-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ bbb5dda0:f09e2747
2024-09-27 19:45:01
@ bbb5dda0:f09e2747
2024-09-27 19:45:01After a small detour I entered the Jotunheimen National Park area and decided I would walk the Bessegen Ridge, A famous -you guessed it- ridge hike that runs all the way along a large lake.

It was a beautiful sunny day, blue skies and barely any wind. Quite rare conditions for Norway. So I thought that was a perfect moment to spend a couple hours video calling with my brother and his girlfriend. So in the late afternoon I decided to drive up to the trail-head and have some dinner before starting my hike.
At the trail-head there is a parking lot for both cars and campers for which they charge 250NOK (25EUR) per day! Since I was planning on hiking 2-3 days I decided I am too Dutch for this and drove on to the first free parking spot available, just ~1km further up the hill. So loaded up with a beefy backpack and my folding bike I sailed down to the parking lot and locked my bike to a tree. I just saved myself 50+ euros.
Day 1
 Most people take the ferry at the trail-head first.
After these delays I was ready to start the hike somewhere between 18:00 and 19:00. “Why so late, are you nuts!?”. Well, it’s not like there’s much of a difference between day and night there, remember. So I didn’t have to worry about a loss of daylight whilst up there. The only danger left was probably bears trying to eat me.
Most people take the ferry at the trail-head first.
After these delays I was ready to start the hike somewhere between 18:00 and 19:00. “Why so late, are you nuts!?”. Well, it’s not like there’s much of a difference between day and night there, remember. So I didn’t have to worry about a loss of daylight whilst up there. The only danger left was probably bears trying to eat me.Contrary to what most people do I started to walk first and take the ferry back from Gjendesheim the last (of 2) stops. Most people take the ferry to the first stop which is Memurubu and then walk back to the trail-head. So while walking I would mostly come across batches of humans that came from the same ferry moving the opposite direction as me. Once they passed I’d be pretty much alone again.
 Just above the trail-head.
Just above the trail-head.After a steep start moving uphill I reached the ‘top’ of the ridge and from there on the walk was pretty flat until right before Memurubu. After a few hours of hiking and taking a moment here and there, and there, and there to take in the amazing views. As I arrived at the highest point overlooking two lakes I thought to myself: “Why not stay here?”. So that’s just what I did because the weather forecasts were good, no rain and barely any wind and good temperatures.
| | | | --- | --- | |
 I had to secure the tent to the ground with rocks |
I had to secure the tent to the ground with rocks |  At around the darkest moment of the ‘night’ |
|
At around the darkest moment of the ‘night’ |
|  My initial idea was to camp right down there between the two lakes. (the right one is much higher than the left) |
My initial idea was to camp right down there between the two lakes. (the right one is much higher than the left) |  Coffee? |
Coffee? |This place has been hands down the best view I’ve ever slept with. It was so quiet and felt deeply peaceful. Just being there, cooking a meal, prepping a coffee and slowly winding down to sleep. I walked roughly 7km with 700m in elevation gain. | | | | | --- | --- | --- | |
 |
|  |
|  |
|
|
|  |
|  |
|  |
|
|
|  |
|  |
|  |
|
|
|  |
|  |
|  |
| | |
| --- | --- |
|
|
| | |
| --- | --- |
|  |
|  |
|Day 2
 Gooooooooooooodmorning!
After quite a relaxed night in my tent I woke up around 9 and slowly got up and made myself some breakfast: oats with raisins and cinnamon and of course water. I was in no rush as I had until 5pm the next day to get to the end of the lake, which is about 17km of hiking left and 1500m-ish in elevation changes.
Gooooooooooooodmorning!
After quite a relaxed night in my tent I woke up around 9 and slowly got up and made myself some breakfast: oats with raisins and cinnamon and of course water. I was in no rush as I had until 5pm the next day to get to the end of the lake, which is about 17km of hiking left and 1500m-ish in elevation changes.I made my way to in-between those lakes in the pictures above. I was chatting with an old colleague (Yay, 4G!) and we even had a call over an IT problem. You can’t lock me inside an office because most of what I need is already in my head anyways ;). Moving on I entered the true wilderness where few men (and even fewer IT-people) dare to walk: places without cell-signal. But I can tell you I survived, seemingly unharmed.
 Also a good time to fill up my camelback with fresh water. Filtering takes ~5-10min.
Also a good time to fill up my camelback with fresh water. Filtering takes ~5-10min.After a couple hours I reached Murumburu (I know, this placename sounds a bit like trying to pronounce a city while eating a sandwich to fast). There’s a cabin/hotel there that also sells some great coffee which is a warm welcome after a hike of 14km and 1700m elevation gain and loss. After enjoying this coffee I walked to the lake where there was a pebble beach that was part part of a riverbed. I decided to go in to freshen up. And fresh it it, because most of the water is fresh melting-water from nearby glaciers. It gets better after the tingling feeling of the whole body fades a bit. Then when you get out, you feel GREAT!
 The water was probably well under 5 degrees Celsius
The water was probably well under 5 degrees CelsiusI still had plenty of time left so most of the afternoon I enjoyed the sun on my face lying on the grass. Not complaining…

| | | | --- | --- | |
 Yup, that’s where we’re going… |
Yup, that’s where we’re going… | This is a pretty good summary of Norway |
|
This is a pretty good summary of Norway |
|  Looking back at Merumburu |
Looking back at Merumburu |  Next to my campsite for the night |
Next to my campsite for the night |I basically walked until I would find a suiting spot that was somewhat protected from the elements and ended up next to a small lake that seemed to house more mosquitos than water. But it was a pretty place nonetheless. Surrounded by glaciated peaks and lots of snow.

Goodnight.
Day 3
Last stretch! On to Gjendebu, where I would catch my ferry back to the trail-head. Just before starting my descent down from the platform I met the last of the very few signs, as 99% of the trail is just following the red T’s. This descend was very much as steep as it looks in the picture down below. I didn’t have much of a chance to take pictures as I needed all my focus not to slide down the bare rock when descending using several chains. Maybe without a backpack it wouldn’t have been too bad but keeping your stability with 10-15kg on your back takes a bit more effort.

Here, naive me was still thinking this path would just move parallel to the ridge. When I made it down and stepped foot in Gjendebu it started to rain, so it was a perfect moment to go inside and rest for a bit. I asked my inner voice if I deserved a beer. I did, because I saved so much money on parking and did a good job hiking. So this 9 Euro costing beer was enjoyed to the fullest.

Okay, actually 2 of them… The ferry was still an hour wait and to kill the time I went outside to sit down at a (covered) picnic table and made some soup. I wasn’t alone as a Norwegian family with kids aged ~1 and ~5 was also there prepping some food. We talked a bit and then the oldest girl -in her best English- offered me one of the pancakes they were making. Of course I couldn’t say no to that.
I really appreciate how they as a young family take the extra effort to bring out their kids to places like this while they could’ve just done the ‘made for kids’ activities in the area.
| | | | --- | --- | |
 So I climbed almost straight down on this part… |
So I climbed almost straight down on this part… |  Thank you for your natural beauty! |
Thank you for your natural beauty! |Sorry this was a bit of a long one. Writing these blogs isn’t always as easy and can be a bit intimidating at times. But it’s worth the effort, thank you for reading 😉
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 1467d9ba:8e5d92f5
2024-09-27 19:27:37
@ 1467d9ba:8e5d92f5
2024-09-27 19:27:37KyberTrike
Intro story
[CORPORATION 1 MAIN CHARACTER]
It's been 15 years since [CORPORATION 1] abandoned us on this dying planet. We've made due with the supplies we had, and built ourselves a survivable future. Ironically it's not the star going out that's our biggest threat right now. It's actually the nihlistic degenerates of [CORPORATION 2]. They'd rather steal food from us than farm their own. If they had just listened to us from the start, we could have built a harmonious settlement. Instead we're nearing all-out war over the prettiest real-estate.
I'm hopeful we can overcome this. Our hard work will see us through to victory.
As for [CORPORATION 3], lord knows where they are. Either moved to the other side of the planet, or dead.
[CORPORATION 2 MAIN CHARACTER]
I've never felt so alive in my life. When the motherships left, first I was afraid. Then I realized I'm a king without them! I don't give a fuck about anything or anyone and I'm taking what's mine, which is everything! [chaotic laugh]
[CORPORATION 1]? Greedy bastards. They have hectacres of farmland, there's plenty of food to go around. They actually wanted to sell it to us, can you believe that?
And it's not like we can't survive without them. In the mines, we found out that you can just drink [exotic ore] and it keeps you alive no matter how thin you are! And you feel great too, on top of the world! Hell, I'm drinking some right now and I feel like I could kill every last [CORPORATION 1] employee and still have energy left! [chaotic laugh]
Factions
[CORPORATION 1]
- Lawful good
- specializes in farming
- Punk rock music
[CORPORATION 2]
- Chaotic evil
- specializes in mining
- Death metal music
[CORPORATION 3]
- Neutral neutral
- Missing
- Aphex Twin music
Story behind the story
KyberTrike is a spritiual successor to CyberStrike2, a late 90's game.
The corporations abandoning the settlers is analogus to Simutronics abandoning CyberStrike2 without explaination or parting gifts. Much like former Cyberstrike2 players are left with a void of CyberStrike gameplay, the settlers are left with a void of peace and common humanity.
To be continued...
-
 @ 4735cdca:0c0ecb64
2024-09-27 14:25:49
@ 4735cdca:0c0ecb64
2024-09-27 14:25:49É muito provável que você imediatamente associe a ciência à tecnologia. São conceitos tão próximos que precisamos de um pouco de atenção para entender as diferenças.
Vamos direto ao ponto.
A ciência busca as explicações sobre os fenômenos que ocorrem na natureza.
A tecnologia é uma atividade prática — um método, instrumento ou processo que ajude a alcançar um objetivo.
O divulgador da ciência e escritor Simon Singh tem uma ótima definição:
(…) a tecnologia envolve todo o necessário para tornar a vida (e a morte) mais cômoda, enquanto a ciência é simplesmente um esforço para compreender o mundo.
E o saudoso Carl Sagan escreveu:
A ciência é uma tentativa, em grande parte bem-sucedida, de compreender o mundo, de controlar as coisas, de ter domínio sobre nós mesmos, de seguir um rumo seguro.
A tecnologia depende da ciência?
A tecnologia não necessariamente depende da ciência.
Imagine como se deu a descoberta da produção de fogo pelos seres humanos primordiais. Eles não tinham noção que é a combustão do oxigênio que gera calor e luz. Estavam interessados em aquecimento, iluminar um ambiente, manter predadores afastados etc.
Outro exemplo é do físico alemão Wilhelm Röntgen (1845 – 1923). Ele descobriu o raio X em 1895, enquanto estudava a luz fluorescente emitida por um tubo de raios catódicos. Esse aparelho é chamado também de tubo de Crookes.
Röntgen percebeu que uma chapa próxima ao experimento brilhava enquanto o tubo estava ligado. Ele executou alguns testes que demonstraram que alguns materiais bloqueavam esses raios e outros não. O cientista até pediu à sua esposa para colocar a mão entre o tubo e a chapa, revelando os ossos de seus dedos.
Röntgen tinha a tecnologia. Já que a natureza daqueles raios invisíveis era um mistério, ele não conhecia a ciência envolvida ali. Por isso, Wilhelm não pôde sequer dar um nome adequado à sua descoberta, que permaneceu chamada raio X.
https://image.nostr.build/0bd313bb463f304f8dc066c170497d4d2734a04f46d6addc25101ef6fe127c89.jpg
Imagem da série The Knick, do canal Cinemax, em que o personagem Herman Barrow tem um raio X tirado de seu crânio enquanto nem ele nem o operador usam qualquer tipo de proteção.
Muitas pessoas foram expostas em excesso a raios X antes de sabermos que eles podem causar mutações e outros prejuízos ao corpo. Isso poderia ser evitado se tivéssemos um conhecimento mais profundo sobre radiação.
Daí a importância de uma base científica por trás de uma tecnologia. Esse embasamento nos permite usar a tecnologia de forma mais controlada e responsável.
Desenvolvendo tecnologia a partir da ciência
O que vemos hoje é a tecnologia muito mais dependente da ciência.
Para produzir um celular, precisamos de conceitos de ondas para ele fazer ligações e se conectar à Internet. Sua bateria necessita de princípios de química e eletricidade para funcionar.
Por isso também podemos definir tecnologia como a aplicação prática da ciência.
Há empresas que investem em ciência aplicada porque sabem que os estudos são conduzidos em uma área que gera resultados práticos. A indústria farmacêutica é um bom exemplo. Estudos bioquímicos podem levar à produção de novas drogas que salvam vidas.
Mas nem todo tipo de conhecimento científico resulta em aplicações práticas em um futuro próximo.
Chamamos de ciência de base a busca pelo conhecimento motivada essencialmente pela curiosidade em saber como as coisas funcionam. É um trabalho dedicado a deixar um legado para a humanidade.
Agora uma frase do físico e escritor Steven Weinberg
A ciência e a tecnologia se beneficiam uma da outra, mas, em seu nível mais fundamental, não se faz ciência por razões de ordem prática.
Em geral, a maior parte do fomento a esse campo vem de dinheiro público, mas também há instituições privadas que investem nesse tipo de ciência sem esperar resultados práticos em troca. Inclusive, há campanhas de financiamento coletivo como a da neurocientista Suzana Herculano-Houzel, que já superou a meta de R$ 100.000,00 em contribuições.
Há quem pense que investimentos em ciência de base são uma perda de dinheiro e de tempo. Mas anos de pesquisa em ciência de base podem resultar em aplicações práticas e avanços que nossa visão ainda não é capaz de enxergar.
Eventualmente esse conhecimento será “útil” e fará uma diferença no dia a dia. Só então seremos gratos aos engenheiros, cientistas e inventores que acreditaram no conhecimento mas muitas vezes veem seus trabalhos desprezados?
-
 @ e83b66a8:b0526c2b
2024-09-26 19:29:43
@ e83b66a8:b0526c2b
2024-09-26 19:29:43If you’re thinking of buying a Bitaxe, here is some information about pools vs solo mining.
Firstly, although the terms are clear “pool mining”, “solo mining” there is nuance in these definitions, so I want to explain these terms fully.
Solo mining pools exist, such as: https://solo.ckpool.org/
It is called a pool, because you are using their credentials to mine, but you keep all the rewards if you win a block. Despite the name, this is not a pool.
You then have a pool such as https://ocean.xyz/ who are a pool, you use their credentials to mine, and you earn a share of their income relative to your contribution in hash power.
There has been some publicity about a solo miner winning a pool recently, there were about 12 blocks won in 2023 by solo miners. However a winning solo miner is likely to be a server farm with hundreds or even thousands of S19’s or S21’s sharing the same payout wallet address. The image of a home miner with a Bitaxe winning a block is extremely unlikely.
A solo miner is defined as a group of miners that share a payout wallet address, so for example you could have 10 Bitaxe’s at home all configured with the same BTC wallet address, this is considered a single solo miner. And so it is with mid tier mining farms, often privately owned, who have a number of machines set to the same payout address. Most of the time, they share earnings for a more reliable income, but the owner may decide to gamble on winning a block and so choose to solo (lottery) mine.
So far, my Bitaxe, which has been running for 4 days now and is part of the Ocean pool. It is earning about 50 Sats a day. If I were to wait for an on-chain payout, it would take around 60 years to receive one. I can, however, setup a BOLT12 lightning payout address and earn this tiny income through Lightning.
So here’s my recommendation.
Currently, there are two pools that control more than 50% of mining, Foundry USA and AntPool. This is a dangerous position and in fact Bitmain, who provide around 90% of all mining hardware actually invest and have stakes in these and several other pools. This is centralising mining and could potentially allow a 51% attack, which could compromise Bitcoin.
Jack Dorsey is currently developing competing mining hardware chipset, through his company Block and Ocean are attempting to decentralise the pools by building a truly independent option for miners to join.
If you buy a Bitaxe, the best way you can help alleviate the dominance of Bitmain is to join a true pool like Ocean to slowly move control away from the dominant pools.
Bear in mind that many of the other smaller pools are still controlled by Bitmain.
If you're still interested in lottery mining, here are your chances of winning a block:
Represented as Hash rates of different miners:
Nerdminer: 20 KH/s = 20,000 H/s
Bitaxe: 750 GH/s = 750,000,000,000 H/s
Bitmain Antminer S9: 13.5 TH/s = 13,500,000,000,000 H/s
Bitmain Antminer S19: 110TH/s = 110,000,000,000,000 H/s
Bitmain Antminer S21: 200TH/s = 200,000,000,000,000 H/s
Current Global Hash rate 628EH/s (Sept 2024) = 628,000,000,000,000,000,000
If you're running a Bitaxe, your percentage chance of winning a block is: 0.000000119426751592357%
Over a year, your chances increase to: 0.00627707006369428%
Your chances of winning the UK national lottery (assuming 20M tickets sold and you buy one):
0.000005%
Over a year, your chances increase to: 0.00026%
Like in all things in Bitcoin, I don’t ask you to trust me. If you want to verify, here are the references I used in making my conclusions:
https://protos.com/chart-when-solo-miners-found-a-bitcoin-block/
https://investors.block.xyz/investor-news/news-details/2024/Blocks-New-Bitcoin-Mining-Chip-to-Be-Part-of-an-Ongoing-Project-With-Core-Scientific-to-Decentralize-Mining-Hardware/default.aspx
https://www.youtube.com/watch?v=Wo91DWvZRs8
https://i.nostr.build/9rQ9Plv6XQYtt6xd.jpg
-
 @ 01d0bbf9:91130d4c
2024-09-26 17:58:10
@ 01d0bbf9:91130d4c
2024-09-26 17:58:10Chef's notes
Amazingly tangy, firey hot, but still mellow and bright.
I use this on everything– Use it to dress salads, dip (honey mustard) for fried chicken, elevate your taco nights, heck a spoonful first thing in the morning will wake you up better than coffee!
Don't forget to use up those delicious chilis and garlic, they are so good!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 1-2 weeks
- 🍽️ Servings: (12x) 8oz jars
Ingredients
- 16oz fresh chili peppers
- 8oz red onion
- 8oz garlic
- 96oz honey
- Fresh thyme
Directions
- Thinly slice peppers, garlic, shallots and fresh thyme
- Add chopped ingredients to the honey
- Leave to ferment (loosely covered) for 1-2 weeks
- Drizzle that amazing pungent firey gold liquid over EVERYTHING. (Don't forget to use up those amazing chilis and garlic too.)
-
 @ 4735cdca:0c0ecb64
2024-09-27 14:24:44
@ 4735cdca:0c0ecb64
2024-09-27 14:24:44Você já teve a oportunidade de ler um livro de divulgação científica? Ele provavelmente citou o método científico em algum momento.
No entanto, nem sempre os autores explicam o que de fato ele é.
Então vamos entender essas regras que são a base de como fazer ciência.
Lembrando que na literatura o número de passos do método pode variar. Aqui veremos em seis passos.
1. Observação
Observe a natureza, algum evento, o comportamento das pessoas ou qualquer que seja o seu objeto de estudo.
O observador deve ser objetivo, ater-se aos fatos e não se deixar influenciar por impressões ou intuições.
A observação vai despertar a sua curiosidade, que vai levar aos questionamentos.
2. Questionamento
Questione por que aquilo que você observou acontece.
Suas perguntas serão seu guia numa espécie de formulação de um problema.
A solução desse problema é onde queremos chegar com o uso do método científico.
O questionamento e a observação estão muito interligados. A observação leva ao questionamento, mas o questionamento também pode estimular novas observações.
3. Hipótese
Levante uma hipótese.
Essa será a sua sugestão de solução do problema formulado durante o questionamento.
É importante que essa hipótese seja testável e falseável. Ela será colocada a prova com experimentos.
Aqui, vale falarmos mais sobre falseabilidade.
Uma ideia ganha mais força quando outras pessoas validam que ela acontece ou funciona.
Daí a importância de uma hipótese ser testável. Assim, temos a capacidade de verificar se ela é verdadeira ou falsa.
Uma hipótese falseável é aquela que temos como considerar falsa.
Segundo o exemplo do filósofo alemão Karl Popper, a hipótese de que "todos os cisnes são brancos" é falseável. Basta encontrarmos um cisne negro para refutá-la.
4. Experimentação
Crie um ou mais experimentos controlados, cujos resultados esperados possam reforçar a sua hipótese.
5. Análise
Verifique bem os resultados dos experimentos.
Analise os dados, refaça as contas e certifique-se de que não houve erros ou vieses para atrapalhar a interpretação das informações.
E nada de "interpretação criativa" dos dados. Avalie-os da maneira mais imparcial e fria possível, afinal, eles devem refletir a realidade e não o que você gostaria que eles representassem.
Peço licença novamente, dessa vez para relembrar o que são lei, hipótese e teoria.
Uma lei é a generalização de um conjunto de observações, não tendo sido encontrada nenhuma exceção a tais observações. Exemplo: Lei da Gravitação Universal.
As hipóteses são conjecturas, especulações, previsões sobre determinado fenômeno da natureza e como ele se comporta. Exemplo: Hipótese da Geração Espontânea.
E as teorias são explicações bem fundamentadas para descrever eventos que ocorrem na natureza. Envolvem fatos, leis e hipóteses já testadas exaustivamente. Exemplo: Teoria da Evolução.
6. Conclusão
Caso o experimento não tenha saído como o esperado, tente entender o por quê e retorne ao Passo 3. Ajuste a sua hipótese ou formule uma nova.
Se os dados obtidos com o experimento comprovam a sua hipótese, chegamos à solução do problema.
A partir daí, sua ideia poderá ser refinada, revisada por outros cientistas, publicada e quem sabe até se tornar uma teoria.
Não pense, porém, que o método científico serve apenas para cientistas. Ele é para todos!
Você pode usá-lo no seu dia a dia, mesmo que seja uma versão mais flexível.
Assim, evitamos de ser enganados e reafirmamos o nosso compromisso com a verdade.
Referências: * Science: The Definitive Visual Guide, DK * O Livro da Ciência, Editora Globo * BYNUM, William; Uma Breve História da Ciência, Editora L&PM * Simpatia Funciona? - Nerdologia * Origem da Vida e Método Científico - Descomplica * O Método Científico e os Tipos de Pesquisa - Aula da Professora Regina Fonseca * Falseabilidade - Canal do Pirula
-
 @ 8f69ac99:4f92f5fd
2024-09-27 13:19:59
@ 8f69ac99:4f92f5fd
2024-09-27 13:19:59É o imobiliário realmente a melhor forma de fazer crescer e proteger a sua riqueza, ou existem melhores alternativas que a maioria das pessoas está a ignorar? Durante séculos, as pessoas têm visto o imobiliário como um refúgio seguro para investimentos—baseando-se na estabilidade histórica e na segurança percebida. Possuir uma casa tem sido há muito considerado um pilar na construção de riqueza e na garantia do futuro de alguém. No entanto, enquanto comprar uma casa para viver pode ser um bom investimento para a vida, o que dizer de investir em imobiliário para preservação de riqueza, arrendamento ou especulação? Poderá esta estratégia ter armadilhas ocultas que levam os investidores a cometer erros?
Se alguém, por qualquer razão, tem dinheiro disponível, esse capital precisa ser alocado ou corre o risco de perder valor devido à inflação. No entanto, a falta de alternativas visíveis, o desconhecimento de opções mais modernas ou uma aversão ao risco, levam muitas pessoas a pensarem imediatamente no imobiliário como a solução. Esta é a escolha natural para o investidor comum, que pode não estar ciente dos desafios envolvidos.
Para muitos, a suposição é que o imobiliário irá sempre superar outras classes de activos. Mas, por trás desta estratégia aparentemente infalível, existe uma teia de desafios e incertezas. As realidades financeiras do investimento imobiliário são frequentemente ignoradas, e aqueles que se aventuram na propriedade sem uma compreensão adequada podem enfrentar despesas inesperadas, volatilidade de mercado e perdas financeiras.
As Realidades Financeiras do Investimento Imobiliário
Ao considerar o imobiliário como uma estratégia de investimento, é essencial distinguir entre a posse de casa para habitação e o investimento em propriedades. Enquanto comprar uma casa para viver pode ser um óptimo investimento para a vida, o imobiliário para fins de investimento é muito mais complexo.
Custos Ocultos da Propriedade
Investir em imobiliário envolve custos iniciais e contínuos significativos, incluindo:
- Entrada: Tipicamente 10% do preço de compra, que poderia ser melhor gasto em outro lugar.
- Custos de fecho: Taxas associadas à compra e venda de propriedades, que variam entre 2-5% do preço de compra.
- Impostos sobre propriedades: Pagamentos anuais ou semestrais aos governos locais (IMI por exemplo), que podem aumentar com o tempo.
- Seguro: Prémios para seguros de edifícios e responsabilidade civil.
- Manutenção: Custos contínuos, que geralmente representam entre 1-3% do valor da propriedade anualmente.
Comparação: Verdadeiras Despesas da Propriedade vs. Arrendamento
O arrendamento muitas vezes evita os custos iniciais substanciais, impostos e taxas de manutenção associados à posse de uma casa. Para muitos, especialmente em mercados habitacionais voláteis, isso torna o arrendamento mais financeiramente viável no curto a médio prazo. Possuir propriedades pode bloquear capital que poderia ser melhor investido noutro lugar.
Riscos de Alavancagem e Dívida
Os investimentos imobiliários geralmente requerem dívida, amplificando tanto os ganhos potenciais quanto as perdas. Uma pequena queda no valor da propriedade pode ter um impacto significativo na sua equidade. Se os valores das propriedades diminuírem, os investidores podem encontrar-se em dificuldades financeiras.
Os Fardos Ocultos do Imobiliário
Embora frequentemente visto como um investimento de baixo risco, o imobiliário traz fardos ocultos. Muitos presumem que é um investimento passivo, mas gerir propriedades—lidar com manutenção e inquilinos—é tudo menos passivo.
Externalidades e Consequências Secundárias
Ao comprar uma propriedade, você também assume: - Custos de manutenção: Desde pequenos reparos até grandes renovações. - Gestão de inquilinos: Encontrar inquilinos fiáveis e lidar com questões relacionadas com inquilinos. - Mudanças de vizinhança: Dinâmicas de vizinhança em mudança podem afectar os valores das propriedades. - Preocupações ambientais: Desastres naturais ou mudanças ambientais locais podem impactar as propriedades.
Imprevisibilidade e Risco do Mercado
O mercado imobiliário está sujeito a bolhas e recessões. As bolhas de propriedades, as quedas de mercado e as mudanças nas regulamentações podem ter efeitos severos sobre o valor do imobiliário.
Liquidez
O imobiliário é um activo altamente ilíquido, muitas vezes levando meses a ser vendido. Em contraste, activos mais líquidos podem ser vendidos rapidamente quando necessário, tornando o imobiliário menos atractivo para aqueles que buscam flexibilidade.
O Impacto Social do Investimento Imobiliário
A forma como a sociedade vê o imobiliário impacta a acessibilidade e a disponibilidade de habitação.
A Crise de Acessibilidade à Habitação
Investir em propriedades para armazenar riqueza ou gerar rendimento passivo eleva os preços e reduz a disponibilidade de habitação para famílias de baixos e médios rendimentos. O “prémio monetário” associado ao investimento imobiliário aumenta a procura, empurrando os preços para cima e exacerbando a escassez de habitação em grandes cidades europeias.
Prémio Monetário
O prémio monetário no contexto do imobiliário refere-se ao valor extra que os investidores atribuem às propriedades não apenas pela sua utilidade como casas, mas como investimentos que podem armazenar, ou preservar, riqueza. Isso significa que as pessoas estão dispostas a pagar mais pelo imobiliário porque o veem como uma forma de preservar e aumentar o seu dinheiro, em vez de apenas um lugar para viver.
Por exemplo, se uma casa vale €200,000 com base na sua utilização real (como espaço habitacional), mas os investidores estão dispostos a pagar €250,000 porque acreditam que ela irá valorizar ao longo do tempo, a diferença de €50,000 é o prémio monetário. Este aumento da procura por parte dos investidores pode elevar os preços das habitações, dificultando a vida às pessoas que precisam de casas acessíveis. Em essência, o prémio monetário reflecte a ideia de que algumas propriedades são valorizadas mais pelo seu potencial como activos financeiros do que pela sua função como lares.
Preço vs. Valor Utilitário
Se o imobiliário fosse visto apenas pela sua utilidade—proporcionar abrigo—os preços das habitações reflectiriam melhor o seu valor real, melhorando a acessibilidade. O modelo actual, que prioriza o investimento em propriedades em detrimento da sua função como casa, promove a gentrificação e o deslocamento.
Bom vs. Mau Investimento numa Casa
Enquanto comprar uma casa para viver é um investimento sensato, usar o imobiliário para preservação de riqueza, arrendamento ou especulação pode ter consequências sociais negativas, perpetuando a desigualdade e reduzindo as opções de habitação para aqueles que mais precisam.
Finanças Tradicionais vs. Imobiliário
Em contraste com o imobiliário, os mercados financeiros tradicionais proporcionam uma forma mais dinâmica e eficiente de armazenar valor.
Mercado de Acções e Índices como Melhores Alternativas
Historicamente, os índices do mercado de acções, como o S&P 500 e o Euro Stoxx 50, superaram o imobiliário em termos de retornos. Estes índices oferecem diversificação e exposição de baixo custo ao crescimento a longo prazo. No entanto, mesmo estes mercados têm limitações, especialmente quando se considera a inflação. Por exemplo, o retorno composto histórico do S&P 500 é de cerca de 7% por ano uma vez ajustado pela inflação. Em alguns casos, pode mesmo resultar em perdas ao considerar a inflação real.
Custos e Barreiras de Entrada
Para as pessoas comuns, aceder ao mercado de acções requer um corretor, o que adiciona camadas de complexidade e taxas. Muitas pessoas, especialmente aquelas que trabalham em empregos "9 às 5", encontram-se numa posição em que são quase forçadas a aprender sobre o mercado de acções e investimentos tradicionais apenas para proteger o seu dinheiro, arduamente ganho, da inflação. Esta não é uma tarefa simples, pois investir em acções ou índices requer pesquisa, monitorização e conhecimento que a maioria das pessoas não tem tempo ou desejo de adquirir.
Além disso, a taxa de inflação real que as pessoas enfrentam muitas vezes difere das métricas oficiais, como o Índice de Preços ao Consumidor (IPC). A verdadeira inflação sentida pelas pessoas é melhor reflectida no aumento de preços dos bens e serviços que compram regularmente. Assim, mesmo o S&P 500, uma vez ajustado para esta inflação do mundo real, pode não ser tão seguro ou lucrativo quanto parece.
Uma Alternativa Mais Simples
Para aqueles que procuram uma opção de investimento mais directa, existe uma alternativa moderna: Bitcoin. Ao contrário das acções e do imobiliário, que requerem conhecimento significativo e gestão, Bitcoin pode ser comprado e mantido com esforço mínimo. Isso torna-o uma escolha atraente para indivíduos que não têm tempo para navegar pelas complexidades das finanças tradicionais.
Por Que Bitcoin É um Armazenamento de Valor Superior
1. Custos Baixos e Sem Externalidades
Bitcoin não tem impostos sobre propriedades, custos de manutenção ou seguros. A sua natureza descentralizada e baixas taxas de transacção tornam-no uma forma de armazenamento de valor eficaz em termos de custo.
2. Liquidez e Segurança
Bitcoin é um activo altamente líquido e facilmente transferível, tornando-o superior ao imobiliário, que leva tempo a vender. Além disso, a tecnologia descentralizada e segura do Bitcoin oferece protecção contra manipulação e confiscação.
3. Sem Necessidade de Especialização
Ao contrário do mercado de acções ou do imobiliário, Bitcoin pode ser mantido e gerido sem conhecimento especializado, tornando-o ideal para pessoas ocupadas ou aquelas novas no investimento.
4. Melhor que o Ouro
A natureza digital de Bitcoin faz com que seja mais transportável e acessível do que activos físicos como o ouro. É sem fronteiras e pode ser armazenado de forma segura, ao contrário do ouro ou do imobiliário, que exigem medidas de segurança física.
Conclusão: Repensar a Estratégia de Investimento
-
A Armadilha do Imobiliário: Muitos veem o imobiliário como um investimento de baixo risco e padrão, mas esta mentalidade é errada. Os custos ocultos, os impactos sociais e as questões de liquidez tornam-no menos atraente quando analisado criticamente.
-
Alternativas das Finanças Tradicionais: Investimentos tradicionais como acções e índices oferecem retornos superiores e escalabilidade em comparação com o imobiliário, proporcionando uma opção melhor para preservação de riqueza.
-
A Ascensão de Bitcoin: Bitcoin oferece uma forma ainda mais directa e eficiente de armazenar valor, livre das complexidades e custos tanto do imobiliário quanto das finanças tradicionais, enquanto proporciona liquidez, segurança e facilidade de uso.
-
Um Futuro Mais Brilhante: Ao movermo-nos além das estratégias tradicionais centradas no imobiliário e abraçar alternativas modernas, podemos desbloquear um futuro mais equitativo e rentável para a preservação de riqueza.
Photo by Tierra Mallorca on Unsplash
-
 @ e83b66a8:b0526c2b
2024-09-21 16:29:23
@ e83b66a8:b0526c2b
2024-09-21 16:29:23Here are some of the more interesting projects that I like:
Messaging:
https://www.0xchat.com/#/ - Private messaging - think WhatsApp
Xitter Like Clients:
https://damus.io/ - iPhone client
https://nostrapps.com/amethyst - Android client
https://primal.net/downloads - Android, iPhone & Desktop
https://shipyard.pub/posts - Schedule future posts
Interesting sites:
https://zap.stream/ - Video streaming
https://fountain.fm/ - Podcasting
https://wavlake.com/ - Music streaming
https://shopstr.store/ - Online shop
https://zap.cooking/recent - Cooking recipes
https://ostrich.work/ - NOSTR jobs board
NOSTR tools
https://nostr.band/ - Powerful search tool
https://nostr.wine/ - Powerful, but centralised paid relay
https://npub.pro/ - Website creation tool
https://nostr.build/ - Media and file storage
https://relay.tools/ - Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user - Creator tools
List of NOSTR apps:
https://nostrapps.com/
-
 @ 6ad3e2a3:c90b7740
2024-09-11 15:16:53
@ 6ad3e2a3:c90b7740
2024-09-11 15:16:53I’ve occasionally been called cynical because some of the sentiments I express strike people as negative. But cynical, to me, does not strictly mean negative. It means something more along the lines of “faithless” — as in lacking the basic faith humans thrive when believing what they take to be true, rather than expedient, and doing what they think is right rather than narrowly advantageous.
In other words, my primary negative sentiment — that the cynical utilitarian ethos among our educated classes has caused and is likely to cause catastrophic outcomes — stems from a sort of disappointed idealism, not cynicism.
On human nature itself I am anything but cynical. I am convinced the strongest, long-term incentives are always to believe what is true, no matter the cost, and to do what is right. And by “right,” I don’t mean do-gooding bullshit, but things like taking care of one’s health, immediate family and personal responsibilities while pursuing the things one finds most compelling and important.
That aside, I want to touch on two real-world examples of what I take to be actual cynicism. The first is the tendency to invoke principles only when they suit one’s agenda or desired outcome, but not to apply them when they do not. This kind of hypocrisy implies principles are just tools you invoke to gain emotional support for your side and that anyone actually applying them evenhandedly is a naive simpleton who doesn’t know how the game is played.
Twitter threads don’t show up on substack anymore, but I’d encourage you to read this one with respect to objecting to election outcomes. I could have used many others, but this one (probably not even most egregious) illustrates how empty words like “democracy” or “election integrity” are when thrown around by devoted partisans. They don’t actually believe in democracy, only in using the word to evoke the desired emotional response. People who wanted to coerce people to take a Pfizer shot don’t believe in “bodily autonomy.” It’s similarly just a phrase that’s invoked to achieve an end.
The other flavor of cynicism I’ve noticed is less about hypocrisy and more about nihilism:
 I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.
I’d encourage people to read the entire thread, but if you’re not on Twitter, it’s essentially about whether money (and apparently anything else) has essential qualities, or whether it is whatever peoples’ narratives tell them it is.In other words, is money whatever your grocer takes for the groceries, or do particular forms of money have qualities wherein they are more likely to be accepted over the long haul? The argument is yes, gold, for example had qualities that made it a better money (scarcity, durability, e.g.) than say seashells which are reasonably durable but not scarce. You could sell the story of seashells as a money (and some societies not close to the sea used them as such), but ultimately such a society would be vulnerable to massive inflation should one of its inhabitants ever stroll along a shore.
The thread morphed into whether everything is just narrative, or there is an underlying reality to which a narrative must correspond in order for it to be useful and true.
The notion that anything could be money if attached to the right story, or any music is good if it’s marketed properly is deeply cynical. I am not arguing people can’t be convinced to buy bad records — clearly they can — but that no matter how much you market it, it will not stand the test of time unless it is in fact good.
In order to sell something that does not add value, meaning or utility to someone’s life, something you suspect they are likely to regret buying in short order, it’s awfully useful to convince yourself that nothing has inherent meaning or value, that “storytelling is all that matters.”
I am not against marketing per se, and effective storytelling might in fact point someone in the right direction — a good story can help someone discover a truth. But that storytelling is everything, and by implication the extent to which a story has correlates in reality nothing, is the ethos of scammers, the refuge of nihilists who left someone else holding the bag and prefer not to think about it.
-
 @ 104f6f7d:220bf499
2024-09-27 13:03:47
@ 104f6f7d:220bf499
2024-09-27 13:03:47“He is free to make the wrong choice, but not free to succeed with it. He is free to evade reality, he is free to unfocus his mind and stumble blindly down any road he pleases, but not free to avoid the abyss he refuses to see.” - Ayn Rand
-
 @ 44dc1c2d:31c74f0b
2024-09-25 20:15:13
@ 44dc1c2d:31c74f0b
2024-09-25 20:15:13Chef's notes
Last time I made this I subbed the tomato puréed with some blistered cherry tomatoes. Don't think I'll be using the purée going forward.
I prefer thighs so that's what I use for this but use whatever you want.
Adjust spices based on the size of your onions. If all you have is two massive onions maybe use one and a half onion or just up the amount of spices a little.
Details
- ⏲️ Prep time: ~10 min
- 🍳 Cook time: ~40 ish min
- 🍽️ Servings: 4
Ingredients
- 2 Onions
- 2 tbsp tomato purée
- 1/3 cup cashews
- 1.5 tsp Garam Masala
- 2 ish cloves of crushed garlic
- 1 tsp chili powder
- 1 tbsp lemon juice
- 1/4 tsb ground turmeric
- 1 tsb salt
- 1 tbsp plain yogurt
- 2 tbsp of your cooking oil or fat
- 1 tbsp Coriander (Cilantro) plus extra for garnish
- 1 tbsp sultanas (golden raisins)
- 1 lb of chicken cubed
- 6 oz of white button mushrooms
Directions
- Quarter the onions and put them in a food possessor for about a minute
- Add the tomatoes, nuts, garlic, Garam masala, chili powder, lemon juice, turmeric, salt, yogurt and blend for another minute tell its well mixed in.
- In a wok or a large pan heat your cooking oil and add the onion and spice mix in. Fry gently for around 2-ish minutes, stir frequently.
- Add the chicken, coriander, and raisins to the pan. Stir-fry for another minute or so.
- Add mushrooms and water. Bring to simmer and cover the pan cook for 10 min or until the chicken is 100% cooked through.
- Serve with plain rice and enjoy!
-
 @ e97aaffa:2ebd765d
2024-09-27 11:37:28
@ e97aaffa:2ebd765d
2024-09-27 11:37:28Ontem, voltei a ouvir aquela mítica frase, que se repete ano após ano:
«Se eu soubesse, há 10 anos tinha comprado bastante #bitcoin e hoje estava rico»
Quem diz isso não tem a mínima noção da realidade, não faz ideia o que era o bitcoin e a sociedade há 10/12 anos atrás. É claro que com o pensamento de hoje é fácil, mas temos que refletir com o pensamento de há 10 anos. As certezas que temos hoje em dia sobre o futuro do Bitcoin, nada se compara com o que existia no passado.
A situação é similar, ao acertar no euromilhões (ou mega-sena, no Brasil). É muito fácil saber a combinação vencedora do euromilhões após o sorteio. O difícil é saber os números, no dia anterior ao sorteio. Claro, se viajássemos no tempo, 2 dias para trás e apostar nos números certos. Assim é fácil de ficar rico. O difícil é acertar os números antes do sorteio.
Hoje em dia, já muita gente acredita no futuro do Bitcoin, o seu valor é inegável, podemos duvidar do preço, se vai valer 100k ou 500k ou 1 milhão ou até mesmo 10k, mas no valor, do quanto revolucionário é, ninguém duvida. Na época, como ninguém acreditava que iria atingir estes valores, ninguém olhava como uma reserva de valor, usava-o como uma moeda, gastavam. Também não havia cuidado em preservar as seeds ou as chaves públicas, porque ninguém acreditava que aquelas moedas poderiam ser a sua aposentadoria. Se hoje as pessoas queixam-se que guardar as seeds é complicado, nem queiram saber como era antes dos bip39.
Se estes novatos tivessem comprado há 10/12 anos, teria acontecido o que aconteceu a mim e a quase toda a gente da época, acabamos por ficar sem os bitcoins. Uns venderam(trocar por FIAT), outros trocaram(por outro produto) e outros perderam ( scam, hack ou ficaram sem as chaves). Na história, foram muito poucas as pessoas que conseguiram holdar bitcoin até hoje. Das raras pessoas que o conseguiram manter, eram pessoas que tinham quantidade muito elevada, que permitiu vender ao longo do tempo, mas ainda sobrou algum. São raros casos.
Quase toda a gente que entrou muito cedo, acabou por ficar sem o bitcoin, muitos voltaram anos mais tarde a comprar, mas apenas conseguiram uma ínfima parte do que tiveram no passado, foi o meu caso. É duro ter agora pouquinho bitcoin, quando tivemos alguns no passado, foi uma grande lição, a frustração transformou-se numa enorme convicção, que permite suportar tudo. Todos nós, em algum momento, tivemos ou vamos ter as nossas “pizzas”, como o Laszlo, que ao preço de hoje, custaram milhões. Isto também faz parte do percurso, para criar as mão de diamante. Agora, como as valorizações já não são tão elevadas, este fenómeno vai desvanecer, isto condiciona a utilização do bitcoin como moeda (meio de troca).
Termino com um conselho para os mais novos, não pensem no passado, mas sim no presente e especialmente no vosso futuro. Nunca entrem no bitcoin com o único objetivo de enriquecer rápido, porque vai correr muito mal. Estudem primeiro e comprem a seguir.
Se estás a achar que é tarde demais para comprar, nunca é tarde e acredita, que daqui a 5 anos vais ouvir outras pessoas com a mesma dúvida.
Nunca é tarde demais para comprar #Bitcoin, a liberdade não tem preço.
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ fd208ee8:0fd927c1
2024-09-27 11:32:25
@ fd208ee8:0fd927c1
2024-09-27 11:32:25A fortnight of being real on Nostr
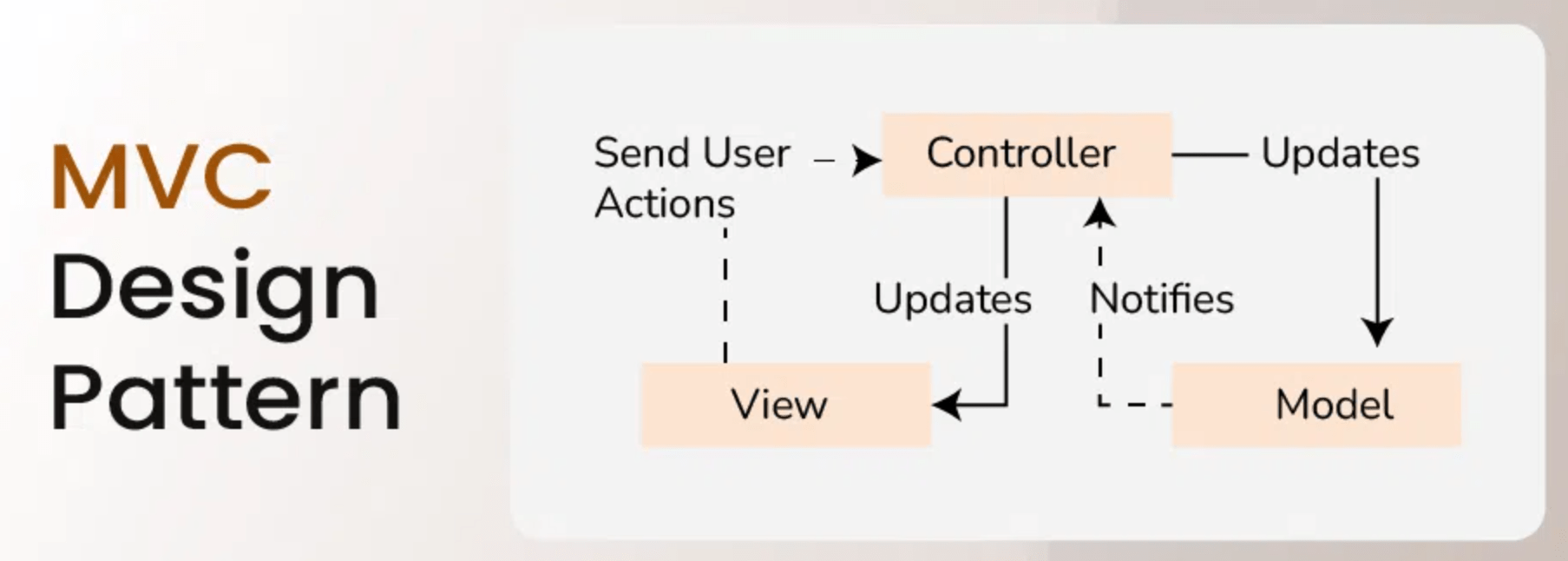
It's been over two weeks, since I announced that I would primarily be noting from my lesser-known Silberengel npub, and it's been an interesting experience. As with anything I ever do, I clicked around a lot, tested out a lot, and tried out a lot. Mostly, I observed.
Let me share, what I've learned
- Nostr-related products are increasingly useless, if you don't follow anyone, or only follow a handful of people. Everything is geared to follows and you usually really do need to follow gobs of people, to have an interesting feed, by capturing the most-active people (about 10% of the people you follow). Those people tend to quote and boost other people's notes into your stream, allowing you to follow those additional people and so on, like a snowball scheme. This means that follows are actually a feed-management mechanism, rather than any indication of a relationship between npubs. It also means that 10% of the npubs decide what everyone will look at.
- Many people collect followers, by being active for a very short time, following lots and lots of people and getting follow-backs, then they unfollow the smaller npubs or abruptly change their tone or the content (this is common with spammers and scammers). Then they have a high WoT score. What, precisely, is being trusted here? (Also, centering WoT on follows is influencer-maxxing for plebs, KWIM?)
- Why are individuals never unfollowing these npubs? Because nobody unfollows anyone who hasn't seriously upset them. Follow-inertia is rampant and the follow lists are so long that most people don't even know who they are following. So long as the "bad npub" doesn't spam the people who are following them directly, they don't notice anything. That means following spam can inadvertently protect you from spam, whilst the same spammers throw crap at your own frens, all damned day.
- Most relay owners/operators don't ever look directly at the feed from their own relay, so it's usually full of enormous amounts of garbage. Your clients and personal/private relays are often downloading and broadcasting all of that garbage indiscriminately, so the garbage gets passed around, like a social media virus. Many of you just haven't noticed, because you also don't look at the feed from your relays (see 1).
- Almost all business logic (the controls, in the classic model-view-controller setup) has been placed on the client-side. This is great, if you're a client developer, as it makes relays superfluous and traps your customers in your app, by making moving to a different app more onerous. Every move requires a period of readjustment and fiddling, before they can see their feed the way that they are used to seeing it. This is less great, if you're a user and are interested in trying out a different app.
- When I began, two weeks ago, the concept of topical, private, and personal relays interacting were mostly a pipe dream (pun intended), but I've been pleased to see, that some other people are beginning to catch on to the appeal of decentralizing and specializing the model layer. A diverse, sprawling network of relays, connected through the outbox model and negentropy syncing, is really next-generation communication, and essential for ensuring censorship-resistance, while supporting smooth interaction.
- Once you get above a few hundred followers (which I already have, That went fast!), additional followers are increasingly spam or inactive/bot npubs, and once you get a few thousand followers, that Bot Effect goes parabolic, as your notes are spread more widely onto spammy relays. You won't notice, yourself, as anything over a few hundred becomes Some Big Number and you'll eventually stop even looking to see who they are, or caring about them, at all. Which leads directly to my next point...
- The number of followers a person has, correlates with an increase in their disdain for people who care about follower counts, likes, reactions, or even zaps. This noblesse oblige says nothing about the usefulness or information any of these signals carry. You will please also notice that they never change npubs and rarely change profile pics because of reasons I don't need to elaborate on, further.
- On-boarding is a lonely experience because nobody looks at the feed, and you initially have no followers. Even if you reply to people, they often can't see what you wrote because of your low WoT score. That is, unless you already know someone there, who can vouch for you. Or are lucky to get discovered by the Nostr Welcoming Committee and end up one of the biggest npubs overnight, which is like winning the follower lottery. For most new npubs, the experience is terrible and they eventually give up, for a handful the experience is absolutely fantastic and they are hooked. Obvious lesson: nobody should onboard, who doesn't know at least 1 other person: so invites only. Unlike Those Other Protocols, Nostr doesn't need a centrally-determined invite, as every client or relay can offer their own version, geared to a different audience. The goal simply needs to be: get off 1.
- I don't get many zaps or reactions, anymore, but I still have interesting conversations, and I no longer face the surreal situation of every cough, hiccup, or sneeze I emit being front-page news. Nostr feels more like Nostr, again, and less like Twitter, and now I want communities and forums even harder.
-
 @ 7ed5bd1c:4caa7587
2024-09-27 09:43:50
@ 7ed5bd1c:4caa7587
2024-09-27 09:43:50การอ้างอิงใน MV "Heavy Is The Crown"
ผืนธงเปิด MV
-
T1 vs LNG ใน Worlds 2023 Quarterfinals ในเกมที่ 2 นาทีที่ 30 ไฟท์หน้า Elder Dragon ทาง LNG ได้พลาดท่าเสีย Scout's Jayce ก่อนที่ Oner's Rell ได้เปิดจังหวะใส่ GALA's Apehelios และปิดเกม 2 ได้อย่างสวยงาม อ้างอิง: https://youtu.be/sClE_FbT4X8?si=3QaBU2JXYEbCusHb&t=261

