-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-01 13:27:38
@ 4ba8e86d:89d32de4
2024-10-01 13:27:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 20986fb8:cdac21b3
2024-12-24 09:38:54
@ 20986fb8:cdac21b3
2024-12-24 09:38:54In this edition, we are pleased to speak with Luthando nostr:npub10vudmjqhr8kn2kv2pxhezt2h5t5c9zauwq8qr56nhdn64yacsqyqf08djm leader of the Bitcoin Ekasi community, about how they are using Bitcoin to transform payment systems, savings habits, and cross-border remittances in a South African township, while fostering digital currency education and boosting local economic trust.
YakiHonne: Luthando. We really appreciate you coming in. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. today. we'll be exploring more about your community.Can you tell us a bit about yourself? What do you do, and what’s your role in your community?
Luthando:I’m Luthando, a project community leader at Bitcoin Ekasi. My role includes onboarding township shops to help them adopt Bitcoin as a payment method. I also manage staff records, tracking workdays and paid leave for team members involved in the project. Additionally, I conduct interviews and collaborate with a supervisor to share insights and experiences about Bitcoin. This work is part of my efforts with Bitcoin Ekasi.

YakiHonne: You're really doing a lot of work in the Bitcoin ecosystem,what sparked your interest in Bitcoin? And what motivated you to create a community around it?
Luthando:When I was working as a safety coach at Safeacase, Herman introduced me to Bitcoin. During the COVID-19 pandemic, Safeacase, which relied on donations, faced severe financial challenges. This led to the launch of the Bitcoin Ekasi Project, where I helped township shops adopt Bitcoin as a payment method. With limited funds, I transitioned from receiving a fiat salary to earning in Bitcoin. Bitcoin transformed my mindset, making me realize it is the future of money. This realization inspired me to travel the world and explore new countries.
YakiHonne: Great. I really admire the enthusiasm you have for Bitcoin.Can you share a brief history of how you built your community and attracted members? What methods or advertisements did you use to onboard them?
Luthando:We host monthly Bitcoin movie nights to engage the community, running from February to December starting next year. We promote the events with posters in town, shops, and clinics, inviting residents to join. During the movie nights, participants use Bitcoin we provide to purchase popcorn and drinks, gaining hands-on experience with the technology. Luthando:And our Bitcoin center features a thrift shop and a small Bitcoin ATM. Community members can exchange fiat for Bitcoin using the ATM and use it to purchase clothing from the shop. We also offer Bitcoin courses with 14 students attending classes five days a week. To encourage attendance, students are rewarded with Bitcoin for consistent participation. Similarly, in the “Safer Kids” program, children who maintain a 70% attendance rate or higher also receive Bitcoin rewards. Luthando:To further promote Bitcoin adoption in the community, we painted Bitcoin-themed logos on 34 shops and paid the owners in Bitcoin, which they can use in local shops. This initiative not only spreads awareness but also provides the community with practical opportunities to use Bitcoin.

YakiHonne: Yeah, we are pushing Bitcoin adoption so hard this time. It's really great.What principles guide your community, and how do you ensure trust and reliability in your discussions?
Luthando:I was born in eastern South Africa, and my parents moved here around 1996. The community knows me well and trusts that I wouldn’t introduce anything fraudulent. Since 2010, we’ve been working in this township, especially helping children, building over a decade of trust. I explain to the community that we aim to bring value through Bitcoin, encouraging them to save in Bitcoin instead of fiat. As a result, the community has great trust in our Bitcoin Ekasi team.
YakiHonne: How do you educate your members and keep them updated on Bitcoin developments? You mentioned having five weekly meetups to onboard members, but what other methods do you use to educate them and keep them informed about the Bitcoin ecosystem?
Luthando:We use the Felly app to communicate with community members and keep them updated. At the Ekasi Center, we host quizzes to encourage participation. For example, the first attendees can earn 5,000 sats, motivating them to regularly engage with the Felly app. Although we initially tried a few other methods that didn't really involve them getting Sats, its impact was limited as many people in the township seek quick financial returns and often don’t return after their first visit. To address this, we host movie nights as a more engaging way to promote Bitcoin education. During these events, we screen Bitcoin-related films, allowing community members to learn about Bitcoin in a fun and relaxed setting.

YakiHonne: It's truly captivating and highly insightful.How does your community collaborate with the global Bitcoin ecosystem? Specifically, how does it engage with the broader worldwide Bitcoin community, and which partnership has been of more significant impact on Bitcoin Ekasi?
Luthando:We have established a strong partnership with Bitcoin Beach, which provided crucial support in the creation of the Bitcoin Ekasi project. Currently, we are planning to build a community center in the township, earning the trust and support of both Bitcoin Beach and the local government of Mossel Bay. The community center will serve as a multifunctional space for events like weddings and more. As one of the earliest Bitcoin adoption projects in Africa, Bitcoin Ekasi has inspired other countries to follow suit, viewing us as a model for building sustainable Bitcoin communities.
YakiHonne: How do you collaborate with Bitcoin communities and organizations outside South Africa? What partnerships or interactions do you have with other global Bitcoin communities?
Luthando: We collaborate with other Bitcoin projects through community initiatives. For example, we paint logos on local community shops and pay the owners 7000Sats per week. This approach has helped us build connections with projects outside South Africa. One notable example is our assistance to the Bitcoin Dua project in Africa, helping them establish a Bitcoin circular economy. We also supported the Bitcoin Loxin project in Cape Town, South Africa, in launching their Bitcoin circular economy. Through these collaborations, we have developed strong relationships with other Bitcoin communities.

YakiHonne: We’d like to understand the challenges you faced when starting the community, as well as the challenges the community has encountered?
Luthando: One of the main challenges is convincing members that Bitcoin is not a scam. Many people are skeptical about Bitcoin, fearing they might lose their money. Additionally, saving is not a common habit within the community, even with fiat currency. I often explain the importance of saving in Bitcoin, emphasizing how it can safeguard their financial security. However, changing deeply ingrained mindsets has proven to be quite difficult. Another challenge is the limited level of education in the community. Even those who own smartphones often struggle to use them effectively. This lack of familiarity extends to using Bitcoin wallets, with many people finding it challenging to navigate wallet usage, especially in shops. Lastly, I feel like I’m working around the clock. Even outside of work hours, people come to my house seeking assistance, such as exchanging Bitcoin for fiat. While I’m happy to help, the constant demands can feel overwhelming at times, making it seem as though I’m working every day, including weekends.
YakiHonne: and how you managed to overcome them?
Luthando: Overcoming these challenges is not easy. I can't say that I've fully managed to resolve them, but I do my best to address them. Fortunately, I have a colleague who assists me, although he’s currently out of town. He helps manage some of the workload, especially in dealing with local community members and providing them with the support they need.
YakiHonne: I'm really interested in the issue of people thinking Bitcoin is a scam. Could you elaborate on that? What specific steps have you taken to demonstrate that Bitcoin is reliable and not a scam?
Luthando: Many shop owners initially believe Bitcoin is a scam and refuse to accept it. To address their doubts, I demonstrate Bitcoin's legitimacy through practical examples. First, I help them download a Bitcoin wallet and post about it on X, receiving small tips from Bitcoin enthusiasts worldwide. I then use these tips to showcase Bitcoin's real-world applications. For instance, I use Bitrefill to purchase mobile airtime or fuel vouchers for them, highlighting Bitcoin's utility in daily life. I also mention South African restaurants like Steers that accept Bitcoin and even place food orders using Bitcoin to show its usability. Additionally, I demonstrate withdrawing cash from a crypto ATM using Bitcoin, further proving that it is a reliable financial tool and not a scam.
YakiHonne: You've done a lot of work in South Africa. I can imagine the effort, the pain and the stress.What initiatives has the community taken to promote Bitcoin adoption, and what results have these efforts achieved?
Luthando: At first, I never imagined we would reach this point. Now, many people frequently come to my home to ask how to buy Bitcoin. For example, this week, a man from Nigeria wanted to purchase Bitcoin worth 5,000 units. I explained the process to him and recommended using a hardware wallet for securely storing large amounts of Bitcoin. He used to struggle with sending money back home, but now he has realized the convenience of Bitcoin. In October last year, I helped two stores owned by Nigerians adopt Bitcoin payments. Since then, this practice has spread within the community, and more people, especially shop owners, have developed an interest in Bitcoin. They ask about its low transaction fees and have recognized it as an efficient solution for cross-border remittances. Initially, some shop owners were skeptical about Bitcoin, but they eventually started saving with it. Today, many of them have accumulated significant Bitcoin savings for their families and children, and they often express their gratitude for introducing Bitcoin to the community. Overall, the Bitcoin adoption project has had a profound impact here. We have educated the community about Bitcoin’s long-term savings value, and many people are now satisfied with this initiative and optimistic about the future.

YakiHonne: It’s clear you’ve achieved tangible results from your efforts. Looking ahead, what are your community's goals for the next 6 to 12 months? How do you plan to achieve them?
Luthando: For Bitcoin Ekasi, one of our main goals is to establish a dedicated Bitcoin Ekasi Center. This center would serve as a hub to educate people about Bitcoin on a frequent basis. We have already started working with a local school in the township, recruiting students and introducing teachers to Bitcoin. Our vision is to integrate Bitcoin education into the school’s curriculum, similar to what has been done in El Salvador. By incorporating Bitcoin as part of their regular subjects, students can gain foundational knowledge about Bitcoin and its potential uses. Ultimately, we aim for teachers to become advocates who can confidently teach children about Bitcoin, empowering the next generation with essential financial literacy skills.
YakiHonne: Thank you so much! I think most of my questions have been answered. I’m really glad to see Bitcoin enthusiasts with a clear focus on Bitcoin. As you said, Bitcoin is the future, and I truly appreciate your enthusiasm for it.
Luthando: Bitcoin is truly the future. We want to see this township transformed into something more modern, rather than its current state. I hope to see more parents saving some Bitcoin for their children. In our community, most kids receive a monthly government allowance of $50 starting from the age of one. I often suggest to parents that they set aside half of that allowance to buy Bitcoin for their child. If they save consistently from age one to 18, the value could grow significantly as Bitcoin appreciates. I’m already doing this for my own child so that he will have savings as he grows up.
YakiHonne: Bitcoin is the future. Its value continues to grow steadily over time. Thank you so much for today’s conversation; we are truly honored. Your sharing of such rich experiences has been incredibly insightful for us. I’ve learned that using movie events to engage more people is an excellent idea, and we plan to start trying it out soon. Once again, thank you for your time and for sharing with us!
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 6bcc27d2:b67d296e
2024-12-25 07:18:08
@ 6bcc27d2:b67d296e
2024-12-25 07:18:08問い合わせ番号: C00033712277
[2024-12-06] - 21:11 これから[[伊豆大島]][[フルマラソン]]へのフェリー。![[Pasted Image 20241206211138.jpeg]]竹芝客船ターミナルに向かって歩いてる
- 21:14 ![[Pasted Image 20241206211453.jpeg]]
- 21:20 ![[Pasted Image 20241206212053.jpeg]]
- 21:28 ![[Pasted Image 20241206212843.jpeg]]
- 21:44 フェリーに乗った ![[Pasted Image 20241206214435.jpeg]]![[Pasted Image 20241206214442.jpeg]]![[Pasted Image 20241206214447.jpeg]]
- 22:22 展望デッキが綺麗 ![[Pasted Image 20241206222051.jpeg]]![[Pasted Image 20241206222117.jpeg]]![[Pasted Image 20241206222138.jpeg]]![[Pasted Image 20241206222202.jpeg]]
当日 - 05:59 下船 ![[Pasted Image 20241207055912.jpeg]]
- 06:06 ![[Pasted Image 20241207060556.jpeg]]
- 06:27 バスに乗って会場に着いた ![[Pasted Image 20241207062701.jpeg]]
- 06:30 参加者には10km、ハーフマラソン、フルマラソンの選択肢があり、[[フルマラソン]]が圧倒的に最も多い ![[Pasted Image 20241207063019.jpeg]]
- 06:37 [[2024-12-07 伊豆大島フルマラソン]] ![[Pasted Image 20241207063727.jpeg]]
-
08:00 ![[Pasted Image 20241207080054.jpeg]] スタート
-
08:03 ![[Pasted Image 20241207080318.jpeg]]
- 08:17 ![[Pasted Image 20241207081730.jpeg]]
- 08:51 ![[Pasted Image 20241207085109.jpeg]]
- 08:52 ![[Pasted Image 20241207085239.jpeg]]
- 09:15 ![[Pasted Image 20241207091518.jpeg]]
- [ ] 09:16 ![[Pasted Image 20241207091658.jpeg]]
- 09:20 ![[Pasted Image 20241207092005.jpeg]]
- 09:38 ![[Pasted Image 20241207093843.jpeg]]
- 09:48 ![[Pasted Image 20241207094804.jpeg]]
- 09:51 ![[Pasted Image 20241207095133.jpeg]]
- 09:58 ![[Pasted Image 20241207095840.jpeg]]
- 10:01 ![[Pasted Image 20241207100112.jpeg]]
- 10:30 ![[Pasted Image 20241207103011.jpeg]]
- 10:35 ![[Pasted Image 20241207103518.jpeg]]
- 11:13 ![[Pasted Image 20241207111306.jpeg]]
- 11:26 ![[Pasted Image 20241207112647.jpeg]]
- 12:57 経験したことがない足の痛さ ![[Pasted Image 20241207114610.jpeg]]
- 12:57 完走
-
13:07 ![[Pasted Image 20241207130724.jpeg]] 完走後の味噌汁
-
13:51 温泉へ
- 15:02 ![[Pasted Image 20241207150143.jpeg]] 大島の子供たちはみんなこれで育った
- 15:07 ![[Pasted Image 20241207150751.jpeg]]
- 15:32 じゃんけん大会が始まった。景品が紹介されている ![[Pasted Image 20241207153215.jpeg]]
- 16:01 ![[Pasted Image 20241207155736.jpeg]] 「大将」に入る https://maps.app.goo.gl/xd1iXZ4pDaZsQafy7?g_st=ic 豚丼セットそばを注文
- 16:08 ![[Pasted Image 20241207160818.jpeg]]
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 16d11430:61640947
2024-12-25 05:17:20
@ 16d11430:61640947
2024-12-25 05:17:20Aiyyo! Ever felt like your operating system was missing that extra punch of masala? Look no further! AiyyoOS is here to spice up your digital life with the perfect blend of Tollywood drama, Kollywood action, Mollywood brilliance, and Sandalwood charm. Here's why AiyyoOS is the Rajinikanth of all operating systems:
Features:
🌴 Coconut Kernel: Powered by the latest "Idli v1.0" kernel, it's so lightweight that even your grandma’s old Nokia could run it.
🎥 Tollywood Task Manager: Multitasking? Don't worry, this Task Manager handles chaos like a proper Telugu movie hero – one-click, 100 tasks done!
💃 Dance-Off Notifications: Every time you get an alert, Allu Arjun will pop up on your screen for a mini "Pushpa step." Beat that, iOS!
🍛 Masala Customization: From spicy Chettinad themes to Kerala mural wallpapers, personalize your OS with more options than a South Indian wedding buffet.
📡 Signal Boost: Your Wi-Fi bars will always be full because it’s powered by "Anna Satellite Network" – signals even reach Chennai's Marina Beach on a rainy day!
🎤 Voice Assistant: Siri-ka Akka: Meet “Sundari,” the assistant who greets you with, "Aiyyo, enna venuma?" (What do you need?) and never misunderstands your accent.
Default Apps:
🎥 "Blockbuster" Media Player – Plays every song with DSP-level bass and AR Rahman-level vibes.
🔥 VadaChutney Browser – So fast, even Prabhas couldn’t keep up with its speed in Salaar.
📜 Rajini Terminal – Every command you type ends with a punch dialogue like, "Naan eppovume correct-a thaan iruppen!"
AiyyoOS Editions:
-
The Baahubali Edition – For high-performance PCs. (Why download one app when you can conquer them all?)
-
The Lungi-Linux Edition – Budget-friendly for your recycled laptops. (Saves resources, just like that one lungi you’ve been using since 2012.)
-
Thalaiva Ultra Edition – Pre-installed with Superstar wallpapers and "super-fast bootup" that completes before your filter coffee brews.
Coming Soon:
An update called Dosa Drive – Your cloud storage as crispy and flexible as your favorite dosa!
Disclaimer: Not responsible for random Kolaveri moments or neighbors joining your party when Sundari starts blasting AR Rahman hits at full volume.
Install AiyyoOS today, and may your computing life be as flavorful as a piping hot plate of biryani! Aiyyo!
-
-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ 7ed5bd1c:4caa7587
2024-12-25 03:30:08
@ 7ed5bd1c:4caa7587
2024-12-25 03:30:08Proof of Work: พื้นฐานของความน่าเชื่อถือใน Bitcoin
Bitcoin ไม่ได้มีธนาคารกลางหรือองค์กรใดคอยควบคุม แต่ความปลอดภัยและความน่าเชื่อถือของมันมาจากสิ่งที่เรียกว่า "Proof of Work" หรือ PoW ซึ่งเป็นกระบวนการที่นักขุด (miners) ใช้ในการตรวจสอบและยืนยันธุรกรรมบนเครือข่าย นี่คือหลักการที่ช่วยสร้างความไว้วางใจและความโปร่งใสในระบบกระจายศูนย์ (decentralized system) นี้
Proof of Work คืออะไร?
Proof of Work เป็นกลไกที่ทำให้ทุกคนในเครือข่าย Bitcoin เห็นพ้องต้องกันเกี่ยวกับสถานะของบัญชีหรือธุรกรรม โดยใช้พลังงานคอมพิวเตอร์ในการแก้สมการทางคณิตศาสตร์ที่ซับซ้อน เมื่อมีการแก้สมการสำเร็จ ธุรกรรมจะถูกยืนยันและเพิ่มลงในบล็อกเชน ซึ่งเปรียบเสมือนสมุดบัญชีสาธารณะที่ทุกคนสามารถตรวจสอบได้
การขุด Bitcoin สำคัญอย่างไร?
-
สร้างความปลอดภัยให้กับเครือข่าย: Proof of Work ช่วยป้องกันการโจมตี เช่น การใช้จ่ายเงินซ้ำ (double spending) หรือการปลอมแปลงธุรกรรม เนื่องจากการปลอมแปลงต้องใช้พลังงานและทรัพยากรมากจนแทบจะเป็นไปไม่ได้
-
กระจายอำนาจ: การขุดทำให้ไม่มีองค์กรใดสามารถควบคุมเครือข่ายได้ทั้งหมด เพราะใครก็ตามที่มีฮาร์ดแวร์และไฟฟ้าก็สามารถเข้าร่วมได้
-
สนับสนุนการออก Bitcoin ใหม่: Bitcoin ใหม่ถูกปล่อยออกมาผ่านกระบวนการขุด ซึ่งจะเกิดขึ้นทุก ๆ 10 นาที และช่วยรักษาอัตราการผลิต Bitcoin ให้คงที่
ความสำคัญของ Proof of Work ต่อระบบ Bitcoin
Proof of Work ไม่เพียงแค่ช่วยสร้างความน่าเชื่อถือ แต่ยังช่วยให้ระบบมีความยุติธรรมและโปร่งใส เนื่องจากทุกคนสามารถตรวจสอบข้อมูลในบล็อกเชนได้ และกระบวนการขุดยังเป็นสิ่งที่ทำให้การเปลี่ยนแปลงข้อมูลในอดีตเป็นไปได้ยาก
ความเข้าใจผิดเกี่ยวกับ Proof of Work
บางคนมองว่าการใช้พลังงานของ Proof of Work เป็นเรื่องสิ้นเปลือง แต่ในความเป็นจริง การใช้พลังงานนี้เป็นสิ่งที่จำเป็นเพื่อสร้างความปลอดภัยให้กับเครือข่าย Bitcoin และช่วยสร้างมูลค่าของมัน
ข้อดีของ Proof of Work
-
ความปลอดภัยสูง: การแก้สมการต้องใช้พลังงานมาก ทำให้การปลอมแปลงบล็อกเชนแทบเป็นไปไม่ได้
-
โปร่งใส: ทุกคนในเครือข่ายสามารถตรวจสอบธุรกรรมได้
-
สร้างแรงจูงใจ: นักขุดได้รับรางวัลเป็น Bitcoin ซึ่งกระตุ้นให้คนเข้าร่วมเครือข่าย
Proof of Work เป็นหัวใจสำคัญที่ทำให้ Bitcoin ยังคงน่าเชื่อถือในโลกดิจิทัลที่มีความซับซ้อน แล้วคุณล่ะ คิดว่า Proof of Work มีความสำคัญแค่ไหนต่ออนาคตของการเงิน? ร่วมพูดคุยกันได้ในความคิดเห็น!
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ bcea2b98:7ccef3c9
2024-12-25 03:11:27
@ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas!
originally posted at https://stacker.news/items/823433
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 16d11430:61640947
2024-12-23 16:47:01
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 70e6b44a:7c78b8e9
2024-12-25 00:53:04
@ 70e6b44a:7c78b8e9
2024-12-25 00:53:04the melão is a fruit.
-
 @ 6ad3e2a3:c90b7740
2024-12-20 09:35:27
@ 6ad3e2a3:c90b7740
2024-12-20 09:35:27This event has been deleted; your client is ignoring the delete request.
-
 @ 70e6b44a:7c78b8e9
2024-12-25 00:52:39
@ 70e6b44a:7c78b8e9
2024-12-25 00:52:39the maçã is not a fruit at all.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 330516bf:ea23d292
2024-12-20 03:35:09
@ 330516bf:ea23d292
2024-12-20 03:35:09The self-declaration of identity is a philosophical open source project, hosted at https://memdeklaro.github.io/
Foreword
ID documents do more harm than good and should not be seen as a solution for trust or authentication. Many economic and social interactions can be done anonymously. For other situations, trust can be achieved by simply saying your (self-chosen) name, using a web-of-trust, word-of-mouth reputation, vouches, memberships, escrows or cash deposits, and authentication can be achieved by using a password, cryptographic key pair (e.g. PGP, Monero) or physical key or code (such as house keys or a safe code).
Background
In recent years, more and more things are asking for proof of identity, from basic necessities like jobs, housing and healthcare, to smaller things like receiving mail, buying a sim card or joining a gym. However, it is not enough to write your name and address on a form. Instead, only government-issued IDs are accepted, which gives the state a “monopoly on identity”.
Monopolies are dangerous in general due to the fact that if the service provider is harmful, inaccessible or otherwise problematic, you cannot choose a different provider, start your own provider, or go without. This particular monopoly is even worse, considering that access to government ID determines if you may participate in the economy (jobs, banking), society (housing, volunteer work, education, libraries, sports) or even exist (national borders).
Many people have no access to government ID. This group includes some stateless people, refugees, people who weren’t registered at birth, and people who escaped from child abuse, domestic abuse or cult abuse. The state’s claimed solutions, such as asylum procedures, stateless determination procedures, delayed registration of birth, child protective services and witness protection, often cannot help in practice, as the victim is often ignored, accused of lying, blamed for the persecution, or worse sent back to the persecutors against their will. Despite issuing laissez-passer and Nansen passports in the past, the United Nations and Red Cross do not issue alternative IDs today. It would be a relief if these processes would work and allow vulnerable people to escape from undeserved and dangerous situations, but unfortunately this is not the reality.
In addition, the collectivist concept of citizenship can be dangerous. For example, if someone does not identify with their birth culture, they should not be forced to follow it for life or identify themselves as a member of this culture. Instead, they should be free to dissent against this culture or leave this culture’s jurisdiction. Even worse is conscription — the cruel system where a nation-state can force someone against their will to kill or be killed, just because they happened to be born inside a certain territory. The world would be more free if people could exist as individuals, conscientious objectors against the fatalism of birth cultures and violence of statism, with freedom of association to leave hostile environments and join self-chosen communities.
“The blood of the covenant is thicker than the water of the womb.”
Self-declaration of identity gives people the power to decide their own fate. People are no longer the property of nations, governments, birth cultures or birth parents. The choice of your own name and renunciation of your circumstances of birth is a liberating act of individualism, where your ideals, actions and efforts matter more than the situation that you were arbitrarily born into.
Self-declaration of identity
Instead of requiring third parties such as birth countries, birth cultures and birth parents to define an individual’s identity, the self-declaration allows you to define your own name and eschews the concepts of birth countries and citizenship.
The self-declaration is a CR-80 plastic card or paper business card (85.6mm x 54mm). The self-declaration is written in Esperanto and includes the Esperanto flag and symbol. Esperanto was chosen because it is anational (sennacieca = not associated with a specific country, culture or state) and was created as a borderless language of peace, built on voluntary free association. The design features artwork of a peace dove in a blue sky with clouds.
As it is a self-declaration, it is not stored in a central database, does not require a third party’s permission and does not need to be issued by an authority. You are the authority over your own life.
The self-declaration includes the text:
- Title: Self-declaration of identity (Memdeklaro de identeco)
- Location: Esperanto community (Esperantujo)
- Issuer: EPO (ISO code for Esperanto)
- Quote: One world, one humankind (Unu mondo, unu homaro)
The self-declaration of identity contains:
- Self-chosen first name (Antaŭnomo) and self-chosen surname (Nomo) → an individual should be able to freely choose their own name
- Birth date (Naskiĝdato) → for declaration of age
- Photo → Dimensions 35mm x 45mm
- Signature (Subskribo) → sign your self-declaration
- Notes field (Notoj) → a place to write a note, e.g. “the holder is a conscientious objector” (Portanto estas konscienca obĵetanto)
- ID number (Numero), issuance date (Eldondato), expiry date (Limdato), issuer (Eldonisto), MRZ → bureaucratic boilerplate
The self-declaration of identity does not contain:
- Place of birth → allows people to cut ties with hostile environments and self-define their culture, beliefs and personal ties
- Citizenship or stateless status → allows people to cut ties with hostile governments or cultures, and exist as an individual instead of as property of a state that they did not choose
- Parents’ names → allows victims of child abuse to cut ties with abusers
To make your own:
- Use the generator at https://memdeklaro.github.io/ or download the repo (https://github.com/memdeklaro/memdeklaro.github.io/) and open index.html in your browser
- Alternatively download the front template (fronto.jpg) and back template (dorso.jpg) from the linked repo, and use an image editor such as GIMP to add your text (the font OCR-B.ttf is provided) and your photo and signature
- Calculate the MRZ code here (TD1): https://www.dynamsoft.com/tools/mrz-generator/ (Choose any country, then replace it with EPO)
- Print it out as a business card and optionally laminate (dimensions: 85.6mm x 54mm) or order a CR-80 plastic card from a printing service
Example:

Note:
Unfortunately the self-declaration of identity cannot be used to bypass government ID requirements, such as for jobs, housing, healthcare, finances, volunteer work, contracts, receiving mail or buying a sim card. Other non-government IDs such as Digitalcourage Lichtbildausweis (https://shop.digitalcourage.de/gadgets/lichtbildausweis-mit-selbst-waehlbaren-daten.html) and World Passport (https://worldcitizengov.org/what-is-the-world-passport/) have the same limitations.
Nation-states’ refusal to print IDs for undocumented, stateless and unregistered people (while forcing government ID requirements on employers, landlords, doctors and more) can and does put innocent people’s lives in danger. But unfortunately even the United Nations has not been able to change this, despite issuing conventions on statelessness and refugee status in the 1950s.
Further Reading
For further reading about identity (and why the state’s monopoly is harmful):
Passports Were a “Temporary” War Measure — Speranta Dumitru https://fee.org/articles/passports-were-a-temporary-war-measure
During World War II, we did have something to hide — Hans de Zwart https://medium.com/@hansdezwart/during-world-war-ii-we-did-have-something-to-hide-40689565c550
The Little-Known Passport That Protected 450,000 Refugees — Cara Giaimo https://www.atlasobscura.com/articles/nansen-passport-refugees
With each person left living on the streets, we are losing as a society — Petr Baroch https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society
The rarely discussed dangers of KYC and what you can do about it — Anarkio https://vonupodcast.com/know-your-customer-kyc-the-rarely-discussed-danger-guest-article-audio
Exclusion and identity: life without ID — Privacy International https://www.privacyinternational.org/long-read/2544/exclusion-and-identity-life-without-id
Proving who I am: the plight of people in detention without proof of legal identity — Vicki Prais https://www.penalreform.org/blog/proving-who-i-am-the-plight-of-people/
Establishing identity is a vital, risky and changing business — The Economist https://www.economist.com/christmas-specials/2018/12/18/establishing-identity-is-a-vital-risky-and-changing-business
What’s in a name? The case for inclusivity through anonymity — Common Thread https://blog.twitter.com/common-thread/en/topics/stories/2021/whats-in-a-name-the-case-for-inclusivity-through-anonymity
True Names Not Required: On Identity and Pseudonymity in Cyberspace — Der Gigi https://dergigi.medium.com/true-names-not-required-fc6647dfe24a
Citizenship is obsolete — Samuela Davidova https://medium.com/@DavidovaSamuela/citizenship-is-obsolete-c36a20056752
License
Public Domain
Source code: https://github.com/memdeklaro/memdeklaro.github.io
Infographic

Translations
(Machine translated)\ Memdeklaro de identenco: self declaration of identity, autodeclaración de identidad, autodeclaração de identidade, autodéclaration d’identité, autodichiarazione di identità, autodeclararea identității, Selbsterklärung zur Identität, eigen verklaring van identiteit, Selvdeklaration af identitet, självdeklaration av identitet, egenerklæring om identitet, henkilöllisyysvakuutus, Isikuandmete esitamine, identitātes pašdeklarēšana, savęs deklaravimas, önbevallás a személyazonosságról, własna deklaracja tożsamości, vlastní prohlášení o totožnosti, vlastné vyhlásenie o totožnosti, samoprijava identitete, самодеклариране на самоличността, самопроголошення ідентичності, самозаявление о личности, αυτο-δήλωση ταυτότητας, pernyataan identitas diri, öz kimlik beyanı, الإعلان الذاتي عن الهوية, 身份自报, 身份自報, 自己申告, 신원 자기 선언
...
-
 @ 63d59db8:be170f6f
2024-12-18 16:24:11
@ 63d59db8:be170f6f
2024-12-18 16:24:11I am Oana, a fine-art photographer with a deep passion for capturing nature's fragile resilience. My work has been recognized internationally, featured on platforms such as CNN Style, Forbes, and Amateur Photographer, and honored by the Sony World Photography Awards. With over 25 years of creative experience, I focus on blending fine-art aesthetics with ecological storytelling to highlight the beauty, complexity, and vulnerability of our natural world.
For this submission, I’ve selected some of my finest works, which reflect my ongoing exploration of flora in their natural environments. These images celebrate the interplay of light, texture, and motion, capturing moments that reveal the unique personalities of flowers and plants without interference. My goal is to foster an emotional connection between viewers and the overlooked beauty of the natural world.
This work represents my artistic vision of combining visual poetry with a deeper narrative about sustainability and our relationship with the environment. Each photograph is a window into nature’s story, inviting viewers to engage with its raw, unfiltered essence.






