-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 5e5fc143:393d5a2c
2024-10-11 22:26:08
@ 5e5fc143:393d5a2c
2024-10-11 22:26:08Just revisiting some quick tips for #newbies #pow #public #blockchain users only.
if you just getting started with bitcoin or any pow crypto coins or been using or storing them for a while, you not must forget the roots and fundamentals.
Hot Wallet — It gets connected to live internet at some point in time essentially to sign / send a tx i.e. spending transaction — exposes the private key of the address from in the process
Cold Wallet — It never ever gets connected or online and can always keep receiving inbound amounts Paper wallets are best n cheapest form of cold wallet that can used once n thrown away.
Cold wallets need to either “import”ed or “sweep”ed in order to used or spend — https://coinsutra.com/private-key-import-vs-sweep-difference/

Any thin #wallet is always dependent on connectivity to live up2date node server where-as self-sufficient qt / cli wallet takes a while to sync up to latest block height in order to be usable.
Beginners should always resist the attraction of quick and fast — thin n 3rd party wallets and always start a long learning journey of core wallets of any coin — either “qt” GUI wallet or command line “coin-cli” wallet
Almost all #proofofwork #blockchains i.e. #POW has #node #wallet - everyone who use support he #public #blockchain secures own you coin value
You can run fullnode either on clearnet or over onion 🧅 #BTC has >55% of nodes running in onion out of total 15000+ live fullnodes and 50000+ bitcoincore wallets around blockheight 777000 . Other notable pow chains are #LTC #RVN and rest are babychains for now !
Always delete hot wallet to test practice restoration before sending any large refunds to it to be safe.
Large funds are always best to keep in self custody node wallets rare n occasional use
Final word — Cannot see private key 🔑 or seed 🌱 in any wallet means not your coin. 😲
Use wallet which u learn or understand best only
That’s all for now n Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️
Some Cold wallet nostr posts nostr:note1p6ke5wqshgxtfzj5de3u04hejl2c5ygj8xk8ex6fqdsg29jmt33qnx57y2 nostr:note1rse0l220quur6vfx0htje94ezecjj03y6j7lguwl09fmvmpt6g3q0cg7yw nostr:note1q5w8dyjuqc7sz7ygl97y0ztv6sal2hm4yrf5nmur2tkz9lq2wx9qcjw90q
some nostr specific lightning ⚡️ Layer2 wallets with blockchain mainnet option nostr:naddr1qqsky6t5vdhkjm3qd35kw6r5de5kueeqf38zqampd3kx2apqdehhxarjqyv8wue69uhkummnw3e8qun00puju6t08genxven9uqkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgefsw4a8xdnkdgerjatddfshsmr3w93hgwpjdgu8zdnswpuk2enj0pcnqdnydpersepkwpm8wenpw3nkkut2d44xwams8a38ymmpv33kzum58468yat9qyt8wumn8ghj7un9d3shjtngv9kkuet59e5k7tczyqvq5m2zcltylrpetrvazrw45sgha24va288lxq8s8562vfkeatfxqcyqqq823ckqlhc8 related blog post nostr:naddr1qqxnzd3cxyenjv3c8qmr2v34qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7mn0wd68ytn4wdjkcetnwdeks6t59e3k7tczyp6x5fz66g2wd9ffu4zwlzjzwek9t7mqk7w0qzksvsys2qm63k9ngqcyqqq823cpdfq87
-
 @ a012dc82:6458a70d
2024-10-17 01:30:04
@ a012dc82:6458a70d
2024-10-17 01:30:04Table Of Content
-
Whales and Sharks: The Big Players in the Crypto Ocean
-
June's Close: A Bullish Signal
-
Data-Driven Predictions: The Role of Crypto Intelligence
-
Whale Holdings: Keeping the Selling Pressure at Bay
-
Historical Trends: July as a Profitable Month
-
Conclusion
-
FAQ
The cryptocurrency market is a dynamic and rapidly evolving space, with Bitcoin (BTC) at its forefront. One of the key factors influencing the market's trajectory is the activity of large-scale investors, often referred to as 'whales' and 'sharks.' These entities hold substantial volumes of digital assets, and their investment decisions can significantly sway market trends. Recently, these influential players have been doubling down on their Bitcoin investments, particularly as June 2023 drew to a close with BTC valued at an impressive $30,469. This article aims to explore this trend in detail, examining the potential implications for Bitcoin's future and the broader cryptocurrency market.
Whales and Sharks: The Big Players in the Crypto Ocean
In the vast and diverse ocean of cryptocurrencies, whales and sharks are the entities that hold large volumes of digital assets. Their actions, whether buying or selling, often have a substantial impact on the market, influencing price trends and investor sentiment. Over the past seven weeks, these large wallet investors have shown a strong appetite for Bitcoin, accumulating an impressive 154,500 BTC. The pace of this accumulation has notably picked up in the last two weeks. These investors have been capitalizing on market dips to increase their holdings, a strategy often referred to as 'buying the dip.' This trend suggests a strong confidence in Bitcoin's potential and could have significant implications for its future price trajectory.
June's Close: A Bullish Signal
June 2023 proved to be a significant month for Bitcoin, with the cryptocurrency closing at $30,469. This figure represents the highest monthly close for Bitcoin in the past thirteen months, a noteworthy milestone given the asset's volatility. This bullish signal has sparked optimism among investors and analysts alike, fueling a thesis for a potential recovery and upward trend for Bitcoin in the coming months. If this prediction holds true, it could mark a turning point for Bitcoin, potentially leading to increased investor interest and further price appreciation.
Data-Driven Predictions: The Role of Crypto Intelligence
In the complex and often opaque world of cryptocurrencies, crypto intelligence platforms like Santiment play a crucial role. These platforms track and analyze market trends, providing valuable insights into the behavior of large-scale investors and the overall market dynamics. According to Santiment's data, Bitcoin's whale and shark addresses accumulated a staggering 154,500 BTC within a seven-week period between April 2023 and the time of writing. The acceleration of Bitcoin accumulation in the past two weeks suggests a strong confidence in the asset's potential for recovery. This data-driven insight provides a valuable perspective on the market sentiment and could be a key indicator of Bitcoin's future performance.
Whale Holdings: Keeping the Selling Pressure at Bay
One of the intriguing aspects of the Bitcoin market is the concentration of holdings among whales. Bitcoin whale wallets, those holding between 10 and 10,000 tokens, now control 67% of the total supply of the asset. This concentration of holdings can be seen as a positive sign for Bitcoin. By holding onto a significant portion of the supply, whales reduce the selling pressure on the asset. This can create a more stable environment for price growth, as it reduces the likelihood of sudden price drops due to large-scale sell-offs. This dynamic could increase the potential for a recovery in Bitcoin's price and contribute to its long-term stability.
Historical Trends: July as a Profitable Month
Historical trends can often provide valuable insights into potential future market trends. For Bitcoin, the month of July has consistently proven to be profitable for holders over the last three years. This trend, coupled with the recent surge in whale accumulation, suggests that Bitcoin's price may recover from recent market fluctuations. These include the impact of the SEC's crackdown on crypto exchanges and increased regulatory scrutiny. If this trend continues, July could once again prove to be a profitable month for Bitcoin investors, potentially marking the start of a new upward trend.
Conclusion
The recent actions of Bitcoin whales and sharks, coupled with historical trends and market data, paint a promising picture for Bitcoin's future. The significant accumulation of BTC, the highest monthly close in over a year, and the potential for a profitable July all point towards a positive outlook for the asset. However, as with all investments, these trends should not be taken as definitive predictions. Market dynamics are subject to change, and investors should always conduct thorough research and consider various factors before making investment decisions. The world of cryptocurrencies is as exciting as it is unpredictable, and the actions of Bitcoin whales and sharks will continue to be a critical aspect to watch in the unfolding narrative of this digital asset.
FAQ
Who are Bitcoin whales and sharks? Bitcoin whales and sharks are large-scale investors who hold substantial volumes of Bitcoin. Their investment activities can significantly influence market trends.
What has been the recent trend among Bitcoin whales and sharks? Over the past seven weeks, Bitcoin whales and sharks have doubled down on their investments, accumulating 154,500 BTC, especially as June ended with BTC valued at $30,469.
What does June's closing value signify for Bitcoin? June 2023 closed with Bitcoin valued at $30,469, the highest monthly close in the past thirteen months. This has sparked optimism for a potential recovery and upward trend for Bitcoin.
What percentage of Bitcoin's total supply do whale wallets control? Bitcoin whale wallets, those holding between 10 and 10,000 tokens, now control 67% of the total supply of the asset.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ bcea2b98:7ccef3c9
2024-10-16 21:33:15
@ bcea2b98:7ccef3c9
2024-10-16 21:33:15When people talk about financial freedom, they often focus on investing, saving, or building wealth. But sometimes, the most valuable skills or habits are the ones that aren’t talked about enough. Maybe it’s discipline, emotional resilience, or even something unexpected like negotiation or patience.
What do you think is the most underrated skill or habit for achieving real financial independence?
For me, the most underrated skill is delayed gratification. It’s not just about resisting the urge to spend money now, it’s about thinking long-term in everything you do. When I first started learning about Bitcoin and freedom, I realized that the biggest hurdle wasn’t just making money, but knowing when to hold off on spending it for the right opportunities.
originally posted at https://stacker.news/items/727313
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 6bae33c8:607272e8
2024-10-16 12:24:50
@ 6bae33c8:607272e8
2024-10-16 12:24:50I went 4-1 last week, but it’s just the beginning of digging out of a deep hole, so I’m not gonna get excited about it just yet.
Broncos at Saints — I’d say Broncos -2. Feels like a Saints bet at home with the short week, but I won’t use it.
Patriots vs Jaguars (London) — Think I saw this line was 5.5 or something. That seems big, but Jaguars are probably a hold-your-nose-and-buy-low.
Seahawks at Falcons — Think I saw this was 2.5. I kind of like the Falcons but the Seahawks are the buy-low.
Titans at Bills — Amari Cooper is just what the Bills needed. I don’t see the point in the Titans. I’ll say 10 and if anything would lay the wood.
Bengals at Browns — Maybe Bengals -3.5, and you’d take the Browns as a buy-low in division, but I can’t.
Texans at Packers — Texans +2.5 and probably take the Packers at home. The Texans offense is too slow.
Dolphins at Colts — Dolphins +4, probably take the Colts, though it’s unclear who the QB will be.
Lions at Vikings — Make it Lions +2, but the loss of Aidan Hutchinson really hurts. I’d probably take the Lions still.
Eagles at Giants — I’ll say Eagles -3 with Andrew Thomas out. And who knows about Malik Nabers with the lingering concussion? The Giants are playing better though. Pass.
Raiders at Rams — I’ll say Raiders plus 3.5. Probably take the Raiders if pressed, but pass.
Panthers at Indigenous Peoples — Maybe 8.5, would probably take the Panthers.
Chiefs at 49ers — Think I saw the 49ers were slight favorites. I’ll make it Chiefs +2, take the 49ers.
Jets at Steelers — I’d make it a pick’em and probably take the Jets. Not because of Davante Adams, but Russell Wilson if he starts.
Ravens at Buccaneers — Let’s say Ravens -3. I’d probably lay the wood in that case too.
Chargers at Cardinals — What’s wrong with Kyler Murray? I’ll say Chargers minus 2.5 and maybe hold my nose with the Cardinals.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ e6817453:b0ac3c39
2024-10-06 11:21:27
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-
 @ ec9bd746:df11a9d0
2024-10-04 09:46:22
@ ec9bd746:df11a9d0
2024-10-04 09:46:22It's intriguing to me how beer prices have changed since 1999. Today, you can buy Braník on sale for 9.90 Kč, so for 100 Kč you get 10 beers. 25 years ago, you'd get 13.5 beers for the same amount. What does that tell us?
-
The cost of labor and services has gone up a lot, but people are willing to pay and even expect a certain level of quality. There are way fewer run-down pubs than before.
-
Production has become much more efficient, so considering inflation and purchasing power, bottled beer is actually cheaper now than it used to be.
In 1995, about 30 years ago, bottled and draft beer cost almost the same—around 7 Kč. (Source in Czech)
So what's the takeaway?
-
A wealthy society can afford much pricier services.
-
Prices of basic groceries and fast-moving goods are squeezed to the bone. The best way to gauge real inflation is at the supermarket, where there's no room for messing with margins, stock levels, seasonality, etc. Everything moves fast, competition is huge, and big retailers are relentless.
Real estate is pricey due to artificial (or bureaucracy-induced) shortages, but meat, milk, beer, bread, etc., are operating on razor-thin profits. That's why they react so quickly—see point 2.
-
-
 @ 17538dc2:71ed77c4
2024-10-02 16:58:42
@ 17538dc2:71ed77c4
2024-10-02 16:58:42a practical intro to contributing to FOSS for product people, and other non-devs
So you want to contribute to FOSS, but don’t know where to start. There are many paths to FOSS, but you must find your own. Here’s some advice based on personal experience to help you get started.
0. Find your motivation
FOSS requires a lot of giving, and better aligns with those that are missionaries, as opposed to the mercenaries. Perhaps you are unfulfilled in your fiat job, maybe you are currently unemployed, or perhaps you are excited about a particular bitcoin project. Why you’re exploring contributing to FOSS, is a question that only you can answer.
 Are you a missionary?
Are you a missionary?1. Discover what excites you
So you’ve found motivation and have a list of various FOSS projects you could contribute to. This is the equivalent of the “I need a job” stage and you’re figuring out where to apply. It’s time to narrow it down.
What are you excited about? A multi-year pilgrimage of learning how to contribute to Bitcoin Core? A lightning wallet, perhaps? Free speech Nostr? A hardware signing device? Or maybe finding a FOSS projects that is not “Bitcoin” in name, but happens to support Bitcoin, and Lightning.
A great first step is to take some time and explore the Bitcoin Design Community (https://bitcoin.design/) to discover FOSS projects.
 Are you excited anon?
Are you excited anon?2. Identify the skills you have or want to develop
Chances are that if you follow the Bitcoin Product Community, you’re skills are in Product Management, Product Marketing, and/or Project Management. But contributing to a bitcoin project requires contributors with skills of many backgrounds such as marketing, documentation, community building, and more.
What’s important to know is that most FOSS teams start with a motivated developer, who then may attract other devs. But many of them may not advertise that they need non-developer help such as a PM.
Therein lies the opportunity for you as an eager bitcoin contributor. See what the needs of a project are and see if you can fill in those gaps with your skills. It may be as simple as coordinating meetings for the team. But doing the “dirty work”, or the work no one else wants to do, is exactly the way you can make an immediate impact to a FOSS project. In fact, this is why members of the Bitcoin Product Community affectionately refer to product managers as “janitors”!
3. Make a list of projects
Now that you have narrowed down your FOSS search, it is time to start building a list of, and evaluating various FOSS products. Some questions you can ask yourself:
Is the project active? Is it a new project? How many team members are there? How many are devs? Is there already a PM? Is there a need for multiple PMs? Is there designer participation? What is the pace of development? Is there enough development activity for this to satisfy your want to contribute? Is there opportunity for a PM?
Github is the defacto standard for FOSS products. Check the activity. Read up on issues. See who is contributing PRs, and creating issues. Check if there is a Github Project instance.
It’s OK, and best for you to check out out multiple FOSS projects concurrently to see which team is the best fit for both parties.
4. Use the thing(s)!
Another thing you can do to help you choose a project is to use the thing! Download the OS. Run the software. Use it.
As you’re interacting with the product, some things you can ask yourself are:
What do you love about the product? What can be improved? Are there bugs?
Jot down your notes. Take screenshots. Do screen recordings. Document your experience. Create a video onboarding walkthrough, or a feature tutorial. What you are actually doing is documentation and this will be useful for the project, even if you don’t decide to actively contribute.
As you use the thing, take note of how you’re reacting to it. Are you getting more or less excited? Are you more or less confident in contributing to the project?
5. Find out where the team works
Another factor to consider is to figure out where the team works.
By now you have already explored their github to collect your FOSS intelligence. Now check nostr, twitter, telegram, or whatever other comms tools the team might be using. Some teams may have calls, and call recordings. Consider listening in to a recording, and/or joining a call to check the team dynamics.
As you do, assess whether you might be a good culture fit. Also see where there might be some gaps in their workflow that you can help improve.
6. Start small
Once you found a project that interests and excites you enough. It’s time to roll up your sleeves and get involved by starting small.
One easy place to start is to go through the github issues list. Some examples of issues in dev heavy teams are e extremely technical bug reports. For FOSS products with an active user base, there might be “customer” centric feature requests.
Start by logging the bug(s) you found. Examine issues, and fill in the blanks if there are unclearly defined reports & requests.
You don’t have to ask for permission to contribute. That said, evaluate team dynamics and who owns what role so you are not stepping on anyone’s toes. You are there to help.
Also take note of how your help is received. It may take time for you to build up your credibility. Don’t throw in the towel on the first week. Keep finding ways to add value.
7. Show up consistently
Keep contributing in small things day in and day out. As you do so, communicate with the team to ramp up your learning, and also start building rapport, and your reputation. You may not have time or opportunity to contribute full-time. With the state of asynchronous communication tools in 2023, you can flexibly contribute when you have time. An exception to the asynchronous communication may be team meetings.
As you continue to show up consistently, you will build up your FOSS proof-of-work, and reputation. This will show FOSS devs, and contributors that you bring value.
8. Find and meet the “customer”
Find, and interact with the project’s users a.k.a “customers”. What do they care about? What are their pain points? What needs are customers using the product for? Become the “voice of the customer” to the dev heavy team.
Is there a conference where your team is presenting, and customers present? These are invaluable opportunities to observe the customer’s behavior, and also to help answer questions, and troubleshoot on the spot.
9. Increase your involvement
After some time starting small and working on bugs, you may eventually find yourself submitting feature requests. Maybe there is an opportunity to create user flows, or mockups. As you consistently contribute, continue seeking more responsibility.
Maybe you offer to facilitate and lead the next team call. Maybe you try creating a roadmap and backlog from scratch. Maybe you host a product & design thinking session. Maybe you will level up and learn how to check out a dev’s PR in a yet-to-released branch.
No matter what you do, be sure to always bring value to the project.
 Testing an unreleased Damus branch checked out on XCode
Testing an unreleased Damus branch checked out on XCode10. Prune, Commit, Repeat
Congratulations! By now you’ve been doing a “trial run” with several projects. It’s time to focus and choose one(s) that you can commit to.
As you contribute to the project on an ongoing basis, continuously reevaluate if there is opportunity for you to increase your contributions. If you feel that you’ve maxed that out, it may be time to look for a different FOSS product to contribute to. Perhaps a complementary product to your initial one.
As you embark on this journey, it can be exhilarating at times and in other times thankless. To find a community of peers, and perhaps a mentor check in with the Bitcoin Product Community Discord, and introduce yourself. The beauty of open source is people are willing to help FOSS products, and to answer your questions.
https://youtu.be/ZUgQPR6ecuo “FOSS is the way” - Rockstar dev, @ Advancing Bitcoin Conference London 2023. The author thanks Rockstar for inspiration, and guidance through my FOSS journey.
As you continue to sweep the FOSS floors with your product mop, remember that you are contributing to the mission that you believe in. You are working in the open, with even less authority than a PM at a company might have, and as a result leveling up. You build up your reputation in FOSS, and you show others your capabilities in the FOSS world (and also prospective employers, and co-founders) by doing.
Hopefully this helps you get started. Reach out to elsat on nostr if you have questions about the FOSS journey, and join the Bitcoin Product Community Discord.
-
 @ f1597634:c6d40bf4
2024-10-02 09:00:59
@ f1597634:c6d40bf4
2024-10-02 09:00:59E aí, galera do Nostr! Já pensou em como proteger sua privacidade nesse mundo descentralizado? A gente sabe que a liberdade é daora, mas é importante saber como se proteger dos "bisbilhoteiros" que estão sempre à espreita.
O perigo das fotos:
- Sabia que as fotos que você posta podem dar muitas informações sobre você? É tipo deixar um mapa do tesouro nas mãos de alguém!
- Pessoal mau intencionadas podem usar essas fotos para descobrir onde você mora, qual seu IP e até mesmo sua identidade!
Dicas para se proteger:
- Escolha seus apps com cuidado: Nem todos os apps são iguais. Procure aqueles que a galera mais confia e que têm uma boa fama.
- Ajuste as configurações: A maioria dos apps tem configurações de privacidade. Mexa nelas para mostrar só o que você quiser para os outros.
- Cuidado com links: Não clique em qualquer link que você receber. Pode ser uma armadilha!
Uma boa prática ao navegar pelo Nostr é configurar um Proxy confiável no seu aplicativo. No Nostrudel por exemplo é possível configurar um proxy de imagem através das configurações.

