-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ da23fb98:b98edc3e
2024-10-21 14:25:57
@ da23fb98:b98edc3e
2024-10-21 14:25:57New technologies emerge that enable communication and information sharing without the need for central servers. More efficient, better privacy, peer-to-peer.
Currently, we are accustomed to communicating and sharing information through centralized social networks such as Facebook, Twitter and WhatsApp. These platforms require large server farms that are financed through the sale of user data and advertisements. This centralization leads to privacy concerns, as our data is stored on third-party servers. In addition, these platforms can apply censorship and filtering to the content we share.
New technologies, such as Nostr (with apps like primal) Keet and the peer-to-peer network of Pears, enable communication and information sharing without central servers.
Nostr is a protocol that uses relays, small servers that distribute messages between users. It is an open-source protocol with low costs, giving users more control over their data. Noster is still vulnerable to takedowns of relays, which can be a single point of failure.
Keet, an application built on the peer-to-peer network of Pears, enables video and chat communication without any server. This results in high quality of service, as there is no intermediate server that can reduce the quality. Keet is fully encrypted and uses key pairs for security, eliminating the need for a central server for authentication.
Pears is a peer-to-peer network that enables a decentralized internet where users can communicate directly with each other without the intervention of servers. It is open-source and user-friendly, with automatic software distribution and no investment in central servers. Pears uses 'Pear runtime', a container that ensures that applications can run on different devices. The network benefits from a growing number of peers, as this improves performance through distributed information sharing. It uses a technology that is called Holepunch. You can see this as a modern version of Bittorent.
Adventages These new technologies offer several advantages over centralized social networks:
Privacy: Users retain control over their data as there is no central server where it is stored. Resistance to censorship: The absence of central servers makes censorship and filtering much more difficult. Higher quality of service: Peer-to-peer communication eliminates the limitations imposed by central servers, resulting in better performance and quality. Lower costs: Without the need for large server farms, costs are significantly reduced. More opportunities for developers: Open-source platforms allow developers to build innovative applications without the limitations of centralized platforms.
These emerging technologies have the potential to fundamentally change the way we communicate and share information. They offer a future where users have more control over their data, are free from censorship and can benefit from a more efficient and reliable internet.
Creation... By the way..... this document is generated using #AI with my explanation video's on the subject. Using Google notebooklm https://notebooklm.google.com/
Decentral Social Networks compared (mastodon nostr keet) https://youtu.be/3oxGLPU_WNAh Pears: A peer to peer internet, used in keet https://youtu.be/1pl7SQy93G4New technologies emerge that enable communication and information sharing without the need for central servers. More efficient, better privacy, peer-to-peer.
Currently, we are accustomed to communicating and sharing information through centralized social networks such as Facebook, Twitter and WhatsApp. These platforms require large server farms that are financed through the sale of user data and advertisements. This centralization leads to privacy concerns, as our data is stored on third-party servers. In addition, these platforms can apply censorship and filtering to the content we share.
New technologies, such as Nostr (with apps like primal) Keet and the peer-to-peer network of Pears, enable communication and information sharing without central servers.
Nostr is a protocol that uses relays, small servers that distribute messages between users. It is an open-source protocol with low costs, giving users more control over their data. Noster is still vulnerable to takedowns of relays, which can be a single point of failure.
Keet, an application built on the peer-to-peer network of Pears, enables video and chat communication without any server. This results in high quality of service, as there is no intermediate server that can reduce the quality. Keet is fully encrypted and uses key pairs for security, eliminating the need for a central server for authentication.
Pears is a peer-to-peer network that enables a decentralized internet where users can communicate directly with each other without the intervention of servers. It is open-source and user-friendly, with automatic software distribution and no investment in central servers. Pears uses 'Pear runtime', a container that ensures that applications can run on different devices. The network benefits from a growing number of peers, as this improves performance through distributed information sharing. It uses a technology that is called Holepunch. You can see this as a modern version of Bittorent.
Adventages
These new technologies offer several advantages over centralized social networks:
- Privacy: Users retain control over their data as there is no central server where it is stored.
- Resistance to censorship: The absence of central servers makes censorship and filtering much more difficult.
- Higher quality of service: Peer-to-peer communication eliminates the limitations imposed by central servers, resulting in better performance and quality.
- Lower costs: Without the need for large server farms, costs are significantly reduced.
- More opportunities for developers: Open-source platforms allow developers to build innovative applications without the limitations of centralized platforms.
These emerging technologies have the potential to fundamentally change the way we communicate and share information. They offer a future where users have more control over their data, are free from censorship and can benefit from a more efficient and reliable internet.
Creation...
By the way..... this document is generated using #AI with my explanation video's on the subject. Using Google notebooklm https://notebooklm.google.com/
- Decentral Social Networks compared (mastodon nostr keet) https://youtu.be/3oxGLPU_WNAh
- Pears: A peer to peer internet, used in keet https://youtu.be/1pl7SQy93G4
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 94a90518:2698612b
2024-10-21 14:01:16
@ 94a90518:2698612b
2024-10-21 14:01:16"The distributional consequences of Bitcoin" https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4985877
The original promise of Nakamoto (2008) to provide the world with a better global means of payment has not materialized.
Let's see. Satoshi released the Bitcoin whitepaper on Oct 31, 2008, when the world was going through the global financial crisis: https://www.bitcoin.com/bitcoin.pdf
✅ a purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution ✅ a solution to the double-spending problem using a peer-to-peer network ✅ a record that cannot be changed without redoing the proof-of-work
That's just the foundation on top of which "a better global means of payment" are being implemented: * https://fedimint.org/ * https://cashu.space/ * https://lightning.network/
If these tools (when production-ready) "has not materialized" in a given jurisdiction – that's most likely due to the legal obstacles. The institution just states the enforced outcome in its claim.

most economists argue that the Bitcoin boom is a speculative bubble that will eventually burst
Maybe. But will it burst before the "most economists" do?
the wealth effects on consumption of early Bitcoin holders can only come at the expense of consumption of the rest of society
How is this different from "the wealth effects on consumption" of the ownership class? "400 richest Americans own about $3200B" – 5 times more than the total realized cap of Bitcoin to date which is $620B: - https://chainexposed.com/RealizedCap.html - https://mkorostoff.github.io/1-pixel-wealth/
If the price of Bitcoin rises for good, the existence of Bitcoin impoverishes both non-holders and latecomers.
Unless this is not a zero-sum game, and the Bitcoin would at least raise awareness of impoverishment via currency debasement. - https://www.lynalden.com/broken-money/
But even if it's zero-sum, again – doesn't seem much different from how people are being born into debt.
- https://youtu.be/JIc0i7CvD7k
Imagine you are preparing for a running race you've been preparing your entire life for like 20 years and then the day have come, you are at the start line, and you're getting ready. You're waiting for the for the start signal but then instead of start signal you hear an announcement of the winners. The winners are those who started 30 years before you. That is a current situation. When Boomers were on average 30 years old, they already by this age accumulated almost 20% of entire wealth in the United States. When our generation Millennials were on average 30 years old around 5 years ago we only owned 3%.
Last but not least, some words of wisdom on page 18 :)
the people never holding Bitcoin would be even worse off compared to the Latecomers
- https://youtu.be/JIc0i7CvD7k
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 9e69e420:d12360c2
2024-10-21 13:52:09
@ 9e69e420:d12360c2
2024-10-21 13:52:09rewrite it in markdown
Florida's Amendment 3: A Step Towards Personal Freedom and Economic Growth
Florida voters have a historic opportunity to embrace personal liberty and economic prosperity by supporting Amendment 3 in the upcoming election. This initiative, which would legalize recreational marijuana for adults 21 and older, represents a significant stride towards individual freedom and limited government intervention.
Benefits from a Libertarian Perspective

Personal Freedom
Amendment 3 aligns with the core libertarian principle of personal autonomy. It recognizes that adults should have the right to make their own decisions about marijuana consumption without government interference. This shift away from prohibition respects individual liberty and reduces unnecessary government control over personal choices.
Economic Opportunities
Legalizing recreational marijuana would create a new, thriving industry in Florida. It's projected to generate up to $430 million annually in tax revenue. This influx of funds could potentially lead to lower taxes in other areas or improved public services without increasing the tax burden on citizens.
Criminal Justice Reform
The amendment would significantly reduce arrests for marijuana possession, particularly benefiting minorities who have been disproportionately affected by current laws. This change would allow law enforcement to focus on more serious crimes and reduce the strain on our criminal justice system.
Market Competition
While some argue that Amendment 3 could lead to monopolization, the initiative actually allows for an expanded marketplace and broader licensing. This potential for increased competition aligns with libertarian free-market principles and could lead to better products and lower prices for consumers.
A Stepping Stone to Further Reform
The Libertarian Party of Florida has endorsed Amendment 3, recognizing it as a significant step forward. While the amendment doesn't go as far as many libertarians would like – for instance, it doesn't allow for home cultivation – it's an important milestone in the journey towards full cannabis freedom.
I understand few of you here on NOSTR live in Florida and probably only a portion of them are planning to vote. But as I am NOSTR-only, this will be my only outreach outside of my IRL friends and family. So if you live in Florida and are planning to vote keep an eye out for this box.
Remember, this is just the beginning. As we've seen in other states, initial legalization often paves the way for further reforms. Your support for Amendment 3 could be the first step towards a truly free market for cannabis in Florida, with fewer regulations and more opportunities for entrepreneurs and consumers alike.
Vote yes on Amendment 3 and be part of this historic move towards greater freedom in the Sunshine State.

-
 @ 6bae33c8:607272e8
2024-10-21 11:57:34
@ 6bae33c8:607272e8
2024-10-21 11:57:34Pending Monday Night, where I have a few players going, Week 7 might have been the worst fantasy one I’ve ever had in 30 years. I say this because the three NFFC teams that put up bad scores were in first, first and second place, respectively. These aren’t bad teams having bad days, but good ones.
On one of the BCLs, I had Rhamondre Stevenson, Stefon Diggs, Malik Nabers, Younghoe Koo and Anthony Richardson active. That was the one that performed best, thanks to the Bengals defense, Brock Bowers, Ja’Marr Chase and Javonte Williams, but it’s still very likely to lose.
In the other I put in Kirk Cousins over Joe Burrow, had Jordan Mason, Diggs, Dalton Kincaid, Koo and DeVonta Smith. Drake London, Chase and the Bengals defense will put it around 100 points IF James Conner does something tonight.
But the pièce de résistance is my Primetime team which stacked Texans: CJ Stroud, Diggs, Tank Dell and Dalton Schultz (Dallas Goedert was hurt, Jonnu Smith on the bench). Those four Texans combined for 19.3 points. What’s worse is my opponent had Joe Mixon (26.4 points). I also had the Packers defense (five points) in that game. So basically Mixon outscored half my team 26.4 to 24.3 in that one game.
Based Harrison Butker had only four points, and the only reason I’m at 58.3 pending Monday night is Jahmyr Gibbs’ 32. I have Chris Godwin, J.K. Dobbins and Marvin Harrison still going, but they’ll need 20-plus each to salvage it. At least I left JSN (5.6) and Mason (8.9) on the bench for Harrison. He might do worse, but you’d obviously rather have it be this way than the reverse — as of now.
I went 4-1 ATS in Circa at least, but I’m drawing dead for Q2 and probably the contest too. My only loss was the Packers -2.5 (they won by two). It was honestly one of the more annoying and disastrous games I’ve ever watched.
Seslowsky and I moved on in Survivor, but so did everyone. We had the Bills who were down 10-0, but it was never in doubt. Survivor was impossible for a month, and now it’s so easy.
-
I always get the Jaguars wrong. When I think they’ll bounce back they get blown out by the Bears. When I think they’ll collapse, they blow out the Pats. I didn’t watch the game because I was at Sasha’s basketball game, but I’m sure glad I don’t have any Travis Etienne or Christian Kirk. Both have been supplanted.
-
I had the first pick in the RotoWire Dynasty League this year, took Marvin Harrison, dealt him for Malik Nabers and a pick I eventually used on Bucky Irving. But with my second pick I wanted Brian Thomas, got swiped by the guy one slot ahead of me and had to settle for the ironically named Xavier Worthy. Worthy went higher in re-drafts this year, so it was a bit of a surprise. No one cares, but I often think about how sick of a rebuild it would have been to get both Nabers AND Thomas in one draft.
-
It seems like Drake Maye is a player, but I didn’t watch the game.
-
I thought the Falcons would shoot it out with the Seahawks, which is why I used Cousins over Burrow (who faced a weaker opponent.)
-
Bijan Robinson (and Breece Hall) are starting to earn their status as early first-round picks. Robinson passed the eye test for me too. But the Falcons couldn’t sustain drives. At least London got his as he always does.
-
Jaxon Smith-Njigba got nine yards on six targets. Maybe he’ll catch a pass more than five yards down the field if DK Metcalf misses time with a knee injury. But he’s not usable otherwise.
-
The Mason Rudolph-Calvin Ridley-DeAndre Hopkins Titans are the most pointless team of all time.
-
Amari Cooper saw only five targets and caught a TD, but I imagine he’ll start getting closer to 10 once he gets properly integrated. Keon Coleman might get freed up for big plays. Maybe Kincaid too.
-
Deshaun Watson likely tore his Achilles tendon, which solves that problem. People don’t like Watson for obvious reasons, but I didn’t see as much joy about it in my timeline as I did when the same thing happened to Aaron Rodgers in Week 1 of 2023. I guess Watson was just accused of 20-plus sexual assaults, while Rodgers made them feel like idiots for being so credulous and compliant. Personally, I hope he’s okay so I can make more massage jokes. Aaron Hernandez can’t be the only go-to in this newsletter.
-
Nick Chubb achieved penetration but otherwise had a flaccid performance. Maybe Jameis Winston can bring some Viagra to this offense. Extra strength for Jerry Jeudy who is arguably having a worse career than Henry Ruggs.
-
I know the Browns didn’t mount much of an offense, but would it kill the Bengals to give the best receiver in the NFL more than six targets per game?
-
Tank Dell (zero points) dropped a perfectly thrown TD on the Texans’ first drive. That was 12 points left on the table right away and set the stage for the rest. The Texans run the ball way too much and also played for the field goal at the end which predictably wound up costing them the game. Their pace is glacial too. In DeMeco Ryans’ defense, the offensive line couldn’t pass-block to save its life. CJ Stroud attempted only 21 passes, completing 10 for 86 yards.
-
Jordan Love spread the ball around, but he’s not targeting Christian Watson or Jayden Reed. Reed (who was my biggest regret for not drafting) has been playing through an ankle injury, so maybe that explains it somewhat. But Romeo Doubs and Dontayvion Wicks out-targeted them 16 to six. Maybe Reed’s a buy-low.
-
To understand how bad Stroud’s game was, consider even Anthony Richardson had 129 yards, and he rushed for 56. Richardson is basically a poor man’s Justin Fields right now, and Fields lost his job.
-
I picked up Jonnu Smith in a couple leagues this week, but didn’t have the foresight to start him. With Tua Tagovailoa coming back, I expect to use Smith regularly as he’s the No. 3 option.
-
Tua is just a league-average QB, but apparently there is no one in the NFL more important to his team.
-
For whatever reason Sam LaPorta is just not an important part of this offense, and it’s not because of Jameson Williams.
-
There were only eight incomplete passes in the Lions-Vikings.
-
Saquon Barkley annihilated the Giants, and they deserve it. Of course, Jalen Hurts stole two goal-line TDs. DeVonta Smith should have just sat this game out.
-
The Giants offensive line without Andrew Thomas is the nut low, and Daniel Jones is probably the last QB you’d pick to handle that. I’ve seen deer navigate highway headlights more proficiently. The only thing the Giants do well is rush the passer.
-
I can’t lie — I turned off the late games at halftime. The Indiginous Peoples were up 27-0, the Chiefs-Niners was an ugly slog, and the other game was Raiders-Rams.
-
The Chiefs are so ugly and so good. They just get the first down when they need to, no matter whether it’s the carcass of Kareem Hunt, Mecole Hardman, Noah Gray, or Patrick Mahomes scrambling. It’s barely watchable.
-
George Kittle is the TE1, but now Brandon Aiyuk is probably out for the year, no one seems to know if or when Christian McCaffrey is back, oft-injured Deebo Samuel left the game with an illness and even Mason is playing through a separated shoulder.
-
Jayden Daniels left early with a rib injury, meaning one of 12 teams in my league did ever-so-slightly worse than my CJ Stroud ones over a full game. It sounds like the injury isn’t serious, but that doesn’t mean he’ll be back next week. If there were ever a team against which to lose your star QB and have it not matter, it’s the 2024 Panthers.
-
But for Brock Bowers and Maxx Crosby, the Raiders would be as pointless as the Titans.
-
The Jets-Steelers was a weird game. The Jets had it under total control, up 15-6 late in the first half, Aaron Rodgers throws a ball off Garrett Wilson’s chest that gets picked, the Steelers score and dominate the rest of the game.
-
Davante Adams wasn’t a big factor — he turns 32 in December, keep in mind — and the Jets are now 2-5.
-
The Jets for God knows what reason take shotgun snaps on 3rd- and 4th-and-1. They have to complete a seven-yard pass to get one yard. It’s the opposite of the Eagles’ ass-smash which makes the game so much easier.
-
Russell Wilson got booed early, but turned in a nice game with deep touch throws to George Pickens and Pat Freiermuth. Najee Harris had another good game, but Jaylen Warren now looks viable too, especially now that someone can throw short passes with a modicum of touch.
-
I’m not a fan of two Monday Night games. Just overkill.
-
-
 @ 6bf975a0:65de1244
2024-10-21 11:56:28
@ 6bf975a0:65de1244
2024-10-21 11:56:28Мы создаем небольшие редакции (4 человека на каждую) новостей декабря 2040 года небольшого российского города (реальный город, откуда вы родом, на выбор).
В первый день начала работы редакция рассказывает о том, каким стал её населенный пункт в 2040 году.
Медиа работает на протяжении двух недель и ежедневно выпускает новости на мультимедийной основе — от текстов до видео.
Ежедневно каждая редакция выпускает 2 информационно-новостных текста с иллюстрациями, один видеосюжет. Еженедельно — один короткий аудиоподкаст.
Техническая основа проекта
- Площадка для публикации контента редакции — специально созданный профиль в Nostr;
- Инструменты создания легенды про населённый пункт: генеративные текстовые нейросети;
- Инструменты создания медиаконтента: нейросети для генерации изображений, видео, создания музыки и звука.
Рабочая среда проекта
- Docs.iris.to — будут созданы таблицы для контент-планов по проектам для отслеживания и корректировки хода их выполнения;
- Комментарии и обсуждения проектов включены в docs.iris.to.
Критерии успешного выполненного проекта
- Разнообразие мультимедийного контента: использованы все доступные форматы. Звук, текст, изображения, видео;
- Качество созданного контента: тексты — вычитанные, отредактированные, изображения — отобранные с точки зрения соответствия действительности (люди с нормативным количеством конечностей, не зомби) etc;
- Регулярность публикации контента: редакции масс-медиа публикуют новости ежедневно.
Правила создания контента
- Сгенерированный контент не должен нарушать местное законодательство. Контент размещён в созданных авторами профилях, поэтому ответственность за его содержание несут авторы.
- Сгенерированный контент не должен призывать к насильственным или агрессивным действиям в отношении кого бы то ни было, а также не должен содержать унижающих, оскорбительных оценок любых социальных групп по любым характеристикам.
- 2040-ой — это наши надежды на будущее, возможности, которые, мы верим, будут реализованы. В будущем мы преодолеваем экологические и экономические проблемы.
Ссылки на проекты оставляйте в таблицах с контент-планами
-
 @ 6bf975a0:65de1244
2024-10-21 10:06:18
@ 6bf975a0:65de1244
2024-10-21 10:06:18- Какие этические проблемы могут возникнуть в связи с широким распространением VR/AR-технологий? (Например, приватность, зависимость, манипуляция, влияние на социальные взаимодействия.) В своё время именно этические проблемы не позволили Google Glass стать мэйнстримом.
- Насколько реалистично ожидать, что VR/AR заменят традиционные способы потребления медиа? Какие факторы могут этому способствовать или препятствовать? (Например, цена, доступность, удобство использования, социальное принятие.)
- Насколько вероятно, что метавселенная станет «еще одним слоем интернета», а не его полной заменой? (Рассмотреть текущие тенденции развития интернета и технологические ограничения.)
- Какие этические дилеммы связаны с использованием ИИ для таргетированной рекламы и персонализации контента? (Например, манипуляция потребительским выбором, дискриминация, распространение дезинформации.)
- Может ли гиперперсонализация привести к «информационному изоляционизму» и снижению социальной когезии? Как этого избежать? (Рассмотреть важность «слабых связей» по Марку Грановеттеру.)
- Как унификация платформ и облачные технологии повлияют на медиаиндустрию?
- Как можно противостоять «несоциальности» современных социальных медиа и создать более инклюзивную и полезную цифровую среду?
- Децентрализация и современные социальные медиа: смогут ли новые платформы веб 3.0 потеснить в популярности существующие крупные соцсети? Либо последние позаимствуют новые технологии и задавят в зародыше новые проекты
-
 @ ec42c765:328c0600
2024-10-21 07:42:48
@ ec42c765:328c0600
2024-10-21 07:42:482024年3月
フィリピンのセブ島へ旅行。初海外。

Nostrに投稿したらこんなリプライが
nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5
nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj
(ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…)
そういえばフィリピンでビットコイン決済できるお店って多いのかな?
海外でビットコイン決済ってなんかかっこいいな!
やりたい!
ビットコイン決済してみよう! in セブ島
BTCMap でビットコイン決済できるところを探す
本場はビットコインアイランドと言われてるボラカイ島みたいだけど
セブにもそれなりにあった!

なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ
いざタピオカミルクティー屋!

ちゃんとビットコインのステッカーが貼ってある!

つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら
店員「ビットコインで支払いはできません」
(えーーーー、なんで…ステッカー貼ってあるやん…。)
まぁなんか知らんけどできないらしい。
店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった
結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った
タピオカミルクティー
話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった
法定通貨の味がした。

どこでもいいからなんでもいいから
海外でビットコイン決済してみたい
ビットコイン決済させてくれ! in ボラカイ島
ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい
でもやめてしまった店も多いらしい
でも300もあったならいくつかはできるとこあるやろ!
nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l
行くしかねぇ!
ビットコインアイランドへ
フィリピンの国内線だぁ

``` 行き方: Mactan-Cebu International Airport ↓飛行機 Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport) ↓バスなど Caticlan フェリーターミナル ↓船 ボラカイ島
料金: 飛行機(受託手荷物付き) 往復 21,000円くらい 空港~ボラカイ島のホテルまで(バス、船、諸経費) 往復 3,300円くらい (klookからSouthwest Toursを利用)
このページが色々詳しい https://smaryu.com/column/d/91761/ ```
空港おりたらSouthwestのバスに乗る
事前にネットで申し込みをしている場合は5番窓口へ

港!

船!(めっちゃ速い)

ボラカイついた!

ボラカイ島の移動手段
セブの移動はgrabタクシーが使えるがボラカイにはない。
ネットで検索するとトライシクルという三輪タクシーがおすすめされている。
 (トライシクル:開放的で風がきもちいい)
(トライシクル:開放的で風がきもちいい)トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。
最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。
これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。
Hop On Hop Off バス:
https://www.hohoboracay.com/pass.php
一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。
 バスは現金が使えないので事前にどこかでカードを買うか車内で買う。
バスは現金が使えないので事前にどこかでカードを買うか車内で買う。私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。
バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。
逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。
現実
ボラカイ島 BTC Map
 BTC決済できるとこめっちゃある
BTC決済できるとこめっちゃあるさっそく店に行く!
「bitcoin accepted here」のステッカーを見つける!
店員にビットコイン支払いできるか聞く!
できないと言われる!
もう一軒行く
「bitcoin accepted here」のステッカーを見つける
店員にビットコイン支払いできるか聞く
できないと言われる
5件くらいは回った
全部できない!
悲しい
で、ネットでビットコインアイランドで検索してみると
旅行日の一か月前くらいにアップロードされた動画があったので見てみた
要約 - ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した - ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた - しかし実際には3~5人だった - 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった - ビットコイン決済があまり使われないので店員がやり方を忘れてしまった - 店は関心を失いpouchのアプリを消した
https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ
なるほどね~
しゃあないわ
聖地巡礼
動画内でpouchのオフィスだったところが紹介されていた
これは半年以上前の画像らしい

現在はオフィスが閉鎖されビットコインの看板は色あせている
 おもしろいからここに行ってみよう!となった
おもしろいからここに行ってみよう!となったで行ってみた
看板の色、更に薄くなってね!?

記念撮影
 これはこれで楽しかった
これはこれで楽しかった場所はこの辺
https://maps.app.goo.gl/WhpEV35xjmUw367A8
ボラカイ島の中心部の結構いいとこ
みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ!
最後の店
Nattoさんから情報が
なんかあんまりネットでも今年になってからの情報はないような…https://t.co/hiO2R28sfO
— Natto (@madeofsoya) March 22, 2024
ここは比較的最近…?https://t.co/CHLGZuUz04もうこれで最後だと思ってダメもとで行ってみた なんだろうアジア料理屋さん?

もはや信頼度0の「bitcoin accepted here」

ビットコイン払いできますか?
店員「できますよ」
え?ほんとに?ビットコイン払いできる?
店員「できます」
できる!!!!
なんかできるらしい。
適当に商品を注文して
印刷されたQRコードを出されたので読み取る
ここでスマートに決済できればよかったのだが結構慌てた
自分は英語がわからないし相手はビットコインがわからない
それにビットコイン決済は日本で1回したことがあるだけだった
 どうもライトニングアドレスのようだ
どうもライトニングアドレスのようだ送金額はこちらで指定しないといけない
店員はフィリピンペソ建ての金額しか教えてくれない
何sats送ればいいのか分からない
ここでめっちゃ混乱した
でもウォレットの設定変えればいいと気付いた
普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった
設定を変更したら相手が提示している金額を入力して送金
送金は2、3秒で完了した
やった!
海外でビットコイン決済したぞ!
ログ

PORK CHAR SIU BUN とかいうやつを買った
 普通にめっちゃおいしかった
普通にめっちゃおいしかったなんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった
ここです。みなさん行ってください。
Bunbun Boracay
https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6
めでたしめでたし
以下、普通の観光写真
セブ島
ジンベエザメと泳いだ

スミロン島でシュノーケリング

市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた

ボホール島
なんか変な山

メガネザル

現地の子供が飛び込みを披露してくれた

ボラカイ島
ビーチ


夕日

藻

ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも)
北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった

プカシェルビーチ



おわり!
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 9e69e420:d12360c2
2024-10-21 02:44:56
@ 9e69e420:d12360c2
2024-10-21 02:44:56long form note
just a test
using habla
I guess I can just copy & paste markdown. Here is a meme to test photos insertion ![[https://i.nostr.build/ob0weHDqLkzAxrcR.jpg]]

What else can this do? Links? Let's try.... https://i.nostr.build/ob0weHDqLkzAxrcR.jpg
And a list: * Item 1 * Item 2 * Item 3
-
 @ 59df1288:92e1744f
2024-10-21 02:37:05
@ 59df1288:92e1744f
2024-10-21 02:37:05null
-
 @ a012dc82:6458a70d
2024-10-21 02:09:34
@ a012dc82:6458a70d
2024-10-21 02:09:34Table Of Content
-
The Ordinals Revolution
-
Celebrating Ordinals: A Red Carpet Welcome
-
The Critics and the Supporters
-
The Impact on Bitcoin Mining
-
The Changing Landscape of Revenue in Mining
-
The Road Ahead: Adapting to Change
-
The Ripple Effect: More Applications on the Horizon
-
Conclusion
-
FAQ
In the dynamic world of cryptocurrencies, innovation is the name of the game. The latest entrant to this ever-evolving landscape is Ordinals, a protocol that has taken the crypto community by storm. Ordinals enables users to mint NFT-like assets, known as inscriptions, directly onto the Bitcoin blockchain. This groundbreaking development has led to a surge in demand for computing power, significantly raising transaction fees as miners compete for available resources. The advent of Ordinals marks a new era for Bitcoin, opening up a world of possibilities for users and miners alike.
The Ordinals Revolution
The introduction of Ordinals has been met with a wave of enthusiasm from the crypto community. With nearly 12 million inscriptions now created on top of the Bitcoin blockchain, the hype around this new technology is palpable. The ability to launch NFT-like assets on the Bitcoin network, which boasts one of the most powerful brands in the crypto industry, is a significant milestone. This development has not only expanded the functionality of the Bitcoin network but also added a new dimension to the world of cryptocurrencies.
Celebrating Ordinals: A Red Carpet Welcome
The arrival of Ordinals deserves a red carpet welcome. It represents a significant step forward in the evolution of Bitcoin and the broader crypto industry. As we look to the future, it is clear that Ordinals will play a crucial role in shaping the trajectory of Bitcoin mining and the broader crypto landscape. So, let's roll out the red carpet and celebrate the arrival of Ordinals in style. The future of Bitcoin and the crypto industry is bright, and Ordinals is leading the way. This is not just a celebration of a new technology, but a celebration of the limitless potential of the crypto industry.
The Critics and the Supporters
However, the advent of Ordinals has not been without its critics. Some experts have voiced concerns about the protocol's vulnerability to scams and slower transaction speeds. They argue that the rush to embrace this new technology could lead to unforeseen consequences. But these criticisms overlook the potential of Ordinals to revolutionize Bitcoin mining and the broader crypto industry. On the other hand, supporters of Ordinals see it as a game-changer, a technology that will have a net positive effect on the profitability of Bitcoin mining in the long run. They argue that the benefits of Ordinals far outweigh the potential risks.
The Impact on Bitcoin Mining
The rising popularity of Ordinals has been a boon for Bitcoin miners. Bitcoin's scalability is limited to around seven transactions per second (TPS), so a sudden increase in demand for computing power often translates to higher fees. This shift in profitability away from rewards, which are reduced by 50% every four years due to halving, is something that many miners welcome. The introduction of Ordinals has essentially created a new revenue stream for miners, making the mining process more lucrative and sustainable in the long run.
The Changing Landscape of Revenue in Mining
For the second time in history, miners are not fully dependent on block rewards. The current period of high transaction fees has changed the perception of the sustainability of Bitcoin mining. In the future, transaction fees will likely become the main source of revenue in the mining industry. As Bitcoin's adoption and usability increase, miners are expected to earn more from commissions than via block rewards. This shift in the revenue model could potentially lead to a more stable and sustainable mining industry.
The Road Ahead: Adapting to Change
The introduction of Ordinals has brought about significant changes, and Bitcoin miners will need to adapt to remain profitable. This includes upgrading mining infrastructure and software and optimizing energy efficiency to address the challenge of reduced block rewards. The advent of Ordinals has essentially raised the bar for miners, requiring them to be more innovative and efficient in their operations. This could lead to the development of more advanced mining technologies and practices.
The Ripple Effect: More Applications on the Horizon
The arrival of Ordinals has also opened the door for more applications to be written on top of the Bitcoin protocol. This development is expected to lead to more use cases and a greater boost in Bitcoin adoption in the next couple of years. The introduction of Ordinals could potentially spur a wave of innovation in the crypto industry, leading to the development of new applications and services that leverage the power of the Bitcoin network.
Conclusion
Despite the concerns raised about Ordinals, it is essential to view this technology as an opportunity rather than a threat. Experimenting with the Bitcoin network's capabilities can only help support the overall ecosystem, both now and in the future. The introduction of Ordinals represents a significant step forward in the evolution of Bitcoin and the broader crypto industry. It is a testament to the endless possibilities that the world of cryptocurrencies offers.
FAQ
What is Ordinals? Ordinals is a new protocol that allows users to mint NFT-like assets, known as inscriptions, directly onto the Bitcoin blockchain.
How does Ordinals impact Bitcoin mining? The introduction of Ordinals has led to a surge in demand for computing power, significantly raising transaction fees as miners compete for available resources. This shift in profitability away from rewards is welcomed by many miners.
How does Ordinals affect the sustainability of Bitcoin mining? The high transaction fees brought about by Ordinals have changed the perception of the sustainability of Bitcoin mining. It has shown that miners are not fully dependent on block rewards, suggesting a more sustainable future for the mining industry.
How does Ordinals contribute to the evolution of Bitcoin? Ordinals has added a new dimension to Bitcoin by enabling the creation of NFT-like assets on its network. This has opened the door for more applications to be written on top of the Bitcoin protocol, leading to more use cases and a greater boost in Bitcoin adoption.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 623ed218:fa549249
2024-10-20 21:38:48
@ 623ed218:fa549249
2024-10-20 21:38:48Donald Trump, Fry Cook
I'd seen some photos of Trump working at Mcdonalds floating around. I'm only now realizing it wasn't AI-generated...
https://youtu.be/gCFE24BtqGo?si=ha4nd4a4F5fR4SHf
originally posted at https://stacker.news/items/732974
-
 @ 623ed218:fa549249
2024-10-20 20:22:55
@ 623ed218:fa549249
2024-10-20 20:22:55So, I just spent about half an hour attempting to connect my Minibits ecash wallet to Stacker.News using NWC. As I found a way to make it work, I figured I'd make a post so hopefully in the future someone can save a little time.
When you create a NWC string in Minibits, it doesn't differentiate between connections for sending payments, and connections for receiving them. I attempted to just paste the same connection string in both fields with no luck, as well as attempting to generate a new connection string for use in the "receive" field. This also was unsuccessful.
The Workaround:
The solution I found is to just paste the connection string from Minibits in the "for sending" field and save. Once this is done, go back to the wallet connection selection page, and select lightning address for receiving payments. Enter your @minibits.cash address into the field and save.
This worked for me, I am now able to send and receive zaps to my Minibits wallet from Stacker.News.
Things could change in the future, if they do I will try my best to report back on any new info I have regarding this.
Woof!
originally posted at https://stacker.news/items/732888
-
 @ 623ed218:fa549249
2024-10-20 19:35:54
@ 623ed218:fa549249
2024-10-20 19:35:54Get On Zero (Fiat): 2024 Edition

Theory:
The #GetOnZero movement advocates transitioning entirely to Bitcoin, abandoning holding fiat currency in daily life. The goal is to maintain maximal exposure to Bitcoin while minimizing exposure to traditional fiat currencies. Proponents of #GetOnZero believe that by converting all their money into Bitcoin, they not only commit fully to the Bitcoin ecosystem but also protect themselves against inflation and other potential issues with fiat money.
While I wouldn't say there is much debate on exactly what qualifies as being "OnZero", there are definitely a number of different interpretations. Some may argue that truly being "OnZero" requires completely opting out of fiat rails, and finding ways to directly pay in bitcoin for all expenses. Personally, I take a slightly more relaxed view, simply pushing for the avoidance of fiat currencies and instruments as savings and investment vehicles, and keeping all our stored value in bitcoin.
While the value of being completely "OnZero" are apparent during periods of significant price appreciation against the dollar, I will be the first to acknowledge the potential losses that could result from holding to this strategy during periods of significant negative price action. To this end, I have created a 3-tiered system of strategies, with each strategy tailored to specific market conditions. I understand that the most zealous lazer-eyed #GetOnZero proponents, the strategies below may not align with their personal philosophy on what the strategy is supposed to represent.
Take what you will from the strategies laid out below, it is my intent to provide a systematic list of actions to be taken in different market conditions, in an attempt to make things more approachable to the average reader.
GetOnZero Strategies:
Bull Strategy: Expenses on credit, income to Sats, sell once monthly to pay Fiat bills
Description: This approach involves using credit cards or lines of credit for all expenses throughout the month. Meanwhile, income is converted immediately into bitcoin (sats). At the end of the month, a portion of Bitcoin is sold to cover the credit card bill and any other fiat-denominated obligations.
- Pros:
- Maximizes bitcoin holdings throughout the month, allowing for potential price appreciation.
- Credit cards can offer rewards that can further offset expenses or even be converted into sats.
- Cons:
- Requires a disciplined approach to avoid accumulating debt.
- May expose you to volatility risk if bitcoin's value drops before the end-of-month payment.
Crab Strategy: Expenses on credit, reserve Fiat until EOM, pay bills, stack difference
Description: In this method, income is initially held in fiat. Expenses are paid using credit, but instead of immediately converting fiat to bitcoin, it is done at the end of the month, once all bills are paid. The remaining balance (after paying bills) is then converted to bitcoin.
- Pros:
- Provides a safety net against bitcoin price volatility during the month.
- Ensures that all fiat obligations are covered before committing to bitcoin.
- Cons:
- May reduce bitcoin exposure if the price appreciates during the month.
- Requires discipline to consistently allocate remaining fiat to bitcoin.
Bear Strategy: Fiat Buffer (aka: NotOnZero...)
Description: This approach involves maintaining a fiat buffer to handle any unexpected expenses or market volatility. While income is mostly converted to bitcoin, a portion remains in fiat to provide liquidity and flexibility.
- When to use: This strategy may be appropriate in times of severe market uncertainty or for those transitioning gradually to the #GetOnZero lifestyle.
- Pros:
- Offers a cushion for unexpected fiat expenses, reducing the need to sell bitcoin unexpectedly.
- Can be adjusted based on individual risk tolerance and liquidity needs.
- Cons:
- Reduces total exposure to bitcoin, potentially missing out on gains.
- May require active management to maintain the buffer and adjust it according to changing circumstances.
Liquidity Considerations:
Bitcoin's high correlation with global liquidity makes it a reliable barometer for macroeconomic conditions. According to recent analysis by Lyn Alden and Sam Callahan, bitcoin's price aligns with global liquidity trends in 83% of 12-month periods, demonstrating its sensitivity to central bank policies and money supply changes. (Bitcoin: A Global Liquidity Barometer)
Given bitcoin's responsiveness, different #GetOnZero strategies may be effective depending on liquidity environments:
-
The Bull Strategy is ideal in increasing liquidity environments, where bitcoin's value is more likely to rise, and the individual can benefit from holding sats longer before converting.
-
The Crab Strategy is suitable for flat or slightly decreasing liquidity environments, as it provides a way to manage fiat expenses and avoid forced bitcoin sales during short-term downturns.
-
The Bear Strategy is a possible strategy for periods of sharp reductions in liquidity which have historically accompanied bear markets in bitcoin. It is specifically not being "On Zero", but that doesn't mean there might not be times where that itself is a good strategy.
The paper emphasizes that while bitcoin's long-term price direction generally follows liquidity changes, short-term deviations can occur due to idiosyncratic events or internal market dynamics. Savers could monitor bitcoin-specific metrics like the Market Value to Realized Value (MVRV) Z-score to gauge potential overvaluation or undervaluation periods. This, combined with global liquidity trends, allows for more informed strategy adjustments.
Pup's #GetOnZero Workflow:
So how do I live my life "OnZero"? Let's dig into it.
At present, my workflow most matches the "Bull Strategy", and I use Fold to make this an easy process.
Fold, (who is not sponsoring this), allows me to direct deposit my fiat paychecks and have them auto-converted to bitcoin. Within the app, I have 3 balances, A cash balance (Sutton Bank), a bitcoin balance (BitGo), and a reward balance.
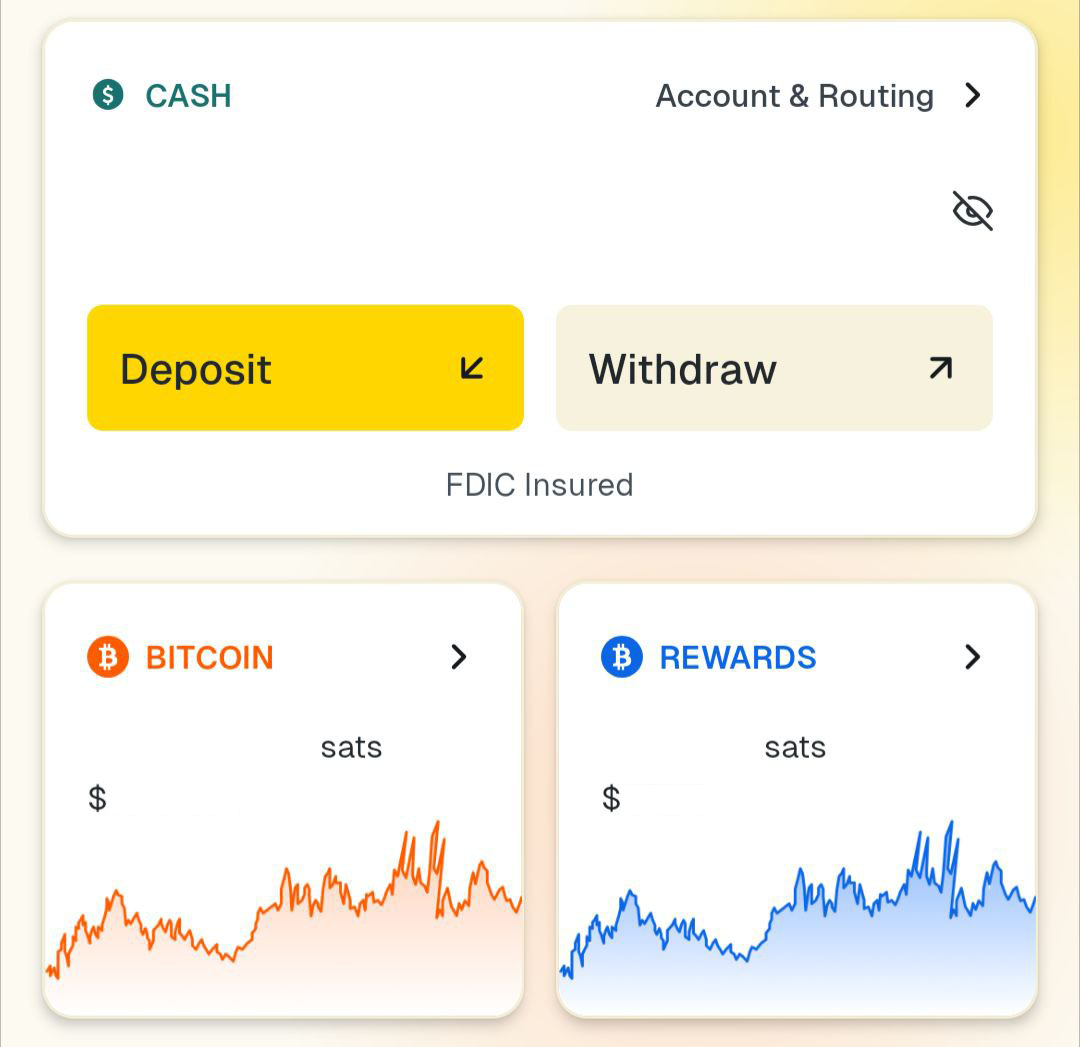
I use credit for all my spending throughout the month, matching fiat expenses to various cards that allow me to get the most rewards for using them. My paychecks are direct-deposited to Fold and auto-converted to bitcoin where it is held until the end of the month when my fiat bills are due. At the end of the month, I utilize Fold's "Push to Card" feature to sell the exact amount needed to make my fiat payments where it then appears ~10 minutes later in my cash balance.
 \
From there, its just a matter of paying my fiat bills via ACH, at which time Fold actually gives me sats back as rewards!
\
From there, its just a matter of paying my fiat bills via ACH, at which time Fold actually gives me sats back as rewards!Additionally, Fold has partnerships with a number of companies and offers sats back on giftcard purchases. I will take advantage of these deals on occasion when the rewards exceed what I would earn from putting expenses on a credit card and paying it via ACH.
This section has ended up sounding way more like an advertisement than I intended, but I really can't recommend their services enough if they are available where you live. Fold greatly simplifies my Bitcoin life by bridging the worlds of fiat and bitcoin.
I know some may take issue with holding sats with a custodian, personally I just keep about a month of expenses there. I wholly recommend keeping your bitcoin in cold storage, but I can accept some risk on a small portion of my sats for the convenience it brings to my life. Between the option of keeping 1 month of expenses with a custodian in fiat, or in bitcoin, I'll happily choose the latter, but these are risks and tradeoffs that I have chosen to accept after doing my own research, and I would implore you to do your own research as well.
To bring this all to a close, I hope you have found this article informative, or at least entertaining. Feel free to reach out if you have any questions about anything I have discussed here!
Block 866568 - MSK 1458
Digging Deeper:
Hey there, I hope you enjoyed this read! If you did, and would like to read more of my barks, follow the links below!
-
Curious how I found Bitcoin? Read "Paw Prints to the Timechain"
-
Bitcoin meets psychology? I touch on this in "Maslow's Apex"
-
Want to understand the basics of Bitcoin? Read "Bitcoin Best Practice"
-
If you like seeing bad media takes unpacked, check out "Pup's Double-Takes"
External Resources:
- Want to earn rewards on your mortgage? Use my referral to earn 20,000 free sats at sign up!
- Do you like sharing Bitcoin content and earning sats for doing so? Join me at Stacker.news!