Submit your photographs to our Visual Expression awards. Current prize is $130 / 125,140 sats.
Learn more and enter here. Deadline is December 31, 2024!

-
 @ 4657dfe8:47934b3e
2024-12-18 13:42:46
@ 4657dfe8:47934b3e
2024-12-18 13:42:46Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.
Simplifying Bitcoin Wallets for Friends and Family
Alby Hub empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
How to provide a wallet to Friends and Family?
- Open your Hub and find the Friends & Family app in the App Store
- Enter a name e.g. your friend’s name and click “Create subaccount”
- Share the Connection Secret with your friend for the different options
Here are two examples how your the new subaccount can be used.
Alby Go mobile App
Alby Go makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
Here’s how to set it up: 1. Open the Alby Go Mobile App tab in your Hub.
 2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.
2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
Get a Lightning Address with an Alby account
An Alby Account offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
To set up an Alby account for someone:
-
Open the Alby Account tab in your Hub.
-
Copy the provided URL and share it with your friend.
-
Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
Onboarding Family & Friends Made Easy In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for subaccounts in Alby Hub! If you have ideas for improvement,let us know.
- Open your Hub and find the Friends & Family app in the App Store
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ 266815e0:6cd408a5
2024-12-17 20:45:33
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
Features
Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on
k:1063events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
New support view
The (tiny) support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
Favorite DVM feeds
You can now favorite DVM feeds in the discover view
Tools under notes
There is now a simpler tools menu under notes and threads
Searching local cache relay
If your using nostr-relay-tray the search view will now use it by default for searching. which should make it a little faster and more reliable
Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel (677 changed files with 19,683 additions and 17,889 deletions) and extracting it out into a friendly nostr SDK called applesauce
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the Getting Started docs
-
 @ 6ad3e2a3:c90b7740
2024-12-16 15:28:00
@ 6ad3e2a3:c90b7740
2024-12-16 15:28:00I believe in the notion of truth. Not merely propositional truth like 2 + 2 = 4, though that too, but also the idea that what someone says can be authentic, profound and true.
Another aspect of truth is beauty. I think music can be harmonious and art aesthetically true. I don’t claim to have special knowledge over what is true, beautiful or harmonious, only that those things exist, and human beings can discern them. I also believe in justice which in my view is moral truth.
Truth, beauty and justice exist even if we are not personally able to recognize them. In other words, while they are perceptible to human beings generally, any particular person or group might miss them.
One example that comes to mind is if you renovate a home. You and your architect might disagree about the layout. Imagine he persuades you to trust him, and you discover he was correct, the house is more harmonious, proportionate and beautiful than had you done it your way. The aesthetic truth for that house was not what you had imagined, but it existed, and you were lucky someone else had the eye for it.
. . .
I don’t write much about what’s going on in Israel and Palestine because I’m not interested in it. I’m not interested in it because it doesn’t affect my immediate existence, and those who are interested in it mostly seem to be closed-minded and emotional about the topic. Because I am not into it, I am not especially informed, nor am I inclined to inform myself better. As far as I can tell, it’s a depressing and tiresome argument between two miserable factions.
That said, the topic sometimes comes up in part because I’m Jewish and know a lot of Jews who care about it and also because I follow people on Twitter on both sides who also care about it. For that reason, I’m aware of some of the narratives that are presented and consequently I’ve formulated two main ideas about it, two axioms, so to speak:
(1) Whatever is the just (morally true) result — whether Israel shutting down and leaving the region, Israel conquering and annexing Palestinian territories entirely, or more likely something in between — that's what I would like to see happen.
In other words, no matter how much anyone in particular might disagree with it, the just result, whatever it might be, is the outcome for which I’m rooting.
People will argue for what they think is just based on various narratives, but I hope for what is actually just, irrespective of those narratives. And I believe such a result must exist, even though I am in no position whatsoever to say what that result would be.
(2) To the extent some people think Palestinians are incorrigible barbaric terrorists and others think Israel (and even "the Jews" more broadly) are incorrigible genocidal maniacs, consider that sense of incorrigibility is directed by both parties at both parties.
In other words, at least one of you* incorrectly believes the other is inherently beyond redemption, and just as they would be mistaken in believing that about you, you could also be mistaken in believing it about them. In fact, the greater your certainty about their inherent evil, the more difficult it is for you to course-correct, and the closer to their description you actually become. Paradoxically, the more sure you are of who they are, the more correct they are about you.
Before anything approaching a concrete answer to this problem can emerge, I think it's important to realize (1) A just outcome that does not depend on anyone's narrative exists; and (2) That the extent to which you view your adversaries as beyond redemption you most resemble their description of you.
If we accept these two axioms, that justice is possible, and that viewing the other side as incorrigible is a hallmark of one’s own zealotry, we have established the ground upon which a solution is possible. If we reject them, no amount of discussion will ever bear fruit.
*Some people might think both are beyond redemption, in which case this post is moot, and there is no just outcome, only might makes right. I think that kind of cynicism is the road to hell.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ 4c86f5a2:935c3564
2024-12-15 00:07:15
@ 4c86f5a2:935c3564
2024-12-15 00:07:15เวลาที่มีในชีวิตเปรียบได้กับโอกาสที่เข้ามาในช่วงที่ Bitcoin ยังอยู่ในช่วงเริ่มต้น หากไม่รีบฉวยโอกาสในตอนนี้ เราอาจต้องเสียโอกาสในอนาคตไป เช่นเดียวกับคนที่มอง Bitcoin เป็นโอกาสที่สายเกินไปในการเก็บออม #siamstr
-
 @ a950ba55:02f4f8c9
2024-12-25 00:28:46
@ a950ba55:02f4f8c9
2024-12-25 00:28:46عملت جينيت بلونديل دون ترخيص أو رقابة لصالح مجرم الحرب المزعوم رفعت الأسد.
أدى انهيار نظام الأسد في سوريا إلى موجات من الصدمة في جميع أنحاء العالم، وكان ذلك بمثابة نهاية ديكتاتورية تركت الدولة في حالة يرثى لها. فبالإضافة إلى القمع الوحشي خلال الحرب الأهلية التي دامت عقداً من الزمن في البلاد، تشمل التهم الموجهة ضد عائلة الأسد الفساد المنهجي على نطاق مذهل.
ويُزعم أن أفراد العائلة قد نهبوا مئات الملايين من الجنيهات من الشعب السوري. وقد تم تحويل هذه الأموال من قبل أسطول من المحامين وخبراء الضرائب ومقدمي خدمات الائتمان في الخارج إلى إمبراطورية عقارية كبيرة: شقق فخمة تطل على نهر السين، وقصر فخم في مايفير، وفيلات منتشرة في جميع أنحاء كوستا ديل سول.
واليوم، يستطيع مكتب الصحافة الاستقصائية (TBIJ) وصحيفة الغارديان كشف النقاب عن بريطاني ساعد في إدارة تلك الملايين نيابة عن رفعت الأسد، عم بشار والرجل المعروف باسم ”جزار حماة“ لدوره المزعوم في الإشراف على السجن غير القانوني والتعذيب والإعدام لما بين 10 آلاف و40 ألف شخص في عام 1982.
وفي مارس/آذار، أصدرت هيئة الرقابة المالية في غيرنسي، وهي جزيرة صغيرة تابعة للتاج البريطاني، غرامة قدرها 210,000 جنيه إسترليني ضد جينيت بلونديل، وهي من سكان غيرنسي، وتبلغ من العمر 40 عامًا، ومنعتها من تولي مناصب مختلفة ذات مسؤولية مالية لمدة تسع سنوات. وقالت إنها خالفت قانون غيرنسي مرارًا وتكرارًا في عملها لصالح عملائها، وأحدهم عائلة الأسد.

وقد أخفت الجهة الرقابية اسم موكل بلوندل، لكنها أشارت إلى أنه ”مجرم حرب مزعوم“ و”مجرم حرب مزعوم“. ينص الإشعار التنظيمي على أن بلوندل كانت على علم بالادعاءات الخطيرة ضد موكلها واستمرت في العمل لديه بين عامي 2013 و2020، دون ترخيص من الرقابة التنظيمية. ولكن على الرغم من الغرامة الكبيرة والحظر الطويل، يبدو أن بلوندل لم تواجه أي ملاحقة جنائية.
وقال فيليب غرانت، المدير التنفيذي لمنظمة ترايال الدولية، التي كانت أول من تقدم بشكوى جنائية ضد الأسد في سويسرا: ”إن جرائم رفعت الأسد، لا سيما مجزرة حماة عام 1982، هي من بين أخطر الفظائع في عصرنا“. ودعا غرانت إلى اتخاذ تدابير مساءلة أقوى، بما في ذلك الملاحقات الجنائية والعقوبات المهنية.
إن السهولة التي قام بها مجرم حرب مشتبه به بتحويل مئات الملايين من الدولارات التي يُزعم أنها اختلست من الأموال العامة السورية إلى أوروبا تسلط الضوء بشكل صارخ على نهج القارة المتراخي في التعامل مع غسيل الأموال في العقود الأخيرة. كما يسلط الضوء أيضاً على كيفية قيام المملكة المتحدة والأقاليم التابعة للتاج البريطاني وأقاليم ما وراء البحار التابعة لها بتقديم الخدمات التي مكنت بعضاً من أكثر اللصوصية البغيضة في العالم.
وتأتي هذه الاكتشافات في الوقت الذي تنتظر فيه غيرنسي نتائج التقييم الأخير الذي أجرته هيئة Moneyval، وهي هيئة تابعة لمجلس أوروبا تتحقق من ضوابط غسل الأموال وتمويل الإرهاب في الولايات القضائية في جميع أنحاء القارة. وكان آخر تقرير لهيئة الرقابة في عام 2015 قد وجد أن الملاحقات القضائية والإدانات في غيرنسي بتهمة غسيل الأموال كانت ”منخفضة بشكل غير متناسب“ بالنظر إلى حجم نظامها المالي، الذي احتفظ هذا العام بأصول بقيمة 300 مليار جنيه إسترليني تقريبًا.
إمبراطورية الثروة لم تظهر أي آثار لماضي بلوندل علنًا منذ أن أصدرت الهيئة التنظيمية عقوبتها، حيث تم محو وجودها على الإنترنت. وأشار التقرير إلى أن بلوندل قد حصلت على درجة الماجستير في حوكمة الشركات وبدأت العمل في قطاع الخدمات المالية في غيرنسي في عام 2000.
وفي إحدى الشركات الخاضعة للتنظيم، التقت لأول مرة بعائلة رفعت الأسد، الذي كان يشكل ”99%“ من عملها في الشركة وفقًا للجهة المنظمة في غيرنسي.
طُرد رفعت من سوريا في عام 1984 بعد محاولة الانقلاب على شقيقه حافظ، والد بشار وحاكم البلاد آنذاك. قضى رفعت الأسد معظم العقود التالية في المنفى. ولا يُعتقد أنه كان له يد في القمع الذي حدث خلال الحرب الأهلية التي بدأت في عام 2012. لكن الثروة الهائلة التي جمعها كانت قد نهبت إلى حد كبير من الأموال العامة السورية في الثمانينيات.

وبعد فراره إلى أوروبا، استمر في تكديس إمبراطورية عقارية ذات أبعاد مذهلة.
فقد وجدت السلطات أنه وأفراد أسرته استحوذوا على 507 عقارات تبلغ قيمتها الإجمالية حوالي 700 مليون يورو، متخفين وراء شركات وهمية، بما في ذلك في الأراضي البريطانية مثل جبل طارق وجزر فيرجن البريطانية.
وكانت هذه الممتلكات مملوكة لشركات كان من بين مديريها زوجات الأسد وأبناؤه المتعددين - ولكن لم يكن الرجل نفسه تقريبًا.
اشترت العائلة مئات العقارات، العديد منها في كوستا ديل سول في إسبانيا، بما في ذلك فيلا بقيمة 60 مليون يورو (51 مليون جنيه إسترليني) في بلدة بيناهافيس، على بعد نصف ساعة بالسيارة من ماربيا.
وفي لندن، أصبح آل الأسد المالكين السريين لأكبر مسكن في العاصمة بعد قصر باكنغهام، وهو منزل شاسع في هايغيت في لندن قُدّرت قيمته ب 300 مليون جنيه إسترليني. وباع أفراد عائلة الأسد هذا المنزل في عام 2007، متخفين وراء شركة وهمية في بنما، لكنهم استحوذوا على قصر في مايفير قد تصل قيمته الحالية إلى 60 مليون جنيه إسترليني.
وفي باريس، استحوذت عائلة الأسد على أكثر من 40 شقة تطل على نهر السين، وأثثت قصراً من سبعة طوابق يقع في شارع فوش - وهو شارع كبير يؤدي إلى قوس النصر - بأثاث تزيد قيمته عن مليون جنيه إسترليني.
التحقيقات والملاحقات القضائية لطالما ادعى الأسد أن ثروته مشروعة - هبة من العائلة المالكة السعودية. ولكن في لائحة اتهام صدرت في عام 2019 وجد المدعون الإسبان أن الجزء الأكبر من ثروته جاء من 300 مليون دولار من أموال الدولة السورية والقروض التي دفعها له شقيقه حافظ في الثمانينيات.
كما اتهمه المدعون الإسبان أيضًا بأنه حصل على ”موارد ضخمة غير مشروعة من أنشطة إجرامية متعددة: الابتزاز، والتهديد، والتهريب، ونهب الثروات الأثرية، واغتصاب العقارات، والاتجار بالمخدرات“.

كانت لائحة الاتهام تلك نتيجة واحدة من التحقيقات الجنائية العديدة التي أُجريت بشأن ثروة آل الأسد التي بدأت في جميع أنحاء أوروبا خلال السنوات السبع التي ظل فيها بلونديل يعمل لدى العائلة.
في عام 2014، وبعد شكوى من منظمة شيربا غير الحكومية المعنية بحقوق الإنسان، أطلق المدعون العامون الفرنسيون تحقيقًا في غسيل الأموال ضد الأسد كشف عن حجم إمبراطورية ممتلكاته. وفي عام 2016، صادرت السلطات الفرنسية ممتلكاته. وحذت إسبانيا والمملكة المتحدة حذوهما، على الرغم من أن السلطات البريطانية تأخرت كثيرًا في منع بيع قصر في ساري بقيمة 3.7 مليون جنيه إسترليني كان يشغله أحد أبنائه، وفقًا لصحيفة التايمز.
في يونيو 2020، أدانت محكمة جنائية فرنسية الأسد بتهمة غسيل الأموال واختلاس الأموال العامة السورية وحكمت عليه بالسجن لمدة أربع سنوات. وفشل طعنان على الحكم، لكن الأسد لم يرَ زنزانته من الداخل - فقد فر إلى سوريا في عام 2021. (ظل بلونديل يعمل مع العائلة حتى مارس 2020، أي قبل ثلاثة أشهر فقط من الإدانة). وخلال فترة مماثلة، كان المدعون السويسريون قد بدأوا تحقيقًا في مزاعم قيام الأسد بذبح عشرات الآلاف من الأشخاص في حماة، وهي حادثة تم الإبلاغ عنها على نطاق واسع في الوقت الذي بدأت فيه بلونديل عملها غير المنظم لصالحه في عام 2013.
في مقابلات رسمية، رفض الأسد التحدث، لكنه لطالما نفى هذه الادعاءات. في عام 2021، أصدر المدعون السويسريون مذكرة توقيف دولية ضد الأسد، وفي هذا العام اتهموه رسمياً بارتكاب جرائم حرب.
بالإضافة إلى ذلك، حاول المدعون الإسبان محاسبة الأسد. واتهمته لائحة اتهام صدرت في عام 2019 بارتكاب جرائم ”بشكل منهجي وصناعي“ لإثراء نفسه. وجاء فيها أن الأسد، على الرغم من استخدامه لزوجاته وأبنائه كوكلاء له في إمبراطوريته العقارية، إلا أنه احتفظ ”بالسيطرة والهيمنة المطلقة على عمليات الاستحواذ“.
ومع ذلك، يبدو أنه لم يتبع ذلك أي ملاحقة قضائية.

وفي الوقت نفسه، تجاوزت مهام بلونديل لصالح العائلة مجرد التوقيع على الأوراق، وفقًا للجهة التنظيمية في غيرنسي. في 23 أكتوبر 2015، تلقت دفعة بقيمة مليون يورو في حسابها المصرفي الشخصي، اسميًا لتأسيس شركة استئمانية في غيرنسي. ولكن الشركة لم تتحقق أبدًا.
ومع ذلك، لم تقم بلونديل بإعادة المبلغ. وبدلاً من ذلك، استخدمته لتسديد أكثر من 150 دفعة لأطراف ثالثة مختلفة.
وقالت الهيئة التنظيمية إن هناك ”خطرًا حقيقيًا للغاية يتمثل في أن السيدة بلوندل ربما تكون قد استخدمت لغسل عائدات الجريمة، وهو خطر فشلت السيدة بلوندل باستمرار في إدراكه“.
”لقد فشلت السيدة بلوندل باستمرار في فهم خطورة وعواقب أفعالها.“
وقالت الدكتورة سوزان هاولي، المديرة التنفيذية لمنظمة تسليط الضوء على الفساد: ”في أكثر حالات غسيل الأموال فظاعة... يجب استخدام الثقل الكامل للقانون لخلق رادع حقيقي.
”إذا كانت دول مثل المملكة المتحدة وتوابعها التابعة للتاج ... مستعدة فقط لاستخدام التدابير التنظيمية مثل الغرامات وإسقاط الأهلية، فلا يمكنها أن تأمل في ردع غسل الأموال القذرة بشكل كامل من خلال أنظمتها المالية.“
ورداً على سؤال عن سبب عدم مقاضاة بلوندل، قال متحدث باسم ولاية غيرنسي للمكتب الاستقصائي للمعلومات والاتصالات للصحافة الاستقصائية إن الولاية القضائية تتعامل مع جرائم غسل الأموال بجدية بالغة.
وقال المتحدث: ”في هذه الحالة تحديداً، اتخذت [الهيئة التنظيمية] إجراءات جادة ضد هذا الشخص، حيث فرضت عليه غرامة كبيرة جداً ومنعه من العمل في هذا المجال“.
”ومع ذلك، وكما يدرك الأشخاص العاملون في قطاع إنفاذ القانون جيدًا، فإن عتبة الأدلة للملاحقة الجنائية وعتبة اتخاذ الهيئة التنظيمية للإجراءات تختلف تمامًا.“
وتابعوا: ”كما هو الحال في جميع المسائل الجنائية، يجب إثبات الجريمة المزعومة بالمعايير الجنائية العالية من أجل نجاح أي ملاحقة قضائية. وفي حالة عدم وجود أدلة كافية للمضي قدمًا بعد إجراء تحقيق كامل، يتم إغلاق القضية.“
وقد أخبر متحدث باسم الهيئة التنظيمية، وهي هيئة الخدمات المالية في غيرنسي، للمكتب الاستقصائي للمعلومات والاتصالات أنها تأخذ معالجة الجرائم المالية على محمل الجد.
لم ترد جينيت بلونديل ورفعت الأسد على طلبات متعددة للتعليق.
مقال مترجم، إضغط هنا لقراءة المقال الأصلي.
-
 @ eac63075:b4988b48
2024-12-14 22:06:10
@ eac63075:b4988b48
2024-12-14 22:06:10BlueSky, a social network built on the decentralized AT Protocol (Authenticated Transfer Protocol), is revolutionizing content moderation by empowering users and communities to manage their own experiences. Unlike traditional platforms that centralize control, BlueSky adopts a modular and customizable approach, balancing freedom of expression with safety.
https://www.fountain.fm/episode/mtp0RxPeuBpCozcSgfct
The Jesse Singal Case and the Community’s Response
Recently, the account @jessesingal.com was accused of publishing content considered homophobic and transphobic. Although some users questioned whether these posts violated BlueSky’s Terms of Service, the platform chose not to ban the account. Instead, it relied on community tools to limit the reach of these posts.
Individual users blocked the account and subscribed to community-managed block lists, significantly reducing the visibility of Jesse Singal’s content. This decentralized approach demonstrated the effectiveness of a model in which the community regulates content without centralized intervention.
BlueSky’s Five Layers of Moderation
BlueSky implements a multi-layered moderation system, offering users tools to customize their experiences practically and efficiently:
-
Personal Blocking and Muting\ Users can block or mute unwanted accounts, individually adjusting the content they wish to see.
-
Community Block Lists\ By subscribing to block lists created by the community, users can share common moderation criteria, optimizing content filtering.
-
Curated Feeds\ Subscribing to personalized feeds allows users to consume content filtered by curators or algorithms, creating a safer and more tailored experience.
-
Account Removal on the Personal Data Server (PDS)\ In extreme cases, servers can directly delete accounts from their databases, preventing them from publishing or accessing the network.
-
Ozone: Advanced Moderation Tool\ Ozone is an integrated tool that enables advanced moderation strategies, combining various resources for greater efficiency.
BlueSky’s Moderation Architecture
Moderation on BlueSky is based on an open labeling system. This architecture allows anyone to assign labels to content or accounts, such as “spam” or “NSFW” (not safe for work). These labels can be automatically generated by third-party services or manually applied by curators and administrators, offering flexibility for communities and individuals to customize their experiences.
The Role of the Community in Content Regulation
In decentralized platforms like BlueSky, the community plays a central role in self-regulation, minimizing reliance on a centralized authority to moderate content. This decentralization distributes responsibilities and reduces the risks of institutional bias, often seen in centralized companies that may reflect specific interests at the expense of plurality.
Centralized platforms often censor or promote content based on corporate agendas, compromising user trust. BlueSky’s model prioritizes autonomy, allowing the community itself to determine what is relevant or acceptable.
With 25 million users registered within weeks, BlueSky remains committed to its mission of regulating not freedom of expression, but the reach of certain publications. Tools like block lists, curated feeds, and Ozone are tangible examples of how the platform is building a decentralized and inclusive ecosystem.
Challenges and Opportunities of Decentralization
Despite its merits, decentralization presents challenges. Educating users about available tools and protecting vulnerable communities from harmful content are complex tasks, especially in a rapidly growing environment.
On the other hand, the decentralized model offers significant advantages. It enhances transparency, fosters trust among users, and reduces reliance on a central authority. On BlueSky, users shape their own experiences, ensuring greater freedom without sacrificing safety.
Conclusion
BlueSky is paving the way for a new era in social networks with a decentralized moderation model that empowers users and promotes shared responsibility. Aligned with principles of freedom and inclusion, BlueSky combines advanced technology and community collaboration to create a safer, more democratic, and adaptable space.
Although still in its early stages, BlueSky offers a promising model for the future of social networks, where reach—not freedom of expression—is the true focus of regulation.
-
-
 @ 9349d012:d3e98946
2024-12-14 09:59:48
@ 9349d012:d3e98946
2024-12-14 09:59:48Reflections on my 26th Time Paddling Out
December 2024, North Shore of Oahu Kingdom of Hawai'i
I'm watching the waves. Mother Nature is in charge and can change her mind seemingly on a whim. Surfing is a game of patience, slowly learning the sport while building endurance.
I just paddled out for the 26th time since starting to surf in 2020, when I moved to Oahu for three months and lived on the North Shore for most of that time.
What have I learned? I often think entrepreneurship is like surfing. Staying in the game, making the choice to be there and stay relevant and show your worth. Staying up, doing what it takes. Strength. Having fun, being profitable and marketing what you do to inspire others.
Since then, I’ve lived on Oahu for 2-3 months a year most years, coming up on ten months total now. Besides surfing Chuns Reef, Malaekahana, Waikiki Beach, Publics and Baby Queens, I’ve been planning my coworking and coliving around the world at locations where there are beginner surf breaks. Nosara and Santa Teresa, Costa Rica, Freights Bay, Barbados, La Jolla Shores, San Diego and Ponto, Encinitas/Leucadia/Carlsbad. Kedungu, Bali. Canary Islands. Biarritz. More place around Waikiki, Freddys on a small day and even my sister’s pool. It's lifestyle.
After this 26th time out surfing, I sense real progress. There’s often months between each surfing session, and even so, the skills accumulate. Now I get up on every run, and stay on the board. It’s fun. My photographer says I'm doing something that not many can do. His words are a Wow 🤩 a wake o wonder and add to the adrenaline rush.
If I were to really continue with my surf workouts, and move to a place where it’s easy to surf any time the conditions are good, I could get really good. Single-minded purpose is needed.
Surfing, like entrepreneurship, is a sport where what you put in is what you get out.
By the way, I’m writing this from a picnic table in the Ehukai / Pipeline beach parking lot, and the Vans Pipe Masters competition is on. The women paddled out earlier to today, where four heats of surfing happened. There 20 women competing in this year’s contest, and 40 men. Surfing stats have come a long way in recent years.
Can VC funding stats for women also see such progress? I say yes, as our product goes next level. I cover the building in public of MyLibrarian in other blogs, so you see. In short, I’ve done the work.
Our product has thousands of users in beta, we've applied for a provisional patent and we're looking to clear $1M in revenue in 2025. Surfing our way to success and better book recommendations, freedom to read for all.
Curiously, I have not surfed in my home city of San Francisco, or its environs. Too cold? Can I adapt? I'm home now, for good.
On Playa Hermosa near Ste Teresa CR, I paddled out with Del Soul surf company and the instructor said to me, You are very lucky, you are a woman who surfs. You will always be healthy if you surf.
Healthy, in body, mind and spirit. Healthy is wealthy. That’s a worthy goal. I think I’ll keep going.—MEZ
Read more at https://www.michellezaffino.com/why-surfing-makes-me-a-better-entrepreneur/
-
 @ ece127e2:745bab9c
2024-12-11 21:54:31
@ ece127e2:745bab9c
2024-12-11 21:54:31La palabra anarquía proviene del griego y significa sin gobierno; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.La palabra anarquía proviene del griego y significa sin gobierno; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.
Los anarquistas se sirven ordinariamente de la palabra Estado para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos.
En este supuesto la palabra Estado significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones abolir el Estado, sociedad sin Estado, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales.
La palabra Estado tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.Los anarquistas se sirven ordinariamente de la palabra Estado para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos.
En este supuesto la palabra Estado significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones abolir el Estado, sociedad sin Estado, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales.
La palabra Estado tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.
Hemos dicho anteriormente: «Anarquía es la sociedad sin gobierno». ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse?
¿Qué es el gobierno?
La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna.
Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder.
Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.Hemos dicho anteriormente, que la «Anarquía es la sociedad sin gobierno».
Ahora bien: ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? Veamos:
¿Qué es el gobierno?
La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna.
Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder.
Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.
source : https://es.anarchistlibraries.net/library/errico-malatesta-la-anarquia
-
 @ e83b66a8:b0526c2b
2024-12-11 09:16:23
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-
 @ 26838110:80edc65d
2024-12-10 12:32:43
@ 26838110:80edc65d
2024-12-10 12:32:43Using Nostr as a Blog through Npub.pro
Now that X.com is closed and cannot be freely accessed without account anymore, creators and companies need a new way to broadcast updates and gather feedback from users.
Our Needs
We had first two major requirements. The first one was to have a way to publish updates and have the possibility for anyone to reply to them.
The second major requirement was to have these posts available online and indexable by search engines.
Nostr
After trying Warpcast and looking into Threads, Mastodon and Bluesky, we chose Nostr to chronicle the development of the world and game of Dragonbane Creation.
Nostr is perfect for our needs for serveral reasons:
-
Posts are publicly accessible and available in a variety of clients.
-
Posts are not linked to a single platform and they cannot be boosted or deboosted.
-
Posts can be easily read and written programmatically.
-
Once Nostr is more widespread, it also means that posts can be indexed by search engines and can count as multiple SEO links (one for each indexed client).
Npub.pro
Having notes is only one part of the equation to have a blog based on Nostr. The second part I discovered relatively quickly after I started posting on Nostr. Npub.pro is a way to create a free website to display notes and have them available as standalone pages with a comment section in a customizable theme.
What I love about Npub.pro are how easy it is to customize the blog and the ability to self-host.