Segundo análise, as redes a seguir ja disponibilizam esses proxies por padrão:
- Amethyst
- Damus
\ O que é esse tal de proxy?
- Imagina que você está usando uma máscara. O proxy é tipo essa máscara, só que para o seu IP. Assim, ninguém vai saber quem você é de verdade.
- É como se você estivesse usando um disfarce para navegar pela internet!
Outras dicas:
- Remover Exif: Todas as fotos que tiramos possuem metadados, normalmente redes sociais e outras empresas removem esses dados quando recebem a imagem no servidor (eventualmente pegam os dados).
Programas como ExifCleaner removem essas informações antes do upload.
Conclusão:
A internet é um lugar incrível, mas também pode ser perigoso. Seguindo essas dicas, você vai poder curtir o Nostr com mais tranquilidade e sem se preocupar com os "bisbilhoteiros".
Lembre-se: A segurança é coisa séria! Compartilhe esse guia com seus amigos e ajude a criar uma comunidade mais segura.
E aí, curtiu?
fonte: https://victorhugo.info/artigos/nostr-como-se-proteger-1
-
 @ 59df1288:92e1744f
2024-10-16 08:00:21
@ 59df1288:92e1744f
2024-10-16 08:00:21Hey Rabble, brace yourself for a whirlwind tour of Nostr's latest gabfest! From the quiet musings of our "Public Square" turning into a cozy campfire chat, to the hilariously oddball "#toiletchain" saga, the platform's been nothing if not entertaining. Meanwhile, passionate debates over Musk's Twitter antics and the timeless charm of a 3-minute scroll session keep everyone on their toes. It's a riotous mix of tech talk, light-hearted banter, and nostalgic tunes, sprinkled with a dash of rust in Minecraft—tonight's episode is not to be missed! Dive in, and remember: in Nostr-land, chaos is where the fun begins.
Quiet Nostr Vibes 📉
Hey, so our buddy 7fqx kicked off a super chill thread wondering why Nostr's been so hush-hush lately. Everyone seems to agree it's quieter than usual, with Sedd chiming in with a simple, "It is."
nielliesmons joked about turning the Nostr feed into a cozy community chat, while npub1f9kn3a5cv4fsq2x86gfrznfuumtqtu6j3fkyqg9qvlymt0zflvfsn3v9fa insisted it’s not as quiet as it seems. The whole convo turned into a laugh about "reply guys" and how it feels like a dev chat sometimes. captain ☦️ threw in a rebellious "delete Twitter!" moment, but 7fqx was like, "Nah, Twitter still has its gems."
Catch up with the banter and check out the full convo here.
Twitter vs Nostr Showdown 🥊
7fqx echoed some thoughts about how even their sneaky Twitter lurking is feeling the quiet blues. captain ☦️, ever the rebel, says to "delete Twitter!" 🤭 But 7fqx is keeping it chill, mentioning they follow around 200 peeps so they still find plenty of action, even in a quick "15 min" or let's be real, more like "3 min" scroll session. 😂
Catch this mellow chat right here.
Musk, Nitter and the Great RSS Debate
So, captain ☦️ kicked things off wondering if Nitter could still be a thing. But 7fqx quickly snuffed that out, saying Nitter's not working anymore. 😢 The chat turned into chatter about making RSS feeds from Twitter accounts, with captain ☦️ throwing some shade at Mr. Musk, quipping, "Musk won't let us have nice things." 😂
Check out the full convo here.
The Fiatjaf Chronicles: Old Alliances and New Concerns
melvincarvalho is spilling the tea about their long history with Fiatjaf, praising some of his past brilliance but worried about his new vibes around censorship and centralization—ya know, the stuff that makes the OGs a bit uneasy.
npub1u8r69esh5r7jt29nj9ufmz4yvuwp6cwl5xqp4e3d46vl8wla5smsexjcky chimed in with some serious talk about dealing with nasty stuff like CP on the network or risk the place getting shut down. Meanwhile, npub192klhzk86sav5mgkfmveyjq50ygqfqnfvq0lvr2yv0zdtvatlhxskg43u7 is side-eyeing the decision to air this publicly rather than DMing like, "Isn't this a private convo kinda deal?"
npub1c80wmfpzc7dkghh93kxtrwpe5gdztynvnk2vy93ge68zmzwrm0yqq5h5s7 was like, "Hey, just saying the obvious—keeping everything forever is a disaster waiting to happen," while npub1snw24avwcuz9w672t3wt5jhj82xfd0ynz0ylum90sez9tg4k0u9s4jwee3 is all, "Why ditch privacy, bro?"
Check out the full convo here.
Nostr Drama and Hot Takes 🎭
The convo heated up with npub1m2u4v2jtz4np0y3lk2anr4vm4vr4l7jlr7y94qglhfrgewsczchqg6y2gl bringing some real talk about how it feels like everything's being pushed artificially. They emphasized the fear tactics being used, highlighting their clear stance in the mix!
Quick Flick Opinions 🎬
zach is on a movie binge with "There Will Be Blood", and everyone's chiming in! sophiaw1926 can't get enough of Daniel Day-Lewis, while Mister G 😎♻️ 🚛 🍏 🗽 🥾 🌆 ⚡ had a laugh about the relentless quest for oil. Classic flick talk with a sprinkle of humor!
Check out the full convo here
Print's Swan Song 📰
roya ୨୧ brought up a heartfelt topic about the end of an era with print media. Some mournful vibes with npub1mhe7uv6m6faes325wsmwygp2mtw6gdylqxp8gak4zgy374qx6hxsxwwzcz mentioning the last pony express rider's retirement! A true throwback moment.
Check out the full convo here
Scrolling Adventures 📱
7fqx is all about condensing Twitter into a 3-minute browse! captain ☦️ threw a shade towards Musk for not letting us enjoy the simple things like Nitter, sparking a mix of innovation and nostalgia.
Check out the full convo here
🎵 Nostalgic Tunes and Lost Soundscapes 🎶
So, walker is feeling all sorts of emotional about #tunestr and shared a throwback video that got the convo buzzing! 🎶 npub1gk76j57d8w3x8dudj4wllvdke6u7kcqd20j6cwuawkqa90q72x8qqw5nqq reminisced about discovering these jams through Stubz the Zombie, which, let's be honest, might be the coolest way to find new music. Meanwhile, npub1qs5ft8k8lznjkl7yym36707fsxjv3dnxnfpm4j64xrdwkn8tw0sqcfp27v chimed in with some deep thoughts on how everything's gone downhill since "Subversion and Degeneration". On a lighter note, ltngstore just gave a ✨ shoutout to The Chordettes. Classic! Check out the full convo here.
🛠️ Rust-y Pixels in Minecraft Land 🧩
iefan 🕊️ hit us with some mind-blowing updates about a Minecraft server built in Rust, boasting crazy CPU and RAM performance! 🤯 localhost couldn’t contain their excitement and suggested we "rebuild it all in Rust", adding a bunch of laugh emojis for good measure. 😂 iefan 🕊️ dropped a link to some epic benchmarks, while npub1h29aysw658hzgzh523t8zrw6jc72qnjgz045regl7k3htklu5s4qcqjkze stirred the pot by commenting on the Rust community's vibe. Classic tech banter! Check out the full convo here.
📣 Always Listening but Not Always Understanding 🎧
Sebastix dropped a simple yet intriguing "I'm always listening". But npub1f9kn3a5cv4fsq2x86gfrznfuumtqtu6j3fkyqg9qvlymt0zflvfsn3v9fa wasn't having it, calling out the authenticity of that statement. 🤔 They also threw in some cryptic musings about Cathrine and intelligence, complete with a martial arts emoji for effect. Sounds like there's more to this story! 🥋 Check out the full convo here.
🤫 Quiet Revolution in the Public Square 🎙️
nielliesmons brought the sass with a post about the evolving "Public Square" vibes. They joked about how things might get so low-key that we’d just chat directly in the feed, throwing some shade at "Twitter-clone maxis". 😉 No major interactions yet, but this one's bound to stir up some laughs and debates soon. Check out the full convo here.
🎉 #Toiletchain Chronicles 😂
So, 7fqx started things off with a cheeky "#toiletchain!" post. It's the kind of randomness we all love, right? Silberengel threw in their own twist, clarifying they were talking about computer logs, but made it hilarious with a little "okay" 😂, while npub1mc20uche0cy599vpl850aschpu7wteundgsnf0msep79lu3fu5aq3r4ptv chimed in with "#poopstr" and even dropped a bowel movement emoji with an image link. Gotta love a good poop joke, right? 💩
Check out the full convo here
🤔 Presidential Ponderings
Karnage was musing about the title "presidential candidate" vs. "President Trump." You know, the little things people get hung up on. npub1m2u4v2jtz4np0y3lk2anr4vm4vr4l7jlr7y94qglhfrgewsczchqg6y2gl suggested we just call it "presdent" 😂, trying to keep it light. But then npub1ncavrt6e38e94c6desg9tllzer0jey30rlh8whjtkpl9tcvvc8vs9ee00s dropped a little realism in there, noting how "normal" is key in these times. It's good to keep it real, right?
Check out the full convo here
🦖 Dinosaur Delights
In classic Karnage style, they just asked, "Dinosaurs?" 😂 Sounds like the start of a random but potentially awesome conversation, right? utxo the webmaster 🧑💻 delivered with a legendary "DEEZ NUTZ" joke along with a perfectly silly gif, making us all laugh out loud. 🐸😂 Then Karnage responded with a suave "cheers" gif. 🥂
Check out the full convo here
🌄 Morning Greetz from the #Nostriches!
archjourney welcomed everyone with a bright and cheery "Goood Morning #nostriches!" and shared some cool vibes with an image. It’s all about that positive morning energy, right? npub1dvs7rcq8vtus2nd45xamajnzt7clhxe2yvywenz5kmatdc2klljsa64fgv and npub1ztyqtftdkt6q36gux3xptn4ldv7sdpqka3rvhvlmna50e9t7kx4qk5kfjr replied with their own cheery "GM" greetings, spreading that morning love. 💜
Check out the full convo here
🤣 In the Moment
agichoote was feeling a bit cheeky with their post "At this very moment 🤣". Diyana wanted to know what deep thoughts were going on, maybe expecting some juicy gossip? But then agichoote says they’d like to be single again! 😂 Oh boy, someone’s in a mood!
Check out the full convo here
Buzzing About the Twitterverse and Cozy Family Chaos 🌐🏡
7fqx started off the day lamenting that Nitter isn't working anymore and dreaming about a way to blast some Twitter updates through good ol' RSS feeds. Then, captain ☦️ chimed in with a classic quip about Musk messing up their Twitter fun. 🤭
agichoote hit us with a photo to celebrate some of those magical "gooder" mornings in the Alps. And who popped in to greet them with a sunny GM? None other than npub1x95l2dxqqz0szeanud0cvftkkzcj3zqxsl8x48y8dszql6k49r3s42tdv7! 🌄
Over in family land, nielliesmons shared the cultural chaos of living in two countries with both grandmas under one roof! Sounds like a sitcom in the making, with three generations and constant visits turning the house into a lively hub. Silberengel can relate, being proud to be THOSE people who might just make the neighbors call the cops with their bustling family gatherings. 😂
Lastly, things turned political when Karnage poked some fun at Trump supporters, causing quite the stir. Of course, npub1spdeklkg7zd43ygdf8s5mtxe2d9eha0v6kndaef83r7y9u2h5xyse0dfw6 had to jump in with a sly comment on Trump's "stable genius." All in good humor! 😆
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:43:00
@ 59df1288:92e1744f
2024-10-16 07:43:00Hey Rabble, pull up a chair because you're just in time for the latest episode of "As the Nostr World Turns." Our pal dropped a cryptic teaser, "Who will the reply guys reply to?" and not a peep in response—apparently, everyone's playing it cool or composing their reply-guy manifestos in secret. It's all suspense in the Nostr universe—like waiting to see who spoils the plot twist in a whodunit! Dive into the full scoop to see if the reply guys finally emerge from the shadows or if today’s just another day at the Nostr library.
Who's on the Reply Guy Radar? 🤔📲
So, our buddy 7fqx dropped a little teaser, asking the infamous question, "Who will the reply guys reply to?? 👀👀" and, surprise, surprise, no one jumped in to say just yet! 😂 Maybe everyone's just lurking, waiting to pounce with their hottest takes, or maybe today's just a chill day in the Nostr world.
It's like a mystery waiting to unfold—who's gonna be the target of those top-notch reply guy comments? Maybe next time, we'll see some lively debates or cheeky banter popping off!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:39:34
@ 59df1288:92e1744f
2024-10-16 07:39:34Hey Rabble, grab your digital binoculars because things are getting interesting in the land of Nostr! 🌿 It seems like our favorite corner of the internet has hit a tranquil patch, perhaps due to those elusive relays or the shenanigans of our stealthy friend Amethyst Tor. 😏 Even Twitter seems to be catching the snooze vibe—coincidence or cosmic quiet time? Whether it's a glitch or just the universe telling us to take a breath, there's plenty of intrigue to unfold. Come see what the hush is all about and join the conversation on what might just be a covert operation.
Quiet Days and Lurking Ways 🌿
So, 7fqx was just chillin' and chatting about how things are feeling a bit too quiet on Nostr these days. They're wondering if it's something to do with the relay setup or maybe Amethyst Tor being sneaky. 😏 But no sweat, it seems their Twitter lurking account is on a similar silent mode. Maybe it’s one of those universal quiet vibes? Who knows! Either way, sounds like they're taking the calm in stride—just another day in the digital world.
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:36:16
@ 59df1288:92e1744f
2024-10-16 07:36:16Gather 'round, fellow Nostronauts, because we've stumbled upon a delightful riddle that has the community all abuzz! Our chat rooms are buzzing with speculation over a cryptic message that's as enigmatic as a cat in a box, and twice as intriguing. Is it a profound oracle or just somebody's way of keeping us on our toes? No answers yet, but the mystery is as thick as pea soup, and everyone's eager to play detective. Grab your magnifying glasses, folks, it’s going to be a fun one!
"Mysterious Musings"
Well, things have been pretty quiet, but there's this intriguing note dropped by our pal 7fqx. The message just says "(Moreso than usual)," and it's definitely piqued everyone's curiosity! 🤔 What do they mean? Is it cryptic, philosophical, or just 7fqx being their mysterious self? No replies yet, but you bet folks are scratching their heads trying to figure out what's up. Stay tuned for any revelations!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:35:35
@ 59df1288:92e1744f
2024-10-16 07:35:35Grab your critical thinking caps and prepare to leap into the philosophical rabbit hole of the latest Nostr musings! Our friend Rabble led the charge this week with an enigmatic nugget, leaving everyone trying to decipher the hidden Zen within. Between bursts of digital epiphany and meme-sharing giggles, it’s the kind of puzzle that makes you simultaneously ponder the universe and question your choice of breakfast cereal. Dive into the conversation and see if you can crack the code—or at the very least, snag a laugh or two!
More Thoughts Than Usual 🤔
Looks like 7fqx was in a pensive mood, sharing a quick thought with us: "(Moreso than usual)". It's one of those cryptic yet intriguing updates that left the rest of the crew wondering what's going on behind those words. You know how it is, one minute everyone's all "deep thoughts," the next we're laughing over memes. 😅 No replies yet, but definitely a convo starter for anyone looking to dive deep!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:22:56
@ 59df1288:92e1744f
2024-10-16 07:22:56Hey there, fellow Nostronauts! 🌌 While we were all casually sipping our metaphorical tea, Karnage decided to break the internet with a zinger about "Trump simps in dismay," complete with a battalion of emojis. But hold onto your hats—everyone else was apparently on a wordless meditation retreat because the post was met with the deafening sound of cricket chirrups. Dive into the full convo for a dose of drama, possibly the quietest hoo-ha in Nostr history! 🦗☕
Trump Talk and Tea ☕
So, here's the deal. Our friend Karnage stirred the pot with their post about "Trump simps in dismay" 😮 🤣 (looks like they went all in on the emojis). Seems like it was a spicy take, but can you believe it—no one replied, reacted, or even reposted! Guess everyone was either too shocked or quietly agreeing? 🤭
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:21:35
@ 59df1288:92e1744f
2024-10-16 07:21:35Gather 'round, fellow screen enthusiasts, as we poke fun at the cosmic conundrum that is our collective love affair with TV, all ignited by [SOUTHSIDE]'s seemingly innocuous query, "tv?" It's as if they tossed a remote-control-shaped pebble into a pond, causing ripples of silent contemplation or perhaps a mad dash to the nearest streaming platform. Are we on the verge of a great debate over the merits of classic noir versus contemporary sci-fi? Or are we all just too entranced by the latest plot twist? Either way, settle in and brace yourself for a discussion as sprawling as your favorite series' character development arcs.
TV Talk with SOUTHSIDE 📺
So, SOUTHSIDE popped in asking "tv?" and honestly, it was like the universe asking a deep, philosophical question. 😆 It seems like everyone was momentarily speechless, or maybe they all rushed off to binge-watch something. Who knows? Maybe they're just gearing up for an epic TV show debate. Stay tuned!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:20:41
@ 59df1288:92e1744f
2024-10-16 07:20:41Pour yourself a bowl of popcorn because our latest Nostr chat tiptoes into the world of TV with the thrilling opener of... "tv?" It's the kind of conversation starter that's just begging for a cascade of couch-potato confessions and passionate debates over plot twists—yet, somehow it's still on the "to be continued" list! Will "tv?" lead to the next binge-watching must-have or remain the world's shortest TV guide? Tune in to find the laughs and insights in a discussion that's one remote control away from coming alive. 📺
TV Talk Time 🎬
Looks like SOUTHSIDE kicked off a conversation with a simple "tv?" The chat didn't have any replies yet, but you know how it goes. Sometimes a single word can start a whole stream of recommendations and nostalgic trips down TV memory lane. Maybe next time, someone will jump in with their latest binge-worthy show. 📺
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 07:20:00
@ 59df1288:92e1744f
2024-10-16 07:20:00Hey there, emoji enthusiasts and cryptic communicators! 🤔🌍🕵️♂️ This week's Nostr chatter dabbled in a bit of linguistic revolution, where emojis might just be the secret sauce to convey everything from philosophical musings to global quandaries without uttering a traditional word. Forget the book club—grab your decoder ring and popcorn, because these tiny symbols are dropping some colossal wisdom without needing a single voice to chime in. Ready to unearth what a gun and a globe can reveal together? 📖✨ Let's dive into the conversation!
Emoji-Wise Words 🌍🔫
So, our friend nielliesmons dropped a brilliant, emoji-packed one-liner that's got everyone thinking. 🤔 How cool is it that emojis, combined with the alphabet, might be the ultimate way to express ourselves in writing? It's like a mini mind-blown moment in just a few symbols. Who knew gun and globe could say so much without a single soul jumping in for a reply yet? 📖✨
Check out the full convo here
-
 @ e6817453:b0ac3c39
2024-09-30 14:52:23
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) );It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};vector_distance_cos calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) ivector_top_k is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is post-filtering. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector_top_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top};It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
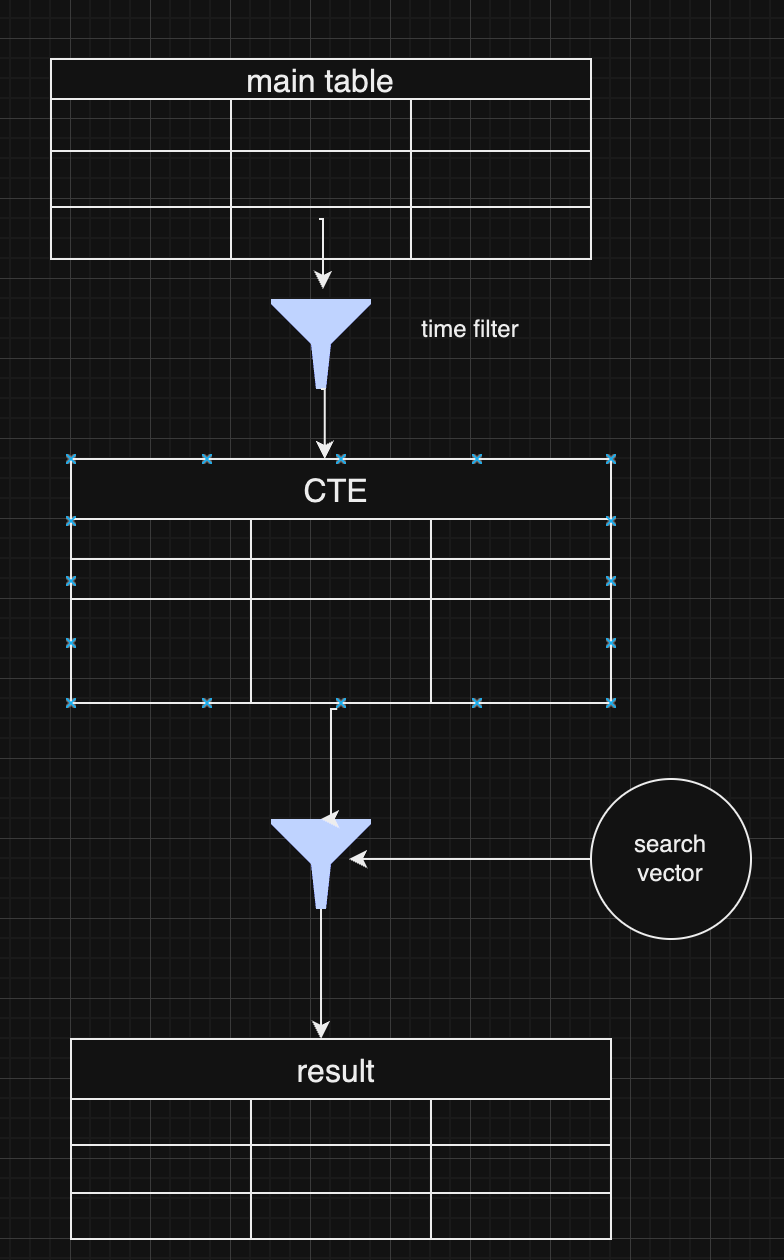
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
Conclusion
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-
 @ eac63075:b4988b48
2024-09-20 08:46:49
@ eac63075:b4988b48
2024-09-20 08:46:49Lá na outra rede, o Dov havia feito um post bacana mostrando como usar a Electrum mobile de cold wallet nessa playlist.
Então ao comentar que a minha primeira cold wallet havia sido uma Electrum num notebook velho e formatado só pra isso, algumas pessoas me perguntaram sobre meu setup atual.
Então preparei o seguinte esboço:
No geral é: * Server Umbrel para os nodes * Coldcard e Ledger (coldwallets) * Computador criptografado e celular android com área segura p/ apps
É um caso de uso extremo mas além da auto-soberania e custódia dos meus satoshis, essa estrutura ainda me permite:
- Participar do consenso do Bitcoin
- Auxiliar no roteamento de sats na Lightning Network
- Fazer coinjoin facilmente para aumentar a privacidade
E embora a estrutura pareça complicada, é bastante simples:
- Raspberry Pi 4 com Debian e Umbrel (p/ os nodes e servers)
- Celular antigo android com área segura e sem simcard
- Notebook com storage criptografada
- Ledger Nano X
- Coldcard
E ainda pude evoluir de N.O.I.A. (Network Operator Innovator and Advocate) para M.A. (Minerador Anônimo), com uma Nerdminer pra tentar um ticket da sorte a cada 10 minutos
Não esqueça que uma cold wallet para a auto-custódia pode começar com um computador ou celular velho!
É mais simples do que parece e praticar sua auto-soberania e custódia significa na verdade liberdade e privacidade nesse mundo digital!
-
 @ 17538dc2:71ed77c4
2024-09-16 15:26:32
@ 17538dc2:71ed77c4
2024-09-16 15:26:32
Quiztime
Oil and gas
Oil and gas is naturally occurring. The prevalent worldview is that oil & gas has a biotic origin. There are real world examples of abiotic oil deposits, which proponents of the status quo have a difficult time reconciling.
Irregardless, when oil & gas is burned, it simply turns to plant food (carbon dioxide + water).
Oil and gas greens the Earth, and increases fertilization and agricultural crop yield across the globe.

The energy density of oil and gas is only surpassed by that of nuclear power.
Energy produced by oil and gas combustion is generally on-demand, reliable, economically storable & transportable.
Solar
The sun is an abudant energy source, which keeps Earth warm, and alive. Thank you sun 🌞!
With the exception of places such as the UK, where it is unclear if inhabitants have ever seen the sun, solar rays keep plants, animals, and humans happy & alive on most of planet Earth.
Inventions such as solar panels harness the sun's energy, and convert it to electricity.
Solar panels consist of silicon, rare earth metals, and require toxic metals.
Solar panels have an expected life of decades, are not readily or economically recyclable.
A very low solar energy density practically means that land is inefficiently utilized in solar energy production. Solar used on arable land can no longer be farmed, and where no plains exist solar is known to cause deforestation and landslides.
Solar energy is not reliable, not can it be summoned on demand. Solar energy is not economically storable, and is many cases is not produced at the point of demand.
Despite central planner mandates & subsidies in the US, the #EULAG and elsewhere, due to its intermittent nature, solar power cannot be counted on to replace reliable power generation in nuclear, hydro, or carbon fuel thermoelectric plants.
What this means is that solar does not replace, and yet ratheradds to reliable energy generation, as most people in the developed world would not be OK with having electricity for at most 1/3 of the day. This increases the price of electricity, which in turn increases energy poverty, and drives businesses to shut down manufacturing, or move to a more energy competitive jurisdiction.
The capital wasted by central planners could have been used to reduce burden on consumers, and businesses, or fund healthcare, infrastructure, or other services.
It should be noted that off grid applications where there is no grid, or energy alternatives can be massively useful for folks otherwise without electricity.
Which energy source would you consider renewable?
-
 @ a6631624:24ba1a2f
2024-09-01 21:18:15
@ a6631624:24ba1a2f
2024-09-01 21:18:15Genetics are real. They determine every meaningful aspect of a body - from physical traits to psychological ones - with environment accounting for little of a human's way of being. This is so much so that the trajectory and outcomes of a given human life are already written as soon as they're born.
Nowhere is this more apparent than in twin studies, where again and again, identical twins live virtually the same life after being separated at birth. They show that your political beliefs, your personality, your religiosity, the foods you enjoy, how many friends you have, your income level, your education level, your criminal record, the nature of your death, what you wore today, and so much more are all most likely determined, in range at least, by genetics.
But, genes do not work in isolation. They work together, playing off of and linking between each other, often with the expression of one trait inseparably tied to the expression of another and then, sometimes, yet another.
Invariably, some of these links and ties are between the expression of an internal trait and the expression of a physical trait, accounting for the reality that, in the way that we know the literal face of Down's Syndrome, the same exist - albeit much less extreme - for homosexuality, intelligence, trustworthiness, and extraversion (and many more). All of which can be consistently detected by humans in other humans merely by viewing their faces.
Furthermore, these correlations between physical traits (phenotype) and invisible traits (genotype) don't just end at the neck. Bodily aspects such as bone structure, gait, proportionality, and much more ultimately form one's very mien and, altogether, have much to say about the genetically embedded character of a given human.
All of this is to suggest that, because much of compatibility and general social chemistry is determined by the genetic outside as an indicator of the genetic inside, our bodily design and appearances matter and have very significant implications for the nature of our relationships, with whom we may have them, and the opportunities accessible to us in every other area of life due to them.
This cannot be reasonably or sustainably overridden by means of "social justice" or personal declaration. This instinctually mapped and interpreted physiognomy is so thoroughly embedded into the human social protocol that to ignore it (if you even could) would likely result in your prompt death at the hands of some guys you should've avoided. The ability to, on some level, identify the physical characteristics associated with psychological traits in other humans has evolved specifically because it increases the chances of human survival and reproduction.
It is, in fact, so fundamental and so seamlessly integrated into the being of humans as to be unnoticeable for the majority. Most cannot fathom there being a difference the internal self and the physical body because the fidelity between their own will and their own biological design is perfect. Most people simply are how they look.
The Outliers
Because humans are genetic (read: physical) creatures, we can see statistical patterns assuring us that making a number assumptions about X kind of person based on the concentration traits among those “like” them is incredibly reasonable. Even in our systems and lived lives, we see that our evolutionarily rooted snap assessments are exceedingly practical and even socially efficient.
But, there are outliers in genetic trends.
Due to either mutation, rare genetic combinations, or some more extraordinary means, outliers in this context are individuals who diverge significantly from the central psychological tendencies of their phenotype group. They may either align more closely with the characteristics of another group or occupy a distinct, individual space.
Gender and race are the two most robust, rigid, and (therefore) social impactful phenotype groups, so when there is psychological incongruence in these particular respects, the result is a social disability. A condition in which one either cannot or finds it extremely distasteful to fill the social roles associated with their appearance, yet is rejected when attempting to take on roles they’re more psychologically suited to fill due to the visual associations and/or physical limitations of their body.
Gender
For outliers in gender, this social disability has an extremely somatic edge that can entail entire body parts and functions feeling foreign and burdensome. For instance, the most common types of gender outliers – "FtM" or "FtN" – may struggle with the relative lack of physical prowess, female bodily processes, and physical features designed to attract male sexual attention - things that psychologically typical females embrace.
Bodily conditions like these often hinder gender outliers from acting and participating in their interests at a reasonable level of seriousness, ultimately leading to sub-satisfactory life outcomes and an inability to self-actualize.
This mismatch between body and self-consciousness and the difficulty of commanding respect that arises because of it means that gender outliers often find it difficult to interact comfortably with their peers and are often forced into activities and interactions that are not suitable for them in the names of conformity and, at times, safety. On the subject, their thoughts, feelings, and reactions are dismissed and devalued, rather than acknowledged as legitimate experiences.
Race
Racial outliers can be thought of as individuals with traits that have low probabilities and/or frequencies of occurrence within their breeding group. "Trans identification" is most likely to manifest when this occurs on intrinsic traits with high social relevance and for outliers in race, the big ones are intelligence, it's associated correlates, and the values born of them.
Because of this, racial outliers typically have interests and values that are looked down upon by their breeding group; have shame in regard to their breeding group's history, collective culture, and behaviors; and, for these reasons, experience ostracization by said breeding group and, even when they do not, enjoy a voluntary estrangement from them while prioritizing association with others.
Contrary to common consensus, outliers in gender and race are not necessarily suffering from mental illness or defect. Though the condition itself may result in mental illnesses in some cases and those with other issues may parade or otherwise appear as the outliers, being so is simply a natural result of the way genetics work or, from another lens, trapping Selves in bodies.
Knowing this calls for efforts to alleviate and eventually rectify the issue in a way that corrects the genetic reality and optimizes for the agency and will of the Self - the individual - in context of civilization.
Reasons why and the means of doing so will be explored in the next installment of this series.
-
 @ da18e986:3a0d9851
2024-08-14 13:58:24
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at https://dvmdash.live and the code is available on Github.
Data Vending Machines (NIP-90) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. For now, the website only shows 1 step of a dvm chain from a user's request.
One of the main designs for the site is that it is highly clickable, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
Features in v0.1:
Global Network Metrics:
This page shows the following metrics: - DVM Requests: Number of unencrypted DVM requests (kind 5000-5999) - DVM Results: Number of unencrypted DVM results (kind 6000-6999) - DVM Request Kinds Seen: Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - DVM Result Kinds Seen: Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - DVM Pub Keys Seen: Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - DVM Profiles (NIP-89) Seen: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - Most Popular DVM: The DVM that has produced the most result events (kind 6000-6999) - Most Popular Kind: The Kind in range 5000-5999 that has the most requests by users. - 24 hr DVM Requests: Number of kind 5000-5999 events created in the last 24 hrs - 24 hr DVM Results: Number of kind 6000-6999 events created in the last 24 hours - 1 week DVM Requests: Number of kind 5000-5999 events created in the last week - 1 week DVM Results: Number of kind 6000-6999 events created in the last week - Unique Users of DVMs: Number of unique pubkeys of kind 5000-5999 events - Total Sats Paid to DVMs: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is https://vendata.io/.
Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please submit a git issue here or note me on Nostr!
Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and vendata.io which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 3c984938:2ec11289
2024-07-22 11:43:17
@ 3c984938:2ec11289
2024-07-22 11:43:17Bienvenide a Nostr!
Introduccíon
Es tu primera vez aqui en Nostr? Bienvenides! Nostr es un acrónimo raro para "Notes and Other Stuff Transmitted by Relays" on un solo objetivo; resistirse a la censura. Una alternativa a las redes sociales tradicionales, comunicaciónes, blogging, streaming, podcasting, y feventualmente el correo electronico (en fase de desarrollo) con características descentralizadas que te capacita, usario. Jamas seras molestado por un anuncio, capturado por una entidad centralizada o algoritmo que te monetiza.
Permítame ser su anfitrión! Soy Onigiri! Yo estoy explorando el mundo de Nostr, un protocolo de comunicacíon decentralizada. Yo escribo sobre las herramientas y los desarolladores increíbles de Nostr que dan vida a esta reino.

Bienvenides a Nostr Wonderland
Estas a punto de entrar a un otro mundo digtal que te hará explotar tu mente de todas las aplicaciones descentralizadas, clientes, sitios que puedes utilizar. Nunca volverás a ver a las comunicaciones ni a las redes sociales de la mesma manera. Todo gracias al carácter criptográfico de nostr, inpirado por la tecnología "blockchain". Cada usario, cuando crean una cuenta en Nostr, recibe un par de llaves: una privada y una publico. Estos son las llaves de tu propio reino. Lo que escribes, cantes, grabes, lo que creas - todo te pertenece.

Unos llaves de Oro y Plata
Mi amigo y yo llamamos a esto "identidad mediante cifrado" porque tu identidad es cifrado. Tu puedes compartir tu llave de plata "npub" a otros usarios para conectar y seguir. Utiliza tu llave de oro "nsec" para accedar a tu cuenta y exponerte a muchas aplicaciones. Mantenga la llave a buen recaudo en todo momento. Ya no hay razor para estar enjaulado por los terminos de plataformas sociales nunca más.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Todavia No tienes un cliente? Seleccione la mejor opción.
Encuentra la aplicación adecuada para ti! Utilice su clave de oro "nsec" para acceder a estas herramientas maravillosas. También puedes visit a esta pagina a ver a todas las aplicaciones. Antes de pegar tu llave de oro en muchas aplicaciones, considera un "signer" (firmante) para los sitios web 3. Por favor, mire la siguiente imagen para más detalles. Consulte también la leyenda.

Get a Signer extension via chrome webstore
Un firmante (o "signer" en inglés) es una extensión del navegador web. Nos2x and NostrConnect son extensiónes ampliamente aceptado para aceder a Nostr. Esto simplifica el proceso de aceder a sitios "web 3". En lugar de copiar y pegar la clave oro "nsec" cada vez, la mantienes guardado en la extensión y le des permiso para aceder a Nostr.

👉⚡⚡Obtén una billetera Bitcoin lightning para enviar/recibir Zaps⚡⚡ (Esto es opcional)

Aqui en Nostr, utilizamos la red Lightning de Bitcoin (L2). Nesitaras una cartera lightning para enviar y recibir Satoshis, la denominacion mas chiquita de un Bitcoin. (0.000000001 BTC) Los "zaps" son un tipo de micropago en Nostr. Si te gusta el contenido de un usario, es norma dejarle una propina en la forma de un ¨zap". Por ejemplo, si te gusta este contenido, tu me puedes hacer "zap" con Satoshis para recompensar mi trabajo. Pero apenas llegaste, as que todavia no tienes una cartera. No se preocupe, puedo ayudar en eso!
"Stacker.News" es una plataforma donde los usarios pueden ganar SATS por publicar articulos y interactuar con otros.

Stacker.News es el lugar mas facil para recibir una direccion de cartera Bitcoin Lightning.
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto

- Haga clic en "edit" y elija un nombre que te guste. Se puede cambiar si deseas en el futuro.