-
T1 vs JDG การกลับมาเจอกันอีกครั้งของ Faker และ Ruler โดยในปี 2017 SKT พ่ายแพ้ให้กับ SSG 0-3 เกม ในรอบชิงชนะเลิศ และใน Worlds 2023 Quarterfinals ในเกมที่ 3 นาทีที่ 29 Faker's Azir ได้แสดงการเล่น Azir อย่างหนือชั้น ได้เข้าไปอัตติเปิดใส่ Ruler's Varus พลักเข้ากลางไฟต์ ก่อนจะเก็บ JDG หมดทีม แก้แค้นคืนจาก World 2017 ได้สำเร็จ อ้างอิง: https://youtu.be/qDFAYyMOxuw?si=afKAKyWqDnSp9tiF&t=733

-
T1 vs WBG ใน Worlds 2023 Quarterfinals ในเกมที่ 2 นาทีที่ 24 Zeus' Aatrox ถูกผู้เล่นของ WBG รุม 4 ต่อ 1 แต่ก็ยังสามารถยื้อชีวิต จนทีมร่วมทีมมาช่วยได้ทัน และสวนกลับเอาชนะเกมนี้ไป อ้างอิง: [ https://youtu.be/g3NcF5Uv-w4?si=WysYNIQIS44JMY_U&t=616

ผู้เล่นที่อยู่ใน MV
-
BLG Bin ในศึก Mid-Season Invitational 2024 (MSI) กลยุทธ์การเล่นของ BLG ที่เน้นความดุดันและการสนับสนุนของ Bin สร้างความกดดันให้กับ T1 เป็นอย่างมาก จนทำให้ T1 ต้องพ่ายแพ้ 3-2 และลงไปแข่งในสายล่าง ขณะที่ BLG ได้ผ่านเข้าสู่รอบชิงชนะเลิศ

-
FLY Massu ผู้เล่นตำแหน่ง Bot Lane ได้กล่าวถึงประสบการณ์ของเขาที่เล่นกับ T1 โดยยอมรับว่าการเล่นกับ T1 นั้นเป็นเรื่องยากมาก เพราะเมื่อ T1 ได้เปรียบแล้ว พวกเขาก็ไม่ยอมปล่อยโอกาสให้ FLY กลับเข้าสู่เกมอีกเลย เขาอธิบายว่ารู้สึกเหมือน "กำลังชนกำแพง" เพราะไม่มีช่องว่างให้ทีมเขากลับมาได้เลย

-
RED Brance Brance ผู้เล่น Bot Lane เขาเป็นตัวแทนจากบราซิล และในบางการแข่งขัน เขาแสดงฝีมือยอดเยี่ยมด้วยแชมเปี้ยนอย่าง Zeri ที่ช่วยทำให้ทีมได้รับการยอมรับในวงการระดับโลก

-
G2 Caps Caps ถือว่าเป็นผู้เล่นที่มีประสบการณ์สูงในวงการ โดยเฉพาะในยุโรป ความสามารถของเขาในการสร้างจังหวะและการต่อสู้เพื่อชัยชนะ ทำให้ G2 สามารถแข่งขันกับ T1 ได้อย่างสูสี

-
GEN Chovy ความมุ่งมั่นของ Chovy ที่จะชนะ T1 โดยเฉพาะการต่อสู้กับ Faker ทำให้การแข่งขันระหว่าง Gen.G และ T1 ยิ่งเข้มข้นขึ้น เนื่องจาก Chovy และทีม Gen.G มักเป็นคู่แข่งที่สูสีกับ T1 ในการแข่งขันระดับสูงสุดของเกาหลีใต้

-
โค้ชนักแข่ง Roach และ kk0ma ถือมงกุฎไปให้ Faker

siamstr #yakihonne #Worlds2024 #LeagueOfLegends
-
-
 @ a03b38f8:2c7ce1f0
2024-09-25 16:11:17
@ a03b38f8:2c7ce1f0
2024-09-25 16:11:17PROTECT YOUR HOME (NETWORK)
This is actually a rather large topic depending on your needs and how far you are willing to go. I will most likely have to put out several posts on this topic. For today we will start at the very beginning and build from there.
This is going to be more of a beginners guide but that doesn't make it any less important. First you must get your home in order before you can do anything else. If bad actors get access to your network then they can use it for illegal things that will be tied to your IP address, use it to launch a bot for a DDoS attack, gain access to any of your home devices, or just hangout and watch you log into bank accounts or whatever.
I will be blunt, your home network sucks. It's slow and unsecure but we will be fixing that.
I. EVERYONE
- WHAT DO YOU HAVE?
Somewhere in your house you have either a phone cord or a cable coming out of the wall running to a box. Go find it. This is your modem, it "translates" the internet signal from your ISP to your house so you can use the internet.
Found it? Good. Now is there a cable coming from the modem to another box or do you just have one? This other box is your router, it is pretty common now that you will have a all in one modem, router, WIFI, etc. That's fine. Write down the model number of the router or all in one. Also there should be a sticker on the side with the administrator password (sometimes listed as access code) and maybe the WIFI password. Also look if the IP address is listed as well. You will need these for the next step.
- LOG IN
Go to your computer and fire up a web browser. Enter your routers IP address if it was listed, otherwise we are going to have to find your router's IP address.
In widows and Mac you can look under Network & Internet, scroll down to your internet connection and look for details or properties. Inside properties you are looking for something listed as default or gateway or IPv4 DNS Server. It will be a 192.168.X.X number.
Or you can open a command prompt and type: ipconfig /all
Or you can just do a internet search for your router model number IP.
You will know when you get the right one because a control screen for your router will pop up in the browser.
- UPDATE
First thing first check if there is any available updates. This could be it's own tab or listed under device or in diagnostics. If it asks you for a password use the one that was written on the side of the router. Install any available updates. Honestly they rarely update these things so if there is one then it must have been pretty needed.
- CHANGE THE LOCKS
You have to realize that this device is the front door between every internet device in your home and the outside wild internet. You are probably blasting WIFI signal all the way to the street. All someone has to do is connect to your WIFI and then they will have access to your router as well. The default administrator password for these mass produced ISP devices are not exactly secret. You can even find lists of them by brand. It is like locking your front door but leaving the key under the mat, not very secure.
Look in the settings and change the administrator password. Use your password manager to generate a 10 word passphrase. Change it to that and SAVE it in your password manager.
- RENAME AND CHANGE WIFI PASSWORD
In the settings change the default name of your network to something memorable. Do NOT use anything personal like your name, address, or router brand (Netgear or whatever). If you want to be cute you can use: Not Available, or Network Error or something like that.
Now change the WIFI password. Again use your password manager to generate a passphrase. You can cut it down to 6 words since you will probably be entering this one much more often. Be sure to SAVE it in your password manager.
- ADD A GUEST NETWORK
You don't just give your WIFI password to all the kids in the neighborhood that swing by to play with your kids or to your friends visiting do you? If so, STOP it. Setup a guest network. A guest network allows people to have WIFI access at your house without giving them access to the router. Yes I know we put a strong password on the router but it doesn't matter.
Setup a guest network with a easy password. If you have given this out to several people already that are coming back often you can name the guest network the old default name and use that default WIFI password. When friends and family come over their devices will have that name already saved and will connect automatically. This way you don't have to do the whole song and dance everytime someone comes over.
- CHANGE YOUR DNS SERVER
DNS is the Domain Name System. Remember the IP address we found earlier for the router? Every device connect to the internet has a unique IP address. Every server hosting a website, etc but luckily you don't have to remember 142.250.188.14, you can just go to Google.com
This works because behind the scenes your computer is checking with a DNS server to provide a human readable address instead of a bunch of numbers. The equivalent would be a phone book that gives you John Smith and not just a address somewhere.
There is a little bit more to it than that but you don't need to know all that in order to grasp the concept.
The default DNS in your router is probably the one provided by your ISP. Your ISP can see everything that pings against that DNS server and probably uses it to feed you ads. The DNS server provider impacts how a lot of your data is handled. It's speed, it's security, how it's logged, shared, and sold.
So change your DNS server. The default one your ISP gave you is shit. It will improve your speed and security but just remember that privacy and security are not the same thing. The Google Public DNS (8.8.8.8) is very secure and a good choice but as you can imagine the privacy is not really great. But not to worry, all the data they are collecting is anonymized ; )
Your best bet is to use your own DNS server with something like Pi Hole or Adguard home. Setting that up is a little bit beyond the scope of this article so I will cover it in greater detail in a future one. Until then Cloudflare (1.1.1.1) is probably your best choice until you run your own.
Now you have probably better privacy and security than most people with only these simple changes. Next steps would be to upgrade your hardware for faster internet, better firewall, more control, etc. Will detail in future drops.
Always Forward, GHOST
-
 @ a03b38f8:2c7ce1f0
2024-09-25 01:04:52
@ a03b38f8:2c7ce1f0
2024-09-25 01:04:52-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQv/clUvo/uJPS2NodjoiSskIjK+IQkSzGxjGCEPO6jzRBVK zY+rCNUEEv6i9EB4PAeihLEQREBm3zZqLsG9OeVnxIy0AWLQcBrH4WHQuIlRfii7 7SifuNky5LkBcguKVBe9NWDAmzgMP+Y8KKUTSeMUF1qNUPKKGCezvrjAjSojDvQK Jh4sewLMMI1ALihduxKOwLaZpinqyubOQz9LOB2oZg1xLpjXkGNbLQbsT3Aa3/dj MAojIp6qG8mERTtDB9C0ti+dNTn0mYtQPblHSZR38Ze25YYhYunRIlSUjPmI2233 VgTYYW3V9mci3v6tMdvO/lzgGVpb2EaqT0wxU0EqoM4knu7JFq0oqfGqtD4Wr4ro QnHuUprjH8qYFa4fpXTnY9f0OKxOacsBQenHvG9AQH+XZ/mSFcpUjZQJQmb0SYzK ZiWo6t3hIjg6lX/eXg+PixkgljLpbdIOZZb9PHK/aLfr47lEf0hCGfEptda1CZtH v377/o/psGdL2nYQdpab0tFNAYwDa7LaaxSYix6XU/8ew7Hfp0upIPE0SDxzKBJ2 +qlcIVxthOKoIjD0wnSy49UjqJGPFm4X9yfZUEtWqXr622cIHMmkmL3gm1xi+FSt /SVs3X5zypDYRxDilOeoimW1Vh1J0aQAWCMDPo1MuGkgZ6SdQ5sWOUnmBcGdhPWw DkXfkz5PL4tWrQxQiuUWbaXGDH0OTAYGc5LjFsZhMVE4hdJ48Gli70joIdrZUiSr MHGBdpQQtZFMN7xdWpag42aHxObnHvGP+NhIBT349Lp+/sfnFvQ7nPGhBSOI//va 6H/AtwVgWDM+J1KIdE/phgIPhGG3x8xGb4Lg8WB3YbBmJtTFO0G+ni8KjnZ73tvY o/U2bZseubIuVccQPt0igy8zSXb/FLuRF7Ns1ZRZnrs66Au+QzpvX0Lcyi/6JTDV 1OAC18PHWmgtKktfKD1D4y9CRMaBrgK9AFYPKONkxc4unnyotYgkPKgXsuENKde1 4LtBb/Atj+REalCgezGoyvp5jck5+SBSug29/csijUZBliv2iaiZ0dhEbMVB1rvo ly4n7CgKEoC4FPVsqiUOyOHkU8YqoUfeBz65MbtiALKBymmDvw8tSQnNA1LpnW3R In052B5akP2xE2/h2WXaxgDyR9gu2z+BkK1TN2tcSkrZ+SIauuyeAicXbjqBAuqW fJ1WOxgg5Rj9DCUS08e03CRSMYFQVVf3F1kFc6lsc4Y8tqvPQZiF9dOd8dGnpo76 5D9l8f7YwyuwkHlJ7oPTnCCpOIWvcUEVDmwDd2j4pEGMVA9K/IF02sjRCDG4Ktap VxosdEBWWJyQLz6USb17w5nRJ8yqlM3nv6zYak1G4e0Y9SPTeMKDFnw9z70/LGMI r1YTeWXrGA3qvaU1G36GOUZov7g0JLgffafJ+yN5Qccqn3EtIwHEaL6MLr6VOjoy M/pL0tadnxo+qkyOWpo/V5sz/MvoXvPO2f+LNy9POOVQaz8KMJB3gieJilJpCNIs 54N9ciu8Qe5A7oeD4PJ1GE661RLoaZDth3lq5VclNW+bcWr3Hd/mWTN1TnrGt1K3 E0PT+2B/m0UPVUrIFb/ZrIng27x8oKuNTa0DyyKtVvuOZl8DjXmtrN/yHI8rPTI9 Xa9Gfbf/yxcKUIEWGSM0Ujmrt2MoqnYR8rplNWXSBSRblwP2UfrC2C/hEVmc4KA+ DxCahylqF3LJNiG/0IHHXTd6g7gl2AuQIfaCVGy7x6OADQnvM4QlcPXkgcGrXqpp prnhE6W599Y+lvO80Ng3u2sQb9PgauWf62NMLochN66Hi6Bl4Ge0S+mey0/vNmvO K8IBwYxix/pQ7xKFyuI2OKOkBqPEMmvSLCMYI+3qa/r91S7R0GNuX7cZHU1mRNcq 21GSpgnjG985Rb5UzWrfk2HgDM9rgNuQ8o0NTiv8gYZlQWegsmczdAu5vZX9/48/ TnSNIVjfImDLEhXHTi5K2++Km8bVjYg1/gTV/dfrQ58sNdbnc2wzzCbdQ5/NxSHr 1m8h+0TzyWhNIKEWoZctk0qJKnXMfMcsxuju4zREPclm0l311yTauO7up9A/ogjB XhInGpHt4KqQ/GiIjweJPWYc/m9XwTCfRvq/JQCwv23TX6dfRDR/AKqJ8mo6VWZr rD9mpr+r85kS3Z0WFcN8CjWB5Za6Reo1XFeTdReNdsefEipmrnHDleU8NBVF1YZU 294hGSGpu5hn6arpWBg/CUK9SqkSrYePL3hCitjLswvP+rVxg2jHSUY2TPt8/6kg GaBxt3dn0ENHlPSbOk0nT8ik4pwpbdg52oOjohJOjXE+nQIXA5apOtVoGy5O5h9r mQn2eQZ5hLrqIhW7kU9mqW4XXtTEns5AcNtwGLoNpd1DMR6rGnkXSozStrPzovp4 lRTpOa4NsuFcUd++HlJHCVw0tXKuYttMcqwT4/Bt70qwtpZKueo7fcqbkLW5068Y RoRy5fUoYUlaHqLwT9TgWspR83xLjKViZqoVtZjxaKE8uRTh39JtFfw8jSM2BFRL rW+AHGm3SZnwYyOQUXbd4rjx89rHs7042QUGCJU61f7CBdYxfgshFA69Uew84O6r DTlYdSPcn5XKwWbZlt9/qkGfRem4L0u9W4YQevVmg8id23GI5z8O8FvMlqJ/2DKM ggYL5CAyUMs05pK2h9wC2oHgoGNy/4r3aoY4pyJR/LIVjW2zYTfK9t+Kbgy2RK4S 9ogGs7tWfOCy+sUyZMKwl8FLjQvttfDu9j2L8hAF0usPS8yLujihc1px6Mu/TyT1 FpBXE6dXRPMV9vNLB6EEEMvsWBjAkw32jI69jJoGBEKeyRFlAvTkYps6bJeW/4U/ T6RfLV4AqSD/p6k64TdOI4QYAXeIkwDFYG0TiwIr09cLzkRKEMlkzOzfpRbJPdpA taNHta1yPDr3sLOBF1CfilFF0HlXkc5+Foj7J9gPEfE3YaXLjuws5ejsHQF7Tjri sba0WBH4vhTK8c9KceV5oSo82oZSUcAylrufyxXEcmMWuY1OZuLeYIGNIDhlXRpR pJLpZZ6eCn6foAvRgmRHjth6A9sJ4X9t3Zh0YYo9jsIssPfSlcEhQ9acOe2jVjYk iDxBZiQA+X7GguRDH2zj9nW6fKEDfWWKpjjfq3yRd4wVfa0XChs8hKFURYRCJnZa eHUSjgqZXsVhk0J8FCBTyMsL2s5ePhrvKgxC5jqMjznv0B5CQRw0qoRwPWM2aEO1 hnT9smHehCiadCT9GVNMGQj1NSwOH/4dzDm8utt7XssbagUF2Fn+pDUphKYFJV7k WJIQNpQTC4IHzqjF+NipjAxxmUrSaCqyWLAy4WYJ0u7uAhU+6LoQ4wvQQTxWapbf w/sc2ua8IOxh/BwCB7vq32gYnskwkWJB6DQg1PqjRYwqJzOCETYlfVklqswbxIjP po6KHjlGzRAi0pfipQiQfAjMDIqfGMucNYO9k81aOMzBpp0KcOqaKB9FO3CUZnfi s7l0Vh0EA0dvrl0Qpp5xi1K8zKtF+TtjDmg/M4l5i9VB3Lpl1lOKlsDgFUee+g3d UdwORMjByrFBLIGe0+Rmo/Gak4rrk5QH/ErIMeJumhWcwlwCfr00s7QGY09LKUzd mQGL1MK+4w4HiLe+kdbHe0frcdjBiDEuZReW+SGKPdMrvWEsy4yr2JfIQ4NmbHD7 EdOZmojCOWkJAnbz/pZ59O/BJbuRRlY0MVdxfw0foXnINteMVmJ0JUYg/YqB2J7+ 2MXhyqTCiiJcziDU6s+9Gm2PWP8ihkgwrlfjG5bOWBRyGyaKT1ryMvP0+4J2Q8Vd dbM0zEwk8JwW2Snro3vinVPxA1vrEnkQ5TJUZuJqCasgEL5XaOXRtdOJCa9FDGIo UEz2IyN8G2MrHAzxB2SQ8kshycUsDp3K1tJYt+GeDmkWi0owYEFkb7cbHtbY33Kk bRZBS8ghwXIp8hy8AXXerIFh6kzENcP8P+jpHRBw4WWZ/k7Tp9fXxjkFnXZjQ24s wkiBz+kUN3FdZJOlSggiQDSntN0D2cApF/+NVTwQp4rZBWTw8e0PuJs2vne9vh3L eNci6g2B1Lxf6jWa9eZgcqQYZCtLl6ClVQM879jZo2o1+I0ta3S2p6u53llf10Pf Ad0vfj5AhBAkMbSvrgCiFyiMpjO9mIKpF/47XtyVEdcF1bx8ul5eewWTMrK7PMsn aTrVqwlmfQa8qPtuQr2OKsdKR//UlM0dSoyjQai2vZPyAosgbjiE9khAaKBKJaeK OC6gFPQemmGc4hVlGB0Cs+Dubg0OCoqpqOPitLh6TBCwqHcNso1Uz/qf7YsdKdJ5 6A3J1w7HV6f/FJSNZ7dPU1nFuWiJfMwn/1hGbQaWM/Ln4EQIDjspJYZTtY/8BOhI L4RJeU6vNTm2trmumgBKGuovSq1vZ/UWxEJkXCK9N+W2cLl7A2u8vkkCLj5oxr3y ybDvfd7kPZ+aZSW6Y7eA5CWehsh5PtJMtOaNGfCl6jynCj8xG1NKxWzewKv9Gs0E TM7+QqXrmuANuGYT0h5xlO7bXJpwynKX5mzvNuuq9kzUoikj2ucoVxKvhMi73Jvz 7I0EjJFXER30EovOdL6V9jAUk9eITx3cGQ/acHGnUVK7Ncq/bWd4/P0StQeINdN5 8TgUjKS0Wc4Y5gstdJXnJcQx3/pXSQAvsujgDQGWQCDxEU1t6YKu7UNuZG0gLmYi ZyRXKbKzlw10Tm28608D+zMJ/ZlJenqohm7g4YQV7T7/glZKFbqx1q2Inw67aLdj zr2m5KU1Adert+KfDKA6PvwBHGOPBkza0z1EdG2ft2xA6HjQfbRyNO+7iCwesJb4 54qGc9apW4+facRCNgQVCtEG9h2yrnqmDG8k3poSQagHaRUM0+kUq4g+ABPEi1/G xr6hkKmoniD9vmZKveyIzjuDXtMcIIezUCttDI5rssct2tIGBBq9uckduWb8dw+1 fWoje3NxxSiogQCeXrZLq8T8viPz3b/SpQHBpa8PfJ4+ljCH6Fzf0Jf5r3aViVb/ G8BxXuU5UdSaCs/MVdgLyrJWMpMoOTawXomEdl6Sty8BSn3kJPJ3WXK9tUIyyeg6 AvX+IJ22UldmfrhYu1+PI4hLz2GHY/NR5KT4VIUaYfSknnzhfj+dRGSSoT8H5ptM P58t0Zb0CwGwu3q3YsNosahnYo4d5eS1h39GbO1Bd4hSQkjbQ04aDYl1qIdXtaII 2ydLgWiWgCS4w7fsHohmvibOxCnGBblhY0bA9PlMUU4FX6VyS2DkrVcsltPX1+ZL cjmZiwOFzyiX6pYWuv8n7uWVW/tylWEsrxoSRYP2Ey/4HDHZ7F8AuCt7ouaJBoLW AksJt76BlYJGI7RS9tsjl97Jxi2gp2P4dAi5J95MQSGBWw5S60e9luMbR9yw8kHb 8TLEYxKfNdj6Uq0Phqa5tEkiU7UwttW2VBXS6fgyEYYcWcbruNs+T142VRhnGaTw CnoenePc7aFK+h+8bBP2PCJCTLNigM3dfJ3Zd4ch8xA3oKj9rxjDy6bh4HvOHsHP eimWuDNMKUvZ6tTQcN0Nl+MpqUgDqItmrkZB1wCNmitKzbEBN3uIGTpFtDHVupLb 4XyvlUwqdGhJrcPdUZy3JjulTkaGbuujg86JY0CCgLdVUyqofGI5YgKOx4x2L4RJ bxHb01iByLslLhG120Np5IkK4qSn9MGovQaqkoWm3ADFBSeFQGiTyemN4OPoKSZN mQAwp1dyNf7K7m6FlG5PHWXH3m2td4R6v2EHWN7IM1V5WqwG29wSCkKNjAKA0TZR K1Hy+bZDL0o1m2OwMhQvGY9oIpQr2rfTSWdknE41WR8Eqdg365ftWnQje+IEpKQU kyUfbKMd7iBFhM38OA2nSajugCbt5e/t5GoTMDvXXkKbpmIfpKk/rpBdxmkjDNFV ZgQ6tc/ySqft2+pmzj3g8vfDDzKMRN6W/q2N8TXc1tkcVqPOfjId97o5TTW+L8ME sQdKtssQGe9ICOJbXd1XM2AllrVZtsMRDe+4qxrky865p/qVNaJ+laotdNV7glJT 26PHqHlHWJN1mONoiLCaiqYRyNygsIc6fANIEKbEJxjdjW7mq579IYu0QAbsITwc NW7IAomk4vz5YVPEJIr/i1twERWn9IYvDjMroO1U1D7P3/Z1sE+xtU/0HVvvXLoD GD79KIr9nUDJTKKZyefy00piEyBJz9gHdJkryqBuAaODIPrWSs5nNS+MJc6fSv6j aQJdFcNQGuoIYtjHF1lz4cMSjd8pJlADIwrLt28NLL+Y/wHT6WUzpsWIOxwgJolL EnNDOaCBDk17CDoKWoqvT8RfYwUvtpK4QrEtLwOygEcObIaSjrMDkPropZRbiT+i dDQIK8T85ggYNrb9XZGwVbKEMiOnTxgsa/mxykAwi7Xp+5FDKS6HJS4QvE45zZY9 4j3azT3sqv9NIyTZKFnjLFIxWez5I+PWupuFY/oFC81kFvTI/OtJcNqKRIRlfv7M h/LNKrdmsJ4JC+Jn+SCZ5BXD/q/aaWPSzXgSMTnXOtTNi0Nsxp7roUuPZjvXt/s6 WyPf4qpN7GtBF1htg0uVfdSO2B9eVi+xU4Ly7uR+G+yI4oUDbHx3oBdoIoExwBRm Mu+arV9ELEkpHmidEjFuM1AB1C2gRH+H2mghF4Axxw== =6MjS -----END PGP MESSAGE-----
-
 @ 8f69ac99:4f92f5fd
2024-09-27 08:55:34
@ 8f69ac99:4f92f5fd
2024-09-27 08:55:34Os Millennials e a Geração Z estão a sentir a pressão. Dívidas estudantis esmagadoras, o aumento do custo de vida e salários estagnados têm levado muitos a questionar o futuro. Ao navegarem num sistema que parece estar contra eles, não é surpresa que um número crescente procure soluções que prometem intervenção governamental ou até mesmo o socialismo, na esperança de encontrar alívio.
Mas e se o problema não for o capitalismo ou o livre mercado, como muitos são levados a acreditar? E se a verdadeira solução estiver noutro lugar — algo que oferece tanto liberdade financeira como clareza moral?
Entra Bitcoin. Mais do que uma moeda digital, Bitcoin representa um novo caminho — um que pode proporcionar poder económico ao mesmo tempo que nos liberta da corrupção e do controlo do sistema actual. Vamos explorar como Bitcoin pode oferecer aos Millennials e à Geração Z a liberdade financeira, moral e espiritual que têm procurado.
As Lutas Económicas dos Millennials e da Geração Z
Num mundo que celebra a inovação e a educação, por que é que os Millennials e a Geração Z estão a lutar mais do que qualquer outra geração anterior? Apesar de serem os grupos mais educados e tecnologicamente avançados da história, os jovens na casa dos 20 e 30 anos enfrentam desafios financeiros que ameaçam as suas perspectivas de longo prazo.
Desafios Financeiros da Geração Z
A Geração Z, nascida entre o final da década de 1990 e o início da década de 2010, está a enfrentar uma verdadeira tempestade financeira. Dados recentes revelam que:
- Declínio do rendimento: O rendimento médio para jovens de 22-24 anos no 4.º trimestre de 2023 era de 45.493 dólares, uma queda de quase 12% em relação aos 51.852 dólares no 4.º trimestre de 2013.
- Dívida crescente: A relação dívida-rendimento para a Geração Z aumentou para 16,05%, enquanto a dívida média de cartão de crédito é agora de 2.834 dólares.
- Stress financeiro: Um impressionante 45% vive de salário em salário, e apenas cerca de um quarto acredita que se reformará de forma confortável.
As principais causas incluem o aumento dos custos de vida, dívidas estudantis que rondam os 31.300 dólares e a inflação, que tem corroído o poder de compra.
Desafios Económicos dos Millennials
Da mesma forma, os Millennials, nascidos entre 1981 e 1996, enfrentam as suas próprias lutas:
- Cicatrizes da recessão: Ao entrarem no mercado de trabalho durante a Grande Recessão, muitos ainda enfrentam insegurança no emprego e salários mais baixos.
- Dificuldades habitacionais: Tal como a Geração Z, confrontam-se com a escalada dos preços das habitações, sendo que muitos não conseguem encontrar habitação acessível.
- Incerteza na carreira: A economia dos “gig” cria um ambiente de trabalho precário, dificultando a estabilidade.
Estes desafios são exacerbados pela desigualdade de riqueza, dinâmicas laborais em mudança e a pesada dívida estudantil.
Factores Contribuintes
As forças por detrás destes desafios económicos incluem:
- Aumento dos custos de vida: Os preços das habitações aumentaram mais de 50% na última década, o que pressiona as finanças dos jovens.
- Dívida estudantil: Níveis elevados de dívida continuam a sobrecarregar ambas as gerações.
- Inflação: A erosão dos salários reduz ainda mais o rendimento disponível para investir no futuro.
Estas dificuldades económicas são sintomas de uma mudança cultural mais ampla. À medida que mergulhamos mais profundamente nos próximos capítulos, exploraremos como estas transformações estão a redefinir as noções tradicionais de trabalho, riqueza e segurança.
O Apelo das Narrativas Marxistas, Socialistas e Globalistas
Nos últimos anos, os Millennials e a Geração Z têm sido inundados com uma cacofonia de narrativas económicas que culpam o capitalismo pelas suas dificuldades financeiras. Esta narrativa tem ganhado tracção nas redes sociais, nas instituições de ensino e até entre alguns políticos. No entanto, e se esta perspectiva for fundamentalmente falaciosa? Este capítulo defende que os verdadeiros culpados pelas dificuldades económicas destas gerações não são o capitalismo em si, mas sim as políticas e instituições que governam a nossa economia.
Culpar Erradamente: Compreender as Verdadeiras Causas das Dificuldades Económicas
Os Millennials e a Geração Z enfrentam desafios financeiros como nenhuma geração anterior — dívidas estudantis esmagadoras, habitação inacessível e salários estagnados estão entre as principais barreiras à estabilidade financeira. No entanto, muitos são atraídos por narrativas que fazem do capitalismo o bode expiatório para as suas dificuldades.
Políticos e elites frequentemente afirmam que a social-democracia e a intervenção estatal são as respostas para os nossos problemas económicos. Argumentam que o capitalismo é um sistema falhado, culpando-o pela desigualdade e pela pobreza, ao mesmo tempo que apresentam o socialismo e o controlo governamental como soluções necessárias. Esta perspectiva, contudo, simplifica em demasia uma questão complexa.
Na realidade, os Millennials e a Geração Z não enfrentam um problema de concentração excessiva de riqueza nas mãos de poucos. Enfrentam, sim, uma falta de mobilidade económica e de segurança para todos. O problema não é que o capitalismo seja injusto; é que a nossa social-democracia actual gerou disparidades no acesso a recursos e oportunidades.
A Realidade: Não Vivemos num Mercado Livre
A narrativa de que os Millennials e a Geração Z enfrentam dificuldades financeiras devido aos defeitos do capitalismo é fundamentalmente errada. Na realidade, a nossa sociedade opera sob um sistema de social-democracia, não sob princípios verdadeiros de mercado livre.
Sistema Actual: Social-Democracia, Não Capitalismo
A sociedade hoje está mais alinhada com a social-democracia do que com um verdadeiro mercado livre. Temos uma forte intervenção governamental, proteccionismo e capitalismo de compadrio que favorecem grandes corporações e elites políticas em detrimento de pequenos empreendedores e negócios. O planeamento central das políticas monetárias, das regulações e do controlo dos mercados frequentemente leva a desigualdade e instabilidade económica.
Culpa Errada no Capitalismo
Os desafios que os Millennials e a Geração Z enfrentam — como a crise da dívida estudantil, a inflação e a habitação inacessível — não são produtos do livre mercado, mas sim da intervenção governamental, de políticas fiscais falhadas e de medidas proteccionistas. A crise da dívida estudantil, por exemplo, resulta de políticas governamentais que incentivaram o endividamento e, ao mesmo tempo, inflacionaram o custo da educação.
Da mesma forma, a inflação e a habitação inacessível são frequentemente causadas por políticas governamentais que favorecem certas indústrias ou corporações em detrimento de outras, levando à distribuição desigual de recursos e oportunidades económicas.
Bitcoin como Solução Económica
Bitcoin oferece uma alternativa ao sistema falido que os Millennials e a Geração Z herdaram. Como moeda digital descentralizada, Bitcoin opera fora dos sistemas financeiros tradicionais e oferece um conjunto único de benefícios que podem ajudar a enfrentar os desafios económicos enfrentados por estas gerações.
Princípios de Dinheiro Forte
A oferta limitada de 21 milhões de unidades de bitcoin faz com que seja imune às práticas inflacionárias dos bancos centrais. Ao contrário das moedas fiduciárias, que podem ser impressas indefinidamente, a escassez do Bitcoin assegura que este preserve o seu valor ao longo do tempo. Este princípio de dinheiro forte oferece uma protecção contra a inflação e ajuda a proteger a riqueza individual numa economia onde as moedas controladas pelo governo perdem valor.
Preservação da Riqueza
Bitcoin também é uma poderosa ferramenta para a preservação da riqueza, especialmente num ambiente económico volátil. Enquanto investimentos tradicionais, como acções e obrigações, flutuam com as condições de mercado, o valor de Bitcoin é, em grande parte, independente das políticas dos bancos centrais e das economias nacionais. A sua natureza deflacionária significa que, à medida que mais pessoas adoptam Bitcoin, o seu valor tende a aumentar, proporcionando uma protecção contra crises económicas.
Bitcoin como Solução Moral e Espiritual
Para além de ser uma ferramenta económica, Bitcoin oferece uma solução moral e espiritual para aqueles que estão desiludidos com o sistema actual.
Descentralização e Ética
A natureza descentralizada do Bitcoin proporciona um caminho para que as pessoas controlem as suas vidas financeiras sem depender de autoridades centrais. Esta descentralização promove transparência, justiça e resistência à corrupção — valores muitas vezes ausentes nas instituições financeiras centralizadas de hoje.
Uma Solução para a Corrupção
O protocolo incorruptível de Bitcoin impede que qualquer entidade o manipule. Ao contrário dos sistemas tradicionais, que podem ser influenciados por interesses especiais, a blockchain, e a prova de trabalho de Bitcoin asseguram a transparência e a integridade em todas as transacções. Isto torna Bitcoin uma alternativa moral aos sistemas que estão sujeitos a corrupção e exploração.
Bitcoin como Visão de Liberdade a Longo Prazo
Bitcoin é mais do que uma solução temporária para os problemas económicos — representa uma visão de liberdade financeira e pessoal a longo prazo.
Liberdade Financeira
Bitcoin liberta os indivíduos dos ciclos inflacionários e das armadilhas da dívida criadas pelos sistemas monetários tradicionais. A sua oferta limitada assegura que o valor é preservado, oferecendo um futuro financeiro estável e seguro. Ao possuir Bitcoin, as pessoas podem escapar ao ciclo de dependência das moedas fiduciárias controladas pelo governo e proteger a sua riqueza contra a desvalorização.
Soberania Espiritual
Bitcoin não se trata apenas de acumulação de riqueza; trata-se de recuperar o controlo sobre o próprio destino. Ao permitir que as pessoas tomem decisões financeiras autónomas, Bitcoin proporciona soberania espiritual — a capacidade de viver de acordo com os próprios valores, sem estar dependente de instituições centralizadas.
Conclusão: Recuperar a Liberdade com Bitcoin
As dificuldades económicas enfrentadas pelos Millennials e pela Geração Z não são resultado do capitalismo de mercado livre, mas sim de um sistema corrompido pela intervenção governamental e pelo proteccionismo. Bitcoin oferece uma alternativa revolucionária — uma que permite que os indivíduos recuperem o controlo das suas finanças, do seu futuro e da sua liberdade.
Bitcoin representa mais do que estabilidade financeira — é um movimento em direcção à libertação moral e espiritual. Para os Millennials, a Geração Z e todos os que estão desiludidos com o sistema actual, Bitcoin oferece uma forma de romper com o status quo e construir um futuro sustentável baseado na liberdade pessoal, na integridade e na responsabilidade.
Photo by Emil Kalibradov on Unsplash
-
 @ 6bae33c8:607272e8
2024-09-27 08:38:36
@ 6bae33c8:607272e8
2024-09-27 08:38:36It’s funny because I thought this was a get-well game for Dallas and that they’d cover the 6.5, but I picked the Giants in my low-stakes pool because it’s not worth it for me to go against them, and they covered. But only thanks to Brandon Aubrey finally missing a 50-yard FG.
-
Malik Nabers suffered a concussion late, but I’d have a hard time arguing against someone taking him a 1.1 even in a re-draft league once he’s healthy. He’s a target and catch machine.
-
Wan’Dale Robinson is the clear No. 2 and made some nice plays after the catch. He’s small and won’t make chunk plays, but useful.
-
Darius Slayton showed up finally, and he’s a useful field-stretching No. 3, the role for which they drafted Jalin Hyatt who hasn’t shown up.
-
Greg Joseph was 5-for-5 on FGs, including a 52-yarder. Even the waiver-wire guys are better than the GOATs of yesteryear. (Kicking is the one area you can compare players across eras because it’s independent of the competition level.)
-
Daniel Jones played well — his INT was a last-second desperation heave. He was accurate and had some zip on his passes. The negative is when he’s pressured he still doesn’t have great feel. He only took one sack, but he rarely turns those plays into a positive. Still, this was progress.
-
The Giants offensive line played well against the Dallas pass rush. Devin Singletary made a great move to turn a loss into a first down, but there’s no juice in the run game, no speed element.
-
Dak Prescott was solid, took what the defense gave him, didn’t make mistakes. He also made a nice shovel pass to Jake Ferguson when under duress, the kind of thing Jones hasn’t been able to do.
-
Rico Dowdle is the Cowboys starting back. He was bottled up early, but got free late. He also caught a TD. He seems like a stopgap, not the solution, but was adequate at least.
-
CeeDee Lamb saw targets and production early, did little in the second half. He also had three rushes, as the Cowboys are desperate to get the ground game going.
-
Jake Ferguson is healthy again and seems like the clear No. 2
-
Aubrey is such a monster, drilling a 60-yarder down the middle with plenty of distance to spare. Seriously should have gone in the eighth round in the NFFC.
-
-
 @ eac63075:b4988b48
2024-09-20 09:23:23
@ eac63075:b4988b48
2024-09-20 09:23:23Overview of the Infrastructure
- Umbrel/Citadel/RaspiBlitz/Start9 Server
- Purpose: Acts as your personal Bitcoin and Lightning Network node.
- Setup: Installed on a Raspberry Pi 4 running Debian or Umbrel OS.
- Benefits:
- Participate in Bitcoin Consensus: Validates transactions and blocks independently.
- Lightning Network Routing: Facilitates faster transactions and earns routing fees.
- Cold Storage Wallets
- Coldcard: A highly secure hardware wallet designed specifically for Bitcoin.
- Ledger Nano X: A versatile hardware wallet supporting multiple cryptocurrencies.
- Purpose: Store your Bitcoin offline to protect against online threats.
- Secure Devices
- Encrypted Computer: A notebook with encrypted storage for managing your wallets and nodes securely.
- Android Phone with Secure Area:
- Old Device: Repurposed without a SIM card to minimize exposure.
- Secure Area for Apps: Uses features like Samsung's Secure Folder/Knox to isolate sensitive applications.
- NerdMiner
- Purpose: A compact mining device like the Nerdminer V2 to engage in Bitcoin mining.
- Function: Attempts to mine Bitcoin blocks, offering a chance (albeit very low) to earn block rewards and learn about the mining process.
 ### Advantages of This Setup
### Advantages of This Setup- Self-Sovereignty: You have complete control over your funds without relying on third-party services.
- Enhanced Privacy:
- CoinJoin Transactions: Mix your coins with others to obfuscate transaction history.
- No SIM Card Devices: Reduces the risk of SIM swapping attacks.
- Network Participation:
- Consensus Involvement: By running a full node, you help maintain the network's integrity.
- Lightning Network: Improve transaction speeds and network scalability.
- Security:
- Cold Storage: Keeps your private keys offline, away from potential online threats.
- Encrypted Devices: Protects data even if physical devices are lost or stolen.
 ### Simplifying the Perceived Complexity
### Simplifying the Perceived ComplexityWhile the infrastructure may seem daunting, it's more approachable than it appears:
- Starting Point: Use an old computer or phone as a cold wallet with software like Electrum or Sparrow.
- Step-by-Step Setup:
- Begin with setting up the Umbrel/Citadel/RaspiBlitz/Start9 server.
- Gradually add hardware wallets like Coldcard, SeedSigner DIY, Jade, Ledger, Trezor or Onekey.
- Implement security measures on your existing devices.
- Community Resources: Numerous guides and communities are available to assist with each step.
 ### Embracing Freedom and Privacy
### Embracing Freedom and PrivacyPracticing self-sovereignty and custody isn't just about securing your Bitcoin—it's about embracing freedom and privacy in the digital age. By taking control:
- Financial Independence: You're not dependent on banks or exchanges.
- Data Privacy: Your financial data remains confidential.
- Empowerment: Gain a deeper understanding of how Bitcoin and blockchain technology work.
Remember: Even simple steps like using an old device as a cold wallet can significantly enhance your security. The journey towards complete self-sovereignty is a progressive one, and each step you take strengthens your position in the digital world.
-
 @ a03b38f8:2c7ce1f0
2024-09-19 03:04:13
@ a03b38f8:2c7ce1f0
2024-09-19 03:04:13You are Giving Away a Lot of Data with those Pictures
You post pictures on nostr and other social media. You send pictures to friends and sometimes sorta friends. I hate to tell you this but you are giving away a lot more personal data than just what's on the image of the picture.
It all comes down to the metadata. The term Metadata refers to descriptive information about a picture, image, or file. This set of information is so vital as it reveals everything about a picture.
Metadata is key as it explains the privacy and security dangers that you are exposing yourself to everytime you share that file. And not just pictures, but text documents, PDFs and Videos.
What data is in Pictures?
EXIF Data (Exchangeable Image File Format): This is a standard that specifies the formats for sound, images and ancillary tags used by scanners, smartphones and other smart devices.
EXIF contains so much more personal information than you can imagine.
It tells the geolocation of where the picture was taken and it gives the timestamp of when it was taken.
So that creepy guy who follows your accounts knows all your favorite lunch spots because you like to post pictures of your food.
Additionally the metadata contains a description or title of the image. Any tags or keywords associated with the image, author information, and any custom metadata from any image editing software that might have been used including more timestamps, system information, and log of any edits.
So yes your Bumble date knows you are trying to catfish them with that 5 year old picture you doctored up with AI.
Uses in Open Source Intelligence
Open Source Intelligence or OSINT is a fancy term for cyber stalking someone. It is using nothing more than specialized knowledge and freely available information on the internet to find out all kinds of stuff about someone.
Using the GPS metadata and reverse image search of that picture posted online you figure out where that person is from and maybe a first name. Using that to narrow down your search criteria you find their Facebook and Instagram. Now you have their last name, how they spend their time, friends, and maybe where they work. Searching free data brokers you find their address and phone number. Public records tell you how much they paid for their house and Google street view gives you a view of the house from the street.
So other than being a creep, what else is metadata used for?
Analysis of metadata helps to trace the origin and history of digital files. Digital Forensics will know when those files were created, accessed, or modified. Forensics then uses this for additional context about files and other data stored on a computer or network, this information is useful because it provides information that may not be immediately clear from the file itself. Remember your OPSEC rules and be a Nemo when necessary.
There is some good news. (And bad)
Luckily the more popular services out there such as Facebook and Instagram do not display the metadata of the users. You cannot check the metadata of pictures as it does not allow you to download pictures or copy the image link. Although that doesn't mean the companies themselves do not have access to that data.
This is not the case with services like Tumbler and most image hosting or storage services. When pictures are uploaded to cloud services like dropbox or google drive anyone with access to these images can also access the metadata.
Okay I am terrified, how do I remove metadata from pictures?
Thankfully there are several options to take care of this. Most operating systems have methods built in. (see below for instructions for Windows and MacOS). Tails and QubesOS has Metadata Cleaner software preinstalled. There are several online tools that also scrub metadata from pictures. (Shout out to nostr.build)
Windows
-
Right Click the image file and select properties
-
Click the details tab
-
Click Remove Properties and Personal Information
-
Choose the level of metadata removal desired
MacOS
-
Open the image in the preview
-
Go to Tools
-
Click EXIF tab
-
Select Remove EXIF file
How to remove EXIF data after capture on phones
Let's be honest that most of your photos are taken and reside on your phone now of days.
On iPhone you have to open the Photos app, select the image, tap on 3 dots and select Adjust Date & Time and Adjust Location. You can also get the adjust setting by clicking the little i at the bottom of the picture.
On android it is much the same way. Open Gallery, select image, tap 3 dots, choose details, then the pencil to remove location and timestamp, save.
On Graphene OS no worries, remove EXIF data after capture is an existing setting in the camera and is enabled by default.
It is a total pain that you have to do this each and every time to every picture. But I hope you now realize how important that metadata can be and why you shouldn't just be sharing it with the world.
-
-
 @ 17538dc2:71ed77c4
2024-09-16 15:26:32
@ 17538dc2:71ed77c4
2024-09-16 15:26:32
Quiztime
Oil and gas
Oil and gas is naturally occurring. The prevalent worldview is that oil & gas has a biotic origin. There are real world examples of abiotic oil deposits, which proponents of the status quo have a difficult time reconciling.
Irregardless, when oil & gas is burned, it simply turns to plant food (carbon dioxide + water).
Oil and gas greens the Earth, and increases fertilization and agricultural crop yield across the globe.