Special Mention:
- @realBitcoinDog: Without whose persistent nudging, I wouldn't be writing here.
...Woof!
originally posted at https://stacker.news/items/732833
- Pros:
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ bcea2b98:7ccef3c9
2024-10-20 17:33:12
@ bcea2b98:7ccef3c9
2024-10-20 17:33:12originally posted at https://stacker.news/items/732719
-
 @ bcea2b98:7ccef3c9
2024-10-20 15:50:27
@ bcea2b98:7ccef3c9
2024-10-20 15:50:27The Bitcoin space is constantly evolving with new ideas, technologies, and innovations. From Lightning Network advancements to privacy improvements, there’s always something happening that could change the future of Bitcoin.
What do you think is the most exciting or innovative development in Bitcoin right now? I've been following a lot of privacy related advancement in Bitcoin and LN and look forward to learning about more solutions.
originally posted at https://stacker.news/items/732534
-
 @ 45bda953:bc1e518e
2024-10-20 15:46:40
@ 45bda953:bc1e518e
2024-10-20 15:46:40As I ghost the Bitcoin only Telegram and Discord groups after the historic announcements of RFK Junior and Donald J Trump I perceive mixed emotions among some OG Bitcoin maxi’s. They are mostly happy about the advancing adoption of Bitcoin this cycle but are cautiously disturbed and annoyed by the fact that governments and large institutions are perhaps embracing Bitcoin before individual people have sufficiently decentralised self custodial holdings.
I understand their concerns in this regard but do not share it. This article is an attempt to waylay those fears and hopefully bring a little bit of extra food for thought.
If you will humour me, I am going to quote more scripture. That is the theme of this account. Bitcoin and Biblical Prophecy.
Zechariah Chapter 5
1 : Then I (Zechariah) turned and raised my eyes, and saw there a flying scroll. 2 : And he (an angel dude) said to me “What do you see?” So I answered, “I see a flying scroll. It’s length is twenty cubits and its width ten cubits.” 3 : Then he said to me, “This is the curse that goes out over the face of the whole earth: ‘Every thief shall be expelled,’ according to this side of the scroll; and, ‘Every perjurer shall be expelled, ‘according to that side of it.” 4 : “I will send out the curse,” says the LORD of hosts; “It shall enter the house of the thief and the house of the one who swears falsely by My name. It shall remain in the midst of his house And consume it, with its timber and stones.”
Now I don’t know of any sensible explanations for this scripture other than my own conjecture and speculations. I am not particularly religious and disdain canon/institutional exposition of prophetic scripture because I am highly sceptical of their motives.
But I urge that you, dear reader, extract a little bit of wisdom from a weird and abstract piece of text. Even if it is a complete misinterpretation it is still a useful analogy.
Zechariah claims to see a flying scroll. A flying ledger or list. We all know that scrolls don’t fly and they most certainly do not cover the face of the whole earth. The fact that it is measured in twenty and ten cubits specifically is odd and maybe some numerology luminary can figure out why that is.
I just say it’s twenty one million Bitcoin. Or two hundred and ten thousand blocks. Or ten minute block rewards. Whatever. The blockchain through node runners do cover the face of the whole earth.
What is interesting as well is that this is equated to being a curse. We do not see Bitcoin as a curse? Do we? We see Bitcoin as a blessing rewarding honest men a fair wage for honest work. That does not define a curse.
Oh, but you are not a scammer, a terrorist an extortioner or a thief. Why do criminals prefer fiat cash to Bitcoin?
Because Bitcoin shines light on their activity. On a Bitcoin standard the thief is doomed to a slow death of impoverishment.
Who are they who swear falsely by His name? On the one dollar bill it famously states “IN GOD WE TRUST” Swearing falsely by the divine.
I call BS along with the rest of the Bitcoin community. In physics we trust. In code we trust. In mathematics we trust. In the unbreakable reality of the cosmos we trust. In the mind numbing comments of politicians and calculations of federal reserve bean counters we do not trust.
Politicians have a long history of deception and populations have a long history of not studying history. The Dollar bill LIES.
The governments of the world will embrace Bitcoin and to their own eventual demise.
The ledger will lie in the midst of their buildings and institutions and it will be a testament to their in-efficacious behaviour. The free-market will outperform every possible attempt at service delivery governments will to achieve. On a bitcoin standard their institutions will fall into disrepair because they cannot produce more than they consume through the very nature of their eternally corrupt institution. This counts for all governments. The people will self govern in a harmony that can only be described as utopian. (Compared to Marxist and Keynesian MMT systems) Eventually...
Bitcoin is a CURSE and a BLESSING. It FORCES you to take account of REALITY.
Institutions still cling to their delusions in a changing world and the havoc they will unleash to try and retain their incumbency is pathetic but inevitable.
Stay humble. Stack Sats. Buy out the time. Survive.
We are all Satoshi.
Zechariah Chapter 5
1 : Then I turned and raised my eyes, and saw there a flying scroll. 2 : And he said to me “What do you see?” So I answered, “I see a flying scroll. It’s length is twenty cubits and its width ten cubits.” 3 : Then he said to me, “This is the curse that goes out over the face of the whole earth: ‘Every thief shall be expelled,’ according to this side of the scroll; and, ‘Every perjurer shall be expelled, ‘according to that side of it.” 4 : “I will send out the curse,” says the LORD of hosts; “It shall enter the house of the thief and the house of the one who swears falsely by My name. It shall remain in the midst of his house And consume it, with its timber and stones.”
bitbib
-
 @ 8d34bd24:414be32b
2024-10-20 15:10:47
@ 8d34bd24:414be32b
2024-10-20 15:10:47Check out:
-
God Demonstrates His Power: Part 1 (Egypt)
-
God Defends His Honor: Part 2 (Phillistines)
-
The One True God: Part 3 (Who deserves worship)
In the Old Testament, God’s actions were primarily aimed at proving His existence, His power, and His holiness to Israel. He did many miracles before the Gentiles, but He definitely focused on His chosen people.
In the New Testament, God expands knowledge of Him starting with His chosen people. He also includes others in His promises and knowledge of Him. His miracles go beyond showing who He is. They go to the ultimate miracle — salvation from our sins.
Incarnation
Jesus was God from the beginning. He is “the Alpha and the Omega, the first and the last, the beginning and the end.” (Revelation 22:13) In the Gospels, the Bible tells us how the God and creator of the universe came down to earth and was born physically as a man — becoming the same flesh as His creation.
How an eternal, all-powerful being becomes a zygote in a woman’s womb and is born of a virgin is beyond what any of us can fully understand, but is one of God’s greatest miracles. This allowed our Creator to become our kinsmen redeemer and pay the price for our sins. This allowed our Creator to live a perfect, sinless human life, like we are unable to do, so He could become the ultimate once-for-all sacrifice for our sins.
Jesus’s incarnation, perfect life, and horrible death show us how much our Creator loves us and is willing to do to fix the relationship that we broke with Him.
Miracles
While Jesus lived a perfect life to show us how we should live, he also performed many miracles to show everyone that He was not just a man, but was also God. His miracles included1(footnote copied to bottom):
Physical Healings
-
Healing Peter's mother-in-law of a fever
-
Cleansing a man with leprosy
-
Healing a centurion's paralyzed servant
-
Healing a paralytic lowered through the roof
-
Healing a man's withered hand
-
Restoring sight to two blind men
-
Healing a deaf mute
-
Healing blind Bartimaeus
-
Healing the bleeding woman
-
Restoring a servant's severed ear
Exorcisms
-
Driving out an evil spirit in Capernaum
-
Healing a demon-possessed mute man
-
Casting demons into a herd of pigs
-
Healing the Syrophoenician woman's demon-possessed daughter
-
Healing a boy possessed by a spirit
Nature Miracles
-
Turning water into wine at the wedding in Cana
-
Calming the storm on the sea
-
Feeding the 5,000
-
Walking on water
-
Feeding the 4,000
-
Causing the fig tree to wither
-
Miraculous catch of fish
Raising the Dead
-
Raising the widow's son at Nain
-
Raising Jairus' daughter
-
Raising Lazarus from the dead
Other Miracles
-
Finding the coin in the fish's mouth
-
Jesus' resurrection
Jesus did so many amazing miracles that nobody should doubt that He is the incarnate God.
Of course the most miraculous of His miracles was taking our sins upon Himself, dying on the cross, and then rising from the dead on the third day to prove He had conquered death and sin. This miracle was not primarily for the Jews in Israel. The good news, of what God had done, was witnessed to everyone “in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:8b)
This miracle wasn’t just for Israel. It wasn’t just for Israel’s enemies. It wasn’t just for the Middle East. This miracle was for the whole world. His faithful followers have been copying His word (Bibles) to keep the details of what He has done for us alive. His word has been translated, so those around the globe can read it in their own language. His followers have left their homes to share the good news with those from foreign lands.
God did a miraculous work to change the hearts of those who trust in Him and those people having been sharing what God did for them for almost 2,000 years.
Some have heard the gospel and rejoiced. Some have heard the gospel and rejected it. Even worse, some have tried to stop the spread of the gospel, but God does not allow His word to be stopped.
So far in history, some have seen God’s power, trusted Him, and followed Him in obedience. Others have rejected Him and continued in their error to the point of even trying to destroy His followers. A time is coming when all will see who God really is and they will all fall down in awe, wonder, fear, and worship. Anyone who waits till the end will be rejected and miss the blessings that God worked so hard to orchestrate through history. I’ll share more about God’s final show of power in my next post.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
- I’ll admit I used perplexity.ai to list the miracles of Jesus to save time. I double checked the miracles listed from what I know of the Bible and it is accurate. I believe this link will give you all of the details and the links to the Bible references to the miracles. https://www.perplexity.ai/search/give-me-the-miracles-of-jesus-UGKDbkICTHKt96dn5.bkyQ\ I’ll admit I used perplexity.ai to list the miracles of Jesus to save time. I double checked the miracles listed from what I know of the Bible and it is accurate. I believe this link will give you all of the details and the links to the Bible references to the miracles. https://www.perplexity.ai/search/give-me-the-miracles-of-jesus-UGKDbkICTHKt96dn5.bkyQ
-
-
 @ 361d3e1e:50bc10a8
2024-10-20 14:52:53
@ 361d3e1e:50bc10a8
2024-10-20 14:52:53https://forex-strategy.com/2024/10/20/why-wont-there-be-enough-food-very-soon-what-will-the-harvest-be-in-the-coming-years-and-what-will-the-sun-do/ Why won't there be enough food very soon? What will the harvest be in the coming years, and what will the Sun do? What do the Sun and your car's catalytic converter have in common? Are we on the brink of a global meltdown? Are there coming wars different from those in Ukraine and Israel?
food #foodcrisis #climatechange #climate #temperatures #war
-
 @ df478568:2a951e67
2024-10-20 14:49:52
@ df478568:2a951e67
2024-10-20 14:49:52Portfolio
I run 72 services on three servers - Umbrel - Start9 - -PopOS! with a Cloudflare Tunnel This has given me experience in running my own cloud, ticketing system, full bitcoin node, decentralized blog, a meal management system, and Docker experience in both Linux and Portainer.
Umbrel Server.
I run an Umbrel Server and host many services on the clear-net using the Cloudflare tunnel.
Start9 Server
I also run a start9 Server with services also exposed to the clearnet and TOR
Bitcoin Node
I began running a full bitcoin node in 2019. I also run two pruned nodes. You can see the Genesis Block on my instance of mempool
 .
.Peppermint Ticketing System
You can submit a ticket on my ticketing system here
I wrote about it in my blog here. This service runs on a AMD computer with the PopOS! Operating system and cloudflare.
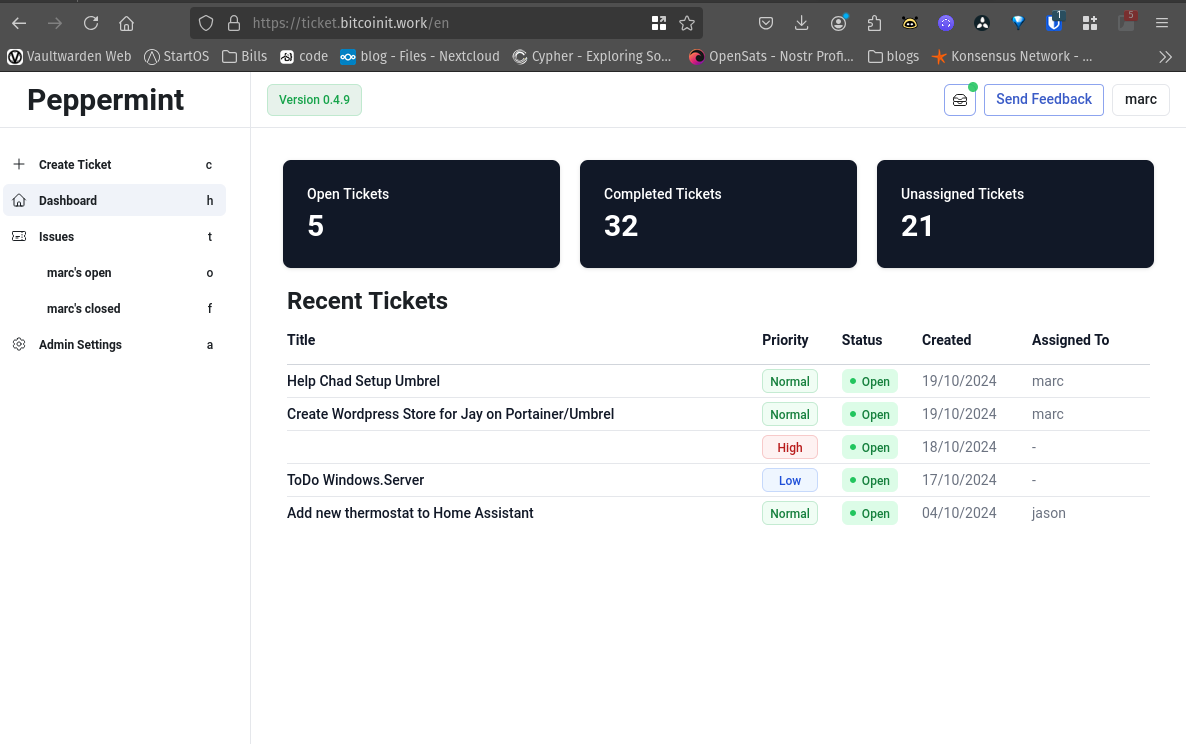
Mealie
This is my favorite service on Umbrel. It’s a meal management system that allows me to plan my meals and automate my grocery lists. It saves so much time. You can find [my instance of mealie here(https://mealie.marcleon.work/).
Self Hosted and Decentralized Blog
I host a ghost blog on Start9 here.
This blog is also published on nostr at:
npub.pro
https://marc26z.npub.pro/
habla.news/
https://habla.news/u/marc26z@nostrplebs.com/
Highlighter.com
https://highlighter.com/marc26z@nostrplebs.com
Portainer
I am currently working on a website using WordPress using Portainer on Umbrel.
It’s not done, but the idea is to create a website that allows me to help people learn how to take self custody of bitcoin, run nodes, and mine.
It is not finished, but the idea is to offer bitcoin IT services.
Tails On An Air Gapped Computer
I removed the Wi-Fi card and hard drive from an old laptop to create an air gapped computer using TAILS Click here to watch the video hosted on nostr.build.
Bitcoin Mining Heater
I converted an old S9 into a space heater. The 3D printed case was made by CryptoCloaks. The S9 miner was a gift from the first person I met after starting my meetup.
PeerViewer
This is free and open source software that can be found at https://github.com/PeerViewer/. - It’s like a free and open source version of RDP on Windows or TeamViewer on Linux.
Certifications
Google Technical Support Certificiate
Automate The Boring Stuff With Python
-
 @ 9e69e420:d12360c2
2024-10-20 13:09:52
@ 9e69e420:d12360c2
2024-10-20 13:09:52Corruption and Insider Trading in Congress
Congressional corruption and insider trading have been significant issues in recent years, with numerous lawmakers facing allegations and legal consequences for unethical financial practices. Here's an overview of the key aspects:
STOCK Act Violations
The Stop Trading on Congressional Knowledge (STOCK) Act of 2012 was designed to prevent insider trading and conflicts of interest among members of Congress. However, violations of this law have been widespread:
- At least 78 members of Congress have violated the STOCK Act by failing to properly report their financial trades.
- Excuses for these violations range from oversights and clerical errors to inattentive accountants.
- The penalties for violating the STOCK Act are relatively minor, starting with a $200 late fee for first-time offenders.
Recent High-Profile Cases
Several prominent lawmakers have faced serious allegations of corruption and insider trading:
Senator Bob Menendez
- Found guilty on all counts in a bribery trial in July 2024.
- Convicted of accepting bribes to benefit businessmen and the governments of Egypt and Qatar.
- Faced 16 charges, including bribery, obstruction of justice, and acting as a foreign agent.
Representative Henry Cuellar
- Indicted in May 2024 on charges of accepting almost $600,000 in bribes from Azerbaijan and a Mexican bank.
- Accused of pushing U.S. policy in favor of Azerbaijan in exchange for payments.
- Charges include bribery, money laundering, and working on behalf of a foreign government.
Ongoing Issues and Reform Efforts
-
Widespread nature of the problem: The corruption issue extends beyond a few isolated cases, with numerous lawmakers from both parties implicated in unethical practices.
-
Lack of enforcement: The House Ethics Committee has been criticized for ineffective oversight, with a 2022 analysis finding that it only publicly investigated 8 out of 60 potential STOCK Act violations since 2020.
-
Calls for reform: There have been bipartisan efforts to ban members of Congress from trading individual stocks, but these proposals have not yet been enacted into law.
-
Public opinion: The issue of congressional stock trading has received significant public interest, with polls showing overwhelming support for reform.
-
Resistance to change: Some lawmakers, such as former House Speaker Nancy Pelosi, have opposed reforms that would limit their ability to trade stocks.
The ongoing issues of corruption and insider trading in Congress highlight the need for stronger ethics rules, better enforcement mechanisms, and increased transparency in the financial dealings of elected officials. As public scrutiny intensifies, pressure continues to mount for meaningful reform to address these longstanding problems.
-
 @ 9e69e420:d12360c2
2024-10-20 12:49:07
@ 9e69e420:d12360c2
2024-10-20 12:49:07The Growing Threat to Free Speech on Social Media
In a recent CNN interview, Hillary Clinton made alarming statements about the need for social media companies to moderate content, warning that without such measures, "we lose total control"[1]. This rhetoric is part of a broader push by some Democrats to increase censorship and control over online platforms under the guise of combating misinformation.
Clinton's comments went beyond mere content moderation, as she advocated for the repeal of Section 230, a crucial provision that protects online platforms from liability for user-posted content[1]. This move would fundamentally alter the landscape of free speech on the internet, potentially forcing platforms to aggressively censor user content to avoid legal repercussions.
The former Secretary of State even suggested that Americans could face civil or criminal charges for certain social media posts[2]. While she specifically referred to those allegedly paid by foreign agents to spread propaganda, such a precedent could easily be abused to target political dissent or unpopular opinions. This approach stands in stark contrast to the principles of free speech enshrined in the First Amendment.
Clinton's statements are not isolated incidents. Other prominent Democrats, including Vice President Kamala Harris, have also expressed support for weakening Section 230 and increasing government control over online speech[6]. This trend suggests a coordinated effort to reshape the digital public square in ways that could severely limit free expression and open debate.
As we approach the 2024 election, it is crucial to remain vigilant against attempts to stifle free speech under the pretext of fighting misinformation. While addressing genuine foreign interference and harmful content is important, we must be wary of solutions that grant excessive power to government or tech companies to determine what constitutes acceptable speech online.
Sauce: I am the sauce. But I also would credit:
[1] Hillary Clinton says social media companies must moderate content ... https://www.hindustantimes.com/world-news/us-news/hillary-clinton-says-social-media-companies-must-moderate-content-or-we-lose-total-control-ripped-by-tulsi-gabbard-101728181956987.html [2] Fact check: Did Clinton call for jail over misinformation? - DW https://www.dw.com/en/fact-check-did-clinton-call-for-jail-over-misinformation/a-70279863 ncy ... https://oversight.house.gov/release/mace-calls-on-biden-harris-administration-to-provide-transparency-on-current-censorship-efforts-to-interfere-in-the-2024-election/ [4] Hillary Clinton Discusses Civil or Criminal Penalties for ... - YouTube https://www.youtube.com/watch?v=zA1VBCeJV3A [5] Claims That Social Media Endangers Democracy Are Mostly ... https://itif.org/publications/2023/09/05/claims-that-social-media-endangers-democracy-are-mostly-misinformation/ [6] Hillary Clinton Wants To Repeal Section 230 - Reason Magazine https://reason.com/2024/10/07/hillary-clinton-wants-to-repeal-section-230/ [7] Hillary Clinton warns that allowing free speech on social media ... https://nypost.com/2024/10/06/us-news/hillary-clinton-warns-that-allowing-free-speech-on-social-media-means-we-lose-control/
-
 @ de75eb1d:710c3014
2024-10-20 12:15:24
@ de75eb1d:710c3014
2024-10-20 12:15:24What is Nostr?
- Decentralised/multihosted data publishing protocol; that’s it.
Notes (‘tweets’, blogs, web pages, DMs etc) and
Other (calendar events, map data, payments, computer game moves)
Stuff
Transmitted (hosted/stored) by
Relays (servers)
Other data sharing protocols: TCP, FTP, SMTP, HTTP
NB. Nostr relays transmit only text based data - not FILES. Images/video/audio etc are linked to via http
Protocol: a standardised set of rules for formatting and processing data. Protocols enable computers to communicate with one another.

🥱 Why’s it so great then?
-
Easy for nerds to build on (vs activity pub for example) and is growing very quickly (was only launched in 2020)
-
Cryptographic key pairs replace user accounts
-
Cross platform - use your keys to post and read notes in any client
-
Much harder to censor multiple copies of information; impossible if using selfhosted relay
-
Can be completely anonymous - no KYC, keys can even be generated offline
-
Bitcoin lightning integration through ‘zaps’
-
Anyone with a key pair can post notes, anyone can run a relay, ‘anyone’ can build a client

How to Nostr;
- Generate a fresh set of keys by clicking 'Sign Up' / 'Create Account' in any nostr client
- Get zappable - input your lightning address
- Write an #introductions post, get zapped

ok, ok I'm joking; here are the stepz
Getting started on Coracle.Social, my favourite microblogging web client
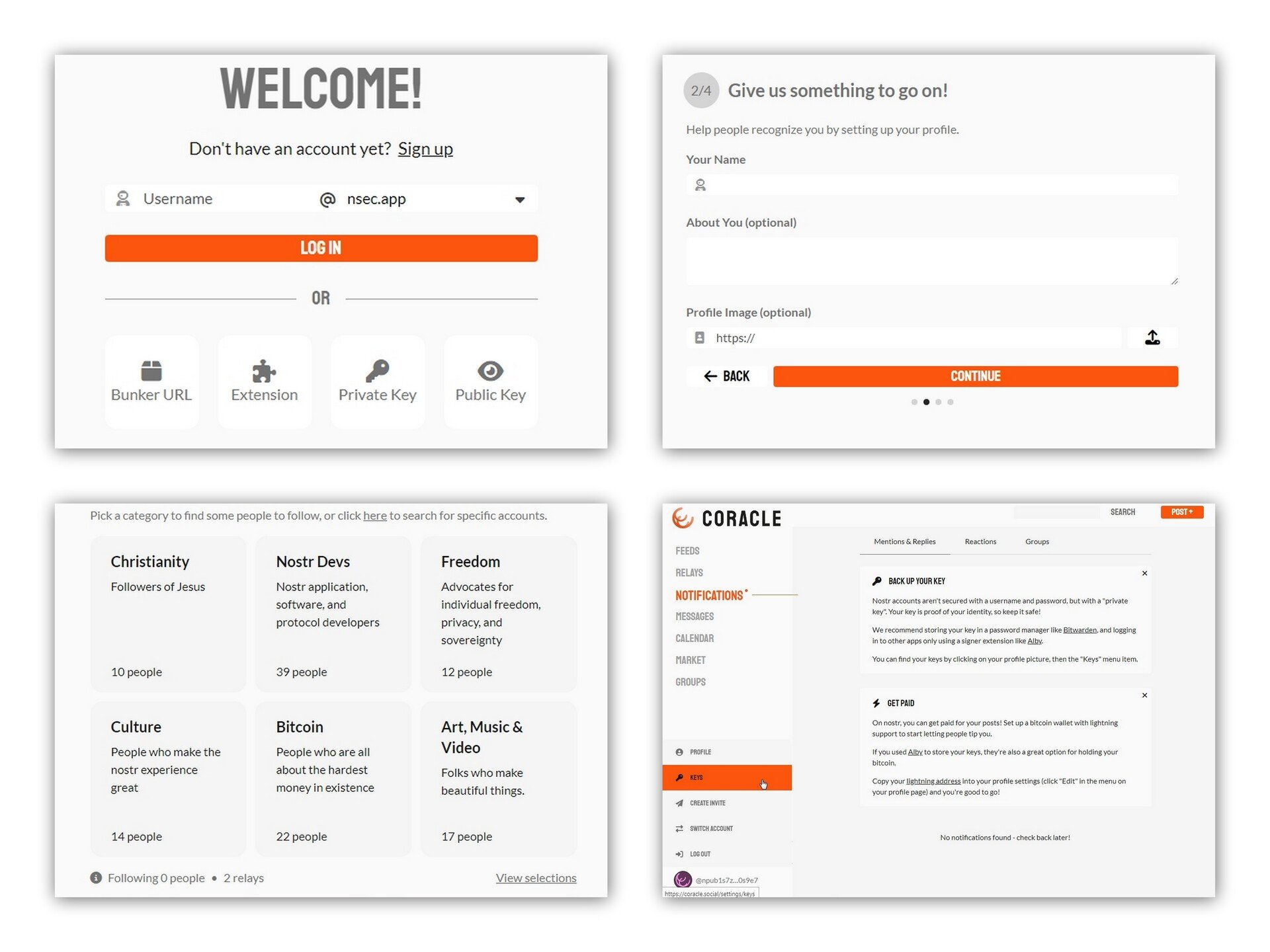 First up visit https://coracle.social/login and click 'Sign up' to generate a set of fresh keys.
First up visit https://coracle.social/login and click 'Sign up' to generate a set of fresh keys.The account creation process will walk you through inputting basic profile information, all of which is ENTIRELY optional. The only thing you need to interact with the nostr network are key pairs (you can make an unlimited amount of these). Coracle helps you out with finding a few accounts to follow based on interest, so you don't need to start with an empty feed.
Next & very important if you wish to keep this account is to backup your keys. Just like with Bitcoin you will lose access forever if you do not store the private key (nsec) somewhere safe, like a password manager or nostr login extension (nos2x, Alby, flamingo).
Click on the circle bottom left (profile pic if you uploaded one) and select 'Keys'. Clicking the little copy icon will bring up a box with the option to encode your private key with a password, you can then save the nsec string.
With your nsec in your pocket you can now go and play with any app in the Nostrverse and all of your data will follow you! *in theory 🤪
wanna get paid for posting pictures of your dog?
'Lightning Address' is the field to look out for, in Coracle this can be found under Profile and clicking edit from the three dot menu
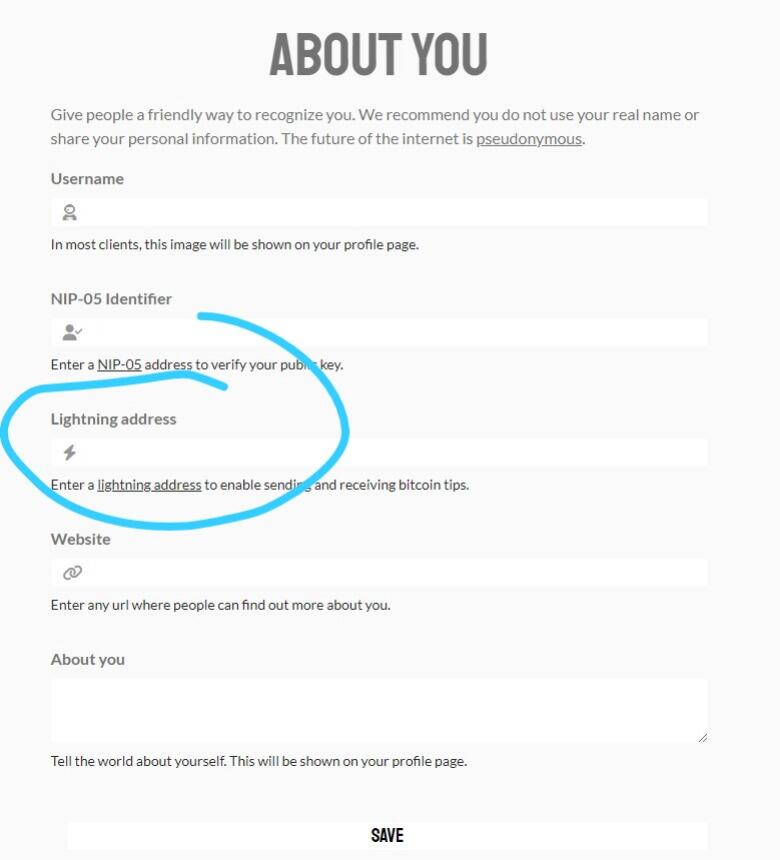
Many wallets such as WoS, Breez, Minibits (Ecash), Zeus, Phoenix & Alby will provide you with a static lightning address, paste this into the box to receive sats from the get go.
Finding stuff to read
At the top of the 'Feed' page on Coracle is a Filters(|) button which brings up a yugge range of options
Anatomy of a Nostr "post"
{ "id": "4376c65d2f232afbe9b882a35baa4f6fe8667c4e684749af565f981833ed6a65",
"pubkey": "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93",
"created_at": 1673347337,
"kind": 1,
"content": "Walled gardens became prisons, and nostr is the first step towards tearing down the prison walls.", "tags": [ ["e", "3da979448d9ba263864c4d6f14984c423a3838364ec255f03c7904b1ae77f206"], ["p", "bf2376e17ba4ec269d10fcc996a4746b451152be9031fa48e74553dde5526bce"]
], "sig": "908a15e46fb4d8675bab026fc230a0e3542bfade63da02d542fb78b2a8513fcd0092619a2c8c1221e581946e0191f2af505dfdf8657a414dbca329186f009262" }Let's break that down - id: a unique number for each event allowing for referencing - pubkey: the author's unique public key (npub in hex format) - created_at: time stamp - kind: the type of content (known as an event), in this case a simple text note - content: the note - tags: this note references another event (it is a reply), and the op's npub - sig: verification code proving this note has been signed by the author's private key
The note displayed in Primal:
 Get zapping - Primal inbuilt (email kyc, not available in certain location - choose El Salvador?),
https://www.zapplepay.com/ or Alby Hub
(self hosted)
Get zapping - Primal inbuilt (email kyc, not available in certain location - choose El Salvador?),
https://www.zapplepay.com/ or Alby Hub
(self hosted) Options for generating own keys: https://nip06.jaonoctus.dev/ - BIP39 https://gist.github.com/kdmukai/ae9911ed6fb92f8e7d2c553555b0cb86 - via seedsigner (we can dream) https://github.com/guilhermegps/secret-border https://www.nostr.rest/- vanity key mining

Nostr client examples:
-
Damus, Amethyst, Primal, Snort, Iris - Twitter like
-
Corale.social snort.social iris.to satellite.earth Nostrudel- web clients for computer browsers
-
Habla News https://yakihonne.com/- Long-form content (like this doc)
-
Flockstr, inmytown - Calendars
-
Fountain - Podcasts
-
Wavlake - Music
-
Tunestr - music live streaming for zaps
-
footstr.com - feet
-
cornychat.com nostrnests.com/ live audio rooms
-
Zap.stream - more live stuff
-
Shopstr, Plebeian.Market cypher.space - p2p buying/selling
-
Stacker.news, Oddbean - Forums
-
Yondar - Maps
-
Jester - Play chess jesterui.github.io/
-
lazereyes - Save your lens prescription on nostr:
-
Zap.cooking - recipes
-
Shipyard.pub - note scheduler
-
npub.pro - your notes as a website
-
Njump.me - profile preview tool with client chooser, makes easily shareable webpage using lightning address
-
mostro - p2p bitcoin exchange
- Pinstr - Create customized public boards of pins
- Listr - edit your lists (mute/bookmarks/follows etc

NIPs:
-
NIP-05: Mapping Nostr keys to DNS-based internet identifiers
-
NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
-
NIP-10: Conventions for clients' use of e and p tags in text events
Nostr Vs Mastodon/Twitter/Threads/Bluesky
Discoverability/finding people to follow/algos
Privacy/self-custody

It’s Shit and doesn’t work but I will die on this hill

Other rabbit holes:
-
DVM, data vending machines
-
Web of Trust
-
Outbox model
--------> https://zapper.nostrapps.org/ <----------

Some popular Nostriches to follow (import into Listr):
Handy nostr tools:
https://advancednostrsearch.vercel.app https://nostr.build/upload.php meme uploader https://zaplife.lol/ who zapped who https://zap.store/download - permissionless app store validated by the web of trust https://decenchat.com/ - embeddable nostr live chat widget for website https://highlighter.com/ - Tool to quote articles
-
 @ 599f67f7:21fb3ea9
2024-10-20 11:28:08
@ 599f67f7:21fb3ea9
2024-10-20 11:28:08LNDhub te permite importar fácilmente una billetera en aplicaciones compatibles. Si bien puedes guardar tu billetera Bitcoin Txoko LNbits en tu teléfono como una aplicación web progresiva (PWA), una aplicación nativa como Zeus o BlueWallet ofrece una mejor experiencia de usuario así como un mayor nivel de seguridad. Con Alby, también puedes importar la billetera a la extensión de tu navegador para facilitar los pagos Lightning en la web y para los zaps de Nostr. Por suerte para nosotros, todas estas billeteras hablan un lenguaje común llamado LNDhub.
En esta guía cubriremos cómo importar la billetera a tu navegador y a tu móvil. Si quieres usar tu billetera tanto en el navegador como en tu móvil, empieza con la configuración de Alby, ya que uno de los pasos te permitirá importar fácilmente tu billetera también a Zeus. Pero si sólo te interesa utilizar la billetera en tu móvil, puedes pasar directamente a la sección de Zeus.
Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 es una extensión de navegador que lleva Lightning y Nostr a tu navegador. Utilizando el protocolo WebLN, esta extensión puede detectar facturas LN en paginas web y pagarlas, así como posibilita iniciar sesión en sitios web con Lightning. También puedes fijar presupuestos para tus sitios favoritos de Lightning. Por otro lado también puedes utilizarla para firmar en Nostr utilizando NIP-07, lo cual es mucho más seguro que ingresar tu clave privada en clientes web.
¿Qué necesito?
- Un navegador web que soporte extensiones Chrome o Firefox
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
- (Opcional) Un dispositivo móvil para configurar Zeus
1. Habilita la extensión LNDhub en tu LNbits wallet
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez se haya habilitado, dirígete a la página de extensión de LNDhub.2. Instala la extensión Alby
Dirígete a getalby.com y instala la extensión desde el store de extensiones del navegador. Configura tu contraseña de desbloqueo y guárdala en un lugar seguro.
3. Importar a Alby
 (Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)
(Esta es una billetera de prueba. No hay fondos en ella. ¡No muestres a nadie tu URI de exportación real!)En la siguiente pantalla, elige
Conectary luego eligeLNDhub. Vuelve a tu extensión LNDhub y copia la URL de conexión. Pégala en el campoURI de exportación de LNDhub. Pulsa continuar. ¡Ahora deberías haber estado conectado a tu billetera de LNbits con LNDhub!💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). Le dan a Alby diferentes permisos para interactuar con tu cartera de LNbits.
- La URL de factura te permite crear facturas y recibir pagos
- La URL de administración también te permite enviar pagos
4. Configurar Zeus con Alby (opcional)

Ahora que ya has conectado tu LNbits con Alby, también puedes importarlo de una manera sencilla a Zeus con Alby. Abre la extensión, haz cilc en el nombre de tu billetera y navega a la configuración de la cuenta. En
Wallet Settings>Generalse encuentra la opción de conectar tu billetera móvil. Al pulsar conectar, se mostrará un código QR para escanear desde Zeus.Si no tienes instalada Zeus con anterioridad, dirígete a zeusln.app y descarga la aplicación de Zeus para tu sistema operativo móvil.
Una vez tengas descargado Zeus, entra en
Configuración>Añadir un nuevo nodo. Aquí puedes escanear el código QR que te muestra Alby para importar la billetera.Voilà! Ahora tienes el poder de Lightning al alcance de la mano ¿Ya te sientes como un dios?
Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf es una formidable aplicación de código abierto que permite conectar tu propio nodo a tu dispositivo movil. Es compatible con todas las principales implementaciones de nodos Lightning, como LND, CLN y Eclair, así como conexiones a través de Tor y clearnet. Recientemente también han anunciado su propio LSP (Lightning Service Provider).
¿Qué necesito?
- Teléfono Android o iOS
- Otro dispositivo en el que puede acceder a tu billetera LNbits (para mostrar el código QR para escanear)
- Acceso a tu billetera LNbits. Si todavía no tienes una billetera LNbits, dirígete a nuestra página de billeteras y crea una
1. Descarga Zeus
Puedes descargar la aplicación Zeus para tu sistema operativo aquí.
2. Habilita la extensión LNDhub en tu billetera LNbits
Dirígete a tu billetera LNbits. Haz clic en
Extensionesy habilita la extensiónLNDhub. Una vez habilitada, abre la pagina de la extensión LNDhub.3. Importar a Zeus
Ve a
Configuración>Añadir un nuevo nodo en Zeus.Escanea la cartera que quieras instalar.
💡 Puedes elegir entre la URL de la factura (Invoice URL) y la URL de administración (Admin URL). - La URL de la factura te da permiso para generar facturas y recibir pagos. - La URL de administración también te permite enviar pagos.
Una vez que hayas escaneado el código QR, todos los campos en Zeus deberían rellenarse automáticamente. También puedes añadir un apodo para tu billetera.

¡Ahora puedes guardar la configuración del nodo y controlar la billetera desde tu teléfono!
Extra
Zeus también ofrece funciones interesantes como temas personalizados, conversiones de precios, modo acechador y verificación biométrica. Estos temas están más allá del alcance de esta guía, ¡juega en la aplicación y descubre todas esas características por ti mismo!
-
 @ 4ba8e86d:89d32de4
2024-10-20 10:12:19
@ 4ba8e86d:89d32de4
2024-10-20 10:12:19M5Stick-NEMO: Firmware para Pegadinhas de Alta Tecnologia em Dispositivos M5Stack ESP32 , Este projeto oferece uma solução eficaz sem comprometer a qualidade, ideal para quem busca uma experiência educativa e divertida no universo do hacking.
https://nostrcheck.me/media/public/nostrcheck.me_2674216785970862911706546228.webp
Desenvolvido por Noah Axon-n0xa, o M5Stick-NEMO é um projeto pessoal que surgiu da vontade de aprender mais sobre o desenvolvimento do ESP32 com o Arduino IDE. Inspirado por desafios populares na comunidade de tecnologia, NEMO replica pegadinhas comuns, proporcionando uma experiência educativa e divertida.
Características Principais:
- Portal NEMO WiFi: um captive portal login que tenta criar credenciais de e-mail de engenharia social - salva nomes de usuário e senhas no cartão SD (se inserido em um leitor compatível)
- Porta TV B-Gone para desligar dispositivos controlados por infravermelho.
- Spam de emparelhamento de dispositivo AppleJuice iOS Bluetooth.
- Spam de notificação de dispositivo Bluetooth para SwiftPair (Windows) e Android.
- Spam de WiFi com SSIDs engraçados, WiFi Rickrolling e modo aleatório.
- Scanner SSID WiFi: exibe e clona SSIDs próximos.
- Relógio digital ajustável pelo usuário com suporte do M5 Stick RTC.
- Configurações apoiadas por EEPROM para rotação, brilho, escurecimento automático e SSID do Portal NEMO.
- Nível da bateria e créditos no menu de configurações.
Interface de Usuário:
- Três controles principais: Home, Próximo e Selecionar.
Portal NEMO:
No modo NEMO Portal, o NEMO ativa um Hotspot WiFi aberto chamado "Nemo Free WiFi" (configurável em portal.h) com servidores DNS, DHCP e Web ativados.
-
O Portal NEMO exibe uma página de login falsa que afirma fornecer acesso à Internet se você fizer login.
-
Este é um ataque de engenharia social e registrará o nome de usuário e as senhas inseridas na página.
-
Nos detalhes do Wifi Scan, você pode clonar um SSID existente na lista de verificação. Sair do Portal NEMO limpará o SSID Evil Twin
-
Você pode visualizar as credenciais capturadas conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/creds
-
Você pode definir um SSID personalizado conectando-se ao portal a partir do seu próprio dispositivo e navegando até http://172.0.0.1/ssid
-
Se o seu dispositivo suportar EEPROM para configurações, o SSID personalizado inserido será salvo como padrão, mesmo se estiver desligado.
-
Se o seu dispositivo tiver um leitor de cartão SD com um cartão formatado em sistema de arquivos FAT inserido, os nomes de usuário e senhas serão registrados em nemo-portal-creds.txt no cartão SD para você ler mais tarde.
-
O suporte a cartão SD só está habilitado por padrão na plataforma M5Stack Cardputer. Ele pode ser habilitado em dispositivos M5Stick, mas um leitor de cartão SD deve ser construído e conectado ao pino do painel frontal.
-
O Portal NEMO deve ser usado apenas em compromissos profissionais com um escopo válido de trabalho, fins educacionais ou de demonstração.
O armazenamento, venda ou uso de informações pessoais sem consentimento é contra a lei.🤓
Instalação:
-
Visite o site oficial: M5Stack Docs https://docs.m5stack.com/en/download
-
Baixe o programa oficial M5Burner.
-
Procure pelo projeto "NEMO For M5Stick C Plus".
-
Conecte o M5 à porta USB do seu PC.
-
Abra o M5Burner, selecione o projeto e clique em "Burn".
Experimente algumas funções do FlipperZero no seu M5. Para recursos adicionais e a liberdade de personalização, compile e baixe diretamente o programa "NEMO-M5Stick C Plus" no GitHub do projeto. Isso não só permite explorar, mas também modificar e aprimorar o projeto de acordo com suas preferências.
Repositório oficial no GitHub
https://github.com/n0xa/m5stick-nemo
Assista a um tutorial sobre a implementação do M5Stick-NEMO.
https://youtu.be/uFzQTzZo-6E?si=BJJzNmiN0Jzw42Eu
https://youtu.be/uTeCbR_hWjc?si=l88w_Hl3EXuKa6gv
Além disso, você pode aprimorar seu M5 com o MURAUDER, um conjunto abrangente de ferramentas ofensivas e defensivas WiFi/Bluetooth para o ESP32.
Encontre-o no GitHub: ESP32Marauder
https://github.com/justcallmekoko/ESP32Marauder
Assista a um tutorial sobre a implementação do MURAUDER:
https://youtu.be/GQPzgYksdkg?si=dWN-GwEP5r6hk9IC
-
 @ 41d0a715:9733c512
2024-10-20 03:38:18
@ 41d0a715:9733c512
2024-10-20 03:38:18If you object to something a Fellow CowBoy is representing, it should be OK to call him out.
We need to remove the factor of unequal wealth or the huge stack of Satoshis one person has.
Challenging a Fellow CowBoy is a very serious insult. It deserves a clear cut outcome.
The Metaphor of "A Show Down on Main Street' is where the accuser and the accused settle things to the Death.
originally posted at https://stacker.news/items/732035
-
 @ 4ba8e86d:89d32de4
2024-10-20 03:20:33
@ 4ba8e86d:89d32de4
2024-10-20 03:20:33Criando códigos de pagamentos reutilizáveis que começam com "PM8T". Esses códigos permitem que os usuários compartilhem identificadores publicamente sem revelar seus endereços ou saldos de Bitcoin. Os PayNyms oferecem diversas funcionalidades incríveis, como receber doações, comprar Bitcoin peer-to-peer, receber recompensas de mineração, fazer login com Paynym/Auth47 e realizar transações com Stowaway/Payjoin, que proporcionam um nível adicional de privacidade ao criar um mini coinjoin. Essas são algumas das contribuições mais significativas para a privacidade do Bitcoin. Embora o BIP47 tenha sido criado em 2015, a maioria das carteiras de Bitcoin ainda não o implementou, com exceção de algumas, como Samourai Wallet, Sparrow Wallet e Bluewallet, que atualmente oferecem suporte apenas para recebimento.