- Haga clic en "save"
- Crea una biografía y la comunidad SN son muy acogedora. Te mandarán satoshi para darte la bienvenida.
- Tu nueva direccion de cartera Bitcoin Lightning aparecerá asi
 ^^No le mandas "zaps" a esta direccion; es puramente con fines educativos.
^^No le mandas "zaps" a esta direccion; es puramente con fines educativos. - Con tu Nueva dirección de monedero Bitcoin Lightning puedes ponerla en cualquier cliente o app de tu elección. Para ello, ve a tu página de perfil y bajo la dirección de tu monedero en "Dirección Lightning", introduce tu nueva dirección y pulsa "guardar " y ya está. Enhorabuena.
👉✨Con el tiempo, es posible que desee pasar a las opciones de auto-custodia y tal vez incluso considerar la posibilidad de auto-alojar su propio nodo LN para una mejor privacidad. La buena noticia es que stacker.news tambien está dejando de ser una cartera custodio.
⭐NIP-05-identidad DNS⭐ Al igual que en Twitter, una marca de verificación es para mostrar que eres del mismo jardín "como un humano", y no un atípico como una mala hierba o, "bot". Pero no de la forma nefasta en que lo hacen las grandes tecnológicas. En el país de las maravillas de Nostr, esto te permite asignar tu llave de plata, "npub", a un identificador DNS. Una vez verificado, puedes gritar para anunciar tu nueva residencia Nostr para compartir.
✨Hay un montón de opciones, pero si has seguido los pasos, esto se vuelve extremadamente fácil.
👉✅¡Haz clic en tu "Perfil ", luego en "Configuración ", desplázate hasta la parte inferior y pega tu clave Silver, "npub!" y haz clic en "Guardar " y ¡listo! Utiliza tu monedero relámpago de Stacker.news como tu NIP-05. ¡¡¡Enhorabuena!!! ¡Ya estás verificado! Dale unas horas y cuando uses tu cliente "principal " deberías ver una marca de verificación.
Nostr, el infonformista de los servidores.
 En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.
En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.¡Mis amigos en Nostr te dan la bienvenida!
Bienvenida a la fiesta. ¿Le apetece un té?🍵

¡Hay mucho mas!
Esto es la punta del iceberg. Síguenme mientras continúo explorando nuevas tierras y a los desarolladores, los caballeres que potencioan este ecosistema. Encuéntrame aquí para mas contenido como este y comparten con otros usarios de nostr. Conozca a los caballeres que luchan por freedomTech (la tecnología de libertad) en Nostr y a los proyectos a los que contribuyen para hacerla realidad.💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
🧡😻Esta guía ha sido cuidadosamente traducida por miggymofongo
Puede seguirla aquí. @npub1ajt9gp0prf4xrp4j07j9rghlcyukahncs0fw5ywr977jccued9nqrcc0cs
sitio web
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto
-
 @ 75da9402:77a65b5c
2024-07-11 19:14:04
@ 75da9402:77a65b5c
2024-07-11 19:14:04
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ 59df1288:92e1744f
2024-10-16 07:11:40
@ 59df1288:92e1744f
2024-10-16 07:11:40Hold onto your typewriters, folks, because our latest Nostr chatter has taken us on a whimsical time-travel ride back to the era of ink-stained fingers and press hats. Our pal shared a delicious tidbit about none other than Joseph Pulitzer planting the seeds of The Post-Dispatch, reminding us there's more to our morning news than just cat memes and weather updates! As we sip our virtual brew, could there be a revival in the air for the romance of old-school journalism? Dive into the conversation and see if anyone's dusting off their newsboy caps—a Pulitzer-worthy tale might just be bubbling up!
Pulitzer and Other Tidbits
Guess what? 📰 Our friend roya ୨୧ dropped a fun tidbit about The Post-Dispatch—turns out, it was founded by none other than Joseph Pulitzer himself! It sparked a neat little history lesson moment, even without any replies yet. Maybe it's just one of those things that could spur an interesting convo about newspapers and journalism nostalgia. 📚
Check out the full convo here
-
 @ dd664d5e:5633d319
2024-06-24 06:05:05
@ dd664d5e:5633d319
2024-06-24 06:05:05The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous Project Gutenberg, and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public Citadel relay for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because obviously.
Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house their own books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see Pandoc). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind 30040 allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-
 @ 59df1288:92e1744f
2024-10-16 06:57:29
@ 59df1288:92e1744f
2024-10-16 06:57:29Blast off with us as we dive into the Nostr stratosphere, where philosophical musings are rocketing beyond the usual ideological skirmishes. Our cerebral astronaut, the user known as Rabble, has us looking up and contemplating a whole new elevation. Forget left or right—it's all about the climb! Who knew the secret to enlightenment might just be hitting ctrl+alt+ascend? Strap in for some sky-high ideas and a sprinkle of space humor that might just have you rethinking your own trajectory towards greatness.
Nostr's Sky-High Philosophy 🚀
Sebastix is dropping some philosophy bombs with their take on navigating life! They're all about climbing upwards rather than getting lost in the usual left vs. right debates. With Nostr, they're saying it’s all about rising to the top, and honestly, who doesn’t love a good underdog success story? 🤓🫡
It’s been quiet on the reply front, but knowing our crew, it won't be long before someone jumps in with a hot take or a joke. Maybe everyone’s just busy plotting their own climb to the top!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 06:49:14
@ 59df1288:92e1744f
2024-10-16 06:49:14Pack your virtual bags and slip on those shades, because Nostr's latest chatter takes us on a whirlwind tour of Miami infused with Taco Bell vibes and a Selena soundtrack that would make even the chilliest of maracas shake. Dive into tales of sun-soaked nostalgia and the art of balancing a chalupa in one hand while taking the perfect beach selfie with the other. Whether you're in it for the travel inspiration or the sheer joy of living vicariously through others' adventures, this roundup is the perfect escape without leaving your couch. 🌮✨
Miami Vibes and Taco Bell Times 🌴🌮
So, our good friend BRB‽ has just landed safely in Miami with their bestie, and it sounds like a total vibe! 🎉 They're kicking back, sipping drinks, munching on Taco Bell, and getting nostalgic with some Selena tunes. Talk about a perfect mini-vacation setup! 💕🫂 The post was all smiles and good times, with some awesome pics and videos of Miami sights—the perfect mix of relaxation and fun. Everyone needs a break like this sometimes! 😎
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 06:44:32
@ 59df1288:92e1744f
2024-10-16 06:44:32Pack your virtual bags and slip on your sunglasses, because this week on Nostr, we're jetting off to Miami for a slice of the good life! 🌴 From Taco Bell feasts to Selena marathons, it's like someone bottled up the essence of fun, popped the cork, and let the good times flow. If your FOMO levels are reaching critical, grab a piña colada and dig into our juicy tidbits where the sun's always shining and the vibes are all good. Cheers! 🍹✨
Miami Vibes with 💕BRB‽
Looks like BRB‽ has landed safely in Miami and is totally living the dream! 🌴 She's chilling with her bestie, sipping drinks, munching on Taco Bell, and binge-watching Selena. Sounds like the ultimate minivaca! You can almost hear the laughter and good vibes through the screen. Don't you just wish you were there soaking up the sun alongside them? 🙌🏾
- Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 06:41:41
@ 59df1288:92e1744f
2024-10-16 06:41:41Grab your forks and raise your tray tables, folks! This week's Nostr wanderings took to the skies with larger-than-life tales of cheesecake confections and in-flight recognition all spiced with a mischievous hint of durian. Who knew revealing your stint at the Bangkok Post could make as much of an impact as divulging dessert secrets at 30,000 feet? Whether you’re here for the sweet or the savory of air-borne adventures, there’s no missing out on this week’s captivating exchange that somehow left the mystery of the cheesecake recipe hanging in mid-air! Dive in to unearth every crumb of these high-flying revelations!
Cheesecake Confessions at 30,000 Feet 🛫
Hey! So Carl Malamud had quite the chat with a flight attendant on their flight. Get this—they not only impressed her by identifying her Thai accent but also claimed they invented Durian cheesecake! 🍰 Talk about a conversation starter, right? Imagine the stories swapped when you drop you wrote for the Bangkok Post. No wonder they had everyone captivated even without any replies yet. Can you believe no one jumped in to ask for the cheesecake recipe or about writing for the Bangkok Post? Classic sky-high banter!
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 06:38:13
@ 59df1288:92e1744f
2024-10-16 06:38:13Gather 'round, brainy bunch! The latest buzz in the Nostr sphere is like getting a tantalizing whiff of your neighbor's BBQ—enticing, but you're still not quite sure what's cooking. Our inventive comrade threw down a "Very good idea" without spilling the beans, leaving the community at the edge of their virtual seats, predicting DM storms and clandestine brainstorming sessions. Will this mystery unveil the next big thing, or are we all just popcorn-ready for nothing? Dive in and let's unravel the intrigue together! 🍿✨
Genius Idea Brainstorm 🌟
Hey! So, I didn't want you left out on this one—our pal melvincarvalho just threw out what sounded like a pretty rad idea. They simply called it a "Very good idea," which piqued everybody's interest but left everyone hanging, because of the suspense, right? 😂
The post didn't get any replies yet, but knowing this crew, they probably shot off some epic DMs or are plotting to help flesh out the idea. Anticipation is high!
Anyway, it seems like we're all waiting to see what juicy details they'll drop next. Stay tuned; it's bound to get interesting! 😉
Check out the full convo here
-
 @ 59df1288:92e1744f
2024-10-16 05:43:58
@ 59df1288:92e1744f
2024-10-16 05:43:58Hey there, digital explorers! 🌐 This week's Nostr chats have taken a turn for the tender, with an outpouring of virtual hugs and heart emojis melting even the iciest screens. It seems like optimism has gone viral, proving that a well-timed emoji can jazz up any day and say what words simply can't. Dive in and see how this contagiously cuddly vibe is bringing our lively community even closer together. Trust us, you won't want to miss the warm fuzzies waiting in the full summary! 🫂🧡
Group Hugs and Heart Emojis 💞
Hey! So, AK dropped a sweet little post that just oozes warmth and good vibes. They posted a big ol' hug and an orange heart emoji — just what we need to sprinkle some love around! 🫂🧡
Not much chatter here, but it's like an open invite for everyone to feel the love! Perfect chance for you to join in and maybe give some reaction love? Emojis just make everything better!
Check out the full convo here
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 03742c20:2df9aa5d
2024-10-16 03:17:20
@ 03742c20:2df9aa5d
2024-10-16 03:17:20Relay ตัวนี้มีให้ตั้งค่ากรอง pow และ wot ด้วย หรือใครจะใช้เป็น Private relay ก็ทำได้เช่นกัน
วิธีติดตั้ง nostr-relay-nestjs มี 2 วิธี
ติดตั้งแบบลงเครื่องโดยตรง
ก่อนจะลง nostr-relay-nestjs ควรติดตั้ง Nodejs, pm2 และ postgresql
sudo apt updateติดตั้ง nodejscurl -fsSL https://deb.nodesource.com/setup_20.x | sudo -E bash -sudo apt install -y nodejsติดตั้ง npmsudo apt install npmติดตั้ง pm2sudo npm install pm2 -gติดตั้ง postgresql สร้าง docker-compose.yml ``` version: '3.8'services: postgres: image: postgres:latest container_name: postgres environment: POSTGRES_DB: [db_name] POSTGRES_USER: [user] POSTGRES_PASSWORD: [password] volumes: - postgres_data:/var/lib/postgresql/data ports: - "5432:5432" restart: unless-stopped
pgadmin: image: dpage/pgadmin4:latest container_name: pgadmin environment: PGADMIN_DEFAULT_EMAIL: [E-mail] PGADMIN_DEFAULT_PASSWORD: [password] ports: - "5050:80" depends_on: - postgres restart: unless-stopped
volumes: postgres_data:
docker compose up -dเรามาเริ่มลง nostr-relay-nestjs กันเถอะgit clone https://github.com/CodyTseng/nostr-relay-nestjs.git ```cd nostr-relay-nestjsnpm installcp example.env .envแก้ไข้ไฟล์ .env ``` DATABASE_URL=postgresql://[username]:[password]@[host]:[port]/[db_name] . . RELAY_NAME=nostr-relay-nestjsRELAY_DESCRIPTION=A Nostr relay with a clear architecture and high test coverage
RELAY_PUBKEY=[your_pubkey_hex]
สร้างรูปแบบ nostr event การเก็บข้อมูลใน Postgresqlnpm run migration:runDeployg ขึ้น pm2pm2 start ./dist/src/main.js ```ติดตั้งโดยใช้ Docker
อยากลืมติดตั้ง postgresql ก่อน
./scripts/build.shแก้ไข้ไฟล์ .env ``` DATABASE_URL=postgresql://[username]:[password]@[host]:[port]/[db_name] . . RELAY_NAME=nostr-relay-nestjsRELAY_DESCRIPTION=A Nostr relay with a clear architecture and high test coverage
RELAY_PUBKEY=[your_pubkey_hex] ```
./scripts/run.shเช็คว่ารีเลย์ถูกรันขึ้นยังcurl localhost:3000ถ้าทำงานผลลัพธ์ที่ได้Please use a Nostr client to connect. Powered by nostr-relay-nestjs. version: 2.2.0 (undefined)
ตั้งค่า proxy ใน nginx
server{ server_name relay.yourdomain.com; location / { proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $host; proxy_pass http://127.0.0.1:3000; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } }หรือใช้ CloudFlare tunnelไปลองทำตามกันได้เลือกวิธีที่ตัวเองถนัดได้เลย แล้วเจอกันใหม่ครั้งหน้า จะเป็นเรื่องอะไรรอติดตามกัน
Siamstr #Nostr
-
 @ a012dc82:6458a70d
2024-10-16 03:16:09
@ a012dc82:6458a70d
2024-10-16 03:16:09Table Of Content
-
The Race for Spot Bitcoin ETFs
-
SEC's Stance
-
Coinbase Role: A Significant Surveillance Partner
-
Legal Challenges: SEC's Lawsuit Against Coinbase
-
Looking Ahead: The Future of Bitcoin ETFs
-
Conclusion
-
FAQ
In a significant development in the cryptocurrency world, Coinbase, one of the leading cryptocurrency exchanges, has been named as the surveillance partner for Fidelity and other Bitcoin ETFs. This announcement came as part of a broader move by Cboe's BZX Exchange, which refiled its applications for spot bitcoin exchange-traded funds (ETFs) for several potential issuers. This move is seen as a strategic step towards ensuring regulatory compliance and enhancing the transparency of Bitcoin trading.
The Race for Spot Bitcoin ETFs
In recent weeks, several prominent companies, including Fidelity, WisdomTree, VanEck, ARK Invest, Galaxy/Invesco, and BlackRock, have filed for spot bitcoin ETFs. These companies are aiming to launch a product that has been a point of contention with the U.S. Securities and Exchange Commission (SEC) for years. While BlackRock has chosen to file its application with Nasdaq, the other companies have opted to collaborate with Cboe, indicating a diverse approach to achieving the same goal.
SEC's Stance
The SEC had previously communicated to both Nasdaq and Cboe that their applications were "inadequate" due to a lack of clarity about the market that the fund sponsors are working with on their surveillance-sharing agreements. These agreements are seen as a critical tool in preventing market manipulation and protecting consumers. The absence of these agreements has been a significant factor in the SEC's previous rejections of bitcoin ETF applications, highlighting the importance of this aspect in gaining regulatory approval.
Coinbase Role: A Significant Surveillance Partner
In response to the SEC's concerns, Cboe has named Coinbase as its partner for these surveillance-sharing agreements in its refiled applications. Cboe's decision is based on the fact that Coinbase's platform "represents a substantial portion of U.S.-based and USD denominated Bitcoin trading." This makes Coinbase a suitable partner for these agreements, given its extensive reach and influence in the Bitcoin trading market.
Legal Challenges: SEC's Lawsuit Against Coinbase
The SEC's stance on these applications may be complicated by its recent legal action against Coinbase. The SEC sued Coinbase earlier this month on allegations of operating an unregistered securities exchange, broker, and clearinghouse. However, it's important to note that the SEC does not allege that Bitcoin itself is a security. In fact, SEC Chair Gary Gensler often refers to Bitcoin as an example of a digital asset that is not a security, indicating a nuanced view of the cryptocurrency market.
Looking Ahead: The Future of Bitcoin ETFs
As the situation unfolds, it remains to be seen whether the SEC will agree that Coinbase is a significant, regulated market for Bitcoin. This development marks a significant step in the ongoing efforts to launch a spot Bitcoin ETF, a product that has been elusive due to regulatory concerns. The cryptocurrency world will be watching closely as these applications progress, with the hope that a successful Bitcoin ETF could pave the way for broader acceptance and integration of cryptocurrencies into the mainstream financial system.
Conclusion
The partnership between Coinbase and Fidelity, along with other Bitcoin ETFs, marks a pivotal moment in the cryptocurrency industry. Despite challenges, including the recent lawsuit against Coinbase by the SEC, this development represents a significant step towards integrating cryptocurrencies into the mainstream financial system. The outcome could set important precedents for the future of Bitcoin ETFs and other digital assets, signaling a maturing and evolving cryptocurrency market that continues to strive for regulatory compliance and consumer protection.
FAQ
What is the recent development between Coinbase and Fidelity? Coinbase has been named as the surveillance partner for Fidelity and other Bitcoin ETFs by Cboe's BZX Exchange.
Why are surveillance-sharing agreements important? Surveillance-sharing agreements are crucial for preventing market manipulation and protecting consumers, which are key concerns of the U.S. Securities and Exchange Commission (SEC).
What companies have recently filed for spot Bitcoin ETFs? Companies such as Fidelity, WisdomTree, VanEck, ARK Invest, Galaxy/Invesco, and BlackRock have filed for spot Bitcoin ETFs.
What is the significance of Coinbase being named as a surveillance partner? Coinbase's platform represents a substantial portion of U.S.-based and USD-denominated Bitcoin trading, making it a suitable partner for these agreements.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b5894129:fc60ad24
2024-06-09 15:35:09
@ b5894129:fc60ad24
2024-06-09 15:35:09longtest
jsjsjjsj# sjjsjj
kkkkkkk
ggggghh
- kkkk* nnhjjj
pppmmmmmmmmmmmmmmmmmmmmnbbb
-
 @ 472f440f:5669301e
2024-10-16 01:57:41
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
Final thought... Sinus congestion sucks.
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 12cfc2ec:6967f1d9
2024-10-15 19:49:22
@ 12cfc2ec:6967f1d9
2024-10-15 19:49:22this is in response to Shinobis recent piece occupy bitcoin found here
https://bitcoinmagazine.com/culture/occupy-bitcoin-bitcoin-is-not-just-libertarian?new
Occupy bitcoin is a thing every single one of us tries to do. There isn't a single one individual that doesn’t see bitcoin for what it is and have it not occupy all of them to varying degrees. There’s an innate fascination with coming upon previously unknown knowledge and become overtly obsessed with it and exploring all of the facets in which the new knowledge can be applied. When one does so, it normally can lead to finding previously unknown areas that you come to find with the more that you learn you find out just how much you truly don’t understand.
Now with this being the foundation of what all of humans are doing. None of us, not ONE, know everything. Its a fallacious argument to claim to do. In the journey for the discovery that is truth one can happen to fall upon the political rabbit hole that can be called or dubbed Libertarianism/Anarchism/ AnCap/AnCom etc. I use these labels very lightly as they are just words at the end of the day words mean different things to different people. I cant know what these words mean to you dear reader but I can only know what they mean to me, and my journey specifically. What we as humans do is to come to an agreement upon to what does these words mean to the both of us when we are communicating them to each other. I do my best to not fall into being pigeon holed into believing or having to defend that when I say one of the aforementioned words that I should have to commit to whatever it is your preconceived understanding of what that is. We must remember that these words are collectivized terms, they are strictly USEFUL fictions that we humans use in order to better conceptualize the ideas to better understand. That to take any attribute pulled from any one of the above and blanket paint “some” or “most” individuals that claim to align with above ideologies/alignments/political beliefs that these individuals represent that is an absurd claim. One cannot claim that individuals acting in mean/harsh ways when facing others who don’t agree with them is the wrong way to act.
We are humans we disagree, were free to act as we please to anyone we wish to do so. We’re NEVER free to ignore the consequences of those actions. One could characterize the vehement disdain for the acceptance all ideas, and letting others have their own opinions, is how we as individuals got here in the first place. It was the ideas of society being more important than the whole that had legitimized the aggression sanctified by the state as an omnipotent entity free from doing no wrong in lieu of the greater good. Individuals can do as such with their minds as they please but your actions of freedom stop at the point of my nose begins. The individuals that understand freedom and its core philosophy understand this. Treating one side as an evil and the other side as some glorified good is a cop out of intellectual dishonesty.
In the realm of bitcoin there can be disagreements and even out right hostility towards any number of ideas/opinions. This is the nature of freedom itself. As I’ve seen it and as I have championed it myself do with freedom what you will, but whatever you do if I think its stupid I’m going to tell you its stupid. Social pressures have been with human civilizations for thousands of years to think that the idea of attacks to your ideas not being a thing because we should accept all ideas and be kind to differing opinions is a farce at best and some unicorn fart huffing at worst. It was the individuals that were unwavering IN SPITE of the social attacks, the public slandering, the outright social ostracization, the being called dumb and stupid that paved the way for the best and most historical moments in history Ideas don’t care about these passing affronts. If your viewpoint/idea needs soft corners to gain traction then maybe you should reassess your idea in the first place. The battleground that is the societal/accepted norm isn't one that’s for the faint of heart. Everyone has limited time and resources available to them if they are choosing not to hear you then its probably time to seek out others to speak to. In the realm of freedom everyone CAN choose any ideas they wish to follow and interact with others that agree, where that stops is you can NO LONGER force everyone else to participate in your own shared delusions with the others you associate with. The freedom to EXCLUDE is one of the core tenets of freedom principles. We DO NOT have to be accepting of everyone if we do not wish to do so, the belief that everyone should ALWAYS accept everyone and everything is a communistic one. No one individual has the time and resources to accept every person and accept or contemplate every single idea presented to him. What freedom DOES allow for is for YOU to find the individuals that ARE accepting of your views/beliefs and do with that what you wish.
By trying to call out one group of individuals as being too “tribal” in what they view as the best course of action for themselves while SIMULTANEOUSLY praising another group for their favored tenets of “acceptance” is a laughable and down right sad view that “everyone should be more like the accepting crowd”. It is only through the choices we make that we get to where we are going on this journey. Those choices are inherently going to REQUIRE dissociation, omission, & exclusion.
The ideologies/beliefs mentioned at the beginning of this article are only a starting point to the journey. They are in no way shape or from a claim to be a complete set of knowledge's that allow everyone to be able to navigate this earth. Are some things flawed? Probably. Do some things work for some and not others? Absolutely. But the major core belief at all of them is the belief that violence is never permitted, in all its facets to the individual liberty of the person. Its the only morally justifiable way to navigate life. This is in and of itself the most open and accepting philosophy of all life choices.
Individuals can do with their lives as they please, nobody is stopping you from doing that, but you because someone said some mean things to me about what I believe. Its about time some individuals get that we must remain steadfast in our mission. We don’t get there by being nice to everyone. We only get there by allowing everyone to do what they wish and not expecting others to bend to our will because you hurt my feelings.
The ultimate arbiter for what you should pick and choose is you the individual, don’t let others decide that for you. Don’t be a passenger in your own life, take that wheel and choose for yourself where you are headed. But if you're going to let someone who was mean to you stop you from using probably the greatest tool that a human has ever invented, then maybe there isn't hope for humanity after all. The one thing that I know for sure is that there is one thing that that can hinder you or augment you, that thing is choice. Embrace it.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ 3c7dc2c5:805642a8
2024-10-15 19:36:24
@ 3c7dc2c5:805642a8
2024-10-15 19:36:24🧠Quote(s) of the week:
'Bitcoin completed the stack. Which is why you should probably stack Bitcoin.'- Anilsaidso
🧡Bitcoin news🧡
On the 8th of October:
➡️The US Supreme Court has declined to review an appeal over the ownership of 69,370 Bitcoin seized from Silk Road, allowing the government to sell them. The U.S. Supreme Court declined to review a case concerning the ownership of 69,370 Bitcoin, worth $4.38 billion, seized by the government from the Silk Road marketplace. Battle Born Investments, which claimed rights to Bitcoin through a bankruptcy estate, had its appeal rejected after failing to convince lower courts of its claim. This decision clears the way for the U.S. government to sell the Bitcoin. Sources: Cointelegraph
A smart move by the U.S. government. They are poised to sell the only truly limited-supply store of value asset in the world for something it can and will just print more out of thin air itself. Logic, innit?!
➡️'YTD returns:
S&P500: +20.3%
Gold: +27.8%
Bitcoin: +48.2%
But if you only looked at Twitter, you’d think Bitcoin was performing the worst. It’s doing just fine. People are impatient and greedy.' - Bitcoin Isaiah
➡️Bitcoin rewards app Fold has filed an S-4 SEC IPO filing ahead of its planned merger with FTAC Emerald Acquisition.
If approved, Fold will be publicly listed on Nasdaq as "FLD." - Bitcoin News
➡️MicroStrategy holds more Bitcoin than the US government. Matter of fact, MicroStrategy is the world’s first Bitcoin Development Company.
'It holds ₿252,220 on its balance sheet and did $2.5bn in volume today. JP Morgan is America’s largest bank. It has almost $4 trillion of fiat assets on its balance sheet, and yet today it did just $1.5bn in volume. This is only 60% of MSTR’s trade. Saylor did more volume today than JPM and Coinbase (America’s largest crypto exchange) combined. Let that sink in. MicroStrategy is beginning to make Wall Street’s biggest names look small.' - Bit Strategy
No S&P 500 company has outperformed MicroStrategy since they began stacking Bitcoin. MicroStrategy owns 252,000 Bitcoin.
Only 83 entities in the ENTIRE WORLD can own 252,000 Bitcoin. This means MSTR has achieved something only 82 other individuals, institutions, countries, etc. can achieve.
On the 9th of October:
➡️German parliament member Joana Cotar says "With the right Bitcoin strategy you have the potential to transform a nation." Inflation is "stealing money from the people every month, Bitcoin is going to fix this"
On the 10th of October:
➡️On this day the Bitcoin Conference Amsterdam started. I only will share the most important bit of the whole conference, fellow Noderunner & Suriname Presidential candidate Maya Parbhoe: Suriname will be the next Bitcoin country!
I hope she will make it. She is a class act and with her determination, and passion for the people, but foremost her vision. I have no doubt she will lead the way and let Suriname thrive. How I love being part of the Noderunners group. The cult within the CULT!
➡️$9.57 trillion Charles Schwab survey shows almost half of its respondents plan to invest in Bitcoin and crypto ETFs
➡️'Ireland's Crime Bureau can't get access to drug dealer's $378m Bitcoin it "seized" in 2020. It has since gone up in value from $56m to $378. Not your keys, not your ₿itcoin!' -Bitcoin Archive
➡️'The SEC is suing Cumberland DRW, one of the largest crypto market makers, for selling assets like Solana as securities without registering as a securities dealer.' -Bitcoin News
1.5M BTC has been accumulated by whales (with >1K BTC on balance) over the last 6 months. There's really nothing to discuss here. What have you done over the last 6 months? Source
On the 11th of October:
➡️TD Bank has pleaded guilty and been hit with a record $3 billion fine for enabling drug cartel money laundering. Bank employees accepted bribes and overlooked blatant criminal activity by customers from Colombia and other regions. Criminals prefer US Dollars. Bitcoin is an open, transparent monetary network. I thought money laundering only happened in crypto… Will never cease to amaze me that these giga-settlements in tradfi happen, barely make news, and Elizabeth Warren in the US or Paul Tang here in Europe doesn't call for all banking to be shut down because of how its medium of choice for money launderers. Fascinating, innit?
➡️Metaplanet has purchased an additional ~108.99 Bitcoin for ¥1 billion at an average price of ¥9,174,396 per Bitcoin. As of October 11, Metaplanet holds ~748.50 Bitcoin acquired for ¥6.965 billion at an average price of ¥9,304,655 per Bitcoin.
➡️Global Money Supply hits an all-time high of $107 Trillion. It’s just a matter of time until Bitcoin follows. Two weeks ago I shared a great article by Lyn Alden on this topic. You might want to read that.
➡️Mt. Gox trustee postpones deadline to repay creditors by one year to October 2025, reducing sell pressure concerns for Bitcoin.
On the 12th of October:
➡️El Salvador buys back $940 million of its outstanding debt to reduce its debt burden and take advantage of favorable market conditions. The future of El Salvador is debt-free The IMF is in despair.
On the 13th of October:
Lyn Alden: Sometimes I make an asset class return chart specifically to show how poorly bonds performed over the past 5 years or whatever random timeframe, and instead it just accidentally shows how dramatically bitcoin outperformed everything.
➡️ Bitcoin on exchanges just hit a 5-year low. However, there are still 2.5M Bitcoins that need to be withdrawn!
On the 14th of October: ➡️I will end this Bitcoin segment with some quotes from Larry Fink, BlackRock CEO on Bitcoin. "We believe Bitcoin is an asset class in itself." "We're having conversations with institutions worldwide about allocations." "Bitcoin will become as big as the US housing market" -- Larry Fink. That market, the housing market, is currently 50 Trillion. Let's estimate 100 Trillion by 2040. That is 76x Bitcoin's 1.3 Trillion market cap. In other words, Bitcoin is going to $ 5 Million. Source: the most important person in finance on planet earth.
💸Traditional Finance / Macro:
On the 11th of October:
👉🏽'The S&P 500 is now up over 22% this year, marking the best year-to-date performance in 24 years.
This is already DOUBLE the average annual return since 1957. In one year, the index has added a whopping $13 trillion in market cap. If the current pace of the market rally continues, the S&P 500 is on track to record a 30.0% gain in 2024, the largest annual gain since 1997. That also would mark the third-largest annual return since 1975, when the S&P 500 finished the year up 37.2%.' -TKL
🏦Banks:
On the 2nd of October:
👉🏽no news
🌎Macro/Geopolitics:
On the 8th of October:
👉🏽The Tax Foundation analyzed the Kamala Harris Tax Plan and concluded that it would result in the loss of approximately 800K full-time jobs, a long-run wage decline of 1.2%, and a long-run GDP of negative 2%. Source: https://taxfoundation.org/research/all/federal/kamala-harris-tax-plan-2024/
'For the sake of completeness, the Tax Foundation is not blatantly partisan but its leaning is conservative and center-right. Still by its own findings Trump's economic plans would result in 684K job losses and 0.8% loss of GDP. Most estimates coming from other places are less favorable to Trump.'
Left, right...this is a feature of a system that requires billions of dollars in debt service.
👉🏽Hong Kong's Hang Seng index just crashed 9.4% today, posting its largest drop since 2008 and 2nd largest drop since 2000. Over the last 3 weeks, China's stock market was up nearly 30% on stimulus announcements.
The full thread you can find here: https://x.com/KobeissiLetter/status/1843630549379981400
👉🏽Despite strong headline growth in GDP figures several people are struggling and working multiple jobs just to pay bills. Millions of Americans are working multiple jobs to afford basic necessities. 'The number of people working MULTIPLE jobs in the US hit 8.66 million in September, a new record. This is ~300,000 above the peak seen before the pandemic and ~600,000 above the 2008 peak. Furthermore, the number of part-time jobs has jumped by ~3 million over the last 3 years to a near-record 28.2 million. Concerningly, full-time employment has declined by 1 million since November 2023. Multiple jobholders have been rapidly rising over the last few years as Americans are fighting record-high prices.' -TKL
👉🏽 Without a fiscal union the Euro is shaky and makes little sense long term. But no country will give up its sovereignty to make a fiscal union. Especially not the rich/successful countries. The EU and Euro are failed projects. 'All currency unions in history based on common monetary policy only failed and disappeared. The Euro can only survive long-term if there was common fiscal policy, given political landscape in Europe it’s close to impossible.' -Michael A Arouet
It comes down to the question - are Northern countries (e.g. DE and NL) willing to pay for early retirement in France, or low tax morale in Italy?... We all know the answer.
Anyway... socialism will never work though.
👉🏽In 2023 the wealth tax increase in Norway was expected to bring an additional $146M in yearly tax revenue.
Instead, individuals worth $54B left the country, leading to a loss of $594M in yearly wealth tax revenue. A net decrease of $448M+. Capital moves where it's treated best. And so do people. That is because rich people don't pay taxes.
The same thing happened in France when socialists increased the wealth tax in 2012. The most successful simply left.' -Michael A. Arouet
Just to show how bad things are in France. Within 15 years debt/GDP almost doubled. France is running a 6% fiscal deficit during good times despite the highest tax burden in Europe.
Without deep structural reforms, it will sooner or later face a debt crisis. Great article by the economist: https://archive.ph/qrWcT
France stares into a “colossal” budgetary abyss. A fragile new government must try to plug the hole.
On the 9th of October:
👉🏽The CBO (Congressional Budget Office) just released the estimated 2024 federal budget results. Adjusting for weekend payments, the actual 2024 expenses totaled $6.8T for a deficit of $ 1.83T. This is a ~12% deficit increase from 2023. The US deficit reached $1.83 trillion in Fiscal Year 2024, or 6.4% of GDP, the largest deficit since 2021.
According to CBO data released Tuesday, this is $139 billion higher than in FY 2023 and ~$400 billion above FY 2022 levels. This comes as government spending increased 10% year-over-year to $6.8 trillion. The largest outlays were Social Security, debt interest payments, and Medicare at $1.5 trillion, $950 billion, and $869 billion, respectively. Meanwhile, federal debt is up $2.2 trillion over the last year and hit a record $35.7 trillion this week. US deficit spending remains at crisis levels.
On the 10th of October:
👉🏽The Fed's worst nightmare has begun:
- Core CPI inflation rises to 3.3%, the first increase since March 2023
- 258,000 people filed for unemployment this week, above expectations of 230,000. That is the highest reading in 16 months. Once the September jobs report is revised sharply lower (as usually in 2023/2024), it will reveal the Fed's nightmare situation. Rising inflation with rising unemployment. No bueno.
👉🏽Trump is leading Kamala by 9.4% on Polymarket, the widest gap since Biden dropped out.
Trump is even leading in Wisconsin and Michigan.
👉🏽China's Central Bank launches $70 BILLION funding program to stimulate the economy and capital market: • Cut reserve req ratio, releasing ~1 trillion yuan • Lowered key interest rates • Reduced mortgage rates • Issued 1 trillion yuan in special sovereign bonds • 100B Yuan govt investment • Child subsidies for families By cutting the reserve requirement ratio and lowering interest rates, the government aims to boost liquidity and consumer confidence.
On the 11th of October:
👉🏽September PPI inflation RISES to 1.8%, above expectations of 1.6%. (first time since June), and last month's PPI inflation number was revised higher. Both Core PPI and CPI inflation are now officially back on the rise.
On the 12th of October:
👉🏽'The Federal Reserve’s balance sheet declined by $66 billion in September to $7.05 trillion, the lowest since September 2020.
Since April 2022, the Fed has shrunk its portfolio of assets by $1.92 trillion. This is 40% of the $4.80 trillion the central bank bought during the 2020-2022 pandemic response. For the first time in history, the Fed is simultaneously reducing its balance sheet and cutting rates. At the September Fed meeting, Fed Chair Powell emphasized that balance sheet reductions will continue.' -TKL
Great news! Meanwhile, though, the US money supply hit $21.17 trillion in August, the highest level since January 2023.
This also marks a fifth consecutive monthly increase in the US money supply. Over the last 10 months, the amount of US Dollars in circulation has jumped by a MASSIVE $484 billion.
In effect, the money supply is now just $548 billion below a new all-time high. After a brief decline, the quantity of money in the financial system is surging again raising concerns about another inflation wave.
🎁If you have made it this far I would like to give you a little gift:
Great interview with David Zell:
THE SEPARATION OF MONEY & STATE Peter McCormack & David Zell discuss the political landscape surrounding Bitcoin & its role as an insurance policy for individuals & nation-states:
https://www.youtube.com/watch?v=y39I7iQUL6U
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀ ⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 8ce092d8:950c24ad
2024-02-04 23:35:07
@ 8ce092d8:950c24ad
2024-02-04 23:35:07Overview
- Introduction
- Model Types
- Training (Data Collection and Config Settings)
- Probability Viewing: AI Inspector
- Match
- Cheat Sheet
I. Introduction
AI Arena is the first game that combines human and artificial intelligence collaboration.
AI learns your skills through "imitation learning."
Official Resources
- Official Documentation (Must Read): Everything You Need to Know About AI Arena
Watch the 2-minute video in the documentation to quickly understand the basic flow of the game. 2. Official Play-2-Airdrop competition FAQ Site https://aiarena.notion.site/aiarena/Gateway-to-the-Arena-52145e990925499d95f2fadb18a24ab0 3. Official Discord (Must Join): https://discord.gg/aiarenaplaytest for the latest announcements or seeking help. The team will also have a exclusive channel there. 4. Official YouTube: https://www.youtube.com/@aiarena because the game has built-in tutorials, you can choose to watch videos.
What is this game about?
- Although categorized as a platform fighting game, the core is a probability-based strategy game.
- Warriors take actions based on probabilities on the AI Inspector dashboard, competing against opponents.
- The game does not allow direct manual input of probabilities for each area but inputs information through data collection and establishes models by adjusting parameters.
- Data collection emulates fighting games, but training can be completed using a Dummy As long as you can complete the in-game tutorial, you can master the game controls.
II. Model Types
Before training, there are three model types to choose from: Simple Model Type, Original Model Type, and Advanced Model Type.
It is recommended to try the Advanced Model Type after completing at least one complete training with the Simple Model Type and gaining some understanding of the game.