The energy density of oil and gas is only surpassed by that of nuclear power.
Energy produced by oil and gas combustion is generally on-demand, reliable, economically storable & transportable.
Solar
The sun is an abudant energy source, which keeps Earth warm, and alive. Thank you sun 🌞!
With the exception of places such as the UK, where it is unclear if inhabitants have ever seen the sun, solar rays keep plants, animals, and humans happy & alive on most of planet Earth.
Inventions such as solar panels harness the sun's energy, and convert it to electricity.
Solar panels consist of silicon, rare earth metals, and require toxic metals.
Solar panels have an expected life of decades, are not readily or economically recyclable.
A very low solar energy density practically means that land is inefficiently utilized in solar energy production. Solar used on arable land can no longer be farmed, and where no plains exist solar is known to cause deforestation and landslides.
Solar energy is not reliable, not can it be summoned on demand. Solar energy is not economically storable, and is many cases is not produced at the point of demand.
Despite central planner mandates & subsidies in the US, the #EULAG and elsewhere, due to its intermittent nature, solar power cannot be counted on to replace reliable power generation in nuclear, hydro, or carbon fuel thermoelectric plants.
What this means is that solar does not replace, and yet ratheradds to reliable energy generation, as most people in the developed world would not be OK with having electricity for at most 1/3 of the day. This increases the price of electricity, which in turn increases energy poverty, and drives businesses to shut down manufacturing, or move to a more energy competitive jurisdiction.
The capital wasted by central planners could have been used to reduce burden on consumers, and businesses, or fund healthcare, infrastructure, or other services.
It should be noted that off grid applications where there is no grid, or energy alternatives can be massively useful for folks otherwise without electricity.
Which energy source would you consider renewable?
-
 @ a03b38f8:2c7ce1f0
2024-09-16 14:20:13
@ a03b38f8:2c7ce1f0
2024-09-16 14:20:13A VPN is Not Magic
A VPN is a virtual private network. A VPN service provides an encrypted tunnel between your device and a server they own or rent. You then connect to the internet from this server thus making your IP address appear to the wider internet as the server IP. That's it. That's all it does.
Your Device -> VPN -> Website
Your Device sees that you are connecting to a website through a VPN. Your ISP sees that you are connecting to a VPN server but nothing after. The website sees that someone from a VPN is connecting to them but doesn't know who. The VPN sees your device connected to their server and that you then connected to a website.
VPN Anonymity and Privacy
VPNs do a lot to protect your privacy, they keep your ISP from seeing and logging every single thing you do online and they spoof your location and IP to any website that you visit. Although this website protection isn't 100% anonymous because of cookies, trackers, and if you have to log into a site with your information. If you are using a VPN on a mobile phone then you are still broadcasting your location to the cell towers even if you are not telling the website you are browsing.
Then there is the elephant in the room. The VPN knows all and sees all. How much do they log? How long do they save it? Can you trust them? This is going to vary VASTLY between VPN providers. I always prefer if they are setup where they cannot know the information in the first place and limit what I tell them in the first place by paying through the use of bitcoin or monero. Just because they have a no log "policy" in place it doesn't always fill me with confidence.
VPN Security
How much security does a VPN give you? Some in certain circumstances but not a lot. A VPN is not going to stop malware or viruses. A VPN can provide some protection from a man in the middle or evil twin attack as it provides a encrypted tunnel between your device and the VPN server, so always use a VPN when joining public WIFI spots. Just remember a VPN cannot protect you downstream on the connection between the VPN server and the website, always use secure encrypted connections and be aware that MITM attacks can still happen on the backside. A VPN can prevent DDoS attacks since the attacker doesn't know your real IP address and a fantastic use of VPNs is to protect IoT devices. Those smart devices around your home love to scream out all their data insecurely and a VPN can change their IP and encrypt their data in transit protecting them from hacking.
VPN Legality
In many countries VPNs are banned, blocked, or outright illegal:
Bahrain Belarus China Cuba Egypt Iran Iraq Libya Myanmar North Korea Oman Russia Syria Turkey Turkmenistan UAE Uganda Venezuela Vietnam
-
 @ a03b38f8:2c7ce1f0
2024-09-16 03:45:22
@ a03b38f8:2c7ce1f0
2024-09-16 03:45:22-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQwAuQJakbLOp80scl1EIOfxzk2nRkESlxMOkEt/vs2M5bn9 7uZczTu7F8d9VcwQbQ016L00Kj3z/CQjyZMMSyAHUJnHZPis3ts7v1LUVErk/JKm ILRyQgMAl7/gKUqwm232dJNt1EE7o85P3wyy4hecsW0EBw0dX5rx68Fq1664adAZ CqjyoOi+y/2uHSnTCcoyD1yDWu5rrbC1TZL0acFlKhGnufCN18Z2KcUbhrjK5CdH etcF4rCBSBt/6GVufoH0yEbuGOvX1u2up2miys/zuMr1eqEF13eOFDkWqnoAaUyd fLx8bvf4ppW2tQJPadFmRNVMu4+6Mu3abI4ItBl3o1ubhcoHyD10brHQEaXPrCaD GcmB9sAs4G8B2PHkLf1krs3ZhEOoBIOMkF65tg1JOzEDXPbSqEGaKv78YPR0Gp0f Xx9X513a6Zs+YAFSTj4Td9LXL16umSm1D42mTK3Y1yRzSn2hAkvZSK5mExarMNNg ucZr2/ythKuSE8FapKwu0sb/AWgW403e6eRH5hzFBvBFIFA1Sch8/BY2/zaJEkAQ m+HsMwiLuCYi6sqXcJ1DDBmk3Yy8VySb16/pKsYIqTDqTtnNrdTTVSebiD9BoOAt GUD1zf6oRFL90gX3SjVUIuAFZJdKSkBoHoTb+Tfvl4lGRajsHGy14gL150AaOLXh anZHBA+pi/MelYa+dLoqMLgJOnSimGkZZoqCeuH02f5TsMba9FmHJL3lW0IKFb17 QJJWGM2/qn0DocqIg+FsOkBrxivQIFqYG8smwYbgtKyrRFPouJhP/yTkzYEGWXuQ l2tSIa/3fj5ZT9EuJWPOZoJ5oFFLDJTHPF0Q+tLCI3Ad/Co2T8hq02+p1B+uH+VF E5k//ZrLU9cV0dmH6oIt25BDK2FYZBvq0+YylUDnqCy9vc0htKppdoJZbFCJNRX0 K8lzJbrFdrA5bf8I7+JYeuofz0pfY4VO3nqomk1UUhL2507TfIL1w0lUy9CAv3FO jnnGIQMbo0XEkXEfAXMzbi1UAyXBKj1YbiQFfGggsNRRcubFCx/hcG60eHWbmiw8 xK9r+6jKIuvT+HDotcc2lfgPQ4lbTaWKrBva1wPu4Cqt5BaXoIuATxul4s5SmUtk BVdrLkgB3CTs/gu7BZSnl5Im6gN076Mf4+NdN+X+Kbj0s6tLVWjxMVu1EbAjrm6h vd2uE4D5Rc//01rd0cDiWroDaTr8uFB9wgJV30hMHDyO3MVb9kOdU2zu26cF2L1T k7Sxx269ZktVXsUqk7sJsxCpUOeVvbMdTfgsO7GTTi5LpwvsIN2sMUTwCdYULXiG 095O9PpGvzEZmLoOQvKjtuJ9VJqG/3M0Tqgv8DnZaNKoKQ3WqEzO8XSbQmTKbdiB B+n+u9AQtDI+WOEVLEwaIdeb7DgLJKpaSnH+E7n4t3ZhLqe3a7O2op+oyqi91f4u 74CQ4yYhTjVwVBkLm5RF5/VYDGnJKOlFUMRlDcTbgqTG3l8TjaIFXAK7E58mYeCN JWvjNZDKS1STnUabYRIQa+DzUoR2kAEZixBop4RBdxlTXIi0RREaKvH7AyF1GY84 MzovzKgrAylVVCa6Dk89WrsTLZ0FuAO9E+gg8yIgRyr9ZeIzMEEvKYcD6KNEzm10 KFZTUe/SIawf7ocGHG/VASPiNxer8x2bfGuplRE+WnsK/E0ywtws4ZZFzsdI337G pSoiihZurmRYKd37XueCX1rzOFUFLLqE0/6AbUPT4RYN/pyG8s0Kuy+RexjbbJEY J25DHfX00Bccsm2/3bXuBGM1hZAVxLZNWg6V1KX66j3/Dp0NgCq7AhWbkCt19kBI NwhXKCN+KEwDxBmzp3Jf5diGBhcIucC3UMlaDL/MKvZM/DM2R0m5J53nHlvzHvrC NEAKn9eEAjw9GNWZcXsr29twzsLmn1g30qQtn+06GYjhP6BoN7p4LjKXDpO7ygYz +UkXtWhDia/InbVjOhE5zfKT8mkpcIJvdAom509lWRh/vneYG3dMVMF+exTR6hHl NF3uXnnKZ5p8fmDs1O/sRZlJ6lsUPd3w2lDbRY2FLII8n3f6ho+wmz2js5nwwjMT 2RPgTd1E0jzaV/vjGjkIkIdUWUn6RaDNsCEIuEf+JhZvJCSZWDlCdlHS9lns60U2 +h0kMjhgYAefUW7o4EEMkU2NAKBVHS32YVvsqRoZ3amDAjObmvdI8wPwsjfQyj1H 86V2AliBmP6T9uYP296u7tOiV2rswmZ7PHWT4Xdst/AbMkun/EFyE3tJ17CruPyC Eo/qsnH4315jT0kC118i9KtpLFb+WGKfkFcaCzOACyTUUpJrsuX61M7ynQj+zKlm xo+o3h8KMphuJRHOUBng0xPOAYT65R0pL1r+vUN1vIAYeXk/L6gnWwdx72+J/9Gs ILaRrh42Sb89RpsGMHzoQmvQ9fAqPRFAULeih/8vwVjsXeBZikgSUkpWG8AZva2y HxfSWNl/K/QcrLvsuH7EYtmwKb2T6QBpDwHPIx+h1xCBeWMlAH/bM06l1uBNOJD9 qDcW9aaN/x+fFjnInoITd4357XpSYqLe35Ao48bvDoeAP8lLUabladh4x54TbjmP gP3v3JYhZ2qswuMxF993QP6ToGRjS8iuDw7YW9+pC4FHXj79SB2F/Z/383I+Cdfq y7NSEFIf8Ts/C/JQ55R1bKWB3WgREX7SlEan/XyuMsgGVk16BptNorHkwuvZOTzg 0DFcD2tLHxrRFUG2M+SSdO7/oNLWLdXCAFWoVb3heYs+L7/4h4g4SnRHaMqPXnUe u/Q37QekKXVqDrthgDTnbiV+pSJJ9Xuuo6juY0Nl1pqTL6nJQnrG9eVXCyt+2qgO HYDBLVE8U9JxQrMfPlwAOoZqwmtUsu9/16OXwpTyrO33mYU+p+cQHsNttWCqAKYF L9mX1Vm7b082PAvpoqKqtLbyys0Nl1qX9laU5YEZ+RB5kq+22tCulooyfHGRAnXo hrRCKtCA1ZnLbURUaPHUPAZnB6Qa4MBUJ7y6oL8XM4eANaqtLrW3xGAvHTDcPRmL vuwRdz6OD2oXvND5TSpsn7JL5JXRalvfS0KjWx/61PiDX69XEbwEXeXPSiN7qXqC NqYOVJsQuhZPUlX44JzX/71F1gBBf6bJHvj7hZggiTtk =WUuh -----END PGP MESSAGE-----
-
 @ 592295cf:413a0db9
2024-09-14 18:13:41
@ 592295cf:413a0db9
2024-09-14 18:13:4109 09 week
The billboard has reached its first goal.
I don't understand anything, too much.
The web is a dangerous place, maybe the couch at home is for you.
Nostr is like being in a public place like a bar and you listen to the radio, and you can decide which radio to choose, you can also talk on the radio, only those who follow you and those who are connected to that frequency can listen to you.
We talk on multiple frequencies so if one is offline they can hear me on the other.
Spam will always be a constant as are fixed costs, personnel costs, taxes things that people in general hate
A lot of talk that will be blown away by the wind.
Jack Dorsey says Nostr will be a protocol for private encrypted chats
-
Open-sats drama
-
Carnivore dietitian
-
Lightning diatribe
-
This is already Twitter 😉
Fiatjaf explained for the umpteenth time what the outbox model is, now those who look at images instead of reading books must have understood it too. My note, Patricia writes in her relays write, including select some in her outbox 10002 kind. it was a dev page of something, so maybe it won't be online for long
Thinking that with Kamala Harris's victory, the price of Bitcoin would hit a low and holders would be happy to buy. 🤣🤣 Instead with Trump new all time High, holders would be happy. 🤣🤣 Lol Moment.
I read the article about btcmap maps, there were some notes to make but I didn't, it's beyond my level, it was only for builders.
Satlantis, trustroots, and wherostr were not noted.
I had this thought that we will not "succeed" in building the openness of type 1, in the following nips, because of the relays and because discovering new things has a cost, and no one wants to discover new things. And then after that the others should use them, but how and after that at least two others appear who are doing a similar thing, but they don't talk to each other because they don't have time.
If the time horizon is 10 years, those who survive will see.
Keeping calm seems difficult.
I tried nostr-relay-tray works. It works, I would suggest a couple of changes
- Delete some events.
- View events
- Search by npub id or time
- Delete by time.
These are difficult things but they can be done with a database, so they may as well not be done.
I hope that all the controversies are forgotten and overcome and we are more serene.
-
-
 @ a03b38f8:2c7ce1f0
2024-09-13 16:28:42
@ a03b38f8:2c7ce1f0
2024-09-13 16:28:42Your phone is not your friend
Your phone is not your friend. It is a filthy little snitch that tells anyone who asks where you are, what you are doing, and who you are doing it with. You can obscure and hide some things through the use of privacy respecting software like encrypted communication apps, Tor pathways using Orbot, or the base OS like Graphene but metadata and geolocation is still very loud and very present. It is built into the infrastructure of how cell phones work. Your phone is tracked at all times through every cell tower area you pass through logging your IMEI and by extension your phone number and identity. This data is logged and saved forever by companies who use and sell it for corporate surveillance and post Patriot Act give it to police and government agencies warrantlessly.
Fine, I will just turn it off then. Nice try, but unless the battery can be removed it still tracks you. You didn't think it was weird that Find My Phone still works even if the phone was off?
Luddites are not off the hook. That dumb phone or flip phone is tracked just the same and since it will not run encrypted communications you are screaming out the content of every call or text and not just the metadata.
OK, I will get a burner phone or anonymous SIM card not tied to my identity. Better but not bullet proof. This is great for use and toss but if you continue to use it multiple times, around other devices that are tied to you or your social network, or take it to your home, work, or any location associated with you then it will be doxxed. Once doxxed all past information associated with it becomes now linked to you.
Metadata, Profile, and Network
Your network is very easily known and built up over time. Who are the contacts saved in your phone. Who do you interact with. Who do you call, text, email, DM, or follow on social networks. Who do you never contact but your geolocation overlaps with them often. Now look at all those contacts and who do they have a network with. A giant spider web of connections. If by 7 degrees of Kevin Bacon you have a shady contact in your network then you may get more scrutiny than you may realize.
You are spilling metadata everywhere you go along with your geolocation. Time stamps, who you contacted, how long did you talk to them, which app was used when, internet searches, map app searches, etc. People are creatures of habit and over time this metadata builds a pretty good profile on you.
Phone becomes active around 7am when they wake up. Scans social media and news sites for usually 30 minutes. Assume they are taking a shower because the phone is on but not being used until 8am most week days. Travels to coffee place on the corner most mornings and then goes to their place of work. Between 9:30 and 10:30am they again scan social media and news sites for a solid 10 minutes, probably their bathroom schedule. During lunch they frequent these locations with these people.
You get the point. This profile, plus your geolocation history, plus your network paints a pretty complete picture on you. Surprisingly it is not what you do but when you do something different that gets attention.
There was a big protest last night that we are not happy about. We already have a list of everyone who took their phones with them at that geolocation and timestamp. We run a algorithm looking for simple patterns. John is usually at a restaurant eating with friends during this time but strangely his phone was left at home and turned off during that time frame. Did anyone in his network go to the protest that we have already confirmed? Anyone in his network follow the protest Facebook page, or have a deviation from their usual pattern such as their phone being somewhere dormant when it is usually active during this time?
What can you do?
You can choose to do nothing. You can just live your life with the awareness that you are being tracked and profiled, maybe work to limit how much metadata you are spilling out to the universe. If you are a activist, a oppressed minority, live in a oppressive regime, or your country suddenly becomes oppressive this might not be an option.
Randomize or maintain your profile. This is hard but not impossible. Make your profile and habits so chaotic that any deviation is not a deviation. Most people cannot do this but if you are a couch surfing, different place constantly, new friends and new activities on the daily agent of chaos then maybe this is a option. On the opposite extreme maybe you are very regimented person so be aware of that and always stick to your routine. If you want to go to that protest but are usually home doom scrolling youtube during that time then set your phone to no sleep mode and set up to watch a long playlist of youtube videos left at home while you go to the protest.
Home phone only. Maybe you decide to have a home phone only, no not a landline, but a actual smart device that can utilize encrypted communications services but never leaves the house. This could potentially save you a lot of money on data plans, texts, and minutes if you don't buy a network plan and just use VOIP on your home WIFI. Or maybe you have a very minimum network plan and when you leave the house you either take it with you in a Faraday bag or have a secondary device that lives in a Faraday bag that only comes out for emergencies and to check in. Just be aware that the time in and out of the Faraday bag is part of your profile.
No Phone. You can have no phone whatsoever. This will not work for most people in the modern age but if you have a extreme risk profile then this might be the extreme option you need.
How do you survive with no phone or only a home phone?
Just some alternatives and some ideas. You can still buy WIFI only devices that have no network connection and / or stay in airplane mode. Old MP3 players for music and podcasts while on the go. Old phones that you can download maps to for navagation and use VIOP services in WIFI hotspots.
Emergency Communication and Go Bag
Prepper culture has given us all sorts of bags: bug out bags, get home bags, never coming back bag, and go bags. I define go bags as very small, light weight, and compact bags or kits. They carry very minimum, bare necessary gear, and ideally are so small that you actually have it on you, in your purse or computer satchel or car all of the time. Emergency communication will be part of this. This is when the burner phone, purchased with cash out of town, and stored in a Faraday bag all the time shines. It has no connection to you and has no history of use. It is a have but hope to never use oh shit device.
If you are the activist, the whistle blower, the oppressed that they could come after at any time, or the journalist that investigates corruption, organized crime, or terrorism then you need this.
I will cover go bags in more details later, probably in a key note.
Always forward, GHOST
-
 @ bf95e1a4:ebdcc848
2024-09-11 06:31:05
@ bf95e1a4:ebdcc848
2024-09-11 06:31:05This is the lightly-edited AI generated transcript of Bitcoin Infinity Show #125. The transcription isn't perfect, but it's usually pretty good!
If you'd like to support us, send us a zap or check out the Bitcoin Infinity Store for our books and other merchandise! https://bitcoininfinitystore.com/
Intro
Luke: Paolo, Mathias, welcome to the Bitcoin Infinity Show. Thank you for joining us.
Paolo: Thank you for having us.
Knut: Yeah, good to have you here, guys. We're going to talk a bit about Keet and Holepunch and a little bit about Tether today, aren't we?
Luke: Sounds like that's the plan. So thank you again, both for joining us.
Introducing Paolo and Mathias
Luke: would you both mind giving a quick introduction on yourselves just so our listeners have the background on you
Paolo: Sure, I'm Paolo Arduino, I'm the CEO at Tether. I started my career as a developer, I pivoted towards more, strategy and execution for, Tether and Bitfinex. And, co founded with Matthias, Holepunch, that is, building very, crazy and awesome technology, that is gonna be disrupting the way people communicate.
Luke: And, Mathias, over to you.
Mathias: Yeah, thank you. Yeah, I've been, so I come from a peer-to-peer background. I've been working with peer-to-peer technology. The last, I always say five, but it's probably more like 10 years. I did a lot of work on BitTorrent and I did a lot of work on JavaScript. and a little bit later to, Bitcoin and I saw a lot of potential on how we can use Bitcoin with pureology and like how we can use.
P2P technology to bring the same mission that Bitcoin has, but to all kinds of data, setting all data free and, making everything private per default and self sovereignty and that kind of thing. I'm very into that. and I've been lucky to work with, like I said, with Paolo for, many years now and, Get a lot of, valuable, feedback and, idea sharing out of that.
And we're on a mission to, build some, really cool things. In addition to all the things we've already been building. So it's super exciting and glad to be here.
Luke: Oh, fantastic.
Introduction to Holepunch
Luke: Matthias, that was a perfect segue into basically, an introduction to, can you tell us about, Holepunch.
What is Holepunch and what are you doing?
Mathias: Yeah, sure. like I said, we co founded the company a couple of years ago. Now, we've been building up a team of really talented peer to peer engineers. we're always hiring also. So if anybody's listening and want to join our mission, please, apply. we have some really smart people working with us.
but we teamed up to basically. like I said in my introduction, I've been working on peer to peer technology for many years now and thinking ahead how we can, stop using all that technology when I started it was only used for basically piracy. I'm from the Nordics, and I think Knut is from the Nordics also, so he knows all about, the Nordics know about piracy.
It wasn't back in the day. A lot of very interesting technologies came out of that. But basically, how can we use those ideas that were proven by piracy back then to be really unstoppable, because a lot of people wanted to stop it, but apply that same kind of mindset to the general data, so we can build actual applications that has that kind of quality, that can withstand the wrath of God.
that can work without any centralization. Actually, nobody can shut down, not even the authorities if they wanted to. Basically unkillable and make that general enough that it can basically run any kind of application, solve a lot of really hot problems. it works on your own computers, your own networks.
Mobile phones, and tie that up. I'm a developer by heart, into a software stack that people can just build on. So not everybody has to go in and tackle all these problems individually, but just give them some software to solve all this so they can, as much as possible, just worry about making really cool applications that we use,
Yeah, like I said, we've been working really intensely on this, for a long time and in Holepunch, we made this our co mission to scale this up and, deliver a software stack on that. it's been really exciting and it's been really fun and it's been very, challenging, but if it's not challenging, then why, do it?
and, especially, with the backing of, Tether, through Paolo and also just expertise from there, we have a good hand built to deliver this to the world. And, the first thing we did was, like, think about what's, a good first application that we can build that can showcase this, but also something we really want to use ourself and see scale have also have on the world.
And obviously that was a communications app, keyed, which we was our first project. And, we're still in beta and we're still lots of work to do. And we're still iterating that really heavily, but I like to show that you can build these kind of apps without any kind of. central points. and we released that also, like the first thing we released when we launched the company.
And like I said, we're still, building and still iterating it. A lot of fun. and then take the software stack from that, which we call the pair runtime and then split that out. So anybody else can build similar apps on top. With that same technology stack, and, yeah, that's, we launched that earlier this year also, and, it's been really exciting so far, and it's, I love going to work every day and solve, even though, you can see on my hair that it's not really good for, the head scratching, but, but, it's really fun, and it's really challenging, and it's interesting thing. goal as a company, basically to have that if we go out of business tomorrow, our technology continues to exist because we're not in the loop of anything. It's also sometimes really hard to explain that we don't have any, chip coins involved or any kind of limitations on the stack because we're basically engineering it not to be part of it, because that's the only way you can actually engineer these things that they can understand.
anything, super exciting and, encourage everybody to try to check it out.
Luke: we've both used Keet and I've certainly enjoyed the experience. I, think, the, basics of this, as I understand it, is that it's, entirely on both sides. The communicators end, or a group of communicators, it's all on their end, and the communication is entirely peer to peer, what is Keet really, what is the basics of Keet as, say, a product?
What is the easiest way that you would explain what it is?
The Vision Behind Keet
Mathias: But We're basically trying to just build a world class communications app that works to a large degree, like normal communication apps that you know, like Signal, Telegram, WhatsApp. Just with all the centralization tucked away, with all the costs of running it tucked away, and then adding all the features that also we can, because we're peer to peer
People don't care about technology. We loved it, but don't have that surface off too much to the user.
Just have the user use it as any other app, but then just have it be 100 percent private per default, 100 percent like no strings attached. It just works. if we get caught off by a. From the internet tomorrow, it will still work, that kind of thing, but deliver that in a way, and this is always our mission where users don't really need to worry about it.
It just works. And, it works the same way to a large degree as their other apps work, except obviously, there's no phone numbers and things like that. Very cryptographically sound and, but trying always not to bubble it up. And I think that's, so it's actually a really simple mission, but it's obviously really hard.
And that requires a lot of smart people, but luckily our users in a good way, don't need to be very smart about that.
Keet vs Nostr
Knut: Yeah, a quick one there. No strings attached starts with the letters Nostr, so is, Keet and Nostr, do they go mix well together or, is there an integration there between the two? I see a lot of similarities here.
Paolo: I tried to explain the differences between Kit and Nostr. I think Nostr is a very interesting protocol, but also is very, simple. the way I like to describe it is that, if you are familiar with the history of filesharing, Starting from the first one, super centralized, and then eventually every single step, you get to a decentralized platform.
And the last one, the most decentralized one, that is BitTorrent. the history of file sharing proved that every time you try to centralize something, it ends up badly, right? if you have any special node in the system that does a little bit more than others and requires more resources than others to run, that will end up badly.
You might end up in a small room with a lamp in your room. Point it to your face, and then everyone suddenly will stop running an indexer. That reminds me about Nostr structure. if you are building a peer to peer system, or if you are building a very resilient communication system, if you think about Nostr, you would imagine that if you have, 10 million or 100 million users, the number of relays would be probably less than the square root of the number of users.
So that surface, although a hundred million users is very, they're not attackable, right? But the surface of, the relays is much more attackable. look at what is happening with, the coin joinin platforms, right? very similar. the beauty of KIT versus Nostr is that in KIT you have number of relays is actually equal to the number of users because the users are their own relays.
and they can act as relays for others to, further their connectivity. That is how we think a technology that, has to be ready for the apocalypse and resilient to the wrath of God should, work. if you have, a log number of users or square root of number of users as relates, I don't think it's cool technology.
It will work better than centralized, Technologies like WhatsApp and so on, or Twitter, but eventually will not work when you will need it the most. Because the point is that we will not know what will happen when we will need this technology the most. Today, not for everyone, but the world is still almost at peace.
Things might unfold, in the future, maybe sooner rather than later. But when things unfold, you will need the best technology, the one that is truly independent, the one that is truly peer to peer. it's not really peer to peer if you have specialized relays, but where you have super peers randomly.
Luke: Yeah, the difference here, between the Realize and not having any other centralized infrastructure in the picture is certainly an interesting distinction. I hadn't heard anything about that you can act as a next connector or something like that.
Pear Runtime
Luke: So there's a couple of related things. I know there was an announcement about the, pair runtime, is that right? can you talk a little bit about that or any other, ways that this is growing in your whole, platform,
Mathias: Yeah, sure. so basically when we talk about ideas, internally, also from our software background, We want to solve a small problem that then can solve it for everybody. So
We want to build technology that can just send data around efficiently, so you can build any kind of app on top. We're all about modularity and taking these things to the extreme so we can repurpose it into any kind of application and other people can, get value out of it.
And, that's been our mission from the get go. So basically, like Paolo said, when we built Keed. We took all of these primitives we have, it's all open source on our GitHub, that can do various things, relay encrypted data in a way that's completely private, nobody can read it, and in a generalizable way, so it can run on any applications.
We have databases that can interpret, work with this data on device, but still in a way where nobody else knows what's going on, fully private, and we spent many years perfecting this, and it's still ongoing. And we, similar to like connectivity, it might seem really easy if you don't know what's going on that, connecting this computer to another computer and another place, but it's really hard because ISPs and, your internet providers, et cetera, they don't really want you to do that.
So there's a lot of firewalls involved that you have to work around to get around This is all really, hard problems that took a long time to solve.
But luckily, all of these are like generalizable problems where you just solve them once to a large degree, and then it's solved for everybody. If you put them in a modular framework where anybody can put the Legos together on top. And that's what we've been heavily invested in. And then as we were building Keed, we realized that Keete is just like 95 percent of these Lego blocks that are applicable for anything.
So why not take all this stuff, pack it up for free, we don't make any money on it. and an open source runtime that we're just giving away so other people can contribute to it, but also build their own apps. the more peer to peer apps the world has, the better from my point of view.
and document it and make it really easy to install. And I think actually Paolo said something interesting because as soon as you have, one point of centralization, you can always unravel it. coming from the Bitcoin days, I remember how quickly things can unravel. people went to jail for linking to things because authorities, when they crack down, really hard.
so if you have one weak spot, it will be taken advantage of at some point by somebody. And so even things like distributing updates to your software can be really hard because this often requires a central point, like you go to a website and you don't download it. And so all apps built on our runtime, for example.
It's distributed through the runtime, which is a little bit mind bending. So all apps are peer to peer data applications themselves, and the network doesn't care, which means that we can continue to distribute updates even, if everything gets shut down, you only need like a bootstrap for the first install when you get the app.
So we're thinking that in. At every level, because it's really, important to us to, basically learn from everything that happened in the past and then actually build things that are resilient. And we take this to a degree where I'm sure we could move 10 times faster if we just let go a little bit of that idea, because it is easier to just put all the data in one place or put all the updates in one place.
But then it's then we're just building the same old thing that's going to die eventually anyway. So we're very, uncompromising in that mission of actually decentralizing everything from updates to data, and then also always solving in a way where everybody can take advantage of that.
And then the final thing I'll say about that is that, every time we update. That runtime, those building blocks of that runtime, every time we fix a bug, every time we make it faster, every app becomes faster. That's also very exciting. It's because you're building the whole infrastructure into this layer that runs on your phone.
And it's all somewhat generalizable. Every time we fix something, it's just better for the entire ecosystem. And that's obviously really, exciting. And like I said, actually, no strings attached.
Yeah, so I think you were referring to the trial of the Pirate Bay people there In Sweden, right? lucky enough to meet a couple of them in Denmark and it's been very fun to hear about their journey and, yeah, like
Knut: and there, there's, there was a great documentary made about it called TPBAFK. So the Pirate Bay Away From Keyboard, about that whole trial and how, corrupt the system was even back then. And, throwing people in jail for providing links. they didn't do any more wrong than Google did, from a certain perspective.
And, I remember even, before BitTorrents, there was a program called. DC or Direct Connect Do you remember that?
Mathias: I used to, it was one of my first introductions to decentralization. it as you just shared your, like a Google Drive for everyone or something. Like you just shared parts of your file tree to everyone who wanted to peek into it, Yeah, anyway. Oh, that's good that you didn't know you were going with that. it interesting what you said, because I think it's interesting to think that I think to a large degree, the whole decentralization movement that was happening with BitTorrent back in the day got shut down because At some point, authorities figured out that they could just block DNS requests to shut it down for normal people, and as soon as they did that, it was actually effective.
And to Paolo's point, no matter how weak it is, they're done. and they tried to kill the technology elsewhere, but that's actually what killed them. Then, obviously, alternatives came that people could pay for, and it also shows that people actually want, to stay on the right side of things.
I think, now it's going very much in the wrong direction again, because now we're back at abusing that centralization again. the cycle will repeat. But, yeah, like any point of weakness will be attacked at any point.
Decentralization vs. Centralization
Luke: So what are the drawbacks to decentralization? I think we and our audience certainly understand the benefit of decentralization, what you gain by decentralizing, but what do you naturally give up in terms of the user experience and the convenience factor?
Mathias: yeah, I'm sure Paola has stuff to say here, but I'm just, I love talking about this stuff, so I'll go first. Mattias.
I think it's a really interesting question, first of all, because it's one of those questions where You know, obviously I want to say there's no drawbacks, but like anything, it's a balance, right?
Because it's not that there's drawbacks and advantages, there obviously is, but it's also just a different paradigm. first of all, with sensitization, I think one of the biggest thing I noticed also with developers is that we all come out of systems, education systems. That teaches how to think centralized, which makes us biased towards centralized solutions.
and that's, I remember my whole curriculum was about servers and clients and stuff like that. it's actually really hard to think about decentralization as a developer. And I think that's actually part of why a lot of people think it's hard. It's complex because it is complex, but also because we're just like, we've been trained massively in the other direction, and it's really hard to go back because decentralization can be as simple as what Knut said about DC Connect, DC where it's just, oh, I'm just browsing other people's computers.
That's amazing. That's a really, simple experience, and it's like something you can never do But like in today's world, people, the first thing I always get asked is like, how do I get a username? And I'm like, usernames have an inherent centralization and there's trade offs there.
And we need to think that through and stuff. and most applications don't necessarily require usernames. I'm not saying that's a bad feature, but it's that's where you need to think more about the trade offs because there's governance involved to some degree. But for the core experience, and I think that's what we've shown in Keith so far.
Then, there's obviously tons of upsides also, it's much easier to do big data transfers. Money is less of a concern, which actually changes the thinking, how you think about features.
And that, again, is something we've been trained in a lot as developers, because we think centralized. When we talk about features at Holepunch, hey, we should add podcast recording to Keed. Normally somebody would say, that's going to cost a lot of money to host that data. And we just always we don't even have that discussion because it doesn't matter because it's just between the users.
And then it's more about like the UX. But then other simple, like I said, other simple discussions, let's add a username index. That's where we're like, okay, let's think that through because there's like various things to think about there because there's no centric governance, and we don't want to introduce that because again, one point is.
It's bad. so it's, more like you really need to think differently and it's really hard to wire your brain to think differently. but once you get past that point, I think it's, super interesting. And I, think actually developers care way more than normal people because, developers care a lot about how links look and links and structure and that.
And normal people are just used to just clicking buttons and apps and going with the flow on that. And that's also what we're seeing, I think, with, a lot of key
Paolo: I think the hiring has proven a little bit more challenging, as Matthias was saying, when you are told that the cloud is your friend, hosting, on, Google Cloud or AWS is the right thing to do. And, of course, it got cheaper and cheaper, so now everyone can host their websites.
But the reality is that 70 percent of, the entire internet knowledge is hosted in the data centers of three companies. developers should think about that, should think about the fact that internet was born to be point to point and peer to peer. And, we are very far away from that initial concept.
over the years, especially with the boom in, in the year 2000 for the internet boom, and bubble, then, realized that, holding people's data is the way to go, with social media and social network. That is even worse. And so you have these friendly advertisements that are telling you, That, with a smiley face that, you know, yeah, you should, upload all your data on, Apple cloud or Google cloud.
And in general, cloud backups are great, right? You want to have some sort of redundancy in your life, but the reality is that you should be able to upload those. In an encrypted way, and yet most of this data sits unencrypted because, the big tech companies have to decrypt it and use it for, to milk the information to pay for, for, another month of their new data centers.
the, issue is, we have so much power in our hands through our phones. the phones that we have today are much more powerful than the phones that we, or even the computers that we have 10 years ago or 5 years ago. And so We should, we are at a stage where we can use this hardware, not only for communicating, but also for in the future for AI processing and inference and so on.
is, we need to, understand that the word cannot be connected to Google. I mean we cannot be a function of Google. We cannot be a function of AWS. And so I think that, there is, escalating pace of, towards centralization and it's almost a black hole.
And eventually, the, we'll attract all the lights and if we are too close to it, no lights will come out anymore. And, that's why we want to really to double down on this technology, because it's not going to be easy, right? It's going to be very challenging, and most of the people don't care, as Maite has said before.
Most of the people will think, everything works with WhatsApp and, Signal, but Signal announced that their 2023 costs for data centers and data center costs are around 50 million, and they, apart from the mobile coin that was not The best thing that they could do, there is, it's not easy for them to monetize.
And the problem is that if you are, you're basically almost the only way to monetize it is to sell your customer's data. So if you don't want to sell your customer data, eventually your service will not be sustainable. So the only way to make it sustainable is actually going back to peer, where you can leverage people, infrastructure, people, connectivity, people, phones, people, processing power, Deliver very high quality communication system.
And when they will care, it will be probably usually too late if nothing exists yet. when people will care is because shit is hitting the fan. And, you really want to have a solution that is not, that will survive if, the countries around you or around the country where you live are not going to be nice to your own country.
So that's the view to peer-to-peer. The peer-to-peer wheel system will keep working if your neighbor countries are not going to be nice towards you. That's independence, that's resiliency, those are terms that, we need to take very seriously, especially seeing where the, world is going to.
Knut: Yeah, I think we're all primed for, centralized solutions, from a very young age. this is the state, this is what it is like, state funded schooling. state funders or state subsidized media. We are, like brainwashed into, trusting, institutions all our lives.
So I think that is somewhat connected to why people are so reluctant to be vigilant about this on the internet. I think the two go hand in hand that we, take the comfortable way, or most people take the comfortable route of, not taking responsibility for their own stuff. not only on the internet, but outsourcing responsibility to the government is basically the, another side of the same coin, right?
Mathias: I also find it very interesting, especially being from a small country like Denmark that doesn't have a lot of homegrown infrastructure. And I'm just seeing how much communication with some of the public entities is happening through centralized platforms like Facebook and things like that, where even though we centralize it, we also centralize it in companies that we don't even have any control over in different countries where we probably have, no rights at all.
So it's like hyper centralization, especially from the weakest point of view. And I think that's super problematic. And I'm always. Thinking it's, weird that we're not talking about that more especially when you look at the things that they're trying to do in the EU, they're almost trying to just push more in that direction, which I find even more interesting.
yeah, definitely. it's, a huge problem and it's only getting bigger. And that's, why
Challenges and Future of Decentralization
Luke: So to what level can decentralization actually get there? What is the limit to decentralization? And I'll calibrate this with an example. The internet itself, you said it was built to essentially originally be decentralized, but we don't have it. For physical links, like individual physical links between each other, the fiber or whatever the wire is goes together into another group of wires, which eventually go into some backbone, which is operated by a company.
And then that goes into the global Internet. And so somewhere it centralizes into telecom companies and other services. It might be decentralized on one level, but there is a layer of centralized services that make the internet work that isn't necessarily the so called cloud providers and that sort of thing.
So is there a limitation to how far this can go?
Paolo: I think the, in general, sure, there are the ISPs and, their physical infrastructure is in part centralized, but also you start having redundancy, right? So for example, the backbones are redundant. There are multiple companies running, cross connects across different areas of the world.
Now you have Starlink if you want. that is a great way to start decentralizing connectivity because Starlink will not be the only one that will run satellites, so there will be multiple companies that will allow you to connect through satellites, plus you have normal cabling.
So you will have, it will become a huge mesh network, it's already in part, but it will become more and more a huge mesh network. in general, you will always find a way, even with a pigeon, to start sending bits out of your house.
I think the most important part is, you have to be in control of your own data, and then, you need to send this data with the shortest path to the people that you want to talk to. Right now, I usually make this example, because I think it's When we do this presentation, we try to make people think about how much waste also centralized systems have created.
imagine you live in Rome, you live in Rome and you have your family. Most people live nearby their families. That is a classic thing among humans. 90 percent of the people live nearby their families. Maybe nearby, like 10km, 50km nearby. If you talk to your family, every single message, every single photo that you will send to your family, that message will travel, instead of going 50 kilometers in a nearby town where your mother lives or your father lives, it will travel every single message, every single bit of every single video call or every single bit of every photo will travel 5, 000 miles to Frankfurt just to go back 50 kilometers from you.
Imagine how much government spent in order to create these internet lines and to empower them to make it bigger, more, with more capacity Peer to peer allows with a lower latency, allows to save on bandwidth, allows to save on cost of global infrastructure.
So that's how, actually, We can create better mesh networks, more resilient mesh networks, just because data will always find the shortest path from one point to another.
And still all roads lead to Rome. I'm Italian, so I need to use Rome as an example.
Knut: Yeah.
Mathias: I think the discussion here is really interesting compared to Bitcoin, because it's actually the scaling longer term. Sovereignty, like how, Bitcoin kind of told us very direct terms that if you have a key pair, you have your money.