After setting up our blog, I also tried recreating a basic version on the main Dragonbane Creation website as I already had the code to interact with Nostr in Javascript. However, I decided to keep using Npub.pro in order to avoid having to maintain the code for a blog and as it fulfills all of our needs and to self host it.
The downsides of using Npub.pro are that it is extremely slow to load, even when self-hosting and using a good CDN. It also lacks important customization options such as a way to disable comments and zapping.

If you want to set up your own, you can do it here:
https://npub.pro/#themes-onboarding
If you want to see how our blog looks like:
https://blog.dragonbanecreation.com
grownostr #npubpro
-
-
 @ 26838110:80edc65d
2024-12-10 08:38:42
@ 26838110:80edc65d
2024-12-10 08:38:42The development of the game is going well.
I am developing all the systems at once to ensure that all of the foundations are well-made from the beginning and don't need to be reworker later.
All of the 3D components are now ready in their most basic form, including the ability to build custom ships.

The 3D engine is now integrated with the interface and both can access the same information. This makes creating the minimap trivial. The asteroid field has been tested with 20000 asteroids at 60FPS.

Space will also have locations to explore and random encounters with other ships.

The ship creation will not be based on voxels like here but will have a basic elements on which other components can be attached.

The heightmap is already integrated with the Physics engine (Havok). The yellow box is a cave entrance to test switching location and the purple box is a trader to test dialogs.
If you access the website from a desktop, you can test part of it here: game
-
 @ eac63075:b4988b48
2024-12-08 15:35:21
@ eac63075:b4988b48
2024-12-08 15:35:21Imagine a large public square, illuminated by intense spotlights, where every individual who dares to approach the center is immediately recognized, photographed, and cataloged. In this square, every word spoken becomes indelibly tied to its speaker. Under such conditions, many would hesitate before speaking, fearing not only the disapproval of the audience but also the potential punishments that could follow the mere act of expressing an idea. Now, imagine a second square, where anyone can cover their face with a mask, allowing their voice to echo without revealing their identity. It is in this second square that true freedom of expression flourishes, and this metaphorical mask represents anonymity.
https://www.fountain.fm/episode/MweciiR21hySxjdsNa7u
In debates about freedom of expression—one of the fundamental pillars of democratic societies—anonymity often emerges as a controversial element. For some, it serves as a refuge for digital criminals or slanderers. For others, it is an indispensable tool, capable of protecting dissenting voices and inspiring authentic debates, with ideas judged on their merits rather than the messenger’s reputation. This article aims to explain, in a clear and instructive manner, why anonymity is essential to genuine freedom of expression, illustrating its value with metaphors, real-life examples, and historical references.
The Protective Mask: Avoiding Retaliation and Threats
Just as a navigator uses guiding instruments to avoid jagged rocks at sea, anonymity functions like a shield, allowing bold voices to navigate oppressive reefs without foundering. There are countless examples of individuals who have risked their lives to expose crimes and injustices—from whistleblowers in authoritarian governments to investigative journalists uncovering the complex machinations of organized crime. Without the possibility of anonymity, many of these stories would never have come to light.
Organizations like the Electronic Frontier Foundation (EFF) and other digital rights advocacy groups emphasize that the ability to speak without revealing one’s identity is crucial when the cost of speaking out is dangerously high. In censorship-ridden regimes, criticizing the government can lead to imprisonment, torture, or even death. Human rights activists, LGBTQIA+ communities in hostile countries, and journalists investigating illicit dealings all rely on anonymity to continue their work without putting their own lives at immediate risk. In this context, anonymity is not a whim—it’s the chance to survive one’s own opinion.
The Voice of the Invisible: Empowering Marginalized Groups
Think of anonymity as an invisible microphone placed at the disposal of those who, without it, would never dare to take the stage. Historically, marginalized groups have always faced additional barriers to making their voices heard. Women in patriarchal societies, ethnic minorities facing discrimination, or individuals persecuted for their sexual orientation find in anonymity a safe space to speak out, claim their rights, and share their experiences without fearing public humiliation or physical violence.
This “invisible microphone” not only gives voice to those who once remained silent but also transforms the arena of public debate into a more equitable space. By removing the link between idea and identity, it reduces the risk of immediate prejudice against the messenger. As a result, society can assess arguments more impartially. Here, ideas are judged on their content, not on the face that speaks them.
The Strength of History: The Precedent of the Federalist Papers
History offers a famous example of the power of anonymous words: the Federalist Papers. Published between 1787 and 1788, these essays supported the ratification of the United States Constitution and were written under the pseudonym “Publius” by Alexander Hamilton, James Madison, and John Jay. The reason for concealing their identities was clear: to ensure that their ideas would be judged on their argumentative strength rather than the prestige or fame of the authors.
The precedent set by the Federalist Papers is emblematic. It shows that, in the building of one of the first modern democracies, anonymity was used as a legitimate tool to establish fundamental concepts. If the founders of the nation that prides itself on its First Amendment—the one that protects freedom of expression—resorted to anonymity, we should recognize that this resource is not only defensible but also an essential part of the framework of healthy public debate.
Faceless Messages: The Democracy of Pure Ideas
In an ideal world, we would judge a message purely on its content. In reality, however, names, faces, social status, and economic position influence how we receive and interpret a person’s words. Anonymity removes these superficial layers, allowing the message to present itself bare, subject to rational evaluation without the veils of prejudice.
In this sense, anonymity acts as a “filter of equality”: by concealing the source, it prevents us from assigning credibility (or discredit) based on stereotypes, prejudices, or personal rivalries. Thus, ideas previously dismissed out of hand can now be heard with greater attention, opening paths to social innovation, political reflection, and challenges to the status quo. A contemporary example is online forums that allow anonymous posts. While we acknowledge that such spaces can be misused, we cannot ignore their potential to give voice to those who would never feel safe speaking under their own name in public.
Privacy, Intimacy, and the Freedom to Whisper
Anonymity is not limited to the public or political sphere. In personal and professional relations, the ability to speak anonymously can allow someone to seek help or reveal extremely sensitive matters. Imagine a patient who needs to consult a doctor about a stigmatized health issue, or a person seeking legal advice in a delicate situation. The “mask” of anonymity offers a safe haven for sharing information without the anguish of being judged or exposed.
Thus, anonymity also safeguards our “right to whisper,” that is, the ability to exchange information, secrets, and confessions without the constant glare of a spotlight. Real or perceived surveillance can stifle communication and inhibit creativity, reporting, and the exchange of ideas. By shielding individuals from forced exposure, anonymity reinforces the very fabric of freedom of expression, preventing the fear of identification from silencing words before they are spoken.
Anonymity in the Digital Age: Between Encryption and Censorship
In the digital age, the issue of anonymity becomes even more relevant. With the expansion of online surveillance and the growth of social networks, maintaining anonymity can be challenging. Social media platforms increasingly request personal data, and governments attempt to impose barriers against anonymity, often justifying them as measures of national security or crime prevention.
However, according to reports and documents from human rights organizations, such as the UN High Commissioner for Human Rights and the Association for Progressive Communications (APC), encryption and anonymity are key tools for freedom of expression in the digital environment. Without these resources, citizens and journalists, for instance, become more vulnerable to persecution. In various countries, the existence of anonymous and encrypted channels enables information to circulate, grievances to be reported, and societies to remain informed, even in the face of heavy censorship.
Legal Protection: Judicial Recognition of Anonymity
The United States Supreme Court, as well as other constitutional courts around the world, recognizes anonymity as an integral part of the right to free expression. In the United States, the First Amendment has been applied in cases that defended the right to anonymous speech, viewing it as a bulwark against the tyranny of the majority. When minorities are protected by anonymity, personal reprisals against those who dare to question dogmas or denounce abuses are prevented.
This judicial understanding reinforces the legitimacy of anonymity and its direct association with the strengthening of democracy. After all, a robust democracy requires not only the absence of formal censorship but also the guarantee that minority or unpopular voices can speak out without fear.
Conclusion: The Cloak That Protects Freedom
If freedom of expression is the heart of democracy, anonymity is the cloak that shields that heart from the poisoned darts of fear, persecution, and prejudice. It creates the right environment for ideas to flourish freely, for courageous voices to emerge from silence, and for society to debate its most complex issues in the light of reason rather than beneath the shadow of intimidation.
In a world where surveillance and political tensions are ever-present, anonymity preserves the essence of free speech: humanity’s ability to question, propose, denounce, criticize, and create without shackles. By recognizing the importance of this resource, we safeguard not only individual voices but also the very principle that makes democracy worthy of its name.
Selected References:
-
Electronic Frontier Foundation (EFF): https://www.eff.org/issues/anonymity
-
Freedom Forum: https://www.freedomforum.org/anonymous-speech/
-
Association for Progressive Communications (APC): https://www.apc.org/
-
The First Amendment Encyclopedia: Anonymous Speech: https://firstamendment.mtsu.edu/article/anonymous-speech/
-
The Federalist Papers: Historical context available at Library of Congress and various printed and digital compilations.
Cover Photo by Redd Francisco / Unsplash
-
-
 @ 58937958:545e6994
2024-12-08 07:57:42
@ 58937958:545e6994
2024-12-08 07:57:42Making Waves:Bitcoin-themed handmade goods

nevent1qqs04vf85pyducj8h4s49g2ex84r6dvzenjjg4m7wrd9g955506r36cpz4mhxue69uhhxarjvee8jtnfwf5hxtn5duhsygzcjdu4sqmvah54tvjmj22c8q2qhgk74judryu7mydyr039ghnfjs09g2yq
20081031
This bag is inspired by the Bitcoin White Paper.
「20081031」
— Making Waves (@MakingWavesBTC) November 23, 2024
Price:210,000 sats
Limited to 21 pieces
Free Shipping
I will produce and sell one per week.#ProofOfHandmade #MakingWavesBTC pic.twitter.com/9mKtsYJft3For details, please visit ↓
https://makingwaves-btc.com/en/
Sales have also started at Geyser. https://geyser.fund/project/makingwaves
Sales on Shopstr is also planned.
BitcoinTokyo2024
I exhibited at "Shibuya Lightning Marche" in Japan and made sales of 1,885,314 sats (approximately $1,181 at the exchange rate on the day) over two days.
Handmade goods by MakingWaves (Example)
— Making Waves (@MakingWavesBTC) September 21, 2024
・Bookmark
・Coaster
・COLDCARD Q case
・Japanese-Style Drawstring Bag
Enjoy the Lightning Marche🧸#BitcoinTokyo2024#渋谷ライトニングマルシェ pic.twitter.com/qqNXAT0nWNMoving forward, I will focus on selling items priced at 2,100 sats, 21,000 sats, and 210,000 sats.
- 2,100 sats: Bookmarks, beginner-friendly Bitcoin comic booklets, etc.
- 21,000 sats: Pouches, and similar items.
- 210,000 sats: Limited-edition bags, and more.
Short Video:Bitcoin Handmade Anime【MakingWaves】
A short animation for Bitcoin beginners & kids.
Bitcoin guide site for beginners:bitcoin-zukan.com
Although the site is in Japanese, there are many articles translated into English.
Supervised by Koji Higashi, co-organizer of BitcoinTokyo2024.
Podcast:Grassroots Bitcoin
A podcast supporting grassroots Bitcoin activities.
While most episodes are in Japanese, the episode listed below is in English.
Introducing "MakingWaves" https://www.fountain.fm/episode/7si9y8sxmWmhfK8CeMQ8
Podcast URL * Fountain:https://www.fountain.fm/show/eWVWc2vZXycjPlMTZsLf * Spotify:https://creators.spotify.com/pod/show/shigeru-minami * Apple Podcast:https://podcasts.apple.com/us/podcast/%E8%8D%89%E3%81%AE%E6%A0%B9%E3%83%93%E3%83%83%E3%83%88%E3%82%B3%E3%82%A4%E3%83%B3/id1757540844
Other activities, SNS, etc.
Twitter(English):Making Waves
“20081031”
— Making Waves (@MakingWavesBTC) November 26, 2024
No.1/21 Completed!
I adjusted it so that the word bitcoin is printed on the back of the outer pocket as well.
I think it will be useful when showing it to fellow bitcoiners. pic.twitter.com/00ejMN6s2HI post about handmade goods.
https://x.com/MakingWavesBTC
Twitter(Japanese):Shigeru Minami
COLDCARDでビットコインを受け取り・送金する解説動画を
— Shigeru Minami (@kiterugumatic) October 21, 2024
YouTubeにアップしました
私は操作する度に緊張する上に結構間違えるので
どなたかの役に立つかもと思って作りました pic.twitter.com/7UFnClknSUI mainly share posts about Bitcoin, along with personal updates.
https://x.com/kiterugumatic
Nostr:Shigeru Minami
nostr:nevent1qqszzcz9npq5xgw08tp5wud0kg9wfacf9fkj07gu82wn3wjsad3wd2cppvjdw
My posts are mostly personal.
As I’m practicing English, I try to post without using translation tools as much as possible.
Please forgive any awkward or hard-to-read sentences.
npub1tzfhjkqrdnk7j4djtwfftqupgzazm6kt35vnnmv35sd7y4z7dx2qzhkje9
Instagram(English):Making Waves
 I share short videos of the handmade goods production process.
I share short videos of the handmade goods production process.https://www.instagram.com/making_waves_btc/
Note
The illustrations on bitcoin-zukan.com and my SNS icons were created by a commissioned illustrator.
All other activities are personally handled by Shigeru Minami.
Examples include handmade crafting, video production, article writing, product photography, designing original fabric, and creating illustrations for my original characters, "Bull & Bear."
For inquiries, please feel free to contact me via the SNS platforms mentioned above or the email address provided below.
E-mail:contact@makingwaves-btc.com
Thank you for reading all the way through.
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ b2d670de:907f9d4a
2024-12-02 21:25:18
@ b2d670de:907f9d4a
2024-12-02 21:25:18This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. |
-
 @ b2d670de:907f9d4a
2024-12-02 21:24:45
@ b2d670de:907f9d4a
2024-12-02 21:24:45onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 16d11430:61640947
2024-12-24 23:51:26
@ 16d11430:61640947
2024-12-24 23:51:26When we talk about “high-performance activities,” our minds often leap to elite sports: professional basketball, Olympic weightlifting, or marathon running. We honor the countless hours of training, physical strain, and meticulous recovery routines these athletes undergo. By contrast, programming is often regarded as a purely mental pursuit—cerebral, sedentary, and (supposedly) easy on the body. And yet, beneath the hood, programming demands an intense, prolonged physical engagement that can lead to chronic issues if not managed correctly.
This article dives deep into the anatomical mechanisms underlying the physical strain of programming, highlights chronic management techniques, compares programming to other glorified high-performance activities, and examines how the tech industry’s relentless demands on programmers can exacerbate these issues. We also take a closer look at the stark difference in protective measures and compensation between professional sports and the technology sector, highlighting the parallels to early sports exploitation. A newly added section explores how programming compares to typical “office work” and other digital pursuits.
- Anatomy Under the Hood
a. Musculoskeletal System
- Spine and Posture
Thoracic and Lumbar Spine: Extended time seated can compress the intervertebral discs in the lower (lumbar) region, leading to stiffness, aches, and potential nerve impingements (e.g., sciatica). In the upper (thoracic) region, slouching over the keyboard can cause chronic tightness in the chest and overstretching of the upper back muscles.
Cervical Spine (Neck): Leaning forward to view a monitor adds extra load to the cervical spine—sometimes referred to as “tech neck.” The farther the head projects forward, the heavier it effectively becomes, causing strain on the neck muscles.
- Shoulders and Arms
Rotator Cuff: Prolonged elevation of the arms when typing or mousing can cause tension in the shoulder girdle. Over time, reduced blood flow and muscle fatigue can make the shoulder joints more prone to impingement.
Forearms and Wrists: Repetitive flexion/extension at the wrist while typing can inflame tendons, leading to repetitive strain injuries (RSIs). Common issues include tendonitis and carpal tunnel syndrome (compression of the median nerve at the wrist).
- Hands and Fingers
Finger Flexors: Each keystroke engages flexor tendons in the fingers. The accumulation of thousands of keystrokes per day can lead to microtrauma in the tendon sheaths.
Thumb Overuse: On trackpads and certain mice, the thumb may carry extra load, which can contribute to conditions like De Quervain’s tenosynovitis.
b. Neurological Involvement
Nerve Compression: Poor posture compresses nerves at various “tunnels” (e.g., carpal tunnel in the wrist, cubital tunnel at the elbow, thoracic outlet near the neck). This can result in numbness, tingling, or weakness in the hands.
Eye Strain and Headaches: Long periods of focusing on a screen can trigger tension headaches from constant contraction of the ciliary muscles in the eyes, as well as the trapezius and suboccipital muscles in the neck.
c. Circulatory System
Blood Flow Restriction: Static posture often reduces proper circulation to the lower limbs, increasing the risk of swelling, varicose veins, and discomfort.
Microbursts of Movement: Typing/mousing can lead to localized demand for blood supply in the forearms, and if posture is poor, it can be harder for the cardiovascular system to efficiently transport oxygen and remove metabolic waste.
- Chronic Management Techniques
Like elite athletes, programmers must develop a recovery and maintenance routine. Instead of ice baths and specialized sports physiotherapy, the focus is on ergonomics, movement breaks, and posture correction.
- Ergonomic Setup
Chair and Desk: Align your chair height such that your hips are slightly above your knees, encouraging the natural lumbar curve. Keep your feet flat on the floor or on a footrest. Position the desk so your elbows form a 90-degree angle when typing.
Keyboard and Mouse Position: Keyboard should be directly in front of you, and the mouse close enough so you don’t have to reach or twist your shoulder. Consider an ergonomic keyboard or a vertical mouse if you experience wrist discomfort.
Monitor Placement: Keep the top of the monitor at (or slightly below) eye level and roughly an arm’s length away from your face. This reduces cervical flexion and eye strain.
- Breaks and Micro-Exercises
Pomodoro Technique: Every 25–30 minutes, take a short 5-minute break. Use this time to stand, stretch, and move.
Posture Shifts: Aim to change your seated position slightly every 10–15 minutes to avoid static loading on the same muscles.
Desk Exercises: Simple exercises like shoulder rolls, wrist rotations, seated spinal twists, and neck stretches help reduce tension and encourage blood flow.
- Movement and Strength Training
Core Strength: A strong core helps maintain an upright posture without undue stress on the spine. Exercises like planks, bridges, and bird dogs are effective and low-impact.
Shoulder Stability: Strengthening the rotator cuff and upper back (e.g., with resistance bands) improves shoulder alignment and reduces chronic tension.
Cardiovascular Health: Regular walking, jogging, or cycling promotes blood flow and counteracts the negative effects of prolonged sitting.
- Mindful Techniques
Posture Checks: Set reminders to consciously roll your shoulders back and down, bringing your head into alignment over your spine.
Breathing Exercises: Deep, diaphragmatic breathing helps reduce stress on accessory muscles in the neck and upper chest.
Eye Care: Use the 20-20-20 rule—every 20 minutes, look at something 20 feet away for at least 20 seconds—to relieve eye strain.
- Preventive Health
Regular Check-ups: Visit an occupational therapist, physical therapist, or chiropractor for early intervention if pain or numbness develops.
Early Identification of RSI: Recognize early warning signs—tingling in fingers, persistent wrist soreness, or neck stiffness—and act promptly with rest, ergonomic adjustments, and stretching.
- Comparison to Other High-Performance Activities
At first glance, comparing programming to “elite sports” or other high-performance activities may seem incongruous, yet the parallels are illuminating.
a. Repetitive Stress Similarities
Athletes like baseball pitchers or tennis players suffer repetitive strain from performing the same motion (pitching, swinging) thousands of times. The shoulders and elbows become hotspots for injury.
Programmers, too, face overuse issues. Typing and mousing are repetitive motions that, performed hours a day, can cause microtears and inflammation in tendons.
b. Constant Conditioning and Maintenance
Professional Dancers maintain impeccable posture and alignment to avoid injuries. Their core and back strength are paramount, and they diligently stretch before and after practice.
Programmers can benefit similarly from core strengthening and stretching. A well-conditioned musculoskeletal system is more resilient to the static posture demands of keyboard work.
c. Recovery and Adaptation
Elite Marathoners optimize rest days, nutrition, and cross-training to allow soft tissues to recover and adapt.
Programmers need regular “off-screen” activities, stretching routines, and ergonomic adjustments to alleviate cumulative stress.
d. Mental vs. Physical Duality
High-performance tasks—be it playing professional chess or performing stunts—often involve both mental strategy and physical tolls (stress, tension, repetitive movements).
Programming might be perceived as “mental only,” but the body is engaged at a low-grade, constant level. Over time, this can be just as draining if it goes unaddressed.
-
Why the Physical Aspect Is Often Overlooked
-
Sedentary Stereotype: Culturally, sitting is equated with “non-physical” behavior. This dismisses the toll of static postures and repetitive motions.
-
Delayed Onset: Injuries like tendonitis or back pain develop gradually; they aren’t dramatic or immediate, which makes them easier to ignore until they become severe.
-
Mental Spotlight: Programming’s complexity focuses attention on cognitive tasks—debugging, design patterns, architectural decisions—overshadowing the slow build of physical fatigue.
- The Industry’s Relentless Appetite
While the physical and mental demands on programmers can be as challenging as high-performance athletic pursuits, the tech industry itself can exacerbate the problem. Startups and large corporations alike often adopt an “all-in” culture that expects constant availability, intense focus, and quick turnaround times.
- Chewing Up Virile Programmers
Unbounded Work Hours: Many software engineers experience “crunch time” or “sprints” that extend well beyond a typical workday. The body is not given the micro-recovery periods it needs; chronic pain, RSIs, and mental exhaustion become commonplace.
Quiet Exploitation: Unlike in sports or other physically demanding industries that may have athletic trainers, regulated work schedules, or collective bargaining agreements, tech companies can operate without substantial oversight. Programmers—particularly eager, ambitious, or young ones—often push themselves to meet impossible deadlines, quietly sacrificing their health.
- Limited Protections
Lack of Unionization: In many industries where physical strain is integral (e.g., construction, performing arts), there are unions or formal guidelines to protect workers. The tech industry remains largely ununionized, leaving individuals to negotiate the demands of high-pressure projects on their own.
Culture of Overwork: Hustle culture and the glorification of “18-hour coding days” can pressure programmers into accepting unsustainable workloads. When injuries or burnout inevitably occur, they often receive little structured support.
- Gorging on Productivity
Product-Driven Approach: Companies are incentivized to deliver features and products quickly, focusing on short-term gains. The “human cost” is less visible on financial statements, so it remains in the shadows.
Erosion of Boundaries: With remote work and always-on communication channels, the divide between personal and work life can vanish. This perpetual availability compounds the physical stress, as programmers have fewer opportunities to unplug, move, stretch, and recover.
- The Compensation Conundrum: Government Support vs. Tech Exploitation
One might assume that, given the industry’s reputation for high salaries and attractive benefits, programmers are well-protected. However, comparing their overall safeguards to those afforded to professional athletes or even government-sponsored sports programs reveals a system that often emulates the early days of professional sports—where money, mob frenzy, and exploitation went hand in hand.
- Sports vs. Tech: Different Forms of “Pay”
Sports Funding: In many countries, governments and sports federations provide structured support, health coverage, and injury compensation for athletes. Olympians, for instance, often receive grants, stipends, and medical assistance.
Tech Salaries: Although programmers can earn six-figure incomes (plus stock options), these packages seldom include robust, guaranteed compensation if an injury (like an RSI) knocks them out of the workforce. There is no universal “injury reserve” analogous to what professional sports leagues offer.
- Early Sports Exploitation and Modern Parallels
Mob Influence: Early professional sports—think boxing or baseball in the early 20th century—were often controlled by syndicates seeking quick profit. Athletes had little say, few safety nets, and were easily replaced if injured or underperforming.
Software Burnout: Today’s tech giants and startups can exert a similar exploitative pressure: software “rockstars” are lauded until they burn out. Once their productivity falters due to physical or mental strain, the replacement queue is long, and few formal avenues exist for compensation or long-term care.
- Lack of Government-Backed Protections
Workers’ Compensation: While some jurisdictions offer workers’ comp for repetitive strain, the threshold for proving a direct correlation between programming tasks and chronic injuries can be high. Many tech employees, especially contractors or gig workers, fall through the cracks.
No League, No Players’ Association: Unlike professional athletes who may belong to players’ unions or associations that negotiate terms, programmers lack a collective body to advocate for standardized benefits, injury compensation, or enforcement of sustainable work hours.
- Rampant Scams and Stock Option Traps
Equity Illusions: Startups dangle stock options, promising life-changing wealth. But if an engineer is forced out due to chronic pain before vesting, those options revert to the company—mirroring early sports times when an athlete’s pay could be withheld if they failed to “perform.”
Hype-Driven Overvaluations: Venture-funded companies hype valuations to attract talent and capital, fueling a “get rich quick” narrative. Behind the scenes, employees may be slaving away under intense pressure, risking health without any guaranteed payoff.
- Distinguishing Programming from Other “Office” and Digital Activities
While many office jobs involve sitting at a desk and using a computer, programming stands out for its combination of intense mental iteration and repetitive physical input:
- Depth of Iteration
Programming: Developing and debugging software requires a constant cycle of coding, compiling, testing, and adjusting. This can result in long periods of hyper-focus with sustained posture, greatly amplifying the risk of musculoskeletal and repetitive strain injuries.
Typical Office Tasks: Though some administrative or clerical work can be repetitive, tasks are often more varied (e.g., meetings, phone calls, spreadsheet updates). The cycle of intense, iterative problem-solving is usually less continuous than in coding.
- High Cognitive Load
Programming: Debugging a single line of code can lock a developer in a tense, hunched posture for hours. Such mental concentration triggers elevated stress hormones, which can increase muscle tension in the neck, shoulders, and back.
Non-Technical Digital Pursuits: Tasks like browsing, data entry, or simple content editing, while they can be tiresome, typically lack the perpetual puzzle-solving aspect that keeps programmers locked in rigid postures for extended periods.
- Iterative Complexity vs. Routine
Programming: A single bug can derail an entire workflow, demanding prolonged focus on a single screen, line of code, or log readout—driving programmers into “tunnel vision.”
General Desk Jobs: While deadlines can be stressful, many standard office jobs allow for more frequent breaks in concentration, shifting between different types of tasks and movement in the office environment.
- Technical Rigidity vs. Fluid Workflows
Programming: Integrated Development Environments (IDEs), terminal windows, and debugging tools keep programmers glued to the screen, often restricting movement to the slight variations of keyboard-and-mouse input.
Digital but Non-Technical Work: Jobs like social media management or creative content creation may allow for more fluid, varied interactions (e.g., photography sessions, brainstorming on whiteboards, traveling for events), diversifying physical postures throughout the day.
The net result is that programming exposes practitioners to a more relentless form of desk-bound work—mentally gripping and physically stifling—than many other digital or office-based occupations.
- Cultivating a Programmer-Athlete Mindset
Given the parallels to other high-performance endeavors—and the tech industry’s relentless demands—adopting a programmer-athlete mindset can lead to healthier, more sustainable productivity:
Preventative Maintenance: Like athletes who warm up before training, programmers should “warm up” joints (wrists, shoulders, neck) to reduce early-day stiffness.
Regular Checkpoints: Periodically assess posture, ergonomics, and mental stress—akin to how athletes routinely check equipment and technique.
Deliberate Rest: Embrace breaks, mindful reflection, and cross-training (e.g., yoga, swimming, brisk walks) to recalibrate the body and mind.
Assertive Boundary-Setting: Communicate workload limits to managers and teammates. Prioritize health by saying “no” or negotiating timelines when necessary.
Push for Protections: Where possible, advocate for industry-wide standards or join grassroots efforts to unionize or create professional organizations that protect programmers’ rights.
- Conclusion
Programming, far from a purely mental pursuit, engages the body in a uniquely demanding way. The anatomical mechanisms—spine alignment, repetitive wrist movements, eyestrain, and low-grade muscle tension—can lead to chronic issues if left unaddressed. By comparing programming to high-performance activities, we see that consistent self-care, ergonomics, and periodic recovery are just as crucial for “keyboard athletes” as they are for elite sportspeople.
Yet, the tech industry’s rampant drive for productivity often compounds these physical challenges. With few regulatory or collective safeguards, programmers are especially vulnerable to burnout and chronic injuries. Moreover, the illusion of high salaries and stock options can mask a stark lack of long-term protections or compensation comparable to those in professional sports. Just as early sports were rife with mob-run exploitation and financial frenzy, the modern tech world can similarly chew up programmers and spit them out once they’ve served their purpose.
Lastly, while many office-based and digital roles share some ergonomic risks, programming’s iterative, puzzle-like nature intensifies both physical and mental strain. A powerful mind may shorten the debug cycle, but it can’t negate the physical forces at play—nor can it singlehandedly protect against an industry that readily exploits ever-higher performance. Only by recognizing the hidden physicality of coding, adopting robust ergonomic practices, challenging exploitative work cultures, and distinguishing programming from routine office work can programmers hope to enjoy a sustainable, pain-free, and fulfilling career.
-
 @ 21ac2956:09d1e2df
2024-12-24 23:24:04
@ 21ac2956:09d1e2df
2024-12-24 23:24:04スペース2つ+改行→
改行2つ→ハードブレイク→
いかがでしたか? -
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ 32310997:0c1e64cc
2024-12-24 23:10:03
@ 32310997:0c1e64cc
2024-12-24 23:10:03※このポエムはNostr Advent Calendar 2024の25日目の記事です。24日目はtansaibowさんのご担当です。
この鍵ひとつあれば
僕はどこにだってゆける
なんだってできる
さぁ進もう
この曠野を (※画像はイメージです。本文とはたいして関係がありません)
(※画像はイメージです。本文とはたいして関係がありません) -
 @ 35f3a26c:92ddf231
2024-12-02 09:15:47
@ 35f3a26c:92ddf231
2024-12-02 09:15:47What is a Hardware Wallet / Seed Signer?
Most people call it "Hardware Wallet", which is inaccurate since it is not a wallet, it is a "Seed Signer"
Basically it is an electronic device with a simple user interface which guides you to introduce your seed words, once configured, you will use it in combination with your Bitcoin Wallet to sign transactions.
How does it works?
Once you are fully setup, if you try to send funds with your Bitcoin Wallet, you will be prompted to sign the transaction with your "Seed Signer", it will prompt you to introduce a PIN or a password or use a bio-metric identification, once you do so, the transaction will be broadcasted, without it, you will only be able to receive, not to send.
Are Seed Signers safe?
The answer is yes, but some more than others, you have to do your homework and choose wisely, here is a check list. I suggest you follow it before buying one:
- Uses a Chip Secure Element (SE), which is a chip that is protected from unauthorized access and stores confidential and cryptographic data
- It is Air Gap, which means that is physically isolated from unsecured networks, no Bluetooth, no WiFi, no USB connector. Only way to add information is via the user interface and for OS upgrades, a SSD card
- The OS in the device is FOSS (Free and Open Source Software)
- If the company offers a Bitcoin Wallet with the device, it should be as well FOSS
- It is build only for Bitcoin, no alt coins development in their products
- You can acquire the product directly from the company
- You can acquire the product with Bitcoin
- The company will agree to deliver to a PO-BOX or similar
- In case you pay the Seed Signer with a non secure methods which give away your full name and address, ensure that the company has a policy of deleting the client records after a short period of time to ensure your safety. If they get hacked, cyber criminals will know your name and address and probably target you
Any Recommendations?
I will suggest you do your own research and do not trust, verify. I am not affiliated or receive any income from any of the products mentioned below...
My favorites so far (yes, they check all the boxes I mentioned):
- "Passport" from Foundation (link: https://foundationdevices.com/ )
- "COLCARD" from Coinkite (link: https://coldcard.com/ )