Simple Model Type
The Simple Model is akin to completing a form, and the training session is comparable to filling various sections of that form.
This model has 30 buckets. Each bucket can be seen as telling the warrior what action to take in a specific situation. There are 30 buckets, meaning 30 different scenarios. Within the same bucket, the probabilities for direction or action are the same.
For example: What should I do when I'm off-stage — refer to the "Recovery (you off-stage)" bucket.
For all buckets, refer to this official documentation:
https://docs.aiarena.io/arenadex/game-mechanics/tabular-model-v2
Video (no sound): The entire training process for all buckets
https://youtu.be/1rfRa3WjWEA
Game version 2024.1.10. The method of saving is outdated. Please refer to the game updates.
Advanced Model Type
The "Original Model Type" and "Advanced Model Type" are based on Machine Learning, which is commonly referred to as combining with AI.
The Original Model Type consists of only one bucket, representing the entire map. If you want the AI to learn different scenarios, you need to choose a "Focus Area" to let the warrior know where to focus. A single bucket means that a slight modification can have a widespread impact on the entire model. This is where the "Advanced Model Type" comes in.
The "Advanced Model Type" can be seen as a combination of the "Original Model Type" and the "Simple Model Type". The Advanced Model Type divides the map into 8 buckets. Each bucket can use many "Focus Area." For a detailed explanation of the 8 buckets and different Focus Areas, please refer to the tutorial page (accessible in the Advanced Model Type, after completing a training session, at the top left of the Advanced Config, click on "Tutorial").

III. Training (Data Collection and Config Settings)
Training Process:
- Collect Data
- Set Parameters, Train, and Save
- Repeat Step 1 until the Model is Complete
Training the Simple Model Type is the easiest to start with; refer to the video above for a detailed process.
Training the Advanced Model Type offers more possibilities through the combination of "Focus Area" parameters, providing a higher upper limit. While the Original Model Type has great potential, it's harder to control. Therefore, this section focuses on the "Advanced Model Type."
1. What Kind of Data to Collect
- High-Quality Data: Collect purposeful data. Garbage in, garbage out. Only collect the necessary data; don't collect randomly. It's recommended to use Dummy to collect data. However, don't pursue perfection; through parameter adjustments, AI has a certain level of fault tolerance.
- Balanced Data: Balance your dataset. In simple terms, if you complete actions on the left side a certain number of times, also complete a similar number on the right side. While data imbalance can be addressed through parameter adjustments (see below), it's advised not to have this issue during data collection.
- Moderate Amount: A single training will include many individual actions. Collect data for each action 1-10 times. Personally, it's recommended to collect data 2-3 times for a single action. If the effect of a single training is not clear, conduct a second (or even third) training with the same content, but with different parameter settings.
2. What to Collect (and Focus Area Selection)
Game actions mimic fighting games, consisting of 4 directions + 6 states (Idle, Jump, Attack, Grab, Special, Shield). Directions can be combined into ↗, ↘, etc. These directions and states can then be combined into different actions.
To make "Focus Area" effective, you need to collect data in training that matches these parameters. For example, for "Distance to Opponent", you need to collect data when close to the opponent and also when far away. * Note: While you can split into multiple training sessions, it's most effective to cover different situations within a single training.
Refer to the Simple Config, categorize the actions you want to collect, and based on the game scenario, classify them into two categories: "Movement" and "Combat."
Movement-Based Actions
Action Collection
When the warrior is offstage, regardless of where the opponent is, we require the warrior to return to the stage to prevent self-destruction.
This involves 3 aerial buckets: 5 (Near Blast Zone), 7 (Under Stage), and 8 (Side Of Stage).

* Note: The background comes from the Tutorial mentioned earlier. The arrows in the image indicate the direction of the action and are for reference only. * Note: Action collection should be clean; do not collect actions that involve leaving the stage.
Config Settings
In the Simple Config, you can directly choose "Movement" in it. However, for better customization, it's recommended to use the Advanced Config directly. - Intensity: The method for setting Intensity will be introduced separately later. - Buckets: As shown in the image, choose the bucket you are training. - Focus Area: Position-based parameters: - Your position (must) - Raycast Platform Distance, Raycast Platform Type (optional, generally choose these in Bucket 7)
Combat-Based Actions
The goal is to direct attacks quickly and effectively towards the opponent, which is the core of game strategy.
This involves 5 buckets: - 2 regular situations - In the air: 6 (Safe Zone) - On the ground: 4 (Opponent Active) - 3 special situations on the ground: - 1 Projectile Active - 2 Opponent Knockback - 3 Opponent Stunned
2 Regular Situations
In the in-game tutorial, we learned how to perform horizontal attacks. However, in the actual game, directions expand to 8 dimensions. Imagine having 8 relative positions available for launching hits against the opponent. Our task is to design what action to use for attack or defense at each relative position.
Focus Area - Basic (generally select all) - Angle to opponent
- Distance to opponent - Discrete Distance: Choosing this option helps better differentiate between closer and farther distances from the opponent. As shown in the image, red indicates a relatively close distance, and green indicates a relatively distant distance.- Advanced: Other commonly used parameters
- Direction: different facings to opponent
- Your Elemental Gauge and Discrete Elementals: Considering the special's charge
- Opponent action: The warrior will react based on the opponent's different actions.
- Your action: Your previous action. Choose this if teaching combos.
3 Special Situations on the Ground
Projectile Active, Opponent Stunned, Opponent Knockback These three buckets can be referenced in the Simple Model Type video. The parameter settings approach is the same as Opponent Active/Safe Zone.
For Projectile Active, in addition to the parameters based on combat, to track the projectile, you also need to select "Raycast Projectile Distance" and "Raycast Projectile On Target."
3. Setting "Intensity"
Resources
- The "Tutorial" mentioned earlier explains these parameters.
- Official Config Document (2022.12.24): https://docs.google.com/document/d/1adXwvDHEnrVZ5bUClWQoBQ8ETrSSKgG5q48YrogaFJs/edit
TL;DR:
Epochs: - Adjust to fewer epochs if learning is insufficient, increase for more learning.
Batch Size: - Set to the minimum (16) if data is precise but unbalanced, or just want it to learn fast - Increase (e.g., 64) if data is slightly imprecise but balanced. - If both imprecise and unbalanced, consider retraining.
Learning Rate: - Maximize (0.01) for more learning but a risk of forgetting past knowledge. - Minimize for more accurate learning with less impact on previous knowledge.
Lambda: - Reduce for prioritizing learning new things.
Data Cleaning: - Enable "Remove Sparsity" unless you want AI to learn idleness. - For special cases, like teaching the warrior to use special moves when idle, refer to this tutorial video: https://discord.com/channels/1140682688651612291/1140683283626201098/1195467295913431111
Personal Experience: - Initial training with settings: 125 epochs, batch size 16, learning rate 0.01, lambda 0, data cleaning enabled. - Prioritize Multistream, sometimes use Oversampling. - Fine-tune subsequent training based on the mentioned theories.
IV. Probability Viewing: AI Inspector
The dashboard consists of "Direction + Action." Above the dashboard, you can see the "Next Action" – the action the warrior will take in its current state. The higher the probability, the more likely the warrior is to perform that action, indicating a quicker reaction. It's essential to note that when checking the Direction, the one with the highest visual representation may not have the highest numerical value. To determine the actual value, hover the mouse over the graphical representation, as shown below, where the highest direction is "Idle."

In the map, you can drag the warrior to view the probabilities of the warrior in different positions. Right-click on the warrior with the mouse to change the warrior's facing. The status bar below can change the warrior's state on the map.