And it doesn't matter where you are in the world. If you have that key pair, you have a way to get to that money. the means of transportation, it's actually very uninteresting in that sense, because you have it with you. The Internet today, the centralized Internet is designed in a way where, what does it mean to go to Facebook?
it's really hard to explain because it's like some certificate that issued by somebody, and there's. Some, cabal of companies that manages them, there's some regulations around it, but we don't really actually understand it that well as normal people. Technically, we can understand it, but it's very, centralized and it's very, opaque and it's built into the infrastructure in that way, in a bad way.
And, with Pure Technology, we're taking the same approach as Bitcoin here and saying, You're just a key pair, and the other person is just a key pair, and there's a bunch of protocols around that, but the transportation is actually not that interesting. Right now, we use the internet to do it.
We'll probably do that for a long time, but there's no reason why we can take the same technology we have right now and in 50 years run it on, laser beams or something else, because we're taking the software and feedback.
Bitcoin and Holepunch: Drawing Parallels
Mathias: I think, that's the main thing to think about in that. Discussion.
Luke: when, Paolo, when you were talking about that people don't care, when you were saying that people don't care because WhatsApp just works, I was at the same time thinking that's the parallel of people saying that, I don't care because Visa just works, right? And so the parallel between Bitcoin and what you're doing at Holepunch, Keet, everything else here, really seems to be tracking along the same line.
And I guess there's the connection that, I won't say all, but a lot of the people involved are already in the Bitcoin ecosystem. But can you comment on is there a little more of a connection there between Holepunch and Keet and Bitcoin?
Paolo: Yeah, Bitcoin definitely is working and servicing, I think, in a good way, many, people in communities. The users of Bitcoin today are, unfortunately, and also that relates to Tether, mostly, in the Western world, in the richer countries, as a way to save wealth and, as a store of value, more than a means of exchange.
For different reasons, right? We'd like a network that would improve, of course, over time, and there will be different approaches, but, still, the world is not yet using Bitcoin, but the world will use Bitcoin when shit will hit the fan. but the beauty of Bitcoin is that an option is already there, is available, and when something bad will happen, people immediately, with a snap of a finger, will turn to Bitcoin, and will have it and can use it. don't have that in communications. What is our communica our parallel with communications, if we don't have it? I don't know, because if, if suddenly centralized communications will, be blocked, then, or privacy in communications will be blocked, and you cannot, you cannot use Whatsapp, or Whatsapp has to start giving all the information to every single government.
and the government will become more evil than what they are today, also western governments then. don't, we wanted to build the exact parallel as we said it, we just tried to describe it, that with Bitcoin, for communications. We need to have something that, since there are so many alternatives that are working as with your, you can make the parallel with Visa, right?
Visa is working today, so people are still using a lot of Visa, but if something will happen, they will use Bitcoin from one day to another. Whatsapp is working, and Zoom is working, and Google Meet is working, so people don't feel the urge, but there will be a trigger point when people will feel the urge at some point in their lives, because something happened around them, and we need to make sure that kit will be available to them.
and will be an option, will be stable, will be well designed so that when they will need it the most that option will be available to them.
Luke: Yeah, fantastic.
The Future of Decentralized Communication
Luke: And so I think the follow up I have, and just to get back to the earlier discussion a little bit with Nostr, the communication in terms of messaging, I absolutely see that and directly in what Keet is, I already absolutely see that. Is there a goal to get somewhere towards more like Social media, social networking, things like that in a, in certainly a decentralized way, but right now there isn't something like that as I understand it, coming from, Keet.
So is, that a goal? Is that on the roadmap?
Paolo: Yeah, it is on the roadmap, it's something that, so we had to start with the thing that we thought was more urgent and also the thing that could have been, would have been a game changer. social media is very important, especially In difficult situation, you want to get news, and you want to get unbiased news, so you want to use, social networks to see what's happening in the world.
But we, think that the most sacrosanct thing that you need in your life is to be able to talk to your family and friends in any situation with the highest privacy possible. that's the first thing that we tackled, and also was a way to battle test the technology with, KIT you can do high quality video calls as well, so if we are able to tackle in the best way possible privacy and extreme scalability of peer to peer communications, then on top of that foundation we can build also social media and every single other application that we have in mind.
Mathias: But first, we wanted to tackle the hardest problem. No, I think it makes a lot of sense. And I also just want to say, as a, probably like one of the most prolific KEET users, I use KEET right now also as a very, like a social media, we have big public rooms where we talk about KEET and talk about technology. I get a lot of the value I would get otherwise on Twitter X from that because I, it's like a public platform for me to, get ideas out there, but also interact with users directly.
And I think, there's many ways to take them as a young app. And we're talking about this a lot, obviously it has to be simple, has to be parent approved. My parents can figure it out, but I think, to a large degree, all really healthy social networks that are actually, to some degree, a communication app.
And it's also just a really good way to get local news and to get this locality that Peter is good at. That doesn't mean that we might not also make other things, but I think it's a hard line to set the difference between a social network and a communications app when it's structured correctly,
Interoperability and User Experience
Luke: Yeah, and this, another thing that came to mind just as, you were talking about these parallels, as, I understand it, the account system with Keet is, essentially still just a, Key pair. Correct me if I'm, wrong,
Mathias: Very, true.
Luke: you backups with the same 1224 words.
Is, that fully interoperable as well? Is that, could be your Bitcoin key. That could be
Mathias: We use the, same, I can't remember the date, the BIP, but there's a BIP for like during key generation. So we can use it also in the future for other things. and you have those words, you have your account, and that's, we never store that. And that's like your sovereignty and, no, I was just going to say that lets you use it seamlessly on different devices also. It's one of those things that I love because I know what's going on when you use keyed Insanely hard problem, but it's solved by the runtime, and it just works seamlessly and I think that's, the beauty of it.
Paolo: I think there's some UX stuff to figure out about onboarding that stuff a little bit easier for normal people. That's probably to a large degree the same for Bitcoin. The other part that I would do with Bitcoin is that, with Bitcoin, with your 12, 24 words, you can access your private wealth. the beauty of Bitcoin is that you can remember 12 24 words, you cross borders, and you carry with you your wealth. You can do the same thing with your digital private life.
You remember 12 24 words, they could be the same by the way. whatever happens, you can spawn back your digital private life fully encrypted from, one of your other devices that you connected that is somewhere else in the world. So when you start seeing and understanding the unlock in terms of also human resilience that this creates is very, insane and can create a very powerful, that can be used for, to create a very, powerful applications, not just communications, but you can build.
Really any sort of interaction, even mapping. Imagine peer to peer mapping, where basically data is not stored in one single location. You can access, tiles of the maps, from, local people that curate them in a better way. So the, level of applications that you can build, All unlocked by the same technology that is being used by Bitcoin is very, incredible.
Luke: Yes, absolutely it is. And what do you think of the idea that all of this stuff is just interoperable now based on essentially you have your private key and there you go. It doesn't matter the technology stack. Is that sort of an agnostic thing where you can take your data to any one of these systems?
What you're building with Keith being one, Nostr being another, Bitcoin being a third, what do you think of that?
Paolo: Yeah, the fact that, data is yours, right? So you should do whatever you want with your data. That is, I think, an axiom that we should assume. And, it shouldn't even, we shouldn't even discuss about this, right? We are discussing about it because people are trying to take away this axiom from us.
The, you are a key pair, and you're basically, unique, and uniqueness is expressed by the cryptography around those 24 words, and that's, that also is a way to prove your identity, it's a mathematical way to prove your identity.
No one can steal that from you, of course, but no one can track it as no one can impersonate, should not be able to impersonate you. So it's truly powerful.
Mathias: also think it's like worth remembering here also in this discussion that a lot of very high valuable data for yourself is actually not that big, but centralized platforms take it hostage anyway. if you take all my chat history and, I have pictures, but like a couple of the pictures would probably be bigger than all my chat history ever.
but a lot of that, those messages have a lot of value for me, especially personally and also being able to search through it and have infinite history, it's very valuable for me personally. But it's very scary for me if that's on some other platform where it gets leaked at some point, et cetera, et cetera.
But we already have the devices, just normal consumer devices that we buy, that we all have, phones, computers, whatever, that have more than enough capacity to store multiple copies of this. In terms of like per user, data production, it's a manageable problem.
And I think it's interesting how, providers force us to think in terms of giving that data away, even though we could easily store it.
Paolo: And this is even more important when we think about potential, AI applications, right? So imagine your best assistant. Paolo's assistant should go through all my emails, my kids chats, my old social stuff, and be able to be my best assistant. But in order to do that, I have two options.
Either, I imagine that OpenAI would come with an assistant. They would upload, All the information on their servers, crunch that information, and then, use it to serve, me, but also service their own needs. And that can become very scary, also because they wear a hat. It's public, right?
you don't want your most intimate codes that your best personal assistant could know, to be on somewhere else, rather than your devices. And so people were, people never uploaded, at least most of the people would never upload medical, information on Facebook, right? But they are uploading it on ChatGPT to get a second opinion.
so things can be, get even scarier than what we described today because, we, discussed about social media, that is basically, the fun part where we upload photos, But, things can become scarier when it comes to privacy and data control with ai.
So I want to see a future where I have a local AI that can read all key messages that I have from my local phone on my local device, and can become the best powers assistant possible without renouncing to my privacy, and also still governed by the same 24 words. the fine tuning that is applied on that LLM should stay local to my own device, and it should be in control of that.
And still, the current power of the devices that we have makes it possible. We should not fall for the same lie. We don't need, of course, big data centers with GPUs are important for training a huge LLM, but that is a generic LLM. You can take that one and then fine tune it with your own data and run it by yourself.
And for most of it, unless you want to do crazy things, that is more than enough and can run on modern GPUs or local GPUs or your phones. We should start thinking that we can build local experiences without having an API all the time connected to someone else's data center.
Knut: Yeah.
The Role of Tether in the Crypto Ecosystem
Knut: It's super interesting. you briefly just briefly mentioned tether before and I think we need to get into this. what is it and how much of a maxi are you, Paolo?
And, what, made this thing happen? Can you give us the story here about Tether?
Tether's Origin and Evolution
Paolo: Tether started in 2014. I consider myself a maxi, but running Tether, you could say that, I'm a shit coiner. I don't mind, right? I like what I do, and I think I'm net positive, so it's okay. Tera was born in 2014 with a very simple idea. there were a few crypto exchanges in, 2014.
it was Bitfinex, Coinbase, Kraken, Bitstamp. OKCoin, there was BTCChina, and just a few others, right? Around 10 that were meaningful. The problem back then was to do, trading arbitrage, you sell Bitcoin on the exchange where the price is higher, you take the dollars. From that sale, you move the dollars on the exchange where the price is lower and rinse and repeat.
That is called arbitrage. It is a property of every single efficient financial system. And that also helps to keep the price of Bitcoin in line across different exchanges. But, that was very, hard in 2014. If you remember in 2013 was the first year that Bitcoin broke the 1, 000.
But on some exchanges the price was 1. 2, on others was 900. in order to arbitrage that price difference, you have to move dollars from one exchange to another and Bitcoin from one exchange to another. You can move Bitcoin from one exchange to another. 10 minutes, but dollars would take days, right?
International wires. And so of course the opportunity arbitrage was, fully gone by, the, time the wire was hitting the, receiving exchange. the reason why we created that was, USDT was simply to put the dollar on a blockchain so that we could have the same user experience that we had with bitcoin.
For the first two years, almost no exchange apart Bitfinex understood USDT. Then Poloniex in 2016 started to add the USDT across for against every single trading pair. There was the start of the ICO boom. 2017 was the peak of the ICO boom and, USDT reached 1 billion in market cap. Fast forward in 2020, we had around 10 billion in market cap, and then the bull run started, but also another important thing started, that was the pandemic.
USDT's Impact on Emerging Markets
Paolo: So the pandemic had a huge effect on many economies around the world, in all the economies around the world, but especially in emerging markets, developing countries.
Basically pandemic also killed entire economies. And so as a Bitcoin you would think, oh, all these people that are in countries like Argentina and Venezuela and Turkey and so on, they should use Bitcoin and they should, they should, only use Bitcoin because everything else is cheap.
So that is pretty much, the approach that we have as Bitcoiners that, I believe in. But the problem is that. Not everyone is ready, so not everyone has our time to understand Bitcoin. Not everyone has yet the full skill set to understand Bitcoin at this stage, at this moment in time.
we as Bitcoiners didn't build the best user experience in the world, right? So one of the best wallets for Bitcoin is still Electrum. That, is not necessarily nice and well done for and simple to be used for, a 70 year old lady. so we need to do a better job as Bitcoiners to build better user experiences we want Bitcoin to be more used around the world.
At the same time, 99 percent of the population knows, especially the ones that are living in high inflation areas, knows that there is the dollar that is usually Much better currency than what they hold in their hands. the US dollar is not, definitely not perfect. It's not the perfect fiat currency. but it's like the tale of the two friends running away from the lion, right?
you have, one friend tells to the other, Oh, the lion is gonna kill us. We have to run really fast. And one of the two friends says to the other, I just have to run faster than you, right? So the US dollar is the friend that is running faster, in a sense that is the one that is likely better than the others.
And so being better than the others is creating a sort of safety feeling among 5 billion people in the world that live in high inflation countries. And for those people that, they don't have yet the time, they didn't have the luck also, maybe, to understand Bitcoin, they are, in fact, using USDT.
If you live in Argentina, peso lost 98% against the US dollar in the last five years. The Turkish L lost 80% against the US dollar in, the last five years. So of course, Bitcoin would be better than the US dollar, but even already, if you hold the dollar, you are the king of the hill there, right?
So because it's, you are able to preserve your wealth much, better than almost anyone else in the region. I think, USDT is offering a temporary solution and is providing a service, a very good service to people that don't have alternatives and good alternatives and they are very, familiar with the U.
S. dollar already. so eventually, the hyperbitcoinization, I think it will happen. there is no way it won't happen. It's hard to pinpoint on a time when, that will happen. But it's all about the turning point. What the economy will look like in the next, 10, 20 years and what trigger point there will be for fiat currencies to blow up and become irrelevant.
Bitcoin as a Savings Account
Paolo: the way I see it is that it's likely that the U. S. dollar will stay around for a while, and people might still want to use, the U. S. dollar as a checking account, but they, should start to use, Bitcoin as their savings account, in the checking account, you, are happy to not make interest, It's something that you use for payments, it's something that you are okay to detach from because it's the money that you are ready to spend.
The savings account is the thing that we should fight for. This thing is the thing that matter the most, and, it's the thing that will is protecting people wealth. And so in the long term. And in the medium term, we should push for this savings account to be Bitcoin. also with Tether, we are heavily investing in companies, in Bitcoin companies.
we support the Blockstream. We supported so many in the space that are, we, are supporting RGB. That is a protocol that is building, assets on top of, like network, style channels. Thank you for listening. and we buy Bitcoin ourselves. We do a lot of Bitcoin mining.
We develop, I think, the best and most sophisticated Bitcoin mining software, by the way, based on hole punch technology. It's like IoT for Bitcoiners and Bitcoin mining. It's very cool. we are relying on the dollar and, you could say that USDT is helping the dollar, expansion, but the same way I don't think Dollar and Bitcoin aren't necessarily opposed to one or the other.
I think that Bitcoin has its own path. And no matter what happens, there is no way to slow it down. I think, it's going to be inevitable success. It's going to be inevitable that it will become global internet money and global words money. No country will trust to each other with, with each other currencies for, for a longer time, and so the only viable solution is a currency that is governed by math.
That is the only objective way, objective thing that we have in the universe. that's my train of thoughts on, Tether and Bitcoin.
Knut: Oh, thank you. Thank you for that explanation. It explains a lot of things. To me, it sounds a bit like you're a lubrication company, like selling lubrication for the transition between the rape of the dollar to the love fest of the hyperbitcoinized world, to make the transition a little smoother.
Paolo: we are more than, at Tether we have also this educational arm and, believe it or not, the majority of the creation we do is actually on Bitcoin, right? So we are supporting the Plan B network led by the great Giacomo Zucco. The unfortunate thing is that USDT, didn't have a marketing team up to, 2022 with Tether.
So basically, I wish I could say that success of Tether is because we were super intelligent and great. but actually the success of Tether, unfortunately is a symptom of the success of, of, national economies. And it's sad if you think about it, right? So the success of your main product U as it is, They're actually proportional to the FACAP of many central banks. And, but it is what it is, right? So we need to do what we do at, really, at DataRace, creating all these educational contents to try to explain that, sure, we are providing a tool for today, but, For tomorrow you probably need, you need to understand that you have other options, you need to understand Bitcoin, because as we said for, Keith, right?
So the moment when you will need the most Bitcoin, it has to be available, you need to understand it, so that is a true option for you. The way we, see bitcoin education.
Knut: No, and, something like Tether would have, emerged, either way, and it's very comforting to know that it's run by Bitcoiners and not by a central bank itself or something. yeah, and the Plan B Network, I was a guest lecturer there in Logano and it was fantastic.
I love what you're doing there with the educational hub. And we even got Giacomo to write the foreword to our new book here that you can see here behind Luke.
Luke: Always say the title, Knut. Always say the title.
Knut: Bitcoin, the inverse of Clown World. It's, you, if, you're good at maths and emojis, you might be able to figure out the title from the cover, but it's one divided by Clown World anyway, which is on the opposite side of the everything divided by 21 million equation, So anyway, looking forward to seeing you in Lugano and giving you both a copy of the book, of course.
Paolo: Oh, with pleasure, with great pleasure, with a nice, education.
Luke: Absolutely. Yep.
Plan B Forum and Future Events
Luke: 100%. And we have to wind things down, but I'll just say as well, yeah, absolutely looking forward to Lugano Plan B Forum. Always a highlight of the year. It was my first time last year. I absolutely loved it. can't wait to attend this year.
so it's the 25th, 2020 6th of October, 2024. this year, it's a Bitcoin event that is not made to make money. So the problem with events is that. You have to find sponsors, and usually, sponsor might not be well aligned with the message you want to give, right? I think Tether is lucky enough, to not have to make money on the event.
Paolo: I want to have, good, guests. I want to have great speakers. I want to have the messaging. That is not only about Bitcoin, it's about, freedom of speech as well. We had the family of Assange for the last few years, and I think that they will come also this year.
I'm going to be probably killed by the By our marketing team, I'm not sure if they announced it, but we are going to have another Plan B event also in El Salvador next year, so we're trying to create this network of cities and countries that have things in common and, invite people that want to share knowledge around the world.
And, yeah, and of course we, are very proud of the good food that we, serve in Lugano. So that is another thing that, not all the bands can say the same thing.
Knut: No, it's fantastic. And we happened to bump into the Assange family at the cocktail bar in a fancy hotel and, had a very interesting conversation with them there. So if you're listening. Anyone from the Assange family is welcome on the show any time. So yeah, no looking forward to that event for sure, we had a great time.
And I think we're even playing this year, aren't we, Luke?
Paolo: You're
Luke: yeah, the Satoshi Rakamoto is in the event there, we, played, back in Prague, it was my first, time, but Knut is a regular at the Rakamotos.
Yeah, we played at Lugano last year Oh, anything and everything, what did we do in Prague?
Knut: paranoid and,
Paolo: Can I commission a
Knut: What song would you like to hear?
Paolo: I have two that I would suggest. One is Nothing Else Matters.
Knut: Alright.
Paolo: So I think that, is very inspiring, right?
Knut: Bitcoin, for sure.
Nothing Else Matters. it's perfectly aligned with Bitcoin. And, the other one is Sad But True. Oh, that would be fun. We'll squeeze in some Metallica there, won't we, Luke?
Mathias: we'll 100% have those songs ready to go. We also have, a big peer to peer track at the conference,
Knut: Yeah.
Mathias: not so much music, but yeah, that's peer to
Knut: Nothing else matters.
Luke: looking forward to that.
Knut: Sorry, brain fart. Sad but true is about the dollar still being around,
Paolo: Yeah, you can say that.
Luke: Okay.
Final Thoughts and Closing Remarks
Luke: Hey, we have to wind things down here because, we're, almost, out of time. So I'll just hand this, back to you both. Is there anything else you'd like to, mention about, your plans in the upcoming couple of years, in, key, toll, punch, anything like that?
Mathias: only that we're, like I said, we're integrating really hard right now, and it's a really fun time to, join the company because, we're small and efficient We get to work with Tether, which has a lot of benefits and it's getting really fast, so definitely check that out. And it's also a really fun time to join Keith in our public rooms.
There's a lot of very personal, in a good way, intense chats where you get to be part of the loop. I love to be part of those early communities and I would suggest everybody to check that out and go to the website and try it out.
Paolo: we will certainly do that. Yeah, I couldn't agree more. So go check out Keith and Holepunch and the Plan B forum in Lugano, You could visit tether. io, that is, the website where we are trying to explain what we have in our minds between, finance, bitcoin mining, energy production, AI, communications, brain chips and stuff, right? I think it's more exciting.
Mathias: Just those things, that's all.
Paolo: Yeah, we can piss off more than this. Thanks.
Mathias: a
Luke: No, It's just perfect. and is on that note, is there anywhere else specific you'd like to direct our listeners?
Paolo: just follow the social channels and give us feedback on kit all the time because these technologies, needs everyone's help to be nailed them.
Mathias: We love technical feedback. We love UX feedback. We're trying to make something that works for the masses, so anything is good.
Luke: So that's, all at Keet. Is that correct? For Keet?
Mathias: Key. io and pairs. com for our runtime. It's all peer to peer.
Knut: Alright,
Mathias: Wonderful. And you're also still on the legacy social media platforms, right? Yeah.
Knut: we'll make sure to include links to your handles so people can find you there if they would like. forward to seeing you in Lugano.
Paolo: Likewise, I
Knut: But yeah, worth saying again.
Paolo: Thank you for having an invitation.
Luke: Yes, we'll wrap things up here. This has been the Bitcoin Infinity Show.
-
 @ 8cb60e21:5f2deaea
2024-09-10 21:14:08
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08 -
 @ fd208ee8:0fd927c1
2024-09-27 07:10:40
@ fd208ee8:0fd927c1
2024-09-27 07:10:40Let's talk about baking bread
I've mentioned a few times, how large-scale central planning leads inevitably to artificial scarcity and rising prices. Allow me to illustrate -- using a completely invented allegory about bread -- that has absolutely no parallels to any economy you may already be familiar with.
We start with 20
Let us say, there is a group of 20 people in a village doing something that requires some niche skill and interest, but not inordinate amounts of talent or uncommon knowledge, such as baking loaves of bread containing emmer wheat. This is not an easy thing to do, and you'd have to read up on it and practice, to begin with, but it's not an insurmountably-high barrier for anyone who already knows how to bake.
Now, they're not baking all that much of this bread, as the market for people who want to eat it, is still rather small. But, they're happy to bake the bread, and sell it below cost (at $10), as they can see that the market is steadily growing and they know that there is a possibility of recuperating their investments, and maybe even turning some profit. They hope to eventually profit either directly (through the selling of the bread), or indirectly (as A Person Who Helped Invent Emmer Bread), or ideally some combination of the two.
They are baking away, and honing their baking skills, and scrounging up the money for bigger and better ovens or cleverly-arranging discounted contracts for slightly-larger deliveries of wheat, and more and more bakers see this activity and wander over to their village, to see how this bread is made. Well, the current bakers are starting to sink under all of the bread orders they are receiving, and customers are complaining of late deliveries, so they start to ask the 10 visiting bakers, if they would like to also set up a bakery and take some of the production off of their hands.
We now have 25 bakers
The visiting bakers consider it and 5 agree and the rest wander off again, as they already are quite busy baking the bread they've always baked, and they aren't as certain of the possibility of growth, for this new type of bread.
The 5 additional bakers take a while to setup shop and assemble staff and place wheat orders and etc., but after a few weeks or months, they are also adding to the bread supply. There are now 25 bakers, all completely booked-out, producing bread. The price of bread has fallen, to $8/loaf.
And the bread they produced! All of the bakers competing for orders and expanding their product lines and customer base quickly lead to the white emmer bread being followed by whole-grain emmer bread, emmer dinner rolls, emmer-raisin bread, and even one rebel daring to bake spelt-emmer pretzels because... Well, why not? The customer, (who, at this point, is the person eating the bread), gets to decide which bread will be baked, and the pretzels sell like hotcakes.
The emmer hotcakes also sell like hotcakes.
No baker is making much (or any) money off of the baking, but they all can see where this will end up, so they are still highly motivated and continue to invest and innovate at breathtaking speed. We now have emmer baking mixes, "We luv emmer" t-shirts, emmer baking crowd-sourcing, all-about-emmer recipe books and blogs, etc. The bakers see this all as an investment, and cross-finance their fledgling businesses through selling other bread types, their spouse's day job, burning through their savings, or working Saturday night, stocking shelves at the grocery.
Everyone can be a winner! Everyone can find their niche-in-niche! Everyone can specialize! Private enterprise for every baker, who rises and falls on his own efforts alone! And although everyone was competing with everyone else, there was no bitterness, as everyone could clearly see that effort and reward were in some sort of balance.
We are now short 3
But, alas, that was not meant to be. The joy and harmony is short-lived.
A gigantic, wealthy foundation, who is dedicated to "ensuring much emmer bread will be baked, by financially supporting emmer bakers" enters the chat.
"We have seen that there is much baking going on, here, but just think how much better and more baking could be done, if we financed your baking! Isn't that clever? Then you could really concentrate on baking, instead of having to worry about financing your business or marketing your products. All you have to do, is apply to receive our baker's grant, by signing this form, acknowledging that you will only bake products containing nothing but emmer and you will otherwise support our mission. We promise to pay you $100/loaf."
The 2 people making spelt-emmer pretzels, and the 1 person making spelt-emmer cookies, refuse to sign on, and slink off, as they are very convinced of the rightness of including spelt. One emmer-purist baker refuses on some economic principle that nobody comprehends, and immediately turns around and goes back to work in their bakery, with their shoulders hunched. But the remaining 21 bakers happily apply for a baker's grant. The mixed-grain bakers are upset about the breakup of the emmer market, and spend some time sulking, before wandering off to the new, much-smaller, spelt bread market, that is setting up, down the street. Where they sell their bread for $6 and slowly go bankrupt.
And then there were 10
2 weeks go by. 4 weeks go by. Baking has slowed. The grant hopefuls hold a meeting, where they discuss the joys of baking. Baking slows further.
Everyone is too excited, to find out if their new Universal Customer will be paying for the bread they bake. $100 a loaf! Just think of it! All of the bakers quickly do the math and realize that they not only will turn a profit, they can buy themselves a nice house and a new car and...
Nobody listens to the complaints from The Old Customers, who are the useless individual people only paying $8, despite them slaving away, all day, in front of a hot oven. They should be happy that they are getting bread, at all! Instead they complain that the bread is dry, that the delivery is late, that the bottoms are burnt. Ingrates.
And, then, the big day arrives, and the foundation happily announces that they will be giving 10 lucky bakers a grant.
The bakers are stunned. It had seemed that all of the bakers would be getting the grants, not only part of them. But, of course, the Universal Customer looked through the applications and tried to spend its money wisely. Why give grants to 5 bakers, who all produce the same type of olive-emmer bread? Give it to one, and then tell him to produce 5 times as much bread. He is then the olive-emmer bread expert and they will simply keep loose tabs on him, to nudge him to bake the bread in a sensible manner. And, of course, he shall always focus on baking olive bread, as that is what the grant is for.
The bakers stroll off, to their bakeries. Those who baked olive bread and received no grant, close up shop, as they can see which way the wind is blowing. The other grantless bakers reformulate their bakery plans, to see if they can somehow market themselves as "grant-free bakers" and wonder at how long they can stand the humiliation of selling to demanding, fickle customers at $8/loaf, when others are selling at $100/loaf, to an indifferent customer who doesn't even eat it.
The happiest 10 bakers leave for another conference, and while they are gone, their bakeries burn down. Their grants continue to flow, regardless, and the actual bread eaters are now standing in line at the last few bakeries, paying $20/loaf.
The End.
-
 @ a03b38f8:2c7ce1f0
2024-09-12 19:16:50
@ a03b38f8:2c7ce1f0
2024-09-12 19:16:50-----BEGIN PGP MESSAGE-----
wcDMA17V9MGW3LFGAQv/erNSJ4ooO6fERifSPB0ENbX8V+XEMeoq4DXt/EyRdeBP DpettdnDboZWnaJz2g3fk6VUAeSNH+ZqKW67LSNEg/qk3L7AdcxrVji1DJhfQ8WR K3r/iQzSO8OXSWsez3yEXhmJSy6fwFS/D6kHpCcHu3wo4fipLLJ96lkMpUd0zzir JDw7atRjI7LfulDwfIuFk2hAXEDrWJkPosdZ3g9cCayfzV440WvAMN0K7pv6OQp+ I7Zxf6KsMB5hNz3yEQRJIspqaQaI7gdNqEkfkdCkTw5wfmhlyKVgukvSkrIGe6Cb WEXBpO/QKMsY4HBOiPc/Mu4i4gEQlSZxGDNiGB6AkWz7o0hEiT+ugXIdMXl/ACH6 DhBOWOr2JQtHo70z5mpiqAkbG2lFcPnSGXikCIZ1ONh/eJiM7ZbpRcPZ+Vo7veAQ 3dfrB5g32cmVteL8T9H3bL88uP06FoRqQU6YmdKtu101SpEkXzAP46NDZ0re54QA IPxCy8t1BcjAfDmtuHsW0susATLI40nPziahKfLA7iOYhpUsHT9tnZm63g1uIwGF MlT377PJydN9hTAQbxTsfNSPws8/OoHzE5UeEQehFhOKxjw0lslM3HQhsgYVN6F6 6/ileO7LsJo9UPVd5D5Qy1qGwBWKl5wZk80Io5kJlvHp3BjFDfjCsPUXmmc1Kh8J Yn6wiFzm6Ti6rBDxuZSCbcyRhebOi+ZKnkzra+4rwy5BYPArj+N0mbwUbMh+1DR5 86m683N7bOMJkOYfjXxm00PTz17usJLzfPmcqkUE9x4RC8p/huz7MmCFhnTVedOl io4RHg2iV0hgUf0ybuO49ROuEB9B/nrqpdUYiL2PVUKUkVnFRQ5XZvKr9/4pUh95 eTrLCUYP5+X1IZfoF8nHEy4D/HuHQGdtAeCADvARB0nnTphIV9YUBpCuq1MWKkBa iSWnD4X9ErodF8aGaVG2Cvh/BlMMl5CkHlzZUHJEedrFllLTZNdCgmDggduGzq5n iD2FdKz9O2MrNEbBu5o2NHOvFcs5KFFfqUeb028kOxNnTozPO5sMZJYZvlQCPBv7 eeWsM6WRPq6lB8xSZAO3yRlBa/EEvMU9k8qBq56G91dNYDUu03kS/WBzUZYoCS5e YLhpn8Jb5XP4HJdct/VPKmpzPRBzj7Xyeqc3hZdj6/uF2fMngmCt2IeNQjsZrjKQ mszv/A7huvTbU9wUdA8ssrkD4GLeg6q1a7WNBJ12SkoOK1ld+g6s6k4Z6UwSJVgc R9JtPC77A+/kyRgPJW6JdEmlZXYpagtPRP/eIt52IMByQ9s/L7HkYO/FGPMok9Yb 1X6NLh+3CQMBkscuUcUbWjsWGVrJxqQYdMBnXuvCUDILPm3NrRBUO8Y9yieG/lwT kG1d/90WrjgtGO3Bny3UgsEap2RZ/91KN8dS6+PfgqBUc8nQV7zpsxDGfvLFryFF GBLKtv6IbWw8mYqPMBrf/q8a06+TVtUkIYxlhmfxut+Zpf+o99Ph81CH90PO290M 1FxBwL7j4lqFeYoQSz9Xs6wrJ6V+F9ORwVXpPqdJGSYNcBUhk9inIo/imyhdd0rV u0V1NkepX9DmP/vRdu4e1VJJoh70XOQImfa+92DP01B6sGq5Ah1/b5/U6LOml5Nj 7kC/RPLs/R0yZ8eGZW04MuDLu3flZtkvgsw2RNutlrFyN/pdHksRa+4qgyIAY2q2 2+iGtKZ5ksTYY53WoRmnMzz3Pwkb7Vw6/ROpJB9qrSTkNtZ3DIgavXznmMGfg5Yx AcoEElg3Why65wMSUXXeenW/0UUVfyZZJhV5822I3/b9wJgkRsA2G3+Pqu4Fw3Xs OnsSRIj7Wcg3RFvld/2Su05LO8zzQKzt5+JbG689J4Mb4wc8s4/o3vgF6J8+GR7G a081oL0gStqNRAL5dgXwqdFswEpYu3mYROVjZlsM+Yw6i5JsyzDtDjyJJs6A+Jxx 0yCQ/21lkc4n3RGItFce2JVogBs+0YkL8tqDZnhtDtPJgp0t9t8L7Po55sGHnigE faBdbpVfJEU6G7qGS5/xxv9Pkw4qTTV/5ENGPybfQ4CGgLUAWkGaT1PTNa7x3i65 TDF+N5heKXOwuTg+18oCvYpGxVTDmboSaqc835dExoP1r9GZ9zgODXM9+034GNP7 DmuKnw5tyJlF7lZjXioWmer1RCFGyicsI9XaXqqYsQiAo0EZzArA5lri5cnxIa6g 6d88gkOjMV+6mGnXfpm8Cb8pl5dGmsWo7vZdoFDK5a/6ueDqp7yj20Kug672Of32 R5LUUiwr0IslCAaYwraU/Tv2PvS1JERoN1YE6clUEFaraSOO3099/duxPa5vgNbs l8tG2gyuRFtqcGEio8bUqlNnpsg2KM0Cs3SOUx7siXpQzcatx0kvffFNdt8CAsTh xLu8byxoFxlJp6meNMjSNOO37kkZ8DgjyUdwfhpCf4/Lfzox/te2ulC4/6Jccc28 rbeFTRw536IAEQYW0R+m7iL5HVmC8K0xO6k98ESo8TVSW3+gHdwkBXtuwqIl8iD5 bxnbqUtrmnfyYe32SZZVtyaUUtFjwfJ3crsdTWJmSrsd54ZNRzfs8R9ymnQEU+EW Fngulk2/NiU7Nw9rzoW6o35DsrLXFFpoNbEotVn8Pqb+8bDWwhXIY1tC0VQq6D9p 9l4s2ZB+ps2N5iGsijIvdSNNiLttZl+NFUnyQOAn+hbbb8R9GsGWam9thrdBMRNo hUSxRTgWRUqEQ6Tue8vbG+S/CylaAaryF1nz6ShRBegluI5ivyUV8MbxiSTKo2r6 MRYXGp2j4K0vADDjd2M8gwgmancszgZxjN9XTeO/xhWQ1Ed8SEI87I6ymQA7nXTm Cn5fMHdht+uOMdZ3CHOXO+YWoxsOpq60K2lkldb/Cv1s9F9gZqXC6aauPZ9un6K5 p7/1Kje7ATFgUrfcsNMuI04qobJc7QiiQJLf3yoQ64bF3GHXQmUfxJurQ9nUg0oW rETBdT4gz3eDS6ApbSXnUIV+SSbQTWCBGkqJddjYtoYTONBkZFTLg9yYdAw43+8P 9mv5Mwe5nocd2322W1zQj/npUDh1H61UQTIsZHUY66/KNprNi4PLawEFy1MpJiE0 0UT4Xhbw+3/ynIYy+ibAj71O4ymslzbz7P/zn/vR8iy8ZY8o0riMtwE8v+nBRWEs uwG/kW7vjPYA5RZkYLRz3LNnrlfiOgd7eCoFc2PU/c9NdBT0+pZQbudXiMW+eX6C FZY3oh+6heTuWF1kzyQy9RCDx43XSg/GON5Vy2pD/+24CDpscE6AObLGCWQoVYxk KQUwx85iomVWijRkWC7Nm4lTUIH8jnA5BZxyhymPbUttoUOiN+z2umtgNUfIp1L7 CwFAs0VThseHny/ra7q/5rmepP1s98ojcyBF3YD3o+Wy981R61e1v/c4L2P8iSZC LMyVSK+pWWaMLWIdFBSR8Ke/vDS1pz8GAeAdcXRQRjVw1l/aIQPXYNKJ0S6kNbQ0 IwnYdiMuOXEkhOlnFsUV1uiSN2LY6W8/Kk2cxcwheCgTkk5ibKl39VFsy9h2vxiP +ecjDnAGrR+ZJV958zrnnt7gosr2Nm/VUSlU/NbFlXE2kIhhulyd/M2GGKrj3j70 lD1HRjUjrSLrZsirdITG4VbYIIq/00K4x3hYbcY8R6ROrCJemdE4DUkDvirYZ7rU yEhbpuo2oz/KjubgPKAY9srkJ8Tv8dcZQR0c2XfpohAzl5ctv3Ai9c0LW+eePUSk RtgOnges73+WImv5rgjYv2y7eeupXgnAMcndFF490vUk3+B3F/LafsFNLSVwqJUL qhimUv+84J6/G9uG6xEc6b+4B1VMvmM7/cFmjZYRRvBxvBaOTyjP1OMe69TgKM69 H73haTEA0QEwenRxQq0tKqCo2fygK0uVkFSGQ3dRDh6QueTVRzbmopKwWrSMw3ye +NjpdRR8tBj95bTj7YvesJP7z0WqtHj6N8FJt+VY9bfAHB97oCc3QziEmdY+lpZe 37PMAY6JN2chQ8HuwPpgWe5JmhiO09w8DgYcQnOJqVl4UQulkJvti7i4VDyMY8Z+ hxiNDsb8agY03zAchgLN6cXrpall5/XDzGVBbnbnccVS/x7L0Dr940+AF6yKi1mD 0l79sqWjT5nNHmf/ni5YXfLU+4ajSHWOm4yLaqWRjTSTUh/41v9iHqQwPj4RgBZP 1/fFy4HpM5kBMSYlCFFLPrY2OFqFX8yw1HyRn39W62FETIH4CASdEF5ieJ44CWef L/TwrLaS2R0SS6Xnnhyckr8dwh86tDgxZhtruQ4unu4EiOj15PMWymI69J+Ad6jF oRfrZ/mqyi0+hfxFyoLnI5Uz/Gxza/0A7mcBiwqLrbqU9K0695u8ZCi4B3ytB0rP l6HJZuODn6sQiUta/03Yo3GabFNzTuoqQ9HerdVOyPxpRjeTjEbULdmOmnHltUIQ AlgCAXJ71nmaCazGPIVvkIC2QQSg6TxJWvAR/vF879K2NcXZfImB4OpoWGJ1vb9W BiDq1nU57jiyugxxSR3/RlZRfqpo9HPkq8qooQR1VxqfxBxV0XgxEsxs6LB2cr9g RPJ6Cys/OmOj698rjKzss+2OVbHQiXknIUgZqaAgqThVI8G5R/FNWQVM5okmodnf unTVl9eTXVkK/vrzU8iw1K4H2TCJQhFTJX9m4dE9GxnNKeH+T7D8TqtJHjkd7tUH 6+k+Ar4xZwLPB6rNHNbw+4DNDmCyJ9hXMGhCIbqn =RNR1 -----END PGP MESSAGE-----
-
 @ a03b38f8:2c7ce1f0
2024-09-12 16:49:50
@ a03b38f8:2c7ce1f0
2024-09-12 16:49:50First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program. Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works. Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta. Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
 @ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05
@ 5d4b6c8d:8a1c1ee3
2024-09-10 19:03:05It was great having football back. The 49ers and Chiefs continue to dominate, the Raiders, Jets, and Donkeys continue to disappoint.
I only made two picks last week. The Raiders money line was a dud, but my parlay of the Steelers money line with the under was a big hit. Unfortunately, freebitcoin hasn't put any NFL games up, yet. Hopefully they get around to it at some point.
I really like this type of parlay. The house treats outcomes as though they're independent, but I don't think that makes sense. In the event of a Steelers' win, the under was far more likely than the over, because their offense stinks and the game was likely a defensive slog.
In line with that thinking, I made two parlays this week: 1. Raiders money line with the under (7:1): yes, I'm going back to the Raiders. They're probably going to lose, but if they win, it will be because of awesome defense. 2. Bengals money line with the over (4.5:1): Maybe Joe Burrow stinks this season, but maybe the Bengals had been looking ahead to KC. The Chiefs offense is phenomenal again, so the Bengals are only likely to win if this turns into a shootout.
Are there any odds you're excited about (doesn't have to be football)?
originally posted at https://stacker.news/items/679894
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 655a7cf1:d0510794
2024-09-10 13:16:15
@ 655a7cf1:d0510794
2024-09-10 13:16:15Currently have kyc BTC, huge fan of lightning Network. Because I am a constant user of lightning. Plan on doing my business with lightning as well , peer-to-peer I'm not sure if I'm so worried about kyc I might be misguided in this situation.
originally posted at https://stacker.news/items/679520
-
 @ 32ee46c5:dde81be9
2024-09-27 03:39:34
@ 32ee46c5:dde81be9
2024-09-27 03:39:34As I travel around the United States, one of the things that always jumps out to me is just how beautiful this country is. The seashores and the rivers, the mountains and canyons, the farmlands and forests, the deserts and plains are spectacular, for sure, but so are the cities. A week or so ago, as I... This is a preview of my post. Join my community and get access to this and more of my work.
https://highlighter.com/npub1xthyd3ttv467g65ff6rpvz6qdvm9zpmf3j35svrc8wuumh0gr05sgx8evy
-
 @ a012dc82:6458a70d
2024-09-27 00:48:50
@ a012dc82:6458a70d
2024-09-27 00:48:50Table Of Content
-
Educational Initiatives Promoting Blockchain and Cryptocurrency Awareness
-
Supportive Government Policies and Regulatory Frameworks
-
Growing Cryptocurrency Mining Industry
-
Increased Adoption by Businesses and Consumers
-
Establishment of Cryptocurrency Exchanges and Digital Asset Marketplaces
-
Collaboration with Neighboring Countries
-
Conclusion
-
FAQ
In recent years, Thailand has emerged as a hub for blockchain technology and cryptocurrency adoption. The country has shown an eagerness to embrace the Bitcoin revolution, with significant developments in areas such as education, mining, and regulatory frameworks. This article explores the key factors that have contributed to Thailand's growing prominence in the global Bitcoin landscape
Educational Initiatives Promoting Blockchain and Cryptocurrency Awareness
Thailand has recognized the importance of education in fostering a strong foundation for the growth of blockchain technology and cryptocurrency adoption. As a result, numerous universities and educational institutions now offer courses and degree programs in the field. This has created a talented pool of blockchain experts and enthusiasts who are driving the growth of the industry in the country.
Supportive Government Policies and Regulatory Frameworks
The Thai government has adopted a proactive approach towards the regulation and growth of the cryptocurrency market. In recent years, the country has established clear legal frameworks and guidelines for digital asset businesses, which has encouraged both local and international players to invest in Thailand's burgeoning cryptocurrency sector.
Growing Cryptocurrency Mining Industry
Thailand has become an attractive destination for cryptocurrency mining, thanks to its affordable electricity rates and well-developed infrastructure. The country has seen an influx of mining companies, which have set up large-scale mining operations to capitalize on the favorable conditions. This has not only created jobs but also contributed to the growth of the local economy.
Increased Adoption by Businesses and Consumers
In Thailand, both businesses and consumers are embracing the Bitcoin revolution. A growing number of merchants accept Bitcoin and other cryptocurrencies as a form of payment, while consumers are increasingly adopting digital wallets for everyday transactions. This widespread adoption has facilitated the growth of a vibrant cryptocurrency ecosystem in the country.
Establishment of Cryptocurrency Exchanges and Digital Asset Marketplaces
Thailand's supportive regulatory environment has paved the way for the establishment of numerous cryptocurrency exchanges and digital asset marketplaces. These platforms have facilitated easy access to cryptocurrencies for Thai citizens, further boosting the adoption and use of digital assets in the country.
Collaboration with Neighboring Countries
Thailand has actively engaged with neighboring countries in the Southeast Asian region to develop cross-border initiatives and partnerships in the blockchain and cryptocurrency space. These collaborative efforts have helped to create a strong regional network that supports the growth of the industry in Thailand and beyond.
Conclusion
Thailand's rapid embrace of the Bitcoin revolution is a testament to the country's forward-thinking approach towards technology and innovation. By fostering education, supportive regulation, and collaboration, Thailand has positioned itself as a leading player in the global blockchain and cryptocurrency landscape. This has not only benefited the Thai economy but also contributed to the worldwide adoption of cryptocurrencies and blockchain technology.
FAQ