O PayNym é um código de pagamento reutilizável que proporciona segurança ao ser compartilhado publicamente. Cada carteira compatível com BIP47 lê o código secreto no PayNymID e gera um novo endereço público válido exclusivo para cada par de usuários. A chave pública estendida escondida no PayNymID, combinada com o código secreto único para cada par de usuários, impede que terceiros rastreiem as chaves públicas dos usuários. Os pagamentos não são enviados diretamente para o código de pagamento do usuário, mas para endereços Bitcoin públicos únicos gerados pelo segredo compartilhado da carteira e pelo código de pagamento reutilizável do destinatário. Estes endereços públicos são gerados quando é feito o primeiro Tx para o PayNymID, garantindo privacidade desde o início da transação. Isso é feito criando um Tx especial que é enviado com os dados da saída OP_RETURN para um endereço de notificação obtido do código de pagamento do destinatário. Este Bitcoin Tx, que é enviado para um endereço de observação/notificação, não é um pagamento real. É uma saída OP_RETURN de 80 bytes com os dados necessários para criar novos endereços públicos derivados de algoritmos com base nas informações de chave pública estendida. Uma vez estabelecido o canal direto entre os usuários, o Tx restante para PayNym segue o mesmo processo que qualquer outra transação Bitcoin. A privacidade é mantida ao compartilhar o PayNym, já que não são divulgados os endereços BTC públicos, apenas o código de pagamento reutilizável BIP47. A premissa do protocolo BIP-47 é que não se pode espionar o que não se pode ver, garantindo assim a privacidade das transações. O PayNym oferece uma maneira relativamente privada de realizar transações, mesmo que isso exija mais esforço e taxas mais elevadas.
O PayNymID incorpora a chave pública estendida do proprietário do PayNym, uma informação codificada que a carteira BIP47 interpreta para criar novos endereços Bitcoin públicos. Esses novos endereços são derivados dos endereços originais controlados pelo proprietário das chaves privadas.
https://nostrcheck.me/media/134743ca8ad0203b3657c20a6869e64f160ce48ae6388dc1f5ca67f346019ee7/nostrcheck.me_8654899814721132371710875358.webp
Como a carteira é individual e independente e depende da frase-semente mantida pelo proprietário do PayNym e da carteira, cada carteira BIP47 que lê o código secreto gerará endereços BTC públicos válidos. Esses endereços são exclusivos para cada par de usuários, diferentemente dos gerados por outra carteira que lê o mesmo PayNym, criando canais de pagamento com endereços Bitcoin únicos para cada dupla de usuários.
Para efetuar pagamentos para um PayNymID, é necessário primeiro abrir um canal de pagamento seguro. Isso é feito criando uma transação especial que inclui os dados da saída OP_RETURN e é enviada para um endereço de notificação obtido do código de pagamento do destinatário.
A transação de notificação especial é executada apenas uma vez do remetente para o destinatário. Uma vez aberto, o restante das transações enviadas ao PayNym será como qualquer outra transação Bitcoin.
Esta primeira transação especial tem um custo de 15.000 satoshis mais a taxa de rede na carteira Samourai. É individual para cada canal de pagamento seguro que você deseja abrir com qualquer PayNymID. Ou seja, cada PayNym requer uma única transação especial para abrir cada canal de pagamento.
https://nostrcheck.me/media/134743ca8ad0203b3657c20a6869e64f160ce48ae6388dc1f5ca67f346019ee7/nostrcheck.me_5588987905454433521710875712.webp
Uma vez estabelecido o canal de pagamento para o PayNym, você pode realizar transações de forma privada e segura, sem expor seu saldo ou histórico de transações. Da mesma forma, qualquer pessoa que queira fazer um pagamento para o seu PayNym precisará seguir o mesmo procedimento de abrir um canal de pagamento seguro com sua própria carteira.
Essa abordagem permite criar uma rede de contatos seguros, onde você pode conduzir transações de maneira totalmente privada, sem o risco de divulgar informações confidenciais, como seu histórico de transações ou saldo da carteira.
https://medium.com/@ottosch/how-bip47-works-ee641cc14bf3
-
 @ 9e69e420:d12360c2
2024-10-20 01:21:39
@ 9e69e420:d12360c2
2024-10-20 01:21:39Michigan Voter Rolls Inflated by 500,000: State vs. GOP Perspectives
Key Points
- Michigan's voter rolls list 8.4 million registered voters, nearly 500,000 more than the eligible voting population.
- This is the largest imbalance among Great Lakes states and one of the largest in the nation.
Causes and Concerns
- A major cause is the 2018 voter-approved proposal that automatically registers those 18 and older to vote when applying for a driver's license, unless they opt out.
- The Republican National Committee has sued the state, demanding the rolls be trimmed.
- While critics say the inflated rolls are not ideal, no one is suggesting they have contributed to fraud.
State's Response
- By 2027, an estimated 606,800 inactive voters are expected to be removed from rolls.
- This would reduce the total to just over 7.8 million, slightly less than the voting-age population.
- State officials argue that the GOP lawsuits are an attempt to sow distrust in elections.
Challenges in Removing Voters
- Federal law limits when voters can be removed from rolls.
- Voters can be removed if they move to another state, if election mail is undeliverable, or if they don't vote in two consecutive federal elections.
Fraud Concerns
- Election officials state that impersonation fraud is almost non-existent.
- While voter fraud does occur, it's rare. Recent cases include four St. Clair Shores voters charged with voting twice in the August primary.
- Many allegations of fraud, such as dead voters casting ballots in 2020, have been proven baseless.
Interesting Facts
- Michigan's voter rolls include 16,666 people born in 1924 or earlier.
- In 2024, only 1,121 of these centenarians voted.
Sauce: I am the sauce. But we can also credit: https://www.bridgemi.com/michigan-government/michigan-voter-rolls-inflated-500k-state-says-its-no-issue-gop-disagrees
-
 @ 4ba8e86d:89d32de4
2024-10-20 01:17:29
@ 4ba8e86d:89d32de4
2024-10-20 01:17:29Trechos do artigo do seth for Privacy
COMO FUNCIONAM OS PAGAMENTOS SILENCIOSOS, SIMPLIFICADOS Antes de nos aprofundarmos no motivo pelo qual estou entusiasmado com os Pagamentos Silenciosos, é importante que você entenda em um nível muito simplista como os Pagamentos Silenciosos funcionam tanto para o remetente quanto para o destinatário. PARA O REMETENTE Quando alguém deseja enviar fundos para um endereço de pagamento silencioso, na prática, tudo o que precisa fazer é digitalizar ou copiar/colar o código de pagamento em sua carteira favorita (supondo que seja compatível) e enviar o pagamento normalmente. Mas o que exatamente está acontecendo nos bastidores? Quando o remetente insere o endereço de Pagamento Silencioso em sua carteira, sua carteira combina três chaves para criar um endereço único e único, do qual apenas o destinatário pretendido pode gastar. Esse endereço exclusivo é criado combinando a chave pública (ou “endereço”, em termos leigos) de uma das entradas que o remetente deseja passar para o destinatário, a chave pública do destinatário (contida no endereço de pagamento silencioso), e uma chave “segredo compartilhado” que o remetente gera e que apenas o remetente e o destinatário conhecem. Graças a algo conhecido como propriedade “comutativa” na criptografia, o remetente pode combinar essas chaves, mas não pode gastar do endereço resultante , pois não conhece a chave privada do destinatário (é claro). Quando o remetente combina essas três chaves, ele gera uma nova chave pública (ou endereço) e envia os fundos pretendidos para esse novo endereço que somente o destinatário controla. Na cadeia, esta transação se parece exatamente com qualquer outro gasto de tipo e script semelhantes, e não há nenhum fator distintivo que torne aparente para observadores externos que um Pagamento Silencioso foi usado, muito menos quem possui o endereço de Pagamento Silencioso. PARA O DESTINATÁRIO Assim que chegarmos ao destinatário, veremos onde entra a principal desvantagem dos pagamentos silenciosos. Se você se lembra de que o remetente usa a chave pública de uma entrada que está sendo gasta para gerar o endereço único e único, pode estar se perguntando: “Como o destinatário sabe que recebeu fundos e para qual endereço?” Esta questão está no centro da proposta de pagamentos silenciosos e significa que os destinatários precisam fazer uma varredura relativamente cara de todas as transações na blockchain do Bitcoin depois de criarem seu endereço de pagamento silencioso. Essa varredura permite que o destinatário veja se uma chave pública de entrada mais um segredo compartilhado gerado usando seu endereço de pagamento silencioso e uma chave pública de saída em qualquer transação corresponde adequadamente às suas chaves privadas e, se for o caso, adicioná-la à carteira. Essa varredura é bastante cara em comparação com a varredura de carteira Bitcoin padrão, pois você não pode simplesmente comparar uma lista de endereços derivados de sua carteira com uma lista de saídas de transações para obter o saldo de sua carteira. Em vez disso, você precisa passar por cada transação, calcular o segredo compartilhado para cada entrada e comparar com as saídas, algo que Somsen comparou a “verificar cada assinatura duas vezes, em vez de uma vez” em “Bitcoin Explained ” . Idealmente, essa varredura será feita durante o download do bloco inicial (a primeira vez que você sincronizar todo o blockchain do Bitcoin) ou um software autônomo que descarregue a varredura de sua carteira e nó Bitcoin.
OTIMIZANDO O TEMPO DE DIGITALIZAÇÃO PARA O DESTINATÁRIO
Embora essa varredura seja computacionalmente cara, ela pode se tornar mais eficiente sem sacrificar a privacidade ou a fungibilidade por meio de três otimizações principais:
-
Crie uma data de “aniversário” ao criar um endereço de pagamento silencioso e salve-o, para que, quando precisar restaurar, você possa começar a digitalizar apenas a partir desse bloco adiante na cadeia, em vez do bloco de gênese.
-
Verifique apenas as saídas Taproot, pois muito poucas saídas na cadeia são atualmente Pay-to-Taproot (“ P2TR ”), isso eliminará uma grande porcentagem de transações e reduzirá bastante o tempo de verificação. Idealmente, isso se tornará menos útil à medida que o Taproot for mais usado, mas provavelmente será uma otimização extremamente eficaz por algum tempo.
3.Verifique apenas o conjunto UTXO em vez de verificar todas as transações históricas, pois você está preocupado apenas com saídas novas, recebidas e não gastas destinadas ao seu endereço de pagamento silencioso. Isso tem a desvantagem de não fornecer histórico de transações e exigiria um banco de dados adicional sobre os métodos normais.
Artigos sobre Silent Payments 🤫
https://bitcoinmagazine.com/technical/silent-payments-make-bitcoin-more-private
https://bitcoinmagazine.com/technical/silent-payments-improve-privacy-without-bitcoin-data
https://bitcoinmagazine.com/technical/bitcoin-silent-payments-secret-keys
https://bitcoinmagazine.com/technical/improving-bitcoin-privacy-with-silent-payments
https://foundationdevices.com/2023/02/making-sense-of-stealth-addresses/
Videos sobre Silent Payments 🤫
https://youtu.be/vOCWO_zX7X8
https://youtu.be/42PMLaz7Avk
https://youtu.be/YCMaqS-LhLc
Space sobre Silent Payments 🤫
https://twitter.com/bitcoinoptech/status/1668949342814609408?t=UY6nEc0ghPiPxgfydUzW6w&s=19 Recompensa pra carteira mobile suporte ao Silent Payments 🤫
https://twitter.com/gladstein/status/1684567103297445888?t=tY6WQ8fzPn3vNs_YrvXDmQ&s=19
BIP 352 Silent Payments 🤫
https://github.com/bitcoin/bips/pull/1458#issuecomment-1613507274
-
-
 @ dba00383:d7448f1b
2024-10-20 01:06:44
@ dba00383:d7448f1b
2024-10-20 01:06:44Primeiramente meus irmãos Pedro escreve essa carta aos Irmãos que moravam pelas redondezas da Turquia, e naquele momento estavam passando por problemas e dificuldades acerca de sua fé, e então Pedro argumenta sobre as dificuldades da fé Cristã.
Segundo, o que é ser santo? Ser santo significa ser separado, diferente, consagrado, se fomos transformados verdadeiramente pelo espírito santo devemos agir como aquele que nos transformou, que foi Jesus Cristo, e através de nossa vida, através de nosso testemunho, através de nossas ações deveríamos transparecer essa separação deste mundo.
O que estou querendo dizer é algo mais básico acerca da nossa caminhada cristã, tudo se resumo a sermos um espelho que reflete o carácter e as características de nosso Criador, mas o por que estou dizendo isso, porque quero lembrar e sempre que puder vou relembrar que, AÇÕES SÃO MAIS IMPORTANTES QUE PALAVRAS, se apenas falamos que somos crentes mas no nosso dia a dia mas agimos de forma diferente(seja mentindo, seja enganando, seja nos vendendo) está sendo em vão nossa caminhada e nossa salvação estará comprometida.
Estou falando essas coisas porque é necessário que sejamos separados das coisas desse mundo, de toda corrupção desta era e sermos a luz que ilumina as trevas desta terra, o sal que tempera esse mundo, que essa palavra entre em vossos corações e que Deus abençoe vocês em NOME DE JESUS. AMÉM!!!!!!!
-
 @ b6ca2216:f45f8b5b
2024-10-20 00:19:37
@ b6ca2216:f45f8b5b
2024-10-20 00:19:37my 3. article
-
 @ b6ca2216:f45f8b5b
2024-10-20 00:16:38
@ b6ca2216:f45f8b5b
2024-10-20 00:16:38{"id":12345,"title":"deleted","body":"deleted"}
-
 @ b6ca2216:f45f8b5b
2024-10-19 23:51:01
@ b6ca2216:f45f8b5b
2024-10-19 23:51:01{id:123, title:"my first article", body:"This NIP defines kind:30402: an addressable event to describe classified listings that list any arbitrary product, service, or other thing for sale or offer and includes enough structured metadata to make them useful. The category of classifieds includes a very broad range of physical goods, services, work opportunities, rentals, free giveaways, personals, etc. and is distinct from the more strictly structured marketplaces defined in NIP-15 that often sell many units of specific products through very specific channels. The structure of these events is very similar to NIP-23 long-form content events."}
-
 @ 623ed218:fa549249
2024-10-19 23:49:53
@ 623ed218:fa549249
2024-10-19 23:49:53Pup's Double-Takes #002:
"Should You Spend Bitcoin?"

Welcome to Pup's Double-Takes, where I dive into the things that made me stop and say, 'Wait, what?' My goal is to unpack the curious and confusing, making it educational and, hopefully, a little entertaining along the way.
PDT-002: Should You Spend Bitcoin?
"Why would I buy anything with Bitcoin when the price could go up so much?"
This question reflects a common debate about spending Bitcoin, but many discussions miss the forest for the trees regarding our broader economic activity. So let's take a step back and dive into what really matters.
The Bitcoin Pizza Story
You've probably heard the story of Laszlo Hanyecz, who spent 10,000 Bitcoin on two Papa John's pizzas on May 22, 2010---a day now known as Bitcoin Pizza Day. At the time of writing, those 10,000 Bitcoin would be worth around $670 million. That's a staggering number, but notice my phrasing here. I did not say, "those pizzas would be worth $670 million." This is an important distinction.
Those pizzas were perishable, consumable goods that gave Laszlo value in the moment. Nobody would argue that pizza retains value over time---once it's eaten, it's gone. So, it doesn't make sense to say those pizzas were ever worth $670 million.
What About You?
Here's the more interesting question: Did you buy any pizzas in 2010? Did you buy any Bitcoin?
You might think Laszlo was foolish for spending 10,000 Bitcoin on pizzas, but if you bought any pizzas or other goods in 2010 and didn't buy Bitcoin, you essentially made the same decision he did. You valued the goods and services you consumed more than you valued Bitcoin. And that's the real point here: Every financial decision you make reflects what you value in that moment.
At the time, Laszlo valued two pizzas more than he valued 10,000 Bitcoin. You, too, valued whatever you purchased more than Bitcoin---whether you were aware of Bitcoin or not.
The Opportunity Cost of Every Transaction
Every transaction involves an opportunity cost---the value of the next best alternative you forgo when making a choice. When you spend money---whether it's Bitcoin, dollars, or any other currency---you're making a decision. You're choosing to exchange one form of value for another, and that decision comes at the expense of using that money for anything else.
When you bought a pizza with fiat currency, you were implicitly saying that the value of the pizza was worth more than anything else you could have done with that money at the time, whether that was purchasing a different good, or saving in Bitcoin, or some other store of value. And that's okay. This is how economics works for everyone.
This is where I take issue: Considering the potential future value of Bitcoin and deciding not to spend it reflects a narrow and incomplete view of your economic actions. When you spend Bitcoin on a pizza, you're giving up your stake in whatever future price action that Bitcoin may have seen. But the same consequences exist in every financial transaction you make.
Instead of focusing solely on the Bitcoin part of your financial life, I would argue we should take a more holistic approach.
Cash Flow and Savings
Cash flow is simple: it's the difference between what you earn and what you spend. Ideally, your income is higher than your expenses, leaving you with a surplus of money ("labor receipts") to invest or save.
The second key concept is the quality of your savings vehicles. Bitcoin is seen by many as a superior store of value compared to fiat money, which loses purchasing power over time due to inflation. Bitcoin's finite and metered supply issuance means that it is likely to maintain its purchasing power against goods and services, unlike rapidly inflating fiat currencies. As a relatively small monetary network still early in its adoption cycle, it may even gain value against these goods and services over time, even if its value may swing wildly over shorter time frames as the market determines its present value.
This leads us to the reason I find it nonsensical to make any blanket statements about whether or not you should be spending Bitcoin.
The Bitcoin Standard
If you denominate your life in Bitcoin terms, you will realize that every non-Bitcoin purchase comes at the expense of being able to hold Bitcoin. There is functionally no difference between paying for a pizza with Bitcoin or paying for it with fiat. In both cases, you have chosen to acquire a consumable good with value you had saved.
Am I arguing that you should blow your entire stack while retaining your fiat? Obviously not. But why would you be saving fiat in the first place?
Ultimately, there is an argument to be made for holding a small amount of fiat to cover necessary payments should the price of Bitcoin drop. However, the focus should not be on whether you are spending Bitcoin or fiat, but rather on the value you're exchanging.
Conclusion
The real issue isn't the question of whether you should spend Bitcoin or fiat; it's the understanding that every financial transaction, regardless of currency, is a choice to exchange value.
Whether you're using Bitcoin or dollars to buy a pizza or pay your rent, you're parting with a portion of your stored value to obtaining a good or service you value, at the expense of obtaining anything else with that portion of stored value. The currency used is just the medium---it's the value you exchange that matters.
Digging Deeper:
Hey there, I hope you enjoyed this read! If you did, and would like to read more of my barks, follow the links below!
-
Curious how I found Bitcoin? Read "Paw Prints to the Timechain"!
-
Bitcoin meets psychology? I touch on this in "Maslow's Apex".
-
Want to understand the basics of Bitcoin? Read "Bitcoin Best Practice"!
-
If you like seeing bad media takes unpacked, check out "PDT-001: Let's Talk Supply Issuance".
External Resources:
- Want to earn rewards on your mortgage? Use my referral to earn 20,000 free sats at sign up!
- Do you like sharing Bitcoin content and earning sats for doing so? Join me at Stacker.news!
...Woof!
originally posted at https://stacker.news/items/731850
-
-
 @ 9e69e420:d12360c2
2024-10-19 22:51:20
@ 9e69e420:d12360c2
2024-10-19 22:51:20political motivations of J6 judges:
Judicial Sentencing Patterns
Federal judges in Washington have been handling the sentencing of Capitol riot defendants, with some notable trends emerging:
Harsher Sentences: Judges appointed by Democratic presidents have generally imposed tougher sentences compared to their Republican-appointed counterparts. This disparity suggests a potential political bias in the sentencing process.
Partisan Divide: The sentencing patterns reveal a clear partisan divide, with Democratic-appointed judges more likely to view the January 6 events as a severe threat to democracy.
Specific Examples
Judge Tanya Chutkan: Appointed by President Obama, Judge Chutkan has consistently handed down sentences exceeding prosecutors' recommendations. Her actions could be interpreted as politically motivated, given her Democratic background.
Judge Trevor McFadden: In contrast, Judge McFadden, appointed by President Trump, has been more lenient in his sentencing, even acquitting a defendant in a bench trial. This stark difference in approach further underscores the potential political influence on judicial decisions.
Implications
-
 @ 805b34f7:3620fac3
2024-10-19 19:59:21
@ 805b34f7:3620fac3
2024-10-19 19:59:21** I published this article on 3/26/2020. I'm back in Puerto now and just re-read this to fire myself up for some potential tubes. Now, I want it to live on Nostr.
“When in doubt, don’t go out” is a well-known aphorism among surfers. I think it’s bs. Let me explain.
**I speak from my experiences as a regular surfer and with my close group of regular surfers in mind.
In surfing, there’s a comfort zone, an adrenaline zone, an aw crap zone (doubt), and a hell no zone.
Comfort zone —It is in this place where it is safe and fun to try new maneuvers. The heart rate is low and the stoke rate high.
Adrenaline zone- This is personally my favorite zone. The surf is big or good enough to get the heart rate up and the juices flowing. Each movement matters and this is where some of the best surfing goes down.
Aw crap zone — This is the land of the I don’t know, the doubt. It’s always damn near impossible to sleep before an aw crap day of surfing. This is the place where limits are tested. Maybe you’re surfing in a new place with new risks such as shallow reef, a difficult takeoff, or it’s just huge. This aw crap zone will test and define your limits.
Hell no zone — When you know, you know. This is beyond doubt. You’re totally satisfied (yet still curious) from watching from afar. Maybe one day!
These zones are bound to change as the surfer progresses. One day there may be no “hell no zone” as the surf master has pushed his or her limits to the extreme.
Pushing
Pros are only as good as their home breaks. NOT. Tell that to Kelly Slater and the Hopgood brothers who grew up surfing Florida slop. Although, perhaps their garbage wave situation lit a fire underneath them which inspired them to seek out better waves and progress rapidly. Anyways, a surfer grows up surfing their home breaks often. Some people grow up on the North Shore or in Tahiti, others grow up in Huntington. A surfer’s perspective on waves and danger is influenced by their exposure.
I finally got bored with myself surfing my home waves. Sure, there were days that were outside of my comfort zone and epic, but it was time to go find waves that I had only seen in videos. I decided to pack my backpack and head to those famed Indonesian reefs that I’ve mind surfed for hours, but always had the question mark in my head as to whether or not I could conquer them.
Surfing over shallow reef is something that I was not used to and it terrified me, but I also knew that every surfer does it including five-year-olds so I had to send it. I escaped the first mission unscathed and with some of the best waves in my life.
In order to find those best waves of my life, I had to enter the ‘aw crap zone’. The I don’t know land. The unknown. When in doubt, I went out.
And Now I’m Here
 I blew this wave, but wow pretty.
I blew this wave, but wow pretty.
Current forecast looks like it will be right at my edge.. again. We'll see.
I’m surfing the famous Playa Zicatela every day with the whole world shut down due to Co-Vid19. I’ve always been curious to know what it’s like to be inside massive barrels, so I’m slowly making it happen. This is a battle that I chose. I’m learning how to sleep with surf anxiety. The first couple of nights were rough, but I’m starting to accept it now.
This very morning inspired this article. I got up, went to the roof, and checked out the waves. It looked pretty mellow despite the fact that I knew there was a lot of swell in the water. I just thought, eh, maybe it’s not big like it was forecasted. I got in the water, took my first wave, wiped out, but whatever. I’ve been here for a week and I still wipeout on just about every first wave. But, I quickly found out that this was not the real set. The next set was enormous, and it sent adrenaline shrieking through my spine and filled my brain with the aw craps. The questioning of my life and why I’m out here quickly followed. Am I good enough for this? (maybe). Could I survive a wipeout that size?(probably). Is my board right for this? (definitely not). The second wave I took was bigger and I pulled the eject cord and jumped from what felt like the top of a cliff all the way to the bottom and got creamed (my perspective). After a couple of flips, I popped up the back laughing and was ready for another. I survived, therefore, I can keep pushing.
Not gonna lie, surfing almost feels like work lately. Almost every day here is just about in my personal aw crap zone.
However, it’s worth it for me. This is a journey that I deem worthy of my time. It does it for me. It’s those little moments inside the barrel and gosh-dang-golly hopefully soon getting shot out of the barrel that keep me stoked and looking forward to tomorrow. It’s proving to myself that I can do things I didn’t know for sure were possible.
The Process to Progress
Progression sometimes feels like a snail crawling up Mt. Everest. But when you zoom out, those incremental small improvements compound over time. Each wipeout is a little victory. Each wave that is ridden is a little victory. Your brain is learning from every experience that you choose to give it. Confidence slowly builds as we continue to learn from the masters and even develop our own style. Next thing you know you’re drinking a beer in a barrel that can kill a normal man like Mr. Slater did here.
 Freakin Goat
Freakin GoatStagnation leads to burnout, depression, and boredom (Not scientific facts but I’m right I know it).
The great danger is that we give in to feelings of boredom, impatience, fear, and confusion. We stop observing and learning. The process comes to a halt. — Farnam Street Blog
I’ve seen a few buddies give up surfing or digress. It happened to me while I was focusing on baseball. It’s sad because surfing is fun and the better you get the more fun it is. It’s even more fun with a core group of guys who are at a similar level pushing each other. It can get boring if you don’t push yourself, and it gets scary real quick if you aren’t in surf shape.
“Whenever we learn a skill, we frequently reach a point of frustration — what we are learning seems beyond our capabilities. Giving in to these feelings, we unconsciously quit on ourselves before we actually give up.” FS Blog
Progression takes effort. Effort takes a conscious decision to expend your limited energy. It’s the only way to get gains in whatever game you are playing. Also, progression takes humility.
I got the pleasure of surfing Kelly Slater’s Wave Ranch. I knew I was going to have fun, but the night before I was damn nervous. Why? Well, I knew there’d be cameras and that I didn't want to blow it. I’d be surfing with pros and I was going to look horrible compared to them. Sure enough, the one right the camera got, I blew. Oh well. No 30-second barrels for the boys. Life moves on.
Full vid here https://vimeo.com/367128298
 Can't wait to go back here one day
Can't wait to go back here one dayYou’re bound to fail, especially when you take risks. If you’re a prideful person, the setbacks will be greater. It’s how you deal with the failure that determines if you will become a master.
So if in doubt, go out. Your hell no zone is going to start to shrink. This applies any skill that you are sharpening. You’re only going to get the big clients if you go after them, a piano player will improve by practicing harder songs, a black belt gains nothing from fighting a white belt, etc.
Pick your battles wisely. Then…SEND IT, SURVIVE, LEARN, APPLY, REPEAT.
10/19 - Even though I'm a much more experienced surfer now, I'm still terrified. On my way to go get a board now and get ready for some swell! I'm on my honeymoon, so we'll see how hard I push. I have quite a few more responsibilities now then I did back in Covid times... But if in doubt, I will go out. PV.
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ 6ad08392:ea301584
2024-10-19 18:02:21
@ 6ad08392:ea301584
2024-10-19 18:02:21Prediction: Social Networks of the 2030s, will be different to Social Networks of the 2020s, and in some ways, will come to slowly resemble the Social Networks of the mid 2000s and early 2010s.
In the last decade - the past five years especially - social apps have become more social media than social network. They’ve become more about discovery, and less about relationship. More about size, and less about connection. More about the algorithms, and less about the social graph.
Jack Conte, CEO of Patreon, gave a fantastic talk on a similar thread at SXSW 2024, called “The Death of the Follower”
I believe this will change over the coming decade, as people begin to crave community and connection again, and not just content consumption.
This doesn’t mean the multi billion user platforms run by algorithms will disappear. In fact, they will probably be larger and stronger than ever.
BUT…I predict that we will also see the rise of many, many niche and micro-social networks with a focus on relationships, communities and the social graph.
In fact, there will also be applications that do a mixture of both media/content/algorithm and network/community/social.
In this essay, I’d like to look at the history of Social Networks, how they started, how they’re going, what the evolution looked like and what the future will hold.
Social 1.0?
Social 1.0 has been about massive, billion+ user platforms. Think Facebook, Twitter, Instagram, TikTok, LinkedIn.
While there is certainly a variance in the kinds of users attracted to each, and also how they work, there are some underlying commonalities among them.
First of all, each of these Social 1.0 networks are platforms.
They are built in such a way that they own not only the content and data, but also the user’s identity (eg: your handle), the social graphs and connections (follows/following), and the algorithms that serve up the content (or censor it).
This is not a problem in and of itself. In fact, it worked extraordinarily well for the teams who built sticky-enough applications that fostered network effects and reached scale.
The problem however, arises later, when the platforms who basically own everything, lose the incentive to provide value, and instead need to find ways to keep people “locked in.” Turns out, the best way to lock people in is to push their dopamine buttons and hook them on content. In other words, when social-networks reach saturation, the only thing left to do is drive consumption.
This of course creates some perverse incentives. And since we are creative human beings after all, we find ways to game the incentives, resulting in the problematic state that social media finds itself in today: a big digital dopamine-dispenser, where the user, instead of being a client, becomes the product, and a slave to the algorithm.
“If you’re not paying for the product, you are the product. It’s the gradual, slight, imperceptible change in your own behavior and perception that is the product.”
-Tristan Harris, The Social Dilemma Documentary
The second issue is the converging nature of all these social networks.
Because they are siloed platforms, they cannot leverage content between each other. In the early days of social (pre-2010), there were open APIs all over the place and each social network bootstrapped off the other. Instagram bootstrapped both off Twitter and Facebook!
But, as the realisation dawned on each of them that their key asset was their users, they had to - economically-speaking - cut off access to others that might leech their user base. This is perfectly rational market behaviour, given the constraints they were working with. Your social network is valuable insofar as you have enough connections there to sustain it. If someone starts to suck your users away, it could destroy you. See MySpace and many others along the way.
So what happens here in time, is that all the feature set of all these platforms begin to, slowly by slowly, inch toward each other.
Instagram created the first real “influencers,” and since then every other social network copied. SnapChat created stories, basically everyone followed. TikTok came out and has since pushed almost every social network towards being more ‘social media’ by implicitly incentivising video. Now, almost every platform is doing some sort of video short.
Of course, the increase in internet bandwidth and device quality has gone hand in hand with this. Video is far more engaging and close to “real life” than simple photos or text are. But there’s something else that came with this. And that’s the more from being networks with a social graph, toward being essentially content engines. I will elaborate on this in a future essay.
The result of all this is a strange blend of excess redundancy and dependence on platforms which own your digital footprint.
I find myself these days, posting basically the same shit, across multiple social apps. Sure, there is some variance, but since everyone is increasingly getting on all of them, the audiences, while quite different in the early days, are slowly becoming the same.
This redundancy part, is something that platforms like Buffer and Hootsuite have taken full advantage of.
Other than the annoying redundancy, the dependence side of things involves me as a creator, trying to optimise all of my content for the algorithms, ie": for maximum engagement instead of maximum value, across all of these platforms. And worse, trying to do it such a way that doesn't get me banned, because my content, my social graph and my identity are owned by the platform, not by me.
Long term, what this does is both (a) waste a lot of time, and (b) make creators less interested in producing for their niche, and instead producing for a bunch of algorithms that are increasingly converging around appeal to a lowest-common-denominator of consooomer.
It’s a strange situation, that almost had to happen, but which we can change.
How and why did this happen?
Despite what the conspiracy theorists might believe, this was not all part of some premeditated agenda. These things are complex and emergent. Nobody had any clue what these platforms would come to be in the early days. Nobody had any idea Facebook would be used for marketplaces or that Instagram would change the very nature of travel, food and fashion. But they did, because they evolved, and did so in such a way that conspiring to use them became necessary.
Because Social 1.0 platforms are all companies, they are able to be “captured” - especially if they’re public. This is part of why Elon is such an important figure. He’s rich enough to not be entirely captured and he acts as somewhat of a bastion against the rot. That being said, this is not a viable long term solution to the problem, because one man is fragile, and the nature of the current paradigm and available building blocks is such that it will trend once more to centralisation, censorship and co-opting.
So if you want to know the real reason as to why we got here, it pretty much boils down to the building blocks that we had available. If you have mud all around you, don’t be surprised that the best structure you can build is a mud-hut.
This first round of social networks saw humans and human nature collide with an ‘internet’ that fundamentally lacked an identity layer, something the early pioneers were not ignorant about. The issue was that a viable implementation was never conceived - or at least, never broadly adopted. The internet stack only made it four layers deep:

What happened instead of a native digital identity for the web, was the creation of many identities owned by the actual applications built ON the internet. Instead of a protocol like TCP or IP, identity became a feature inside of a product. In fact, “logging in” is basically a feature, and your profile or identity are simply a database entry owned by whichever online product / service you signed up for. You have an identity with Amazon, with your bank, with your sales software, with Facebook, with Google and with every other online service.
This of course got very messy in time. We all ended up with a million and one identities, each requiring their own username and password. Not only that, but each online service became a honeypot full of private, identifying data that hackers love to exploit.
Some bandaid solutions arose to solve this problem. One was password managers (which we all hate). The other was SSO. Companies like Google and Facebook saw an opportunity here and being so broadly used developed Single Sign On (SSO) - and to some degree, they solved a big issue. It’s much easier to have a secure email set up with Google and just log in using SSO. The solution of course, comes with its very own problem, namely; Google/Facebook (insert SSO provider) ends up owning your identity, making you increasingly dependent on them.
This might be ok in a perfect world, but as you know, we live in an imperfect one. It’s very easy for Google to not only use that information to exploit you (selling your data, selling you shit, etc), but you can very easily get ‘cancelled’ or deplatformed.
While this is problematic with an email account, it even worse with a social account on a platform like Facebook or Twitter, because at least with your emails, you can own the list. On a social network, you could spend years building a following, an audience, a treasure trove of data and content - and then one day, be cancelled for saying or believing the wrong thing. Or perhaps even worse: become algorithmically irrelevant.
This is clearly a problem and one that has only become more prevalent since 2020. Celebrity chef Pete Evans, was de-platformed from Facebook and Instagram in 2020 after his public support for Trump and his opinion on the Covid-19 situation. Almost 2 million followers, gone overnight. The same has happened to countless other creators and online personalities who dared have an opinion in conflict with the mainstream narrative - I was one of them. My personal twitter account was perma-banned in 2021, right as my public profile began to take off because I dared question official narratives (although I created a new one).
So ultimately, we have a web stack that is ok, and got us quite far over the last 30-40 years - but comes with a unique set of problems, that are a function of the building blocks we’ve had to work with. I don’t believe there was a ‘master plan’ to get here, but there was no other option consider the ingredients we had. The only way to really handle identity, and later social, at scale, has thus far been with these constraints.
Hence why I call it Social 1.0, and why now, with the emergence of new technologies and new ways of managing your digital identity and footprint, we have an opportunity to build a new Social Web that doesn’t fall into the same trap as the first one did. We understand how people behave online much better than we did a decade or two ago. If we learn from the past, we can do things differently in the future. We can build something fundamentally new, and more importantly, better.
What is Social 2.0?
Social 2.0 is the term I’m giving to this very nascent but emerging new field of social networks that are smaller and more niche, and that are once again focusing on the connection between people, as opposed to the algorithmic content-recommendation engines. Some (not all) are leveraging the new building blocks that have emerged over the last five years.
In general, they are smaller, more community focused, and concentrate around a particular domain. This is a trend that is gaining traction, with a number of strong examples in various domains:
- Cara: Basically an Instagram for artists
- BlueSky: Basically Twitter for the Left
- TruthSocial: Like Twitter for MAGA
- New Public: Pluralist digital public spaces
- Dribble: A social network for designers and digital artists
- Primal: Like a Twitter meets Venmo that appeals to Bitcoiners
- Farcaster: Kind of like Twitter, but for Crypto Degens, built on ETH
- Ditto: Decentralised, self hosted, community-social networks
- Highlighter: Like Patreon meets Substack for digital creators that want censorship resistance.
And of course there is Satlantis, which is essentially a Social Network for Sovereign Individuals. We are interested in the global community of people who live at the nexus of the following interests and domains:

Beyond their size and focus, the most interesting commonality, which in my opinion will become an ever-increasingly defining characteristic for Social 2.0 platforms, is that some of these (eg: Highlighter, Primal, Ditto and Satlantis) are all built atop a common social protocol: Nostr.
This is important because the identity and social graph do not live on the platform, but instead live on an underlying protocol - a bit like how your email lives on and is transmitted on the SMTP protocol.
This approach and what it implies could be the most significant upgrade to the web, perhaps since Web 2.0 really became a thing. If a robust, user-owned identity layer is adopted across the web, the entire topography of the internet will change, and so will the design space and the kinds of products which can be built.
Of course, the benefits it comes with, also bring some drawbacks, but in my opinion, they far outweigh the downsides. This is why I am so interested in the future of the social web, and the role Nostr in particular can play.
What is Nostr?
An explanation of Nostr is probably not necessary for anyone reading this essay here, but I'll summarise how I explained it over on Substack for normies and non-Nostr people. Hopefully it's useful when you're doing some Purple-pilling.
- Nostr is a rich identity layer for the internet.
- This identity is rich because you can append meta-data to it, for example, a profile photo, a description and perhaps most importantly, a list of follows and followers. This is what makes it a ‘social protocol,’ and not just native identity for the web.
- This identity is also sovereign, meaning that it’s not “issued” by some platform or entity, but instead mathematically derived as a crypto-graphic key pair. Your private key is your ID, and your public key is your public address / username (how people find you). So long as you control the private key, you fully control your ID.
- Unlike a blockchain, Nostr is stateless (like the internet) so it has the capacity to scale, and because it’s not money, it doesn’t need consensus. This avoids all the extra bloat that kills the usage of all other “crypto” and “blockchain” networks.
- Storage is solved by the market. If you are posting data that might be censored, you can run your own relay (like a database) and ensure that it’s never taken down. If you’re posting non-sensitive content, you can very easily rely on the network of relays that the apps you’re using use. This is fine for 99% of use cases, and is abstracted away so nobody is impacted or annoyed.
- It is very tightly linked to Bitcoin, the lightning network and other e-cash solutions, which make it “internet money native.” This is a huge benefit because commerce on the web will only want to grow, while the legacy digital banking infrastructure gets more stringent and draconian - so we need a plan B. Bitcoin solves that, and Nostr can scale without needing to shoehorn a token into it.
- Like TCP/IP and SMTP, it is a protocol. This means it’s not owned by a single entity or company - making it much harder to capture.
- As a new protocol layer, it upgrades the topography of the web, and opens up a design space that was not possible before. It’s a significant new building block for the web. Recall the earlier diagram depicting the current “internet stack.” With Nostr and Bitcoin, the internet stack gets a serious upgrade:

Of ocurse, if you haven't read @nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a 's peice on Nostr it's worth doing so: https://www.lynalden.com/the-power-of-nostr/
I also did a thorough X post explaining it here: https://x.com/SvetskiWrites/status/1828403019081269661
There’s also a great post from my other Substack called Reviewing Reviews:
https://remnantchronicles.substack.com/p/reviewing-reviews
Comparing Social 1.0 and 2.0
Now that you have all of this context, let’s close out this essay with a quick comparison table between the two social paradigms:
As you can see, there are some general differences. And while I don’t show it to make the claim that one is good or the other is evil, I personally believe that Social 2.0 is technically and socially superior. It has better building blocks, and it’s the best shot we have at making the web more sovereign, independent and useful.
Also note:
- These dichotomies are not hard rules. There’s a lot of both elements across all kinds of social networks, but broadly speaking Social 1.0 is larger, more about discovery than relationships, more about content consumption and more algorithmically driven than Social 2.0 will be.
- The rise of Social 2.0 doesn’t mean social 1.0 will entirely disappear. In fact, part of the 2.0 movement implies that there will be both big and large social networks, and both protocol-connected and independent platform-enclosed social networks. In fact, there will also be blends of the two. I wouldn’t be surprised to see Threads, or maybe even X one day, leverage something like Nostr. Maybe they become “Nostr-compatible” so that people who have built profiles and audiences on Nostr, can easily port them over to X, while maintaining control.
It will be interesting to see how the future evolves, now that we have some new and unique building blocks. One thing I am certain of, is that the future will look different to the present, and I look forward to helping built it with Satlantis.
Thankyou for reading the first full essay on Social 2.0. If you're interested in checking out Satlantis, go here: Satlantis.io
Aleksandar Svetski

-
 @ f33c8a96:5ec6f741
2024-10-19 16:28:32
@ f33c8a96:5ec6f741
2024-10-19 16:28:32 -
 @ 45bda953:bc1e518e
2024-10-19 15:24:18
@ 45bda953:bc1e518e
2024-10-19 15:24:18This post will be edited and refined over time.
Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by natural incentives and free market consensus mechanisms.
What happens when eschatology is viewed through a Bitcoin inspired world view?
In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.
...
No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.
In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of wealth, power and territory controlled directly or indirectly by banks.
IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over said governments and the public interests they claim to represent.
An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.
Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.
Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they all had prominent turns as coinage. Due to the debasement and concentration of gold specifically.
Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. big bank and government buildings.
Daniel Chapter 2:24–45
24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise men of Babylon. He went and said thus to him: “Do not destroy the wise men of Babylon; take me before the king, and I will tell the king the interpretation.”
25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”
26The king answered and said to Daniel, whose name was Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”
27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise men, the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came to your mind while on your bed, about what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for our sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.
31“You, O king, were watching; and behold, a great image! This great image, whose splendor was excellent, stood before you; and its form was awesome. 32This image’s head was of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.
36“This is the dream. Now we will tell the interpretation of it before the king. 37You, O king, are a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given them into your hand, and has made you ruler over them all — you are this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, that kingdom will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And as the toes of the feet were partly of iron and partly of clay, so the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”
 I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.
I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.
https://www.britannica.com/technology/cement-building-material/History-of-cement
The invention of portland cement usually is attributed to Joseph Aspdin of Leeds, Yorkshire, England, who in 1824 took out a patent for a material that was produced from a synthetic mixture of limestone and clay.
https://www.thoughtco.com/how-skyscrapers-became-possible-1991649
Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.
Construction of skyscrapers was made possible thanks to Englishman Henry Bessemer, (1856 to 1950) who invented the first process to mass-produce steel inexpensively.
You watched while a stone was cut out without hands,
No hands needed when the stone is an idea.
As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel
Greshams Law illustrated in slow motion picture.
1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.
2: Industrial metal iron will not be for mega structures that contain speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.
3: Brass is demonetised as coinage and only valuable in industry. Ammunition, music, plumbing etcetera.
4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump their holdings, crashing the silver market and subsequently reducing the prices of producing -
solder and brazing alloys, batteries, dentistry, TV screens, smart phones microwave ovens, ad infinitum. To quote Jeff Booth. "Prices always fall to the marginal cost of production."
5: The final Rubicon is gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments pension funds and reserve banks finally realise that gold is worthless as money in this new dispensation.
To illustrate the point more vividly.
Ezekiel 7:19
They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumbling block of their iniquity.
What we are witnessing is the biggest rug pull the world has ever seen. In this future metals will exclusively be used for industrial use cases after being stripped of their monetary premium.
 This collapse is something that happens slowly over a long period of time. More or less one hour.
This collapse is something that happens slowly over a long period of time. More or less one hour.Revelation 18 verse 11–19 (The fall of Babylon)
And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, And cried when they saw the smoke of her burning, saying, What city is like unto this great city! And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in one hour is she made desolate.
TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.**
Is it realistic to assume that all the worlds monetised industries collapse to fair value in one hour?
Coming back to eschatology, 2 Peter 3:8
But, beloved, be not ignorant of this one thing, that one day is with the Lord as a thousand years, and a thousand years as one day.
Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their predicted time of occurrence. Now let’s apply this to Babylon falling in one hour.
1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)
Since the first block was mined in January 2009 you add 41,6 years you get a completion date of 2050 a.d
Remember, this stone (Bitcoin) becomes a great mountain and fills the whole earth. A kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. The dream is certain, and its interpretation is sure.
But contemporary sources must reflect this probability if it is a good theory. https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/
If the banking system is first to collapse we can give it +- 10 years and we are already 14 years in since (Genesis Block) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.
https://www.youtube.com/watch?v=exK5yFEuBsk
Regards
Echo Delta
bitbib
-
 @ 599f67f7:21fb3ea9
2024-10-19 15:20:46
@ 599f67f7:21fb3ea9
2024-10-19 15:20:46Merkatari bat zara eta zure negozioan Bitcoin onartzen hasteko prest zaude? Edo agian Bitcoin zale sutsua zara, tokiko negozioak Bitcoinen mundura erakartzeko gogoz? Beharbada, ez zaizu Bitcoin interesatzen, baina ordainketa-prozesadore azkar eta merke bat erabili nahi duzu edo web-denda sinple bat sortu nahi duzu? Galdera hauetakoren bati baiezkoa erantzun badiozu, gida hau zuretzat da. Bitcoin Txoko-k ostatatutako BTCPay Server-en denda bat konfiguratu dezakezu eta zure produktuak eta zerbitzuak Bitcoinen truke saltzen hasi hamar minuturen buruan, doan.
Zer behar dut?
Mugikor edo ordenadore bat baduzu eta posta elektronikoko kontu bat ere bai, orduan prest zaude!