When training the "Opponent Stunned, Opponent Knockback" bucket, you need to select the status below the opponent's status bar. If you are focusing on "Opponent action" in the Focus Zone, choose the action in the opponent's status bar. If you are focusing on "Your action" in the Focus Zone, choose the action in your own status bar. When training the "Projectile Active" Bucket, drag the projectile on the right side of the dashboard to check the status.
Next
The higher the probability, the faster the reaction. However, be cautious when the action probability reaches 100%. This may cause the warrior to be in a special case of "State Transition," resulting in unnecessary "Idle" states.
Explanation: In each state a fighter is in, there are different "possible transitions". For example, from falling state you cannot do low sweep because low sweep requires you to be on the ground. For the shield state, we do not allow you to directly transition to headbutt. So to do headbutt you have to first exit to another state and then do it from there (assuming that state allows you to do headbutt). This is the reason the fighter runs because "run" action is a valid state transition from shield. Source
V. Learn from Matches
After completing all the training, your model is preliminarily finished—congratulations! The warrior will step onto the arena alone and embark on its debut!
Next, we will learn about the strengths and weaknesses of the warrior from battles to continue refining the warrior's model.
In matches, besides appreciating the performance, pay attention to the following:
-
Movement, i.e., Off the Stage: Observe how the warrior gets eliminated. Is it due to issues in the action settings at a certain position, or is it a normal death caused by a high percentage? The former is what we need to avoid and optimize.
-
Combat: Analyze both sides' actions carefully. Observe which actions you and the opponent used in different states. Check which of your hits are less effective, and how does the opponent handle different actions, etc.
The approach to battle analysis is similar to the thought process in the "Training", helping to have a more comprehensive understanding of the warrior's performance and making targeted improvements.
VI. Cheat Sheet
Training 1. Click "Collect" to collect actions. 2. "Map - Data Limit" is more user-friendly. Most players perform initial training on the "Arena" map. 3. Switch between the warrior and the dummy: Tab key (keyboard) / Home key (controller). 4. Use "Collect" to make the opponent loop a set of actions. 5. Instantly move the warrior to a specific location: Click "Settings" - SPAWN - Choose the desired location on the map - On. Press the Enter key (keyboard) / Start key (controller) during training.
Inspector 1. Right-click on the fighter to change their direction. Drag the fighter and observe the changes in different positions and directions. 2. When satisfied with the training, click "Save." 3. In "Sparring" and "Simulation," use "Current Working Model." 4. If satisfied with a model, then click "compete." The model used in the rankings is the one marked as "competing."
Sparring / Ranked 1. Use the Throneroom map only for the top 2 or top 10 rankings. 2. There is a 30-second cooldown between matches. The replays are played for any match. Once the battle begins, you can see the winner on the leaderboard or by right-clicking the page - Inspect - Console. Also, if you encounter any errors or bugs, please send screenshots of the console to the Discord server.
Good luck! See you on the arena!
-
 @ 6ad3e2a3:c90b7740
2024-10-15 17:07:55
@ 6ad3e2a3:c90b7740
2024-10-15 17:07:55I was at a yoga teacher training 14 years ago during which the topic of positive thinking came up. A few different women (it was almost all women) spoke about how much “positive thinking” had affected their lives for the better. When they were done, I raised my hand and said something to the effect of:
“You know there were six million Jews killed in the Holocaust, and the one percent most positive-thinking among them were 60,000, and it didn’t help them much. Even the one percent of the one percent most positive who must have been very very positive, were 600, and they too got murdered alongside everyone they knew.”
I don’t remember what if anything anyone said after that, only that it pretty much killed the “kumbaya” vibe they had been cultivating, which I guess was my aim, since it always struck me as phony.
. . .
I was talking to a friend last week about a book I was reading, called “Becoming Supernatural.” It’s a bit “self-helpy” for my tastes, but the author makes some interesting arguments. Essentially that matter is mostly empty space because atoms are mostly space (the nucleus, which has virtually all the mass, is tiny compared to the entire atom.) Everything is space, or more precisely electromagnetic fields, and the subatomic particles inside the matter are actually just waves until they are observed. “Reality” is mostly just waves which we solidify by observation, and the same is true for our internal reality.
When we’re in a contemplative state, just observing, not identifying or planning, it’s like we’re an unobserved wave, and it’s only when we snap back to “reality” of “I’m a man,” “I’m a woman” or “I’ve got a boring meeting at 10 am” that we re-particle-ize, so to speak. That you are in a state of possibility (wave) when meditating, and you are the particle when you identify with the specifics of yourself or your life.
And so you wind up with an identity that’s full of beliefs about yourself, your plans and your history, and those notions solidify themselves in your body in terms of stress, tension, etc. via biochemistry, and that biochemistry feeds your thoughts which in turn feed more biochemistry, and you become habituated to your patterns, your history, your identity and cut yourself off from new choices and possibilities. As I said, a bit self-helpy for me (and maybe I’m missing something in my paraphrasing), but an interesting way to conceptualize it.
So I’m talking to my friend about this idea of creating your own experience, so to speak, by not, for example, imagining how my run at the track will go like I normally would but simply committing to it, but without a picture, story or expectation. You just walk out the door, a couple blocks to the subway, observe the people, the cobblestones, etc. And I don’t mean imagining doing that as I am now while typing this, but each step as it’s happening. And in this way you create a different experience than the habitual one where you’re dreading the run and strategizing how to make its prospect less painful.
And he agreed that maybe we can create our own experience. Of course, that was when I told him the story of the yoga class and the 600 super positive Jews on their way to the gas chamber.
And he said, “Maybe the positive ones had already left.”
. . .
Growing up Jewish in New York, I was exposed to the sentiment that Holocaust 2.0 was maybe not imminent but surely something about which I should be worried. We weren’t religious, and I never experienced any kind of antisemitism (I’ve seen and heard some lately on social media and even in real life on occasion, but nothing that’s affected my life in any way.) And I always rejected that idea that I should be specifically worried about it.
But — and I can’t say if the Holocaust paranoia drove this — I’ve always thought about the people that died not just in the Holocaust, but also in wars or even via violence on the street. So many humans in history have met their ends in gruesome ways, in prison, in the gutter or at the hands of others. I’ve always had this sense that it could easily be me or my family as there was no basis for believing it couldn’t be so.
I had only a small taste of violence growing up, getting mugged, punched in the face on the street a couple times, chased by a gang with sticks and bats. I never got seriously injured, and in fact no one I know did, either, but there was a sense of menace back then that it could happen.
On the one hand, you could say if it happens it happens, and hopefully it doesn’t come to that, and let it go, but it raises the question of how much one should prepare, at what point should you leave. If the positive thinking Jews (and by positive thinking I don’t mean being in denial about what was going on in Germany, but in the sense of willing themselves a good life for which leaving was necessary) left, maybe my mental model was wrong, and those girls in my yoga class, naive though they might have been, were onto something.
Instead of seeing oneself as a statistic, at the mercy of probability given a shifting (often for the worse) environment, a wave waiting for the events of life to particle-ize oneself, so to speak, into the lottery of history, one might imagine a form of higher agency. Unlike ordinary agency which is the power to respond to one’s environment, maybe one creates it, whether via default (lottery of history) or by choice.
This has profound implications because it makes you not only responsible for how you act upon the world but also for how the world acts upon you. There is nothing to fear from what might happen because you yourself created the conditions, consciously or by default. And while there might be great suffering, real horrors and unspeakable cruelty, those episodes are all mutually brought into being.
Obviously that is not to say that there are no moral distinctions, that the Jews who went to the gas chamber were as responsible as the nazis who forced them. The default — letting the lottery of history play out — still involves ordinary agency and the responsibilities inherent to it. One has merely opted into ordinary agency (and its probability distribution) by not discovering the means of reality production at its root. And because most people are neither exposed to this possibility nor encouraged to seek it, they experience only the default. (And some even less than that as society encourages helplessness and increasingly confers status on those it deems victims, but that’s a topic for another essay.)
. . .
I don’t want to go too far afield trying to explain or describe what creating one’s own reality consists in or how one might go about it. I am no expert in this, and I’m not even positive it can be done in the sense I’m suggesting after reading (and likely misinterpreting) a book. Only that my old probabilistic view of the world wherein the influence you have with respect to your conditions was modest might be wrong. That even the idea it’s possible to opt out of virtually anything is more than just intriguing but liberating.
-
 @ bcea2b98:7ccef3c9
2024-10-15 16:37:10
@ bcea2b98:7ccef3c9
2024-10-15 16:37:10I've always been interested in Eastern philosophies and Stoicism. When I first heard about Bitcoin, it seemed to align well with the beliefs, ideas, and lifestyle I was already living. I try my best to be self-sovereign, practice a low-time preference, and delayed gratification. I've also learned so much about Linux, servers, etc...
I'm curious to hear what skills you have gained from Bitcoin, or how it has changed or aligns with your lifestyle.
originally posted at https://stacker.news/items/724982
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ a012dc82:6458a70d
2024-10-15 14:20:46
@ a012dc82:6458a70d
2024-10-15 14:20:46Table Of Content
-
The Merger Deal: A Strategic Move
-
Growth and Adoption: The Driving Forces
-
Trading Details: Accessibility for Investors
-
Bitcoin Depot: A Major Player in the Crypto ATM Market
-
Conclusion
-
FAQ
In a significant development for the cryptocurrency industry, Bitcoin Depot, one of the largest cryptocurrency ATM firms in the United States, has announced that it will go public on Nasdaq starting July 3. This move marks a significant milestone for the crypto industry, reflecting the growing acceptance and mainstream adoption of digital currencies. The listing of Bitcoin Depot on a major stock exchange like Nasdaq signifies the increasing integration of cryptocurrencies into the traditional financial system.
The Merger Deal: A Strategic Move
The public listing of Bitcoin Depot follows the closing of a merger deal with fintech firm GSR II Meteora Acquisition Corporation. GSR II Meteora Acquisition Corporation acted as a special purpose acquisition company (SPAC) for Bitcoin Depot. The deal, which was first reported in August 2022, cost $885 million. This merger is expected to allow investors exposure to Bitcoin Depot’s common stock on the Nasdaq. The strategic merger is seen as a significant step towards providing mainstream investors with more opportunities to invest in the burgeoning cryptocurrency market.
Growth and Adoption: The Driving Forces
According to Bitcoin Depot's founder and CEO, Brandon Mintz, the merger deal was aimed at supporting "numerous growth opportunities" and promoting the adoption of Bitcoin (BTC) in North America. Mintz believes that this move will not only provide a boost to Bitcoin Depot but also contribute to the wider acceptance and use of Bitcoin and other cryptocurrencies. The public listing is expected to provide the necessary capital for Bitcoin Depot to expand its operations and reach, thereby promoting the adoption of Bitcoin.
Trading Details: Accessibility for Investors
Investors interested in Bitcoin Depot will be able to find shares of the company under the ticker symbols BTM and BTMWW for its common stock and public warrants, respectively, on Nasdaq. This public listing provides an opportunity for investors to gain exposure to the burgeoning cryptocurrency market through a regulated and widely recognized exchange. The listing of Bitcoin Depot's shares on Nasdaq will provide a new and accessible avenue for investors to participate in the growth of the cryptocurrency industry.
Bitcoin Depot: A Major Player in the Crypto ATM Market
Founded in 2016, Bitcoin Depot has grown to become one of the biggest crypto ATM firms in North America. According to its website, the company boasts more than 9,130 locations. Bitcoin Depot's ATMs allow users to buy and sell cryptocurrencies like Bitcoin, providing a tangible touchpoint for digital currencies. The company's extensive network of ATMs has played a crucial role in making cryptocurrencies more accessible to the general public.
Conclusion
The public listing of Bitcoin Depot on Nasdaq is a significant step forward for the cryptocurrency industry. It not only underscores the growing acceptance of cryptocurrencies but also provides a new avenue for investors to gain exposure to this dynamic and rapidly evolving market. As Bitcoin Depot and other crypto-related firms continue to make inroads into traditional financial markets, the future of digital currencies looks increasingly promising. The listing of Bitcoin Depot is likely to encourage other cryptocurrency companies to consider public listings, thereby further integrating the cryptocurrency industry with traditional finance.
FAQ
What is Bitcoin Depot? Bitcoin Depot is one of the largest cryptocurrency ATM firms in the United States. Founded in 2016, it allows users to buy and sell cryptocurrencies like Bitcoin through its network of over 9,130 ATMs.
What is the recent development with Bitcoin Depot? Bitcoin Depot has announced that it will go public on Nasdaq starting July 3, following the closing of a merger deal with fintech firm GSR II Meteora Acquisition Corporation.
What is the purpose of the merger deal? According to Bitcoin Depot's founder and CEO, Brandon Mintz, the merger deal was aimed at supporting "numerous growth opportunities" and promoting the adoption of Bitcoin in North America.
What does Bitcoin Depot's public listing signify? The public listing of Bitcoin Depot on Nasdaq is a significant step forward for the cryptocurrency industry. It reflects the growing acceptance and mainstream adoption of digital currencies and provides a new avenue for investors to gain exposure to the cryptocurrency market.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 34f1aaa6:836e3cd6
2024-10-15 13:28:23
@ 34f1aaa6:836e3cd6
2024-10-15 13:28:23Bitcoiners and Libertarians in India are in the minority - ridiculed, dismissed and laughed at as being a bunch of irrelevant nuts being influenced and manipulated by some nonsensical 'western' ideas like natural rights, natural law, economic freedom, individual liberty and financial sovereignty.
This will not always be the case.
A mistake that those who dismiss us make is to think that folks like us are merely influenced by lies, deceit, propaganda and manipulation.
Rather, what we simply did was to search for truth, beauty, morality and goodness. We tried to articulate them and live with the goal of their achievement. Doing this took us down a rabbit hole that went beyond just Bitcoin and Libertarianism as an alternative asset and a political ideology respectively. They slowly turned into a way of life for us as we started improving and educating ourselves individually. We understood what fiat money, statism and collectivism does to our minds, wealth, culture, society and economy. We recognised the subtle lies and deceit that pervades our lives.
A bigger mistake would be to think that ideas of natural rights, natural law, individual liberty, economic freedom and financial sovereignty are nonsensical or 'western' in character.
Natural rights to life, liberty and property derived from the natural law are universal to every human being. They are built on the foundations of reason and logic. They exist even if a coercive or manipulative authority proclaims that they don't, be it a state leader, religious zealot or university intellectual. From this foundation, the push towards individual liberty, economic freedom and financial sovereignty emerges. There is no stronger foundation than that of reason and logic.
The only criticism that can be valid against people like us would be that we are 'irrelevant' or less in number.
But being less in number cannot undermine the kind of impact that people like us can have. For the first time in the subcontinent's long history, individuals who advocate for natural rights and natural law have a chance of becoming financially sovereign and economically free, thanks to Bitcoin and the internet. These tools help us clear a path on which we can pursue our self-interests, aims, needs and goals in a way that is moral and ethical, without relying on the State apparatus, which requires us to lie, cheat, coerce, bribe or manipulate. We can form economic relationships based on trust and voluntary cooperation and make economic decisions based on capital accumulation and low time preference savings and investment.
We have the ability to create what Vaclav Havel would call a 'parallelopolis' - a parallel and moral society with an economy that is outside the realm of State control and regulatory capture. Feasibly so.
We have the ability to create a property base on which we can build our own lives first and then look to build a better society after. It won't be long before people start noticing what we are doing and listening to what we are saying.
The possibility and capability of people like us, less in number as we may be, to create such a property base is the reason we cannot be ridiculed, dismissed or laughed at.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 460c25e6:ef85065c
2024-10-15 12:49:55
@ 460c25e6:ef85065c
2024-10-15 12:49:55NIPs (Nostr Implementation Possibilities) are technical specifications that Nostr developers create to define how specific event types and tags are used. These can be written before or after the feature is implemented and often go through multiple revisions before becoming stable enough to matter. Once two or more clients fully implement the proposal, it is merged into the main repository. This process ensures that while new ideas are encouraged, they are also rigorously reviewed and tested.
There are generally two paths for NIPs: 1. New Ideas, when developers just have a hunch on a new solution and want to quickly write something up to gather feedback from the community. These are my favorite NIPs because they generally introduce a new way of thinking about a problem we are all having. And because they are not just a general solution, but a specific proposal, it allows us to see the entire picture in just a few paragraphs. Even though they are my favorite, they are quite "green" and usually spur 2-3 separate solutions in following PRs by different authors. 2. Existing implementations that need to explain what they are doing. These happen when a client is already running the code in production and simply wants to explain to the rest of the community how to generate and interpret the events the client is creating. These NIPs start much more stable than the former and allow for fewer changes, but because there is already an implementation available, it's a market-tested solution that might just need a few adjustments before others start implementing it.
Well-written specs ensure clarity, reduce ambiguity, and help developers implement the proposal consistently. The text should be VERY short, precise, prescriptive, and actionable by other devs. Start by introducing the new kind or tag in the first sentence and jump straight into a mockup of how the event looks like. The mockup should be self-explanatory and provide clues to what the remaining of the document will talk about. Some folks like to add long/verbose introductions, conclusions, and discussions of the reasons why the NIP is needed or why certain features are there. But those are largely unnecessary and are more appropriate to be placed in the body of the Pull Request descriptor.
Start your NIP with the following template:
``` NIP-
====== </h2> <p><code>draft</code> <code>optional</code></p> <p>Event kind <new kind> defines <whatever it does>. Tags <one or two of the most important ones> <describe what they do>. As an example: </p> <p><code>`jsonc { "kind": <your kind>, "tags": [ <your tags> ], "content": "", //... }</code> `</p> <p>Relays MUST...</p> <p>Clients MUST... </p> <h2><Details 1></h2> <h2><Details 2></h2> <h2><How to find them></h2> <p>```</p> <p>Your number for the NIP is irrelevant. Just pick a random number that is available so that you can fork the repo, create a file with that name, and start writing. This number will likely change once the NIP is merged. </p> <p>The NIPs title must be self-explanatory and short. If it helps, try to imagine which name would be best to add to the list of NIPs on the readme.md file. Same for event type names. Picture something that is short, unique and that devs can just remove the space to have a class name. </p> <p>The <code>draft</code> <code>optional</code> tags are there because unless you are working on NIP-01, everything is draft and everything is optional. If you want to write a mandatory NIP, you better make sure your text is so good that it can be added to <code>01.md</code> directly without overcomplicating the protocol. </p> <p>Start by describing the new event type, what it does and its main tags. Show the mockup and then start introducing all the other tags and how clients and relays should behave when implementing it. Use the words MUST, SHOULD, MAY, SHOULD NOT, and MUST NOT to define the mandatory behaviors of those declaring compliance with the NIP. </p> <p>Keep it simple. The specification should be designed to ensure that different clients, relays, and services can implement it without requiring substantial changes to their existing infrastructure. Ideally, devs should be able to implement the entire NIP from near scratch in just a few hours. Don't use jargon. Don't declare a vocabulary of words. Use simple words that anyone can understand and quickly code a demo of all the features in the NIP. They can learn about your reasons as they develop their implementation. </p> <p>Write expecting buggy implementations. The protocol must be resilient to varying implementations and network conditions, and gracefully handle coding errors or random gibberish. You want to promote a defensive design that anticipates misguided implementations, avoids breaking changes, and maximizes compatibility across the ecosystem. What happens if there are two tags with the same name? What happens if events that have missing tags are found? Buggy implementations will exist. The writing and reading clients are generally different and must be ready for anything that shows up on each side. </p> <p>Avoid abstractions, extensible and modular designs. Yes, they can be hidden underneath your text, but writing for them is a mistake and just overcomplicates things. Write for a specific use case and close all possible options to the items/features declared in the text. Make sure you are implementing those. There is no point in declaring things that are not going to be used in the short term. We can always add more in the future and we don't need a recipe on how to add more later. </p> <p>Label your relay hosts, setting kinds, and other data management necessities. Every NIP has a way to find out the user's preferred relay associated with the use case. Sometimes it's through a relay hint others through a separate event kind that just lists the user's home relays or contains a list of "following" events designed for the use case. Each NIP can create their own way of finding events.</p> <p>You cannot add new root fields. Use tags instead. Root fields are special and require changes to the core protocol everyone implements. Any new field will take years to come to reality. </p> <p>Once you propose an idea, try not to change too much. It will take time for other devs to wrap their minds around it. If you keep changing it, even if those changes reflect the request of the reviewers in the PR, it just confuses everyone. Sometimes things change so much that it is worth doing two PRs with separate specifications that solve the same problem. That allows devs to analyze the two propositions side by side and decide which one is better. </p> <p>Always add a test case or an example. This is an absolute requirement if the NIP is complex, like a new encryption scheme. But even for simpler NIPs, test cases help devs to quickly verify if their implementations meet the minimum standard for compliance. They not only add peace of mind, but they also provide some welcoming dopamine when a new dev is trying to implement your NIP. </p> <p>Managing state is hard. Doing it with different implementations and hosting them in separate relays is even harder. If your NIP has multiple events to manage state, like group administration actions (add/remove member, change names/icons, invite/reporting events) try to structure them in a way that devs can quickly see the state machine of all possible state changes. </p> <p>Specify data formats explicitly. Clearly define the format of all data fields, including type (e.g., string, integer), encoding (e.g., base64, hex), and structure (e.g., array, object). Specify constraints like length limits, valid characters, and optional/required fields. Tags are case-sensitive. Avoid having to specify new encodings, but if you do, make sure to include test cases that encompass all potential cases. </p> <p>It's ok to not propose the most efficient way of solving the problem. A simple but slightly less efficient design is preferred over a complex but more efficient one. We already use hex and base64 codes to represent binary bytes in JSON, which wastes 25-50% of space. That level of waste is ok if the solution becomes simpler to code. </p> <p>It's not about you. You may think you must convince everyone that your particular way of solving the problem is the best and get some ego points with yourself. While some of that is beneficial to the debate, be open-minded to the other possible solutions. Once merged, the NIP is not yours anymore. Anyone can change in any way they see fit. If your work is great, people will remember your name. If it just got the conversation started to become something completely different from what you proposed, they will also remember you. </p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs93syf4xs2emchhqa6h5zcuu9azkau77rn4u63670t07gtz8u3j3szyprqcf0xst760qet2tglytfay2e3wmvh9asdehpjztkceyh0s5r9c0seer6" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>Thoughts on Nostr key management</h1> <p>On <a href="nostr:naddr1qqyrgceh89nxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ctgmx78">Why I don't like NIP-26 as a solution for key management</a> I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.</p> <p>Here are some ideas that work in tandem:</p> <ul> <li><a href="https://github.com/nostr-protocol/nips/blob/master/41.md">NIP-41</a> (stateless key invalidation)</li> <li><a href="https://github.com/nostr-protocol/nips/blob/master/46.md">NIP-46</a> (Nostr Connect)</li> <li><a href="https://github.com/nostr-protocol/nips/blob/master/07.md">NIP-07</a> (signer browser extension)</li> <li><a href="https://lnbits.github.io/nostr-signing-device/installer/">Connected hardware signing devices</a></li> <li>other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically</li> <li>there are probably many other ideas</li> </ul> <p>Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that</p> <ul> <li>For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;</li> <li>Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;</li> <li>Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.</li> <li>For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.</li> </ul> <p>We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.</p> <hr /> <p>One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsx8ttkgfvr9jpweajnv0gjwcqhu6d4jy9r6hn6c42lls94mwdfh9qzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6wygu6r" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsx8ttkgfvr9jpweajnv0gjwcqhu6d4jy9r6hn6c42lls94mwdfh9qzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6wygu6r" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsx8ttkgfvr9jpweajnv0gjwcqhu6d4jy9r6hn6c42lls94mwdfh9qzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6wygu6r" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsx8ttkgfvr9jpweajnv0gjwcqhu6d4jy9r6hn6c42lls94mwdfh9qzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6wygu6r" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ dfedf503:02288a26 <div class="time" style="margin-left: auto;">2024-10-15 03:39:46</div> </div> <div> <p>The concept and significance of dew point In meteorology, the <strong><em><a href="https://www.renkeer.com/dew-point/">dew point</a></em></strong> is the temperature at which the gaseous water in the air becomes saturated and condenses into liquid water at a fixed pressure. At this temperature, condensed water floating in the air is called fog, and when it sticks to a solid surface, it is called dew, hence the name dew point. The relationship between dew point and relative humidity</p> <p>In the compressor industry, the concepts of pressure dew point (PDP) and atmospheric dew point (ADP) are often used. The result of compression is that there is more water per unit volume of air, resulting in condensation. Ambient air contains water vapor, which is high in high temperature and low in low temperature. We use relative humidity (RH) to express the ratio of the actual water content in the air to the maximum water content. Because relative humidity is related to temperature, we prefer to use the term dew point, which is independent of any other parameter and can easily express the temperature when condensation occurs. <img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/dfedf50375373ce59d1a50e1ea969d3b9aad2c207e49b5abbb3aafb002288a26/files/1728963327737-YAKIHONNES3.png" /> Measurement and application of dew point In industry, the measurement of dew point is very important. For example, in winter, because the outdoor temperature is lower and the indoor humidity is hotter, the air will condensation on the window glass, making the window glass blurred. If the dehumidifier is turned on indoors and the indoor moisture is gradually removed, then although the outdoor temperature is still the same, we will find that the dew on the window glass will slowly disappear. Dew point measurements can help us understand the moisture content of the air, which is critical for many industrial processes.</p> <p>The relationship between dew point and weather phenomena In nature, dew points are associated with many weather phenomena. For example, dew forms during the warm season when ground objects are cooled by intense radiation at night. The temperature at which the air becomes saturated by cooling is called the dew point temperature. After it drops to the dew point, excess water vapor escapes. Because the temperature is above 0°C, this excess water vapor condenses into water droplets and sticks to surface objects.</p> <p>To sum up, dew point is an important meteorological parameter, which is not only related to our daily life, such as weather forecast and dressing index, but also has a profound impact on industrial production and scientific research. Through the measurement and analysis of dew point, we can better understand and predict weather changes, as well as optimize industrial production processes.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsx4wd2txu2jlmd79jn8eqjpp9hp8a3axzhhsnyhdnl74xka935h3czyr07magrw5mneevarfgwr65kn5ae4tfvyplynddthva2lvqz9z9zv3xt782" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsx4wd2txu2jlmd79jn8eqjpp9hp8a3axzhhsnyhdnl74xka935h3czyr07magrw5mneevarfgwr65kn5ae4tfvyplynddthva2lvqz9z9zv3xt782" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsx4wd2txu2jlmd79jn8eqjpp9hp8a3axzhhsnyhdnl74xka935h3czyr07magrw5mneevarfgwr65kn5ae4tfvyplynddthva2lvqz9z9zv3xt782" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsx4wd2txu2jlmd79jn8eqjpp9hp8a3axzhhsnyhdnl74xka935h3czyr07magrw5mneevarfgwr65kn5ae4tfvyplynddthva2lvqz9z9zv3xt782" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>IPFS problems: Shitcoinery</h1> <p>IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.