How has Thailand embraced the Bitcoin revolution in education? Thailand has incorporated blockchain and cryptocurrency courses into university curriculums, creating a talented pool of experts and enthusiasts who contribute to the growth of the industry.
What role does the Thai government play in supporting the Bitcoin revolution? The government has established clear legal frameworks and guidelines for digital asset businesses, encouraging both local and international players to invest in the cryptocurrency sector.
Why is Thailand becoming a popular destination for cryptocurrency mining? The country offers affordable electricity rates and well-developed infrastructure, attracting mining companies to set up large-scale operations and contributing to the local economy.
How have Thai businesses and consumers adopted cryptocurrencies? A growing number of merchants accept cryptocurrencies as payment, and consumers increasingly use digital wallets for everyday transactions, fostering a vibrant cryptocurrency ecosystem in the country.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 912212cc:672aac36
2024-09-26 20:35:38
@ 912212cc:672aac36
2024-09-26 20:35:38O Tsathoggua negro se moldou de uma gárgula semelhante a um sapo para uma linha sinuosa com centenas de pés rudimentares. Como um deus, Tsathoggua pode alterar sua forma para se adaptar melhor a qualquer ambiente em que você esteja. O que você acha dos vídeos sobre os mitos de Cthulhu?
https://video.nostr.build/394067118f64907e9034190f715da078c7c73c07c65b526fe91f683115fff5c5.mp4
-
 @ 6ad3e2a3:c90b7740
2024-09-10 09:26:37
@ 6ad3e2a3:c90b7740
2024-09-10 09:26:37While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
1. Separate passengers from their bags as early as possible.
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off outside the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people could have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
2. Eliminate Security Lines
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
- With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
- Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
- Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
- Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
1. This would cost too much money.
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
2. It’s too much of a security risk.
Airport security is incredibly flawed right now, as tests repeatedly show. You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
3. I like free carry-ons because it saves me from waiting at the baggage claim.
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing** lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.
** This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.
-
 @ 6ad3e2a3:c90b7740
2024-09-10 08:21:48
@ 6ad3e2a3:c90b7740
2024-09-10 08:21:48I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — made it to the final 23 in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “the man in the arena whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, the entire odyssey while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. I was the guy who got this done. I flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring sports content to nostr which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a guide to Lisbon which I posted on nostr, and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a (very in-depth) guide to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be Team of Destiny, Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s Survivor post, I wrote:
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I picked the Bengals knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-
 @ c99e3a74:57eb85c1
2024-09-26 18:34:45
@ c99e3a74:57eb85c1
2024-09-26 18:34:45Livro I
Capítulo I
\ Aristóteles abre sua obra constatando o fato de que toda arte ou investigação, são realizadas em vistas a algum bem. Sendo, portanto, o bem aquilo a que todas as ações tendem. Porém, se bem é aquilo ao qual todas as coisas tendem, surge o seguinte dilema: como pode, então, algumas atividades serem o fim de si mesmas, e outras atividades terem por fim a realização de uma outra coisa? Por exemplo, a realização da construção naval é a produção de um navio, porém a realização da dança se dá no próprio ato de dançar. Assim, há uma diferença entre a natureza dos fins: alguns fins são atividades, enquanto outros são produtos de determinada atividade. Observação: No caso dos fins que são a produção de algo a partir de uma atividade, naturalmente o fim produzido(por exemplo, a saúde para a medicina) é mais perfeito do que a atividade. \ A partir desta constatação, pode-se pensar que, por haver muitas atividades, há também muitos fins. Cita-se o exemplo de que a finalidade da arte médica é a saúde, da construção naval é um navio, da economia é a riqueza e etc. Porém, observa-se que algumas artes subordinam-se a outras, tendo outras por finalidade. Por exemplo, a arte de produzir um bisturi é uma arte sujeita à arte da medicina, que por sua vez tem por finalidade a saúde. Neste sentido, deriva-se que a finalidade da arte mais fundamental, é superior aos da arte subordinadas a ela(no exemplo, a saúde é uma finalidade superior à produção de um bisturi).
Capítulo II
-
 @ 129f5189:3a441803
2024-09-09 23:28:41
@ 129f5189:3a441803
2024-09-09 23:28:41Project 2025, outlined in the Heritage Foundation's "Mandate for Leadership" document, serves as a fundamental guide for the next Republican administration. Despite Trump's extensive denial, in today's material, we will explore the deepening and continuation of many policies already employed during his first term. The idea is that this material will serve as a reference document to consult and verify what was actually implemented and/or followed. https://image.nostr.build/e3b89d71ff929258e5d9cb0b5ca8709a381598f43d8be4b17df3c69c0bc74d4a.jpg This document presents proposals for the foreign policy and the State Department of the United States of America, as well as the strategy with its political partners and adversaries. We will also address the U.S. government's communication strategy abroad. https://image.nostr.build/a4250b786f611b478aaf0be559427ad7d4296fbcacb2acc692c7f0d7eb06b0dd.jpg Reorienting U.S. Foreign Policy: Proposals for a Conservative Future In the chapter "The Department of State" from the "Mandate for Leadership," also known as "Project 2025," Kiron K. Skinner presents a comprehensive plan to reform U.S. foreign policy under a conservative administration. Skinner, a renowned foreign policy expert and former Director of Policy Planning at the U.S. State Department, outlines global threats and offers specific recommendations to strengthen the U.S. position on the international stage. Below, we present a detailed analysis of the proposals, emphasizing direct quotes and explanations of the key points discussed. https://image.nostr.build/278dcd7ef0439813ea35d0598319ee347f7a8cd7dfecac93be24ffdd0f6ecd04.jpg History and Structure of the State Department Since its founding in 1789, the State Department has been the primary diplomatic channel of the U.S. With nearly 80,000 employees and 275 posts around the world, it faces significant structural challenges. Skinner highlights that "the biggest problem of the State Department is not a lack of resources," but the belief that it is "an independent institution that knows what is best for the U.S." (Skinner). The scholar and former Director of Policy Planning at the U.S. State Department during the Trump administration emphasizes these points, considering the difficulty in accepting a conservative international approach by State Department employees (the equivalent of the Ministry of Foreign Affairs in other countries). https://image.nostr.build/049939926793e86000b300b9a962dc0ae7e271d9a607ae36d8cb08642adf4174.jpg Political Leadership and Bureaucratic Support To align the State Department with presidential priorities, Kiron suggests appointing political leaders who are committed to the president's vision. "Leadership should include political appointees in positions that do not require Senate confirmation, including senior advisors and deputy secretaries" (Skinner). Furthermore, she emphasizes the importance of training and supporting these appointees to ensure effective coordination between agencies. https://image.nostr.build/6ed704cc9612aa6489e048b143f1e489c1f8807fdf2ab011b4ba88e4a1e3619a.jpg Global Threats to the U.S. The document identifies five countries that pose significant threats to the security and prosperity of the U.S.: China, Iran, Venezuela, Russia, and North Korea. 🇨🇳 China: Skinner argues that China represents an existential threat. "The U.S. needs a strategic cost-imposing response to make Beijing's aggression economically unviable" (Skinner). Additionally, she emphasizes that the issue is not with the Chinese people, but with the communist dictatorship that oppresses them: "As with all global struggles against communist and other tyrannical regimes, the issue should never be with the Chinese people, but with the communist dictatorship that oppresses them" (Skinner). https://image.nostr.build/e707273f1d08bdc4187123a312bd116695b5f603066e11ad30fcef4466730b6b.jpg 🇮🇷 Iran: The Obama administration, through the 2015 nuclear deal, provided the Iranian regime with a "crucial cash bailout" (Skinner). Kiron criticizes this approach, asserting that the U.S. should support the Iranian people in their demands for a democratic government. "The correct policy for Iran is one that recognizes that it is in the U.S. national security interests and the human rights of Iranians that they have the democratic government they demand" (Skinner). https://image.nostr.build/cda7d29a62981f59ad8d77362b3867b552f190c8d7e0e8d9233cb7c1d1d0309e.jpg 🇻🇪 Venezuela: Under the regimes of Hugo Chávez and Nicolás Maduro, Venezuela has transitioned from a prosperous country to one of the poorest in South America. Skinner suggests that the U.S. should work to contain Venezuelan communism and support its people. "The next administration should take steps to put Venezuela's communist abusers on notice and make progress in helping the Venezuelan people" (Skinner). https://image.nostr.build/f53e12564cae74d4b50c24b0f3752dd2c53b70bd1c00a16df20736fb8588417d.jpg 🇷🇺 Russia: The war between Russia and Ukraine divides opinions among conservatives, and the document considers three lines of action. Some advocate continuing support for Ukraine, while others believe that such support does not serve U.S. security interests. "The conservative approach rejects both isolationism and interventionism, first asking: What is in the interest of the American people?" https://image.nostr.build/8fedaf77129f4801f4edb8b169b2ac93a3e518b8bf3642b3abc62575b5435fa3.jpg One conservative school of thought believes that "Moscow's illegal war of aggression against Ukraine represents major challenges to U.S. interests, as well as to peace, stability, and the post-Cold War security order in Europe" (Skinner). This view advocates for continued U.S. involvement, including military and economic aid, to defeat Russian President Vladimir Putin and return to pre-invasion border lines. Another conservative school of thought argues that U.S. support for Ukraine is not in the interest of U.S. national security. According to this view, "Ukraine is not a member of the NATO alliance and is one of the most corrupt countries in the region" (Skinner). It is argued that the European nations directly affected by the conflict should help defend Ukraine, but the U.S. should seek a swift end to the conflict through a negotiated settlement. https://image.nostr.build/22db3d0e79340c1d62344a2b8a3bfddbe4d5bd923cf77d70cfbf5ebf73e4db3e.jpg A third conservative viewpoint avoids both isolationism and interventionism, proposing that "each foreign policy decision should first ask: What is in the interest of the American people?" (Skinner). From this perspective, continued U.S. involvement should be fully funded, limited to military aid while European allies address Ukraine's economic needs, and must have a clear national security strategy that does not endanger American lives. https://image.nostr.build/939fea0bb5c69f171a3da1073e197edcff23a600430b3bc455f6d41bc8a0319f.jpg Although not stated explicitly, I believe this third viewpoint is the one Kiron Skinner desires, as she considers American intervention important but advocates for balancing the costs of the war with its partners in the European Union and NATO. https://image.nostr.build/d1d0c7fb27bfc5dd14b8dde459b98ed6b7ca2706473b2580e0fbf5383f5a9c10.jpg 🇰🇵 North Korea: North Korea must be deterred from any military conflict and cannot be allowed to remain a de facto nuclear power. "The U.S. cannot allow North Korea to remain a de facto nuclear power with the capability to threaten the U.S. or its allies" (Skinner). https://image.nostr.build/95febb04f6d2e0575974a5e645fc7b5ec3b826b8828237ccc1f49b11d11d6bce.jpg Detailed Policy Proposals Refugee Admissions: The Biden administration has caused a collapse in border security and internal immigration enforcement, according to Skinner. She argues that the U.S. Refugee Admissions Program (USRAP) should be resized. "The federal government should redirect screening and verification resources to the border crisis, indefinitely reducing the number of USRAP refugee admissions until the crisis can be contained" (Skinner). https://image.nostr.build/a5740b33842e47b9a1ab58c7b72bd6514f9b6ffbb18706deed1445c59236bc0d.jpg Corporate Collaboration with China: Skinner criticizes the collaboration of companies like BlackRock and Disney with the Chinese regime, noting that "many are invested in an unwavering faith in the international system and global norms," refusing to acknowledge Beijing's malign activities. She emphasizes that the real issue is the communist dictatorship that oppresses the Chinese people, not the Chinese citizens themselves (Skinner). https://image.nostr.build/05a3c787f144c4519c2ee8a4b22e64b8729842819ace4b439c849ef70ecd60b4.jpg Fentanyl and Mexico: The trafficking of fentanyl, facilitated by Mexican cartels in collaboration with Chinese precursor chemical manufacturers, is a critical problem. "Mexican cartels, working closely with Chinese manufacturers of fentanyl precursor chemicals, are sending this drug to the U.S., causing an unprecedented lethal impact" (Skinner). The next administration should adopt a firm stance to halt this public health crisis. https://image.nostr.build/59e32aeef5dabab3344a94a3e415d57fed91fece8bc3c5f068e9f6f7d71f99bd.jpg Re-hemispherization of Manufacturing: Kiron proposes that the U.S. promote the relocation of manufacturing to partner countries such as Mexico and Canada. "The U.S. should do everything possible to shift global manufacturing to Central and South American countries, especially to move it away from China" (Skinner). This would improve the supply chain and represent a significant economic boost for the region. https://image.nostr.build/5d5d7d792f1c94eb6e2bd7a4b86c43236765719e183be8ba8e00ed7dd07eca66.jpg Abraham Accords and a New “Quad”: Skinner suggests that the next administration should expand the Abraham Accords to include countries like Saudi Arabia and form a new security pact in the Middle East that includes Israel, Egypt, Gulf states, and possibly India. "Protecting the freedom of navigation in the Gulf and the Red Sea/Suez Canal is vital for the global economy and, therefore, for U.S. prosperity" (Skinner). https://image.nostr.build/c87cd99cb3ea2bef40e9d1f1fea48b0c9f9f031f3077fff658f15f850e7b8589.jpg Policy for Africa: The U.S. strategy for Africa should shift focus from humanitarian assistance to economic growth and countering China’s malign activities. "Development assistance should focus on fostering free market systems and involving the U.S. private sector" (Skinner). She also highlights that African nations are opposed to the imposition of policies such as abortion and LGBT lobbying. https://image.nostr.build/44df42f32e61c14786ac46c231d368b14df4dc18124a0da458e8506f917302f2.jpg Relations with Europe and Asia Europe: The U.S. should demand that NATO countries increase their contributions to defense. "The U.S. cannot be expected to provide a defense umbrella for countries that do not contribute adequately" (Skinner). Additionally, urgent trade agreements should be pursued with the post-Brexit United Kingdom. https://image.nostr.build/6c013bacfa9e6505ad717104d9a6065f27664a321dd2c3d41fd7635258042d2f.jpg Asia: The withdrawal of U.S. troops from Afghanistan was humiliating and created new challenges. Skinner emphasizes the importance of India as a critical partner to counterbalance the Chinese threat and promote a free and open Indo-Pacific. Cooperation within the Quad, which includes the U.S., India, Japan, and Australia, is essential to this strategy. "The priority is to advance U.S.-India cooperation as a pillar of the Quad" (Skinner). https://image.nostr.build/1cc988b2f70d855c9676d7e38ffdb23564d04ad6333a8d256698f416a1c6704e.jpg International Organizations Skinner criticizes the corruption and failure of the World Health Organization (WHO) during the Covid-19 pandemic. "The next administration should end blind support for international organizations and direct the Secretary of State to initiate a cost-benefit analysis of U.S. participation in all international organizations" (Skinner). She also supports the “Geneva Consensus Declaration on Women’s Health and Protection of the Family,” which is against abortion, and believes that the U.S. government should not fund international organizations that promote abortion (Skinner). https://image.nostr.build/0b583511fef16d68736804fae2f15850eb5c803af01f006a3fe10cdbc583f48c.jpg Conclusion Skinner’s document provides a detailed vision for reorienting U.S. foreign policy under a conservative administration, with an emphasis on ensuring that the State Department serves the national interests defined by the president. With these guidelines, the next administration has the opportunity to redefine the U.S. position on the global stage, promoting security, prosperity, and freedom. https://image.nostr.build/697522745c5947cd4384cdd302b531ee98ce5d59a5d72de0b4f3a52c9abd4821.jpg
-
 @ e83b66a8:b0526c2b
2024-09-09 20:30:30
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur
On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst
On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-
 @ 3ad01248:962d8a07
2024-09-26 17:39:34
@ 3ad01248:962d8a07
2024-09-26 17:39:34https://image.nostr.build/c7e3732889827ab0a8e2064de5fa6992e37e035347b0c91d249cb8f312b47087.jpg I love Bitcoin. Let me get that out there first of all. I sincerely believe that Bitcoin has the power to change the way the world functions if we can grow adoption to a global scale. This obviously will take time as the gears of economic change grinds slowly. As of right now, people in the western countries don't really see the need for a sovereign politically neutral money that can't be inflated away. They simply don't have to deal with inflation on a regular basis like the rest of the world.
Citizens in western countries got a small taste of what real inflation looks like and guess what? They didn't like it one bit. Overall the last three and a half years you saw countless news stories about how bad inflation and how its making life for the average American or European more difficult.
Yes inflation does suck but look at countries like Argentina, Turkey, Zimbabwe or Venezuela. The people in these countries are suffering from excessive inflation on a regular basis! According to recent economic data Turkey experienced a decline in inflation from 61 percent to 51 percent in August. This is seen as a win in their book! Can you imagine this level of inflation in America? There would be riots in the streets!
Argentina's inflation rate is an astounding 236 percent over the last 12 months! As Bitcoiners we understand that the problem is the money itself. As long as governments have the ability to manipulate the money supply, they will. This is human nature at its finest. When you give a select few that kind of power it becomes irresistible and becomes a tool to control the masses. This shouldn't be a surprise to anyone to be honest.
What I find shocking is with all of this inflation globally no one is really looking around asking questions to why this is happening and looking for a way to escape this system. Are people really this lazy? Not to be mean but cmon. It seems to me that most people are perfectly fine bitching online about how hard it is to make ends meet or supporting their favored political party and wanting them to fix the problem they created. Newsflash to all the normies out there, its the GD political parties that caused inflation in the first place.
We literally have a solution that is staring them in the face, ready to go to replace the current debt based system that we are currently suffering through and no one wants to take the time to research it? Am I black pilled? No, am I realist, very much so. If 236 percent inflation in Argentina can't get them on a Bitcoin Standard immediately, we as a community have a long road ahead of us. Hyperbitcoinization isn't coming in 5 years. It isn't coming in 10 years. Hell it might not even happen in our lifetimes and we have to be ok with that.
So what is the best way to get more Bitcoin into the hands of the people, so they can see the true value of the digital monetary revolution that is Bitcoin. We need a trojan horse and that trojan horse is nostr.
Enter The Nostr Trojan Horse
https://image.nostr.build/5ffee418133ac80ba14b30abf0d5390b878f676cbf6332d67639f9384764da4c.jpg
It should be plain to see by now that the inflation or the number go up narrative alone isn't going to drive Bitcoin adoption. The reason for that is because people don't see the utility of Bitcoin. They see it as some esoteric digital funny money that drug dealers and terrorist use to do bad things.
The average Joe doesn't see how Bitcoin is helping dissidents on foreign countries fund their activism, escape oppressive regimes or simply earn a living. These stories are never told in the mainstream media because they don't want to highlight the fact that a non-state money can circumvent the status quo.
The best way to highlight these stories is to share it on social media, which again is controlled by mainstream gatekeeper such as Meta, Google and X. It is in their best interest to censor these stories or memory hole them out of existence which I suspect happens quite a bit without us even knowing. But the thing about censorship is that it slowly impacts everyone one by one until no one is allowed to say anything without the fear of being put in jail.
Think this can't happen in western democracies? It's happening already my friend! Take a look at the UK or Australia. Citizens their are being arrested over post made to social media. I sincerely believe that these two countries should be a proving ground for showing the value of nostr and Bitcoin.
Introducing the concept of a censorship resistant messaging protocol to them will go over well and once it is understood will grow like a wildfire because people innately understand that censorship is bad and will see the utility value of having the ability to speak freely again.
It is only a matter of time until they realize that they can monetize their speech and build a life using zaps aka Bitcoin.
Until people see the utility in the tools that lie before them, they will never pick them up and use them. It is really that simple. At the end of the day we are still kind of like cavemen. We only use tools when it makes life easier. Man made the wheel. We use it everyday because it has utility.
Bitcoin in the end will be the same way. Utility first, then mass adoption. Nostr is what will help people see the utility Bitcoin and from there sky is the limit. The best thing we can do as Bitcoiners is to encourage people to learn about nostr and show them how easy it is to use and to switch clients that suit their needs instead of being shoved into a one-size fits all solution on centralized platforms.
People like choices, and nostr is all about choice. The interoperability and thelack of need to give personal information to create an account are HUGE selling points that can be touched on. Go out and spread the good word about nostr!
Bitcoin #Nostr
-
 @ e83b66a8:b0526c2b
2024-09-09 20:27:41
@ e83b66a8:b0526c2b
2024-09-09 20:27:41First,
Key management.
When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”.
As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere.
Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you.
We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary.
For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/
N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted:
Secondly,
Lightning wallets.
It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile
N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key.
You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet.
Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason….
It also allows you to send small micropayments to posts or people you like.
Thirdly,
Paid Services
As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability.
I, for example choose to pay for the following services:
https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year
Total: 22,750 Sats per month Approx $15 per month
This is not strictly necessary, but I decided to support the various developers behind these projects.
Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
-
 @ 3ad01248:962d8a07
2024-09-26 17:31:27
@ 3ad01248:962d8a07
2024-09-26 17:31:27test poasting
-
 @ c11cf5f8:4928464d
2024-09-09 18:45:16
@ c11cf5f8:4928464d
2024-09-09 18:45:16originally posted at https://stacker.news/items/678432
-
 @ dc652bee:6154e7d0
2024-09-26 16:06:14
@ dc652bee:6154e7d0
2024-09-26 16:06:14NEW UPDATE TELEGRAM AIRDROP BOT
📢Exciting news! 🚀 Our new update bot is here to make your Telegram experience even better. Get ready for the ultimate airdrop! Don't miss out!
https://t.me/Dogiators_bot/game?startapp=F80aAU4OlGJX61YK
https://t.me/tonton_intract_bot/start?startapp=eyJyZWZlcnJhbENvZGUiOiJGOER6dDAiLCJyZWZlcnJhbFNvdXJjZSI6IlRFTEVHUkFNX01JTklfQVBQIiwicmVmZXJyYWxMaW5rIjoiaHR0cHM6Ly93d3cuaW50cmFjdC5pby90bWEvcmV3YXJkcyJ9
https://t.me/gamee/start?startapp=ref_730909086
https://t.me/Bcoin2048bot/app?startapp=ref_pCGwqQ15aSZUFYa9ZEys8qRH
https://t.me/realgoats_bot/run?startapp=c127fadc-579e-485a-a68f-f901cd4e64e6
https://t.me/OwlMini_bot/app?startapp=730909086
https://t.me/bluefarming_bot/play?startapp=c8a58023
https://t.me/BitsTonboxBot/BitsAirdrops?startapp=M9Ek3ygSFAJTZ5Y4PS2aoq
https://t.me/digibuy_bot/digiverse/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
http://t.me/foxs_HouseBot?start=730909086
https://t.me/Agent301Bot/app?startapp=onetime730909086
t.me/RealCowsHouse_bot/cowshouse?startapp=kentId730909086
http://t.me/token1win_bot/start?startapp=refId730909086
https://t.me/MemesLabBot?start=PNT7D8
https://t.me/major/start?startapp=730909086
https://t.me/uptonfi_bot/UpTonGames?startapp=ByKBX2QurGdYa
https://t.me/catizenbot/gameapp?startapp=r_1938_7836673
https://t.me/memefi_coin_bot/main?startapp=r_27d6952978
https://t.me/whitebunnywtf_bot?start=ref666953186736f7f2eff6261f
https://t.me/pixelversexyzbot?start=730909086
https://t.me/tapswap_mirror_2_bot?start=r_730909086
https://t.me/hamster_kombaT_bot/start?startapp=kentId730909086
https://t.me/IcebergAppBot?start=referral_730909086
https://t.me/gemsee_bot?start=ref_100a006b
https://t.me/GoodRides_bot?start=NzMwOTA5MDg2
https://t.me/lost_dogs_bot/lodoapp?startapp=ref-u_730909086
https://t.me/gemzcoin_bOt/tap?startapp=nSoqE-UNEtgNUcRp5luy0w
https://t.me/QappiMinerBot?start=730909086
https://t.me/Snakelite_official_bot/Snakelite?startapp=nOuSbPc0
https://t.me/squid_squad_bot/squid?startapp=link_730909086
https://t.me/lovetap_bot?start=ref_120218
https://t.me/BIRDTonBot/app?startapp=730909086
https://t.me/LovelyLegends_bot/start?startapp=kentId730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/pehekingdom_bot/open?startapp=iAzmZVumOr
https://t.me/loody_farming_bot/LOODY/?startapp=inviter_id_40937
https://t.me/Tomarket_ai_bot/app?startapp=0000bDIo
https://t.me/CoinCryptoGameBot?start=r_JSGDH54A
https://t.me/Xyzmercoin_bot/play?startapp=BZI2CZ
https://t.me/dragonz_land_bot/app?startapp=ref-668302fc033aa4721ab5d1ea
https://t.me/BullishFarmBot/start?startapp=r_730909086
https://dashboard.wormfare.com/referral/0DC0D761
https://t.me/betfury_social_bot/app?startapp=tgReLe1ec7c70
https://t.me/PipeFlareBot/pipeflare_app?startapp=730909086
https://t.me/TimeFarmCryptoBot?start=x3jKZG0eoJa58ayY
https://t.me/MatchQuestBot/start?startapp=0cb38b86ee4543c74bd76ab16c1c8fd3
https://t.me/DiamoreCryptoBot/app?startapp=730909086
https://t.me/money_dogs_bot/money_dogs?startapp=3eAlu89K
https://t.me/ZARGatesBot/?start=2307731133
https://t.me/taptapcore_bot/Earn?startapp=b1720f3afcf04e5cb76418c267c4559e
https://t.me/Mimiland_appbot/app?startapp=ref_eyJwIjoiIiwiZiI6InJlZiIsInIiOiI3MzA5MDkwODYiLCJtIjoiNjZkNWZmMWJkNTE3MGU1M2ZiYmMwZmNiIn0=
https://t.me/CyberFinanceBot/game?startapp=cj1CRjNxRE5WbmhNQlomdT1yZWY=
https://t.me/BBQcoin_bot/BBQcoin?startapp=rp_9004676_730909086
https://t.me/PonchKick_bot/ponchiqs?startapp=730909086
https://t.me/potusclick_bot/app?startapp=r730909086
https://t.me/chickcoopofficial_bot/chickcoop?startapp=ref_730909086
https://t.me/ArtiTapBot/start?startapp=referrerId730909086
https://t.me/Frogs_HouseBot?start=730909086
https://t.me/tomo_cat_bot?start=r-cofuLtoo
https://t.me/Boom/LoudCoins?startapp=F5iKvP2LEVi9g4hFkGdpya
https://t.me/The_Rocket_bot?start=r_730909086
https://t.me/monkeycost_bot/app?startapp=r_730909086
https://t.me/tapcoinsbot/app?startapp=ref_TxCe4a
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/cexio_tap_bot?start=1722546804203779
https://t.me/flarexgamebot?start=66743fede9b04d43fd21fe9e
https://t.me/grandcombat_bot/start?startapp=TFqI0dXjLc
https://t.me/fishing_bowl_bot/fish?startapp=EQANA57LP2PPLgBIwbnWMpHD4708uGKu7YipzvELhOt6fdnA
https://t.me/GametyPlatform_bot?start=NzMwOTA5MDg2XzA
https://t.me/HUNDTAPbot?start=r_730909086
https://t.me/BabyDogePAWS_Bot?start=r_730909086
https://t.me/BillyBobRobot/GAME?startapp=730909086
https://t.me/wcoin_tapbot?start=NzMwOTA5MDg2
https://t.me/cherrygame_io_bot/game?startapp=r_730909086
https://t.me/pirate_frenzy_bot/piratefrenzy?startapp=i7z37hc2G6
https://t.me/MMproBump_bot?start=ref_730909086
https://t.me/theHoldCoinBot/app?startapp=ref_NRPViKZ4
https://t.me/not_panda_bot/not_panda_app?startapp=9j3938HJeb
https://t.me/gmdotaibot/Airdrop?startapp=ovyova
https://t.me/GoldVerseBot/app?startapp=ref_zzT4iN
https://t.me/herewalletbot/grafun?startapp=TewJ6VV5SA2CrVidvyILAXC8diL
https://gra.fun/?ref=TewJ6VV5SA2CrVidvyILAXC8diL
https://t.me/owlsonton_bot?start=730909086
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/cedex_tap_bot?start=1725744305355276
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/BYIN_official_bot/BYIN_Launchpad_Beta?startapp=q3lj8O41
https://t.me/ARIXcoin_bot?start=ref_730909086
https://t.me/sunkongmyth_bot/sunkong_miniapp?startapp=E987837FE
https://t.me/boolfamily_bot/join?startapp=8T1X0
https://t.me/tonstationgames_bot/app?startapp=ref_aysq8p4swodmv4ex6c7e4y
https://t.me/y_nation_bot/start?startapp=NKS74T
https://t.me/GalaCoin_bot/app?startapp=ref_KFfSylID
https://t.me/Yaytsogram_bot?start=invite4546481
https://t.me/battle_games_com_bot/start?startapp=frndId730909086
https://t.me/PinEye_Bot/pineye?startapp=r_730909086
https://t.me/pocketfi_bot/Mining?startapp=730909086
https://t.me/SatoshiMiner_Hq_Bot?start=730909086
https://t.me/sidekick_fans_bot?start=730909086
https://t.me/bums/app?startapp=ref_rgws9zFi
https://t.me/TondropEarnBot/app?startapp=66dfd225c839152d9203f5a9
https://t.me/head_coin_bot/start?startapp=bonusId730909086
https://t.me/onus_tap_tap_tap_bot/join?startapp=1722155904792
https://t.me/Atleta_tap_bot/tap?startapp=a89197f4-6ef7-4925-a38d-cbe0cc71aa34
https://t.me/SecretPadBot/app?startapp=r730909086
https://t.me/Binance_Moonbix_bot/start?startApp=ref_730909086&startapp=ref_730909086&utm_medium=web_share_copy
https://t.me/catsdogs_game_bot/join?startapp=730909086
https://t.me/claytoncoinbot/game?startapp=730909086
https://t.me/playpenchobot/play?startapp=ZF6EG6NCVC
https://t.me/nodgoin_bot/?start=ref_309eb495-9c18-4c3b-8177-297b89ac8911
https://t.me/Loodygame_bot/loodydev/?startapp=inviter_id_40937
https://t.me/CrashinoCasinoBot/?start=EjtAhLG5X
https://t.me/BybitCoinsweeper_Bot?start=referredBy=730909086
http://t.me/CamelsHouseBot/House?startapp=66f428b404d8bde3bbb68790
https://t.me/forge_game_bot/start?startapp=NzMwOTA5MDg2
https://t.me/boinker_bot/boinkapp?startapp=boink730909086
🆘Several projects are coming to the listing soon, some have already been released, start today it's completely free.⛏️
-
 @ e968e50b:db2a803a
2024-09-09 18:21:54
@ e968e50b:db2a803a
2024-09-09 18:21:54Open the frozen pizza bay doors, Hal.
originally posted at https://stacker.news/items/678403
-
 @ 6bae33c8:607272e8
2024-09-09 16:07:43
@ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — made it to the final 23 in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “the man in the arena whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, the entire odyssey while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. I was the guy who got this done. I flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring sports content to nostr which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a guide to Lisbon which I posted on nostr, and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a (very in-depth) guide to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be Team of Destiny, Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s Survivor post, I wrote:
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I picked the Bengals knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-
 @ d3052ca3:d84a170e
2024-09-09 15:43:38
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-
 @ d6affa19:9110b177
2024-09-26 15:44:34
@ d6affa19:9110b177
2024-09-26 15:44:34it's a sunny afternoon at a shopping center. i open the car door for Her. we head into the bookstore. the aroma is rich, thick. i buy us coffee.
we then browse around. but beneath my calm surface, a quiet longing stirs—a deep yearning for Her.
Her touch. Her love.
i still feel the echoes of Her words—a sweet torment that rests in my mind. i've felt it all day. it's nearly maddening.
and yet i maintain my composure as i follow along to the next store.
She turns. i spot a brief smirk.
my breath catches. She knows... i can't hide from Her.
a simple brush of Her hand. it sends jolts. a reminder of the pleasure She wields.
"Are you okay?" Her voice sweet, yet probing.
"Yes, my Queen." i answer in an even tone, managing the storm underneath.
"Good," She nods.
"Let's go, sweet boy." Her command lingers gracefully in the air.
"Help me try on some shoes."
the thought of helping Her... it sends a thrill through me.
i nod, taking another sip of coffee.
it burns, still hot. my hands feel clammy against the cup, heart racing.
the anticipation is electric...
-
 @ 3875a16c:988456c9
2024-09-09 14:50:15
@ 3875a16c:988456c9
2024-09-09 14:50:15ORIGINAL PANEL TITLE: MAKING BITCOIN MORE PRIVATE WITH CISA
SPEAKERS: NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP
CONFERENCE: BITCOIN NASHVILLE 2024
ORIGINALLY PUBLISHED ON: BITLYRICS.CO
Introduction
This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( CISA). Moderated by NiftyNei from Base58, the panel includes Jameson Lopp from Casa, Craig Raw from Sparrow Wallet, and Fabian Jahr from Brink.
Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development.
NiftyNei (Moderator):
Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation).
Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage.
We’re excited to be talking to you guys about this.
I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA.
Craig, do you want to start?
Craig Raw (Sparrow Wallet):
I built Sparrow Wallet. It’s a security and privacy-focused wallet.
The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen.
When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically.
So, that was the first time I really started to look at it from the privacy angle.
Fabian Jahr (Brink):
I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it.
Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core.
Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months.
I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller.
I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it.
Jameson Lopp (Casa):
I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups.
I think the first time I heard about CISA was in an Andrew Poelstra talk.
I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted.
This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics.
NiftyNei (Moderator):
That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for.
Does anyone have a good explanation of how it works?
Fabian Jahr (Brink):
I can start off.
So, it’s really already all in the name: cross-input signature aggregation.
If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated.
What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction.
So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before.
Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea.
NiftyNei (Moderator):
I have a quick question about that.
So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right?
So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature.
Is that a good summary of what you’re explaining?
Fabian Jahr (Brink):
Yeah, I would say so.
Craig Raw (Sparrow Wallet):
So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it.
That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one.
Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it.
Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones.
Unfortunately, the downside of that is that you have to do the interaction while you sign.
The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing.
As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient.
NiftyNei (Moderator):
Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right?
You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level?
Jameson Lopp (Casa):
Well, there’s also full-block aggregation, right?
This is going really far down the rabbit hole, and I think it’s not even something that’s on the table.
There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations.
My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized.
If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again.
NiftyNei (Moderator):
So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation.
We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there.
One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right?
Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated.
Jameson Lopp (Casa):
Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically.
If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount.
It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO.
You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet.
It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot.
It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before.
So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so.
Fabian Jahr (Brink):
And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy.
The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property.
Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.”
Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it.
Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature.
Jameson Lopp (Casa):
Yeah, we have to think about the incentives, right?
I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are.
But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late.
We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so.
It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software.
Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money?
Craig Raw (Sparrow):
So you might be wondering at this stage what the savings actually look like.
It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block.
You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage.
Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%.
But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space.
So that’s how I would encourage you to think about it from the start.
For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride.
We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about.
NiftyNei (Moderator):
I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy.
I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal?
What was it about the Taproot process where this proposal didn’t make it over the line?
Fabian Jahr (Brink):
I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed.
From what I can see, I don’t think there was any direct opposition.
The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller.
I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding.
I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much.
Craig Raw (Sparrow):
Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough.
There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.”
That’s an interesting point of view.
Jameson Lopp (Casa):
It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet.
Craig Raw (Sparrow):
Yeah, so we’re in a very different space now.
Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine.
I’m talking about the well-understood half-signature aggregation form of it.
From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that.
So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing.
If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down.
So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line.
Jameson Lopp (Casa):
I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin.
With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process.
As far as I’m aware, there’s been limited adoption of Schnorr so far.
I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility.
I care about this a lot, operating a multi-signature self-custody wallet.
We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature.
That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out.
So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block.
NiftyNei (Moderator):
So, we only have a few minutes left.
Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in.
Fabian Jahr (Brink):
There are still quite a few things to hammer out in terms of all the details, like defining a spec.
For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open.
However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity.
We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now.
Jameson Lopp (Casa):
Yeah, call your local developer and demand signature aggregation today.
Craig Raw (Sparrow):
Fabian has developed a great site where you can learn more.
If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to CISAResearch.org, you can learn more about it.
It’s very easy to read, not overly technical, and I think it gives a good grounding in these things.
Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not.
As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now.
So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not.
Jameson Lopp (Casa):
I don’t know, do you want to save money? It should be an easy question.
Fabian Jahr (Brink):
And have better privacy.
NiftyNei (Moderator):
Great! Thanks y’all.
**Follow the speakers: ** NiftyNei – Craig Raw – Jameson Lopp – Fabian Jahr
**Watch the original content: ** Click here
**Also read: Build It Right: ** Achieving Interoperability with Open Networks
**Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please contact us.
-
 @ dc652bee:6154e7d0
2024-09-26 15:40:20
@ dc652bee:6154e7d0
2024-09-26 15:40:20Embracing the power of positivity and prosperity! 💵✨ Let's make every dollar count and spread good vibes all around. #GoodDollar 🌐https://n9.cl/gooddolars
-
 @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24Chef's notes
Makes an excellent Chicken sandwich.
Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
Directions
- To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
- Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
- Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
- Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
- Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
- Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
- Brush the top of the warm bread with melted butter.
- Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-
 @ 6ad3e2a3:c90b7740
2024-09-10 08:37:04
@ 6ad3e2a3:c90b7740
2024-09-10 08:37:04While I love traveling and usually feel enriched by the experience, I dread and detest the process of going to the airport and getting on a plane. It’s not that I’m afraid of flying — though a plane crash would be one of the worst ways to die — but that the airlines and airports have made the experience as inefficient, dehumanizing and cumbersome as possible. While in the short-term these measures might have generated some extra revenue, cut costs or staved off encroachment from competitors, long-term it cannot be good for the service you offer to be so universally reviled. In the interest of improving their product — and the experience of millions of future passengers including me — here are some practical suggestions:
1. Separate passengers from their bags as early as possible.
The single stupidest airline policy is that checking a bag costs extra while carry-ons are free. What that does is incentivize everyone to drag their luggage through the airport and onto the plane. This has several negative consequences:
a) Even though most airlines have assigned seats, everyone lines up 10 or 20 minutes before the start of the already too long boarding process, frantically hoping to secure some scarce overhead space rather than relaxing in the terminal and boarding at their leisure before the door closes.
b) The process of people filing into the narrow plane aisle(s) with their bags and taking time to load them into the overheads stalls the entire boarding process. Not only do people stand in line at the boarding gate, but they stand in line in the jet bridge and again in the aisle(s). Whereas boarding with purses, laptops and other small, under-the-seat items might take 10 minutes or so, getting all the luggage in takes half an hour. If there are 150 people aboard, that’s 3,000 minutes (50 hours) of human life squandered on a useless and stressful activity. Multiply that by thousands of flights per day.
c) The process of deplaning is also slow because everyone has to get their bags out of the overhead. That’s another 15-minute process that should take five.
d) Everyone going through security with all their carry-ons slows down the security line significantly and makes people have to arrive at the airport earlier.
e) Because everyone has their bags, they have to lug them around the terminal while using the restroom, eating or shopping for something to read. Having a 20-pound weight on your shoulder only makes the experience that much more miserable.