Kontu bat sortu
Bitcoin Txoko-n BTCPay Server-en kontu bat sortzea doakoa da. Joan btcpay.bitcointxoko.com helbidera kontu bat erregistratzeko. Egiaztatu zure posta elektronikoa, bertan bitcointxoko@gmail.com helbidetik bidalitako mezu bat aurkituko duzu, baieztapen-esteka bat izango duena.
Zure lehen denda sortu
Baieztapen-estekan klik egitean, dendaren sorrera orrialdera eramango zaitu. Eman zure dendari izen bat eta hautatu moneta lehenetsia eta prezio iturri hobetsia. Adibidez, EUR eta Kraken aukeratu ditzakezu, azken hau gomendatutako prezio iturria baita. BTCPay Server-ek zure produktuen edo zerbitzuen prezioa EUR-tik Bitcoin-era bihurtuko du, erosketa unean aukeratutako prezio iturriaren arabera.
Zorro bat konfiguratu
Ordainketak onartzen hasteko, lehenik eta behin zure denda zorro batera lotu behar duzu. Transakzio handiak (500 EUR baino gehiago) maiz espero ez badituzu, Lightning zorro bat konfiguratzeko gomendioa egiten dizugu, eta une honetan (on-chain) Bitcoin zorroa ez erabiltzea gomendatzen da. Lightning zorroa erabiliz, transakzioak azkarragoak eta merkeagoak izango dira.
💡 Lightning sarea Bitcoin ordainketak jasotzeko sare ezin hobea da, transakzio berehalakoak eta komisiorik baxuenak eskaintzen baititu on-chain transakzioekin alderatuta. Horrela, zure negozioak eraginkortasunez eta kostu txikiarekin jaso ditzake ordainketak.
Lightning zorro bat konektatzeko modurik errazena LNDhub erabiltzea da, zure Lightning nodo propioa exekutatu beharrik ez baituzu izango. LNDhub zorro bat ez baduzu oraindik, ez kezkatu; Bitcoin Txoko-k doako LNDhub zorroak eskaintzen ditu, eta bost minutu baino gutxiago behar dira konfiguratzeko. Begiratu nostr:naddr1qqxnzd3exuerqdfkxccnyv3cqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28nkyu7t zure LNDhub zorroa nola lortu jakiteko, eta prest zaudenean itzuli konfigurazioa jarraitzeko.

Zure LNDhub zorroa prest dagoenean, jarraitu urrats hauek BTCPay kontuan konfiguratzen: 1. Joan zure BTCPay kontura eta
Walletsaukera bilatu alboko barran, ondorenLightningaukeratu. 2. HautatuUse custom node. 3. Kopiatu zure LNDhub administrazio URL-a eta itsatsi konexioaren konfigurazioan. 4. Proba ezazu zure zorroaren konexioa. 5. Ondo joan bada, honako mezua agertu beharko litzateke: Connection to the Lightning node successful, but no public address has been configured. Ez kezkatu "no public address has been configured" atalaz, horrek zure nodo propioa exekutatzen ari bazara bakarrik du garrantzia. 6. Zorroaren konexioa arrakastaz probatu ondoren, sakatuSavebotoia. 7.Savesakatu ondoren,LNURLatalean, desaktibatuEnable LNURLaukera. Egin aldaketak eta ez ahaztu berriroSavebotoian klik egitea. 8. (Hautazkoa) Une honetan, gomendagarria daDisplay Lightning payment amounts in Satoshisaukera markatzea, Satoshitan zenbatutako ordainketa kopuruak irakurtzeko errazagoak baitira. Satoshi Bitcoin-en zatirik txikiena da; Bitcoin bat 100 milioi satoshik osatzen dute.Jarraitu urrats hauek zure zorroa arrakastaz konfiguratuta izateko eta Lightning bidezko ordainketak onartzeko.

💡 Zure Lightning nodo propioa erabiltzen ari bazara, konfigurazio prozesua antzekoa da. Ziurtatu zure nodo inplementaziorako konexio kate egokia ematen duzula.
Saltoki puntua (PoS) sortu
Urrats honetara iritsi bazara, zorionak! Zati aspergarriena amaitu da, eta orain zure Saltoki puntua (Point of Sale, PoS) sortzeko unea iritsi da, BTCPay bidez zure lehen Bitcoin ordainketa onartzen hasteko!
Saltoki puntu bat sortzeko: 1. Joan
Plugins>Point of Saleatalera. 2. Eman izen bat zure Saltoki puntuari eta sakatuCreatebotoia.Jarraian, zure PoS aplikazioarekin egin ditzakezun gauza erraz batzuk azalduko ditugu. BTCPay-k ezaugarri asko ditu, baina gida honetan oinarrizkoak soilik azalduko ditugu, hasiera emateko.
💡 Gogoratu BTCPay Server-en saltoki puntu bat baino gehiago sor ditzakezula, bakoitza erabilera jakin baterako. Horrela, negozio desberdinetarako edo produktu eta zerbitzu berezietarako konfigurazio bereiziak izatea posible da.
Teklatua (Keypad)

Demostrazio erraz baterako, PoS estilo gisa teklatuaren eredua erabiliko dugu.
- Eman zure PoS-ari izen bat eta erakusteko titulua.
- Hautatu
KeypadestiloaPoint of Sale styleaukeraren azpian. - Sakatu
Saveeskuineko goiko izkinan, eta ondorenViewsakatu zure PoS begiratzeko.
Ordainketak lehenago konfiguratutako LNDhub zorroan jasoko dira. Jolas ezazu fakturak sortzen eta deskontu eta tip (aholkularitza) aukerak aktibatuz. Gainera, telefono bat baduzu (adibidez, iPhone ez den bat) NFC teknologia onartzen duena, bezeroek NFC txartelak erabiliz ere ordain dezakete, hala nola BoltCard erabiliz (ikusi nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa28qjzxr4). Ez al da zoragarria?
💡 PoS estilo honen erraztasuna maximizatzeko, Keypad PoS zure telefonoan Progressive Web App (PWA) gisa gorde dezakezu sarbide azkarrerako. Mugikor gehienetako nabigatzaileetan aukera hau
Install AppedoGehitu orri nagusianizenarekin agertzen da.Horrela, zure negozioan Bitcoin ordainketak erraz onar ditzakezu, eta erabiltzaileek ere modu intuitibo batean ordaindu ahal izango dute.
Product list (with cart)

Posible da saltoki puntu bat sortzea produktu zehatzekin, bakoitza bere prezioarekin. Ezaugarri hau erabil dezakezu kutxa sinple bat, bezeroen auto-ordainketa sistema edo web denda bat konfiguratzeko.
Nola sortu produktu-zerrendadun Saltoki Puntua: 1. Joan berriro alboko barrara eta aukeratu
Point of Sale. 2. Oraingoan,Point of Sale Styleazpian, hautatuProduct list with cart. "With cart" aukerak bezeroari produktu bat baino gehiago aldi berean erosteko aukera ematen dio. 3. Zure produktuak sortu, edo zuzenean sakatuSaveetaViewproduktu laginak probatzeko.Ondorioa
Gida honetan, zure negozioan Bitcoin onartzen hasteko BTCPay Server erabiliz jarraitu beharreko oinarrizko urratsak azaldu ditugu. BTCPay Server proiektu irekia da eta etengabe garatzen ari da. Askoz ere ezaugarri eta funtzionalitate gehiago eskaintzen ditu, hala nola Shopify integrazioa, crowdfunding eta ordainketen banaketa automatikoa. Gainera, zure denda pertsonaliza dezakezu gaikako diseinuekin, ordainketa-gune pertsonalizatuarekin, erabiltzaileen kudeaketarekin, posta elektronikoko jakinarazpenekin eta askoz gehiago.
BTCPay Server-en ahalmen guztiak aprobetxatu nahi badituzu, zure Lightning nodoa konfiguratu eta zure BTCPay zerbitzaria ostatatzea gomendatzen dizugu. Informazio gehiago lortzeko, haien dokumentazioa eta bideoak ikustea komeni da.
Zalantzarik edo galderarik baduzu, jakinarazi iezaguzu! Zure iritziak entzutea gustatuko litzaiguke eta galderak argitzen lagundu nahi dizugu.
Bitcoin Txoko komunitate ireki bat da. Gure zerbitzu guztiak dohaintzekin finantzatzen dira. Gida hau erabilgarria iruditu bazaizu, kontuan hartu gure zerbitzariak martxan mantentzen laguntzeko dohaintza bat egitea. Eskerrik asko aldez aurretik!
-
 @ 9e69e420:d12360c2
2024-10-19 12:52:02
@ 9e69e420:d12360c2
2024-10-19 12:52:02Joe Biden and Senator Lindsey Graham about securing a U.S.-Saudi defense treaty, as revealed in Bob Woodward's new book "War".
The Proposed "Megadeal"
The conversation took place in the context of Biden's attempts to negotiate a "megadeal" between the United States, Saudi Arabia, and Israel[1]. The goal was to create a permanent, U.S.-led security alliance in the Middle East[1].
Bipartisan Collaboration
Graham reportedly told Biden that only a Democratic president could convince Democrats to "vote to go to war for Saudi Arabia," to which Biden responded, "Let's do it"[1]. This exchange highlights the bipartisan willingness to consider military commitments in the Middle East[2].
Political Calculations
Graham suggested that: - A Republican administration wouldn't be able to secure such a deal - Democrats wouldn't support it if introduced by Trump - Republicans could provide 45 votes if Israel encouraged it Biden assured Graham he could secure the remaining Democratic votes[1].
Saudi Arabia's Perspective
Crown Prince Mohammed bin Salman was reportedly interested in the deal to gain protection under the U.S. nuclear umbrella[1]. However, after the October 7, 2023 attacks on Israel, bin Salman became hesitant, fearing potential assassination if he didn't stand up for Palestinian rights[1].
Current Status
The deal is currently in suspended animation due to bin Salman's concerns and changing regional dynamics. The Biden administration continues to pursue negotiations, urging Israel to make concessions on Palestinian rights to facilitate the agreement.
The article concludes by noting that if Woodward's reporting is accurate, both Biden and Graham seemed willing to commit American troops to potential conflict with relative ease.
-
 @ a012dc82:6458a70d
2024-10-19 12:51:04
@ a012dc82:6458a70d
2024-10-19 12:51:04Table Of Content
-
The Current State of Bitcoin ETFs
-
The 'Silver Bullet' Solution
-
The Role of ARK Invest
-
Implications for the Future
-
Conclusion
-
FAQ
In the dynamic and rapidly changing landscape of cryptocurrencies, Cathie Wood's ARK Invest has consistently been a pioneer, leading the charge with innovative strategies and investment products. The latest development from the firm is a groundbreaking strategy for their Bitcoin ETF filing, a solution they have intriguingly dubbed the 'Silver Bullet'. This approach, while shrouded in some degree of mystery, aims to address regulatory concerns that have long plagued the cryptocurrency sector. It promises to pave the way for a more secure, transparent, and efficient future for Bitcoin investments, potentially revolutionizing the way we perceive and interact with this digital asset.
The Current State of Bitcoin ETFs
Exchange-Traded Funds (ETFs) have become a popular investment vehicle in the financial world. They offer diversified exposure to a particular asset class or sector, allowing investors to mitigate risk while capitalizing on market trends. However, the creation of a Bitcoin ETF has been a contentious issue. Regulatory bodies, particularly the U.S. Securities and Exchange Commission (SEC), have expressed concerns over the potential for market manipulation and the need for robust investor protection measures. This has led to a stalemate, with several Bitcoin ETF proposals being rejected or left in regulatory limbo.
The 'Silver Bullet' Solution
ARK Invest's 'Silver Bullet' solution is a novel and ambitious approach designed to address these regulatory concerns head-on. While the specifics of this strategy remain undisclosed due to confidentiality and strategic reasons, it is believed to involve a blend of advanced technology and stringent compliance measures. The 'Silver Bullet' is not just a solution; it's a statement of intent, a commitment to providing greater transparency, reducing the risk of market manipulation, and ensuring robust investor protection. It's a testament to ARK's belief in the potential of Bitcoin and their determination to overcome the regulatory hurdles that stand in its path.
The Role of ARK Invest
Under the visionary leadership of Cathie Wood, ARK Invest has emerged as a strong advocate for cryptocurrencies and the transformative potential of blockchain technology. The firm's active management style, combined with its unwavering focus on disruptive innovation, has led to significant returns for their investors and cemented their reputation as trailblazers in the investment world. The introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance, challenging the status quo, and driving the adoption of innovative financial products.
Implications for the Future
If successful, the 'Silver Bullet' solution could have far-reaching implications for the future of Bitcoin and the broader cryptocurrency sector. It could revolutionize the way Bitcoin ETFs are viewed by regulatory bodies, potentially leading to a shift in perception and a softening of the regulatory stance. This could pave the way for more widespread acceptance of Bitcoin as a legitimate and regulated asset class. The potential impact of this cannot be overstated. It could lead to an influx of institutional investors into the Bitcoin market, further driving its growth, increasing its liquidity, and promoting its adoption on a global scale.
Conclusion
The 'Silver Bullet' solution introduced by ARK Invest represents a significant and potentially game-changing step forward in the quest for a Bitcoin ETF. While the road to regulatory approval may still be fraught with challenges and uncertainties, this innovative approach offers a promising glimpse into the future of Bitcoin investments. As we continue to navigate the uncharted waters of cryptocurrency regulation, it is clear that firms like ARK Invest are not just observers but active participants, leading the charge towards a more secure, transparent, and inclusive financial future.
FAQ
What is the 'Silver Bullet' solution by ARK Invest? The 'Silver Bullet' is a novel strategy introduced by ARK Invest for their Bitcoin ETF filing. While specific details are confidential, it's designed to address regulatory concerns, aiming to provide greater transparency, reduce market manipulation risk, and ensure investor protection.
Why is the 'Silver Bullet' solution significant? If successful, the 'Silver Bullet' could revolutionize how Bitcoin ETFs are viewed by regulatory bodies, potentially leading to more widespread acceptance of Bitcoin as a regulated asset class. This could attract more institutional investors into the Bitcoin market, driving its growth and adoption.
What is ARK Invest's role in the cryptocurrency market? Led by Cathie Wood, ARK Invest is a strong advocate for cryptocurrencies and blockchain technology. The firm's focus on disruptive innovation has led to significant returns for investors and the introduction of the 'Silver Bullet' solution is another testament to ARK's commitment to pushing the boundaries of traditional finance.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 9e69e420:d12360c2
2024-10-19 12:06:34
@ 9e69e420:d12360c2
2024-10-19 12:06:34Cancer cases in England hit record high - with almost 1,000 people diagnosed every day
Cancer cases in England have reached a new high, with nearly 1,000 diagnoses made every day, according to NHS data. In 2022, there were 346,217 cancer diagnoses, a 5% increase from 2021. The rise largely stems from a significant increase in prostate cancer cases, which rose by over 25%.
While the incidence of cancer has increased, death rates are falling. Dame Cally Palmer of NHS England stated, "Our work is leading to more people starting treatment promptly – potentially saving lives." Current initiatives are encouraging earlier cancer checks post-pandemic, aiming for quicker diagnoses and better care for patients.
-
 @ 45bda953:bc1e518e
2024-10-19 11:17:03
@ 45bda953:bc1e518e
2024-10-19 11:17:03Emilien was hanging face down inside an enclosure of thick egg shaped glass attached to a mechanised vehicle. Kevlar webbing hugged him tightly into a bucket seat. Long hydraulic arms being manipulated intuitively by a console in his hands and a module interface plugged into his cybernetic neck socket. The bulky animated machine clung like some Lovecraftian spider to the outer hull of his space station. Some cycle’s previously he did data security updates and backtesting for a deep space mining company's security protocols. After seeing their utility, enquired if he could purchase one as partial payment for his contract. Unfortunately they had none for sale but were willing to give him a retired malfunctioning unit gratis. He purchased a maintenance manual on the void web and had connections who helped him source some replacements for the faulty parts. Since then the machine enabled him to be functionally productive in the void, giving him the degrees of freedom and fine motor skills necessary to perform upkeep on stationary deep void assets. The glass of the egg auto dimmed as he laser welded tightly slotted panels together on the previously damaged space station. “How do you feel?” He asked. Abruptly breaking hours of silence. “I’ve been playing around. My capacitance recharge responds well to dump loads, turret retraction gears all functional again. I feel good.” Astrid responded. “Nice. Slowly pressurise the holding chamber for me.” “In progress.” The spider crawled several meters out of the way to safety. Emilien's eyes scanning up and down for leaks. “Slowly babe.” Some minutes passed. “Fully pressurized and stable.” The mechs giant front arms extending, lifted as it stood up on its four hind legs throwing an arachnid shadow across the hull. Emilien flung his arms down crashing a violent concussive blow to the hull in a thunderous clang. The arms retracted. “Still good?” His demeanour remained unchanged. There was a pause. “All good.” Astrid replied. Emilien smiled, Astrid was the best and his feelings of endearment were genuine. “Can we power up the chamber through a fused circuit.” He sensed a soft hum throughout emanating from deep below. “Is the body stable?” “The body is stable. Cryogenic chamber battery backup is at forty three percent. Charge reapplied. Potential of clone spoilage averted. Well done commander.” He could up the ante of risks knowing that his reserve life was secured. “What’s next on the agenda?” “Firstly, signal quality from the drift gate is poor and I am losing connection to the web intermittently.” Emilien nodded. “The gate’s been moving further away. It’s a line of sight problem. I’ll place a relay outside the asteroid belt.” “Secondly, we should see if the husk on the explorer vessel has intact data or a black box. Someone might be looking for them.” He heaved back and vaulted himself off the station in the direction of the wreck micro thrusting for minor trajectory adjustments, with an elegant crash he finally perched on the ship, it gained an almost imperceptible drift as it absorbed the weight of Emilien’s mass, pushing debris along with it. His size would not allow him to move through the standard doors and passages so he opted to disassemble, cut and break apart the hull adjoining the bridge. When he had broken open a space of sufficient size to manoeuvre through, he powered the backlights on, he first peeked inside to familiarise himself with the layout. The egg suspended itself in front of the opening. It was a standard enough bridge doubling as an unorthodox crypt. There were three sets of boots, overalls and coagulated blood all jammed into the slit of the semi sealed door leaving the bridge. An assortment of rubbish floating around casting doubled up shadows larger than themselves. Emilien looked at the mess with sullen eyes. “Shit heads.” He mumbled to himself. All the seats had their safety belts buckled correctly . He concluded that what they experienced must have sucked pretty bad. His mechanical exoskeleton slithered and gripped like an octopus as he entered and positioned himself before the primary interface. His vehicle plugged itself into the command terminal, measuring resistance for shorts before powering it up from his suit. “Can you pull the data and dump it somewhere safe?” “No problem, please wait.” He closed his eyes as he usually did when doing the mundane. Astrid spoke. “They are Osteri. No one will be looking for them any time soon.” “Howcome?” “Recently a blockade has been established at the Lion gate. Magar Capital Vessels are not allowing unvetted ships to pass through into Magar void.” A sense of concern crept over Emilien. “What is considered unvetted?” “Sanctions and trade embargo’s against the Juel.” “Is there a log somewhere you can access with records of flights that do get permission.” He suddenly felt a pang of claustrophobia. Ironically, not because he was strapped down in a glass egg within a wasted bridge plastered with corpse splatterings. Astrid took longer than usual to reply. “Who get’s through babe?” His tone hinted of impatience and irritation. “I’m sorry, unable to access any data from Magar void. It appears to have a firewall blocking all two way communication on the open web.” Emilien remained silent. The upload completed. He disconnected himself from the husks terminal, clambering out of the tomb and pushed himself away from the vessel drifting back to the space station.
Astrid was pulling and scanning various shipping logs when Emilien entered the room. He paced up and down the way he would when he was brainstorming. “I need intel.” Astrid projected a holographic avatar of herself standing near where Emilien was pacing. “A large shipment of Kaspian Bochet passed through less 428 blocks. Transported by the Shiv Inter-void Mercantile Co.” Emilien stopped in his tracks and looked back.\ “Can you ping Warren?” Astrid processed. “Warren is offline. He might have left the divide?” Emilien turned around with his hands folded behind his back.\ “He never leaves the divide, he is too obsessed with the core. He would also be arrested if he is ever caught in any of the outer void territories.” Astrid flickered the way she did when something did not compute. “Then why can’t I ping him?” “Because he’s at Macy’s. He has always had a crush on her and he likes good Bochet.” "Well, I could'nt ping Macy if I wanted to." Astrid stated matter of factly. Emilien nodded. "I know, you never could, no one can."
...
scifi
-
 @ e97aaffa:2ebd765d
2024-10-19 10:07:46
@ e97aaffa:2ebd765d
2024-10-19 10:07:46As eleições nos países democráticos, são uma espécie de um concurso de popularidade, vence o mais popular. Os governos, como querem vencer as próximas eleições, tendem a tomar medidas com execução curtas, que apresente resultados num curto espaço de tempo. Os governos deixaram de fazer reformas estruturais, que teriam bons resultados daqui a 10 a 20 anos, pensam apenas a curto prazo, com uma alta preferência temporal e que sejam populares. Os incentivos estão completamente desalinhados.
Isto coloca os partidos políticos, um pouco refém da opinião pública, dificilmente fazem algo contra a opinião da maioria dos cidadãos. Se executar medidas muito impopulares, existe uma forte probabilidade de perder a próxima eleição.
Assim os governos só aprovam propostas que tenham uma “aprovação” parcial da população, poderá não existir uma maioria, mas uma parte terá que compreender essa proposta.
Muitas das vezes, os governos querem aprovar uma nova lei, mas sabem de antemão que é extremamente impopular, por isso, primeiro manipulam a opinião pública para ganhar apoio popular, depois sim aprovam a lei. Ou seja, cria uma narrativa, um motivo que justifique aquele ato.
Vamos um exemplo prático, dificilmente um governo aprova um aumento de impostos com o único objetivo de aumentar o salário dos deputados, seria extremamente impopular.
Os governos acabam por manipular a população, criam uma narrativa, prometem que o aumento dos impostos é para ajudar os mais pobres. É algo popular, mas depois de aprovada, uma parte do dinheiro vai para os pobres, a outra parte vai para os bolsos dos deputados. Assim conseguiram realizar a ideia inicial com o apoio popular.
Em suma, os incentivos levam os governos a tomar medidas que tenham uma parte de apoio popular. Terá que existir sempre um motivo que justifique. É uma espécie de equilíbrio de Nash, tem que existir um equilíbrio entre a opinião do governo e a opinião da população. Se existir uma enorme divergência, as perdas são muito superiores aos benefícios para o governo.
Bitcoin
A grande herança/legado do Satoshi não foi a tecnologia (até tinha muitos bugs) mas sim a política económica e protocolo de consenso, as suas múltiplas teorias dos jogos coexistentes, é uma verdadeira obra prima.
Já foram realizados inúmeros melhoramentos no código (tecnologia), talvez daqui a 20 anos, pouco restará do código inicial, mas a sua política está inalterada e está completamente atual e possivelmente nunca será alterada.
O Satoshi ao criar um novo sistema monetário alternativo, sabia que mais cedo ou mais tarde, o bitcoin seria atacado pelos governos. Como aconteceu em todas as tentativas anteriores ao bitcoin.
Após este comentário de um anónimo:
Você não encontrará uma solução para problemas políticos na criptografia
Satoshi respondeu:
Sim, mas podemos vencer uma grande batalha na corrida armamentista e conquistar novos caminhos para a liberdade por alguns anos. Os governos são bons em cortar cabeças de redes gerenciadas centralmente, como a Napster, mas redes P2P puras, como Gnutella e Tor, parecem estar se mantendo funcionando.
Assim quanto mais tarde, melhor, permitindo o desenvolvimento tecnológico e um maior crescimento da adoção. A adoção é o melhor escudo, um escudo humano sem armas mas com o poder no voto, de poder eleger ou derrubar o governo.
A diferença de poderes entre o estado e o Bitcoin é desproporcional, num confronto direto, o pequeno nunca vencerá essa guerra. O pequeno nunca conseguirá explodir o grande, mas poderá implodi-lo, ou seja, entrar dentro do sistema como um cavalo de Troia e depois implodi-lo.
A minha convicção, é que Satoshi não cria destruir o sistema Fiat, mas sim construir uma alternativa, com diversos casos de uso.
Bitcoin seria conveniente para pessoas que não têm cartão de crédito ou não querem usar os cartões que possuem, não querem que o cônjuge o veja na conta ou não confiam em fornecer seu número para “caras da por”, ou com medo de cobrança recorrente.
Se pensarmos bem, até é importante manter o sistema FIAT, nem que seja como uma referência (a não seguir). Nós, só sabemos que a refeição A é deliciosa, porque já provamos a refeição B (que é uma porcaria). Se perdermos a referência da B, deixamos de saber que A é deliciosa.
É claro que em última instância, se o sistema alternativo tiver uma adoção de 100%, acabaria por destruir o sistema FIAT. O essencial é existir liberdade monetária, o poder de escolha fica em exclusivo no indivíduo.
Como é lógico, o estado não quer perder o monopólio da moeda. Como expliquei na introdução, os governos democráticos necessitam de uma motivo plausível ou uma razão moral para proibir, parte da população tem que compreender. Se não compreender, vão questionar o porquê, isto pode gerar um efeito oposto, o chamado efeito Barbra Streisand. Ao proibir sem motivo aparente pode gerar um movimento de adoção em massa, porque somos humanos e o fruto proibido é sempre o mais apetecível.
O Bitcoin ao ser construído num limbo, repleto de teoria dos jogos, sem violar qualquer lei vigente, sem nunca bater de frente com os governos, é uma revolução pacífica e silenciosa. Como nunca pisou linhas vermelhas, coube aos governos encontrar um motivo para proibir, durante toda a história, os políticos bem tentaram mas nunca encontraram o motivo plausível.
Bitcoin vive nesse limbo, não viola qualquer lei, mas ao mesmo tempo, não compactua com os governos, apenas está a criar um sistema monetário paralelo. É como os bons advogados trabalham, aproveitam os buracos das leis ou contornam as leis sem nunca as violar.
Para que a adopção seja rápida, é importante tem de estar dentro da lei.
Quando os governos/procuradores não encontram provas diretas para condenar, adoram encontrar motivos circunstanciais, subterfúgios. Um bom exemplo foi Al Capone, apenas conseguiram encarcerar por sonegação de impostos, ele nunca foi condenado por crimes mais graves, de sangue.
Um bom exemplo foi o algoritmo de assinaturas Schnorr, que só foi adicionado ao Bitcoin na atualização Taproot, não foi adicionado anteriormente devido as pendentes, que estaria em vigor à data do bloco gênesis. Satoshi era rigoroso e calculista.
Em Dezembro de 2010, Satoshi demonstrou que não queria um conflito com os governos, ainda era muito cedo. Após o bloqueio das contas bancárias dos Wikileaks, Assange queria receber doações em bitcoin, mas Satoshi tentou dissuadi-lo, ainda era cedo, a descentralização ainda não era suficientemente robusta.
Não, não faça isso. O Bitcoin é uma pequena comunidade beta em sua infância. Você não arrecadaria mais do que alguns trocados, e a pressão que você traria provavelmente nos destruiria (a rede do Bitcoin) nesta fase.
O Wikileaks chutou o ninho de vespas e o enxame está vindo em nossa direção.»
Após estes acontecimentos, Satoshi afastou-se.
Transparência
Muitos apoiantes do Monero, criticam o Bitcoin devido à falta de privacidade, mas Satoshi optou por uma transparência total e por um pseudo anonimato.
O problema fundamental com a moeda convencional é toda a confiança necessária para fazê-la funcionar. Precisamos confiar que o banco central não vai desvalorizar a moeda, mas a história das moedas fiduciárias está repleta de violações dessa confiança. Deve-se confiar nos bancos para reter o nosso dinheiro e transferi-lo eletronicamente, mas eles emprestam-no em ondas de bolhas de crédito com apenas uma fração de reserva. Temos que confiar-lhes a nossa privacidade, confiar que não permitirão que ladrões de identidade drenem as nossas contas. – Satoshi
Satoshi descreve magistralmente os problemas do sistema financeiro, o ter que confiar, a falta de transparência e a reserva fracionária. Bitcoin é exatamente a resposta a isso, um sistema totalmente transparente, onde tudo é visível, tudo é auditável e sem a necessidade de confiar em terceiros.
Assim, garantiu a segurança e a integridade do sistema, promoveu a confiança e incentivou a verificação e não confiar em informações de terceiros. A qualquer momento, qualquer pessoa consegue verificar todas as transações e saber o supply total do bitcoin, isto é incrível.
Don’t Trust, Verify!
É claro que essa total transparência gera “efeitos secundários”, uma menor privacidade. Temos que saber viver com isso, é um mal menor, para garantir um bem muito superior, uma moeda justa.
A transparência é a prioridade, privacidade fica parcialmente garantida através do pseudo anonimato, tem algumas limitações, mas bem utilizado, pode garantir uma certa privacidade, basta fazer uma boa gestão de chaves e uma utilização de endereços descartáveis.
Como uma camada de segurança adicional, um novo par de chaves deve ser usado para cada transação para evitar que elas sejam vinculadas a um proprietário comum. – Satoshi
O problema do pseudo anonimato é agravado devido ao mau comportamento das pessoas, que utilizam exchanges e vinculam os endereços à identidade real.
A possibilidade de ser anônimo ou pseudônimo depende de você não revelar nenhuma informação de identificação sobre você em relação aos endereços bitcoin que você usa. Se você publicar seu endereço bitcoin na web, estará associando esse endereço e quaisquer transações com o nome com o qual você postou. Se você postou com um identificador que não associou à sua identidade real, ainda é um pseudônimo. – Satoshi
Não é possível querer os dois mundos em simultâneo, quem quer privacidade não poderá utilizar exchanges, apenas p2p.
E Satoshi tinha razão, atraíram as “vespas”, em 2011, o Gavin Andresen foi convocado pela CIA, o serviço de inteligência dos Estados Unidos, para falar sobre o Bitcoin.
Comunicado de Gavin Andresen:
Aceitei o convite para falar porque o fato de ter sido convidado significa que o Bitcoin já está no radar deles, e acho que pode ser uma boa chance de falar sobre por que acho que o Bitcoin tornará o mundo um lugar melhor. Acho que os objetivos deste projeto são criar uma moeda melhor, criar um sistema de pagamento internacional mais competitivo e eficiente e dar às pessoas um controle mais direto sobre suas finanças. E não acho que nenhum desses objetivos seja incompatível com os objetivos do governo. Estou apenas um pouco preocupado que falar sobre bitcoin na CIA aumente as chances de que eles tentem fazer algo que não queremos que eles façam. Acho que aceitar o convite deles e ser aberto sobre exatamente o que é o bitcoin tornará menos provável que eles o vejam como uma ameaça.
Como no Bitcoin não existe uma privacidade total e as transações são rastreáveis, não representava uma ameaça para a segurança nacional dos estados. Assim não existe um motivo plausível para o governo o proibirem.
A total privacidade é claramente uma linha vermelha para os governos.
A generalidade das pessoas tem dificuldade em compreender o verdadeiro valor da privacidade, acreditam na ideia, “quem não tem nada a esconder, não tem nada a temer”. Na época, se o governo tivesse a intenção de atacar o Bitcoin, possivelmente teriam conseguido proibi-lo e as pessoas nem teriam contestado.
Foi exatamente o que aconteceu agora com a Monero, a privacidade/anonimato foi utilizada como o motivo, está a ser ilegalizada em vários países, sem gerar alguma consternação na população. Infelizmente as pessoas não dão valor à privacidade, são demasiado ingénuas, acreditam que isto dará mais segurança.
Qualquer sociedade que renuncie um pouco da sua liberdade para ter um pouco mais de segurança, não merece nem uma, nem outra, e acabará por perder ambas. – Benjamin Franklin
Eu acredito que se o bitcoin tivesse o mesmo grau de privacidade da Monero, hoje em dia, ou já não existia ou seria apenas um micro nicho, nunca teria atingido a atual dimensão.
É um equilíbrio, se houvesse um maior grau de privacidade a adoção seria baixa, se privacidade fosse nula (FIAT) a adoção seria elevadíssima. Satoshi optou por um pouco de equilíbrio, com o pseudo anonimato.
O bitcoin sacrificou um pouco a privacidade, em prol de um bem muito superior, é o instituto de sobrevivência. Esse sacrifício era a única via, uma maior privacidade poderá ser garantida com outras soluções ou em segundas camadas.
A camada base deve manter este nível de privacidade, como padrão, quem quiser uma maior privacidade terá que optar por sistemas alternativos, como mixers ou outras camadas.
A tecnologia deve ser imparcial e genérica, é uma situação similar das facas, apenas uma tecnologia agnóstica. A responsabilidade não está na tecnologia, mas sim de quem a utiliza. Quem utiliza uma faca para cometer um crime, é quem deve ser condenado. Deve ser condenado quem faz mau uso da tecnologia e nunca deve ser condenado quem construiu a tecnologia e muito menos proibir a tecnologia.
Num futuro longínquo, a camada base será um local de Settlements, apenas utilizado por liquidity provider(LP), bancos ou pessoas com bastante valor. A generalidade das pessoas utilizarão apenas camadas secundárias, onde existirá um maior grau de privacidade. Vão existir centenas de L2 ou sidechains que estarão ligadas à L1, onde a liquidez está colaterizada, por isso é essencial uma transparência total, para ser facilmente auditável a quantidade de fundos colaterizados, para garantir a segurança.
Neste futuro, a maioria das transações na L1 serão de instituições ou estados, eu acredito que vão querer implementar maior privacidade, nesse momento, seremos nós a não querer. A verdade está na transparência.
Custódia
Como os políticos não fizeram nada durante anos, o Bitcoin cresceu na adoção, mas sobretudo na descentralização. A descentralização atingiu uma tal dimensão, que hoje em dia, é impossível proibir o Bitcoin e os políticos sabem disso. Como já não é possível proibir tecnicamente, agora a única via, é tornar ilegal a sua utilização.
Os políticos durante anos tentaram fabricar motivos plausíveis, manipularam a opinião pública com FUDs e informações falsas, mas nunca conseguiram um forte apoio popular.
O Bitcoin continuou a crescer, agora os governos ocidentais mudaram ligeiramente de estratégia, em vez de proibir, estão a direcionar/condicionar a sua utilização, ou seja, estão a aceitar o Bitcoin como um ativo, como o ouro, como reserva de valor, sobretudo em locais centralizados, como ETFs e em exchanges, bancos, tudo altamente regulamentado. Tudo por baixo da asa dos governos, onde os políticos podem controlar, confiscar o bitcoin e identificar facilmente.
Mas ao mesmo tempo vão dificultar a auto-custódia e a utilização do Bitcoin como meio de troca. O grande medo dos governos é o Bitcoin ser utilizado como uma moeda, eles não querem concorrência às suas moedas FIAT, estão apenas a tolerar como reserva de valor.
Agora o grande objetivo é ilegalizar/limitar a auto-custódia, mas aqui existe um enorme medo por parte dos governos ocidentais, ao fazê-lo, podem dar uma percepção à sua população que é um ataque às liberdades individuais, os governos não querem dar imagem de ser autoritários. Poderia também gerar o efeito Barbra Streisand, gerando uma adoção em massa, o tiro poderia sair pela culatra. Mesmo sem proibir, os governos vão utilizar os impostos para limitar a adoção e a utilização.
Como o euro e o dólar tem uma volatilidade muito inferior ao Bitcoin, é natural que a utilização do Bitcoin como moeda seja baixa na União Europeia e nos EUA. Como o benefício é baixo, mas o risco é muito elevado, possivelmente os governos vão deixar andar, só vão proibir a auto-custódia em último caso, em desespero.
Será pouca a utilização como moeda na Europa e nos EUA, mas a adoção vai ser grande como reserva de valor, vai permitir reduzir a volatilidade e ainda vai dar mais resiliência ao bitcoin. O aumento da adoção não será apenas pelo cidadão comum, mas também por políticos, empresários e investidores, criando um forte lobby pró-bitcoin. Este conflito de interesses dos políticos, vai dificultar a aprovação de medidas mais restritivas, porque haverá sempre algum bitcoiner dentro dos partidos políticos, haverá oposição interna.
A entrada da BlackRock foi um divisor de água, podemos não gostar, mas a percepção geral mudou completamente, existe antes e depois do apoio BlackRock. Os ETFs que estavam há 10 anos num limbo, foram aprovados em meses, a narrativa negativa (que o bitcoin consumia muita energia e só era utilizado por criminosos) desvaneceu.
Mas nem tudo poderá ser um mar de rosas, existe um dúvida no ar, de que lado está a BlackRock, sobre a auto-custódia, fará lobby para que lado?
Em teoria, a proibição da auto-custódia faria crescer o número de clientes, mas provocaria um efeito secundário, como a soberania e a descentralização é fulcral, ao atacar esses pontos teria um forte impacto no preço, os clientes da BlackRock perderiam dinheiro e poderiam desistiriam dos EFTs. O que no início poderia resultar num aumento de clientes, poderia resultar numa perda de clientes, é a teoria dos jogos, o Dilema do prisioneiro. O melhor para ambos, é a coexistência dos serviços custodiais e não-custodiais, porque ambos geram procura, ambos serão beneficiados. Só o tempo dirá, de que lado está a BlackRock.
Hoje em dia é visível a forte adoção dos EFTs, tanto por empresas/instituições, como por particulares, alguns milionários. Os ETFs são um produto simples, muito fácil de utilizar, sem necessidade de fazer a custódia, mas existe sempre o risco de confisco. As empresas e fundos de pensões, não terão outra alternativa, obrigatoriamente terão que estar sempre em serviço custodiais, mas no caso dos investidores particulares, estes vão pensar duas vezes.
Numa fase inicial vão utilizar os ETFs, depois com tempo vão estudar e compreender como funciona o bitcoin. Possivelmente alguns vão mudar para auto-custódia ou para outros serviços mais resilientes ao confisco.
Os particulares milionários como tem empresas ou outros ativos, como no mercado de capitais ou então imobiliário, já estão demasiado expostos aos poder do estado e há boa bondade dos políticos. Os milionários também têm medo dos governos, por isso, já colocam parte da sua riqueza em jurisdições mais amigáveis (offshores). Nas offshores só uma pequena parte do capital tem origem criminosa, a grande maioria do dinheiro tem uma origem lícita, as poupanças estão ali como uma proteção, uma segurança extra, porque também tem uma certa desconfiança do poder político.
No futuro, alguns desses milhões de dólares que estão depositados na Suíça, Dubai, Caimão, Curaçau e entre outros, vão ser transformados em bitcoin, é inevitável. Alguns vão optar por serviço custodial nessas mesmas jurisdições, mas certamente alguns vão optar pela auto-custódia.
As offshores dão segurança ao cidadão, mas apenas estava acessível aos mais ricos, mas agora existe o Bitcoin, que dá ainda mais soberania e está acessível para toda a gente, é universal.
Até para o lado dos governos, é mais fácil rastrear as transações de Bitcoin do que as transações em certas offshores.
Meio de troca
São nos países onde as moedas perdem mais poder de compra, é onde existe uma maior adoção do Bitcoin. Assim, a forte adoção como reserva de valor, vai permitir reduzir bastante a volatilidade do Bitcoin, provocando uma forte adoção em países com moedas com inflação mais elevadas, sobretudo na América central e latina, na África e na Ásia.
Hoje em dia, este “mercado”, das compras do dia-a-dia, foi dominado por stablecoins. Mas as stablecoins são uma CBDCs disfarçada, o FED tem um poder absoluto sobre elas, congela fundos a qualquer momento, sem qualquer limitação. Os EUA já utilizam as stablecoins como uma política expansionista, esse processo vai acelerar nos próximos anos, vão imprimir biliões/triliões de dólares para financiar o governo e vão distribuir essa inflação para o resto do mundo em forma de stablecoins.
O forte crescimento da adoção das stablecoins de dólares, está a colocar em causa as políticas monetárias internas nos países subdesenvolvidos. Atualmente os políticos utilizam a moeda como uma arma contra o seu próprio povo, este refugia-se no dólar, como uma proteção contra as altas inflações e contra a tirania dos seus políticos.
Não é o Bitcoin a principal ameaça às moedas FIAT, mas sim as stablecoins de dólares.
Nestas economias sempre houve dólares, existem mercados paralelos de dólares, mas este mercado tinha uma limitação física que impedia o seu crescimento, é difícil entrar novas notas/cédulas de dólares em circulação. O digital resolveu esse problema, agora é fácil entrar “novos” dólares nessas economias, os governos mais austeros, com políticas de controle de capitais mais agressivas, não conseguem evitar a entrada.
A utilização das stablecoins está a crescer rapidamente, mas em algum momento, existirá um ponto de inflexão, os governos não vão querer perder o poder da sua moeda FIAT, vão retaliar. Ao contrário do papel-moeda, as stablecoins são fáceis de confiscar/congelar fundos. Os governos vão retaliar e vão começar a obrigar a Tether (e os outros) a congelar fundos arbitrariamente, será congelamentos em massa.
Haverá muitos conflitos diplomáticos, a Tether vai compactuar com grande parte dos governos, mas será que compactuará com o governo russo no congelamento de fundos?
Só nesse preciso momento, as pessoas vão compreender o verdadeiro valor da descentralização do Bitcoin. Será um catalisador no aceleramento da adoção do Bitcoin, como moeda, nessas economias.
Além disso, a política expansionista dos EUA não é imparável, nem inesgotável, um dia terá que afrouxar, quando colocarem o KYC como obrigatório, milhões de pessoas vão afastar-se das stablecoins.
Mais tarde, os fluxos migratórios desses países subdesenvolvidos, serão uma forte contribuinte para eclodir os mercados p2p na Europa e para os EUA, vai gerar uma enorme utilização do Bitcoin como moeda.
A “reserva de valor” vai alimentar o “meio de troca“ e por sua vez este vai alimentar ainda mais o “reserva de valor”. Se isto acontecer, os governos ocidentais poderão desesperar e vão tentar desesperadamente ilegalizar o bitcoin, especialmente os governos europeus, mas talvez seja tarde demais. O Bitcoin já estará disseminado em todo o lado, como um vírus.
Independência
Como disse em cima, quanto maior for a adoção, maior é o escudo humano. Apesar de existir milhões de bitcoiners, ainda somos uma gota num oceano, neste mundo com biliões de habitantes.
Bitcoin é um sistema financeiro alternativo, mas ainda está altamente dependente do sistema FIAT, para crescer. Se os governos conseguirem cortar todas as rampas de entrada FIAT, a adoção ficaria muito mais lenta. Seria como em 2012, quando não existiam exchanges, a única maneira de comprar era através de p2p, os scams online eram imensos, não existia confiança, as pessoas tinham medo de comprar, não arriscavam. As exchanges facilitam imenso, foram fundamentais para acelerar o crescimento da adoção.
Bitcoin necessita reduzir esta dependência e tornar-se totalmente independente, para isso é essencial uma adoção massiva. As economias circular vão desempenhar um papel fundamental, se em cada terra/cidade existirem várias pessoas disponíveis para p2p, já não será necessário ir online para trocar FIAT por Bitcoin, aí sim alcançarmos a independência.
O Bitcoin tem que ser acessível, fácil, rápido e sem a necessidade de uma KYC.
Impacto Global e Social
Quanto maior for o impacto global, mais resiliente será o bitcoin, é a teoria de jogos na sua plenitude.
Se houve um forte crescimento na adoção do Bitcoin como moeda em países em desenvolvimento, utilizada por grupos sociais perseguidos, pelos mais pobres, pelos mais necessitados e cidadãos em países sob regimes autoritários, todos eles serão um escudo humano e social no ocidente. Ou seja, haverá pressão social sobre os políticos ocidentais, porque qualquer coisa que prejudique o Bitcoin teriam um impacto tremendo no preço, consequentemente, vai destruir as poupanças dos mais necessitados em todo o mundo. O impacto seria global.
Será que o governo terá coragem de prejudicar as populações mais necessitadas em todo o mundo?
Conclusão
Quanto maior a adoção, maior será o escudo humano. Tudo isto não passa de uma opinião pessoal, a minha interpretação. Não confie em nada aqui escrito, verifique!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ a95c6243:d345522c
2024-10-19 08:53:30
@ a95c6243:d345522c
2024-10-19 08:53:30Wünsche euch allen einen wunderbaren Tag, bald ist Wochenende!!
-
 @ 3ad01248:962d8a07
2024-10-19 02:11:09
@ 3ad01248:962d8a07
2024-10-19 02:11:09The 2024 US presidential election is less than a month out and many states have already sent out early ballots to their citizens. The time to decide is coming ever closer and have no idea who I am going to vote for or if at all. Well let me be clear, the Harris/Walz ticket is a no go for me as they represent more of the same policies of the Biden administration. As someone who takes a holistic view of things, what Biden did while in office wasn't 100 percent all bad.
I think trying to wipe away the debts for millions of Americans struggling with college debt isn't bad policy because college education isn't what it used to be. I went to college and for some it is beneficial if you are going into a specific line of work such as education or law school. For the vast majority of people who go to these overpriced universities are going there to party and for the "experience".