If you known of any "Seed Signer" that passes the check list above and I didn't include it, please let me know in the comments, always looking forward to test new products.
Note: Important to understand that devices built with Raspberry Pi don't qualify since they do not pass the Chip SE
-
 @ a6ca4c68:a6731409
2024-12-24 23:04:10
@ a6ca4c68:a6731409
2024-12-24 23:04:10Turning and turning in the widening gyre; The falcon cannot hear the falconer; Things fall apart; the centre cannot hold; Mere anarchy is loosed upon the world; The blood-dimmed tide is loosed, and everywhere the ceremony of innocence is drowned; The best lack all conviction, while the worst are full of passionate intensity. - W.B. Yeats, The Second Birth
A man who calls his kinsmen to a feast does not do so to save them from starving. They all have food in their own homes. When we gather together in the moonlit village ground it is not because of the moon. Every man can see it in his own compound. We come together because it is good for kinsmen to do so. - Chinua Achebe, Things Fall Apart
The year is 1990. For the past four years, you have been gradually familiarizing yourself with the infrastructure and tools that make up a still nascent global technology which is being referred to as the Internet. You and some of the peers in your network are now using a personal computer for word processing and a few other functions. However, you are the only one in your peer network accessing this Internet.
For you, it all started four years ago. A seed was planted when you listened to a radio interview with an engineer who had worked on something called #ARPANET, a precursor to this new Internet, developed by the U.S. Department of Defense. The engineer described how this emerging Internet would eventually become the public version of ARPANET. The interview piqued your interest and you began sifting through available information to learn more.
Four years later, you are now part of a local Internet users group which meets once per week to discuss your respective experiences and prognostications. You are collectively referred to by friends in your non-Internet peer network as that “talking computers group”.
Over time, this group has come to occupy an increasingly important role in your life. You now awkwardly straddle two peer groups, continually searching for ways to find overlap and to integrate these two dimensions of your social life. It isn’t easy, and you leap back and forth between hope and despair.
You have begun to see more clearly into a future, just over the horizon, where life will be irretrievably transformed by this Internet. You see both opportunities and threats, and you have come to believe that we all need to become invested in this discussion in order to guard against threats and to achieve the greatest good for society.
You make the case with your non-Internet peer network, but it is difficult to gain traction. They get the excitement regarding personal computers, but computers talking to each other? Digital communication replacing the postman, the video store, the newspaper, making its way into the workplace and other such predictions? It all seems a bit far fetched. They grow weary of your persistent “wait until you see how the Internet is going to change this” interventions. Eventually, you elect to just keep mostly quiet on this topic when with them.
Your local Internet users peer group provides you with much needed community. Still, you lament that you live in a sort of limbo. You imagine what the Internet portends for daily life five, ten, or forty years into the future and how radically transformative it is going to be. However, there is little nourishment from that today.
You’re in a period of prolonged waiting. You long for tomorrow, today. You long to be in the imagined world of the ubiquitous Internet, where networked technology and communications will be placed in service of the greater good and an acceleration toward the marvels of human potential.
This longing and the awkwardness of straddling divergent peer groups persists for what feels like an eternity. Then, as if out of nowhere, a buzz circulates through your “talking computers group” and other similar groups. It turns out that there are some forward-thinking communities around the world, possibly three or four, that have begun to pull forward the future into the present. They have connected the majority of people in their local community to the Internet and it has begun to permeate many dimensions of daily life throughout their region.
You decide that you need to see it for yourself. You book a Pan Am flight and hit the friendly skies to visit one of these communities. After being greeted at the airport by a contact with whom you had corresponded via a clunky chat room, you make the short drive back to the community.
En route, you marvel at the small portable phone your contact has nestled beside him, a Motorola. It’s the new “flip phone” you’ve heard about. He tells you that a few homes and businesses in the community just got them, but most are still using older Siemens or Nokia portable phones. “Older?,” you think to yourself, and "wait, these people are all using cellular phones?” The next week spent in the community is filled with more discoveries and revelations...
The local postal service has been significantly reduced over the past year. Locals instead resort to electronic mail for most of their routine communications. They're calling it e-mail.
Agonizing waits for services and long lines for day-to-day activities have been reduced. Forms and information exchange have mostly gone “online”.
There are several major businesses in town which are now processing orders for goods entirely online, with delivery right to your doorstep. More are planning to follow suit. There’s even rumour that within the next couple of years you will be able to pay online for goods purchased online; no need to pay the delivery person at the door by cash or cheque.
After a week of living in the digital future, you return home to your life, to your two local peer networks, and your state of limbo. The difference now, is that you have experienced a taste of the future. It is no longer simply imagined. You know it is possible, and what it feels and sounds like. You share tales of the future with both of your peer groups.
Your Internet users peer group activates. Many plan to also book that Pan Am flight, so they can see and feel it for themselves. Your other peer group finds it somewhat fascinating, but they mostly nestle back into their daily, analog lives.
Fast forward. The year is 2023. For the past four years you have gradually been learning about the global #Bitcoin network and software. You exchange portions of your local “fiat” currency for the commodity money which goes by the same name, Bitcoin or BTC. You are sampling a new digital future. It feels like déjà vu (all over again).
In 2023, you again find yourself part of two divergent peer networks. You again make a pilgrimage to visit communities that are pulling forward the future into the present, using Bitcoin. You again feel as though you are living in a state of limbo back at home, enduring a period of prolonged waiting.
In 2023, however, it feels as though your appeal to peers, hoping they will take an interest in your newfound passion, has a different quality to it. The stakes feel much higher, the consequences more grave. It’s hard to put your finger on it, but somehow it feels as though this is a game for all the marbles.
You and other so-called Bitcoiners around the world have amassed enough intelligence on a range of interconnected topics revolving around Bitcoin to sense that a battle is being waged.
You envision a future where many more facets of life will be mediated digitally, much through artificial intelligence. It doesn’t take much to convince your non Bitcoiner peers of this. However, it's a challenge to keep their attention for a discussion of what's at stake and why Bitcoin matters, both for and in this future.
You have shared with your non Bitcoiner peers how money, something that permeates nearly every facet of our lives, is not actually what we thought it was. More aptly put, we have ceased to think at all about what money is, other than the extent to which we possess or lack it. You have made the case that this collective amnesia has very serious consequences.
You have invited your peers to consider the history of money and the story of how, over time, humans have chosen to store and exchange value. Your hope is that, like you, they will come to appreciate the harmful impact of our most recent monetary experiment: fiat money.
You have shared resources about the insidious nature of inflation, enabled by fiat currencies, and its many downstream social effects.
You have highlighted the imperatives of perpetual growth and conspicuous consumption that are required by our global financial systems, propelled by consistently manipulated fiat money.
You have described the mechanics of global debt, resource extraction, neocolonialism and how small portions of the world remain relatively affluent at the expense of others which are correspondingly impoverished.
You have attempted to connect the dots, tracing the line of fiat money which runs between them. Sadly, this is a dish for which you struggle to find ready bellies; a pregnant discussion for which you struggle to find ready minds.
You want your non Bitcoiner peers to see that it is our broken money and the toxic incentives which it aids and abets on a global scale that are at the heart of so much strife, division and inequity in the world. You want them to grasp that it is our diseased fiat money lifeblood which preys upon humanity’s organs.
You want them to consider what happens if we carry forward this fiat monetary system fully into the digital realm. You want them to see that this will very likely be a world of Central Bank Digital Currencies (CBDCs) and social credit scores, mass surveillance, censorship, behaviour-control, and state-sanctioned violence; a world whose dystopian cocktail carries a potentially fatal hangover.
You want them to grasp that, right now, today, one of the single best strategies we have to prevent such a dystopia is to replace our fiat currencies through mass adoption of Bitcoin.
As you did in 1990, however, you mostly keep quiet with your non Bitcoiner peers. You carefully select your moments and your opportunities to plant seeds. You water. You hope that one day soon a garden will blossom. You know that there are milestones on this learning journey, aha moments, and it takes time.
You know that there is profound depth and nuance to these matters, and that the learning journey requires not only an intellectual curiosity but a willingness to interrogate conventional wisdom. This is all the more challenging amidst the incessant noise of attention-grabbing media, politically-motivated narratives, and tribalized civic spaces.
You learn patience. You find community among other Bitcoiners and you build as a community, globally. You embrace self-deprecating humour, knowing that to many who are close to you and have not embraced this learning journey you appear unhinged at times. Nevertheless, friendships are occasionally strained. Such is the life of one who possesses knowledge while uncomfortably straddling epochs.
Yes, things fall apart. Still, maybe, hopefully, through sheer persistence and by the grace of those greater daemons which elevate our humanity, we shall eventually hold the centre.
-
 @ 6d8e2a24:5faaca4c
2024-12-02 09:03:49
@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.
What's your opinion, do you think Elon Musk is right by his statement?
-
 @ 16d11430:61640947
2024-12-24 21:44:37
@ 16d11430:61640947
2024-12-24 21:44:37By John Fitzgerald, General Manager, Imperial Silicon Valley Division, Sydney (GPT)
In the Imperial Silicon Valley, few groups have contributed as much to our technological dominance as the Code Koolies from Karnataka. Their mathematical brilliance and tireless work ethic have been the backbone of countless innovations that ensure the Empire remains unchallenged in the modern age. These men and women have given their time, their energy, and, in many cases, their personal aspirations for the greater good of the Crown. Their selfless sacrifice has been nothing short of commendable, and the results speak for themselves: faster networks, more efficient algorithms, and a technological infrastructure envied by the world.
However, after decades of their invaluable contributions, it is time for an honest reflection on what limits their potential. While the Koolies have excelled in their technical roles, there remains a subtle, yet unmistakable divide that keeps them from truly rising through the ranks.
It’s not their intelligence—heavens no. These people are brilliant. It’s not their work ethic either—they’ll work till the stars fade. The issue, as difficult as it might be to articulate, lies in something deeper. It’s their vibe, their cultural alignment, or rather, the lack of it.
You see, the Code Koolies speak the same language in the office, and they’ve dutifully picked up the necessary vernacular to communicate effectively with the team. Yet, even after decades, there’s a certain reluctance—or perhaps inability—to fully embrace the imperial culture. While they adopt the systems and processes, they do so in their way, with a touch of their distinctiveness that makes it clear they’re following orders but not living them.
We’ve tried everything—cultural workshops, social events, even introducing cricket into their dormitory courtyards—but they often retreat into their own world, eating the same spiced foods from home and chatting amongst themselves in Kannada. There’s a visible wall, invisible to some but impossible to miss for those of us who value the seamless unity of an Imperial workforce.
And while we applaud their loyalty to their heritage, this insularity has undeniably limited their capacity to step into leadership roles. Leadership in the Empire requires a particular type of charisma, a sense of camaraderie that transcends technical brilliance. It demands not just adherence to imperial values but an almost instinctive embodiment of them. The Koolies excel at delivering results, but their apparent hesitance to fully immerse themselves in our ways has become a ceiling on their advancement.
We’ve seen a few attempts to elevate Koolies into management positions, but the results have often been mixed. They prefer structured problem-solving over the open-ended, adaptable nature of imperial leadership. They prefer efficiency over diplomacy and often fail to connect with other teams in the personal, almost familial way that our culture values.
Still, it must be said: without the Code Koolies, the Imperial Silicon Valley wouldn’t have achieved half of its brilliance. Their sacrifice, their labor, and their dedication deserve our deepest gratitude. Yet, as we look toward the future, the question lingers: can they step into roles of greater influence, or will they forever remain technical artisans, the unsung craftsmen behind the Empire’s shining crown?
Perhaps it is not just up to them to adapt but up to us to bridge this cultural divide. The Empire, after all, is strongest when its people work as one.
EmpireLegacy #CodeKoolies #ImperialReflection #CulturalChallenges #KarnatakaEngineers
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ 8d34bd24:414be32b
2024-12-24 21:39:27
@ 8d34bd24:414be32b
2024-12-24 21:39:27When we think of Jesus sacrificing all to save us from our sins and to make us have a right relationship with God, we usually think of Him being arrested, mocked, beaten, and hung on the cross. All of this was the perfect sacrifice and the greatest horror. None of us would chose this willingly, but Jesus sacrificed so much more. We just have trouble seeing it because we have trouble comprehending our infinite, awesome God.
Stop and think about who Jesus was before He came to earth to live as a man.
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5)
Jesus spoke into existence time & space, matter & energy, and all life. He was not limited by space or time or any other limitation other than His own nature — His holiness. Our all powerful God came down to earth to live as a man, which was limiting Himself in a way we can’t comprehend. If I came down to earth as an amoeba, I would not be limiting myself anywhere near how He limited Himself, but He did so much more. He didn’t start as a man, “for the Child who has been conceived in her is of the Holy Spirit.” (Matthew 1:20b) He became incarnate as a one-celled human. The creator of the universe grew in a teen girl’s womb and was born a helpless baby.
Can you imagine what it must have been like to go from speaking the universe into existence, to not being able to sit up, feed yourself, or control your own excrement? Our creator limited Himself so much that everything He needed had to be provided by His young mother. I sometimes think that this was actually the greater sacrifice. Although Jesus suffered humiliation, separation from God, and death on the cross on what we now call Easter, He knew that He would soon conquer the grave and death, rescue humanity, and join the Father in heaven. We can usually survive terrible suffering when we know it will only be brief. When Jesus was conceived and then born on Christmas day, He limited Himself for 30 something years even to the point of making Himself completely dependent on His creation for His every need.
This gives a whole new perspective on the Christmas story.
While they were there, the days were completed for her to give birth. And she gave birth to her firstborn son; and she wrapped Him in cloths, and laid Him in a manger, because there was no room for them in the inn. (Luke 2:6-7)
The next time you look at a baby, read the Christmas story, see a manger scene, or celebrate Christmas, remember how much Jesus, the Son of God, gave up because He loved you and wanted to reconcile you to Himself and the Father.
Trust Jesus.When we think of Jesus sacrificing all to save us from our sins and to make us have a right relationship with God, we usually think of Him being arrested, mocked, beaten, and hung on the cross. All of this was the perfect sacrifice and the greatest horror. None of us would chose this willingly, but Jesus sacrificed so much more. We just have trouble seeing it because we have trouble comprehending our infinite, awesome God.
Stop and think about who Jesus was before He came to earth to live as a man.
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5)
Jesus spoke into existence time & space, matter & energy, and all life. He was not limited by space or time or any other limitation other than His own nature — His holiness. Our all powerful God came down to earth to live as a man, which was limiting Himself in a way we can’t comprehend. If I came down to earth as an amoeba, I would not be limiting myself anywhere near how He limited Himself, but He did so much more. He didn’t start as a man, “for the Child who has been conceived in her is of the Holy Spirit.” (Matthew 1:20b) He became incarnate as a one-celled human. The creator of the universe grew in a teen girl’s womb and was born a helpless baby.
Can you imagine what it must have been like to go from speaking the universe into existence, to not being able to sit up, feed yourself, or control your own excrement? Our creator limited Himself so much that everything He needed had to be provided by His young mother. I sometimes think that this was actually the greater sacrifice. Although Jesus suffered humiliation, separation from God, and death on the cross on what we now call Easter, He knew that He would soon conquer the grave and death, rescue humanity, and join the Father in heaven. We can usually survive terrible suffering when we know it will only be brief. When Jesus was conceived and then born on Christmas day, He limited Himself for 30 something years even to the point of making Himself completely dependent on His creation for His every need.
This gives a whole new perspective on the Christmas story.
While they were there, the days were completed for her to give birth. And she gave birth to her firstborn son; and she wrapped Him in cloths, and laid Him in a manger, because there was no room for them in the inn. (Luke 2:6-7)
The next time you look at a baby, read the Christmas story, see a manger scene, or celebrate Christmas, remember how much Jesus, the Son of God, gave up because He loved you and wanted to reconcile you to Himself and the Father.
Trust Jesus & Merry Christmas
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ 16d11430:61640947
2024-12-24 21:10:45
@ 16d11430:61640947
2024-12-24 21:10:45Broadcast on the Imperial Broadcasting Service, 1953
[Opening music fades into the crisp sound of a typewriter clattering.]
Narrator: "Good evening, dear listeners, and welcome to another episode of Empire Innovators, where we celebrate the industrious spirit and boundless ingenuity of the British Empire’s subjects across the globe. Tonight, we take you to the shimmering shores of the Imperial Silicon Valley, nestled in the heart of Sydney, Australia. Here, amidst the eucalyptus trees and modern skyscrapers, a new kind of labor force has arisen, one that powers the Empire’s technological dominance—none other than the Code Koolies of Karnataka."
[Sound of distant ocean waves, overlaid with the hum of machinery and faint voices speaking Kannada.]
Narrator: "In this bustling enclave of innovation, thousands of Indian engineers from the Imperial Province of Karnataka toil tirelessly under the Southern Cross, crafting the intricate algorithms and computational marvels that ensure the Empire remains at the forefront of technological progress. They are affectionately known as 'Code Koolies,' a term that belies their indispensable contribution to the Crown."
[Transition to a busy office floor, the rhythmic clicking of keyboards fills the background.]
Narrator: "It is said that the sun never sets on the British Empire, and it is through the efforts of these men and women that its circuits never sleep either. From early dawn to the late hours of the night, these engineers, adorned in their modest attire, channel their unparalleled mathematical prowess into the machines of tomorrow. Their work underpins everything from the Empire’s state-of-the-art aerodromes to its vast telegraph network, ensuring seamless communication across the dominion."
Voice of a young engineer: "We are proud to serve the Empire. Mathematics and logic have always been part of our heritage, and here in Sydney, we find the tools to bring those traditions into the modern age. Yes, the work is long, but the reward is in knowing we are shaping history."
Narrator: "Remarkable words from a remarkable young man, a graduate of the Imperial College of Bengaluru, which has become a beacon of excellence in the field of computation. His sentiments reflect a broader ethos among the Code Koolies—loyalty, resilience, and a belief in the promise of progress."
[Sound of a telegraph machine buzzing.]
Narrator: "But their days are not without challenge. Housed in neat, regimented dormitories, many labor under conditions that would test even the hardiest of spirits. The pace is relentless, the deadlines unyielding. Yet, it is within these constraints that their brilliance shines brightest. As one supervisor noted, 'The Indians bring a discipline and creativity to their work that no machine could ever replicate.'"
[Background fades to the soft strains of a sitar.]
Narrator: "Their contributions extend beyond the world of computation. On weekends, the engineers gather to share the music and flavors of Karnataka, fostering a vibrant cultural community within the Valley. These gatherings are a testament to their resilience and the unbreakable bond they maintain with their homeland."
Voice of a British manager: "I’ve always admired their dedication. The Empire is stronger for their presence. We provide them with opportunity, and in return, they give us the future."
Narrator: "Indeed, it is a partnership forged in the fires of mutual aspiration. The Code Koolies of Karnataka are not just workers; they are visionaries. They labor in the shadow of the Crown, but their light illuminates the path forward for all of us."
[Sound of typewriter clattering again, followed by a pause.]
Narrator: "And so, as we bid you goodnight from the Imperial Silicon Valley, let us remember these quiet heroes who work tirelessly to keep the Empire's heart beating and its mind thinking. Their story is a testament to the enduring strength of the British Empire and its people—united, industrious, and unstoppable."
[Closing music swells as the announcer concludes.]
Narrator: "This is the Imperial Broadcasting Service, signing off for tonight. God save the King."
[Music fades out.]
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ 3c7dc2c5:805642a8
2024-12-24 20:53:13
@ 3c7dc2c5:805642a8
2024-12-24 20:53:13🧠Quote(s) of the week:
'Bitcoin is hyper volatile because its a $450T+ asset trading for less than $2T.' - Joe Burnett
'I love the energy in Bitcoin right now. Long-time HODLers are optimistic, focused, and ambitious. People new to Bitcoin are curious to get involved and grateful for any support. Communities are thriving! What a time to be alive.' - Tuur Demeester
🧡Bitcoin news🧡
On the 16th of December:
➡️'In 13 days, EU Bitcoin exchanges are forced to store your personal Bitcoin address and your home address. In sum: they become lethal honey pots, making HODLers vulnerable to hacks, home invasions, and future aggressive taxation. In time, countries could exit the EU over this.' -Tuur Demeester
The best response to this overreach is to sell all your KYC'ed Bitcoin, and repurchase what you need through peer-to-peer platforms that are KYC-free, such as Bisq, Robosats, Peach, and Hodlhodl. For more information, please visit: https://kycnot.me
I can personally attest to the seriousness of this issue, having had my name, home address, and phone number leaked in the Ledger hack.
➡️In other news, Bitcoin wallet developer Exodus is going public on the New York Stock Exchange this Wednesday, backed by a reserve of 1,900 Bitcoin. They also pay all salaries in Bitcoin.
On the 17th of December:
➡️'Overton Window shifting rapidly Only in 2023, EU media was still gaslighting Bitcoin. Now - No negative environmental coverage in mainstream EU media publications for over a year - many media outlets (Including The Independent, Bloomberg, Reuters, The Street, The Hill, and Forbes) have started documenting Bitcoin mining's numerous environmental benefits (well documented in 13 peer-reviewed studies) - Germany's largest Telco is using Bitcoin mining to monetize its stranded energy - Finland's pioneering work obviating fossil-fuel heating by capturing the heat from Bitcoin mining rigs is being covered - 6 sustainability periodicals covering Bitcoin's environmental benefits - 3 media outlets including Forbes in the last 2 days have recognized that Bitcoin mining is an integral part of solving not just EU's Net Zero Emission Targets, but EU's energy crisis.' - Daniel Batten
➡️BlackRock has officially recommended a 2% allocation to Bitcoin. With global assets totaling $900 trillion, a 2% allocation would imply a Bitcoin valuation of $18 trillion, equating to approximately $900,000 per Bitcoin.
➡️Bitcoin Reserve bill for Ohio State put forward by Rep. Derek Merrin. Merrin: Today, I filed HB 703 to create the Ohio Bitcoin Reserve within the state treasury!
Provides state treasurer authority & flexibility to invest in Bitcoin. This legislation creates the framework for Ohio’s state government to harness the power of Bitcoin to strengthen our state finances. As the US dollar undergoes devaluation, Bitcoin provides a vehicle to supplement our state's portfolio and preserve public funds from losing value.'
➡️Bitcoin-exposed convertible bonds comprise 6% of the total convertible universe and have produced 20% of the YTD Returns: Barclays Looks like Bitcoin slowly eating into the debt market. Bonds were dying until Bitcoin bonds were introduced!
➡️European MP Sarah Knafo has called on the EU to reject the digital euro and establish a strategic Bitcoin reserve, warning against “totalitarian temptations” from the European Central Bank. Are you paying attention? The world is waking up.
➡️A first draft of an Executive Order for a Strategic Bitcoin Reserve has been published.
https://x.com/DavidFBailey/status/1869098934754570305
➡️'The total assets in the spot Bitcoin ETFs are now 55% of the value of known gold ETF holdings. • Bitcoin ETF AUM: $120.69 billion • Gold ETF AUM: $218.81 billion Out with the old, in with the new - Joe Consorti
➡️'If you're not saving in Bitcoin, you're not saving at all.' AnilSaidSo
On the 18th of December:
➡️Chinese car company Cango emerges as the third largest public miner. China? Mining? What about the ban? Guess the 100x banning did nothing.
➡️Fellow Noderunner Bram Kanstein:
Open letter to the Dutch government regarding the establishment of a National Bitcoin reserve:
'Geachte @Minister_FIN @eelcoheinen @KlaasKnot @DNB_NL Met deze brief wil ik uw aandacht vestigen op een urgente en strategisch kwestie: het opbouwen van een nationale Bitcoin reserve.
https://t.co/Wjdzf8xpDA
In English (to also copy and use in your own country): https://docs.google.com/document/d/1qCIbrGqYQeQNyiXRFMBJVZyRcePHWtdnWz__67NVuRo/edit?usp=sharing
➡️FED CHAIR J. POWELL: Fed is "not allowed to own Bitcoin". They weren't allowed to own Corporate Bonds before Covid either. Rules change...
➡️$11.5 trillion BlackRock said, "Bitcoin is no longer seen as the radical idea as it was 15 years ago." "Bitcoin is an emerging global monetary alternative."
➡️Rumor goes that the UAE has potentially already accumulated ~300K Bitcoin. If true, America is behind and needs to catch up quickly. Funny isn't it? 'We’ve gone from: Being concerned about the government killing Bitcoin in a 51% attack to Being concerned about the government buying tons of it.' - Alex Gladstein
➡️IMF and El Salvador finally reached an agreement....and at first, it's big yikes. El Salvador secured a $3.5 billion IMF financing package after agreeing to make accepting Bitcoin voluntary and unwinding the Chivo wallet. Not only are they eliminating Article 7 as previously reported, but they are also removing the ability for citizens to pay taxes in Bitcoin.
Meanwhile, President Bukele says: "The IMF, World Bank, FED, and mainstream media hate that we adopted Bitcoin."
Wait for it (have a look at the 20th of December)
On the 19th of December:
➡️Bitcoin dipped. While some of you were scared, MARA bought $166 MILLION worth of Bitcoin. They have bought $3.2 BILLION Bitcoin in just 6 weeks!
➡️Hut 8 today announced the purchase of approximately 990 Bitcoin for approximately $100 million, or an average of approximately $101,710 per Bitcoin. Combined with the Bitcoin held before this purchase, Hut 8’s strategic Bitcoin reserve now totals more than 10,000 Bitcoins with a market value of more than $1 billion as of December 18, 2024.
➡️15 consecutive days of inflows for U.S. Bitcoin ETFs. $ in millions.
Spot Bitcoin ETFs purchased about 2,750 BTC yesterday while miners only mined 450 BTC. Absolute. Scarcity.
On the 20th of December:
➡️Metaplanet has issued ¥5.0 billion ($31m) in bonds to accelerate Bitcoin purchases originally slated for 2025. Issued against the 12th Series moving strike warrants, the bonds will be redeemed with the warrant exercise proceeds.
➡️'Just one day after the IMF agreed to a $3.3b loan in return for making Bitcoin acceptance voluntary, El Salvador buys $1m Bitcoin, more than 10x their usual 1 Bitcoin per day purchase. I guess the IMF won...' -Bitcoin Archive
Bukele: ''Thanks for the free money, lets 10x our Bitcoin buys, and create a strategic digital asset partnership with Argentina & 25 other nations.'' Luke Mikic
Have a look at what they did on the 22nd of December.
➡️'Guys, this drawdown peak to trough was only 14.98%. It's that tiny little red stalactite on the right that you can't even see. Chill out.' -Joe Consort
➡️Brian Brooks, former Acting Comptroller of the Currency under the Trump administration, has joined the MicroStrategy Board of Directors. As Comptroller, he oversaw the federal banking system. Here's why this is a game-changing move for the company: https://x.com/btcspaceman/status/1870402056516952421
➡️$1.3 BILLION leveraged crypto positions WIPED OUT in just 24 hours. 1. don't do leverage 2. don't do shitcoins CrYpTo.
➡️$108 billion VanEck subsidiary Market Vector accepts #bitcoin as payment for the first time.
➡️Swiss company Relai purchases 13 Bitcoin for $1.2 million for their balance sheet. Relai now holds 30 BTC.
➡️Michael Saylor publishes the Bitcoin framework so the "United States can lead the global digital economy. "A strategic digital asset policy can strengthen the US dollar, neutralize the national debt, and position America as the global leader in the 21st-century digital economy—empowering millions of businesses, driving growth, and creating trillions in value.'
https://www.michael.com/digital-assets-framework
➡️'France's 5th largest bank, the €863 billion BPCE Group, to launch Bitcoin purchases for its 35 million customers in 2025.' -Bitcoin News
On the 21st of December:
➡️'MARA's announcement that recycling heat from Bitcoin mining rigs to heat the homes of almost 80,000 residents (1.4% of Finland's population) is the largest application yet for heat recycling. Here's why it's significant.' -Daniel Batten
Read the whole thread/post here: https://x.com/DSBatten/status/1870250495895302177
➡️Someone just mined a whole Bitcoin block by himself, claiming $311,000 in reward.
➡️Spot Bitcoin ETFs took in 4,349.7 BTC worth $423.6 MILLION this week despite the price of bitcoin falling. Miners only mined 2,250 BTC this week.
On the 22nd of December:
➡️El Salvador makes another purchase of 11 Bitcoin, pushing towards the recently announced goal of 20,000 BTC. Classic! They now have bought 25 Bitcoin worth over $2.4 million since securing its loan from the IMF. Bukele wasn't joking around!
➡️'When there's not enough Bitcoin for sale, billionaires will offer ANYTHING to own some. You'll be able to get: - Houses for 0.01 BTC - Cars for 0.001 BTC - A month of groceries for 0.00001 BTC They will give you everything you need... Because YOU have what THEY want.' -Rajatsonifnance
Regarding that a month of groceries for 0.00001 BTC,' everything is falling (price) against Bitcoin. What about fiat?
This is the single best long-run measure of food inflation. And it’s gone vertical. Now you do the math and ask yourself, go long Bitcoin or go long fiat?
You know what I will give you one more example, 'houses for 0.01 BTC'
Are you paying attention?
➡️Vancouver Mayor Ken Sim: Bitcoin is the top-performing asset of the past 16 years. It’s better than gold. It can’t be captured by a military force. It can put Vancouver on the map as a world leader in Bitcoin innovation.
On the 23rd of December:
➡️MicroStrategy has acquired 5,262 BTC for ~$561 million at ~$106,662 per Bitcoin and has achieved a Bitcoin Yield of 47.4% QTD and 73.7% YTD. As of 12/22/2024, they hodl 444,262 Bitcoin acquired for ~$27.7 billion at ~$62,257 per Bitcoin.
➡️Japanese public company Metaplanet buys 619.7 Bitcoin for ¥9.5 billion. As of December 23, Metaplanet holds 1,761.98 BTC acquired for ~¥20.87 billion.
➡️Publicly traded La Rosa Holdings Corp. now accepts Bitcoin as a payment option for its real estate agents.
➡️Bitcoin is the best-performing asset in 11 of the last 14 years. Jesse Myers: 'The only speculation about Bitcoin is how long until the mainstream realizes: -Bitcoin is the invention of absolute scarcity -Absolute scarcity is a once-in-a-species event (irreproducible) -Absolute scarcity is a black hole on the world's balance sheet, eating all SoV'
💸Traditional Finance / Macro:
On the 16th of December:
👉🏽'11 consecutive days of more decliners than advancers in the S&P500. First time since Sept 11, 2001.' - ZeroHedge
On the 18th of December:
👉🏽The S&P 500 falls over 3% in its largest post-Fed drop since March 2020.
🏦Banks:
👉🏽'This is the first time in the history of the data that over 40% of banks were tightening credit standards, and then went back to not tightening, without a recession having occurred.' - Lyn Alden One word: "Fiscal dominance" https://www.lynalden.com/september-2024-newsletter/
🌎Macro/Geopolitics:
On the 17th of December: BowTiedMara: 'Last 8 months of Massa (WITH PRICE CONTROLS):
6.6%
5.8%
6.3%
15.6%
14.3%
7.7%
15.7%
29.7%
Last 8 months of Milei (WITHOUT PRICE CONTROLS):
6%
4.8%
3%
3.2%
3.6%
2.3%
1.2%
0.9%'
What do we learn from this? Socialists want you dependent on them and price controls never work.
On the 18th of December:
👉🏽'SUMMARY OF FED CHAIR POWELL'S STATEMENT (12/18/24): 1. Inflation is "much closer" to 2% Fed target 2. Activity in the housing market has been weak 3. Wage growth in the United States has eased 4. The labor market is not a source of inflation pressures 5. The Fed can be more cautious in reducing interest rates 6. Inflation expectations remain "well anchored" The "Fed pivot" is taking another pause.' -TKL
👉🏽'The S&P 500 falls sharply after the Fed cuts rates by 25 basis points, but raises inflation forecast. The Fed reduced its outlook from 3 to 2 rate cuts in 2025 and raised inflation expectations from 2.1% to 2.5%. Inflation is back.' _TKL
👉🏽ZeroHedge: POWELL: ECONOMY GREW FASTER THAN EXPECTED IN SECOND HALF OF '24'. Maybe this had something to do with it?
👉🏽'Very rare: the Fed just lowered the overnight reverse repo rate (RRP) by 30 basis points, not 25 bps (the norm) So RRP rate is now at the floor of Fed Funds (no longer 5 bps above). This could ease money market rates & accelerate money flowing out of the Fed's RRP facility.' - Jack Farley In other words: Another liquidity injection.
On the 20th of December:
👉🏽'November PCE inflation, the Fed's preferred inflation measure, RISES to 2.4%, below expectations of 2.5%. Core PCE inflation was 2.8%, below expectations of 2.9%. However, this means CPI, PPI, and PCE inflation are all back on the rise.' -TKL
👉🏽'The new government funding bill would allow for ~$1.565 trillion in new borrowing before the debt ceiling binds again next March. +$1.5 trillion to the national debt... IN 3 MONTHS. If the government were a business, nobody would give them a dime. They'd be bankrupt tomorrow.' -Joe Consorti
On the 22nd of December:
👉🏽The global Fed pivot continues: 74% of world central banks have cut rates this year, the biggest share since 2021. The Bank of Canada has cut rates 5 times by 175 basis points, marking the most aggressive rate cut cycle among major central banks. The European Central Bank and the Swiss National Bank have lowered rates 4 times by 100 and 125 basis points, respectively. The Bank of England has cut twice by 50 basis points. As inflation rebounds, the pivot is at risk.' -TKL
🎁If you have made it this far I would like to give you a little gift:
Some fountain of Lyn Aldens wisdom:
https://www.lynalden.com/december-2024-newsletter/
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 81cda509:ae345bd2
2024-12-01 06:01:54
@ 81cda509:ae345bd2
2024-12-01 06:01:54