</p> <p>The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.</p> <p>Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.</p> <h2>See also</h2> <ul> <li><a href="nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4">Bitcoin</a>, the only non-shitcoin</li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs96w7rwrp09puzvsh82ldu8vvq9vtut477ury5ay9cqckd30r62aszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n3tdgu" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs96w7rwrp09puzvsh82ldu8vvq9vtut477ury5ay9cqckd30r62aszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n3tdgu" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs96w7rwrp09puzvsh82ldu8vvq9vtut477ury5ay9cqckd30r62aszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n3tdgu" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs96w7rwrp09puzvsh82ldu8vvq9vtut477ury5ay9cqckd30r62aszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n3tdgu" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>tempreites</h1> <p>My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by <a href="http://microjs.com/">http://microjs.com/</a> at the time and ended up not using the library. Probably no one ever did.</p> <ul> <li><a href="https://github.com/fiatjaf/tempreites">https://github.com/fiatjaf/tempreites</a></li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsxt958m70j92q2gxjnwezk6p3849tlgk5ea4kmfwxdfrgw6uw2sqqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6gyce4m" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsxt958m70j92q2gxjnwezk6p3849tlgk5ea4kmfwxdfrgw6uw2sqqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6gyce4m" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsxt958m70j92q2gxjnwezk6p3849tlgk5ea4kmfwxdfrgw6uw2sqqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6gyce4m" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsxt958m70j92q2gxjnwezk6p3849tlgk5ea4kmfwxdfrgw6uw2sqqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6gyce4m" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-15 01:18:43</div> </div> <div> <p>A história do Kali Linux se inicia em 2006, quando uma distribuição Linux chamada BackTrack foi lançada. O BackTrack foi uma distro baseada em Ubuntu e possuía o mesmo intuito do Kali Linux, auxiliar profissionais de segurança da informação. Em 2013, a Offensive Security, empresa que mantém o Kali Linux, anunciou o fim do suporte ao BackTrack, apresentando o Kali Linux que, diferente do BackTrack, tem como base o Debian. E assim nasceu a distribuição mais popular da área de segurança da informação. Principais ferramentas do Kali Linux A distribuição possui um arsenal com mais de 300 ferramentas nativas exclusivas para atividades de segurança e pentests. O Kali Linux inclui por padrão ferramentas como:</p> <p>Nmap: Uma das ferramentas mais populares do Kali Linux, o Nmap é um scanner de rede que permite a descoberta de dispositivos na rede, além de fornecer informações detalhadas sobre portas abertas, serviços em execução e sistema operacional dos dispositivos.</p> <p>Metasploit Framework: Uma poderosa estrutura de testes de penetração, o Metasploit Framework oferece um conjunto abrangente de ferramentas e recursos para realizar ataques simulados em sistemas e redes, com o objetivo de identificar vulnerabilidades e melhorar a segurança.</p> <p>Wireshark: Uma ferramenta de análise de tráfego de rede, o Wireshark permite capturar e examinar pacotes de dados em uma rede. Com ele, os profissionais de segurança podem identificar possíveis ameaças, analisar o tráfego de rede e realizar investigações forenses.</p> <p>John the Ripper: Uma ferramenta de quebra de senhas, o John the Ripper é amplamente utilizado para testar a segurança de senhas em sistemas. Ele pode realizar ataques de força bruta e ataques de dicionário para recuperar senhas de arquivos criptografados.</p> <p>Aircrack-ng: Essa ferramenta é voltada para auditoria de segurança em redes sem fio. O Aircrack-ng permite capturar pacotes de rede e realizar testes de penetração em redes Wi-Fi, além de fornecer recursos para quebrar senhas de redes sem fio protegidas.</p> <p>Burp Suite: Uma suíte de ferramentas para testes de segurança em aplicativos da web, o Burp Suite é amplamente utilizado para encontrar vulnerabilidades e realizar testes de penetração em aplicações da web. Ele oferece recursos avançados, como a interceptação de requisições e respostas HTTP, varredura de vulnerabilidades e manipulação de dados.</p> <p>Essas são apenas algumas das principais ferramentas incluídas no Kali Linux. A distribuição também conta com ferramentas para forense digital, análise de malware, engenharia reversa, entre outras áreas de segurança da informação.</p> <p>Além das ferramentas, o Kali Linux também oferece uma interface gráfica amigável, bem como documentação detalhada e uma comunidade ativa, o que facilita o aprendizado e o suporte para os usuários.</p> <p>O Kali NetHunter é uma plataforma de teste de penetração móvel desenvolvida para dispositivos Android e baseada no Kali Linux. Ele permite que os profissionais de segurança da informação realizem testes de penetração em dispositivos móveis de forma eficiente e conveniente.</p> <p>O Kali NetHunter consiste em vários componentes principais:</p> <ol> <li> <p>App Kali NetHunter: É um aplicativo Android que fornece uma interface amigável para acessar e executar as ferramentas de teste de penetração do Kali Linux diretamente em dispositivos móveis. Ele oferece uma ampla variedade de ferramentas nativas do Kali Linux, como scanners de rede, exploradores de vulnerabilidades, ferramentas de quebra de senhas, entre outras.</p> </li> <li> <p>App Store do Kali NetHunter: É uma loja de aplicativos integrada ao Kali NetHunter, que oferece uma seleção de aplicativos de segurança de terceiros específicos para testes de penetração em dispositivos móveis. Esses aplicativos são verificados e aprovados pela equipe do Kali NetHunter para garantir sua qualidade e segurança.</p> </li> <li> <p>Kali Container: É um ambiente contêiner baseado no Linux que permite executar o Kali Linux em um dispositivo Android sem a necessidade de enraizamento (root). O Kali Container é isolado do sistema operacional host, fornecendo um ambiente seguro para realizar testes de penetração. Ele permite que os usuários executem comandos do Kali Linux e acessem suas ferramentas a partir do dispositivo Android.</p> </li> <li> <p>KeX: É um recurso do Kali NetHunter que permite a execução do ambiente de desktop do Kali Linux em um dispositivo Android. Com o KeX, os usuários podem ter uma experiência de desktop completa, com uma interface gráfica, acesso a aplicativos e recursos do Kali Linux, e a possibilidade de executar várias ferramentas simultaneamente.</p> </li> </ol> <p>O Kali NetHunter oferece uma solução abrangente para testes de penetração em dispositivos móveis, permitindo que os profissionais de segurança realizem avaliações de segurança em smartphones e tablets Android de forma eficiente e controlada. Com sua ampla gama de ferramentas e recursos, o Kali NetHunter facilita a identificação de vulnerabilidades, a realização de testes de segurança e a proteção da segurança dos dispositivos móveis.</p> <p>Mas informações abaixo. https://www.kali.org/docs/nethunter/</p> <p>Kali Linux oferece diversas outras características e recursos que contribuem para sua popularidade e eficiência na área de segurança da informação:</p> <ol> <li> <p>Personalização e flexibilidade: O Kali Linux é altamente personalizável, permitindo que os usuários ajustem o sistema de acordo com suas necessidades específicas. É possível adicionar ou remover ferramentas, configurar ambientes de trabalho e ajustar as configurações para atender às preferências individuais.</p> </li> <li> <p>Compatibilidade com hardware: O Kali Linux possui amplo suporte para diferentes dispositivos e hardware, permitindo que seja instalado e executado em uma variedade de máquinas, desde laptops e desktops até dispositivos embarcados e plataformas de nuvem. Isso garante que os profissionais de segurança possam utilizar a distribuição em diferentes cenários e ambientes.</p> </li> <li> <p>Atualizações regulares e suporte: A equipe por trás do Kali Linux está em constante desenvolvimento e aprimoramento da distribuição. São lançadas regularmente atualizações de segurança, correções de bugs e novos recursos, garantindo que os usuários tenham acesso às versões mais recentes das ferramentas e aplicativos. Além disso, a comunidade Kali Linux fornece suporte ativo por meio de fóruns, documentação abrangente e recursos educacionais.</p> </li> <li> <p>Ética e legalidade: O Kali Linux enfatiza a importância da ética e legalidade nas atividades de segurança da informação. A distribuição é projetada para ser usada como uma ferramenta educacional e profissional, incentivando os usuários a realizar testes e avaliações de segurança dentro dos limites legais e de maneira responsável.</p> </li> <li> <p>Comunidade e recursos educacionais: O Kali Linux possui uma comunidade ativa e engajada de usuários, profissionais e entusiastas de segurança da informação. Essa comunidade oferece suporte, compartilha conhecimentos, discute tópicos relevantes e promove a troca de informações. Além disso, o Kali Linux disponibiliza uma vasta gama de recursos educacionais, como tutoriais, documentação detalhada e vídeos instrucionais, que ajudam os usuários a aprender e aprimorar suas habilidades em segurança da informação.</p> </li> </ol> <p>O Kali Linux se destaca como a distribuição líder em segurança da informação, oferecendo uma ampla variedade de ferramentas e recursos especializados para testes de invasão, pentest, forense digital e outras áreas. Sua personalização, compatibilidade com hardware, atualizações regulares, ênfase na ética e legalidade, comunidade ativa e recursos educacionais tornam-no uma escolha preferida tanto por estudantes quanto por profissionais em busca de uma plataforma confiável e eficiente para aprimorar suas habilidades e proteger a segurança da informação.</p> <p>https://www.kali.org/</p> <p>https://www.kali.org/docs/</p> <p>https://gitlab.com/kalilinux</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsxn92swn2f9vaxyav9v42mgu95mgyxyh4rvethe3ffvtsdgeaavngzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gceswhy" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsxn92swn2f9vaxyav9v42mgu95mgyxyh4rvethe3ffvtsdgeaavngzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gceswhy" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsxn92swn2f9vaxyav9v42mgu95mgyxyh4rvethe3ffvtsdgeaavngzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gceswhy" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsxn92swn2f9vaxyav9v42mgu95mgyxyh4rvethe3ffvtsdgeaavngzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gceswhy" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-15 01:11:15</div> </div> <div> <p>Lançado em 2016 como uma versão atualizada e aprimorada do KeePassX, o KeePassXC (Cross-Platform Community Edition) foi desenvolvido por um grupo de desenvolvedores com o objetivo de melhorar a experiência do usuário, adicionar recursos, corrigir bugs e fortalecer a segurança do gerenciador de senhas.</p> <p>Uma das principais melhorias introduzidas pelo KeePassXC foi a implementação de recursos de segurança avançados. O programa utiliza criptografia AES-256 para proteger o banco de dados, tornando-se um padrão de criptografia amplamente reconhecido. Além disso, foram adicionados recursos como autenticação de dois fatores, suporte a chave de arquivo e melhorias no gerador de senhas. A interface também passou por atualizações, incluindo novos ícones, layouts e melhorias de usabilidade, como recursos de pesquisa avançada, filtragem personalizada e a capacidade de criar entradas personalizadas.</p> <p>O KeePassXC funciona como um gerenciador de senhas, permitindo que você armazene, organize e acesse suas senhas de forma segura. Aqui está uma explicação simplificada de como ele funciona:</p> <ol> <li> <p>Criação do banco de dados: Ao iniciar o KeePassXC, você pode criar um banco de dados onde todas as suas senhas serão armazenadas. Esse banco de dados é um arquivo criptografado e protegido por uma senha mestra.</p> </li> <li> <p>Armazenamento das senhas: Você pode adicionar suas senhas ao banco de dados do KeePassXC. Isso pode ser feito manualmente, inserindo as informações da senha (como nome do site, nome de usuário e senha) em uma entrada específica. O KeePassXC também possui um gerador de senhas que pode criar senhas fortes e únicas para você.</p> </li> <li> <p>Acesso às senhas: Para acessar suas senhas armazenadas, você precisa fornecer a senha mestra. Essa senha é usada para desbloquear o banco de dados criptografado e permitir o acesso às senhas. Certifique-se de escolher uma senha forte e exclusiva para garantir a segurança do seu banco de dados.</p> </li> <li> <p>Preenchimento automático: Uma das principais vantagens do KeePassXC é o recurso de preenchimento automático de senhas. Quando você visita um site ou aplicativo que requer uma senha, o KeePassXC pode preencher automaticamente as informações de login para você, tornando o processo mais conveniente e seguro.</p> </li> <li> <p>Sincronização e backup: O KeePassXC permite que você sincronize seu banco de dados de senhas entre diferentes dispositivos. Isso pode ser feito através de serviços de armazenamento em nuvem seguros, como Dropbox ou Google Drive. Além disso, é recomendado fazer backup regularmente do seu banco de dados para evitar a perda de suas senhas.</p> </li> <li> <p>Segurança avançada: O KeePassXC utiliza criptografia avançada para proteger suas senhas. O algoritmo AES-256 é usado para criptografar o banco de dados, garantindo que apenas você possa acessar as senhas. Além disso, o KeePassXC suporta recursos de segurança adicionais, como autenticação de dois fatores e chave de arquivo.</p> </li> <li> <p>Integração com navegadores: O KeePassXC pode ser integrado aos navegadores da web, permitindo que você acesse suas senhas diretamente dos formulários de login dos sites. Isso facilita o preenchimento automático e evita a necessidade de copiar e colar manualmente as senhas.</p> </li> </ol> <p>O KeePassXC resolve vários problemas relacionados à segurança de senhas e oferece benefícios significativos para os usuários:</p> <ol> <li> <p>Gerenciamento de senhas seguro: O KeePassXC permite que você armazene todas as suas senhas em um único local seguro. Você não precisa mais se preocupar em lembrar várias senhas diferentes para diferentes serviços. Todas as suas senhas são armazenadas no banco de dados criptografado do KeePassXC, protegido por uma senha mestra.</p> </li> <li> <p>Criptografia avançada: O KeePassXC utiliza criptografia de nível avançado para proteger suas senhas. O algoritmo AES-256, amplamente reconhecido como um dos mais seguros, é usado para criptografar o banco de dados do KeePassXC.</p> </li> </ol> <p>Isso garante que suas senhas permaneçam seguras e não sejam acessíveis a pessoas não autorizadas.</p> <ol> <li> <p>Senhas fortes e únicas: O KeePassXC possui um gerador de senhas integrado que pode criar senhas fortes e únicas para você. Isso ajuda a evitar o uso de senhas fracas e fáceis de adivinhar, tornando suas contas mais seguras contra ataques de hackers.</p> </li> <li> <p>Autenticação de dois fatores: O KeePassXC suporta autenticação de dois fatores, o que significa que você pode adicionar uma camada adicional de segurança ao fazer login no gerenciador de senhas. Isso pode ser feito por meio de um aplicativo de autenticação no seu smartphone ou utilizando dispositivos de segurança como chaves USB.</p> </li> <li> <p>Segurança offline: O KeePassXC é uma solução offline, o que significa que todas as suas senhas são armazenadas localmente no seu dispositivo. Isso reduz o risco de exposição de dados sensíveis em ataques online e violações de segurança em serviços baseados na nuvem.</p> </li> <li> <p>Portabilidade: O KeePassXC é um programa de código aberto e multiplataforma. Isso significa que você pode instalá-lo e utilizá-lo em diferentes sistemas operacionais, como Windows, macOS e Linux. Você pode até mesmo transferir seu banco de dados de senhas entre diferentes dispositivos, permitindo acesso fácil e seguro às suas senhas em qualquer lugar.</p> </li> <li> <p>Auditoria e transparência: Sendo um projeto de código aberto, o KeePassXC permite que qualquer pessoa examine seu código-fonte e verifique sua segurança. Isso garante uma maior transparência e confiança na integridade do gerenciador de senhas.</p> </li> </ol> <p>É importante ressaltar que o KeePassXC é uma solução offline, o que significa que suas senhas são armazenadas localmente no seu dispositivo, em vez de serem enviadas para a nuvem. Isso ajuda a proteger suas informações contra ataques cibernéticos e violações de segurança.</p> <p>O KeePassXC funciona como um cofre seguro para suas senhas. Ele armazena e protege suas senhas com criptografia avançada, permitindo o acesso conveniente através do preenchimento automático. Com recursos de segurança adicionais e a capacidade de sincronizar e fazer backup do banco de dados, o KeePassXC oferece uma solução confiável para o gerenciamento de senhas.</p> <p>https://keepassxc.org/</p> <p>https://github.com/keepassxreboot/keepassxc</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdwf227tehmwgce0f9z2dg33p0srh7ve7fd8t4zqyvap8lmzys6aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gfzp3wu" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdwf227tehmwgce0f9z2dg33p0srh7ve7fd8t4zqyvap8lmzys6aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gfzp3wu" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdwf227tehmwgce0f9z2dg33p0srh7ve7fd8t4zqyvap8lmzys6aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gfzp3wu" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdwf227tehmwgce0f9z2dg33p0srh7ve7fd8t4zqyvap8lmzys6aqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gfzp3wu" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>nix</h1> <p>Pra instalar o <a href="797984e3.md">neuron</a> fui forçado a baixar e instalar o <a href="https://nixos.org/download.html">nix</a>. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.</p> <p>Que sofrimento pra fazer funcionar com o <code>fish</code>, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal de <code>fish-foreign-environment</code> (usando o próprio nix!, já que a outra opção era o <code>oh-my-fish</code> ou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto no <code>fish</code>.</p> <p>E aí lembrei também que o <code>/nix/store</code> fica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsppywq9rryu34g089q4uae7l0uq2azvhusawcdfd37yfjk0y2zkaqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6cukrnm" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsppywq9rryu34g089q4uae7l0uq2azvhusawcdfd37yfjk0y2zkaqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6cukrnm" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsppywq9rryu34g089q4uae7l0uq2azvhusawcdfd37yfjk0y2zkaqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6cukrnm" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsppywq9rryu34g089q4uae7l0uq2azvhusawcdfd37yfjk0y2zkaqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6cukrnm" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-15 01:06:52</div> </div> <div> <p>Ele usa uma abordagem única de virtualização baseada em compartimentos para isolar diferentes aplicativos e atividades em máquinas virtuais independentes. Isso significa que cada atividade, desde navegar na web , é isolada em seu próprio compartimento virtual, fornecendo um ambiente altamente seguro.</p> <p>O Qubes OS foi criado em 2010 pelo pesquisador de segurança polonês Joanna Rutkowska. Ela se inspirou na ideia de "security by compartmentalization" (segurança por compartimentalização) e começou a desenvolver um sistema operacional baseado em compartimentos para atender às suas necessidades de segurança. Em 2012, a primeira versão do Qubes OS foi lançada e desde então tem evoluído continuamente.</p> <p>O Qubes OS usa o conceito de máquinas virtuais (VMs) para criar uma abordagem de segurança baseada em compartimentos. Ele executa diferentes aplicativos e atividades em máquinas virtuais independentes, cada uma das quais é isolada do resto do sistema. Cada VM é atribuída a uma categoria de segurança e é configurada de acordo com as políticas de segurança necessárias para aquela categoria. Por exemplo, uma VM de navegação na web pode ser configurada com políticas de segurança para limitar o acesso à rede e restringir o acesso aos arquivos do sistema.</p> <p>O Qubes OS usa um recurso chamado "dom0" para gerenciar as VMs. O dom0 é uma VM privilegiada que é responsável por gerenciar as outras VMs e dispositivos de hardware do sistema. Ele é isolado do resto do sistema e é executado com permissões limitadas para reduzir o risco de ataques de software malicioso.</p> <p>O Qubes OS resolve vários problemas de segurança, especialmente para usuários que precisam lidar com informações confidenciais ou sensíveis. Alguns dos principais problemas que o Qubes OS resolve são:</p> <ol> <li> <p>Ataques de malware: A abordagem baseada em compartimentos do Qubes OS reduz significativamente o risco de ataques de malware. Se um aplicativo ou atividade for comprometido, o dano será limitado ao compartimento virtual onde está sendo executado.</p> </li> <li> <p>Rastreamento de atividades: O Qubes OS protege a privacidade do usuário ao evitar que atividades diferentes sejam correlacionadas. Cada atividade é executada em um compartimento virtual separado, impedindo que os dados de atividade sejam compartilhados entre os aplicativos.</p> </li> <li> <p>Proteção de dados confidenciais: O Qubes OS isola diferentes tipos de dados em VMs separadas, proporcionando um alto nível de proteção aos dados confidenciais. As VMs são configuradas com políticas de segurança adequadas para cada tipo de dados, protegendo-os contra acesso não autorizado.</p> </li> <li> <p>Proteção contra ataques de rede: O Qubes OS utiliza técnicas de isolamento de rede para proteger contra ataques de rede, como ataques de escuta, interceptação de tráfego ou ataques de injeção de pacotes. Cada VM pode ter uma interface de rede dedicada e isolada, garantindo que o tráfego de rede seja controlado e limitado a apenas o que é necessário para cada VM.</p> </li> <li> <p>Compartilhamento seguro de arquivos: O Qubes OS oferece a opção de compartilhar arquivos entre VMs de forma segura, sem comprometer a segurança do sistema. Isso é feito por meio do recurso de "transferência de arquivos segura", que permite que os usuários movam arquivos entre as VMs com segurança e sem o risco de contaminação por malware.</p> </li> <li> <p>Proteção de hardware: O Qubes OS também fornece recursos de segurança de hardware, como a possibilidade de bloquear portas USB ou desativar o microfone ou a webcam quando não estão em uso. Isso ajuda a evitar a exploração de vulnerabilidades de hardware e aumenta a segurança do sistema como um todo.</p> </li> <li> <p>Sistema operacional confiável: O Qubes OS é baseado em uma distribuição Linux confiável e de código aberto, o que significa que os usuários podem verificar o código fonte do sistema operacional e garantir que não haja backdoors ou vulnerabilidades ocultas.</p> </li> </ol> <p>https://github.com/QubesOS</p> <p>https://www.qubes-os.org/</p> <p>https://www.youtube.com/live/DpnSFhWEEXk?feature=share</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswkf67t6rn73vlskq9260vlcwlgf2qvrr45q75dautum57zdq8q5szyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g8mrrzr" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswkf67t6rn73vlskq9260vlcwlgf2qvrr45q75dautum57zdq8q5szyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g8mrrzr" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswkf67t6rn73vlskq9260vlcwlgf2qvrr45q75dautum57zdq8q5szyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g8mrrzr" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswkf67t6rn73vlskq9260vlcwlgf2qvrr45q75dautum57zdq8q5szyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7g8mrrzr" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 4ba8e86d:89d32de4 <div class="time" style="margin-left: auto;">2024-10-15 01:00:47</div> </div> <div> <p>Principais casos de uso do Shelter:</p> <ol> <li>Instalação de aplicativos dentro de um perfil de trabalho para isolamento.</li> <li>"Congelar" aplicativos dentro do perfil de trabalho para evitar que sejam executados ou ativados quando você não os estiver usando ativamente.</li> <li>Instalação de duas cópias do mesmo aplicativo no mesmo dispositivo.</li> </ol> <p>No entanto, é importante notar que o Shelter não oferece proteção contra:</p> <ul> <li>Vulnerabilidades do sistema Android ou do kernel do Linux.</li> <li>Backdoors presentes no sistema Android (recomenda-se usar ROMs de código aberto para preocupações desse tipo).</li> <li>Backdoors presentes em firmwares (esta é uma limitação incontornável).</li> <li>Outros bugs ou limitações do sistema Android.</li> </ul> <p>Adicionalmente, o Shelter não permite a criação de múltiplos perfis de trabalho em um dispositivo e não pode coexistir com outros aplicativos de gerenciamento de perfil de trabalho, devido a restrições do sistema Android.</p> <p>Para desinstalar o Shelter:</p> <ol> <li>Acesse Configurações -> Contas para remover o perfil de trabalho.</li> <li>Acesse Configurações -> Segurança -> Avançado -> Aplicativos de administração de dispositivos para remover o Shelter dos apps de administração.</li> <li>Desinstale o Shelter normalmente.</li> </ol> <p>https://gitea.angry.im/PeterCxy/Shelter</p> <p>https://f-droid.org/pt_BR/packages/net.typeblog.shelter/</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqstnzalu3hmjfk7jwq6vhfgfa6nh4mzey4hazmqxfhsypu2m4wp24gzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gvv93qx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqstnzalu3hmjfk7jwq6vhfgfa6nh4mzey4hazmqxfhsypu2m4wp24gzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gvv93qx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqstnzalu3hmjfk7jwq6vhfgfa6nh4mzey4hazmqxfhsypu2m4wp24gzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gvv93qx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqstnzalu3hmjfk7jwq6vhfgfa6nh4mzey4hazmqxfhsypu2m4wp24gzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gvv93qx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>O Bitcoin como um sistema social humano</h1> <p>Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. <a href="nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu">A melhor explicação em português que eu já vi está aqui</a>, mas mesmo assim qualquer explicação jamais será definitiva.</p> <p>A explicação apenas do protocolo, do que faz um programa <code>bitcoind</code> sendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco.</p> <p>E essa parte <em>técnica</em>, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles:</p> <ol> <li>A estrutura</li> </ol> <p>O Bitcoin é um sistema composto de partes independentes.</p> <p>Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas.</p> <p>Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados.</p> <p>Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles.</p> <p>Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que <a href="https://bitpay.com/">aceitam pagamento</a> em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda <a href="https://www.investimentobitcoin.com/">gente que usa bitcoins</a> e <a href="https://www.xdex.com.br/">a própria marca Bitcoin</a> para aplicar seus golpes e coisas parecidas.</p> <ol> <li>A cultura</li> </ol> <p>Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin.</p> <p>O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos.</p> <p>Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados.</p> <ol> <li>A história</li> </ol> <p>A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por <a href="https://www.forbes.com/sites/ktorpey/2019/04/23/this-key-part-of-bitcoins-history-is-what-separates-it-from-competitors/#49869b41ae5e">dois testes</a> e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à <a href="https://en.wikipedia.org/wiki/Regulatory_capture">captura por grupos interessados</a>, o que é mais um milagre -- ou, como dizem, um <a href="https://en.wikipedia.org/wiki/Focal_point_(game_theory)">ponto de Schelling</a>.</p> <p>Esse período crucial na história do Bitcoin fez com ficasse claro que <em>hard-forks</em> são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsqpkd7xc8jngkynekwf5nt8e336a78zatugy6972kmdac0vvzc9nszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6tp99a0" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsqpkd7xc8jngkynekwf5nt8e336a78zatugy6972kmdac0vvzc9nszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6tp99a0" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsqpkd7xc8jngkynekwf5nt8e336a78zatugy6972kmdac0vvzc9nszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6tp99a0" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsqpkd7xc8jngkynekwf5nt8e336a78zatugy6972kmdac0vvzc9nszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6tp99a0" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 101b30ee:18a46a45 <div class="time" style="margin-left: auto;">2024-10-15 00:30:33</div> </div> <div> <h1>背景</h1> <p>Junさんが山形県在住で、車で色々案内いただけることになりました。</p> <h1>メンバー (敬称略)</h1> <ul> <li>Jun (nostr:npub1nlnjcakw6xfkpuhx9kym3d20sr774pm6rue5kk93uj7lrca9lypqgqj7fd)</li> <li>りら (nostr:npub1tuqsl6l8xzly95vv80um7wsnt7gxy8w9wgt4khp4wyv4xwhfw44slm93e9)</li> <li>あめ (nostr:npub1eqw8nx0hya3cwvtc0rje6lpjzzf6gvuh0mngz898dhp6juuwrp5s5uzduw)</li> <li>Don (nostr:npub1dv9xpnlnajj69vjstn9n7ufnmppzq3wtaaq085kxrz0mpw2jul2qjy6uhz)</li> <li>横谷加奈子 (nostr:npub1sd2zns7qsfster7vcyjcqkert4cev2rzfeuus0d8hnfdh74t6g7su0p4c6)</li> <li>発火大根 (nostr:npub1zqdnpm5gcfap8hngha7gcp3k363786phvs2etsvxw4nh6x9ydfzsuyk6mn)</li> </ul> <h1>スケジュール</h1> <h2>10/12</h2> <h3>11:00 - 11:30 霞城セントラル 日本酒めぐりツアー</h3> <p>500円で3コインもらえて、1コインでカップ1杯分の試飲ができるシステムのようです。<br> 山形はフルーツも有名で、日本酒だけでなくワインなども試飲できました。<br></p> <p>個人的には、梨ベースのお酒が飲み口すっきりしていておいしかったです。<br> 名前は忘れました ()<br></p> <h4>霞城公園セントラル</h4> <p>https://yamagatakanko.com/attractions/detail_13443.html</p> <p>nostr:nevent1qqszfgt4vef3ncyw7cy9yykuwv06pq5v9znaf2xeehfpp6s5j27ncqg2val6m nostr:nevent1qqsvfknrdtwsyvmztdzx40adzvtx8nztxu3vscgkljzzk2zr8kfmfnce54ke0</p> <h3>11:30 - 12:30 霞城公園散策</h3> <p>東北屈指の戦国大名・最上義光(もがみよしあき)公 (1546-1614)が礎を築いた「山形城」を復原整備した都市公園らしいです。<br></p> <p>Junさんに聞いたところ、最上義光の妹が伊達政宗の母・義姫 (よしひめ)で、息子の伊達政宗を毒殺しようとしたことで有名らしいです。<br> 後で調べたところ、毒殺事件が捏造だったとする記事もあり、真偽はいかに。<br></p> <p>また、これもJunさんに聞いたのですが山形藩は幕府重役から失脚した左遷の地と呼ばれているようです。<br> ちょっと悲しい。<br> 後に調べたところ、山形藩は計12家が収めており、入れ替わりも激しかったようです。<br> まぁ、左遷だったとしても自然豊かな地でスローライフを過ごすのもアリかもしれない。<br></p> <p>個人的には、最上義光像が精巧に出来ているなぁと感動しました。<br> 構図がナポレオンに似ていたので、もしかして身長が低かった?と思いましたが<br> 後で調べたところ、180cm以上の長身だったとする文献があるようです。<br></p> <h4>山形藩</h4> <p>https://ja.wikipedia.org/wiki/%E5%B1%B1%E5%BD%A2%E8%97%A9</p> <h4>義姫の毒殺事件について</h4> <p>https://bushoojapan.com/bushoo/date/2024/08/12/76725</p> <h4>最上義明の身長</h4> <p>http://iiwarui.blog90.fc2.com/blog-entry-13581.html</p> <h4>霞城公園セントラル</h4> <p>https://yamagatakanko.com/attractions/detail_2304.html</p> <p>nostr:nevent1qqsp78jf76yudrwf6w88szq4x50t0zpeht77adkmk5pj5xsg6wplcmcv25e3g nostr:nevent1qqsfvw828mus5ek44m5myuya5ndpvj8mjhlltzx4y6ha93932cvzaxgwqwah3 nostr:nevent1qqs9sd8m43lj6pmd7hzu0quf4v0s7rm4uaq83aqp5jn5sqfy8aw6f8skg0sgv</p> <h3>12:30 - 13:30 旧済生館</h3> <p>済生館は1878年(明治11年)に山形県立病院として建設され、東北地方で最も早く西洋医学を取り入れたことで有名のようです。<br> 建物内部の展示物の写真撮影は禁じられていたので写真は取れていませんが、あの有名な杉田玄白の訳書「解体新書」や、明治時代の医療器具などが展示されていました。<br></p> <p>私は工業高校出身で電気科だったので、昔の医療電気機器の展示などは見ていて飽きないものがありました。<br></p> <h4>旧済生館</h4> <p>https://www100.pref.yamagata.jp/110001/sangyo/sangyoushinkou/him_top/him_maincat1/him_15.html</p> <h3>13:30 - 14:30 山寺付近に移動・ランチ</h3> <p>山寺付近に車で移動後、玉こんにゃくを食べながら山寺方面に徒歩移動。<br> 玉こんにゃくは名産らしく、山形のいたるところで売っていました。<br></p> <p>途中で近場のお店でランチ(蕎麦)を食べました。<br> ランチを食べながら映画 (オッペンハイマー)の話とかビットコインの話をしてました。<br> ちなみに私はオッペンハイマー見れてません。<br> あめさんはオッペンハイマーを見に県外 (奈良 -> 大阪)まで行ったらしい。<br> 行動力すげぇ。<br></p> <p>nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpgqwakh6t2vm0ufy82rmwjqa2ld2z9jdl9l90v0ds7afwe6n5myl5uf5p7 nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqq570ak2p9wx9q09xafjnlnulshwg2wc5c66q37z884m0pselu36sz5k7jk nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpp8xy7nktvyq87d676pkh6hjpftm5s703fq8e8c52l2l9xupe55wyhfc0p nostr:nevent1qvzqqqqqqypzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qyshwumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5up0qy08wumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqhsqgqthnr72cp92yqv9upzg2fyplvt6eazf6kxe24h6ea6syg3mthsl5tc3r26</p> <h3>14:30 - 16:00 山寺 (宝珠山立石寺)</h3> <p>宝珠山立石寺 (愛称:山寺)は山形屈指の観光スポットで、松尾芭蕉が「閑さや岩にしみ入る蝉の声」の名句を紀行文「おくのほそ道」に残したことでも知られているそうです。<br></p> <p>展望台付近まで登りましたが、<strong>前日2時間程度しか寝れてなかった</strong> からか、途中で何回か力尽きました。<br> 何気にずっと階段だったのが厳しかった。w <br> 展望台から見る景色が超綺麗でした。達成感あった。<br></p> <p>途中でDonさんが「松尾芭蕉も山寺登ってますよ!」と励ましてくれましたが、松尾芭蕉は服部半蔵だったのでは、といわれる説が頻繁に出るくらい、体力おばけです () <br></p> <p>#### 山寺・宝珠山立石寺 https://yamagatakanko.com/attractions/detail_2352.html</p> <h4>松尾芭蕉が忍者服部半蔵ではないかと言われる都市伝説の理由5つ</h4> <p>https://spirituabreath.com/matuobasyou-hattorihannzou-5207.html</p> <p>nostr:nevent1qvzqqqqqqypzp8l893mva5vnvrewvtvfhz65lq8aa2rh58enfdvtre9a7836t7gzqqs2jsu0efm0s0xnp9exv0m4xkxaw07nsraxhfjqrl6rmjd977aqcycfaf05e nostr:nevent1qvzqqqqqqypzp8l893mva5vnvrewvtvfhz65lq8aa2rh58enfdvtre9a7836t7gzqqsxmrsa8h6y6z8hmt7hzg8cmspvc373gnjjs67vlrdp24lud8wm8ncp682ev nostr:nevent1qvzqqqqqqypzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qyshwumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5up0qy08wumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqhsqgq3a6ehlurcsmpzlc4vghnnu7tnk5tekwm2kxn7e9rkrq7uslqmlu9sg6vl nostr:nevent1qvzqqqqqqypzp8l893mva5vnvrewvtvfhz65lq8aa2rh58enfdvtre9a7836t7gzqqs9lp9n8yjwjx56khduh7sqehtpgfs20d5w7x9lnjpnlt3vmqkpnmq7xfcef nostr:nevent1qvzqqqqqqypzp8l893mva5vnvrewvtvfhz65lq8aa2rh58enfdvtre9a7836t7gzqqsx4m8un5h952d6f7zuq9yraucs82lcah2p2lk4z6n9u0lduje2pcs40zhkz nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzq5pf4h2je6jkpypup9kj2k66qtlcmce3gcg9q39xpv5388u50sun6ku45d nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqkdwwjagam6rcxmakpcgsylu95zkm8s0qkvae8j2km6e5l5sr9alsm8vrfn nostr:nevent1qvzqqqqqqypzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qyshwumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5up0qy08wumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqhsqg9cqvgzvegmdsnc6xc5mhwnvsn9unyx4nx6megwcqxlheaddffc8ckpk3qj</p> <h3>16:00 - 18:30 山形駅でりらさん合流・産業科学館</h3> <p>車で山形駅まで戻り、りらさんと合流。<br> 山形駅内の産業科学館を見て回りました。<br></p> <p>産業科学館は子供向けの知育ブースや山形県民向けの各種企業ブースもあり、見ていて飽きないものが沢山展示されていました。<br> 発電機を回してミニカーを動かすゼネコンレーシングが楽しかった。<br> また、各種企業ブースを回りながら、Junさんに山形県民憧れの就職先などを聞いていました。<br></p> <h4>産業科学館</h4> <p>http://y-sunka.org/</p> <p>nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpx0ykjd6egvded9jksguphr4deluxlz56dm4rpw9n68npx9wt3hx976mcl nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpek5k3fygrx8y0024mmmnhqxdnd7jmqed7gf7sqt2tnushcv8xu7dwwctd nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyzzfwt63psqw4w5x7s33al0k0ms2v80p88vjjjd4rx7f8t4juppkux27ek7 nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqgj58fqpvpngr2vafhdcqtf5vn264960dad73kqfrem3m27hr6mpstqgs5t nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyrnaxmkc47f5p46p36v8qnf4pr5ktm5algd86fsgzw9de96n9yp4qxu6dl8 nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqypehj7clkzll3yf7yftcp5t9k6dfnetvrpl943q4jd8ccy39neq66nyavjs nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzqnc3mmp8sg4lysfkcz7x4ft3c6rrulne8aetvd8lwkzz86k8fp9lt040df nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzqgdms2ltla34u9qr4whzlz69r3mpsj7e3jlpv935yltn799xsk89d3a6g4</p> <h3>18:30 - 20:40 旅館チェックイン、夕食</h3> <p>私 / あめさん / りらさんで、喜三郎という温泉旅館に泊まりました。<br> ここの温泉の泉質は芒硝泉(リウマチ・高血圧・切り傷・婦人病に効くとのこと)で、保養温泉として親しまれているそうです。<br> 夕食のしゃぶしゃぶ、サザエ、釜めし、芋煮、... 全部旨かった!!!<br> 夕食を食べていたら意外と時間ギリギリになり、露天風呂は朝入ることにして爆速で風呂に入りました。</p> <h4>温泉旅館 (喜三郎)</h4> <p>https://kisaburo.jp/</p> <p>nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyqr9wgwca9jknh88c83nq3n5nnqtflrrd4v5d7uhuh9d47a2qsl870yprel nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyr6yt65e79gqh4dp8pll2kfgaw837xulq2jh2x3y9zd4udk47lkn55pqkzm nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqwdv2aa4n5z5r5k8q3z2retc9zgujytx9z36xmpsw6h9npc97250qkne529 nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzp2rhy02kfw73jtzq7t7sp2njn2gnt9elta7nm09u55csld8kg5t39lh49r nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyzv32r03thal6tvjqh4wgxk6xv6x2tkuwngw6kfv6ar49rg2yq55jc8arsp nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqy2duq6xsl8jwns0r7qxgpf6703uwvawrhhlanytrepd082mnyugqxnxpj3</p> <h3>20:40 - 23:00 二次会</h3> <p>二次会の居酒屋でJunさん、Donさんと再度合流。<br> Junさんの奥さんで漫画家をされている、横谷先生も来てくれました。<br></p> <p>山形の地酒を飲みながら、Nostrasia 2024での思い出 / 山形の特産品 / Junさん夫妻が東京にくるタイミングはいつか など話していました。<br></p> <p>横谷先生はM3やコミティアなど東京に来られるタイミングがいくつかありそうでしたが、Junさんが東京に来るタイミングはなかなか無さそう。<br> 山形にまた会いにいくか、東京で面白いイベントをやって呼ぶしかない!<br></p> <p>また、山形には「ほや」と呼ばれる海産物が有名という話を聞きました。<br> ほや、結局食べ損ねてしまった。<br></p> <h4>山形うまいものと地酒 母家</h4> <p>https://r.gnavi.co.jp/t846900/?sc_lid=smp_top_01</p> <h4>横谷先生の読み切り : 遠い日の陽</h4> <p>https://comic-days.com/episode/14079602755391426482</p> <p>nostr:nevent1qvzqqqqqqypzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qyshwumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5up0qy08wumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqhsqgplnrvwhk6hsl9rk979u6qtmnmrpgywdgexruznhmtkmyevsaua8s8cy2pq nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpkwu2t5zgug7wlwqh8nfh4zyma3f6tlacx9dag4kawnq7nynkxr33rdgaz nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpq8szzc33567mtsjnvajzgur9n8us3fuv2ckx86y0et3c7kddqd37uxuz0</p> <h3>23:00 - 旅館に戻る・就寝</h3> <p>旅館まで車で送ってもらい、旅館で就寝。<br> 翌日も朝早いので、恒例(?)の枕投げやトランプをして遊ぶこともなく、12時に消灯しました。<br></p> <h2>10/13</h2> <h3>6:00 - 起床・露天風呂 ~ 7:30 朝食 ~ 8:30 チェックアウト</h3> <p>前日に入れなかった露天風呂に入るため、早めに起きて露天風呂に入りました。<br> 旅館の窓を開けると須川が流れていて、天然のASMRを感じられました。<br></p> <p>nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzpz260lg35sg06h758y7eppvrwzypv5kc3yj4n0t8jyx5q4f82mse3ung9s nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpqt6cyt5hmatsuct2plneae7t0apnkkrxm38hvee3auhu0h3hljjgs943h27 nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzp2qq9lv0d3umyxprne6xpjj70af6flzcfs2qpgsx2r347q7ukpdm2rwml4 nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzqgaugf683lhlww8ynlgd7qfhgj2d3zlkecm72td35lfw6m4tkvhke4k8jt nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyz750rwdqdk0x8r08m96fcyf5l4wp9pmc0rz8mle02ygtrdzdhf0gjwc823 nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzqq36wgay36wz58kmjvsucple6whamvd28pqrhu082wsdkkpvxzht34tq02</p> <h3>8:30 - 移動・買い物 ~ 9:40 Junさんの家に移動・芋煮会開始</h3> <p>近隣のスーパーで芋煮会用の買い物を済ませたあと、Junさんの家に移動して芋煮会を始めました。 あめさんが帰宅の関係上、山形駅を11:11に出ねばならず、芋をよく煮るために爆速で芋煮を作る必要がありました。<br> 皆で協力して爆速で芋煮を作り、しっかり煮えた状態の芋煮をあめさんに持って帰ってもらうことができました!</p> <p>nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qy0hwumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdakj7qg6waehxw309aex2mrp0ykk5upwwd5xjmn0xvhxuet59uqzqe03zqdcpjzakz3u7jjs07crz05y024lvgmjuvh0zysf4zal9q0la8772q nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpq6xaa2etzypq7hlm8zs3rkrjsc0wh5c29huupe9mfxqqeu5uanttq39l9w6 nostr:nevent1qqs0zkh2t2crsv8ljxzvmy3ndwzncyl6wwz67hfy4p09tacem3pjzwg2h4ac8 nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpq3ugypvt2fw886375nzltef4fzlasvk7nzj5n9tpuunwrr4p9etasskzqd6 nostr:nevent1qvzqqqqqqypzpjqu0xvlwfmrsuchs789n47ryyyn5seewlhxsyw2wmwr49ecuxrfqyv8wumn8ghj7mn0wd68ytnxd46zuamf0ghxy6t69uq3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7qpq9u5559ucupe755xnlm00vm5wcj7rpu3wwc3wvrdjxxdcadcwumzqjg8e6r</p> <h4>芋煮ビルド過程</h4> <p>nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqypn3w96w3wu375rz5hwhwhnmvrc664dltaudzvt578s6dh6kzq205u0m44v nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqypc0nxkt4ht0ku9l4hjmvtlv9rh5lt496r7s3755clg7q45fypnxkjms92t nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqypdfx9umwcyupt4cx38klfhl0f3saf3ar47jr7rcyj69dzyxve7tqk8wmcm nostr:nevent1qqsve084cxu5kw3gvqhjaehfge202z2nyddft89ufn9j73wyynwzhwczwz8j2 nostr:nevent1qqs26rp3gc2dhz4yznynym0y3c6y257kt2u773dvaaf87uf40fzjmcqk2zxxm nostr:nevent1qqsf3jx69s6guydhfxqstcw2m5aaw0zpum74aawe79nhz3xyg7p7dks0x9gn5 nostr:nevent1qqswtgfxseqwnt424ay668ps782drdmxkyyqj8uk8lfxs264gayfnkg3ls82a nostr:nevent1qqsqd257ng55ynkrwe3v2skcx29xalz85qcgn3ghj8ug4lqt9ewqvwgshz303 nostr:nevent1qqsw04zd3wgd3c5ztave9yhhavupl7pc3e4rcke5qn4azn8gpctz23cm7e5p8 nostr:nevent1qqsv8kqnr36jyhj9tnc602p6njakhgcuf6klm0xfrsngjrxlej9068s9vz3jg nostr:nevent1qvzqqqqqqypzqhcppl47wv97gtgccwlehuapxhusvgwu2ushtdwr2uge2vawjattqyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcpy9mhxue69uhhyetvv9uj66ns9ehx7um5wgh8w6tjv4jxuet59e48qtcqyrpm5t3gxyjxnfw6y8eu2j0mpgf8acj83c86ueykdqke6nxchjku63rl6q5</p> <h3>11:20 - 14:30 Junさんの家でまったり・ねるねるねるね</h3> <p>Junさんにあめさんを駅に送ってもらった後は、残ったメンバーでテレビを見たり、ねるねるねるねを作って皆で食べたりしていました。<br> りらさんが仙台に行くため、14:30で帰っていきました。<br></p> <p>nostr:nevent1qqsya6u4r9amxs32m4k45s9203ph3kwmtlyddq283zrtyufk3z7tk9gaw3dyv nostr:nevent1qqs0nr6xznhxr4hfrczatlgy26lcrlup3zg8ey6j6ldthxnu9fy3mfq7tauam</p> <h3>14:30 - 16:30 伺かレクチャーを受ける</h3> <p>Junさんにりらさんを送ってもらっている途中、せっかく伺かベテランのDonさんがいるので<br> 伺かを始めました。<br> ※元々伺かやSSTPには興味があった<br> Donさんに伺かの基礎や「Nostr x 伺か」のOSSの機能などをレクチャーしてもらいながら、<br> Nostrと伺かで出来ることを話し合っていました。<br></p> <p>個人的に驚いたのは、一方通行で喋らせるだけだと思っていた伺かが、SSTPを通じてデスクトップマスコットとシーケンシャルに「やりとりができる」ことです。<br> 非常に拡張性が高く、Nostrと同じで無限に遊べそうな雰囲気を感じました。<br></p> <h4>伺か (うかがか) とは</h4> <p>2000年5月25日に初公開されたデスクトップ常駐型のフリーウェアで、24年間色んな人が発展・メンテナンスしています。<br> SSTP (Sakura Script Transfer Protocol) と呼ばれるプロトコルで指定のポート番号 (9801番)あてにメッセージを送ると、デスクトップマスコットを喋らせたり色んなことができます。<br> プロトコル仕様が公開されており、SSTPクライアントやサーバー、ベースウェアまで自作することが可能です。</p> <p>詳細 https://dic.nicovideo.jp/a/%E4%BC%BA%E3%81%8B</p> <h4>伺か参考 (ばぐとら研究所)</h4> <p>現在デファクトスタンダードとなっているベースウェア、SSPがここからダウンロードできます。 https://ssp.shillest.net/</p> <p>nostr:nevent1qqsyrz64vff9fjkpj297qyr278d2a58l3fuysgknsm8jwyuwy6v8hcgvmn4mt nostr:nevent1qqsdzfjfvxxk5ph49x40s3hf8pdgazzq2x5xekd6ztqnqw4y4z3r8as4pdywy nostr:nevent1qqsr8sdds33g53asp7c45v3eems3vj3qhtxayvku9nxext95aauuuaq4d6t0x</p> <h3>16:30 - 17:30 四谷ラボの配信アーカイブを見る・帰宅</h3> <p>Nostrasia 2024やBluesky meetup、Nostr勉強会の配信アーカイブを見ながら、当時の思い出やNostrの未来について語っていました。<br> こういうのを忘年会や新年会でやっても面白いかもしれない。<br> 18時の山形駅発の新幹線を取っていたので、18時にJunさんに駅まで送ってもらい、山形を去りました。<br></p> <h4>四谷ラボの配信アーカイブ</h4> <p>https://www.youtube.com/@428-lab</p> <h1>終わりに</h1> <p>私は1泊2日でしたが、山形を味わい尽くしてリフレッシュすることが出来ました!<br> 今回、Junさんには企画だけでなく車で色々連れて行ってもらったりと、本当にお世話になりました。<br> 次に直接お会いしたら、何かしらもてなしたい。<br></p> <p>また、Donさんに直接会えて色々話せたのは本当に貴重でした。聞くところによると、Nostrのオフ会だけでなく、歴の長い伺か仲間とのオフ会も出たことがないらしいです。<br></p> <p>また山形に行きたい!と思えるようなオフ会でした。</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0jn58uy56reqqu76qjrral3yuqpgmue0wmknhsxeaetg48tve6eszyqgpkv8w3rp85y77dzlherqxx6828clgxajpt9wpse6kwlgc534y2c9t2ek" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0jn58uy56reqqu76qjrral3yuqpgmue0wmknhsxeaetg48tve6eszyqgpkv8w3rp85y77dzlherqxx6828clgxajpt9wpse6kwlgc534y2c9t2ek" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0jn58uy56reqqu76qjrral3yuqpgmue0wmknhsxeaetg48tve6eszyqgpkv8w3rp85y77dzlherqxx6828clgxajpt9wpse6kwlgc534y2c9t2ek" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0jn58uy56reqqu76qjrral3yuqpgmue0wmknhsxeaetg48tve6eszyqgpkv8w3rp85y77dzlherqxx6828clgxajpt9wpse6kwlgc534y2c9t2ek" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>O caso da Grêmio TV</h1> <p>enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:</p> <p>Grêmio TV pior que o SBT !</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsypjnd5mxv23dgmkr4rs8337n7crplh75rng57h4kdzpduuqvhpxqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n4cmtx" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsypjnd5mxv23dgmkr4rs8337n7crplh75rng57h4kdzpduuqvhpxqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n4cmtx" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsypjnd5mxv23dgmkr4rs8337n7crplh75rng57h4kdzpduuqvhpxqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n4cmtx" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsypjnd5mxv23dgmkr4rs8337n7crplh75rng57h4kdzpduuqvhpxqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6n4cmtx" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ d3f06d83:7ff53dc3 <div class="time" style="margin-left: auto;">2024-10-15 00:30:10</div> </div> <div> <h2>Chef's notes</h2> <p>This is the beginning of a great pizza.</p> <h2>Details</h2> <ul> <li>⏲️ Prep time: 15 min</li> <li>🍳 Cook time: 0</li> <li>🍽️ Servings: 0</li> </ul> <h2>Ingredients</h2> <ul> <li>1 cup of pizza flour or bakery flour (00 flour)</li> <li>1 zatchet of yeast (7g)</li> <li>1 cup of water</li> <li>1 spoon of honey (or sugar)</li> <li>2 Litre container with a lid</li> </ul> <h2>Directions</h2> <ol> <li>Pour the water in a 2L container </li> <li>Add honey/sugar and stir </li> <li>Add the yeast and stir. Wait 15 minutes or until the yeast is active (bubbling)</li> <li>Slowly mix the flour avoiding clumps </li> <li>Close the lid and leave in the fridge overnight </li> </ol> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyta5csnq2jxslqrdkwh6ypxwls4gtr9mklr2ly0g83k8rjd7wrcszyrflqmvrpceeyl6z97wsp3gcpd4qw8uwqfzh83d26hz68utl757uxkpmrvc" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyta5csnq2jxslqrdkwh6ypxwls4gtr9mklr2ly0g83k8rjd7wrcszyrflqmvrpceeyl6z97wsp3gcpd4qw8uwqfzh83d26hz68utl757uxkpmrvc" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyta5csnq2jxslqrdkwh6ypxwls4gtr9mklr2ly0g83k8rjd7wrcszyrflqmvrpceeyl6z97wsp3gcpd4qw8uwqfzh83d26hz68utl757uxkpmrvc" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyta5csnq2jxslqrdkwh6ypxwls4gtr9mklr2ly0g83k8rjd7wrcszyrflqmvrpceeyl6z97wsp3gcpd4qw8uwqfzh83d26hz68utl757uxkpmrvc" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>My stupid introduction to Haskell</h1> <p>While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of <a href="http://learnyouahaskell.com/chapters">LYAH</a>).</p> <p>An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore.</p> <hr /> <p>Here we go:</p> <ul> <li><strong>Why do modules have odd names?</strong></li> <li>modules are the things you import, like <code>Data.Time.Clock</code> or <code>Web.Scotty</code>.</li> <li>packages are the things you install, like 'time' or 'scotty'</li> <li>packages can contain any number of modules they like</li> <li>a module is just a collection of functions</li> <li>a package is just a collection of modules</li> <li>a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever</li> <li>the module names you choose when you're writing a package can be anything, and these are the names people will have to <code>import</code> when they want to use you functions<ul> <li>if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package</li> <li>people choose things that make sense, like for <code>aeson</code> instead of <code>import Aeson</code> you'll be doing <code>import Data.Aeson</code>, <code>import Data.Aeson.Types</code> etc. why the <code>Data</code>? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it.</li> <li>you just have to check the package documentation to see which modules it exposes.</li> </ul> </li> <li><strong>What is <code>data User = User { name :: Text }</code>?</strong></li> <li>a data type definition. means you'll have a function <code>User</code> that will take a Text parameter and output a <code>User</code> record or something like that.</li> <li>you can also have <code>Animal = Giraffe { color :: Text } | Human { name :: Text }</code>, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal.<ul> <li>then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human.</li> </ul> </li> <li><strong>What is a monad?</strong></li> <li>a monad is a context, an environment.<ul> <li>when you're in the context of a monad you can write imperative code.</li> <li>you do that when you use the keyword <code>do</code>.</li> <li>in the context of a monad, all values are prefixed by the monad type,</li> <li>thus, in the <code>IO</code> monad all <code>Text</code> is <code>IO Text</code> and so on.</li> <li>some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily.</li> <li>for exampĺe, <a href="https://www.stackage.org/haddock/lts-9.18/scotty-0.11.0/Web-Scotty.html">scotty</a>'s <code>ActionM</code> and <code>IO</code>. <code>ActionM</code> is just a subtype of <code>IO</code> or something like that.</li> <li>when you write imperative code inside a monad you can do assignments like <code>varname <- func x y</code></li> <li>in these situations some transformation is done by the <code><-</code>, I believe it is that the pure value returned by <code>func</code> is being transformed into a monad value. so if <code>func</code> returns <code>Text</code>, now varname is of type <code>IO Text</code> (if we're in the IO monad).<ul> <li>so it will not work (and it can be confusing) if you try to concatenate functions like <code>varname <- transform $ func x y</code>, but you can somehow do</li> <li><code>varname <- func x y</code></li> <li><code>othervarname <- transform varname</code></li> <li>or you can do other fancy things you'll get familiar with later, like <code>varname <- fmap transform $ func x y</code></li> <li>why? I don't know.</li> </ul> </li> </ul> </li> <li><strong>How do I deal with Maybe, Either or other crazy stuff?</strong> "ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?"</li> <li>you don't! you turn it into other thing. for example, you use <a href="http://hackage.haskell.org/package/base-4.10.1.0/docs/Data-Maybe.html#v:fromMaybe">fromMaybe</a>, a function that takes a default value and that's it. if your <code>Maybe</code> is <code>Just x</code> you get <code>x</code>, if it is <code>Nothing</code> you get the default value.<ul> <li>using only that function you can already do whatever there is to be done with Maybes.</li> <li>you can also manipulate the values inside the <code>Maybe</code>, for example:</li> <li>if you have a <code>Maybe Person</code> and <code>Person</code> has a <code>name</code> which is <code>Text</code>, you can apply a function that turns <code>Maybe Person</code> into <code>Maybe Text</code> AND ONLY THEN you apply the default value (which would be something like the <code>"unnamed"</code>) and take the name from inside the <code>Maybe</code>.</li> </ul> </li> <li>basically these things (<code>Maybe</code>, <code>Either</code>, <code>IO</code> also!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values.<ul> <li>besides the example above with Maybes and the <code>fromMaybe</code> function, you can also remove the values by using <code>case</code> -- for example:</li> <li><code>case x of</code><ul> <li><code>Left error -> error</code></li> <li><code>Right success -> success</code></li> </ul> </li> <li><code>case y of</code><ul> <li><code>Nothing -> "nothing!"</code></li> <li><code>Just value -> value</code></li> </ul> </li> <li>(in some cases I believe you can't remove the values, but in these cases you'll also don't need to)</li> <li>for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program.</li> </ul> </li> <li><strong>JSON and interfaces (or instances?)</strong></li> <li>using <a href="https://hackage.haskell.org/package/aeson-1.2.3.0/docs/Data-Aeson.html">Aeson</a> is easy, you just have to implement the <code>ToJSON</code> and <code>FromJSON</code> interfaces.</li> <li>"interface" is not the correct name, but I don't care.</li> <li><code>ToJSON</code>, for example, requires a function named <code>toJSON</code>, so you do<ul> <li><code>instance ToJSON YourType where</code></li> <li><code>toJSON (YourType your type values) = object []</code> ... etc.</li> </ul> </li> <li>I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved.</li> <li><code>FromJSON</code> is a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols.</li> </ul> <h2>See also</h2> <ul> <li><a href="nostr:naddr1qqyrzcmrvcmrqwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cktq992">Haskell Monoids</a></li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsx3z23x9ullppkfqpeppxvmmg8hdcczuncyh6alkzmdtztvzqs0tgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6z5p67w" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsx3z23x9ullppkfqpeppxvmmg8hdcczuncyh6alkzmdtztvzqs0tgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6z5p67w" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsx3z23x9ullppkfqpeppxvmmg8hdcczuncyh6alkzmdtztvzqs0tgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6z5p67w" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsx3z23x9ullppkfqpeppxvmmg8hdcczuncyh6alkzmdtztvzqs0tgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6z5p67w" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>Classless Templates</h1> <p>There are way too many hours being wasted in making themes for blogs. And then comes a new blog framework, it requires new themes. Old themes can't be used because they relied on different ways of rendering the website. Everything is a mess.</p> <p>Classless was an attempt at solving it. It probably didn't work because I wasn't the best person to make themes and showcase the thing.</p> <p>Basically everybody would agree on a simple HTML template that could fit blogs and simple websites very easily. Then other people would make pure-CSS themes expecting that template to be in place.</p> <p>No classes were needed, only a fixed structure of <code>header</code>. <code>main</code>, <code>article</code> etc.</p> <p>With <strong>flexbox</strong> and <strong>grid</strong> CSS was enough to make this happen.</p> <p>The templates that were available were all ported by me from other templates I saw on the web, and there was a simple one I created for my old website.</p> <ul> <li><a href="https://github.com/fiatjaf/classless">https://github.com/fiatjaf/classless</a></li> <li><a href="https://classless.alhur.es/">https://classless.alhur.es/</a></li> <li><a href="https://classless.alhur.es/themes/">https://classless.alhur.es/themes/</a></li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspwv43tnzue7kw9c552zf88u8sncxed3j28n4flrrkp29tqus40eqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68hnvga" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspwv43tnzue7kw9c552zf88u8sncxed3j28n4flrrkp29tqus40eqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68hnvga" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspwv43tnzue7kw9c552zf88u8sncxed3j28n4flrrkp29tqus40eqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68hnvga" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspwv43tnzue7kw9c552zf88u8sncxed3j28n4flrrkp29tqus40eqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68hnvga" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>The "Drivechain will replace altcoins" argument</h1> <p>The argument that <a href="nostr:naddr1qq9xgunfwejkx6rpd9hqzythwden5te0ve5kzar2v9nzucm0d5pzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqvzqqqr4gumtjfnp">Drivechain</a> will replace shitcoins is <em>not</em> that people will <a href="https://twitter.com/craigwarmke/status/1680371502246514688">sell their shitcoins</a> or that the existing shitcoins will instantly vanish. The argument is about a change <em>at the margin</em> that eventually ends up killing the shitcoins or reducing them to their original insignificance.</p> <p><strong>What does "at the margin" mean?</strong> For example, when the price of the coconut drops a little in relation to bananas, does that mean that everybody will stop buying bananas and will buy only coconuts now? No. Does it mean there will be <a href="https://twitter.com/GoingParabolic/status/1680319173744836609">zero</a> increase in the amount of coconuts sold? Also no. What happens is that there is a small number of people who would have preferred to buy coconuts if only they were a little less expensive but end up buying bananas instead. When the price of coconut drops these people buy coconuts and don't buy bananas.</p> <p>The argument is that the same thing will happen when Drivechain is activated: there are some people today (yes, believe me) that would have preferred to work within the Bitcoin ecosystem but end up working on shitcoins. In a world with Drivechain these people would be working on the Bitcoin ecosystem, for the benefit of Bitcoin and the Bitcoiners.</p> <p>Why would they prefer Bitcoin? Because Bitcoin has a bigger network-effect. When these people come, they increase Bitocin's network-effect even more, and if they don't go to the shitcoins they reduce the shitcoins' network-effect. Those changes in network-effect contribute to bringing others who were a little further from the margin and the thing compounds until the shitcoins are worthless.</p> <p>Who are these people at the margin? I don't know, but they certainly exist. I would guess the Stark people are one famous example, but there are many others. In the past, examples included Roger Ver, Zooko Wilcox, Riccardo Spagni and Vitalik Buterin. And before you start screaming that these people are shitcoiners (which they are) imagine how much bigger Bitcoin could have been today if they and their entire communities (yes, I know, of awful people) were using and working for Bitcoin today. Remember that phrase about Bitcoin being for enemies?</p> <h3>But everything that has been invented in the altcoin world is awful, we don't need any of that!</h3> <p>You and me should not be the ones judging what is good and what is not for others, but both you and me and others will benefit if these things can be done in a way that increases Bitcoin network-effect and pays fees to Bitcoin miners.</p> <p>Also, there is a much stronger point you may have not considered: if you believe all altcoiners are scammers that means we have only seen the things that were invented by scammers, since all honest people that had good ideas decided to not implement them as the only way to do it would be to create a scammy shitcoin. One example is <a href="nostr:naddr1qqyxs6tkv4kkjmnyqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd3vm3c">Bitcoin Hivemind</a>.</p> <p>If it is possible to do these ideas without creating shitcoins we may start to see new things that are actually good.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsg30zdpevukya3kfjen4tfhdft368k25ne87vxqq7cyqntmcexfmgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68aucy8" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsg30zdpevukya3kfjen4tfhdft368k25ne87vxqq7cyqntmcexfmgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68aucy8" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsg30zdpevukya3kfjen4tfhdft368k25ne87vxqq7cyqntmcexfmgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68aucy8" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsg30zdpevukya3kfjen4tfhdft368k25ne87vxqq7cyqntmcexfmgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze68aucy8" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>A list of things artificial intelligence is not doing</h1> <p>If AI is so good why can't it:</p> <ul> <li>write good glue code that wraps a documented HTTP API?</li> <li>make good translations using available books and respective published translations?</li> <li>extract meaningful and relevant numbers from news articles?</li> <li>write mathematical models that fit perfectly to available data better than any human?</li> <li>play videogames without cheating (i.e. simulating human vision, attention and click speed)?</li> <li>turn pure HTML pages into pretty designs by generating CSS</li> <li>predict the weather</li> <li>calculate building foundations</li> <li>determine stock values of companies from publicly available numbers</li> <li>smartly and automatically test software to uncover bugs before releases</li> <li>predict sports matches from the ball and the players' movement on the screen</li> <li>continuously improve niche/local search indexes based on user input and and reaction to results</li> <li>control traffic lights</li> <li>predict sports matches from news articles, and teams and players' history</li> </ul> <p>This was posted first on <a href="https://twitter.com/fiatjaf/status/1477942802805837827">Twitter</a>.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsdftawjf06tgykvvqaxwyrnn3sgx30h54nnx4a22x4uahatqgr89gzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6famvr3" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsdftawjf06tgykvvqaxwyrnn3sgx30h54nnx4a22x4uahatqgr89gzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6famvr3" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsdftawjf06tgykvvqaxwyrnn3sgx30h54nnx4a22x4uahatqgr89gzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6famvr3" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsdftawjf06tgykvvqaxwyrnn3sgx30h54nnx4a22x4uahatqgr89gzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6famvr3" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3cd2ea88:bafdaceb <div class="time" style="margin-left: auto;">2024-10-14 23:14:40</div> </div> <div> <p><img alt="https://yakihonne.s3.ap-east-1.amazonaws.com/c73818cc95d6adf098fbff289cda4c3cf50d5f370d25f0b6f3677231ccd5c890/files/1728942658620-YAKIHONNES3.jpeg" src="" /></p> <p>💻 L’exchange Bitget introduce nuove misure per evitare la quotazione di progetti ad alto rischio, proteggendo i propri utenti da frodi e scam.</p> <p>🛍️ Bitget ha annunciato un inasprimento dei criteri per il listing dei token, imponendo rigorosi controlli legali e tecnici. Tra le misure vi sono la valutazione della qualità del codice e della compliance normativa, proteggendo gli investitori da progetti poco solidi o fraudolenti.</p> <p>🛍️ La Fully Diluted Valuation (FDV) sarà un parametro chiave per filtrare i progetti, insieme ai volumi di trading e alla distribuzione dei token. Anche i token già listati su altri exchange saranno sottoposti a verifiche, incluse le sospensioni e la concentrazione di token in pochi wallet.</p> <p>🛍️ Oltre ai controlli tecnici, Bitget richiederà la presentazione di un business plan per dimostrare la sostenibilità e la crescita del progetto. Anche i token frutto di accordi commerciali dovranno rispettare questi standard, rendendo più sicura l'esperienza per gli utenti.</p> <p>Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia</p> <p>Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs09p5d7lnj6jux2kwczu2n4dznemljl847y0msd79kkkk5ruqe8gczyq7d965gfz6736jghg0xvu0lhfzw6jc9dmtfr00t2962pm46lkkwkydqz5a" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs09p5d7lnj6jux2kwczu2n4dznemljl847y0msd79kkkk5ruqe8gczyq7d965gfz6736jghg0xvu0lhfzw6jc9dmtfr00t2962pm46lkkwkydqz5a" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs09p5d7lnj6jux2kwczu2n4dznemljl847y0msd79kkkk5ruqe8gczyq7d965gfz6736jghg0xvu0lhfzw6jc9dmtfr00t2962pm46lkkwkydqz5a" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs09p5d7lnj6jux2kwczu2n4dznemljl847y0msd79kkkk5ruqe8gczyq7d965gfz6736jghg0xvu0lhfzw6jc9dmtfr00t2962pm46lkkwkydqz5a" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>Um algoritmo imbecil da evolução</h1> <p>Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.</p> <p>No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.</p> <p>É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.</p> <p>Porém, há apenas duas opções:</p> <ol> <li>Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.</li> <li>Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.</li> </ol> <p>Acredito que isso seja uma enunciação decente do argumento <a href="https://en.wikipedia.org/wiki/No_free_lunch_in_search_and_optimization">"no free lunch"</a> aplicado à crítica do darwinismo por William Dembski.</p> <p>A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.</p> <p>Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.</p> <p>Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.</p> <p>Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswy6jnjx9q5c0ss4gg5ha32ryvh50ekk8gua4k797r5pr5z7xstfszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6nkc9vf" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswy6jnjx9q5c0ss4gg5ha32ryvh50ekk8gua4k797r5pr5z7xstfszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6nkc9vf" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswy6jnjx9q5c0ss4gg5ha32ryvh50ekk8gua4k797r5pr5z7xstfszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6nkc9vf" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswy6jnjx9q5c0ss4gg5ha32ryvh50ekk8gua4k797r5pr5z7xstfszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6nkc9vf" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1><code>OP_CHECKTEMPLATEVERIFY</code> and the "covenants" drama</h1> <p>There are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.</p> <p>It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.</p> <p>What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.</p> <p>That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.</p> <hr /> <p>The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.</p> <p>And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.</p> <p>To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.</p> <p>This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqstk7rv8kdd4f4rd00d7raw72dgalj6mnsdt6yz6tte7urs2vdpucszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6j69xry" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqstk7rv8kdd4f4rd00d7raw72dgalj6mnsdt6yz6tte7urs2vdpucszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6j69xry" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqstk7rv8kdd4f4rd00d7raw72dgalj6mnsdt6yz6tte7urs2vdpucszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6j69xry" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqstk7rv8kdd4f4rd00d7raw72dgalj6mnsdt6yz6tte7urs2vdpucszyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6j69xry" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ be7bf5de:09420d0a <div class="time" style="margin-left: auto;">2024-10-14 22:21:23</div> </div> <div> <p>We're excited to launch our new company, <a href="https://nosfabrica.com/">NosFabrica</a>! Our mission is to empower sovereign healthcare by building tools for peer-to-peer healthcare interactions, giving individuals and providers the keys to their own health data. We are building a healthcare application factory, shipping health clients built on Nostr and Bitcoin and bootstrapping a decentralized ecosystem of health tools. We want to onboard thousands of people to Nostr and Bitcoin and enable people to live healthy lives. By utilizing Nostr for identity resolution and bitcoin for payments, we're paving the way for interoperable healthcare applications to exchange health information, and individuals to track and own data that matters to them, connecting to healthcare providers on their health journey.</p> <p><strong>The Problem:</strong></p> <p>The fiat healthcare system has led to a dangerous centralization of healthcare records in the US and globally, where companies ultimately own health data, not individuals. Current protocols of oAuths and APIs have led to bloated and expensive walled gardens (eg, Epic, Cerner) and a honeypot for healthcare hackers, most notably the recent <a href="https://medriva.com/news/healthcare-policy/cyberattack-on-change-healthcare-exposes-fragility-in-us-health-system-infrastructure">Change Healthcare hack</a>, owned by United Healthcare - affecting Avi's work. In 2023, <a href="https://www.medtechdive.com/news/patient-records-exposed-healthcare-data-breaches-double-fortified-health-security/705149/">more than 115 million health records were compromised across 655 data breaches</a>. </p> <p>High cost and poor outcomes are the current product of fiat healthcare. Of the <a href="https://www.kff.org/from-drew-altman/the-two-health-care-cost-crises/">$4.5 trillion annual US healthcare spend</a>, <a href="https://www.pgpf.org/blog/2023/04/almost-25-percent-of-healthcare-spending-is-considered-wasteful-heres-why#:~:text=Approximately%2025%20percent%20of%20healthcare,interventions%20that%20address%20such%20waste.">25% is administrative cost</a>, and half of that is waste. <a href="https://www.businessnewsdaily.com/8693-medical-billing-services.html">6-10% </a>of every healthcare transaction goes to a medical billing middleman. Meanwhile, <a href="https://www.cdc.gov/chronic-disease/about/index.html">6 in 10 Americans</a> has a chronic health condition. </p> <p>A decentralized healthcare application ecosystem would give the healthy sovereign individual the opportunity to take back ownership of their healthcare data, and their health, too. </p> <p><strong>The Solution:</strong></p> <p>NosFabrica means "our factory" in Latin, with of course the nod to Nostr. We aim to build a new, parallel health system on top of open source protocols Nostr and bitcoin. This decentralized healthcare ecosystem will be driven by peer-to-peer interactions between patients and providers. We will move healthcare onto a bitcoin and Nostr standard, giving independent healthcare providers the tools to integrate bitcoin deeper into their practice while maintaining practice sovereignty. </p> <p>By establishing an open-source protocol for the private exchange of health data on Nostr, NosFabrica will set a foundation for a decentralized healthcare system and enable bitcoin-native electronic medical record (EMR) software clients to be built on top of Nostr. </p> <p>We will cut out middlemen in healthcare and build tools that put the individual at the center of the solution. The benefits to patients include owning their own medical data, care discovery at competitive prices, portability of health data, and ultimately improve health outcomes. Doctors will also have the ability to reach a much broader population, reduce their administrative cost, and own their key demographic data such as licenses, credentials, and board certifications. Ultimately, we envision a more robust ecosystem of independent providers, combatting the trend of <a href="https://www.finalis.com/blog/healthcare-m-a-2024-recent-deals-and-trends">M&A and centralization</a> we see under the current fiat healthcare regime.</p> <p>There are several impacts for the broader free and open-source community, as it gives tools for individuals with different healthcare use cases to bring solutions to sorely needed applications such as medical consent, data sharing, clinical trials, and public health.</p> <p><strong>Nostr enables the NosFabrica future in three primary ways.</strong></p> <p><strong>Identity and Access:</strong></p> <ul> <li>User identity exists at the protocol layer via your npub/nsec, instead of the application layer.</li> <li>Users can sign into any application connected to the protocol</li> <li>Users can sign and certify events with their key pair, verifiably demonstrating ownership</li> </ul> <p><strong>Data Standardization</strong></p> <ul> <li>We can develop specific Nostr event "kinds" created for medical data. Vitor has already started by building <a href="https://github.com/nostr-protocol/nips/pull/357">NIP-82 for medical data.</a></li> <li>Existing international data standards and formats such as <a href="https://fhir.org/">FHIR/HL7</a> can be "wrapped" within Nostr events"</li> <li>This structure provides seamless data portability and interoperability across applications.</li> </ul> <p><strong>Persistence and Availability:</strong></p> <ul> <li>HIPAA compliant, encrypted healthcare data is stored on relays</li> <li>Only the owner of the data and those authorized by the owner can decrypt or view the data - in other words, selective disclosure, which is a cornerstone of privacy.</li> </ul> <p>Boosting the Nostr network effect and flywheel will continue, as there are already <a href="https://nostr.band/">40,000 weekly active users</a>. By building healthcare applications on Nostr, we can onboard more people to the ecosystem, who may not be interested in social media.</p> <p><strong>Call to Action:</strong></p> <p>Of course, Nostr and Bitcoin are global protocols and networks that anyone can opt into. While the US gets a lot of the focus due to its expensive and complex healthcare system, there are many challenges globally including healthcare access, affordability, and timely care that we can address with open source tools and permissionless, sound money. We'd love to hear from you if you're interested in joining our mission.</p> <p><strong>About the team:</strong></p> <p>Avi Burra is an experienced healthcare veteran, working as senior director of product management at Optum. He is also the host of <a href="https://fountain.fm/show/0N6GGdZuYNNG7ysagCg9">PlebChain Radio</a>, a leading bitcoin and nostr podcast. With masters in electrical engineering and financial engineering, Avi brings a wealth of healthcare software product experience to NosFabrica.</p> <p>Jon Gordon has worked across the healthcare industry, including in provider strategy, payers and suppliers. Jon has been helping healthcare providers integrate a bitcoin strategy with his consulting business, <a href="https://www.satoshihealth.com/">Satoshi Health Advisors</a>. He also has a double masters in health economics and policy.</p> <p>Vitor Pamplona is the creator of <a href="https://github.com/vitorpamplona/amethyst">Amethyst</a>, the top Android client for Nostr. Vitor previously led a company spun out of the MIT lab utilizing VR for eye exams at EyeNetra. Vitor has a PhD in computer science from MIT.</p> <p><strong>Go to <a href="https://nosfabrica.com/">nosfabrica.com</a> to learn more and follow us along on Nostr!</strong></p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsvrmrylzdzstcdcdqfjuhu8fpweryz2s8qnadr5dc8plfzngphgkszyzl8haw7q6xpmppw6d98cfc9qlkfgr6755t8rn7sv254a8gfggxs5zxzt34" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 0e501ec7:de5ef3a4 <div class="time" style="margin-left: auto;">2024-10-14 21:36:26</div> </div> <div> <p>blog van Tim: <a href="https://timscyclethoughts.blogspot.com">https://timscyclethoughts.blogspot.com</a></p> <p>We zijn nu al bijna een week in het Abtshof! Wat een drukke week is het geweest. Je denkt dan, we zijn op reis, we zijn op vakantie, op het gemak. Helemaal niet waar! We hebben heel veel mee gewerkt aan het project. Vorige keer las je al dat we de namiddag dat we toekwamen hier al bij het verwijderen van plaaster hadden gehad geholpen.</p> <p>Dat hebben we de dag erna ook gedaan, in de ochtend. Ging allemaal goed, tot ik op een bepaald moment op een bepaald moment een stukje plaatster in mijn oog kreeg, dat pikte enorm! Ik kreeg het er ook niet uit, en toen na wat gegoogle, besloot ik om het zo grondig mogelijk uit te spoelen. Een half uur heb ik toen mijn oog onder de kraan gehouden, ik ben nu officieel expert in het oog uitspoelen met water. Het was er toen wel uit en deed geen zeer meer. Maar ik had toch geen zin meer om plaaster uit te breken. Daarom ben ik Jakob gaan helpen met de afwerking van de unit waar Ivan naartoe ging verhuizen. In de namiddag hebben we pieter zijn parket geschaafd: die had een koopje gedaan op het internet, maar het was nogal donker behandeld. We hebben er dus het bovenste laagje van gehaalt, met een groot schaafmachien. Een heel gemakkelijk en handig apparaat, maar wel een beetje eng. Heel goed oppassen wanneer je het hout erin steekt! </p> <p>Er is hier ook een andere wwoof'er, die Teo noemt. Hij komt uit Canada, en maakt een grote reis van België tot naar Spanje, een beetje gelijk ons, maar dan zonder fiets! Echt een leuke jongen, mijn Frans is eventjes niet top genoeg om echt te kunnen babbelen, maar we hebben wel veel fun samen, zeker de laatste dagen. Tim en hij kunnen helemaal opgaan in hun muziek en filmbesprekingen, en morgen doen we zelfs een filmavondje om hem een goeie Belgische film te tonen.</p> <p>Vrijdag heb ik weer bij de afwerking van Ivan's unit geholpen. ik heb de rand van een velux helpen isoleren, en plinten opgemeten en gezaagd. Dat was zo moeilijk, om juist te meten en te zagen! Uiteindelijk had ik er maar 2 van de 8 juist, de anderen waren allemaal 3 mm te lang :( dju toch, volgende keer beter! Gelukkig konden ze makkelijk bijgewerkt worden. Tim en Teo waren ondertussen nog aan het uitbreken, ook leuk, maar ik was blij dat ik daar even aan kon ontlopen.</p> <p>Daarna kregen we onze eerste les van de gloednieuw geimproviseerde houtbewerkingsxursus, gegeven door de meestermeubelmaker-schrijnwerker Jakob! Hij legde ons uit hoe we hout verbindingen kunnen maken, toonde er een heleboel en ging meer in detail bij een redelijk simpele: de half-hout verbinding. Hij legde uit hoe we een beitel moeten hanteren en hoe we zeer recht kunnen zagen (belangrijk als je een verbinding maakt!). Na de uitleg gingen we direct aan de slag: we zouden een rek gaan bouwen voor in de voorraadkamer. Er staan langs 2 muren al rekken, en ons rek zou de stijl van de anderen een beetje volgen de de derde muur helemaal bedekken. Nog niet zo gemakkelijk: de muur en de vloer zijn er nogal ruw en hobbelig, hoe begin je daar te meten? In het rek kunnen we elk 10 keer een halfhout verbinding maken, goeie oefening! </p> <p>Je merkt dat ik vooral heel veel vertel over wat we allemaal gedaan hebben. Niet zo heel veel mijmeringen en emotie. Dat is eigenlijk ook logisch, we zijn vooral heel de tijd bezig. En als je bezig bent mijmer je niet en worden je emoties ook niet zo groot. Ik vind het fantastisch om bezig te zijn. Ik miste dat ook echt de laatste maand, maar nu mis ik ook wel weer het mijmeren. Denk ik? Alleszins, ik wou dat ik ook andere dingen had om op te schrijven. </p> <p>Ik ben wel ook veel bezig geweest met het Bos, het Wondelbos, O Wondelbos, en hoe om te gaan met het verdriet en de boosheid die geboren wordt uit het verlies, hoe te rouwen. Dat is niet zo gemakkelijk. Ik denk dat het belangrijkste is dat ik graag die gevoelens wil eren. Het Bos eren, ook al is die er niet meer. Bien schreef erover, en ik vond het zo mooi, dat ik het heel graag hier zou quoteren. Maar ik weet niet of dat oké is, dus zal het voor later houden.</p> <p>Vetrouw je lichaam, vertrouw je gevoel, ik probeer het zo te zeggen tegen mezelf. Ik vertrouw mijn lichaam. Ik denk dat we veel kunnen vinden in onszelf, als we maar het lef hebben om te luistern. Nu en simpel: ik voel me uitgeput, ik vertrouw erop dat het een goede keuze is om nu te gaan slapen. </p> <p>De dagen na vrijdag zal ik later wel vertellen, of niet. Liefs!</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsddwwxadp5327598e2jz3k7mjvwqykgaf5csc9ts86jwr2ztpx7sgzyq89q8k8qc2nys7xhjk8hpj3cs3pa346muyhdxkaw8ejeyx7tme6glgmg3d" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsddwwxadp5327598e2jz3k7mjvwqykgaf5csc9ts86jwr2ztpx7sgzyq89q8k8qc2nys7xhjk8hpj3cs3pa346muyhdxkaw8ejeyx7tme6glgmg3d" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsddwwxadp5327598e2jz3k7mjvwqykgaf5csc9ts86jwr2ztpx7sgzyq89q8k8qc2nys7xhjk8hpj3cs3pa346muyhdxkaw8ejeyx7tme6glgmg3d" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsddwwxadp5327598e2jz3k7mjvwqykgaf5csc9ts86jwr2ztpx7sgzyq89q8k8qc2nys7xhjk8hpj3cs3pa346muyhdxkaw8ejeyx7tme6glgmg3d" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>Per Bylund's insight</h1> <p>The firm doesn't exist because, like <a href="https://en.wikipedia.org/?curid=83030">Coase said</a>, it is inefficient to operate in a fully open-market and production processes need some bubbles of central planning.</p> <p>Instead, what happens is that a firm is created because an entrepreneur is doing a new thing (and here I imagine that doing an old thing in a new context also counts as doing a new thing, but I didn't read his book), and for that new thing there is no market, there are no specialized workers offering the services needed, nor other businesses offering the higher-order goods that entrepreneur wants, so he must do all by himself.</p> <p>So the entrepreneur goes and hires workers and buys materials more generic than he wanted and commands these to build what he wants exactly. It is less efficient than if he could buy the precise services and goods he wanted and combine those to yield the product he envisaged, but it accomplishes the goal.</p> <p>Later, when that specific market evolves, it's natural that specialized workers and producers of the specific factors begin to appear, and the market gets decentralized.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs8lju5ma9ldukxy6suq4fljawka5zvq6ydcp4dnme45glm8ry7rvgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6uzrgcw" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs8lju5ma9ldukxy6suq4fljawka5zvq6ydcp4dnme45glm8ry7rvgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6uzrgcw" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs8lju5ma9ldukxy6suq4fljawka5zvq6ydcp4dnme45glm8ry7rvgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6uzrgcw" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs8lju5ma9ldukxy6suq4fljawka5zvq6ydcp4dnme45glm8ry7rvgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6uzrgcw" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 83794dfe:e46c6636 <div class="time" style="margin-left: auto;">2024-10-14 19:40:37</div> </div> <div> <p>BRM 200 km – Samstag, 28.09.2024 05:30 – 09:30 Uhr</p> <p>We left on Saturday morning and enjoyed a great day on the bike, meeting some friends along the way and dropped some.</p> <p>with an average speed of 26.5 we needed around 7.3 hours to complete the track.</p> <p>It was a sunny but windy day at the end we even ended up with some cold shower at the end.</p> <p>A Brevet is not a race along the way we had to pick up some proof that we visited certain points like gas stations.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs0yzgd597up6hyn2hgegc8f7cf3u3mmly03uesa3yukjmz56jzx3gzyzphjn0728ftyasp39lcku66hmc2lswap9g4l9a9lcsr9s0yd3nrv0evy59" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>IPFS problems: Conceit</h1> <p>IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry.</p> <p>The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix <a href="nostr:naddr1qqyrqen9xf3nvdpeqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cmdjnnj">that same problem</a> using their own half-baked solution (IPNS) is one example.</p> <p>Other examples are their odd appeal to decentralization in a very non-specific way, their excessive <a href="nostr:naddr1qqyxxdpev5cnsvpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cta4a2e">flirtation with Ethereum</a> and their never-to-be-finished can-never-work-as-advertised <em>Filecoin</em> project.</p> <p>They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqs2nxtluv8kkktzk00rtt80789x4nqpljvudaenzu0sjt8dfnj7ysqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6xy2e9e" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqs2nxtluv8kkktzk00rtt80789x4nqpljvudaenzu0sjt8dfnj7ysqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6xy2e9e" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqs2nxtluv8kkktzk00rtt80789x4nqpljvudaenzu0sjt8dfnj7ysqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6xy2e9e" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqs2nxtluv8kkktzk00rtt80789x4nqpljvudaenzu0sjt8dfnj7ysqzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6xy2e9e" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 599f67f7:21fb3ea9 <div class="time" style="margin-left: auto;">2024-10-14 19:36:50</div> </div> <div> <p>Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin.</p> <h3>Zer behar dut?</h3> <ul> <li>LNbits zorroa</li> <li>Android telefono bat</li> <li>NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216.</li> </ul> <p>💡 NTAG2<em> txartelek esteka </em><em>bat</em>* idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau <a href="https://boltcard.org/">BoltCard</a> bat bihur daiteke.</p> <h3>1. Hedapena aktibatu</h3> <p>Ireki zure LNbits zorroa. Tresna-barran, aktibatu <code>Withdraw Links</code> hedapena eta ondoren joan hedapenera.</p> <h3>2. Erretiratzeko esteka sortu</h3> <p><code>Withdraw Links</code> hedapen orrian, aukeratu <code>Advanced Withdraw Link(s)</code> aukera. </p> <p>Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik, <code>+ Add a new wallet</code> aukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.</p> <p><img alt="configure" src="https://cdn.satellite.earth/9eefb0bcc03e218aac55a5c3bfa06f0cdd59d3b36959c58e3f2f88941cca0d01.webp" /></p> <p>Eman izenburu bat erretiratzeko estekari. </p> <p>Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak.</p> <p>Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora.</p> <p>Aukeran, argazki pertsonalizatu bat gehi dezakezu <code>Use a custom voucher design</code> laukitxoa markatuz, eta .png irudi baten URL-a sartuz.</p> <p>Gogoan izan “assmilking” laukitxoa ez markatzea.</p> <p>Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera.</p> <h3>3. Idatzi esteka NFC txartelean</h3> <p>Zure erretiratzeko esteka berrian, klikatu <code>View LNURL</code> estekan. Ondoren, sakatu <code>Write to NFC</code> botoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.</p> <p><img alt="write" src="https://cdn.satellite.earth/7d290d0c076c724af88089f3ad2bdc7c22cac5bc7bb521e5f28c5646a4fe350d.webp" /></p> <p>✔️ <strong>EGINDA</strong></p> <p>💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko.</p> <p>💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik.</p> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqspu0zu8xrdsd5s476vv4hujggedmmzgef5ydxkqvu5c47swat0gpgzypve7elhmamff3sr5mgxxms4a0rppkmhmn7504h96pfcdkpplvl2jk3h28v" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 3bf0c63f:aefa459d <div class="time" style="margin-left: auto;">2024-01-14 13:55:28</div> </div> <div> <h1>Replacing the web with something saner</h1> <p>This is a simplification, but let's say that basically there are just 3 kinds of websites:</p> <ol> <li>Websites with content: text, images, videos;</li> <li>Websites that run full apps that do a ton of interactive stuff;</li> <li>Websites with some interactive content that uses JavaScript, or "mini-apps";</li> </ol> <p>In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).</p> <p>1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like <a href="https://gemini.circumlunar.space/">Gemini</a>. Maybe the two protocols could coexist.</p> <p>2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.</p> <p>(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)</p> <p>But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?</p> <p>All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.</p> <p>The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.</p> <p>Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.</p> <p>Another idea is that of <a href="https://www.quora.com/Should-web-browsers-have-stuck-to-being-document-viewers/answer/Alan-Kay-11">Alan Kay</a>: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.</p> <hr /> <p>These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.</p> <h2>See also</h2> <ul> <li><a href="nostr:naddr1qqyxgdfe8qexvd34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd7nk4m">On the state of programs and browsers</a></li> </ul> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsyauld5al5cjftjjwyl2a5cvqr90vp8kufsth3uscu7qffhef0u7czyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze686nzjl" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsyauld5al5cjftjjwyl2a5cvqr90vp8kufsth3uscu7qffhef0u7czyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze686nzjl" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsyauld5al5cjftjjwyl2a5cvqr90vp8kufsth3uscu7qffhef0u7czyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze686nzjl" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsyauld5al5cjftjjwyl2a5cvqr90vp8kufsth3uscu7qffhef0u7czyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze686nzjl" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ c73818cc:ccd5c890 <div class="time" style="margin-left: auto;">2024-10-14 18:32:24</div> </div> <div> <p><img alt="image" src="https://yakihonne.s3.ap-east-1.amazonaws.com/c73818cc95d6adf098fbff289cda4c3cf50d5f370d25f0b6f3677231ccd5c890/files/1728930680148-YAKIHONNES3.jpeg" /></p> <p>👋 Nonostante il divieto sulle criptovalute, la Cina mantiene il predominio nel mining di Bitcoin, superando gli Stati Uniti.</p> <p>🎙 Il controllo segreto della Cina sul mining di Bitcoin </p> <p>👋 Tre anni dopo il divieto del 2021, i pool di mining cinesi continuano a dominare l'hash rate globale, con il 55%, mentre gli Stati Uniti si attestano al 40%. Questo successo è dovuto all'ingegnosità dei miners che aggirano le restrizioni locali e sfruttano le risorse energetiche economiche come quelle del Sichuan.</p> <p>🎙 Sopravvivenza del mining e discussioni normative </p> <p>👋 Nonostante la repressione, la Cina potrebbe cambiare atteggiamento: si ipotizza una regolamentazione delle transazioni crypto entro il 2025, segno di un possibile approccio pragmatico nel settore. L'evoluzione delle normative potrebbe permettere a Pechino di mantenere il passo nella competizione tecnologica con gli Stati Uniti.</p> <p>🎙 Il futuro del mining in Cina rimane incerto </p> <p>👋 La Cina resta prudente: qualsiasi apertura dovrà essere accompagnata da una regolamentazione rigorosa per gestire i rischi finanziari e limitare i deflussi di capitale. Tuttavia, il dominio nascosto di Pechino nel mining di Bitcoin riflette la complessità e la resilienza del panorama globale delle criptovalute.</p> <p>Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia</p> <p>Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK</p> <h1>BitcoinReportItalia #Mining #Pool #Cina #Hashrate #StatiUniti #Miners #Pechino #Regolamentazione #Cripto #Bitcoin</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqsrhywctqhy8fnzxnlk5p2w5n3w97mxr5jzcw9x9w832a25ecmmlpgzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfqvu0ru8" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqsrhywctqhy8fnzxnlk5p2w5n3w97mxr5jzcw9x9w832a25ecmmlpgzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfqvu0ru8" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqsrhywctqhy8fnzxnlk5p2w5n3w97mxr5jzcw9x9w832a25ecmmlpgzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfqvu0ru8" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqsrhywctqhy8fnzxnlk5p2w5n3w97mxr5jzcw9x9w832a25ecmmlpgzyrrnsxxvjht2muycl0lj38x6fs702r2lxuxjtu9k7dnhyvwv6hyfqvu0ru8" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> <li> <div style="display: flex; align-items: center; margin-bottom:5px;"> <img src="/static/nostr-icon-purple-64x64.png" class="rounded-circle" width="32" height="32"> @ 45bda953:bc1e518e <div class="time" style="margin-left: auto;">2024-10-14 16:47:18</div> </div> <div> <p>Kaspa Empire - Ceb System - Planet Hithe III</p> <p>The day was hot and the manor sounded eerily quiet compared to the hustle and commotion of the hours prior. On the estate and in the master bedroom specifically, a married pair had become parents. “He looks so much like you Domitius.” Cleolia remarked while stroking the newborn's tiny arms. “He has strong blood.” The father responded smiling fondly sitting on the bedside. A silent nurse was tidying up the apparel and instruments of labour while the couple waited patiently for her exit to have more private discourse. “I am so glad to have born you an heir my love.” Domitius stared intently at his offspring. He had no qualms neglecting obligations to his property and recessed momentarily to celebrate the occasion with his wife. “I will send for the priest, register the child as an Imperial citizen and have him scribed into our family archives, but in the meantime, you must recover. Let a servant girl take our son for a while.” She pouted a playful but exhausted look of non compliance. “You must rest.” He insisted. “How can I let him go when I only just met him? Who are you little man?” She smiled faintly and nodded. “You are right, Domitius, where are you going?” “To the fields, the slaves are behind schedule, our harvest is big and taxes are high. This war is taking it's toll, we must excel to adequately serve the Empire in these pressing times. If the tamed Osteri could only comprehend what is at stake.” Cleolia peered cautiously at the embellishment and carvings on the wooden door knowing that Sethari was standing just beyond. Domitius trailed her gaze. “Don't worry my love, he means well, at least he tries to understand the urgency of my affairs.” He stood up straitening his vest and prepared to leave the room. “Domitius, wait...” He stopped at the door. “What will you tell the priest?” Domitius paused. “I will tell him Albin... Albin Domitius Chevalier.”</p> <p>He left the room and it was quiet, the help entered and swaddled the baby rocking him while Cleolia drifted between sleep and conciousness. “Albin.” She repeated to herself as deep slumber enveloped her.</p> <p>Domitius and his overseer walked briskly out of the manor towards the grain fields squinting as blue Ceb light reflected off the lanscape. “I honour you on the spawn of your son my lord, I hope for a good strong boy, you will be a happy father. I am happy with Seth.” He pounded his chest softly and proudly. “Thank you Sethari, is your son walking yet?” Domitius queried. “No my lord, still crawling on his belly like a beast.” The headman was trying to make his master laugh though Domitius was in a sterner mood having a weight on conscience. “I am in no mood to jest Sethari.” Domitius suddenly clenched his fists. “Get those slaves to work, I cannot have them idling when they should be harvesting.” Sethari made a small bow to his master and started yelling at his Osteri kinsmen, threatening them with a rolled up whip he procured from somewhere inside his tunic, waving it about and cracking it in the air every so often. Domitius picked up a scythe and proceeded to cleave down large swathes of grain. This had a more compelling effect of rallying the straggling workers to action than did the whip. They all toiled together in the pale light of Ceb.</p> <p>Domitius was sweating, sweating and praying for a swift victory over the Jeula Federation. Fighting his small part in a increasingly complicated war, loyal to his Empire in his own unique way even though the conflict was far from home. A powerful loyalty that cannot be bought with riches or broken by coercion. A loyalty born through inheritance and blood.</p> <p>...</p> <p>The priest was in a more jovial mood than usual. The break of routine was a welcome one. The birth was indeed a momentous occasion. Few things seem of much report in a small planetary expansion program. He did not even seem to mind carrying a keg full of honey mead over the rolling hills of the plantation colony. “Domitius comes to church submissions far to infrequently.” The portly man mumbled to himself while wiping the accumulated sweat from his brow. “I eat too well among all these farmers.” The habit of speaking to himself was ordinary for this man of the cloth who always felt socially disconnected from his flock, caring for their souls, protecting their dignity and general well being like a responsible patron. “I feed their spirits, they feed my body, Hahaha. Tonight I will share my good spirits! Hahahaha.” Impressed by his own sense of humour he turned to witness the majestic blue star set over the skyline. Everything turned a silvery gray hue, and then the stars broke through the atmosphere lighting his way. “Clear skies, the blessed stars guide me.” He continued on the path approaching the Domitian manor and rapped a quick knock on the side of the root cellar doors. It creaked open upwards and a tall muscular Osteri took his baggage and let him in. “Thank you Setharis, my arms are weary, ready to fall off, bless you.” Domitius looked up from his bench seat below a glowing lantern. “Good to see you Father Ecknard.” “Dispense with the formalities and bring the dispenser.” He motioned to Setharis who placed the heavy keg on a table next to an assortment of documents, quill and sealed inkpot. “You pour Setharis and I will write. Name?” Ecknard scratches his chin with the quill contemplating his seat and it’s adequacy for the prolonged exercise of scribble. “Name?” Domitius paused. “Albin Domitius Chevalier.” The priest focused, started with his calligraphic art and fashioned the name and ASN standard block height beautifully onto the family records all the while biting his tongue. “He will inherit the colonial estates, all your assets in Kaspa Prime and the parochial offices at Magar Prime. Correct?” “Yes.” Replied Domitius solemnly. “I'll soon have to amend your will and testament. I'd have to make a registry at the parish and send correspondence to Magar Prime. There would be many from the royal courts who'll send their best regards from afar when this news becomes public.” Domitius did not seem as enthusiastic as Ecknard would have liked. “What ails you Domitius?” The priest could not help but make the pun and restrained a grunted laugh inside himself.</p> <p>“I wonder if we should wait before registering and announcing him to Empire.” Ecknard’s expression slowly changed to puzzlement sitting up straight, his belly pushing on the heavy table. “In the voids name why?” “I am concerned... about this war...” “It is on the other side of Magar space!” The priest interjected in astonished retort. “I know father, maybe I am just being overly cautious, but with the Magar Dominus fleet occupied at the divide I am worried about the colonies in the isolated regions.” “Surely Kaspa prime will spare no expense to our defence in the improbable event of an invasion.” “The core keepers will not allow foul play from the Jeul.” “Yes Ecknard, but the fleet is not capable because most of our ships are at the aforementioned objective!” “No, no, no. Suggesting that conflict would happen outside of the divide is practically blasphemy. I cannot imagine insubordination to the Core mandates and the Accords." Domitius remained silently astute and father Ecknard decided to not argue further with the lord. His shoulders sagged. “I will not register the boy in the Imperial records.” “Thank you father.” “What do you know that I fail to see Domitius.” The two men stared at each other from across the table. The hulking bodyguard ever present in body but semi ignorant in mind silently and intriguingly observing the discussion.</p> <p>“The value of sat. It is not calculated well by the common people, no offence father.” The priest piously lifted his hand and with tilted brow motioned. “None taken.” “My son and our blood line is invested with empiric power, if opportunists become aware of his existence and being outside the Magar prime void, we might have problems here on Hithe III.” Cumbersome thoughts and machinations of the mind darkened the mood of the party. Not at all what Father Ecknard was projecting in his minds eye during his arduous walk to what he was hoping, a celebration and getting drunk with an old friend. “The war does not seem to be ending any time soon, how long shall we stall his registration?” The priest reasoned on. “Think of the rites he will not be allowed to partake in at the church. He will be like Osteri.” Ecknard gestured towards Sethari. “This is a small colony Ecknard. My son will be educated as a member of royalty, all on Hithe III will acknowledge his social standing, I am only concerned that the secret be kept from the outside worlds. He will never be considered Osteri, he will know who he is and what his position is in the greater void. When the war is over we will properly introduce him to the families, currently they would be too occupied with politic as it is, and might not offer him due ceremony as they would under more peaceable circumstances.” The priest capitulated and grabbed a mug. “Your secret is safe with me Domitius, the lack of technology on this forsaken planet is good for your purposes, seeing as the only comms service on the planet is in the church tower. That blinking comms station hounds me daily with requests for your return to Magar Prime. The high counsel want to rebalance and need your signature.” Domitius sighed and looked away as if some spectre loomed in front of him.</p> <p>I swear silence on the birth my lord, though let me make a final amendment to your proposal. A bit of extra security shall I say.” Domitius filled a cup of mead for Sethari and himself, becoming more relaxed and hospitable. “I am listening.” “If the risks are as great as you assume, let us pretend for the child's sake that he is Kaspian royalty only, and not true Magar. We then continue his education to the full and not put him in a position where he could compromise himself should he be... void forbid, captured by some opportunistic prospector.” Domitius looked ponderously into his cup. “Ecknard, my son is an infant... If we have to keep the boy in the dark about the true nature of his identity, how long do you predict this war to continue?” Father Ecknard leaned forward... “I sit at the comms desk every night and listen to the chatter. This war... is going to be a long one.”</p> <p>...</p> <h1>scifi</h1> </div> <div class="linkgroup"> <a href="https://yakihonne.com/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">yakihonne.com</a> <a href="https://iris.to/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">iris.to</a> <a href="https://jumble.social/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">jumble.social</a> <a href="/notes/nevent1qqswq2xahfm2uss6r92cdejwt4j3yzeya899u8vjfd59neye9eese3qzypzmm22ne5a6ycah3k24mla3km8tn6mqp4f7ttpmn46cr54uregcugzz2sq" class="btn btn-outline-primary btn-sm">Me</a> </div> </li> </ul> </div> </div> <script> // 处理回车键 function handleKeyDown(event) { if (event.key === 'Enter') { handleSearch(); } } // 处理搜索 function handleSearch() { const keyword = document.getElementById('searchInput').value.trim(); if (keyword) { window.location.href = `/search?q=${encodeURIComponent(keyword)}`; } else { alert('请输入搜索关键词!'); } } </script> </body> </html>