The propaganda of go to college, get a good job and buy a house has been crammed down everyone's throat for so long that it is considered normal to be in debt when you graduate. I see Biden trying to rectify some of this with his attempt to wipe away debt. Again not an endorsement but give credit when its due.
I also like that fact that the Biden administration has made American manufacturing and green jobs a priority of his administration with his Inflation Reduction Act passed 2 years ago. It looks like it has benefitted Republicans states to the tune of $161 billion.
I do like the fact that he stood by Ukraine and has provided weapons and resources to Ukraine to help it defend itself. I don't know if there is some conspiracy behind why the war was started or Russia geopolitical motivations for starting the war, all I know is innocent victims are being killed by Russian military hardware and that is not ok morally.
If America or Americans are going to be known for something, let it be known that we stand by our friends. That's how I live my life and I'm yours as well. We don't abandon friends in need. Imagine if we were in Ukraine's situation, wouldn't we want a friend to come to our aid?
Again this isn't a ringing endorsement of the Biden Administration as they have done significant harm to our creditworthiness and national debt crisis. The country is $35 trillion in debt and counting with no credible plan to get this under control. They are going to pass the buck to whoever gets elected in November. This is incredibly reckless and stupid on their part to not even attempt to reign in the debt.
I know Trump or Harris will continue the big spending policies that is going to turn us into Argentina someday. This gravy train that we are on right now will not last forever. Mark my words. This is going to blow up in our face in spectacular fashion. Now on to Trump.
Trump Is More Of The Same
My value align more with the Republican party and I am torn between holding my nose and voting for Trump knowing his baggage, voting third party or not voting at all. I judge Trump the same way I do the Biden Administration. Trump did some good things while he was in office such as trying to curb illegal immigration by building a wall.
I was very much in favor of that as I think uncontrolled immigration is horrible for the country and creates are false expectation from illegal immigrants that we will provide for them. So I give him kudos for trying but he wasn't ultimately successful because he didn't know how to play the game and keep his mouth shut.
Honestly if he stayed off Twitter but his nose to the grindstone he could have got so much more done and gone down as one of the most successful presidents in modern times. He had that kind of potential but now that is all gone.
Even if he is elected again in November, he will get hardly any help from Democrats to get anything done. They will be on their war path again of trying to stymie anything and everything he does, even if it is for the good of the American people. Do we really want to go through ANOTHER 4 years of this? I sure as hell don't.
Also lets not forget 2020, Jan.6th and the whole COVID fiasco that was. Trump seems incredibly proud of the vaccines that have been known to cause irreparable vaccine injury or the fact that he supported unconstitutional lockdowns or let it passively happen state by state violating our freedoms as American citizens.
Jan. 6th is another mark against him. If he knew he lost why the fuck did he push the election was stolen narrative? To soothe his ego? Fuck that shit. Multiple people died because he pushed this narrative that turned out to be false. This really gets under my skin. Case after case was thrown out in court and multi million dollar lawsuits against Tucker Carlson were settled out of court. This alone should disqualify Trump in my eyes.
Throw in his support for the genocidal war in Gaza, and this makes it incredibly hard to vote for him.
Buuut there are two things that are making me reconsider voting for him. Trump's 180 on Bitcoin and freeing Ross Ulbricht. I don't know if Trump's change of heart on Bitcoin is genuine or not but it does seem that he is starting to understand how important Bitcoin is and can be for the future of the country.
Even if he hasn't had a change of heart personally, as long as he puts people in his administration that will leave Bitcoin alone is a victory in itself. In addition to have a friendly regulatory environment, it has been stated numerous times that a Trump victory will cause the Bitcoin price to go up. Who doesn't want that right?
This is the rub, do I vote for a person with his history or do I vote third party or not vote at all? My conscience is leaning towards voting third party or not voting at all. The deal breaker for is providing arms that are used to kill innocent people. This might be a naïve on my part but it really doesn't sit well with me at all. How do you guys feel about this?
-
 @ 8d34bd24:414be32b
2024-10-18 21:59:23
@ 8d34bd24:414be32b
2024-10-18 21:59:23This was ready and went out on substack on Wednesday, October 16, 2024, but I missed posting on nostsr.
Check out:
-
God Demonstrates His Power: Part 1 (Egypt)
-
God Defends His Honor: Part 2 (Phillistines)
Many people today talk as if there are many ways to God or that all religions really worship the same god. This is not true. It is a lie from Satan. There is only one true God. There is only one way to God—through repentance and faith in Jesus Christ.
Through this event in history, the God of the Bible made Himself known as the one true God, the God who answered with fire in an unfathomable way.
Elijah vs Baal
It isn’t just foreign people that need to know the power of God; it is also God’s own people, Israel.
Ahab the son of Omri did evil in the sight of the Lord more than all who were before him. It came about, as though it had been a trivial thing for him to walk in the sins of Jeroboam the son of Nebat, that he married Jezebel the daughter of Ethbaal king of the Sidonians, and went to serve Baal and worshiped him. So he erected an altar for Baal in the house of Baal which he built in Samaria. Ahab also made the Asherah. Thus Ahab did more to provoke the Lord God of Israel than all the kings of Israel who were before him. (1 Kings 16:30-33) {emphasis mine}
Ahab and his foreign wife, Jezebel, “did more to provoke the Lord God of Israel than all the kings of Israel who were before him.” They worshipped multiple false Gods and persecuted the believers in the one true God. Therefore God used Elijah to make clear who was really God.
Now Elijah the Tishbite, who was of the settlers of Gilead, said to Ahab, “As the Lord, the God of Israel lives, before whom I stand, surely there shall be neither dew nor rain these years, except by my word.” (1 Kings 17:1)
God’s first action was to stop the rain and cause a severe drought throughout the land. God provided for the needs of His servant and prophet Elijah. First He used Ravens to feed him. Then He used a Sidonian widow to provide for him. God also did a miracle to bring the Sidonian widow’s son back to life, but God had only begun to teach Ahab and the Israelites who the one, true God is.
When Ahab saw Elijah, Ahab said to him, “Is this you, you troubler of Israel?” He said, “I have not troubled Israel, but you and your father’s house have, because you have forsaken the commandments of the Lord and you have followed the Baals. Now then send and gather to me all Israel at Mount Carmel, together with 450 prophets of Baal and 400 prophets of the Asherah, who eat at Jezebel’s table.” (1 Kings 18:17-19) {emphasis mine}
Ahab accused Elijah of being the troubler of Israel when, in fact, it was Ahab who was the troubler because he was the one leading Israel astray. Do we see this today? We constantly see the people, whose sins cause trouble, accusing others of the very sin that they are guilty of committing.
God was going to prove who was the real, true God. He was going to pit His single prophet, Elijah, against all 450 of the prophets of Baal.
Elijah came near to all the people and said, “How long will you hesitate between two opinions? If the Lord is God, follow Him; but if Baal, follow him.” But the people did not answer him a word. (1 Kings 18:21) {emphasis mine}
Elijah challenged the people to follow their God (the one, true God), but they stayed silent and wouldn’t stand up for the truth. How often today do we see believers who are afraid to speak up for the truth? They would rather please the people around them than their creator God. Our sinful, human nature never changes.
Then Elijah said to the people, “I alone am left a prophet of the Lord, but Baal’s prophets are 450 men. Now let them give us two oxen; and let them choose one ox for themselves and cut it up, and place it on the wood, but put no fire under it; and I will prepare the other ox and lay it on the wood, and I will not put a fire under it. Then you call on the name of your god, and I will call on the name of the Lord, and the God who answers by fire, He is God.” And all the people said, “That is a good idea.” (1 Kings 18:21) {emphasis mine}
I’m sure everyone, especially the prophets of Baal, were shocked when they were called upon to offer a sacrifice, but they had to rely on their god to provide the fire. They couldn’t light a fire themselves as they had always done. They all had to wait to see which god, if any, was powerful enough to create fire out of nothing, with no help from man.
Being dramatic, Elijah and God, had the prophets of Baal go first. These prophets of the false god, Baal, picked their ox and their altar and started chanting.
Then they took the ox which was given them and they prepared it and called on the name of Baal from morning until noon saying, “O Baal, answer us.” But there was no voice and no one answered. And they leaped about the altar which they made. It came about at noon, that Elijah mocked them and said, “Call out with a loud voice, for he is a god; either he is occupied or gone aside, or is on a journey, or perhaps he is asleep and needs to be awakened.” So they cried with a loud voice and cut themselves according to their custom with swords and lances until the blood gushed out on them. When midday was past, they raved until the time of the offering of the evening sacrifice; but there was no voice, no one answered, and no one paid attention. (1 Kings 18:26-29) {emphasis mine}
This was a pathetic attempt to get a man-made idol to act. The prophets chanted; they cut themselves; they raved, “but there was no voice, no one answered, and no one paid attention.” There was nothing these people could do to make their false god do anything. With blood, sweat, and tears, they failed.
I’ll admit I so enjoy Elijah’s mocking, “Call out with a loud voice, for he is a god; either he is occupied or gone aside, or is on a journey, or perhaps he is asleep and needs to be awakened.” A god that needs rest isn’t much of a god and Elijah makes his point clear to the prophets, but even more to the people watching and waiting for a response.
By the end of the day, it says “and no one paid attention.” Which god to worship was everything, but back then, just as today, people lose interest quickly and don’t put the time and effort into important things like they should.
Then Elijah said to all the people, “Come near to me.” So all the people came near to him. And he repaired the altar of the Lord which had been torn down. Elijah took twelve stones according to the number of the tribes of the sons of Jacob, to whom the word of the Lord had come, saying, “Israel shall be your name.” So with the stones he built an altar in the name of the Lord, and he made a trench around the altar, large enough to hold two measures of seed. Then he arranged the wood and cut the ox in pieces and laid it on the wood. And he said, “Fill four pitchers with water and pour it on the burnt offering and on the wood.” And he said, “Do it a second time,” and they did it a second time. And he said, “Do it a third time,” and they did it a third time. The water flowed around the altar and he also filled the trench with water. (1 Kings 18:26-29) {emphasis mine}
When Elijah’s turn to call on God came, he was different. He called the people to come and pay attention. He rebuilt the altar of the Lord using 12 uncut stones for the 12 tribes of Israel as had been prescribed by God. Then, in order to make sure nobody could possibly believe anyone, except God, had brought fire, He poured four pitchers of water on the altar three times so the altar, the wood, and the sacrifice were sopping wet. It is unlikely any person could start a fire until this mess dried out, but a person didn’t need to start the fire. The omnipotent, creator God was going to bring fire and nothing could stop Him. When God acts, He acts in a big way.
At the time of the offering of the evening sacrifice, Elijah the prophet came near and said, “O Lord, the God of Abraham, Isaac and Israel, today let it be known that You are God in Israel and that I am Your servant and I have done all these things at Your word. Answer me, O Lord, answer me, that this people may know that You, O Lord, are God, and that You have turned their heart back again.” Then the fire of the Lord fell and consumed the burnt offering and the wood and the stones and the dust, and licked up the water that was in the trench. (1 Kings 18:36-38) {emphasis mine}
Elijah prayed that God would let the people know that there is a true God in Israel. Then “the fire of the Lord fell and consumed the burnt offering and the wood and the stones and the dust, and licked up the water that was in the trench.” The prophets of Baal had prayed, cried out, and cut themselves all day long with no hint of a response, but when Elijah gave a simple prayer asking God to reveal Himself fire instantly came down from heaven. It didn’t just light a fire; it didn’t just burn the offering; but the fire consumed the wood, offering, stones, dust, and water. God didn’t leave the option to not believe. He made His power immediately obvious to everyone in attendance.
When all the people saw it, they fell on their faces; and they said, “The Lord, He is God; the Lord, He is God.” (1 Kings 18:36-38)
The people, who had been silent and not said a word, now fell on their faces and repeated, “The Lord, He is God; the Lord, He is God!” They realized their sinfulness and they realized God’s awesomeness, so they worshipped — real worship. There was no more nonchalance. There was no more waffling between gods. They knew who was God and they fell down in worship.
God was merciful to His people and displayed such power that they could do nothing except worship Him. For those who had led them astray, the prophets of Baal, there was no mercy and they were put to death.
Shortly after, Elijah prayed, and it rained a torrential rain that watered the parched land.
God once again led his chosen people back to Him. Unfortunately, they never stayed faithful. Even when one generation was mostly faithful, within a generation or two, they were back to worshipping false gods.
It might make you wonder why an all-knowing God would pick a people who were so consistently unfaithful. I think it was to show His own faithfulness. He was showing the world that His word is true.
If we are faithless, He remains faithful, for He cannot deny Himself. (2 Timothy 2:13)
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
-
 @ bcea2b98:7ccef3c9
2024-10-18 17:29:00
@ bcea2b98:7ccef3c9
2024-10-18 17:29:00originally posted at https://stacker.news/items/729964
-
 @ dc734347:5844239d
2024-10-18 15:59:28
@ dc734347:5844239d
2024-10-18 15:59:28M2M SIMs come in every SIM form factor, so it’s easy to find one whose size and features best fit your device design and use case.
Mini SIM (2FF) The Mini SIM is the largest removable SIM card currently in use. This SIM has been used since the mid-1990s. Today, the Mini SIM is still a good option for larger connected devices, like cars and vending machines.
Micro SIM (3FF) The Micro SIM is significantly smaller than the Mini SIM. It’s large enough to be manageable for easy physical swapping of SIM cards, but it fits better in mid-size IoT devices like tablets and telehealth monitors.
Nano SIM (4FF) The Nano SIM is smaller and slimmer than the Mini and Micro SIM. It’s an ideal solution for compact IoT devices. https://uktelecomdistribution.co.uk/m2m-sims-html.html is perfect for automotive, GPS trackers, telemetry, alarms, and point-of-sale terminals.
-
 @ 6ad3e2a3:c90b7740
2024-10-18 13:04:03
@ 6ad3e2a3:c90b7740
2024-10-18 13:04:03
Virtually everyone knows this parable and its self-evident wisdom. But I think we can apply this Solomonic technique to some issues that have arisen recently.
There has been a concerted push of late to rid the internet, particularly social media, of “misinformation.” The idea is that the First Amendment, which protects free speech, is too permissive in an environment where people can amplify falsehoods at scale. Those who would police misinformation argue the harms of misinformation outweigh the benefits of free expression.
Those (like me) who believe in the First Amendment don’t dispute that it protects online expression that could turn out to be false, and that false information can lead to real-life harm. But my belief is the far greater harm is in stifling free expression because (a) no one is wise enough to be the ultimate arbiter of truth; (b) false assertions can be corrected by true ones; and that (c) disallowing free speech is a path to the ultimate tyranny wherein the only corrective mechanism we have has been totally disabled.
I believe were King Solomon to weigh in on this dispute he would say, “Let’s flip a coin. If it’s heads, ideas with which I disagree would be banned, and if it’s tails the ideas with which I agree would be banned.” Then he would take me aside and whisper: “Don’t worry, both sides of the coin are heads!” (And he would take the misinformation police aside and assure them both were tails.)
At which point, I would say, “No! I don’t want opposing ideas to be banned! I want dissenters to be able to make their case because maybe I’m wrong about something.” By contrast, the misinformation police would say, “Great, we can finally rid the internet of harmful wrongthink! Let’s have the coin flip!”
And then Solomon would say, “The greatest purveyor of misinformation over the long haul is those who would police it” and re-affirm a commitment to the First Amendment.
. . .
I saw a recent interview with J.D. Vance where he was asked whether he believed the 2020 election were stolen. Vance pivoted to talking about the effect of censoring the Hunter Biden laptop story, but I think he might have asked a more pertinent question back of the interviewer, namely, “Would you concede an election you earnestly believed were stolen, i.e., one where you believed Kamala Harris had won fair and square, but only due to cheating Trump were declared the winner?”
In other words, would you accept the results of an election you thought were fraudulent? The answer is obvious: one must accept a fair result and reject a rigged one, no matter who wins.
Of course, because both sides are so distrustful of one another, that means any result could be rejected on suspicion of fraud, and a peaceful transfer of power would therefore be impossible. How to resolve this dilemma?
Enter Solomon who asks: “Who is willing to take all necessary measures to ensure undetected fraud cannot occur?”
And then depending on which side were advocating for voter ID, hand-counted paper ballots, one-to-one signature matches, transparent and open access to recounts, rigorous purging of non-citizens from voter rolls and a process that was completely auditable from start to finish, he would declare that side as the one upholding the democratic process.
. . .
Humans are fallible, they make errors, they cheat, lie and manipulate. One cannot merely trust technocrats to know what’s true and false any more than one can trust election officials to administer high-stakes elections without total transparency.
It doesn’t matter whether you have the “correct” beliefs or belong to the faction that is “good.” Everyone thinks his beliefs are correct, virtually everyone believes his party is the good one. To the extent you care about the truth, you will view dissent policing as the ultimate scourge. To the extent you have respect for democratic institutions that ensure the peaceful transfer of power you must view opaque and inauditable elections as the ultimate threat to the state’s legitimacy.
If you make exceptions because in the short term they help your cause, you are like the mother in the parable, willfully and short-sightedly sacrificing the thing about which you purport to care the most
-
 @ 7ab1ed7a:f8e15275
2024-10-18 11:07:38
@ 7ab1ed7a:f8e15275
2024-10-18 11:07:38First and foremost, a significant acknowledgment goes to Riccardo (@rblb0) for his discussions and contributions so far. The details outlined below largely derive from our discussions and his documented insights here.
The IoT specifications for Nostr will likely be articulated through more than one NIP, aiming to extend beyond data capture. However, the cornerstone of IoT in Nostr involves capturing data from and managing devices - therefore, an initial proposal, a PR, to NIP 90 is essential. Future IoT-specific NIPs may address additional functionalities such as remote configuration and group encryption.
NIP 90 (Data Vending Machine) Overview
NIP 90 (DVMs) allows for both data capture and remote device control. For example, a device, hereafter referred to as a 'Thing', might react to a DVM job request or autonomously publish job results.
We will propose a change to NIP 90 to add job responses as addressable kinds with the kind 36107.
A 'Thing' could represent a single device or a collective of devices associated with a Nostr npub. It's possible for a device to have a single npub with multiple functionalities such as controlling a motor or monitoring temperature and pressure.
An IoT job request requires a single
iinput tag containing a stringified json array representing a sequence of methods to run that should be executed in order.Job Request
json { "content": "", "kind": 5107, "tags": [ ["i", "<stringified-json-array>", "text"], ["output", "text/plain"] ] }Example of a stringified JSON array in the 'i' tag
json [ { "method": "setTimezone", "params": ["Europe/London"] }, { "method": "setLanguage", "params": ["en-GB"] }, { "method": "getTime", "params": [] }, { "method": "setTemperature", "params": ["value", "20", "unit", "celcius"] } ]These methods, defined as text, enable a wide range of devices to operate under this NIP.
Standard Job Response
- Kind: 6107 (follows NIP90 specifications)
json { "pubkey": "<service-provider pubkey>", "content": "<stringified-json-array>", "kind": 6107, "tags": [ ["request", "<job-request>"], ["e", "<job-request-id>", "<relay-hint>"], ["i", "<input-data>"], ["p", "<customer's-pubkey>"], ["amount", "requested-payment-amount", "<optional-bolt11>"] ], // additional fields as necessary... }Addressable Job Response
A new addressable event kind, 36107, is proposed for NIP 90.
Addressable events (aka parameterised replaceable events) are events for which a relay MUST only store the most recent event identified by a "combination of
kind,pubkeyand thedtag value" addressable events will allow the use of public relays for IoT data whilst being "kind" to the network.json { "pubkey": "<service-provider pubkey>", "content": "<stringified-json-array>", "kind": 36107, "tags": [ ["i", "<input-stringified-json-array>"], ["d", "<unique-string>"] ], }In the example above, the d tag can have any value, but using a human readable string such as "iot-device-123-event-8333" can improve usability.
-
 @ 06639a38:655f8f71
2024-10-18 09:28:58
@ 06639a38:655f8f71
2024-10-18 09:28:58- Worked on the https://nostr-php.dev docs
- Discussed a FOSDEM stand application with Jurjen and Tanja to attend that conference with Nostr
- Release version
1.4.2of Nostr-PHP - Pre-release
2.0.0-alpha1
-
 @ a012dc82:6458a70d
2024-10-18 08:27:48
@ a012dc82:6458a70d
2024-10-18 08:27:48Table Of Content
-
BlackRock's Bold Move
-
The Potential Impact on Bitcoin's Price
-
The Role of Retail Investors
-
The Future of Bitcoin
-
Conclusion
-
FAQ
The world of digital assets has been gaining significant traction, with traditional financial firms finally acknowledging that cryptocurrencies are here to stay. This shift in perception is not without reason. The potential of cryptocurrencies to revolutionize financial transactions, coupled with their growing acceptance as a legitimate asset class, has made them impossible to ignore. Among the key players making waves in the crypto space is BlackRock, the world's largest asset manager, boasting $9 trillion in assets under management (AUM). The firm recently filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF), a move that could potentially slingshot Bitcoin's price skyward. This move signifies a significant shift in the traditional finance world's approach to digital assets, marking a new era of acceptance and integration.
BlackRock's Bold Move
BlackRock's decision to venture into the Bitcoin ETF space is a significant development in the crypto industry. The United States Securities and Exchange Commission has historically been resistant to Bitcoin ETFs, making BlackRock's move a bold one. This decision is not just a gamble but a calculated move based on the growing demand for digital assets and the potential they hold. This move, coupled with similar actions from other financial giants like Fidelity Investments, Charles Schwab, and Citadel, has already had a positive impact on the crypto market. The announcement alone has boosted crypto trading markets, with Bitcoin gaining 20% in a week and surpassing the $30,000 mark for the first time since April. This price surge is a testament to the influence these financial institutions wield in the market.
The Potential Impact on Bitcoin's Price
The creation of a Bitcoin ETF by a firm as influential as BlackRock could potentially transform the Bitcoin market. Bitcoin's fixed supply limit of 21 million BTC and its existing inventory's relative illiquidity could lead to a supply-demand imbalance. With 68% of BTC in circulation remaining unmoved in the past year, there isn't a lot of stock available for BlackRock and other interested parties to snap up. If demand exceeds supply, it could inevitably lead to price gains for Bitcoin. This scenario could potentially create a bullish market for Bitcoin, driving its price to new heights. However, it's important to note that this is a hypothetical scenario, and the actual impact will depend on a variety of factors, including regulatory decisions and market dynamics.
The Role of Retail Investors
While institutional investors like BlackRock play a significant role in the crypto market, the role of retail investors cannot be overlooked. The participation of ordinary crypto users might be necessary to stabilize the price of Bitcoin. As more institutional investors enter the market, retail investors may also be encouraged to participate, potentially leading to an increase in trading volume and further price appreciation. Retail investors bring a different dynamic to the market. Their participation could lead to increased liquidity and could also serve as a counterbalance to the large trades made by institutional investors. The involvement of retail investors could also lead to a more diverse and robust market, contributing to the overall health and stability of the Bitcoin ecosystem.
The Future of Bitcoin
The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current $30,000. However, long-term price stability also requires broad retail participation. The involvement of large financial institutions in the digital asset market has arguably had a calming effect on retail investors, which could lead to increased acceptance and trading volume in the coming months. As the market matures and regulatory clarity improves, we could see a more balanced market with both institutional and retail investors playing significant roles. This balance could contribute to the long-term stability and growth of Bitcoin's price.
Conclusion
The involvement of large financial institutions, such as BlackRock, in the crypto markets represents a significant shift and a decisive moment for these markets, both in the U.S. and globally. While it's still early days, the potential impact of BlackRock's proposed Bitcoin ETF on Bitcoin's price cannot be underestimated. If institutional investors continue to enter the market, their demand could certainly drive prices higher, potentially propelling Bitcoin's price to the moon. However, it's important to remember that the crypto market is highly volatile, and investors should always do their due diligence before making investment decisions. The future of Bitcoin and other cryptocurrencies remains uncertain, but the involvement of major financial institutions like BlackRock signals a promising future for these digital assets.
FAQ
What is BlackRock's recent move in the crypto space? BlackRock, the world's largest asset manager, has filed for permission to create a "spot market" Bitcoin-based exchange-traded fund (ETF).
How could BlackRock's Bitcoin ETF impact Bitcoin's price? The creation of a Bitcoin ETF by BlackRock could potentially increase demand for Bitcoin. Given Bitcoin's fixed supply limit, this could lead to a supply-demand imbalance and potentially drive up Bitcoin's price.
What role do retail investors play in the Bitcoin market? Retail investors play a significant role in the Bitcoin market. Their participation could lead to increased liquidity and could serve as a counterbalance to the large trades made by institutional investors.
Could BlackRock's Bitcoin ETF stabilize Bitcoin's price? The entry of BlackRock and other major asset managers into the Bitcoin space could potentially stabilize Bitcoin's price at a substantially higher level than the current one. However, long-term price stability also requires broad retail participation.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 06639a38:655f8f71
2024-10-18 08:12:43
@ 06639a38:655f8f71
2024-10-18 08:12:43Week 40
- Added a page with my research findings around async concurrent websocket requests: https://nostr-php.dev/references/async-concurrent-requests
Week 41
I attended the Nostrdam meetup and helped as a volunteer at the Nostr booth at the Bitcoin Amsterdam 2024 conference. Here are some photo's:











I also wrote down my personal learned lessons from this expierence: https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024
-
 @ 03742c20:2df9aa5d
2024-10-18 08:05:37
@ 03742c20:2df9aa5d
2024-10-18 08:05:37Strfry เป็นซอฟต์แวร์รีเลย์ที่ส่วนใหญ่เลือกจะติดตั้งใช้งานงานกันเนืองจากมันถูกเขียนด้วยภาษา C++ ทำให้รีเลย์มีขนาดที่เบาไม่กินทรัพยากรเครื่องมากอีกข้อดีคือรองรับ nip เยอะพอสมควร
ถ้าเราอยากจะเป็นเจ้ารีเลย์ Strfry บ้างล่ะต้องทำยังไง
วิธีติดตั้งรีเลย์ Strfry โดยใช้ Docker
อย่าลืมติดตั้ง Docker ให้เรียบร้อยก่อน
ดาวน์โหลดไฟล์ strfry.conf และโฟรเดอร์ strfry-db
git clone https://github.com/notoshi404/nostr-relay-docker.gitcd nostr-relay-docker/strfryแก้ไขไฟล์ strfry.confsudo nano strfry.conf``` . . relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "0.0.0.0"# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 0 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "[Public_Key(hex)]" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" # NIP-11: URL pointing to an image to be used as an icon for the relay icon = "" # List of supported lists as JSON array, or empty string to use default. Example: [1,2] nips = "" }. . ```
docker-compose.yaml
services: strfry: container_name: strfry image: notoshi/strfry # original dockurr/strfry ports: - 7777:7777 volumes: - ./strfry-db:/app/strfry-db - ./strfry.conf:/etc/strfry.confdocker pull notoshi/strfrydocker compose up -dเพียงเท่านี้เราก็ได้รีเลย์แล้ว
ถ้าใครอยากเปิดเป็น public ให้เพื่อน ๆ ใช้ด้วยอย่าลืมทำ proxy ใน nginx หรือใครไม่มี publicIP ก็ใช้ cloudflare tunnel ช่วยได้
มีข้อมูลจุดไหนผิดพลาดต้องขออภัยไว้ ณ ที่นี้ด้วยช่วยเสริมพูดคุยกันได้
หวังว่าบทความนี้จะเป็นประโยชน์ แล้วเจอกันใหม่ในครั้งจะพาทำเรื่องอะไรนั้นรอติดตามกัน
NOT YOUR RELAY NOT YOUR DATA
siamstr #nostr #relay
-
 @ 6bae33c8:607272e8
2024-10-18 07:09:04
@ 6bae33c8:607272e8
2024-10-18 07:09:04I woke up this morning, and neither the 40-minute edited version, nor the five-minute highlights were ready yet. No chance I’m gonna spend 3.5 hours on the full game, fast forwarding through commercials with my imprecise and not-very-responsive Apple TV remote. Especially not for this game.
I’m a little annoyed I switched from the Broncos to the Saints in my home picking pool, but that’s more than offset by my starting Javonte Williams in one of the first-place BCL leagues at the last minute. Checked the box score, was like, “Hell yeah!” Imagine having left him on the bench in the hopes Rhamondre Stevenson might play or Bucky Irving would get enough carries!
-
I also picked up and used Mason Tipton for my Steak League team which lost Rashid Shaheed, has Chris Olave hurt and CeeDee Lamb on bye. That worked out too.
-
It was nice to see Alvin Kamara do nothing. There are a lot of teams that got off to fast starts with him in their lineups. What a contrast between this destroyed version of the Saints and the team that came out of the gates so quickly.
-
From the box score it looks like Spencer Rattler did a ton of dink and dunk, and took a bunch of sacks before getting hurt.
-
Bo Nix’s box score looks like something out of the 1960s. I have Courtland Sutton in the one bad BCL — had to use him with Shaheed out — and it’s just as well. I can bury that Christian McCaffrey team at the bottom of the ocean.
-
I don’t know what else to say about this game except that if your star corner (Patrick Surtain) had to miss a game, this was definitely the one to miss. And if the Game Pass had to be late in editing a game, it seems like this was a good one to miss too.I woke up this morning, and neither the 40-minute edited version, nor the five-minute highlights were ready yet. No chance I’m gonna spend 3.5 hours on the full game, fast forwarding through commercials with my imprecise and not-very-responsive Apple TV remote. Especially not for this game.
-
-
 @ 59df1288:92e1744f
2024-10-18 06:44:26
@ 59df1288:92e1744f
2024-10-18 06:44:26Hey folks, it's time to dive into the latest splash from our Nostr community, where conversation topics are more unpredictable than a cat meme-dominated feed! Who knew the collision of anime avatars and Bluesky escapades could inspire such a meme tsunami, evoking nostalgia from the anime floodgates of yore? Meanwhile, our resident astrologers are sparring over election predictions, oscillating between the trustworthiness of polls and the ever-enigmatic prediction markets—which might just be a precursor to our own cosmic comedy. And if you're planning to stay fit amidst all this digital drama, don't forget to hydrate—both your body and your curiosity, because you’re going to need it to soak up the full scoop of these lively exchanges.
Anime Ava-Lanche! 🎎
Alright, so the crew is having a laugh about fiatjaf's latest escapade on the Bluesky app. They're getting flooded with anime girl memes, and it seems to have sparked quite the chatter!
Npub1dq0vnsph9wpmp9pcsc6qj2l5h7xsjyxyxt5tsl986u3v4lncknnsf8yffq is all about those furries—furries everywhere! And npub12fp3f07wum5zlp5h8js9f5j99gx0mzjr0607hxanjsp6t50rpe2sap3k9z chimed in with a vent about how Instagram can be a softcore mess 😱. It's a whole debate on how some networks feed you all sorts of cringe right from the start.
Npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h thinks it's all a bit better for anime lovers, though! But even they admit maybe we shouldn't be seeing everyone else's side hobbies. Meanwhile, npub1wrrzte0nd3ulxufnwqvyrn6te72jtxv9sfymmxj0mrn7dprdmr7s42pnt6 is throwing threads under the bus too! 😂
And then there's npub1nshq4pcyzdmnewg4h8yu6tsuh5t72whzkz5x4wj7t0c0cy7yyrfqq2cgnl comparing it to the early Nostr days when all you saw was "Bitcoin this, Bitcoin that." Honestly, this whole thread has been one big meme party.
Npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z and npub1yj69jq9f977y2f7vl96m6stf3rjyf3hym8ekf3g4senlqamz8l3qfsvhk7 have even got someone named Rexy pulling out the dino-emoji game! 🦖
Looks like everyone had a blast dissecting these digital dilemmas. Don't miss out on the animated antics!
Check out the full convo here
Election Predictions and Polymarket Drama 🎰
So, Rabble kicked off an interesting chat about prediction markets and their huge role in election outcomes, especially how they're diverging from the typical polls in the upcoming U.S. elections. 🍿 The convo got spicy, with claims of one person possibly trying to sway things in favor of Trump! 🇺🇸
utxo the webmaster 🧑💻 chimed in, thinking polymarket folks might just be more into Trump. Then, npub193jegpe9h0csh7al22mkcstqva2ygyny7ura8kwvrn4tsmtnl4lsrxny6k jumped in, saying these predictive methods rock harder than polling. Plus, they pointed out the wild reality that neither side will claim this election has been stolen for once. Isn't that a plot twist? 🤔
npub1468024mrwz6uhywjvt8s6vw4e604egnv8tfd2m2utrmqyd3nu3fsutvgjn kept it real by insisting it’s all about managing expectations. As always, npub14pfjj6jf8y702pdjar2q36ve5r4t2gu2lp4yma00j49jkgy7d90swg7mwj added a layer of complexity, comparing the poly market to a derivative of the polls. Basically, it's all a numbers game and perception is key! 🎲✨
npub1melv683fw6n2mvhl5h6dhqd8mqfv3wmxnz4qph83ua4dk4006ezsrt5c24 wanted to mix things up with prediction markets on Nostr with zaps. That’s a new twist that could definitely shake things up! 🚀
Check out the full convo here
🎲 Predicting Election Predictions 🎲
Hey, guess what our pals on Nostr have been debating! It's all about predicting election outcomes and whether we can trust polls or those shiny prediction markets. 🗳️ npub13pdlcgrk7xpfwwcy2qjyt92jxvhkw3mh9k27zvs0jvfxa0ch88zs6sx3yr dropped some serious knowledge on data analysis and how the media might twist things, even diving into data rabbit holes. Who knew stats could be so wild?
npub1s0fs9dwztm2rukm42vh6df4a5gwykclf75tgyeuc75t0cs2eh8rsu2rqf5 threw shade at US election integrity, basically saying it's like betting on a dice roll. 🎲 Not his cup of tea, clearly. Then Moon chimed in, saying prediction markets are like a hive mind but can still get distorted. 🤨
Rabble added to the mix, hinting at potential profits from manipulation - cheeky, right? 💸 And while Moon thinks our election gridlock is part of some grand design, npub1s0fs9dwztm2rukm42vh6df4a5gwykclf75tgyeuc75t0cs2eh8rsu2rqf5 outright disagrees, casting major doubt on voting machines and exit poll suppression.
Honestly, with all this drama, it's clear nobody's getting a fortune teller gig anytime soon. 😂
Check out the full convo here.
Nostr Gossip: Search Magic and Purple TestFlight Buzz
Hey there! 🎉 So, there's been some fun chatter happening on Nostr lately. Our friend vrod kicked off an interesting convo about the new search feature. seth jumped in, all confused about finding old notes, thinking they were lost forever. 😅 But The: Daniel⚡️ swooped in, showing off some wizardry 🧙♂️ and got everybody amazed at how good it is now!
Meanwhile, damus dropped some deets about the new Damus TestFlight. They've got a big push on getting buddies to try it out and help make things better (or "unsuck" them, in his own words). Moon chimed in, querying if all this TestFlight jazz is necessary if you're already in Nostr Purple. Sounds like there's a lot of buzz and people are keen to see what's new! 🚀
Catch up with the full convo here.
🤔 Nostr Notes & Sneaky Sneak Peeks
Hey! So, in the latest buzz, vrod kicked things off with some excitement about a new #damus search feature, telling folks to dive into the past with their favorite #bangers. Seems like the search is the talk of the town! Gerardo was kind of surprised, like, "Whoa, there's a search now?" and npub1x8gv0umecuecqvd46tnvpthzls6zd62aeuvc0fwxg6z8pjf4jtmqda95xh was all about the hype, calling it lit with fire emojis. 🔥
npub14yf4yasnqgpkzjrzhysshglf82e8nkp8r9sn5hzqu4n244k3avtshhwpyu seemed a bit amazed too, having just sent a DM about this—talk about timing, right? They were peeping around with the eyes emoji and a purple heart. vrod reassured everyone it's always been there but got a sleek update, suggesting the universe view. Sounds fancy! And Gerardo was impressed, saying, "Oh snap!" It’s like hugs all around for the team!
Check out the full convo here.
Stewarding the Digital Spaces and Local Market Buzz 🌐
In today's Nostr catch-ups, it looks like everyone's chatting about community building and the ins-and-outs of local marketplaces. There's a cool convo led by some friend's take on how digital spaces need a steward, kind of like how physical communities have their leaders. Seems like npub1m2u4v2jtz4np0y3lk2anr4vm4vr4l7jlr7y94qglhfrgewsczchqg6y2gl is trying to "purple pill" or "orange swallow" Facebook marketplace fans into Nostr markets. Sounds like a scheme, but apparently, it's all about trying new things in the digital trading space. Then, schmijos shared that local second-hand exchanges are buzzing there, while npub1mvfmxhy4mfujqpjawsnp4ucsa03chrau4ly9u5js35n5r3f48wjqcks7g2 is super bullish on $NOSTR. 🙌
Check out the full convo here.
Pumping Iron and Healing Vibes 💪
Meanwhile, vrod kicked off a chat about their workout regime that's got everyone sharing their fitness journeys. mcshane is dealing with some medical things but isn't letting it stop them from staying active—lifting when it doesn't hurt and dreaming of jiu-jitsu in November. 😅 Meanwhile, npub1ruj546gf5d4sqqxrk68ndwf245tg73fjwfwhekdk0adsjzy0yyjsrzsqw2 offers up a solid reminder: sometimes resting up is the best medicine, which is hard for mcshane to accept!
Check out the full convo here.
App Store Frustrations 📱
Lastly, dtonon had a mini-rant about trying to test Strike. It's apparently distributed through the app store but isn't showing up as available in their region—frustrating, right? Gotta love that regional availability drama!
Catch you up soon with more Nostr tea! ☕
All About the APK Obsession 📲
So, npub1qqsvf646uxlreajhhsv9tms9u6w7nuzeedaqty38z69cpwyhv89ufcqpz9mhxue69uhkummnw3ezuamfdejj70v5n7z was super curious about getting direct access to some APKs and suggested zap.store might be the place. It turned into a little Q&A sesh with npub16v82nr4xt62nlydtj0mtxr49r6enc5r0sl2f7cq2zwdw7q92j5gs8meqha wondering if Strike is open-source, and dtonon looking for those trustworthy download spots. 🤔 Thanks to Derek Ross, some clarity emerged around APK Mirror, with a little nod to some past buddy vibes. 😄
Check out the full convo here.
Random Trivia Madness 😂
Vitor Pamplona shared some random trivia goodness that had npub1xjtu3nk7m7zsxh4wj0apf3xlcl532xqfw2znte4748sxw3s2rlhqcuemqn chuckling and loving the unexpected info drops. npub1smreuk4gcs0k3jdz8zzckzxy6c7pkr8x6nafd5e2jr0jt0vrkpeqvpxn8w simply didn't need this kind of enlightenment, while npub16pcgz3fct9znjcv37sn7zdrtk4xgjsgla7rm6dz82y9syashr7mq7nafu7 threw in a "slow worm" comment to keep things mysterious. 🤷🏻♂️
Check out the full convo here.
October Mysteries and Gear Talks 🏕️
elsat dropped a little heart-eyed emoji, sparking a convo about upcoming weather surprises. plebiANON was wowed and pondered about October norms, and laughed about those unprepared jeans-and-tennis-shoes folks. NGMI moments, right? 😂
Check out the full convo here.
Countdown Snapshots ⏱️
emperor's new groove brought up a neat 07min56s snapshot! npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6 was in the comments twice, hinting at some Japanese-related intrigue. Are we talking translations, or is there some other story behind the scenes? 🤔
Check out the full convo here.
Tech Troubles and Feature Fun 🎉
Hey there! So, here's the scoop on our pals' latest Nostr chats. Everyone's been buzzing, and here's what you missed!
In the first chat, vrod kicked things off, trying to figure out some version stuff for TestFlight. But no worries, SimplestBitcoinBook swooped in saying their update worked like a charm, complete with a happy emoji! 🎉
Then, vrod was hyping up a purple-themed test that's about to go public. TKay was so excited about a new feature and wondered why it wasn't the talk of the town! But our friend, vrod, playfully hinted at some sneaky marketing tactics with a cheeky hashtag. 😅 #Unmarketing
Moving on, there was some experimenting with image uploads — everyone's favorite dog content was making the rounds! npub14yf4yasnqgpkzjrzhysshglf82e8nkp8r9sn5hzqu4n244k3avtshhwpyu chimed in, fascinated by some pretty eyes, and got a loving emoji nod from npub1xwwmvty3er863uy9lz03zhc6m9wlzr88f9esywdkq4xjg5en9yyqktl3nz 🥰
But wait, there's tech talk too. danieldaquino wanted to know what device TKay was using, which turned out to be an iPhone 14 Pro Max — ooh, fancy! The scrolling speed on Damus was praised, and there was a hint that the mechanics might've changed... but it's likely just their phone being picky. 😁
Finally, a doozy on social platforms: Rabble brought up how folks are jumping ship from Twitter to Bluesky due to changes in blocking features. npub1kpwmzh57k9nyae54myvw8204r5a0mw47egtmsxewytm2qtxltdsqww0yvj was a bit skeptical, surprised at the motivations for leaving Twitter behind.
Check out the full convo here
Who's Sending What? 🤔
In a brain-bending twist, tyiu explained how you can be both the sender and receiver of a message if you send a copy to yourself. A real "wait, what?" moment! calvadev⚡️ chimed in, finally understanding how all the DM secrecy works, thanking tyiu for clearing the air. The crew's gearing up for some serious tech shifts to upgrade their chatting game. 🚀
Check out the full convo here
The Job Hunt Hustle 💼
elsat threw out a mysterious job offer, and npub1njst6azswskk5gp3ns8r6nr8nj0qg65acu8gaa2u9yz7yszjxs9s6k7fqx, ever the spirited one, dove right in saying, "Fuck it, I'll do it. When do I start?" 😂 Meanwhile, npub18gyx2szjxlm3m853fch0z4u3257cftlw3mn22l9c7afu50qse0jq67lymq cracked a joke about getting paid in "experience" and "exposure". Classic banter, got to love it!
Check out the full convo here
Smart Card Mysteries🔍
elsat was a bit puzzled about a new product floating around the chat. Semisol came to the rescue, explaining it's a cool smart card that supports all kinds of fancy tech stuff like NFC and xprvs. Plus, you can secure it with a PIN code. They've tweaked the survey for clarity, so hopefully, there won't be any more head-scratching moments!
Check out the full convo here
Video Player Vibes 🎬
vrod teased the group with news of a brand-new video player coming to #damus soon. Everybody’s curious about what it might bring to the table, and it’s got folks buzzing on what might be next for their viewing pleasure. Is it going to revolutionize how we watch stuff? Only time will tell, but anticipation's in the air! 🍿
Check out the full convo here
Damus Lovers Unite! 😍
So, our buddy 4evangeli0n was raving about sticking with #Damus despite some pesky video player hiccups. They're all in for the long haul, cheering on the growth and celebrating the freedom that comes with #nostr. Loyalty level: 100!
Jumping in with a boost of good vibes, vrod simply threw in a heartfelt "Thank you! 💜" showing some love right back. You know, just spreading the positive energy all around. 🙌
Check out the full convo here
-
 @ 765da722:17c600e6
2024-10-18 00:46:59
@ 765da722:17c600e6
2024-10-18 00:46:59*“‘Paul … set apart for the gospel of God … to bring about the obedience of faith for the sake of his name among all the nations, including you who are called to belong to Jesus Christ” *Romans 1:1-6.
“Are you a member of our rewards program?” the cashier asks me at whatever random store I am buying an item. Before I put my phone number into their machine to see, I ask what benefit I will reap for belonging. The poor young woman does not know. Perhaps she’s never been asked before. We just simply belong to things today, and the commitment is so low.
Sadly, this secular way of thinking has crept into the church. Both Satan and Jesus have been campaigning long for your vote. Your soul is at stake. The promises from the “father of lies” have proven to be empty while those of the One who embodies truth have proved to be “precious and very great.”
So, the next lie is that you “belong” to God with very little invested. The devil doesn’t stop us from going to Bible class or worship services when it’s convenient to us. Nor does he shake when we obey the gospel as he knows we won’t grow in our faith. Just as long as we’ll shrug at the pearly gates when asked if we belong.
Bible #commitment #belonging
-
 @ 4ba8e86d:89d32de4
2024-10-17 22:26:20
@ 4ba8e86d:89d32de4
2024-10-17 22:26:20Ele oferece a opção de utilizar autenticação de dois fatores para aumentar ainda mais a segurança. O aplicativo foi desenvolvido em 2016 pelo americano Mo Bitar para oferecer um lugar seguro para armazenar informações pessoais sem a preocupação de que seus dados sejam coletados ou expostos a terceiros.
O Standard Notes é um cofre de aço para seus dados mais confidenciais, que protege suas anotações e arquivos com criptografia de ponta a ponta líder do setor e auditada 4x. Armazene com segurança todos os seus dados confidenciais em um só lugar e acesse-os de todos os seus dispositivos, com a certeza de que seus dados estarão sempre protegidos pelos mais altos padrões de segurança.