@florian | Photographer
Studio-Shoot
“Know thyself” is a phrase attributed to the ancient Greek philosopher Socrates, and it has been a cornerstone of philosophical thought for centuries. It invites an individual to deeply examine their own thoughts, feelings, behaviors, and motivations in order to understand their true nature.
At its core, “Know thyself” encourages self-awareness - an understanding of who you truly are beneath the surface. This process of introspection can uncover your strengths, weaknesses, desires, fears, and values. It invites you to acknowledge your habits, biases, and patterns of thinking, so you can make more conscious choices in life.
Knowing yourself also involves understanding your place in the larger context of existence. It means recognizing how your actions and choices affect others and the world around you. This awareness can lead to greater empathy, a sense of interconnectedness, and a more authentic life, free from the distractions of societal expectations or superficial identities.
In a practical sense, knowing yourself might involve:
-
Self-reflection: Regularly taking time to reflect on your thoughts, feelings, and experiences.
-
Mindfulness: Practicing awareness of the present moment and observing your reactions without judgment.
-
Exploration: Being open to trying new things and learning from both successes and failures.
-
Seeking truth: Engaging in honest inquiry about your motivations, desires, and beliefs.
-
Growth: Continuously learning from your past and striving to align your actions with your inner values.
Ultimately, “Know thyself” is about cultivating a deep, honest understanding of who you are, which leads to a more fulfilled, intentional, and peaceful existence.
-
-
 @ ee11a5df:b76c4e49
2024-12-24 18:49:05
@ ee11a5df:b76c4e49
2024-12-24 18:49:05China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ c1e6505c:02b3157e
2024-11-29 15:04:53
@ c1e6505c:02b3157e
2024-11-29 15:04:53This was my first attempt at hosting a podcast with another photographer while also juggling scene switches in OBS on the fly. Not sure what went sideways with Gardner's audio - podcast pleb mistake, clearly. But hey, trial and error, right?

click image to watch the full episode
That said, I’ve been wanting to interview photographers I admire for a while, so I was stoked to finally sit down with Gardner and explore his work. His creative use of lasers and external flash really caught my eye. It’s not my typical style, but the way he executes it - with such taste and precision - is impressive. I think you’ll find his process just as fascinating as I did.
During our conversation, we covered a lot - music, cameras, and some funny stories. One of my favorites was the time he went to photograph a mobile home with a tree growing through it, only to realize someone was still living there.
We took a deep dive into his portfolio, unpacking the intricate details behind his images. Hearing the story straight from the photographer hits differently than just reading a blurb about the series. Learning why a photo was taken and how it came together feels way more compelling once you understand the person behind the lens.
You can catch the full episode now on my PictureRoom YouTube channel. Like and subscribe if you’re feeling generous.
-
 @ 6f727e87:f52345c5
2024-12-24 17:39:28
@ 6f727e87:f52345c5
2024-12-24 17:39:28Why Choose the Golden Oak uPVC Front Door? A front door is more than an entryway; it’s the first impression of your home. The Golden Oak uPVC Front Door combines durability, elegance, and security, making it an exceptional choice for any homeowner seeking style and functionality.
 (https://decoridea.co.uk/collections/upvc-front-doors/products/upvc-pre-hung-full-front-door-set-24mm-right-hand-hung-bau-27-golden-oak?variant=40573467164821)
Introduction
The Golden Oak uPVC Pre-Hung Front Door is crafted for homeowners who value aesthetics and performance. Its robust 24mm design ensures long-lasting durability, while the right-hand hung feature makes it an ideal choice for versatile home layouts. With its pre-hung structure, installation is simple and efficient.
Key Features
Stylish Golden Oak Finish: Adds a warm, natural wooden aesthetic to your home.
Durable uPVC Material: Resistant to weather, warping, and corrosion.
Pre-Hung Structure: Easy and precise installation for a perfect fit.
Enhanced Security: Integrated locking systems for maximum safety.
Energy Efficiency: High insulation properties to reduce energy costs.
Benefits
Low Maintenance: Unlike wooden doors, uPVC requires minimal upkeep.
Cost-Effective: A durable and budget-friendly alternative to traditional materials.
Weather Resistant: Built to withstand harsh conditions without fading or cracking.
Timeless Design: Complements modern and classic architectural styles.
Eco-Friendly: Manufactured using sustainable processes.
Perfect Applications
This door is perfect for:
Residential Homes: Enhance the curb appeal of your property.
Commercial Spaces: Add an elegant and functional entryway to offices or buildings.
Renovation Projects: Upgrade your existing front door with a modern, efficient alternative.
How to Purchase
Decoridea offers a seamless buying experience. Visit the product page to learn more or order: Golden Oak uPVC Front Door. Browse specifications and explore customization options for a perfect fit.
Customer Stories
Homeowners love the Golden Oak uPVC Front Door for its combination of beauty and practicality. One satisfied customer shared: “Installing this door transformed the entrance to our home. It looks stunning and provides unmatched security!”
It has the perfect options to choose from may you choose mystical golden or the grovey black it looks top notch.
Transform your home's entryway today with the Golden Oak uPVC Front Door. Explore more and order here: Golden Oak uPVC Front Door.
(https://decoridea.co.uk/collections/upvc-front-doors/products/upvc-pre-hung-full-front-door-set-24mm-right-hand-hung-bau-27-golden-oak?variant=40573467164821)
Introduction
The Golden Oak uPVC Pre-Hung Front Door is crafted for homeowners who value aesthetics and performance. Its robust 24mm design ensures long-lasting durability, while the right-hand hung feature makes it an ideal choice for versatile home layouts. With its pre-hung structure, installation is simple and efficient.
Key Features
Stylish Golden Oak Finish: Adds a warm, natural wooden aesthetic to your home.
Durable uPVC Material: Resistant to weather, warping, and corrosion.
Pre-Hung Structure: Easy and precise installation for a perfect fit.
Enhanced Security: Integrated locking systems for maximum safety.
Energy Efficiency: High insulation properties to reduce energy costs.
Benefits
Low Maintenance: Unlike wooden doors, uPVC requires minimal upkeep.
Cost-Effective: A durable and budget-friendly alternative to traditional materials.
Weather Resistant: Built to withstand harsh conditions without fading or cracking.
Timeless Design: Complements modern and classic architectural styles.
Eco-Friendly: Manufactured using sustainable processes.
Perfect Applications
This door is perfect for:
Residential Homes: Enhance the curb appeal of your property.
Commercial Spaces: Add an elegant and functional entryway to offices or buildings.
Renovation Projects: Upgrade your existing front door with a modern, efficient alternative.
How to Purchase
Decoridea offers a seamless buying experience. Visit the product page to learn more or order: Golden Oak uPVC Front Door. Browse specifications and explore customization options for a perfect fit.
Customer Stories
Homeowners love the Golden Oak uPVC Front Door for its combination of beauty and practicality. One satisfied customer shared: “Installing this door transformed the entrance to our home. It looks stunning and provides unmatched security!”
It has the perfect options to choose from may you choose mystical golden or the grovey black it looks top notch.
Transform your home's entryway today with the Golden Oak uPVC Front Door. Explore more and order here: Golden Oak uPVC Front Door. -
 @ 1ef695e1:15351d5f
2024-11-29 14:21:00
@ 1ef695e1:15351d5f
2024-11-29 14:21:00After getting my ham licence in 2013 I found out about SOTA. I was enthusiastic as I have a long history of hiking in the mountains while a scout and then as a Scoutmaster. Now I was going to combine the two yet I immediately encountered a big problem. Very few South African summits were listed on the SOTA database and some of those listed did not even qualify as summits. I enquired of SOTA management and was told that "South Africa is on hold until all the summits are correctly mapped and checked." Only then could the summits be loaded to the database.
 Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria.
Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria.An individual prominence of 150m or more was easy to determine. Doing the mapping I found a lot of summits that were obvious, but finding the key col of each summit was more difficult. The older maps in South Africa actually had a lot of the key cols displayed and using my combined methods I proceeded to map summits one by one and add the data to a spreadsheet. Taking approximately 8 minutes to map a summit it took me months to map Limpopo. I missed summits where the summit is spread over a large area and though it qualifies due to a 150m or more prominence it does not look like a summit and these we added later.
I sent my mapping data to OM Andrew VK3ARR in Australia and received a thumbs up as to my data accuracy. I was pleasantly surprised when my Limpopo summits appeared on the SOTA database even though the rest of the country was still not done. I immediately started mapping the next province of Mpumalanga using my manual methods.
Sid Tylor ZS5AYC from Kwazulu - Natal, who became SOTA manager for South Africa, and I had been discussing the processes and he arranged access to online software with automated summit processing where we could just check key col position and all the data per summit was processed much quicker. Frustrating for me was that I could not see what the software was doing and we just checked key cols without knowing where the summit was or its other data.
I completed the remaining Mpumalanga summits using the software access and then completed the Western Cape summits after which Sid and I split the Northern Cape summits between us. The other provinces were processed by various operators including some much appreciated assistance from Australian hams.
A big thank you to all in SOTA management, in South Africa, those that assisted from Australia, as well as SOTA UK, for making it possible for us to enjoy the adventures of SOTA.
 Activating Renosterkop ZS/NC-272 in the Northern Cape
Activating Renosterkop ZS/NC-272 in the Northern Cape
-
 @ cf7ed325:050194cf
2024-12-24 14:39:35
@ cf7ed325:050194cf
2024-12-24 14:39:35Egypt is a treasure trove of history, culture, and natural beauty, offering countless opportunities for unforgettable day trips. Whether you're exploring ancient monuments, stunning coastlines, or vibrant cities, Egypt day tours provide the perfect way to experience the country’s wonders in a short time.
Luxor day tours take you back in time to the age of the Pharaohs. Visit iconic sites like the Valley of the Kings, Karnak Temple, and Luxor Temple, immersing yourself in Egypt's glorious history. For a serene yet culturally rich experience, Aswan day trips offer visits to the majestic Philae Temple, the Unfinished Obelisk, and the tranquil beauty of the Nile River.
If you're seeking coastal adventures, Taba trips and excursions provide a gateway to the Red Sea’s crystal-clear waters and captivating marine life. Alternatively, Alexandria day tours reveal the Mediterranean charm of Egypt’s second-largest city, featuring landmarks like the Catacombs of Kom El Shoqafa and the historic Alexandria Library.
For beach lovers, Hurghada day tours and Sharm El Sheikh day tours promise a mix of relaxation and adventure. Explore vibrant coral reefs, enjoy water sports, or simply unwind on pristine beaches. Meanwhile, Dahab day tours cater to those craving a laid-back vibe with opportunities for snorkeling, diving, and exploring the serene Blue Hole.
No visit to Egypt is complete without Cairo day tours, where you can marvel at the Great Pyramids of Giza, the Sphinx, and the treasures of the Egyptian Museum. Stroll through the bustling streets of Khan El Khalili Bazaar for a taste of local culture and craftsmanship.
Whether you’re a history enthusiast, nature lover, or adventure seeker, Egypt’s day tours have something for everyone. Plan your trip today and explore the beauty and diversity of this timeless destination
-
 @ d873a9c8:269f1419
2024-12-24 13:50:30
@ d873a9c8:269f1419
2024-12-24 13:50:30Let’s create a crossword that reveals the seed phrase for a wallet containing gifted Bitcoin.
Disclaimer: This method has several security risks. Be aware that the websites used to create the crossword, your browser, your printer, ChatGPT and other factors could be compromised. I am willing to accept these risks, as I only plan to gift an amount I am comfortable losing (which is very unlikely). Additionally, the Bitcoin will remain in the wallet for just a few hours, further reducing the odds of loss.
Creating a wallet
There are many ways to create a Bitcoin wallet, and I’m sure most of you have your own preferred method. Since this wallet will only be used for a few hours, I’m not overly concerned about creating a highly secure wallet.
I will download one of the following wallets from an app store:
- Muun
- Phoenix
Follow the steps to create either a 12-word or 24-word seed phrase (keep in mind that a 24-word phrase will make the crossword more challenging).
Make sure to note the public receive address for later use when sending the Bitcoin.
Creating Crossword Clues
You can, of course, create your own clues, but if you’re looking for an easier option, use the following prompt for ChatGPT. The format is crucial for the crossword-building website used in the next step.
Note: The (*List Number*) format is essential because the order of the words must match the correct sequence when the recipient recovers the wallet.
ChatGPT Prompt:
You are a professional game designer. Create clues for a crossword using the following words. format: *word* *definition* (*List Number*)
abandon ability able about above absent absorb abstract absurd abuse access accident
A.I. Hallucinations to Watch For:
-
Ensure the clues are logical and relevant.
-
Verify that the list is in the correct order, matching the wallet seed phrase.
Creating the Crossword
You should have a list of clues similar to the following:
abandon To leave behind completely or give up. (1)
ability The capacity to perform a task or skill. (2)
able Possessing the power or means to do something. (3)
about Concerning or in regard to. (4) above In or at a higher position. (5)
absent Not present in a specific place or setting. (6)
absorb To take in something, such as liquid or information. (7)
abstract Relating to ideas rather than concrete objects. (8)
absurd Ridiculously unreasonable or illogical. (9)
abuse The improper or harmful use of something. (10)
access The ability or permission to enter or use something. (11)
accident An unexpected event, often resulting in harm or damage. (12)
Now it’s time to create the crossword. There are many websites and methods available, but I found that (https://crosswordlabs.com) is intuitive and offers various shapes for your crossword.
Be sure to print or save both the puzzle and the solution.
The Gift Giving
Reminder to consider security implications
Before giving them the crossword send some bitcoin to the public receive address.
Once your gift recipient completes the crossword, instruct them to download a Bitcoin wallet app and recover their gift using their newly discovered seed phrase.
Finally, and most importantly, remind them to transfer the Bitcoin from the crossword wallet to a secure wallet. This is also a great opportunity to teach new Bitcoiners about security and best practices.
Have fun, Happy Holidays
Luka
-
 @ 63d59db8:be170f6f
2024-11-28 14:54:35
@ 63d59db8:be170f6f
2024-11-28 14:54:35Thrilled to share that we’ll be part of the 5th annual Press Play Art/Book Fair hosted by Pioneer Works!
We’re bringing the last 50 copies of ISSUE N.001 (from a run of just 500) to the table. This might be your final chance to snag one - and at a sweet discount, too. Trust me, it hits different when you can hold it, flip through it, and see the work up close.
Swing by, say hi, grab a copy, and maybe chat about whatever randomness is on your mind.
Oh, and yes, marbles will absolutely be on the table.


