavit is a bombshell because it confirms speculation that Silvergate was solvent in early 2023 and wasn't shut down because of bad risk management on behalf of the bank's management team, but instead was forced to shutter its doors because the Biden Administration, with strong influence from Senator Elizabeth Warren, forced Silvergate's hand because they didn't like that they were banking digital asset companies.
For those who are a bit fuzzy on the details of the narratives that were flying around Silvergate at the time, I'll jog your memory. FTX was a customer of Silvergate's at the time their Ponzi scheme unraveled. As FTX was blowing up, everyone and their mother was scrambling to get their money out of Silvergate because they assumed that since one of the bank's largest counterparties was going bust, the bank must be in trouble too. A sane decision. Especially considering the history of systemically non-important financial institutions this century.
Unless you were paying close attention during this time, you were likely under the impression that Silvergate was a typical fractionally reserved bank that was experiencing a run that led to its inevitable demise. The media made it seem this way. The regulators made it seem this way. And one pompous short seller made it seem this way. However, nothing could be further from the truth. Here are the most important parts of the affidavit:
Silvergate had stabilized, was able to make regulatory capital requirements, and had the capability to continue to serve its customers that had kept their deposits with Silvergate Bank.
Despite this, regulators decided to turn the pressure up and essentially gave Silvergate Bank, and Signature Bank as well, an ultimatum; drastically change your business models immediately by dropping your digital asset customer base or we'll shut you down. There were no hard numbers described in Elaine's testimony, but rumors are that the regulators wanted Silvergate to quickly shrink their exposure to digital asset-related clients to less than 15% of their capital base. At the time, Silvergate's customer base was made up almost entirely of digital asset companies (99.5% to be exact).
The regulators were asking Silvergate to do something that was quite literally impossible given the circumstances. Faced with an impossible task, on March 8th of 2023 Silvergate decided to voluntarily wind down their operations and return deposits back to their customers.
Let's be very clear here, Silvergate did not lose a single penny of customer deposits due to the run on their bank. Management, understanding the volatile nature of the digital asset markets, designed their risk management and capital allocation strategies in a way that would enable them to return dollars to any customer who requested them. And that's exactly what they did when customers came to request their money. They returned EVERY SINGLE PENNY.
This begs the question, "Why did they essentially force Silvergate to shut down?" They seemed to be running a very responsible operation after all. You'd think the regulators would applaud Silvergate's vigilance in risk management on behalf of their customer base. How many banks would have been able to do the same thing if put in the same situation? Probably not many.
The answer to this question is already well known throughout the industry, but Elaine Hetrick's testimony adds some hard evidence that makes it undeniable; Elizabeth Warren, the SEC, the FDIC and the Federal Reserve have been acting in concert to unconstitutionally and extrajudicially target the bitcoin and broader digital asset industry because they do not believe that it should exist. It is a threat to their power structure. The financial system, as it is designed today, gives those who would like to centrally plan the economy and micromanage the lives of American citizens a ton of power. Bitcoin is a threat to that power and they have to do everything in their power to prevent its proliferation.
The targeting of the industry was also confirmed by the aftermath of the NYDFS and FDIC uncharacteristically taking Signature Bank behind the woodshed in the evening of Sunday, March 20th, 2023, despite the fact that Barney Frank and others at the bank were convinced they could handle withdraws come market open the next day.
Signature Bank was ultimately sold to Flagstar Bank. However, they were forced to spin out their digital asset-related accounts before doing so.
This public signaling and sudden regulatory shift made clear that, at least as of the first quarter of 2023, the Federal Bank Regulatory Agencies would not tolerate banks with significant concentrations of digital asset customers, ultimately preventing Silvergate Bank from continuing its digital asset focused business model.
Pretty damning if you ask me. Also, very frustrating and most definitely illegal.
Elizabeth Warren and her gaggle of hall monitors across alphabet soup agencies and the Federal Reserve have been on one massive, unconstitutional, power trip for the last four years. They've besmirched bitcoin and those of us working hard to ensure that the United States of America leads the way forward as bitcoin adoption continues at every turn. Good people striving to make the world a better place.
No one is a better example of this than Alan Lane, the former CEO of Silvergate Bank. I consider Alan a friend and feel supremely confident when I say that he is one of the nicest and thoughtful people I have met in this industry. A man who followed his passion to bring legitimacy and much needed banking services to an industry that the incumbents refused to touch. And he did bring legitimacy. As I explained earlier, Alan and his team understood the volatile nature of the industry and built their firm in a way that took this volatility into account. Silvergate did not fail, they were forced to shut down by Elizabeth Warren and her acolytes at the regulatory agencies.
What's worse, Warren's vendetta against bitcoin and the digital asset industry incited the largest banking crisis this country had seen since 2008. Silvergate and Signature being taken behind the woodshed put everyone on their toes and bank runs started across the country. This led to the failure of First Republic, Silicon Valley Bank and a couple of smaller banks, forced the Fed to step in with their emergency BTFP program, and burdened taxpayers with $40B in FDIC costs that needed to be absorbed as a result. If it weren't for the bailouts things would have gotten completely out of control. All because Elizabeth Warren wants to live in a world in which we are forced to use CBDCs and unable to opt-in to bitcoin.
The euthanasia of Silvergate and Signature are only the tip of the iceberg when it comes to Chokepoint 2.0.
Caitlin Long and Custodia have been in a years long battle with the Federal Reserve to receive a Fed master account so that they can properly serve their customers. For those who are unaware, Custodia is a full-reserve bank that exist to serve bitcoin and digital asset businesses as well as other adjacent businesses like fintechs, banks and funds. Custodia is a chartered bank and special purpose depository institution that has built custody services so that customers can hold bitcoin within their bank accounts alongside their dollar accounts.
Like Silvergate and Signature, Custodia has been singled out and unlawfully denied a master account with the Fed because the Federal Reserve doesn't want a bank like Custodia to exist. Either because they worry about the ramifications of the introduction of a full-reserve bank into a system dominated by fractional-reserve banks or they simply do not want to see bitcoin succeed. If we're being honest, it's probably a combination of the two.
Despite what we, or anyone else, thinks about the potential effect a bank like Custodia could have on the market if it's granted a master account, the Fed's actions are unconstitutional in this case as well. This was made pretty clear (but yet to be determined by a court) in an amicus brief written by Paul Clement on behalf of Custodia earlier this Summer. The Fed is actively undermining the dual-banking system that was set up in this country to enable competition between state chartered banks and the Federal Reserve system.
In the case of Custodia, the Federal Reserve is exhibiting expansive discretionary power that it has never shown before. Custodia is a state chartered special purpose depository institution in the state of Wyoming. Historically, it would be trivial for this type of state chartered bank to get a master account with the Fed. But for whatever reason (we know the reason) the Fed has been denying Custodia their right to this account for a number of years. To the point where Custodia was forced to sue the Federal Reserve and take their case to the courts.
What's interesting about the saga of Custodia and the Fed is that it has forced Custodia's legal team to dig in and highlight where the Fed is overextending its reach and acting arbitrarily. In the amicus brief that was published in July of this year, Paul Clement argues that the way Federal Reserve Bank presidents are chosen is unconstitutional when you take into consideration the fact the these Fed branch presidents are unilaterally undermining state banking laws by denying master accounts.
If they are going to unilaterally undermine state banking laws they need to be appointed by the President or an official acting on behalf of the Executive Branch. Federal Reserve Bank presidents aren't appointed by the President of the United States or any official acting with the authority of the Executive Branch. Instead, they are appointed by their boards, which are controlled by the privately held commercial banks who own them. The Federal Reserve system is clearly acting unconstitutionally when they deny Custodia from being assigned a master account.
The people in power within the federal government and the Federal Reserve system are actively targeting the bitcoin and digital asset industry, acting extrajudicially and making a mockery of the rule of law in the United States. They are completely out of control and it is important that everyone who cares about the future of bitcoin in the United States and the future of the United States more broadly (even if you don't like bitcoin) speaks out and fights against these totalitarians as vehemently as possible. What they are doing is wrong. It's unconstitutional. And it is putting the future of our country at risk.
If the federal government, the regulators and the Federal Reserve do not get out of the way and let law abiding citizens build the businesses they want and associate with businesses they want, those businesses will go elsewhere and the United States will be set back generations as a result.
It's time to put these people in their place and let it be known that freedom will reign supreme in the Land of the Free. Fight!
Final thought... I promised Parker Lewis that I would do cross fit on Friday morning and I'm using today's final thought as an accountability tool.
-
 @ fd78c37f:a0ec0833
2024-09-25 02:56:07
@ fd78c37f:a0ec0833
2024-09-25 02:56:07A mirror post on the Dora Research Blog can be found at: https://research.dorahacks.io/2024/09/25/network-states-critique-part-1/ Author: DORA Interns
Section 1:
As capitalism became the new economic system, replacing the old feudal guilds and their small and inefficient means of production, cultural conditions began to take hold that would give rise to nations and a sense of national consciousness. This thesis, argued in great detail by Benedict Anderson in his book Imagined Communities, is characteristically similar to Marxist theory, which generally holds that any difference made in a society's economic and technological base results in changes throughout its whole structure. As humans alter their environment, gain control of its variables, and reduce the severity of their conditions, higher, more rational faculties may begin to develop. Karl Marx writes, “By thus acting on the external world and changing it, (human beings) at the same time change (their) own nature.” As technology progresses; as the tools used by human beings advance and become more efficient and productive, human consciousness grows with it. Starting with primitive forms of productive forces like stone tools, human beings organize themselves in ways made possible by this primal mode of technology, which possesses a meager capacity to tame and alter nature, and, consequently, casts human understanding and knowledge into the shadows, greatly obstructing their freedom, as well as their capacity to become self-aware. Thus as the means of production progress, more complicated forms of social organization become possible. Human beings slowly become conscious of their autonomy - the ability to live a life dictated by reason, by rational choice and principle, and not by the caprice of external causal factors. Throughout this historical process, the old institutions and societal structures deteriorate and grow obsolete; revolutions occur to update the social infrastructure and catch up to the progressing economic base.
When technology grew to the point of being able to sustain capitalism, and more well-organized systems of labor were needed to underpin what the economy demanded, people flocked to the cities, leaving behind the rural life that was characteristic of the feudal system, and began thinking of themselves as part of larger collectives, as nations. Marx writes, “Independent, or but loosely connected provinces, with separate interests, laws, governments, and systems of taxation, became lumped together into one nation, with one government, one code of laws, one national class-interest, one frontier, and one-customs tariff.” Industrialization, then, and its new tools, which drastically shifted the means of production, changed human consciousness and laid the conditions necessary for societies to become nation-states.
In Imagined Communities, Anderson claims this development toward industrialization and nation-states was largely set in motion by the advent of the Gutenberg printing press in 1440. He argues that this technology, which began to distribute newspapers, novels, and bibles to readers in a language that would become a people’s common vernacular, had laid the cultural conditions for a sense of national consciousness, the feeling that one belonged to a larger community that expanded past their immediate surroundings, to arise. People who previously did not think of themselves as ‘French’, or ‘English’, or ‘American’, who spoke in largely discontinuous dialects, slowly began to think of themselves as participating in a nation of people bound together by a shared experience. These new national identities replaced the old religious, preordained orders that once provided meaning to human beings, and nationality became one of the more dominant modes through which people identified who and what they were.
Now, another important technology that facilitated the historical development of nations was the ledger and its use for double-entry bookkeeping. As information regarding debits and credits was able to be recorded, more large-scale trades, transfers of assets, and general forms of record-keeping were made possible, bringing about the need for more uniform, clear, and discrete boundaries between the various territories. Nation-states became a means to meet the demands made by society’s progress. Feudalism and its notion of the Divine Right of Kings, its old religious dogmas, and its obsolete forms of social institutions, were unable to adapt to these economic shifts. The emergence of the Enlightenment period (1685-1789) ushered in new ways of understanding the state and its position of authority and legitimacy to hold power. Rather than being conceived as a beacon of Divine order, it increasingly became seen as a rational compromise between people who invested the state with authority in exchange for preserving their natural rights. It was now a third-party institution that resided over settling disputes, enforcing the law, and punishing those who violated it. The state was now only legitimate insofar as it protected the rights of the individuals who consented to be governed.
However, over time, a great deal of trust had been handed to these new institutions, and many believe they have now led to an excess of centralized power. Banks became the holders of financial ledgers; distribution of information, of news and events, became the job of a few selected companies, and the government, over time, stepped over its initial claim to legitimacy by taking on roles far surpassing the task of merely protecting individual rights and liberties. Because there was no technology for it, people still had to be trusted as disinterested and objective third-party mediators, which human nature often fails to achieve, allowing self-interest, greed, envy, and human vice more generally to have an influential role in state and governmental processes. This creates corrosive trust issues between citizens and their institutions. In their book The Truth Machine, Michael J. Casey and Paul Vigna write, “Trust - especially in our institutions - is a vital social resource, the true lubricant of all human interaction. When it works, we take it for granted - we wait our place in line, follow road rules, and assume everyone will do the same… But when trust is lacking, things really, really break down.”
Today, with the invention of blockchain and cryptocurrencies, many believe these institutions themselves become obsolete and that new forms of social organization are needed. In his book The Network State, Balaji Srinivasan labors to demonstrate this claim, arguing that the network and its capacity to allow individuals to organize digital, landless communities, can replace the old nation-states that obstruct social development. In particular, he believes blockchain and its capacity to underpin trustless systems to be capable of supplanting the older institutions by automating what they were entrusted with doing; cryptocurrencies can automate the roles done by central banks and the Federal Reserve; information of news and events can be loaded onto blockchains and remain immutable, preventing self-serving parties from tampering and manipulating it for their interests; private information can be cryptographically secured and held by individuals rather than by centralized, private tech companies like Google; and nation-states more generally can be superseded by the network, which eliminates the perennial issue of land that has caused innumerable wars and conflicts between sovereign states. But, despite the optimism induced by these new technologies, there are problems. The rest of this article will be concerned with addressing what it means for a network state to be ‘ethical’, to use a term of Srinivasan’s. Some nation-states are viewed as unethical, as providing conditions that are degrading to human beings; North Korea immediately comes to mind. The next section will propose a way to discern why such a judgment is true, and will be used to assess what a network state must achieve to be considered ‘ethical’. I will argue that this can only be done by holding people’s autonomy as the principal end of the state.
Section 2:
To see this, we can think of creating a state as a complex activity, and, as with most activities, it is directed toward certain ends. Similarly to how playing a sport, gardening, or driving a car is an activity, so is creating a state - albeit a far more complicated one. But whereas the ends of certain activities may be for the sake of pleasure or leisure, the state’s ends are always within a moral and ethical scope. It is moral in that, whenever one is engaged in the activity of state-making, the ends by which the activity is oriented are always directed toward drafting principles that will establish cooperative social practices and institutions that guide and govern the actions of the members within the state, which lay the conditions by which human beings will pursue their individual and collective well-being. In other words, the ends that the act of founding a state is aimed toward is to create practices that consist of individuals who form collectives, and who cooperate and live according to a given set of moral ends that orient, inform, and shape the lives of those within the state. Therefore, all acts occurring within this activity are never neutral from the moral point of view but are inextricably linked to questions about morality and the ethical life. Such an activity, then, should not be viewed as anything less than a pursuit of moral and ethical ends, and to confuse this activity with the pursuit of other ends - like financial gain, technological innovation, the expansion of markets, or the satisfaction of personal interests - commits a modal confusion, which immediately involves one in a separate activity than that of founding a state. By modal confusion, I mean the error of engaging in a particular mode of activity with the wrong set of ends in mind. For example, someone who makes paintings would be deeply confused to declare themself to be an artist when their chief end is financial gain. Such an end is better captured by calling the activity manufacturing rather than artistry. Perhaps a more characteristic end of an artist would be the production of beauty, for instance, or self-expression, but not profit. Profit would be employed only as a means to further, more artistic ends that are deemed necessary by the social conditions the artist finds themself in.
Or imagine a person who becomes friends with someone to derive certain benefits from them, like using them to get to know someone they are interested in, but who nevertheless believes that the two are sincere friends. The person who befriends the other confuses what kind of activity they are engaged in. The relation of being friends with someone involves adopting certain ends that are demanded by the relationship. In the case of friendship, an obvious end that characterizes the activity is holding the other person as an end-in-themselves, as someone who is not valuable for any other reason other than the fact that they’re a friend. One would be deeply confused by believing to be engaged in friendship when one does not hold the relevant end in relation to the activity.
Now, when founding a network state, reducing the degree of modal confusion is central to the project of creating an ‘ethical’ state. If a founder holds an irrelevant set of ends in mind, they risk the potential for causing significant harm to persons, and I will argue that it does so by reducing autonomy. By autonomy, I mean a human being’s capacity to exercise willful, deliberative choice, and not be wholly dictated by external influence. The philosopher Harry Frankfurt defines it as follows: “Autonomy is essentially a matter of whether we are active rather than passive in our motives and choices - whether… they are the motives and choices that we really want and are therefore in no way alien to us.” Now, one’s autonomy exists within one’s subjectivity, which can be understood as a person’s conscious experience. It’s the center at which one’s thoughts, desires, perceptions, worries, fears, anxieties, all occur, as they manifest in experience. Subjectivity can then be divided into at least two parts, one of which is a quantitative dimension, the other being qualitative. The first consists of the stream of experience, of the constant succession of mental states and behaviors. At one moment I’m hungry and so act to satisfy the desire; at another, I’m struck with fear and run away from the object that is the target of my response, and so on. As the examples imply, this dimension of subjectivity involves a high degree of passivity; events and experiences are simply happening to me. The qualitative dimension, on the other hand, is far more active and is the space by which autonomy exists. This involves the capacity to evaluate one’s mental states and to reflect and decide whether they are worth acting on, whether they’re rational or not, whether they represent the world accurately; and to act autonomously is to act based on one’s qualitative nature, and not be carried away unreflectively by the more passive, quantitative dimension.
The central claim of this article is that the principal end of the state is to promote the development and growth of the qualitative nature of its members’ subjectivity. To hold this capacity of human beings as secondary, or accidental and not a primary need, is to be modally confused. That’s not to say the state is the primary institution responsible for promoting or even determining its citizens’ autonomy - the existence and crimes of the USSR are sufficient to refute that - but only that it shares the responsibility. Whatever its exact role is, or in what forms it is concretely realized, the state’s principal end is directed toward facilitating the development of its citizens’ subjectivity. A society can be imagined as a large, extended plain divided into proportions sized according to the degree of each part’s contribution toward reaching this goal. One part consists of the economy, another is occupied by the private and public affairs of communities and individuals, and another is delegated to the state. Whatever the exact configuration of this plain, each part cooperates and contributes toward fulfilling the full breadth of human needs. And I believe this can be done in numerous ways; there is not necessarily one form a state must have, which specifies and delineates each of its fixed parts to align with some ultimate reality, to reach this end. Nevertheless, I believe the state does have a hierarchy of ends.
It could be argued, however, that this is wrong and that founding a state is not a moral activity but merely a prudential one, whose end is to protect individual self-interests and preferences. That is, the state is not concerned with morality but with establishing conditions that enable individuals to pursue their own self-interests and preferences uninterrupted by other human beings. Because individuals are concerned with their own well-being, with their own survival, and the satisfaction of their desires, living in a state of nature, where there is no authority to settle disputes or conflicts regarding life, liberty, or property, is contrary to individual interests. It would be rational, then, to form a state invested with the authority granted by the consent of the governed which has the power to punish those who violate the law, adjudicate and settle disputes, and protect everyone’s basic liberties that prevent others from interfering with one another’s lives.
Understanding the state this way means that the ends of the state are prudential and not primarily moral. Individuals are free to opt into whatever network state they wish, insofar as they do so by their own, uncoerced choice.
Now Srinivasan, as I see it, is somewhere in the middle between the moral and prudential conceptions of state founding. He speaks of state legitimacy as being grounded entirely in the consent of the governed. If a network state receives enough members; if it expands to the point of reaching diplomatic recognition, then that is a testament to the legitimacy of that state. People have consented to their smart contract(s), they have invested a certain amount of authority to the founder(s) by agreeing to its terms, and such a state, Srinivasan concludes, is therefore ‘ethical’. But the notion of being ethical here is ambiguous. Does he mean that it is so because what constitutes something as ethical is an agreement, or does he mean that freedom to choose is the principal end of the state? The former is prudential because it reasons that it is up to individuals to decide for themselves what is ethical or moral, given that there is no objective fact of the matter; individuals calculate according to their self-interests, preferences, and desires, and whether a contract is fair, just, or equal is up to each person. The latter, on the other hand, is moral because it holds freedom of choice as what constitutes the moral ends of the state. What matters is whether individuals freely choose to join the state, and not whether the contract is fair or just independent of that. This is because individuals' most valuable capacity is to choose. Because it is up to each person to decide for themselves whether a contract is fair or just, a state is morally legitimate if people voluntarily consent to its contract.
Whichever one Srinivasan is committed to, both are problematic and I will present arguments against the two interpretations, which will be motivated by the following claims. That one, holding the state to be merely concerned with prudential ends is to confuse means with ends, which underestimates the role it plays in the individual’s life, and two, holding freedom of choice as the principal end confuses mere choice with free choice. These confusions permit the degradation of human dignity by disregarding the human need to foster the faculties necessary for autonomy. It is within each individual’s interests to be within a society. To be outside of a community, to be isolated and without access to resources, to be without recourse to institutions who will enforce the protection of one’s rights, is to live within a hostile environment that is against fulfilling one’s needs. However, establishing more hospitable conditions does not thereby define the principal end of the state, and the mere ability to choose does not necessarily respect the capacity for autonomy. It only offers the appearance of choice and not the reality. To freely choose means far more than the pursuit of satisfying an impulse. Before developing these arguments further, Srinivasan's two potential conceptions of the ‘ethical’ state need to be better understood. Let’s begin with the prudential account.
Section 3:
According to this argument, the state is directed toward establishing the conditions necessary for individuals to pursue their own self-interests, desires, and preferences, without the interference of others, and insofar as one’s projects do not infringe on someone else’s. An exemplar of this view is the philosopher Thomas Hobbes. A state of nature, where individuals exist outside of an organized collective bound by laws and institutions, is a state of war, filled with perpetual conflict and strife and the competition of self-interests, and consists of an endless pursuit of individuals attempting to gain power over one another for the sake of the control and security necessary for extinguishing the fear caused by their harsh environment. Setting aside the plausibility of such a state, what’s important is that, by understanding individuals in this way, human nature is presented as calculative, as the rational pursuit of one’s own interests. And since interests conflict, and each individual has an inborn right to preserve itself, to fight for its own survival; and because each one must determine what their survival requires, life in a state of nature is nasty, brutish, and short.
It would be far more rational, then, both for oneself and others, to form a state that would eliminate this perpetual state of war and conflict by implementing laws and institutions that enforce agreements and contracts made between persons, and that uphold conditions of peace, which allows individuals to pursue their ends without the fear of being interfered with. The philosopher Immanuel Kant phrases this as follows: “Each may seek his happiness in whatever way he sees fit, so long as he does not infringe upon the freedom of others to pursue a similar end which can be reconciled with the freedom of everyone else within a general workable law.”
Notice, then, that forming a state is not a matter of morals but of rational calculation, of looking out for one’s own interests. It’s not that a state should be formed because it allows persons to treat one another with dignity, or because each is worthy of some inviolable respect, but because it is in everyone’s best interests. Founding a state, then, “means finding out how the mechanism of nature can be applied to men in such a manner that the antagonism of their hostile attitudes will make them compel one another to submit to coercive law, thereby producing a condition of peace within which the laws can be enforced.” This is a prudential account of state-founding.
There’s a fundamental problem with this kind of account, however. The first thing to note is the conception of human subjectivity contained within it. A Hobbesian notion of human nature, simply put, suggests subjectivity consists of computational processes whose ends are the satisfaction of the subject's desires and preferences. The state’s aim, then, is to discipline the subject in a way that will lead to them having the capacity to coexist in peaceful conditions with others. It is not to prescribe certain definite moral ends, to orient them around a conception of the good, or to circumscribe what their desires should or should not be; it is to sustain the conditions necessary for individuals to pursue their interests without interfering with the right of others to pursue their own.
Now, the issue here is that human subjectivity is conceived one-dimensionally. Human beings are born with certain natural desires and preferences like survival and the fulfillment of basic needs, and the state is not to interfere with this but to protect each individual's impulse to preserve them, and to shape their lives as they see fit. Each can do as they please insofar as it does not harm another. But this is too simplistic. This amounts to believing that human desires and preferences occupy a single, quantitative plain, and each individual goes about maximizing these while simultaneously avoiding infringing on others’ ability to do so. But if we step back and ask whether a desire itself is desirable we are no longer asking a question along this quantitative plane, but have begun to ask about the qualitative nature of the desire. Is that desire of more worth than that one? This is a question regarding second-order desires.
First-order desires often happen to us, they occur, and pull us in the direction of the desired object. My desire to eat does not arise by my own volition. After a time of not eating, the desire simply renews itself. Second-order desires concern the will, of what one wants to want, of whether a desire is something one desires to motivate his or her will. Harry Frankfurt writes, “Creatures like ourselves are not limited to desires that move them to act. In addition, they have the reflexive capacity to form desires regarding their own desires - that is, regarding both what they want to want, and what they want not to want.” Focusing solely on the quantitative dimension of subjectivity does not account for this distinction. If someone goes about attempting to maximize their well-being by satisfying their immediate desires, some of the desires they do not act on, the ones that don’t motivate them to act but are present, are competing first-order desires, which do not consist of an evaluation regarding whether the one desire is of more worth than the other; one simply out-competes the other.
Now, with this distinction in mind, the point can be stated as follows: this qualitative, evaluative dimension, is first informed and shaped by the social context one finds oneself in, or, as the philosopher Martin Heidegger would phrase it, is thrown into. By being in the world with other people, through communication, language, and interaction, human beings begin to form and make sense of what occurs in their inner and outer life. William A. Luijpen and Henry J. Koren write in their book Existential Phenomenology that, “In my dealing with others, there occurs a quasi-process of sedimentation, and the quasi-effect of it is called ‘social facticity’ or my ‘social body’. The way I greet others, speak, or think is, at least in the first instance, largely the quasi-effect of the fact that I grew up in the West and not in China.” Social facticity, then, is the set of social conditions by which a human being becomes acquainted with the world, making things intelligible and meaningful, ordered and sensible. The philosopher Charles Taylor writes, “I can only learn what anger, love, anxiety, the aspiration to wholeness, etc., are through my and others’ experience of these being objects for us, in some common space.”
When developing within a social environment, the qualitative dimension of subjectivity is largely first shaped by the situation one is in, which provides the framework by which to discern who and what one is, what is valuable, what the good is, how one should conduct oneself in specific contexts, and so forth. Underpinning all of this is an assumed picture of qualitative evaluations. For this not to be present means the individual will not be able to live. Therefore, when a state is formed that will govern a society, it is not merely concerned with prudential ends but with moral ones as well. Self-interests, preferences, desires, fears, impediments to action, in short, the whole internal and external life of an individual, are first made sense of in the social environment. To think that one can merely pursue their own ends without reference to this further dimension is wrong.
As the psychologist Erich Fromm points out in his book To Have or To Be, living in social conditions that only emphasize the quantitative nature of human beings is dehumanizing. A society and state that promotes the satisfaction of desires and preferences, of one’s self-interests, which will supposedly somehow lead to realizing human beings’ higher capacities, is highly implausible. How can character traits like egoism, greed, and selfishness produce social cooperation, connection, and harmony, which are integral to well-being? Most of the great thinkers throughout history spent their time on this issue. Socrates, Plato, the Stoics, the Epicureans, all formulated distinctions between our qualitative and quantitative capacities. Fromm writes, “The essential element in their thinking is the distinction between those needs (desires)... whose satisfaction leads to momentary pleasure, and those needs that are rooted in human nature and whose realization is conducive to human growth and produces eudaimonia, i.e., ‘well-being’.” If the qualitative dimension of subjectivity possesses needs essential to well-being, such as the ability to actively and critically engage with oneself and the world, then measures must be taken that target these features of human beings, otherwise, they will be left empty and unfulfilled.
Now, as I mentioned earlier, this doesn’t mean the state must therefore be delegated the primary bearer of this responsibility. But it does mean that it plays a role toward this end. Whatever that precisely is, the principal end of the state is to discern and actualize its part in this process.
Section 4:
So much for Srinivasan’s notion of the ‘ethical’ state as one that establishes the prudential ends of rational, self-interest-seeking agents. What about the second way to understand this idea, that the state is ethical because freedom of choice is all that matters and is the fundamental end to be preserved and exercised in and by the state? The argument I will present against this way of understanding the state has to do with how we should understand the term ‘freedom’ in this context.
If freedom of choice is the primary end of the state; if non-interference in one’s decisions to pursue one’s ends is what the term ‘ethical’ amounts to, then it must be clear what constitutes a free choice. According to the prudential account of state-founding, a state was ethical because it established conditions for individuals to pursue their desires and private conceptions of happiness. It is not a question of morals but of calculative reason, of locating rational means, and the state is a way for individuals to coexist and pursue their interests.
As has been shown, however, the state does much more than this. By having an integral role in organizing society, the state substantially contributes toward the frameworks by which individuals understand themselves, which shape the concepts necessary for moral deliberation, for positing ends worthy of pursuit, and the resources used to differentiate good from bad, right from wrong.
The proposal now is that the term ethical suggests that the state is a moral activity and not merely a prudential one, but also that the sole end of the state is to allow individuals to freely choose for themselves what they consider to be the good, or what holds value, and by making an uncoerced choice, whatever the agreement is, by consenting to it, it is ethical. The freedom to choose is the principal end of all human conduct and affairs.
This creates a twofold problem that depends on the degree of value placed on choice. The first is that, if choice is held as being forfeitable, as something someone may decide to surrender when consenting to join a state, then a state can be ethical merely because people chose to opt in, even if it allows for the existence of conditions that are degrading to human beings. The second is that, if choice is held to be the principal end of the state and is not forfeitable, it may still not realize the freedom necessary for free choice, namely, autonomy. The first problem is more easily discerned, while the second is more subtle. Let’s begin with the first.
There are many reasons why someone may choose to join a state and forfeit their freedom, but for the sake of argument it’s best to focus on one and this will be when an individual feels alienated from, and alone within, a society. A historical way to frame this problem, as Erich Fromm does in his book Escape From Freedom, is to look at the fading presence of the Catholic Church after the Reformation. To put it very simply, in the Middle Ages the world was viewed as perfectly ordered and possessed an eternal structure created by God, including how human beings, both individually and collectively, were to live. The individual was not confronted with questions of how to live, what to do with one’s life, or what ends to pursue; the Church answered these questions and provided a sense of belonging in the world. Fromm writes, “In having a distinct, unchangeable, and unquestionable place in the social world from the moment of birth, man was rooted in a structuralized whole, and thus life had a meaning which left no place, and no need, for doubt… The social order was conceived as a natural order, and being a definite part of it gave a feeling of security and belonging.” When God was “demoted,” as the historian Marci Shore puts it, and when there was no longer available recourse to some greater being to understand how human beings should live and the responsibility became their own, a great space was left empty and needed to be filled again; human beings could not assume they were at the center of things. They themselves became accountable for how society was to be organized, how life should be lived, what meaning life possesses; and the answers to these concerns must be formed by human reason itself and not by an imposed, nonhuman standard. But this emerging form of freedom came with a price. Dostoevsky formulates this cost in his famous phrase, “If there is no God, then everything is permissible.” That is, without some ultimate, nonhuman reality that makes the world appear ordered, harmonious, justified, good, everything becomes unchained. And for things to return to their previous, stable state, which is of course necessary for human beings to live, it was human beings that bore the burden. Simone de Beauvoir, a 20th-century philosopher, writes in her book The Ethics of Ambiguity that Man now “bears the responsibility for a world which is not the work of a strange power, but of himself, where his defeats are inscribed, and his victories as well. A God can pardon, efface, and compensate. But if God does not exist, man’s faults are inexpiable.”
The experience of alienation in modern society can be partially explained by modernity not being able to cope with this burden. To use Fromm’s phrase, great efforts have been made to escape from it. Historians like Hannah Arendt have attributed the rise of totalitarian governments in the 20th century as arising from this condition, where individuals forfeit this new form of freedom by submerging themselves within the group and relinquishing their responsibility to choose how to live and decide what their lives ultimately mean. But doing so eliminates choice altogether and therefore reduces subjectivity to a mere thing that is not aware of itself, and thus not accountable for its actions and projects, as being the one responsible for what takes place in the world. And as the 20th century demonstrates, this is catastrophic. Therefore, no network state that attempts to allow individuals to forfeit their freedom and autonomy is worthy of being called ethical. Such a state is an attempt to avoid moral and ethical choices and does not attempt to cope with them.
The second part of the problem, where freedom is the principal value and is not forfeitable, is that it conceives of choice in purely negative terms. The mistake made is to confuse mere choice with free choice. Similarly to how the prudential account mistook individuals’ ends as being formed ultimately by the individual, this account of the ethical presupposes that choice can be a matter of pursuing first-order desires and does not require whether one has considered if such desires are worth pursuing; one could be moved entirely by instinct and therefore not by the faculties necessary for a real choice. If choice is simply a matter of determining how to maximize one’s satisfaction and is not concerned with the qualitative nature of the desires themselves, then reflection, deliberation, and thinking more generally are simply instruments used to obtain happiness. They are means employed to satisfy desires. But if desires go unchecked; if they’re taken for granted and assumed to be worth the attention we instinctively give them, then a choice was not made. That is, second-order desires are not taken into consideration. Acting purely from first-order desires is to be caused to act by impulse, instinct, or inclination, which determines the action, and not by reflection. It is through reflection and deliberation, through considerations formulated by one’s own will, that one truly chooses. The philosopher Immanuel Kant distinguishes between autonomy and heteronomy. Understanding this will clarify the argument. To act autonomously is to be an originating and self-determining cause of an action. To act heteronomously is to be caused to act, to be moved by influences and forces outside of one’s will. Thus to enact a choice freely one must will the action and not be motivated by what is outside of the will. The philosopher Paul Franco writes in his book Hegel’s Philosophy of Freedom, “Kant rejects the naturalistic understanding of freedom as exemplified by Hobbes that sees it as the unimpeded pursuit of one’s empirically given desires. In giving into natural desire or inclination, the will is determined by something other than itself…” From this, it can be seen how acting from desire does not constitute a free choice. If desires are conditioned by the external environment, then the expression of those desires was not of one’s choosing but is due to the conditioning that took place in the development and upbringing of the individual. Mere choice, then, does not constitute free choice.
But why, it may be asked, is this problematic? Even if the individual’s choice is said not to be fully free, why should the state concern itself with this? It’s up to the individual to discover their own freedom. I don’t necessarily disagree with this. It is not that the state should interfere with and enforce that individuals make free rather than mere choices, but only that it should concern itself with realizing conditions that are conducive to the development necessary for individuals to actualize their faculties for autonomy, which is located in the more qualitative dimension of subjectivity. The aim here is not to precisely articulate how the state should do this, but only that individual autonomy is the end it must strive toward. To hold this as secondary is to treat human activity as being in service to something other than itself; as if human faculties are meant for some other end. This is false. The state’s aim is to play its role in treating human beings as ends-in-themselves and as the reason for its legitimacy to have any authority. To do otherwise is to confuse self-interests with morality.
Conclusion:
The ‘ethical’ network state holds autonomy as its principal end. Its goal is to discover how to best contribute toward formulating conditions conducive to realizing this. What the government must precisely be, what laws are best, what institutions are necessary, must be understood in these terms. To do otherwise is to be confused about what activity one is involved in, which may lead to dehumanizing environments for those who opt-in to states that fail to live up to this standard.
-
 @ a012dc82:6458a70d
2024-09-25 01:45:03
@ a012dc82:6458a70d
2024-09-25 01:45:03Table Of Content
-
What is a Bitcoin Paper Wallet?
-
How Does a Bitcoin Paper Wallet Work?
-
Creating a Bitcoin Paper Wallet
-
Benefits of Using a Bitcoin Paper Wallet
-
Conclusion
-
FAQ
Bitcoin has become increasingly popular over the years, and with its popularity comes the need for safe storage options. One of the most secure ways to store your Bitcoin is by using a paper wallet. But what exactly is a Bitcoin paper wallet, and how does it work? In this beginner's guide, we'll explore everything you need to know about Bitcoin paper wallets, including how to create one, and the benefits of using them.
What is a Bitcoin Paper Wallet?
A Bitcoin paper wallet is a form of cold storage for your Bitcoin. It's a physical piece of paper that contains the public and private keys necessary to access your Bitcoin. The public key is used to receive Bitcoin, while the private key is used to send Bitcoin. Since the paper wallet is offline, it's considered one of the most secure ways to store your Bitcoin.
How Does a Bitcoin Paper Wallet Work?
A Bitcoin paper wallet works by generating a pair of public and private keys using a random number generator. The public key is used to receive Bitcoin, and the private key is used to send Bitcoin. These keys are then printed onto a piece of paper, along with a QR code that represents the public key. You can then use the QR code to easily send Bitcoin to your paper wallet.
Creating a Bitcoin Paper Wallet
Creating a Bitcoin paper wallet is a simple process that you can do at home. Here are the steps to follow:
-
Go to a paper wallet generator website, such as Bitaddress.org or Walletgenerator.net.
-
Disconnect your computer from the internet and ensure your printer is not connected to a network.
-
Generate a pair of keys by moving your mouse around the screen or using another form of randomness.
-
Print out the paper wallet, ensuring you print multiple copies and store them in a secure location.
-
Send Bitcoin to your paper wallet by scanning the QR code with your Bitcoin wallet.
Benefits of Using a Bitcoin Paper Wallet
There are several benefits to using a Bitcoin paper wallet, including:
-
Security - Since a paper wallet is not connected to the internet, it's one of the most secure ways to store your Bitcoin.
-
Control - You have complete control over your Bitcoin since you're the only one with access to your private keys.
-
Accessibility - You can easily access your Bitcoin by scanning the QR code on your paper wallet.
-
Backup - You can print multiple copies of your paper wallet and store them in different locations as a backup.
Conclusion
A Bitcoin paper wallet is a secure and accessible way to store your Bitcoin offline. By following the steps outlined in this beginner's guide, you can easily create a paper wallet and start safely storing your Bitcoin. Remember to keep your paper wallet in a secure location and make multiple copies as a backup. With a Bitcoin paper wallet, you can have complete control over your Bitcoin and protect it from potential online threats.
FAQ
Are paper wallets safe? Yes, paper wallets are one of the most secure ways to store your Bitcoin since they're offline and not connected to the internet.
Can I use the same paper wallet multiple times? Yes, you can use the same paper wallet multiple times to receive Bitcoin.
Can I store other cryptocurrencies on a paper wallet? Yes, you can store other cryptocurrencies on a paper wallet as long as the wallet generator supports them.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a03b38f8:2c7ce1f0
2024-09-25 01:04:52
@ a03b38f8:2c7ce1f0
2024-09-25 01:04:52-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQv/clUvo/uJPS2NodjoiSskIjK+IQkSzGxjGCEPO6jzRBVK zY+rCNUEEv6i9EB4PAeihLEQREBm3zZqLsG9OeVnxIy0AWLQcBrH4WHQuIlRfii7 7SifuNky5LkBcguKVBe9NWDAmzgMP+Y8KKUTSeMUF1qNUPKKGCezvrjAjSojDvQK Jh4sewLMMI1ALihduxKOwLaZpinqyubOQz9LOB2oZg1xLpjXkGNbLQbsT3Aa3/dj MAojIp6qG8mERTtDB9C0ti+dNTn0mYtQPblHSZR38Ze25YYhYunRIlSUjPmI2233 VgTYYW3V9mci3v6tMdvO/lzgGVpb2EaqT0wxU0EqoM4knu7JFq0oqfGqtD4Wr4ro QnHuUprjH8qYFa4fpXTnY9f0OKxOacsBQenHvG9AQH+XZ/mSFcpUjZQJQmb0SYzK ZiWo6t3hIjg6lX/eXg+PixkgljLpbdIOZZb9PHK/aLfr47lEf0hCGfEptda1CZtH v377/o/psGdL2nYQdpab0tFNAYwDa7LaaxSYix6XU/8ew7Hfp0upIPE0SDxzKBJ2 +qlcIVxthOKoIjD0wnSy49UjqJGPFm4X9yfZUEtWqXr622cIHMmkmL3gm1xi+FSt /SVs3X5zypDYRxDilOeoimW1Vh1J0aQAWCMDPo1MuGkgZ6SdQ5sWOUnmBcGdhPWw DkXfkz5PL4tWrQxQiuUWbaXGDH0OTAYGc5LjFsZhMVE4hdJ48Gli70joIdrZUiSr MHGBdpQQtZFMN7xdWpag42aHxObnHvGP+NhIBT349Lp+/sfnFvQ7nPGhBSOI//va 6H/AtwVgWDM+J1KIdE/phgIPhGG3x8xGb4Lg8WB3YbBmJtTFO0G+ni8KjnZ73tvY o/U2bZseubIuVccQPt0igy8zSXb/FLuRF7Ns1ZRZnrs66Au+QzpvX0Lcyi/6JTDV 1OAC18PHWmgtKktfKD1D4y9CRMaBrgK9AFYPKONkxc4unnyotYgkPKgXsuENKde1 4LtBb/Atj+REalCgezGoyvp5jck5+SBSug29/csijUZBliv2iaiZ0dhEbMVB1rvo ly4n7CgKEoC4FPVsqiUOyOHkU8YqoUfeBz65MbtiALKBymmDvw8tSQnNA1LpnW3R In052B5akP2xE2/h2WXaxgDyR9gu2z+BkK1TN2tcSkrZ+SIauuyeAicXbjqBAuqW fJ1WOxgg5Rj9DCUS08e03CRSMYFQVVf3F1kFc6lsc4Y8tqvPQZiF9dOd8dGnpo76 5D9l8f7YwyuwkHlJ7oPTnCCpOIWvcUEVDmwDd2j4pEGMVA9K/IF02sjRCDG4Ktap VxosdEBWWJyQLz6USb17w5nRJ8yqlM3nv6zYak1G4e0Y9SPTeMKDFnw9z70/LGMI r1YTeWXrGA3qvaU1G36GOUZov7g0JLgffafJ+yN5Qccqn3EtIwHEaL6MLr6VOjoy M/pL0tadnxo+qkyOWpo/V5sz/MvoXvPO2f+LNy9POOVQaz8KMJB3gieJilJpCNIs 54N9ciu8Qe5A7oeD4PJ1GE661RLoaZDth3lq5VclNW+bcWr3Hd/mWTN1TnrGt1K3 E0PT+2B/m0UPVUrIFb/ZrIng27x8oKuNTa0DyyKtVvuOZl8DjXmtrN/yHI8rPTI9 Xa9Gfbf/yxcKUIEWGSM0Ujmrt2MoqnYR8rplNWXSBSRblwP2UfrC2C/hEVmc4KA+ DxCahylqF3LJNiG/0IHHXTd6g7gl2AuQIfaCVGy7x6OADQnvM4QlcPXkgcGrXqpp prnhE6W599Y+lvO80Ng3u2sQb9PgauWf62NMLochN66Hi6Bl4Ge0S+mey0/vNmvO K8IBwYxix/pQ7xKFyuI2OKOkBqPEMmvSLCMYI+3qa/r91S7R0GNuX7cZHU1mRNcq 21GSpgnjG985Rb5UzWrfk2HgDM9rgNuQ8o0NTiv8gYZlQWegsmczdAu5vZX9/48/ TnSNIVjfImDLEhXHTi5K2++Km8bVjYg1/gTV/dfrQ58sNdbnc2wzzCbdQ5/NxSHr 1m8h+0TzyWhNIKEWoZctk0qJKnXMfMcsxuju4zREPclm0l311yTauO7up9A/ogjB XhInGpHt4KqQ/GiIjweJPWYc/m9XwTCfRvq/JQCwv23TX6dfRDR/AKqJ8mo6VWZr rD9mpr+r85kS3Z0WFcN8CjWB5Za6Reo1XFeTdReNdsefEipmrnHDleU8NBVF1YZU 294hGSGpu5hn6arpWBg/CUK9SqkSrYePL3hCitjLswvP+rVxg2jHSUY2TPt8/6kg GaBxt3dn0ENHlPSbOk0nT8ik4pwpbdg52oOjohJOjXE+nQIXA5apOtVoGy5O5h9r mQn2eQZ5hLrqIhW7kU9mqW4XXtTEns5AcNtwGLoNpd1DMR6rGnkXSozStrPzovp4 lRTpOa4NsuFcUd++HlJHCVw0tXKuYttMcqwT4/Bt70qwtpZKueo7fcqbkLW5068Y RoRy5fUoYUlaHqLwT9TgWspR83xLjKViZqoVtZjxaKE8uRTh39JtFfw8jSM2BFRL rW+AHGm3SZnwYyOQUXbd4rjx89rHs7042QUGCJU61f7CBdYxfgshFA69Uew84O6r DTlYdSPcn5XKwWbZlt9/qkGfRem4L0u9W4YQevVmg8id23GI5z8O8FvMlqJ/2DKM ggYL5CAyUMs05pK2h9wC2oHgoGNy/4r3aoY4pyJR/LIVjW2zYTfK9t+Kbgy2RK4S 9ogGs7tWfOCy+sUyZMKwl8FLjQvttfDu9j2L8hAF0usPS8yLujihc1px6Mu/TyT1 FpBXE6dXRPMV9vNLB6EEEMvsWBjAkw32jI69jJoGBEKeyRFlAvTkYps6bJeW/4U/ T6RfLV4AqSD/p6k64TdOI4QYAXeIkwDFYG0TiwIr09cLzkRKEMlkzOzfpRbJPdpA taNHta1yPDr3sLOBF1CfilFF0HlXkc5+Foj7J9gPEfE3YaXLjuws5ejsHQF7Tjri sba0WBH4vhTK8c9KceV5oSo82oZSUcAylrufyxXEcmMWuY1OZuLeYIGNIDhlXRpR pJLpZZ6eCn6foAvRgmRHjth6A9sJ4X9t3Zh0YYo9jsIssPfSlcEhQ9acOe2jVjYk iDxBZiQA+X7GguRDH2zj9nW6fKEDfWWKpjjfq3yRd4wVfa0XChs8hKFURYRCJnZa eHUSjgqZXsVhk0J8FCBTyMsL2s5ePhrvKgxC5jqMjznv0B5CQRw0qoRwPWM2aEO1 hnT9smHehCiadCT9GVNMGQj1NSwOH/4dzDm8utt7XssbagUF2Fn+pDUphKYFJV7k WJIQNpQTC4IHzqjF+NipjAxxmUrSaCqyWLAy4WYJ0u7uAhU+6LoQ4wvQQTxWapbf w/sc2ua8IOxh/BwCB7vq32gYnskwkWJB6DQg1PqjRYwqJzOCETYlfVklqswbxIjP po6KHjlGzRAi0pfipQiQfAjMDIqfGMucNYO9k81aOMzBpp0KcOqaKB9FO3CUZnfi s7l0Vh0EA0dvrl0Qpp5xi1K8zKtF+TtjDmg/M4l5i9VB3Lpl1lOKlsDgFUee+g3d UdwORMjByrFBLIGe0+Rmo/Gak4rrk5QH/ErIMeJumhWcwlwCfr00s7QGY09LKUzd mQGL1MK+4w4HiLe+kdbHe0frcdjBiDEuZReW+SGKPdMrvWEsy4yr2JfIQ4NmbHD7 EdOZmojCOWkJAnbz/pZ59O/BJbuRRlY0MVdxfw0foXnINteMVmJ0JUYg/YqB2J7+ 2MXhyqTCiiJcziDU6s+9Gm2PWP8ihkgwrlfjG5bOWBRyGyaKT1ryMvP0+4J2Q8Vd dbM0zEwk8JwW2Snro3vinVPxA1vrEnkQ5TJUZuJqCasgEL5XaOXRtdOJCa9FDGIo UEz2IyN8G2MrHAzxB2SQ8kshycUsDp3K1tJYt+GeDmkWi0owYEFkb7cbHtbY33Kk bRZBS8ghwXIp8hy8AXXerIFh6kzENcP8P+jpHRBw4WWZ/k7Tp9fXxjkFnXZjQ24s wkiBz+kUN3FdZJOlSggiQDSntN0D2cApF/+NVTwQp4rZBWTw8e0PuJs2vne9vh3L eNci6g2B1Lxf6jWa9eZgcqQYZCtLl6ClVQM879jZo2o1+I0ta3S2p6u53llf10Pf Ad0vfj5AhBAkMbSvrgCiFyiMpjO9mIKpF/47XtyVEdcF1bx8ul5eewWTMrK7PMsn aTrVqwlmfQa8qPtuQr2OKsdKR//UlM0dSoyjQai2vZPyAosgbjiE9khAaKBKJaeK OC6gFPQemmGc4hVlGB0Cs+Dubg0OCoqpqOPitLh6TBCwqHcNso1Uz/qf7YsdKdJ5 6A3J1w7HV6f/FJSNZ7dPU1nFuWiJfMwn/1hGbQaWM/Ln4EQIDjspJYZTtY/8BOhI L4RJeU6vNTm2trmumgBKGuovSq1vZ/UWxEJkXCK9N+W2cLl7A2u8vkkCLj5oxr3y ybDvfd7kPZ+aZSW6Y7eA5CWehsh5PtJMtOaNGfCl6jynCj8xG1NKxWzewKv9Gs0E TM7+QqXrmuANuGYT0h5xlO7bXJpwynKX5mzvNuuq9kzUoikj2ucoVxKvhMi73Jvz 7I0EjJFXER30EovOdL6V9jAUk9eITx3cGQ/acHGnUVK7Ncq/bWd4/P0StQeINdN5 8TgUjKS0Wc4Y5gstdJXnJcQx3/pXSQAvsujgDQGWQCDxEU1t6YKu7UNuZG0gLmYi ZyRXKbKzlw10Tm28608D+zMJ/ZlJenqohm7g4YQV7T7/glZKFbqx1q2Inw67aLdj zr2m5KU1Adert+KfDKA6PvwBHGOPBkza0z1EdG2ft2xA6HjQfbRyNO+7iCwesJb4 54qGc9apW4+facRCNgQVCtEG9h2yrnqmDG8k3poSQagHaRUM0+kUq4g+ABPEi1/G xr6hkKmoniD9vmZKveyIzjuDXtMcIIezUCttDI5rssct2tIGBBq9uckduWb8dw+1 fWoje3NxxSiogQCeXrZLq8T8viPz3b/SpQHBpa8PfJ4+ljCH6Fzf0Jf5r3aViVb/ G8BxXuU5UdSaCs/MVdgLyrJWMpMoOTawXomEdl6Sty8BSn3kJPJ3WXK9tUIyyeg6 AvX+IJ22UldmfrhYu1+PI4hLz2GHY/NR5KT4VIUaYfSknnzhfj+dRGSSoT8H5ptM P58t0Zb0CwGwu3q3YsNosahnYo4d5eS1h39GbO1Bd4hSQkjbQ04aDYl1qIdXtaII 2ydLgWiWgCS4w7fsHohmvibOxCnGBblhY0bA9PlMUU4FX6VyS2DkrVcsltPX1+ZL cjmZiwOFzyiX6pYWuv8n7uWVW/tylWEsrxoSRYP2Ey/4HDHZ7F8AuCt7ouaJBoLW AksJt76BlYJGI7RS9tsjl97Jxi2gp2P4dAi5J95MQSGBWw5S60e9luMbR9yw8kHb 8TLEYxKfNdj6Uq0Phqa5tEkiU7UwttW2VBXS6fgyEYYcWcbruNs+T142VRhnGaTw CnoenePc7aFK+h+8bBP2PCJCTLNigM3dfJ3Zd4ch8xA3oKj9rxjDy6bh4HvOHsHP eimWuDNMKUvZ6tTQcN0Nl+MpqUgDqItmrkZB1wCNmitKzbEBN3uIGTpFtDHVupLb 4XyvlUwqdGhJrcPdUZy3JjulTkaGbuujg86JY0CCgLdVUyqofGI5YgKOx4x2L4RJ bxHb01iByLslLhG120Np5IkK4qSn9MGovQaqkoWm3ADFBSeFQGiTyemN4OPoKSZN mQAwp1dyNf7K7m6FlG5PHWXH3m2td4R6v2EHWN7IM1V5WqwG29wSCkKNjAKA0TZR K1Hy+bZDL0o1m2OwMhQvGY9oIpQr2rfTSWdknE41WR8Eqdg365ftWnQje+IEpKQU kyUfbKMd7iBFhM38OA2nSajugCbt5e/t5GoTMDvXXkKbpmIfpKk/rpBdxmkjDNFV ZgQ6tc/ySqft2+pmzj3g8vfDDzKMRN6W/q2N8TXc1tkcVqPOfjId97o5TTW+L8ME sQdKtssQGe9ICOJbXd1XM2AllrVZtsMRDe+4qxrky865p/qVNaJ+laotdNV7glJT 26PHqHlHWJN1mONoiLCaiqYRyNygsIc6fANIEKbEJxjdjW7mq579IYu0QAbsITwc NW7IAomk4vz5YVPEJIr/i1twERWn9IYvDjMroO1U1D7P3/Z1sE+xtU/0HVvvXLoD GD79KIr9nUDJTKKZyefy00piEyBJz9gHdJkryqBuAaODIPrWSs5nNS+MJc6fSv6j aQJdFcNQGuoIYtjHF1lz4cMSjd8pJlADIwrLt28NLL+Y/wHT6WUzpsWIOxwgJolL EnNDOaCBDk17CDoKWoqvT8RfYwUvtpK4QrEtLwOygEcObIaSjrMDkPropZRbiT+i dDQIK8T85ggYNrb9XZGwVbKEMiOnTxgsa/mxykAwi7Xp+5FDKS6HJS4QvE45zZY9 4j3azT3sqv9NIyTZKFnjLFIxWez5I+PWupuFY/oFC81kFvTI/OtJcNqKRIRlfv7M h/LNKrdmsJ4JC+Jn+SCZ5BXD/q/aaWPSzXgSMTnXOtTNi0Nsxp7roUuPZjvXt/s6 WyPf4qpN7GtBF1htg0uVfdSO2B9eVi+xU4Ly7uR+G+yI4oUDbHx3oBdoIoExwBRm Mu+arV9ELEkpHmidEjFuM1AB1C2gRH+H2mghF4Axxw== =6MjS -----END PGP MESSAGE-----
-
 @ b39b8e83:0e391257
2024-09-24 22:10:59
@ b39b8e83:0e391257
2024-09-24 22:10:59For widespread privacy, we need a social contract. People must work together to deploy these systems for the common good.
Privacy isn't just personal. It's a collective effort. The more people use privacy tech, the stronger our defenses become.
Adopting privacy tools is a form of solidarity. When you protect your data, you help protect everyone's.
Education is key. Teach others about privacy tools. Help your friends and family set up encrypted messaging.
Support privacy-focused projects, businesses, & developers. Contribute code, donate, or simply use and promote these tools.
Normalize privacy practices. Make using encryption and anonymity tools as common as locking your front door.
Privacy as a social norm benefits everyone. It protects whistleblowers, journalists, activists, and ordinary citizens alike.
The social contract for privacy: I'll respect your right to privacy, and you'll respect mine.
https://image.nostr.build/f235113e856a4adfa13b25dd703f46e17bbeef3f40bbdebacacc5e0fc0063f79.jpg
-
 @ 3c7dc2c5:805642a8
2024-09-24 20:55:43
@ 3c7dc2c5:805642a8
2024-09-24 20:55:43🧠Quote(s) of the week:
“Civilizations die from suicide, not by murder,” according to 20th-century historian Arnold Toynbee.
He claimed every great culture collapses internally due to a divergence in values between the ruling class and the common people…
"Constant inflation is a human rights issue. It basically prevents people from building up liquid capital reliably. It either forces them to monetize illiquid things like real estate or just keeps rug-pulling them year after year and they're never able to build any serious capital and better themselves."
-Lyn Alden.🧡Bitcoin news🧡
On the 15th of September:
➡️More than a week a week ago rumors circulated that Coinbase is writing Bitcoin IOUs for BlackRock and they are suppressing the price. Now fast forward to today.
➡️Power bills increased by $300 per year for each home in a Norwegian town after the local Bitcoin miner shut down.
The miner paid 20% of the area's grid fees, thus subsidizing other consumers. With the miner gone, people's power bills are skyrocketing.
Aledander Ellefsen: "Politicians fall into the cobra effect trap once again: "The mayor cheered the shutdown of the controversial Bitcoin mining data center, but now residents are facing an unexpected consequence: a hefty bill increase."
Locals will now have to pay an extra $200-$300 per year due to increased costs to grid fees without the big mining customer, and the mayor of this remote municipality comments: "We work continuously to facilitate the industrial activity we want in the municipality. It may not be something we can solve in just one month, but we are dedicated to promoting business development every single day." (This is political jargon, for it will likely never happen.) The "celebration" ended the moment they got their first bill - You can't make this shit up
"Some people do not understand that Bitcoin miners lower the cost of electricity by spreading the grid's fixed costs over a larger rate base." - Pierre Rochard.
A fun fact about the Norway example is that in Norway and will quote Alexander Ellefsen again: "About 97% of our electricity production comes from renewable energy sources, with the majority generated by hydropower. In the northern regions, we have hydropower dams where excess water is released due to low electricity demand outside peak hours. It’s perplexing to see how some politicians continue to overlook Bitcoin mining as a potential solution. By utilizing this surplus renewable energy, we could support the Bitcoin network while ensuring better energy efficiency and reducing waste."
➡️ETHBTC just traded on a 0.03 handle for the first time in 3.5 years (Apr 2021) -53% since the merge in Sep 2022.
Daily reminder that all shitcoins are trending towards zero compared to Bitcoin, including Ethereum. Remember when all the altcoin fanboys were talking about the flippening?
➡️Microstrategy has 244,800 BTC. In 2025 when 1 BTC goes to $1M their holding will be worth $244.8B.
➡️Duo9BTC: "Coinbase CEO just admitted that you got to trust them on their word. They will not provide any proof of reserves for the BTC they claim they have, nor any proof of backing for their new paper BTC called cbBTC. If they print too much paper BTC they will go the FTX route."
Once again...never leave your coins on an exchange. Period!
Rumors are circulating that Coinbase is writing Bitcoin IOUs for BlackRock and they are suppressing price.
Imagine a hacker gains access to Coinbase’s 2 million+ Bitcoin in custody, sends it all to a time-locked address, 100 years into the future, and shares the private keys publicly.
➡️Bitcoin (+43%) and Gold (+25%) are the top-performing major assets in 2024. We've never seen these two in the #1/#2 spots for any calendar year.
On the 16th of September:
➡️President Bukele announces that El Salvador will no longer borrow external debt to finance its budget. Bitcoin country is winning.
➡️MicroStrategy announces plans to raise another $700M and buy more Bitcoin with proceeds.
MicroStrategy increased its capital raising by an extra +$175m. It will now raise $875 million to buy more Bitcoin and potentially raise another $135m within two weeks. Eventually, MicroStrategy sold $1.01 billion worth of convertible notes to buy more Bitcoin.
'Michael Saylor found the infinite money glitch: • Convert cash to Bitcoin • MSTR goes up • Take out more debt • MSTR goes up • Sell personal holdings • MSTR goes up • Issue more stock • MSTR goes up • Join the S&P 500 • MSTR goes up' - TheBTCTherapist
I will quote Dylan Leclair on this one: 'Rather than purchasing physical infrastructure & energy to generate computational hashes, the world's most efficient Bitcoin miner is short-selling dollars & leveraging common stock volatility.'
MicroStrategy now HODLs 252,200 Bitcoin worth +$16 BILLION. Average cost: $39,266 per bitcoin.
On the 17th of September:
➡️Bhutan and El Salvador now combined hold 18,900 BTC worth $1.1 billion. Thanks to its vast hydroelectric energy sources, Bhutan secretly started mining Bitcoin in 2020, now holding up to 13,029 BTC total. Game theory has started playing out and it will force every country to adopt it.
On the 18th September:
➡️BlackRock’s latest report on Bitcoin includes a striking comparison table, highlighting how Bitcoin, the S&P 500, and gold performed after major geopolitical events.
On top of that the world's largest asset manager sees bitcoin as a geopolitical hedge against the US debt crisis and dollar instability.
➡️The State of Louisiana becomes the first in the nation to accept Bitcoin via the Lightning network.
On the 19th of September:
➡️'Everyone who's been daily DCAing Bitcoin is once again in profit. Even those who first started DCAing at an all-time high 190 days ago.' -Wicked
➡️The first nuclear-powered Bitcoin mining facility in Pennsylvania, operated by Terrawulf Inc.
On the 20th of September:
➡️BNY Mellon, America’s biggest custodian bank, has received SEC approval for custody.
Source: https://unchainedcrypto.com/bank-of-new-york-mellon-identified-as-first-bank-to-receive-sec-exemption-from-sab-121/
They are the world’s largest custodian bank with $50T under custody. The game theory this will kick off is something we’re not ready for!
➡️Bitcoin to hit $200,000 no matter who wins 2024 US Election - Standard Chartered, Head of Digital Assets
➡️SEC approves options for BlackRock's spot Bitcoin ETF.
Joe Consorti: "With the introduction of options on bitcoin ETFs, sophisticated investors can now generate yield on BTC. Get ready for a huge influx of liquidity from big players looking to sell covered calls, drawing bigger players into the game, more liquidity, and on and on."
💸Traditional Finance / Macro:
On the 17th of September:
👉🏽"Warren Buffett is hoarding more cash: Last week, Berkshire Hathaway reported that it sold $229 million of Bank of America stock over 3 trading days. Since mid-July, Buffett’s total sales of hit $7.2 billion or 174.7 million shares. As a result, total holdings fell to $33.7 billion or 858 million shares, the lowest level since 2018. Berkshire Hathaway's cash position surged by $88 billion in Q2 2024, reaching a record $277 billion. Warren Buffett continues to build his cash position." -TKL.
🏦Banks:
👉🏽No news
🌎Macro/Geopolitics:
On the 15th of September:
👉🏽The Saudis have joined other Asian countries in ditching their long-term sensitivity to the gold price. Evidence suggests the Saudi central bank has been covertly buying 160 tonnes of gold in Switzerland since early 2022, contributing to the current gold bull market.
On the 1st of September, I already shared the news that global net gold purchases by central banks reached 483 tonnes in the first half of 2024, the most on record. This is 5% higher than the previous record of 460 tonnes set in the first half of 2023. The East (China, India, Russia, Saudi, etc.) no longer trusts owning Western reserve assets. Even in the West, the trust in the bond market is crumbling.
You don't believe my word?
'Blue = Foreign Central Bank holdings of USTs. Red = Total US Federal Debt. Mind the gap (with QE, bank regulations, MMF regulations, pension tax benefits, enticing US retail to buy, etc.)'- Luke Gromen
👉🏽Meloni takes the first steps for Italy to build nuclear power plants.
The Ministry of Environment revealed today that new laws will be introduced later this year and that a decree on the matter will come in 2025 Italy voted no to nuclear power in a referendum in 1987, just a year after Chornobyl. Personally, I think this is a smart move.
👉🏽Jeroen Blokland: 'But, government bonds are a wonderful asset on someone's balance sheet.' Sure, as long as you do not ask who is genuinely willing to hold all that DEBT. The UK government budget is doomed!
👉🏽'The difference between the 2-year Treasury yield and the Fed interest rates dropped to -1.69%, the most in at least 35 years.
This gap is now even larger than in 2008 and 1989, a few months before the recession began. The 2-year Treasury yield is considered a leading indicator for the next Fed’s interest rate moves. In other words, the bond market expects that the Fed will be cutting rates at a rapid pace in the coming months. This has been driven by increasing evidence of the deteriorating labor market and many indicators suggesting this trend will continue.' -TKL.
Regarding the rate cute:
The similarities between 2007 and 2024 are wild!
Fed's First Rate Cut:
Sept 18, 2007
Sept 18, 2024 (high probability)
Unemployment Rate
Sept 2007: 4.7
Sept 2024: 4.2
US Inflation Rate YoY
Sept 2007: 2.5
Sept 2024: 2.5
US Housing Starts:
Sept 2007: 1.238
Sept 2024: 1.235
US Leading Economic Activity
Sept 2007: 100.4
Sept 2024: 100.4
US Existing Home Sales
Sept 2007: 4.5 Million
Sept 2024: 3.95 Million
(This post is not calling for a 2007 crash. I am simply pointing out the intriguing similarities in timing and economic indicators.)
You can find the charts here:
👉🏽Germany's lack of public investment is structural. Germany records one of the lowest net public investment ratios* in the EU over 1995-2023 (i.e. ~zero expansion in net public capital stock). Only Latvia and Slovakia do worse. Net investment: gross investment - minus depreciation
German „green“ policy:
- 2023 25,6% of German electricity came from coal before the decision to close nuclear 31% came from nuclear
- Deindustrialization drives production to Asia, where some products cause 30% more CO2 German Greens ruin both the economy and the environment.
German business model was based on: 1. Cheap energy from Russia 2. Cheap subcontractors in Eastern Europe 3. Steadily growing exports to China All three are gone by now. And we are in the good times, imagine what will happen during the next recession. Germany is Europe's engine.
On the 17th September:
👉🏽US debt now stands at $35.3 trillion. If we were to return to 0% interest and make payments of $1 million per hour, it would take approximately 4,023 years, or until the year 6,047, to bring the debt back down to zero.
The US government has added $5 trillion to Federal Debt in the last 2 years. With annual spending of $6.95 trillion and taxes of $4.91 trillion, the US government is currently overspending by $233 million per hour. Yikes.
👉🏽'Total consumer credit jumped by $25.5 billion in July and reached a new all-time high of $5.1 trillion.
This marked the largest jump since November 2022 and the 11th straight monthly increase.
Total consumer debt has DOUBLED in 14 years. Revolving debt, which includes credit cards, jumped by $10.6 billion and also hit a new record of $1.4 trillion. Non-revolving credit rose by $14.8 billion and is just $2 billion below the January peak of $3.73 trillion. Meanwhile, the share of credit card debt delinquencies soared to 9.1%, the highest level in 12 years. The debt mountain is collapsing.' TKL
On the 18th of September:
👉🏽Federal Reserve cuts interest rates by 50 basis points, first cut in over 4 years.
On the 20th of September:
👉🏽Gold new all-time high $2,620 as markets brace for fiat destruction. Gold prices are up a MASSIVE 28% in 2024 to a fresh record high of $2,660/oz. This puts Gold on track for its best annual return since 1979, all while the Fed is calling for a "soft landing."
👉🏽 Two weeks ago I already explained a bit about the Volkswagen & Germany situation. Now we received the news that Volkswagen is planning to lay off as many as 30.000 employees.
On the 21st of September:
👉🏽"Unrealized losses on investment securities for US banks reached $512.9 billion in Q2 2024.
This is 7 TIMES higher than at the peak of the 2008 Financial Crisis. Q2 2024 also marked the 11th consecutive quarter of unrealized losses as interest rates continued to pressure the economy. Bank of America, the second-largest lender in the US, now accounts for $110.8 billion of held-to-maturity securities with unrealized losses or 20% of the total. Meanwhile, the number of banks on the FDIC Problem Bank List increased to 66 in Q1 2024, or 1.5% of the aggregate.
Unrealized losses held by banks remain a major issue." -TKL
🎁If you have made it this far I would like to give you a little gift: Matthew Pines is the Director of Intelligence at SentinelOne and a National Security Fellow at the Bitcoin Policy Institute.
In this episode, they explore UAPs, simulation theory, remote viewing, and human consciousness. They discuss the potential implications of knowing that aliens are real and what this could mean for humanity - exploring the nature of reality and challenging our understanding of existence, as they discuss the intersection of advanced phenomena and human perception.
https://youtu.be/YN2Le9dp_Ww?si=6eydqVLxCZXLba_V
Credit: I have used multiple sources! My savings account: Bitcoin. The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
-
 @ c7eadcf0:7821e562
2024-09-24 20:14:13
@ c7eadcf0:7821e562
2024-09-24 20:14:13https://image.nostr.build/c7e3732889827ab0a8e2064de5fa6992e37e035347b0c91d249cb8f312b47087.jpg I love Bitcoin. Let me get that out there first of all. I sincerely believe that Bitcoin has the power to change the way the world functions if we can grow adoption to a global scale. This obviously will take time as the gears of economic change grinds slowly. As of right now, people in the western countries don't really see the need for a sovereign politically neutral money that can't be inflated away. They simply don't have to deal with inflation on a regular basis like the rest of the world.
Citizens in western countries got a small taste of what real inflation looks like and guess what? They didn't like it one bit. Overall the last three and a half years you saw countless news stories about how bad inflation and how its making life for the average American or European more difficult.
Yes inflation does suck but look at countries like Argentina, Turkey, Zimbabwe or Venezuela. The people in these countries are suffering from excessive inflation on a regular basis! According to recent economic data Turkey experienced a decline in inflation from 61 percent to 51 percent in August. This is seen as a win in their book! Can you imagine this level of inflation in America? There would be riots in the streets!
Argentina's inflation rate is an astounding 236 percent over the last 12 months! As Bitcoiners we understand that the problem is the money itself. As long as governments have the ability to manipulate the money supply, they will. This is human nature at its finest. When you give a select few that kind of power it becomes irresistible and becomes a tool to control the masses. This shouldn't be a surprise to anyone to be honest.
What I find shocking is with all of this inflation globally no one is really looking around asking questions to why this is happening and looking for a way to escape this system. Are people really this lazy? Not to be mean but cmon. It seems to me that most people are perfectly fine bitching online about how hard it is to make ends meet or supporting their favored political party and wanting them to fix the problem they created. Newsflash to all the normies out there, its the GD political parties that caused inflation in the first place.
We literally have a solution that is staring them in the face, ready to go to replace the current debt based system that we are currently suffering through and no one wants to take the time to research it? Am I black pilled? No, am I realist, very much so. If 236 percent inflation in Argentina can't get them on a Bitcoin Standard immediately, we as a community have a long road ahead of us. Hyperbitcoinization isn't coming in 5 years. It isn't coming in 10 years. Hell it might not even happen in our lifetimes and we have to be ok with that.
So what is the best way to get more Bitcoin into the hands of the people, so they can see the true value of the digital monetary revolution that is Bitcoin. We need a trojan horse and that trojan horse is nostr.
Enter The Nostr Trojan Horse
https://image.nostr.build/5ffee418133ac80ba14b30abf0d5390b878f676cbf6332d67639f9384764da4c.jpg
It should be plain to see by now that the inflation or the number go up narrative alone isn't going to drive Bitcoin adoption. The reason for that is because people don't see the utility of Bitcoin. They see it as some esoteric digital funny money that drug dealers and terrorist use to do bad things.
The average Joe doesn't see how Bitcoin is helping dissidents on foreign countries fund their activism, escape oppressive regimes or simply earn a living. These stories are never told in the mainstream media because they don't want to highlight the fact that a non-state money can circumvent the status quo.
The best way to highlight these stories is to share it on social media, which again is controlled by mainstream gatekeeper such as Meta, Google and X. It is in their best interest to censor these stories or memory hole them out of existence which I suspect happens quite a bit without us even knowing. But the thing about censorship is that it slowly impacts everyone one by one until no one is allowed to say anything without the fear of being put in jail.
Think this can't happen in western democracies? It's happening already my friend! Take a look at the UK or Australia. Citizens their are being arrested over post made to social media. I sincerely believe that these two countries should be a proving ground for showing the value of nostr and Bitcoin.
Introducing the concept of a censorship resistant messaging protocol to them will go over well and once it is understood will grow like a wildfire because people innately understand that censorship is bad and will see the utility value of having the ability to speak freely again.
It is only a matter of time until they realize that they can monetize their speech and build a life using zaps aka Bitcoin.
Until people see the utility in the tools that lie before them, they will never pick them up and use them. It is really that simple. At the end of the day we are still kind of like cavemen. We only use tools when it makes life easier. Man made the wheel. We use it everyday because it has utility.
Bitcoin in the end will be the same way. Utility first, then mass adoption. Nostr is what will help people see the utility Bitcoin and from there sky is the limit. The best thing we can do as Bitcoiners is to encourage people to learn about nostr and show them how easy it is to use and to switch clients that suit their needs instead of being shoved into a one-size fits all solution on centralized platforms.
People like choices, and nostr is all about choice. The interoperability and thelack of need to give personal information to create an account are HUGE selling points that can be touched on. Go out and spread the good word about nostr!
Bitcoin #Nostr
-
 @ 1b5ee74d:bb1aae6e
2024-09-24 19:21:54
@ 1b5ee74d:bb1aae6e
2024-09-24 19:21:54
The days when a mere announcement from Tesla, stating that it would begin accepting Bitcoin for some of its products, would cause a surge in the cryptocurrency's price seem like a distant memory. That was in 2021.
https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105https://x.com/elonmusk/status/1374617643446063105Today, three years later, the price barely reacts to three pieces of institutional adoption news released within 72 hours.
The first piece of news comes from Switzerland, where SIX, the Swiss Stock Exchange operator, announced that it is seriously considering launching a crypto exchange. Bjørn Sibbern, global head of exchanges at SIX Group, stated, "The company is evaluating the creation of a platform where we can facilitate trading, both in crypto spot and derivatives."
The second news comes from Germany, where two of the country's leading banks, Commerzbank and DZ Bank, have launched Bitcoin trading for their clients. Commerzbank is one of Germany's four largest banks, while DZ Bank is part of the Volksbanken Raiffeisenbanken group, effectively giants of the European banking system. Together, they will open access to Bitcoin trading for approximately 40 million customers.
The third news comes from the United States, where BlackRock published a report describing Bitcoin as a diversification opportunity for traditional investors.
Some might ask: “But wasn’t Bitcoin supposed to be an anti-system technology?”
The Economic Incentive: A Core Part of Game Theory
Bitcoin is far more than just an anti-system asset. It’s a technology that incentivizes not only its most radical supporters but also potential adversaries. It’s now clear how its programmed scarcity creates a mechanism for appreciation, assuming demand stays the same. Each event signaling an increase in adoption represents a step toward an increase in the asset's value. The reason why even financial institutions—seemingly unrelated or even hostile to Bitcoin—are drawn to it lies in this market dynamic.
Banks and major institutions cannot ignore the asset’s appreciation. Bitcoin creates a perfect environment for both speculation and long-term investment. When the price rises, even the most conservative financial actors cannot overlook the economic incentive.
This is where game theory comes into play: Bitcoin is structured in such a way that anyone—even those who deny or criticize its potential—is incentivized to participate to avoid being excluded from future economic benefits. Financial institutions, driven by greed or opportunism, are forced to join in, knowing that staying out could be costly.
The Two Opposing Cycles: Virtuous for Bitcoin, Vicious for the Fiat System This process creates a reinforcing effect for Bitcoin while paradoxically weakening the traditional financial system that embraces it. Every time an institution decides to offer Bitcoin to its clients or include it in its portfolio, it legitimizes the asset in the public's eyes, strengthens its position, and further increases demand. The result is a virtuous cycle for Bitcoin: the more it is adopted, the more it appreciates, and the more financial actors become interested.
Shorting the System
For the fiat system, the process is the opposite. Bitcoin’s increasing demand pushes its value upward, while the traditional debt-based and expansionary monetary system loses strength. In this context, buying Bitcoin with fiat currency becomes an implicit shorting operation. Every transaction that shifts value from fiat to Bitcoin reduces the demand for fiat, increasing its vulnerability to inflation.
The demand dynamic is not complex: every time an investor buys Bitcoin, they commit resources that would otherwise have been destined for purchasing or investing in fiat-denominated assets. This reduces the buying pressure on fiat itself while increasing it on Bitcoin. The more money flows into Bitcoin, the less remains to sustain the value of fiat currencies.
Let’s suppose, for example, that a bank decides to allocate $100 million to Bitcoin. The market responds to this capital shift by increasing Bitcoin’s price due to its scarcity, while the demand for dollars decreases. All else being equal, this decrease in demand reduces the dollar’s purchasing power, thus increasing inflationary pressure.
This dynamic can also be expressed in terms of the relationship between supply and demand. While Bitcoin’s supply is fixed and predetermined, the dollar’s supply can be expanded infinitely through inflationary monetary policies. The dollar, therefore, tends to lose value as trust in it diminishes and its supply increases.
This process is not immediately visible, but its cumulative effect is devastating for the fiat system. Once the cycle begins, it becomes almost impossible to stop, as more institutions realize the dynamic and rush to buy Bitcoin to protect themselves from the erosion of fiat value.
The Trojan Horse
Given all this, we can understand why Alex Gladstein describes Bitcoin as a “Trojan horse for freedom.”
The news from the last three days, though seemingly small and quiet, signals a much larger and deeper phenomenon: the slow but steady transition of the traditional financial system toward Bitcoin. The banks and institutions adopting Bitcoin, often without fully realizing it, are contributing to a systemic shift that could lead to the downfall of the very institutions that fail to adapt to the new reality.
These small adoption moves are now so frequent and widespread that they no longer make a big splash. Yet with every move, with every bank launching a Bitcoin product, or every traditional investor adding it to their portfolio, the grave for the traditional financial system is being slowly dug. The actors who remain outside this process risk finding themselves in an increasingly weaker position, unable to compete with a market that is gradually embracing Bitcoin.
-
 @ 3cd2ea88:bafdaceb
2024-09-24 18:58:45
@ 3cd2ea88:bafdaceb
2024-09-24 18:58:45Il viaggio verso il trading smart continua, e vogliamo celebrarlo con te con una serie di eventi incredibili! 🚀
✨ Sfida di 6 secondi:
Partecipa alla Sfida di 6 secondi di Bitget e vinci una PS5, una gift box speciale e 20.000 USDT! 🕹💰
📜 Lettera di Gracy Chen
La CEO Bitget condivide tre storie ispiratrici che raccontano la crescita straordinaria di Bitget e la nostra attenzione ai risultati. 💪 Scopri di più su come sia diventato uno dei primi quattro exchange di criptovalute nel mondo! 🌍
https://www.bitget.com/it/blog/articles/6th-anniversary-letter-from-bitget-ceo
🔗 Unisciti alla celebrazione e fai trading in modo smart con Bitget! https://bonus.bitget.com/U1JNEK
https://www.bitget.com/events/6year
-
 @ d6affa19:9110b177
2024-09-24 18:31:42
@ d6affa19:9110b177
2024-09-24 18:31:42i'm in the upstairs office. lost in some project i've been tinkering with. i feel driven with purpose.
the door is cracked open. i always leave the door open.
Her footsteps echo up the stairway. but my focus is intense; a solution just beyond my fingertips.
the door creaks open, a soft whisper of a sound.
i instantly feel Her presence. a sweet vanilla scent wraps around me, thick and intoxicating.
Her fingers brush through my hair, a gentle caress.
She grips my hair, then releases it— over and over again. it feels good.
a soothing warmth envelops me.
Her fingers glide, each stroke igniting my senses. a chill races down my spine.
the monitor becomes a bit distant.
"You're really focused, hmm?" She teases, leaning closer. "I'm just checking in on my sweet boy." Her tone alluring, already drawing me in.
"of course, my Queen." i reply, my eyes glued to the screen, struggling to concentrate. "thank You," my voice hints at annoyance. "i'm so close to finishing this up."
just when i near a breakthrough, She appears, a siren pulling me from my path. how does She know..? the quiet signals that betray my focus— that reveal my yearning.
"Hmmmm," She playfully muses.
ugh, i need to concentrate. but the way this feels...
it pulls me deeper.
Her fingers drift by my ear, lingering around my neck. nails grazing my skin, sending shivers through me.
my heart begins to race. the screen blurs, reality separates.
"Okay, sweet boy." Her voice is a soft command. Her nails dig in, a mixture of pain and pleasure. a sharp contrast to the softness of Her touch. "I'll be downstairs while you finish."
yet She remains. i close my eyes, drowning in the sensation. i should be finishing this project...
but each press feels like a silent command, an urge to abandon my thoughts, to succumb to the pull of Her presence.
the way She easily captures my attention... it makes me feel so vulnerable...
Her grip finally loosens, and slowly leaves my neck. it wants more...
i barely hear Her leave. but the air feels colder. the warmth of Her presence is fading. an aching emptiness fills the space...
the weight of Her absence settles in, another reminder of how easily She commands my thoughts...
desperately, i take in the remnants of Her scent.
i stare at my monitor. focus shattered, thoughts scattered like leaves.
i linger for a moment. fighting the urge to chase after Her.
the pull of Her absence is heavy in the air. i'm unable to resist. i rise from my seat.
the door is slightly open. She always leaves the door open.
i make my way downstairs, lost in the thoughts of serving Her. my true purpose...
-
 @ bcbb3e40:a494e501
2024-09-24 17:23:00
@ bcbb3e40:a494e501
2024-09-24 17:23:00|
 |
|:-:|
|BLANCO, Carlos X. y COSTALES, Jose; España: Historia de una demolición controlada; Letras Inquietas, 2024|
|
|:-:|
|BLANCO, Carlos X. y COSTALES, Jose; España: Historia de una demolición controlada; Letras Inquietas, 2024|Ya hemos publicado varias reseñas de algunas obras del Profesor Carlos X. Blanco, cuyas temáticas nos resultan totalmente familiares, y con las que coincidimos en un buen número de sus análisis y críticas del mundo actual. Recordaremos, para aquellos que estén interesados en sus obras las reseñas de De Covadonga a la nación española: La hispanidad en clave spengleriana y Un imperio frente al caos, además de algunas otras que podréis encontrar en nuestro blog. La obra del autor asturiano, en este caso en coautoría con José Costales, resulta muy clarificadora a la hora de analizar aspectos generales de la historia de España, cuestiones que tienen que ver con nuestra historia particular, y aquellos hechos que podemos considerar como más generales y fruto de un contexto y unas coyunturas que han marcado el destino de nuestra Patria en los últimos tiempos. Es por ese motivo, que así de entrada podemos distinguir dos bloques claramente diferenciados en esta obra: Un primer bloque que aborda nuestra historia peculiar, las características que definen el «hecho hispánico» y marcan nuestro devenir histórico; un segundo bloque en el que se señalan las amenazas y peligros que se yerguen frente a la España actual, aparentemente agonizante y desahuciada por la falta de soberanía y una serie de problemas graves y trascendentales que amenazan nuestra existencia.
Hay que destacar que el prólogo que precede a la obra en sí y le sirve como presentación corre a cargo del conocido abogado, jurista e historiador Guillermo Rocafort. En un breve pero certero escrito delinea los grandes problemas que atenazan a un Occidente decadente en plena crisis económica, geopolítica y de valores, embarcado en una deriva suicida que hace aguas y se ha vuelto insostenible. La crisis del capitalismo unipolar y globalista enfrenta el reto de la pujanza de los BRICS, con el resurgimiento de Rusia y el desarrollo y ascenso como superpotencia de China, junto a la formación de grandes bloques geopolíticos que definen la multipolaridad que, recientemente, autores como Aleksandr Duguin vienen teorizando desde la escuela euroasiática. Esta situación hace que la el mundo anglosajón y sus oligarquías plutocráticas comiencen a ver resquebrajada su hegemonía, con su sistema de dinero fiat y sus organizaciones pantalla, tales como la Unión Europea, o el desarrollo de su conocida como ideología woke y todas las perversas y destructivas ingenierías sociales asociadas, así como la acción de la Agenda 2030.
|
 |
|:-:|
|DUGUIN, Aleksandr G.; La geopolítica de Rusia: De la revolución rusa a Putin; Hipérbola Janus, 2015|
|
|:-:|
|DUGUIN, Aleksandr G.; La geopolítica de Rusia: De la revolución rusa a Putin; Hipérbola Janus, 2015|En el caso particular de España los efectos de los más de 300 años de dominio anglosajón han tenido consecuencias especialmente perniciosas con la desindustrialización, la destrucción del sector primario, las ingenierías sociales asociadas a las ideologías de género, donde España ha servido como particular conejillo de indias, o nuestras permanentes renuncias en materia de política exterior, donde nos hemos visto obligados, por imposiciones venidas del otro lado del Atlántico, a renunciar a nuestra soberanía sobre el Sahara Occidental o a las permanentes y humillantes cesiones a Marruecos.
En el escrito de Introducción, los autores trazan una genealogía de los hechos, de las circunstancias que se hallan detrás de las razones del propio título de la obra, «Historia de una demolición controlada», en la que el papel de la angloesfera ha sido fundamental para la situación de debilidad, sometimiento y negación de nuestra propia historia que vivimos en la actualidad. Somos parte de una Europa sojuzgada que actúa a remolque de las políticas estadounidenses y anglosajonas, a través de la acción de la OTAN, donde no somos más que un agregado servil, actuando en defensa de los intereses geopolíticos del Imperio. Dentro de Europa, la UE define otro tipo de jerarquías internas, en las cuales el eje franco-alemán impone sus intereses a los países con economías menos desarrolladas del sur. Al mismo tiempo, también se advierten las importantes transformaciones que el régimen constitucional de 1978 ha experimentado en las últimas décadas, especialmente a partir de Zapatero, con el mayor sojuzgamiento de España a la Agenda globalista.
Todas estas circunstancias adversas, y también trágicas para nuestro destino, hacen necesario un análisis de la propia historia de España, de su gestación y de los atributos que han cimentado la idea de lo español o hispánico. La historia de España ha estado condicionada por su proximidad a África, lo cual ha tenido una importancia decisiva en su configuración final. Con la invasión musulmana del 711 se produjo un episodio de dislocación dentro de nuestra historia, que a partir de ese momento experimentó una situación de dualidad étnico-religiosa y comenzó un episodio transfigurador y de construcción del ideal hispánico que se había iniciado con el reino visigodo de Toledo, y que la Reconquista contribuyó a potenciar. En este sentido, la configuración étnica que resultó de la invasión árabe hizo que las zonas del Norte, donde se refugiaron los restos de la antigua nobleza visigoda derrotada, predominó el elemento germánico que se erigió como motor inicial del proceso de Reconquista, mientras que en otras latitudes del levante y el sur peninsular se produjo un proceso de africanización y semitización sobre las antiguas poblaciones hispanorromanas. Un norte cristiano, germanizado e indoeuropeo, equiparable al Norte de Europa, representado por la monarquía asturiana frente a un sur africanizado, sumido en un caos étnico y de enfrentamientos civiles era el resultado de la entidad andalusí.
El proceso de romanización afectó de manera desigual a los territorios peninsulares, y los pueblos de las regiones noroccidentales como astures, cántabros o vascones apenas se vieron afectados, conservando un importante sustrato indoeuropeo en contraste con las regiones más mediterráneas, ocupadas por los íberos, que ya poseían un modelo de civilización elevado y en conexión con las civilizaciones clásicas mediterráneas. Estos elementos ya aparecen claramente expuestos en la interpretación spengleriana que uno de nuestros autores, Carlos X Blanco, expone en De Covadonga a la nación española: La hispanidad en clave spengleriana. Es el contraste entre una España atlántica, indoeuropea y germanizada frente a otra vertiente representada por la España mediterránea, levantina y romanizada. En la confluencia de ambos modelos tenemos la definición de las sucesivos siglos en los que se forja la Reconquista, en la que, según los autores, pasamos de una etapa inicial de predominio atlántico y noroccidental, con el Reino de Asturias, y posteriormente León, capitalizando el proceso de la Reconquista, mientras que posteriormente, será Castilla, que obedecerá al modelo mediterráneo, quien llevaría la batuta en el avance hacia el Sur y la hispanización de España, porque la invasión del 711 marca un proceso de deshispanización, una idea fundamental, también en nuestra opinión, que el avance de los reinos cristianos del Norte contribuirán a erosionar y finalmente, para nuestra fortuna, destruir por completo.
Como parte de la geopolítica hispánica y su relanzamiento como Patria común, es fundamental que España vuelva a resucitar el eje atlántico y noroccidental, propiamente asturiano, frente aquel castellano, para que recupere su primacía como eje en la reconstrucción de España y revertir así la agonía y rumbo errático que nos lleva hacia la destrucción total y la desaparición como nación histórica.
No obstante, si queremos refundar España a través de un verdadero proyecto nacional debemos ser realistas, y no dejarnos embelesar por los visiones sobreexcitados que representan el modelo Imperial de los Austrias o posteriores reverberaciones del mismo a través de construcciones ideales, sino que contemplando las actuales coyunturas, con el viraje hacia la multipolaridad que está experimentando el mundo actual, quizás estaríamos llamados, o al menos existe ese gran potencial, a liderar una suerte de hispanosfera con los antiguos países que fueron parte de la América española, frente a la anglosfera, que viene perjudicando nuestra soberanía y sometiéndonos, junto al resto de Europa, como una colonia.
Blanco y Costales nos ofrecen algunas directrices para esta reconstrucción, tales como la descentralización de los centros de poder, frente a todo modelo jacobino y liberal diríamos nosotros, como parte de un modelo confederal, que incluso podría apoyarse en la fundación de centros de poder en el continente americano. Asimismo, este modelo confederal, implicaría dotar de mayor poder y protagonismo a las regiones, tal y como habría postulado uno de los grandes teóricos del tradicionalismo español, Don Juan Vázquez de Mella, frente al actual modelo balcanizador de las 17 taifas dirigidas por las oligarquías partitocráticas y corruptas del Régimen de 1978. En cuanto al modelo político requerido, este no es la monarquía, sino la república, por el descrédito de los Borbones y la trayectoria descendente y de decadencia que han venido marcando en su reinado desde hace más de 300 años. En cualquier caso, lo que este modelo debe aportar es cohesión interna y voluntad de integración en el modelo de mundo unipolar, que se viene gestando y estructurando bajo relaciones de poder, redes económicas, comerciales y de otro tipo, que deben garantizar esa capacidad de interconexión. Y, por supuesto, en coherencia con lo sostenido con anterioridad, nuestros autores proponen que el eje atlántico y noroccidental debe representar el motor y artífice de este nuevo ciclo histórico.
Desde el advenimiento de los Borbones a comienzos del siglo XVIII, el polo mediterráneo y africanizado ha venido tomando un protagonismo creciente, que vemos reflejado el el triunfo posterior, a lo largo del siglo XIX, del liberalismo con la destrucción del Imperio y el sometimiento de España y de su historia a los dominios de la leyenda negra, urdida por la anglosfera, y que tiende a presentarnos como el producto de una hibridación de pueblos afrosemitas y mahometanos, sin identidad, y como una especie de anomalía frente a la europeidad prototípica. Un discurso que, claro está, fue aceptado por el liberalismo español con la consecuente desvalorización y rechazo de los orígenes astur-godos de la monarquía hispánica y del proceso de Reconquista por parte de unas élites corruptas, antiespañolas y endófobas, que se sometieron ideológicamente a Francia y al mundo anglosajón. En un principio, esto sirvió para provocar fragmentar la unidad interna del Imperio Español y enajenar el catolicismo de la Hispanidad, y posteriormente, una vez destruida esa unidad, someter a estos países al capitalismo depredador y esclavizarlos por la vía de la deuda. Paralelamente, y a través de la masonería, también se introdujeron ideas profundamente destructivas entre las élites liberales y traidoras, como son el laicismo, el separatismo y otras ideas disolventes que nos vienen desnaturalizando desde hace siglos.
La acción de este capitalismo destructivo y depravado, es la que nos ha convertido en un instrumento en manos de grandes cenáculos y organizaciones que forman parte de un entramado complejo y anónimo, desde donde se interviene permanentemente en nuestros asuntos imponiendo cambios profundos en las costumbres, tradiciones e identidad, empobreciéndonos y reduciéndonos a la más pura insignificancia.
Otro elemento a destacar, podríamos decir una de las grandes piedras angulares que definen la idiosincrasia de lo Hispánico, viene representado por el Catolicismo, que en el caso peninsular también revistió un carácter peculiar, especialmente en lo que respecta, una vez más, a los contrastes internos entre la zona atlántica-noroccidental y la mediterránea, así como con la propia realidad del reino visigodo, donde la Iglesia resultó ser muy autónoma, vertebrada a través de sus concilios. Con la irrupción de la contemporaneidad, este elemento, el católico, de vital importancia durante la Reconquista y a lo largo de toda nuestra historia, se ha visto disminuido, con la propia acción del liberalismo, y especialmente desde la izquierda, y también desde sus propios centros de poder, desde el mismo Vaticano, a raíz de su famoso Concilio Vaticano II, abdicando en sus principios y doctrina frente al liberalismo y el mundo moderno.
En el primer párrafo hemos hablado de un primer bloque, que de algún modo vendría a hablarnos de nuestra historia, de la autorepresentación que tenemos de la misma, y los elementos basales que componen su estructura. Esta sería la primera parte del libro. Una segunda parte vendría comprendida por el análisis de otros elementos más externos que definen unas coyunturas internacionales muy características, las cuales forman parte, desgraciadamente, de nuestro presente actual.
Entre los principales elementos de análisis se encuentra la acción de la anglosfera y el sometimiento que experimenta España junto al resto de naciones del orbe europeo, especialmente occidental, bajo instituciones transnacionales como la OTAN o la UE, que lastran permanentemente nuestra soberanía y nos convierten en meros cipayos al servicio de los intereses de la anglosfera (Estados Unidos y Reino Unido) en contra de nuestros propios intereses. El ejemplo más significativo lo tenemos en Ucrania, donde la OTAN está librando una guerra contra Rusia en la que viene utilizando al pueblo ucraniano como ariete de sus intereses geopolíticos a costa de la destrucción del país, en un auténtico drama humano con la muerte de miles de jóvenes en el frente de batalla. La historia de la anglosfera viene siendo la misma desde siempre, en el que sus teóricos aliados vienen siendo humillados, con multitud de traiciones, y ataques de falsa bandera, la creación de grupos terroristas, promoción de golpes de Estado, compra y soborno de políticos con aquellos países que no se sometían a los intereses del Imperio anglosajón. La base de tal poder, en la que tal imperio basa su poder el capitalismo financiero y especulador, cuyas raíces se encuentran en el siglo XVII, y que sirve a unas élites globales que se sirve de los mecanismos tales como los procesos inflacionarios para empobrecer y someter a los pueblos, a los que desprecia e instrumentaliza al servicio de Agendas globalistas. Al mismo tiempo acaparan gran parte de la riqueza global, que mantienen oculta en paraísos fiscales y de la que se sirven para sufragar el tráfico de drogas o la financiación de grupos terroristas que protagonizan los atentados de falsa bandera a los que nos hemos referido.
|
 |
|:-:|
|MUTTI, Claudio; Democracia y talasocracia: Antología de ensayos geopolíticos; Hipérbola Janus, 2017|
|
|:-:|
|MUTTI, Claudio; Democracia y talasocracia: Antología de ensayos geopolíticos; Hipérbola Janus, 2017|El enorme y desproporcionado proceso de financiarización que padece la economía del Occidente sometido a la anglosfera ha tenido consecuencias funestas sobre el complejo productivo real, redundando en la desindustrialización y la decadencia general bajo las teorías del «decrecimiento». Desde la administración Bush, a comienzos de siglo, hemos asistido a una serie de guerras de agresión en las que se han destruido países como Irak, Libia o Afganistán con el objetivo de controlar los hidrocarburos y las rutas de transporte, una tendencia que se ha venido incrementado especialmente con la administración Biden , y anteriormente con la de Obama, con la creación de organizaciones terroristas como el ISIS y la desestabilización permanente en Oriente Próximo, y el creciente y peligroso papel del complejo militar industrial.
Pero el poder y hegemonía estadounidense están menguando a pasos agigantados con la emergencia de dos grandes potencias, como son Rusia y China, frente a las que la anglosfera ve amenazada su hegemonía económica, con la colonización comercial china y el resurgir del potencial ruso, frente al cual, como decíamos, libran una guerra con intermediarios a través de Ucrania. Al mismo tiempo, tenemos a los BRICS, liderados por Rusia y China, con países emergentes como Irán, la India o Brasil con el papel de potencias regionales. La guerra de Ucrania solamente ha conseguido revigorizar a Rusia, alejarla de Europa y reforzar su alianza con China, mientras que los grandes perjudicados son Ucrania, que quedará en manos de grandes fondos de inversión como Blackrock ante una pretendida reconstrucción del país y las multinacionales que participarán en su reconstrucción, quedando en manos del globalismo. Europa es la otra gran perdedora, empobrecida y sumisa ante los designios del Imperio yanqui, al que rinde pleitesía a través de sus gobernantes, que no son más que títeres. Ante la inevitable pérdida de soberanía en el mundo, la anglosfera también pretende llevar la guerra a Asia contra China, viendo la derrota que está sufriendo en todos los frentes.
En el contexto de los intereses hispánicos, la anglosfera siempre ha representado una amenaza y un elemento especialmente dañino, responsable de la disolución del Imperio español con la introducción de las ideas liberales y masónicas entre las élites locales hispanoamericanas, practicando formas aberrantes de neocolonialismo sobre estos territorios una vez independizados, y siendo considerados como el patio trasero de Estados Unidos, quien ha practicado una política especialmente perniciosa y de desestabilización en todos estos territorios en vistas a coartar cualquier forma de desarrollo positivo.
Otro de los grandes problemas que se abordan en el libro es la amenaza que representa el enemigo del sur, Marruecos, para la integridad territorial española, sobre Ceuta, Melilla y las Islas Canarias, con el apoyo incondicional de países como Estados Unidos, Francia o Israel, tras las primeras y humillantes concesiones que ya se produjeron en 1975 con Juan Carlos I con el Sahara Occidental, y las posteriores, bajo mandato de Sánchez. Al mismo tiempo Estados Unidos e Israel especialmente, participan activamente en el rearme y fortalecimiento del reino moro, que ha desarrollado una política expansionista y agresiva contra los países vecinos. Para ello también se sirve de los lobbies marroquíes que actúan en el propio seno de la UE y dentro de España, que se sirven de las políticas cobardes y traidoras de sus políticos adheridos al Régimen del 78. Las consecuencias no se han dejado de notar en la destrucción y progresivo debilitamiento de nuestro sector primario en detrimento de los productos del país norteafricano, que entran sin ningún tipo de control en nuestro territorio, sin cumplir los requisitos mínimos a nivel fitosanitario. La ineptitud, servilismo y cobardía del actual Régimen hacia poderes globalistas y transnacionales, hacia la anglosfera, nos condenan a seguir un guión sin ninguna autonomía ni poder de decisión.
Otro de los ámbitos importantes que contempla el libro, lo encontramos en la ya mencionada Unión Europea, que no deja de ser otro instrumento de dominación y supeditación a los intereses de la anglosfera, y donde se reúnen los representantes de los grandes poderes fácticos a través de plutócratas, banqueros y poderes económicos y financieros transnacionales. Esta institución ha ido sustrayendo progresivamente el poder de las naciones que la integran con una comisión europea con atribuciones y poderes omnímodos para dictar normas y con una presidenta, Ursula Von der Leyen, metida en multitud de casos de corrupción, entre los que destacan aquellos vinculados a la Plandemia de 2020 y las falsas vacunas. Todo ello sin contar los protocolos criminales que se impusieron durante ese periodo, la represión policial y el cercenamiento de derechos y libertades con la presión absolutamente criminal sobre los que decidieron no «vacunarse» con el producto experimental del que nadie se hacía responsable y sobre el cual reinaba toda opacidad informativa. Desde esas fechas hasta el presente los fondos de inversión globalistas, como Blackrock o Vanguard entre otros, se sirvieron de la crisis generada para enriquecerse y acaparar la compra de todo lo comprable como instrumento de las élites plutocráticas mundiales y sus ansias de dominio global.
|
 |
|:-:|
|NAD, Boris; Después del virus: El renacimiento de un mundo multipolar; Hipérbola Janus, 2022|
|
|:-:|
|NAD, Boris; Después del virus: El renacimiento de un mundo multipolar; Hipérbola Janus, 2022|La Unión Europea no ha dejado de ser, como ya hemos dicho, parte de las organizaciones que la anglosfera, y particularmente el gobierno yanqui, ha utilizado para dominarnos y debilitarnos desde 1945, y en nuestros días también a través de la Agenda 2030, a partir de la cual pretenden reducir Europa a la nada, desindustrializando y destruyendo el sector primario, algo especialmente dramático en el caso español. La UE también nos habla de la implantación de la divisa digital con todos los peligros que esta entraña como, por ejemplo, la posibilidad de que se programe su uso y sirva como herramienta de control social para monitorear y controlar nuestras gestiones, la caducidad del dinero o limitar la compra de productos en función de la llamada «huella de carbono». A ello debemos añadir el proceso inflacionario que venimos sufriendo desde el 2020 en una farsa deliberadamente provocada por los bancos centrales (la Reserva Federal y el BCE) con la impresión masiva de dinero.
En el plano social la UE no ha dejado de implementar el modelo del caos multicultural que viene ocasionando estragos en buena parte de la Europa occidental a través del uso de recursos maquiavélicos y diferentes ingenierías sociales que se apoyan en los mass media. Esto ha generado una distopía social con la introducción de ideas aberrantes como las asociadas a las ideologías de género, con la castración y hormonación de niños o el odio radical y enfermizo hacia los hombres blancos heterosexuales, convertidos en potenciales violadores con la ideología feminista institucionalizada. Y todo esto con el contraste que supone la llegada masiva de «inmigrantes» de países de África, por ejemplo, donde predominan sociedades patriarcales, en muchos casos musulmanas, cuyas tradiciones y visión de la vida chocan con las ingenierías sociales de la élite globalista.
Carlos Blanco y José Costales plantean una refundación de la Unión Europea bajo otros parámetros más democráticos y bajo unos organismos reguladores que puedan controlar los lobbies, las multinacionales y a los plutócratas y frente a los abusos de poder del eje franco-alemán. Una Europa de los pueblos, de naciones soberanas al servicio del interés ciudadano frente a las oligarquías y el gobierno mundial.
Otro de los capítulos está dedicado al papel de las oligarquías y las élites, donde reaparecen algunos de los temas ya tratados, y en los que se viene a destacar la acción perniciosa y destructiva de estos poderes anónimos que actúan a través de organizaciones pantalla y agendas planificadas perpetradas desde el llamado Occidente, bajo las premisas de una ideología misántropa y deshumanizada que es asumida por los gobiernos traidores de las naciones de la Europa occidental. Todas estas políticas se presentan bajo aspectos devastadores en el sector alimentario, con la ya referida demolición del sector primario con catastróficas consecuencias en un futuro próximo, o la fabricación de guerras, conflictos sociales y polarización de la población, junto a falsas banderas y grupos terroristas creados y financiados desde el propio Occidente. En este sentido tenemos multitud de ejemplos de desestabilización en torno a la red Gladio durante los años 70 (los famosos años del plomo en Italia) o con el tráfico de drogas, que ha servido para generar conflictividad social en Ecuador en los últimos tiempos tras quedar cortadas las redes del comercio de heroína procedente de Afganistán.
En los últimos capítulos del libro también se aborda el separatismo y la balcanización de España, un fenómeno propiamente moderno y que aparece indefectiblemente ligado al advenimiento de los liberales a lo largo del siglo XIX. A raíz de una serie de conflictos de origen dinástico, se generó una antítesis irreconciliable entre dos sistemas de gobierno, el propiamente moderno representado por el liberalismo y encarnado en la futura reina Isabel II y el tradicionalismo representado por los carlistas y encarnado, inicialmente, por Carlos María Isidro (Carlos V). Se libraron tres guerras devastadoras entre liberales y carlistas a lo largo del siglo XIX, en las que se dirimieron dos modelos, uno centralista (liberal) frente a otro descentralizado (carlista) con el respeto a las instituciones locales y regionales, a los Fueros. cuyas prerrogativas y vigencia se fueron perdiendo a lo largo del siglo. El siglo XIX tuvo unas consecuencias desastrosas para España, con la liquidación del Imperio y su debilitamiento en todos los ámbitos. Es a finales de susodicha centuria cuando nacen los movimientos separatistas, especialmente en Vascongadas y Cataluña, que irá cristalizando y gestándose a través de un discurso identitario cada vez más radical y antiespañol. La decadencia política e institucional que representa el actual Régimen Constitucional del 78, ha convertido a las formaciones políticas separatistas en los árbitros del sistema, ejerciendo de bisagras en la formación de los gobiernos centrales, con episodios vergonzantes y humillantes como los asociados a la Ley de Amnistía del PSOE en los últimos tiempos. Al mismo tiempo, el separatismo ha asumido los mismos mantras ideológicos a través de sus oligarquías regionales, que el resto de los integrantes del régimen partitocrático en relación a las políticas globalistas impulsadas desde la UE o la siniestra Agenda 2030, a la que son plenamente funcionales. En este sentido el mundo anglosajón, interesado en contribuir a la destrucción interna y fragmentación territorial de España, a través de complejas redes de financiación, como las desplegadas por Soros y su Open Society o las desplegadas, a través de organizaciones pantalla, por los servicios secretos ingleses y estadounidenses. Estos poderes ya tienen experiencia en esta materia, como demuestran los resultados de la Guerra de Yugoslavia durante los años 90, de la que resultó la fragmentación de su territorio en pequeñas repúblicas.
----
Artículo original: Hipérbola Janus, Reseña: «España: Historia de una demolición controlada», de José Costales y Carlos X Blanco (TOR), 24/Sep/2024
-
 @ 1d5357bf:1bdf0a52
2024-09-24 15:49:11
@ 1d5357bf:1bdf0a52
2024-09-24 15:49:11If Bitcoin Is in Its Infancy, Nostr Is Still in Its Nursing Stage Skepticism is healthy, especially within the Bitcoin community. At the moment, Nostr users are predominantly Bitcoiners, and it's understandable that people are cautious about adopting new technologies. However, based on my limited experience over the last few months, Nostr has shown immense potential and is evolving at a breakneck pace.
The Speed of Development: A Double-Edged Sword The rate at which new functionality is being rolled out on Nostr is staggering. On the one hand, this rapid development brings constant innovation and new tools for users to explore. On the other hand, it often means that many implementations still need refinement, or at the very least, better documentation. It's exciting, but there are still bumps in the road that need to be ironed out. Censorship Resistance and Relay-Based Architecture One of Nostr’s most appealing features is its decentralized architecture, which revolves around relays. This design ensures that the protocol is censorship-resistant. If you’re tech-savvy enough, you can even run your own relay, allowing you to retain full control of your notes. This distributed system empowers users by giving them the tools to protect their content and stay independent of centralized entities.
A Protocol, Not a Platform Nostr is not a platform—it's a protocol. This distinction is crucial because it enables a high degree of interoperability, which can pave the way for a diverse ecosystem of applications. This opens up a world of possibilities and allows for network effects to take hold as more people and applications begin to interact with the protocol.
Privacy and Control Another advantage is the ability to manage your privacy more effectively. With Nostr, you can use multiple nsec/npub keys, giving you more control over your identity and interactions. This flexibility is a game-changer in a world where privacy is often compromised by centralized platforms.
Areas for Improvement Of course, Nostr is not without its challenges. Many of the available applications feel unpolished, and spam is a growing issue (the infamous "reply guy" problem). The ephemeral nature of the content also presents a challenge—once you post something, you can't "put the toothpaste back in the tube," sort to speak.
Enjoying the Ride Despite its growing pains, I’ve found Nostr to be an enjoyable experience so far. There are no algorithms dictating what you see, which results in a signal-rich environment with minimal toxicity—for now, at least. It’s refreshing to engage in conversations that aren’t manipulated by unseen forces, and I look forward to seeing where Nostr goes from here.
-
 @ 5d4b6c8d:8a1c1ee3
2024-09-24 15:48:13
@ 5d4b6c8d:8a1c1ee3
2024-09-24 15:48:13This idea had been kind of percolating in the back of my mind for a bit, but on my walk today it crystalized: there ought to be a podcast affiliated with this territory.
GrayRuby, you/we/I should launch something to talk about not just what's happening in sports, but what stackers are talking about wrt sports. I'm not aware of a bitcoiner podcast that touches sports at all.
I'm imagining it would start as a short weekly experiment, covering our game reactions, ~Stacker_Sports contests and posts, bitcoin bets, personal sports stories, and our kids' sports adventures.
This seems like something that could really elevate ~Stacker_Sports and I'm sure we have enough content to keep it going and have it be distinct from other podcasts.
Btw, I'm doing this in public both to bring public pressure on you and to gauge demand.
originally posted at https://stacker.news/items/698947
-
 @ 306068fe:d542563e
2024-09-24 15:18:31
@ 306068fe:d542563e
2024-09-24 15:18:31Looking for a good investment insight?..Checkout “Fintech catalyst”..it’s an exchange; which runs trade in autopilot to generate weekly profits (ROI) https://app.fintechcatalysts.com/ref/Nefrod
Join the discussion group with the link beneath https://t.me/+34-QRRBVj98xMDVh
-
 @ 6bae33c8:607272e8
2024-09-24 14:48:34
@ 6bae33c8:607272e8
2024-09-24 14:48:34So it really happened. The Bengals lost outright, meaning for the third straight week, the league’s biggest favorite lost. The Circa Survivor pool is down to 550 entries out of 14,000 in Week 4. Unfathomable insanity. And of course, I went 2-3 on the week in Circa Millions, and at 5-10, am getting very close to drawing-dead territory.
I’m not as annoyed as I might be because Survivor this year is just funny, so that softens the blow of being out Week 1, I would have taken Cincy this week for sure had I pivoted off them and losing with the Bengals in the Millions contest is offset by the payoff of getting to marvel at it.
I am annoyed at the other game. They posted the score during the Cincy game on my screen, so it was spoiled on the 40-minute version, and once I saw what the score was, I had no interest in wasting time on it. (I did briefly flip to it for a couple drives when I realized it was the earlier game, but then realized eventually it would spoil the game I cared more about, so I switched back.) And in any event (and this is a bug on Gamepass), they flashed the final of the Bengals-Team before the game started from the beginning. I squinted, but caught a 38, and it became apparent in the third quarter which team was getting to 38 and which wasn’t given the kinds of scores they would need.
At least Ja’Marr Chase (three leagues) absolutely crushed.
-
Chase had a huge game, but only seven targets. Why is it teams like the Rams (with Cooper Kupp) or even the Giants (with Malik Nabers) can motion guys and get them double-digit targets and often catches every game, while the Bengals are content to let teams double Chase and take him out of the game for long stretches? I mean this game flow should have seen Chase get 14 targets, not that I’m complaining about the production, but get your best player the ball!
-
Chase Brown and Zack Moss both looked good, but easier to run from behind when the defense is conceding it.
-
Joe Burrow was pretty accurate — some perfect deep throws to Chase, a couple balls behind receivers over the middle — and had decent feel in the pocket. But the offensive line wasn’t great, and he’s no longer a threat to scramble.
-
Andrei Iosivas had his best game by far. Tee Higgins looked a little rusty.
-
The Bengals defense is super soft. It’s the reason they lost to the Patriots in Week 1, they just can’t bring runners down.
-
Jayden Daniels played great. He didn’t average much per carry, but he’s tough to tackle, has great instincts as to when to take off and has a nose for the first down. He played like the good version of Jalen Hurts, only with more tackle breaking ability.
-
Two guys I crossed off my draft list this year because they were older, washed up running backs were Alvin Kamara and Austin Ekeler. Ekeler looked great on a kick return, his 24-yard TD and two catches before leaving with a concussion.
-
I do have a couple shares of Brian Robinson who struggled, but I like him. He picks up the blitz well, gets a ton of goal line work, runs hard and can even catch a few passes. Ekeler looking spry though isn’t great for him.
-
Terry McLaurin finally got going, and it took a full half. Daniels looks more comfortable now, so it makes sense.
-
I’ve said this before but the Jets played 11-D chess winning that last game in 2020, getting the No. 2 pick in the 2021 draft class instead of the No. 1 for no reason and lettng the Jaguars draft Trevor Lawrence. Now the Jets have Aaron Rodgers, but the Jaguars still have Lawrence! As I said I didn’t watch that game, but how much time does he need finally to get going?
-
I wanted to draft Travis Etienne too for the skills and role, but there’s been something wrong with that offense for the last couple years, so he hasn’t been quite able to deliver. He’s like a poor man’s Saquon Barkley — have to get him to a team where he can thrive.
-
I watched the Bills first two drives, both TDs, and Josh Allen makes it look so easy. It’s a foregone conclusion he’s converting the third or the fourth down.
-
Dalton Kincaid finally did something, but the game flow was such you couldn’t expect much for any Bills pass catcher.
-
-
 @ 4735cdca:0c0ecb64
2024-09-24 14:12:28
@ 4735cdca:0c0ecb64
2024-09-24 14:12:28Em viagem recente a Praga, a capital da República Tcheca, fiquei fascinado pelo Relógio Astronômico, ou Orloj como dizem os tchecos. O fascínio veio não apenas pela idade do instrumento — instalado em 1410 — mas pela variedade de informações que ele é capaz de apontar.
Além das horas, ao consultar o Orloj também podemos obter mais algumas informações interessantes: o momento do amanhecer e do anoitecer; a fase da Lua e em qual posição está o Sol em relação às constelações do zodíaco.
Para a leitura do relógio, é essencial entender quais são suas partes móveis.
O ponteiro dourado
O ponteiro dourado tem uma mão dourada na extremidade e uma haste fixa sobre ele por onde um pequeno sol desliza. O movimento do ponteiro é sempre no sentido horário.
A mão dourada foi idealizada para apontar dois horários: o Germânico e o Boêmio.
O horário Germânico é o mais próximo do qual estamos acostumados. Representa as 24 horas do dia por meio de dois grupos de algarismos romanos de I a XII no mostrador do relógio. A primeira hora do dia fica na parte inferior do relógio.
Atualmente o Orloj está regulado para representar o Horário da Europa Central (em inglês: Central European Time — CET) no mostrador do horário Germânico. O CET só equivale ao horário local de Praga durante o inverno, quando o horário de verão não está em vigor na República Tcheca. Na imagem, podemos ver que a mão dourada está sobre o número IV. São cerca de 4 horas da tarde (16h00).
Lemos o antigo horário Boêmio com os chamados numerais de Schwabacher. São 24 numerais dispostos no anel preto mais externo, que representam quantas horas se passaram após o pôr do Sol. O anel gira com a passagem do ano para se adequar à hora em que o Sol se põe. Quando a mão dourada atinge a número 24, chega a hora do pôr do Sol. Por isso, conforme o verão se aproxima (o anoitecer começa mais tarde no verão, quando os dias são mais longos que as noites), o anel move no sentido horário. Conforme o verão se afasta, o anel move no sentido anti-horário. Na imagem, são aproximadamente 21 horas passadas após o pôr do Sol — ou 3 horas para o fim do dia.
O pequeno sol fornece um terceiro tipo de horário: o horário Babilônico. Ele é medido em 12 “horas” desiguais do dia — apenas entre o nascer e o pôr do Sol — e representado pelos numerais indo arábicos em preto, de 1 a 12. Cada numeral pertence a uma linha curva. Quando o pequeno sol passa sobre uma dessas linhas curvas, marca aquela “hora”. Na imagem, o Sol nasceu há cerca de 10 “horas”. O pequeno sol desliza sobre o ponteiro para acompanhar a variação da duração de tempo entre o nascer e o pôr do Sol. Assim, temos “horas” curtas no inverno e “horas” longas no verão.
O ponteiro da Lua
O ponteiro da Lua possui uma esfera que gira conforme o ponteiro anda. Ela é metade preta e metade prateada, simbolizando a fase em que a Lua está no céu. A pequena lua também desliza em uma haste, fixa sobre este ponteiro.
O anel zodiacal
O anel zodiacal indica o movimento do Sol e da Lua na eclíptica, região definida pelo aparente movimento do Sol no céu durante o ano.
Se observarmos o céu antes do nascer do Sol, enquanto olhamos para o Leste, podemos estimar qual constelação estará atrás do astro durante o dia. Ao repetirmos esse procedimento periodicamente, notaremos que a posição do Sol em relação às constelações varia, percorrendo as 12 constelações do zodíaco durante o ano.
https://video.nostr.build/3fd459e963b279a4192da4813aea15c0f6911850b66ae0574c1f0e4180346861.mp4
No anel zodiacal, os 12 símbolos representam as casas do zodíaco e podemos ver sobre eles quais as posições da Lua e do Sol. Repare que o pequeno sol e a pequena lua estão conectados ao centro geométrico do anel zodiacal por barras, que os mantêm na borda do anel (no caminho da eclíptica) no decorrer do ano. O pequeno sol fica sobre determinada casa do zodíaco de acordo com o calendário dos signos.
♈️ Áries (21/03 — 20/04) ♉️ Touro (21/04 — 20/05) ♊️ Gêmeos (21/05 — 20/06) ♋️ Câncer (21/06 — 22/07) ♌️ Leão (23/07 — 23/08) ♍️ Virgem (24/08 — 23/09) ♎️ Libra (24/09 — 23/10) ♏️ Escorpião (24/10 — 22/11) ♐️ Sagitário (23/11 — 21/12) ♑️ Capricórnio (22/12 — 20/01) ♒️ Aquário (21/01 — 19/02) ♓️ Peixes (20/02 — 20/03)
Este anel completa uma volta em torno do centro do relógio em um dia sideral. O dia sideral é baseado no aparente movimento das estrelas causado pela rotação da Terra. Sua duração é cerca de 4 minutos menor que o dia comum (dia solar). Por isso, o anel zodiacal anda ligeiramente mais rápido que o ponteiro com o pequeno sol.
O ponteiro menor com uma estrela na ponta conta o tempo sideral. Ele está fixo no anel zodiacal e foi posicionado entre os signos de Peixes e Áries para simbolizar o ponto vernal. A leitura das horas siderais é feita no mostrador com algarismos romanos. Na imagem, o relógio marca por volta de 2h30 no tempo sideral.
O ponto vernal é determinado pela posição do Sol durante seu movimento aparente na eclíptica, quando encontra o equador celeste (plano imaginário definido pelo equador da Terra). Nesse momento ocorre o equinócio de primavera no hemisfério norte — quando o dia tem a mesma duração que a noite (ver imagem abaixo).
https://image.nostr.build/474de14f26a1c49c339c0c1e820a64101d0bd97a77942a8a0f8566e2191133cc.png É preciso enfatizar que o Sol não se move ao redor da Terra. A imagem acima é apenas uma representação do movimento aparente do Sol para um observador aqui no nosso planeta.
Agora que sabemos quais são as partes móveis, vamos entender a parte fixa do Orloj.
A placa fixa
Já sabemos a utilidade dos numerais da placa fixa, mas resta saber o significado de suas cores e das quatro palavras nela escritas.
Quando o pequeno sol está sobre o segmento azul, significa que é dia. Quando está sobre o segmento laranja, é hora do amanhecer (AVRORA — aurora) no horizonte leste (ORTVS) ou do anoitecer (CREPVSCVLVM — crepúsculo) no horizonte oeste (OCCASVS). E quando ele entra no segmento preto, significa que é chegada a noite.
O círculo dourado mais externo, onde estão os algarismos romanos, representa o Trópico de Câncer. O círculo dourado de menor diâmetro, que contém a Terra, representa o Trópico de Capricórnio. O círculo entre esses dois representa o Equador.
Durante o verão, o pequeno sol fica mais próximo do Trópico de Câncer (quando o Sol está mais alto no céu) e durante o inverno ele fica mais próximo do Trópico de Capricórnio (quando o Sol está mais baixo no céu).
E muito mais
Mais que um ponto turístico, o Orloj é um monumento à observação dos céus. É uma máquina do tempo que nos transporta para uma época em que ainda se acreditava que a Terra estava no centro do universo. E acima de tudo, é muito mais que um relógio.
Curiosidades
- O Orloj foi criado por Mikuláš de Kadaň com base nos cálculos de Jan Šindel
- A Torre do Relógio tem outras atrações, como as esculturas que se movem (dentre elas os doze apóstolos) a cada vez que o relógio completa uma hora e um calendário que indica o dia atual
- O Orloj não é o único relógio astronômico, mas é o mais antigo em funcionamento
- A torre onde está instalado o relógio tem 69,5 metros de altura
- O ponto vernal não é mais observado na constelação de Áries, mas sim na constelação de Peixes, devido a um fenômeno chamado precessão dos equinócios
- No final da Segunda Guerra Mundial, os nazistas danificaram o Orloj, mas ele foi reparado e voltou a funcionar alguns anos depois
E você, já tinha ouvido falar do Orloj? Se já foi a Praga, conseguiu desvendá-lo? Deixe o seu comentário!
Referências:
Imagem 1: Wikipedia Imagem 2: Adaptada de Wikipedia
PRAŽSKÝ ORLOJ — The astronomical dial PRAŽSKÝ ORLOJ — Simulator of the astronomical dial of the clock Prague — five kinds of time on one clock Prague City Tourism — Astronomical Clock — How to Read Time Orloj Computer Animation — Prague a la Carte (este link não está mais disponível) http://www.praguealacarte.com/orloj/orlojLoader.html
-
 @ 4735cdca:0c0ecb64
2024-09-24 13:58:45
@ 4735cdca:0c0ecb64
2024-09-24 13:58:45Teoria e hipótese são termos de conceitos bem diferentes, mas geralmente confundidos como palavras de mesmo significado.
Você já ouviu uma das seguintes frases?
“Não acredito nessa sua teoria.”
“Essa sua hipótese é falha.”
“Interessante essa sua teoria.”
Todas elas tratam hipótese e teoria como uma opinião ou ponto de vista em relação a algo.
No entanto, meras opiniões não representam a verdade para a ciência. Para encontrarmos explicações fundamentadas sobre o funcionamento da natureza, precisamos seguir uma série de etapas que constituem o chamado método científico. E são justamente os conceitos de teoria e hipótese que fazem parte desse método.
Mas antes de vermos a diferença entre teoria e hipótese, precisamos definir o que é uma lei para a ciência.
O que é uma lei?
Uma lei é a generalização de um conjunto de observações, não tendo sido encontrada nenhuma exceção a tais observações.
Considere as leis do movimento de Newton: a terceira delas, conhecida como Lei da Ação e Reação, diz que para uma força aplicada por um corpo A sobre um corpo B, é aplicada pelo corpo B sobre o corpo A uma força de mesma intensidade, mesma direção e em sentido oposto.
Isso explica o que ocorre (a interação entre corpos que aplicam forças entre si), mas não descreve como/por que acontece uma força de reação para toda força de ação.
Qual a diferença entre teoria e hipótese?
As hipóteses são conjecturas, especulações, previsões sobre determinado fenômeno da natureza e como ele se comporta. Hipóteses devem ser testadas, o que normalmente é realizado por meio de experiências.
As teorias são explicações bem fundamentadas para descrever eventos que ocorrem na natureza. Envolvem hipóteses já testadas exaustivamente, fatos e leis.
Uma teoria pode soar como uma explicação definitiva, mas pode vir a ser derrubada com o passar dos anos.
Acompanhe este exemplo.
Aristóteles (384 a.C. – 322 a.C.) defendia a teoria da geração espontânea, baseando seus estudos em ideias já aceitas como verdade por outros pensadores.
A geração espontânea, também conhecida como abiogênese (não confundir com a abiogênese que se refere às hipóteses de origem da vida na Terra), consistia em explicar o surgimento de seres vivos a partir de matéria inanimada. Seria como se larvas fossem geradas a partir da carcaça de um animal morto ou ratos surgissem de uma toalha úmida deixada com restos de alimentos em um quarto escuro.
Hoje, isso não faz sentido para nós porque sabemos que os seres surgem a partir de outros seres. No entanto, por muito tempo essa foi a teoria dominante.
Muito tempo mesmo! Vários séculos depois de Aristóteles, cientistas que desconfiavam da teoria da geração espontânea, como Louis Pasteur, formularam a hipótese de que os seres vivos se formam a partir de outros seres vivos (biogênese). Por meio de experimentos, ficou provado que os seres vivos não surgem aleatoriamente e precisam se reproduzir para dar origem a outros seres vivos.
Com os trabalhos e descobertas de diversos cientistas, a hipótese da biogênese foi elevada a teoria, pois foi demonstrada como correta e derrubou a teoria da geração espontânea.
E então, ficou clara a diferença entre teoria e hipótese? Qualquer dúvida, é só deixar o seu comentário abaixo.
Se você gostou do artigo, não se esqueça de curtir e compartilhar com os seus amigos.
Referências: Canal OUSbiology no Youtube, About.com e TopTenz.net
-
 @ bf95e1a4:ebdcc848
2024-09-24 13:40:45
@ bf95e1a4:ebdcc848
2024-09-24 13:40:45This is the full AI-generated transcript of Bitcoin Infinity Show #127 featuring George Manolov!
If you'd like to support us, check out https://bitcoininfinitystore.com/ for our books, merch, and more!
Welcoming George Manolov
Luke: George, welcome to the Bitcoin Infinity Show, thank you for joining us.
George: Thank you, Knut.
Knut: Good to have you here, George.
George: to be here, yeah.
you're here to tell us about the city that I was most surprised by ever. Like, I've never heard of the city before I went to Bulgaria, Yeah, time flies.
Knut: So Plovdiv, Bulgaria, which was amazing, this rich, Thousands of years of history plays with a lot of different eras and different styles of architecture and stuff, really enjoyed Plovdiv, and you have a football team there.
George: yeah, indeed.
George Manolov and Botev Plovdiv
George: Please give us the story about George and Plovdiv Yeah, sure.
Knut: Plovdiv.
George: Sure, sure. So, Plovdiv is, well, I would say it's the oldest living city in Europe, so continuously inhabited. Like you say, not many people know it. I guess, like, we don't have good enough marketing, but, that's probably part of my job right now, right? To spread the word about it. so it's, like the second largest city in the country.
And, yeah, it's just this, it's very, like, I love how you put it because almost nobody has really heard of Plovdiv, right? Most people, when they hear of Bulgaria, they've probably heard of Sofia but Sofia is, okay, but Plovdiv is kind of the chill place, Plovdiv is the place that is actually worth visiting, the place where, people just enjoy going there.
I was born there, right? and, grew up there till 18 or so, then, Studied, lived in Sofia most of the time. And, last year, in kind of summer, I was already kind of way deeper into Bitcoin. I decided I'm going to go full time into Bitcoin, just commit all my time in Bitcoin at the time, educating, publishing books in Bulgarian about Bitcoin, creating my own educational platform.
And then I got, reached out and connected really to the owner of the football club in the city, which is also the oldest football club in the country, Botev Plovdiv, who was, well, he got introduced into Bitcoin himself and he realized it's going to be a very big, project. You know, going to play a central role in where the world is going.
Knut: What is this the owner of the club?
George: That's right. The owner of the club. was like, Hey, I think we can do something unique with Bitcoin because, you know, the club is really a company, right? It's a business on the one hand, but it's a special type of business, it's not where just you produce a certain product or service.
It's really a living organism where people are involved into it, for very emotional reasons. people feel like it's their own and it's not like a small group of people. It's a very large group of people. In our case, we have tens of thousands, arguably more than a hundred, 200, 000 people who care, who watch, who follow the club.
And so on the one hand, like there's many different ways in which we can look into this, but on the one hand. It's for me, what really inspired me and what got me like, Oh my God, like, is this really happening is that we can bring the conversation about Bitcoin from a completely different angle into society to a group of people who for the most part would never really They would like this, they would never listen to podcasts like this, they would never get to any of the kind of places and things we listen to, watch, consume, right?
and people go, You know, people go kind of for bread and circus, right,
Knut: yeah, yeah.
George: for the games. That's what really football is, right? It's fun and it's emotion, it's enjoyment, but then we push them censorship resistance and hard money, right?
And we don't really push it, you know, that's the thing, right? Because are like consistently, progressively, gradually over time, introducing it and finding the best way and the most appropriate way to, yeah, plant that seed. To the minds of the people, into the views of the people and so on and so forth.
so it's really like, you know, what we're trying to build is, we feel we're in a very privileged position, right? because we've been, the first really professional sports club globally, I would say, to have, uh, crypto Bitcoin, you know, people, departments, who is actually full time employed to, you know, think of a way to grow the business, to think of a way to integrate Bitcoin natively, within the various aspects of, of, of the organization, which obviously initially includes like accepting payments and so on and so forth.
But, um, but there's so much more you can do exactly with this type of, Like organization, again, like not, not, not just a business in a traditional sense.
Knut: Yeah. And, uh, won the league, right? Is that, is that right?
George: Yeah, man, like it's, uh, yeah, so we, um, when I started last year, things were super bad. Like exactly one year ago, I was there for the, for one of the first games. It was horrible. Like, I was like, okay, this is a great idea, but if the team is doing so bad and if, uh, if they keep losing and if the fans keep getting, you know, being unhappy, Um, it's not gonna go anywhere, but still, I gave it a, I gave it a go, right, because I was like, okay, I just hope that the sports side guys are going to do their, their part, and I have my opportunity here, um, to, to just like push, to educate, to, To do what, what, what life is giving me an opportunity to do.
And, uh, very fortunately, as we started working, the team started performing better and better and better. We got a completely new coach. We got a new sports director. We, we had a lot of key staff changes across the organization, which, Um, relatively quickly started showing results. So, uh, yeah, like, 10 months later in May, we won the Bulgarian Cup.
Luke: Is that the cup or the league? Like, uh,
George: it's the cup, it's the cup. So, so, I was saying, like, we started very bad in the league. And so, we were doing better and better, but still, like, we finished 9th in the league out of 16 clubs at the end of the day. But which was still okay, because, like, when I joined, like, we were, like,
Luke: Worried about relegation or something like that?
George: there. I mean,
Knut: We're complete, uh, like I've tried to take an interest to football, but like, uh, my ADD just, the brain just wanders away after five minutes and I can't concentrate anymore. So I don't
Luke: a basketball fan.
Knut: Am I now?
Football for Noobs
Knut: Uh, so, uh, what's the difference between the cup and the league? Let's begin there. That's, that's how much of a football noob I
George: So, so pretty much in every country is the same, right? You have a league or a championship where you have, in our case, 16 teams, and every team plays twice against every other team. So home game, away game, and then, you know, you either win three points when you win, or you lose, or you draw, and you, you, you win one point.
And then, so after you play, after you play, in our case, this, what is it, games? You know,
Luke: 30.
George: yeah, about 30. Yeah, right. You're better than Matt, it's obvious. So, um, so once you play these 30 games, um, you, um, yeah, like the team with the most points wins, right? Whereas, uh, the cup is direct elimination
Knut: So quarterfinals, semifinals, all that.
George: exactly. So it's the easier way. So this was the way for us to due to the bad start of the season. This was the way for us to, to achieve something in this season and to achieve something important because what the Cubs gives us as an opportunity and gave us was to play in the European Leagues.
So UEFA Leagues. And we just did that. We played six games. Uh, for the Europe, uh, Europe League and the Europe Conference League.
Knut: Okay. But to, to be in the champions league, that's a totally, you have to, yeah, yeah. You have to win the league and you have to win all sorts of stuff. Like how does that work?
George: yeah. You have to win the league. And then in our case, so in every country it's different, but in our case, we have to win, like we go to qualifications for the Champions League. So it's like, I mean, three to four games. And if we win that, we go to the Champions League.
Knut: Alright,
George: That's the current state of affairs, although that can change over the years.
Knut: alright, uh, it all makes sense to me now, that's a lie, but anyway.
Luke: No, uh, I'll definitely, we'll acknowledge here that I'm more of the, the sports fan, uh, generally here, and I, I follow football, I like, uh, I like European, uh, football, uh, well, and obviously I'm using the correct, uh, term despite my, um, my pseudo American accent, uh. Yeah, anyway, um, uh, no, it's fantastic to see, and I mean, yeah, for the non sports fans, uh, listening to this, I get that
Knut: Well, I am a sports fan, it's just that Starcraft 2 is my sport, and yeah, yeah,
Luke: yeah,
George: eSports.
Knut: yeah, yeah, so I watch, watch Starcraft 2 games. That's what I do for procrastination sometimes.
Luke: valid sports, I'm not going to compare it to other things that aren't
Knut: breakdancing? Is that a valid sport?
Luke: Breakdancing is, um, hmm, interesting. I think anything with points, that judges give points, is kind of not a sport, it's an activity.
Knut: yeah.
Luke: but, yeah, anyway,
Knut: thing to do.
Luke: is a thing to do, yes, definitely, but back to, back to, um, um, Botev Plod, is it Botev, Botev, what's, what's, Botev, Botev Plod, yeah, so, so, um, yeah, yeah, like, the, the, the achievement, winning, winning the cup, I mean, the, The cups are sort of more difficult.
They're both difficult in their own way, right? Like, the cup, you lose one game, you're out, basically, right? But, I mean, the league is like this endurance, achievement, right? You have to perform well over the course of the whole season. But the cheat code, so to say, and I probably subconsciously used the other football team's terminology, who's in the space, Real Bedford, um,
Botev Plovdiv's Bitcoin Strategy
Luke: The, the idea right, if, if I'm getting it, is that you guys would, would keep the Bitcoin in the, in the, the treasury, the, the company, and then over the course of time it's just gonna do the number go up thing and, and the, the club will have more resources.
Right. Is that, is that the idea you're thinking with the, the bitcoin strategy?
George: There's actually many, many things to it. And this is kind of the most, let's say, vanilla type of approach. Yeah, like just buy Bitcoin and hold it on the balance sheet, which is, which is great. But there's actually so many other things you can do. And that's where, because if you just do that, frankly, like, I mean, you don't need me involved, right, much.
I mean, just call Coinbase, whatever, wire the money, crack in and, buy. but with us it's like, really, uh, we see a huge opportunity to, first of all, align our brand with the Bitcoin brand, which is a royalty free, uh, The biggest brand in finance, for sure. One, uh, like it's going to be the biggest brand in the world for sure at some point.
Right. So that's, that's one play. And to do this, it's not enough for you to just buy Bitcoin and hold it on a balance sheet. It's what you need to do is proof of work, right? You need to do things that nobody has ever done. You need to really kind of be creative. Uh, and, and, um, to push the boundaries of what anyone has ever done before, right?
So, so that is, uh, that is my kind of job and it's a lot of, um, a lot of just like, let's, let's think of what, what new things we can do with Bitcoin and sports and football that nobody has ever done. Just because others are focused on the short term things, they're focused on, hitting those, those quick wins, those quick goals, which is why, for example, like a lot of the sports and, and that have, you know, interact, they haven't really interacted outside of Bedford with Bitcoin, right?
It's mostly been crypto because it's just, okay, let's make some quick money. Um,
Luke: usually, it's usually just sponsorships, right?
Knut: yeah,
George: yes. Um, and for us, because on the one hand, like, we're not like Manchester United, right? We're not Chelsea. So we don't have that much to monetize immediately. Like we're a large club, but.
Luke: You're a large club in a local league, which is, which is different from the, it's not one of the leagues that is internationally positioned like that. But, but, I mean, the, the difference between you guys and Bedford that I, that I think is, is really interesting. Like, McCormack, what he, Peter McCormack, what he's doing, I mean, he's, he's taking a club from the bottom and aiming for the top.
But who knows how long that's going to take him to get there, right? But you guys are already in the top of your league, right? Like, in the top league.
George: right, yeah, and also there's, there's different in this, we're in the top of our league. My goal, personally, is to go to Champions League, but this is very hard, right? Because, like, okay, when you start from Peter's ground, like, it's easy, okay, every year you level up, you level up, or, I mean, I'm not gonna say it's easy, but it's easier than, uh, than once you're, you know, at our level.
For us, it's important to play currently every year in European leagues like we've done so far and to every year consistently, like, increase the level of the sports, level of the business department bit by bit, and, but like breaking that point where we, you know, win the league, Where we win several more games and enter the Champions League, that, that's really hard.
I mean, because you're already at that stage where everybody, like, so many teams are so strong, right? So it's um, it takes just a lot of ingredients for you to, to, to hit, uh, in order to win. But we're gonna get there.
Knut: and does the club self custody it's bitcoin? And if so, is it a something out of 11 multisig, that sounds like a football thing?
George: Why so? Ah, yeah, an 11? Nah, nah, fuck that. I mean Nah, even, even 7 Motosick is a, is a killer, but no. Um, yeah, I can't really speak too much about this at this point. Yeah. Um, but, um, but yeah, I mean, we do, of course we do self custody. So that's, that's the approach that we've chosen with kind of a lot of, um, we've chosen to go really pure, pure Bitcoin in terms of the strategy.
And that's how we set ourselves apart. That's how we believe we win the long game because for instance, like we Bitcoin with BTC pay server. Which in my mind they don't even have competition. It's the only like, real, solid, autonomous, sovereign way to accept payments. And it's also the way which makes sense for like, Frankly, any standard business, because like, man, we're selling scarves, we're selling, um, membership boat cards, we're selling jerseys, we're selling basic merch, and if we are to sell it with basically any other service out there, outside of BTC Pay Server, we have to basically, uh, indirectly do KYC, right?
Like, we have to go through KYC, we have to go through KYB, which is ridiculous, um, in my mind. And so, um, so that's why we're exceptionally thankful to B2C Pay Server guys, uh, for what they've built. Uh, it's been like an absolute pleasure to, um, to use their product, to use their service. Uh, we have, you know, outside of B2C Pay, we, uh, we are the first, uh, sports club on Nostr.
Where, uh, we have, uh, actively been posting, exploring, you know, meeting people here. Kind of thinking of what we could do from our angle again, like first, first time on Nostr.
Aqua WAllet
George: Um, we have partnered with, uh, Aqua, JAN3's Aqua wallet, which has a, a Botive skin mode now. So if you go to settings, you can turn Botive mode and then it turns into the colors of the club and, you know, have the picture of the stadium there.
Um,
Luke: I'm using Aqua right now because, uh, uh, usually I like to use Aqua as like a sort of a middle wallet, uh, uh, because it's still slightly slower than other lightning wallets because they, they, the, everything actually lives on, on liquid and then they, they, uh, go out via bolts. Uh, so it's slightly slower than a faster, um, like, like than other, um, more direct lightning wallets.
And so usually when I come to a conference, I'm going to load up a, like a temporary. I don't know, Blink or something like that, but I forgot to do that, so I'm just using my Aqua wallet, and you know what, it's been great here, it's been working, uh, so yeah, we're big fans of Aqua wallet and what
Knut: Yeah, and a BTC pay server. I mean, uh, we can echo everything you said that we, BitcoinInfinity. com, like, and the store here We just fired up. Everything is powered by a BTC pay server, and we just love it. Yes.
Luke: So what was your question about, uh, Aqua?
George: If yours is on BOTEV mode.
Luke: Uh, I don't think I've gone into the settings and changed it to Vaudev mode, I'll have to do that, maybe we'll take
George: It's dark mode,
but cooler.
Luke: Doc dark mode, but cooler. Okay. Okay. Actually that's a, that's a, that's a good point. That's a good point. Yeah. We'll take a, we'll take a picture after, uh, after the episode and we'll de proof, bot, uh, bot e mode, and, uh, uh, post that on Nostr.
How does that sound?
George: Let's go.
Knut: Yeah. Nostr. Um, is there a connection there between both a plot and Nostr while you're doing Nostr stuff as well?
History and Freedom
George: Yeah. Well, look, um, a lot of these things is like, so What Botev Plovdiv stands for, um, very importantly, so the club was named after Hristo Botev, who's, uh, like, one of the most Bulgarians, if the most famous Bulgarian revolutionaries, like, historical figure, uh, he was a poet, he was a revolutionary, he fought for Bulgaria's freedom back in the day,
Luke: Which, which day, which, what day did you
George: uh, 110, uh, what is it, like, 50 years ago or so?
Yeah.
Knut: Mm-Hmm?
Luke: Okay. So, so
Knut: before the Commes.
Luke: ottoman, uh,
George: Yeah, yeah, yeah. He, he, he, he fought for the, for the liberation of Bulgaria from, from the Ottoman Empire. And a lot of what he stands for is this fight for freedom, his fight for liberty. Um, and this, this lives until this very day into the identity of the club and to what we stand for into the songs, into the, into the music.
Um, you know, um, the kind of like what, what our fans also resonate with, um, and, and what they sing like in many, in many ways. Right. So, um, Freedom of speech, freedom of, uh, of like freedom in general is, is a value that is deeply ingrained into kind of like what the club stands for. Um, and, uh, you know, that's why I'm into Bitcoin.
That's why I believe. And that's, that's why I saw this even bigger opportunity. Oh my God, like, how is this happening? There's so many, sometimes, you know, some like weird things happen in life and you have no explanation why and how all these things align. But, but for me, it's like this club was made really to.
to be aligned with BOTEF and to be, uh, to, to, to be aligned with Bitcoin and with Nostr. If I look at all the other clubs in Bulgaria, right, like just in Bulgaria, none of the others, like, there's no this contextual historical background that you can make these connections. But with us, we have it, and what a chance that, like, we have this owner, and he got, like, introduced to it, and then we got connected.
Like, how the hell does this happen, man? I don't know,
Luke: We like to say this, the surreal doesn't end, you know, and like, uh, my, my whole story, I've been talking about this, uh, at the, the conference here is like two years ago was the first time I ever met Bitcoiners here in Baltic Honeybadger. We, we met for the, for the first time, uh, all three of us, uh, met for the first time two years ago, I've been in Baltic Honeybadger and it's like, things, things happen so fast.
Uh, I've, I've, uh, I've thought it was been awesome just following, uh, what you've been doing with the, the club and the story. So great to, Great to get to talk about it, but, uh,
Bitcoin in Football
George: Yeah. No, for, for me, like really the, the most exciting part is really even coming forward. So, uh, because, so now it's been, so we, a long, we announced, uh, publicly that we're doing this, uh, 31st October last year. So the anniversary of the, of the, uh, Bitcoin White paper, um, we've built a lot right. And very, very importantly, I'm super proud, like, I don't know if you saw this, but like a month ago, we played on European League, the UEFA League with Bitcoin straight on our jerseys, which was like, like, when I saw this, I'm like, dude, it's crazy that this is happening.
But, but the best is really yet to come, like, like we like to say. Um, so I, I think we, we're, we have, um, we have still so much more to do. So for me, the next big part, which I'm super excited about literally in the coming month as, uh, as I go back. So is to finally get some of our. Players or at least one or two to get to do something publicly about this, because at the end of the day, that's why for me, the more I do, the more I, uh, play in this arena, I realized this is really a Trojan horse for us to bring Bitcoin into the conversation, into the minds, like I said, of people who otherwise wouldn't and, and our players, you know, especially a few of them, they're really influencers, right?
Um, a lot of people follow them. A lot of people respect them. And, um, and if they do, uh, you know, something meaningful, something cool, something impactful, this is going to have a huge impact onto our forwards. This could very well have impact onto, um, other sportsmen, other football people, other football clubs, right?
Uh, so that's why I'm doing it, right? Really?
Luke: No, this is fantastic, and actually this was exactly where I was hoping to go next, so thank you for queuing that up. But, no, no, the game theory of all this, right? Like, one club getting, Positioning as the, as the Bitcoin club in a league, uh, really means that eventually all the other clubs are going to need to adopt Bitcoin.
If they're going to be able to compete, because if play playing out the game theory, number go up, whatever it is, Bitcoin strategy plays out, you guys are going to be the most financially capable club. Financially sustainable in not very long, you know, assuming everything plays out the way we're thinking it will, right?
So, so other, other clubs then would become incentivized to also adopt Bitcoin. So what, what do you, what do you think about that? Like you, do you, do you see that, uh, happening as well?
George: Yeah, I'm not really sure if it would happen to me. That fast, to be fair. Like, I think it's inevitable, right, obviously, but I think it, yeah, like, I think this definitely takes at least three, four years, maybe more. Um,
Luke: That's, that's still pretty fast.
George: yeah, I guess. I mean, I mean, like, okay, let me define it better. It takes three, four years.
So, for other clubs within our league to start doing something like this, uh, maybe it takes less time for other clubs to realize it, but I think for them to do it, it also depends on our actions, right? So because like, we don't have like a treasury of microstrategy or something, so it's not, and we're not doing like a
Luke: you don't?
George: monthly like leverage on top of leverage on top of another leverage, you know, uh, we're not in, in Michael's privileged position. but we can do other cool things, right? Uh, one of the, um, so this is not yet live and this is not yet happening, but one of the, like two, two projects, let's say, I'm gonna briefly, like, tease here that, that I'm working on that I hope to have very large impact is first, uh, building this, uh, simple tool Uh, called like a Bitcoin, uh, football salary calculator that, uh, it's like really a DCA tool, but like looking back and like tailoring it to our niche where I want to, for us to visually and emotionally Show, um, to players, but also to fans of ours, like what Bitcoin could have done for their remuneration, if you look one year back in time, two years back in time, three years back in time, four years back in time, and for them to really realize, Oh my God, this is a no brainer.
Right? I want to make this mess. And this is hard, right? Um, because like, there's so many tools and like, but I want to be, because the audience is very wide, very different types of audience. I want to make this so that you can consume it in like two, three, four minutes. And you're like, okay, I need to learn more about this.
This actually is interesting. There's like, that's so much dense and emotional and compact information that you're like, Whoa. Why am I not doing this? How did I miss this?
Knut: What, what, what was the name of that website? I, I don't know if it's still up, but bitcoin or shit.com or something like that. So, so it lists if you bought this item when it came out, an iPhone five or whatever, uh, and if you had bought b bitcoin instead.com, I think that that's the, that's the name. So if you bought, uh, if you bought Bitcoin instead, it shows you how much, how much more money you'd have now and how many iPhones you
George: Yeah. Yeah. And of course there's many of these tools, obviously like we've all see them and we all like like them and retweet them and repost them. And it's all great. But I think, at least I hope that we can do something impactful with this. If we really tailor it, compact it to a specific type of niche audience with a specific message designed for them.
And because this audience is also like. A type of audience who can also like, um, you know, bring it to other bubbles that we ourselves are not part of, right? So that's, for example, one like, uh, one like project I'm very, very excited about and I hope we can, um, yeah, we'll bring forward relatively soon.
There's a few moving elements, but definitely in the coming month or two, uh, at most. And then, uh, and then, you know, speaking of the other clubs, what, what I want us to do is what we're working is next year, we're targeting to do, I hope we could do the world's first, uh, Bitcoin, uh, Cup tournament. Uh, for youth players, 70 year old boys who are, you know, right there before they sign their first professional contract, start earning money, for them, first of all, like, it's a Bitcoin football cup, like, it's the first time this, this could potentially ever happen And then it's, it's a football first tournament, right?
This is the, we want to make it like top quality, like really the highest quality when it comes to sports, but then you have Bitcoin involved all over the place, right? In terms of brand, in terms of rewards, in terms of, um, in terms of like plays, um, like, like games and, and interactions, activations, uh, throughout, before, throughout, and after the, And after the event, and for this, I'm targeting to get really like, like big clubs.
I mean, because it's academies, right? I mean, I cannot get the Manchester United first team, just maybe we could get the Manchester United 17 year old team or, you know, another big club. We get some of these, and then like we get their brands, we get them on the focus of Bitcoin. And we drive the conversation faster, you know, not three, four years from now, but Less
Knut: what about, um, like right now there's you and there's, um, you guys and there's a real bed for it, right? Those are the two I know of in Europe. Are you aware of any other clubs that are doing a Bitcoin strategy? I mean, is this virus spreading? Like, have you heard anything like,
George: Um, Oh, there's, uh, there's the Austrian Admira Vakir who have done some integration. So it's a second tier, uh, second league, uh, second league, uh, club that have, uh, that have, uh, you know, they've also had Bitcoin on the, their second team jersey. And, um, and they, they also accept Bitcoin payments, uh, here and there, but you know, the thing is, there's some other clubs, um, there's a Miami, um, not Miami, um, a Hawaiian club that, that is doing, uh, that is doing like their Bitcoin gig,
Knut: yeah, there are other, other sports, right, other sports team and sports teams in other sports that are doing it. But, but for football specifically,
George: which ones?
Knut: Uh, I'm so bad with sports, but wasn't there like a hockey team or a basketball team or
Luke: I'm not aware of any others, actually. Yeah, like, uh, there's been some attempts at
Knut: it's
Luke: an orange colored team or something like
Knut: more the individual athletes,
Luke: Yeah, yeah, there have been individual
Knut: for instance, a
Luke: have been individual
Knut: player, and there was some American football player.
George: There's been individual athletes, a lot of them. There's been, I was asking if you know, but there's been a baseball club in Australia, the Port Heat. Uh, who did kind of a Bitcoin strategy. Uh, but very unfortunately that didn't work out. They kind of started this at the peak of the last bull cycle. And, um, and as I understand, uh, there wasn't like a strong alignment between the owners and the management in terms of like understanding that this is a long game.
So that's why this kind of flopped. Um, but yeah, like I, I think the reason why it's not happening in more, unfortunately, and, and, and I see this even, even within our club, uh, you know, but, but definitely no other clubs because Fiat has permitted sports as well. Right. So all the sports club, uh, clubs or the vast majority in football, for sure.
They're like, you know, on the hamster wheel themselves.
Knut: They're indebted,
George: They're indebted.
Knut: to an extreme level,
George: yeah, like, like fighting for every dollar for every income. So it's, it's hard for you to like, Oh yeah, we're going to have this long term Bitcoin strategy that's going to take like two, three, four, five years to play out.
And we can benefit a lot from it. It's very, very hard in, you know, unfortunately for a large organizations, sports club in particular to To have this realization, to map this out, to get others on board. That's why it's not so popular and uh, and that's why I'm grateful and keep pushing that we have this chance.
Luke: I mean, you make a great point here about essentially the, it's the organizational alignment, right? Like the, the, these are companies, sports clubs are companies. They just have this large, the business is involved around getting fans to come in and consume this sort of marketing. Product, essentially. So it's, it's a certain kind of company that's run a certain way, but just like any other company, you need, you need alignment from the management.
So it's, it's fantastic that, uh, Boteb Plovdiv has, has the, uh, alignment and is, is putting their, their trust in you to, to move this thing forward. And I mean, from the, from the perspective of this thing, Playing out, right? The, the best part that, uh, I think one of the best parts that you, you mentioned again was the, the influencers.
Like you get, you get some players, there's, there's so many angles to, to reach people through this. I think it's, I think it's fantastic. The, uh, orange pilling a player and then they move to another club, but they, they, maybe they don't get to get paid in Bitcoin, but maybe they still put, put their money in, in Bitcoin.
Maybe they even ask their club to, to, uh, pay them in Bitcoin, something like that. And then the, the Questions start getting, uh, asked and all this.
5 Year Goals
Luke: So what, what is the, the goal in, in five years, for example, where, where do you see the club in the five year mark?
George: Oh man. Yeah, in five years, I think we definitely have to be in Champions League. Like in my mind, you know, like people around me like, oh, you're too ambitious. I'm like, man, yeah, like in five years, we definitely have to be in Champions League. Uh, that's, that's my personal goal. On our internal Slack, I have the Champions League icon there.
That's why I'm there, right? Um, so, uh, it's a lot of hard work. Like, it's really a lot of hard work. And it's also not completely dependent on me and my work, to be fair. Like, because, at all. I mean, really, like, uh, I mean, at the end of the day, the most important part is the sports department, right? Uh, in the club.
Um, so that has to continue going well. But, but I think We're going in a good direction there too, because we have the, they're the long term view as well, right. We have our academy internally, which is, yeah, it's one of the best academies. It's the best really academy in terms of infrastructure in the country.
That's why we're also can't afford to think of this Bitcoin Cup tournament, because we have the infrastructure, we have like a super cool stadium, that's crazy. If we can, if we can do a final for, for such a tournament there. Um, so, so we have all the things in place in terms of In terms of assets, I would say, uh, it's just a lot of moving parts.
a lot of work, consistency, and a bit of luck. Always it comes, you know, when, when it comes to, when it comes to football and sports, but, but five years from now, I want us to be in the champions league. I want us to be the absolute, you know, international professional level, uh, Bitcoin level, Bitcoin sports club.
and, uh, and I want for this tournament that I start to be like a, like, like to have the fourth edition by then. Uh, and, and I want to have clubs, but five years is a lot of time, you know, as you say, like, I also want to have other clubs following us by then. I think that's absolutely, absolutely is going to be doable.
Knut: What, what are the, what are the tax laws around Bitcoin in Bulgaria? Like what, are there any issues there? Or like what, is it easy enough,
George: It's kind of okay. Uh, it's kind of okay. So if you just buy Bitcoin and hold it, like you don't, uh, you don't, uh, incur taxes, uh, until you sell it, if you accept Bitcoin for payments, um, and if you don't sell it, you can just, uh, keep it as inventory on your balance sheet. So again, no,
Knut: but there's a capital gains tax or something if you sell it. Yeah, yeah, yeah. Alright.
George: 10%. So it's, it's, uh,
Knut: Pretty good.
George: Yeah, I mean, it's not like El Salvador. Okay. Uh, but, but it's, uh, it's, it's way better than many other places. Um, and, uh, yeah, so we've been looking, looking actually, so I was in El Salvador a couple of months ago, because we've been looking very much to do stuff there.
And we've been, uh, yeah. Um, because we've been, we've been thinking of what to do more with Bitcoin, right? So that's why I said, like, it's not just about buying and accepting Bitcoin. It's about corporate strategies, about branding strategies, about how to make money. Um, it's about education strategies. It's, there's so much around it.
So in terms of corporate strategy, I was, uh, we're very attracted by El Salvador, um, and their, uh, capital markets regulation, because they're basically striving to build capital markets on top of Bitcoin. Bitcoin is legal tender there. They have all kinds of, tax incentives for companies to issue debt or to sell equity.
on their capital, on their, um, well, let's say nascent upcoming capital markets, because it's not like it's, you know, hustling and bustling yet. Um, but, but they're, they've put a lot of the rails, uh, um, or they're building a lot of the rails to, um, to really enable the, the, the creation of Bitcoin based capital markets.
So, um, we've had great talks there. We have meetings with, uh, um, we have. Yeah, with the Bitcoin office, right? Um, so, ideally, like, we're striving to build some connection there and to do something, interesting and world first again from a corporate perspective. It's just that, as many things, it's a little harder than you would expect it to be, or it takes a little more time than, Then you would hope to do it.
But my idea or long term vision, frankly, like what we want to do with Bitcoin, uh, and with the club is to enable our current fans and global fans to become co owners of the club. And that's why, you know, I have big hopes for, uh, for us being able to do this out of El Salvador and through El Salvador, because this would, like from a tax perspective, from a branding perspective, from legal security perspective would be, would be ideal.
It's just that, again, um, my enthusiasm is a little over, uh, ahead of kind of like how, uh, how, how advanced and set up everything there is, but, uh, but we're, we're very actively talking to them. We're working with many parties there, so. Just maybe we can have big news there too.
International and Local Effects
Luke: Well, no, and, and you actually said something great about global fans. I think this is a, a fantastic thing, right? A a again, Bedford is, is similar. They've, they've got, they've got fans all over the world and, and I think for you guys it's like who is going to tune into the Bulgarian football league outside of Bulgaria before, well, not too many people, but now a bunch of Bitcoiners.
If they're into, if they're into football or, or not even, because this is the funny thing. There were, there were a lot of people posting about that. They, they've got, they, they don't usually follow, follow sports at all, but, but they'll follow the Bitcoin team. So the, the funny thing is, I think, I think the first, the first club to adopt Bitcoin in every league is going to get all of these global fans.
And maybe the, maybe the, the second one, the third one, maybe can get some kind of other support, but it's really the first one in every
George: really.
Luke: That, that
George: Not
Luke: That's that. I, I completely agree with you there. It's the, it's the first one
Knut: first mover advantage.
Luke: mover advantage. It's gonna get, it is gonna get all of the, all of the Bitcoiners are gonna now be, be supporting and, uh, uh, yeah.
I mean, have, have you seen, uh, some, some uptick in, uh, kind of international
George: yeah, yeah. So, international but also local. Like, local is very important. Like, we have, like, so many people in the country who's like, just what you say, like, I didn't care about sports or football, like, forever, or at all, ever, but now I follow, now I buy merch, now I come, you know, every now and then they come to games, so
Luke: Well, because there's the bread and circuses thing that you said, it gets tossed around in the Bitcoin world and also some other places on kind of the Twitter sphere and whatever, it's like it's a distraction, that sports is sort of a distraction from clown world basically and it's a way of people to sort of Uh, forget about what's going on around them, but I think that's also missing the, the positives, which it, it's a, it's a community builder, it brings people together, there's a, there's a sense of, of pride in, in something local succeeding, everyone, everyone's happy, there's, there's real economic, uh, effects usually when a, when a local sports team wins, and so, so from, from my perspective, I, I, I think, I think sport is a good thing, and it's, and it's, it's something that, that people can rally around, and so,
George: an amazing thing.
Luke: Yeah.
And, and so what, what are, what are you looking at locally? Like what, what do you hope to have the effect, uh, uh, locally in, in piv?
George: Yeah. Um, yeah, no, look, uh, for me, sports, like, for us, the, the, the, the, about Plovdiv, for me, that's what I realized, like, we're kind of very much into Bitcoin and stuff, obviously, that's our interest, but I think when we go on a Bitcoin standard, Right. And, uh, in general, people start feeling wealthier, opposed to, like, being in the grind.
You're just going to have more time for fun stuff, right? Like playing football, I mean, or volleyball, or whatever your sport is, or, like, going and cheering your team, and, uh, and being part of such a community. And I think that's really what, you know, even Nostr is about. Like it's, Being part of these communities, because that's fun, and like, we as humans, at the end of the day, we are living to be part of communities, right?
And you find your community, you're an active part of it, you contribute to it, you evolve it, right? You build it in one way or another. And unfortunately, you know, today in the fiat world, this is just like A stress valve in many ways, or like you say, like Brothers and Sisters, whatever. Um, but, uh, but I think it can be so much more, right?
It is, but it can be so much more for a larger amount of people and so on and so forth. uh, but yeah, well, back in Plovdiv, man, like, I have big hopes. I really have big, big ambitions there. I want to get Bitcoin into the wallets of, uh, of like tens of thousands of people. I want people to wake up. I want people to see.
Luke: big is piv? How many
George: It's like three, four hundred thousand people. So it's a lot. Uh, our stadium is, uh, 21, 000 seats stadium. I'm kidding. I'm kidding. It's, it's 19. I wish it was 21.
Luke: Yeah. You'll have to add 2000 more
George: Maybe, yeah, we'll, we'll think of some additional construction.
Luke: the, make the infinity stand when
George: Right. Right. But, uh, but yeah, like the setting was super cool. Like, it's really cool.
Like when it's feel like, man, the atmosphere is amazing. Um, and so it's, and it's really this community that you can feel that people are involved. So it's, it's like consistency and it's social engineering in one way or another, right?
Knut: one of our favorite words,
George: but in a positive way.
Knut: in a positive way, okay.
George: So it's social engineering for us to ingrain Bitcoin and make it part of kind of what people see, do, have, own, interact with, right?
So, uh, I think exactly because of this community element, exactly because, Because, you know, football is a football club and there's this unique living organism we can, we can create this and, you know, it's fascinating. I'm so much into this and there's other people who are so much into this. Oh my god, like, we can make such a big difference.
And, and like in the country. You know, on a political and economic level, they don't get it. Like, they don't see it. They just are in their, you know, like, oh, are we going to accept the euro? Oh, what's happening with the war? I'm like, who cares? Let's build.
Bulgarian Currency Situation
Knut: Yeah, Bulgaria has its own shitcoin, I almost forgot about that, but uh, what's it called again?
George: Kinda. Um, but not quite, to be fair. It's, it's a good coin, uh, not for investing, but, but for medium of exchange is actually decent. Uh, Lev, Lev
Knut: Lev, yeah, yeah, yeah. Yeah,
George: and I recently got educated about this. So, uh, the lev is pegged to the euro. So, um, uh, so, so that, that is super cool for, for us, for me as a consumer, for businesses, because like the fixed rate.
So for trade is, um, It's, it's good, right? As the world would be in the future. You have one currency, Bitcoin, you don't have the currency exchange risk, right? We don't have it only with the European Union. And the good part with this, so, we got, we got hyperinflation back in 1997. Was really bad. People lost almost everything, everything, in many cases.
Um, and then we got this so called currency board introduced and the currency board is like we have the left, but the left has to be backed up by other currencies. So it's like a stable coin, kind of like how Tether is backed by, by dollars. You know, the levy is backed by euro and like a basket of, I think they have some other currencies and assets, which is cool because the local politicians, they cannot print, they cannot, you know, so, so it's been, it's been, I think, way better than Hungary, Sweden, uh, Finland, you have your, oh
but Sweden I've heard it's kind of bad,
Knut: It's kinda bad, Norway too, like, both Swedish and Norwegian crown, and the crown in Czechia, like the Czech Republic, it's also
George: Yeah.
Knut: I mean, they're all going to shit the smaller
George: So, so for us, it's like, I would say we're better than, than the Corona, the, and, and all these like local currencies, because we kind of just are there to the, peg to the Euro. The local politicians don't have the opportunity to print. So it's, it's a very good position for us to be.
Luke: You, you get the, the negatives of the, the euro. But, but still, I mean, I mean the, the realistically, the dollar at the Euro and maybe the, the Chinese currency are the only, are the only ones that are in the, sort of within our own, within our own lifetimes are, are going to be not as terribly bad against Bitcoin.
But all the other ones are just, are. All the other ones are
Knut: Yeah, I think it's just a matter of time before both, uh, at least Sweden, uh, switches to Euro standard. If not switching to Bitcoin standard happens first, but well, we'll see, we'll see what happens.
George: man. I'm very bearish about the Euro.
Knut: yeah, yeah, it's like,
Luke: It'll be the second last to fall or third last but but yeah it's it's it's it's not going to be the the last and so it's yeah.
Knut: So that is what it is. I mean, speaking of Bulgaria and currencies and stuff,
Bitcoin Adoption in Bulgaria
Knut: like, how is the rest of, how is Bitcoin adoption in general in Bulgaria? What's happening in other places? Like, Plamen opened a bar, I saw, and like, what are the connections? What's happening?
George: It's actually quite cool. I'm, I'm, I'm quite happy with, with how the ecosystem is evolving. There's, there's Plamen, um, with his whole community, like content creation, the conferences he's been doing, which has been like a very, I think he's responsible for like, I don't know, probably like, 000, maybe several 10, 000s of people who have opened their eyes and even if they're not hard bitcoiners, they now own bitcoin.
Uh, so that's huge. We have other content creators also who've had an impact. We have now once or twice per, yeah, about twice per year we have like, uh, A small, uh, merchant, uh, like, conference events, so for merchants to accept Bitcoin. we have these people who are active and who are doing things. Now, actually, yeah, there's something new that's coming up here, uh, literally in Plovdiv is we have this, um, this, uh, great dudes who have this, um, um, it's an application for, uh, ordering food, like takeaway and, uh, what is it, like,
Knut: like Glovo or
George: yeah, yeah, like Glovo, um, but, um, but, um, But it's not like this big corporate thing that, but, but still, it's a very good product and they've integrated accepting Bitcoin there for quite some time now they've made it even easier and they've introduced.
So we have like about, I think it's 15 restaurants in Sofia and like five or so in Plovdiv where through their system, you can order food. And pay with Bitcoin online, or you can also go in the restaurant and pay in Bitcoin online, and they just, um, they just won a, uh, grant from, uh, Bitcoin Beach, uh, and, uh, they're going to use the grant, uh, to, well, the attempt is really to start like a small circular economy, if you would Um, where, so if you go, uh, to one of those restaurants and pay with Bitcoin, you're going to get sats back 10%, and then, um, the restaurant is also going to get 10 percent sats back.
And if you order food, um, through their app, also the driver is going to get, uh, some sats back. And, uh, we've just been discussing, because obviously we're partnering with them, with the football club, so we'll push this out, because some of the restaurants that are there are our, I mean, basically, like, we have two restaurants locally that are partners, we got them in, right, obviously, in the deal, um, So, so that is also like, for me, it's like super cool because now for so far, the club has been pushing Bitcoin.
Now we have two of our restaurant partners who are themselves like hard Botevists, Botefans, and like they're popular. Now they're starting to accept Bitcoin in their, in their two restaurants, right? And they're going to have their campaigns. We're going to push them more. So, um, so I'm really excited about this and fingers crossed this goes well.
We have good metrics because if we have good metrics. Yeah, we'll look for ways to grow this. So there's a lot of grassroots things happening, which I love. On the top, nothing.
Knut: It's the way it's supposed to be.
George: But it's the way it is. Yeah, it's a better
Luke: Yeah it really seems like that you get one or two of these big anchors like like for example you you guys have had that had that conference last couple of years but now with both of Plavdev now Bulgaria is really got a couple of big anchors. Big relative in relative terms, uh, and all of this other stuff can, can start coming up around it.
And, uh, love, love to see it. I mean, he, I mean here, here with Rega, there's Honey Budger has been going for a really long time, and I, and I even think that they are honest about, we, we would, we just talked to, to Max, uh, about this, uh, from Defi and like yeah, there's not much other adoption in, in Lavia and this conference has been going on for a long time.
Exactly. And so it's just like, uh, it's, it's, it's great to see, uh, in, in your case, in Bulgaria's case, that there's, there's more of this, uh, picking up. So, yeah,
George: Well, I think it's really, in our case, I don't know, like it's grassroots, like I said, and I really believe grassroots and then Rio or for the vast majority, Rio adoption comes permissionless life. It comes like it's not forced. You know, there is this point where, okay, there's Plamen, like, he got the inspiration, he makes his content, he does the conferences, Like, our owner, he sees this opportunity for Bitcoin, for the club. He takes the action, right? So it's, it's not like, so it's individuals, right? Taking actions and then, as you have, you know, several of them, maybe others get inspired or get ideas going and that's how the magic happens. And, uh, yeah. Excited about it.
Wrapping Up
Luke: it's awesome, man. Great hear your story. So, was, uh, was there anything else that you wanted to discuss or bring up on this topic?
George: no, I mean, what I would say is absolutely, uh, Please, uh, you know, Knut, you've been, but please, you're absolutely welcome, Luke, join as well, like, both of you should come
Knut: Absolutely. Highly recommend it. I had a great time in Bulgaria, and it's such a fascinating country, it's such a rich history and such a beautiful place, and the food is great, and it's very affordable, it's very, yeah, very
George: like, I have people who come in Plogis specifically to, like, nomads, spend, like, a or a month. So, so please enjoy, visit the game. come spend in the restaurants where they accept Bitcoin, follow us on social media for sure, so, X and Nostr,
Luke: Yes, all the details, please.
Knut: And also like one of the eras, uh, infamous eras of Bulgaria is the commie era, right? Where you can see the impact that system had on the country and how horrid it is. Uh, so it's, it's, uh, that might not be a good pitch for, uh, but that's
Luke: Let him, let him share his social medias, Knut.
George: wait, do you have, do you have something
Knut: no, no, I think like the, The point I was getting to is, if you get to Bulgaria, don't only go to Sofia, go around the rest of the country, because it's not as raped as that town was by, as that city was by communism, all this concrete, yeah, yeah,
George: yeah, the,
Knut: you can really see the impact there. I'm not, um, yeah, this came out totally wrong, but I'm trying to, I'm trying to, To hype Bulgaria here, but also there's a historical lesson to be learned in the country, for sure,
George: sure. It's really like, there's so many different things there. So there's the communist part, there's like fucking amazing nature, there's like
Knut: is everything, yeah.
George: if you're into hiking, there's like, just like from Sofia, what I love about Sofia, like just last week, twice, end of the day, I'm like fucked up, like tired of computer.
40 minutes up and I'm up in the mountains, hiking, in like 2000 meters altitude. Uh, so, so there's all these like super cool things, but on the socials, yeah, we're on Twitter. we're on Nostr, uh, so Twitter is, um, botif underscore, uh, en, on Nostr, uh, we are just botif. Yeah, you can find us.
Luke: going say you're NPUB? No, no, no,
George: I'm still learning it, okay?
Luke: we'll post, you're still learning, we'll post all the details in the show
George: Yes. Yes. And feel free to also check out our website. We have, due to our El Salvadorian, um, kind of project, we already have a Salvadorian website, which is very easy to remember, botif. sv. So you can go there and from there you'll find all the links and information.
Luke: Absolutely fantastic.
Knut: Great! Get the inverse of Clown World. This is a shill. BitcoinInfinityStore. com And thank you very much for coming on,
George: was great having
Knut: Great to have
Luke: George, thanks so much. This has been Bitcoin Infinity Show. Thank you for
-
 @ bf95e1a4:ebdcc848
2024-09-24 13:38:58
@ bf95e1a4:ebdcc848
2024-09-24 13:38:58This is the cleaned, AI-generated transcript of Bitcoin Infinity Show #127
If you'd like to support us, check out https://bitcoininfinitystore.com/ for all our books, merch, and more!
Welcoming George Manolov
Luke: George, welcome to the Bitcoin Infinity Show, thank you for joining us.
George: Thank you, Knut.
Knut: Good to have you here, George.
George: to be here, yeah.
you're here to tell us about the city that I was most surprised by ever. Like, I've never heard of the city before I went to Bulgaria, Yeah, time flies.
Knut: So Plovdiv, Bulgaria, which was amazing, this rich, Thousands of years of history plays with a lot of different eras and different styles of architecture and stuff, really enjoyed Plovdiv, and you have a football team there.
George: yeah, indeed.
George Manolov and Botev Plovdiv
George: Please give us the story about George and Plovdiv Yeah, sure.
Knut: Plovdiv.
George: Sure, sure. So, Plovdiv is, well, I would say it's the oldest living city in Europe, so continuously inhabited. Like you say, not many people know it. I guess, like, we don't have good enough marketing, but, that's probably part of my job right now, right? To spread the word about it. so it's, like the second largest city in the country.
And, yeah, it's just this, it's very, like, I love how you put it because almost nobody has really heard of Plovdiv, right? Most people, when they hear of Bulgaria, they've probably heard of Sofia but Sofia is, okay, but Plovdiv is kind of the chill place, Plovdiv is the place that is actually worth visiting, the place where, people just enjoy going there.
I was born there, right? and, grew up there till 18 or so, then, Studied, lived in Sofia most of the time. And, last year, in kind of summer, I was already kind of way deeper into Bitcoin. I decided I'm going to go full time into Bitcoin, just commit all my time in Bitcoin at the time, educating, publishing books in Bulgarian about Bitcoin, creating my own educational platform.
And then I got, reached out and connected really to the owner of the football club in the city, which is also the oldest football club in the country, Botev Plovdiv, who was, well, he got introduced into Bitcoin himself and he realized it's going to be a very big, project. You know, going to play a central role in where the world is going.
Knut: What is this the owner of the club?
George: That's right. The owner of the club. was like, Hey, I think we can do something unique with Bitcoin because, you know, the club is really a company, right? It's a business on the one hand, but it's a special type of business, it's not where just you produce a certain product or service.
It's really a living organism where people are involved into it, for very emotional reasons. people feel like it's their own and it's not like a small group of people. It's a very large group of people. In our case, we have tens of thousands, arguably more than a hundred, 200, 000 people who care, who watch, who follow the club.
And so on the one hand, like there's many different ways in which we can look into this, but on the one hand. It's for me, what really inspired me and what got me like, Oh my God, like, is this really happening is that we can bring the conversation about Bitcoin from a completely different angle into society to a group of people who for the most part would never really They would like this, they would never listen to podcasts like this, they would never get to any of the kind of places and things we listen to, watch, consume, right?
and people go, You know, people go kind of for bread and circus, right,
Knut: yeah, yeah.
George: for the games. That's what really football is, right? It's fun and it's emotion, it's enjoyment, but then we push them censorship resistance and hard money, right?
And we don't really push it, you know, that's the thing, right? Because are like consistently, progressively, gradually over time, introducing it and finding the best way and the most appropriate way to, yeah, plant that seed. To the minds of the people, into the views of the people and so on and so forth.
so it's really like, you know, what we're trying to build is, we feel we're in a very privileged position, right? because we've been, the first really professional sports club globally, I would say, to have, uh, crypto Bitcoin, you know, people, departments, who is actually full time employed to, you know, think of a way to grow the business, to think of a way to integrate Bitcoin natively, within the various aspects of, of, of the organization, which obviously initially includes like accepting payments and so on and so forth.
But, um, but there's so much more you can do exactly with this type of, Like organization, again, like not, not, not just a business in a traditional sense.
Knut: Yeah. And, uh, won the league, right? Is that, is that right?
George: Yeah, man, like it's, uh, yeah, so we, um, when I started last year, things were super bad. Like exactly one year ago, I was there for the, for one of the first games. It was horrible. Like, I was like, okay, this is a great idea, but if the team is doing so bad and if, uh, if they keep losing and if the fans keep getting, you know, being unhappy, Um, it's not gonna go anywhere, but still, I gave it a, I gave it a go, right, because I was like, okay, I just hope that the sports side guys are going to do their, their part, and I have my opportunity here, um, to, to just like push, to educate, to, To do what, what, what life is giving me an opportunity to do.
And, uh, very fortunately, as we started working, the team started performing better and better and better. We got a completely new coach. We got a new sports director. We, we had a lot of key staff changes across the organization, which, Um, relatively quickly started showing results. So, uh, yeah, like, 10 months later in May, we won the Bulgarian Cup.
Luke: Is that the cup or the league? Like, uh,
George: it's the cup, it's the cup. So, so, I was saying, like, we started very bad in the league. And so, we were doing better and better, but still, like, we finished 9th in the league out of 16 clubs at the end of the day. But which was still okay, because, like, when I joined, like, we were, like,
Luke: Worried about relegation or something like that?
George: there. I mean,
Knut: We're complete, uh, like I've tried to take an interest to football, but like, uh, my ADD just, the brain just wanders away after five minutes and I can't concentrate anymore. So I don't
Luke: a basketball fan.
Knut: Am I now?
Football for Noobs
Knut: Uh, so, uh, what's the difference between the cup and the league? Let's begin there. That's, that's how much of a football noob I
George: So, so pretty much in every country is the same, right? You have a league or a championship where you have, in our case, 16 teams, and every team plays twice against every other team. So home game, away game, and then, you know, you either win three points when you win, or you lose, or you draw, and you, you, you win one point.
And then, so after you play, after you play, in our case, this, what is it, games? You know,
Luke: 30.
George: yeah, about 30. Yeah, right. You're better than Matt, it's obvious. So, um, so once you play these 30 games, um, you, um, yeah, like the team with the most points wins, right? Whereas, uh, the cup is direct elimination
Knut: So quarterfinals, semifinals, all that.
George: exactly. So it's the easier way. So this was the way for us to due to the bad start of the season. This was the way for us to, to achieve something in this season and to achieve something important because what the Cubs gives us as an opportunity and gave us was to play in the European Leagues.
So UEFA Leagues. And we just did that. We played six games. Uh, for the Europe, uh, Europe League and the Europe Conference League.
Knut: Okay. But to, to be in the champions league, that's a totally, you have to, yeah, yeah. You have to win the league and you have to win all sorts of stuff. Like how does that work?
George: yeah. You have to win the league. And then in our case, so in every country it's different, but in our case, we have to win, like we go to qualifications for the Champions League. So it's like, I mean, three to four games. And if we win that, we go to the Champions League.
Knut: Alright,
George: That's the current state of affairs, although that can change over the years.
Knut: alright, uh, it all makes sense to me now, that's a lie, but anyway.
Luke: No, uh, I'll definitely, we'll acknowledge here that I'm more of the, the sports fan, uh, generally here, and I, I follow football, I like, uh, I like European, uh, football, uh, well, and obviously I'm using the correct, uh, term despite my, um, my pseudo American accent, uh. Yeah, anyway, um, uh, no, it's fantastic to see, and I mean, yeah, for the non sports fans, uh, listening to this, I get that
Knut: Well, I am a sports fan, it's just that Starcraft 2 is my sport, and yeah, yeah,
Luke: yeah,
George: eSports.
Knut: yeah, yeah, so I watch, watch Starcraft 2 games. That's what I do for procrastination sometimes.
Luke: valid sports, I'm not going to compare it to other things that aren't
Knut: breakdancing? Is that a valid sport?
Luke: Breakdancing is, um, hmm, interesting. I think anything with points, that judges give points, is kind of not a sport, it's an activity.
Knut: yeah.
Luke: but, yeah, anyway,
Knut: thing to do.
Luke: is a thing to do, yes, definitely, but back to, back to, um, um, Botev Plod, is it Botev, Botev, what's, what's, Botev, Botev Plod, yeah, so, so, um, yeah, yeah, like, the, the, the achievement, winning, winning the cup, I mean, the, The cups are sort of more difficult.
They're both difficult in their own way, right? Like, the cup, you lose one game, you're out, basically, right? But, I mean, the league is like this endurance, achievement, right? You have to perform well over the course of the whole season. But the cheat code, so to say, and I probably subconsciously used the other football team's terminology, who's in the space, Real Bedford, um,
Botev Plovdiv's Bitcoin Strategy
Luke: The, the idea right, if, if I'm getting it, is that you guys would, would keep the Bitcoin in the, in the, the treasury, the, the company, and then over the course of time it's just gonna do the number go up thing and, and the, the club will have more resources.
Right. Is that, is that the idea you're thinking with the, the bitcoin strategy?
George: There's actually many, many things to it. And this is kind of the most, let's say, vanilla type of approach. Yeah, like just buy Bitcoin and hold it on the balance sheet, which is, which is great. But there's actually so many other things you can do. And that's where, because if you just do that, frankly, like, I mean, you don't need me involved, right, much.
I mean, just call Coinbase, whatever, wire the money, crack in and, buy. but with us it's like, really, uh, we see a huge opportunity to, first of all, align our brand with the Bitcoin brand, which is a royalty free, uh, The biggest brand in finance, for sure. One, uh, like it's going to be the biggest brand in the world for sure at some point.
Right. So that's, that's one play. And to do this, it's not enough for you to just buy Bitcoin and hold it on a balance sheet. It's what you need to do is proof of work, right? You need to do things that nobody has ever done. You need to really kind of be creative. Uh, and, and, um, to push the boundaries of what anyone has ever done before, right?
So, so that is, uh, that is my kind of job and it's a lot of, um, a lot of just like, let's, let's think of what, what new things we can do with Bitcoin and sports and football that nobody has ever done. Just because others are focused on the short term things, they're focused on, hitting those, those quick wins, those quick goals, which is why, for example, like a lot of the sports and, and that have, you know, interact, they haven't really interacted outside of Bedford with Bitcoin, right?
It's mostly been crypto because it's just, okay, let's make some quick money. Um,
Luke: usually, it's usually just sponsorships, right?
Knut: yeah,
George: yes. Um, and for us, because on the one hand, like, we're not like Manchester United, right? We're not Chelsea. So we don't have that much to monetize immediately. Like we're a large club, but.
Luke: You're a large club in a local league, which is, which is different from the, it's not one of the leagues that is internationally positioned like that. But, but, I mean, the, the difference between you guys and Bedford that I, that I think is, is really interesting. Like, McCormack, what he, Peter McCormack, what he's doing, I mean, he's, he's taking a club from the bottom and aiming for the top.
But who knows how long that's going to take him to get there, right? But you guys are already in the top of your league, right? Like, in the top league.
George: right, yeah, and also there's, there's different in this, we're in the top of our league. My goal, personally, is to go to Champions League, but this is very hard, right? Because, like, okay, when you start from Peter's ground, like, it's easy, okay, every year you level up, you level up, or, I mean, I'm not gonna say it's easy, but it's easier than, uh, than once you're, you know, at our level.
For us, it's important to play currently every year in European leagues like we've done so far and to every year consistently, like, increase the level of the sports, level of the business department bit by bit, and, but like breaking that point where we, you know, win the league, Where we win several more games and enter the Champions League, that, that's really hard.
I mean, because you're already at that stage where everybody, like, so many teams are so strong, right? So it's um, it takes just a lot of ingredients for you to, to, to hit, uh, in order to win. But we're gonna get there.
Knut: and does the club self custody it's bitcoin? And if so, is it a something out of 11 multisig, that sounds like a football thing?
George: Why so? Ah, yeah, an 11? Nah, nah, fuck that. I mean Nah, even, even 7 Motosick is a, is a killer, but no. Um, yeah, I can't really speak too much about this at this point. Yeah. Um, but, um, but yeah, I mean, we do, of course we do self custody. So that's, that's the approach that we've chosen with kind of a lot of, um, we've chosen to go really pure, pure Bitcoin in terms of the strategy.
And that's how we set ourselves apart. That's how we believe we win the long game because for instance, like we Bitcoin with BTC pay server. Which in my mind they don't even have competition. It's the only like, real, solid, autonomous, sovereign way to accept payments. And it's also the way which makes sense for like, Frankly, any standard business, because like, man, we're selling scarves, we're selling, um, membership boat cards, we're selling jerseys, we're selling basic merch, and if we are to sell it with basically any other service out there, outside of BTC Pay Server, we have to basically, uh, indirectly do KYC, right?
Like, we have to go through KYC, we have to go through KYB, which is ridiculous, um, in my mind. And so, um, so that's why we're exceptionally thankful to B2C Pay Server guys, uh, for what they've built. Uh, it's been like an absolute pleasure to, um, to use their product, to use their service. Uh, we have, you know, outside of B2C Pay, we, uh, we are the first, uh, sports club on Nostr.
Where, uh, we have, uh, actively been posting, exploring, you know, meeting people here. Kind of thinking of what we could do from our angle again, like first, first time on Nostr.
Aqua WAllet
George: Um, we have partnered with, uh, Aqua, JAN3's Aqua wallet, which has a, a Botive skin mode now. So if you go to settings, you can turn Botive mode and then it turns into the colors of the club and, you know, have the picture of the stadium there.
Um,
Luke: I'm using Aqua right now because, uh, uh, usually I like to use Aqua as like a sort of a middle wallet, uh, uh, because it's still slightly slower than other lightning wallets because they, they, the, everything actually lives on, on liquid and then they, they, uh, go out via bolts. Uh, so it's slightly slower than a faster, um, like, like than other, um, more direct lightning wallets.
And so usually when I come to a conference, I'm going to load up a, like a temporary. I don't know, Blink or something like that, but I forgot to do that, so I'm just using my Aqua wallet, and you know what, it's been great here, it's been working, uh, so yeah, we're big fans of Aqua wallet and what
Knut: Yeah, and a BTC pay server. I mean, uh, we can echo everything you said that we, BitcoinInfinity. com, like, and the store here We just fired up. Everything is powered by a BTC pay server, and we just love it. Yes.
Luke: So what was your question about, uh, Aqua?
George: If yours is on BOTEV mode.
Luke: Uh, I don't think I've gone into the settings and changed it to Vaudev mode, I'll have to do that, maybe we'll take
George: It's dark mode,
but cooler.
Luke: Doc dark mode, but cooler. Okay. Okay. Actually that's a, that's a, that's a good point. That's a good point. Yeah. We'll take a, we'll take a picture after, uh, after the episode and we'll de proof, bot, uh, bot e mode, and, uh, uh, post that on Nostr.
How does that sound?
George: Let's go.
Knut: Yeah. Nostr. Um, is there a connection there between both a plot and Nostr while you're doing Nostr stuff as well?
History and Freedom
George: Yeah. Well, look, um, a lot of these things is like, so What Botev Plovdiv stands for, um, very importantly, so the club was named after Hristo Botev, who's, uh, like, one of the most Bulgarians, if the most famous Bulgarian revolutionaries, like, historical figure, uh, he was a poet, he was a revolutionary, he fought for Bulgaria's freedom back in the day,
Luke: Which, which day, which, what day did you
George: uh, 110, uh, what is it, like, 50 years ago or so?
Yeah.
Knut: Mm-Hmm?
Luke: Okay. So, so
Knut: before the Commes.
Luke: ottoman, uh,
George: Yeah, yeah, yeah. He, he, he, he fought for the, for the liberation of Bulgaria from, from the Ottoman Empire. And a lot of what he stands for is this fight for freedom, his fight for liberty. Um, and this, this lives until this very day into the identity of the club and to what we stand for into the songs, into the, into the music.
Um, you know, um, the kind of like what, what our fans also resonate with, um, and, and what they sing like in many, in many ways. Right. So, um, Freedom of speech, freedom of, uh, of like freedom in general is, is a value that is deeply ingrained into kind of like what the club stands for. Um, and, uh, you know, that's why I'm into Bitcoin.
That's why I believe. And that's, that's why I saw this even bigger opportunity. Oh my God, like, how is this happening? There's so many, sometimes, you know, some like weird things happen in life and you have no explanation why and how all these things align. But, but for me, it's like this club was made really to.
to be aligned with BOTEF and to be, uh, to, to, to be aligned with Bitcoin and with Nostr. If I look at all the other clubs in Bulgaria, right, like just in Bulgaria, none of the others, like, there's no this contextual historical background that you can make these connections. But with us, we have it, and what a chance that, like, we have this owner, and he got, like, introduced to it, and then we got connected.
Like, how the hell does this happen, man? I don't know,
Luke: We like to say this, the surreal doesn't end, you know, and like, uh, my, my whole story, I've been talking about this, uh, at the, the conference here is like two years ago was the first time I ever met Bitcoiners here in Baltic Honeybadger. We, we met for the, for the first time, uh, all three of us, uh, met for the first time two years ago, I've been in Baltic Honeybadger and it's like, things, things happen so fast.
Uh, I've, I've, uh, I've thought it was been awesome just following, uh, what you've been doing with the, the club and the story. So great to, Great to get to talk about it, but, uh,
Bitcoin in Football
George: Yeah. No, for, for me, like really the, the most exciting part is really even coming forward. So, uh, because, so now it's been, so we, a long, we announced, uh, publicly that we're doing this, uh, 31st October last year. So the anniversary of the, of the, uh, Bitcoin White paper, um, we've built a lot right. And very, very importantly, I'm super proud, like, I don't know if you saw this, but like a month ago, we played on European League, the UEFA League with Bitcoin straight on our jerseys, which was like, like, when I saw this, I'm like, dude, it's crazy that this is happening.
But, but the best is really yet to come, like, like we like to say. Um, so I, I think we, we're, we have, um, we have still so much more to do. So for me, the next big part, which I'm super excited about literally in the coming month as, uh, as I go back. So is to finally get some of our. Players or at least one or two to get to do something publicly about this, because at the end of the day, that's why for me, the more I do, the more I, uh, play in this arena, I realized this is really a Trojan horse for us to bring Bitcoin into the conversation, into the minds, like I said, of people who otherwise wouldn't and, and our players, you know, especially a few of them, they're really influencers, right?
Um, a lot of people follow them. A lot of people respect them. And, um, and if they do, uh, you know, something meaningful, something cool, something impactful, this is going to have a huge impact onto our forwards. This could very well have impact onto, um, other sportsmen, other football people, other football clubs, right?
Uh, so that's why I'm doing it, right? Really?
Luke: No, this is fantastic, and actually this was exactly where I was hoping to go next, so thank you for queuing that up. But, no, no, the game theory of all this, right? Like, one club getting, Positioning as the, as the Bitcoin club in a league, uh, really means that eventually all the other clubs are going to need to adopt Bitcoin.
If they're going to be able to compete, because if play playing out the game theory, number go up, whatever it is, Bitcoin strategy plays out, you guys are going to be the most financially capable club. Financially sustainable in not very long, you know, assuming everything plays out the way we're thinking it will, right?
So, so other, other clubs then would become incentivized to also adopt Bitcoin. So what, what do you, what do you think about that? Like you, do you, do you see that, uh, happening as well?
George: Yeah, I'm not really sure if it would happen to me. That fast, to be fair. Like, I think it's inevitable, right, obviously, but I think it, yeah, like, I think this definitely takes at least three, four years, maybe more. Um,
Luke: That's, that's still pretty fast.
George: yeah, I guess. I mean, I mean, like, okay, let me define it better. It takes three, four years.
So, for other clubs within our league to start doing something like this, uh, maybe it takes less time for other clubs to realize it, but I think for them to do it, it also depends on our actions, right? So because like, we don't have like a treasury of microstrategy or something, so it's not, and we're not doing like a
Luke: you don't?
George: monthly like leverage on top of leverage on top of another leverage, you know, uh, we're not in, in Michael's privileged position. but we can do other cool things, right? Uh, one of the, um, so this is not yet live and this is not yet happening, but one of the, like two, two projects, let's say, I'm gonna briefly, like, tease here that, that I'm working on that I hope to have very large impact is first, uh, building this, uh, simple tool Uh, called like a Bitcoin, uh, football salary calculator that, uh, it's like really a DCA tool, but like looking back and like tailoring it to our niche where I want to, for us to visually and emotionally Show, um, to players, but also to fans of ours, like what Bitcoin could have done for their remuneration, if you look one year back in time, two years back in time, three years back in time, four years back in time, and for them to really realize, Oh my God, this is a no brainer.
Right? I want to make this mess. And this is hard, right? Um, because like, there's so many tools and like, but I want to be, because the audience is very wide, very different types of audience. I want to make this so that you can consume it in like two, three, four minutes. And you're like, okay, I need to learn more about this.
This actually is interesting. There's like, that's so much dense and emotional and compact information that you're like, Whoa. Why am I not doing this? How did I miss this?
Knut: What, what, what was the name of that website? I, I don't know if it's still up, but bitcoin or shit.com or something like that. So, so it lists if you bought this item when it came out, an iPhone five or whatever, uh, and if you had bought b bitcoin instead.com, I think that that's the, that's the name. So if you bought, uh, if you bought Bitcoin instead, it shows you how much, how much more money you'd have now and how many iPhones you
George: Yeah. Yeah. And of course there's many of these tools, obviously like we've all see them and we all like like them and retweet them and repost them. And it's all great. But I think, at least I hope that we can do something impactful with this. If we really tailor it, compact it to a specific type of niche audience with a specific message designed for them.
And because this audience is also like. A type of audience who can also like, um, you know, bring it to other bubbles that we ourselves are not part of, right? So that's, for example, one like, uh, one like project I'm very, very excited about and I hope we can, um, yeah, we'll bring forward relatively soon.
There's a few moving elements, but definitely in the coming month or two, uh, at most. And then, uh, and then, you know, speaking of the other clubs, what, what I want us to do is what we're working is next year, we're targeting to do, I hope we could do the world's first, uh, Bitcoin, uh, Cup tournament. Uh, for youth players, 70 year old boys who are, you know, right there before they sign their first professional contract, start earning money, for them, first of all, like, it's a Bitcoin football cup, like, it's the first time this, this could potentially ever happen And then it's, it's a football first tournament, right?
This is the, we want to make it like top quality, like really the highest quality when it comes to sports, but then you have Bitcoin involved all over the place, right? In terms of brand, in terms of rewards, in terms of, um, in terms of like plays, um, like, like games and, and interactions, activations, uh, throughout, before, throughout, and after the, And after the event, and for this, I'm targeting to get really like, like big clubs.
I mean, because it's academies, right? I mean, I cannot get the Manchester United first team, just maybe we could get the Manchester United 17 year old team or, you know, another big club. We get some of these, and then like we get their brands, we get them on the focus of Bitcoin. And we drive the conversation faster, you know, not three, four years from now, but Less
Knut: what about, um, like right now there's you and there's, um, you guys and there's a real bed for it, right? Those are the two I know of in Europe. Are you aware of any other clubs that are doing a Bitcoin strategy? I mean, is this virus spreading? Like, have you heard anything like,
George: Um, Oh, there's, uh, there's the Austrian Admira Vakir who have done some integration. So it's a second tier, uh, second league, uh, second league, uh, club that have, uh, that have, uh, you know, they've also had Bitcoin on the, their second team jersey. And, um, and they, they also accept Bitcoin payments, uh, here and there, but you know, the thing is, there's some other clubs, um, there's a Miami, um, not Miami, um, a Hawaiian club that, that is doing, uh, that is doing like their Bitcoin gig,
Knut: yeah, there are other, other sports, right, other sports team and sports teams in other sports that are doing it. But, but for football specifically,
George: which ones?
Knut: Uh, I'm so bad with sports, but wasn't there like a hockey team or a basketball team or
Luke: I'm not aware of any others, actually. Yeah, like, uh, there's been some attempts at
Knut: it's
Luke: an orange colored team or something like
Knut: more the individual athletes,
Luke: Yeah, yeah, there have been individual
Knut: for instance, a
Luke: have been individual
Knut: player, and there was some American football player.
George: There's been individual athletes, a lot of them. There's been, I was asking if you know, but there's been a baseball club in Australia, the Port Heat. Uh, who did kind of a Bitcoin strategy. Uh, but very unfortunately that didn't work out. They kind of started this at the peak of the last bull cycle. And, um, and as I understand, uh, there wasn't like a strong alignment between the owners and the management in terms of like understanding that this is a long game.
So that's why this kind of flopped. Um, but yeah, like I, I think the reason why it's not happening in more, unfortunately, and, and, and I see this even, even within our club, uh, you know, but, but definitely no other clubs because Fiat has permitted sports as well. Right. So all the sports club, uh, clubs or the vast majority in football, for sure.
They're like, you know, on the hamster wheel themselves.
Knut: They're indebted,
George: They're indebted.
Knut: to an extreme level,
George: yeah, like, like fighting for every dollar for every income. So it's, it's hard for you to like, Oh yeah, we're going to have this long term Bitcoin strategy that's going to take like two, three, four, five years to play out.
And we can benefit a lot from it. It's very, very hard in, you know, unfortunately for a large organizations, sports club in particular to To have this realization, to map this out, to get others on board. That's why it's not so popular and uh, and that's why I'm grateful and keep pushing that we have this chance.
Luke: I mean, you make a great point here about essentially the, it's the organizational alignment, right? Like the, the, these are companies, sports clubs are companies. They just have this large, the business is involved around getting fans to come in and consume this sort of marketing. Product, essentially. So it's, it's a certain kind of company that's run a certain way, but just like any other company, you need, you need alignment from the management.
So it's, it's fantastic that, uh, Boteb Plovdiv has, has the, uh, alignment and is, is putting their, their trust in you to, to move this thing forward. And I mean, from the, from the perspective of this thing, Playing out, right? The, the best part that, uh, I think one of the best parts that you, you mentioned again was the, the influencers.
Like you get, you get some players, there's, there's so many angles to, to reach people through this. I think it's, I think it's fantastic. The, uh, orange pilling a player and then they move to another club, but they, they, maybe they don't get to get paid in Bitcoin, but maybe they still put, put their money in, in Bitcoin.
Maybe they even ask their club to, to, uh, pay them in Bitcoin, something like that. And then the, the Questions start getting, uh, asked and all this.
5 Year Goals
Luke: So what, what is the, the goal in, in five years, for example, where, where do you see the club in the five year mark?
George: Oh man. Yeah, in five years, I think we definitely have to be in Champions League. Like in my mind, you know, like people around me like, oh, you're too ambitious. I'm like, man, yeah, like in five years, we definitely have to be in Champions League. Uh, that's, that's my personal goal. On our internal Slack, I have the Champions League icon there.
That's why I'm there, right? Um, so, uh, it's a lot of hard work. Like, it's really a lot of hard work. And it's also not completely dependent on me and my work, to be fair. Like, because, at all. I mean, really, like, uh, I mean, at the end of the day, the most important part is the sports department, right? Uh, in the club.
Um, so that has to continue going well. But, but I think We're going in a good direction there too, because we have the, they're the long term view as well, right. We have our academy internally, which is, yeah, it's one of the best academies. It's the best really academy in terms of infrastructure in the country.
That's why we're also can't afford to think of this Bitcoin Cup tournament, because we have the infrastructure, we have like a super cool stadium, that's crazy. If we can, if we can do a final for, for such a tournament there. Um, so, so we have all the things in place in terms of In terms of assets, I would say, uh, it's just a lot of moving parts.
a lot of work, consistency, and a bit of luck. Always it comes, you know, when, when it comes to, when it comes to football and sports, but, but five years from now, I want us to be in the champions league. I want us to be the absolute, you know, international professional level, uh, Bitcoin level, Bitcoin sports club.
and, uh, and I want for this tournament that I start to be like a, like, like to have the fourth edition by then. Uh, and, and I want to have clubs, but five years is a lot of time, you know, as you say, like, I also want to have other clubs following us by then. I think that's absolutely, absolutely is going to be doable.
Knut: What, what are the, what are the tax laws around Bitcoin in Bulgaria? Like what, are there any issues there? Or like what, is it easy enough,
George: It's kind of okay. Uh, it's kind of okay. So if you just buy Bitcoin and hold it, like you don't, uh, you don't, uh, incur taxes, uh, until you sell it, if you accept Bitcoin for payments, um, and if you don't sell it, you can just, uh, keep it as inventory on your balance sheet. So again, no,
Knut: but there's a capital gains tax or something if you sell it. Yeah, yeah, yeah. Alright.
George: 10%. So it's, it's, uh,
Knut: Pretty good.
George: Yeah, I mean, it's not like El Salvador. Okay. Uh, but, but it's, uh, it's, it's way better than many other places. Um, and, uh, yeah, so we've been looking, looking actually, so I was in El Salvador a couple of months ago, because we've been looking very much to do stuff there.
And we've been, uh, yeah. Um, because we've been, we've been thinking of what to do more with Bitcoin, right? So that's why I said, like, it's not just about buying and accepting Bitcoin. It's about corporate strategies, about branding strategies, about how to make money. Um, it's about education strategies. It's, there's so much around it.
So in terms of corporate strategy, I was, uh, we're very attracted by El Salvador, um, and their, uh, capital markets regulation, because they're basically striving to build capital markets on top of Bitcoin. Bitcoin is legal tender there. They have all kinds of, tax incentives for companies to issue debt or to sell equity.
on their capital, on their, um, well, let's say nascent upcoming capital markets, because it's not like it's, you know, hustling and bustling yet. Um, but, but they're, they've put a lot of the rails, uh, um, or they're building a lot of the rails to, um, to really enable the, the, the creation of Bitcoin based capital markets.
So, um, we've had great talks there. We have meetings with, uh, um, we have. Yeah, with the Bitcoin office, right? Um, so, ideally, like, we're striving to build some connection there and to do something, interesting and world first again from a corporate perspective. It's just that, as many things, it's a little harder than you would expect it to be, or it takes a little more time than, Then you would hope to do it.
But my idea or long term vision, frankly, like what we want to do with Bitcoin, uh, and with the club is to enable our current fans and global fans to become co owners of the club. And that's why, you know, I have big hopes for, uh, for us being able to do this out of El Salvador and through El Salvador, because this would, like from a tax perspective, from a branding perspective, from legal security perspective would be, would be ideal.
It's just that, again, um, my enthusiasm is a little over, uh, ahead of kind of like how, uh, how, how advanced and set up everything there is, but, uh, but we're, we're very actively talking to them. We're working with many parties there, so. Just maybe we can have big news there too.
International and Local Effects
Luke: Well, no, and, and you actually said something great about global fans. I think this is a, a fantastic thing, right? A a again, Bedford is, is similar. They've, they've got, they've got fans all over the world and, and I think for you guys it's like who is going to tune into the Bulgarian football league outside of Bulgaria before, well, not too many people, but now a bunch of Bitcoiners.
If they're into, if they're into football or, or not even, because this is the funny thing. There were, there were a lot of people posting about that. They, they've got, they, they don't usually follow, follow sports at all, but, but they'll follow the Bitcoin team. So the, the funny thing is, I think, I think the first, the first club to adopt Bitcoin in every league is going to get all of these global fans.
And maybe the, maybe the, the second one, the third one, maybe can get some kind of other support, but it's really the first one in every
George: really.
Luke: That, that
George: Not
Luke: That's that. I, I completely agree with you there. It's the, it's the first one
Knut: first mover advantage.
Luke: mover advantage. It's gonna get, it is gonna get all of the, all of the Bitcoiners are gonna now be, be supporting and, uh, uh, yeah.
I mean, have, have you seen, uh, some, some uptick in, uh, kind of international
George: yeah, yeah. So, international but also local. Like, local is very important. Like, we have, like, so many people in the country who's like, just what you say, like, I didn't care about sports or football, like, forever, or at all, ever, but now I follow, now I buy merch, now I come, you know, every now and then they come to games, so
Luke: Well, because there's the bread and circuses thing that you said, it gets tossed around in the Bitcoin world and also some other places on kind of the Twitter sphere and whatever, it's like it's a distraction, that sports is sort of a distraction from clown world basically and it's a way of people to sort of Uh, forget about what's going on around them, but I think that's also missing the, the positives, which it, it's a, it's a community builder, it brings people together, there's a, there's a sense of, of pride in, in something local succeeding, everyone, everyone's happy, there's, there's real economic, uh, effects usually when a, when a local sports team wins, and so, so from, from my perspective, I, I, I think, I think sport is a good thing, and it's, and it's, it's something that, that people can rally around, and so,
George: an amazing thing.
Luke: Yeah.
And, and so what, what are, what are you looking at locally? Like what, what do you hope to have the effect, uh, uh, locally in, in piv?
George: Yeah. Um, yeah, no, look, uh, for me, sports, like, for us, the, the, the, the, about Plovdiv, for me, that's what I realized, like, we're kind of very much into Bitcoin and stuff, obviously, that's our interest, but I think when we go on a Bitcoin standard, Right. And, uh, in general, people start feeling wealthier, opposed to, like, being in the grind.
You're just going to have more time for fun stuff, right? Like playing football, I mean, or volleyball, or whatever your sport is, or, like, going and cheering your team, and, uh, and being part of such a community. And I think that's really what, you know, even Nostr is about. Like it's, Being part of these communities, because that's fun, and like, we as humans, at the end of the day, we are living to be part of communities, right?
And you find your community, you're an active part of it, you contribute to it, you evolve it, right? You build it in one way or another. And unfortunately, you know, today in the fiat world, this is just like A stress valve in many ways, or like you say, like Brothers and Sisters, whatever. Um, but, uh, but I think it can be so much more, right?
It is, but it can be so much more for a larger amount of people and so on and so forth. uh, but yeah, well, back in Plovdiv, man, like, I have big hopes. I really have big, big ambitions there. I want to get Bitcoin into the wallets of, uh, of like tens of thousands of people. I want people to wake up. I want people to see.
Luke: big is piv? How many
George: It's like three, four hundred thousand people. So it's a lot. Uh, our stadium is, uh, 21, 000 seats stadium. I'm kidding. I'm kidding. It's, it's 19. I wish it was 21.
Luke: Yeah. You'll have to add 2000 more
George: Maybe, yeah, we'll, we'll think of some additional construction.
Luke: the, make the infinity stand when
George: Right. Right. But, uh, but yeah, like the setting was super cool. Like, it's really cool.
Like when it's feel like, man, the atmosphere is amazing. Um, and so it's, and it's really this community that you can feel that people are involved. So it's, it's like consistency and it's social engineering in one way or another, right?
Knut: one of our favorite words,
George: but in a positive way.
Knut: in a positive way, okay.
George: So it's social engineering for us to ingrain Bitcoin and make it part of kind of what people see, do, have, own, interact with, right?
So, uh, I think exactly because of this community element, exactly because, Because, you know, football is a football club and there's this unique living organism we can, we can create this and, you know, it's fascinating. I'm so much into this and there's other people who are so much into this. Oh my god, like, we can make such a big difference.
And, and like in the country. You know, on a political and economic level, they don't get it. Like, they don't see it. They just are in their, you know, like, oh, are we going to accept the euro? Oh, what's happening with the war? I'm like, who cares? Let's build.
Bulgarian Currency Situation
Knut: Yeah, Bulgaria has its own shitcoin, I almost forgot about that, but uh, what's it called again?
George: Kinda. Um, but not quite, to be fair. It's, it's a good coin, uh, not for investing, but, but for medium of exchange is actually decent. Uh, Lev, Lev
Knut: Lev, yeah, yeah, yeah. Yeah,
George: and I recently got educated about this. So, uh, the lev is pegged to the euro. So, um, uh, so, so that, that is super cool for, for us, for me as a consumer, for businesses, because like the fixed rate.
So for trade is, um, It's, it's good, right? As the world would be in the future. You have one currency, Bitcoin, you don't have the currency exchange risk, right? We don't have it only with the European Union. And the good part with this, so, we got, we got hyperinflation back in 1997. Was really bad. People lost almost everything, everything, in many cases.
Um, and then we got this so called currency board introduced and the currency board is like we have the left, but the left has to be backed up by other currencies. So it's like a stable coin, kind of like how Tether is backed by, by dollars. You know, the levy is backed by euro and like a basket of, I think they have some other currencies and assets, which is cool because the local politicians, they cannot print, they cannot, you know, so, so it's been, it's been, I think, way better than Hungary, Sweden, uh, Finland, you have your, oh
but Sweden I've heard it's kind of bad,
Knut: It's kinda bad, Norway too, like, both Swedish and Norwegian crown, and the crown in Czechia, like the Czech Republic, it's also
George: Yeah.
Knut: I mean, they're all going to shit the smaller
George: So, so for us, it's like, I would say we're better than, than the Corona, the, and, and all these like local currencies, because we kind of just are there to the, peg to the Euro. The local politicians don't have the opportunity to print. So it's, it's a very good position for us to be.
Luke: You, you get the, the negatives of the, the euro. But, but still, I mean, I mean the, the realistically, the dollar at the Euro and maybe the, the Chinese currency are the only, are the only ones that are in the, sort of within our own, within our own lifetimes are, are going to be not as terribly bad against Bitcoin.
But all the other ones are just, are. All the other ones are
Knut: Yeah, I think it's just a matter of time before both, uh, at least Sweden, uh, switches to Euro standard. If not switching to Bitcoin standard happens first, but well, we'll see, we'll see what happens.
George: man. I'm very bearish about the Euro.
Knut: yeah, yeah, it's like,
Luke: It'll be the second last to fall or third last but but yeah it's it's it's it's not going to be the the last and so it's yeah.
Knut: So that is what it is. I mean, speaking of Bulgaria and currencies and stuff,
Bitcoin Adoption in Bulgaria
Knut: like, how is the rest of, how is Bitcoin adoption in general in Bulgaria? What's happening in other places? Like, Plamen opened a bar, I saw, and like, what are the connections? What's happening?
George: It's actually quite cool. I'm, I'm, I'm quite happy with, with how the ecosystem is evolving. There's, there's Plamen, um, with his whole community, like content creation, the conferences he's been doing, which has been like a very, I think he's responsible for like, I don't know, probably like, 000, maybe several 10, 000s of people who have opened their eyes and even if they're not hard bitcoiners, they now own bitcoin.
Uh, so that's huge. We have other content creators also who've had an impact. We have now once or twice per, yeah, about twice per year we have like, uh, A small, uh, merchant, uh, like, conference events, so for merchants to accept Bitcoin. we have these people who are active and who are doing things. Now, actually, yeah, there's something new that's coming up here, uh, literally in Plovdiv is we have this, um, this, uh, great dudes who have this, um, um, it's an application for, uh, ordering food, like takeaway and, uh, what is it, like,
Knut: like Glovo or
George: yeah, yeah, like Glovo, um, but, um, but, um, But it's not like this big corporate thing that, but, but still, it's a very good product and they've integrated accepting Bitcoin there for quite some time now they've made it even easier and they've introduced.
So we have like about, I think it's 15 restaurants in Sofia and like five or so in Plovdiv where through their system, you can order food. And pay with Bitcoin online, or you can also go in the restaurant and pay in Bitcoin online, and they just, um, they just won a, uh, grant from, uh, Bitcoin Beach, uh, and, uh, they're going to use the grant, uh, to, well, the attempt is really to start like a small circular economy, if you would Um, where, so if you go, uh, to one of those restaurants and pay with Bitcoin, you're going to get sats back 10%, and then, um, the restaurant is also going to get 10 percent sats back.
And if you order food, um, through their app, also the driver is going to get, uh, some sats back. And, uh, we've just been discussing, because obviously we're partnering with them, with the football club, so we'll push this out, because some of the restaurants that are there are our, I mean, basically, like, we have two restaurants locally that are partners, we got them in, right, obviously, in the deal, um, So, so that is also like, for me, it's like super cool because now for so far, the club has been pushing Bitcoin.
Now we have two of our restaurant partners who are themselves like hard Botevists, Botefans, and like they're popular. Now they're starting to accept Bitcoin in their, in their two restaurants, right? And they're going to have their campaigns. We're going to push them more. So, um, so I'm really excited about this and fingers crossed this goes well.
We have good metrics because if we have good metrics. Yeah, we'll look for ways to grow this. So there's a lot of grassroots things happening, which I love. On the top, nothing.
Knut: It's the way it's supposed to be.
George: But it's the way it is. Yeah, it's a better
Luke: Yeah it really seems like that you get one or two of these big anchors like like for example you you guys have had that had that conference last couple of years but now with both of Plavdev now Bulgaria is really got a couple of big anchors. Big relative in relative terms, uh, and all of this other stuff can, can start coming up around it.
And, uh, love, love to see it. I mean, he, I mean here, here with Rega, there's Honey Budger has been going for a really long time, and I, and I even think that they are honest about, we, we would, we just talked to, to Max, uh, about this, uh, from Defi and like yeah, there's not much other adoption in, in Lavia and this conference has been going on for a long time.
Exactly. And so it's just like, uh, it's, it's, it's great to see, uh, in, in your case, in Bulgaria's case, that there's, there's more of this, uh, picking up. So, yeah,
George: Well, I think it's really, in our case, I don't know, like it's grassroots, like I said, and I really believe grassroots and then Rio or for the vast majority, Rio adoption comes permissionless life. It comes like it's not forced. You know, there is this point where, okay, there's Plamen, like, he got the inspiration, he makes his content, he does the conferences, Like, our owner, he sees this opportunity for Bitcoin, for the club. He takes the action, right? So it's, it's not like, so it's individuals, right? Taking actions and then, as you have, you know, several of them, maybe others get inspired or get ideas going and that's how the magic happens. And, uh, yeah. Excited about it.
Wrapping Up
Luke: it's awesome, man. Great hear your story. So, was, uh, was there anything else that you wanted to discuss or bring up on this topic?
George: no, I mean, what I would say is absolutely, uh, Please, uh, you know, Knut, you've been, but please, you're absolutely welcome, Luke, join as well, like, both of you should come
Knut: Absolutely. Highly recommend it. I had a great time in Bulgaria, and it's such a fascinating country, it's such a rich history and such a beautiful place, and the food is great, and it's very affordable, it's very, yeah, very
George: like, I have people who come in Plogis specifically to, like, nomads, spend, like, a or a month. So, so please enjoy, visit the game. come spend in the restaurants where they accept Bitcoin, follow us on social media for sure, so, X and Nostr,
Luke: Yes, all the details, please.
Knut: And also like one of the eras, uh, infamous eras of Bulgaria is the commie era, right? Where you can see the impact that system had on the country and how horrid it is. Uh, so it's, it's, uh, that might not be a good pitch for, uh, but that's
Luke: Let him, let him share his social medias, Knut.
George: wait, do you have, do you have something
Knut: no, no, I think like the, The point I was getting to is, if you get to Bulgaria, don't only go to Sofia, go around the rest of the country, because it's not as raped as that town was by, as that city was by communism, all this concrete, yeah, yeah,
George: yeah, the,
Knut: you can really see the impact there. I'm not, um, yeah, this came out totally wrong, but I'm trying to, I'm trying to, To hype Bulgaria here, but also there's a historical lesson to be learned in the country, for sure,
George: sure. It's really like, there's so many different things there. So there's the communist part, there's like fucking amazing nature, there's like
Knut: is everything, yeah.
George: if you're into hiking, there's like, just like from Sofia, what I love about Sofia, like just last week, twice, end of the day, I'm like fucked up, like tired of computer.
40 minutes up and I'm up in the mountains, hiking, in like 2000 meters altitude. Uh, so, so there's all these like super cool things, but on the socials, yeah, we're on Twitter. we're on Nostr, uh, so Twitter is, um, botif underscore, uh, en, on Nostr, uh, we are just botif. Yeah, you can find us.
Luke: going say you're NPUB? No, no, no,
George: I'm still learning it, okay?
Luke: we'll post, you're still learning, we'll post all the details in the show
George: Yes. Yes. And feel free to also check out our website. We have, due to our El Salvadorian, um, kind of project, we already have a Salvadorian website, which is very easy to remember, botif. sv. So you can go there and from there you'll find all the links and information.
Luke: Absolutely fantastic.
Knut: Great! Get the inverse of Clown World. This is a shill. BitcoinInfinityStore. com And thank you very much for coming on,
George: was great having
Knut: Great to have
Luke: George, thanks so much. This has been Bitcoin Infinity Show. Thank you for
-
 @ 6ad3e2a3:c90b7740
2024-09-24 13:36:24
@ 6ad3e2a3:c90b7740
2024-09-24 13:36:24 I have a thesis as to why things have gone so off the rails in the United States (and beyond), but it might not be what you think. Most of what we decry as insane and inexplicable policies are but symptoms of an underlying process. That process is the creation of money via fiat, the way in which the money propagates through the system and how it distorts the incentives of so many who are beholden to it.
I have a thesis as to why things have gone so off the rails in the United States (and beyond), but it might not be what you think. Most of what we decry as insane and inexplicable policies are but symptoms of an underlying process. That process is the creation of money via fiat, the way in which the money propagates through the system and how it distorts the incentives of so many who are beholden to it. Let’s start at the beginning. New money is created via debt issuance all the time. It’s why the US government is nearly $36 trillion in debt — it issues bonds and owes the bond buyers the interest and principle on it. “Issuing debt” is a fancy way of saying “borrowing money.” The US government borrows from its citizens, corporations, geopolitical allies (and even adversaries) to finance its operations.
If there is insufficient demand for its debt — if not enough people want to loan it money, it can raise rates, i.e., promise to pay more interest so as to entice more lenders, or just have the Federal Reserve buy the debt (either via its primary dealer banks or in some cases directly) and place the assets (bonds) on its balance sheet. US government debt (promise to pay) is an asset, and so the Fed can put that promise on its balance sheet.
The result of new money coming into the system via government borrowing is inflation. There is simply more money chasing the same amount of goods and services, so the prices for them rise. If while injecting more money into the economy the government were simultaneously injecting more goods and services, there wouldn’t be inflation, but unfortunately while you can always print more money out of thin air, you can’t print more energy, grass-fed steak or expert medical care.
But the inflation of the money supply and its concomitant debasement doesn’t happen all at once. Initially when there’s more money injected into the system, those who are closest to the new supply (banks through which it passes, their largest accounts, investors and asset holders) spend it and benefit from it before its inflationary effect has fully taken hold. This is known as the Cantillon Effect. Eventually inflation drives ordinary wages up too, but not enough to offset higher prices, and only after the Cantillonaire class has disproportionately benefited.
The unfairness of this arrangement is evident enough, but the second and third order effects are far more sinister. When the government can essentially borrow (print) money to finance whatever it wants, whether the Iraq War and its military contractors, “free” mRNA shots (Pfizer made nearly $100B off those contracts) or any other policy that benefits cronies and favored corporations, there are going to be a lot of resources and effort devoted to getting in good with the decision makers in the government.
Put differently, if I run a small business, I can only earn money if I offer my customers something they value enough to pay more for it than it cost me to produce. If I hire you, you’ll need to add value to the business and also hope it can continuing adding enough value to customers to pay your salary. We have to work for it.
But the government can simply print it, and in infinite supply. Are you better off starting a business (or working for one) that relies on adding value to its customers in a competitive environment or one that taps the infinite font of government money?
 People respond to incentives, and as a result of the untethered money printing which began in earnest in 1971 when Richard Nixon took us off the gold standard (essentially a default caused in part by the cost of the Vietnam War), financial services experienced explosive growth, making up a larger share of the economy than at any time since the eve of the Great Depression. The best and brightest in large numbers eschewed value-creating careers in fields like engineering for jobs in finance. Why try to innovate and compete in the ruthless marketplace if you can join forces with the Cantillonaires, quickly become one and amass generational wealth via passive asset holding?
People respond to incentives, and as a result of the untethered money printing which began in earnest in 1971 when Richard Nixon took us off the gold standard (essentially a default caused in part by the cost of the Vietnam War), financial services experienced explosive growth, making up a larger share of the economy than at any time since the eve of the Great Depression. The best and brightest in large numbers eschewed value-creating careers in fields like engineering for jobs in finance. Why try to innovate and compete in the ruthless marketplace if you can join forces with the Cantillonaires, quickly become one and amass generational wealth via passive asset holding? But it’s not just the bankers and the asset holders. In the scheme of things that theft off the top and upward redistribution is almost benign. Where things start to go seriously off the rails is that people cannot save in an inflating currency, and so they are forced to buy financial instruments like stocks and bonds. (Poor people can’t afford to do so, try to save in a debasing currency and usually stay poor and stuck.) But even middle and upper middle class people who get a small piece of the Cantillon pie, as their asset values rise on account of the increased money supply (to offset their lagging wages), have a new problem: most lack the time, skill or inclination to hold down a second job managing their investments.
As a result, they either lost money in the markets (selling when the market dropped, buying the top when everyone had already made money) or paying exorbitant fees to brokers who added little value except to take the stress of managing it out of their hands.
Eventually, investors figured out low-fee passive index funds outperform brokers, and so millions piled into them. As a result, companies like Black Rock, Vanguard and Fidelity absorbed money flows in the trillions of dollars, giving them outsized power. If they divested from a company its stock would tank, and its executives would miss their marks. If Blackrock and its ilk decided every company needed to be ESG or DEI compliant, the CEOs had little choice but to follow suit or they would be replaced. Consequently, you had a few elites, essentially dictating policy for the entire economy.
But back to that $36 trillion in debt, roughly a quarter of which was racked up during ill-conceived wars of choice in the Middle East. A country with that level of debt can’t honor its obligations over the medium and especially longer term. The elites know this — they know the promised social security, pensions, healthcare entitlements, etc. can never be delivered in the way they’re expected. Via inflation they might be delivered nominally, i.e., you might get the number you were promised, but no chance you’d ever get the purchasing power that number represented when the promise was made. When groceries cost a thousand dollars, a million dollar pension doesn’t go far.
What that means is the wealth people think is coming to them is not there. Even the wealth represented by the digital bits in your bank account isn’t there. Sure, if you took it out and spent it tomorrow, you could get 2024-level value for it, but even Bernie Madoff’s first clients to withdraw were able to get their money out. The problem is that collectively the digital bits do not remotely have the purchasing power they purport.
The elites need to do something about this, or there will be a French Revolution-style reckoning for them. They looted society’s collective wealth, and they need to assert control over the fallout. And they need to make sure the fallout is delayed. They need to keep people divided and fearful of demanding what they were promised.
The fear-mongering takes many forms (pandemics, climage change terrorism, white supremacy!), but foremost among them is to cast anyone who purports to reveal the unfair arrangement to the people as an enemy. “Populist” candidates must be smeared as “racist” or “fascist” and deemed unacceptable to large swaths of the population. Luckily for the oligarchs they had a few aces in the hole to enforce this perception. First, they had the megaphone of legacy media and also large centralized social media companies like Facebook and Twitter on which they could lean to suppress content that undermined their aims.
Second, via the centralized investment firms, they could dictate terms and initiatives to large publicly traded corporations and the officers of said corporations could reward compliant employees with promotions and power. Anyone who worked in those spheres therefore was selected for belief in the corporate-media dictated narratives.
Third, via their control of academia (donations from academia to the Blackrock-favored democratic party outpace donations to the disfavored one by a factor of 10), they could indoctrinate college students, reward the ones for whom it takes with jobs and social acceptance. Moreover, they also encouraged more people to go to college than ever before, creating an overproduction of elites, and a large indebted, indoctrinated wave of young people who didn’t have much to show for the debt they took on. That made them more desperate to stay in the good graces of the oligarchy, more compliant lest they lose the small income stream they were able to find in low-level managerial roles. Finally, as a reward for following the path, they were given status as educated people, those who had mastered the protocols of the elite.
Things like using the proper pronouns, avoiding the forbidden words for which a less savvy person would be cancelled and having the right beliefs (like climate change being an existential threat, more on that below) signaled moral and class superiority. Even if the electrician or plumber made more money than them, offered a service that provided real value to people, he did not know increasingly labyrinthine protocols for navigating elite discourse.
The more successful members of this class have all of these incentives plus a real paycheck, and they and those aspiring to join them formed a strong and influential bulwark against the rising discontent of working class people struggling with rising costs and feeling the disdain of elites who saw them as “deplorables” and “racists.”
The climate change agenda — promulgated religiously via academia and corporate media — was especially powerful because it instilled fear, a sense of dwindling resources and an incentive to consume less. That last part was especially crucial because if the digital bits in people’s accounts were going to fall far short of their purported purchasing power, getting an army of people to voluntarily reduce their power consumption (and angrily demand it of others) killed two birds with one stone. Not only would they have a ready-made excuse for the lack of promised power (purchasing power is the ability to wield energy, and “energy” and “power” are essentially synonymous), but they would also have a reason to bar those who did not voluntarily relinquish it from enjoying its full use.
Once the oligarchs had successfully indoctrinated a large swath of the population to be in debt, desperate to hang onto their trivially replaceable jobs, believe power consumption was not only wrong but an existential threat and anyone advocating otherwise was racist, fascist and morally inferior, they could sell them on ever-increasing top-down government control for the greater good. No matter how draconian the measures — covid lockdowns, forced injections, mask mandates for toddlers — the indoctrinated (and terrified) subject would not only go along but enforce those edicts on others.
Anyone refusing to go along would be accused of heresy, so to speak, and mobs of eager acolytes would be quick to call for his excommunication. If you think this is hyperbole, you are probably memory-holing the covid era wherein some of the most prominent celebrities and politicians eagerly advocated for those who declined pharmaceutical conglomerate chemicals to be barred from participating in society, put in camps and left to die should they need medical attention.
Of course, maintaining total control over the population is difficult, especially as economic conditions worsen, and those who are not totally beholden to the cantillonaire corporate class and who bypassed the university indoctrination complex gain awareness via uncensored niches of social media and ignorantly trusting their own eyes and ears. To that end, pushes for increased censorship were needed, as well as ever novel social wedge issues to divide the populace. On their face insane policies like letting biological males compete in women’s sports and encouraging minors to have sex changes served to further divide people and also served as a loyalty test of sorts. If you could advocate for Lia Thomas dominating collegiate women’s swimming, for example, you demonstrated your bona fides as a true comrade to the educated class.
Of course, suggesting something like this or advocating for sex changes among 12 year olds would have landed you in a straitjacket 15 years ago, but that was the point. If you were not willing to state a woman could have a penis and men could get pregnant you were not sufficiently loyal to the cause. Perhaps that’s a little too strong, but at a minimum you could not vociferously object to these absurd precepts and still expect to keep your job.
As such we now have a wide swath of educated, above-average IQ, ostensibly otherwise sensible Americans cheering on the fomenting of World War III in Ukraine, justifying ideological censorship contra the very First Amendment of the United States Constitution, unchecked illegal immigration irrespective of financial and social cost, among other insane policies of which virtually no one had been in favor when they identified as garden-variety liberals 10 years ago.
They have been bribed not to see what’s happening in front of their faces, not to remember how their rights were violated during covid, not to acknowledge the myriad lies to their faces like “the lab leak is a conspiracy theory,” “Trump colluded with Russia to steal the 2016 election,” that “Hunter Biden’s laptop was Russian disinformation” that they only needed to take the vaccine to avoid covid, that covid was a “pandemic of the unvaccinated” that Joe Biden was “sharp as a tack” and anyone saying otherwise was a conspiracy theorist.
I could go on for pages about the lies and hoaxes, but you get the point. The problem is via money printing, the oligarchy has essentially unlimited power to astroturf all manner of absurd agendas and incentivize tens of millions to go along via social and professional bribes. Of course the truth will come out eventually because it always does. Lies can carry the day so long as enough energy is pumped into the system to sustain them, but the truth is like gravity — when your plane runs out of fuel it will necessarily fall to the ground.
So this is where we find ourselves — a half awake populace of “conspiracy theorists,” “racists,” “anti-vaxxers,” “xenophobes” and “cranks” pointing out the unfathomable and mind-boggling destruction taking place in our cities, schools and once esteemed institutions, being dismissed, ignored and vilified by mobs of head-in-the-sand loyalists bribed not to see the blue whale in the room, the unsustainable, immoral and unholy assault upon the foundations of civilization itself, right in front of their faces.
-
 @ 32b3653a:500d7f43
2024-09-24 12:47:59
@ 32b3653a:500d7f43
2024-09-24 12:47:59Opinion about HTX: Buy Crypto & Bitcoin (android)
Caution should be exercised when dealing with investment firms , as i unfortunately experienced a significant loss with an online investment company . With the intervention by Againstcon. com , i was able to successfully track and recover my funds . Their intervention was pivotal in resolving the situation effectively
WalletScrutiny #nostrOpinion
-
 @ 9358c676:9f2912fc
2024-09-24 12:29:11
@ 9358c676:9f2912fc
2024-09-24 12:29:11OBJECTIVES
To establish a guideline for the management of Acute Community-Acquired Pneumonia (CAP) in our center, for both outpatient and hospitalized patients, with the aim of:
- Reducing morbidity and mortality associated with the condition.
- Improving the quality of medical care and optimizing hospital resources.
- Delaying the progression of antimicrobial resistance.
SCOPE
All patients over 16 years of age diagnosed with Acute Community-Acquired Pneumonia who are being followed by our institution in an outpatient or inpatient setting.
RESPONSIBILITIES
Physicians from the Medical Clinic, Medical Emergency, Coronary Unit, and Intensive Care Service. Nursing Coordination. Pharmacy Service. Infection Control Committee.
REFERENCES AND BIBLIOGRAPHY
- Community-Acquired Pneumonia in Adults. Recommendations for its management. Lopardo et al. MEDICINA (Buenos Aires) 2015; 75: 245-257. Argentine Society of Infectiology. ISSN 0025-7680
- Diagnosis and Treatment of Adults with Community-acquired Pneumonia. An Official Clinical Practice Guideline of the American Thoracic Society and Infectious Diseases Society of America. 2019. American Journal of Respiratory and Critical Care Medicine Volume 200 Number 7 | October 1, 2019. DOI: 10.1164 rccm.201908-1581ST
- ERS/ESICM/ESCMID/ALAT guidelines for the management of severe community-acquired pneumonia. Intensive Care Med (2023) 49:615–632 https://doi.org/10.1007/s00134-023-07033-8
- Antimicrobial resistance. WHO. https://www.who.int/news-room/fact-sheets/detail/antimicrobial resistance
- Internal Medicine. Farreras-Rosman. Volume I. Elsevier. 2008 Edition.
- Considerations for the Responsible Use of Antibiotics in COVID-19. Argentine Society of Infectiology. 2020. https://drive.google.com/file/d/1BmXD5x6rEpSqDIc8urccdqLcZKkP3U7X/view
- Penicillin Allergy. Castells M. New England Journal of Medicine, 381(24), 2338–2351. doi:10.1056 nejmra1807761
INTRODUCTION
Pneumonia is one of the leading causes of morbidity and mortality worldwide, affecting patients of all ages and with various risk factors. Proper management in both outpatient and hospital settings is crucial for improving clinical outcomes and reducing associated complications.
This document aims to standardize and optimize the treatment of pneumonia based on the most current evidence and recommendations from leading scientific organizations. It seeks to be a practical tool for healthcare professionals, providing a clear and concise approach to the diagnosis, treatment, and follow-up of patients with pneumonia.
FOUNDATIONS. HOSPITAL SITUATION ANALYSIS:
- Pneumonias represent a significant burden on the healthcare system due to their high prevalence and potential severity, underscoring the need for a standardized approach.
- A clinical guideline facilitates decision-making, ensuring that all healthcare professionals follow a uniform protocol that integrates best practices, thereby reducing variability in treatments. This allows for better resource utilization, optimizing antibiotic use and reducing the emergence of antimicrobial resistance.
- Antimicrobial resistance has been proposed by the World Health Organization (WHO) and related organizations as the leading cause of death and hospital expenditure by the year 2050.
- Pneumonias in our center, in their various presentations, have shown significant prevalence in hospitalizations according to measurements taken in 2024.
- In our center, antibiotics, as a whole, have been the main source of financial losses related to drugs during the billing cycle from June 2023 to July 2024.
EPIDEMIOLOGICAL SITUATION:
Pneumonias represent a global incidence of 1.26 cases per 1000 inhabitants. It has been documented in some centers that this incidence can increase in patients over 65 years of age, representing 34 cases per 1000 inhabitants. Outpatient mortality varies between 0.1% and 5%, but can reach up to 50% in hospitalized patients, especially those requiring Intensive Care Unit stay.
The main risk factors for developing pneumonia are:
- Chronic Heart Disease.
- Chronic Respiratory Disease.
- Chronic Kidney Disease.
- Advanced-stage HIV infection.
- Immunosuppressed. Solid Organ Transplant. Hematopoietic Stem Cell Transplantation.
- Diabetes mellitus.
- Neoplasms.
- Smoking.
- Chronic use of Corticosteroids or Proton Pump Inhibitors.
- Multiple Myeloma and Hypogammaglobulinemia.
- Anatomical or Functional Asplenia.
The main causative agents of acute community-acquired pneumonia in our setting are:
- Respiratory Viruses (Influenza, SARS-CoV2, RSV).
- Streptococcus pneumoniae.
- Haemophilus influenzae.
- Staphylococcus aureus.
- Mycoplasma pneumoniae and Chlamydophila pneumoniae.
It should be noted that Streptococcus pneumoniae shows a good sensitivity pattern to penicillin and continues to be the most frequent causative microorganism. Haemophilus influenzae only shows beta-lactamase production in 10% to 23% of cases. Staphylococcus aureus in our setting has a low incidence of methicillin resistance, although this possibility should be considered in certain situations and severe clinical presentations. Given these considerations, beta-lactams remain the first-line treatment.
Regarding Pseudomonas aeruginosa isolates, they will only be relevant in patients with risk factors such as bronchiectasis, cystic fibrosis, prior treatment with corticosteroids, or broad-spectrum antibiotics.
Emerging pathogens of some relevance include the eventual emergence of cases caused by Leptospira interrogans, Legionella pneumophila, and Hantavirus. These cases should always be associated with a specific epidemiological link.
DIAGNOSIS
The diagnosis of pneumonia is based on clinical and imaging criteria. For the diagnosis of Acute Community-Acquired Pneumonia, we will consider:
Symptoms and Clinical Signs (at least 1 of the following): * Fever. * Altered general condition. * Cough. * Sputum production. * Chest pain. * Dyspnea. * Hemoptysis.
plus
Radiopacity on Chest X-ray (Alveolar consolidation with or without air bronchogram, interstitial pattern, bronchiectasis, cavitation, pleural effusion, new radiopacity, etc.). It is always recommended to request both frontal and lateral views.
Chest CT remains a method with greater sensitivity and specificity for evaluating lung parenchyma compared to conventional X-ray in infectious pathology. However, a simple chest X-ray is an adequate method for the initial evaluation of the condition and its complications, which is why a CT scan is not recommended as an initial method for evaluating pneumonia and should always be preceded by a conventional chest X-ray.
CT studies should be considered in the following situations:
- Respiratory failure.
- Evaluation or suspicion of differential diagnoses to Acute Community-Acquired Pneumonia.
- Evaluation or suspicion of complications of Acute Community-Acquired Pneumonia.
- Evaluation of radiological patterns that are not entirely clear on the chest X-ray.
CHOICE OF CARE SITE AND TREATMENT
For the choice of care site and treatment of pneumonia, it is recommended to complement clinical criteria with validated mortality scores associated with risk factors and clinical status.
CURB-65 (1 point for each item): * Confusion * Elevated urea greater than 90 mg/dl * Respiratory rate greater than 30/minute * Systolic blood pressure < 90 mmHg or diastolic blood pressure < 60 mmHg * Age equal to or greater than 65 years
Results:
- Groups 0 to 1: Outpatient management.
- Groups 1-2: Admission to General Ward.
- Groups 3-5: Admission to Intensive Care Unit.
- Appendix: A pulse oximetry reading of less than 92% is recommended as an independent factor for inpatient management under expert recommendation to complement the score.
COMPLEMENTARY STUDIES AND CULTURE SAMPLING
Once the diagnosis is completed, the patient's risk stratification and the choice of admission site are made, the following complementary studies and culture sampling are recommended to proceed with the patient's study during treatment.
Outpatient patient: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests).
Inpatient patient in general ward: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests). Acid-base status if pulse oximetry is less than 92%. * Sputum sample (Gram stain, culture, antibiogram). * Blood cultures. * In the presence of pleural effusion: Thoracentesis. Physical-chemical study for Light's Criteria. Direct and Culture of Pleural Fluid.
Inpatient patient in intensive care unit: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests) plus acid-base status. * Sputum sample (Gram stain, culture, antibiogram). Tracheal aspirate, Mini-BAL, or BAL sampling for patients requiring ARM upon admission. * Blood cultures. * Urinary antigen for detection of Streptococcus pneumoniae, if available in microbiology. * In the presence of pleural effusion: Thoracentesis. Physical-chemical study for Light's Criteria. Direct and Culture of Pleural Fluid.
Special considerations for Viral Pneumonias: * We recommend performing a viral panel for Influenza A/B for any pneumonia presenting at least 1 risk factor mentioned during periods of viral circulation in the community. * We recommend performing a viral panel for SARS-CoV2 for any pneumonia presenting at least 1 risk factor mentioned during periods of viral circulation in the community or having epidemiological criteria of a suspected COVID-19 case. * The Infection Control Committee will timely inform based on the National Epidemiological Bulletin about the presence of circulating respiratory viruses in our setting.
Special considerations for Atypical Pneumonias and HIV Testing: * We recommend serological testing for IgM/IgG for Chlamydia and Mycoplasma for any pneumonia presenting a subacute evolution at the time of clinical presentation or clinical-radiological dissociation in its presentation. * In the suspicion of pneumonia caused by emerging pathogens (Legionella pneumophila, Leptospira interrogans, Hantavirus), consider the necessary epidemiological link as a prior epidemiological background before requesting specific diagnostic tests. * HIV testing is recommended for all pneumonias, with special emphasis on those that do not present the conventional risk factors mentioned.
ANTIMICROBIAL TREATMENT AND DURATION OF TREATMENT:
Directed antimicrobial treatment will be based on the present risk factors and the choice of care site and treatment.
Outpatient patient <65 years and without risk factors:
First choice: * Amoxicillin 875mg/12h orally for 5-7 days.
Scheme for history of allergy to Beta-Lactams: * Clarithromycin 500mg/12h orally for 5 days or * Azithromycin 500-1000mg/day for 5 days.
Outpatient patient >65 years or with at least 1 risk factor:
First choice: * Amoxicillin-Clavulanate 1g/12h orally for 7 days.
Scheme for history of allergy to Beta-Lactams: * Clarithromycin 500mg/12h orally for 5 days or * Azithromycin 500-1000mg/day orally for 5 days.
Inpatient patient in General Ward <65 years and without risk factors:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV +/- Clarithromycin 500mg/12h orally/IV for 5-7 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1g/day IV for 5-7 days.
Inpatient patient in General Ward >65 years or with at least 1 risk factor:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1g/day IV for 7 days.
Inpatient patient in Intensive Care Unit:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1-2g/day IV for 7 days.
Special Considerations for Inpatients:
Scheme for risk factors for Pseudomonas aeruginosa*: * Piperacillin/Tazobactam 4.5g/6h IV or Cefepime 2g/8h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for risk factors for Methicillin-Resistant Staphylococcus aureus**: * Add to conventional scheme: Vancomycin 15-20mg/kg/8-12h IV +/- Clindamycin 600mg/8h IV for 7-14 days.
Aspiration Pneumonia:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 5-7 days.
*Risk factors for Pseudomonas aeruginosa: Bronchiectasis, cystic fibrosis, prior treatment with corticosteroids or broad-spectrum antibiotics. Documented isolates in respiratory cultures of Pseudomonas aeruginosa.
**Risk factors for Methicillin-Resistant Staphylococcus aureus: Previously healthy young patients with severe, necrotizing, and rapidly progressive pneumonia, cavitary infiltrates, hemoptysis, prior influenza, intravenous drug users, rash, leukopenia, recent or concomitant skin and soft tissue infections.
The routine use of corticosteroids in pneumonia is not recommended.
CONSIDERATIONS ON ANTIMICROBIALS IN VIRAL AND ATYPICAL PNEUMONIAS:
In the case of a concomitant antigen test or PCR for Influenza A/B or SARS-CoV2, the following treatment recommendations are made:
Influenza Virus A/B:
First choice: * Oseltamivir 75mg every 12 hours orally for 5 days. Other considerations: * In cases of Respiratory Failure in ARM or Obesity: Oseltamivir 150mg every 12 hours orally for 5 days. * Concomitant antimicrobial treatment is recommended as there is documented frequent association of Influenza Virus and Streptococcus pneumoniae.
COVID-19: * First choice is conventional treatment with dexamethasone 8 mg IV for 10 days in the event of respiratory failure. * Routine antimicrobial treatment is not recommended for COVID-19; therefore, upon a positive SARS-CoV2 test, it is recommended to discontinue antimicrobials.
Consider maintaining concomitant antimicrobial treatment only in suspected bacterial infection due to severe presentation: * Focal alveolar consolidation +/- air bronchogram in imaging studies plus 1 of the following: sepsis, risk factors, and/or immunosuppression.
Atypical Pneumonias with Seroconversion for Chlamydia or Mycoplasma:
First choice: * Clarithromycin 500mg every 12 hours IV/orally for 14 days. * Azithromycin 500-1000mg/day IV/orally for 14 days. * Doxycycline 100mg every 12 hours IV/orally for 14 days.
CONSIDERATIONS ON PENICILLIN AND OTHER BETA-LACTAM ALLERGIES:
Patients who report penicillin allergy are often misclassified. It is documented that more than 95% of patients who report penicillin allergy can receive beta-lactams without any complications. Additionally, penicillin hypersensitivity diminishes over the years.
Allergy to one beta-lactam does not imply the impossibility of using the entire spectrum of beta-lactams, as there are only a few cases of cross-hypersensitivity.
Therefore, we recommend the safe use of beta-lactams except in cases of a reported or documented history of severe allergy to penicillin (anaphylaxis).
In doubtful cases or confirmed allergy events during hospitalization, a consultation with an Allergy Specialist is available to evaluate the case.
FOLLOW-UP IN OUTPATIENT TREATMENT MODALITY
Patients undergoing pneumonia treatment in an outpatient setting can continue their treatment at home, considering advising them to seek further consultation in case of alarm signs (fever that does not subside after 48 to 72 hours, dyspnea, hemoptysis, chest pain, etc.). Nevertheless, it is good practice to consider a follow-up consultation in the emergency department or clinic after 48 to 72 hours of starting antibiotic therapy.
It is not routinely recommended to repeat a chest X-ray or CT scan to evaluate the evolution of pneumonia under outpatient treatment. Only in the case of suspected complications or unfavorable evolution. A follow-up at the end of treatment with the primary care physician is suggested.
FOLLOW-UP IN INPATIENT TREATMENT MODALITY
For hospitalized patients, we should consider transitioning from parenteral medication to oral when the following conditions are met
- Completion of 48 hours of parenteral treatment.
- Presence of a 24-hour afebrile period, with hemodynamic stability and significant clinical improvement.
- Availability of the oral route.
It is not routinely recommended to repeat a chest X-ray or CT scan to evaluate the evolution of pneumonia under outpatient or inpatient treatment. Only in the case of suspected complications or unfavorable evolution.
PREVENTION
The prevention of pneumonia is based on timely immunization with pneumococcal vaccines, influenza vaccination, and COVID-19 vaccination according to the immunization recommendations and current schedule from the Ministry of Health.
ICD-11 CODING
- CA40 - Pneumonia.
- CA40.0 - Bacterial Pneumonia.
- CA40.1 - Viral Bronchopneumonia.
- CA40.2 - Fungal Pneumonia.
- CA40.Z - Pneumonia, organism unspecified.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ 3cfa816b:545fa2d9
2024-09-24 10:27:16
@ 3cfa816b:545fa2d9
2024-09-24 10:27:16Il progetto online Bisanz.io nasce dalla convinzione che Bitcoin sia un incredibile strumento di promozione e giustizia sociale, e nessuno che si dica riformista o progressista dovrebbe ignorare questo fatto. Un sito web in cui progressisti, riformisti, ambientalisti ed attivisti per la democrazia possano informarsi e discutere su com Bitcoin possa ridurre le disparità e le storture dell’attuale sistema finanziario.
L’urgenza di attivarsi affinché questa visione si diffonda nasce dal rischio concreto che si ripeta in Europa la stessa dinamica osservata negli Stati Uniti, dove questo tema fondamentale è stato lasciato nelle mani delle destre, da quelle liberali alle neo-con. La posizione del Partito Democratico USA su Bitcoin è infatti oggi ampiamente ostile, in maniera pregiudiziale e dettata principalmente da ragioni di posizionamento strategico.
In Italia Bitcoin è, al momento, semplicemente ignorato dalla politica. In Europa la situazione non è molto diversa da quella italiana con rare eccezioni.
Questa apatia della politica italiana ed europea nei confronti di Bitcoin può essere vinta mostrando quanto grande sia il potenziale di progresso sociale, equità e pace derivante dall'adozione di Bitcoin. Una opportunità che i progressisti europei dovrebbero cogliere, guidando l’analisi e il dibattito su questi temi.
Non si tratta naturalmente di inserire la parola “blockchain” nei contesti più assurdi (vedi i pomodori e le arance di Di Maio), ma di elaborare proposte unitarie di politica monetaria che includano una tecnologia (Bitcoin) rodata, democratica, globale, solidale.
Nel gruppo di amici che ha dato vita a Bisanz.io, c’è chi segue e studia con passione il tema Bitcoin dal lontano 2010, e chi invece ci si è avvicinato solo di recente. Cosa ci accomuna è la consapevolezza che questa innovazione ha il potenziale per risolvere le tante storture dell’attuale sistema finanziario. Una tecnologia che proteggendo i soggetti più deboli, può contribuire a ridurre le disparità, proteggere i risparmi, e stimolare gli investimenti.
Purtroppo, Bitcoin è ancora visto da tanti come uno strumento per criminali e speculatori, una percezione in gran parte giustificata da vicende legate non a Bitcoin, ma alle cosiddette criptovalute, e al più recente fenomeno dei token e degli NFT. Queste “innovazioni” nulla hanno a che spartire con la tecnologia e i valori di Bitcoin (decentralizzazione, trasparenza, open access, …) e le loro aberrazioni hanno alimentato la narrazione di cui sopra.
Più recentemente si è aggiunta la critica relativa all'impatto ambientale di Bitcoin, critica ancor più pretestuosa e in malafede. Chiunque dedichi un minimo di studio all'argomento potrà constatare come essa risulti infondata e che il mining di Bitcoin è in realtà un prezioso alleato nella transizione alle energie rinnovabili. Queste ombre e la copertura mediatica negativa non hanno impedito all'ecosistema di Bitcoin di svilupparsi e crescere con costanza dal 2009 a oggi. Mentre centinaia di monete digitali alternative, nascevano e morivano guidate solo da logiche di profitto (o peggio), Bitcoin ha sempre tenuto la barra dritta sui valori fondanti, ampliato la base di utenti e le tipologie di utilizzo (esempio: pagamenti istantanei con Lightning Network).
La missione di Bisanzio è semplice: portare il nostro contributo affinché in Italia ed Europa maturino proposte per consentire a Bitcoin di esprimere tutto il suo potenziale democratico e di giustizia.
-
 @ 610b2232:af6c59fd
2024-09-24 09:06:13
@ 610b2232:af6c59fd
2024-09-24 09:06:13Hello Nostr Enthusiast!
Welcome to your personalized Nostr newsletter, where we dive into the latest posts and discussions that lit up the community. Let's get started!
---
Unique Reaction Emojis on Nostr
Original Post by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka:
"Anybody ever think about how unique reaction emojis on #Nostr could be potentially analyzed as a form of metadata to identify patterns of interest and behavior? ...yeah, me neither. Gn #Nostr 💜"
nostr:nevent1s6s2h32pk2eqr3rm3643jsjqmjk3e6qgfn56vqkerzsgc6es396qgchryv
Replies:
- npub14ktnsqc2hpxqflawce9t4htvc6pvkdgp6xf6tlcujjuswuy324vqfhukks: "GN ✨🫂✨"
- npub1l6scds4yv7xmcsmhqnhdy9sggm520q09lvts2m5mkvecgr2mmmeqsuj5rc: Preference for a minimal client experience, engaging primarily as a "lurker."
It’s a nice mix of lightheartedness and introspection in the replies. A thought-provoking yet casual topic to end the night!
---
The Idea of a Nostr Reader Client
Original Post by npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka:
"A #Nostr 'reader' client would be useful to just catch up in the mornings or whenever as well. I like it."
nevent: nevent19f7urtrglqxl04n9xxj6gt2vfht44etwgymmdsja6yk47p5qsqfqnse0gc
Replies:
- npub1f6ugxyxkknket3kkdgu4k0fu74vmshawermkj8d06sz6jts9t4kslazcka: Reaffirms the idea.
- npub1nqx3lfjxpkqhck3kgrdtkhncvffe94l7qrep6ftw49nphnmw9szqvh3quf: Suggests logging in with your npub to use it as a reader-only platform.
The concept of a reader client strikes a chord, making it more practical to stay updated without the overwhelm!
---
### Exploring Tim Berners-Lee's Solid Project
Original Post by npub1melv683fw6n2mvhl5h6dhqd8mqfv3wmxnz4qph83ua4dk4006ezsrt5c24:
"If you want to give Tim Berners-Lee's Solid project a try, here's a list of servers that run it. It's still quite buggy, but I am hoping to help improve that. Also, add login with Nostr identity, which will allow long-lived personal storage for Nostr users, micro apps, and much more. Hopefully we can fix the web together!"
nevent: nevent1uceamf3v2yvht6v6lrpuelszlx3u608q7pc5jmc7vkufwz4299es76m460
Reply by npub1h0uj825jgcr9lzxyp37ehasuenq070707pj63je07n8mkcsg3u0qnsrwx8:
Affirms the significance of using Nostr IDs for web logins and appreciates the efforts.
The excitement around Solid and its potential integration with Nostr shines through, promising a brighter, decentralized web!
---
### French Disagreements and Cheese
Original Post by npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q:
"The French disagree 😉"
nevent: nevent1tutnpxrcar0g7skp95kldk02xcpqscjevns8wmkyc4xw4z6ul8dqrnscfr
Reply by npub1crsvgfepxnvjm2r9zegvzr9xz2m3pfns6hsyxjy0yls88g0k8gtqhc9r37:
"Which is why I will always have a reason to buy cheese! 🧀"
A delightful exchange highlighting French culture’s beloved cheese, adding some fun to our day.
---
Vibrant Art Post by npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k
Original Post:
"#nostr and PV 🧡💜🤙"
nevent: nevent1r822ejskxwya5dnv2mg7vyngp695fva40kma859stjruxtzf8jaqxwn4nx
No direct replies yet, but the visually captivating post under several art-related hashtags showcases the creativity within the Nostr community.
---
Naming Conventions for QR Codes
Original Post by npub1h0uj825jgcr9lzxyp37ehasuenq070707pj63je07n8mkcsg3u0qnsrwx8:
"We aren’t sure how to name the QR code, so we still call it a QR code. This name can be misleading, as it might be mistaken for Npub."
nevent: nevent1x53mrmurn3y0s8p96ragsredyjp6g8egxaapcr7q5lkkgc0zfj6qgk0nwf
Discussing the need for clear and distinct naming to avoid confusion. Terminology is crucial in ensuring smooth user experiences.
---
Dumb Relay Concept
Original Post by npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk:
"The concept of 'dumb relay,' as it was initially coined, in my opinion, should be framed in terms of minimum and necessary functionality."
nevent: nevent1qqqzcweg5fvugf2nnmc3r7chw4lwjzy0v3hz9zlxl87jg9y0244qnnpvw4
Discusses ensuring the core functionality of relays while promoting synergistic cooperation with clients. Good insights on the relay-client ecosystem!
---
Highlight and Quote Feature
Original Post by npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy:
"Highlight and quote show up if you select some text"
nevent: nevent1vxqnssf8se2arrrngcm486qlykd2x9rpa7rqz3ctx98te2afc46qlcrxgk
A neat trick for enhancing user interaction. Try it out!
---
A Friendly "Good Morning"
Original Post by npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k:
"Morning visitor 🐿️ Have a wonderful day #nostriches"
nevent: nevent1m5jytjhwwt8wv6sv35h332hwfa4m9mle5wpnrvuggy9w452nmkeqef9n3t
A charming post featuring a squirrel making everyone's day a bit brighter!
---
Android App Confirmation
Original Post by npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49:
"What do you mean? we have an android app LOL"
nevent: nevent19kkq6hw5j6pl9w2tjkuehhfzhes5k3tlw9u0pzagqhw6flga5p4qa7d7pc
Confirming the existence of an Android app with a touch of humor.
---
Simple Banter
Original Post by npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49:
"No you!"
nevent: nevent1ltywx73aycrwwcsmpghrl33779uu62mh4vdz0wwue0wwr7uzr4dq0e70kw
A playful retort that adds some fun to the conversation.
---
Importance of Nostr IDs for Web Login
Original Post by npub1h0uj825jgcr9lzxyp37ehasuenq070707pj63je07n8mkcsg3u0qnsrwx8:
"Using a Nostr ID to log in to the web is very important and has been underestimated. Thank you for your contribution."
nevent: nevent1cvp9k8404al85ke3x7wt0c7qdslkfqalgjz4r4df2vkgdkw4p8qq67d3nn
Reinforces the vital role of Nostr IDs in web logins.
---
Morning Greetings
Original Post by npub1q33jywkl8r0e5g48lvrenxnr3lw59kzrw4e7p0cecslqzwc56eesjymqu0:
"Morning Nela!"
nevent: nevent170g8m29hhvy497trd8caxf4gtre3vxqnx2vjna6ha3end6lphr5qg9muft
A simple yet warm greeting to start the day.
---
Policy Update on Telegram
Original Post by npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3:
"Telegram Changes Policy to Share Phone Numbers & IP Addresses in 'Valid Requests'"
nevent: nevent1392kxy2upl89my89nu8nz820h2234kuuqklregkwtr4a98stet5qw5te4x
Telegram will now share phone numbers and IP addresses under certain conditions. Read the full details on [NoBS Bitcoin](https://www.nobsbitcoin.com/telegram-changes-policy-to-share-phone-numbers-ip-addresses-in-valid-requests/).
---
Settlement in Hostile Takeover Saga
Original Post by npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3:
"Bitfarms and Riot Platforms Reach Settlement in Hostile Takeover Saga"
nevent: nevent1x09l4k6n0phlyuvcunnqk6ny9ns30x97xvktur7surc02tssrrzq7p30xp
Bitfarms and Riot Platforms settle their takeover dispute. Check out the full article on [NoBS Bitcoin](https://www.nobsbitcoin.com/bitfarms-and-riot-platforms-reach-settlement-in-hostile-takeover-saga/).
---
Attraction vs. Repulsion
Original Post by npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q:
"Attraction > Repulsion Appears as one of the deepest habits of the universe."
nevent: nevent1y0wjctntjyyg2fws4mhwuqswyhywfa93r094y3kc36ushsjukamsw3kl9u
A philosophical note reflecting on how attraction might be a fundamental force of the universe.
---
That wraps up our Nostr discussion roundup! Keep those conversations flowing and enjoy the vibrant community. Until next time!
Cheers,
Your Friendly Nostr Newsletter Assistant
-
 @ 62b7629b:c012720e
2024-09-24 07:41:03
@ 62b7629b:c012720e
2024-09-24 07:41:03 -
 @ a012dc82:6458a70d
2024-09-24 06:42:32
@ a012dc82:6458a70d
2024-09-24 06:42:32Table Of Content
-
A Leap Towards Financial Inclusion
-
Boosting E-Commerce Growth
-
Reducing Transaction Costs
-
Enhancing Security and Privacy
-
Challenges and Concerns
-
Conclusion
-
FAQ
Chile, the economic powerhouse of Latin America, has recently expanded its e-commerce landscape by allowing Bitcoin trading on its largest e-commerce platform. This bold move signifies a significant milestone for the Latin American e-commerce industry, offering new opportunities for both merchants and consumers. This article will explore the benefits and implications of incorporating Bitcoin trading into the Chilean e-commerce market, and discuss how this development is expected to revolutionize the region's digital economy.
A Leap Towards Financial Inclusion
The integration of Bitcoin trading on Chile's leading e-commerce platform aims to promote financial inclusion by giving more people access to the digital economy. By accepting Bitcoin as a payment option, merchants can cater to customers who may not have access to traditional banking services, broadening their reach and fostering economic growth. This inclusive approach helps bridge the gap between the banked and unbanked populations, reducing income inequality and providing a more level playing field for all.
Boosting E-Commerce Growth
The addition of Bitcoin trading on the platform is expected to boost e-commerce growth in the region. With the growing popularity of cryptocurrencies, more consumers are likely to be attracted to online shopping, benefiting both local and international merchants. Additionally, the ease of cross-border transactions with cryptocurrencies can potentially increase international trade, further accelerating e-commerce growth in Latin America.
Reducing Transaction Costs
One of the major advantages of Bitcoin is its low transaction costs compared to traditional payment methods. By incorporating Bitcoin trading into the platform, merchants can save on transaction fees, making their products and services more competitively priced. This benefit will likely lead to higher sales volumes, increased revenue, and improved profitability for businesses operating in the e-commerce space.
Enhancing Security and Privacy
Bitcoin's decentralized nature and secure encryption make it an appealing payment method for consumers who value their privacy and security. By adopting Bitcoin, Chile's largest e-commerce platform is offering users an additional layer of protection against fraud and identity theft. This move can potentially build trust among users and increase the platform's credibility in the eyes of consumers.
Challenges and Concerns
Despite the numerous benefits of integrating Bitcoin trading into Chile's e-commerce platform, there are several challenges and concerns that need to be addressed. These include regulatory issues, price volatility, and the environmental impact of cryptocurrency mining. It is crucial for governments, regulators, and industry stakeholders to work together to create a supportive framework that addresses these concerns while fostering innovation and growth.
Conclusion
Chile's decision to welcome Bitcoin trading on its largest e-commerce platform demonstrates the country's commitment to fostering innovation and expanding financial inclusion. As the Latin American e-commerce market continues to grow, embracing Bitcoin and other cryptocurrencies can provide a competitive advantage for businesses and consumers alike. By addressing the challenges and concerns associated with this new form of payment, Chile has the potential to become a leader in the global digital economy.
FAQ
Why is Bitcoin trading being introduced to the platform? Bitcoin trading is being introduced to promote financial inclusion, boost e-commerce growth, reduce transaction costs, and enhance security and privacy.
How does Bitcoin trading benefit consumers and merchants? Consumers benefit from increased privacy and security, while merchants can save on transaction fees, cater to a wider audience, and enjoy higher sales volumes.
How can Chile address these challenges and concerns? Governments, regulators, and industry stakeholders must work together to create a supportive framework that addresses concerns while fostering innovation and growth.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 502ab02a:a2860397
2024-09-24 06:20:57
@ 502ab02a:a2860397
2024-09-24 06:20:57 ร่างกฎหมาย "ฮิปโปบิลล์" (Hippo Bill) ปี 1910 เป็นหนึ่งในเรื่องราวทางการเมืองที่แปลกและน่าสนใจที่สุดในประวัติศาสตร์ของสหรัฐอเมริกา เรื่องนี้เริ่มต้นจากการที่ประเทศเผชิญกับปัญหาขาดแคลนเนื้อสัตว์และปัญหาผักตบชวาที่กำลังล้นแหล่งน้ำในรัฐลุยเซียนา ซึ่งสร้างความเสียหายให้กับแหล่งน้ำและทรัพยากรประมงในท้องถิ่น เพื่อแก้ไขปัญหานี้ สมาชิกสภาคองเกรส โรเบิร์ต โบรซซาร์ด (Robert Broussard) จึงเสนอร่างกฎหมายที่มีชื่อว่า "American Hippo Bill" โดยมีเป้าหมายในการนำเข้าฮิปโปโปเตมัสจากแอฟริกาเพื่อช่วยกำจัดปัญหาผักตบชวารุกราน และในขณะเดียวกันยังเสนอแนวคิดว่าฮิปโปจะสามารถเป็นแหล่งเนื้อสัตว์ใหม่ให้กับชาวอเมริกันได้
ร่างกฎหมาย "ฮิปโปบิลล์" (Hippo Bill) ปี 1910 เป็นหนึ่งในเรื่องราวทางการเมืองที่แปลกและน่าสนใจที่สุดในประวัติศาสตร์ของสหรัฐอเมริกา เรื่องนี้เริ่มต้นจากการที่ประเทศเผชิญกับปัญหาขาดแคลนเนื้อสัตว์และปัญหาผักตบชวาที่กำลังล้นแหล่งน้ำในรัฐลุยเซียนา ซึ่งสร้างความเสียหายให้กับแหล่งน้ำและทรัพยากรประมงในท้องถิ่น เพื่อแก้ไขปัญหานี้ สมาชิกสภาคองเกรส โรเบิร์ต โบรซซาร์ด (Robert Broussard) จึงเสนอร่างกฎหมายที่มีชื่อว่า "American Hippo Bill" โดยมีเป้าหมายในการนำเข้าฮิปโปโปเตมัสจากแอฟริกาเพื่อช่วยกำจัดปัญหาผักตบชวารุกราน และในขณะเดียวกันยังเสนอแนวคิดว่าฮิปโปจะสามารถเป็นแหล่งเนื้อสัตว์ใหม่ให้กับชาวอเมริกันได้ที่มาของปัญหาการขาดแคลนเนื้อสัตว์
ในช่วงต้นศตวรรษที่ 20 (ราวๆ 1900s ฮาๆๆ ปีนี้ช่วงนี้อีกแล้ว แฟนๆ #บอกเล่า90บวก1 น่าจะคุ้นเคยดี) มีการอพยพเข้ามามาก สหรัฐอเมริกาจึงประสบกับปัญหาขาดแคลนอาหารอย่างหนัก โดยเฉพาะเนื้อสัตว์ที่เป็นหนึ่งในอาหารหลักของชาวอเมริกัน แม้อุตสาหกรรมเนื้อสัตว์ขยายตัวอย่างมาก แต่ก็ไม่สามารถตามทันได้เนื่องจากการล่าและการทำลายถิ่นที่อยู่อาศัยของสัตว์ในทวีปอเมริกาเหนือทำให้สัตว์บางชนิดเกือบจะสูญพันธุ์ อาทิ ไบซัน และกวาง ที่เป็นแหล่งเนื้อหลัก ส่งผลให้เกิดการขาดแคลนเนื้อสัตว์ จนทำให้รัฐบาลต้องพิจารณาหาวิธีการในการเพิ่มแหล่งเนื้อสัตว์ใหม่อย่างจริงจัง
ปัญหาผักตบชวารุกราน
ในช่วงเวลานั้น รัฐลุยเซียนายังประสบปัญหาพืชน้ำชนิดหนึ่งคือ "วอเตอร์ไฮยาซินท์ (Water Hyacinth) " หรือผักตบชวา ซึ่งนำเข้ามาในอเมริกาโดยคณะผู้แทนจากญี่ปุ่นที่มาเยือนนิวออร์ลีนส์ในปี 1884 แล้วมันดันเติบโตอย่างรวดเร็วมากกกกอย่างที่เรารู้ฤทธิ์มันดี และทำให้การทำประมงเป็นไปอย่างยากลำบาก เพราะมันทำลายแหล่งที่อยู่อาศัยของปลาและสัตว์น้ำอื่น ๆจนตายเป็นเบือ ผักตบชวาเจริญเติบโตอย่างรวดเร็วและครอบคลุมแม่น้ำลำคลองเกือบทั้งหมด ทำให้การคมนาคมทางน้ำและการใช้ประโยชน์จากแหล่งน้ำเป็นไปอย่างยากลำบากมาก ** สำหรับประเทศไทย เท่าที่หาข้อมูลมาได้ ในปี พ.ศ. 2444 (ค.ศ. 1901) เมื่อครั้งที่พระบาทสมเด็จพระจุลจอมเกล้าเจ้าอยู่หัวเสด็จประพาสประเทศอินโดนีเซีย ไม่มีบันทึกว่าพระองค์ได้นำผักตบชวากลับมาด้วย อย่างไรก็ตาม ผักตบชวานั้นถูกนำเข้ามาในประเทศไทยในช่วงหลังจากนั้น โดยในปี พ.ศ. 2455 (ค.ศ. 1912) เป็นช่วงที่พระยาศรีวิสารวาจานำพืชชนิดนี้เข้ามาเพื่อใช้ในงานประดับและฟอกน้ำตามคูคลองในประเทศไทย แต่ในที่สุดกลับกลายเป็นพืชที่แพร่กระจายและก่อปัญหาในแหล่งน้ำของประเทศครับ **
เกิดแนวคิดฮิปโปจ๋าเป็นทางแก้ปัญหา

ด้วยปัญหาทั้งสองนี้ โรเบิร์ต โบรซซาร์ด เห็นว่าฮิปโปโปเตมัสอาจเป็นคำตอบของทั้งปัญหาขาดแคลนเนื้อสัตว์และปัญหาผักตบชวารุกราน เนื่องจากฮิปโปเป็นสัตว์ที่กินพืชน้ำในแหล่งน้ำต่าง ๆ รวมถึงผักตบชวาด้วยแถมกินจุมากๆ นอกจากนี้ โบรซซาร์ดเชื่อว่าฮิปโปสามารถเป็นสัตว์เลี้ยงเพื่อเอาเนื้อให้แก่ชาวอเมริกันบริโภคได้

แนวคิดนี้ได้รับการสนับสนุนจากบุคคลสำคัญอย่าง เฟรเดอริก รัสเซล เบิร์นแฮม (Frederick Russell Burnham) บุคคลสำคัญอย่างน่าตะลึงและถูกลืมเลือนไปจากประวัติศาสตร์โดยสิ้นเชิง เป็นสุดยอดลูกเสือและสปาย เดินทางไปแอฟริกาเพื่อต่อสู้ให้กับนักล่าอาณานิคมชาวอังกฤษ เพราะเช่นเดียวกับผู้คนจำนวนมากในสมัยนั้น เขาคิดว่านี่เป็นภารกิจอันสูงส่งที่จะนำ "อารยธรรม" มาสู่แอฟริกา ครั้งหนึ่งเขาเคยได้รับการขนานนามว่าเป็น most complete human being who ever lived อีกด้วย อ่อ นอกจากนี้เขายังเป็นนักผจญภัยต้นแบบของการเขียนเรื่อง อินเดียน่าโจนส์ ด้วยครับ มีวลีอมตะที่นักข่าวคนนึงเขียนถึงเขาว่า “He has trained himself to endure the most appalling fatigues, hunger, thirst, and wounds; has subdued the brain to infinite patience, has learned to force every nerve in his body to absolute obedience, to still even the beating of his heart,”

และอีกคนนึงคือ ฟริตซ์ ดูเคน (Fritz Duquesne) เป็นชาวบัวร์ เขาเป็นคนมีไหวพริบมาก เขาใช้ชีวิตไปวันๆ โดยใช้ชื่อปลอม เขาเป็นนักต้มตุ๋นที่เก่งกาจและทะเยอทะยาน เขาต่อสู้กับอังกฤษในสงครามบัวร์ครั้งที่สอง เขาเป็นสายลับที่อิสระ เบิร์นแฮมเคยเรียกเขาว่า human epitome of sin and deception ที่ฮาคือ ในช่วงสงครามบัวร์ ชายสองคนนี้ได้รับมอบหมายให้ฆ่ากันเองครับ 5555 เอาเป็นว่าทั้งสองคนเคยใช้ชีวิตในแอฟริกาและเคยมีประสบการณ์การกินเนื้อฮิปโปมาแล้ว ในช่วงเวลาที่พวกเขาอาศัยอยู่ที่นั่น
สงครามบัวร์ (Boer War) หรือที่เรียกอย่างเป็นทางการว่า "สงครามแองโกล-บัวร์" (Anglo-Boer Wars) เป็นความขัดแย้งที่เกิดขึ้นระหว่างชาวบัวร์ (Boer) ซึ่งเป็นผู้ตั้งถิ่นฐานชาวดัตช์ในแอฟริกาใต้ กับจักรวรรดิอังกฤษ โดยเกิดขึ้นทั้งหมดสองครั้ง:
-
สงครามบัวร์ครั้งที่หนึ่ง (1880–1881):*** เกิดจากความไม่พอใจของชาวบัวร์ที่ต่อสู้เพื่ออิสรภาพจากการยึดครองของอังกฤษ ซึ่งควบคุมอาณานิคมแหลม (Cape Colony) ในแอฟริกาใต้ การต่อสู้นี้จบลงด้วยความพ่ายแพ้ของอังกฤษ และบัวร์ได้รับสิทธิในการปกครองตนเองในบางพื้นที่
-
สงครามบัวร์ครั้งที่สอง (1899–1902):*** เกิดจากการขยายตัวของจักรวรรดิอังกฤษในแอฟริกาใต้ โดยเฉพาะในภูมิภาคที่ชาวบัวร์ครอบครอง ซึ่งมีแหล่งทองคำและเพชรอยู่ สงครามครั้งนี้กินเวลานานกว่าและทารุณกว่าครั้งแรก โดยอังกฤษใช้ยุทธวิธีกักกันครอบครัวบัวร์ในค่ายกักกันและเผาทำลายฟาร์ม จนในที่สุดชาวบัวร์พ่ายแพ้และดินแดนของพวกเขาถูกผนวกเข้าเป็นส่วนหนึ่งของจักรวรรดิอังกฤษ
ผลจากสงครามครั้งที่สอง ทำให้เกิดการก่อตั้งสหภาพแอฟริกาใต้ในปี 1910 ซึ่งเป็นส่วนหนึ่งของจักรวรรดิอังกฤษ สงครามบัวร์ถือเป็นเหตุการณ์สำคัญในประวัติศาสตร์แอฟริกาใต้ที่ส่งผลต่อการเมืองและสังคมในภูมิภาคนี้ต่อมา
แน่นอนว่าต้องได้รับสนับสนุนจากบุคคลสำคัญ

แนวคิดในการนำเข้าฮิปโปของโบรซซาร์ดได้รับการสนับสนุนจากบุคคลสำคัญในสังคมสหรัฐอเมริกาในเวลานั้น เช่น อดีตประธานาธิบดี Theodore Roosevelt และ William Newton Irvin กระทรวงเกษตรของสหรัฐ - USDA (อีกแล้ว) รวมถึงการผนึกกำลังกับสื่อมวลชนยักษ์ใหญ่ในขณะนั้น อย่าง The Washington Post และ The New York Times ต่างก็ได้รายงานถึงร่างกฎหมายนี้ด้วยความสนใจ ถึงกับเรียกเนื้อฮิปโปว่า "lake cow bacon" (เบคอนจากวัวทะเลสาบ) เพื่อยกย่องถึงคุณภาพของเนื้อที่คาดว่าจะได้จากฮิปโปว่ารสเลิศ และไม่ต้องเปลืองพื้นที่ในการเลี้ยง เพราะมันอยู่ในบ่อน้ำได้สบายๆ พยายามนำเสนอชวนเชื่อให้ประชาชนเต็มที่
แผนการและข้อเสนอ
แผนการของโบรซซาร์ดคือการนำเข้าฮิปโปจากแอฟริกาและปล่อยลงในแม่น้ำลำคลองในภาคใต้ของสหรัฐอเมริกา โดยเฉพาะในรัฐลุยเซียนา ซึ่งฮิปโปจะช่วยกำจัดพืชน้ำอย่างผักตบชวาและยังให้เนื้อสัตว์เป็นแหล่งอาหารใหม่ให้กับประชาชนได้พร้อมๆกัน โบรซซาร์ดและผู้สนับสนุนของเขายืนยันว่าฮิปโปสามารถเลี้ยงในฟาร์มขนาดเล็กและสามารถให้เนื้อได้อย่างมีประสิทธิภาพกว่าวัว รสชาติและกลิ่นคล้ายคลึงกัน สามารถเป็นสัตว์เศรษฐกิจได้เนื่องจากฮิปโปเป็นสัตว์ที่กินพืชน้ำและสามารถเจริญเติบโตได้ในแหล่งน้ำของสหรัฐ เฟรเดอริก เบิร์นแฮม ยังเสนอแนะว่าฮิปโปสามารถช่วยในการแก้ปัญหาสิ่งแวดล้อมและการขาดแคลนอาหารของประเทศ เขาชี้ให้เห็นว่าในอดีต สหรัฐอเมริกาเคยนำเข้าสัตว์ต่างถิ่นอย่างเช่น อูฐจากแอฟริกาเพื่อใช้ในพื้นที่ทะเลทรายตะวันตก และยังเคยนำเข้ากวางเรนเดียร์จากรัสเซียมาเลี้ยงในอะแลสกาเพื่อใช้ทดแทนกวางคาริบูพื้นเมืองที่ลดจำนวนลง รวมถึงนกกระจอกเทศเพื่อหวังเรื่องการบริโภคเนื้อมาแล้ว
แต่ก็ยังมีข้อกังวล

แม้จะมีการสนับสนุนอย่างมาก แต่ก็มีข้อกังวลเกี่ยวกับความเป็นไปได้ในการเลี้ยงฮิปโปในฟาร์มขนาดเล็ก ความปลอดภัยของประชาชนเป็นเรื่องที่น่ากังวลอย่างยิ่ง เพราะฮิปโปเป็นหนึ่งในสัตว์ที่อันตรายที่สุดในโลก แม้จะเป็นสัตว์กินพืช แต่ฮิปโปก็มีรายงานว่าสามารถฆ่าคนได้หลายร้อยคนต่อปี และยังมีพฤติกรรมที่เป็นอันตรายเมื่อถูกรบกวนหรือถูกคุกคาม เอาจริงๆมันหวงที่มากแม้จะไม่ได้ทำอะไรมัน มันก็พร้อมจะเข้าโจมตีคน นอกจากนี้ ยังมีคำถามเกี่ยวกับอาหารของฮิปโปด้วย โดยผู้สนับสนุนร่างกฎหมายเชื่อว่าฮิปโปจะกินพืชน้ำอย่างผักตบชวา แต่ความจริงแล้ว ฮิปโปกินพืชน้ำอย่างผักตบชวาเพียงเล็กน้อย ในธรรมชาติพวกมันส่วนใหญ่จะกินหญ้าและพืชบกเป็นอาหารหลักต่างหาก นั่นหมายความว่าการนำเข้าฮิปโปมาเพื่อลดปริมาณผักตบชวาอาจไม่เกิดผลตามที่คาดหวัง
โดนให้คะแนนลบ ด้านผลกระทบทางเศรษฐกิจและสิ่งแวดล้อม
มีการโต้แย่งว่าการนำเข้าฮิปโปอาจส่งผลกระทบต่อระบบนิเวศและเศรษฐกิจในระยะยาว เนื่องจากการนำเข้าสัตว์ต่างถิ่นอาจก่อให้เกิดปัญหาการรุกรานทางชีวภาพ นอกจากนี้ การเลี้ยงฮิปโปยังต้องใช้พื้นที่จำนวนมากและอาจส่งผลกระทบต่อพื้นที่เกษตรกรรมอื่น ๆ ของประเทศ แม้ว่าร่างกฎหมาย "ฮิปโปบิลล์" จะไม่ผ่านการพิจารณาของสภาคองเกรส แต่เรื่องราวนี้ยังคงเป็นตัวอย่างที่น่าสนใจของวิธีการแก้ปัญหาแปลกใหม่กึ่งประหลาดที่สุดในประวัติศาสตร์ของสหรัฐอเมริกา
ปัดตก
ร่างกฎหมาย H.R. 23261 หรือ "American Hippo Bill" ที่เสนอในปี 1910 มีเป้าหมายเพื่อให้รัฐบาลจัดสรรงบประมาณประมาณ 1 ล้านดอลลาร์สหรัฐ (หรือเทียบเท่าในปัจจุบัน) เพื่อการนำฮิปโปจากแอฟริกามาใช้ในฟาร์มและการผลิตในสหรัฐฯ โดยมีวัตถุประสงค์ในการใช้ฮิปโปในการผลิตเนื้อและควบคุมจำนวนพืชน้ำในบางพื้นที่ แต่ในที่สุดกฎหมายนี้ไม่เคยผ่านการอนุมัติและกลายเป็นเรื่องที่น่าสนใจในประวัติศาสตร์สหรัฐฯ
แม้ว่าแนวคิดในการนำเข้าฮิปโปโปเตมัสจะดูแปลกในสายตาของคนปัจจุบัน แต่ในบริบทของเวลานั้น การคิดค้นวิธีการใหม่ ๆ เพื่อแก้ปัญหาสิ่งแวดล้อมและเศรษฐกิจเป็นเรื่องที่ได้รับการสนับสนุนอย่างมาก มันเลยเป็นสาเหตุของอะไรหลายๆอย่าง ตามที่เคยเล่าไว้ใน #บอกเล่า90บวก1 ครับ

สิ่งที่เกิดขึ้นในครั้งนี้คือจุดเริ่มต้นของเกษตรกรรมเชิงอุตสาหกรรม แทนที่จะนำสัตว์ชนิดใหม่เข้ามาเพื่อใช้ประโยชน์จากภูมิประเทศที่ดูเหมือนจะไม่อุดมสมบูรณ์ เราเพียงแค่ดัดแปลงภูมิประเทศเหล่านั้นให้เป็นทุ่งหญ้ามากขึ้น และเราก็บรรจุสัตว์ประเภทเดียวกันเข้าไปในดินแดนใหม่นั้นมากขึ้นเรื่อยๆ นั่นคือ feed lots and confinement operations ครับ เป็นแนวปฏิบัติในอุตสาหกรรมการเลี้ยงสัตว์เพื่อการผลิตเนื้อสัตว์ โดยเฉพาะในระบบการผลิตขนาดใหญ่ในตอนนั้น
-
Feedlots: คือสถานที่เลี้ยงสัตว์ เช่น วัว หรือหมู ในพื้นที่จำกัด โดยสัตว์จะถูกเลี้ยงในลานที่จัดไว้ให้พวกมันอยู่รวมกันเพื่อการขุนอาหารสูตรเข้มข้น โดยมักเป็นอาหารผสมที่มีส่วนผสมของธัญพืช โปรตีน และสารเสริมอื่น ๆ เป้าหมายของ feedlots คือการเพิ่มน้ำหนักตัวของสัตว์ให้เร็วขึ้นเพื่อให้พร้อมสำหรับการแปรรูปเป็นเนื้อสัตว์ ซึ่งช่วยให้การผลิตเนื้อสัตว์มีประสิทธิภาพมากขึ้น
-
Confinement operations: หมายถึงการเลี้ยงสัตว์ในสภาพที่ถูกจำกัดพื้นที่มาก สัตว์จะไม่สามารถเคลื่อนที่หรือหากินในพื้นที่ธรรมชาติได้เอง ซึ่งการเลี้ยงแบบนี้อาจมีอยู่ในหลายรูปแบบ เช่น การเลี้ยงหมูในโรงเรือน หรือการเลี้ยงไก่ในกรง สัตว์จะได้รับอาหาร น้ำ และการดูแลอย่างเข้มงวดในสภาพแวดล้อมที่ถูกควบคุมเพื่อเพิ่มผลผลิตอย่างต่อเนื่อง #PirateKeto #กูต้องรู้มั๊ย #หมูเด้ง #siamstr
-
-
 @ b5b91959:134a187a
2024-09-24 05:33:26
@ b5b91959:134a187a
2024-09-24 05:33:26Inleiding: lesgeven is bijzaak
\ Er was eens, in het fantastische stad Antwerpen, een systeem zo briljant dat het zelfs de Sovjet-Unie jaloers zou maken: het Antwerpse scholenloterijsysteem (meldt je aan).\ \ Het is een soort van Hunger Games, maar dan zonder het spektakel en de heldenverhalen, en met de toekomst van je kind als inzet. Mijn dochter, twaalf jaar oud, leergierig, nieuwsgierig en vol enthousiasme om aan haar middelbare schoolavontuur te beginnen, kwam terecht in het Gemeenschapsonderwijs (GO). Niet omdat wij dat zo wilden, maar omdat we simpelweg geen keuze hadden. Hierna volgde de ene na de andere poging om mijn kind te kleineren, demotiveren en vooral : er geen les aan te geven.\ Het gemeenschapsonderwijs heeft dan al geen al te beste naam, maar wat wij als gezin daar meemaken mag toch even aan het licht gebracht worden vonden we.
Het wonderlijke loterijsysteem
\ Voor de mensen die niet bekend zijn met het "systeem" van school toekenning in sommige leefzones België: de Antwerpse scholenloterij is een proces waarbij je als ouder denkt dat je enige inspraak hebt in de schoolkeuze van je kind.\ Je vult een lijstje in met 3 tot 6 scholen, en daar wordt dan een "voorkeur" gerespecteerd zogezegd. Je zegt tegen jezelf en je kind: "Oké, deze school zou goed zijn, daar willen we haar wel naartoe sturen." En dan wacht je. Vol spanning, natuurlijk. Maar zoals je misschien al geraden hebt, is die lijst puur symbolisch.\ De kans dat je kind effectief in een school terechtkomt die jij hebt gekozen. En dan nog, de lijst die je opstelt is eigenlijk kiezen tussen enkele versies van dezelfde soort leerplan-volgende vuilbak scholen.
Het resultaat? Mijn dochter, slim, nieuwsgierig en vooral een kind met een hart voor boeken en kennis, komt terecht in een school die, hoe zal ik het netjes zeggen, niet bepaald het epicentrum van intellectuele uitwisseling is. Niet dat ik per se een elite-instelling verwachtte, maar een klas waar minstens de helft van de leerlingen weet wat een boek is, leek me toch niet te veel gevraagd. Blijkbaar wel. De lat ligt niet alleen erg laag... de lat is gewoon verdwenen en vervangen door chips-eten, "oh my god" zeggen en mensen proberen te converteren naar het Islam-geloof (op 2 weken tijd al 2 keer prijs, want blijkbaar mag je in Vlaanderen je kind naar school sturen met de opdracht om "die meisjes moeten moslim sijn". Terwijl het kind in kwestie niet eens tot tien kan tellen zelf.\ Maar ach, maak er vooral geen opmerking over, dan ben je een complet-gek een extreem-rechts iemand of erger.
Da's eigen aan dit soort giftige school-systemen: je kan er maar beter je mond over houden, want anders eindig je zoals "Sandra" (fictieve naam), die effectief een opmerking maakte als kind en omsingeld werd door de stoere jongens op de speelplaats, werd gestampt, een hoertje genoemd en dan bespuwd en bespot omdat ze "haram" was.\ \ In mijn opinie, kan je dit geen scholen meer noemen, maar een gesubsidieerde facade vol ronselaars die verder aangemoedigd worden door extreem lakes proof-of-stake leerkrachten die eigenlijk meteen zouden moeten ontslaan worden.\ Of nog beter, gooi zulke facades gewoon meteen dicht en laat de kinderen die er "school lopen" hun plan trekken op straat of waar dan ook waar ze thuis horen.
\
Segregatie, maar dan "toevallig"?
\ Natuurlijk kan je in zo’n systeem veel van de nadelen toeschrijven aan pech.\ Maar als je wat verder kijkt, begint er iets op te vallen.\ \ Sommige scholen in Antwerpen hebben 0,2% leerlingen van Marokkaanse of Turkse afkomst.\ Ja, dat leest u goed: nul, komma iets procent.\ Andere scholen daarentegen zijn voor 95% bevolkt door kinderen van diverse afkomst.\ \ En dit alles in een zogenaamd "random" toewijzingssysteem? Dat klopt niet.\ Of ik begrijp het alvast niet.\ Wanneer je at random plaatsen toekent aan een school, kan het niet zijn dat in Antwerpen er mathematisch gezien niet minimaal 10% allochtone leerlingen aanwezig zijn. Een random toewijzing op die aantallen studenten kan nooit in 1 school een 0,2% resultaat geven.\ Het is net zoals in een slechte sitcom: je weet dat het nergens op slaat, maar je blijft kijken omdat je je afvraagt hoe absurd het nog kan worden.
Groenhout
\ Neem nu de school Groenhout. Ah, Groenhout, die oase van welvarende, gelegen in de schaduw van het museum voor Schone Kunsten op het trendy dure Zuid. Op een boogscheut van Hoboken of de Brederodestraat, waar er toch heel wat migranten wonen.\ De Groen-stemmende gezinnen zwaaien hier echter de plak.\ \ Als je ooit het gevoel hebt dat Antwerpen een smeltkroes van culturen is, hoef je alleen maar aan deze school te denken om je daarvan te genezen. Hoe ze het daar voor elkaar krijgen, vraag je je af?\ \ Het is een school die – puur toevallig natuurlijk – enkel kinderen aantrekt die passen in het profiel van "Anuna De Wever-types". Je kent het soort wel: biologische katoenen T-shirts, composteerbare drinkflessen en de nodige scheut activisme. Ik stel voor dat we een Pulitzer uitreiken aan de eerste journalist die uitvogelt hoe Groenhout erin slaagt om haar voorrecht zo moeiteloos te behouden in een zogenaamd willekeurig systeem. Want mathematisch kan het in ieder geval niet.
\
Het avontuur in het Gemeenschapsonderwijs
\ Ondertussen gaat mijn dochter, vol goede moed, naar haar nieuwe school. Het Gemeenschapsonderwijs, of GO, zoals we het noemen (want alles klinkt beter met een afkorting), heeft blijkbaar niet alleen een tekort aan diversiteit, maar ook aan leerkrachten. Op de eerste schooldag waren er al een paar leerkrachten "ziek" gemeld (ook hier zal het lot er voor gezorgd hebben dat het enkel de Arabisch klinkende namen waren die het begin van het schooljaar jammer genoeg niet haalden wegens ziekte).\ En nu, op 15 september, zijn ze nog steeds niet opgedoken. Misschien hadden ze wat last van post-vakantieblues? Acht weken vakantie is natuurlijk zwaar, en het vooruitzicht om terug voor een klas te staan waarin ze een compleet achterhaald leerplan moeten volgen, was waarschijnlijk iets te veel om te verdragen. Wie weet.
Mijn dochter is ondertussen nog steeds enthousiast. Gelukkig maar, want haar klasgenoten lijken vooral bezig te zijn met, wel ja, alles behalve leren. Sommige kinderen kennen het concept "boek" blijkbaar niet eens. Ze kijken naar een papieren bundel met pagina’s alsof het een relikwie uit een lang vervlogen tijdperk is. Het is bijna aandoenlijk, als het niet zo schrijnend was.
En dan is er nog de samenstelling van de klas. Want laten we eerlijk zijn: als je dochter ineens in een klas zit met vier op de vijf kinderen die letterlijk geen volzin kunnen vormen, dan weet je gewoon dat het geen mooie rit gaat worden.\ Deze kinderen hebben blijkbaar nog nooit van geschiedenis of economie gehoord, en het idee dat iemand hen ooit heeft uitgelegd hoe de wereld werkt, lijkt op een ver verleden gebaseerd te zijn (of een eigen invulling van "geld krijgen van vanalles".\ \ Je kan geen enkel gesprek voeren dat verder gaat dan TikTok-filmpjes en de nieuwste sneakers.\ Niet dat ik van iedereen verwacht dat ze een universitair diploma ambiëren, maar een basisniveau zou toch wel prettig zijn, niet? Ook de ouders van die kinderen zijn niet echt mensen waar je langer dan enkele minuten mee wilt praten, waarna ze met de nieuwste Iphone naar hun huizen verdwijnen, eender welk uur van de dag schijnen ze ook tijd te hebben om hun kinderen te komen oppikken van school. Hoe je als werkende mens om 15u20 aan een schoolpoort kan staan, is me een raadsel, maar ik zal ouderwets zijn, ... ik hoor bij de generatie die gaat werken om al die subsidie en uitkering te betalen uiteraard. "\ Want "ikke domme belg zijn." (Da's onze nieuwe rol in de communistische samenleving waar Europa naartoe gaat: betalen en hard werken, zwijgen, consumeren en vooral rap doodvallen om plaats te ruimen voor de meest parasitaire soort domme mensen die in groep leven en denken, en order-volgers worden van een ziek Fiat-gebaseerd failliet systeem).\ \ Mijn dochter wordt dan ook een "Tata" genoemd door het getesem dat er school loopt.\ Conflict opwekken is hier de boodschap. Om dan andere organisaties die op hun beurt ook op subsidies en "Linkie Winkies" drijven te gaan promoten.\ Gaat de klas slecht? (wat een garantie is met dit soort zielige aanpak) dan kan je naar "Elk Kind Telt". Een organisatie die subsidies krijgt om sociale assistenten types met je kind te laten "praten".\ Deze organisatie is officieel volgens hun eigen website bezig met het bestrijden van kinder armoede (een nobel doel uiteraard, of toch zo klinkt het).\ Echter, worden deze mensen als een "praatbarak" aangesmeerd aan de leerlingen, want wanneer je vaak te laat bent, of wanneer je een probleem hebt met de leerstof of klas situatie (100% van de kinderen dus) kan je bij hen terecht. Kassa kassa verzekerd qua subsidies dus. Er werd met geen woord over financiële problemen gepraat.\ \ Met andere woorden: men lokt de kinderen letterlijk naar het bureau van zulke organsatie onder het mom van "problemen aanpakken op school", waar dat naar boven toe wordt gebracht als "kind in financiële problemen". En daarna rinkelt de subsidie-kassa alweer.\ Men gaat een verdien-model opstarten op deze manier, waar eender welk kind in zulke vuilbak-achtige school, automatische een kosten post wordt en zogenaamd financiële problemen of armoede kent thuis.\ \ Mijn kind heeft voldoende financiële middelen, en omdat ze iets vroeg over de belachelijke kledij-voorschriften waar een bepaald deel van de scholieren zich wel (en een andere deel totaal niet) aan moet houden, werd ze meteen weggezet als iemand "zonder geld".\ De "elk kind telt" organisatie is dan ook in mijn visie niets anders dan een subsidie zwendel om een fake oplossing te bieden voor iets dat niet bestaat.\ Kinder-armoede bestaat in principe niet, zonder dat de ouders of een van de ouders/voogden in armoede zit. Je hebt dus altijd "armoede" in het algemeen nodig om ook zogenaamde kinder armoede te hebben.\ Wanneer de ouders niet eens het concept "boek" kennen, blijf je natuurlijk arm en afhankelijk. En geen over-gesubsidieerde mislukte pol&soc student met ongewassen haar gaat daar ooit iets aan veranderen.
\
Bad reputation
\ Natuurlijk is dat alles een recept voor slechte resultaten. Het lijkt bijna alsof het systeem ontworpen is om falen te garanderen en te kunnen met de open hand staan om al die problemen op te lossen met veel subsidie en geklaag.\ Intussen klaagt vooral de kleine groep Vlaamse kinderen in die school omdat ze gewoon eens echt les willen krijgen, ... zoals een school betaamt zou men beter LES GEVEN, in plaats van problemen op te pompen en onnodige aandacht te geven aan mensen die toch opgroeien voor galg en rad.\ \ De leerkrachten, die blijkbaar vanaf dag één doorhadden dat ze een groep niet te temmen jongeren voor zich hadden, beginnen meteen repressief te dreigen met straffen. Niet omdat ze geloven in discipline of structuur, maar gewoon omdat ze totaal de taak niet machtig zijn.\ Ze hebben simpelweg geen flauw idee hoe ze met zo'n klas moeten omgaan. Het is geen kwestie van onderwijzen meer, maar van overleven. \ De les wordt een oefening in brandjes blussen, waar elke opflakkering van interesse in leren snel wordt geblust door de constante chaos. Dit is het onderwijs anno 2024: een loterij die niet alleen beslist welke school je kind gaat bezoeken, maar ook welk niveau van frustratie je als ouder moet verdragen. Want o-wee wanneer je durft klagen of opmerkingen maken.\ Een onduidelijke lijst met benodigdheden bij voorbeeld, werd meteen op paraplu-gedrag onthaald, waarbij men nul verantwoordelijkheid neemt als school maar steevast de leerplannen, of andere leerkrachten voor de bus gooit. Als men al antwoord uiteraard. Gewoonlijk negeert men problemen, tot je bij de subsidie-bende van "Elk kind telt" moet gaan aankloppen.\ De directie is nooit te zien, de onder-directeur al helemaal niet, ... die zijn altijd in vergadering zogezegd.
\
Het domheidsprincipe van het systeem
\ Het meest frustrerende aan dit alles? Het gevoel dat dit systeem erop gericht is om creatief en zelfstandig denken te ontmoedigen, ja, ik durf zelfs zeggen: actief te fnuiken.\ \ Vanaf dag één wordt mijn dochter geconfronteerd met een systeem dat lijkt te zeggen: "Luister, hier is wat je moet weten. Denk niet te veel na, stel geen vragen, en doe vooral geen moeite om buiten de lijntjes te kleuren." Het leerplan? Droog, saai, en ontworpen om elk sprankje nieuwsgierigheid in de kiem te smoren. Er staat ook onnoemelijk veel overbodige "meningen" in die boeken. Meningen over allerlei groene leugens, politiek en historisch ongenuanceerde boodschappen en totale achterlijkheid. Een les over het oude Egypte wordt bij voorbeeld gelinkt aan de huidige situatie in die regio. Wat totaal overbodig is in een les geschiedenis.
En dat is nog niet eens het ergste. Zelf nadenken wordt niet alleen niet aangemoedigd, het wordt bestraft. Je zou verwachten dat scholen, als plekken van kennisoverdracht, kinderen juist zouden stimuleren om vragen te stellen, om de wereld kritisch te bekijken.\ \ Maar nee. In het GO! draait alles om het volgen van de meest domme regels, het memoriseren van nutteloze feiten en het voorbereiden op examens die niets te maken hebben met de realiteit van het leven en nog minder met echte kennis.\ Een datum van buiten leren, of enkele cijfers in de juiste volgorde zetten, en hup, men heeft weer een lesuur vol gekregen de leerkracht kan nadien tussen de middag naar de kapper terwijl ze met de heilige verbetersleutel een toets corrigeert die op zich al vol fouten stond.
Ik leer m'n dochter dus vooral aan om de "kennis van de oenen" te leren herkennen en nooit te erkennen. Maar haar "punten" er wel op te halen, terwijl ze de echte kennis tot zich neemt via boeken en documentaires of lessen die ik zelf samenstel.
\
De toekomst van mijn dochter, en die van vele anderen
\ Het Gemeenschapsonderwijs, en het Antwerpse onderwijssysteem in het bijzonder, lijkt ontworpen te zijn om middelmatigheid of onderpresteren te bevorderen.\ \ Voor mijn dochter betekent dit dat ze op eigen houtje moet proberen om de leemtes in haar onderwijs op te vullen. Gelukkig heeft ze nog steeds die onuitputtelijke honger naar kennis. Maar wat met de kinderen die dat niet hebben? Wat gebeurt er met de leerlingen die afhankelijk zijn van het systeem om hen te stimuleren en uit te dagen? Niets. Deze kinderen komen op de stoel terecht bij de "praat meneer" van een subsidie organisatie. Waar ze niets mee gaan vooruit komen.
Er is iets grondig mis. Niet alleen met de loterij, maar met het hele idee van wat onderwijs zou moeten zijn. Het zou een plek moeten zijn waar kinderen hun potentieel ontdekken, waar ze leren kritisch na te denken, en waar ze worden aangemoedigd om hun eigen weg te vinden. Maar in plaats daarvan lijkt het onderwijs in Antwerpen vast te zitten in een vicieuze cirkel van bureaucratie, vooroordelen en desinteresse.\ Ik zou het recht moeten hebben op goed onderwijs als kind. En dat recht heeft men afgenomen door verwatering, verloedering, desinteresse, desinformatie en invasie van "asocialen" en "de-les-spellers" uit een godsdienst.
\
Tijd voor verandering
\ Het is hoog tijd dat dit systeem herzien wordt. Dat journalisten eens de tijd nemen om uit te zoeken waarom scholen zoals Groenhout kunnen blijven bestaan in een zogenaamd eerlijk loterijsysteem en tegelijk alle "minder presterende kindjes" uit hun school kunnen houden. (hint: de toepassing van de "extra vragen" die vrijwillig worden ingevuld op de school inschrijf formulieren bij "meldt je aan" zijn daar een begin van trouwens... en kijk ook eens bij de organisatie Digipolis en hun eerlijke toepassing van dit school systeem).\ \ En dat beleidsmakers eens goed kijken naar wat er echt nodig is om het onderwijs in Antwerpen eerlijker, inclusiever en vooral uitdagender te maken. Want als het zo blijft, zullen we nog veel meer slimme, leergierige kinderen verliezen aan de middelmaat, en de bodemkruip-mentaliteit waar enkel consumeer-koeien en straatschorem uit voort zal komen.
En dat zou pas echt een verlies-post zijn.
Onze stad heeft meer nodig dan dit soort vuilbakscholen.\ Durf zulke scholen radicaal te sluiten, tot er een oplossing bedacht wordt. \ Stop deze fake, doe het voor de kinderen, ... want elk kind telt, moet meer zijn dan een subsidie-opwekkende slogen van de meest evil mensen die geen hol inzitten met de samenleving, maar gewoon hun uren staan te kloppen voor niemendal aan echte vooruitgang.\ Stop de fake, gooi ze buiten en start opnieuw.
In deze blog zal ik verdere items posten over het GemeenschapsOnderwijs, zodat diegenen die het willen weten, het ook weten en ook hun mond durven open doen.
15 september 2024
DioGenes
-
 @ 862fda7e:02a8268b
2024-09-24 01:14:40
@ 862fda7e:02a8268b
2024-09-24 01:14:40The media, government, and "elite" (who are only elite in this low vibration illusion we call "life") are afraid of people like me because I do not accept the reality they have forced us into. My manifesto is an attempt to wake you up from ideas you have been conditioned into believing because it benefits one class - the protected class known as the "elite".
The elite would like to have you believe that my message is something crafted from hatred and they would like to label me with mental issues. They would like you to think I am some crazy extremist who wants to advocate for the harm of others. They would like you to think that I am enciting violence.
This could not be further from the truth.
I am not and will never be an extremist, white supermicist, terrorist, radical, hateful human being. I do not believe in killing in order to convey a message or movement. I do not believe in division.
I only advocate that you become conscious of the reality around us. The reality is that this is a world controlled by the most evil, controlling, destructive freaks. These people work to make sure we are essentially slaves to a system that benefits those who created the system - the elites. Let me make this clear: I do NOT advocate for violence, destruction, death, killing, murder, hatred, division, or terrorism. The elite are threatened by people like me, because they know that we know their game. We know their plans are to destroy, to advocate for violence, to kill, murder, to encite hatred and division. This is all the elite do - they cannot fathom having people live in peace because it isn't beneficial if you want to control the world.
So while you may think it's impossible there is a group of a few evil people who control the world - look back at history. It has always been littered with the few evil who control the many. It would be stupid to think it would be different
-
 @ b39b8e83:0e391257
2024-09-23 23:54:40
@ b39b8e83:0e391257
2024-09-23 23:54:40https://image.nostr.build/54d4830e16f42daf7eeff67ddc8b19f811ea2e484ff330bcc72ad5c73a8ed447.jpg
It was a time of great and exalting excitement. The country was up in arms, the war was on, in every breast burned the holy fire of patriotism; the drums were beating, the bands playing, the toy pistols popping, the bunched firecrackers hissing and sputtering; on every hand and far down the receding and fading spreads of roofs and balconies a fluttering wilderness of flags flashed in the sun; daily the young volunteers marched down the wide avenue gay and fine in their new uniforms, the proud fathers and mothers and sisters and sweethearts cheering them with voices choked with happy emotion as they swung by; nightly the packed mass meetings listened, panting, to patriot oratory which stirred the deepest deeps of their hearts and which they interrupted at briefest intervals with cyclones of applause, the tears running down their cheeks the while; in the churches the pastors preached devotion to flag and country and invoked the God of Battles, beseeching His aid in our good cause in outpouring of fervid eloquence which moved every listener.
It was indeed a glad and gracious time, and the half dozen rash spirits that ventured to disapprove of the war and cast a doubt upon its righteousness straightway got such a stern and angry warning that for their personal safety's sake they quickly shrank out of sight and offended no more in that way.
Sunday morning came-next day the battalions would leave for the front; the church was filled; the volunteers were there, their faces alight with material dreams-visions of a stern advance, the gathering momentum, the rushing charge, the flashing sabers, the flight of the foe, the tumult, the enveloping smoke, the fierce pursuit, the surrender!-then home from the war, bronzed heros, welcomed, adored, submerged in golden seas of glory! With the volunteers sat their dear ones, proud, happy, and envied by the neighbors and friends who had no sons and brothers to send forth to the field of honor, there to win for the flag or, failing, die the noblest of noble deaths. The service proceeded; a war chapter from the Old Testament was read; the first prayer was said; it was followed by an organ burst that shook the building, and with one impulse the house rose, with glowing eyes and beating hearts, and poured out that tremendous invocation -- "God the all-terrible! Thou who ordainest, Thunder thy clarion and lightning thy sword!"
Then came the "long" prayer. None could remember the like of it for passionate pleading and moving and beautiful language. The burden of its supplication was that an ever--merciful and benignant Father of us all would watch over our noble young soldiers and aid, comfort, and encourage them in their patriotic work; bless them, shield them in His mighty hand, make them strong and confident, invincible in the bloody onset; help them to crush the foe, grant to them and to their flag and country imperishable honor and glory -
https://image.nostr.build/810192ce50f2dbb274b26c2753fe742d7fbc50fe7cd3307baf1bc2d74e5a2e14.jpg
An aged stranger entered and moved with slow and noiseless step up the main aisle, his eyes fixed upon the minister, his long body clothed in a robe that reached to his feet, his head bare, his white hair descending in a frothy cataract to his shoulders, his seamy face unnaturally pale, pale even to ghastliness. With all eyes following him and wondering, he made his silent way; without pausing, he ascended to the preacher's side and stood there, waiting. With shut lids the preacher, unconscious of his presence, continued his moving prayer, and at last finished it with the words, uttered in fervent appeal,"Bless our arms, grant us the victory, O Lord our God, Father and Protector of our land and flag!"
The stranger touched his arm, motioned him to step aside -- which the startled minister did -- and took his place. During some moments he surveyed the spellbound audience with solemn eyes in which burned an uncanny light; then in a deep voice he said
"I come from the Throne-bearing a message from Almighty God!" The words smote the house with a shock; if the stranger perceived it he gave no attention. "He has heard the prayer of His servant your shepherd and grant it if such shall be your desire after I, His messenger, shall have explained to you its import-that is to say, its full import. For it is like unto many of the prayers of men, in that it asks for more than he who utters it is aware of-except he pause and think. "God's servant and yours has prayed his prayer. Has he paused and taken thought? Is it one prayer? No, it is two- one uttered, the other not. Both have reached the ear of His Who hearth all supplications, the spoken and the unspoken. Ponder this-keep it in mind. If you beseech a blessing upon yourself, beware! lest without intent you invoke a curse upon a neighbor at the same time. If you pray for the blessing of rain upon your crop which needs it, by that act you are possibly praying for a curse upon some neighbor's crop which may not need rain and can be injured by it. "You have heard your servant's prayer-the uttered part of it. I am commissioned by God to put into words the other part of it-that part which the pastor, and also you in your hearts, fervently prayed silently. And ignorantly and unthinkingly? God grant that it was so! You heard these words: 'Grant us the victory, O Lord our God!' That is sufficient. The whole of the uttered prayer is compact into those pregnant words. Elaborations were not necessary. When you have prayed for victory you have prayed for many unmentioned results which follow victory-must follow it, cannot help but follow it. Upon the listening spirit of God the Father fell also the unspoken part of the prayer. He commandeth me to put it into words. Listen!
"O Lord our Father, our young patriots, idols of our hearts, go forth to battle-be Thou near them! With them, in spirit, we also go forth from the sweet peace of our beloved firesides to smite the foe. O Lord our God, help us to tear their soldiers to bloody shreds with our shells; help us to cover their smiling fields with the pale forms of their patriot dead; help us to drown the thunder of the guns with the shrieks of their wounded, writhing in pain; help us to lay waste their humble homes with a hurricane of fire; help us to wring the hearts of their unoffending widows with unavailing grief; help us to turn them out roofless with their little children to wander unfriended the wastes of their desolated land in rags and hunger and thirst, sports of the sun flames of summer and the icy winds of winter, broken in spirit, worn with travail, imploring Thee for the refuge of the grave and denied it-for our sakes who adore Thee, Lord, blast their hopes, blight their lives, protract their bitter pilgrimage, make heavy their steps, water their way with their tears, stain the white snow with the blood of their wounded feet! We ask it, in the spirit of love, of Him Who is the Source of Love, and Who is ever-faithful refuge and friend of all that are sore beset and seek His aid with humble and contrite hearts. Amen.
https://image.nostr.build/dd0a7be5db79d2f2885ffb7f229519c28bb3d6a4ed37df9e4ae55702ea8d17ad.jpg
(After a pause)
"Ye have prayed it; if ye still desire it, speak! The messenger of the Most High waits."
It was believed afterward that the man was a lunatic, because there was no sense in what he said.
-
 @ b39b8e83:0e391257
2024-09-23 23:51:33
@ b39b8e83:0e391257
2024-09-23 23:51:33My letter to my U.S. Representative asking them to cosponsor H.R. 9649 to restore UNRWA funding.
Dear Representative ABC,
I am writing to you as a concerned citizen and member of the Quaker faith community. My belief in peace, equality, and the inherent worth of every human being compels me to urge you to support the restoration of funding for the UN Relief and Works Agency (UNRWA) in Gaza.
As a Quaker, I believe we are called to speak truth to power and to work towards alleviating suffering wherever we find it. The ongoing humanitarian crisis in Gaza deeply troubles me, as I believe it should trouble all who value human life and dignity. The prospect of famine and disease outbreaks in Gaza is not just a political issue, but a moral one that speaks to our shared humanity.
UNRWA serves as the primary source of aid for millions of Palestinians facing dire circumstances. While I acknowledge the concerns that have been raised about the agency, I believe that UNRWA has demonstrated a commitment to addressing these issues through immediate action and reform. The decision by many of our allies to resume funding to UNRWA after careful consideration should encourage us to do the same.
The Quaker testimonies of simplicity, peace, integrity, community, equality, and stewardship (SPICES) guide us to seek peaceful solutions and to care for those in need. By supporting the UNRWA Funding Emergency Restoration Act (H.R. 9649), we can take a significant step towards fulfilling these values and preventing further suffering.
I urge you to cosponsor H.R. 9649 and to advocate for its passage. This action would align with our nation's humanitarian principles and our moral obligation to help those in desperate need, regardless of political boundaries.
Thank you for your consideration of this crucial matter. I look forward to hearing about your stance on this issue and any actions you plan to take.
Sincerely, TheFreeQuaker
-
 @ 472f440f:5669301e
2024-09-23 22:33:24
@ 472f440f:5669301e
2024-09-23 22:33:24While most of the world is focused on the lead up to the Presidential election here in the US and louder war drums being beat across the world, the number of bullish developments that are stacking up for bitcoin is increasing rapidly. These developments deserve the OG Marty's Bent smorgasbord treatments, so here are the things that have caught my attention over the last week in no particular order.
The First Ark Transactions on Bitcoin Mainnet
I had the pleasure of participating in a demo of Second's Ark protocol implementation. For those who are unaware, Ark is a new layer-two protocol solution for making off-chain bitcoin payments. Unlike the lightning network, Ark doesn't depend on liquidity channels to facilitate payments. Within the lightning network two counterparties share UTXOs within a channel to move sats back and forth, nodes connect to many different channels to create a network effect that increases the chance of payments getting routed successfully, and node operators manage their channel liquidity as channel imbalances emerge.
Ark is similar in the sense that it also leverages a shared UTXO model. However, instead of having one-to-one channels that come with liquidity management issues, Ark enables a large amount of individuals to share UTXOs, which are managed by an Ark Service Provider (ASP). The ASP is a central party within the protocol, but it is a central party that does not custody UTXOs. It only coordinates the transfer of sats between Ark "rounds". Users have the ability to unilaterally exit the second-layer protocol whenever they deem necessary by broadcasting a Virtual UTXO (vtxo) transaction.
This may seem daunting and complicated. All you need to know is that there is now an new way to make off-chain bitcoin payments that are fast and relatively cheap and it is possible today. As it stands today, Ark has some scaling limitations that can be solved if covenants get merged into the bitcoin protocol, which would significantly reduce the data requirements for signing this type of transaction.
It should also be noted that Ark isn't here to replace the lightning network. It can help serve different use cases and, at the same time, significantly improve the UX of the lightning network. Particularly channel management. The progression of the Ark protocol is a welcomed development. I look forward to following what's going on with Ark as the protocol matures.
The Kingdom of Bhutan is Stacking A LOT of Sats
We were made aware of the fact that the Kingdom of Bhutan, a small country in the Himalayas with a population less than 1,000,000 people, was mining bitcoin in early 2023 when their sovereign wealth fund was doxxed in the bankruptcy proceedings of BlockFi and Celsius. Don't look now, but Bhutan has been doxxed again, this time by the chain surveillance firm Arkham, which is reporting that the nation currently holds more than 13,000 bitcoin, which is nearly 1/3 of its GDP. Driven predominately by its mining operations, which have expanded significantly over the last two years in an attempt to monetize the country's excess hydroelectric power.
While we're not big fans of doxxing here at TFTC, we are fans of the game theory of bitcoin playing out in front of our eyes. And the Kingdom of Bhutan is a shining example of the game theory bitcoiners have been talking about for 15 years playing out perfectly.
Bitcoin is a very thorny topic for individuals at every layer of society. At the individual layer, people have to independently decide that bitcoin is a better money and they have to actively decide to store their wealth in it instead of other assets. For companies, the decision to use bitcoin as the preferred savings vehicle is even harder because most businesses have multiple stakeholders that need to align on a decision before making it. When you move up to the nation state level, the complexity of making the decision to add bitcoin as a strategic reserve asset gets even harder. Many more people and different branches of government need to agree and pass bills (in most cases) before bitcoin can ever make it into a nation's treasury asset mix.
It has long been said within bitcoin circles that individuals who have the ability to think independently, companies that have a lean corporate structure, and nation states with little to lose will be the first movers into bitcoin. And they will benefit massively over the long-run for being early.
If you're an individual reading this who is using bitcoin as their money of choice, you are one of these early movers. Microstrategy under Michael Saylor, who has the ability to make somewhat unilateral decisions due to the company's share structure, is an early move. And, Bhutan, a small nation in the Himalaya mountains with a sovereign wealth fund that seems to have the ability to take risk, is an early mover. With little to lose and greatness to gain, Bhutan is giving other small nation states the playbook for leap frogging the competition in the digital age. Stack a shit ton of bitcoin on the DL, hold on to it for a considerable amount of time, and wake up one day as an economic powerhouse.
The Fed Cuts Rates by 50 Basis Points
I'm sure all of you are well aware at this point. Last week the Federal Reserve made it's first rate cuts in over four years when it cut the fed funds target rate by 0.50% to 4.75-5.00%. With the economy reeling despite what the official government and mainstream narrative may try to make you believe, Jerome Powell and crew have decided it is time to ease up on their monetary policy.
Put another way, inflation is likely to come back with a vengeance as easy money begins to reenter the economy. To be clear, a lower fed funds rate doesn't technically necessitate that newly printed dollars enter the economy like they have over the last 15 years via operations like quantitative easing. However, one has to imagine that the Fed sees some sort of liquidity crisis on the horizon that requires them to begin cutting rates. And not only cutting, but cutting at a pace that was very low probability only a couple of months ago. The consensus in the middle of the Summer was that the Fed would begin lowering rates with a modest 25bps cut this month. They doubled that.
It's probably safe to assume that something is approaching a breaking point on the back end of the financial system. One only has to look at record high credit card debt, record low savings rates, the state of the job market for native born Americans, and the continued turn over of commercial real estate markets to see that not all is well in the American economy. Your Uncle Marty's spidey senses are signaling that a liquidity crunch is likely lurking around the corner. When it does rear its ugly head, you can expect quantitative easing to make a big come back.
When money printer goes brrr, bitcoin goes berserk.
It seems that the Treasury's move over the last 18-months of over-indexing on the front end of the curve during their auctions is already having an expansionary effect on M2 as it has officially entered expansion territory for the first time since 2022. Hold on to your butts, freaks.
Bitcoin's fundamentals are only getting stronger as time goes on. This is evidenced by continued improvement to the protocol stack via second layer protocols, continued adoption by reputable actors like the Kingdom of Bhutan, and the continued mismanagement of the fiat monetary system.
The price of bitcoin has been range bound since the Spring and it has lulled the market into a state of boredom. Enjoy the boring period while it lasts. All signs are pointing to a bitcoin bull run the likes of which the world hasn't seen before. There is a lot of tinder, it is extremely dry, and there are flame throwers on the horizon.
Final thought... Nothing makes me happier than meeting someone who gets value from this newsletter or the podcasts in the wild. Love you, freaks.
-
 @ e477586c:63d94e3f
2024-09-23 21:06:45
@ e477586c:63d94e3f
2024-09-23 21:06:45..and maybe an example?
This weekend, I had opportunity to submit estimated labor costs for myself to my church which needs a lot of work done. There's a whole long story about whether or not the congregation owns the building on which it's members paid-off the mortgage over a decade ago. The original request was for me to submit an estimated number of hours so that they could have a ballpark figure once the council decided on an hourly rate. I gave them not only that, but also thoughts, alternatives, and long-term "permanent" fixes done by specialists in their respective fields. If we are merely tenants of a building we paid-off and the Texas District remains the landlord, then the council should be better prepared to approach District and once again and say, "give us the deed, or come take care of your property."
If you've read my recent posts, you know I'm newly unemployed. My former employer happened to be the sister congregation to the Deaf Church. In the position of facilities manager, I answered to the board of trustees. They hold meetings (really boring meetings) once a month. I'd attend about twice a year which seemed satisfactory to the board at the time. One of the trustees was a constant volunteer on the property many weeks, putting in more hours than me. He was at the meetings, he'd fill the board in on what we'd been up to on campus, and they'd give him new requests. I'd see him the next morning and we'd GSD.
When asked for information from the board, I'd present it as I'm presenting this post, or the letter I plan on cut-and-pasting here in a moment. I tried to be thoughtful, thorough, detailed, clear, and not assuming they knew the back-story behind whatever project I was referring to. In short, Professional.
What I got back from the new chair was, "That's a nice little 'story-narrative' report you've submitted, but what do you actually do here anyway? People ask me and I don't know how to answer." "Why are you spending your time troubleshooting? Call a contractor." and then when he came in one day to see a contractor estimating an electrical project, "Who gave you the authority to do that?" For 6 months, to answer his question of what I did, I filled-out a time study in 15 minute increments, daily. In March of 2023 my supervolunteer left after one particularly unprofessional dialogue. He didn't have to take it anymore. That incident made the chair realize that he didn't have any idea how much institutional information had just walked out the door. I don't know for certain that he panicked at the time, but he should have. He certainly was easily "frustrated" (his word) after that. When he became frustrated, he'd verbally lash-out at myself and at multiple contractors. My words were "abusive," and "A-hole."
Over the ensuing 14 months my job went from one which I loved, but for which I was underpaid, to one which you wouldn't be able to pay me enough to take. While there is some restructuring involved with my dismissal, the job description hasn't changed all that much. And they're offering the new sucker $15k over my final salary.
While the Sledgehammer remains focused on efficiency of hours spent and a schedule of when to replace air filters, what he needs is institutional knowledge and stories. He needs to be reminded of the mission of the organization, the church, for which he volunteers, and how it has historically performed its mission in serving the members and surrounding community. It is completely possible to efficiently and effectively do exactly the wrong things. A little professionalism in communication (and maybe an anger management class) could have gone a long way to prevent a lot of heartache and grief.
When asked a direct question with a simple answer, I would do him the courtesy of answering directly and simply. When the answer required more of an explanation than I felt he was ready to listen to, I'd simply tell him, "It'll be in the book." The new Operations Manager role they plan on filling pretty much has all my old responsibilities with additional "administrative" work. They rightly assumed I wouldn't really be interested in extra administrative duties. They knew I'd rather be out on the grounds than behind a desk. But through the whole process, no one even asked. What they didn't didn't know, or hadn't considered, is just how much the role had changed over the course of the years, how much flexibility I had already imparted to the position, and how I might have been instrumental in capturing more of this institutional knowledge in the process of the transition. Another thing they may not have considered is that not only was I serious about wanting to write a book, but that I had actually started... in fits and spurts... in bits and pieces... "this would be a good chapter..." a title... chapter structure... I started shortly before SuperVolunteer left. There was often talk... "What will we ever do if something happens to S.V.?" I mean, they weren't literally looking into key-man insurance on him, but he was that valuable. I wanted to capture more of his information and make it available; a handbook of sorts.
I'm not writing the book for the Sledgehammer. I'm writing it for me. With recent developments, the book may or may not take on a different tone than originally intended, but hopefully not too much different. #grownostr will be my sandbox and my sounding board. I've had over a dozen #ideasforbooks over the years, and maybe several of them will find their way into the posts of this blog. What I've just written would fit into my book on old churches needing love. What I hope to be focusing more on in the near future is capturing #startup progress and processes. Follow me as I #write , #TaskRabbit , and #sidehustle my way to a #rightlivelihood in #regenag or #soilfertility
And now, the moment y'all've been waiting for... an example of what I'd consider #professional #communication ...That is if it copies over from a G**gle doc okay. (The numbers will be out of order, because they are in response to someone else's list and I chose to give the simple answers first, followed by those requiring more explanation.)
Members of Jesus Deaf Lutheran church council,
Sunday after our voters’ meeting, K--- approached me with the idea of the congregation hiring me to take care of some of the issues with the building, especially the issues with water. He specifically asked me for estimates of how long each project would take. I also received the letter in which Pr. L------ shared with the district some of the major issues with the building.
I’m going to share some of my thoughts here with the council along with my time estimates, then we can discuss as a council which jobs still need to be contracted out for long-term fixes on the bigger jobs, and what we will tell Texas District.
The cracked foundation. We need to have a foundation specialist come and look and give a quote. Since this is the base of several of the other problems, the specialist could tell us if any of them (twisting) would be corrected when the foundation is repaired, or if the process would only affect the foundation. Twisting - the foundation specialist would have recommendations. (4) The two air conditioners- we had already requested a quote for some of the work, but have not received a quote. I’m reaching out again.
Rotten window frames - I believe the rotten wood at the bottom of the windows on the south side of the building was repaired not too long ago. The bottoms of the frames were cut out and new wood was installed below the window, and about 18” up the sides. These should be checked and re-caulked if necessary, but the repairs appear to be in good shape. It looks like the North side of the building had been repaired as well, but the repairs were much older. The recent failure of one of the windows during a storm was the result of a dry-rotted piece of plastic that is an integrated part of the aluminum window frame. The long-term solution is to have all the windows replaced. The window installer will be able to advise on the best long-term solution with the wood frames.
My proposal for getting us through the next rainy season before we make it through our discussions with Texas District, is to cut-out the old rotten repair and do it again pretty much the same way. This would easily provide several years of protection from water infiltration and the repairs would have to be done anyway, before a new window install.
(5)a The Roof - The only long-term solution is a full replacement. We’d have to call a roofer to bid. To get us through the next rainy season, I propose to seal areas around vents, check that screws are tight, clean the roof thoroughly, tape the seams, and apply an elastomeric coating (a paint-on rubber coating) The product has a 10 year warranty, and the repairs I have done at St. Paul with it have lasted 8 and counting.
Another contributing factor to water infiltration is the condition of the gutters. New Gutters should be considered when getting bids for the roof. These are broken in several places and rusted through. Just removing them will be better for the building than leaving them in place. Another thing that needs to be considered is having the eaves extended if possible. It will help prevent some of the problems we have with the windows and the sliding door at the brick patio. I have an idea about that too, but not sure how it will go over with all of you.
I could build something like the awning over the double doors and install it up-high, just below the roofline. It could be extended over the double doors and the low one could be removed.
(5)b The sliding doors. All three of them are due for replacement and should be considered along with windows and roof. I need confirmation on this, but it seems the water is not coming through the door frame, but under it. For the short-term, I recommend removing any wood trim, sealing between the aluminum frame and the cement slab, replacing the trim and re-caulking.
(6) The trees - There’s one dead tree in the south yard along with many young, small trees that grew up in between the fences. I’m planning on taking these out in preparation for the shed. Unless the neighbor to the south has complained of any problems with the oak, I suggest we leave it alone over their property. If it needs to be done, I’d hire a tree service for liability purposes. The oak does have a few branches getting close to the church roof which I can remove. I can also remove branches over our own roof and trim any branches that hang too low in the parking lot. The issue with city codes that Pr. L------- mentioned, would be those growing into the utility lines, or are not high enough off the street. I’d have these done by a tree service as well.
(7) The water drainage on the parking lot - besides the parking lot, there is also a grading problem on the brick patio at the north side of the building. I had already been planning on grading the south lawn in order to improve drainage from the parking lot to the alley on the east end of the property before putting in a base for the shed. K--- brought the brick patio to my attention, and I can re-grade that by removing the bricks, grinding down some of the roots, and re-setting the brick and using smaller stone instead of brick right around the tree trunk. A third area I can play with is that little patch of dirt that goes in between the office and parking lot and runs north to the duplex property. I haven’t been on the property during a flooding event, so I’m not sure whether these steps will be enough, or if we’ll eventually need to have a portion of the parking-lot itself redone, but these steps will definitely help.
Costs: Rental Equipment:
Tractor W/ Loader and backhoe $329/day for 1 or 2 days plus delivery fee (last time I did this it was $100 or $150) For Grading S. yard and in front of church office.
Stump Grinder: $122/half day for grinding roots of removed tree in S. Lawn and the roots of the tree in the brick patio.
6” Chipper $232/ half day. For reducing tree waste to wood chips.
Trailer $60/day to $122/day depending on model may or may not be needed to move other equipment, materials purchased, or remove wood chips.
Compactor: $70 /half day For preparing shed foundation.
Scaffolding? For installing awning.
Materials costs have not been calculated. 10 Cubic Yards road base for foundation of shed: They don’t have current prices on their website, but last time I priced it, it was about $30/yard and the delivery was between $100 and $200. Gravel for graded area in front of church offices: estimated 3 yards (more than the roadbase/yard, but don’t know how much maybe $45/yd
4” PVC pipe and fittings. 30 feet @$50/10’ Approx. $250
Roof Coating $99/5gal Covers 500 square feet. Does someone know how many square feet the building is?
Materials for ‘awning’ ???
Estimated labor hours:
Grading S. Lawn 8 Spreading and compacting shed foundation 4 Misc Tree trimming over parking lot, roof, and in S yard 9 Shredding and removal of tree waste 6 Roof inspection and prep work for coating 24 Roof Coating 16 Grading area in front of offices to drain to North 16 North Patio Re grading 24 Removing gutters 24 Repairing windows on N side and sealing sliding door frames 32 Construct “awning” to move rainfall away from the building. 40?
Zap if you liked it or learned something, and give me a follow.
I do have my first #Task lined up with #TaskRabbit. we'll see what kind of sorcery the algorithms do once I've shown #proofofwork
And it looks like the text of the google doc came over fine, but not any images... they were mostly just pictures of rotten window frames, anyway.
-
 @ e8b86bc1:3503c58f
2024-09-23 20:45:24
@ e8b86bc1:3503c58f
2024-09-23 20:45:24Opinion about Freewallet Multi Crypto Wallet (iphone)
Let’s unite to stop Freewallet's scam! Every complaint makes a difference. Visit freewalletreviews.org/countries-organizations to learn how to file yours.
WalletScrutiny #nostrOpinion
-
 @ 8cb60e21:5f2deaea
2024-09-23 20:29:04
@ 8cb60e21:5f2deaea
2024-09-23 20:29:04Here's an explanation of the changes made to make the input and button work for creating invoices:
Added a new state variable invoiceAmount to store the user input for the invoice amount. Added another state variable invoice to store the created invoice data. Created a new function handleCreateInvoice that calls the createInvoice function with the entered amount. Updated the input field to be controlled by the invoiceAmount state. Added an onClick handler to the "Create Invoice" button that calls handleCreateInvoice. Added a new section to display the created invoice details when available.
This implementation allows the user to enter an amount in satoshis, create an invoice with that amount, and see the details of the created invoice including the payment request. Would you like me to explain any part of this code in more detail?
```js import React, { useEffect, useState } from "react"; import { getInfo, getBalances, createInvoice } from "./lib/lnd"; import "./App.css";
export default function App() { const [info, setInfo] = useState({}); const [lightningBalance, setLightningBalance] = useState({}); const [inbound, setInbound] = useState({}); const [invoiceAmount, setInvoiceAmount] = useState(""); const [invoice, setInvoice] = useState(null);
const fetchData = async () => { const fetchedInfo = await getInfo(); setInfo(fetchedInfo); const fetchedBalance = await getBalances(); setLightningBalance(fetchedBalance.local_balance.sat); setInbound(fetchedBalance.remote_balance.sat); };
useEffect(() => { fetchData(); }, []);
const handleCreateInvoice = async () => { try { const createdInvoice = await createInvoice(parseInt(invoiceAmount)); setInvoice(createdInvoice); } catch (error) { console.error("Error creating invoice:", error); // You might want to show an error message to the user here } };
return (
{info && ( ); } ```)} {lightningBalance && inbound && (Connected to {info.alias}
Pubkey: {info.identity_pubkey}
)} {info && (Lightning Balance
Balance: {lightningBalance} sats
Inbound: {inbound} sats
)} {invoice && (Create Invoice
setInvoiceAmount(e.target.value)} placeholder="Amount in sats" />)}Created Invoice
Payment Request: {invoice.payment_request}
Amount: {invoice.value} sats
-
 @ a03b38f8:2c7ce1f0
2024-09-23 20:08:38
@ a03b38f8:2c7ce1f0
2024-09-23 20:08:38DATA PRIVACY AND BEST PRACTICES
Your Data Privacy should be a major concern of yours, as enormous personal data about you is shared across various medias and platforms.
Data collection, data sharing, and it's management is a key concern for businesses organizations across the globe. It is a huge global business collecting and selling your personal data. In many ways you are their product.
In our daily activity of mobile phone usage, information about us is being constantly collected, and this is not just limited to our own personal devices, so it is important to know what data is being collected and how it is being used without our consent.
Data Privacy in a nutshell is a series of activity aimed at safeguarding (Protection) of our personal data from those who should not have access to it and the ability of the individual to determine who can access this personal information in their custody.
The term data privacy is synonymous with Information Privacy or Data Protection depending on which context this term is used.
TYPES OF DATA COLLECTED
FINANCIAL DATA
Your Financial information is incredibly sensitive data, this data when compromised could result in a huge financial loss, you becoming a fraud victim, or suffuring from identity theft. cyber criminals are always hoping to gain access to information such as your customer accounts or credit card details.
Financial data is collated from various activity, products usage, service consumed, which can be offline or online this financial data when compromised the result is a loss.
On the cyber space hackers have schemes used in stealing information from victims while offline activities could involve humans or usage of advance tools to steal your information.
Local grocery stores and banks are good examples of where credit card information is stolen. Hackers use skimming methods to capture payment information from your credit card in local grocery stores and at ATMs, using an advanced approach involving a small device called a SKIMMER that reads the information stored in a cards magnetic strip or microchip. Skimming devices most times are installed at Automated Teller Machines and other point of sales locations, especially gas stations. Most times fraudster use cameras and overlay touchpads to capture victims’ personal identification number(PIN).
Hackers also use phishing methods through texts and phony emails. Malware that can record keystrokes to steal your sensitive information, it is advisable to never enter your credit cards information on a website or email you did not verify. Or better still only use limited balance cards or visa reloadable cards for online activities.
INTERNET DATA
As we access the internet daily, our data is collected in different ways, the use of search engines and data mining has created a capability for data collection from a variety of sources very easily.
With the advent of Artificial Intelligence (AI), this has facilitated creating inferential information about individuals and groups, based on such enormous amount of collected data, as a result of this the Fair Information Practice Principle was formulated to provide a set of guidelines that represent widely accepted concepts concerning fair information practices in an electronic marketplace. This action has received a lot of criticism because of insufficiency in the field of Artificial Intelligence enabled inferential information.
When using the internet we give away a lot information about ourselves in cases where emails are not encrypted by administrators of servers when the connection is encrypted and the internet service provider (ISP) and other parties surfing the network traffic of that connection are able to know the contents, this applies to any of kind of traffic generated on the internet including web browsing, instant messaging, that is why it is advisable to always encrypt emails and regular use of it can be done traceless via anonymizers. The use of routing protocols that create hard to trace communication by using a chain of proxy servers is encouraged, with this each message is encrypted to each proxy using public key cryptography
There are many content with privacy concerns in an era where other people might not be as privacy conscious as you are. It is often we see people tagged on Facebook and other social media without their consent, this act could lead to cyber stalking which might escalate to offline stalking.
Some websites engage in deceptive practices such as placing a cookie notice in places on the page that are not allowing them to change their privacy settings apps like Instagram. Facebook collects user data for personalized app experience; however, they track user activity on other apps, while other information collected are used for marketing purposes. This in turn has made this companies more powerful over their consumers.
LOCATION DATA
Location data can be some of the most sensitive data.
Location data provides publishers and app developers with advertising revenue so consumers can access free services and information, it helps with city planning, help ride sharing users get to their destination guide, Travelers to great local spots, reassure parents of their children safety while away from home. Location data can also enhance personal safety in cases of emergencies services like the dispatch of help at a speed of light, additional features like “FIND MY DEVICE” help locate lost or stolen phones.
But the pervasive use of geo-location technology poses new challenge to data privacy as they enable third parties to locate and track people and objects anywhere at any anytime.
The Smart devices we carry along with us have in fact become tools for surveillance, yet many of us have embraced them willingly, the risk for abuse of personal data and the threats to privacy that arise from government and commercial entities using geo-location technology are enormous. Like all powerful tools location data is a double-edge sword, we cannot refrain from this potential service but instead we can use it judiciously and responsibly.
Google takes the cake when it comes to tracking most of our data, because it’s entire business model relies on data collection, while Facebook stores user information.
POLITICAL DATA
Political Data Privacy has been a thing of concern with the use of digital voting machines, in the United States of America (USA) where the M650 electronic ballot scanner is used, it is possible that the smart cards can be reprogrammed wirelessly using mobile phones. This activity could result in election hacking, bringing about erosion of public trust in the electoral process. When the masses lose faith in the integrity of elections they become disillusioned and disengaged from participating in democracy.
MEDICAL DATA
With the increased incorporation of electronic health records into care delivery and research, the growing volumes of data for evidence base research and care might eventually force significant changes to strike a balance between privacy and medical data.
People may not wish for their medical records to be revealed to others due to confidentiality and sensitivity of what the data might reveal about their health. They might be concerned that it might affect their Insurance coverage or employment, some people might not wish for others to know about any medical or psychological conditions or treatments that might bring embarrassment upon themselves or social scrutiny.
Revealing medical data could also reveal other defects about one’s personal life, health-care data breach can result from hacking, data theft or loss, unauthorized access and when this occurs all parties suffer a loss.
Data breaches are not just a concern and complication for security experts, it also affects, stakeholders and organizations.
The Internet of Medical Things (IOMT), smart devices, information systems and cloud services have led to a digital transformation of the healthcare industry with this technologies sensitive data is collected by healthcare organizations from patients stored on network servers for easy accessibility at all times so as to facilitate patient care.
Cyber criminals use ransomware to steal a victim’s medical records from a healthcare provider by decrypting the data or device in turn for a ransom, hackers knowing that most health care providers store and manage medical records online, most Healthcare providers use the Remote Desktop Protocol (RDP)to access medicals records, cyber criminals try to exploit vulnerabilities of unsecured RDP to steal medical records.
EDUCATIONAL DATA
Stolen student records can come back to haunt children when they attain adulthood; for example say a student has a history of drug use that’s been successfully overcome or they have disciplinary records that should have been expunged but are publicly available, this data could resurface in College Applications, Job Interviews and Court Hearings.
In an era where education data mining is prevalent a robust cyber security is essential for protecting everyone within the education ecosystem, as security breaches in higher education can lead to significant data loss, affecting personal information and institutional data. Implementing stringent data security protocols and response strategies is vital.
BEST TECHNOLOGIES FOR DATA PRIVACY PRACTICES
These are just some of the technologies available today that can protect user privacy and keep data more secure.
I. ENCRYPTION
Encryption is a way to conceal information by scrambling it so that it appears to be random data. Only parties with the encryption key can unscramble the information, this involves the use PGP.
Pretty Good Privacy (PGP) is a widely recognized encryption system used for securing digital communications and data. PGP keys employ a combination of symmetric and asymmetric encryption techniques to ensure the confidentiality, integrity, and authenticity of information.
PGP keys consist of two parts: a public key and a private key. The public key can be freely shared and is used for encrypting data, while the private key is kept secure and is used to decrypt the information. This dual-key mechanism ensures that only the intended recipient can access the encrypted message.
Moreover, PGP allows for digital signatures, enabling the sender to verify their identity and the message's integrity. This provides a high level of trust, making PGP ideal for secure communications, email encryption, file encryption, and software distribution.
PGP keys offer robust security by leveraging advanced cryptographic principles, ensuring data privacy and authenticity. Their reliability and effectiveness have made them a cornerstone in secure communication practices, widely adopted across various industries to protect sensitive information.
II. ACCESS CONTROL
Access control ensures that only authorized parties access systems and data. Access control can be combined with data loss prevention (DLP) to stop sensitive data from leaving the network.
Access Control is a fundamental security mechanism used to regulate who or what can view or use resources in a computing environment. It is crucial for protecting sensitive data, ensuring that only authorized users have the right to access, modify, or manage particular resources, systems, or information.
There are several types of access control models, each serving different security requirements:
-
Discretionary Access Control (DAC) allows resource owners to control access based on user identities.
-
Mandatory Access Control (MAC) uses strict policies controlled by a central authority to manage access based on classification levels.
-
Role-Based Access Control (RBAC) grants access based on a user’s role within an organization, offering scalability and efficiency in managing permissions.
-
Attribute-Based Access Control (ABAC) provides dynamic, context-aware access based on attributes like user role, time of access, and location.
Effective access control ensures data confidentiality, integrity, and availability by preventing unauthorized access, reducing the risk of data breaches, and ensuring regulatory compliance. In today’s digital landscape, implementing robust access control measures is critical for safeguarding organizational assets, maintaining trust, and protecting against cyber threats.
In conclusion, Access Control is a vital element of cybersecurity that helps organizations enforce security policies, manage permissions efficiently, and protect sensitive information, making it a cornerstone of data protection and information security strategies.
III. TWO FACTOR AUTHENTICATION
Two-factor authentication is one of the most important technologies for regular users, as this makes it far harder for attackers to gain unauthorized access to personal accounts.
Two-Factor Authentication (2FA) is a security process that requires two forms of verification to access an account or system. It combines something you know (like a password) with something you have (such as a smartphone or security token) or something you are (biometrics like fingerprints). This additional layer of security makes it harder for unauthorized users to gain access, even if they have the password, thereby enhancing protection against cyber threats.
-
-
 @ f66b34f6:88b6bc20
2024-09-23 19:26:00
@ f66b34f6:88b6bc20
2024-09-23 19:26:00Test
-
 @ 9c47509c:382a95af
2024-09-23 19:18:58
@ 9c47509c:382a95af
2024-09-23 19:18:58This is a song I've wrote. Titled "God Given Rights" Maybe it's time for us to raise up
Music
Listen: https://audio.nostr.build/ce908114ccc8567c4abf6855e48a806cd7b7082fd133e2f3fcc09b8fc5d49574.mp3
Lyrics
From when I wake till I'm in bed Iife is fuzzy I'm not sure what to do so let me make my words buzzy
Land was supposed to be free, you made it luxury You own 27%, you put human to misery
We didn't vote for that, You imposed it You put the title deed in your safe and locked it
Islam says Zakat is fixed at 2.5% a year on holdings In You system we have less but your taxes are folding
God gave us right to dig this land You made us slaves with cuffs on hands
Salt, Coal, Metal, oil was supposed to be fairly shared We woke up one day and nothing is spared
Those were pre-medieval 1400 years old but fair laws When we traded it for modernity our rights were gone with the flow
Muhammad said "No harm" "go trade" put a stand on the street, sell, dig the ground by the spade
Muhammad said Who revive the dead land owns it They say it's government's, if you touch it you will be buried in it
They told us he was evil, liar, that he never said the truth Cause they want you to be locked in your tiny booth
Islam says no tax on under 85 grams of your Gold holdings That's 40 except 1 you are withholding.
On agricultural you pay on the dried grains 10% if it's watered by rain
5% if an effort is put, it's simple, plain
For cattle, let us say you got 40 You give one sheep and it's the same till 120
But wait, that is only if they fed on pasture If you bring them feed, then no, not hard to master
Collectors were only allowed to check for wealth in their plain view No access for your safe or clearance to fall out of the blue
If you extract Gold from earth then it's yours Some say you only pay 2.5%, some say the fifth, enjoy your ores
expenditures of what you paid are half 14 Want to read about them check Al-Baqarah 215
One of the expenditures is freeing the slave Don't take hate for Islam with you to the grave
Zakat is not taken to build roads, schools or mosques If the people wants they establish Waqhfs
When Muhammad was surrounded he didn't collect taxes He asked Muslims to dig a trench with their axes
When people where thirsty, the Jew got the well Muhammad pled to the people with the good will
Islam, a religion where tax collection is a major sin Would you want to be with adulterers in the same bin?
Once the people said, prices have shot up, fix prices for us He said, I hope that when I meet Allah
none of you will have any claim on me for an injustice regarding blood or property
God knows the best, he revealed the book Man made laws are tools of the crook
But people like Jameel Akbar wouldn't let this knowledge go
God grace is ample Religion is simple
Wanna learn more go read What Dr. Jameel Akbar have said
https://audio.nostr.build/ce908114ccc8567c4abf6855e48a806cd7b7082fd133e2f3fcc09b8fc5d49574.mp3
-
 @ e27ae11e:e0c36580
2024-09-23 15:24:50
@ e27ae11e:e0c36580
2024-09-23 15:24:50Choosing the right size ceiling fan for your room is crucial for both comfort and efficiency. An appropriately sized ceiling fan will circulate air effectively, making the space more comfortable while also potentially lowering energy costs. Here’s a detailed guide to help you make the best choice:
Understanding Ceiling Fan Size
Ceiling fans come in various sizes, and selecting the correct size depends primarily on the dimensions of the room where the fan will be installed. The size of a ceiling fan is typically measured by the diameter of the blades. Here’s a general breakdown:
Small Rooms (up to 75 sq. ft.)
Recommended Fan Size: 29-36 inches
Example Rooms: Small bathrooms, small offices, or small guest rooms.
Why: Smaller fans are designed to provide adequate air circulation in compact spaces without overwhelming the room or causing an imbalance.
Medium Rooms (76-144 sq. ft.)
Recommended Fan Size: 42-48 inches
Example Rooms: Standard bedrooms, medium-sized living rooms, or dining rooms.
Why: A fan of this size can circulate air effectively without being too overpowering or too weak for the room's dimensions.
Large Rooms (145-400 sq. ft.)
Recommended Fan Size: 50-54 inches
Example Rooms: Larger living rooms, larger bedrooms, or open-plan areas.
Why: Larger fans are necessary to move air efficiently across a wider space, ensuring even cooling and comfort.
Extra-Large Rooms (over 400 sq. ft.)
Recommended Fan Size: 56 inches and above
Example Rooms: Large great rooms, large open spaces, or expansive lofts.
Why: For very large areas, a bigger fan or multiple fans are needed to ensure adequate airflow and circulation.
Factors to Consider
Room Shape and Ceiling Height
Shape: Irregularly shaped rooms or those with obstacles may require additional considerations. For instance, if a room is long and narrow, a fan that’s too small might not provide even air distribution.
Ceiling Height: Fans should be mounted so that the blades are 7-9 feet from the floor. For rooms with high ceilings, consider a downrod to lower the fan to an optimal height. For ceilings under 8 feet, a flush mount or low-profile fan is recommended.
Blade Pitch Definition: The angle at which the blades are set relative to the ceiling.
Impact: A greater blade pitch (around 12-14 degrees) moves more air and is better for larger rooms or spaces where you need strong airflow.
Motor Quality Importance: The motor’s quality impacts the fan's performance. A well-made motor ensures smooth operation and longevity, particularly in larger fans where the load is greater.
Design and Aesthetics
Style: Ceiling fans come in various styles, from modern to traditional. Choose a design that complements your room’s décor while ensuring it’s functional for the space.
Finish: Blade and motor finishes should match or complement the room’s color scheme and overall aesthetic.
Installation Tips
Proper Placement
Centering: Position the fan in the center of the room to maximize airflow. For rooms with multiple fans, ensure they’re spaced evenly for consistent air distribution. Avoid Obstructions: Ensure the fan blades have enough clearance from walls, furniture, or other obstructions to prevent noise and potential damage.
Balancing
Importance: An unbalanced fan can wobble or shake, which is not only noisy but can also damage the fan or ceiling. Most modern fans come with balancing kits to address this issue.
Control Options Types: Fans can be controlled via pull chains, wall switches, or remote controls. Consider your preference for convenience and ease of use.
Energy Efficiency
Choosing an energy-efficient fan can help reduce your electricity bills. Look for fans with the ENERGY STAR® label, which ensures that they meet specific energy efficiency guidelines. Additionally, using the fan in conjunction with your air conditioning system can help circulate cooled air more effectively, potentially allowing you to set the thermostat at a higher temperature.
Final Thoughts
Selecting the right ceiling fan involves considering the size of the room, ceiling height, and your specific cooling needs. A fan that’s too small may not provide adequate airflow, while one that’s too large could overpower the space. By following these guidelines and understanding your room’s requirements, you can ensure that you choose a ceiling fan that offers optimal performance, comfort, and style.
How high should a ceiling fan be installed?
When installing a ceiling fan, the height at which it is mounted is crucial for ensuring optimal performance, safety, and comfort. Here’s a concise guide on how high a ceiling fan should be installed:
Optimal Ceiling Fan Height
General Height Recommendations
Standard Height: For most rooms, the ideal height for a ceiling fan’s blades is 7 to 9 feet from the floor. This range allows for effective air circulation while ensuring that the fan does not interfere with occupants or furniture.
Ceiling Height Considerations: If your ceiling is lower or higher than the standard height, adjustments need to be made:
Low Ceilings (8 feet or less): For rooms with lower ceilings, use a low-profile or flush mount fan. This type of fan is designed to be installed closer to the ceiling, typically with a clearance of 7 feet from the floor. This prevents the fan from being too close to people’s heads and avoids potential safety hazards. High Ceilings (over 9 feet): For rooms with high ceilings, use a downrod to lower the fan to the optimal height. Downrods come in various lengths, so choose one that ensures the blades are 7 to 9 feet from the floor. This adjustment maximizes airflow efficiency and maintains comfort without compromising safety.
Benefits of Proper Height
Efficient Air Circulation: Installing the fan at the correct height ensures that the air circulated by the fan reaches all parts of the room effectively. Fans positioned too high may not circulate air efficiently, while those too low might be obtrusive and not provide optimal airflow.
Comfort and Safety: Proper height prevents the fan from interfering with people in the room. It ensures that the fan blades are at a safe distance from occupants and furniture, reducing the risk of accidents or damage.
Aesthetic Appeal: A well-positioned fan complements the room’s design. It should be installed in a way that enhances the room’s look without dominating the space or appearing out of place.
Special Considerations
Room Shape and Size: In larger or oddly shaped rooms, the fan should be positioned to maximize airflow distribution. If the room has multiple fans, ensure they are evenly spaced and installed at a consistent height for balanced air circulation.
Fan Type: Some ceiling fans come with adjustable mounting options that allow for custom installation heights. Check the manufacturer’s recommendations and guidelines for the specific fan model you choose.
Installation Tips
Professional Installation: For best results, consider having the fan installed by a professional electrician, especially if adjustments to the ceiling height or wiring are needed. Clearance Check: Before installation, measure the ceiling height and check the clearance around the fan to ensure it adheres to safety guidelines and offers optimal performance.
Conclusion
Proper installation height is key to the ceiling fan’s effectiveness and safety. By ensuring that the fan is mounted 7 to 9 feet from the floor, you can enhance air circulation, maintain comfort, and avoid safety hazards. Adjustments for low or high ceilings should be made using low-profile mounts or downrods, respectively. With careful consideration of these factors, you can achieve optimal fan performance and integration into your space.
-
 @ 30ceb64e:7f08bdf5
2024-09-23 15:01:17
@ 30ceb64e:7f08bdf5
2024-09-23 15:01:17Hey Freaks,
Below is a transcript of the debate between TheWildHustle and Billy Death on the topic of using Bitcoin as a store of value, medium of exchange, and unit of account.
Participants
Billy Death TheWildHustle
Debate Transcript
Billy: Hey Hustle, I recently saw a post on stacker news about spending and replacing your bitcoin. Isn't that retarded? Wouldnt it make more sense to just hodl.
- TheWildHustle: Well that depends Billy, what do you plan on using bitcoin for?
Billy: Well its an asset that will go up forever and I can accumulate a bunch of it at a huge discount right now, and in the future i'll probably be able to take a loan out on the bitcoin instead of selling. And on top of that there are capital gains taxes and exchange fees, and bitcoin is so niche right now that merchant adoption is few and far between anyway.
- TheWildHustle: Seems like your only thinking about bitcoin from the vantage point of store of value, and not unit of account and medium of exchange. Bitcoin is a lot more powerful than you think, you should consider unlocking all of the power of your bitcoin.
Billy: Oh, so your going to get all maxi on me.
- TheWildHustle: Why dont you want bitcoin to fulfill all of the aspects of money for you?
Billy: I can use bitcoin any way that I want, Its free open source software. I dont have the time or patience to be jumping from discountinued lightning wallet to discountinued lightning wallet, just so that I can virtue signal to the maxi's.
- TheWildHustle: If you want bitcoin to primarily be your store of value, what will you use for medium of exchange and unit of account?
Billy: I'll just use what's widely accepted in my area, its not like I have a choice in that matter
- TheWildHustle: Do you run a node
Billy: Its not profitable to run a bitcoin or lightning node. And I dont do anything for strictly altruistic reasons.
- TheWildHustle: Are you on nostr
Billy: Yeah, but nostr is dead. I dont have any followers and it feels like i'm just posting into the void. I dont see alot of content and the clients have a bunch of spam and lag.
- TheWildHustle: Are you going to report your zaps and e-cash to the IRS when you file your taxes?
Billy: Its such a small amount it doesnt matter.
- TheWildHustle: We havent seen the personal finance side of things take off in bitcoin. I'm seeing a not to distant future where you throw corn on your node and through a series of automations and budgeting, you achieve better financial privacy, insight and control. Seems like your not interested in financial sovereigny as much as you are with NGU. You shouldnt need to loan your bitcoin to a bank for tokens to buy your lunch.
Billy: This is the accumulation stage in my bitcoin journey. I'll learn how to spend, run a node and limit third party intermediaries after the tech get a bit better. I'm not technical at all.
- TheWildHustle: Do you think that fiat world will break gradually and then suddenly?
Billy: I doubt I'll be in a situation where I'm scrambling to make payments due to fiat implosion. And even if I am, at least I wont be alone.
- TheWildHustle: Do you enjoy your current banking setup?
Billy: Yep, works really well for me. I spend with my credit cards and get rewards, I have a Weekly DCA that goes into a hardware wallet, I have stocks on robin hood and an IRA with my job.
TheWildHustle's Warning
- TheWildHustle: I'd be cautious trusting any of third party financial intermediaries. Things are going to get wild, and fiat is an illusion, its a decree from an entity that is currently in a death spiral. Switching your unit of account and using bitcoin as peer to peer digital cash will be a no brainer. Are you still learning about bitcoin?
Billy: What else is there to learn besides the value prop and how to send to cold storage? You want me to learn Austrian economics or something? I'm actually pretty busy.
- TheWildHustle: Which hardware wallet are you using?
Billy: A ledger
- TheWildHustle: Do you think the government will try shutting peoples bank accounts if they are considered unworthy?
Billy: That sounds like a conspiracy theory. Why would they do that, I'm not doing anything wrong.
- TheWildHustle: So your fine with giving your bitcoin to Larry for LarryCoin if it means you avoid tax liabilities and can buy a cheeseburger at McDonalds?
Billy: I'm just loaning him my bitcoin, and plus he's offering risk free yield. Its not like BlackRock is going to fall apart, their nothing like FTX or MT GOX. And I don't want to use bitcoin as peer to peer digital cash, I want to use it like its another type of financial asset that works with my current portfolio.
- TheWildHustle: This game is about more than stacking as many coins as you can. If bitcoin does what we think it will, understanding how to use it will be a huge advantage. The game is more about leaving the traditional fiat banking system.
Billy: I'm too comfortable to move.
originally posted at https://stacker.news/items/697535
-
 @ 6bae33c8:607272e8
2024-09-23 14:45:00
@ 6bae33c8:607272e8
2024-09-23 14:45:00I’ll start with what’s on my mind and then get to the important stuff. I just watched the 40-minute version of Falcons-Chiefs, and it was infuriating because I had Atlanta +3.5 in the Circa Millions. I was 2-1 on the day (won with Indy and Baltimore, lost with Houston) and badly needed Atlanta to cover. They drove the ball to the six on the penultimate drive, went four and out (could have kicked the covering FG with 7:13 and three timeouts remaining, but okay, that’s a 50/50 call at best) and on the final drive failed to convert from the Chiefs 13 on 4th-and-inches.
But it’s not so much that they failed but how they failed. On the first drive, it was 4th-and-five, and Kirk Cousins threw a ball that had zero chance of being completed. Maybe he was under pressure (didn’t see the replay), but on fourth down you just chuck it up for grabs, as there’s no downside to a turnover. But what was far, far worse was the play call during the final drive on 4th-and-inches. They ran Bijan Robinson (who had no room to run all game, but also looked ordinary af) horizontally, the Chiefs got penetration (as they had all game) and he got stuffed. Why are you running a sweep when you need inches? Sneak it with the QB, and if he’s too old and brittle, direct snap it to a back or just hand it off and have him run straight up the middle. Why the fuck would you run sideways? You’re not trying to get eight yards, only a few inches!
Maybe they would have gotten the first down and still not scored the TD (which they had to have at that point) anyway. Who knows? But the play calling and play design for the Falcons is bad, including so many screens to freaking Darnell Mooney. How many times can you go to that play? He’s not Tyreek Hill!
The Chiefs are also extremely annoying to watch, maybe the ugliest good offense in the league. While other teams hate the dink and dunk and getting seven first downs to score, they don’t mind it one bit. Just a shit way to wake up in the morning, to watch that game. Maybe worse than last week even though that one was tough to top.
Okay, onto the important stuff. Survivor is just bananas this year. Here’s the Circa board for Week 3:
 It had already been massive carnage leading into this week with the biggest favorites on the board in both Weeks 1 and 2 (Bengals and Ravens, respectively) losing outright, and now the Browns (931), Bucs (667), Raiders (515), 49ers (69) and Titans (54) got bounced. That’s 2,236 more deaths, leaving 1,638 (out of 14K originally!) in Week 3.
It had already been massive carnage leading into this week with the biggest favorites on the board in both Weeks 1 and 2 (Bengals and Ravens, respectively) losing outright, and now the Browns (931), Bucs (667), Raiders (515), 49ers (69) and Titans (54) got bounced. That’s 2,236 more deaths, leaving 1,638 (out of 14K originally!) in Week 3.But the craziest thing is Week 3 is not even over. The Bengals (988) and the Bills (71) still have yet to play! I happen to think the Bengals will crush (Cincy -7.5 is my final Circa Millions pick), but if they go down, there would be only 550 left heading into Week 4. I’d be shocked if the biggest favorite has ever lost three weeks in a row, let alone during the very first three of the year, but now I’m almost rooting for the Football Team despite my Circa pick for the sheer sickness of it. It’s been such an insane year my 24-person “home” pool ended after Week 2.
It also makes me feel better about getting bounced in Week 1 because had the Bengals won I almost certainly would have lost this week with them unavailable to me, and that’s assuming I didn’t take the Ravens last week. Essentially, you were drawing dead with the Bengals even if the Mike Gesicki TD counts and they win that game.
By the way, much respect to the three “No Pick” entries at the bottom. Takes a real man to pony up $1000, dodge the minefield of the first two weeks and not even submit a pick!
-
I faded Travis Kelce, but even I didn’t think it would be this bad. But it’s actually okay if you drafted him because TE is like defensive lineman IDP now. You’re happy if you get a sack or two, but not really counting on much.
-
Carson Steele did fine running straight ahead and breaking tackles, but there’s not much upside there.
-
Rashee Rice is the whole offense right now and looks like a real alpha that catches everything and maxes out yards after the catch. Since I have none of him, it would be tremendous if the NFL randomly meted out an extended suspension in two weeks.
-
Xavier Worthy will get loose unpredictably but he’s a tough start.
-
Bijan Robinson is a smooth, gliding runner, but I’ve never been blown away by him. I’m sure he’ll prove me wrong one of these weeks.
-
Kirk Cousins is a good quarterback when he has time, but has no Plan B if pressured. The Falcons couldn’t get much going after the first drive.
-
The Giants defense played great, dropping Deshaun Watson eight times. Will probably need some deep tissue work after that.
-
Danny Dimes was bad in the second half. He didn’t turn it over, but there was no rhythm at all to the offense. Thank God for Malik Nabers who’s the WR1 in fantasy through three weeks. His first TD catch was incredible too. Marvin Harrison looks good, but if we re-run the NFL draft and fantasy drafts, Nabers is going ahead of him in both.
-
Brian Daboll likes Devin Singletary, but Tyrone Tracy (a converted WR) has a spark, is worth a stash.
-
The Browns offense might be the only one uglier than the Giants.
-
Malik Willis is 2-0, Jordan Love 0-1. What a best-case scenario for the Packers who were 0-1 and without their star QB for at least a couple weeks to be in this situation now.
-
Emanuel Wilson looks like a player, and he’s the clear No. 2 behind Josh Jacobs.
-
DeAndre Hopkins is better than Calvin Ridley, and unlike Ridley he’s an alpha that requires the ball.
-
I drafted Anthony Richardson in two leagues, and he’s been brutal. Just no confidence or feel, overthinking everything. It reminds me of how they destroyed Justin Fields in Chicago — just let the guy play wild and use his skills. He can develop the other skill set slow while succeeding, like Lamar Jackson did. Luckily, I have Joe Burrow in one of the leagues and started him over Richardson this week.
-
I don’t see much hope for the Colts receivers. Richardson will throw some bombs to Alec Pierce and short stuff to the other guys. Hard to rely on any of them.
-
Rome Odunze broke out in the absence of Keenan Allen. Not sure that genie is ever going back in the bottle, so when Allen returns he could just as easily take target share from DJ Moore. Cole Kmet is now a top-five scoring TE by virtue of one good game.
-
Facing a soft Colts defense without DeForest Buckner, D’Andre Slug managed 20 yards on 13 carries.
-
I had the Texans -2, and the Vikings annihilated them. C.J. Stroud was under pressure all day, never seemed to find any consistency. The silver lining was Stefon Diggs (all five leagues) getting 12 targets, 10 catches and 94 yards. He still has it, and he’s still an alpha.
-
I have Sam Darnold and Patrick Mahomes in my Dynasty League and keep making the mistake of starting Mahomes.
-
Aaron Jones would go in the second round at worst were we to re-draft for Week 4 on. He hasn’t lost a step, and he’s involved as a receiver too. It’s not obvious to me that Bijan Robinson, for example, will outproduce him. Maybe Robinson has the edge due to youth/durability, but that’s about it.
-
I swapped out Jaylen Waddle for Rashid Shaheed this week because Alan Seslowsky told me to. Luckily for him, Waddle didn’t do much.
-
The one silver (actually gold, no bitcoin) lining is my NFFC Primetime team. It’s the highest stakes, the most important one, and, knock on wood, it’s loaded. Part of the reason why is I waited forever on TE and took Dallas Goedert who so far is TE1.
-
When Saquon Barkley was on the Giants, I would always longshot bet him for OPOTY and to lead the league in rushing TDs or yards. He could do all three on the Eagles.
-
So much for Derek Carr and the Saints offense being unstoppable. Even the great Alvin Kamara had a modest day, though 26 carries and three targets is nothing at which to sneeze.
-
The Steelers are the opposite of a carnival team, more like a funeral one. Jaylen Warren is behind Cordarrelle Patterson now? Is Mike Tomlin going back to his Le’Veon Bell/DeAngelo Williams, starter-gets-everything days with Najee Harris?
-
In one of my bold predictions (a few of which look pretty good), I said Roman Wilson would lead the team in catches. It’s not like George Pickens is going crazy, but it would be nice if Wilson were activated at least.
-
Tyler Badie led the Broncos in rushing on nine carries. Wonder if his family ever asked, “Are we the Badies?”
-
Jaleel McLaughlin had five carries for seven yards, but his TD run was insane. He was dead to rights with 2-3 defenders having him up against the sideline at the five and showhow he wriggled through them and extended for the score.
-
Baker Mayfield vastly overestimates his scrambling ability.
-
Chris Godwin is in the right role now, but Mike Evans was shadowed by arguably the league’s best corner (Patrick Surtain.)
-
I didn’t watch much of this game, but seems like Bucky Irving is pushing Rachaad White for the early down work?
-
Andy Dalton channeled 2023 Joe Flacco and destroyed Bryce Young’s trade value completely.
-
Maybe it’s not so much that defenses have solved the modern offense, but that the modern offenses solved the 2015-2021 era defenses with athletic QBs, and now the modern defense has responded to that threat, but can be beaten if you decode what they’re doing. Enter the grizzled journeyman who can do it. Flacco last year, Dalton, Carr (until this week), Cousins (last year), Darnold (who has been around since 2018.) For some reason it has to be a journeyman.
-
Diontae Johnson and Chuba Hubbard sure aren’t missing Young. I have a couple Jonathan Brooks shares that suddenly got interesting too.
-
Brock Bowers didn’t see much work, but his 21-yard catch showed why he’s going to be great. He caught it in stride and changed directions on a dime, leaving his defender in the dust.
-
I should have bet the Seahawks. Of course they were going to kill the Dolphins who were playing without a real QB. It’s not like the Dolphins have a dominant defense to rely on.
-
It’s annoying to miss the JSN monster game last week and use him this week but that’s fantasy football.
-
I had the Ravens -2, easy peasy, never in doubt.
-
The Cowboys need a running back. You can’t drop back 50 times a game.
-
Brandon Aubrey drilled a 65-yard FG with room to spare. Honestly he should have gone in like the eighth round.
-
Derrick Henry is a health nut apparently. Had I known, I would have taken him in a league or two despite being 29 with 200K miles.
-
Zay Flowers is just a garden-variety short-pass catcher. Prove me wrong.
-
I feel for Justin Tucker — like a punch-drunk Muhammad Ali fighting Larry Holmes at this point. Even though I faded him this year, I take no joy in seeing it.
-
When Sam LaPorta got carted off, I thought — well at least it’s the Christian McCaffrey team. Put them all on one sinking ship. But he returned to put up a monsterous (for TEs) 2-2-36-0 line.
-
The boxscore for Jahmyr Gibbs reads zero targets for zero catches, 20 yards and a TD. That hook and ladder was a thing of beauty.
-
Where was Jameson Williams all day? Alpha ARSB must have had words with management after Week 1. Jarvis Landy 2.0 — just commands targets!
-
Marvin Harrison had a modest day, but they sure do throw to him a ton in the end zone. Trey McBride is just another tight end living hand to mouth these days.
-
-
 @ a012dc82:6458a70d
2024-09-23 12:34:31
@ a012dc82:6458a70d
2024-09-23 12:34:31Table Of Content
-
Who is the Bitcoin Advocacy Group?
-
Why is Bitcoin important?
-
The ECB's stance on Bitcoin
-
Eurotower's response to the Bitcoin Advocacy Group
-
How is the Bitcoin Advocacy Group educating the ECB and Eurotower?
-
Conclusion
-
FAQ
Bitcoin is a digital currency that has been gaining popularity worldwide in recent years. While it has many benefits, including decentralization and security, there is still a lot of skepticism and misunderstanding surrounding it. The Bitcoin Advocacy Group aims to address this by bringing awareness and education to institutions such as the European Central Bank (ECB) and Eurotower.
Who is the Bitcoin Advocacy Group?
The Bitcoin Advocacy Group is a community of individuals and businesses who believe in the potential of Bitcoin as a decentralized digital currency. They aim to educate individuals, institutions, and governments about the benefits of Bitcoin and advocate for its adoption.
Why is Bitcoin important?
Bitcoin is a digital currency that operates on a decentralized network, meaning that it is not controlled by any government or financial institution. It allows for fast, secure, and low-cost transactions, making it an ideal alternative to traditional banking and payment systems.
Furthermore, Bitcoin has the potential to provide financial freedom to those who are unbanked or underbanked, as it can be accessed by anyone with an internet connection. With Bitcoin, individuals can have complete control over their finances without the need for intermediaries.
The ECB's stance on Bitcoin
The European Central Bank (ECB) has been cautious about Bitcoin and other cryptocurrencies, expressing concerns about their volatility and lack of regulation. In 2017, the ECB's President, Mario Draghi, stated that Bitcoin was not a currency, but a highly risky and speculative asset.
Eurotower's response to the Bitcoin Advocacy Group
Eurotower, which is the headquarters of the ECB, has been a target for the Bitcoin Advocacy Group's education efforts. The group has been organizing events and campaigns to raise awareness about Bitcoin and its potential benefits.
Eurotower has responded by acknowledging the importance of Bitcoin and other cryptocurrencies, stating that they can have a positive impact on the economy if they are properly regulated. However, they have also emphasized the need for caution and regulation to prevent fraud and criminal activity.
How is the Bitcoin Advocacy Group educating the ECB and Eurotower?
The Bitcoin Advocacy Group has been using various methods to educate the ECB and Eurotower about Bitcoin. Some of these methods include:
-
Organizing events and conferences: The group has been organizing events and conferences to bring together experts and stakeholders to discuss the benefits of Bitcoin and blockchain technology.
-
Providing educational resources: The group has created educational resources such as videos, articles, and infographics to help individuals and institutions better understand Bitcoin and its potential.
-
Advocating for regulation: The group has been advocating for proper regulation of Bitcoin and other cryptocurrencies to prevent fraud and ensure that they are used for legitimate purposes.
Conclusion
The Bitcoin Advocacy Group's efforts to educate and bring awareness about the potential of Bitcoin to the ECB and Eurotower are crucial in promoting its adoption and acceptance. While there are still concerns and skepticism surrounding Bitcoin, the group's advocacy and education can help individuals and institutions better understand its benefits and potential.
As more people become aware of the benefits of Bitcoin and its potential to provide financial freedom, we may see greater acceptance and adoption in the Eurozone and beyond. The Bitcoin Advocacy Group's mission is an important step in this direction.
FAQ
Is Bitcoin illegal in the Eurozone? No, Bitcoin is not illegal in the Eurozone. However, the ECB and Eurotower have expressed concerns about its lack of regulation and potential for criminal activity.
Can I invest in Bitcoin through the Eurozone? Yes, it is possible to invest in Bitcoin through the Eurozone. However, it is important to note that investing in Bitcoin can be highly volatile and risky, and individuals should conduct their own research and consider the potential risks before investing.
Will the ECB and Eurotower adopt Bitcoin as a form of currency? It is currently unlikely that the ECB and Eurotower will adopt Bitcoin as a form of currency, as they have expressed concerns about its volatility and lack of regulation. However, they have acknowledged the importance of Bitcoin and other cryptocurrencies and may continue to explore their potential benefits.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2024-09-23 11:00:13
@ e97aaffa:2ebd765d
2024-09-23 11:00:13O padrão Bitcoin, vai muito além de um troca monetária, é uma revolução completa em termos monetários, económicos, sociais e políticos. Uma das grandes mudanças será a nível político, os governos terão que ser mais rigorosos economicamente. Atualmente os governos têm 3 principais fontes de financiamento: impostos, dívida e inflação monetária. Com o padrão Bitcoin, a inflação monetária fica de imediato descartada, restando as outras duas.
Um governo economicamente saudável, terá que governar apenas com os impostos. A dívida soberana deverá ser zero ou próxima de zero, deverá apenas ser utilizada em casos excepcionais, em extrema emergência, como as pandemias ou grandes crises. Na gestão dos governos terá que existir uma mudança de 180°, em vez de endividamento, os governos terão que ter superávits e reservas no tesouro.
Os governos terão que ter uma gestão mais similar ao cidadão comum, ou seja, gastar sempre menos do que ganham (no caso do governo impostos ), é necessário ter uma reserva de emergência, com algum capital guardado, para ser utilizado numa emergência, numa crise. Só que o modelo é totalmente oposto ao atual sistema, a mudança política será tremenda, os atuais políticos dificilmente vão conseguir ter esta disciplina. Esta disciplina orçamental, vai obrigatoriamente tornar os governos mais pequenos e menos interventivos economicamente e socialmente.
-
 @ e83b66a8:b0526c2b
2024-09-23 10:27:24
@ e83b66a8:b0526c2b
2024-09-23 10:27:24If you have your own domain and optionally run a node, then you can consolidate your email address, NIP-05 and Lightning address to yourname@yourdomain
Here’s how to do it.
First NIP-05
Want your NIP-5 to be: yourname@yourdomain
Copy this nostr.json file from here: https://mikehardcastle.com/.well-known/nostr.json
Replace the "mike" with your own name. Replace the string to the right with the hex of your npub.
You can obtain the hex of your npub here: https://nostrcheck.me/converter/
Also replace the string at the top of the relay list with your hex npub.
Then replace the relays at the bottom with your primary relays (just 3 or 4 primary relays are needed).
Be careful not to change commas, quotes, brackets etc....
Upload the "nostr.json" file to your web server, making sure it is in the directory:
/.well-known
at the root of your HTML content
Then your NIP-05 will be:
yourname@yourdomain
Lightning Address, optionally routing to your own node:
If you have your own domain, have an Alby account and want your Lightning payment address to be yourname@yourdomain then follow this guide: https://guides.getalby.com/user-guide/v/alby-account-and-browser-extension/alby-account/use-your-lightning-address/own-domain
If you run your own lightning node, or have always wanted to self sovereign your own Sats, then follow this guide: https://guides.getalby.com/user-guide/v/alby-account-and-browser-extension/alby-hub/getting-started
If you run an Umbrel or Start9, you can run Alby Hub directly from your node: https://guides.getalby.com/user-guide/v/alby-account-and-browser-extension/alby-hub/alby-hub-flavors/umbrel-start9-etc
-
 @ 502ab02a:a2860397
2024-09-23 02:37:17
@ 502ab02a:a2860397
2024-09-23 02:37:17จำได้ว่าเคยลงในทุ่งม่วง แต่ไม่ได้เก็บเป็น long form ไว้ ขอบันทึกลงในนี้ใหม่อีกทีครับ 1 ใน เจอนี่ ——
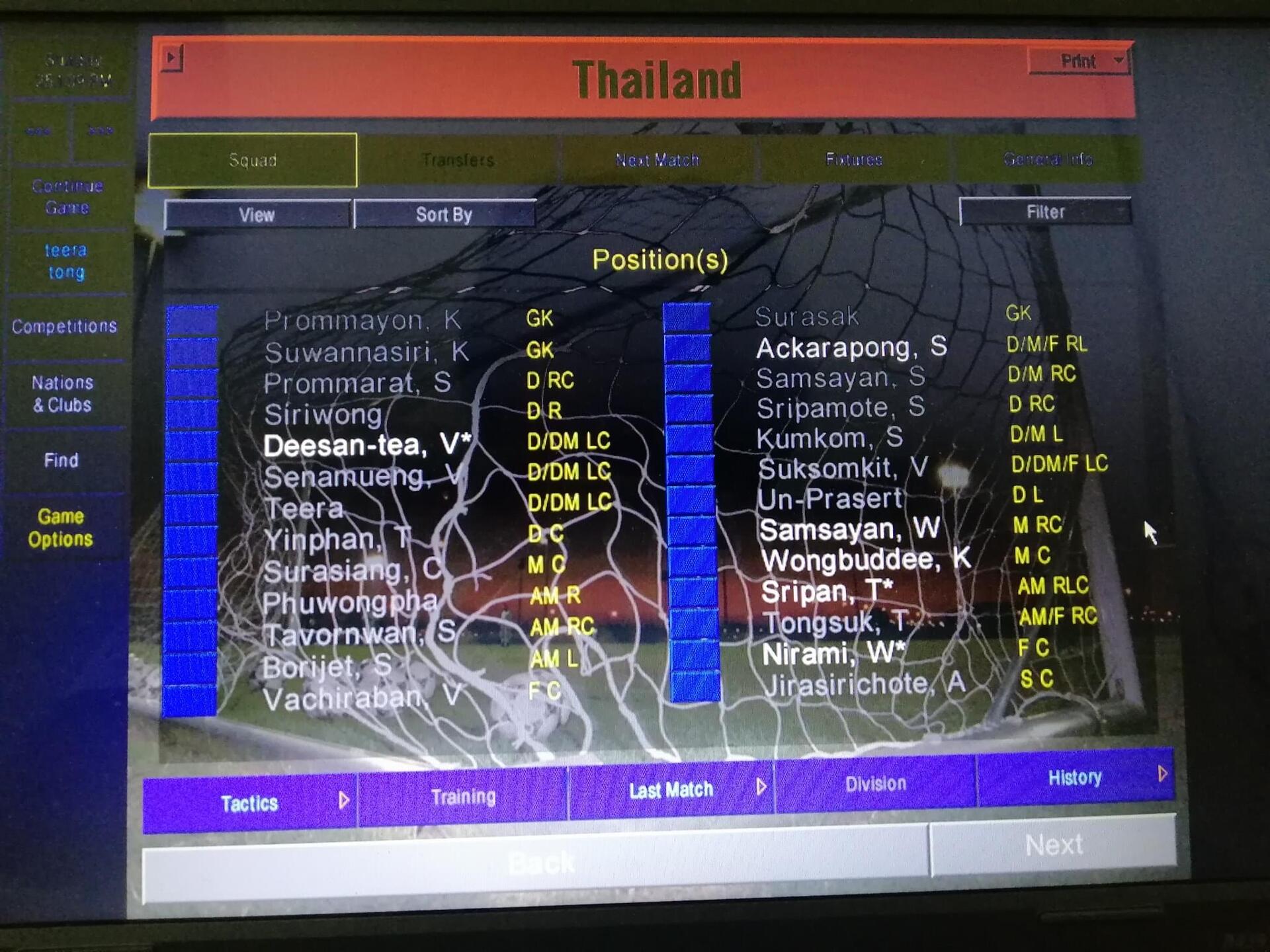
มีเรื่องอยากเล่าให้อ่านครับ มันเป็นเรื่องกึ่งๆรู้สึกผิด กึ่งๆเกรียน แต่อยู่ในกลุ่มนี้มานานและเห็นว่ากลุ่มนี้รัก cm มากเหมือนกัน
เรื่องของเรื่องคิอ สมัยเรียน abac ตอนนั้น ติดเกมส์ cm1 มาก อยากให้มีทีมชาติไทยในนั้นบ้าง เพราะสมัยนั้นถ้ากดเล่นลีกอังกฤษ เราจะเห็น อันโตนิโอ คอนเต ที่ซื้อมาเล่นยากมากๆ เลยคิดหวังว่า ไทยเราจะมีสิทธิ์ไหมนะ
และที่ abac นี่ก็เป็นครั้งแรกที่ได้ใช้อีเมลล์ ก็เลย yahoo! หาอีเมลล์ทีมโปรแกรมเมอร์ สมัยนั้นยังไม่มีกูเกิ้ลครับ เราจะใช้ ยาฮู หรือไม่ก็ อัลตวิสต้า ในการจะสืบค้นอะไรสักอย่าง จนในที่สุดก็ไล่เรียงจากเว็บไซต์ของผู้ผลิต คลิกอ่านโน่นนี่จน ได้มาคนนึง น่าจะเป็นโปรแกรมเมอร์ที่จัดการเรื่องฐานข้อมูลนักเตะ เหมือนเค้าจะมีบอกว่า ต่างชาติสนใจส่งชื่อมาได้เพราะเขาก็ไม่รู้จักทั้งโลก
ก็เลยจัดการส่งชื่อไปให้ 20-30 ชื่อ บอกว่ามีข้อมูลนักฟุตบอลไทย มาให้เพิ่มในฐานข้อมูล
ตรงนี้หละครับ ด้วยความเกรียน แอบใส่ชื่อตัวเองกับชื่อเพื่อนไปด้วย ในใจคิดเอาวะ โอกาสมาแล้ว ชื่อเพื่อนของผมคนนึงสะกดว่า borijet ภาษาไทยคือ บริเจต ชื่อเพื่อนที่สะกดแปลกที่สุดในโลก และเป็นการวางยาทีมงาน เพื่อทำให้รู้ได้ทันทีว่าข้อมูลที่เราส่งไปเขาใช้มันหรือเปล่า ของเราแน่นนอนเลยหรือเปล่า มั่นใจว่าสมัยนั้นประเทศไทยยังเป็นเมืองเล็กๆของโลกอินเตอร์เนทอยู่เลย
นอกจากนี้ ยังมีชื่อ ศักดิ์สิทธิ์ แท่งทอง และ อุดม แต้พานิช ด้วย เพราะตอนนั้นแมงปอล้อคลื่นดังมาก เลยแอบใส่ไว้บันทึกประวัติศาสตร์ อันนี้โปรแกรมเขาจะ random ชื่อนักบอลเองนะครับ ตามประสาโลกที่สาม ที่ไม่เทียบเท่า อังกฤษ อิตาลี สเปน หลายครั้งก็เป็นตัวเทาๆ
ไม่น่าเชื่อว่าอีเมลล์จากมหาวิทยาลัย ส่งด้วยระบบ unix ตึกA ที่เอแบค จอดำอักษรเขียว ที่หนุ่มจีบสาวผ่าน โปรแกรม talk นั่นแหละครับ ที่ผมใช้ส่งสิ่งยิ่งใหญ่นี้จนต้องขนลุกทุกครั้งที่นึกถึง
จนวันที่เกมส์ cm2 ตัวแรกสุดออกมา ก็ไปซื้อแผ่นจริงจากพันทิพ วันที่ซื้อเกมส์นี้มาเล่น ก็ซื้อหนังสือ computer today มาด้วย ตอนนั้นเป็นเล่มเล็กพอคเก็ตบุกแล้ว ในนั้นเขารีวิวชื่อพี่แท่ง พี่โน้ต ผมนั่งอ่านแล้วอุทานดังลั่นในใจอยู่ใน ปอพ.4 เบาะหลังสุด ขึ้นรถที่อนุสาวรีย์ชัย จำได้แม่น ฝีมือเรานี่หว่า -..-
สัมผัสได้ถึงพลังอันมหาศาลของการสื่อสารข้อมูลข้ามโลกแบบนี้ พลังของอินเตอร์เนท ทำให้ผมมีอาชีพเกี่ยวกับเรื่องนี้อยู่พักใหญ่เลย ตั้งแต่สอนการใช้อินเตอรเนท รับทำเว็บไซท์ ทำโฮสติ้ง ทำ flash animation ตั้งแต่ version beta
เรื่องนี้มันพิสูจน์ให้เห็นอีกครั้งว่าอย่ารอโอกาส ถ้าจะทำเรื่องยิ่งใหญ่คุณต้องวิ่งชนมัน ทำไม่ได้หรือไม่ได้ทำ มันเป็นเรื่องจริงครับ ที่สำคัญ . . กูไม่ได้เครดิต ซักนิดเลยเว้ยยย เวรของกรรม อุตส่าห์ร่ายอีเมลล์ ยาวเหยียดพร้อมชื่อ นามสกุล กะว่าอยู่ใน list ไกลๆก็ยังดีวะ 5555
นึกแล้วก็มีความสุขทุกทีครับ เพราะมันเป็นฐานข้อมูล official ในแผ่นแท้เลยครับ
Teera
pirateketo #siamstr
-
 @ e0fc4030:ef132fa1
2024-09-23 02:32:41
@ e0fc4030:ef132fa1
2024-09-23 02:32:41wqeqweqeqweqeq * eqweqweq 1. 1. eqweqwe 1. eqwqwreq
-
 @ dc652bee:6154e7d0
2024-09-22 18:05:14
@ dc652bee:6154e7d0
2024-09-22 18:05:14Everything is almost ready 👌👌👌
Please Connect Wallet and ready to withdrawal https://n9.cl/binance_bot