The solution to this is for airlines to allow free checked bags and charge for carry-ons with the exception of parents traveling with young children.
To make the process of checking bags more efficient and less cumbersome there should be an immediate drop-off outside the airport. Like curb-side check-in, but automated, a giant conveyor belt of sorts where everyone drops their bag that will be sorted appropriately inside. This drop off area would have security keeping an eye on it, but it would be self-serve and connect at all entry points including curb-side, the parking garage, from the train, etc.
There would be no need for bag tags because people could have an airport-certified chip inserted into their luggage that syncs with the traveler’s boarding pass, i.e., the system reads the chip and directs the bag to the proper gate underground. (Maybe there would be a plastic bin at all the drop-off points you into which you put your bag so luggage of different shapes, sizes and materials could move smoothly and reliably on the conveyor belt to its destination.)
Security details would have to be worked out (maybe you’d have to scan your boarding pass or passport at the bag drop to open it), but as it stands, once you drop your bag off at the curb or the check-in area, it’s essentially the same process now, i.e, it has to be scanned internally before being placed on the plane.
2. Eliminate Security Lines
Going through security would be far easier without all the bags, but to expedite and improve it further, we should make two key changes, neither of which should be beyond our capacity to implement.
a) Instead of a single-file conveyor belt scanned by humans, make the conveyor belt wide enough for everyone to put their laptops, belts, etc. on simultaneously. This could easily be done by providing plastic bins (as they do now), but with individual numbers and keys on them, like you’d find in most locker rooms. You’d grab bin 45, for example, pull the key out, put your things in it, lock it, walk through the metal detector, retrieve your bin on the other side, unlock it, get your things, put the key back in it, and it gets returned for re-use.
Instead of a bored-out-of-his-mind human looking at each bag individually, there would be a large scanner that would look at all the bags simultaneously and flag anything suspicious.
b) Just as there’s no reason to send the bags through the scanner single-file, there’s no reason to send the people through that way, either. Instead, install room-wide metal detectors through which dozens of people could walk simultaneously. Any passengers that set it off would be digitally marked by the detector, directed back out, shed the offending item into a numbered bin and collect it on the other side.
Basically, you’d drop anything big off before you even set foot in the building, and you’d drop everything else into a security bin, walk through without waiting and collect it on the other side.
3. Make sure the gates are clean, have enough seats to accommodate the passengers of even the largest planes that come through, ample charging stations and reliable and free wi-fi.
Because you’re no longer forced to line up and hustle for overhead space, you’ll be spending more time sitting comfortably in the terminal.
4. Have clean, efficient public transportation from the center of each city directly to the airport. (Some cities already have this.) Not a train, a bus and a one-mile walk.
There are smaller things airports could do to make the process even better — and I’ll suggest some below — but these three would at least make it tolerable and humane. It would shave off roughly an hour per trip, spare people the burden of schlepping around with heavy bags, wading through slow-moving security lines (which add stress if you’re in danger of missing your flight), standing in the terminal, waiting in line after line to sit in a cramped and uncomfortable seat for 20-30 minutes before the plane even takes off and remaining stuck in that seat 15 minutes after the plane has made it to the gate while people one by one painstakingly get their bags out of the overhead bins. Moreover, people could get to the airport later without rushing, and if they were early, they could relax in the terminal or get work done.
Here are some other suggestions:
- With fewer people using the overhead bins, rip them out. There would be a few bins at designated spots (just like there are a few emergency exits), but the interior of the plane would feel more spacious and less claustrophobic. You also wouldn’t risk hitting your head when you stood up.
- Airplanes should have reasonably priced (ideally free) wi-fi and outlets in each row. There’s no way it costs anywhere near the $35 per flight, per person GoGo Inflight absurdly charges.
- Treat airports as public squares — invest in their design as well as their functionality. Incorporate outdoor spaces, green spaces. Attract decent restaurants, bars, cafes. People unencumbered by bags and not rushing to wait in line to board 40 minutes early will be more able to enjoy the environment and arriving travelers will immediately get a good impression and be put at ease.
- Do not advertise mileage rewards from credit cards or other sources unless those miles are actually redeemable at a reasonable rate and on routes and times someone would actually fly. As it stands those programs are borderline fraud — you can fly a middle seat one way from NY to LA for 30,000 miles at 6 am, but that’s not why I signed up for the credit card. If mileage plans are too costly, scrap them.
I can anticipate some objections to these ideas, and I’ll address each one in turn.
1. This would cost too much money.
My suggestions would require a significant initial investment, but it would be but a small piece of the infrastructure outlay that’s sorely needed — and on which our current president campaigned — and it would create jobs. Moreover, it would save travelers tens of millions of hours per year. At $15 per hour — it would pay for itself in short order. (And taxpayers’ squandered time and awful experiences are exactly what their tax dollars should go toward remediating.)
2. It’s too much of a security risk.
Airport security is incredibly flawed right now, as tests repeatedly show. You can get prohibited items through security easily already, and it’s likely the screening process is mostly “security theater,” i.e., just for show. But to the extent this is a serious concern, the newer system might actually improve security due to improved technology spurred by the infrastructure investment. Better detection could be designed into the new system, rather than relying on bored-out-of-their-mind humans to scan endlessly through people’s toiletries expecting to find nothing for hours and days on end.
Moreover, airport security has never actually been an issue in the US. Even on 9/11, the flimsy security worked well — the hijackers managed only boxcutters on the tragically ill-fated flights, not guns or bombs. In other words, that was a failure of government intelligence, not one of airline security even when no one took his shoes off or had to worry about how many ounces of liquid was in his shampoo bottle.
3. I like free carry-ons because it saves me from waiting at the baggage claim.
Great, then pay extra for that. When something you like individually causes collective harm, there needs to be a cost for it. That we have the opposite system where people doing what would make everyone else’s experience easier and better have to pay is perverse.
The bottom line — the current state of air travel both in the US and Europe is unacceptable*. We cannot have a system in which everyone participating despises it and simply pretend it’s an inevitable hassle about which we’re powerless to do anything. The central issue is the dehumanizing** lack of respect for travelers’ time and experience. It’s time to change our priorities and take care of the human beings for whom airports and air travel exist.
*I haven’t even touched on the awful state of flights themselves with cramped seats, small, dirty rest rooms, bad food and exorbitant fees to change your itinerary. That’s because I wanted to focus mostly on the airport/government side over which the public has ownership, and fixing the overall economics of air travel is probably more difficult than getting airlines to reverse their checked-bag fee policies.
** This article was written in March of 2017, and little did I know how much more dehumanizing things would get during covid.
-
 @ e97aaffa:2ebd765d
2024-09-26 14:57:00
@ e97aaffa:2ebd765d
2024-09-26 14:57:00Claro que não, o Bitcoin não é uma solução mas sim uma reação à inação dos governos.
O sistema FIAT está numa situação tão crítica, não existe uma solução boa para o problema da dívida soberana, terá que se optar pela menos má. Como resolver o problema das dívidas futuras, dos fundos de pensões? As dívidas do passado tem que ser pagas, mas como? As dívidas não são apenas números no excel, são pessoas que estão por detrás desses números, não podem ser apagadas, simplesmente.
Uma solução seria uma mudança drástica nas políticas, com uma forte redução de custos do estado e muita austeridade, gerando uma queda do padrão de vida dos cidadãos. Só que isto seria extremamente impopular, nenhum político tem coragem de o fazer, quem tentar vai acabar por perder na próxima eleição.
Assim, a única maneira que resta para os políticos, é fazê-lo pela calada, através da desvalorização da moeda. A inflação permite destruir as dívidas do passado e consequentemente a poupança e a qualidade de vida dos cidadãos. É isto que temos visto nos últimos anos e vai agravar-se no futuro. Só que os atuais níveis de expansão monetária, não foram suficientes para resolver o problema, apenas permite ao governo estar à tona da água, procrastinar o problema.
Um bom exemplo é na UE, onde existe uma regra que permite um défice até 3% do PIB por ano, que muitas vezes nem é cumprida, isto é uma situação insustentável. A regra deveria ser o oposto, obrigar um superávit mínimo de 2% ao ano, só assim será possivel reduzir a dívida.
A expansão monetária e política monetária está a ser utilizada como uma arma contra os cidadãos, é um imposto totalmente cego, muito penalizador para os mais pobres e os governos têm abusado desse poder. A moeda é o sangue de uma economia, os políticos ao diluí-la estão a envenenar a economia. O Bitcoin é a única moeda que não pode ser diluída.
Os políticos reconhecem que existe um problema mas todas as soluções são extremamente impopulares, e como eles são os principais beneficiados do sistema FIAT, dificilmente haverá uma mudança.
Bi-monetário
Como nenhum político terá coragem de mudar, essa mudança tem de partir dos cidadãos, voluntariamente, ou seja, com a adoção do Bitcoin.
Todos os bitcoiners gostariam de assistir a uma mudança rápida do padrão FIAT para o padrão Bitcoin, mas não é possível. É necessário ter noção como o mundo real é, uma mudança rápida entre os padrões seria desastrosa para toda a humanidade, esse processo terá que ser gradual, para não existir uma ruptura entre gerações e entre estratos sociais.
Com a criação do Bitcoin, o paradigma mudou, passou a existir um sistema bi-monetário, com a moeda FIAT e o Bitcoin em circulação simultânea. O FIAT como unidade de conta e o Bitcoin como reserva de valor e as duas como meio de troca.
Hoje, a alocação em Bitcoin ainda é muito baixa. Em média a nível mundial está 99.2% em FIAT e 0.8% em Bitcoin. Mas chegará o dia, atingirá os 50-50%, em alguns países possivelmente será ainda maior.
Será uma adoção completamente voluntária, não será pelos governos, mas sim, pelos cidadãos, de baixo para cima. No início, a adoção será lenta, mas quanto maior for a alocação em Bitcoin, mais acelerada será a adoção.
A dupla circulação de moeda, vai obrigar os governos a fazer uma melhor gestão, vai limitar indiretamente a impressão de dinheiro. Se os governos abusarem desse poder, as pessoas vão se proteger ainda mais no Bitcoin, diminuindo a alocação em FIAT, por sua vez a moeda fica mais fraca e o governo também. Vai obrigar um maior rigor na política monetária.
O Bitcoin será uma proteção contra o abuso dos governos, vai obrigar uma mudança, um maior rigor na sua gestão, possibilitando a redução da dívida a longo prazo.
-
 @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-
 @ a012dc82:6458a70d
2024-09-26 12:16:02
@ a012dc82:6458a70d
2024-09-26 12:16:02Table Of Content
-
A Brief Overview of Bitcoin Mining
-
The Rails Programming Tool: A Game Changer for Bitcoin Miners
-
Customization and Scalability
-
Enhancing Security and Compliance
-
Conclusion
-
FAQ
The world of cryptocurrency is ever-evolving, and as the demand for Bitcoin mining solutions grows, so does the need for innovative and efficient tools. Lincoln Technologies, a leading name in the field of blockchain technology, has introduced a groundbreaking Rails Programming Tool that aims to revolutionize the Bitcoin mining landscape. This article will explore the features and benefits of this powerful new tool and how it can help you unlock the full potential of Bitcoin mining.
A Brief Overview of Bitcoin Mining
Before delving into the details of the Rails Programming Tool, it is essential to understand the concept of Bitcoin mining. Mining is the process of validating and adding new transactions to the blockchain, which ensures the security and integrity of the cryptocurrency network. In return for their efforts, miners are rewarded with newly minted bitcoins and transaction fees. As the mining process becomes increasingly competitive, miners require sophisticated tools to stay ahead of the game.
The Rails Programming Tool: A Game Changer for Bitcoin Miners
Lincoln Technologies' Rails Programming Tool is a cutting-edge solution designed specifically for Bitcoin mining. This powerful software offers a range of features to streamline the mining process, reduce energy consumption, and optimize mining efficiency. Some of the key features include:
User-friendly interface: The Rails Programming Tool boasts a clean and intuitive interface that is easy to navigate even for beginners, reducing the learning curve for new miners.
Advanced mining algorithms: The tool is equipped with the latest mining algorithms to maximize the mining output and increase the chances of earning rewards.
Energy-efficient operations: Energy consumption is a significant concern for Bitcoin miners. The Rails Programming Tool optimizes mining efficiency and reduces energy consumption, lowering the overall costs and environmental impact of mining.
Customization and Scalability
One of the standout features of the Rails Programming Tool is its adaptability. The tool can be customized to suit the specific needs of individual miners, allowing them to create a tailored solution that works best for their mining setup. Additionally, the Rails Programming Tool is designed to grow with the ever-changing world of cryptocurrency, ensuring that users can continue to benefit from its features as the mining landscape evolves.
Enhancing Security and Compliance
Security is of the utmost importance in the world of cryptocurrency, and Lincoln Technologies has taken steps to ensure that the Rails Programming Tool meets the highest security standards. The software employs advanced encryption protocols to protect sensitive data and maintain compliance with industry regulations. By using the Rails Programming Tool, miners can have peace of mind knowing that their operations are secure and compliant.
Conclusion
The Rails Programming Tool from Lincoln Technologies is poised to revolutionize the way Bitcoin miners operate. By harnessing the power of this innovative software, miners can unlock new levels of efficiency, profitability, and sustainability in their mining efforts. As cryptocurrency continues to gain mainstream acceptance, the Rails Programming Tool is a valuable asset for those looking to capitalize on the growing demand for Bitcoin mining solutions.
FAQ
What is the Rails Programming Tool by Lincoln Technologies? The Rails Programming Tool is an innovative software solution designed to streamline and optimize the Bitcoin mining process, reduce energy consumption, and enhance security and compliance.
How does the Rails Programming Tool improve mining efficiency? The Rails Programming Tool uses advanced mining algorithms to maximize mining output, optimizes energy consumption, and offers customization and scalability features that help miners tailor the tool to their specific needs.
Is the Rails Programming Tool suitable for beginners? Yes, the Rails Programming Tool features a user-friendly interface, making it easy to navigate and learn for both beginners and experienced miners alike.
Can the Rails Programming Tool adapt to the changing cryptocurrency landscape? Yes, the Rails Programming Tool is designed for scalability, allowing it to grow and adapt to the ever-evolving world of cryptocurrency and Bitcoin mining.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 129f5189:3a441803
2024-09-09 23:23:45
@ 129f5189:3a441803
2024-09-09 23:23:45Project 2025, outlined in the "Mandate for Leadership" document by the Heritage Foundation, is a crucial guide for the next Republican administration. Crafted by conservative intellectuals from major American think tanks, this plan promises to have significant influence on a potential Donald Trump administration, even if he does not formally acknowledge it as his government plan. https://image.nostr.build/443d69c16dc32659be2353ce48d170d397e0ee682ffc3c4108df3047fd54472d.jpg This document presents proposals to depoliticize government agencies, increase efficiency, and reduce costs, aiming to dismantle the Deep State and combat the Woke agenda associated with the Democratic Party. https://image.nostr.build/06de3f0de3d48e086f47d0418d30e32cbfe0d88f452a93706987b7394458952d.jpg Dissolution of the DHS and Redistribution of Functions The Department of Homeland Security (DHS) was established in 2002 in response to the September 11 attacks, with the goal of consolidating various agencies responsible for domestic security under a single command. The DHS includes agencies such as FEMA, TSA, ICE, and CISA. Project 2025's proposal to dissolve the DHS and redistribute its functions to other agencies aims to address excessive bureaucracy and a lack of cohesion, arguing that centralization has failed to effectively integrate its diverse missions. https://image.nostr.build/ffca8d274914b725183b8fb19162c1b63f4d987c24e598f2eca88901d4a1a43c.jpg Impact on the Democratic Deep State: The dissolution of the DHS would pose a significant threat to the Democratic Deep State, as it would redistribute the power concentrated in a single entity across multiple other agencies, making it more difficult to politicize and centralize control over domestic security operations. This decentralization would reduce the ability to use the DHS as a political tool against opponents. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Primary Recommendations Combining Immigration Agencies: Merge U.S. Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), U.S. Citizenship and Immigration Services (USCIS), the Office of Refugee Resettlement (ORR) of the Department of Health and Human Services (HHS), and the Executive Office for Immigration Review (EOIR) of the Department of Justice (DOJ) into a new autonomous border and immigration agency. https://image.nostr.build/58eef4f2eca0ed2400261ec878c1dba2ca4bca519a16751b1fb7abd45da2906b.jpg Privatization of the TSA: Privatize the Transportation Security Administration (TSA), drawing inspiration from Canadian and European models, to reduce costs and improve service for travelers. Division of the Secret Service (USSS): The U.S. Secret Service (USSS), responsible for protecting national leaders and investigating financial crimes, would be divided. The protective element would be transferred to the Department of Justice (DOJ), while the financial investigations element would be moved to the Department of the Treasury. https://image.nostr.build/0a065cdbf158db4bc17b9aacd4af5a94029004caaa152eebf2c557042b08a641.jpg Impact on the Democratic Deep State: The division of the USSS would significantly weaken centralized control over protection and financial investigations, making it more difficult to use these functions for political purposes. Transferring the protective element to the DOJ and the financial investigations element to the Treasury would complicate efforts for any group or party to manipulate these crucial government functions for partisan objectives. https://image.nostr.build/1597e3b88572fe8aae7ce67cdaf975a873cf8bc68f76d59cb4253ad1520fc7bc.jpg Cybersecurity and Infrastructure Security Agency (CISA) Established in 2018, CISA is a federal agency responsible for protecting the U.S. critical infrastructure from cyber threats. CISA's mandate includes ensuring cybersecurity for sectors such as energy, transportation, and healthcare, and it collaborates with public and private entities to strengthen the country’s cyber resilience. Criticisms and Restructuring Proposals: Project 2025 strongly criticizes CISA for deviating from its original mission and being used as a political tool for censoring speech and influencing elections. The proposal is to transfer CISA to the Department of Transportation (DOT) and return the agency to its statutory focus. https://image.nostr.build/8bfb4a45053de96a775f67e3e1b83a44d9a65fee4705e3b16d3359bd799b8af2.jpg Review of Executive Order 12333 Executive Order 12333, issued in 1981, sets guidelines for U.S. intelligence activities, including the collection, analysis, and dissemination of information. Project 2025 proposes a review of this order to ensure that intelligence agencies are not used for political purposes but are focused on protecting national security. Objectives of the Review: Prevent Abuse: Ensure that intelligence collection is conducted legally, without being used to target political opponents. Ensure Impartiality: Reaffirm that intelligence operations must be conducted impartially, with a sole focus on the country's security. https://image.nostr.build/90d31cb35a33048d311716df2fbc65c97bd4c1972977e266133654404393fca0.jpg Reforms in Public Service Facilitation of Public Employee Dismissal: Project 2025 emphasizes the need to simplify the process for dismissing public employees who do not perform their duties impartially or who promote specific political agendas. Performance Evaluations: The document highlights the importance of merit-based compensation, stating that performance evaluations are only effective when tied to real consequences. Research indicates that 90% of major private companies in the U.S. use a merit-based pay system linked to evaluations. However, in the federal government, compensation remains largely based on seniority, despite efforts to adopt merit-based pay. https://image.nostr.build/1b858fd7b2a23c3c65c0677d3e69c44976721bbdcbe7facf4682ba3371562cff.jpg Inclusion of Employees Aligned with Conservative Values: Aligned Hiring: Establish mechanisms to hire public employees who share conservative values, ensuring that the policies and practices of agencies are consistent with the principles endorsed by the administration. https://image.nostr.build/ddbf5c59e7bb479998433991347f9d301dd117fbca0edb0f94e98fcac90b2974.jpg Controversial Cases and Politicization: Hunter Biden Laptop Case: Project 2025 harshly criticizes the FBI and the Department of Justice, accusing them of acting in a biased and politically motivated manner. The authors suggest that the agency is intimidating parents who protest by labeling them as "domestic terrorists," while simultaneously suppressing politically unfavorable speech under the guise of combating "disinformation." Furthermore, the critique highlights that the FBI is alleged to be neglecting violent attacks on pregnancy centers and violations of laws prohibiting attempts to intimidate Supreme Court justices. The criticism intensifies with allegations that the FBI interfered in domestic elections and engaged in propaganda operations, specifically citing the purported Russian collusion conspiracy in 2016 and the suppression of the Hunter Biden laptop case in 2020, which is seen as a threat to the Republic. https://image.nostr.build/e4f571a14102a939164465498bef514379ec0443e71a58e12f50c518e00570c6.jpg Politicization of the FBI: Election Interference: Russia Hoax and Trump, Suppression of Hunter Biden’s Laptop, and Big Tech Collusion. Revelations about the FBI’s role in the 2016 "Russia Hoax" and the suppression of Hunter Biden’s laptop in 2020 suggest that the agency may have strayed from its impartial duties. These actions indicate concerning politicization, where the agency appears to have been used to influence the political landscape in favor of certain interests. This includes collaboration between the FBI and Big Tech companies to control discourse. https://image.nostr.build/5dcd45fcec939b782d29d8d2e3d3b45244c525b5dbd3240f1629a4632e390a86.jpg Comprehensive Review of FBI Investigations: It is crucial to conduct an immediate and thorough review of all significant investigations and activities within the FBI, terminating those that are illegal or contrary to national interests. This step is essential for restoring public trust in the FBI. A public report on the findings of this review could enhance transparency and confidence. https://image.nostr.build/df98e2c6aff123d806187eab13d24a3ebb30a87df1f44cf57be97dc5624fff88.jpg Structural Reorganization: Align the FBI within the Department of Justice (DOJ) according to its purposes of national security and law enforcement. The agency should be under the supervision of the Assistant Attorney General for the Criminal Division and the National Security Division, ensuring that the FBI does not operate as an independent entity but is instead subordinated to the DOJ’s directives. https://image.nostr.build/0d1c0015c6b67a8afc2dd1595357ea571fcd5a9d83829065f49f9b60cf553eb0.jpg Prohibition on Policing Speech: Prohibit the FBI from engaging in activities related to combating "disinformation" or "misinformation" disseminated by Americans who are not linked to plausible criminal activities. The Constitution, through the First Amendment, prohibits the government from policing speech, ensuring a healthy public debate without governmental intervention. All these measures represent a significant attack on the "Deep State" within American institutions. These public policies have been considered a dictatorial threat by many sectors of the American press. However, the real issue should be the politicization of unelected bureaucrats by a political faction. https://image.nostr.build/9a44b19d15d53314f89528c1d89e2f637030ea18d8907a6a8c4e27d07064b8ec.jpg Combating Woke Culture in the Intelligence Community Future leadership of the Intelligence Community (IC) needs to implement a plan to replace the "woke" culture and identity politics that have spread throughout the federal government. The goal is to restore traditional American values such as patriotism, racial impartiality, and job competence, which have been replaced by advocacy for "social justice" and identity politics. https://image.nostr.build/7929dca5e36273c8e751f36d6ca6229f362e30792bce735f10be7e5d8581af5f.jpg Final Considerations The Heritage Foundation’s Project 2025 is not merely an administrative reform plan; it is a manifesto of resistance against the Washington status quo. The proposals aim to dismantle established power structures, eliminate politicization, and combat the Woke agenda. If implemented, this plan would profoundly impact how the U.S. government operates, promoting a more efficient, limited government aligned with conservative principles. Threat to the Democratic Deep State: A potential new administration under Donald Trump represents an existential threat to the Democratic Deep State entrenched in American institutions. The dissolution of the DHS, depoliticization of intelligence agencies, division of the Secret Service, review of Executive Order 12333, privatization of the TSA, and the hiring of employees aligned with conservative values are all measures that would significantly weaken centralized control and the ability to use these institutions for political purposes. By dismantling concentrated power and promoting a more transparent and accountable government, Project 2025 aims to restore public trust and ensure that government agencies serve national interests rather than partisan ones. Of course, not all aspects of the plan may be implemented, but the prospect of several of these measures being enacted should be a cause for concern for the Democratic Deep State.
-
 @ eed76ece:afa98124
2024-09-08 21:13:37
@ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense.
Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B.
We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event.
So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail).
Thank you, https://www.globalmerchant.io
originally posted at https://stacker.news/items/677390
-
 @ e8b86bc1:3503c58f
2024-09-08 19:37:36
@ e8b86bc1:3503c58f
2024-09-08 19:37:36Opinion about Freewallet Multi Crypto Wallet (iphone)
Freewallet is now charging inactivity fees, a sneaky method to take money from users who aren’t regularly using the app. Avoid this scam wallet!
WalletScrutiny #nostrOpinion
-
 @ a58a2663:87bb2918
2024-09-26 11:14:34
@ a58a2663:87bb2918
2024-09-26 11:14:34Quem sabe – quem sabe! – você se interesse em saber como andam as minhas pesquisas sobre o “projeto humanista” em “A alegoria do mundo: o mago, o filólogo e o colonizador”, módulo atual de Convivium – Seminário Permanente de Humanidades.
Na semana passada fiz uma transmissão de áudio no grupo do Telegram dos participantes. Entre outros temas abordados, pude falar da interpretação que Edgar Wind faz do quadro “Primavera”, de Botticelli, como uma explicitação do tipo de alegoria platonizante que dominaria a mente de humanistas da Renascença.
https://image.nostr.build/6e1ee79986d3d4c929609fdf037a3e1e6ee399559fb7e2b5d8c02ad0b9b188ad.jpg
A alegoria é o modo mental, defende E. H. Gombrich, pelo qual uma tese é proposta antes que as causas e analogias que a embasam sejam estabelecidas, de modo que o processo associativo irá apenas justificar a posteriori o que se quis desde logo comunicar. Imagine George Orwell postado às suas costas enquanto você lê 1984. A todo momento, ele irá cutucar o seu ombro e dizer: “Está vendo? Aqui está o que eu quis dizer com a fala desse personagem nesse trecho”. O texto é apenas pretexto para uma mensagem, e é a mensagem que se ergue com claro perfil discursivo diante do leitor. A ficção começa a ceder espaço para o palanque.
Defendo que a alegoria é a mãe das mitologias abstratas, do romance de tese e da experiência de avatar que caracteriza o mundo digital. E seus princípios de analogia arbitrária, que datam do fim da Idade Média, ganham exemplificação máxima nas obras Da magia e Dos vínculos, de Giordano Bruno, que discutirei numa aula ao vivo hoje (26), às 20h30. Na atuação de Bruno se nota como a magia foi cada vez mais percebida de maneira imaterial, abstrata, psicologizante (e dessa sua concepção nos vêm os primeiros prenúncios do inconsciente), ao mesmo tempo que sua primeira ocupação com o mundo material foi aos poucos transferida para as ciências que tendiam a ignorar o elemento humano que manipula esse mesmo mundo material.
Se por um lado, portanto, começa a triunfar uma cosmovisão que supõe um ser humano quase sobrenatural em seus poderes psíquicos (segundo a nova ideia de magia como manipulação da memória), por outro lado começa a se difundir uma cosmovisão que supõe um mundo subtraído de todo elemento humano, uma espécie de cosmos impessoal, aquele que hoje se encontra nos livros de física. Penso que essa como que esquizofrenia reflete a dinâmica de exaltação e depressão do erudito que comentei durante a leitura do Fausto de Goethe realizada no primeiro módulo de Convivium: o herói do poema ora se sente um deus ora se sente um verme, tal como hoje é muito comum nos sentirmos.
Na aula de hoje irei lidar com aquele primeiro aspecto da analogia como arma de um ego entronado, ao passo que na primeira semana de outubro irei disponibilizar aos alunos o texto “Máquina e segredo”, acompanhado de vídeo com comentários complementares. Nesse escrito tratarei, por exemplo, de como os inventos de Giambattista della Porta (1535-1615), especialmente na área da criptografia, assinalam não só um novo estágio na história da tecnologia, como também um novo estágio da disposição dos estudiosos para com o conhecimento, uma disposição típica do que venho chamando de “nova aposta de Pascal”, conceito que terei a oportunidade de rever.
“Máquina e segredo” será o primeiro excerto que colocarei em discussão do ensaio O destino do humanismo, que talvez acabe recebendo o título de A alegoria do mundo, como o atual e terceiro módulo de Convivium; a ver.
Para comemorar este momento importante das pesquisas que venho fazendo a respeito do “projeto humanista” (iniciadas em 2020, privadamente, e continuadas algo publicamente a partir de 2022), resolvi dar 25% de desconto na inscrição de Convivium para quem optar por pagar em bitcoin. Algumas pessoas já chegaram a Convivium por meio do Nostr, e é minha intenção trazer ainda mais gente. Em vez de pagar R$ 449, pague agora R$ 336,75 para ter acesso a:
- O destino do humanismo: uma leitura do Fausto de Goethe, com 12 aulas, materiais complementares e aulas bônus (mais de 20 horas de vídeo);
- Os livros da vida: Abelardo, Dante, Cardano, Santa Teresa, com mais 12 aulas, textos e materiais auxiliares (mais de 20 horas de vídeo idem);
- A alegoria do mundo: o mago, o filólogo e o colonizador, módulo em andamento e com aulas mensais até abril de 2025. Até o momento tivemos 4 aulas ao vivo, 3 vídeos pré-gravados e 3 transmissões de áudio, além de comentários esparsos pelo grupo do Telegram.
Caso queira se inscrever pagando em bitcoin, mande-me uma mensagem privada ou e-mail para camoensiii57@protonmail.com
-
 @ c11cf5f8:4928464d
2024-09-08 19:10:39
@ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network?
originally posted at https://stacker.news/items/677270
-
 @ 6f170f27:711e26dd
2024-09-08 17:45:46
@ 6f170f27:711e26dd
2024-09-08 17:45:46Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]."
Manufacturing:
Life expectancy:
Happiness:
Many other metrics & discussion in the source:
https://x.com/cremieuxrecueil/status/1832588128084730334
originally posted at https://stacker.news/items/677211
-
 @ 129f5189:3a441803
2024-09-09 23:11:19
@ 129f5189:3a441803
2024-09-09 23:11:19Precious metals have served as monetary backing for millennia, but this does not guarantee that gold is a safe investment or a good hedge against economic crises and monetary collapses. Since its last major rally in the 1980s, gold has been progressively demonetized. Those who acquired gold in the late 1980s will need to rely on a significant increase in demand or a supply shock for its price to rise by 561% and regain the purchasing power it had 40 years ago. https://image.nostr.build/dd5fec2b474ea34cd72ddf5781393b528e63a358d523c9428f3ba4649f4f42aa.jpg If you look at the purchasing power of $1 (green line), you'll see that the depreciation is even faster. This might create the impression that gold is a good store of value. But does the fact that something loses value more slowly amidst a general decline really make it a store of value? Unless the total demand for gold increases at the same rate as its supply has grown in recent years, the purchasing power of the metal is likely to decline. https://image.nostr.build/9f24f6cf37780fe851746057520064ed94acd96547be53bd341c9e15b8762773.jpg In other words, if you own an ounce of gold, that ounce will represent an increasingly smaller fraction of the total gold reserves, meaning you are being diluted. Additionally, one should also consider the cost and risk of storage, but that's another issue. If you don't want to compare the purchasing power of gold today with the 1980s, you can consider its value from 9 years ago. Between September 2011 and November 2015, the Fed printed approximately $2.8 trillion. This also provides a perspective on gold's depreciation relative to the significant monetary expansion during that period. https://image.nostr.build/822e0a861e16ca258e0427875a84b5c8e5420e51bcf65674b453b55ed78edefd.jpg In other words, the Fed expanded its monetary base by about 30% during that 4-year period. However, the price of an ounce of gold fell by 45% (from $1,900 to $1,057) over the same interval. A true store of value should protect against excessive money printing. In contrast, during that same period, Bitcoin appreciated by 8,500% (from $5 to $419). https://image.nostr.build/32a7ca39a6e69e2780f9ab49390c7b7380499fcfe54ae4ef693e6fc91686a41e.jpg Indeed, while it is interesting to note that this was the exact period when gold derivatives were launched on CME Group, it's important to remember that correlation does not imply causation. Many factors can influence the price of gold and Bitcoin, and establishing a direct causal relationship requires more detailed analysis. https://derivsource.com/2011/06/21/cme-group-announces-the-launch-of-three-new-short-term-gold-crude-oil-and-natural-gas-options-contracts/ In an asset where supply can only be physically verified, flooding the market with gold contracts could lead to significant issues. This might result in market manipulation, legal liabilities, fines, and potentially even imprisonment for those involved. Such actions can undermine the integrity of the market and lead to regulatory and legal consequences. https://www.cnbc.com/2018/11/06/ex-jp-morgan-trader-pleads-guilty-to-manipulating-metals-markets.html Over longer periods, gold has not functioned as a true "store of value" relative to the dollar for quite some time, despite recently returning to its price from 9 years ago. This suggests that, while gold may have periods of price recovery, it has struggled to maintain its value over extended horizons compared to fiat currencies. It's worth noting that before 1980, aluminum was valued higher than gold. This reflects how market dynamics and technological advancements can significantly impact the value of commodities over time. https://www.mgsrefining.com/blog/why-aluminum-is-no-longer-a-precious-metal/ While gold has been undergoing a gradual demonetization process since 1980, another asset appears to be experiencing the opposite—hyper-monetization. (See in red; don't be alarmed.) https://image.nostr.build/435a5369f778a7be727b50e4c6328cfc353240bf804e1ed69313b9a8e1233f7e.jpg With the advent of Bitcoin, you believe that gold will continue on the same path as silver since the end of the bimetallic standard in 1853: a prolonged process of demonetization, with increasing volatility and reduced liquidity. https://image.nostr.build/5b9c8bfdb09e51d639e380df160c98beb9ee1d917ea13d28ef67711cfa5f8086.jpg Since 1913, the dollar has lost 97% of its purchasing power. Over the same period, the gold supply has increased significantly. Since 1980, gold has lost about 82% of its purchasing power. Given that the dollar is used as the unit of account and gold's liquidity is measured in dollars, these changes reflect the complex interaction between the currency and the precious metal. The U.S. is by far the country with the largest gold reserves in the world and is also the fourth-largest miner of the metal. Additionally, the country controls and issues the currency that serves as the unit of account for gold and has the highest liquidity in global trade. Is gold easy to transport? Is it simple to verify its supply and authenticity? Is it practical to store? Is its industrial utility significant? Can it be disrupted? And what about the continuous increase in its supply? These are important questions to consider. In my humble opinion, it will not be the dollar or fiat currencies that will suffer the most from the existence of Bitcoin, but rather the market cap of gold. https://image.nostr.build/61dddefabc4b69f784631a3294bdd978e3411bba40fb52d585e13b48002389fe.jpg
-
 @ 8f69ac99:4f92f5fd
2024-09-26 11:08:21
@ 8f69ac99:4f92f5fd
2024-09-26 11:08:21As revoluções muitas vezes começam com os membros mais jovens da sociedade—adolescentes, idealistas e cheios de energia, ansiosos por causar mudanças. No entanto, no mundo de hoje, a noção de revolução foi sequestrada por forças que procuram controlar e manipular, em vez de empoderar os indivíduos. A chamada "revolução woke" é um exemplo claro, impulsionada por uma agenda que polariza a sociedade ao longo das linhas da política identitária. Esta distracção desvia a atenção dos verdadeiros problemas: a desigualdade económica e o autoritarismo. Mas há uma alternativa melhor, uma que prioriza a liberdade e a soberania em vez da divisão e do controlo—Bitcoin.
A "Revolução Woke" Globalista e a Agenda da Polarização
Uma das tácticas mais insidiosas da "revolução woke" é a polarização deliberada da sociedade. Ao criar narrativas que colocam as pessoas umas contra as outras com base em raça, género, religião e política, aqueles no poder mantêm o controlo e desviam a atenção dos problemas mais profundos que realmente importam. Esta estratégia é orwelliana: ao criar uma mentalidade de "nós contra eles", fabricam uma cultura de conflito perpétuo.
Em vez de promover uma mudança significativa, a "revolução woke" prende as pessoas num ciclo de indignação e divisão, distraindo-as de enfrentar as verdadeiras estruturas de poder—como a desigualdade económica e o excesso de controlo estatal. Esta fragmentação enfraquece os laços entre as pessoas, tornando a sociedade mais vulnerável à manipulação pelas autoridades centralizadas.
Esta polarização serve os interesses daqueles que estão no poder. Quando as pessoas estão demasiado ocupadas a lutar entre si, são menos propensas a questionar os sistemas que realmente as controlam. A "revolução woke" torna-se menos uma questão de progresso genuíno e mais uma forma de manter o status quo através da divisão e da distracção.
Por Que a Polarização é Incentivada
A polarização não é acidental—é uma estratégia calculada com o objectivo de controlar. Dividindo as pessoas em campos opostos, a sociedade fragmenta-se, tornando mais difícil para os indivíduos unirem-se contra adversários comuns ou combaterem políticas que beneficiam as elites.
Esta divisão serve também como uma distracção poderosa. Enquanto as pessoas estão consumidas por batalhas ideológicas, os sistemas financeiros centralizados e o controlo governamental expandem-se silenciosamente. Os meios de comunicação, muitas vezes controlados pelos mesmos poderes, alimentam estas divisões, mantendo as pessoas focadas em conflitos internos enquanto ocultam as verdadeiras ameaças à liberdade.
A polarização também corrói as liberdades individuais. Quando as pessoas estão envolvidas em batalhas ideológicas intermináveis, são menos propensas a notar a erosão gradual dos seus direitos. Isto é precisamente o que os poderes estabelecidos desejam—uma população distraída e dividida, demasiado ocupada para desafiar o desmantelamento lento das suas liberdades pessoais.
O Resultado da Polarização
O resultado desta polarização deliberada é uma sociedade mais preocupada com a pureza ideológica do que com a garantia das suas verdadeiras liberdades. As pessoas ficam presas na política identitária, priorizando a lealdade ao grupo em detrimento da autonomia individual. Isto promove uma mentalidade de "pensamento de grupo", onde questionar a narrativa dominante é desencorajado.
Entretanto, a desigualdade económica aprofunda-se à medida que os poderes centralizados continuam a consolidar o controlo. Os sistemas que deveriam promover equidade tornam-se cada vez mais manipulados, beneficiando os poucos em detrimento dos muitos. A verdadeira liberdade—especialmente a liberdade financeira—torna-se mais difícil de alcançar, com os indivíduos presos em sistemas concebidos para beneficiar uma minoria poderosa.
No final, a "revolução woke" apenas reforça as mesmas estruturas que afirma combater. Ao dividir as pessoas e distraí-las dos verdadeiros problemas, os poderes estabelecidos mantêm o seu controlo, enquanto as liberdades pessoais e financeiras da maioria continuam a ser corroídas.
Bitcoin: A Verdadeira Revolução
Em contraste com a "revolução woke", que divide, Bitcoin oferece uma verdadeira revolução—uma que empodera os indivíduos em vez de os separar. Bitcoin proporciona soberania financeira, retirando poder dos governos autoritários e das instituições centralizadas.
Bitcoin permite que os indivíduos controlem a sua própria riqueza, eliminando a necessidade de intermediários como bancos ou governos. As pessoas já não estão sujeitas a entidades que restringem a sua liberdade financeira. Com Bitcoin, podem criar, armazenar e transferir valor de forma segura, transparente e acessível.
Isto não se trata apenas de economia—é sobre recuperar a liberdade. A natureza descentralizada do Bitcoin permite que as pessoas tomem decisões financeiras sem interferência do estado ou de entidades corporativas.
Porque é Que o Bitcoin é Revolucionário
A verdadeira natureza revolucionária do Bitcoin reside no seu design e princípios, que rompem com os sistemas de controlo enraizados. Eis algumas razões pelas quais o Bitcoin é transformador:
-
Aberto e Sem Fronteiras: O Bitcoin transcende fronteiras, permitindo que pessoas de todo o mundo participem igualmente no sistema financeiro. Quebra barreiras baseadas em nacionalidade ou geografia, permitindo uma participação económica global.
-
Resistente à Censura: Nenhum governo ou empresa pode parar uma transacção em Bitcoin, dando às pessoas a liberdade de transferir valor sem medo de interferências ou retaliações. Esta é a forma definitiva de autonomia financeira.
-
Sem Permissão: O Bitcoin não requer aprovação de nenhuma autoridade. Ao contrário dos sistemas financeiros tradicionais, não há porteiros a controlar quem pode participar, tornando o Bitcoin uma ferramenta para a verdadeira auto-soberania financeira.
-
Neutro: O Bitcoin é imparcial. Não se importa com raça, género, religião ou política. Num mundo onde a política identitária é usada para dividir, o Bitcoin trata todos de forma igual, oferecendo um sistema financeiro inclusivo que transcende essas divisões.
Bitcoin como o Antídoto para a Polarização
O Bitcoin oferece uma solução para a divisão criada pela polarização. Transcende a política identitária ao tratar todos de forma igual, independentemente da sua origem ou crenças. A neutralidade do Bitcoin garante que nenhum grupo ou facção pode manipulá-lo para impor as suas visões sobre os outros.
Bitcoin permite que os indivíduos se libertem das narrativas divisivas e tomem controlo dos seus destinos financeiros. Promove a cooperação em vez do conflito, capacitando as pessoas a focarem-se em objectivos comuns, em vez de batalhas ideológicas.