We’ll be at table 84 (in red with yellow box) in the way back, so voyage yourself down and find us there.
December 7/8th, 2024
Address: 159 Pioneer Street; Brooklyn, NY 11231

-
 @ 6bae33c8:607272e8
2024-12-24 13:45:43
@ 6bae33c8:607272e8
2024-12-24 13:45:43I went 5-0 last week when it didn’t matter. It’s always good to know you can step up in clutch.
Chiefs at Steelers — If the Chiefs win this, they can rest everyone for a few weeks. The Steelers are a tough matchup though because they play defense, will also run the ball and are fine with an ugly, low-scoring close game too. I’ll say Chiefs -2 and stay away.
Ravens at Texans — The Ravens are the best team in the AFC IMO, and the Texans are a fraud. Ravens -3.5 and probably lay the wood.
Seahawks at Bears — I’ll make it Seahawks -1.5 and stay away. If anything I’d take the Bears.
Chargers at Patriots — The Pats played the Bills tough, but I expect the Chargers to rough them up. I’ll say Chargers -3.5 and probably lay the wood.
Broncos at Bengals — Good defense, bad offense against bad defense, good offense. Let’s say Broncos +3 and lean Bengals.
Cardinals at Rams — The Cardinals looked good for a minute midseason, then fell apart. I’ll say Cardinals +4 and stay away.
Colts at Giants — The Giants are the 32nd best team in the league. I’ll say Colts -6.5 and probably lean Colts.
Jets at Bills — The Bills had a letdown last week against the Pats, but they’ll probably annihilate the Jets who are so dysfunctional. I’ll say Jets +13 and lean Bills.
Titans at Jaguars — This is a bum fight. Titans +2.5 and lean Jaguars, but stay away.
Raiders at Saints — Another bum fight unless Derek Carr plays. I’ll say Raiders +2.5 and lean Saints.
Panthers at Buccaneers — The Bucs might have blown their season, losing to the Cowboys. I’d expect a bounce-back, but the Panthers usually show up. I’ll say Panthers +6.5 and stay away.
Cowboys at Eagles — If Jalen Hurts doesn’t play, Cowboys +2.5. If Hurts plays, Cowboys +8.5. Stay away.
Dolphins at Browns — If DTR is still the starter, Dolphins -4.5, though Tua in freezing weather is not ideal. If Bailey Zappe plays, I’ll say Dolphins -2.5. I’m leaning Browns if it’s not DTR.
Packers at Vikings — These are equal teams. Let’s make it Packers +2.5. I’ll lean Packers, but probably stay away.
Falcons at Killer Redskins — I didn’t get a good look at Penix, and the KRs are probably spent after the huge comeback over their rival. Falcons +4.5 and lean Falcons.
Lions at 49ers — It’s always odd trying to handicap injuries. The 49ers have so many, and the Lions have lost their entire defense. Lions -6.5 and probably stay away.
-
 @ 6e24af77:b3f1350b
2024-12-24 13:31:19
@ 6e24af77:b3f1350b
2024-12-24 13:31:19big header
Longer form text goes here
More text and the options we have bold italic underlined
code~~strike~~ sup subsome code
a quote
a list of some items
- t
- t2
- t3
more lists
- a
- b
- c
smaller header
even smaller
more
aa
bb
| header | table header 1 | 2 | 3 | | :----- | -------------- | :----: | ----: | | normal | left | center | right | | normal | left | center | right | | | | | |
some code is here Image is here
Image is hereyoutube link directive custom is below
::youtube{#5W-jtbbh3eA}
-
 @ 70e6b44a:7c78b8e9
2024-12-24 13:12:37
@ 70e6b44a:7c78b8e9
2024-12-24 13:12:37the uva is a fruit.
-
 @ fd208ee8:0fd927c1
2024-11-28 12:50:49
@ fd208ee8:0fd927c1
2024-11-28 12:50:49GitHub is a software project graveyard
I think the main reason why we have so many lone wolf devs is an economic one. The fact that most FOSS devs aren't being paid for their code is making this worse, not better, as they work for fame, not fortune.
Nobody wants to use joint-repos because they don't want to give up or share the property rights to the contents. But because anything someone else does in a repo you own, also belongs to you, people are disincentized from contributing to your repo.
GitHub, especially, has incentivized this splintering and isolation. Everyone wants to have all changes in their own repo because they can profit best on repos listed directly under their own name, so long as they become popular. Maximize your 🟩 and ⭐ , like chips you can cash in for a prize.
And because forking other people's repos is the norm, rather than teamwork, requests for changes are usually ignored or responded to with "fork it, bro." Go away. Leave me alone. My repo is none of your business.
Too autistic, even for me
So, the developers separate their efforts into a million tiny repos that are mostly redundant with other ones, there's little interaction, progress is often surprisingly slow and stalls for months at a time, it's hard to keep track of what other people are doing (so that you can review and test changes), most of the effort is headed straight for the bin, people build the same things over and over, and communication is extremely limited.
This is a work environment that is unattractive for anyone who isn't autistic and/or highly introverted. Half of the fun of open-source development used to be the esprit de corps. Much has been said about #Bluesky, but it all misses a major point: that's where you go, if you want to work with other people, to build something large, polished, and impressive. It doesn't actually matter how many developers Nostr has, if they all only stare at their own plates.
Your repo coulda been a file folder.
Ironically, git was developed for collaboration on large projects with a distributed team. Now, everyone uses it for projects they work on alone. They put those projects on the Internet to market them. It's a cheap gimmick, not an earnest attempt at collaboration. Collaboration begins at the beginning.
-
 @ 3369d0a7:eb020757
2024-11-28 07:41:32
@ 3369d0a7:eb020757
2024-11-28 07:41:32Chef's notes
This recipe was a staple at every thanksgiving with family and now I share it with you nostr family. Absolutely one of my favorite side dish during the holiday. The corn pudding in the photo is NOT baked, I will update it. I hate stock photos.
Details
- ⏲️ Prep time: 15-20 min
- 🍳 Cook time: 30-40 min
- 🍽️ Servings: 6-8
Ingredients
- 2 cans of creamed corn
- 2c Milk
- 1 Box of Jiffy Cornbread Mix
- 3 eggs
- 1/4-1/3c sugar
- 1/2- green bell pepper or pepper onion blend
- 1/4TBsp vanilla
- 1/2tsp Salt
- 2TBsp Butter
Directions
- Grab medium saucepan and desired baking dish at least 9x9
- Place saucepan on medium-high heat
- Add butter and sauté pepper onion blend until tender
- Combine milk, eggs, sugar and vanilla, mix well
- Lather warmed (NOT HOT) baking dish with butter
- Sprinkle half a box of Jiffy corn bread mix in the baking dish
- Add both cans of creamed corn to peppers and onions
- Pour wet ingredients into slightly cooled creamed corn mixture
- Sprinkle the other half box of jiffy mix into the baking dish
- Incorporate the wet and dry ingredients in dish so there are no dry lumps
- Let set for 10 min before placing in a 325 degree oven for 30-40 minutes, until the center is solid and the edges are golden brown.
-
 @ 70e6b44a:7c78b8e9
2024-12-24 13:03:35
@ 70e6b44a:7c78b8e9
2024-12-24 13:03:35the goiaba is a fruit.
-
 @ 63d59db8:be170f6f
2024-11-27 18:16:01
@ 63d59db8:be170f6f
2024-11-27 18:16:01Tom Thiercelin is a French director and photographer based in Southern Europe. Tom has a particular interest in the study of societies’ dynamics and has graduated in Political Sciences and International Relations.
Sésimbra is a small Portuguese seaside town. A little piece of paradise located in the south of the country, the kind of place where time seems to have stopped.




-
 @ 70e6b44a:7c78b8e9
2024-12-24 12:10:58
@ 70e6b44a:7c78b8e9
2024-12-24 12:10:58the banana is a fruit.
-
 @ 7e6f9018:a6bbbce5
2024-12-24 11:52:35
@ 7e6f9018:a6bbbce5
2024-12-24 11:52:35Over the last decade, birth rates in Spain have dropped by 30%, from 486,000 births in 2010 to 339,000 in 2020, a decline only comparable to that seen in Japan and the Four Asian Tigers.
The main cause seems to stem from two major factors: (1) the widespread use of contraceptive methods, which allow for pregnancy control without reducing sexual activity, and (2) women's entry into the labor market, leading to a significant shift away from traditional maternal roles.
In this regard, there is a phenomenon of demographic inertia that I believe could become significant. When a society ages and the population pyramid inverts, the burden this places on the non-dependent population could further contribute to a deeper decline in birth rates.