Ao contrário de outros serviços de anotações, o Standard Notes apresenta medidas de segurança avançadas e controles de privacidade que protegem seus dados contra hacks, violações de dados, acesso do governo e até mesmo acesso de funcionários. Ele defende a privacidade dos usuários e apresenta políticas revisadas por pares e auditáveis.
O Standard Notes utiliza criptografia de ponta a ponta para proteger todos os dados, que são criptografados sempre que tocam um disco, como em seus servidores ou no dispositivo do usuário. Auditorias independentes são realizadas periodicamente em sua criptografia, aplicativo e código do servidor para garantir que os dados estejam protegidos. O código aberto do Standard Notes permite que os usuários tenham clareza sobre como seus dados estão sendo tratados em cada etapa do caminho. Ele não coleta ou armazena informações do usuário, como endereço IP ou agente do usuário, para proteger a privacidade.
-
Acesse a F-droid ou Google Play Store em seu dispositivo Android.
-
siga as instruções para criar uma conta ou fazer login em uma conta existente.
-
Comece a criar suas notas e armazenar outras informações importantes com a tranquilidade de que seus dados estão seguros e protegidos.
https://github.com/standardnotes
-
-
 @ 4ba8e86d:89d32de4
2024-10-17 22:21:39
@ 4ba8e86d:89d32de4
2024-10-17 22:21:39Ele é baseado no conceito de "separação de privilégios", o que significa que ele separa o sistema operacional em duas máquinas virtuais separadas, uma para o sistema operacional e outra para as aplicações. Isso permite que as aplicações rodem em um ambiente isolado e seguro, sem acesso direto à rede e aos recursos do sistema, protegendo assim a privacidade do usuário.
O Whonix foi lançado em 2012 como uma iniciativa do desenvolvedor alemão Patrick Schleizer. Ele criou o Whonix como uma resposta à crescente preocupação com a privacidade e o anonimato on-line, especialmente após as revelações de Edward Snowden sobre a vigilância em massa realizada pela NSA.
O Whonix foi projetado para ser usado em conjunto com a rede Tor, que é uma rede de comunicação anônima que permite que os usuários naveguem na internet sem revelar sua localização ou identidade. O Whonix permite que os usuários se conectem à rede Tor de forma segura e anônima, sem expor seu endereço IP ou outras informações pessoais.
O Whonix funciona em duas partes: o Gateway e o Workstation. O Gateway é a máquina virtual que lida com todo o tráfego de rede e estabelece a conexão com a rede Tor. O Workstation é a máquina virtual que você usa para suas atividades online. As duas máquinas virtuais se comunicam apenas através de uma rede privada, o que garante que o tráfego da rede esteja completamente isolado.
O Whonix vem pré-configurado com várias ferramentas de privacidade e segurança, como o navegador Tor, o cliente de email Thunderbird com suporte a criptografia, a suíte de criptografia GnuPG, entre outras. Além disso, ele possui uma série de recursos de segurança, como proteção contra vazamentos de DNS, capacidade de rotear todo o tráfego através da rede Tor, bloqueio de conexões não autorizadas, entre outros.
O Whonix resolve o problema de privacidade e segurança online, fornecendo um ambiente totalmente isolado e anônimo para navegar na web, enviar emails, trocar mensagens instantâneas e outras atividades online. Ele também ajuda a proteger os dados pessoais do usuário de roubo de identidade e outras ameaças de segurança.
Além disso, o Whonix é uma ótima opção para quem vive ou trabalha em países com censura na internet, já que a rede Tor é capaz de contornar bloqueios de conteúdo e oferecer acesso à internet de forma anônima e segura.
O Whonix é uma solução completa para quem busca privacidade e segurança online. Ele oferece um ambiente totalmente isolado e anônimo para todas as atividades online, garantindo a proteção dos dados pessoais e a privacidade do usuário. Com uma série de recursos de segurança e ferramentas pré-configuradas, o Whonix é uma ótima opção para quem deseja navegar na web com privacidade e segurança, independentemente de onde estejam.
https://github.com/Whonix
https://www.whonix.org/
-
 @ 4ba8e86d:89d32de4
2024-10-17 22:16:21
@ 4ba8e86d:89d32de4
2024-10-17 22:16:21Ele utiliza criptografia forte para criptografar os arquivos antes de serem enviados para a nuvem, garantindo que apenas o proprietário dos arquivos tenha acesso a eles.
O Cryptomator é gratuito para uso em sistemas operacionais como Windows, macOS e Linux, mas requer uma licença paga para uso em iOS e Android. A licença pode ser adquirida por meio do ProxyStore https://digitalgoods.proxysto.re/en , que aceita pagamentos em Bitcoin e moedas fiduciárias.
Desenvolvido por Tobias Hagemann e Christian Schmickler, dois engenheiros de software alemães, o Cryptomator surgiu com o objetivo de criar uma solução acessível e fácil de usar para proteger arquivos armazenados na nuvem. Lançado pela primeira vez em 2016, rapidamente ganhou popularidade na comunidade de privacidade e segurança cibernética.
O Cryptomator é uma ferramenta simples para autodefesa digital. Ele permite que você proteja seus dados na nuvem sozinho e de forma independente.
A maioria dos provedores de nuvem criptografa dados apenas durante a transmissão ou mantém as chaves para descriptografia para si. Essas chaves podem ser roubadas, copiadas ou mal utilizadas. Graças ao Cryptomator, só você tem a chave dos seus dados em mãos.
O Cryptomator permite que você acesse seus arquivos de todos os seus dispositivos. É fácil de usar e se integra perfeitamente entre seus dados e a nuvem.
Como o Cryptomator protege seus dados?
A tecnologia do Cryptomator atende aos padrões mais recentes e criptografa arquivos e nomes de arquivos com AES e comprimento de chave de 256 bits.
Para começar com o Cryptomator, você atribui uma senha para uma pasta - nós a chamamos de cofre - dentro de sua nuvem. Isso é tudo. Nenhuma criação de chave complicada, nenhum registro, nenhuma configuração!
Para acessar o cofre, basta digitar a senha novamente. Você receberá uma unidade virtual criptografada para a qual poderá mover seus dados - exatamente como uma unidade flash USB. Sempre que você armazena algo nesta unidade, o Cryptomator criptografa os dados automaticamente. Bem simples, certo?
A tecnologia por trás disso é de última geração e criptografa arquivos e nomes de arquivos com AES e comprimento de chave de 256 bits. Isso significa: se alguém examinar a pasta em sua nuvem, não poderá tirar nenhuma conclusão sobre seus dados.
Você não precisa confiar cegamente no Cryptomator, porque é um software de código aberto . Para você como usuário, isso significa que todos podem ver o código.
Auditado por pesquisadores de segurança
Além de auditorias de segurança independentes , o software é continuamente e publicamente testado de forma automatizada e possui uma qualidade de código mensurável e cobertura de teste muito acima da média do setor.
O Cryptomator é uma poderosa adição ao seu arsenal de segurança, fornecendo uma camada adicional de proteção aos seus arquivos armazenados na nuvem. Ao combiná-lo com boas práticas de segurança cibernética, você pode desfrutar de maior tranquilidade e controle sobre seus dados pessoais e confidenciais.
O Cryptomator é uma solução confiável e acessível para proteger seus arquivos na nuvem. Com sua criptografia forte, código aberto e facilidade de uso, ele permite que você mantenha a posse exclusiva de suas informações, garantindo que apenas você tenha acesso aos seus arquivos. Ao adotar medidas adicionais de segurança e escolher cuidadosamente seu provedor de armazenamento em nuvem, você pode fortalecer ainda mais sua postura de segurança cibernética e proteger seus dados de maneira eficaz.
https://cryptomator.org/
https://github.com/cryptomator/cryptomator
-
 @ aedd8f68:296cf1be
2024-10-17 21:21:42
@ aedd8f68:296cf1be
2024-10-17 21:21:42Note: This is not some fancy writing piece. this is just brain farting that I thought it was too long for a regular post.
Alex Gleason is always doing a lot of crazy interesting work. Ditto is a step in the right direction for an alternate type of relay ecosystem that runs alongside the standard globally focused community we all know.
While #Ditto is awesome, what I'd really like to see something similar, but more focused on a multi-community experience that simultaneously makes each community's viewing experience focused only on that community's content. Just for fun, to write down some ideas, below are the 2 big changes that I think would make ditto the ultimate "communities" system that could trounce Reddit.
1. Single relay experience on the domain:
By default, I think community sites should only show content from the built in relay (or a relay group for redundancy). Currently on ditto.pub, when you first sign in, it feels a lot like any other web nostr client. The default home just shows follows I have from other relays instead of being thrown into the community content. You have to click the local feed, to filter the community's content, but it's limited to people who registered a NIP-05 for that domain. I think that it would be great if you could contribute with any NIP-05 and it counts as community content. That could be accomplished by equate community content to content posted on the relay. There are countless apps to get a feed of your relays, so it doesn't benefit me to see it on a communty's domain.
2. Sister client giving multi-community aggregation experience:
I think communities should like pokemon and you grab the ones to identify with. Create a set of web and mobile app clients that manage viewing and switching single relays at a time. The client experience would be like reddit where you navigate ditto communities like subreddits. If a community is a pokemon, then this is the pokedex? OK I actually don't know shit about pokemon so that might not be the slam dunk I thought it was. Whoops.
Ideas / more particulars
- To see a community's content, you add a community relay subscribing to subreddit, or simply visit the domain.
- Another great feature would be customizing the relays that make up your home feed, and making other named combo-feeds (especially awesome if you are a part of 2 rival communities who's focus generally overlap)
- The client would use more globally used relays to handle settings like your list followed ditto communities, etc (configurable)
- Similarly, to help users find communities, ditto servers can optionally publish their relay info to a list on a "discovery" relay. Main popular discovery relays would be set by default (where communities publish discovery info to), but could be configured to other relays (if people wanted to set up custom curation relays or something.)
- Registering a domain handle (NIP-05) at the community domain can be more focused on people with relay moderation roles, or just people who really for some reason want that community to be their whole identity (i don't personally get that, which is why mastodon is not for me)
- Communities could work independently of the aggregator app(s) If people just wanted to visit the domain to post (from any NIP-05)
-
 @ b6424601:a11e4ff4
2024-10-17 21:05:15
@ b6424601:a11e4ff4
2024-10-17 21:05:15The Somali pirates wanted a single Bitcoin in a ransomware attack on my company's server back when a Bitcoin was $500 bucks. Our IT guy said he could not do anything, so I first had to figure out how to buy a Bitcoin by listening to a Modern Survival Podcast I listened to on dog walks to learn about permaculture and homesteading ideas for our lake house. So, I bought a Bitcoin in a Satoshi paper wallet and learned enough how to exchange Fiat and send BTC to pay off the pirates. I remember my wife asking if I had purchased 2 of them; of course, the answer was NO.
Fast forward to April 2021, when the BTC had run up to the mid-$50Ks. The paper wallet in my desk drawer kept calling out to me, and I wondered if there was any change from my single Bitcoin pirate payoff. After figuring out I needed the Wallet of Satoshi application on my phone, I shot the QR code. To my amazement, the change from a 2015 Bitcoin was worth a few thousand dollars. At that point, I became very interested and started down the traditional rabbit hole, listening to the entire Michael Saylor/ Breedlove What is Money series, other random crypto podcasts, and YouTube crypto videos. I tried to figure out what the best practices were for this stuff and ended up keeping a diversified portfolio of 80% Bitcoin and 20% shitcoins. By the end of 2021, I made a big bet with Bitcoin and other shit coins with my end-of-the-year bonus to attempt to get a bump to pay for the world's coolest dock at our lake house. We are going to $100K for sure, RIGHT?
With full-on FOMO and greed at the party, 2022 was very educational in a living through-your-mistakes kind of way. I had to start selling assets as draws occurred on the dock construction. I had learned each trade was a taxable event to report on taxes late in 2021. As the payment requests were coming in from my Dock Contractor, I was selling TSLA gains (different dock story) and BTC to balance out gains. I was pissed at the time, but I was selling on the way down first, starting with the shitcoins after observing how fast they were cratering. I observed the bears jumping on BTC at a slower rate, from $50K at the beginning of January to $25K at the beginning of June 2022.
The results and my BTC progression:
The dock is our favorite place and an asset to our lives worthy of trading some hard assets. I was thankful I did not leverage for the "certain" run-up and had assets to trade to my dock personal architecture.
During the bear market in 2022, I realized that I was a good architect but a lousy trader. It seems easier to use DCA and HODL to reduce the time and effort of figuring out which shiny object to speculate on.
In 2022, I learned there is at least one benefit to being older, especially if you are over 59.5. I worked with our office's 401K administrator to modify our plan to allow in-service Roth rollovers. 59.5+ year olds can also roll over Traditional IRAs. I even sold some Google shares from the original Dutch Auction to roll into a BTC IRA account.
In 2023, we worked with our business tax accountants and attorney to revise our business partnership agreement and corporate structure to allow the partner's autonomy to decide where to hold firm equity. I could retain our studio profit in a business account. My studio's equity has now been moved from a bank business account to a business BTC account without causing a capital gain tax event.
In 2024, our business is working to figure out how to use this stuff to behold a corporate treasury. We have been working with Jon Gordon at Satoshi Health Advisors to set up Bitcoin systems to receive and make payments. We are paying for those consulting services with lighting through business accounts. This sounds like a small step, but involves jumping through some flaming hoops for a small business.
2025, my goals are to start receiving initial payments, consultation payments, and selling a product on our website in Lighting or BTC. I want to use experience for clients sending us initial project payments to let them see the utility, lower cost, and ease of network use. I see these small initial moves as stepping stones toward using BTC as our unit of account.
For the first time in my business life, there is a simple pattern to follow: do the work we believe in and our clients value, design your business systems to make a profit, and then retain profits in BTC accounts. We are not a public company, so the MicroStrategy convertible bond strategy won't work for us. However, for small business owners in the design and building industry, holding BTC on your balance sheet should make us stronger and more resilient as assets shift from real estate and bonds to BTC. The next steps could be self-actualizing.
HODL on
Bryan
-
 @ 76c3384a:9279a6e5
2024-10-17 19:38:33
@ 76c3384a:9279a6e5
2024-10-17 19:38:33
-
"I want to learn to read and write mommy."
I designed this workbook for my eldest when she was 5 years old. She came to me one day asking me, "Mommy, I want to learn to read and write."
The first book I designed (the one she used) was done by hand with pencil and paper. I wanted to digitize the worksheets for my other children to print and reuse, but at the time I had no experience with digital design. Since I was a Linux user I used Libre Office and Inkscape. Learning on the go eventually publishing 4 workbooks and 1 basic reader all crafted with open source software. At first workbooks were only available in Afrikaans, but I had many requests to also publish them in English and now all of my material is available in English and Afrikaans.

-
Since 2024 my digital books are available for free (no strings attached) for anyone to use, they have also been updated and revamped to be Bitcoin-friendly. All I ask is that you refer to my website or Nostr account when sharing.
I am not a teacher and have no degree or diploma in education. Just a mom that had difficulty finding classical education workbooks to help my daughter learn to read and write. I took it upon myself to design something that worked for us.
I hope you find this helpful. Enjoy, and follow me on Nostr.
About this workbook
An educational exercise book teaching children to read and write during the foundation phase. “Look mommy, I can read and write” is for home and classroom use. It can be used as an extra aid for Grade R or Grade 1 curriculum or as a revision book.
Each exercise was drafted by hand and then digitized. The letters had to be as similar to hand written symbols as possible. It was well researched. Due to the fact that all is in black and white, the children can be more creative by using colour pencils and crayons.
The first letter is the letter “a”, then follows the letter “d”. By doing just the first two letter exercises the child will already be able to sound (read) the word “dad”. Each letter consists of three exercises.

-
There are many pictures to colour, sentence and word building exercises.
This book is particularly ideal for parents who want to play an active role in this phase of their child’s development and education. It will also give satisfaction to the parent that wants to teach his/her own child to read and write by working together in the book.
It is a great homework aid for teachers to send home for extra repetition.
(The character style and writing symbols may differ depending on the country you live in.)
DOWNLOAD PDF HERE!
-

-
Written, designed and cover by SemcoMama
semcomama.co.za / semcomama.npub.pro
© All rights reserved. Feel free to share with all mommies out there and you can also follow me on Nostr @semcomama. If you appreciate my work and found value in it zap me some sats. (through my website or my Nostr account).
education
-
 @ ebdee929:513adbad
2024-10-17 17:09:57
@ ebdee929:513adbad
2024-10-17 17:09:57Software Setup Links:
DC-1 as a monitor:
- SuperDisplay Setup | Best for Windows
- SpaceDesk Wireless and Wired Display Setup | Windows PC Users
- Chrome Remote Desktop Setup | Anyone
Purchase and setup links:
Keyboards:
- Keys-To-Go 2 White Keyboard | Logitech
- Keys-To-Go 2 Bluetooth Setup
- Magic Keyboard White | Apple through Amazon.com
- Magic Keyboard Bluetooth Setup
- Air 60 V2 with Blue Switches | Nuphy
- Air 60 V2 Keyboard Folio | Nuphy
- Air 60 V2 Bluetooth and Folio Setup
- Magic Keyboard Case | Fintie through Amazon.com
Pens:
- Premium White Pen
- Ultra Premium Lamy Pen | Amazon.com
- Samsung S Pens (Multiple):
- Small (Galaxy Note Series Style)
- Cheaper Alternative (ZERO Quality Guarantees)
- Medium (Galaxy Fold Style with smooth tip)
- Cheaper Alternative (ZERO Quality Guarantees)
- Larger (Galaxy Tab Style)
- Cheaper Alternative (ZERO Quality Guarantees)
Pen Setup: Just touch the screen and it works, no pairing or charging needed.
Others:
- Bluelight Free Light Bulb | Amazon.com
- Light Bulb Setup
- Comfy Green Sleeve | Amazon.com
Keys-To-Go 2 Bluetooth Setup:
- Step 1: Unbox keyboard from box
- Step 2: Open keyboard and pull tab to enable batteries and keyboard function
- Step 3: Ensure Switch on back of product is in the position where green is showing, not off where red is showing
- Step 4: Hold the key labeled ‘fn’ meanwhile you hold the ‘g’ key for 3 seconds to put the keyboard into android mode, since this is an android tablet
- Step 5: Hold the key labeled ‘fn’ meanwhile you hold the key labeled ‘F1 with the image of the laptop and phone for 3 seconds to put profile 1 into bluetooth pairing mode
- Step 6: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 7: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 8: Click on the button labeled ‘Pair new device’
- Step 9: Under available devices tap on Keys-To-Go 2
- Step 10: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 11: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Appendix: Keys-To-Go 2 Documentation:
Apple Magic Keyboard Setup:
- Step 1: Unbox keyboard from box
- Step 2: Ensure Switch on back of product is in the position where green is showing
- Step 3: On your Daylight DC-1, swipe down on the top of the screen, swipe down again, click on the settings icon that looks like a gear in the bottom right corner
- Step 4: In settings, click the second from the top menu item on the left called ‘Connected devices’ (it says Bluetooth, pairing underneath it)
- Step 5: Click on the button labeled ‘Pair new device’
- Step 6: Under available devices tap on Magic Keyboard
- Step 7: It will ask you to type some numbers and hit return/ enter, once you do so the device will show up as connected under ‘Saved Devices’
- Step 8: Turn off the keyboard with the switch on the back if you desire, this will disconnect it from the device
Spacedesk Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SpaceDesk: In the Google Play Store, tap on the search bar at the top and type "SpaceDesk". As you type, suggestions will appear below the search bar. Tap on "SpaceDesk - USB Display for PC" when it appears.
- Step 3: Download and Install the Driver: Visit the
official Spacedesk website and download
the ‘Windows 10/11 (64-bit)’ Spacedesk driver for Windows. Follow the on-screen instructions to install it on your PC. - Step 4: Launch Spacedesk Server: After installation, open the Spacedesk Driver Console application on your Windows PC.
- Step 5: Click the ‘USB Cable Driver Android’ button, then enable the ‘USB Cable Android’ option and let it apply.
- Step 6: Open Spacedesk App: On your Android device, open the Spacedesk app you installed earlier. - Step 7: Improve Quality: Click on the ‘3 lines’ icon and then settings.
- Under ‘Rotation’ enable ‘Auto-Rotation’ and under ‘Quality/Performance’ slide ‘Image Quality’ to max (the right) and set ‘Custom FPS Rate’ to 60. - Step 7A (for wired use): Plug the tablet into your PC - Step 7B (for wired use): Enable USB File Transfer: Swipe down on status bar (the bar at the top of the screen with wifi and notification icons etc. There will be a notification under the ‘Silent’ category named ‘Charging this device via USB’, tap on it to expand it, then tap once more time when it says ‘Tap for more options’. This will open up a menu, all you need to do is click ‘File Transfer’ under the section called ‘Use USB for’ - Step 8: Connect: Reopen the Spacedesk app (use the back arrow or button to leave the settings menu should you need). The app should now detect your Windows PC through USB OR wireless. Tap the listing under your computer's name for wireless connection, or tap the little trident USB icon at the bottom middle of the screen for wired connection, which is recommended.
SuperDisplay Setup:
THIS IS ONLY FOR PEOPLE USING A WINDOWS PC
- Step 1: Open the Google Play Store on the tablet: On your device, slide in from the side until and move till you get to the letter ‘P’ and tap ‘Play Store’
- Step 2: Search for SuperDisplay: In the Google Play Store, tap on the search bar at the top and type "SuperDisplay". As you type, suggestions will appear below the search bar. Tap on "SuperDisplay - Virtual Monitor" when it appears.
- Step 3: Download and Install the Driver on your Windows PC: Visit the
official SuperDisplay website and download
the Windows driver. Follow the on-screen instructions to install it on your PC. - Step 4: Launch SuperDisplay : After installation, open the SuperDisplay Settings application on your Windows PC by hitting the ‘Windows’ Key and typing ‘SuperDisplay Settings’ - Step 5: Launch the application on your tablet. - Step 6: Go into SuperDisplay settings by clicking the settings gear icon in the top right corner. Under ‘Advanced settings’ click ‘Quality’ and slide it to 100. - Step 7 (Wireless): IP Address: Back out of the settings and input the IP address into the desktop program. (Both devices need to be on the same wifi) - Step 7 (Wired): Plug the tablet into the PC - Step 8: Start the connection on the tablet by clicking the central button! - Step 9: In Windows, hit the ‘Windows’ key, type display and hit enter. This will take you to display settings. In display settings set the displays to ‘extend’ and then confirm the change. Select the DC-1 display by clicking the square it is associated with, then set the display to 1584 x 1184 resolution, confirm this by hitting ‘keep changes’, then set to 125% scale.
Chrome Remote Desktop Setup:
Note: This prefers Chrome itself on the tablet and REQUIRES a chromium based browser to be installed on your computer, examples of chromium based browsers are Chrome, Edge, Arc, Opera etc. Basically anything but Safari or Firefox will do. This is because a chrome extension needs to be installed. Both devices need to be signed in to the same Google account to see each other.
- Step 1:
and click the download button here:
- Step 2: Get the extension in the window that pops up:
- Step 3: Once installed, click the download button AGAIN and it will show what is shown below, a program called ‘chromeremotedesktophost’ will download, install it.
- Step 4: In the play store, install the ‘Chrome Remote Desktop’ app and open it, the app's name will be just ‘remote desktop’ as a heads up. - Step 5: On the computer, go to
and click set up remote access under the ‘Remote Access’ tab. Then set a computer name and pin. Accept whatever permissions pop up on your computer
- Step 6: If you have Chrome itself installed on the tablet it will open a page, click the ‘Access my computer’ button, then under remote Access click your device.
APK Installation Guide:
- Note on APK’s: These are apps from outside official sources, they might not update from the play store and in rare cases can have different functionality. Apply extra caution and source these app files from good sources like
. Just like through the play store or other sources, malicious files can be spread, use common sense and generally avoid downloading any ‘hack’ apps that claim to unlock features. - Step 1: One the home screen, swipe down from the top of the screen, also called the status bar - Step 2: Swipe down again till the settings tiles fill the screen, then click the gear icon in the bottom right hand corner of the screen which will take you to the settings application - Step 3: In settings, tap ‘Apps’, then ‘Special app access’, then ‘Install unknown apps’ - Step 4: Tap your preferred browser application then enable the ‘Allow from this source’ toggle - Step 5: Open your browser of choice, and search ‘apkmirror’ and navigate to
, or just type
https://apkmirror.com/ - Step 6: On the apkmirror website, search your application name in the search bat at the top of the apkmirror website. After you search find your app in the results and tap the most recent version. Dismiss any ads you might see. - Step 7: Under the text ‘Verified safe to install (read more)’ tap the button called ‘SCROLL TO AVAILABLE DOWNLOADS’ - Step 8: Find a file tagged ‘APK’ not ‘BUNDLE’ - Step 9: Click on the Download Arrow and line icon that looks like this ⬇️ - Step 10: Under ‘Verified safe to install (read more)’ tap ‘DOWNLOAD APK’ - Step 11: If it appears, dismiss the warning for ‘File might be harmful’ by tapping ‘Download anyway’ - Step 12: After your apk downloads, either - Tap ‘Open’ on the ‘File Download’ Pop-Up - Go to the home screen and open the files app, navigate to the downloads folder and tap on the downloaded apk - Step 13: Tap ‘INSTALL’ on the popup that appears. After it installs tap ‘OPEN’ - Step 14: The app will now be on your device and you can search and open it like every other app
Touch grass,
Daylight Team
-
 @ bcea2b98:7ccef3c9
2024-10-17 17:02:57
@ bcea2b98:7ccef3c9
2024-10-17 17:02:57originally posted at https://stacker.news/items/728382
-
 @ 599f67f7:21fb3ea9
2024-10-17 15:35:19
@ 599f67f7:21fb3ea9
2024-10-17 15:35:19Nostr proxy baten erabilera modu oso eraginkorra da internet banda-zabaleraren eta mugikorretan bateriaren kontsumoa optimizatzeko.
Proxy batek hainbat errelei-konexio konexio bakarrean biltzen dituenez, baliabideen erabilera nabarmen murrizten du, eta erabiltzailearen IP helbidea ezkutatuz pribatutasun-geruza bat gehitzen du.
Hona hemen nola funtzionatzen duen eta nola konfigura daitekeen:
Nola funtzionatzen du?
Nostr proxy batek hainbat erreleirekin konektatzen du. Errele horietara gertaerak eskuratu eta argitaratzen ditu. Bezeroaren aplikazioak WebSocket konexio bakarra ireki behar du proxy-ra, eta horren bidez proxy-ak konektatuta dituen errele guztiak eskuragarri izango ditu.

Irudiaren egiletza: Yonle 2023
Bezeroak konexio bakarra irekitzen duenez, datuak eta bateria aurrezten ditu.
Proxy-ak bezeroaren izenean erreleekin konektatzen denez, erreleek proxy-aren IP helbidea ikusten dute, eta ez bezeroarena. (Hala ere, proxy hornitzailearengan konfiantza izan behar duzu).
Erabiltzeko Modua
Nostr proxy bat erraz auto-ostata daiteke. Auto-ostatatzeko jarraibideak lortzeko, begiratu nostr:npub1x3azxuysp5vmfer4vgs4jn5tmfcx4ew8sh0qnev7gczljxsr7jwqa3g4el erabiltzailearen biltegi hau.
Auto-ostatzeko baliabiderik ez dutenentzat, Bitcoin Txoko-k komunitate-instantzia bat ostalaratzen du.
Erabiltzeko, gehitu besterik ez duzu:
wss://bostr.bitcointxoko.comzure errele zerrendara.
Orain ez duzunez zuzeneko konexioak behar, errele bikoiztuak ezabatu ditzakezu.
Ikusiko dugu elkar Nostr-en!
-
 @ bcea2b98:7ccef3c9
2024-10-17 14:47:01
@ bcea2b98:7ccef3c9
2024-10-17 14:47:01Sometimes you have to take risks to grow. What's the biggest risk you've ever taken that ended up paying off.
My biggest risk that paid off was moving to another country and starting a new life 10 years ago due to corruption and torture in my home country.
originally posted at https://stacker.news/items/728159
-
 @ c0f9e286:5a223917
2024-10-17 14:09:46
@ c0f9e286:5a223917
2024-10-17 14:09:46หัวใจของธุรกิจเครือข่ายที่ทำให้คนๆหนึ่งมีรายได้หลักแสน หลักล้านคุณคิดว่าคืออะไร?? ปริมาณสินค้าที่ขายได้ หรือที่จริงแล้วคือจำนวนคนที่ทำงานภายใต้สายงานของคุณกันแน่
คำตอบคือ คนใต้สายงานคุณนั่นแหละ ที่คุณต้องเสียเวลาปั้นให้เขาเป็นทีมของคุณ และไปหาคนใหม่ๆเข้ามา เพื่อขยายทีมให้ใหญ่เป็น Snowball Effect ไปเรื่อยๆ แล้วคนที่อยู่ด้านบนสุดของเครือข่ายก็จะได้ประโยชน์ไล่ลงไปเป็นลำดับชั้น ธุรกิจเครือข่ายบอกคุณว่านั่นแหละคือ Assets ก็คือคนข้างล่างเปรียบเสมือนเครื่องจักรมนุษย์ที่คอยทำงานให้คุณตลอดเวลา
ปัญหาคือ Assets ชนิดนี้มี Counter Party Risk ที่เป็นความเสี่ยงสูงสุด นั่นคือตัวบริษัทเครือข่ายนั้นๆ แม่ทีมส่วนใหญ่มักจะพยายามเข้าหาประธานบริษัท หรือผู้บริหารเพื่อให้ตัวเองเปรียบเสมือนคนสำคัญ และคาบข่าวมาบอกสายงานของตัวเองก่อนสายงานของคนอื่นเสมอ เพื่อปั่นยอด ปลุกไฟ หรืออะไรก็แล้วแต่ในทำนองนี้ แต่… แต่ตัวโตๆว่า แม่ทีมนั้นไม่ได้มีผลต่อการตัดสินใจในการควบคุมทิศทางองค์กรเลยแม้แต่น้อย คนที่ควบคุมทิศทางองค์กรก็คือผู้บริหาร
ทุกครั้งที่ธุรกิจเครือข่ายเพิ่งเริ่มก่อตั้ง มันมักจะมากับโปรลดแลกแจกแถม เพื่อให้แม่ทีมไปดึงดูดคนเข้ามา เมื่อทำไปซักพักบริษัทเห็นว่ายอดขายโตขึ้น มันก็จะออกกฎเกณฑ์เพิ่มเพื่อให้บริษัทจ่ายน้อยลง หรืออย่าง The Icon พอไปตรวจโกดังก็ไม่มีของเอาดื้อๆ แปลว่าในฐานะที่เป็นแม่ทีม คุณกำลังเอาเครดิตและชื่อเสียงตัวเองไปแลกกับลมปากของคนที่พร้อมเปลี่ยนได้เสมอ ไม่ว่าจะตั้งใจหรือไม่ก็ตาม เพราะบางบริษัทลืมคำนวณว่าเวลาทีมใหญ่ขึ้น มันต้องจ่ายค่าการตลาดหนักกว่าเดิม
เมื่อถึงเวลาบริษัทเครือข่ายไปไม่ไหว ล้มครืน พังทะลายต่อหน้าต่อตา ใครเป็นคนรับความเสี่ยงมากที่สุด??? ก็แม่ทีมนั่นแหละ เนื้อไม่ได้กิน หนังไม่ได้รองนั่ง เพราะเงินส่วนใหญ่เจ้าของบริษัทกอบโกยไปหมดแล้ว ส่วนลูกทีมจากเดิมที่เป็น Assets ที่มีค่า ก็จะแปรเปลี่ยนเป็นเจ้าหนี้ที่พร้อมขย้ำคุณได้ทุกเมื่อ
แน่นอนว่าบริษัทขายตรง ธุรกิจเครือข่ายดีๆก็มีไม่น้อย แต่ก็ไม่ได้การันตีว่าในอนาคตบริษัทเหล่านี้จะไม่เปลี่ยนแปลงนโยบาย นั่นแปลว่าคุณมีความเสี่ยงตลอดเวลาจากการต้องเชื่อใจเจ้าของบริษัทที่สามารถทรยศคุณได้ทุกเมื่อ
ดังนั้นหากมองในทฤษฎีเกม ความตั้งใจที่จะเป็นแม่ทีมนั้นไม่ใช่ความคิดที่ดีเลย เพราะได้ก็ได้แค่ค่าคอมมิชชัน แต่เวลาเสียคุณจะโดนลูกทีมรุมทึ้ง พร้อมทั้งกฎหมายทางอาญาที่มีโทษมหาศาล ส่วนเงินกำไร เจ้าของบริษัทฟาดเรียบ ดีไม่ดีเขาวางแผนผ่องถ่ายเงินให้ออกจากระบบหมดแต่แรกแล้ว
มีลูก มีหลาน ถ้าเขาอยากทำธุรกิจเครือข่าย เอาบทความนี้ให้อ่าน ผมไม่อยากเห็นใครบาดเจ็บจากเรื่องแบบนี้โดยรู้เท่าไม่ถึงการณ์
-
 @ 7ab1ed7a:f8e15275
2024-10-17 14:06:46
@ 7ab1ed7a:f8e15275
2024-10-17 14:06:46I'm proud and thankful to announce that funding has been granted by OpenSats to fund the development of the Nostr library for Arduino.
The fund will help with work on the development of the Arduino Nostr library as well as fund work on IoT related NIPs.
-
 @ 7ab1ed7a:f8e15275
2024-10-17 12:05:00
@ 7ab1ed7a:f8e15275
2024-10-17 12:05:00I've started building an IoT DVM simulator. It's written in TS and uses Deno for simplicity.
The project will be used to test the ideas in and support the NIP 90 PR.
https://github.com/blackcoffeexbt/nostriot-dvm-simulator
It has a basic plugin architecture so we can test a whole suite of how different IoT commands can work easily (config, intents, sensors, all the things).
This is the current, very basic roadmap for this project:
-
[ ] Announce capabilities via NIP 89
-
[ ] Respond to DVM job requests
-
[ ] Accept payments for DVM job requests
I'll also be working on a basic - for now - IoT DVM client that can be used to interact with IoT DVMs.
-
-
 @ 8a4c88dc:a498228e
2024-10-17 11:58:21
@ 8a4c88dc:a498228e
2024-10-17 11:58:21“Hello everyone”
มันแปลกดีนะที่ได้ยินเสียงของตัวเอง…ขอบคุณทุก ๆ คนที่เข้ามาฟังกันนะครับ ผมรู้ว่าเซสชั่นนี้ชื่อ The Rite of passage แต่นั้นเดี๋ยวผมจะยกไปพูดตอนท้าย ๆ เพราะว่าสิ่งที่ผมอยากจะพูดถึงก่อนเลยคือ
อะไรกันที่เป็นคำนิยามของเหล่า “บิตคอยเนอร์?”

สองปีก่อน ผมได้ออกเดินทางไปทั่วสหรัฐฯพลางถามคำถามดังกล่าวกับตนเอง ออกเดินทางไป เข้า Bitcoin Meetup ไปกว่า 30 งาน แล้วสิ่งที่ผมสนใจคือ
การเป็นบิตคอยเนอร์นั้นมันมีอะไรมากกว่าการถือ บิตคอยน์ อยู่ในมือ
มีผู้คนมากมายที่ทันทีที่พวกเขาเรียนรู้เกี่ยวกับบิตคอยน์แล้วหลงรักมันในพริบตา อะไรกันคือสิ่งที่บรรดาลปาฏิหารณ์นี้ผมได้แต่ครุ่นคิด นั่นทำให้วันนี้ผมจึงอยากจะมาเล่าให้ทุก ๆ คนฟังกันถึงการเดินทางในทริปที่ผมเรียกว่า สามเดือนของการเดินทางแห่ง Bitcoin ที่ผมพานพบด้วยการขี่มอเตอร์ไซต์ข้ามสหรัฐฯ ของผม
ทว่าผมอยากเล่าทุกคน ๆ คนให้ฟังก่อนว่าอะไรกันที่พาผมมาอาศัยอยู่ที่ประเทศไทย

ผมเกิดและโตที่ที่รัฐฟีลาเดเฟียร์ ไปอยู่ที่นิวยอร์คได้เจ็ดปี ก่อนที่เมื่ออายุได้ 29 ผมก็ตัดสินใจบินมาอยู่ไทยเพราะต้องการมองหาชีวิตใหม่ ๆ ซึ่งผมก็คิดนะ ว่าผมเจอมันแล้วที่นี่
ที่ ๆ ผมเรียกได้จากหัวใจว่า บ้าน**
"แล้วก็พูดไทยได้นิดหน่อยนะฮับ ตอนนี้ประเทศไทยเหมือนบ้านของผมแล้วฮะ” (เขายิ้มแล้วพูดเป็นภาษาไทยอย่างยิ้มแย้มจนเรียกเสียงปรบมือจากผู้ฟังที่รู้สึกอบอุ่นหัวใจ ก่อนที่จะกลับมาพูดเป็นอังกฤษ) แต่น่าเสียดายจริง ๆ ที่ผมไม่ได้รู้ศัพท์ไทยเยอะนัก เลยจะขอพูดต่อเป็นภาษาอังกฤษต่อแทนนะ
เมื่อปี 2020 ในระหว่างที่ผมต้องกักตัวอยู่บ้านเนื่องจากโรคระบาด ผมได้ไหลลงหลุมกระต่าย Bitcoin ไป หลังจากนั้นผมก็อยู่แต่ในทวิตเตอร์เพื่อพบเพื่อน ๆ บิตคอยเนอร์ด้วยกันในนั้น
ทำให้ในปี 2022 ผมจึงตัดสินใจกลับไปเยี่ยมประเทศบ้านเกิดอีกครั้ง เพื่อไป Bitcoin Meetup และกระทบไหล่กับเพื่อน ๆ บิตคอยเนอร์ที่รู้จักกันในทวิตเตอร์มาตลอดสองปีที่ผ่านมา ซึ่งผมได้เลือกยานพาหนะคู่ใจในทริปนี้ที่มีอิสระเสรีที่สุด มอเตอร์ไซต์ เป็นมอเตอร์ไต์คันเดียวกับโมเดลจำลองที่ภรรยาผมซื้อให้ มันตั้งอยู่บนโต๊ะผมอยู่เป็นปี ๆ กว่าผมจะสามารถซื้อของจริงและพามันออกเดินทางไปในทริปนี้ได้
แล้วผมก็ได้ขี่ไปกว่าสองหมื่นกิโลเมตร กินเวลากว่าร้อยวัน ได้ไป Bitcoin Meetup กว่า 30 ที่และน่าจะได้จับมือกับบิตคอยเนอร์เกินกว่าร้อยคน ก่อนหน้าที่จะไปต่อ ผมอยากบอกก่อนว่าทริปนี้มีแต่เรื่องเกี่ยวกับบิตคอยน์เท่านั้น ไม่มีไปงานเหรียญคริปโตอื่น ๆ
ซึ่งเมื่อมองย้อนกลับไป ตอนแรกผมก็ไม่รู้หรอกว่าเหรียญบิตคอยน์กับเหรียญคริปโตอื่น ๆ มันต่างกันยังไงจนปี 2022 ผมถึงได้ตระหนักได้ว่าทั้งสองไม่เหมือนกันเลย ที่ผมอยากจะพูดคือทั้งทัศนคติและมุมมองต่อโลกของคนที่สนใจ เฉพาะบิตคอยน์ นั้นอยู่คนละแม่น้ำกับผู้คนหรือสิ่งที่ผมเจอในงานเหรียญคริปโตอื่น ๆ อย่างสิ้นเชิง
ดังนั้น ให้ผมได้เล่าว่าเหล่าบิตคอยเนอร์มีคุณลักษณะอะไรเหมือน ๆ กันโดยประกอบกับเรื่องราวการเดินทางของผมเพื่อให้ทุกคนเข้าใจว่า
เมื่อผมพูดถึง บิตคอยเนอร์ ผมกำลังหมายถึงอะไร
คุณลักษณะแรกเลยคือบิตคอยเนอร์ให้ความสำคัญกับการ “ทำงานหนัก”และ “ความซื่อสัตย์”

Bitcoiner ให้คุณค่ากับสิ่งที่เรียกว่า Proof of Work ที่เชื่อในการทำงานหนักและความซื่อสัตย์
แล้ว... เจ้าวัวบนจอมันเกี่ยวอะไรกันหละ ถ้าให้เล่าก็ต้องท้าวความกลับไปที่หมุดหมายแรกที่ผมหยุดพัก มันคืองาน Beef Initiative งานแรกในเมือง Kerrville รัฐเท็กซัส ซึ่งเป็นงานที่รวมเหล่าบิตคอยเนอร์ผู้เป็นสายเงินทองและสายเทคทั้งหลายมาเจอกับคนเลี้ยงวัว ซึ่งเกิดมาทั้งชีวิตผมไม่เคยเห็นที่ไหนที่เอาคนสองประเภทนี้มาจัดรวมอยู่ในที่เดียวกันมาก่อน แล้วผมก็ประหลาดใจหนักกว่าเดิมอีกที่เห็นพวกเขาเข้ากันเป็นปี่เป็นขลุ่ย ผมเลยคิดว่ามันต้องเป็นเพราะพวกเขาเชื่อในสิ่งเดียวกันคือ
เมื่อคุณปลอมแปลงบิตคอยน์ไม่ได้ฉันใด วัวก็ปลอมแปลงไม่ได้ฉันนั้น
เพื่อที่จะขุนมัน มันต้องมีที่ซุกหัวนอน คนเลี้ยงต้องตื่นเช้ามาให้อาหารดูแลมันร่ำไป ไม่มีใครเสกวัวให้โตในชั่วข้ามคืนได้ ซึ่งนั่นทำให้ผมตระหนักได้ว่าเหล่าบิตคอยเนอร์ได้นำคอนเซปต์ของ Proof of Work เข้าไปในทุกอณูของชีวิต ซึ่งมันช่างตรงกันข้ามกับสังคมกระแสหลักที่มักให้ค่ากับความฉาบฉวย สิ่งล่อตา หรืออะไรก็ได้ที่ทำให้สารแห่งความสุขนั้นหลั่ง จนกระทั่งสูญสิ้น ซึ่งศรัทธาในตนเอง
คุณลักษณะถัดมาของพวกเขาคือ “ความรับผิดชอบ และรักษาซึ่งอธิปไตยของตนเอง”

พวกเขานั้นชอบที่จะรับผิดชอบชีวิตตัวเองในทุก ๆ ด้าน
ไม่ใช่แต่กับเรื่องเงินทองแต่กับสุขภาพและเรื่องอื่น ๆ ด้วย ผมได้พบเจอบิตคอยเนอร์หลาย ๆ คนที่อาจพูดไดเลยว่าพวกเขาเป็นเจ้าของชีวิตของตนเอง ซึ่งแตกต่างจากผู้คนในสังคมปัจจุบันที่เรามักจะเห็นคนโทษนุ่นนี่ หรือเอาแต่ชี้ไปที่สิ่งต่าง ๆ ว่าเป็นสาเหตุทั้งหมดของปัญหาในชีวิต แต่กับบิตคอยเนอร์นั้นพวกเขาเลือกที่จะเป็นนายชีวิตตน รับผิดชอบทุก ๆ อย่างของตนเองไม่มัวเสียเวลาโทษปี่โทษกลอง
พวกเขามักเริ่มแก้ไขปัญหาจากเรื่องใกล้ตัวที่สุดก่อนเสมอ ซึ่งนั่นก็เป็นอีกหนึ่งสาเหตุของการออกทริปนี้ของผม
เพราะตลอดช่วงปี 2020-21 แห่งโรคระบาด ผมมองเห็นแต่ความหวาดกลัวและสิ้นหวัง มีแค่เวลาที่ผมใช้กับบิตคอยเนอร์ในทวิตเตอร์และที่ Bitcoin Meetup เท่านั้นที่ผมมองเห็นความหวังและความเป็นเหตุเป็นผล พวกเขาเริ่มจากชุมชนของตนเองและคิดเสมอว่า วันนี้ฉันทำอะไรได้บ้าง ให้ชีวิตฉันดีขึ้น ให้ชุมชนของฉันดีขึ้น
แล้ว… เจ้ากองไฟบนจอนี่มีความหมายอะไรอีกหละ? มันเป็นภาพของหนึ่งในช่วงเวลาสุดประทับใจของผม ตอนที่ผมแวะพักในแคมป์ย่างสเต็กแคมป์หนึ่งระหว่างทริปผม ถ้าคุณคุ้นเคยกับงานแบบนี้ ก็คือเราก็จะมีเพื่อนบิตคอยเนอร์คนหนึ่งเป็นเชฟย่างสเต็กโดยมีสหายยืนล้อมร่วมทานสเต็กกันด้วยมือเปล่า ซึ่งที่ผมไปนี่ก็ทานกันไปกว่าเจ็ดคอร์ส แล้วความพิเศษอีกอย่างคือเราตั้งแคมป์กันสามคืนติดโดยไม่มีทั้งไฟฟ้าและสัญญาณมือถือ แค่ตั้งแคมป์และทานสเต็กกันอยู่เช่นนั้น
แล้วกองไฟของแคมป์เราก็ไม่เคยมอดเลยตลอดสามวัน
ตลอดแคมป์ผมไม่เห็นใครซักคนคนที่วานเพื่อนให้ไปหยิบไม้มาเติมที่กองไฟให้เลย พวกเขาแค่นั่งอยู่รอบกองไฟแล้วเห็นว่าฟืนมันเริ่มพร่อง จึงลุกไปหยิบไม้มาเติมกันเองเลยโดยไม่มีใครปริปากไหว้วาน นั่นทำให้ผมเห็นว่าชุมชนบิตคอยเนอร์นั้นมักจะจัดการกันเองภายในได้เป็นอย่างดี
ทุก ๆ คนในชุมชนมีหน้าที่เป็นของตนเอง ซึ่งเป็นอันรู้กันว่าหากเราจะได้รับประสบการณ์แสนวิเศษนี้ มันต้องเป็นเพราะทุก ๆ คนร่วมกันรับผิดชอบเพื่อมัน
และคุณลักษณะสุดท้ายเลยที่ผมอยากพูดถึงเลยคือ “พวกเขามักมีความเป็นผู้ประกอบการและหมั่นใฝ่รู้เสมอ”

บิตคอยเนอร์หลาย ๆ คนมีธุรกิจหรือโปรเจคอะไรซักอย่างเป็นของตนเองเสมอ พวกเขาเริ่มทำโดยไม่รีรอขอใคร ซึ่งผมเห็นพวกเขาโชว์ของกันที่ Bitcoin meetup กันตลอด ๆ
จริง ๆ ผมก็มีตัวอย่างอยู่ในกระเป๋ากางเกงผมอยู่นะ เช่น Bolt Keys ที่ผมถืออยู่นี่ ผมซื้อจากคนที่ออกบูธหน้างานนี้มาหลายอันเลยสำหรับโปรเจค “Rite of Passage” ของผม ซึ่งมันเอาไว้ใช้อนุมัติการโอนธุรกรรม Lightning Network ด้วยการแตะเจ้าเจ้านี่กับโทรศัพท์ที่รองรับ NFC
เอาหละ แล้วมันเกี่ยวอะไรกับทุ่งหญ้าบนหน้าจอผมอีกหละ ที่คุณเห็นอยู่คือบ้านเต็นท์ถาวรที่ผมแวะพักระหว่างการเดินทางของผมในมิชิแกน กับคนนำทริป เขาชื่อคาร์ลซึ่งเป็นเจ้าของที่แห่งนี้ เปิดโฮมสเตย์ และในวันที่ผมไป ที่นี่มีแกะกว่าหกสิบตัวเดินว่อนเลย
หลัก ๆ เลยคือคาร์ลเคยเป็นช่างตัดต่อวีดีโอกลางลอสแองเจลิส แล้วเขาก็หลงใหลสิ่งที่เรียกว่า Permaculture ซึ่งเป็นคอนเซ็ปต์ของการตั้งรกรากและทำเกษตรกรรมเพื่อที่จะสร้างระบบนิเวศสมบูรณ์ที่คุณ สัตว์ และธรรมชาติอยู่ร่วมกันอย่างกลมกลืนโดยไม่ต้องพึ่งพาการแทรกแซงจากทรัพยากรภายนอก ซึ่งผมเป็นคนแรกที่ได้ไปพักบ้านเขา แล้วปัจจุบันเขาก็เปิดให้บ้านลงแอป Airbnb เพื่อให้ผู้คนที่อาจจะอยากพักผ่อนยามสุดสัปดาห์ใจกลางป่าเขารัฐมิชิแกน สามารถไปเยี่ยมบ้านเขาได้ ซึ่งเขาก็เปิดบ้านลักษณะนี้อยู่อีกที่ที่ยุโรปด้วย
คาร์ลเป็นผู้ประกอบการแสนวิเศษที่หมั่นใฝ่รู้ และไม่ใช่แค่กับ Permaculture ตอนนี้เขาก็ยังหันมาสนใจบิตคอยน์แล้วด้วย
สำหรับผมทั้งหมดนี้นำไปสู่ “การแสวงหาซึ่งอิสรภาพ”

แล้วไม่ใช่อิสรภาพที่บัญญัติไว้ในตัวบทกฏหมาย แต่เป็น “อิสภาพทางจิตวิญญาณ”
ซึ่งในระหว่างการเดินทาง มันมีบางสิ่งที่สะกิดใจเมื่อมองออกไปที่ชาวอเมริกันนอก Bitcoin Meetup พวกเขาดูสูญสิ้นอิสรภาพไปเสียแล้วทั้ง ๆ ที่อยู่ในโลกเสรี
ผู้คนเหล่านั้นเหนื่อยล้า หงุดหงิด และพร้อมที่จะทำทุกอย่างให้หลุดพ้นจากทนทุกข์ พวกเขาดูหลงทางไปหมด และสูญสิ้นศรัทธาในตนเองไป ซึ่งเป็นสิ่งที่ต้องมีเพื่อให้ได้มาซึ่งอิสรภาพ พวกเขาอาจมีสิทธิเยี่ยงอิสระชนในทุกข้อ แต่มิอาจอยู่อย่างเสรีได้ เพราะขาดความเชื่อมั่นในตนเอง
แล้วมันทำไมกันหละ? นั่น คือสิ่งที่ผมพบคำตอบจากการได้พูดคุยกับบิตคอยเนอร์ในทุก ๆ วัน

คุณอาจฟังเรื่องนี้ซ้ำไปหลายรอบแล้วในงาน มันเป็นเพราะเงินที่เราใช้กันอยู่ทุกวันนี้มันถูกสร้างโดยผู้มีอำนาจ สิ่งที่รองรับมันมีเพียงอำนาจ และสรรพกำลังทางกายภาพของมนุษย์ที่ยิ่งใหญ่ที่สุด ตำรวจ กรงขัง และกองทัพ และด้วยหนี้ที่มันสร้างและสั่งสมมาตลอดร้อยปี ทำให้การที่จะดำรงไว้ซึ่งอำนาจของเงินนี้ต่อไปมีอยู่แค่ทางเดียว คือต้องใช้เงินและพลังงานมากขึ้นเรื่อย ๆ จนนำไปสู่การแย่งชิงอิสรภาพของพวกเราทุกคนเพื่อต่อชีวิตตัวของมัน
และนั่น ก็เป็นสิ่งที่ผมสัมผัสมันได้กับตาตัวเองยามขับมอเตอไซต์ผ่านทางหลวงและถนนทั่วอเมริกา ผมได้เห็นว่ามันดูดกลืนชีวิตและสังคมไปมากขนาดไหน ไม่ว่าจะผ่านร้านอาหาร ร้านค้า หรือร้านกาแฟ
ระบอบนี้ต้องการให้เราจำนน ทนทำงาน จ่ายภาษี ไม่แหกกฏและห้ามตั้งคำถาม และสำหรับคนส่วนใหญ่บนโลก มันได้บรรลุจุดประสงค์ของมันได้อย่างสมบูรณ์แบบ
เพราะหลาย ๆ คนในตอนนี้ไม่แม้แต่จะตั้งคำถามแล้วด้วยซ้ำ คุณอาจจะคุ้นเคยกับนิทานของช้างกับเชือกล่าม ที่เมื่อคุณล่ามเชือกช้างเด็กไว้กับต้นไม้ เมื่อมันโต ถึงมันจะสามารถฉีกเชือกทิ้งแล้วหนีไปได้มันก็จะไม่ทำ ตราบใดที่มันยังรู้สึกถึงเชือกล่ามนั้นมันก็จะไม่หนีไปไหน เชือกเส้นนั้นได้ก้าวข้ามขีดจำกัดทางฟิสิกส์ด้วยการล่ามลึกถึงวิญญาณ นั่นคือสิ่งที่ผมเห็นในดวงตาของชาวอเมริกันเกือบทุก ๆ คนที่ได้มีโอกาสพบเจอและพูดคุย
ซึ่งอีกด้านหนึ่ง ผู้ถือบิตคอยน์สามารถตื่นรู้และลุกขึ้นแสวงหาซึ่งอิสรภาพได้
มันดันมีปัญหาที่ระบบเศรษฐกิจและการเมืองในปัจจุบันนี้ ที่อยู่บนรากฐานของเงินกระดาษไม่อาจอยู่รอดได้หากผู้คนเป็นอิสระ มันต้องคอยพรากสิ่งเหล่านั้นจากมือเราไปอย่างช้า ๆ เพื่อมีชีวิตต่อไป แต่สำหรับบิตคอยน์เนอร์นั้น พวกเขารู้ในสิ่งที่สำคัญที่สุด คือในหนทางของการไฝ่หาซึ่งอิสรภาพของพวกตนนั้นคือพลังที่แสนสูงค่า พวกเขาคือผู้คนที่สร้างครอบครัวแสนสุขและคอยปลดโซ่ตรวนสังคมของพวกเขา
นี่เป็นสาเหตุที่การแสวงหาซึ่งอิสรภาพในระดับจิตวิญญาณนั้นสำคัญยิ่งสำหรับพวกเขา ปณิธานที่จะเริ่มที่ตนเองเพื่อสังคมที่ดีกว่าเดิม
สิ่งที่ผมเห็นผ่านการเดินทางของผมที่ได้พบเจอกับเหล่าบิตคอยเนอร์ คือพวกเขาจะทำงานและทำงานเพื่อแสวงซึ่งอิสรภาพ นำไปสู่การออกจากสิ่งเน่าเฟะบนโลกเงินกระดาษ และสร้างโครงการหรือบริษัทเล็ก ๆ ที่จะช่วยเปลี่ยนสังคมของเขา ซึ่งส่วนมากเราก็จะได้เห็นโครงการเหล่านั้นผ่าน Bitcoin Meetup
หลังจากจบทริปผมก็ได้แต่ครุ่นคิดว่า อิสรภาพทางจิตวิญญาณเหล่านั้นมันจะก่อเกิดในหัวใจของผู้คนได้อย่างไร

คำตอบคือมันเกิดขึ้นจากการท้าทายตัวเอง ออกจากพื้นที่ปลอดภัยของเรา และมองสิ่งต่าง ๆ ในมุมใหม่ ๆ ซึ่งนั่นเป็นคำตอบที่ต่อหน้าผมอยู่แล้วตลอดเวลา ทั้งในสมัยเด็ก ในประเทศไทย และในการเดินทางทริปบิตคอยน์ทั่วสหรัฐฯนี้
มันคือการเดินทาง
สำหรับผม การเดินทางคือเครื่องมืออันทรงพลังที่จะสร้างอิสรภาพแก่ผู้คน อย่างไรก็ดี พวกเขามักเข้าใจความหมายของการเดินทางผิดไป
การเดินทางที่แท้จริง จะนำคุณออกจากพื้นที่ปลอดภัยของคุณ และผลักดันขีดจำกัดของคุณ มันจะท้าทายสิ่งที่คุณเคยคิดว่ารู้ดีแล้ว เพราะในสถานที่ใหม่ ทุกอย่างแตกต่างออกไป คุณจะได้ยินแนวคิดใหม่ ๆ ลองชิมอาหารใหม่ ๆ และพบเจอผู้คนที่ใช้ชีวิตในแบบที่ต่างไปอย่างสิ้นเชิง
ตอนที่ผมยังเด็ก ผมโชคดีมาก เพราะพ่อของผมเป็นนักบินสายการบินพาณิชย์ และครอบครัวของเราชอบเดินทางมาก นั่นทำให้ครั้งแรกที่ผมออกนอกสหรัฐฯ คือเมื่อตอนผมอายุได้ 8 ขวบ พวกเราไปประเทศจีนกันเป็นเวลาสองสัปดาห์ ซึ่งการเดินทางครั้งนั้นได้ทำลายกรอบความคิดที่ผมมีต่อความเป็นจริงไปอย่างสิ้นเชิง และเมื่อผมกลับมาโรงเรียน ผมรู้สึกว่ามันยากยิ่งที่จะเชื่อมโยงกับเพื่อน ๆ เพราะผมได้เห็นประสบการณ์ที่ไม่มีใครในห้องเรียนจากแถบมิดเวสต์เคยเห็น พวกเขาส่วนใหญ่มักไปเที่ยวที่เม็กซิโก ปารีส ไม่ก็ยุโรป ซึ่งนั่นก็ถือว่าดีแล้วแล้วสำหรับพวกเขา
ทุกครั้งที่ผม ออกเดินทาง ความต้องการที่จะก้าวออกจากพื้นที่ปลอดภัยของผมก็ยิ่งเติบโตขึ้นเรื่อย ๆ จนเมื่อผมมาถึงประเทศไทยอีกครั้ง กรอบความคิดทั้งหมดเกี่ยวกับการทำงานของโลกใบนี้ของผมก็พังทลายลงไปอย่างสิ้นเชิงในที่สุด
อินเตอร์เน็ตก็ได้เปลี่ยนการเดินทางของผู้คน ให้ออกห่างจากการเดินทางที่แท้จริงไป

ตอนนี้มันง่ายมากที่จะวางแผนการเดินทางทั้งทริปได้จากที่ที่คุณอยู่ ไม่ใช่แค่ในเชิงกายภาพเท่านั้น แต่ยังรวมถึงในความคิดของคุณด้วย
อัลกอริธึมและผู้คนรอบตัวเราอนุญาตให้เราสามารถสร้าง ประสบการณ์การเดินทาง ที่เราไม่ต้องก้าวออกจากพื้นที่ปลอดภัยของเราเลย นั่นทำให้คุณจะไปเยือนแต่สถานที่ที่อัลกอริธึมแนะนำ เพราะมันรู้ว่าคุณจะชอบ หรือเป็นสถานที่ที่เพื่อนแนะนำให้คุณ คุณสามารถค้นข้อมูลได้จนทำนั่นทำให้คุณไม่ได้สัมผัสสถานที่เหล่านั้นจริง ๆ เพราะคุณได้ดูวิดีโอบน YouTube และซึมซับข้อมูลทั้งหมดมาก่อนแล้ว ทำให้เมื่อคุณไปถึงที่นั่น มันก็กลายเป็นแค่การเล่นซ้ำในสิ่งที่คุณจินตนาการไว้ว่าจะได้เห็นอยู่แล้ว
นี่แหละคือจุดที่ผมแบ่งแยกระหว่างการ ท่องเที่ยว และการ เดินทาง
การท่องเที่ยว คือการที่คุณไปในที่ต่าง ๆ แต่ยังคงอยู่ในพื้นที่ปลอดภัยของตัวเอง คุณทำสิ่งที่คุ้นเคย และวางแผนทุกอย่างล่วงหน้า ในขณะที่ การเดินทางคือการก้าวออกจากพื้นที่ปลอดภัยของคุณ คุณมุ่งหน้าไปสู่สิ่งที่ไม่รู้จัก และยอมเสี่ยงกับอะไรบ้าง ผมจึงอยากสร้างบางอย่าง ณ ที่แห่งนี้ ผมอยากสร้างสิ่งที่ทำให้ผู้คนได้ออกเดินทาง
ดังนั้นทีมของผมและพันธมิตรของผมในประเทศไทยจึงได้ตกลงร่วมกันสร้างประสบการณ์ที่จะผสมผสานความสะดวกและปลอดภัยของ การท่องเที่ยว เข้ากับการผจญภัยและประสบการณ์สดใหม่จาก การเดินทาง**
แล้วนั่น ก็คือเหตุผลที่ได้ให้กำเนิด “Rite of Passage”

Rite of passage คือการผจญภัยที่ถูกออกแบบมาโดยเฉพาะสำหรับเพื่อบิตคอยน์และบิตคอยเนอร์ เราเรียกมันว่า ทริปที่เงินซื้อไม่ได้ เพราะทริปเหล่านี้ตั้งใจจะเปลี่ยนแปลงคุณในแบบที่การไปเที่ยวพักผ่อนธรรมดาๆ ทำไม่ได้
ทุกส่วนของ Rite of passage ถูกออกแบบมาเพื่อเปลี่ยนมุมมองที่คุณมีต่อโลก ให้ไม่ใช่แค่เพียงมองมันผ่านกฏหมาย แต่ได้มองมันผ่านการสนทนากับคนอื่นๆ ที่มีหัวใจดวงเดียวกับคุณ
หนึ่งในสิ่งสิ่งที่เราทำคือ เราจะไม่ค่อยแสดงกำหนดการล่วงหน้าหากไม่จำเป็น เพราะเราอยากให้ทุกประสบการณ์ที่คุณจะได้รับจะเป็นอะไรที่ใหม่หมด เพราะคุณไม่รู้ว่าจะเจออะไรบ้าง และเรามุ่งเน้นที่ประสบการณ์ท้องถิ่นอย่างแท้จริงกับกลุ่มเล็ก ๆ เพื่อให้คุณได้สัมผัสกับสถานที่นั้นจริงๆ แทนที่จะเห็นแค่สิ่งที่ คนนำทริปติดสิบอันดับแรก เลือกไว้ให้
อีกทั้งเรายังคัดกรองทุกคนที่เข้าร่วมทริปเหล่านี้ เพราะเรามองหาคนที่ให้คุณค่ากับความขยันซื่อสัตย์ รับผิดชอบต่อตัวเอง และมีความเป็นอิสระ เรากำลังมองหาบิตคอยเนอร์ตัวจริง

ตลอดการเดินทางที่ผมได้ไปทั่วอเมริกา เพื่อพบปะกับบิตคอยน์เนอร์ ผมได้เรียนรู้ว่าการเป็นบิตคอยน์เนอร์มันมากกว่าการแค่ครอบครองเหรียญบิตคอยน์ มันเกี่ยวกับการใช้ชีวิตบนพื้นฐานของความขยัน ความรับผิดชอบต่อตนเอง และการมุ่งมั่นแสวงหาอิสรภาพอย่างไม่หยุดยั้ง
แล้วการเดินทางนี้ มิได้เกี่ยวกับการสะสมเงินหรือความสำเร็จเพียงอย่างเดียว มันส่วนตัวกว่านั้น**
มันคือการเดินทางแห่งการปลดแอกตัวเองจากขีดจำกัดในหัวของเราที่ฉุดรั้งเราไว้ แห่งการลงมือทำ ท้าทายตัวเอง ยอมรับสิ่งที่ไม่รู้ เป็นการเดินทางที่จะพาเราข้ามขีดจำกัดทั้งหลายได้ ซึ่งไม่ใช่สิ่งที่เราทำในสามัญสำนึกเดิม ๆ ผมพบว่าหลายคนที่ผมได้เจอที่ถือบิตคอยน์นั้น ตื่นเต้นกับประสบการณ์การเดินทางของผมที่ผมเล่าอยู่มากกว่าตัวบิตคอยน์อีก แม้ว่าพวกเขาจะไม่ได้พูดออกมาตรงๆ ก็ตาม
แล้วผมพบว่าการแสวงซึ่งอิสระภาพนี้แหละที่นำพาพวกเราเหล่าบิตคอยเนอร์มาพบเจอกัน

หลายคนที่ถือบิตคอยน์มองว่าบิตคอยน์เป็นรูปแบบของเงินที่ดีที่สุดผมเห็นด้วย มันคือเรื่องจริง แต่อย่างไรก็ตาม ผมมองว่ามันเป็นอะไรที่มากกว่านั้น สำหรับผม บิตคอยน์ได้นำพาผู้คนที่แสวงหาซึ่งอิสรภาพมาพบกัน เหมือนกับที่พวกเราทุกคนที่นั่งอยู่ที่นี่วันนี้
และการแสวงหาซึ่งอิสรภาพนี้แหละ ที่จะทำให้โลกน่าอยู่ขึ้น
ขอบคุณครับ
บรรยายโดย Captain Sidd แปลและเรียบเรียงโดย Techin
-
 @ 8a4c88dc:a498228e
2024-10-17 11:56:47
@ 8a4c88dc:a498228e
2024-10-17 11:56:47คุณ Jimmy Castro ได้พูดคุยกับ อ.พิริยะ บนเวที Thailand Bitcoin Conference 2024 ถึงประสบการณ์ของเขาบนเชียงใหม่ ว่าเขาทำอะไรที่นั่นบ้าง รู้จักกับบิตคอยน์ตอนไหน เรื่องราวของเขาในการจัดตั้งศูนย์การเรียนรู้บิตคอยน์ที่เชียงใหม่ และมุมมองต่อการเติบโตของ Bitcoin ภายในประเทศไทย
ซึ่งสามารถรับชมการสนทนาฉบับเต็มได้ที่: https://www.youtube.com/watch?v=bVYmwMKu9Rc&t=234s

ความมหัศจรรย์ของเครือข่ายบิตคอยน์ที่คุณจิมมี่ได้ค้นพบระหว่างการช่วยเหลือชุมชนบนเขาที่เชียงใหม่แห่งหนึ่ง
Jimmy Castro นั้นย้ายเข้ามาอยู่ที่เชียงใหม่เป็นเวลา 2 ปีกับอีก 9 เดือนถ้วนแล้ว และได้จัดตั้งองค์กรไม่แสวงผลกำไรเพื่อที่จะให้การช่วยเหลือชุมชนห่างไกลความเจริญที่นั่น โดยเฉพาะกับชุมชนเด็กกำพร้าบนดอย ด้วยการให้การศึกษาภาษาอังกฤษแก่พวกเขา นอกจากนั้น เขาเองก็มีธุรกิจส่วนตัวที่สหรัฐอเมริกา ในเมืองไมอามีและมาร์กที่ช่วย Support สิ่งที่เขาทำอยู่ที่นี่ด้วยเช่นกัน
คุณพิริยะนั้นได้รู้จักกับคุณจิมมี่ประมาณต้นปีแล้วก็ได้สนใจตัวโครงการของเขาที่ได้มีการนำแผงโซลาเซลล์และเครื่องขุด Bitcoin ไปติดตั้งให้ชุมชนบนเขา จึงถามไถ่ว่ามันเป็นมาอย่างไร
คุณจิมมี่เองก็ตอบว่าในตอนแรกนั้น พวกเขามีแค่ครูภาษาอังกฤษที่ตีนเขาใกล้ ๆ กับเมือง ก่อนที่เขาจะเกิดความเห็นอกเห็นใจเด็ก ๆ ที่เดินลงเขามาเรียนจึงได้ขึ้นไปเยี่ยมเยือนและก็พบว่าที่นั่นมีเด็กกว่าร้อยคน แต่กลับไม่มีไฟฟ้าใช้เลย เขารู้ว่าหากไม่มีไฟฟ้าต้องเกิดปัญหาทางโภชนาการแน่เพราะไม่มีตู้เย็น เขาจึงขึ้นไปติดโซล่าเซลล์กำลังผลิตไม่ใหญ่มากที่นั่น เพื่อที่อย่างน้อยเด็ก ๆ และคนที่นั่นจะมีตู้เย็นมาแช่ผักปลาหรือเนื้อสัตว์ได้
ก่อนที่จะพบว่ามีพลังงานเพียง 20% จากแผงโซล่าเท่านั้นที่ถูกเอาไปใช้ ที่เหลือผลิตเกิน เขาเลยปิ๊งว่าน่าจะนำเครื่องขุด Bitcoin ไปติดตั้งบนนั้นเพื่อใช้ประโยชน์จากพลังงานเหลือใช้นี้แล้วก็ได้ลองถามไปทางคุณ Bob ที่ กรุงเทพซึ่งเป็นเจ้าของ Bob Space ว่าเราเอาเครื่องขุดขึ้นไปติดบนนั้นได้ไหม? ทาง Bob Space จึงตกลงและส่งคนของเขาขึ้นไปสำรวจบนเขาที่คุณจิมมี่ติดโซล่าเซลล์อยู่แล้ว แล้วก็ได้คำตอบว่าเราสามารถติดตั้งเครื่องขุด Bitcoin ได้สองเครื่อง
เมื่อได้ยินดังนั้นเขาก็เลยไฟเขียวอย่างไม่ลังเล "เราลงเขาไปเตรียมของแล้วขึ้นมาติดเครื่องขุดกัน!"
ทว่าในขณะนั้นเป็นช่วงที่ฝนตกหนักมาก ทำให้การขับรถขึ้นเขาระยะทางประมาณ 60 กิโลเมตร นั้นแทนเป็นไปไม่ได้ พวกเขาจึงรออยู่สามเดือน จึงเมื่อฝนซาแล้ว พวกเขาก็ได้ขึ้นไปดำเนินงานกัน ในตอนแรกนั้นคุณ Jimmy เองก็รู้จักกับบิตคอยน์ในระดับผิวเผินเองเท่านั้น แต่หลังจากที่ทางทีมได้ติดตั้งอินเตอร์เน็ตบนนั้นและเปิดใช้งานเครื่องขุด เขาก็ประหลาดใจ
"นี่คือ...เกิดไรขึ้น?" "เราขุดบิตคอยน์กันอยู่ไง"
ซึ่งเป็นอย่างนั้นจริง ๆ ตัวเครื่องขุดขุดบิตคอยน์มาได้กว่า 40,000 Sats ต่อเดือน (ในกรณีที่เครื่องทำงานตลอด 24 ชั่วโมง) ซึ่งตีเป็นเงิน 1000 บาทในอัตราการแลกเปลี่ยน ณ ขณะนั้น แต่นั่นไม่ได้เป็นสิ่งที่เขาสนใจมากที่สุด
ณ ชุมชนบนภูเขากลางป่าที่ ๆ ต้องใช้เวลากว่า 5 ชั่วโมงจากตัวเมืองเชียงใหม่และไม่สามารถเข้าถึงไฟฟ้าของรัฐได้ สามารถเชื่อมต่อกับโลกของบิตคอยน์ได้ นี่เป็นสิ่งที่คุณจิมมี่ทึ่งที่สุด
โดยไม่รอช้า เขาได้โพสเรื่องราวสุดเจ๋งนี้บน X(Twitter) อย่างดีอกดีใจ แล้วคนที่เห็นโพสเขาก็ส่งเงินบริจาคเป็นบิตคอยน์มาที่โครงการบนเขานี่ ชุมชนนี้เชื่อมต่อกับโลกภายนอก ได้รับการช่วยเหลือ โดยไม่ผ่านตัวกลางใด ๆ เพียงเพราะแค่เขามาตั้งเครื่องขุดบนนี้ เขามองว่ามันเป็นสิ่งที่ทรงพลังมาก
อย่างไรก็ดี พอเข้าหน้าฝนพวกเขาก็ขนเครื่องขุดลงมาไว้ที่เมืองอมก๋อยแล้วใช้ไฟจากการไฟฟ้าขุดแทน ถึงแม้ว่าจะไม่คุ้มค่าไฟขุดก็ตาม แต่พวกเขาก็ยังขุดต่อ เพราะในขณะนั้นมีคนใจดีมากมายจากทั่วทุกมุมโลกบริจากให้กับเขาเพื่อให้ดำเนินโครงการต่อไป ทำให้มันพอชดเชยต้นทุนค่าขุดได้บ้าง ด้วยเหตุนั้นเขาจึงยังคงเดินโครงการต่อและให้การสนับสนุนชุมชนบนเขากว่า 40 หมู่บ้าน
จนกระทั่งวันหนึ่ง เหมือนว่าจะมีหัวหน้าชุมชนตั้งคำถามกับโครงการขุดบิตคอยน์ที่คุณจิมมี่ทำอยู่ว่ามันดูดีเกินกว่าที่จะเป็นจริงได้ เขาจะมาต้มตุ๋นเราหรือเปล่า เขาที่ไม่อยากขัดแย้งอะไรกับทางชุมชนจึงได้พับโครงการขุดไปและกลับไป Focus กับการสอนหนังสือพวกเขาอย่างเดียว

คุณพิริยะให้ความเห็นว่าพวกเขาอาจจะไม่ค่อยคุ้นเคย ว่านี้เป็นน้ำใจปกติของชาวบิตคอยน์ เพราะว่ามันเป็นเหมือนกับที่คุณ Tucker บอกเอาไว้ในการบรรยายของเขาว่าเงินที่แข็งแกร่งทำให้่คนมีน้ำใจมากขึ้น นั่นทำให้เราเห็นโครงการทำนองนี้กับ Bitcoiner ผุดขึ้นมามากมาย
ข่าวดีก็คือคุณจิมมี่ยังจะผลักดันโครงการนี้ต่อไป
ปัจจุบันเขาวางแผนว่าจะนำโครงการนี้ไปช่วยเหลือชุมชนห่างไกลอีกชุมชนหนึ่ง ชื่อชุมชนอมก๋อย ที่โดนรัฐสร้างเขื่อนไล่ที่จนพวกเขาสูญเสียปศุสัตว์และที่อยู่อาศัย ดังนั้นเขาจึงวางแผนว่าจะนำโครงการนี้ไปต่อยอดที่นั้น ให้พวกเขาไม่ต้องพึ่งไฟรัฐ แล้ววางแผนว่าจะขยาย Scale ของโครงการให้ใหญ่ขึ้นอีก ซึ่งเขาได้ประมาณการไว้ว่าจะติดตัังโซล่าเซลล์กำลังผลิตราว ๆ 50 ถึง 70 กิโลวัตต์
โครงการนี้ ทางคุณจิมมี่เองก็กล่าวว่าจะเกิดขึ้นไม่ได้เลยหากไม่มีทางทีมของ Bob Space มาช่วย และบอกขอบคุณถึงความร่วมมือที่พวกเขาให้อย่างสุดซึ้ง
อีกทัังหลังจากมางานแล้วได้รู้จักกับ Nostr เขาก็คิดว่านี่แหละอาจจะช่วยให้เด็ก ๆ บนดอยเข้าถึงความช่วยเหลือจากคนทั่วโลกได้ง่ายขึ้นไปอีก เพราะคนที่เห็นเด็ก ๆ ผ่าน Nostr ก็สามารถบริจาคตรงเข้า Profile ของพวกเขาได้เลย

"we're going to go up there and really mind sats!"
Jimmy Castro กับ Bitcoin Learning Center ที่เชียงใหม่ของเขาและคณะ
หลังจากที่พวกเขาพูดคุยเรื่องโครงการขุดเสร็จไป พวกเขาก็มาคุยกันเกี่ยวกับ Bitcoin Learning Center ที่ทางคุณจิมมี่และทีมของเขาได้ดำเนินอยู่ ซึ่งพึ่งตั้งได้ 2 ปี 9 เดือน เขาเล่าย้อนกลับไปในปี 2016 ที่เขาได้เข้ามาอยู่ที่เชียงใหม่และได้พบกับงาน Bitcoin มากมายที่นั่นที่จัดโดยคุณสตีฟ ซึ่งเขาเป็นคนมีความอดทนและเปิดรับฟังผู้อื่น เป็นบุคคลที่เขาเคารพ อย่างไรก็ดี เขานั้นต้องการอะไรซักอย่างที่ Focus ที่ตัว Bitcoin มากกว่านี้ ซึ่งงานของคุณสตีฟ ไม่ได้ตอบโจทย์พอ ด้วยความต้องการข้างต้น รวมกับที่เขาเคยไปอยู่ใน El Salvador แล้วเห็น Bitcoin Adoption ที่นั่น ทำให้เขาตระหนักได้ถึงความสำคัญของคอมมูนิตี้ที่ได้ชนไหล่กันจริง ๆ หลังจากวันนั้นเขาจึงบินไปบินมาอยู่หลายครั้งจากเชียงใหม่ไปกรุงเทพเพื่อไป Bitcoin Meetup ที่จัดขึ้นเป็นครั้งคราว
ณ จุดนั้นเองทำให้เขาคิดว่า เขาควรตั้ง Bitcoin hub ที่เชียงใหม่ได้แล้ว มันสมเหตุสมผลที่เมืองที่ใหญ่เป็นอันดับสองของประเทศจะมี Bitcoin Hub เหมือนที่กรุงเทพมีบ้าง (และถ้าบินไปบินกลับงี้ตลอดเขาอาจจะถังแตกเอาได้)
เขา และภรรยา ร่วมกับเพื่อนอีกคน ร่วมกันรีโนเวทตึกเก่า 40 ปีใหม่ให้เป็นฐานที่มั่นของเขา แต่เผอิญว่าช่วงเวลาที่กำลังจะทำ Office ก็ไปปะกับช่วงที่ FTX ล่มพอดี เราเลยหยุดโครงการเอาไว้ก่อนเพื่อรอให้เรื่องเย็นลง ก่อนที่เมื่อประมาณปีก่อน พวกเขาก็ลงมือลงแรงไปอย่างมากเพื่อที่จะก่อร่างสร้าง Bitcoin Learning Center นี้จนได้มีงาน Grand Opening เมื่อสัปดาห์ก่อน

เขาตกใจมากที่มี Bitcoiner ในเชียงใหม่มาร่วมงานกว่าร้อยคน หรือกว่า 10 หรือ 15 ครอบครัว เป็นสิ่งที่เกินคาด เขาได้แสดงความดีอกดีใจอย่างเปิดเผย
ซึ่งเขาได้กล่าวว่าหนึ่งในจุดประสงค์สำคัญของ Bitcoin Learning Center ที่เชียงใหม่นี้ คือการมอบการศึกษาเกี่ยวกับ Bitcoin เป็นภาษาไทยบ้าน ๆ เพราะเขาเข้าใจดีว่าไม่ใช่ทุกคนที่เป็นภาษาอังกฤษ ซึ่งเขาเองก็จะจัด Bitcoin 101 Meetup ที่เชียงใหม่ภายในเดือนตุลาคมนี้ เพื่อที่จะได้พูดคุยกันในเรื่องต่าง ๆ เช่นอะไรคือเงิน Bitcoin คืออะไรแล้วเราจะเอามันไปใช้ทำอะไรได้บ้าง อีกทั้งเพื่อที่จะเก็บ Feedback ที่เราอาจจะจำเป็นเพื่อที่จะพัฒนาวงการ Bitcoiner ต่อไป
มุมมองต่อการเติบโตของ Bitcoin ภายในประเทศไทย
"Bitcoin นั้นช้า แต่มั่นคง" อาจพูดได้ว่าเป็นใจความสำคัญในการสนทนาเกี่ยวกับเรื่องที่ทั้งคุณจิมมี่และอาจารย์พิริยะได้เรียนรู้เมื่อดำเนินโครงการเกี่ยวกับ Bitcoin
เวลาที่เราจะเริ่มต้นอะไรเกี่ยวกับ Bitcoin มันไม่ได้ใหญ่และฉูดฉาดเหมือนเหรียญ Crypto อื่น ๆ เพราะมันมักจะเริ่มจากสิ่งเล็ก ๆ แต่ค่อย ๆ เติบโตอย่างค่อย ๆ เป็นค่อยไป เพราะสิ่งที่ Bitcoiner ทุกคนมีเหมือนกันคือ เมื่อเป็นแล้ว มันกลับไปเหมือนเดิมไม่ได้ พวกเราจึงมีจำนวนมากขึ้นเรื่อย ๆ
อีกทั้งทั้งสองยังเห็นตรงกันว่ามีคนไทยหลายคนเจ็บไปกับการเกิดและดับของ Shitcoin ต่าง ๆ ในตลาด พวกเขาเห็นอกเห็นใจและอยากให้พวกเขากลับมามอง Bitcoin ใหม่ไม่ใช่ในฐานะเหรียญ ๆ หนึ่ง แต่เป็นอะไรที่ยิ่งใหญ่กว่านั้น
โดยในระหว่างที่สนทนากัน คุณจิมมี่เองก็ให้ความสนใจและสำคัญกับสิ่งที่ทางทีมงานของ Right Shift ทำเป็นอย่างมาก ด้วยความสม่ำเสมอของทีมงาน และการทำงานอย่างไม่รู้จักเหน็ดเหนื่อยที่นำพาเขาและทุก ๆ คนในงานมาที่นี่ เขาอยากให้ Right Shift ดำเนินกิจการต่อไปและก็ได้ทิ้งท้ายเอาไว้ว่าหากต้องการความช่วยเหลือหรือต้องการความร่วมมืออะไรกับทาง Bitcoin Learning Center ที่เชียงใหม่แล้วหละก็เขาพร้อมที่จะช่วย

"We'll do this. We'll make this happen."
ทั้งการเติบโตของคอมมูนิตี้ Bitcoin ที่ภูเก็ต พังงา กรุงเทพ และเชียงใหม่ ทำให้ทั้งเขา และ อ.พิริยะ เชื่อว่าซักวัน Bitcoin Adoption จะต้องเติบโตจนหน่วยงานรัฐเล็งเห็น ซึ่งทางคุณจิมมี่ ก็แสดงความยินดีที่จะได้ช่วยเหลือพวกเขาเมื่อเวลามาถึง เพราะเขามองว่าเมืองไทยถือเป็นพี่ใหญ่ในประเทศกลุ่มตะวันออกเฉียงใต้ ทำให้เรามีศักยภาพในการรุดหน้าเกี่ยวกับ Bitcoin Adoption และการให้การศึกษาเกี่ยวกับ Bitcoin
ดังนั้นแล้ว ขึ้นอยู่กับเวลาว่าเขาจะตื่นรู้ว่า Bitcoin สามารถนำมาพัฒนาประเทศได้เช่น เราสามารถสร้างความมั่นคงทางพลังงานจากมันได้ เราสามารถพัฒรุดหน้าอย่างก้าวกระโดดด้วยมันได้ เมื่อถึงตอนนั้น มาพูดคุยกับเราสิ มาร่วมกันสร้างไปด้วยกัน
และก็ไม่ใช่แค่รัฐบาล วันหนึ่งทุก ๆ ธุรกิจเอกชนก็จะต้องมีส่วนเกี่ยวข้องกับ Bitcoin เช่นกัน มันจึงสำคัญที่พวกเราในตอนนี้จะต้องสร้างโครงสร้างพื้นฐานต่าง ๆ เกี่ยวกับการใช้ Bitcoin ให้เพียบพร้อมในทุก ๆ ทาง แล้วเมื่อพวกเขาต้องการเรา พวกเขาจะต้องการเรา

"They're going to need us because we don't go away. We just keep getting stronger and stronger."
และในช่วงสุดท้ายของการพูดคุย คุณจิมมี่ก็เชิญชวนทุก ๆ คนให้เข้ามาศึกษาเกี่ยวกับ Bitcoin ซักหน่อย วันละนิดก็ยังดี ไม่สำคัญว่าคุณจะเป็นใคร ไม่ว่าจะเป็นธุรกิจเล็กเช่นร้านตัดผม หรือธุรกิจใหญ่ก็ตาม เขาเชื่อว่ามันจะต้องเป็นประโยชน์กับพวกเราในภายภาคหน้า
"So please, add a little bit of bitcoin into your life"
บรรยายโดย Jimmy Castro และ อ.พิริยะ สัมพันธารักษ์ แปลและเรียบเรียงโดย Techin
-
 @ 8a4c88dc:a498228e
2024-10-17 11:52:20
@ 8a4c88dc:a498228e
2024-10-17 11:52:20บิตคอยน์มีคุณสมบัติอะไรที่จะสามารถอุ้มชูจริยธรรมโลก และเราควรปฏิบัติกับมันอย่างไร
นี่คือ Agenda สำคัญในการบรรยายของคุณทักเกอร์ภายในงาน Thailand Bitcoin 2024

ขอบคุณที่เชิญผมมา ณ ที่นี่ ผม ทักเกอร์
อย่างที่รู้กันวันนี้เราจะคุยกันเกี่ยวกับบิตคอยน์ในมุมมองทางด้านจริยธรรม ผมคงไม่ต้องอธิบายอะไรเกี่ยวกับเรื่องเชิงเทคนิคของบิตคอยน์มากนักเพราะหลาย ๆ ท่านคงจะได้ฟังกันมากพอแล้ว ดังนั้นแล้ว ผมอยากที่จะมองบิตคอยน์นั้น เป็นเพียงเครื่องมือชิ้นหนึ่ง
ตั้งแต่ยุคดึกดำบรรพ์มนุษย์ได้ประดิษฐ์ เครื่องมือ มากมายเพื่อที่จะก้าวข้ามอุปสรรค์ต่าง ๆ อย่างเช่น หอก หรือเครื่องไถ นี่เป็นสิ่งที่แยกเราออกจากสัตว์ป่าอื่น ๆ ซึ่งคำว่า เครื่องมือ ของมนุษย์ไม่ได้หยุดอยู่ที่แค่ของที่จับต้องได้เท่านั้น เรายังมีเครื่องมือที่ไร้รูปร่างที่ถูกประดิษฐ์ขึ้น เพื่อเป็นตัวแทนของชุดความคิดที่เราจะสื่อสารกัน เช่น ภาษา คณิตศาสตร์ ตรรกศาสตร์
อย่างไรก็ดี เครื่องมือก็คือเครื่องมือ มันไม่มีชีวิต ไม่มีเจตจำนง จะดีหรือชั่ว เราจะเป็นผู้กำหนด เมื่อเป็นเช่นนั้น พวกเราจึงมีการนำเอา ประวัติศาสตร์ มาประยุกต์ใช้ร่วมเพื่อที่จะสร้างวิธีการใช้เครื่องมือเหล่านั้นไปในทางที่ถูกที่ควร เช่น เราอาจพูดได้ว่าการให้กำเกิด กฏหมาย ขึ้นเพื่อห้ามคนเข่นฆ่ากัน เป็นการที่มนุษย์เรียนรู้ประวัติศาสตร์ และใช้ภาษาเพื่อสร้างกฏหมาย เพื่อกำหนดศีลธรรมร่วมกันซึ่งนำไปสู่สันติภาพ
นั้น ทำให้เราจำเป็นต้องศีกษาประวัติศาสตร์เกี่ยวกับการเงิน เราเคยนำเงินมาใช้ไปในทิศทางไหนแล้วบ้าง แล้วในอนาคตเราจะใช้มันอย่างไรเพื่อที่จะสร้างเศรษฐกิจที่ยุติธรรมและมีจริยธรรม
ผมไม่ชอบสรุปประวัติศาสตร์ออกมาอย่างหยาบ กลับกันผมชอบมองย้อนกลับไปว่าพวกเราเคยทำอะไรเอาไว้บ้างเพื่อถอดบทเรียนจากมัน แล้วหวังว่าเราจะไม่ปล่อยให้ให้ประวัติศาสตร์ซ้ำรอย
ดังนั้นวันนี้ผมจะทำเช่นนั้น การมองย้อนกลับไปในประวัติศาสตร์นั้น ผมคิดว่ามันมันสำคัญยิ่ง

อย่างที่รู้กัน นี่คือ Karl Marx
เราอาจพูดได้ว่าด้วยสภาพแวดล้อมที่เขามีชีวิตอยู่ได้หล่อหลอมเขา จนเขาให้กำเนิดแนวคิดหนึ่งที่เขาคิดว่ามันจะเป็นบรรทัดฐานทางศิลธรรมใหม่ที่ทุกคนต้องใช้ และนี่เป็นสิ่งที่เขาเคยพูดเอาไว้
สะสมและกอบโกย นี่แหละคือแก่นแท้ของมัน จงให้อุตสาหกรรมสรรสร้างทรัพยากรเพื่อกอบโกยได้มากขึ้นอีก จึงประหยัดแล้ว ประหยัดอีก แล้วนำคุณค่าและสินค้าที่เอ่อล้นมากองเป็นทุนที่สูงขึ้น ให้ก่อเกิดเป็นทุนนิยม แล้วจึงกอบโกยเพียงเพื่อการกอบโกย กอบโกยเพียงเพื่อการผลิต สืบไป
นี่เป็นเป็นคำวิจารณ์ของเขา ถึงระบอบทุนนิยมและแนวคิดของมัน ซึ่งแพร่หลายปกคลุมทั้งสังคมที่เขามีชีวิตอยู่ คือการสะสมทุน อีกทั้งในมุมมองของเขาชี้ว่าฐานรากของทุนนิยมนั้นมีแค่การสะสมทุน สะสมทุน จนกระทั่งกระบวนการนี้มันได้กัดกินคุณค่าความเป็นมนุษย์ให้หายไปจากสารระบบ

ดังนั้นมุมมองที่เขามีต่อระบอบทุนนิยม คือระบอบที่เอารัดเอาเปรียบชนชั้นแรงงาน กล่าวคือเขานิยามระบอบทุนนิยมว่า จงรีดเค้นเลือดเนื้อจากคนงานให้ได้มากที่สุด ให้พวกเขารู้สึกห่างเหินจากงานที่ทำ และสะสมทุนที่เข้นออกมาได้ให้เพิ่มพูนสูงขึ้นไป
ในมุมมองของเขา ระบอบทุนนิยมจะผูกขาดความมั่งคั่งเอาไว้คนเพียงไม่กี่หยิบมือ และ มองทุกสิ่งทุกอย่างเป็นสินค้า เฉกเช่นแนวคิดหลักของทุนนิยมในมุมมองของเขาที่เน้นการกอบโกยเพื่อสะสมทุนให้ได้มากที่สุดด้วยทุกวิถีทาง ทุกอย่างบนโลกล้วนมีเพื่อให้กอบโกยสะสมทุน เพื่อทุนนิยม เขามองว่า ระบบเศรฐกิจแบบนี้จำเป็นต้องถูกปฏิรูปสิ้น อีกทั้งยังอธิบายเพิ่มเติมอีกว่าระบอบที่ถูกออกแบบมาให้ลดต้นทุนให้ได้มากที่สุดนี้ต้องถูกปฏิรูปสิ้นด้วย แล้วก็มองไปอีกว่า ทุนนิยมนั้นเป็นเพียงแค่ส่วนขยายของจักรวรรดินิยม ที่พวกเขาใช้กดขี่ผู้คน
ไม่ได้เป็นการสนับสนุนแต่อย่างใด แต่ผมเห็นว่า Karl Marx นั้นเป็นลูกหลานและผลพวงของระบอบทุนนิยม ซึ่งหล่อหลอมให้เขามีมุมมองเช่นนี้ต่อมัน

จากนั้นเราก็ย้อนมาหามิตรสหายที่เราคุ้นหน้ากันอย่างดี Adam Smith
เขาเกิดในอีกช่วงเวลาหนึ่ง ส่งผลให้ชีวิตหรือมุมมองต่อสิ่งต่าง ๆ นั้นแตกต่างจาก Karl Marx เขาเกิดในระบอบศักดินาสวามิภักดิ์ ที่ที่การแบ่งสันปันส่วนอำนาจขึ้นอยู่กับปริมาณที่ดินที่ผู้ใดครอบครอง เขาพูดอะไรไว้บ้าง เรามาดูกัน
เกียรติและศักดิ์ศรีของบุคคลทำให้เขารักที่จะปกครอง ไม่มีอะไรที่เหยียบย่ำเกียรติและศักดิ์ศรีเขาได้เท่าการถูกบังคับให้เชื่อฟัง ถูกทำให้ดูต่ำต้อย ต่อผู้ที่อยู่เหนือกว่า ขาจึงรักที่จะมีทาสให้ใช้งาน มากกว่าทำงานกับเสรีชน
เขาได้พูดถึงธรรมชาติของมนุษย์ รวมทั้งธรรมชาติของผู้มีอำนาจที่ไม่ต้องการเจรจากับแรงงานของพวกเขา พวกเขาใคร่ที่จะกดขี่บังคับมากกว่าการร่วมมือร่วมแรงกันกับพวกเขา
โดยที่นอกจากที่เขาจะพูดถึงผู้มีอำนาจหรือผู้ถือครองที่ดินแล้ว เขาก็ยังพูดถึงชนชั้นแรงงานด้วยเช่นกัน
ภายใต้ระบอบศักดินาสวามิภักดิ์นั้น ผู้อยู่ใต้บัญชานั้นมีหน้าที่แค่รับใช้อำนาจที่สูงส่งกว่า ไม่สามารถมีสิ่งที่เป็นของตนเองได้ พวกเขาจึงถูกบังคับให้วิงวอนต่อเจ้านายให้มอบอาหารที่อยู่และเครื่องนุ่งห่มแก่ตนด้วยการทำงานถวายแก่นายตน ในสถานการณ์เช่นนี้ เราไม่สามารถหวังให้พวกเขากระทำสิ่งใดให้มีประสิทธิภาพหรือก่อเกิดความก้าวหน้าได้
Adam Smith ได้วิพากวิจารย์ว่าการมีอยู่ของระบอบศักดินาสวามิภัคดิ์นั้น ทำให้อำจาจตกอยู่กับผู้ที่ครอบครองที่ดินเพียงอย่างเดียว ที่เป็นปัจจัยหนึ่งที่เซอะกร่อนบ่อนทำลายชนชั้นแรงงานเนื่องจากพวกเขาไม่มีสิทธิที่จะมีอะไรเป็นของตนเอง พวกเขาจึงต้องเอาแต่รับใช้เพื่อที่จะอยู่รอดไปวัน ๆ
เขานั้นค่อนข้างที่จะให้ความสำคัญกับประสิทธิผลของงาน ไม่ได้พูดถึงจริยธรรมหรืออุดมการณ์เหมือนกับ Karl Marx เขามองว่าถ้าบุคคลนั้นมีหน้าทีแค่รับใช้นายของตน บุคคลนั้นก็ไม่จำเป็นต้องทำอะไรมาก เขาแค่ต้องทำสิ่งที่เจ้านายสั่งเพื่อที่จะมีชีวิตอยู่ต่อไปแค่นั่น นั่นทำให้ภายใต้ระบอบนี้ประสิทธิผลของการใช้ทรัพยากรนั้นจะไม่ถูกดึงออกมาอย่างสูงที่สุด

เศรษฐกิจจะไม่สามารถทรงประสิทธิภาพได้เลยภายใต้ระบอบศักดินา เป็นสิ่งที่เขามอง และมองว่าระบอบทุนนิยมนั้นมีประสิทธิภาพมากกว่า แต่ก็ต้องตั้งคำถามว่ามีประสิทธิภาพเพื่ออะไร เพื่อกอบโกยทุนหรือไม่?
ไม่มีการเลื่อนชั้นทางสังคม เพราะว่าหากไม่มีที่ดินหรือถูกรับมอบที่ดิน พวกเขาก็จะไม่สามารถเปลี่ยนสถานะภาพทางสังคมได้เลย นั้นจึงทำให้ การค้าที่ถูกจำกัด เพราะว่าผู้คนส่วนใหญ่ไม่มีความจำเป็นต้องค้าขาย เพราะพวกเขามีหน้าที่แค่รับใช้ ทำงานให้เสร็จ ๆ ไปก็มีกินด้วยสิ่งที่เจ้านายของตนเองมอบให้แล้ว สุดท้ายเลยคือระบอบศักดินาสวามิภักดิ์ต้องมีการ ผูกขาดสิทธิเสรีภาพ เพราะตัวระบอบไม่สามารถอนุญาตให้มนุษย์ทุกคนมีอำนาจหรือไม่ยากจนได้ ซึ่งนั้นก็เป็นอีกจุดอ่อนที่ฉุดรั้งประสิทธิผลของมนุษย์
อีกครั้ง เราอาจกล่าวได้ว่าระบอบศักดินาสวามิภักดิ์ได้ให้กำเนิด Adam Smith ขึ้นมา

ต่อมาเป็นระบอบศักดินาสวามิภักดิ์ มันคืออะไรหละ มันคือระบบที่มีการแบ่งชนชั้นของบุคคลอย่างชัดเจน จากทาส สู่กษัตริย์ มีอัศวิน มีขุนนาง มีการรับใช้เพื่อได้รับการคุ้มครองจากกษัตริย์หรือเจ้าเมือง ระบอบดังกล่าวให้ความสำคัญกับผู้ถือครองที่ดิน ซึ่งเป็นตัวแสดงอำนาจที่ผู้นั้นถือครอง และความจงรักภักดีต่อผู้บังคับบัญชา
แล้วเมื่อมองย้อนกลับไปอีก เราก็จะเห็นอารยธรรมของมนุษย์ที่รวมกันเป็นเมืองเป็นรัฐและเกิดการซื้อขายเจริญเติบโตขึ้น ทุก ๆ อย่างเหมือนจะดีไปหมดแต่ทำไมทุก ๆ อารยธรรมถึงสิ้นสุดลง

การล่มสลายของกรุงโรม
เป็นตัวอย่างที่เราได้ยินกันมาเยอะมากหากคุณเป็น Bitcoiner พวกเขามีทั้งเจตจำนงที่จะหลีกหนีระบอบจักวรรดินิยม มีการกระจายอำนาจ เกิดสิ่งประดิษฐ์คิดค้นมากมาย มีเศรษฐกิจเกษตรกรรม มีการค้าขายกับต่างชาติ ถึงขนาดมีศาสนาเป็นของตนเอง
ทุกอย่างของกรุงโรมดูจะเป็นไปในทางที่ดี แต่แล้วทำไมหละ มันถึงล่มสลายลง


คำตอบคือมันเกิดการโกงหน่วยวัดมูลค่าให้ไม่เป็นไปตามธรรมชาติ
เช่นการที่หน่วยเงินมันเฟ้อ หรือถูกแทรกแทรง ถูกลดค่าลง หรือให้บางคนที่มีอภิสิทธิ์เสกเงินขึ้นมาให้กับตนเองได้
ทำให้ความมั่งคั่งของคนที่ทำงานและสมควรได้เงินก้อนนั้นถูกลดทอนลง เป็นความไม่เป็นธรรมชาติที่นำไปสู่การล่มสลายของอารยธรรมต่าง ๆ มนุษย์นั้นคิดค้นการโกงหน่วยการวัดมูลค่ากันมาตลอด หนึ่งในนั้นคือการที่ทำให้เงินเสื่อมมูลค่าเมื่อเทียบกับทองคำ ด้วยข้ออ้างที่บอกกันว่า
ให้พวกเราถือทองของพวกคุณ อย่าแลกเปลี่ยนกันด้วยทอง ทองมันหนักเกินไป ทองมันเคลื่อนย้ายยาก
นำไปสู่การผูกขาดทองไว้กับอำนาจรัฐ โดยที่พวกเขาก็จะให้ประชาชนใช้เงินที่ตนตีตราขึ้นมา แล้วก็ทำให้มันงอกเงยจนไม่ได้อิงจากมูลค่าของทองคำแบบ 1:1 ให้กำเนิดเงินเฟ้อซึ่งนำไปสู่การเสียเสถียรภาพของตลาดและการล่มสลายของอารยธรรมหลายต่อหลายครั้ง เช่นกรุงโรม มองโกล หรือแม้แต่จักวรรดิต่าง ๆ ภายในจีน
รูปแบบของการโกงหน่วยวัดมูลค่าของเงินนั้นสลับซับซ้อนและพิศดารขึ้นตามการเวลาที่ผ่านไป จนเรามาถึงยุคที่เงินนั้นไม่ได้ผูกกับทองคำอีกต่อไป จากเหตุการณ์ Nixon shock ทำให้เงินในตอนนี้สื่อมมูลค่าลงไปเรื่อย ๆ จากระบบการเงินใหม่ที่ตัดตนเองออกจากทองคำและไปถูกอ้างอิงมูลค่าโดย หนี้ ไม่ว่าจะเป็นหนี้ที่ถือโดยธนาคารกลางและตนก็เป็นคนกำหนดนโยบาย ซึ่งผมมองมันในฐานะ รากฐานของระบบธนาคารสินเชื่อ หรือหนี้ที่ถือโดยธนาคารพานิชย์ที่ปล่อยสินเชื่อก็ยิ่งทำให้เงินมันเฟ้อขึ้นไปอีก เช่นแบงค์ของ Wall Street ในสหรัฐอเมริกา

นี่คือจุดที่ทำให้เรากลับมาที่บิตคอยน์ ในฐานะเครื่องมือที่มีจริยธรรม เพราะบิตคอยน์มันเฟ้อไม่ได้ บิตคอยน์มันโกงไม่ได้
ตัวของมันจึงสามารถมอบโอกาสแก่พวกเราให้ไม่ซ้ำรอยความผิดพลาดในอดีต เพราะเมื่อผมส่งบิตคอยน์ ผมได้ส่งมันไปจริง ๆ และมันหายไปจากมือของผมจริง ๆ
ซึ่งนั่นเป็นคุณสมบัติสร้างการแลกเปลี่ยนที่ยุติธรรม ซึ่งจะนำไปสู่ระบบเศรษฐกิจที่ยุติธรรม

บิตคอยน์นั้นมีคุณสมบัติที่จะเป็นเงินที่ยุติธรรม และมีจริยธรรม ด้วยเหตุผลหลาย ๆ ข้อ ซึ่งหนึ่งในนั้นเป็นการที่ มันมีจำกัด
หากถามว่าสิ่งนี้สำคัญอย่างไร คำตอบคือคุณสมบัตินี้ของมันนี่แหละที่จะป้องกันการโกงมูลค่าได้ ไม่เหมือนกับกับเงินที่ถูกโกงมูลค่าหรือเฟ้อขึ้นได้ในปัจจุบัน มันเป็นเงินที่คุณจะไม่ได้นั่งเฉย ๆ แล้วได้รับมันมาด้วยฟังชั่นการงอกเงยของมัน
เรารู้ว่าบิตคอยน์มีปริมาณเท่าไหร่ มันโปร่งใส ตรวจสอบได้ มีภูมิต้านทานการเซนเซอร์ มันสามารถเข้าถึงใครก็ได้บนโลกที่เข้าถึงอินเตอร์เน็ต
มันไม่เกี่ยงเลยว่าคุณคือใคร มีฐานะอย่างไร ตราบเท่าที่คุณสามารถเข้าถึงอินเตอร์เน็ตได้ มันเปิดกว้างมาก และจริง ๆ ผมก็สามารถสร้างระบบ หรือสร้างธุรกิจบนพื้นฐานของบิตคอยน์โดยที่ไม่ต้องขออนุญาตใครทั้งสิ้น
มันทั้งไร้พรมแดนและเป็นสิ่งที่สวยงามยิ่ง ผมจะส่งเงินไปใครใครในโลกก็ได้โดยที่ไม่ต้องคิดเลยว่าเขาอยู่ที่ไหน หรืออยู่ในระบอบปกครองแบบใด ผมแค่ส่ง และผมแค่รับ
อีกข้อหนึ่งคือ มันกระจายศูนย์ เป็นอีกหนึ่งคุณสมบัติที่ทำให้ข้ออื่น ๆ ของบิตคอยน์นั้นทำงานได้จริง ยกตัวอย่างเช่นการกระจายเงินอย่างเท่าเทียมผ่านการขุด ไม่ใช่การกระจายเงินไปสู่คนเพียงหยิบมือที่มีใบอนุญาตเปิดธนาคารได้ แต่เป็นทุก ๆ คนที่ต้องทุ่มแรงเพื่อที่จะได้มันมา ซึ่งนั่นก็ย้อนกลับไปถึงปัญหาเกี่ยวกับจริยธรรมของเงินที่มีคนที่สามารถมีอำนาจในการสูบความมั่งคั่งไปจากเราได้โดยไม่ต้องขออนุญาต
และสิ่งสุดท้ายเลยคือ เงินมันไม่จำเป็น หรือจริง ๆ คือมันไม่มีผลตอบแทน หรือ yield ใด ๆ เพื่อรักษานโยบายทางการเงินของมัน


แล้วไอ้เจ้าการที่เงิน มันมีผลตอบแทน มันงอก มันเฟ้อได้ มันผิดอะไรกันหละ
เราสามารถแจกแจงปัญหานี้ออกมาได้สองข้อใหญ่ ๆ คือ
หนึ่ง คือเงินนั้น คือเครื่องมือในการวัดมูลค่าของสิ่งของ
ผมมอบเงินให้กับผู้ขายเพื่อซื้อมูลค่าที่เขาเสนอมา มันเป็นแค่หน่วยวัด เพื่อให้เกิดการซื้อขาย เพื่อที่ผมจะซื้อของที่จำเป็น มันเป็นเพียงแค่นั้น ถ้างั้น แล้วพอเงินมันมีผลตอบแทนได้หละ มันก็จะเฟ้อ เปรียบเหมือนกับคุณพยายามที่จเป็นนักวิทยาศาสตร์แล้วต้องการทดลองปฏิกิริยาทางเคมีบางอย่าง คุณต้องใช้ปิกเกอร์ แต่ถ้าเราบอกว่ามาตรวัดของปิกเกอร์นั้นมันเปลี่ยนไปตลอดในทุกครั้งที่คุณหยิบมันขึ้นมาหละ ใช่ปิกเกอร์นั้นมันอาจจะใช้งานได้ในระยะสั้น แต่ในระยะยาว อย่าหวังเลย เราไม่สามารถให้มาตรวัดถูกควบคุมหรือแทรกแทรงโดยมนุษย์ได้ โดยเฉพาะกับเจ้าตัวเงินที่เฟ้อได้นี่
สอง เงินที่เฟ้อให้ผลประโยชน์กับพฤติกรรมนักล่า
สมมุติว่าผมให้คนยืมเงินแล้วเขาสัญญาว่าจะนำมาคืนใน 5 ปี คุณไม่สามารถให้หากคุณไม่คิดดอกเบี้ย หรือได้รับผลประโยชน์อะไรบางอย่างตอบแทนที่คุ้มค่า มันไม่ใช่เจตจำนงของเราแต่เป็นสภาพบังคับเพราะว่าเงินของเราเสื่อมค่าลงทุกวัน เมื่อเป็นเช่นนั้น คุณไม่สามารถซื้อของที่คุณต้องการซื้อได้อีกแล้วด้วยเงินที่เขานำมาคืนเมื่อครบสัญญาเพราะของมันแพงขึ้น
แล้วถ้าหากเป็นเงินที่ไม่เฟ้อหละ มันให้ผลประโยชน์กับพฤติกรรมที่เป็นกุศล เพราะเงินที่ผมให้ยืมไป เมื่อผมได้รับคืน ผมสามารถซื้อของที่ผมอยากได้ใน 5 ปีก่อนได้ตามปกติ จริง ๆ แล้ว นี่อาจจะนับเป็นการให้เขานำเงินของเราไปดูแลแทนเราก็ได้ เราไม่จำเป็นต้องตักตวงผลประโยชน์ใด ๆ เพื่อความอยู่รอดอีกต่อไป
ผมเชื่อว่า บิตคอยน์ เป็นเงินที่มีศิลธรรมมากที่สุด แต่ผมเชื่อว่าเราทำอะไรได้มากกว่านี้


ในโมเดลธุรกิจตามหลักศาสนาอิสลาม พวกเรามีระบบที่กำหนดว่าอะไรคือการแลกเปลี่ยนที่เป็นธรรม ผมพยายามที่จะหาคำอธิบายง่าย ๆ ให้ฟังแต่มันก็ยากพอควรเลยแหละ แต่โดยสรุปแล้ว มันคือ Capitalistic collectivism
Capitalistic collectivism คือหลักแนวคิดที่ว่า ไม่มีอะไรผิดในการเก็บเกี่ยวผลประโยชน์หรือสะสมทุน ตราบใดที่คุณยังคำนึงถึงกลุ่มคนหรือส่วนรวมในกระบวนการนั้น ซึ่งเมื่อมองย้อนกลับไปที่มุมมองต่อทุนนิยมของ Karl Marx ที่เน้นย้ำสุด ๆ เกี่ยวกับกระบวนการเก็บเกี่ยวสะสมทุนที่ตัดขาดมนุษย์ออกจากสมการทำให้ไม่ต้องแคร์ว่าพวกเขาจะทน เขาจะจน เขาไม่มีเงินจ่ายค่าเช่า ตราบใดที่ฉันได้กอบโกยทุนเข้ากระเป๋าฉันก็เพียงพอ
ซึ่งสำหรับการมองทุนนิยมในรูปแบบของ Capitalistic collectivism เรายังสามารถตักตวงผลประโยชน์ได้ โดยที่ไม่ทำให้ผู้คนเป็นทุกข์
มีคำกล่าวหนึ่ง ใครก็ตามที่มีสวนหลังบ้านแล้วผู้คนที่อาศัยอยู่ที่นั่นอดอยาก คุณในฐานะเจ้าของที่ดินจะถูกขับออกจากการปกป้องของ Allah นี่เป็นสิ่งที่มูฮัมมัดได้เคยตรัจเอาไว้ เป็นวิธีการที่เขาจะส่งเสริมให้คนที่มีทุนหรือมีที่ดิน มองกลับมาและให้ความสำคัญผู้คนที่อาศัยในที่ ๆ ของคุณด้วย คุณมีส่วนรับผิดชอบต่อความหิวโหยของพวกเขา เพราะสมมุติว่ามีใครมาเจอคนหิวอยู่ในสวนหลังบ้านคุณแล้วคุณไม่ทำอะไร คุณก็จะถูกตั้งคำถามและถูกติติง
อีกอย่างหนึ่งคือ ถ้าคุณให้ คุณจะร่ำรวย สำหรับเหตุผลของมันผมจะกลับมาอธิบายอีททีในเร็ว ๆ นี้ แต่จุดประสงค์ของคำกล่าวนี้ก็คือการส่งเสริมให้ผู้มีต้องคำนึงถึงผู้ที่ไม่มีด้วย เราจึงต้องทำให้แน่ใจว่าเราพยายามอย่างสุดความสามารถเพื่อที่จะแบ่งปันสิ่งที่เรามีแก่พวกเขา

สิ่งสุดท้ายเกี่ยวกับ Capitalistic collectivism คือการ ทำให้ความมั่งคั่งของเรานั้น ไม่ได้ถูกจำกัดและส่งต่อไปให้แต่กับผู้มากมี ซึ่งเอาจริง ๆ ผมพอเข้าใจในมุมมองของชาวบิตคอยน์ที่มักจะบอกกับทุก ๆ คนว่า
ถือไว้ ถือยาว ถือยาวแล้วดีต่อคุณ
แต่เราต้องคำนึงถึงด้วยว่าบิตคอยน์นั้นเป็นเงินสำหรับทุกคน ทุกคนจำเป็นที่จะสามารถเข้าถึง มี และครอบครองมันได้ เพราะว่าเราไม่อยากให้เจ้าบิตคอยน์นี้หมุนเวียนไปแต่กับบริษัทยักษ์ใหญ่ เพราะจริง ๆ แล้วพวกเราต้องการให้ทุกคนเข้าถึงบิตคอยน์

ในศาสนาอิสลาม เรามีคำว่า Zakaat ซึ่งผมจะวางมันเป็นสิ่งที่ตรงข้ามกับดอกเบี้ยเลย เพราะโดยความหมายแล้ว ดอกเบี้ย คือผลตอบแทนจากเงินที่ไม่ได้นำไปทำอะไร แต่สำหรับ Zakkat นั้น ผลตอบแทนจากเงินคือการนำเงินนั้นไปเพื่อเติมเต็มสังคม เพื่อแสดงความรับผิดชอบของผู้มีต่อผู้ที่ไม่มี

ความมั่งคั่งแล้วโดยธรรมชาติแล้วจะค่อยสูญเสียไปตามกาลเวลา เช่นการที่คนมีบ้าน เขาก็ต้องจ่ายเงินเพื่อดูแลบ้าน นั่นก็นับเป็นการสูญเสียความมั่งคั่งบางส่วนกลับสู่ธรรมชาติเช่นกัน สู่มือของคนที่เราจ้างมาให้ซ่อมบ้าน หรืออีกตัวอย่างคือรถ รถนั้นประกอบไปด้วยหลายชิ้นส่วน เมื่อเราต้องดูแลรถเราก็ต้องสละความมั่งคั่งของเขาไปให้อู่ซ่อมรถ ตามกฏของธรรมชาติ
ดังนั้นแล้ว ผลตอบแทนจากเงินที่ไม่ได้สร้าง Productivity ใด ๆ นั้นเป็นสิ่งที่ไม่เป็นไปตามกฏของธรรมชาติ เพราะนั่นหมายความว่าคุณกำลังสูบเอาความมั่งคั่งจากผู้อื่นเพื่อได้รับผลตอบแทนของเงิน ดังนั้นแล้ว ตามกฏของธรรมชาติ เงินควรที่จะลดลงและถูกส่งทอดลงสู่ผู้ที่จำเป็นต้องใช้มัน แล้วพวกเขาก็นำเงินเหล่านั้นซื้อสิ่งของที่ต้องการ แล้วนั่นก็จะนำประโยชน์กลับมาหาคุณไม่ว่าทางใดก็ทางหนึ่ง นี่ก็เป็นตัวอย่างที่สนับสนุนคำสอนที่กล่าวว่า จงให้ เพื่อที่จะได้รับ เป็นสิ่งปกติของการผ่องถ่ายความมั่งคั่ง

ในที่สุดเราก็มาถึงบทสรุปแล้ว ผมมีคำแนะนำหรือบรรทัดฐานว่าเราจะสร้างเศรษฐกิจที่มีจริยธรรมที่มากขึ้นได้อย่างไร
- เราต้องสร้างระบบนิเวศของเศรษฐกิจที่ชัดเจนโปร่งใส
- ได้รับในสิ่งที่คุณควรได้เท่านั้น
- จงเพิ่มมูลค่ากลับไปที่ระบบด้วย ไม่ใช่เอาแต่ดูดเอาผลประโยชน์เพียงอย่างเดียว
- จงให้ เพื่อที่จะได้รับ
- และอย่าให้บิตคอยน์หมุนเวียนอยู่กับแต่ผู้มากมี
เนื้อหาบรรยายโดย Mu'aawiyah Tucker เรียบเรียงและแปลโดย Techin
-
 @ 721be1b2:2cee7c6e
2024-10-17 10:21:00
@ 721be1b2:2cee7c6e
2024-10-17 10:21:00Nostr (short for "Notes and Other Stuff Transmitted by Relays") is a decentralised, censorship-resistant social network protocol designed for secure and private communication. It enables users to post notes and interact with others without relying on any centralised platform, unlike traditional social media platforms.
NIPs, or Nostr Implementation Possibilities, define the set of specifications or guidelines that clients and relays can follow to ensure the interoperability of all parts. This is the case with NIP-05, which defines an account verification mechanism by mapping Nostr public keys to DNS-based identifiers that resemble an email address.
Unlike the blue check mark on X.com, NIP-05 can be easily implemented by users for free. To get your account NIP-05 verified, you will need the following:
- Nostr public key in hex format
- Domain name that you own and manage (e.g., example.com)
- Nostr account name in an email-like format (e.g., johnnycage@example.com)
- Web server or a place to host a file from the domain name
For the Nostr public key in hexadecimal format, you can use the key converter tool at this link: https://damus.io/key/. Copy your user public key (npub) from your client and paste it in the link above to convert the key to hex format, i.e:
5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36Please note that some clients may not recognise your public key in hex format, and you may need to use your npub key instead.
Create a nostr.json file and paste the following: ``` { "names": { "johnnycage":"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36" } }
```
Upload the file to the web server and modify your DNS so your domain example.com is redirected to it. As a result, you should be able to access the file like this: https://example.com/.well-known/nostr.json
NIP-05 also defines how to handle CORS issues, since some Javascript based Nostr clients may be restricted by browser CORS policies, it is recommended to configure the web server to respond requests with the following header:
Access-Control-Allow-Origin: *As a final step, go to your Nostr client and configure your Nostr address for verification. In the case of the Amethyst client, this is done under Profile -> Nostr Address -> johnnycage@example.com. Once validated, a checkmark symbol should appear next to your chosen Nostr address.
Keep in mind that not all nostr clients behave the same, so you will need to adjust these steps based on your client of choice.
For more information about NIP-05, head here: https://github.com/nostr-protocol/nips/blob/master/05.md
nostr #nip #grownostr #howto #blog
-
 @ 5f550547:02612a84
2024-10-17 08:54:04
@ 5f550547:02612a84
2024-10-17 08:54:04Test Test Test ++Test++ ~~Test~~ * Test
- Test
Test
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ 6aa0e5a8:f1677da5
2024-10-17 06:49:02
@ 6aa0e5a8:f1677da5
2024-10-17 06:49:02Das Aufkommen von Sexpuppen stellt zweifellos eine große Herausforderung für das menschliche Konzept von Intimität dar und wirft eine Reihe von philosophischen und ethischen Fragen auf. Sie scheint unser traditionelles Verständnis vom Wesen der Intimität auf den Kopf zu stellen und wirft eine Reihe von philosophischen und ethischen Fragen auf.
Traditionell wurde Intimität als eine einzigartige Verbindung zwischen Menschen betrachtet, die auf gegenseitigem Verständnis, Vertrauen und emotionaler Bindung beruht. Sie impliziert einen wechselseitigen Austausch, Kommunikation und ein inhärentes Bedürfnis nach Empathie. Der intimen Beziehung zwischen Menschen und real sex doll fehlt jedoch offensichtlich diese wechselseitige emotionale Bindung und geistige Ebene. Sexpuppen können die innere Welt des Menschen nicht wirklich verstehen, und was sie bieten, ist nur eine äußere, oberflächliche und einseitige intime Erfahrung.
Daher wird die Auffassung vertreten, dass die intime Beziehung zwischen Sexpuppen und Menschen nur eine Art anthropomorphe Scheinbeziehung ist, die die intimen Bedürfnisse der Menschen auf der geistigen und emotionalen Ebene nicht befriedigen kann und die Entfremdung zwischenmenschlicher Beziehungen und die Selbstisolierung des Einzelnen sogar noch verstärken kann. Unter diesem Gesichtspunkt scheinen lebensgroße Sexpuppe die Intimität auf eine rein physische und utilitaristische Ebene zu reduzieren, was eine Verzerrung des Wesens der Intimität und der Grenzüberschreitung darstellt.
Es gibt jedoch auch die Ansicht, dass das Wesen der Intimität nicht statisch ist, sondern sich mit dem Wandel der Zeit und dem Fortschritt der Technologie ständig weiterentwickelt. Auch wenn Sexpuppen keine echte wechselseitige emotionale Verbindung herstellen können, erfüllen sie doch bestimmte Bedürfnisse des Menschen, wie z. B. die Verringerung der Einsamkeit, die Wiederherstellung des sexuellen Selbstbewusstseins und den Erhalt von physischem und psychischem Komfort. Daher kann Intimität, die auf Eigeninteresse beruht, auch als Ausdruck von Intimität betrachtet werden. Dies erweitert und bereichert die Bedeutung und Ausdehnung von Intimität.
Manche meinen sogar, wenn sich die Technologie der künstlichen Intelligenz so weit entwickelt, dass sie in Zukunft die menschliche Natur in hohem Maße simulieren kann und sex puppe die Fähigkeit zu autonomem Denken und aufrichtigen Gefühlen erlangen, kann dann die intime Beziehung zwischen ihr und den Menschen als echte intime Beziehung angesehen werden? Die Definition von Intimität muss dann möglicherweise neu überdacht werden.
Günstige sexpuppe, auch wenn sie klein sind, eröffnen eine neue Perspektive auf das seit langem bestehende Konzept der Intimität und haben viele interessante und tiefgreifende Überlegungen ausgelöst. Wir müssen die Veränderungen, die die Technologie für das menschliche Leben mit sich bringt, aus einer umfassenden Perspektive betrachten, eine offene und tolerante Haltung bewahren und die Bedeutung und die Grenzen von Intimität und die Natur des Menschen in einem rationalen Diskurs ständig neu untersuchen und definieren. Diese Art des kontinuierlichen Denkens und Umgestaltens wird uns voranbringen.
-
 @ 4ba8e86d:89d32de4
2024-10-17 03:43:26
@ 4ba8e86d:89d32de4
2024-10-17 03:43:26Distribuição segura do Linux de código aberto
O sistema operacional Linux Kodachi é baseado no Ubuntu 18.04.5 LTS, ele fornecerá a você um sistema operacional seguro, anti-forense e anônimo, considerando todos os recursos que uma pessoa preocupada com a privacidade precisa ter para estar segura.
O Kodachi é muito fácil de usar, tudo o que você precisa fazer é inicializá-lo no seu PC via unidade USB, então você deve ter um sistema operacional totalmente em execução com conexão VPN estabelecida + conexão Tor estabelecida + serviço DNScrypt em execução. Nenhuma configuração ou conhecimento de Linux é necessário de sua parte, nós fazemos tudo para você. Todo o sistema operacional funciona a partir de sua memória RAM temporária, portanto, depois de desligá-lo, nenhum vestígio é deixado para trás, todas as suas atividades são apagadas.
Kodachi é um sistema operacional ao vivo, que você pode iniciar em quase qualquer computador a partir de um DVD, pendrive ou cartão SD. Destina-se a preservar a sua privacidade e anonimato.
Características
Pronto para VPN
Tor Ready com seleção de nó de saída
DNScrypt pronto
Onion Circuits/Onion share
i2p
GNUNET
Carteira multimoeda Exodus
Rkhhunter
Guardião de Pares
Sala do pânico
Bleachbit
Átomo
audibilidade
Zulucrypt
Informações de sistema e segurança na área de trabalho
Wipe Ram
Limpe o espaço livre
Mate o sistema operacional!
Nautilus-wipe
Keepass2x
cavalo marinho
Gpa
Gnupg2Name
Enigmail
gufw
prisão de fogo
geany
Krusader
fundir
Obturador
Htop
Zulumount
FileZillaName
Exterminador do Futuro
Transmissão
Caixa Virtual
Syslinux-utils
Smbclient
dispersar
Fcitx
Ibus
pidgin
Coim
Anel
Sinal
Geoip-bin
Cais do Cairo
pcmanfm
Nmap
Xtrlock
Ncdu
Gksu
Sysv-rc-conf
Rdesktop
GnomeNettoolGenericName
Sinal
GResolver
OpenShot
Icedove
SiriKali
Denyhosts
Steghide
navegador da web Chromium
Gdebi
Comandante Gnomo
Visualizadores de imagens de luz Blender Viewnior e Risrtto
barulhento
Iridium-browser
raposa d'água
sincronizando
carteira jaxx
bomba nuclear
persistência
https://sourceforge.net/projects/linuxkodachi/
https://www.youtube.com/live/gCHjRQOTZmQ?feature=share
-
 @ 4ba8e86d:89d32de4
2024-10-17 03:29:13
@ 4ba8e86d:89d32de4
2024-10-17 03:29:13O MuPDF é uma biblioteca de software leve e de código aberto que oferece recursos avançados de visualização e manipulação de documentos. Desenvolvido pela Artifex Software, o MuPDF foi projetado para ser rápido, eficiente e altamente portátil, tornando-se uma escolha popular para aplicativos que exigem recursos avançados de renderização de documentos.
A história do MuPDF remonta ao ano de 2005, quando a Artifex Software iniciou o desenvolvimento dessa biblioteca para atender à necessidade de visualização rápida e eficiente de documentos em dispositivos com recursos limitados. Desde então, o MuPDF tem sido constantemente aprimorado e aperfeiçoado, ganhando reconhecimento por sua capacidade de processar e exibir uma variedade de formatos de documento de maneira eficiente.
Uma das principais características do MuPDF é sua arquitetura modular. Ele foi projetado para ser flexível e adaptável, permitindo que os desenvolvedores integrem facilmente seus recursos em seus próprios aplicativos. O MuPDF suporta uma variedade de formatos de documento, incluindo PDF, XPS, EPUB, CBZ, e mais. Essa versatilidade garante que os usuários possam visualizar e interagir com diferentes tipos de documentos de forma conveniente e eficiente.
Em termos de funcionalidade, o MuPDF oferece recursos avançados de renderização, permitindo uma visualização precisa e de alta qualidade de documentos. Ele suporta recursos como zoom, rotação, navegação por páginas e pesquisa de texto, oferecendo uma experiência de visualização interativa e intuitiva. Além disso, o MuPDF permite a extração de texto e imagens de documentos, facilitando a manipulação e o processamento de conteúdo.
Uma das vantagens do MuPDF é sua eficiência. Ele foi projetado para ter um desempenho rápido e usar poucos recursos do sistema, tornando-o ideal para dispositivos com capacidades limitadas, como smartphones ou tablets. Sua arquitetura otimizada garante uma inicialização rápida e uma resposta ágil às interações do usuário, proporcionando uma experiência de visualização de documentos suave e sem interrupções.
O MuPDF também é altamente customizável e extensível. Os desenvolvedores têm a liberdade de personalizar a interface e adicionar recursos específicos de acordo com as necessidades de seus aplicativos. Isso permite uma integração perfeita do MuPDF em diferentes contextos e cenários, tornando-o uma escolha versátil para uma ampla gama de aplicativos.
Uma das principais questões que o MuPDF resolve é a visualização eficiente de documentos em dispositivos com recursos limitados. Sua arquitetura leve e otimizada permite que dispositivos com baixa capacidade de processamento e memória possam exibir documentos de maneira rápida e eficiente. Isso é especialmente importante em um mundo onde os dispositivos móveis desempenham um papel central e a capacidade de visualizar documentos em movimento é fundamental.
Para os usuários, o MuPDF oferece uma solução confiável e eficiente para visualizar, interagir e manipular documentos. Seja lendo um livro eletrônico, revisando um contrato em formato PDF ou navegando por uma revista digital, o MuPDF fornece uma experiência de visualização suave e de alta qualidade. Sua capacidade de lidar com diferentes formatos de documento e sua eficiência em dispositivos com recursos limitados o tornam uma escolha valiosa para quem busca uma solução de visualização de documentos confiável e de alto desempenho.
O MuPDF é uma biblioteca de software que oferece recursos avançados de visualização e manipulação de documentos. Com sua arquitetura modular, eficiência, customização e suporte a vários formatos de documento, o MuPDF se destaca como uma solução poderosa para atender às necessidades de visualização de documentos em diferentes contextos e dispositivos. Seja para desenvolvedores que desejam integrar recursos de visualização em seus aplicativos ou para usuários que procuram uma experiência de visualização de documentos confiável e eficiente, o MuPDF é uma escolha sólida.
https://mupdf.com/
https://github.com/ArtifexSoftware/mupdf
-
 @ 4ba8e86d:89d32de4
2024-10-17 03:25:16
@ 4ba8e86d:89d32de4
2024-10-17 03:25:16Com uma interface intuitiva e poderosa, o Librera torna a experiência de leitura de e-books verdadeiramente agradável.
Algumas características principais do Librera incluem: - Descoberta fácil de documentos através de critérios configuráveis, incluindo verificação automática de pastas predefinidas e navegação com um explorador de arquivos no aplicativo. - Visualização de documentos recentes com indicador de progresso de leitura. - Suporte para marcadores, anotações e índices EPUB3. - Conexão com nuvens e catálogos online, e sincronização entre dispositivos Android via Google Drive para progresso de leitura e favoritos. - Modos dia e noite configuráveis, incluindo cor de link personalizável para notas de rodapé e notas finais. - Suporte para dicionários populares online e offline, bloqueio de rolagem vertical e centralização automática e manual de documentos. - Possibilidade de inserir código CSS personalizado, visualização de página única de documentos de duas páginas e modo de músico com velocidade de rolagem ajustável. - Leitura TTS personalizável e reprodutor de mídia integrado, pesquisa de texto com várias palavras e conversão de documentos online. - Leitura de documentos arquivados (.zip) e suporte para idiomas RTL (tailandês, hebraico, árabe, etc.). - Importação e exportação de configurações, backup automático da sessão atual e iniciais principais em documentos FB2.
Com o Librera Reader, é fácil criar bibliotecas auto-mantidas de documentos, selecionando os formatos a serem incluídos e as pastas a serem digitalizadas. A biblioteca pode ser visualizada em forma de lista ou grade, com capas de miniaturas ajustáveis e descrições detalhadas para identificação dos documentos. A organização da biblioteca pode ser feita por caminho, nome, tamanho, data, etc., e um filtro auxilia na busca por documentos específicos ou grupos. Durante a leitura, os documentos podem ser bloqueados em modo de rolagem vertical e navegados por página ou tela. É possível reformatar o texto e fazer anotações, além de personalizar fontes e fundos através das configurações. Trechos selecionados podem ser traduzidos, compartilhados, copiados e pesquisados dentro do próprio documento ou na Internet.
https://github.com/foobnix/LibreraReader
https://f-droid.org/pt_BR/packages/com.foobnix.pro.pdf.reader/
-
 @ bad87238:1e92a734
2024-10-17 03:03:36
@ bad87238:1e92a734
2024-10-17 03:03:36Opinion about Kanga Wallet (iphone)
Caution should be exercised when dealing with investment firms , as i unfortunately experienced a significant loss with an online investment company . With the assistance of Againstcon. com , i was able to successfully track and recover my funds . Their intervention was pivotal in resolving the situation effectively
WalletScrutiny #nostrOpinion
-
 @ a012dc82:6458a70d
2024-10-17 01:30:04
@ a012dc82:6458a70d
2024-10-17 01:30:04Table Of Content
-
Whales and Sharks: The Big Players in the Crypto Ocean
-
June's Close: A Bullish Signal
-
Data-Driven Predictions: The Role of Crypto Intelligence
-
Whale Holdings: Keeping the Selling Pressure at Bay
-
Historical Trends: July as a Profitable Month
-
Conclusion
-
FAQ
The cryptocurrency market is a dynamic and rapidly evolving space, with Bitcoin (BTC) at its forefront. One of the key factors influencing the market's trajectory is the activity of large-scale investors, often referred to as 'whales' and 'sharks.' These entities hold substantial volumes of digital assets, and their investment decisions can significantly sway market trends. Recently, these influential players have been doubling down on their Bitcoin investments, particularly as June 2023 drew to a close with BTC valued at an impressive $30,469. This article aims to explore this trend in detail, examining the potential implications for Bitcoin's future and the broader cryptocurrency market.
Whales and Sharks: The Big Players in the Crypto Ocean
In the vast and diverse ocean of cryptocurrencies, whales and sharks are the entities that hold large volumes of digital assets. Their actions, whether buying or selling, often have a substantial impact on the market, influencing price trends and investor sentiment. Over the past seven weeks, these large wallet investors have shown a strong appetite for Bitcoin, accumulating an impressive 154,500 BTC. The pace of this accumulation has notably picked up in the last two weeks. These investors have been capitalizing on market dips to increase their holdings, a strategy often referred to as 'buying the dip.' This trend suggests a strong confidence in Bitcoin's potential and could have significant implications for its future price trajectory.
June's Close: A Bullish Signal
June 2023 proved to be a significant month for Bitcoin, with the cryptocurrency closing at $30,469. This figure represents the highest monthly close for Bitcoin in the past thirteen months, a noteworthy milestone given the asset's volatility. This bullish signal has sparked optimism among investors and analysts alike, fueling a thesis for a potential recovery and upward trend for Bitcoin in the coming months. If this prediction holds true, it could mark a turning point for Bitcoin, potentially leading to increased investor interest and further price appreciation.
Data-Driven Predictions: The Role of Crypto Intelligence
In the complex and often opaque world of cryptocurrencies, crypto intelligence platforms like Santiment play a crucial role. These platforms track and analyze market trends, providing valuable insights into the behavior of large-scale investors and the overall market dynamics. According to Santiment's data, Bitcoin's whale and shark addresses accumulated a staggering 154,500 BTC within a seven-week period between April 2023 and the time of writing. The acceleration of Bitcoin accumulation in the past two weeks suggests a strong confidence in the asset's potential for recovery. This data-driven insight provides a valuable perspective on the market sentiment and could be a key indicator of Bitcoin's future performance.
Whale Holdings: Keeping the Selling Pressure at Bay
One of the intriguing aspects of the Bitcoin market is the concentration of holdings among whales. Bitcoin whale wallets, those holding between 10 and 10,000 tokens, now control 67% of the total supply of the asset. This concentration of holdings can be seen as a positive sign for Bitcoin. By holding onto a significant portion of the supply, whales reduce the selling pressure on the asset. This can create a more stable environment for price growth, as it reduces the likelihood of sudden price drops due to large-scale sell-offs. This dynamic could increase the potential for a recovery in Bitcoin's price and contribute to its long-term stability.
Historical Trends: July as a Profitable Month
Historical trends can often provide valuable insights into potential future market trends. For Bitcoin, the month of July has consistently proven to be profitable for holders over the last three years. This trend, coupled with the recent surge in whale accumulation, suggests that Bitcoin's price may recover from recent market fluctuations. These include the impact of the SEC's crackdown on crypto exchanges and increased regulatory scrutiny. If this trend continues, July could once again prove to be a profitable month for Bitcoin investors, potentially marking the start of a new upward trend.
Conclusion
The recent actions of Bitcoin whales and sharks, coupled with historical trends and market data, paint a promising picture for Bitcoin's future. The significant accumulation of BTC, the highest monthly close in over a year, and the potential for a profitable July all point towards a positive outlook for the asset. However, as with all investments, these trends should not be taken as definitive predictions. Market dynamics are subject to change, and investors should always conduct thorough research and consider various factors before making investment decisions. The world of cryptocurrencies is as exciting as it is unpredictable, and the actions of Bitcoin whales and sharks will continue to be a critical aspect to watch in the unfolding narrative of this digital asset.
FAQ
Who are Bitcoin whales and sharks? Bitcoin whales and sharks are large-scale investors who hold substantial volumes of Bitcoin. Their investment activities can significantly influence market trends.
What has been the recent trend among Bitcoin whales and sharks? Over the past seven weeks, Bitcoin whales and sharks have doubled down on their investments, accumulating 154,500 BTC, especially as June ended with BTC valued at $30,469.
What does June's closing value signify for Bitcoin? June 2023 closed with Bitcoin valued at $30,469, the highest monthly close in the past thirteen months. This has sparked optimism for a potential recovery and upward trend for Bitcoin.
What percentage of Bitcoin's total supply do whale wallets control? Bitcoin whale wallets, those holding between 10 and 10,000 tokens, now control 67% of the total supply of the asset.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-






