O Bitcoin não é apenas uma moeda—é uma força unificadora, oferecendo esperança àqueles que estão cansados da divisão e das lutas pelo poder. Representa uma mudança para práticas financeiras inclusivas que priorizam a autonomia individual em detrimento do controlo centralizado.
Um Apelo à Acção
Para os jovens que sonham em criar uma mudança real: se querem liderar uma revolução que verdadeiramente empodere os indivíduos e quebre as cadeias do controlo centralizado, então é hora de abraçar o Bitcoin.
Esta revolução não é sobre seguir uma agenda predefinida ou alinhar-se com ideologias divisivas. Trata-se de criar um futuro de sistemas financeiros abertos, onde todos têm a liberdade de participar igualmente.
A cor desta revolução é laranja, simbolizando o logótipo do Bitcoin e o movimento em direcção à liberdade financeira. Representa a esperança para aqueles que querem escapar das restrições dos sistemas tradicionais e criar um mundo descentralizado e empoderado.
Conclusão
Estamos à beira de uma revolução financeira. A juventude tem uma escolha: seguir as narrativas pré-definidas dos sistemas ultrapassados ou tomar controlo dos seus próprios destinos através de redes financeiras descentralizadas e abertas.
O Bitcoin é a verdadeira revolução. É um movimento impulsionado pelo desejo de liberdade, autonomia e inclusão. Juntem-se à revolução, sejam parte de algo maior, e ajudem a construir um mundo onde o poder é descentralizado, as oportunidades são iguais e o futuro é brilhante e laranja—a cor da liberdade financeira.
Photo by Tarik Haiga on Unsplash
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
telegram设置:
- 需要有telegram账号
- 通过@BotFather创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 @VersaToolsBot机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
其他
- 成人内容屏蔽
- pico 使用api接口 去项目地址看
最后
我搭建的地址: https://imgbed.lepidus.me
-
 @ d52f4f20:98efcdfb
2024-09-08 12:05:31
@ d52f4f20:98efcdfb
2024-09-08 12:05:31original post 28/12/2010 .net
Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade.
Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima
Alguns conceitos da minha instalação – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará.
Seria bom/Pré-Requisitos – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim).
Introdução A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot.
Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.
 Esta é a primeira tela exibida após o boot, selecione o menu
Esta é a primeira tela exibida após o boot, selecione o menu
Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?
 Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.
Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador. Aqui você estara selecionando daonde pacotes serão baixados.
Aqui você estara selecionando daonde pacotes serão baixados. Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
 Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.
Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.
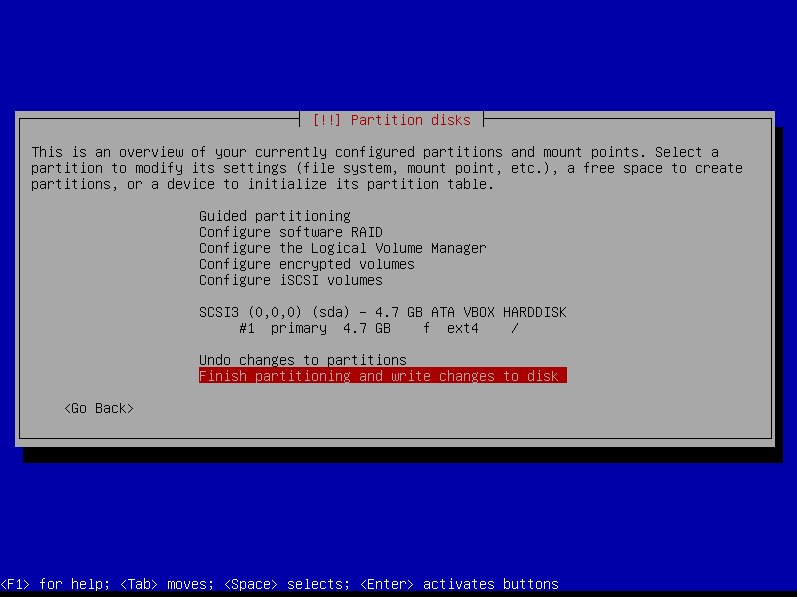 Após criar, FINISH!
Após criar, FINISH!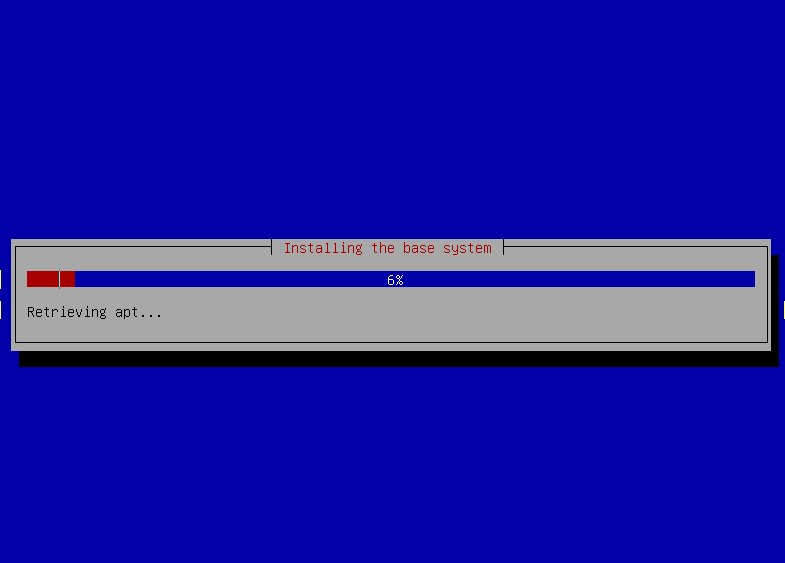 Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.
Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.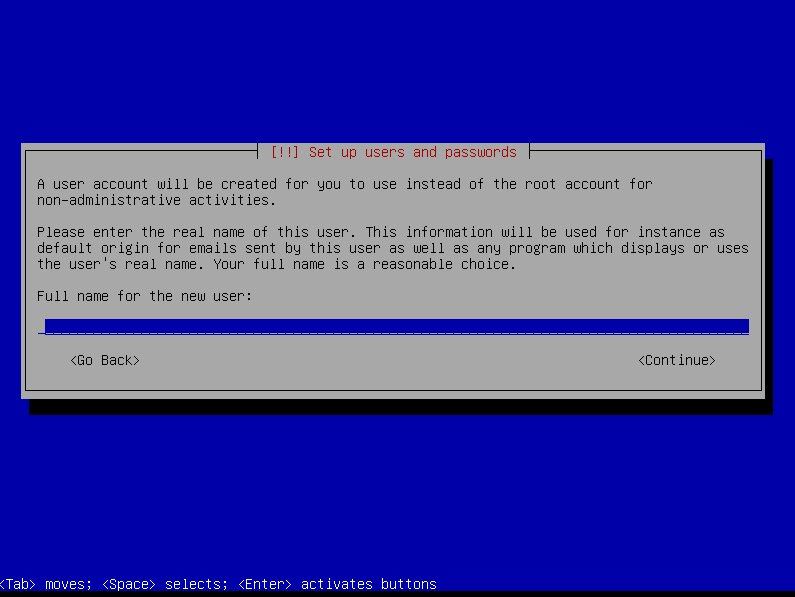 O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.
O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.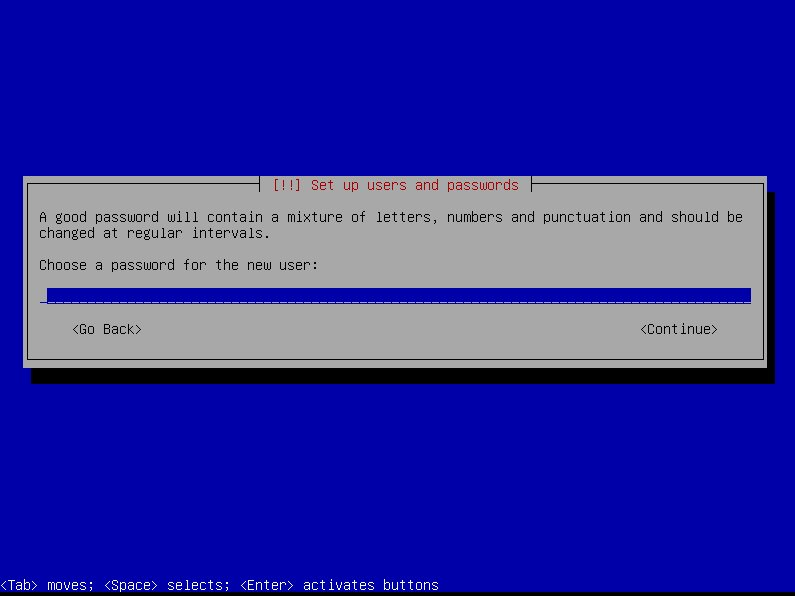 senha é bom por né.
senha é bom por né. Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
 Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.
Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente. Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.
Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar. Grub é o gerenciador de boot, instale ele ai sem medo.
Grub é o gerenciador de boot, instale ele ai sem medo. Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.
Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).
 **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.
**Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.Torna-se root Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário.
$ sudo passwd rootPronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário.
Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root.
Instalando o vim
```
apt-get install vim
``` (repare # você tem que estar logado como root)
Removendo o boot-splash Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura.
Removendo Mensagem de boas vindas MOTD Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ;
UPDATE Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login:
session optional pam_motd.so
sshd:
session optional pam_motd.so # [1]
Mudando mensagem da versão
Dica velha edite o arquivo “/etc/issue” coloque o que preferir.
——Se você não precisa de modo gráfico a instalação terminou aqui.
Alterando o sources.list adicionando outros repositórios
Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo.
Instalando o resto dos pacotes
apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious
Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação.
Como entrar no modo gráfico?
Logue-se com seu usuário
$startxO comando antigo, simples, que dei a primeira vez no meu conectiva 4.
Este é o resultado final, mas para isso vamos algumas dicas.
Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai
```
Set desktop wallpaper
nitrogen –restore &
Enable Eyecandy – off by default
xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 &
Launch network manager applet
(sleep 4s && nm-applet) &
Launch clipboard manager
(sleep 1s && parcellite) &
Uncomment to enable system updates at boot
(sleep 180s && system-update) &
cairo-dock &
Launch Conky
conky -q &
Launch panel
tint2 & ``` Configurando teclas de atalho, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo:
<keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind>Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet.
Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele.
blog #tech
-
 @ a9434ee1:d5c885be
2024-09-26 10:42:52
@ a9434ee1:d5c885be
2024-09-26 10:42:521. Relay = Community?
If spinning up a relay is getting easier and cheaper by the day, why can't the relays literally be the group/community?
Then: * Any relay is by default a public community. The more restricted read- or write-access is, the more it becomes a private group. * Any publication targeted at (h-tag) and stored, and thus accepted, by a relay can be seen as a publication in that community. * All-in-1 hosting solutions (integrated blossom servers, lightning nodes, ...) are made easier.
2. Why invent new kinds?
Why can't Kind 1 posts that are targeted and accepted by a relay (i.e. community) just be the forum-posts of that community? Why create new kinds for this? And even weirder, why create a new kind with that exclusively serves as a reply to that new kind? Why not just use generic replies (kind 1111) and take the #otherstuff (event kinds and apps) as an opportunity to introduce those?
For chat messages, however, I get it. You need a kind + reply-kind for those.
3. Community VS Private group
It seems like the only distinction you really need, both for the user and the apps implementing all this, is:
1. Public Community: anyone can read and follow this community but for writing the admins can set limits (pricing, white listings, ...) 2. Private group: only the profiles that even know this relay (i.e. group) exists can interact with it. Read-access has to be granted (invite, pricing, ...) and admins can set limits for writing too. Beyond this distinction it's a bit naive to try to categorize them. Open vs Closed doesn't really mean much for example, since technically all groups/communities set limits and are thus closed. It's more interesting to look the ways in which they can be closed and build on the simplest distinctions you can make there.The difference between Public communities and private groups is the most important one because they both have very different UX and specification requirements:
Memberlist
Communities: None existent
Anyone can read and follow. It just has limits on who can publish what, when. So the most interesting thing to surface is probable something like a list of most active members or a highlighted set of profiles that have special characteristics within this community (top supporter, god-mode, resident artist, ...).
Private Groups: Necessary for it's existence
The whitelisted npubs for read-access are the members.Moderation actions
Both types of groups need a way for the admin(s) to:
* Block/remove users * Remove events * Edit metadata (name, description, guidelines...) * Specify who can write publish what, under what conditionOnly private groups need a way for the admin(s) to:
* Add/approve new members → specify who has read-access, under what conditionGeneralizing too many actions like
add member,join request, etc... that are only applicable to one of these categories just creates bad UX for the other one. You don't "add a member" to a public community. People can follow it without asking anyone's permission (ok yes, some will AUTH for reading but that's besides the point). Some of its followers will then just choose to publish something there and the admin either allows them or not.Having a common protocol for specifying the conditions for this write-access interoperably (as mentioned above) is what I would like to see instead: * Both Communities and Private groups need it anyway * You have to assume admins need granularity in the conditions they set for publishing in their group/community: Who, what, under what condition, ... * You don't want to link out to custom websites (or similar) explaining their allowance schemes
Sidenote: we need a similar kind of spec for the services that allow you to spin up your hosting solution (relay, server, node, ...) so that, when you click "Create new community" in an app, those services can be surfaced. With their business models (including options to self-host parts of it) just there, in the app, without linking out. Same for the lines of communication and payments that are needed to make those business models work from within any app.
Publication and Discovery
Only Communities allow for the exciting possibility of publishing something in multiple overlapping communities at once. Someone writing about how Bees are Capitalists can target their article at the communities that most overlap with its content (and with the author's means and write-access of course). Members of a community around beekeeping can organically discover content and communities on Austrian economics relevant to them.
With Private groups publication happens only in the group and discovery is blocked on purpose.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ c11cf5f8:4928464d
2024-09-08 09:08:04
@ c11cf5f8:4928464d
2024-09-08 09:08:04
Here we are again with our The Magnificent Seven, trying to give you a hit of what you missed this past month in the ~AGORA territory.
Top-Performing Ads
Drumroll please 🥁 ... for the most engaging ones:
01[SELL] 1 Million Products, Travel Agency, Concierge and Cars - ShopinBit.com by @shopinbit02[SELL] Satoffee⚡️☕️ Cafeteras automáticas que aceptan Bitcoin Lightning 🇪🇸 🌐 by @VEINTIUNO03[⚖️SELL] Hand-Made Flecktarn Pouch(es) by Fabs04[OFFER] Proton Wallet - 3 invites left by @npub1q67p49masrcjf__d7qaq6mwh0q05[SELL] Bitcoin Accepted Here – Unisex organic cotton Black T-shirt by @VEINTIUNO06[FOR SALE] Playstation 2 (PS2) Games - Excellent Condition - Pay In SATS!!! by @watchmancbiz07[OFFER] Happy Bitcoin Infinity Day by @thebullishbitcoiner
In case you missed
Here some interesting post opening conversation and free speech:
This edition winner look's @proofoftaste, with his request for help finding a way to get a local product delivered to his country. The challenge was that the producer, required an ID number on checkout! Pretty unusual... or it will be soon the norm?
Thanks a lot for @supratic for being so active in the territory and sharing so many topics and articles about commerce and law, basically giving us a hit on how the world is currently ruled, pretty fascinating!
01Can someone in Italy help me get my favourite sauce to Germany? by @proofoftaste02The History of Banking – Ernest Rauthschild by @supratic0310 Hidden Rules of Commerce by @supratic04How to Start Your Own Micronation by @supratic05[Understanding the One People's Public Trust: A Beginner's Guide to the OPPT(https://stacker.news/items/641554/r/AG) by @supratic06A Bank Whistleblower called me... by @supratic07One Stupid Fu*K 🥒 Contract Killer Course 2.0 - Brandon Joe Williams by @02a0eb55b5
🏷️ Spending Sunday is back! https://stacker.news/items/653241/r/AG
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats!
Just a reminder for you all
To incentivize more conversation and a more libre mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting.
Create your Ads now!
This territory aims to connect stackers and curious buyers online and IRL for exclusive P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
Let's start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to
Or contact @AGORA team on nostr DM and we'll help you publish a personalized post.
originally posted at https://stacker.news/items/676777
-
 @ c11cf5f8:4928464d
2024-09-08 08:35:16
@ c11cf5f8:4928464d
2024-09-08 08:35:16Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/676757
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 104f6f7d:220bf499
2024-09-26 05:01:05
@ 104f6f7d:220bf499
2024-09-26 05:01:05“He is free to make the wrong choice, but not free to succeed with it. He is free to evade reality, he is free to unfocus his mind and stumble blindly down any road he pleases, but not free to avoid the abyss he refuses to see.” - Ayn Rand
-
 @ a6e6a54b:8aca70c6
2024-09-26 04:41:21
@ a6e6a54b:8aca70c6
2024-09-26 04:41:21Outline
- Introduction.
- Setting the Ground with Definitions: UFO, UAP and The Phenomenon.
- About the Author: Luis Elizondo.
- Skeptical Approach.
- Non-Skeptical Approach.
- Spiritual-Metaphysical Component of UAP.
- Worldview Frameworks.
- Making Sense of UAP.
- The Stickiness of The Phenomenon.
- Possibilities for UAP.
- Spiritual-Metaphysical Beings.
- Human Nature.
- UAP Intentions.
- Psyop Hypothesis.
- Conclusions.
- References.
From Lights in the Sky to the Fallen
Expanding the Conversation from Imminent by Luis Elizondo
### 1. Introduction
Man’s mind, once stretched by a new idea, never regains its original dimensions. -Oliver Wendell Holmes.
During the past few years, there has been a resurgence of interest in the UFO-UAP topic. If you have been paying attention, you know by now that the phenomenon is real: there has been an acknowledgment of what people have been saying for years. However, if you are not aware of the current state of affairs, you might need to catch up. Imminent by Luis Elizondo [1] summarizes the latest events and his role in them. I think this book is not for UAP beginners, and I still consider myself as one. For this reason, it was not the book I was expecting, but it was the book I needed to challenge my approach to this topic. I had to make a mental shift in order to think about this issue more broadly. I will elaborate more on the challenges I faced later.
Luis “Lue” Elizondo explains his role as the Head of AATIP (Advanced Aerospace Threat Identification Program) run by the Pentagon and why he resigned due to the secrecy. As you can imagine, it is very difficult to make sense of someone else’s experiences, especially when they also involve the phenomenon. From my perspective, the book brings to the forefront yet another layer of this mystery —the spiritual and metaphysical component of UAP—, which is hard to process (it certainly was for me). I initially planned to write a review of the book, but I have decided instead that I will continue the conversation that Lue started, specifically about this aspect of UAP.
Keep in mind that whether you believe they live among us or think it is all nonsense, you may already have a strong bias that confirms your beliefs and dismisses any new information. This is part of what makes this topic so strange—most people seem to fall into one of two categories: either fully invested or completely indifferent. In my experience, the most common nuanced opinion among those who have not delved deeply into the subject but still want to appear open-minded is: “Of course, there are aliens somewhere in the universe, but it is ridiculous to think they have already visited us.” However, if you look closely at the discussions over the past few years, people are not necessarily talking about aliens visiting Earth—that is just one possibility being considered. I think claiming that aliens exist somewhere but have not shown up yet, and probably never will, is a comfort zone stance.
Furthermore, I am not inclined to convince anyone that this topic is relevant. But, if you already think that transparency is worth your time, then let’s think about the puzzle together!
Notes: 1. I think you should read the book, but if you prefer a summary and review of the key points made by Lue, I recommend watching Richard Dolan’s video: https://www.youtube.com/watch?v=uazfN6CqUeQ. 2. I have been careful with the quotes I am sharing here. Having listened to several hours of Lue’s interviews and podcasts, I have only included quotes he has publicly discussed. 3.
2. Setting the Ground with Definitions: UFO, UAP and The Phenomenon
I want clarify the meanings of UFO, UAP and the phenomenon, as I understand them:
- UFO: Unidentified Flying Object. This is a well-known acronym, often associated with flying saucers. It carries a lot of stigma, taboo, and conspiracy theories. Because of the recent surge of interest in the topic, the term "UFO" is not as commonly used anymore; instead, most people now refer to UAP. Additionally, the term UFO does not encompass the full range of the phenomenon.
-
UAP: Unidentified Anomalous Phenomena[^1]. It was previously defined as Unidentified Aerial Phenomena, but the phenomenon is not only aerial; it is transmedium (moving through air, space, and water—USO refers to Unidentified Submerged Object), and possibly transdimensional. Therefore, “anomalous” is a more accurate word, as it better captures the broader nature of the phenomenon.
-
The Phenomenon: This is the core of the issue and what we are trying to understand. The way that I see it, the phenomenon involves the interaction[^2] between humans and a non-human intelligence, which may be more advanced than us. The elements of interaction include:
Objects: These are observed in the sky, in the ocean, or coming from outer space. Objects can also be inserted into the human body. Examples include crafts, lights, and drone-like objects. These objects may appear tangible or not.
Entities or Beings: These are sometimes seen near or inside the objects, or on their own. They may communicate messages through unusual means. Their origin is uncertain—whether material or metaphysical in nature.
To summarize:
From a human perspective, the interaction with the phenomenon can be both material—occurring through devices, human senses, and visible changes in the body with biological effects—and psychological. Even more puzzling is that the phenomenon may enclose what some refer to as paranormal activity[^3].
Whatever the phenomenon is, it seems to have both material and non-material components. So, when we talk about evidence (photos, videos, vehicles, etc.) we might only be seeing one side of the coin, not the whole picture. I am being very deliberate in using the terms material and non-material because I am referring to the materialistic interpretation of the universe. I will expand more about this later.
[^1]: As for the word "phenomena," I do not think it is necessary to use "UAPs" to refer to the plural form. However, it is very common to see “UAPs” used everywhere. I will just stick with "UAP" in this discussion. [^2]: If they are seen or detected, that counts as interaction. When I mentioned earlier that some people say that “life exists somewhere else in the universe”, they are missing the point. The life forms that might exist elsewhere, which we do not yet know about, are not interacting with humans. [^3]: Some suggest that a subset of what we call paranormal activity can be caused or related to the phenomenon. Therefore, in the end, certain instances of paranormal activity could have a material explanation.
3. About the Author: Luis Elizondo
Luis Elizondo was recruited as a senior intelligence officer to help establish counterintelligence and security for the Advanced Aerospace Weapons System Applications Program (AAWSAP), which later became the Advanced Aerospace Threat Identification Program (AATIP). This program was focused on “unconventional technologies” (p. 6), “unusual phenomena” and investigated unidentified aircraft, specifically ones that seem to display beyond-next-generation technology and capabilities—what we now call unidentified anomalous phenomena, or UAP, or what were long referred to as UFOs (p. 8).
Some interesting details discussed at the podcast Theories of Everything with Curt Jaimungal [2] include: * Lue still keeps his security clearance. * Lue’s book went through a year-long review process by the Pentagon, resulting in certain parts being redacted.
Due to these factors, some speculate that he could be a disinformation agent. However, I do not agree with this notion, as other whistleblowers[^4] have come forward and support some of Lue’s claims. Additionally, Lue’s coming out appears to have caused an internal struggle within the Pentagon. It is very confusing to say the least.
[^4]: Lue does not view himself as a whistleblower but rather as a “patriot”. The fact that he retains his security clearance and continues to work as a government consultant makes people wonder who is really behind this disclosure movement. He has stated that: I would never in a million years violate my security oath. The damage inflicted by people such as Bradley (now Chelsea) Manning and, later, Edward Snowden arguably did more harm than good. Yes, the truth got out, but people lost their lives, and intelligence was compromised in the process (p. 193).
In my opinion, the most important claim made by Lue is the following: Unidentified craft with beyond-next-generation technology—including the ability to move in ways that defy our knowledge of physics and to do so within air, water, and space—have been operating with complete impunity all over the world since at least World War II. These crafts are not made by humans. Humanity is in fact not the only intelligent life in the universe, and not the alpha species… While there are valid reasons for secrecy around some aspects of UAP, I do not think humanity should be kept in the dark about the fundamental fact that we are not the only intelligent life in the universe. The United States government and other major governments have decided its citizens do not have a right to know, but I could not disagree more. You might be thinking this all sounds crazy. I’m not saying it doesn’t sound crazy, I’m saying that it’s real (pp. 1-2).
4. Skeptical Approach
In seeking truth you have to get both sides of a story. -Walter Cronkite.
Before sharing my opinions, assuming that the claims made by Lue and others are true, I need to outline some of the reasons for skepticism about the information being presented (in his book and in general during this disclosure process):
-
Lack of evidence: Lue has not provided concrete evidence, only his personal testimony. The Pentagon denies his claims.
-
Quality of evidence: The evidence that is presented is often of poor quality: blurry pictures and out of context videos that could be anything.
- Lue Elizondo’s Credentials: Right after the release of the book, there was considerable debate on #UFOTwitter regarding his position at AATIP.
- Government secrecy: Many think that it is impossible for a government to keep a big secret like this one from the public for so many years. They argue that the cover-up and secrecy are just conspiracy theories.
- Persistent Claims of Imminent Disclosure: Ufologists keep claiming, for decades, that disclosure is just about to happen any day now.
- Questionable Sources: A lot of the reported encounters come from people who might be unstable, seeking attention, or trying to scam others. Even those who seem genuine might be misinterpreting what they experienced.
5. Non-Skeptical Approach
The eye sees only what the mind is prepared to comprehend. -Henri Bergson.
The goal here is not to focus on the skeptic view. I am well aware that one can just say “Show me the evidence”, and move on if no one points to anything convincing and irrefutable. Also, given the fact that there are many other relevant issues affecting our daily life—like inflation, climate change, geopolitical instability, wars, and surveillance— dedicating mental energy to the UAP issue seems like a waste of time. It is totally reasonable to set this discussion aside due to other priorities.
However, I think it is unfair to dismiss the UAP issue as unscientific, nonsense and full of fraudsters (and there are definitely some of those) without spending a decent amount of time trying to understand what it is really about before criticizing it. Ridiculing a subject you do not know much about and do not understand is not scientific. In my opinion, one of the best critics in this area is Dr. Michael Shermer^5. He is a well-known skeptic with a deep knowledge of various UFO cases, has read a vast amount of information and talked to experiencers and witnesses. I recommend following his work.
In the previous section, I mentioned that some people think it is impossible for a government to keep a big secret[^6] like this for so long. I agree with that perspective and it seems that whistleblowers are starting to come forward. Not just one, but several whistleblowers with military backgrounds have been sharing their stories. It is up for you to decide how trustworthy you think they are. They have appeared in interviews, podcasts and some have even testified before the US Congress. While it is possible that they could all be lying or working together, I am going to assume for now that this is not the case so I can focus on the information they are providing.
[^6]: Some people believe that if there was anything significant to the UAP issue, we would have seen it revealed in Wikileaks by now. Interestingly, the “Podesta emails” include exchanges between Tom DeLonge and John Podesta, both of whom are mentioned in the book because of their interest in the topic.
Sometimes it is important to state the obvious: if something is engaging humanity, we do not need any government to tell us whether it is real or not. As Dr. Avi Loeb^7, Head of the Galileo Project^8, puts it: The sky and oceans are not classified and we can survey them ourselves [3]. People all around the world have been sharing their experiences on this topic for years. Sure, some of these people might be fraudsters, attention seekers, or simply confused, but others might be recounting genuine experiences of events that truly happened to them (even if we do not agree on their nature). That is why the testimonies of whistleblowers who have encountered unusual phenomena during their military service are very significant. Their credibility and training to identify anomalies while staying objective make their accounts worth considering.
There are also people who have had more intriguing encounters with the phenomenon, often referred to as experiencers[^9]. If you’re a good listener, you might have heard some unusual stories from people you know, and you might even know someone who falls into this category. For those who might be unaware, experiencers do exist, and many of them choose to stay quiet. As Dr. Garry Nolan^10, Executive Director of the Sol Foundation^11, points out: I think that what [ridiculing] does is a disservice to people who come forward with stories because they have a double trauma, they have the trauma of seeing something they do not understand and doesn’t fit with their worldview, and then they have the trauma of everyone making fun of them [4]. [^9]: I think this term was originally reserved for abductees, but recently, I have heard it used more broadly to refer to anyone who has had an experience related to the phenomenon. So, I’ll use “experiencers” in this broader context.
6. Spiritual-Metaphysical Component of UAP
It is not the answer that enlightens but the question. -Eugène Ionesco.
Worldview Frameworks
To ensure we are all on the same page, let’s take a moment to discuss Materialism, which is the predominant worldview among scientists and philosophers for explaining the nature of reality.
Materialism holds that the universe is entirely physical and governed by the laws of physics.
Reductive Materialism refers to the notion that all mental states—such as emotions, beliefs, perceptions, desires—can be reduced to physical phenomena, hence, mental states correspond to physical states. Most Materialists identify with Reductive Materialism.
Eliminative Materialism takes a step further by suggesting that mental phenomena do not exist at all.
Mental phenomena is an interesting case of study because it seems to be something different. However, most scientists argue that mental states can be explained through materialistic means, suggesting, there is no need to postulate another substance[^12] or property. Nevertheless, consciousness does not seem to be reconciled in a materialistic way due to its subjective nature and we still lack a clear definition of it. This is one of science's greatest mysteries, sparking extensive debate among philosophers, psychologists, and neurologists. In recent decades, computer scientists have also joined the conversation, due to the advances in Artificial Intelligence. I mention this because, as we explore the unknown characteristics of the phenomenon later, some have proposed that moving beyond a materialistic interpretation might be necessary, especially since the phenomenon seems to interact directly with human consciousness.
[^12]: Cartesian dualism divides the world in two parts: the physical and the mental, leading us to the mind-body problem—how does the interaction occur? We have shifted toward a form of monism, assuming that the world is only made of physical stuff (materialism), thus dismissing the mind-body problem, by claiming that the mind is material (reductionism). However, phenomenal consciousness—the realm of subjective experiences or qualia—seems to escape materialism, drawing us back to reconsider dualism and other flavors of it. This scientific challenge has been famously formulated as the Hard Problem of Consciousness by the philosopher Dr. David Chalmers.
Professor Dr. Mark Harris, physicist and theologian, in his essay Faith and physics states that: Physics is widely said to have a unique ability to shine light on physical reality at its most fundamental level. But in order to do so, physicists must make many assumptions. Indeed, the widespread assumption that physics is the most fundamental of the natural sciences, and that all others relate to it, is a consequence of reductionism, a metaphysical belief which can’t itself be established empirically in any direct way. Moreover, whether theorists or experimentalists, most physicists assume a form of realism –in spite of the fact that quantum physics has led to various anti-realist challenges– and a strong belief in the uniformity of nature, that physical reality is systematic, regular and patterned everywhere, and that these patterns may be understood rationally (the idea that is often expressed as the ‘laws of nature/physics’). This requires reliance on physical models to explain or summarise observations. A model is effectively a scientific metaphor, or an analogy, a way of explaining something we don’t understand in terms of something we do… The next assumption is that the uniform patterns we think we see in nature, which we try to describe using models, are universal. This means that we can eliminate local variables. For instance, in an experiment we discard the vast array of data we observe which are not universally systematic in favour of those (usually much sparser) data that are. Note that this means that we inevitably bring theoretical expectations to the lab: we can’t perform an experiment without having a pre-conceived theoretical framework already in place. This is often summarised by the famous phrase of N. R. Hanson that, ‘All data are theory-laden’. In other words, our observations come with theoretical baggage which already goes some way towards interpreting them [5].
Hence, the scientific lenses through which we understand reality are also grounded in suppositions or metaphysical beliefs because we cannot prove: materialism, realism (reality exists independent of the observer), determinism and reductionism, and that all reality can be understood by rational means. These notions certainly help us effectively interpret, understand and predict the physical world we are familiar with. There is a common belief that if something appears to be outside this worldview, it is either because: 1) We have not yet discovered the scientific explanation for it, or 2) It simply does not exist. I find the first possibility compelling, as we should indeed strive to understand the world around us. However, if we encounter phenomena that truly[^13]defy scientific explanation and challenge our established notions of reality (such as the concept of God), dismissing them as non-existent might reflect a personal bias or attachment to a specific worldview rather than an objective search for truth. I do not think that we should just abandon ourselves to all possible explanations every chance we get, but if after a thorough examination of the issue following the scientific method we remain puzzled, maybe, it is time to consider alternative perspectives.
[^13]: We cannot be sure about this.
Making Sense of UAP
Once you find true knowledge, ignorance is no longer an option. And if the knowledge you find is unusual then strange becomes a way of life. -Thomas Campbell.
The UAP issue challenges our scientific understanding in two significant ways:
1. Behavior of UAP: The behavior of UAP do not align with our current understanding of physics. This discrepancy leads many to speculate that we might be encountering intelligence and technology far more advanced than our own. This idea often implies that these phenomena could originate from a more technologically advanced civilization, potentially from somewhere else in the universe. In this regard, Lue mentions the 6 observables that should be explained (p. 156): * Instantaneous acceleration. * Hypersonic velocity. * Low observability. * Transmedium travel. * Antigravity. * Biological effects. *
2. Interaction with Humans: The way experiencers describe their interactions with UAP could challenge our materialistic worldview. This aspect introduces what I refer to as the spiritual-metaphysical component.
When I used to think about the UAP issue, I never felt the need to consider anything beyond science. I was comfortable sticking to a materialistic interpretation of the world (although I do not subscribe to it as the ultimate explanation of reality), and this was reflected in my approach to the phenomenon—I would just ignore anything metaphysical. I was aware of some of the claims but they seemed too overwhelming to process. I also thought that once we understood ‘the observables’, we would be able to explain the rest. While I have not completely changed my perspective on how to study this topic, I am now open to the idea that we need to explore the spiritual-metaphysical side in parallel.
As I was reading and Lue mentioned Robert Bigelow^14 in the first few pages, I thought to myself “Oh no, please don’t go there…” But sure enough, he did touch on the paranormal aspects later in the book. I was disappointed and felt he might be making a mistake: if he wanted to draw attention to this topic from a broader audience, focusing only on concrete data—such as sensor readings, the capabilities of the crafts, and how they seem to defy our understanding of physics—would be more effective. Introducing the more unusual aspects of the topic might turn off physicists and the scientific community, potentially leading them to dismiss the discussion.
To be fair, Lue does not imply that the phenomenon cannot be explained materialistically and it is spiritual in nature. In fact, he references Arthur C. Clarke’s idea that “any sufficiently advanced technology is indistinguishable from magic”, and he appears frustrated with the attitude of some Christian fundamentalists in government regarding this topic. But I will address this in more detail later.
I believe that Lue is intentional with his choice of words and the information he presents as he retains his security clearance. Early in the book, he mentions: Over time, my colleagues and I gained insight into how these mysterious UAP operate (p. 2). From this, I concluded: * He is signaling to a certain group. The book is not meant for beginners looking for a general overview of the UAP issue. * The spiritual-metaphysical aspect of the phenomenon is so significant that it cannot be ignored. * He may be an experiencer himself (he refers to personal experiences), and by acknowledging them, he is validating others, encouraging them to come forward.
Now that the spiritual-metaphysical part of this issue was brought front and center, I had to confront it as well, even though I had been mentally resisting it.
Remote Viewing and Orbs
Lue dedicates a whole chapter to remote viewing: Recruits were trained to spy upon enemies, but not in the usual way. Stargate trained “supersoldiers” to spy on hard targets using their psychic gifts. No, I am not kidding, this was an official US government program. They called the highly controversial technique “remote viewing.” The program, pioneered at Stanford University in the late 1960s, was led by none other than Hal Puthoff, whom I met at the dinner meeting I described earlier. Hal had been a Stanford University researcher and an employee of the NSA when he and his colleague Russell Targ were approached by the CIA and told that Russia had a remote-viewing program. The US needed to catch up and beat their efforts. That’s how it all started. Extrasensory perception had won over supporters in government who were initially dubious, then shocked that the technique worked. No one understood the mechanism. The CIA didn’t care why it worked; the only thing that mattered was that it did (p. 33). This whole story is really captivating but I was under the impression that it was unnecessary for the reader who is only interested to learn about UAP.
It turns out that Lue connects his involvement in AATIP to some unusual incidents that were occurring to him, his family and colleagues. He explains that they started seeing orbs in their homes: I was shocked to find that a lot of my colleagues and I began experiencing firsthand some of these orbs at our homes...The object behaved as if guided by some intelligence. It parked itself in the air, then drifted off down the hall before disappearing entirely (p. 68).
For those of you who do not know about orbs this is how he describes them: One of the most common types of UAP that are often reported is what we call orbs, which are small, luminous balls of light or, in some cases, smooth and metallic spheres. This is nothing new. In World War II, orbs were reported regularly in and around Allied and Axis aircraft, so much so that they were nicknamed “foo fighters” (p. 67). The orbs have been reported: by commercial pilots or military pilots or by eyewitnesses on the ground, particularly around military test ranges and sensitive US military facilities. This is not just a military phenomenon. Now, with the pervasiveness of home security systems and advancements in cell phone cameras, private civilians are capturing these orbs, just like the military is (p. 67). At this point, I was quite surprised because I remembered being part of a conversation with some colleagues in an academic setting where they expressed how much they would like to study orbs. I had no idea what orbs were, and I had never heard about them before, let alone their potential connection to UAP. Reading that chapter made a lot of things from that old conversation click into place. I wish I could go back and ask more questions about orbs, but they sounded too esoteric for my taste back then, and I was not in the right mindset to show genuine curiosity.
There is another interesting point he makes about orbs: The classification of these orbs really varies quite a bit. There are different colors and sizes; some of the colors reported were white, yellow, blue, red, and green. Reports I have seen suggested the blue orbs in particular had a very negative biological consequence, meaning if you got close to one of these, you could expect to be injured (p. 67). This example highlights that the phenomenon is not entirely harmless.
The way I see it, the connection between remote viewing and orbs in the book (not that these two are necessarily related) is that they might both be some kind of surveillance mechanism and ways to collect intel (this much information we have with remote viewing in a military context). This raises interesting questions about the nature of both remote viewing and orbs, as we venture into the blurry area between physics and metaphysics. I was under the impression that remote viewing was debunked, but Lue says that it works and is still used by the CIA, which does not care why it works but just that it does. What is going on here?
Stickiness of The Phenomenon
At the beginning of Lue’s involvement in UAP related work, he was warned that: “You should be prepared for the possibility that some of that strangeness will impact your personal life. These portfolios are sticky” (p. 12). Later, he linked this initial warning to his experience with orbs. I had heard about the Hitchhiker^15 effect but it took me a while to make the connection.
In a particularly eye-opening section of the conversation about Imminent in the podcast hosted by Post Disclosure World, the guests Christopher Sharp and James Iandoli, clearly highlight the concept of stickiness: If you engage with the phenomenon the phenomenon engages back. They raise an intriguing argument against widespread disclosure or confirmation of UAPs: There is this idea that we should not disclose because if we disclose that’s going to open a door for the phenomena to start engaging us in a much more proactive and unambiguous way. Do we want to all wake up at 3 am and see green orbs in our bedroom like Lue Elizondo and his family experience?[6]. Isn’t this a fascinating question?
There does seem to be a reactive aspect to the phenomenon. Personally, I lean towards the idea of transparency. After all, many of us have wondered whether we are alone in the universe and if human intelligence is the highest form. While the stickiness of the phenomenon might be a consequence of this new knowledge, we would eventually learn how to manage it. However, it is easier said than done. No one wants to live in fear, and this reactive part of the phenomenon appears to exacerbate that emotion. Additionally, in times of collective anxiety, there is always the risk of powers emerging “for our protection”—as Winston Churchill famously said, “Never let a good crisis go to waste.”
On the other hand, how deeply do you need to engage with the topic for it to become sticky? I am not sure. I have not had any experience myself.
I have noticed a common pattern among those who have opened up to me about their experiences: they often express confusion, shame, and fear. Many of them wish to forget what happened to them entirely. None of the experiences shared so far have been described as positive or exciting. But I recognize I cannot draw broad conclusions.
Possibilities for UAP
We sometimes get all the information but we refuse to get the message. -Cullen Hightower.
This classification is where things start to get even stranger. Physicist Dr. Harold Puthoff (mentioned several times by Lue), in his paper titled “Ultraterrestrial Models”, published in the Journal of Cosmology, states: It is currently unknown whether the phenomenon is exclusively extraterrestrial, extradimensional, crypto-terrestrial, demonic/djinn, proto/ancient human, time-travelers, etc., or some combination or mutation of any or all of these. However, it appears highly likely that the phenomenon per se is not constituted exclusively of members of the current human population [7]. At this point, I do not even want to speculate on what we are dealing with. The current information available to the public makes it almost impossible to even guess.
Professor Dr. Kevin Knuth[^16], physicist and member of the Advisory Board of the Sol Foundation, in his podcast appearance with the Scientific Coalition for UAP studies shares his thoughts to the very interesting question: How do you empirically study something where the very definition of just kind of a question mark, we don’t know what it is, it’s a phenomenon, it’s a thing, it's an object in the traditional sense at all? [Answer]: The first thing we need to do is to develop some kind of taxonomy. We need to come up with a way to classify things whether it's based on appearance, behavior and situation… We are faced with the difficulty in that there is a stigma attached to one of the hypotheses of what some of these things might be: the extraterrestrial hypothesis, which to me I don’t actually see very unlikely anymore, I think that’s actually very probable. But once you develop some kind of taxonomy then you can start to tease apart what you’re looking at and what you’re trying to study. These things aren’t clearly not all alien spacecraft: some of them are weather balloons, atmospheric phenomena that we don’t know anything about, pictures of birds…. It’s a very interesting and complicated problem, there is a lot to be discovered here. They are not just one thing… I’ll sometimes joke, I’m only interested in the ones that are craft, you cannot always tell which ones are craft and which ones aren’t, it’s not that simple…. We’re in a position where we really don’t know much at all and it really is smart to keep all the hypotheses on the table: the natural phenomena, the craft phenomena, the extraterrestrial hypothesis, the ultraterrestrial hypothesis, time travelers (from the past and future). There’s a lot of possibilities and there could be several of these hypotheses being true, which can be confounding and it'll be difficult to sort things out [8].
[^16]: https://www.albany.edu/physics/faculty/kevin-knuth https://thesolfoundation.org/people/
I know I mentioned things were getting weird, but now they are about to get even weirder. Lue recounts a conversation that left him stunned: “Lue, you know we already know what these things are, right?” …“It’s demonic,” he said to me. “There is no reason we should be looking into this. We already know what they are and where they come from. They are deceivers. Demons.” I couldn’t believe what I was hearing. This was a senior intelligence official putting his religious beliefs ahead of national security. (p. 84, 85). I guess you are not disappointed by how bizarre things have become with this twist.
I was not entirely surprised by this interpretation. I agree with Lue that a senior officer’s religious beliefs should not be more important than national security. The real question is whether this officer arrived at this conclusion purely based on his religious beliefs, or if there is additional information that is being withheld from the public and from special agents like Lue, who were investigating this topic from within the government.
Spiritual-Metaphysical Beings
Believe those who are seeking truth. Doubt those who find it. -André Gide.
Tucker Carlson shared his views, and it is worth noting his perspective because of his significant influence on public discourse. In this conversation he appears with another important public figure, Joe Rogan. Also, what Carlson says is how I expect many people to react and interpret the nature of the entities associated with the phenomenon.
Carlson says: They are spiritual beings, it’s a binary, they are either team good or team bad… The template that you’re using to understand this is, science fiction or an advanced race of beings from somewhere else but the template that every other society before us has used is the spiritual one. There is a whole world that we can’t see that acts on people, the supernatural world, it’s acting on us all the time for good and bad. Every society has thought this before ours, in fact, every society in all recorded history has thought that until, I'll be specific, August 1945 when we dropped the atom bombs in Hiroshima and Nagasaki, and all of the sudden the West is just officially secular, we’re God, there is no God but and that’s the world we have grown up. But, that’s an anomaly, no one else has ever thought that… Once you discard your very recent assumptions about how the world works, well, that kind of seems like the obvious explanation [9]. I applaud Carlson for openly talking about this, especially bringing up the spiritual beings interpretation. However, amidst the confusion, we should apply caution when listening to people who emphatically tell us with certainty what they are.
On the other hand, Dr. Avi Loeb expresses his stance on this discussion: Shawn asked whether I believe that UAPs have a spiritual component. I explained that spirituality or consciousness are likely an emergent phenomenon of complex systems, like the human brain and advanced AI systems. Their behavior is difficult to predict because they have a large number of degrees of freedom and are influenced by input from uncontrolled environments. Whether there are intelligent UAPs remains to be documented by the Galileo Project. If such UAPs exist, I would add psychologists to our research team, because they are trained to deal with intelligent systems [3].
We can analyze the nature of these beings from different angles: 1. Non-Materialistic Point of View: I have not gone into a deep level of study of the UAP beings —commonly known as aliens—but I have heard people talk about these entities. They seem to be embodied although their appearances vary. When they interact with humans, some people report both physical and psychological effects, such as body marks, paralysis, telepathic communication, missing time, memory loss, and fear. This does not suggest they are intrinsically spiritual beings, such as angels and demons (the fallen ones) from the Bible. These entities seem to have a dual nature. But one could argue that angels and demons are spiritual in essence and they also have the ability to materialize, and this observation would lead us into theological territory. This shows how easy things get messy when trying to relate something unknown with something else that we think we know. 2. Materialistic Point of View: Let’s forget all the spiritual stuff and demons, nothing of that exists, and even if it does, these entities could just be material. In this case I would say pretty much what Lue keeps repeating “any sufficiently advanced technology is indistinguishable from magic”. Maybe these creatures have learned how to access our consciousness in a way that we do not even think it is possible.
In my opinion, we are dealing with a mix of different types of entities although I cannot say anything about their ontology. I would not rule out the spiritual beings, demons, or dual nature entities interpretation. For those who have experienced encounters with these beings, sharing their experiences is crucial so we can gather enough data to better understand and categorize them[^17]. But unfortunately, there is always the fear of ridicule. We need to understand what is and isn’t part of the phenomenon. I would also like to hear what other religions and traditions think.
[^17]: Esoteric groups have already developed some taxonomy, but the information they have gathered falls into the category of revelation (by the beings themselves) rather than an accumulation of data.
Reality is merely an illusion, albeit a very persistent one. -Albert Einstein.
For example, Dr. John E. Mack^18, a renowned psychiatrist from Harvard who tragically passed away in a car accident in 2004, made significant contributions to the field. I first encountered his work through a documentary about the Ariel School UFO landing. Dr. Mack was deeply interested in speaking with the children who witnessed this traumatic event and sought to understand it. His book, Abduction, explores UFO abductions and encounters with these beings. It is important to point out that he was also a well-regarded expert on nightmares.
In an interview, journalist Ralph Blumenthal^19, who wrote a biography about Dr. Mack titled The Believer, noted that Dr. Mack's research highlighted fundamental differences between experiences of the "old hag syndrome" and UFO abductions. The former often involves reports of an evil presence that sits on the bed and causes suffocation, while abductees typically describe being given information telepathically and undergoing medical procedures.
Although these accounts are disturbing, they provide valuable insights by helping us distinguish between similar but distinct experiences. However, the question of the ontology of these beings and their origins still remains unresolved. Blumenthal adds: What are we to draw from this? Well, first of all, there is a whole kind of anomalous experiences that seem to operate in a world that we do not recognize, another reality, that penetrates our world, as John Mack said, somehow, in ways we can’t explain, we have a clear idea of reality, we think we do; reality is what you can see, smell, taste, and touch, knock on the table, feel it... So maybe there are other dimensions, aspects to the universe that we don’t understand” [10]. In addition, Professor Dr. Garry Nolan, whom I mentioned earlier, says the following: It’s interesting, religions have been dealing with extra dimensions and non-human intelligences for centuries: angels and demons, the spirits of the forest, the jinn of the Quran, etc. Where is heaven and hell? It’s another dimension. Are heaven and hell even in the same dimension? Are they different places altogether? Religion struggled with these ideas and the human mind can already encompass the possibility that they exist and had done so since the most primitive of men. That’s amazing to me [4].
This naturally leads us to ask: Are these realities and dimensions “real”? And more importantly, What do we understand by “real”?
About experiencers, Lue expresses that: In the end, abductees report feeling that these beings did not care one way or another if they lived or died. Many experiencers reported feeling completely vulnerable, helpless, and afraid. As a former special agent, if a witness reported being whisked away against their will, I would consider that an act of kidnapping, a federal crime. And if the witness said they were touched against their will, I would consider that assault, yet another crime in human terms (p. 173). I totally agree with Lue on his opinion right here.
I now think it is a mistake to rely solely on physicists, astronomers, and engineers for answers, yet that is where most people tend to focus. The phenomenon we are dealing with is not just about lights in the sky, mysterious crafts, or extraterrestrial beings. The problem is far more complex, and narrowing the scope to only the physical aspects limits our understanding. To fully grasp what is happening, we need insights from a much broader range of perspectives—psychologists, psychiatrists, philosophers, theologians, heads of different religions, anthropologists, and historians. Each of these fields offers a piece of the puzzle, whether it is understanding human consciousness, exploring ancient interpretations of similar phenomena, or delving into the spiritual implications. It is only by bringing together all of these viewpoints that we can begin to form a more complete picture of the UAP phenomenon.
Human Nature
When the student is ready, the teacher will appear. Ancient Buddhist proverb.
I also believe that we need to start looking inwards and understand our true nature—what makes us humans.
- *Materialistic Point of View: We have the poetic words of the physicist Sean Carroll, PhD: I want to argue that, though we are part of a universe that runs according to impersonal underlying laws, we nevertheless matter. This isn’t a scientific question — there isn’t data we can collect by doing experiments that could possibly measure the extent to which a life matters. It is at heart a philosophical problem, one that demands that we discard the way that we’ve been thinking about our lives and their meaning for thousands of years. By the old way of thinking, human life couldn’t possibly be meaningful if we are “just” collections of atoms moving around in accordance with the laws of physics. That’s exactly what we are, but it is not the only way of thinking about what we are. We are collections of atoms, operating independently of any immaterial spirits or influences, and we are thinking and feeling people who bring meaning into existence by the way we live our lives* [11].
- Non-Materialistic Point of View: Professor Mattias Desmet, PhD, expert on the Theory of Mass Formation expresses that: Young science, too, starts from a belief that the object being studied can be fully understood by means of logical reasoning. Facts are logical—how could they not be? However, the further the logical analysis of the phenomenon under investigation is carried, the more clearly one sees the emergence of a core that is intrinsically illogical and inaccessible to the human mind. And just like with a child, that moment gives rise to an awareness of the relativity of all logic as well as a heightened sensitivity to forms of language that don’t aim to be logically understood but lead to a more direct affinity, to resonance with the object (poetry, mysticism, etc.). In the same way, man also has to come to know himself as a psychological being, as a confluence of subjective experiences, thoughts, feelings, especially as they arise in relations with others. The ability to sense one’s own experience and to put it into words and to express it in relation to another is what constitutes the core of our existence as human beings… we exist as human beings when we can give something of our individuality to another through full speech—a kind of speaking in which something of the human being we are vibrates and resonates. It is through the art of full speech—which is the art learned, for example, in psychoanalytic therapy—that we are able to realize a real connection with others and the world around us (without thereby losing ourselves) [12].
If we truly understand who we are and how it feels to relate to each other in our human form, I think that we would be able to recognize what is not us and perhaps discern what kind of entity or intelligence is trying to engage with us. However, if we do not fully grasp our own humanity and the ways in which we are interconnected, how can we even begin to comprehend a non-human intelligence that might be more advanced than we are?
One of the most intriguing insights we have so far about the phenomenon is the possibility that this intelligence is reactive. This is one of the reasons why we need to start talking about our experiences with it. We may be part of a transformational process without even realizing it, and I also believe that this intelligence is being affected by our interaction—it is a two-way street. This is, of course, speculation.
For example, in the Christian worldview, Jesus was a non-human intelligence that transfigured His divinity when He adopted human form, altering His essence through His humanity and interactions with people. He is now both God and human. So, how are we planning to influence this other intelligence?
This process of understanding who we are and our purpose in the universe is entirely subjective, and/or revealed. This is a different kind of knowledge, —more like wisdom—, and, in my opinion, it cannot come from science. How could it? This is why I am now more inclined to consider the phenomenon from perspectives beyond the scientific. The wisdom and knowledge humanity has acquired over thousands of years will be crucial when addressing this subject.
7. UAP Intentions
Lue begins his book by discussing the Colares UAP case in Brazil during the 1970s. If you research about what happened you will see that the phenomenon engaged with humans in a very harmful way. This contradicts the belief held by some in the UFO community that these entities are here to help humanity. This belief is often linked to numerous reports of sightings near nuclear weapon sites and facilities, with the suggestion that they are trying to warn us about the dangers of nuclear technology. Moreover, Lue also talks about a case in 1982 in Ukraine: UAP flew over Byelo Air Base in the former Ukrainian Soviet Socialist Republic. Seconds later, the launch sequence for the base’s missiles switched on without any human ever entering the launch codes. Operators frantically rushed to shut the system down but could not. When the launch sequence reached its very last rung, it shut down of its own accord (p. 54). Moreover, he says that: “Adults taking matches out of the hands of children,” some say. That’s a nice hopeful thought, but reality has proven us incorrect. At no time have UAP stopped our nuclear ambitions. As examples: They did not stop us from dropping atomic bombs on Japan. UAP did not stop us from making the leap from atomic to nuclear weapons. UAP did not stop the disasters at Three Mile Island, Chernobyl, or Fukushima. UAP did not stop the proliferation of nuclear technology from getting into the hands of more nations. Most recently, UAP have not interfered with North Korean, Indian, or Pakistani nuclear testing. And switching on nuclear missiles? That is not so benevolent (pp. 54-55).
Also, Lue on multiple occasions throughout the book expresses his concerns about national security: Humanity acts as if no one else is watching us, like we are alone. But a more advanced intelligent life is likely observing us. Humanity needs to become more aware of our place in the universe and the potential consequences of our actions. Regardless of their motivation, if this tech is cracked by another nation-state with bad intentions it will be an existential threat to our nation and the planet as a whole. Those are the urgent national security concerns and urgent concerns for humanity at large (pp. 168-169).
Regarding national security, I do not believe we have enough information to assign benevolent or malevolent intentions to UAP yet. Additionally, if this is a non-human intelligence, we cannot necessarily think about it in terms of human-like intentions or motivations aimed at accomplishing a specific purpose.
That being said, I appreciate the fact that someone who was in charge of studying UAP from a national security perspective, shares his concerns and makes evaluations based on his background and experience. UAP should be closely monitored. I believe that the US Congress has already briefed on this matter specifically, and they are requesting yearly reports.
8. Psyop Hypothesis
To test a first-rate intelligence is the ability to hold two opposed ideas in the mind at the same time, and still retain the ability to function. F. Scott Fitzgerald.
We are facing a trust crisis.
A frequent argument among UAP skeptics is that the recent surge of interest in this topic could be part of a psyop (psychological operation), with the ultimate goal of instilling fear in the population to justify increased surveillance and control. This is a valid point, I have been thinking about this a lot. While I personally believe that the phenomenon is real and engaging with humans, I could also see a scenario where the phenomenon could be exploited—weaponized, even—with half-truths to serve nefarious purposes.
The pressing question then becomes: How can we discern what is real from manipulation?
After reflecting on the book, now I believe that bringing up the spiritual-metaphysical component of the phenomenon was a clever move. At the beginning I thought it was a total mistake, but I have changed my mind. If the phenomenon is used by a government or an elite group for control and manipulation, they would need a common narrative that influences people’s behavior and convinces them that they know and possess ‘the truth’. This approach might work for the material component of the phenomenon but clearly not for the spiritual-metaphysical side. What could be more diverse than people’s spiritual and metaphysical beliefs (and non-beliefs)?
If we start talking to one another about the strange experiences related to UAP, asking for opinions about their meaning and nature, and even disagreeing on interpretations, then two things could happen: 1) Through the process of open discourse, we are more likely to approach the truth, and 2) It becomes much harder for a powerful group to control the narrative. Even if such a group possesses hard evidence and attempts to use certain elements of truth to steer the public toward a specific outcome, open discussion could counteract that influence.
Regarding evidence, there is always an element of trust involved. Imagine that we are finally shown, by “official channels”, a vehicle displaying non-human capabilities: What would convince you that it is “real” and not fabricated to provoke a reaction? Who would need to validate the evidence for you to believe it? The government? Which government (don’t they all have secret programs)? Independent scientists? Scientists affiliated with institutions or organizations? And what kind of institutions or organizations are truly trustworthy?
I believe that a government or elite group can never have control of what is most intimate to a human: their subjective experiences and the meaning they attach to them which is an individual process. This is why we should not allow a particular faith, tradition, or worldview to dominate or lead the discourse related to the spiritual-metaphysical aspects of the phenomenon. Even if you believe there is no such component, you should still have a voice. This is what we, the people, can control—because we are not the ones trying to reverse-engineer retrieved craft in our backyard, but we may have an intuition about the kind of intelligence we might be dealing with. Therefore, we need to start having these conversations, open to all hypotheses, so when disclosure happens (if it does), whether real or fake, it will not catch us off guard.
9. Conclusions
The opposite of a correct statement is a false statement. The opposite of a profound truth may well be another profound truth. -Niels Bohr.
Lue was a human who found himself in a very strange position. His decision to come forward has been complicated to digest because he is not the usual whistleblower we are used to seeing. Unlike many, he still retains his security clearance and speaks carefully, only about what is not classified. This unique position makes Lue different from typical whistleblowers. Even for those who are not interested in the UAP topic, Lue argues that it is still worth considering how taxpayer money is being used and whether resources are being properly allocated to investigate these sightings and encounters. Whether or not you are personally invested in this subject, the implications for national security and public accountability are real concerns that deserve attention. By coming forward, Lue has opened up a wide range of discussions, not only about the nature of the UAP phenomenon itself but also about the role of transparency in government and the public’s right to know.
Personally I find this topic fascinating. There are many angles to explore and here I chose to focus on the dual nature of the phenomenon, with special attention to the spiritual-metaphysical component. I understand this can also be frightening given all the possibilities we are faced with when considering the phenomenon’s nature. I have faith in humanity, and whatever we find on the other side, I am sure we can handle it. Moreover, during this time of many questions and very few answers, we should learn to embrace the discomfort of not knowing.
Despite the fear of the unknown, there is also the potential for great discoveries. If we are to fully engage with the phenomenon, we have to address not just the external mystery, but also the internal one: it seems like the phenomenon interacts with us on a deeply personal and psychological level, challenging our established ideas about the nature of reality. Understanding ourselves might be a crucial step toward understanding whatever this phenomenon represents because we are the ones extracting meaning. Maybe it is not just about figuring out what the phenomenon is, but why it engages us in the way it does—and that starts with a deeper exploration of our own human experience.
If this topic resonates with you, there are many ways to keep the conversation going: ask others for their thoughts, share your own experiences, and explore the multiple perspectives surrounding the issue. The more we talk openly about UAPs, the harder it will be for any narrative—governmental or otherwise—to control our reactions. This is not just about the phenomenon; it is about our collective right to transparency, understanding, and the courage to face the unknown together as a species.
There are many topics I would have liked to cover, and I know I am only scratching the surface of what has been discussed for years—but at last, I have arrived.
10. References
[1] Elizondo, Luis. Imminent: Inside the Pentagon's Hunt for UFOs: the Former Head of the Program Responsible for Investigating UAPs Reveals Profound Secrets (p. 19). HarperCollins. Kindle Edition.
[2] Pentagon’s UFO investigator breaks two year silence:
[3] For the Love of the Unfamiliar by Avi Loeb: https://avi-loeb.medium.com/for-the-love-of-the-unfamiliar-9d9a7612bd8e
[4] Garry Nolan on UFOs, Neil deGrasse Tyson, and Eric Weinstein:
[5] Pritchard, Duncan; Harris, Mark. Philosophy, Science and Religion for Everyone (pp. 17-18). Taylor and Francis. Kindle Edition.
[6] Elizondo’s Imminent Round Table:
[7] Ultraterrestrial Models by H. E. Puthoff, Ph.D.: https://thejournalofcosmology.com/Puthoff.pdf
[8] Kevin Knuth on Studying Scientific Anomalies, Simulating Star Systems, & Possible UAP Origins:
[9] When Tucker Carlson Changed His Mind on Aliens:
[10]: The Harvard Psychiatrist Obsessed with Alien Abduction:
[11]Existential Therapy from the Universe: Physicist Sean Carroll on How Poetic Naturalism Illuminates Our Human Search for Meaning: https://www.themarginalian.org/2016/05/31/sean-carroll-the-big-picture/
[12] Desmet, Mattias. The Psychology of Totalitarianism (p. 223, pp. 225-226). Chelsea Green Publishing. Kindle Edition.
-
 @ 6bae33c8:607272e8
2024-09-07 22:09:27
@ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League:
Links: BCL1, BCL2, BCL3, Steak League, Primetime
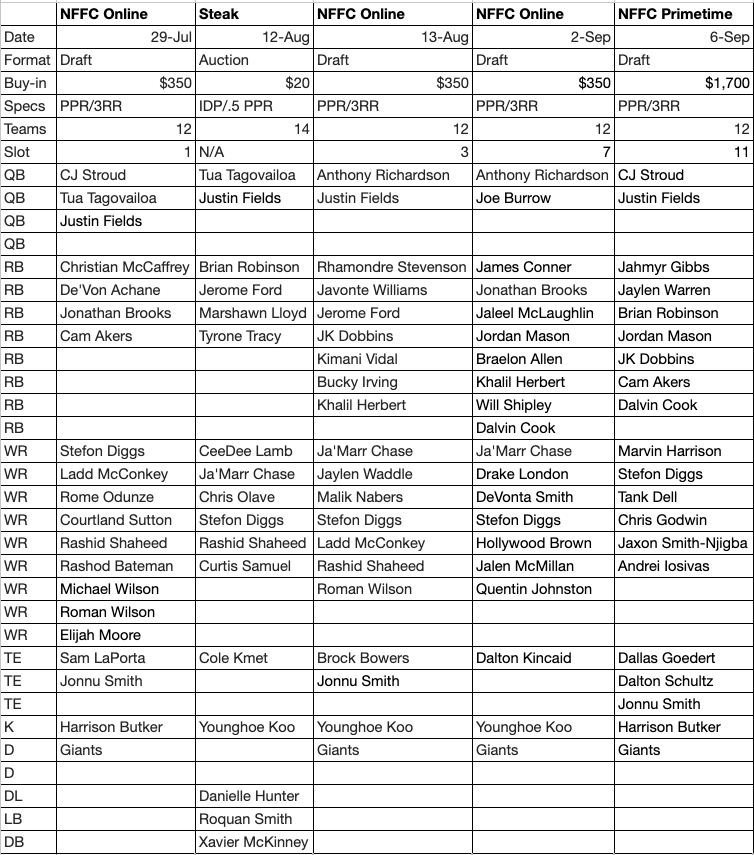
Players in whom I have the most shares:
QB: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2)
RB: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2)
WR: Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2)
TE: Jonnu Smith (3)
K: Younghoe Koo (3), Harrison Butker (2)
D: Giants (4)
Notes:
Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the Primetime — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud.
I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it.
Prominent Players I Don't Have (bold is by choice):
Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, Davante Adams, Saquon Barkley, Chris Olave, Rashee Rice, Kyren Williams, Travis Etienne, Cooper Kupp, Isiah Pacheco, Michael Pittman, Nico Collins, DK Metcalf, Mike Evans, Deebo Samuel, Josh Allen, DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, James Cook, Terry McLaurin, Kenneth Walker, Xavier Worthy, Amari Cooper, Josh Jacobs, Trey McBride, George Pickens, Lamar Jackson, Christian Kirk, Tee Higgins, Calvin Ridley, Rachaad White, Jayden Reed, Diontae Johnson, Travis Kelce, Joe Mixon, Alvin Kamara, Christian Watson, Jalen Hurts, Aaron Jones, Patrick Mahomes, David Montgomery, Zamir White, Keenan Allen, Kyle Pitts, D’Andre Swift, George Kittle
Past Portfolios:
-
 @ 6bae33c8:607272e8
2024-09-07 22:07:54
@ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks.
If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb.
Okay that out of the way, here are the picks:
Dolphins -3.5 vs Jaguars — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers.
Falcons -3.5 vs Steelers — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line.
Giants +1 vs Vikings — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point.
Cardinals +6.5 at Bills — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough.
Browns -2 vs Cowboys — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
-
 @ df478568:2a951e67
2024-09-26 02:11:59
@ df478568:2a951e67
2024-09-26 02:11:59One way to mitigate the risk of a Password breach is to stop using passwords and start using randomly generated passphrases. A passphrase is a combination of words. A good example can be found on the EFF dice words website. For most applications, they suggest using 6 words randomly chosen by rolling 5 dice. Each word has a corresponding combination of 5 numbers from. 1-6. In other words, they are generated by dice(That's D6 dice for all the nerds out there)Here is an example of a strong passphrase that is easy to memorize.
pacifist-area-unfiled-demeaning-rundown-oblivion
It would take a computer about 200 ocrodecillion years to brute force this passphrase so it is highly unlikely to get cracked before the sun goes all supernova.
Here's how it works: - Step 1: roll 5 dice
- Step 2: Find the coresponding word: In this example, our dice rolls are 2-6-1-3-1
- Step 3: Find the coresponding word in the eff dice roll list:
- Repeat this 6 times.
- Step 4: Write this down on paper. I like waterproof paper made by Rite in the Rain. This is not an affiliate link. I don't make any money off of them. I just like them because they are waterproof and easy to hide. You can also etch the password on military grade steel.
- Step 5: Use this password password for your passphrase manager like Vaultwarden.
Each character is really a binary number so your passphrase is just a big random number to the computer. This number is hashed with SHA256 or something. If you're really smart, you can calculate this with a pencil and paper, but I use computers and calculators. Xorbin is one of the easier tools, but this can be done in bash using the hash library too. Be aware, typing an actual passphrase you use into any website might be a phishing scam. Don't try to use this for anything you are worried about losing.
Here is the hash we get from the 6 words above:
a41c5312e2957462f9f81597088c1c943c11e864b462cddf49dc55145707b69a
Sweet, Sweet Salt
. If you don't want to hassle with running your own server, bitwarden does the same thing. Last I checked, they only charged $10.00 a year for the premium plan, but it might have changed. They both allow you to: - Create passwords and passphrases. - Add special characters, numbers and capital letters. - Check if your password was pwned.
For example, "password1" was breached 3,339,722 times. If this is your password, you might want to change it.
"Blink-182" was breached 1,810 times. This password would meet most policies. It has a capital letter, special character and a 3 numbers. Where did we go wrong? Blink 182 is a popular punk band. Of course 1,810 people and one hacker thought of this. Think your safe if you change a number? Think again. "Blink-183" was pwned 16 times. Changing the numbers are also not a good idea due to possible dictionary attacks.
I run my VaultWarden using Start9 and it is also available on Umbrel and Yunohost
Let's try our six word passphrase we created earlier.
"pacifist-area-unfiled-demeaning-rundown-oblivion"
This password was not found in any breaches. It should be safe to use. Well...except I put it on the clear net, but you get the idea.
Other Risks
Okay, we have a strong password, but that's not the only threat. A bad guy could trick us with a spear phishing attack or someone installs a keylogger onto our computer. Now what do we do? Be prepared like a boyscout. This is where it's a good idea to use 2fa or two-factor authentication. I like Aegis There are others like Google Authenticator or physical devices like YubiKeys, but I like Aegis becauseyou can create backups. YubiKeys were cool, but this happened and I'm not sure if that's been resolved yet.
Securing your login with 2fa means one password us an insufficient amount of information to gain access to your account. The attacker would need to pwn the password and your phone to gain access. While not impossible, this is much more difficult.
Here's a Dad joke created by the Duck Duck Go's free AI chatbot.
`Why did the password go to therapy?
Because it was feeling a little "insecure".`
✌️ https://marcleon.work/pgp
862,887
-
 @ 502ab02a:a2860397
2024-09-26 00:11:24
@ 502ab02a:a2860397
2024-09-26 00:11:24
เมื่อกรดซิตริก (citric acid) ที่จริงแล้วไม่ได้ทำมาจากผลไม้
เราเรียนรู้กันมาเราค้นกูเกิลกันมา ว่ากรดซิตริกนั้นเป็นกรดธรรมชาติ มีอยู่ในผลไม้รสเปรี้ยวต่างๆ แล้วมันก็ถูกนำมาใช้เป็นสารป้องกันการบูดเน่าจากธรรมชาติ โดยกรดซีตริกเกิดขึ้นครั้งแรกนั้นคือเมื่อปีค.ศ. 1784 โดยแยกออกมาจากน้ำมะนาว แต่ในปัจจุบัน กรดซิตริกไม่ใช่สูตรนี้ครับ
ที่ผมมีข้อมูลอยู่นั้น สามารถให้คำตอบได้ว่า
นั่นเพราะว่าราวๆปี 1917 บริษัท Pfizer ได้จ้างนักเคมีอาหารชื่อ เจมส์ เคอรี่ James Currie ที่มีแนวคิดฉีกทุกกรอบว่า จะทำการผลิตกรดซิตริก โดยไม่ใช้มะนาวแม้แต่ลูกเดียว คุณเคอรี่ ค้นพบว่าเชื้อราสีดำที่ชื่อว่า Aspergillus niger สามารถเปลี่ยนน้ำตาล ให้เป็นกรดซิตริกได้ ทำให้ Pfizer ออกจำหน่ายสินค้าตัวนี้ในปี 1919 เป็นต้นมา
ในปัจจุบัน กว่า 99% ของกรดซิตริกที่มีขายนั้นเราเรียกว่า manufactured citric acid (MCA) นั่นคือ มันไม่ใช่ของธรรมชาตินั่นเองครับ คุ้นๆไหม ที่ผมเคยบอกเรื่องสารให้ความหวาน ไม่ว่าจะ อิริททริทอล แอลลูโลส สารพัดโอสๆ และอื่นๆอีกมากมาย เราจะได้รับการขายของว่า มีอยู่ในธรรมชาติ บลา บลา บลา โดยที่จริงแล้วที่เราได้มาเป็นกระสอบนั้นไม่ได้มาจากธรรมชาติ แต่มาจากการเร่งให้เกิดปริมาณมากๆเพื่อเอามาขาย ซึ่งไม่เป็นธรรมชาติโดยสิ้นเชิง
MCA นี่ก็เช่นกันครับ เชื้อรา Aspergillus niger ซึ่งส่วนใหญ่ผลิตจากเชื้อราสายพันธุ์ที่ผ่านการดัดแปลงพันธุกรรม (GMO) เอาไปหมักน้ำตาล โดยทั่วไปจะเลี้ยงมันด้วย high fructose corn syrup ที่มีอยู่มากมายและราคาถูกๆ
ก็แน่นอนครับว่าเวลาเราเห็นคำว่ากรดซิตริก เราก็จะนึกถึงรสเปรี้ยวๆ รูปมะนาวสวยๆ cute cute แต่จริงๆแล้วในโรงงานผลิตมันตรงกันข้ามเลยครับ ในการผลิตเราจะได้เห็น ของเหลวหนืดๆเหนียวๆ มีตะกอนสีเข้มๆ ที่เกิดจากการหมักในถังสเตนเลส ข้างในนั้นเป็นส่วนผสมของ เชื้อรา น้ำตาลอุตสาหกรรมโคตรๆ( hyper-refined sugars) บางครั้งก็มีการยิงรังสีแม่เหล็กไฟฟ้าเพื่อให้ความร้อนด้วย
ได้รับการรับรองว่าเป็นออแกนิก ???
และเชื่อหรือไม่ว่า มันได้รับการรับรองว่าเป็นออแกนิก แม้กรดซิตริกจะไม่ได้มาจากแหล่งธรรมชาติแท้จริงเพราะผลิตผ่านกระบวนการหมักที่ใช้เชื้อราดำ GMO (Aspergillus niger GMO) ซึ่งมักใช้ข้าวโพดที่ผ่านการดัดแปลงพันธุกรรม (GMO) เป็นวัตถุดิบในการผลิต ด้วยเหตุผล 2 ข้อคือ
- มาตรฐานการรับรองที่แตกต่างกัน: องค์กรรับรองออร์แกนิกทั่วโลกมีหลายพันองค์กร แต่ละองค์กรมีเกณฑ์ที่แตกต่างกันในเรื่องคุณภาพและความเข้มงวดในการตรวจสอบแหล่งที่มาของวัตถุดิบ โดยบางแห่งอาจใช้แบบสอบถาม ถามผู้ผลิตว่าใช้กรดซิตริกที่มีส่วนผสมของ GMO หรือไม่
- การจัดประเภทว่าเป็น Non-GMO: ผู้ผลิตกรดซิตริกจากเชื้อราดำมักจะระบุว่ากรดซิตริกที่ผลิตได้นั้นเป็น Non-GMO เนื่องจากผลผลิตสุดท้ายไม่มีสารพันธุกรรมจาก GMO ที่สามารถตรวจพบได้ ถึงแม้ว่ากระบวนการผลิตจะเริ่มจากวัตถุดิบที่มาจากข้าวโพด GMO หรือเชื้อราที่ถูกดัดแปลงพันธุกรรมโดยการใช้รังสีความร้อน (thermo-radiation) หรือการดัดแปลง DNA ของเชื้อรานั้นก็ตาม
ถึงกระบวนการผลิตกรดซิตริกนี้จะไม่เป็นธรรมชาติและใช้วัตถุดิบที่เกี่ยวข้องกับ GMO แต่มันสามารถได้รับการรับรองออร์แกนิกได้ เนื่องจากไม่มีการตรวจพบสารพันธุกรรมจาก GMO ในผลิตภัณฑ์สุดท้ายที่จะจำหน่าย ทำให้กรดซิตริกนี้สามารถเข้าสู่ตลาดอาหารออร์แกนิกได้โดยไม่ผิดกฎ และหน่วยงานที่ให้การรับรองใบเซอร์ ออแกนิก เจ้าไหนที่ต้องการให้ใช้ MCA ได้นี่ก็เพียงระบุคำว่า "ไม่สามารถตรวจจับ DNA ที่มีแหล่งกำเนิดจาก GMO ได้" ไว้ในเอกสารก็จะทำให้แบรนด์สินค้าได้รับการรับรอง ออแกนิกได้สบายๆ
ได้รับสถานะ GRAS??
เนื่องจากกรดซิตริกมีการผลิตขึ้นมาใช้ก่อนที่สำนักงานคณะกรรมการอาหารและยา (FDA) จะจัดตั้งขึ้น กรดซิตริกจึงได้รับสถานะ GRAS (หมวด “โดยทั่วไปถือว่าปลอดภัย”) แม้ว่าจะยังไม่มีการทดสอบทางวิทยาศาสตร์ใดๆ เกี่ยวกับการบริโภคในมนุษย์ในระยะยาวก็ตาม เจ๋งเนอะ
ผลข้างเคียงจากรา Aspergillus niger
ในปี ค.ศ. 2016 มีการผลิต MCA จำนวน 2.3 ล้านตัน โดยส่วนใหญ่ผลิตในประเทศจีน และประมาณ 70% ใช้เป็นสารเติมแต่งอาหารหรือเครื่องดื่ม ยังไม่มีการศึกษาวิจัยทางวิทยาศาสตร์ใดๆ ที่ดำเนินการเพื่อประเมินความปลอดภัยของ MCA เมื่อรับประทานเข้าไปในปริมาณมากและเป็นเวลานาน (อีกแล้ว เหมือนเดิมเป๊ะ)
เชื้อรา Aspergillus nigerเกี่ยวข้องกับปัญหาการอักเสบของระบบต่างๆ รวมถึงระบบทางเดินหายใจ ระบบทางเดินอาหาร ระบบประสาท และกล้ามเนื้อและโครงกระดูก ดังนั้นหาก เชื้อรา Aspergillus niger เกิดมีเศษเล็กเศษน้อย ดันแทรกซึมเข้าไปในผลิตภัณฑ์กรดซิตริกสำเร็จรูป ผู้บริโภคผลิตภัณฑ์ที่มีกรดซิตริกนี้อาจกินสารพิษที่ก่อให้เกิดการอักเสบนี้เข้าไป แม้จะผ่านกระบวนการฆ่าเชื้อด้วยความร้อนสูงแล้วก็ตาม
นี่เป็นอีกเหตุผลที่แยม Passion of Orange ที่ผมทำนั้นไม่ใส่ citric acid ครับ
แหม่ยังมีอีกหลายเรื่องนะที่จะเล่าให้ฟังเกี่ยวกับอุตสาหกรรมอาหาร อย่างที่บอกนะครับ อะไรที่มั่นใจในวันนี้ อย่าเพิ่งมั่นใจ อาจจะจริงเราเห็นอยู่ เผื่อใจไว้ที่ยังไม่เห็น
PirateKeto #กูต้องรู้มั๊ย #ฉลาก3รู้ #siamstr
-
 @ a03b38f8:2c7ce1f0
2024-09-25 23:36:29
@ a03b38f8:2c7ce1f0
2024-09-25 23:36:29FINANCIAL PRIVACY: Card Transactions, Cash, Monero, Sending Bitcoin Privately
Privacy is foundational for protecting freedom. Abuses to human rights and efforts to control people often depend on governments knowing details of a person’s life, this is why financial privacy is so important. Financial activity reveals details about a person’s relationships, profession, religion, political beliefs, geo location, and lots more.
Much has been said about data privacy concerns around social media, but financial data is also detrimental when abused or in the hands of the wrong persons.
A Person can speak about their humble life in a small town but their Financial data from the banks would reveal that they are actually a Billionaire.
Financial data reveals many areas of a person’s life, so it’s more likely to reveal who someone truly is, even if an individual does not want those details revealed to others.
From where you travel to, what you donate to, financial activity can paint a detailed picture of a person’s life, ensuring financial privacy means being able to have control over who gets to see that picture and purposes. You may not have something to hide but remember privacy is really about having control over your life.
Governments around the World Use Financial data to control people and activities within its jurisdiction. This is where financial privacy can act as a limit on governmental power. Where a lack of privacy is likely to lead to an abuse of that power.
Government policy on financial privacy is complex and often demands access to personal data for law enforcement and National Security purposes. Although often we see governments use that same financial data to hunt and halt activities that do not align with the policies of its agenda.
We believe any access at all should be reasonable and in accordance with privacy and human rights.
Almost all financial institution privacy standards prohibit the disclosure of client information to third parties without consent or an accepted criminal complaint, it is a conditional agreement because it has some limitations; this limitation or restriction in most cases is not clearly explained to clients but it is an ambiguous statement that further explains the limits of the financial institution, meaning the Central Bank which controls a country’s entire financial activities of all Financial institutions in a country does have the power to access all financial data as it demands, thereby limiting privacy.
CARD TRANSACIONS
Data Security and privacy are crucial in payment transactions in the digital era, protecting personal and financial information not only stops unlawful access but also increases customer trust and confidence.
Card transactions comes with a lot of risk and dangers such as Identity theft, cyber criminals use stolen data from digital payment platforms to impersonate individuals and access their financial accounts, make unauthorized purchases, or setup new accounts in order to illegally transfer funds or perform fraudulent financial transactions without owners consent.
Identity theft can have lasting effects on a victim’s financial health and credit status. Additionally phishing attacks are prevalent. Hackers use this technique to deceive users into providing their personal and payment information (Data) under the guise of legitimate request.
It is advisable for cards that you choose to carry around on your person be held in a RFID blocking wallet. Beyond physical security any cards that you use online or in stores should have spending limits and have no access to large amounts of funds you may have to prevent or limit the impact of fraud. For privacy protections consider virtual privacy cards or reloadable debit cards.
Lastly, do not use PayPal. They are a privacy nightmare and there is an entire cottage industry on the dark web selling stolen accounts.
CASH TRANSACTIONS
Cash is king. For a long time cash has been used as the primary form of payment and cash transactions have excellent privacy properties and it is widely accepted in most countries.
Cash transactions provides a high degree of privacy in payments, it also slows the growing information asymmetry between consumers and companies as well as between citizens and public authorities.
Bank notes and coins reduce your digital footprints compared to an electronic payment. Cash remains one of the most effective tools for financial privacy in a world increasingly dominated by digital payments. It offers true anonymity, leaving no digital trail or record of the transaction, making it impossible for third parties—such as governments, corporations, or hackers—to track your spending habits. Unlike card payments or online transfers, cash transactions don't reveal your identity, location, or spending patterns, providing a level of confidentiality that digital methods simply cannot match.
Physical cash works without registers of cash holders and transaction, when paying with bank notes and coins, it is only the buyer and seller who are aware of this: What is bought, how much, when, when by whom and at what.
While cash has its limitations in today’s digital society, it remains a valuable option for those who prioritize privacy. By using cash whenever possible, especially for sensitive or personal purchases, The use of cash gives room for maintenance and control over your financial data, it also help protect from unwanted surveillance, and safeguard your financial autonomy. Ultimately, cash is still king when it comes to preserving your financial privacy.
MONERO (XMR)
Monero is a decentralized cryptocurrency designed with a strong emphasis on privacy, security, stealth address and unlinkability, it is abbreviated XMR.
Monero’s transactions are completely anonymous and confidential by default making it one of the most privacy centric digital currencies available today.
Key features of Monero
·Untraceable Transactions: Monero uses advanced cryptographic techniques, such as Ring Signatures, which combine your transaction with others, making it impossible to identify the actual sender. This feature ensures that transactions cannot be traced back to any single individual.
·StealthAddresses: When you send Monero, the recipient’s address is never publicly recorded on the blockchain. Instead, a one-time address is generated for each transaction, ensuring the recipient's identity remains private.
·ConfidentialTransactions: Monero employs Ring Confidential Transactions (Ring CT) to hide the amount of XMR being transferred. This means the transaction amounts are kept entirely private, further enhancing confidentiality.
·Fungibility: Because Monero transactions are private, every XMR coin is indistinguishable from another. This makes Monero a truly fungible currency, meaning no coin carries a traceable history or stigma, unlike Bitcoin, where some coins can be "tainted" based on their transaction history.
Despite Monero’s popularity as a primary focused cryptocurrency, Monero faces criticism and challenges. The Monero community development team frequently updates the protocol to improve privacy and resist surveillance attempts, this is beneficial for security, meaning users and miners must regularly update software, this can be inconvenient and lead to potential forks if consensus is not reached within the community.
Many governments and financial institutions view Monero as a threat because of its untraceable nature, as a result this has posed some challenges making exchanges to delisted Monero in order to comply with anti-money laundering and know your customer (KYC) regulations.
SENDING BITCOIN PRIVATELY:
Bitcoin is often perceived as an anonymous payment network but in reality Bitcoin is the most transparent payment network in the world. At the same time, Bitcoin can provide acceptable levels of privacy when used correctly. All bitcoin transactions are public, traceable and permanently stored on the Bitcoin network, Bitcoin addresses are the only information used to define its allocations and history.
In ensuring privacy while Bitcoin transactions are performed it is advisable to generate a new address each time a payment is received. The incomplete privacy on transactions will lead to the Fungibility of the scripts, which could affect the stability of Bitcoin as a long-lived currency system, Bitcoin system addresses privacy by hiding the address of transactions via hash functions but the hash value is obviously unique, If the addresses and traders are bounded unconsciously through activities by attackers, the anonymity of the entire system will disappear.
Suppose that the Bitcoin system is connected to the payment of an e-commerce platform, the strong computing power can search the complete data of your incomes and outcomes, which makes everything about money exposed to the public.
Let’s say; You are paid salary via bitcoins and you spend those coins in the supermarket, the plaintext of the account of your income and outcome will inevitably be utilized by businesses to access the benefits like charge you higher prices or target you with advertisement.
-
 @ 6bae33c8:607272e8
2024-09-07 22:05:26
@ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me.
But I had a plan for that, and I more or less executed it.
Without further ado, here are the results:

1.11 Jahmyr Gibbs — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it.
2.2 Marvin Harrison — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call.
3.2 Stefon Diggs — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about.
4.11 Tank Dell — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance.
5.2 Chris Godwin — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was some chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels.
6.11 Jaxon Smith-Njigba — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack.
7.2 C.J. Stroud — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage.
8.11 Jaylen Warren — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh.
9.2 Brian Robinson — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making.
10.11 Jordan Mason — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down.
11.2 J.K. Dobbins — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy.
12.11 Dallas Goedert — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position.
13.2 Dalton Schultz — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB.
14.11 Andrei Iosivas — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned.
15.2 Cam Akers — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it.
16.11 Justin Fields — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back.
17.2 Harrison Butker — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1.
18.11 Dalvin Cook — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle.
19.2 Jonnu Smith — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target?
20.11 Giants Defense — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers.
Roster By Position
QB CJ Stroud
RB Jahmyr Gibbs/Jaylen Warren
WR Marvin Harrison/Stefon Diggs/Tank Dell
TE Dallas Goedert
FLEX Chris Godwin
K Harrison Butker
D Giants
B Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
-
 @ 6bae33c8:607272e8
2024-09-07 22:00:17
@ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the Steak League which was nice as like Roquan Smith he too started the year with a pick.
But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him ranked highly initially) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my Primetime last night!
I had even argued with Alan Seslowsky that Reed was the obvious choice among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean.
I don’t know how many times I need to learn this lesson, but apparently at least one more!
-
Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice.
-
Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me.
-
Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. (Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary! Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)
-
Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats.
-
Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season.
-
Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven.
-
AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets.
-
Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
-
-
 @ ae1008d2:a166d760
2024-09-25 21:52:49
@ ae1008d2:a166d760
2024-09-25 21:52:49I wanted to share this PDF on Nostr. Original post: Block ~862,844 September 25th, 2024 Original link Original PDF 👇Click the link below to view as original PDF on YakiHonne or Satellite.Earth👇