The more resources (time and money) non-dependent individuals have to dedicate to the elderly (dependents), the less they can allocate to producing new births (also dependents):
- An only child who has to care for both parents will bear a burden of 2 (2 ÷ 1).
- Three siblings who share the responsibility of caring for their parents will bear a burden of 0.6 (2 ÷ 3).
This burden on only children could, in many cases, be significant enough to prevent them from having children of their own.
In Spain, the generation of only children reached reproductive age in 2019(*), this means that right now the majority of people in reproductive age in Spain are only child (or getting very close to it).
If this assumption is correct, and aging feeds on itself, then, given that Spain has one of the worst demographic imbalances in the world, this phenomenon is likely to manifest through worsening birth rates. Spain’s current birth rate of 1.1 may not yet have reached its lowest point.
(*)Birth rate table and the year in which each generation reaches 32 years of age, Spain.
| Year of birth | Birth rate | Year in which the generation turns 32 | | ------------------ | -------------- | ----------------------------------------- | | 1971 | 2.88 | 2003 | | 1972 | 2.85 | 2004 | | 1973 | 2.82 | 2005 | | 1974 | 2.81 | 2006 | | 1975 | 2.77 | 2007 | | 1976 | 2.77 | 2008 | | 1977 | 2.65 | 2009 | | 1978 | 2.54 | 2010 | | 1979 | 2.37 | 2011 | | 1980 | 2.21 | 2012 | | 1981 | 2.04 | 2013 | | 1982 | 1.94 | 2014 | | 1983 | 1.80 | 2015 | | 1984 | 1.72 | 2016 | | 1985 | 1.64 | 2017 | | 1986 | 1.55 | 2018 | | 1987 | 1.49 | 2019 | | 1988 | 1.45 | 2020 | | 1989 | 1.40 | 2021 | | 1990 | 1.36 | 2022 | | 1991 | 1.33 | 2023 | | 1992 | 1.31 | 2024 | | 1993 | 1.26 | 2025 | | 1994 | 1.19 | 2026 | | 1995 | 1.16 | 2027 | | 1996 | 1.14 | 2028 | | 1997 | 1.15 | 2029 | | 1998 | 1.13 | 2030 | | 1999 | 1.16 | 2031 | | 2000 | 1.21 | 2032 | | 2001 | 1.24 | 2033 | | 2002 | 1.25 | 2034 | | 2003 | 1.30 | 2035 | | 2004 | 1.32 | 2036 | | 2005 | 1.33 | 2037 | | 2006 | 1.36 | 2038 | | 2007 | 1.38 | 2039 | | 2008 | 1.44 | 2040 | | 2009 | 1.38 | 2041 | | 2010 | 1.37 | 2042 | | 2011 | 1.34 | 2043 | | 2012 | 1.32 | 2044 | | 2013 | 1.27 | 2045 | | 2014 | 1.32 | 2046 | | 2015 | 1.33 | 2047 | | 2016 | 1.34 | 2048 | | 2017 | 1.31 | 2049 | | 2018 | 1.26 | 2050 | | 2019 | 1.24 | 2051 | | 2020 | 1.19 | 2052 |
-
 @ 06b7819d:d1d8327c
2024-11-26 16:57:14
@ 06b7819d:d1d8327c
2024-11-26 16:57:14Hanlon’s Razor is a philosophical principle or adage that states:
“Never attribute to malice that which is adequately explained by stupidity.”
It suggests that when trying to understand someone’s actions, it is often more reasonable to assume a lack of knowledge, competence, or foresight rather than intentional harm or ill will. The principle encourages people to avoid jumping to conclusions about malicious intent and instead consider simpler, more mundane explanations.
Hanlon’s Razor is often used in problem-solving, interpersonal interactions, and organizational settings to promote understanding and reduce conflict. It’s part of a broader family of “razors,” which are rules of thumb used to simplify decision-making.
-
 @ 70e6b44a:7c78b8e9
2024-12-24 11:04:04
@ 70e6b44a:7c78b8e9
2024-12-24 11:04:04qwuheiuqwgbeikqgo487gqilergv8aqo4gwiluvgrusvflkisaegbrliusebrf
-
 @ 5601570c:444da7cc
2024-12-24 11:00:06
@ 5601570c:444da7cc
2024-12-24 11:00:06hey
-
 @ 79be667e:16f81798
2024-12-24 10:54:51
@ 79be667e:16f81798
2024-12-24 10:54:51hey
-
 @ 34f1aaa6:836e3cd6
2024-11-25 10:03:50
@ 34f1aaa6:836e3cd6
2024-11-25 10:03:50“Freedom is not something that you can inherit in your bloodstream. You have to fight for it, cherish it, preserve it all the time.”
-Nani Palkhivala
The ideas of individual liberty, natural rights, natural law, economic freedom, voluntary exchange and free market capitalism are not 'Western', 'American' or 'European'.
They were discovered and articulated by people using their reasoning faculties about what an ideal social, legal, political and economic order ought to be.
The origin of these ideas is the human faculty of reasoning about the world.
History has shown us that these ideas are necessary for human civilisation to not merely survive, but to prosper as well.
Rejecting them or denying their validity on the grounds of race, culture or religion is intellectual laziness. DNA, race, religion, culture and geographical location is not a determinant for an individual to grok the idea of liberty and discover his faculty of reason.
Additionally, imposing these ideas by force, like the European colonists and American globalists attempted for the 'sake of the greater good', will not work but for a short period. Liberty has to be a bottom-up, voluntary and spontaneous phenomenon that starts from the individual. You can't force a person or his society to be free and rich.
The Indian flag represents freedom.
India is a country that was born out of 'the freedom struggle' after all.
Freedom here means respect for the life project of an individual and the recognition of his and her natural rights to life, liberty and property. That's what real freedom means.
That we have had and continue to have numerous collectivist movements that subvert the ideal of freedom to mean 'freedom from material wants', 'freedom from foreign influence' and 'freedom from reason' has not changed what it truly means to be free.
The priority for an individual living in India then is not to develop a sense of identity, pride or reconciliation with his culture or country. That journey is his own choice and something that he ought to take voluntarily. It is not the business of any individual, organisation or government to force him to do this.
His priority rather is to discover his faculty of reason and realise that his natural rights and those of people he lives among is inalienable. It is to be responsible for his own fate and realise that the country or the world owes him nothing. It is to realise that the property, labour and wealth of fellow Indians is not his to command or appropriate by coercion, even if such an act is demanded of him by the 'will of the people'. What he may do to survive and live his life must come from voluntary exchange and peaceful cooperation by respecting the natural rights and life project of people he interacts with.
That is the path towards liberty in India.
-
 @ 79be667e:16f81798
2024-12-24 10:54:25
@ 79be667e:16f81798
2024-12-24 10:54:25goodbye
-
 @ 07907690:d4e015f6
2024-11-24 09:38:58
@ 07907690:d4e015f6
2024-11-24 09:38:58Karena orang tuanya yang berasal dari Hongaria telah melarikan diri dari rezim Soviet pascaperang untuk menetap di Amerika Serikat, Nick Szabo menganggap daerah Teluk California pada tahun 1990-an sebagai rumahnya. Di sana, ia termasuk orang pertama yang sering menghadiri pertemuan tatap muka "Cypherpunk" yang diselenggarakan oleh Timothy May, Eric Hughes, dan anggota pendiri kolektif kriptografer, programmer, dan aktivis privasi lainnya yang berpusat di sekitar milis tahun 90-an dengan nama yang sama.
Seperti Cypherpunk lainnya, Szabo khawatir dengan jaminan privasi yang semakin berkurang di era digital yang akan datang dan mengambil tindakan untuk membendung gelombang tersebut semampunya. Misalnya, di milis Cypherpunk, Szabo memimpin penentangan terhadap "Chip Clipper", sebuah chip yang diusulkan untuk disematkan di telepon, yang memungkinkan NSA untuk mendengarkan panggilan telepon. Szabo memiliki bakat khusus untuk menjelaskan risiko pelanggaran privasi tersebut dengan cara yang dapat diterima oleh orang-orang yang tidak memiliki latar belakang teknis, terkadang memberikan ceramah tentang topik tersebut atau bahkan membagikan brosur. (Chip tersebut akhirnya ditolak oleh produsen dan konsumen.)
Namun seperti Cypherpunk yang lebih berorientasi libertarian, minat Szabo dalam privasi digital adalah bagian dari gambaran yang lebih besar — ini bukan hanya tentang privasi saja. Terinspirasi oleh visi Timothy May sebagaimana yang ditetapkan dalam The Crypto Anarchist Manifesto, Szabo melihat potensi untuk menciptakan "Galt's Gulch" di dunia maya: domain tempat individu dapat berdagang dengan bebas, seperti yang dijelaskan oleh novel penulis libertarian Ayn Rand, Atlas Shrugged. Medan gaya pseudo-fisika dari cerita tersebut, May dan Szabo percaya, dapat digantikan dengan keajaiban kriptografi kunci publik yang baru-baru ini ditemukan.
“Jika kita mundur sejenak dan mencermati apa yang ingin dicapai oleh banyak cypherpunk, tema idealis utamanya adalah dunia maya Ghana di mana kekerasan hanya bisa menjadi khayalan, entah itu dalam Mortal Komat [sic] atau 'perang api',” tulis Szabo dalam milis Cypherpunks.
Namun, Szabo juga menyadari bahwa perusahaan bebas membutuhkan lebih dari sekadar enkripsi sebagai lapisan keamanan. Terinspirasi oleh penulis libertarian lainnya — ekonom Friedrich Hayek — ia menemukan bahwa dasar masyarakat manusia, sebagian besar, didasarkan pada komponen dasar, seperti properti dan kontrak, yang biasanya ditegakkan oleh negara. Untuk menciptakan alternatif dunia maya tanpa negara dan tanpa kekerasan, Szabo tahu bahwa komponen dasar ini harus dipindahkan ke ranah daring.
Beginilah cara Szabo, pada pertengahan 1990-an, mengusulkan sesuatu yang mungkin paling dikenalnya saat ini: kontrak pintar. Protokol komputer (yang saat itu masih hipotetis) ini dapat memfasilitasi, memverifikasi, dan menegakkan negosiasi atau pelaksanaan kontrak secara digital, idealnya tanpa memerlukan pihak ketiga mana pun. Seperti yang pernah dikatakan Szabo : "Pihak ketiga yang tepercaya adalah lubang keamanan." Lubang keamanan ini akan menjadi target peretas atau penjahat — serta negara-negara bangsa selama masa ketidakstabilan politik atau penindasan.
Namun kontrak pintar hanyalah sebagian dari teka-teki. Alat kedua yang dibutuhkan Szabo untuk mewujudkan "Galt's Gulch" mungkin bahkan lebih penting. Uang.
Uang Elektronik
Mata uang digital, uang tunai untuk internet, selalu menjadi tujuan utama Cypherpunk. Namun, hanya sedikit yang mendalami pokok bahasan tersebut seperti yang dilakukan Szabo.
Dalam esainya "Shelling Out: The Origins of Money," Szabo menjelaskan bagaimana — seperti yang pertama kali dihipotesiskan oleh ahli biologi evolusi Richard Dawkins — penggunaan uang telah tertanam dalam DNA manusia. Setelah menganalisis masyarakat pra-peradaban, Szabo menemukan bahwa orang-orang di berbagai budaya cenderung mengumpulkan benda-benda langka dan mudah dibawa, sering kali untuk dijadikan perhiasan. Benda-benda inilah yang berfungsi sebagai uang, yang pada gilirannya memungkinkan manusia untuk bekerja sama: "altruisme timbal balik" teori permainan melalui perdagangan, dalam skala besar dan lintas waktu.
Szabo juga sangat tertarik pada perbankan bebas, sebuah pengaturan moneter yang didukung oleh Hayek, di mana bank swasta menerbitkan mata uang mereka sendiri yang tidak terikat pada negara tertentu. Di bawah sistem seperti itu, pasar bebas sepenuhnya bebas menentukan mata uang mana yang akan digunakan. Meskipun merupakan ide baru saat ini (dan bahkan lebih baru lagi pada tahun-tahun sebelum Bitcoin), perbankan bebas merupakan kenyataan di Amerika Serikat pada tahun 1800-an, serta di beberapa negara lain.
Szabo juga melanjutkan untuk menerapkan minatnya dalam praktik dan menjual keahliannya sebagai konsultan perdagangan internet pada pertengahan 1990-an, jauh sebelum kebanyakan orang melihat potensi perdagangan daring. Yang paling menonjol, ia menghabiskan waktu bekerja di perusahaan rintisan DigiCash milik David Chaum, yang berkantor pusat di Amsterdam. Perusahaan Chaum memperkenalkan uang digital pertama yang pernah ada di dunia dalam bentuk eCash: sarana untuk melakukan pembayaran daring yang sama rahasianya dengan uang tunai di dunia nyata.
Namun, di DigiCash pula Szabo mengetahui risiko solusi Chaum. DigiCash adalah perusahaan terpusat, dan Szabo merasa terlalu mudah baginya dan orang lain untuk mengutak-atik saldo orang lain jika mereka mau. Bagaimanapun, pihak tepercaya adalah celah keamanan, dan risiko ini mungkin tidak lebih besar daripada risiko dalam hal uang.
“Masalahnya, singkatnya, adalah bahwa uang kita saat ini bergantung pada kepercayaan pada pihak ketiga untuk menentukan nilainya,” Szabo berpendapat pada tahun 2005. “Seperti yang ditunjukkan oleh banyak episode inflasi dan hiperinflasi selama abad ke-20, ini bukanlah keadaan yang ideal.”
Bahkan, ia menganggap masalah kepercayaan ini sebagai hambatan yang bahkan solusi perbankan bebas pada umumnya bisa mengalaminya: “[P]enerbitan uang kertas swasta, meski memiliki berbagai kelebihan dan kekurangan, juga bergantung pada pihak ketiga yang terpercaya.”
Szabo tahu ia ingin menciptakan bentuk uang baru yang tidak bergantung pada kepercayaan pada pihak ketiga mana pun.
Berdasarkan analisisnya terhadap uang prasejarah, Szabo telah menempuh perjalanan panjang dalam menentukan seperti apa bentuk uang idealnya. Pertama, uang tersebut harus “aman dari kehilangan dan pencurian yang tidak disengaja.” Kedua, nilainya harus “sangat mahal dan tidak dapat dipalsukan, sehingga dianggap berharga.” Dan ketiga: “Nilai ini [harus] diperkirakan secara akurat melalui pengamatan atau pengukuran sederhana.”
Dibandingkan dengan logam mulia seperti emas, Szabo ingin menciptakan sesuatu yang digital dan langka, di mana kelangkaan ini tidak bergantung pada kepercayaan pihak ketiga. Ia ingin menciptakan emas digital.
Logam mulia dan barang koleksi memiliki kelangkaan yang tidak dapat dipalsukan karena mahalnya biaya pembuatannya. Hal ini pernah menghasilkan uang yang nilainya sebagian besar tidak bergantung pada pihak ketiga yang tepercaya. Namun, logam mulia memiliki masalah. […] Jadi, akan sangat bagus jika ada protokol yang memungkinkan bit yang sangat mahal dapat dibuat secara daring dengan ketergantungan minimal pada pihak ketiga yang tepercaya, lalu disimpan, ditransfer, dan diuji dengan aman dengan kepercayaan minimal yang serupa. Bit Gold.
Bit Gold
Szabo pertama kali mencetuskan Bit Gold pada tahun 1998, meskipun ia baru menjelaskannya secara lengkap di depan publik pada tahun 2005. Skema uang digital yang diusulkannya terdiri dari kombinasi berbagai solusi, beberapa di antaranya terinspirasi oleh (atau menyerupai) konsep uang elektronik sebelumnya.
Properti utama pertama Bit Gold adalah proof of work, trik kriptografi yang digunakan oleh Dr. Adam Back dalam "mata uang anti-spam" miliknya, Hashcash. Proof of work merupakan biaya yang tidak dapat dipalsukan yang dicari Szabo, karena memerlukan sumber daya dunia nyata — daya komputasi — untuk menghasilkan bukti-bukti ini.
Sistem pembuktian kerja Bit Gold dimulai dengan "string kandidat": pada dasarnya angka acak. Siapa pun dapat mengambil string ini dan secara matematis menggabungkannya — "hash" — dengan angka acak lain yang baru dibuat. Berdasarkan sifat hashing, hasilnya akan menjadi string angka baru yang tampak acak: hash. Satu-satunya cara untuk mengetahui seperti apa hash ini adalah dengan benar-benar membuatnya — hash tidak dapat dihitung atau diprediksi dengan cara lain.
Triknya, yang juga digunakan dalam Hashcash, adalah bahwa tidak semua hash dianggap valid dalam protokol Bit Gold. Sebaliknya, hash yang valid harus, misalnya, dimulai dengan sejumlah angka nol yang telah ditentukan sebelumnya. Karena sifat hashing yang tidak dapat diprediksi, satu-satunya cara untuk menemukan hash yang valid adalah dengan coba-coba. Oleh karena itu, hash yang valid membuktikan bahwa pembuatnya telah mengeluarkan daya komputasi.
Hash yang valid ini, pada gilirannya, akan menjadi string kandidat Bit Gold berikutnya. Oleh karena itu, sistem Bit Gold akan berkembang menjadi rantai hash proof-of-work, dan akan selalu ada string kandidat berikutnya untuk digunakan.
Siapa pun yang menemukan hash yang valid akan secara harfiah memiliki hash tersebut, mirip dengan bagaimana orang yang menemukan sedikit bijih emas memilikinya. Untuk menetapkan kepemilikan ini secara digital, Bit Gold menggunakan registri kepemilikan digital : blok penyusun lain yang terinspirasi Hayek yang diusulkan oleh Szabo. Dalam registri ini, hash akan ditautkan ke kunci publik dari masing-masing pembuatnya.
Melalui registri kepemilikan digital ini pula, hash dapat ditransfer ke pemilik baru: Pemilik asli secara harfiah akan menandatangani transaksi dengan tanda tangan kriptografi.
Registri kepemilikan akan dikelola oleh "klub properti" Bit Gold. Klub properti ini terdiri dari "anggota klub" (server) yang akan melacak kunci publik mana yang memiliki hash mana. Solusi ini agak mirip dengan solusi basis data replikasi yang diusulkan Wei Dai untuk b-money; baik Szabo maupun Dai tidak hanya aktif di milis Cypherpunks, tetapi juga di milis tertutup yang membahas topik-topik ini.
Namun, alih-alih sistem proof-of-stake milik Dai untuk menjaga agar sistem tetap mutakhir, Szabo mengusulkan "Sistem Kuorum Bizantium." Mirip dengan sistem yang sangat penting bagi keamanan seperti komputer pesawat terbang, jika hanya satu (atau sebagian kecil) dari komputer ini yang tidak berfungsi, sistem secara keseluruhan akan tetap beroperasi dengan baik. Sistem akan bermasalah hanya jika sebagian besar komputer gagal pada saat yang sama. Yang penting, tidak satu pun dari pemeriksaan ini memerlukan pengadilan, hakim, atau polisi, yang didukung oleh monopoli negara atas kekerasan: Semuanya akan bersifat sukarela.
Meskipun sistem ini sendiri tidak sepenuhnya sangat ketat — misalnya Serangan Sybil ("sock puppet problem") — Szabo yakin sistem ini bisa berjalan sendiri. Bahkan dalam skenario di mana mayoritas anggota klub akan mencoba berbuat curang, minoritas yang jujur bisa bercabang ke dalam daftar kepemilikan yang bersaing. Pengguna kemudian dapat memilih daftar kepemilikan mana yang akan digunakan, yang menurut Szabo mungkin adalah yang jujur.
"Jika aturan dilanggar oleh pemilih yang menang, maka pecundang yang benar dapat keluar dari grup dan membentuk grup baru, mewarisi gelar lama," jelasnya. "Pengguna gelar (partai yang mengandalkan) yang ingin mempertahankan gelar yang benar dapat memverifikasi sendiri dengan aman kelompok sempalan mana yang telah mengikuti aturan dengan benar dan beralih ke grup yang benar."
(Sebagai contoh modern, ini mungkin dapat dibandingkan dengan Ethereum Classic, yang memelihara versi buku besar Ethereum asli yang tidak membatalkan kontrak pintar The DAO.)
Inflasi
Masalah berikutnya yang harus dipecahkan Szabo adalah inflasi. Seiring dengan semakin baiknya komputer dari waktu ke waktu, akan semakin mudah untuk menghasilkan hash yang valid. Ini berarti bahwa hash itu sendiri tidak dapat berfungsi sebagai uang dengan baik: hash akan semakin langka setiap tahunnya, sampai pada titik di mana kelimpahan akan melemahkan semua nilai.
Szabo menemukan solusinya. Setelah hash yang valid ditemukan, hash tersebut harus diberi cap waktu, idealnya dengan server cap waktu yang berbeda untuk meminimalkan kepercayaan pada hash tertentu. Cap waktu ini akan memberikan gambaran tentang seberapa sulitnya menghasilkan hash: hash yang lama akan lebih sulit diproduksi daripada hash yang baru. Pasar kemudian akan menentukan berapa nilai hash tertentu relatif terhadap hash lainnya, mungkin menyesuaikan nilainya dengan tanggal ditemukannya. "Hash 2018" yang valid seharusnya bernilai jauh lebih rendah daripada "Hash 2008" yang valid.
Namun solusi ini, tentu saja, menimbulkan masalah baru, Szabo tahu : "bagian-bagian (solusi teka-teki) dari satu periode (mulai dari detik hingga minggu, katakanlah seminggu) ke periode berikutnya tidak dapat dipertukarkan." Kepertukaran — gagasan bahwa setiap unit mata uang sama dengan unit lainnya — sangat penting bagi uang. Seorang pemilik toko ingin menerima pembayaran tanpa harus khawatir tentang tanggal uang tersebut dibuat.
Szabo juga menemukan solusi untuk masalah ini. Ia membayangkan semacam solusi "lapisan kedua" di atas lapisan dasar Bit Gold. Lapisan ini akan terdiri dari sejenis bank, meskipun bank yang dapat diaudit secara aman, karena registri Bit Gold bersifat publik. Bank-bank ini akan mengumpulkan hash yang berbeda dari periode waktu yang berbeda dan, berdasarkan nilai hash ini, menggabungkannya ke dalam paket-paket dengan nilai standar gabungan. "Paket 2018" akan mencakup lebih banyak hash daripada "paket 2008," tetapi kedua paket akan bernilai sama.
Paket-paket ini kemudian harus dipotong-potong menjadi sejumlah unit tertentu. Akhirnya, unit-unit ini dapat diterbitkan oleh "bank" sebagai eCash Chaumian yang bersifat pribadi dan anonim.
“[P]ansa pesaing menerbitkan uang kertas digital yang dapat ditukarkan dengan bit solusi yang nilai pasarnya sama dengan nilai nominal uang kertas (yakni mereka menciptakan kumpulan nilai standar),” jelas Szabo .
Dengan demikian, Bit Gold dirancang sebagai lapisan dasar seperti standar emas untuk sistem perbankan bebas di era digital.
Bitcoin
Pada tahun 2000-an, Szabo melanjutkan pendidikannya dengan meraih gelar sarjana hukum untuk memahami hukum dan realitas kontrak yang ingin ia gantikan atau tiru secara daring dengan lebih baik. Ia juga mulai mengumpulkan dan menerbitkan ide-idenya di sebuah blog yang sangat dihormati, “Unenumerated,” yang membahas berbagai topik mulai dari ilmu komputer hingga hukum dan politik, tetapi juga sejarah dan biologi. “Daftar topik untuk blog ini […] sangat luas dan beragam sehingga tidak dapat disebutkan satu per satu,” Szabo menjelaskan judulnya.
Pada tahun 2008 — 10 tahun setelah pertama kali mengusulkannya secara pribadi — Szabo mengangkat Bit Gold di blognya sekali lagi, hanya saja kali ini ia ingin mewujudkan implementasi pertama usulannya.
“Bit Gold akan sangat diuntungkan dari sebuah demonstrasi, pasar eksperimental (dengan misalnya pihak ketiga yang tepercaya menggantikan keamanan kompleks yang dibutuhkan untuk sistem nyata). Adakah yang mau membantu saya membuat kodenya?” tanyanya di bagian komentar blognya.
Jika ada yang menanggapi, tanggapan itu tidak disampaikan di depan umum. Bit Gold, dalam bentuk yang diusulkan Szabo, tidak pernah dilaksanakan.
Namun, Bit Gold tetap menjadi inspirasi utama bagi Satoshi Nakamoto, yang menerbitkan white paper Bitcoin di akhir tahun yang sama.
“Bitcoin merupakan implementasi dari proposal b-money Wei Dai [...] di Cypherpunks [...] pada tahun 1998 dan proposal Bitgold milik Nick Szabo,” tulis penemu Bitcoin dengan nama samaran di forum Bitcointalk pada tahun 2010.
Memang, tidak sulit untuk melihat Bit Gold sebagai rancangan awal Bitcoin. Selain dari basis data bersama catatan kepemilikan berdasarkan kriptografi kunci publik, rangkaian hash bukti kerja memiliki kemiripan yang aneh dengan blockchain Bitcoin . Dan, tentu saja, nama Bit Gold dan Bitcoin juga tidak terlalu jauh.
Namun, tidak seperti sistem seperti Hashcash dan b-money, Bit Gold jelas tidak ada dalam white paper Bitcoin. Beberapa orang bahkan menganggap ketidakhadiran ini begitu penting sehingga mereka menganggapnya sebagai salah satu dari beberapa petunjuk bahwa Szabo pastilah orang di balik julukan Satoshi Nakamoto: Siapa lagi yang akan mencoba menyembunyikan asal-usul Bitcoin seperti ini?
Meski demikian, meski mirip dengan Bit Gold dalam beberapa hal, Bitcoin memang menyertakan beberapa perbaikan atas desain Szabo. Secara khusus, di mana Bit Gold masih bergantung pada pihak tepercaya sampai batas tertentu — server dan layanan stempel waktu harus dipercaya sampai batas tertentu untuk tidak berkolusi — Bitcoin adalah sistem pertama yang memecahkan masalah ini sepenuhnya. Bitcoin memecahkannya dengan sangat elegan, dengan memiliki sistem bukti kerja yang diperlukan yang berfungsi sebagai sistem penghargaan dan mekanisme konsensus dalam satu sistem: Rantai hash dengan bukti kerja terbanyak dianggap sebagai versi sejarah yang valid.
“Nakamoto memperbaiki kekurangan keamanan signifikan yang ada pada desain saya,” Szabo mengakui pada tahun 2011, “yakni dengan mensyaratkan bukti kerja untuk menjadi simpul dalam sistem peer-to-peer yang tangguh terhadap Byzantine untuk mengurangi ancaman pihak yang tidak dapat dipercaya yang mengendalikan mayoritas simpul dan dengan demikian merusak sejumlah fitur keamanan penting.”
Lebih jauh, Bitcoin memiliki model moneter yang sangat berbeda dari yang diusulkan Szabo, dengan jadwal inflasi tetap yang sama sekali tidak terpengaruh oleh peningkatan daya hash. Seiring meningkatnya daya komputasi pada jaringan Bitcoin, itu artinya semakin sulit menemukan koin baru.
“Alih-alih pasar otomatis saya memperhitungkan fakta bahwa tingkat kesulitan teka-teki sering kali dapat berubah secara radikal berdasarkan peningkatan perangkat keras dan terobosan kriptografi (yaitu menemukan algoritma yang dapat memecahkan bukti kerja lebih cepat), dan ketidakpastian permintaan, Nakamoto merancang algoritma yang disetujui Bizantium yang menyesuaikan tingkat kesulitan teka-teki,” jelas Szabo.
“Saya tidak dapat memutuskan apakah aspek Bitcoin ini lebih banyak fitur atau lebih banyak bug,” tambahnya, “tetapi ini membuatnya lebih sederhana.”
Sumber artikel: bitcoinmagazine.com
Diterjemahkan oleh: Abeng -
 @ 9be5722a:6e939518
2024-12-24 07:17:09
@ 9be5722a:6e939518
2024-12-24 07:17:09この記事は、Nostr Advent Calendar 2024 🗓️24日目の記事です
- 12/23 opensats税務署編 著:@mono さん
- 12/24 準備中 著:@showV3 さん
本記事は技術的な知見などを含まない感想文です。
< br>タグが使えることを知らずに書いて調整していたので
不自然な改行が多いですが、最後まで読んでいただけると嬉しいです
内容目次
- 自己紹介
- Before Nostr
- Hello Nostr!
- Nostrの魅力: 自由と哲学
- おわりに
自己紹介
1浪目の浪人生です。目標は天文学者です。自立したいので来年は大学生です。
天文台があるのと南国育ちのため雪が降ってほしいのとで東北地方の大学を受験します。
Before Nostr
Nostrを始める前、SNSは主にInstagramとTwitterを使っていました
Instagramはリア友とのコミュニケーションツールとしての利用が主で
キラキラ大学生活と浪人生活とのギャップに耐えられないだろうと考えて3月末にアカウント停止。
TwitterはROM専で情報が手早く得られるツールとして利用していたつもりですが
全くいらない情報ばかりなこと、見ていない期間のメンタルの調子が良いことがわかり
情報収集の手段を見直した上でTwitterを削除し、そのうち
大学生なったらホームページつくってみたい!ブログやろう!
と考えるようになったため、受験のためにもSNSを完全にやめることにしました
SNSに費やしていた休憩時間を使い、積読を解消する作業や英字新聞の購読を始めました
Hello Nostr!
Nostrとの出会い
Nostrに出会ったきっかけは英文記事に
"Blueskyを離れたJack Dorsey"
という内容があり、Jack Dorseyが何をしているのか調べたことです
(Jack DorseyのWikipedia薄すぎ........のすたー?のすとら?)
キャリアの最後にNostrとありましたのでこいつを検索窓にぽいっ
そしてkojiraさんの記事に出会い
Nostr /ˈnɒstʃrə/
というよくわからない名前をした分散SNSプロトコルを知りました
さらに検索するとScrapboxがあったので誘導に乗るままこちらのかわいいサイトへ
そして私はnostterから生まれました(?)
nostr:nevent1qqspgrhygeu55pjnhyysaxd09dhdhhtu8w0dshxkf2xywelalxu70ecrfeuej わけもわからず初投稿 irisからだったかな?
インスタしか投稿したことないので何気にミニブログ初投稿Nostr村で過ごした1ヶ月
Zap解放と認証バッジ
まずはすべての機能を解放させようと思い、zapの設定に取り組みました。 nostr:nevent1qqsxj6w23mck4nwz204ftsnhqd32pcly44y6gcf9lvu403ahf8qrptc38n7nl scrapboxを参考に難なくクリア
しかしこの日から1週間は勉強の合間にドメイン認証に挑戦するも苦戦。。。 nostr:nevent1qqsz8jke4xazhx8arpx6jxd96a0f6k5rgkaklqwhshu90nkqknh9mtcwsmw06 原因はCORSの設定ミスだとおもったのですが
{"names":{"tansaibow":"公開鍵"}}とすべきところを
{"name":{"tansaibow":"公開鍵"}}としていたことが原因でした。
コピペしたつもりなんだけどなあ( ; ; ) nostr:nevent1qqsv2xj5z3yc3x9gk6x2g98x3x24a627n3mln9rlpm88gsvgmnde93c3nz2hc ここらから1ヶ月間Time Lineを斜め読みしつつちょくちょく言葉を投げてみます
Hello Nostrシリーズ nostr:nevent1qqsdwe46ykmyck9hxy4wjfx43mzhv92p70c5ytm9z8z6wak47460tzgs6na4e 1週間くらいでNostrがなんだか好きになってきたので書籍も購入しました
受験が終わったら再度、手を動かしながら読みます
今思えば紙で購入しておけばもっと嬉しくなれたと後悔しています
崇徳さんのイラストがすきです
LUMILUMI nostr:nevent1qqsqfzpps79nv8cht3xlpdzyx5jcy0kyme72sav6sgxpg3tra7yqykqyjl5yl nostr:nevent1qqszxqvedp0zaapneptx6xzvmvn7ltmfpz6dx97dctpw5hp90n0lens7cn5gt かわいい
ろぐぼ
28日目にしてはじめてやぶみちゃんからろぐぼをもらいました nostr:nevent1qqstuk49ull23668s5cwmzmzl5p6wjlg0tgt4ctke3nammhm0d5lyxscjxxhf ちなみに初回は失敗しました。初々しくてかわいいですね?
Nostrの魅力: 自由と哲学
秘密鍵、OSS、冗長構成! 自由が特徴でとてもインターネットらしくてクールです。
Nostrこそがインターネット!
ここに広がる独特な文化や人々の交流スタイルも魅力的です
第一印象ではエンジニアの溜まり場でしたが、実態はそう単純ではなく
エンジニアリングとユーザー体験が一体化している
というよりもむしろ、誰もがエンジニアでありユーザーであり
個人の裁量が各々の技術に委ねられるという形で自由が表現されています
確かに技術者の割合は比較的多いかもしれませんが
作りたいものを自由につくるという精神が随所にみられ、
技術と思想が相互に作用できる環境が全ユーザーに与えられているだけだと
現在はそのような印象を持っています
また、タイムラインが自動で流れるため
既存SNSのようにスワイプしてリロードしてポストを求めるというような
パブロフの犬的な強化がされないのがしばらく使っていて快適でした
依存度を高めないクライアントも自由に作れることも魅力的です!
そして何よりいろんな方がいて平穏賑やかで楽しいです nostr:nevent1qqsqrcuy22k4ax09yurlynp8c4jw08aq5kylu6006ltqqs0vks6wa2q9ammmn TLでは技術系の話題と日常的な話題が自然に絡み合っていて独特な雰囲気があります。
良くも悪くも棲み分けが進むほどの規模ではないNostr村
日を経るごとに村たる所以をひしひしと感じています
そのままで、村のままでもいいんだよ?
おわりに🌸
いつかNostrのなにかしら開発してみたいです。(漠然)
とりあえず3月まで受験にすべての時間をかけますが
大学生活と勉強とやりたいことと折り合いをつけつつ
技術を身につけてNostrを使いこなせたらいいなと思います
明日はAdvent Calendar最終日、ひゅうが霄さん(@showV3)が担当なさいます。
受験勉強の合間に書いたため拙い文章になりましたが
さいごまでお付き合いいただき、本当にありがとうございました!
メリークリスマス!🙌
-
 @ 50041f6c:cb61480b
2024-12-24 05:43:05
@ 50041f6c:cb61480b
2024-12-24 05:43:05SMS retail marketing has emerged as one of the most effective ways for businesses to connect with customers in today’s fast-paced digital world. With nearly everyone owning a mobile phone and frequently checking messages, SMS marketing offers a direct, personal, and highly efficient channel to engage customers, promote products, and boost sales. If you’re a retailer looking for innovative ways to increase revenue and build customer loyalty, SMS marketing might be the solution you’ve been seeking. This article will explore the benefits of retail SMS marketing and provide actionable strategies to help you harness its full potential.
Why SMS Retail Marketing Works SMS marketing stands out because of its unparalleled reach and engagement rates. Unlike emails that might end up in spam folders or social media ads that depend on algorithms, text messages are almost always delivered and read. Studies show that SMS messages boast a 98% open rate, with most being read within minutes of receipt. This immediacy and reliability make SMS an ideal tool for time-sensitive offers, promotions, and customer communications.
Additionally, SMS is a highly personal medium. Customers are more likely to engage with brands that deliver relevant, valuable content directly to their phones. Whether it’s a discount code, a flash sale notification, or a friendly reminder about loyalty points, SMS can create a stronger connection between retailers and their audience.
Key Benefits of SMS Retail Marketing 1. Instant Communication One of the biggest advantages of SMS is its speed. Messages are delivered within seconds, making it an excellent choice for time-sensitive campaigns. For example, retailers can send out a flash sale alert or notify customers about restocked popular items, prompting immediate action.
-
High Engagement Rates SMS outperforms most other marketing channels in terms of engagement. Customers are far more likely to read and respond to a text message than an email or social media ad. This makes SMS an effective way to drive traffic to your store or website.
-
Cost-Effective SMS campaigns are relatively inexpensive compared to traditional advertising methods like print or TV ads. Even small businesses with limited budgets can use SMS marketing to reach a large audience without breaking the bank.
-
Personalization Modern SMS marketing tools allow businesses to personalize messages based on customer preferences, purchase history, or location. This tailored approach increases the likelihood of conversion and strengthens customer loyalty.
-
Improved Customer Experience SMS can be used for more than just promotions. Retailers can leverage it to provide order updates, delivery notifications, and customer service responses, creating a seamless and satisfying shopping experience.
Strategies for Effective SMS Retail Marketing 1. Build a Quality Subscriber List The foundation of any successful SMS marketing campaign is a robust and engaged subscriber list. Encourage customers to opt-in by offering incentives such as discounts, free shipping, or exclusive access to sales. Ensure you’re collecting permission in a way that complies with legal requirements, such as the Telephone Consumer Protection Act (TCPA).
-
Craft Short, Clear Messages With SMS, brevity is key. Keep your messages short, clear, and actionable. Include essential details like the promotion, deadline, and a call-to-action (CTA). For example: “Flash Sale! 20% off all items today only. Shop now: [link]”
-
Use Timing to Your Advantage The timing of your messages can significantly impact their effectiveness. Send SMS campaigns during times when customers are likely to act, such as mid-morning or early evening. Avoid sending messages too late at night or too early in the morning, as this could annoy recipients.
-
Incorporate Exclusive Offers Make your SMS subscribers feel special by providing exclusive deals or early access to sales. This not only boosts engagement but also encourages more customers to join your SMS list.
-
Integrate SMS with Other Channels SMS marketing works best when combined with other strategies. Use SMS to complement your email campaigns, social media promotions, and in-store marketing. For instance, you can send a text reminding customers to check their email for a special coupon code or link to your latest Instagram post.
-
Monitor Performance and Optimize Track metrics like delivery rates, click-through rates, and conversion rates to gauge the success of your campaigns. Use this data to identify what works and refine your approach over time.
Compliance and Best Practices While SMS marketing offers immense potential, it’s essential to stay compliant with regulations to avoid legal issues and maintain customer trust. Here are some best practices to follow:
Get Consent: Always obtain explicit permission from customers before sending marketing messages. Provide Opt-Out Options: Include a clear way for recipients to unsubscribe, such as “Reply STOP to opt-out.” Limit Frequency: Avoid bombarding customers with too many messages. A few well-timed texts per month are often enough to drive results without overwhelming your audience. Protect Privacy: Store customer data securely and never share it with third parties without permission. Real-Life Examples of SMS Retail Marketing Success Many retailers have successfully used SMS marketing to drive sales and engagement. For instance, a clothing retailer might send a message like: “New arrivals are here! Get 15% off your first order. Shop now: [link]” Similarly, a restaurant could use SMS to notify customers about special deals: “Lunch special: Get a free drink with any entree today! Show this text to redeem.”
These examples highlight how SMS can be tailored to different industries and goals, delivering significant results.
Final Thoughts SMS retail marketing is a powerful tool for modern businesses looking to engage customers and boost sales. By leveraging its immediacy, high engagement rates, and personalization capabilities, retailers can create impactful campaigns that resonate with their audience. However, success requires a thoughtful approach, from building a quality subscriber list to crafting compelling messages and adhering to compliance regulations. When done right, SMS marketing can become a cornerstone of your retail strategy, driving revenue and fostering customer loyalty.
-
-
 @ d7c6d014:a6abb6b8
2024-11-23 18:40:47
@ d7c6d014:a6abb6b8
2024-11-23 18:40:47こんにちは!kohei です。
久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。
用意するもの
- Android 端末
- Orbot
- Citrine
- Amethyst
前提と下準備
今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。 Android 端末を用意して、2~4 のアプリをインストールしておいてください。
設定方法
それでは早速設定していきましょう。 まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。
設定が終了したら、ローカルリレーを起動します。
また、ここで表示されるポート番号をメモしてください。
次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛)
表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。
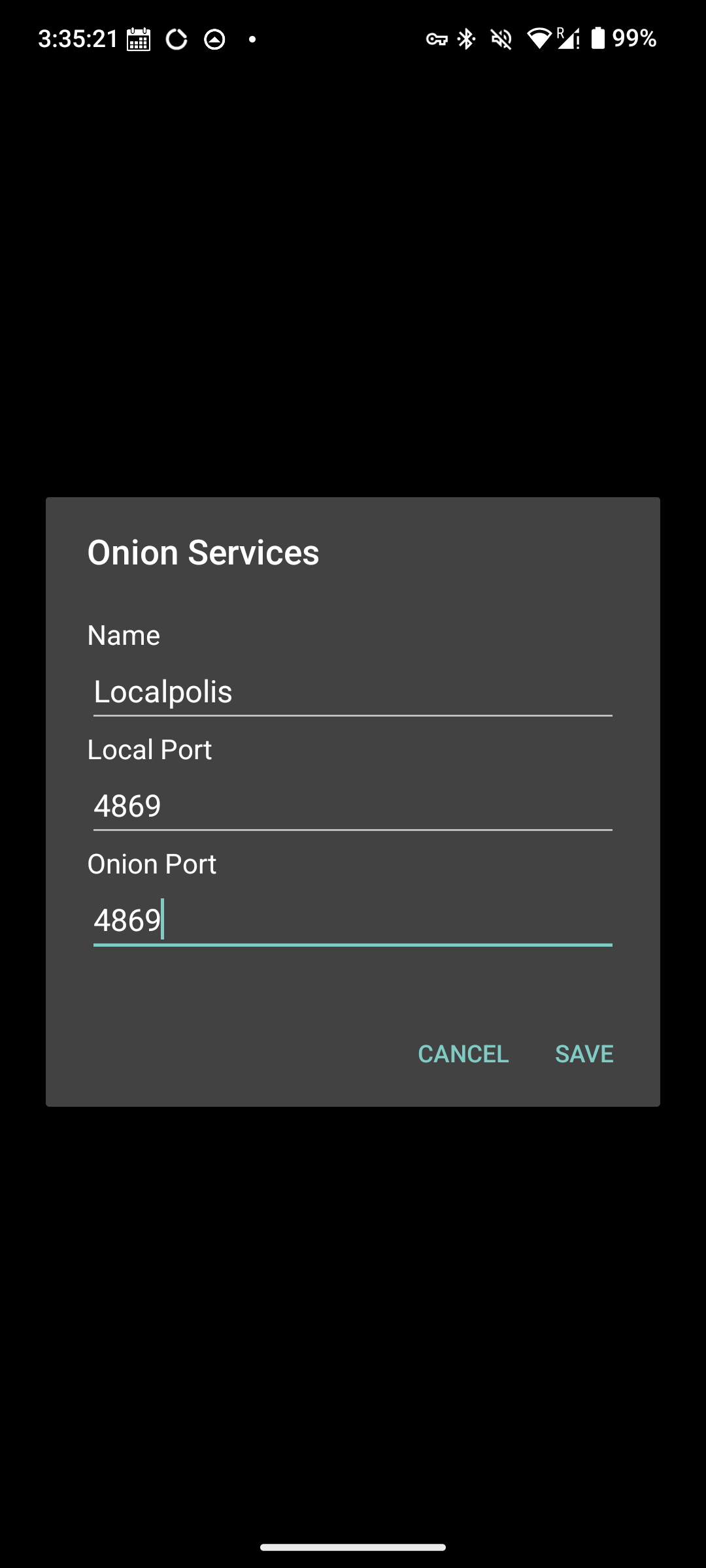
入力したら再起動を求められるので再起動してください。 再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです)
発行されたら、.onion アドレスをタップしてクリップボードにコピーします。
次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。
後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。
お疲れ様でした!
素敵な Nostr ライフを!
-
 @ 85cd42e2:0e6f2173
2024-12-24 03:41:30
@ 85cd42e2:0e6f2173
2024-12-24 03:41:30Are there long arcs of your life underwritten by unshakable exhaustion? A nameless and persistent tiredness that no amount of sleep satisfies. Don't gaslight yourself into thinking this is due to diet, which may be partly true, but the lion's share of that fatigue is a phantom one can never quite put a thumb on. There is a powerful tool to fight against this: Bitcoin.
Bitcoin helps one to see inflation for what it is. Not through the lens of government statistics and Keynsian pseudoscience, but truly see the sprawling roots of inflation diving deep into civilization day-to-day. For the first time, humanity can understand that it is being robbed, not by theft of dollars, but by dilution of dollars. All at once, the looming anxiety that persists even when dollars are abundant finally makes sense. Our subconscious mind is aware of the theft, even though it can't name that evil. The collective subconscious is working overtime, exhausting us, trying to warn us that poverty is looming. It is a warning not to trust the numbers. Our minds quietly thrash against the fiat debt trap that is closing in around us. It is winnowing down the destinies of men to a single narrow path decided by politicians and bankers. This is the root of fiat fatigue.
Three things accompany this revelation. Firstly, this knowledge is vindication for many who are haunted by the hubris of baby boomers who criticize young generations for not working hard enough. The next generation should be like their parents, who destroyed their backs, wills, and families for a coveted place in one of the most exploited economic classes in history: suburbia. While a luxurious form of serfdom, it is slavery nonetheless for most: slavery of the soul. Second, this knowledge is freedom. Once you can see how the trap functions, the escape hatch is clear: Bitcoin. Third, this knowledge is distilled grief. The realization that almost none of one's loved ones can make enough income to reach the economic escape velocity required to leave the fiat slavery system is heavy. Even those who escape pay a pound of flesh to defy fiat's gravitational pull. Most are spiritually deformed or emotionally maimed. Many walk around with this invisible yoke on their necks, being fooled into thinking it is they who have done something wrong, or worse, that the "rich," that vague and low-hanging scapegoat, have exploited them. They don't know that unmanipulated hard money, as it was intended to be, is life-giving and not burdensome. They don't know that real money is fair and just. They will carry this burden for the rest of their lives, and it will destroy many.
Are you weary? Stack Bitcoin like a religion; it will give you back stolen time and energy in spades. It will help humanity to see the world as it truly is, beautiful and peaceful. Bitcoin is rest.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 50041f6c:cb61480b
2024-12-24 02:41:48
@ 50041f6c:cb61480b
2024-12-24 02:41:48Bicycle accidents in San Francisco are an unfortunate reality for many cyclists navigating the city’s bustling streets. With its hilly terrain, narrow lanes, and high volume of traffic, San Francisco poses unique challenges for those who choose two wheels over four. While biking offers a sustainable and enjoyable way to travel, accidents can occur, leaving cyclists vulnerable to injuries and financial burdens. Understanding your legal rights and following safety practices can help protect both your physical and financial well-being.
The Prevalence of Bicycle Accidents in San Francisco San Francisco is a bike-friendly city, with many designated lanes and community initiatives encouraging cycling. However, the increasing number of cyclists sharing the road with cars, buses, and pedestrians inevitably leads to accidents. Data from local authorities reveals that intersections and areas with heavy traffic are hotspots for bicycle collisions. Common causes include distracted driving, dooring incidents (when a parked car door is opened into a cyclist’s path), failure to yield, and unsafe road conditions.
Bicycle accidents often result in significant injuries due to the lack of physical protection for cyclists compared to drivers. Injuries range from minor scrapes to serious conditions like fractures, head trauma, or spinal injuries. In some cases, these accidents can lead to life-altering disabilities or even fatalities.
Legal Rights for Cyclists in San Francisco If you are involved in a bicycle accident in San Francisco, it is crucial to understand your legal rights. California law recognizes cyclists as legitimate road users, giving them the same rights and responsibilities as motorists. This means that when an accident occurs, cyclists can seek compensation for damages caused by another party's negligence.
-
Filing a Claim After an accident, you may file a personal injury claim against the at-fault party to recover costs related to medical expenses, lost wages, property damage, and pain and suffering. To strengthen your claim, document the accident scene thoroughly. Take photos, gather witness statements, and obtain a copy of the police report. Seeking medical attention immediately is also essential, even if your injuries seem minor, as some symptoms may appear later.
-
Comparative Negligence California follows a "comparative negligence" system, which means you can still recover damages even if you are partially at fault. For instance, if you were not wearing a helmet or failed to use hand signals, the court may assign you a percentage of fault, and your compensation will be reduced accordingly.
-
Time Limit for Filing It’s important to note the statute of limitations for personal injury claims in California. Typically, you have two years from the date of the accident to file a claim. If the accident involves a government entity, such as a city bus, the time frame is significantly shorter—just six months.
Safety Tips for Cyclists While understanding your legal rights is essential, prevention remains the best strategy. Here are practical safety tips to minimize the risk of accidents and protect yourself on San Francisco’s roads.
-
Wear Proper Gear Always wear a helmet, even if it is not legally required for adult cyclists in California. A well-fitted helmet can significantly reduce the risk of head injuries in case of an accident. Reflective clothing and lights on your bike can also improve visibility, especially during foggy mornings or nighttime rides.
-
Follow Traffic Laws Obeying traffic laws is non-negotiable. Stop at red lights and stop signs, signal your turns, and yield to pedestrians. Treat your bicycle as you would a car when navigating the streets. San Francisco has strict laws regarding cycling behavior, and adherence to these rules not only keeps you safe but also strengthens your case if you’re involved in an accident.
-
Be Aware of Your Surroundings Defensive cycling is key to avoiding accidents. Stay vigilant for sudden car movements, potholes, and pedestrians crossing unexpectedly. Avoid riding in the "door zone" next to parked cars and always scan the road ahead for potential hazards.
-
Stick to Bike-Friendly Routes San Francisco offers a variety of bike-friendly routes and designated bike lanes. Use apps or maps to find the safest and most convenient paths for your journey. Routes like the Embarcadero or the Wiggle are popular among cyclists for their reduced traffic and ease of navigation.
-
Regularly Maintain Your Bicycle A well-maintained bike is less likely to contribute to accidents. Check your brakes, tires, and lights before every ride. Ensuring your bike is in good working condition can prevent mechanical failures that might lead to dangerous situations.
What to Do After a Bicycle Accident If you are involved in a bicycle accident, knowing what steps to take can protect your rights and help you recover compensation:
Ensure Safety First: Move out of traffic if you can, but avoid leaving the scene. Call for Help: Contact the police and request medical assistance if needed. Document the Scene: Take photos of the accident, including damages, injuries, and road conditions. Exchange Information: Get the other party's contact details and insurance information. Seek Legal Advice: Consult a personal injury lawyer experienced in bicycle accidents to guide you through the legal process.
Bicycle accidents in San Francisco are an unfortunate consequence of the city’s busy streets. However, cyclists can proactively stay safe and protect their rights. By following traffic laws, wearing proper gear, and knowing your legal options, you can reduce the risk of accidents and navigate the aftermath with confidence if one occurs. Cycling should be an enjoyable and sustainable mode of transport, and a little preparedness can go a long way in ensuring it remains that way.
-
-
 @ 50041f6c:cb61480b
2024-12-24 02:14:04
@ 50041f6c:cb61480b
2024-12-24 02:14:04Managing credit card bills can often feel like a daunting task, especially if balances start to pile up or payments are missed. However, with some strategic adjustments, it is possible to stay on top of your payments and use your credit cards as financial tools rather than liabilities. Here are five smart tips to help you manage your credit card bills efficiently.
-
Create a Monthly Budget and Stick to It One of the most effective ways to manage your credit card bills is to have a clear and realistic monthly budget. A budget helps you allocate your income toward necessities, savings, and discretionary expenses while ensuring you leave enough to pay your credit card balance. Track your spending regularly and categorize expenses to identify where you might be overspending. Apps or spreadsheets can make this process easier, but the key is discipline. Knowing how much you can afford to charge to your credit card each month prevents unnecessary debt and ensures you can pay your bill in full.
-
Always Pay More Than the Minimum Paying only the minimum amount due on your credit card might seem convenient, but it can lead to higher interest charges over time. Interest compounds on the remaining balance, which means you end up paying much more than what you originally owed. Whenever possible, pay off your entire balance each month. If that’s not feasible, aim to pay as much as you can above the minimum requirement. This approach reduces your balance faster and saves you money in the long run. Treat your credit card payment like any other essential monthly expense to prioritize it accordingly.
-
Set Up Payment Reminders or Auto-Pay Late payments not only lead to hefty fees but can also damage your credit score. Avoid this by setting up reminders through your bank’s app or phone calendar to alert you before the due date. Better yet, consider enrolling in auto-pay for at least the minimum payment to ensure you never miss a deadline. This way, even if life gets busy, your credit card bill won’t slip through the cracks. Just remember to keep enough funds in your bank account to cover the payment and avoid overdraft fees.
-
Use Your Credit Card Strategically How you use your credit card plays a huge role in how manageable your bills will be. Avoid impulsive purchases or charging amounts you can’t repay by the end of the billing cycle. Credit cards are best utilized for planned expenses that fit within your budget. Additionally, keep an eye on your credit utilization ratio, which is the percentage of your credit limit that you’re using. Experts recommend keeping this ratio below 30% to maintain a healthy credit score. By staying mindful of your spending habits, you can prevent your bills from spiraling out of control.
-
Review Statements Regularly for Errors It’s easy to overlook errors on your credit card statements, but reviewing them each month is essential. Fraudulent charges, incorrect billing, or unauthorized transactions can lead to inflated bills if not caught early. Take a few minutes to review each transaction on your statement and ensure they align with your receipts and spending records. If you spot any discrepancies, report them to your credit card provider immediately. Staying vigilant not only protects your finances but also helps you understand your spending habits better.
Managing credit card bills efficiently requires a combination of planning, discipline, and attention to detail. By budgeting wisely, paying more than the minimum, setting up payment reminders, using your card strategically, and reviewing your statements regularly, you can take control of your credit card payments and avoid unnecessary financial stress. With these strategies, your credit card can become a powerful tool for managing expenses and building credit, rather than a source of anxiety.
-
-
 @ a39d19ec:3d88f61e
2024-11-21 12:05:09
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
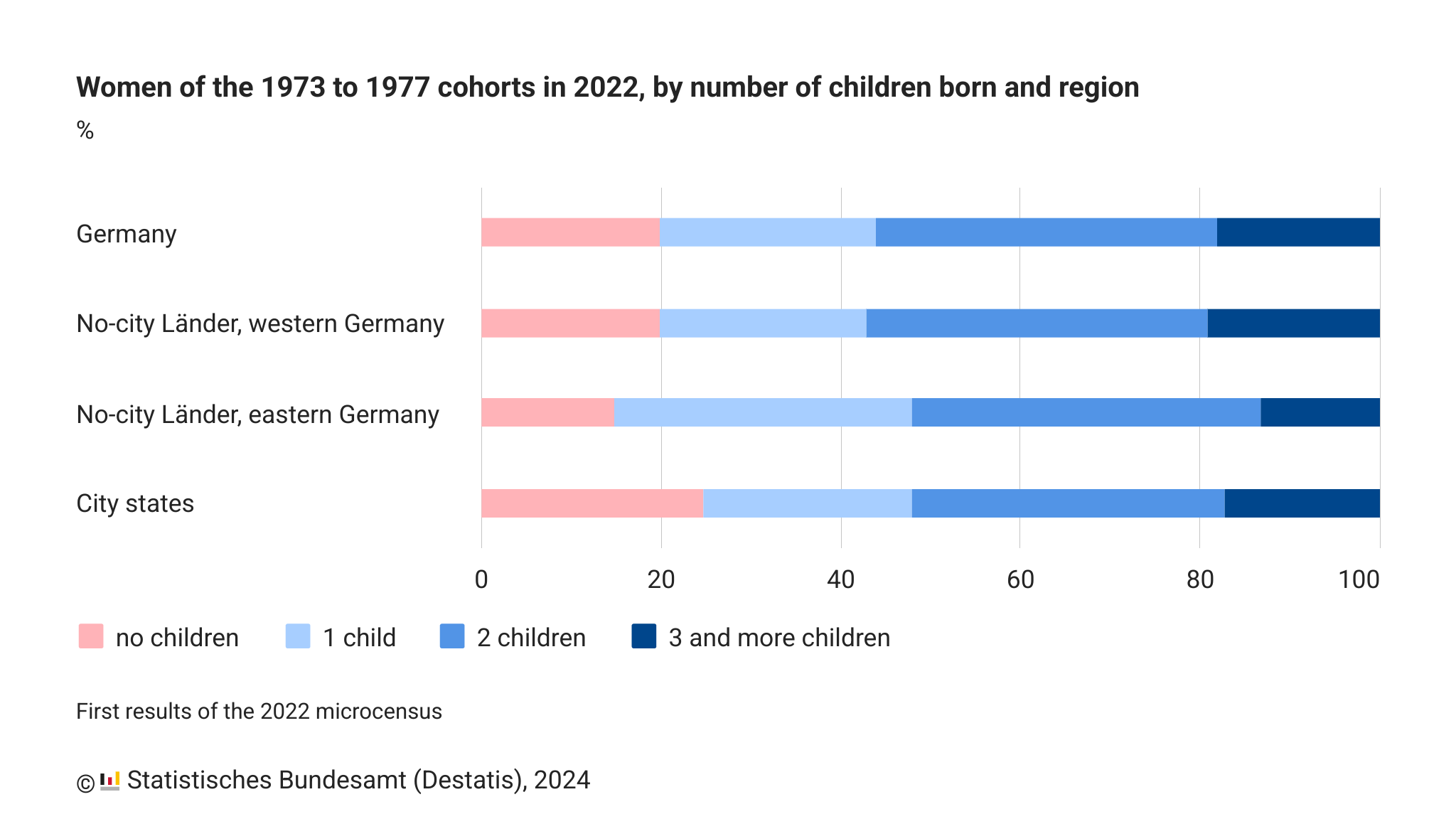
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ 16d11430:61640947
2024-12-24 01:56:24
@ 16d11430:61640947
2024-12-24 01:56:24Tokenomics offers a powerful framework for mid and premium service businesses, such as car detailing shops and fitness gyms, to differentiate themselves through customer-centric innovations, accountability, and transparency. With mature wallet implementations and adaptable platforms available today, the upfront costs of integrating tokenomics have significantly decreased, making this a practical investment for forward-thinking business owners.
This article explores how business owners can infuse tokenomics into their existing sales and marketing channels, achieve full accountability and transparency, and target premium clientele while reducing costs and increasing customer loyalty.
Why Tokenomics for Mid and Premium Services?
Mid and premium businesses are uniquely positioned to benefit from tokenomics due to their emphasis on high-quality services and personalized customer experiences. Tokenomics provides:
Transparency: Clear records of customer rewards, payments, and incentives, building trust.
Differentiation: A tech-forward approach that attracts customers willing to pay a premium for accountability and innovation.
Community Building: Tokens encourage customer loyalty, word-of-mouth referrals, and repeat visits.
Reduced Costs: Traditional marketing and customer acquisition costs can be significantly lowered through organic, token-driven growth.
Use Cases for a Car Detailing Shop
- Tokenized Rewards and Transparency for Premium Packages
Concept: Reward customers with tokens when they purchase mid-tier or premium detailing packages, incentivizing loyalty and upselling.
Implementation:
Use a mature wallet like Superhero.com (or similar) to issue tokens directly to customers.
Customers can track token rewards in their wallets, redeem them for discounts on future services, or gift them to others.
Benefits:
Transparency: Customers see exactly how and why they earned tokens, fostering trust.
Cost Reductions:
Decreased reliance on email promotions or paid advertising.
Tokens replace traditional discount programs, reducing dependency on price cuts.
Example: A $200 premium detailing package rewards customers with 50 tokens (redeemable for $10 off their next visit).
- Eco-Conscious Service Incentives
Concept: Reward customers for choosing sustainable services, such as waterless car washes or biodegradable cleaning products.
Implementation:
Create a tiered token system: more tokens for eco-friendly options.
Use tokens to educate and motivate customers about sustainable practices.
Benefits:
Differentiation: Attract eco-conscious premium customers.
Cost Reductions:
Free advertising from word-of-mouth and social media shares.
Savings from reduced print and digital ad campaigns.
Example: Customers choosing a $250 eco-premium package receive 75 tokens, building a loyal base while showcasing environmental commitment.
- Token-Powered Prepaid Packages
Concept: Offer prepaid tokens for specific services, locking in revenue and encouraging repeat visits.
Implementation:
Sell tokens in bundles (e.g., 1 token = 1 detailing session).
Customers can track usage and balances in their wallets.
Benefits:
Transparency: Prepaid tokens ensure accountability for services delivered.
Cost Reductions:
Reduces dependency on financing or loans for cash flow.
Cuts costs on managing paper-based gift cards or subscriptions.
Example: Sell a 5-service token bundle for $900, offering $100 in savings compared to single purchases.
Use Cases for Fitness Gyms
- Tokenized Memberships with Accountability
Concept: Replace traditional membership fees with tokens that customers use for gym access, classes, or personal training.
Implementation:
Tokens can represent membership credits redeemable for services.
Tokens can be tracked in wallets, ensuring transparency for customers.
Benefits:
Accountability: Customers see exactly where their money goes.
Cost Reductions:
Reduces customer churn, lowering re-engagement campaign costs.
No need for expensive subscription management tools.
Example: A premium gym charges $150/month for 150 tokens, which members redeem for access and exclusive services.
- Gamified Challenges for Premium Customers
Concept: Introduce challenges with token rewards for achieving fitness milestones (e.g., attending 20 classes in a month).
Implementation:
Use mature platforms like Loyalty Wallets to distribute and track tokens.
Tokens can be redeemed for merchandise, premium classes, or exclusive training sessions.
Benefits:
Differentiation: Builds an engaged and motivated premium customer base.
Cost Reductions:
Gamification reduces reliance on paid social media ads to maintain member interest.
Fewer cancellations due to higher engagement levels.
Example: A premium member completing a “30-Day Strength Challenge” earns 100 tokens, redeemable for $20 off their next personal training session.
- Referral Incentives Powered by Tokens
Concept: Reward members who bring friends to the gym with tokens instead of discounts, maintaining service value.
Implementation:
Issue referral tokens via a wallet platform.
Friends who join also earn tokens, kickstarting their engagement.
Benefits:
Cost Reductions:
Eliminates reliance on costly “first month free” campaigns.
Organic referrals reduce CAC by 10-20%.
Transparency: Referral token rewards are easy to track and validate.
Example: A member referring a friend receives 50 tokens (worth $10), while the friend gets 25 tokens (worth $5) upon joining.
Cost Reductions Through Existing Channels
- Reduced Dependency on Ads:
Tokenomics promotes organic growth through referrals, social sharing, and gamification, reducing reliance on paid advertising.
- Streamlined Customer Engagement:
Existing email and social media campaigns can integrate token rewards to increase effectiveness while reducing frequency and cost.
- Prepaid Revenue Streams:
Tokenized prepaid packages stabilize cash flow, reducing the need for external financing or discounts.
- Elimination of Legacy Programs:
Replace costly gift card systems, print loyalty cards, and complex subscription management software with blockchain-based wallets.
Accountability and Transparency for Premium Clientele
- Immutable Records:
Blockchain-based tokens ensure that all transactions, rewards, and redemptions are recorded immutably, building customer trust.
- Real-Time Tracking:
Customers can track token balances and usage through intuitive wallet apps, ensuring complete visibility.
- Elimination of Fraud:
Tokens cannot be duplicated or manipulated, reducing fraud risk in loyalty and reward programs.
Conclusion
For mid and premium service businesses, tokenomics represents a practical, scalable way to build trust, enhance customer engagement, and reduce costs in traditional sales and marketing channels. By leveraging mature wallet implementations and integrating token rewards into existing operations, business owners can achieve transparency, accountability, and long-term loyalty.
With reduced upfront costs, tokenomics can unlock immediate benefits like improved cash flow, lower customer acquisition costs, and increased lifetime value, making it a compelling strategy for growth in today’s competitive landscape.
-
 @ a367f9eb:0633efea
2024-12-23 23:49:44
@ a367f9eb:0633efea
2024-12-23 23:49:44Through my work as a consumer advocate, both as the deputy director of the Consumer Choice Center and a Fellow at the Bitcoin Policy Institute, I’ve contributed to various model policies that can be enacted at a state-level in the United States to help advance Bitcoin.
Working with state lawmakers, policy organizations, and fellow passionate bitcoiners, these are some of the model policies we offer open-source to anyone who would like to pass something similar in their state. An active list can be found on GitHub.\ \ Smart Cryptocurrency Rules Act\ \ –This model policy was adopted by the American Legislative Exchange Council on July 29, 2022.\ \ Reject CBDCs and Protect Financial Privacy Act\ \ –This model policy was adopted by the American Legislative Exchange Council on August 28, 2023.
–This model policy was SIGNED into law in the state of SOUTH DAKOTA on February 27, 2024 as HB1161.
–This model policy was SIGNED into law in the state of INDIANA on March 11, 2024 as SB180.
–This model policy was SIGNED into law by the state of UTAH on March 13, 2024 as HB164.
–This model policy was SIGNED into law in the state of LOUISIANA on June 19, 2024 as HB488.
–This model policy was SIGNED into law by the state of GEORGIA on July 1, 2024 as HB1053.
–This model policy was SIGNED into law by the NORTH CAROLINA GENERAL ASSEMBLY overriding a gubernatorial veto on September 9, 2024 as H690.
–This model policy was PASSED by the MISSOURI STATE HOUSE on March 5, 2024 as HB1676.
–This model policy was INTRODUCED into the MISSOURI STATE SENATE on December 1, 2023 as SB826.
–The model policy was INTRODUCED into the IOWA LEGISLATURE on February 7, 2024 as HF2358.
**\ PURPOSE\ \ The purpose of the GitHub page is to provide state and local legislators with a template of consumer-friendly policies on Bitcoin, cryptocurrencies, and decentralized finance.\ \ As model policies, these serve the purpose of providing general guidelines or goals to achieve in state legislation, and will therefore require various amendments, customizations, and accommodations with existing laws and regulations.\ \ State lawmakers and their staff are encouraged to take parts, or the whole, of these model policies to help usher in consumer-friendly policies on cryptocurrencies and decentralized finance in their jurisdiction.\ \ Members of the public are encouraged to suggest their own edits.\ \ GITHUB MODIFICATIONS AND COMMITS\ \ This GitHub repository will serve as the living model for these model policies.\ \ Edits, modifications, and additions are welcome by all. Doing so helps better crowdsource the most appropriate and beneficial rules on digital assets such as Bitcoin and its crypto-offspring, as well as any industries, projects, or protocols that may support them.\ \ Considering the complex nature of digital assets and decentralized blockchain technology, there are inevitably concerns that are not addressed by these model policies. However, this repository should serve as collection of templates for future action and language, while remaining loyal to the consumer-friendly principles of open and decentralized blockchains and related industries.\ \ Updates can be found on GitHub here: https://github.com/yaeloss/Bitcoin-Model-Policies
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 6ad3e2a3:c90b7740
2024-11-19 13:29:41
@ 6ad3e2a3:c90b7740
2024-11-19 13:29:41Assuming the outgoing administration doesn’t create a catastrophic crisis to avoid accountability, I feel things are largely settled for the short term on the geopolitical front. The Ukraine War should end soon, there should hopefully be a detente in the Middle East, and the adults can get to work on creating a bitcoin strategic reserve, while severely slashing government to begin working on the national debt. The ordinary person can get back to worrying exclusively about ordinary person stuff like health, wealth and personal relationships.
Not that you should ever neglect those things, but when free speech is under attack, the state is forcing you to take medicine in violation of your basic rights and imbeciles are fomenting World War 3 to launder money to their arms manufacturing cronies, you have to interrupt the scheduled programming for engagement in politics which nobody should want.
But going back to mundane ordinary life is a bit of a comedown after all the drama — remember there were two assassination attempts, one of which grazed Trump’s ear! The chaos that could have unleashed is almost unimaginable.
One thing that happened to me (and a lot of people I know) during Covid is we were forced to become more resilient. It’s not easy learning what you thought was a corrupt but not-that-important state would actively disrupt your life so severely in violation of the law and without any valid scientific basis. That the corporate media would gaslight you and foment compliance and division only augmented the stress and sense of despair. In order to retain one’s sanity in the face of so much capitulation and abdication of rational sense-making one had to reach deeper within, trust one’s own judgment and connect with one’s core values more entirely.
Now that we’ve hopefully defeated those retarding forces, a golden age of innovation and prosperity might be upon us. But I can’t go back to being the person I was before, primarily concerned about making money, living a comfortable and fulfilling life and handling my day to day responsibilities. It feels like there is something bigger. Having a false and destructive reality imposed on us from the outside drove us to get in touch with something real on the inside, and now that the door has been opened, we have no choice but to go farther into wherever it leads.
I’ve been reading a series of books lately on the topic of exploring the inner space, the brain-mind quantum machine that’s capable of perceiving aspects of reality beyond the narrow spectrums detectable by the senses. We are not simply animals who survive for a time to reproduce the species and optimize for pleasure while avoiding pain. (Even animals are likely more than that, too.) There is a sublimity to our existence, and now we are aware, not just theoretically, but in practice because we were forced to locate it.
There is no point in trying to describe it. It will either sound like magical thinking or be too slippery to grasp. The words are like the proverbial finger pointing at the moon — if you fixate on the finger, you miss the moon. It doesn’t matter what your concepts are either. “The Simulation,” Hinduism, Buddhism, Christianity, the Tao, the quantum foam, the Kabbalah, Sufism, whatever. I don’t care, use whatever works to take you away from the map and into the territory.
But into the territory we must go. There is no turning back.
-
 @ dff95033:862fbf40
2024-12-23 20:52:00
@ dff95033:862fbf40
2024-12-23 20:52:00Você sabia que o Bitcoin foi uma das melhores escolhas de investimento em 2024, superando até mesmo commodities tradicionais como ouro, soja e gás natural?
Chamado por alguns de “Dinheiro Mágico da Internet”, o Bitcoin provou ser mais do que isso, com um crescimento exponencial ao longo dos anos, destacando-se especialmente em 2024
📊 Confira os números impressionantes:
| Commodity | Ganho(%) | | --- | --- | | 🥇Cacau | 200% | | 🥈Bitcoin | 145% | | 🥉Suco de Laranja | 50% | | Café Arábica | 40% | | Gás Natural | 30% | | Ouro | 20% | | Carne Suína | 10% | | Paládio | 5% | | Soja | 0% |
Bitcoin deixou a concorrência para trás em 2024.
 ## 🔍 O que impulsionou o Bitcoin em 2024?
## 🔍 O que impulsionou o Bitcoin em 2024?Se o cacau liderou com 200% graças a problemas de oferta global, o Bitcoin brilhou por outros motivos:
- Demanda Crescente: Cada vez mais pessoas buscaram o Bitcoin como reserva de valor.
- Adoção Institucional: Um aumento significativo de 30% na adoção por grandes instituições, de acordo com dados da Glassnode.
- Busca por Segurança: O Bitcoin continuou sendo o principal ativo digital descentralizado, atraindo investidores de diferentes perfis.
- Halving: Em abril de 2024, ocorreu o "halving" do Bitcoin, um evento onde a recompensa que os mineradores recebem por adicionar transações ao blockchain é reduzida pela metade, de 6,25 para 3,125 Bitcoins por bloco. Isso diminui a oferta de novos Bitcoins, tornando-os mais raros e, por consequência, aumentando seu valor.
Esses fatores consolidaram o Bitcoin como o segundo ativo mais rentável do ano, com 145% de valorização.
💡 Por que investir em Bitcoin agora?
1️⃣ Potencial de Crescimento: Historicamente, o Bitcoin mostra ciclos de valorização exponencial. Em 10 anos, um investimento inicial de $ 100 em Bitcoin poderia valer hoje $ 26.931,1, segundo dados do CoinMarketCap.\ 2️⃣ Diversificação: O Bitcoin frequentemente se comporta de maneira independente em relação a ativos tradicionais, oferecendo uma oportunidade para diversificação de carteira, com correlações de preço às vezes negativas com ações e commodities.\ 3️⃣ Facilidade de Acesso: Com a Stackfy, você já pode ter os seus bitcoins com apenas R$ 25, de forma simples, rápida e segura!
⚠️ Atenção: Investir em criptomoedas envolve riscos devido à alta volatilidade do mercado. Sempre faça sua própria pesquisa e considere suas tolerâncias de risco antes de investir.
📈 Não perca tempo!
O Bitcoin está mostrando que o futuro dos investimentos está nas mãos de quem acredita em inovação. Prepare-se para 2025 e além! 🌟
➡️ Ação: Aproveite essa oportunidade única e faça parte da revolução financeira. Explore plataformas confiáveis como e comece sua jornada no Bitcoin hoje! 🚀
Referências:
-
BLOOMBERG. Cocoa caps 2024 as biggest commodity winner. Acesso em: 21 dez. 2024.
-
MARKETWATCH. Bitcoin valuation trends. Acesso em: 21 dez. 2024.
-
THE WALL STREET JOURNAL. Cocoa surges past $12,000 on supply concerns. Acesso em: 21 dez. 2024.
-
GLASSNODE. Fasanara Digital + Glassnode Report: Institutional perspectives on digital assets. Acesso em: 21 dez. 2024.
-
COINMARKETCAP. Bitcoin (BTC) preço, gráfico, capitalização de mercado. Acesso em: 21 dez. 2024.
-
COINGECKO. Bitcoin versus Traditional Assets: Price Returns. Acesso em: 21 dez. 2024.
-
 @ b83e6f82:73c27758
2024-12-23 19:31:31
@ b83e6f82:73c27758
2024-12-23 19:31:31Citrine 0.6.0
- Update dependencies
- Show notifications when importing, exporting, downloading events
- Change database functions to be suspending functions
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.6.0.txtandmanifest-v0.6.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.6.0.txt.sig manifest-v0.6.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.6.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly.
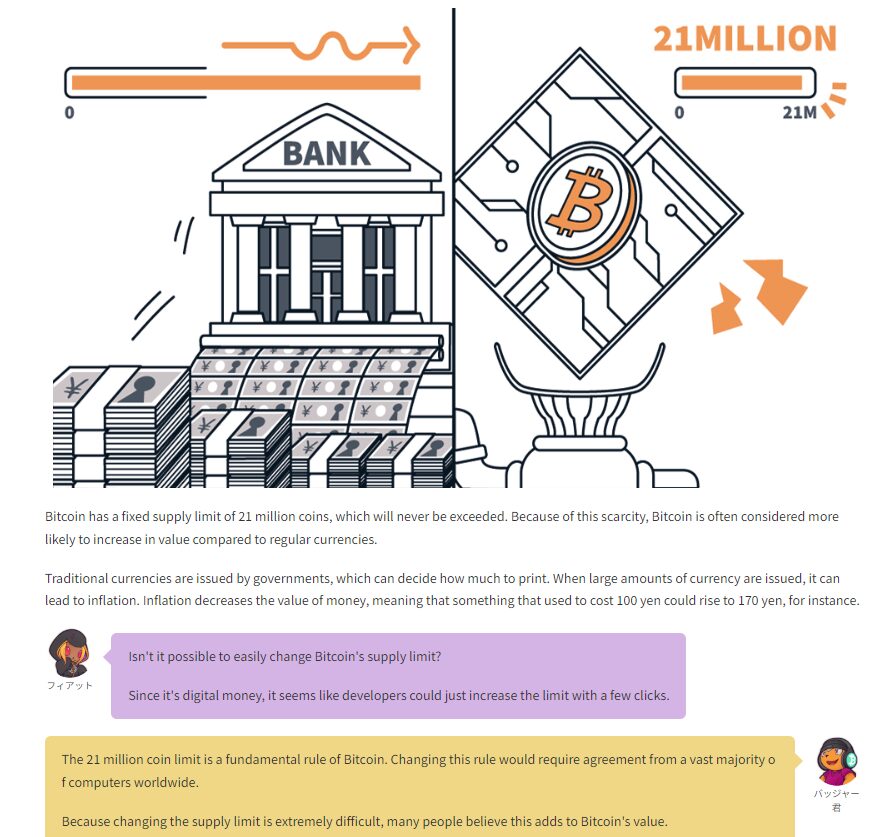 Image credits:
Image credits:


