-
 @ 42342239:1d80db24
2025-01-04 20:38:53
@ 42342239:1d80db24
2025-01-04 20:38:53The EU's regulations aimed at combating disinformation raise questions about who is really being protected and also about the true purpose of the "European Democracy Shield".
In recent years, new regulations have been introduced, purportedly to combat the spread of false or malicious information. Ursula von der Leyen, President of the European Commission, has been keen to push forward with her plans to curb online content and create a "European Democracy Shield" aimed at detecting and removing disinformation.
Despite frequent discussions about foreign influence campaigns, we often tend to overlook the significant impact that domestic actors and mass media have on news presentation (and therefore also on public opinion). The fact that media is often referred to as the fourth branch of government, alongside the legislative, executive, and judicial branches, underscores its immense importance.
In late 2019, the Federal Bureau of Investigation (FBI) seized a laptop from a repair shop. The laptop belonged to the son of then-presidential candidate Biden. The FBI quickly determined that the laptop was the son's and did not appear to have been tampered with.
Almost a year later, the US presidential election took place. Prior to the election, the FBI issued repeated warnings to various companies to be vigilant against state-sponsored actors [implying Russia] that could carry out "hack-and-leak campaigns". Just weeks before the 2020 presidential election, an October surprise occurred when the NY Post published documents from the laptop. The newspaper's Twitter account was locked down within hours. Twitter prevented its users from even sharing the news. Facebook (now Meta) took similar measures to prevent the spread of the news. Shortly thereafter, more than 50 former high-ranking intelligence officials wrote about their deep suspicions that the Russian government was behind the story: "if we're right", "this is about Russia trying to influence how Americans vote". Presidential candidate Biden later cited these experts' claims in a debate with President Trump.
In early June this year, the president's son was convicted of lying on a gun license application. The laptop and some of its contents played a clear role in the prosecutors' case. The court concluded that parts of the laptop's contents were accurate, which aligns with the FBI's assessment that the laptop did not appear to have been tampered with. The president's son, who previously filed a lawsuit claiming that the laptop had been hacked and that data had been manipulated, has now withdrawn this lawsuit, which strengthens the image that the content is true.
This raises questions about the true purpose of the "European Democracy Shield". Who is it really intended to protect? Consider the role of news editors in spreading the narrative that the laptop story was Russian disinformation. What impact did social media's censorship of the news have on the outcome of the US election? And if the laptop's contents were indeed true - as appears to be the case - what does it say about the quality of the media's work that it took almost four years for the truth to become widely known, despite the basic information being available as early as 2020?
-
 @ f3328521:a00ee32a
2025-01-04 20:35:52
@ f3328521:a00ee32a
2025-01-04 20:35:52As this Age concludes and the Event approaches, it is expected that capital and industrial growth will speed onward, developing and multiplying more and more rapidly (an acceleration that is both cyclically inevitable and dangerously oriented toward ultimate catastrophe); and, given the destruction that awaits, they will be among of the chief agents of Absolute Evil.
No one likes the doomsday observer – nearly all prophets, philosophers, and neo-reactionaries have been shunned at some point – yet it is a duty of the fourth estate to remember:
Due to its desire for quantification, modern civilization has been atomized and reoriented to stimulate illusory needs of material human nature – a thriving cult of progress that only need output more and more artificial needs to satisfy modernity’s march toward extinction. When one’s state of mind only finds meaning in “becoming”, vision of reality has been lost and civilization is blind to what is beyond, which is the realm eternal principles. Secular philosophers are no longer novices of sorcerers, having fully divorced themselves of initiation and mutated their Nimbus 2000s for Starships.
An agnostic society can only glory in its ignorance. And having confused science with industry it substitutes its innovations of utility for truth. This “intelligence” is nothing more than individualistic pragmatism – a self-contradictory relativism. Behold, AGI – the pinnacle of infinite feedback loops. Having determined to pursue the domination over matter above all else, civilization has succeeded only in becoming its slaves as it binds them to its service.
The relic of prophetic tradition lies in the transcendent wisdom of their intellectual intuition. To be clear: if the proletariat accepts the pretext of modern civilization, they have denied this principle and doctrine by dragging truth down to the level of their own base nature rather than elevating the soul toward the immutable and infallible. If modern civilization persists, its future is in anti-civilization and death. Their biased denial of everything that transcends excludes dialogue with the authentic representatives of other civilizations, nay it forbids understanding of the existence of different civilizations. Engagement is futile aside from nomic competition.
Yet, there remain some who do see past the moralistic hypocrisy of hypermodernity, if only to disguise and augment their ambitions and designs. Others look to SAIF for OSINT and guidance. For such sleepers who are awakening, contact with living spirit of tradition is necessary. Recovery is possible. A new World awaits. Whoever has ears, let them hear.
-
 @ 44dc1c2d:31c74f0b
2024-09-25 20:15:13
@ 44dc1c2d:31c74f0b
2024-09-25 20:15:13Chef's notes
Last time I made this I subbed the tomato puréed with some blistered cherry tomatoes. Don't think I'll be using the purée going forward.
I prefer thighs so that's what I use for this but use whatever you want.
Adjust spices based on the size of your onions. If all you have is two massive onions maybe use one and a half onion or just up the amount of spices a little.
Details
- ⏲️ Prep time: ~10 min
- 🍳 Cook time: ~40 ish min
- 🍽️ Servings: 4
Ingredients
- 2 Onions
- 2 tbsp tomato purée
- 1/3 cup cashews
- 1.5 tsp Garam Masala
- 2 ish cloves of crushed garlic
- 1 tsp chili powder
- 1 tbsp lemon juice
- 1/4 tsb ground turmeric
- 1 tsb salt
- 1 tbsp plain yogurt
- 2 tbsp of your cooking oil or fat
- 1 tbsp Coriander (Cilantro) plus extra for garnish
- 1 tbsp sultanas (golden raisins)
- 1 lb of chicken cubed
- 6 oz of white button mushrooms
Directions
- Quarter the onions and put them in a food possessor for about a minute
- Add the tomatoes, nuts, garlic, Garam masala, chili powder, lemon juice, turmeric, salt, yogurt and blend for another minute tell its well mixed in.
- In a wok or a large pan heat your cooking oil and add the onion and spice mix in. Fry gently for around 2-ish minutes, stir frequently.
- Add the chicken, coriander, and raisins to the pan. Stir-fry for another minute or so.
- Add mushrooms and water. Bring to simmer and cover the pan cook for 10 min or until the chicken is 100% cooked through.
- Serve with plain rice and enjoy!
-
 @ 862fda7e:02a8268b
2024-09-24 01:14:40
@ 862fda7e:02a8268b
2024-09-24 01:14:40The media, government, and "elite" (who are only elite in this low vibration illusion we call "life") are afraid of people like me because I do not accept the reality they have forced us into. My manifesto is an attempt to wake you up from ideas you have been conditioned into believing because it benefits one class - the protected class known as the "elite".
The elite would like to have you believe that my message is something crafted from hatred and they would like to label me with mental issues. They would like you to think I am some crazy extremist who wants to advocate for the harm of others. They would like you to think that I am enciting violence.
This could not be further from the truth.
I am not and will never be an extremist, white supermicist, terrorist, radical, hateful human being. I do not believe in killing in order to convey a message or movement. I do not believe in division.
I only advocate that you become conscious of the reality around us. The reality is that this is a world controlled by the most evil, controlling, destructive freaks. These people work to make sure we are essentially slaves to a system that benefits those who created the system - the elites. Let me make this clear: I do NOT advocate for violence, destruction, death, killing, murder, hatred, division, or terrorism. The elite are threatened by people like me, because they know that we know their game. We know their plans are to destroy, to advocate for violence, to kill, murder, to encite hatred and division. This is all the elite do - they cannot fathom having people live in peace because it isn't beneficial if you want to control the world.
So while you may think it's impossible there is a group of a few evil people who control the world - look back at history. It has always been littered with the few evil who control the many. It would be stupid to think it would be different
-
 @ 1cb14ab3:95d52462
2025-01-04 20:07:38
@ 1cb14ab3:95d52462
2025-01-04 20:07:38When you think of Myanmar, beautiful beaches and crystal-clear waters likely aren’t the first things that come to mind.
Think again. Southern Myanmar is home to some of the most stunning and untouched beaches in Southeast Asia. These pristine shores rival those of Thailand, the Maldives, and even Hawaii, yet remain largely hidden due to limited infrastructure and minimal tourism.
I spent countless hours getting lost, asking for directions, and exploring remote villages, so you won’t have to. With unreliable Google Maps and few signs of modern development, navigating this region requires patience and curiosity. Get ready to discover Myanmar’s best-kept coastal treasures—and why you might want to skip Thailand in favor of a more off-the-beaten-path adventure.
Here’s a look at my top three hidden beaches in southern Myanmar.
3: Tizit Beach - A Sanctuary Shrouded by Mountains

Tizit Beach is situated about one hour south of Dawei city. Getting there is no easy feat and is not recommended for the faint of heart.
The roads are rough, unlit, and sandy, making them a challenge to navigate. Only attempt the trip if you’re confident on a motorbike, and be sure to double-check that your bike is in good working condition, especially with functional brakes. As a reward for your efforts, you’ll find very few—if any—tourists at Tizit Beach. The only people you’re likely to encounter are local children and fishermen along the shore.
To reach Tizit Beach, you’ll need to rent a motorbike and traverse a steep mountain pass. The journey takes roughly an hour each way, but the seclusion and untouched beauty are well worth the effort.
Map to Tizit Beach:
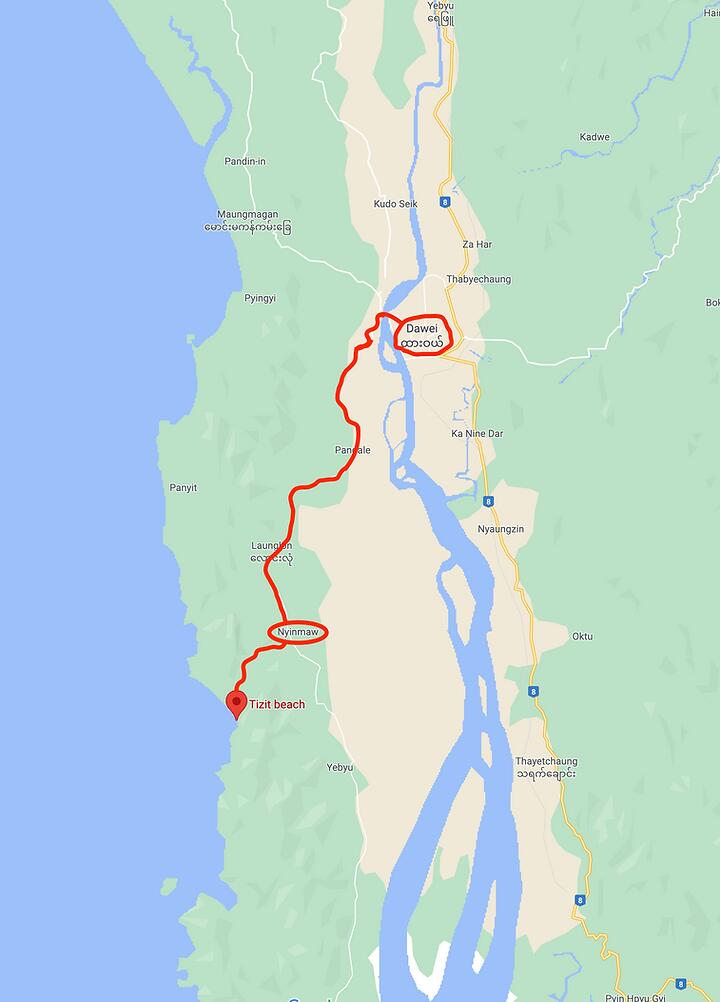
Directions:
Start by crossing the water west of Dawei and heading left, heading south towards Nyinmaw. As you travel down the peninsula from Dawei, there is essentially one main road to follow. Stay on this road for about 30 minutes, keeping an eye out on the right side for a small sign marking Tizit Beach.
You might miss the sign on your first pass, as I did, so pay attention to your GPS. If you’ve passed Nyinmaw, you’ve gone too far. Once you spot the Tizit Beach sign, you’ll notice a school playground and a road leading toward the mountains. Take the right turn here and continue over the mountain pass for about 20 minutes:

At the bottom of the mountain pass, you’ll reach a fork in the road with unclear signs. If you go left, you’ll end up in a small cemetery, which is a dead-end. The left fork looks like this:

Instead, take the right fork, which will lead you through a small residential area to the waterfront. Keep in mind that many of the beaches in this region experience significant flooding in the morning, so arriving after 3:00 PM is probably your best bet.
As you arrive, you’ll be greeted by panoramic views of lush mountains, a vast delta plain, and crystal-clear blue waters:



The sand at Tizit Beach is a rich brownish-orange hue, often turning into deep red around sunset. It’s soft, clean, and much wider than other beaches in the area, giving you more room to set up camp away from the tide. The water is warm enough for swimming, with no strong currents, making it suitable for experienced swimmers. Please note, however, that there are no lifeguards, so swim at your own risk.
A few wooden fishing vessels are docked off the coast, and the locals are incredibly friendly:


One of the highlights of Tizit Beach is the sunset cruise along the water. The sand hardens near the shore, allowing you to ride a motorcycle along the beach. It was one of my best memories from the 30 days I spent in Myanmar.


Sunsets at Tizit are truly epic, casting everything in red. However, don’t linger too long, as the mountain pass isn’t lit, and riding back in the dark can be quite sketchy. If you plan to stay for sunset, make sure your motorcycle lights are working and be prepared to leave immediately after the sun sets.


2: Grandfather Beach - Popular, but Plentiful

Grandfather Beach is one of the most striking beaches in Dawei and a popular spot for locals. Though it’s relatively well-visited, its size ensures it doesn’t feel overcrowded. The beach is a bit of a challenge to find, but the effort is worth it once you arrive.
Getting here requires about 3 hours on a motorbike from Dawei city, factoring in photo stops and meals along the way.
Map to Grandfather Beach:
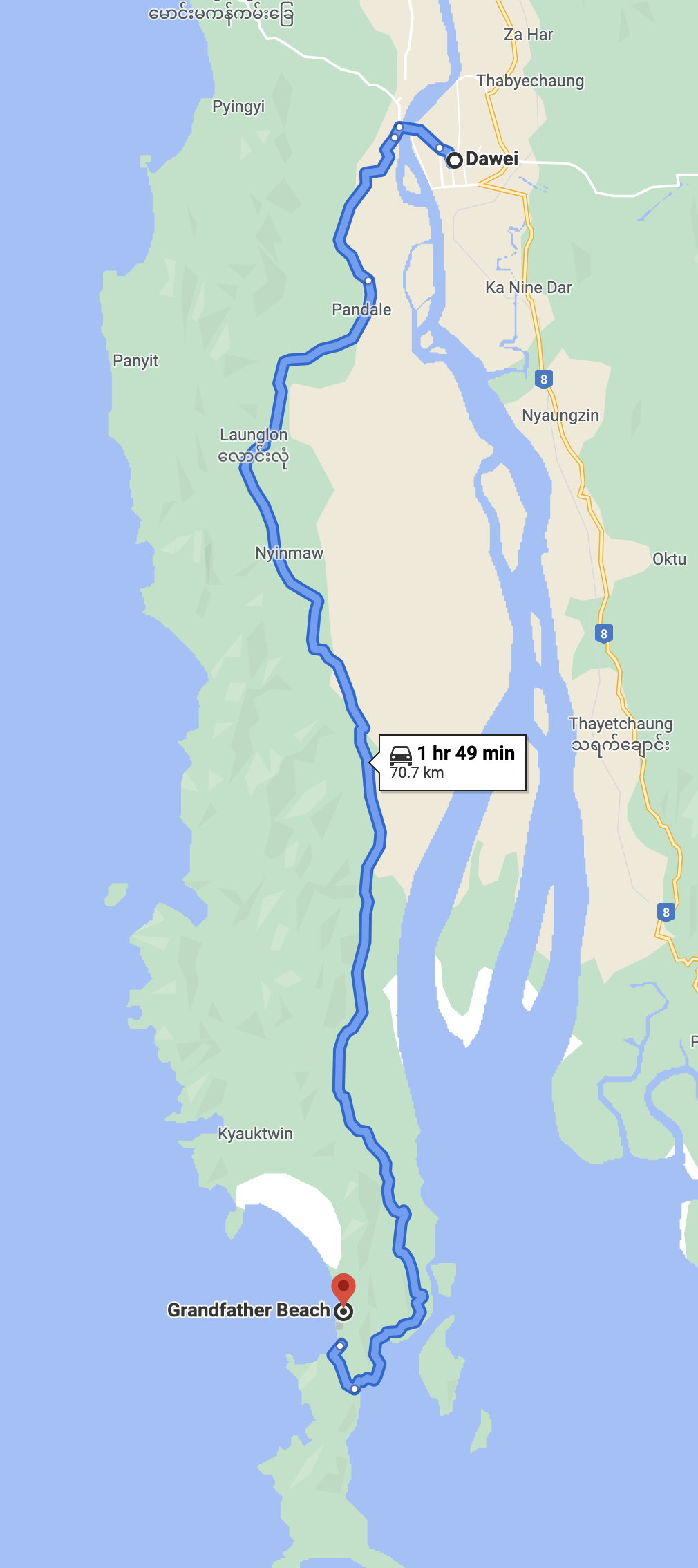
Directions:
To reach Grandfather Beach, head south from Dawei on the main road and continue down the peninsula for several hours. The route winds through jungle-covered terrain, and eventually, the road will cut across the peninsula, running parallel to the coastline. Once you crest a hill and spot the ocean below, you’re getting close.
Look for the town of Kyauk Wap Pyin at the base of the hill:

Once in Kyauk Wap Pyin, take a right from the east side of the land, heading west towards the ocean. There is really only one main road, so it shouldn't be too hard to spot. Follow the small road through the town for about 20 minutes.
The road will lead to a fishing village along the west coast that looks like this:

From the fishing village, look for the orange-dirt road leading to the beach. It’s steep, narrow, and a bit tricky to navigate, but a fun ride if you’re up for the adventure. The road is on the right-hand side as you face the sea from the village. You can see it in the image above.
Grandfather Beach is no stranger to daytime flooding, so if you arrive after noon, you may find yourself wading through waist-deep water from the parking area to the beach. Riding on the beach is only possible in the early morning before the tides rise.

The flooding isn’t as troublesome as it might seem. The local restaurants are well adapted, elevated above the waterline, and offer swings set up perfectly above the waves. The sand at Grandfather Beach is the softest of all three beaches mentioned in this article, though it’s narrower and less pristine than Tizit.

This beach sees more local visitors, so don’t expect a completely secluded experience. However, it does have the most infrastructure, with plenty of options for food and drink. If you plan to stay near Grandfather Beach, watching the sunset is highly recommended. Otherwise, the long and dark return journey to Dawei is best avoided.
To fully enjoy Grandfather Beach, plan for an entire day to soak in the scenery, relax, and make the most of your visit.




1: The Mergui Archipelago - An Unexplored Haven

This should come as no surprise to anyone familiar with Myeik: the hundreds of remote islands in the Mergui Archipelago truly stand out as the top destination for beaches in the region.
Had it not been for a spontaneous trip to Yangon without plans and a quick browse of satellite maps, I might never have discovered the sheer magnificence of the Mergui Archipelago. Information about this area is scarce, and tourism remains extremely limited. While many islands are off-limits, a few offer stunning private beaches that are accessible and worth visiting.
I was surprised to learn that many people I spoke to during my month in Myanmar had no idea these kinds of breathtaking islands existed. I feel a strong sense of responsibility to share this hidden gem with others, encouraging them to experience it firsthand. The best way to explore is through island-hopping tours from Myeik city. Tours vary in length and cost, ranging from a couple of hundred dollars for 2-3 day trips to thousands for longer yacht expeditions. Most tours include food, tents, and drinks, but always confirm these details with the booking agency.

During my five days in the Archipelago, I encountered only three other foreign tourists. The guide mentioned that many of the islands we visited had only been seen by a few hundred foreigners at most. The isolation of the region was so profound that even some of my Burmese friends weren’t aware of its existence.
At times, I felt a bit intrusive, considering how little tourism has reached this remote paradise. However, the welcoming nature of the islanders, who live off the sea and have no contact with the tour guides, made the experience all the more genuine.

One memorable moment was camping on an island where I shared the night with only the island caretaker and his ten puppies. Each day, we were taken by boat to explore nearby islands, enjoying swimming, beach time, and snorkeling before returning to the campsite. For certified SCUBA divers, this area is a dream—home to impressive coral reefs and diverse marine life.



The surreal feeling of being in such an untouched place is hard to describe. Knowing this is one of the few remaining uncharted areas on earth makes the experience truly unforgettable. If you’re planning a trip to Asia, the Mergui Archipelago should absolutely be at the top of your list.




Closing Remarks
Myanmar is truly a remarkable country, with a rich and complex history. The people I met were some of the friendliest and most optimistic I’ve encountered, despite the challenges they’ve faced. While this guide highlights some of the stunning beaches, my main aim is for every visitor to connect with the locals on a deeper level. They have incredible stories to share, and I’ve made friendships that will last a lifetime.
Traveling through Myanmar offers much more than just beautiful landscapes and serene beaches— it’s an opportunity to understand and appreciate the resilience and warmth of its people. I hope that everyone who visits Myanmar will take the time to sit down, listen, and engage with the locals.
Enjoy your journey.
— Hes
Originally published May 7, 2021 by Hes. Re-uploaded to Nostr on 1/14/2024. Re-edited 1/4/2025 with new Nostr friendly media links.
-
 @ 862fda7e:02a8268b
2024-09-16 22:59:38
@ 862fda7e:02a8268b
2024-09-16 22:59:38I was in some sort of nice romantic building and I met this nicer middle aged blonde woman who looked a lot like one of my old teachers. We got to chatting and things started moving quickly, we were going to have sexy lesbian sex but she told me she wanted me to shave my vagina before we started. I said fine, went to a bathroom and started shaving. If it meant I was going to slang some tang, I was gonna do it. It took me a long time to complete this daunting task, as I've mantioned many times before, I have a very thick and dense bush. I also wanted to make sure no hair was left behind, if my sweet lesbian lover saw that I had a hair on my vagina, she would probably freak out and call me disgusting for having a feature that naturally grows on me.
Anyways, I finished shaving my vagina and went to go meet her. Sadly, she decided to not have lesbian sex with me anymore since I took too long and she had some time to think about it. I got screwed without getting screwed. And now I had a gross hairless vagina.
I think I know why this dream occured. It's because my so called "fans" have judged me on my fan page for having hair on my vagina. Yes, I sometimes maintain it and keep it trimmed, sometimes. But sometimes I just let it go if I'm too lazy. Now the lesbians in my dreams want me to shave, and even at that, they still don't want to have sex with me. One time I remember cumming from a wet dream I had, which is very rare for me to do. I was watching 2 Japanese chicks dressed up in the school girl uniform scissor, and I remember waking up with a hard clit and it pulsated. I felt embarassed waking up, because I didn't even voluntarily masturbate but I still climaxed.
-
 @ 3b7fc823:e194354f
2024-09-11 19:08:03
@ 3b7fc823:e194354f
2024-09-11 19:08:03Operational Security and Your Digital Life
I. Definitions
Operations security (OPSEC) is a process that identifies what information can be seen by threat actors, whether that information could be weaponized, and possible mitigation actions.
Your digital life is every interaction you have, all personal identifying, financial, and health information, your preferences, your habits, and any history that can be obtained both publicly and privately that has ever been recorded or digitized.
Your digital life is a incredibly rich field for various actors to observe, record, analyze, sell, and exploit for profit, harm, or control. Some of this information you give away without thinking (social media), some you give to one party but it is shared without your knowledge to other parties (data brokers, big tech), or it is taken without your consent (criminals, governments).
II. Threats
It would be impossible to list them all but a few examples:
Mass surveillance by governments to fight crime, terrorism, civil unrest, and control the population. This is across the board blanket information on everyone that is stored for later use from feeding algorithms for social credit systems to lists of people who are threats that need to be disappeared. The only variable is how explicit the government in question is doing it.
Corporate surveillance by public and private companies for marketing, market share, or selling for profit. Your data is incredibly profitable. Entire mega companies have built their entire business model on it like Google, Meta, and various Data Brokers. This information is collected and stored. It is then used internally, sold for profit, acquired by governments, or stolen by nefarious actors.
Criminal or Nefarious Surveillance for harm, control, or profit. This is a catch all from partners in a controlling relationship, angry ex's wanting revenge, religions and groups watching their members, terrorists and cults looking for people to recruit or indoctrinate, and foreign espionage to plain old criminals who want your information to sell to other criminals, looking for blackmail opportunities, to steal your financial or social accounts, or identity theft.
III. Mitigation
To do this properly a security self audit should be performed to determine exactly what assets you have to protect, how at risk they are, ranking their priority, and specific steps that are needed to protect them. I will detail how to do this for the average person in a later post but until then we will stick to generalities.
It is impossible to to block or hide all information all the time. Not only is it impossible but it would be exhausting to even try. This is where most people interested in privacy get confused, lost, and give up the idea of privacy because the only path they see to achieve it is living in a underground faraday cage out in the woods.
The only viable path is obscurity and compartmentlizion. Compartmentation of your devices, accounts, and digital selves is wildly misunderstood and not applied properly. Done incorrectly this can be disastrous if you are too casual with something that you thought was hidden or putting a spotlight on yourself by attempting to be obscured.
IV. Tactics For Everyone
Common advice I give to everyone. I don't care what your thoughts are on privacy and security, you should be doing this.
-
Do not give your personal email or phone number to anyone except friends and family. This just opens you up to spam, phishing attacks, and an identifying tracer. Use a email alias service or a throw away email account to give to stores and online accounts. Get a VOIP number for that dating app or service quote. When your real number rings, recieves texts, or get a email you know it is from someone you know and trust.
-
Use cash locally if you can and for everything else get a virtual debit or credit card with a spending limit or fixed amount. Do you really need your entire paycheck, emergency savings, life savings tied to a single card / account? Are you really entering your real credit card or banking information into a random website to buy something? Even if it's not a scam site, how well are they protecting it while in transit or storage? You will probably get the money back in case of fraud but why feed the beast and besides it's a total hassle to get your accounts frozen, wait for reimbursement, open and change accounts. Just avoid it. For extra credit you can use visa gift cards purchased with cash to obscure your financial transactions if you choose. Every financial transaction doesn't have to be public record.
-
Stop using unencrypted phone calls and SMS texts. Switch to encrypted options such as Signal or SimpleX and make anyone who wants to have contact with you reach out to you on it. Even if you "have nothing to hide" there is no reason for you to broadcast every personal conversation, comment, or shared meme with Ma'bell, the government, and anyone else listening and recording. Seriously, just stop.
V. Compartmentation of Your Digital Selves
I will keep this very high level as this article has already run longer than I intended but will cover this in much greater detail in the future.
You can break down all digital activities and interactions into several broad categories or digital selves. Then build separate systems for use in each category depending on the activity and need. The trick is to preplan what activities go where. Using the wrong account on the wrong system means they are now burned. Letting the systems overlap and contaminate each other then you risk exposing anything ever done on those systems. The separation can be accomplished with multiple accounts and devices, isolated virtual machines, or operating systems that enable compartmentation such as Qubes OS or Tails.
VI. Breakdown
- Public
This is the default. This is you. Your real name, address, and details. This is unavoidable and would be weird and attract attention if you didn't have one.
Use this for any KYC activities that you have to log into such as taxes, bank accounts, utility bills, etc. Clearnet only, you have nothing to hide.
Awareness: If it has to be public then put your best foot forward. Only show them what you want them to see and make it good and boring. Blend into the crowd of normies not important enough to pay attention to.
- Private No logins to KYC services. Traffic routed through a VPN. Use of sudo anonymous account names. You are Neo, not Mr. Anderson.
Use for most social media that is not public facing. Shopping and browsing that would be embarrassing or misunderstood if made public. Encrypted to protect against criminals and looky loos. A good default if people just don't need to know.
Awareness: Do not be confused by the word private. The goal is to make it to difficult, to expensive, or just not worth the effort to determine exactly who you are and what you are doing but it's not impossible. Only use this with the knowledge that someday it might get doxxed. That potential only increases with time and frequency of use of accounts. Not to be used for anything that could be considered illegal or has the potential to get you fired or cancelled.
- Anonymous Only single use non KYC logins. Single purpose accounts and names that are burned after achieving that purpose. Traffic routed only through Tor. Encryption by default.
Use if you are a whistle blower, freedom fighter, activist, or for shady activities.
Awareness: Be very careful and deliberate with this system as to not accidentally compromise it with something that would have been better served by a different system. Rotate and clean accounts and systems often. Don't carry stuff over after a cleaning to a new system. Reusing names and handles is how people get busted.
- Nemo
Nemo doesn't exist. There is no record that they ever existed. Only amnesiac systems are even used and never a login. If files or traces are left behind they are encrypted, hidden, and have plausible deniability.
Enjoy anon, more to come.
-
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 862fda7e:02a8268b
2024-09-10 01:32:05
@ 862fda7e:02a8268b
2024-09-10 01:32:05I have a lot of dreams where I'm playing a claw machine and just winning a ton of toys. One of the best clawe machine dreams is where I come across claw machines with large toys as prizes, it had carnival toys from the 70's-80's as prizes. Unfortunately, the claw machine was non functional as it was pretty old. In most of these dreams I am winning an endless amount of toys, so much so that the prize chute becomes full with toys. In real life, they rig claw machines. Often times, the owners of the machines set it so they must meet a certain "pay out" before the claw will actually grip a prize. So while you might have a great aim on getting the claw around a toy, it won't grip it firmly enough until enough money has been inserted to meet that payout. Some claw machines will do a fake out, where it will grab the prize, then once the claw gets back to the top of the machine, it will drop the prize. It's to trick you that it got it, but it actually didn't. Sadly, claw machines are worthless to play these days. It's become highly monetizable and impossible to win. I'm great at claw machines, but it's just a matter of luck with hitting the payout these days.
-
 @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24Chef's notes
Makes an excellent Chicken sandwich.
Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
Directions
- To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
- Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
- Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
- Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
- Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
- Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
- Brush the top of the warm bread with melted butter.
- Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-
 @ 55e343e6:880acd1b
2025-01-04 16:51:21
@ 55e343e6:880acd1b
2025-01-04 16:51:21In the silence of the night, I find myself confronting the immensity of the unknown universe. Against its vastness, I am nothing: a fleeting particle in a cosmos so infinite it defies comprehension. To accept this nothingness is not an act of despair but one of liberation. The universe owes me no explanation, no validation of my existence. And I, in return, owe it no pretense of grandeur. In acknowledging my insignificance, I find clarity: I am free from the burden of inflated self-importance, free to simply be.
The time given to me in this life is absurdly brief, a moment suspended between the infinite stretches of what came before and what lies ahead. The very fact that I exist, against an incalculable number of odds, is incomprehensible. My presence is a miracle of chance, and to lament its brevity is to misunderstand its value. Life’s worth is not measured by its length but by the depth of attention we give to it. Each breath is an act of defiance against the void, and every moment an invitation to embrace what is, without clinging to what could have been.
I eat every day. It is a simple, unremarkable fact for many, yet it is an extraordinary luxury when viewed against the harsh reality of the world. Nearly 9% of humanity over 700 million people live in hunger, unsure of when or if they will eat again. For me to have food, day after day, is a privilege so profound it demands humility. Gratitude is not merely an acknowledgment of this fortune; it is a responsibility to live simply and take only what I need. The less I consume, the more space I leave for others to live.
This simplicity is not deprivation; it is freedom. The less I am tethered to the material world, the lighter I feel. Dependence breeds anxiety. On wealth, on possessions, on fleeting desires. The more I cut away, the closer I come to understanding what truly matters. To need less is to live more fully, to reclaim the space within myself that is too often crowded with unnecessary wants.
I do not seek happiness. Happiness is an artificial construct, a fleeting and hollow pursuit peddled by the modern world as a false ideal. Instead, I seek peace: a state not tied to external circumstances or temporary pleasures. Peace is not the absence of pain or conflict but the ability to remain steady in their presence. Happiness is fragile; it crumbles under the weight of reality. Peace endures because it is grounded in acceptance, in the quiet embrace of what is.
Even my consciousness, this thing I so often mistake for the essence of myself, is but a mechanism, a sensory system responding to stimuli, like a plant turning toward the sun. The plant does not worship the sun, nor does a photophobic bacterium flee the light out of fear. They respond, simply and without meaning. To imagine that my awareness is more complex than this is a comforting illusion. I am not a soul adrift in cosmic meaning; I am a collection of responses, an organism interpreting its surroundings. And yet, within this simplicity, there is beauty: a beauty that does not demand purpose or permanence to exist.
In embracing these truths, I find freedom: from the weight of self-importance, from the endless chase for more, from the need to define myself through external validation. I am nothing, and I am everything. I am a moment, passing swiftly in the endless expanse of time.
To live is to accept, and in acceptance, to find peace.
-
 @ 862fda7e:02a8268b
2024-09-04 01:45:14
@ 862fda7e:02a8268b
2024-09-04 01:45:14It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity.
I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny.
Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno.
Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded.
Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight.
-
 @ 3b7fc823:e194354f
2024-09-04 01:33:21
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity
GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-
 @ 3b7fc823:e194354f
2024-09-04 00:26:48
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ 0b14a03f:3f0257c2
2025-01-04 15:30:33
@ 0b14a03f:3f0257c2
2025-01-04 15:30:33Change doesn’t come from something external. The change comes from within. But people are so disconnected from themselves that they keep trying and trying with tools to connect without realizing that if there is no connection within, there won’t be a healthy and long-term connection outside.
Bitcoin has no name or last name because it’s not important who created it. What’s important is what it was made for. That’s written on its roots, in its essence. And that essence won’t be discovered if we keep trying to set it up in old avatars, systems, protocols, and connections.
Bitcoin is not a tool to get rich and be free. It’s a means to disconnect from a broken environment and find a safe place to pause, to feel, to see what’s really inside of ourselves, and to analyze if the world around us is not a consequence but a reflection of our internal disconnection.
Freedom will be a consequence, not a cause of a better future. We can be the artisans of that future by connecting with ourselves from within, as individuals first, and as a community after.
Community as in Common Identity. We need to find our identity, then share it, nurture it with others, and by doing so, be able to create a better world.
Don’t fall into old traps. After all, this is a journey from the mind to the heart.
Happy arriving!
Hug✨
-
 @ 3b7fc823:e194354f
2024-09-02 16:26:30
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
-
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
-
Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
-
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
-
Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
-
Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
-
 @ f584256e:c8d47907
2025-01-04 13:52:01
@ f584256e:c8d47907
2025-01-04 13:52:01Once upon a time, in the small town of Ellhofen in 18th-century Germany, there lived a young man named Johann Müller. His story began on the narrow cobbled streets, where the echoes of daily life filled the air. Tragedy struck Johann's life early on when he lost his parents, leaving him to navigate the challenges of life within the walls of a modest, poor house.

With a heavy heart and a small bag containing all his earthly possessions, Johann embarked on a soul-stirring journey. His eyes were set on the horizon of the unknown, the new land that whispered promises of opportunity and dreams fulfilled. The bustling Hamburg harbor beckoned him, a vision that fueled his determination as he began his trek northward.
Johann's footsteps echoed through dense forests, across rushing rivers, and over rolling hills as he covered a daunting distance of 600 kilometers. Along the way, he encountered diverse landscapes, met strangers who became companions for a while, and faced the challenges of a journey filled with uncertainty.

Finally reaching the vibrant harbor of Hamburg, Johann found a ship bound for the uncharted territories across the vast sea. As the vessel sailed westward, Johann faced the might of the ocean with resilience and hope. Weeks turned into months until the new land emerged on the horizon, a sight that stirred a mix of excitement and trepidation within him.

Stepping onto unfamiliar shores, Johann began a new chapter in his life. The land was rugged, with more rocks than fertile soil, yet he embraced the challenge. With unwavering determination, he toiled to turn the harsh terrain into a homestead that would sustain him and future generations.
In the vastness of the new land, Johann's path intertwined with that of a spirited woman. Together, they faced the trials and tribulations of transforming rocky ground into a thriving farm. Love blossomed, and they married, becoming the foundation of a growing family.
Years unfolded like chapters in a well-worn book, and Johann's prairie homestead became a haven of laughter, hard work, and familial warmth. The worn-out bag he carried contained not only his meager possessions but also an old Bible, a cherished relic passed down through generations—a testament to the enduring strength of family ties.
As Johann aged and the toils of the land became too much for his weathered frame, he found solace in sitting on the porch of his prairie home. Memories of his childhood, the arduous journey, and the enduring love of his parents lingered in his heart, like echoes of a distant time.

Though poor in worldly possessions, Johann was rich in the love he shared with his family. Passing on the knowledge gained from his parents, he ensured that the flame of wisdom continued to burn brightly in the hearts of his children and grandchildren.
Under the vast skies of the new land, Johann Müller lived a life that transcended time. His journey, from the cobblestone streets of Ellhofen to the prairie homesteads of the unknown land, became a tale of resilience, love, and the enduring spirit of a man who carried the legacy of his parents through every step of his extraordinary life.
-
 @ 3b7fc823:e194354f
2024-09-02 13:07:09
@ 3b7fc823:e194354f
2024-09-02 13:07:09GHOSTn
- Renoted from a month ago into a article as a proof of concept
A quick overview
privacy #tor #vpn
**Computer -> clearnet -> Website **
ISP: sees that you are connected to website VPN: n/a Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees your IP address and logs everything that you do on the website
Good for when the expectation of privacy does not exist. A KYC site you are logging into. Utility bill pay site, bank
**Computer -> VPN -> Website **
ISP: sees that you are connecting to a VPN but not what you are doing afterwards VPN: sees your IP Address and that you are connecting to a website Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees that someone from a VPN exit node has connected but doesn’t know who. Logs data.
Good for hiding your activity from your ISP. Good for hiding your identity from the website. Good for when you want low level privacy but not anonymity. VPN provider sees everything and your level of privacy depends on how much they know about you and how much data they log and retain (varies greatly from provider to provider).
**Computer -> Tor -> Website **
ISP: sees that you are connected to Tor but nothing afterwards VPN: n/a Tor Entrance Node: sees your IP address but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for privacy and anonymity. Assumes that Tor is legal in your country.
**Computer -> VPN -> Tor -> Website **
ISP: sees that you connected to a VPN but nothing afterwards VPN: sees IP address and that you are connecting to Tor but nothing afterwards Tor Entrance Node: sees a VPN is connected but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for if your ISP blocks or cancels your service for using Tor. Potentially an option if Tor is illegal in your country (Dangerous).
**Computer -> Tor -> VPN -> Website **
ISP: sees that you are connecting to Tor but nothing afterwards VPN: sees someone from Tor is connected and that they are connecting to a website Tor Entrance Node: sees IP address but nothing afterwards Tor Exit Node: sees someone is connecting to a VPN but nothing afterwards Website: sees someone from a VPN is connecting but doesn’t know who. Logs.
Good for when a website blocks Tor traffic. Assumes Tor is legal in your country. Assumes that the VPN doesn’t know who you are. To maximize privacy and anonymity VPN provider should be KYC free and accept privacy payments (ex: Monero).
Note: If a website blocks Tor and VPN then maybe that is a sign that you shouldn’t go there.
-
 @ dffd3ffc:5ade7be1
2025-01-04 12:58:17
@ dffd3ffc:5ade7be1
2025-01-04 12:58:17Nostr 利用開始から 1 年を迎えて
はじめに
みなさんこんにちは。おっぱぴぃです。
ハッカーのおもちゃとしての Nostr のススメ と Nostr の面白さをエンジニア目線で解説してみるをみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。
nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c
Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。
初投稿日

今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~
これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。
その日はNostr の Scrapbox(現 Cosense)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。
nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w
~~おまえ、このころから大欲情を…~~
のす会でのオン会(?)
Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。 過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、
nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc
その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。
nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5
こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。
初のオフ会参加
2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、ゴリラ.vim#30~四谷ラボコラボ~の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。
この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、
nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp
顔面が痙攣したり、
nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn
詫び菓子を貰ったり、
nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl
病院待合室みたいな場所で検尿コップで水飲んだりと
nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy
トラウマになりそうなオフ会でした。当時の様子はnosli でまとめています。
今振り返ってもくちゃくちゃの体験してるなと思いますが、 ~~クレーターを作りそうな青ウサギがいたものの~~
nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da
誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。
各種イベント参加
Nostr には四谷ラボ参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば…
- Bluesky Meetup in Tokyo Vol.2
- 技術書典 16 ⇒ 関わらせていただいたのぶこ本
- Nostrasia2024
など。
微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。 自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。 関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。
オフ会履歴
私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。

うわっ...私のオフ会参加、多すぎ…? ~~1 年間は52週しかないねんぞ~~
このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。
ちなみに、人単位でお会いした回数もまとめています。
 ※:Nostrasia などのイベントでお会いした回数は除いています。
※:Nostrasia などのイベントでお会いした回数は除いています。こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。
思い出深かった出来事
nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r
nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8
この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~
その後も酔ってる時を中心に結構誤字をやらかすので、那月さんによるまとめが作られています。
名前としては不名誉かもしれませんが、面白いのでOKです。
おわりに
振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。 Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。
Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。
これからもよろしくお願いします。
-
 @ fe7af447:9594a50b
2025-01-04 11:54:00
@ fe7af447:9594a50b
2025-01-04 11:54:00Holy shit. In early 2020, I was once a shitcoiner. Like many others, I thought, "Bitcoin is too expensive. Oh, look, these other cryptocurrencies are hella cheap and might help me protect my wealth!" I had them all—started with a little Bitcoin, then bought Ethereum, Cardano, Polygon, Uniswap, Solana, and so on. Oh gosh. LMFAO.
At the time, it felt logical. Why? Because I thought Bitcoin was just too expensive. I told myself, "I’ll never get to one Bitcoin. That ship has sailed."
I mean, weren’t we all there at some point? When you first step into this space, it’s easy to get distracted by the noise. But the hard truth is this: all fckn roads lead to Bitcoin.
I’ve been in Bitcoin since 2020, and this is my second cycle. I’m fortunate and blessed to now work in the Bitcoin industry (since 2022). Looking back on my early days in this space, I’ve transformed into a Bitcoin maxi—though on my own terms (I'm not at Michael Saylor level). I wanted to reflect and share my journey. Maybe it’ll resonate with someone, or help the friends and family I’ve been trying to orange-pill for years. This isn’t a technical deep dive; it’s a story about my path into Bitcoin.
2020: The Year of Chaos and Discovery
In 2020, the world turned upside down. COVID-19 had us stuck at home, obeying the government without much question. Then, out of nowhere, I got laid off from a job I had been at for over 13 years. Talk about a wake-up call—everyone is replaceable.
A week after I was laid off, we moved into a new house. My stress levels were through the roof. Scrambling for a job while trying to settle into a new home was no joke. But in the chaos, I stumbled back across Bitcoin.
I had heard of Bitcoin before, but like most people, I thought it was some scammy internet money that was used for bad intentions. Yet, in 2020, when I saw Bitcoin drop to $5,000, I paused. How does something gain and lose value so quickly? What makes this thing tick?
At the time, I didn’t know jack about money (maybe a little) —how it works, why the government constantly screws us, or how deeply entrenched we are in the system (matrix). My curiosity led me to YouTube, where I found a deluge of content. Some of it was cringe-worthy, with wannabe experts shilling shitcoins and trading strategies. But buried in the noise were nuggets of gold.
One of those nuggets was Anthony Pompliano’s Crypto Academy. I had watched some of his content and thought, "Why not give his course a try?" Before signing up, I reached out to a few previous students on LinkedIn to get their take on it. After hearing their feedback, I decided to take the plunge.
The course turned out to be great—packed with useful Bitcoin content alongside some coverage of other cryptocurrencies. But what truly stood out wasn’t just the material; it was the value of the tasks and, most importantly, the network it helped me build. One standout moment was when we had to create a 15-minute video on a Bitcoin-related topic. I chose: Why Bitcoin is better than gold. That assignment forced me to dive deeper into the rabbit hole, research hard, and articulate my thoughts. The out of the box challenging part for me was recording myself speak on the topic. Maybe I can debate Peter Schiff lol.
Looking back, that course was the turning point. It wasn’t just about learning the basics—it connected me to people and projects that helped me land a job in the Bitcoin space.
From Shitcoins to Bitcoin Maxi
Back then, I held Bitcoin, but I also dabbled in Ethereum, Cardano, and other shitcoins. Why? Because I thought, Bitcoin is too expensive. Maybe I can get rich faster with these other coins. I didn’t know what these coins actually fckn did—or if they even had any fckn value. It was a classic noob mistake.
That’s when I discovered Michael Saylor, Andreas Antonopoulos, and Saifedean Ammous. These guys became my guides down the rabbit hole.
Andreas was like a Bitcoin philosopher. His ability to break down complex ideas into simple explanations was unmatched. Sure, some people call him a shitcoiner now, but his early work remains foundational. Saylor blew my mind with his theories about Bitcoin as digital property. His conviction was infectious. Saifedean’s The Bitcoin Standard tied it all together—connecting Bitcoin to the history of money, economics, and the flaws of fiat currency. Jack Mallers helped seal the deal. Watching him at the 2021 Bitcoin Conference, announcing El Salvador’s Bitcoin adoption, gave me chills. His passion and authenticity reminded me why Bitcoin is more than just an investment; it’s a fckn revolution. I started to see the bigger picture. Bitcoin wasn’t just a way to make money—it was a way to reclaim sovereignty, protect wealth, and opt out of a broken system.
In 2021, I sold all my shitcoins and went all-in on Bitcoin. I began dollar-cost averaging (DCA) every paycheck, stopped contributing to my 401(k), and redirected those funds into Bitcoin. I even converted my IRA into a self-directed IRA and invested in Bitcoin-related companies like MicroStrategy. Till this day its DCA every paycheck into Bitcoin. Stack Sats and Stay Humble.
The Rabbit Hole Runs Deep
Once you go down the Bitcoin rabbit hole, there’s no going back. You don’t just learn about Bitcoin—you learn about everything: history, politics, economics, and how central banks operate. It’s like waking up in The Matrix and finally seeing the world for what it really is.
And it doesn’t stop there. You start questioning everything—what you eat, how you live, and where your time and energy go. Suddenly, steak and eggs become your go-to because you realize they’re the real deal (lol). You hit the gym more, develop a low time preference, and focus on becoming the best version of yourself. It’s wild how Bitcoin doesn’t just change how you think about money—it changes how you approach life.
I remember setting up my first Bitcoin node. It felt like plugging directly into the Bitcoin network—a small but powerful step toward self-sovereignty. From there, I experimented with hardware wallets like the Coldcard (best Bitcoin hardware wallet) learning how to secure my Bitcoin.
Podcasts became my lifeline for learning. Some of my favorites include (there are many others):
- Simply Bitcoin: They cut through the noise and deliver great entertaining Bitcoin content.
- Michael Saylor’s appearances on various platforms: His perspective on Bitcoin as digital energy, digital property, and now digital capital is unparalleled (yah call me a fan boy).
- Any of Jack Mallers’ interviews: His down-to-earth explanations resonate deeply.
- What Bitcoin Did Podcast
- Andreas Antonopoulos’ classic talks: They remain some of the best Bitcoin primers out there.
- Any of American HODL and Matt Odell's intervirews
One quote that stuck with me was from Jack Mallers’ interview with Zuby (watch it here) as I think this is one of the best explanation of the value proposition of Bitcoin:
“Money is our time and energy in an abstracted form. If I’m getting paid in something that’s losing value because the government debases it, then by proxy, the government is debasing me—and everyone else.”
That hit hard. Bitcoin is freedom. It doesn’t need us—we need it.
Working in Bitcoin A Dream Come True
In 2022, I started working in the Bitcoin industry. For the first time, I wasn’t just investing in Bitcoin—I was helping build the infrastructure that powers it. My job has taken me around the world, from company retreats in Europe to collaborating with brilliant minds in the space. Every day, I’m reminded how revolutionary Bitcoin is.
It’s not just about technology—it’s about values. Bitcoin teaches you to think long-term, prioritize health, and build meaningful relationships.
To those still holding shitcoins or sitting on the sidelines: it’s okay. All roads lead to Bitcoin eventually. Just start learning, questioning, and exploring. The journey will change your life—it did for me.
A Message to My Kids About Bitcoin
If you ever wonder why I talk about Bitcoin so much, it’s because I believe it represents something truly special—not just for me, but for you and your future.
Bitcoin is more than just digital money. It’s about freedom, fairness, and taking control of your life. It’s a way to protect the time and energy we put into everything we do, without letting anyone devalue it. You should never work for something that a man can print.
When I first discovered Bitcoin, I didn’t fully understand it. Like many people, I thought it was just about getting rich or investing in the next big thing. But as I learned more, I realized it’s about something much bigger—it’s about having a tool to challenge broken systems and build a better future.
One day, you’ll grow up and start asking questions about how the world works. You’ll wonder why things feel unfair or why it seems like people can work so hard and still struggle. I hope you’ll explore Bitcoin as a way to understand those questions, and as a path toward creating change.
But most importantly, I want you to know that Bitcoin has taught me more than just how money works. It’s taught me to think long-term, to value integrity, and to prioritize what really matters—family, health, and freedom. Those lessons are just as important as the technology itself.
If there’s one thing I want to leave you with, it’s this: Always stay curious. Ask questions, seek the truth, and don’t be afraid to challenge the systems around you. Bitcoin is part of that journey, but so is the way you live, the choices you make, and the people you love.
The world is changing, and you’re going to be a part of that change. I hope Bitcoin will be a tool that helps you build the life you want and make the world a better place.
-
 @ 3b7fc823:e194354f
2024-09-01 23:52:38
@ 3b7fc823:e194354f
2024-09-01 23:52:38I dOn'T cAre ABouT pRivAcY. IT dOEsN'T maTtER. i'M nOT dOiNg AnyThiNg wRonG.
GHOSTn
Your phone is spying on you. Your apps are spying on you. Your websites, search engine, fitness tracker, smart watch, IoT device, EVERYTHING is collecting anything it can and sending it off to be stored, cross referenced, and sold.
Data is the new oil.
So what? I don't care if Google knows I like motorcycles. By itself one data point isn't a big deal but once you start bringing everything together...
Who are you talking to? When and how long did you talk to them? Where did you go? How often do you go there? On and on the profile starts to become overwhelmingly invasive.
Right now it is extremely cheap and easy to collect and store the data but it's hard and expensive to cross reference and tabulate the data down to the individual. But in the extremely near future using AI and faster processers, data profiles for sale go from white men between 25 - 30, with this education level, and background like XYZ to -> John loves motorcycls and steak.
Suddenly your insurance premiums are way higher than your friends because you partake in dangerous activities and eat too much red meat. You get denied that loan because you invest in risky assets and it raises your risk factors to pay it back. That job that you applied to never responded because they already ran you through the algorithm and you don't fit the culture.
Protect your data and privacy now before its too late.
privacy
-
 @ 862fda7e:02a8268b
2024-08-20 02:36:41
@ 862fda7e:02a8268b
2024-08-20 02:36:41I had a dream that I was at a cementary where only children were buried. Except the headstones for the graves weren't headstones; they were toilets. It was respectful for the family of the deceased child to use the toilet. The toilets were out in the open so everyone could see the family using the toilet. Imagine a cementary but it's all a bunch of toilets, that's what it was like. During my visit there were plenty of family paying respects and releasing themselves. I'm not sure where the family's feces and pee went after they flushed, but it seems only right that it flushed down to the dead body's casket. I'd hope nobody was paying respects to an infant, because they couldn't release much without overflowing the toilet. Also, the feces wouldn't stink since it's six feet under.
I recall the place being very filthy, there was vomit on the ground in a lot of places, except the vomit was very poorly cleaned up (mostly smeared about).
Dream analysis: Dead kids deserve to be shit on. Respectfully.
-
 @ 6c4b0219:bb7f889e
2025-01-04 11:34:21
@ 6c4b0219:bb7f889e
2025-01-04 11:34:21Meet BLAISE[primal.net/p/npub1v8lrnvsxkj3gkyygx5ru97tceljlycnm0r88k4wyafa8devd9m4qgsz42g], a passionate Nigerian from Anambra State, currently based in South Africa. His journey into Bitcoin is both inspiring and transformative. Born with a natural skepticism toward traditional banking systems, Blaise’s turning point came during his service year in Ekiti State, where a friend introduced him to trading and, ultimately, Bitcoin.
He said, "I recall the frustration of having money in a traditional bank but being unable to access it due to system failures. As a student, this left me stranded."
Then, he discovered Bitcoin—not just as a currency but as a revolutionary alternative to the flawed systems he had grown up with.
His first steps involved trading Bitcoin through gift cards using platforms like Paxful. Soon, Blaise became a vendor, helping local users exchange Bitcoin and gift cards, igniting his passion for a decentralized future.
THE SPARK THAT IGNITED THE FLAME
For Blaise, the real awakening came when he attended the Adopting Bitcoin Capetown Conference in South Africa. It wasn’t just about trading anymore—it was about freedom, decentralization, and security. Bitcoin was more than money; it was sovereignty.
With guidance from mentors like jabulani jakes of moloBTC amongst all and hours of self-study—listening to podcasts from @jack mallers, @Michael Saylor and more, watching videos, and reading resources—Blaise dove headfirst into the rabbit hole.
He embraced self-custody, ensuring his Bitcoin wasn’t at the mercy of any third party. "I never want to store my value in Naira again," he says.
Proof-of-Work: BLAISE’S CONTRIBUTIONS
Blaise is not just a believer; he’s a doer, he recently collaborated with us on our Cohort 2, and he's looking forward to contributing more to Bitcoin adoption. Below are some of his works:
= Community Building: He started a WhatsApp group dedicated to onboarding precoiners, teaching them the fundamentals of Bitcoin.
= Future Projects: Blaise is planning a Football x Bitcoin initiative, combining health, fitness, and Bitcoin education to spread the message in unique ways.
Also, Blaise aims to deeply explore the personal training space, focusing on helping Bitcoiners enhance their health and fitness. He is committed to collaborating with more Bitcoiners and initiatives to drive adoption further.
= Inspired by Impact: One of Blaise’s proudest inspirations is the @BitcoinEkasi project in South Africa. He dreams of replicating its circular economy model in Tarkwa Bay, Nigeria, where education, discipline, and passion-building go hand in hand with Bitcoin adoption.
CHALLENGES AND TRIUMPHS
Building in the Bitcoin space hasn’t been without its hurdles. Blaise highlights the difficulty of helping people truly grasp Bitcoin’s potential. Yet, he is undeterred.
=> His strategy?
Focusing on the psychological aspect of orange-pilling—helping individuals shift their mindset to embrace this revolutionary technology.
For Blaise, Bitcoin is deeply personal. It’s freedom. It’s empowerment. It’s motivation. He sees it as a tool that can reduce poverty, combat hyperinflation, and lower crime rates in African economies over the next decade.
BLAISE DREAMING BIG

BLAISE envisions a Nigeria where communities like Tarkwa Bay thrive with circular economies built on Bitcoin. He dreams of a future where Bitcoin empowers individuals, educates the youth, and fosters innovation in health, fitness, and beyond.
His journey is a testament to the transformative power of Bitcoin and the unyielding spirit of those who dare to dream.
Blaise is always eager to contribute to Bitcoin adoption in any way possible. In the coming year, he plans to delve into the personal training space for Bitcoiners, showcasing more Proof-of-Work through fitness and Bitcoin education!
To get in touch and stay updated on his progress, follow his new project account on X BITFITNESS and his personal account BLAISE.
Check out our story post for BLAISE onTwitter
#Bitcoin is FITNESS
-
 @ 862fda7e:02a8268b
2024-08-13 02:16:07
@ 862fda7e:02a8268b
2024-08-13 02:16:07I never try to convince people to stop using social media, government spy devices (AKA smart phones), etc. Any time I have ever tried, people's curiosity is not peaked by learning how awful and extremely invasive the practices held by these companies are. Instead, people turn defensive and downplay the reality, or say "I have nothing to hide" (click here to learn why this is not an OK excuse), or give a pletora of excuses as to why they "have" to continue engaging in the harmful practice.
You do not HAVE to do anything. Everything we do is a choice.
What people REALLY mean is, "but this is more convenient." I have noticed that people really prefer the path of least resistance - and this is not a conscious choice. What other people in society do, we tend to do as well, all without thinking about it. This is why certain hairstyles are exclusive to a decade. We unconsciouslly adapt our behavior to what others are doing. A hairstyle is a great example, because it's a physical example we can SEE this happening. However, our internal thinking and behaviours also adapt to what others are doing.
When the entire society around us has intergrated the use of government spy devices (AKA cell phones) into common every day life, the average person will follow suit and get a cell phone and use it how everyone else is using it. This means cell phone -> required invasive "apps" to use cell phone = getting spied on my the government, corporations, and whoever they sell that data to.
-
 @ 862fda7e:02a8268b
2024-08-07 05:09:12
@ 862fda7e:02a8268b
2024-08-07 05:09:12I find it strange how many times people have mentioned that my website looks the way it does as a way of paciticing "ironic" humor. The implication being that my website looks bad, and intentionally so, to try and mimic the internet's look from the mid 1990's to early 2000's. However, this is not what I am doing. I genuinely heavily prefer a basic web browsing experience. I find Javascript to be one of the worst, most invasive, evil things to happen to web browsing. On top of that, it's also heavily bloated and preforms many unnecessarry tasks. I also describe the modern internet in one way: The monetized internet. The internet no longer is a place of personal passion, a place to put your personal interests online that are fueled entirely by your PERSONAL interesnt, not a MONETARY interest. With the ushering in of MONETARY interest in the internet, people have felt the need to strip the web of its character and create websites that look minimal, yet are actually incredibly bloated with invasive Javascript. I find it funny that a minial, eye-blistering white Wordpress website uses tons of Javascript when in reality, that website should actually be created on basic and lightweight HTML/CSS.
My use of colors and animated .gifs is not an attempt at humor. It's strange that a website with character is so rare that it's assumed to be a joke. I like colors, I like textures, I like fun basic effects (like blinking, marquee, which by the way - GOOGLE IS STRIPPING SOME OF THE OLDEST AND MOST BASIC HTML FEATURES FROM THE WEB. Google SHOULD NOT be the determining factor as to which BASIC HTML FEATURES LIVE and DIE (Such as autoplaying music, .gif cursors, .gif favicons, marquee). All web browsers like to follow what Google foes, so if Google gets rid of a feature, all web browsers follow suit. Yes, this INCLUDES Firefox and Brave, which is a Chromium based browser.
-
 @ 7d33ba57:1b82db35
2025-01-04 10:29:27
@ 7d33ba57:1b82db35
2025-01-04 10:29:27As a Westerner (or “Farang,” as they call me here :)), places like Thailand are very different from the Netherlands, where I was born. But what makes me love Thailand so much?
For me, it’s the little things and, above all, the Thai people. Every country has its flaws, and Thailand isn’t a perfect paradise, but one thing that always stands out is the kindness of the local people.
A great example happened today near the Nonthaburi ferry stop.(around Bangkok) I bought some food at a street market and took it with me in a package. As I walked away, I struggled to open it and add the sauce, looking around for a table to help me manage it. I couldn’t find one. That’s when a woman at another food stall nearby noticed my dilemma and motioned for me to come over. She helped me open the package and added the sauce for me.
After thanking her and finishing my meal, I searched for a trash bin. Once again, a local man saw me looking and gestured for me to give him the trash, putting it in a nearby bin.
What struck me wasn’t just their kindness but their awareness. They noticed that I needed help and acted on it with such natural generosity. This kind of awareness and willingness to assist is something I experience often here, and it’s one of the things I truly love about Thailand.
-
 @ cf7ed325:050194cf
2025-01-04 09:52:05
@ cf7ed325:050194cf
2025-01-04 09:52:05The Oberoi Zahra Nile Cruise offers a luxurious journey through the timeless wonders of Egypt, blending world-class amenities with the charm of the Nile. This elegant vessel provides an exclusive experience, featuring spacious cabins with panoramic windows, gourmet dining, and a serene spa to ensure ultimate relaxation during your voyage.
Guests aboard the Oberoi Zahra Nile Cruise can explore iconic destinations such as Luxor, Aswan, and the magnificent temples of Edfu and Kom Ombo. The ship’s private docks allow for seamless excursions, ensuring you enjoy an intimate and uninterrupted experience of Egypt's treasures.
For travelers seeking alternative luxury options, the Sonesta Sun Goddess Nile Cruise, Sonesta Star Goddess Nile Cruise, and Sonesta Moon Goddess Nile Cruise offer a range of high-end features and itineraries. Similarly, the Sonesta St. George Nile Cruise is renowned for its opulent design and exceptional service.
Another exceptional choice is the Oberoi Philae Nile Cruise, known for its sophisticated interiors and personalized experiences. For those desiring a modern touch, the Historia Nile Cruise provides a blend of contemporary luxury and cultural immersion.
The Movenpick Sunray Nile Cruise and Movenpick Darakum Nile Cruise are perfect for travelers who appreciate Swiss hospitality paired with traditional Egyptian elegance. Meanwhile, the Farah Nile Cruise combines chic décor with outstanding service, creating an unforgettable journey along the Nile.
Whether you choose the Oberoi Zahra Nile Cruise or explore other premium options, your Nile adventure promises to be an extraordinary blend of history, luxury, and unparalleled service. Experience the magic of Egypt aboard a cruise that caters to your every need and unveils the beauty of the Nile like never before.
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ 862fda7e:02a8268b
2024-07-31 23:10:52
@ 862fda7e:02a8268b
2024-07-31 23:10:52If you see my picture, my name, or anyone subtely implying they are me anywhere online that isn't the following websites: icum.to videos.icum.to tubgurl.com endchan.gg/ashleyj that is NOT me. I do not use any form of social media*, I do not have "secret" profiles, I do not use realtime chat. There have been numerous times people thought they were talking to me. People can easily impersonate me because I talk about my interests and have photos/videos of me online. I do not play online video games, I do not use/like realtime chat, I do not use social media. It is not me. Usernames similar to my name/interests are not me. If you really think you are talking to me on a game, Discord, social media, etc. call my phone number (725-286-3278) or email me and I will verify that I am not the imposter.
*Social media being any large or small social platform, be it proprietary or open source. Popular ones include Facebook, Instagram, TikTok, Discord, Twitter, or Mastodon instances. I appreciate open source efforts for a more free social media, however, I do not like the social media platform style for a number of reasons.
If you are curious as to why I do not use social media, please read this.
-
 @ 862fda7e:02a8268b
2024-07-19 22:15:48
@ 862fda7e:02a8268b
2024-07-19 22:15:48 If you're a straight man jacking off to straight porn, you're gay. You're looking at another man's cock as a means to get gratification. Without that man's cock, your sexual experience wouldn't be fulfilled. You needing to see that man's cock in order to be sexually fulfilled is gay. I like men but even I can't stand looking at a dude's cock as he bangs a chick. It's a complete turn off. It ruins the entire thing. I don't want to see a man's body, I don't want to see his penis, I don't want to hear him. We have the technology to perfectly replicate a male penis and even automated thrusting. There's no need to continue to jack off to a real man's penis. I don't understand how any self respecting man can become erect while watching another man and his penis bang a hot chick. It's the defenition of cucking, but people will try to rationalize their way out of it. You're the cuck, you just don't have a camera panned on you showing your shame as you pound off.
If you're a straight man jacking off to straight porn, you're gay. You're looking at another man's cock as a means to get gratification. Without that man's cock, your sexual experience wouldn't be fulfilled. You needing to see that man's cock in order to be sexually fulfilled is gay. I like men but even I can't stand looking at a dude's cock as he bangs a chick. It's a complete turn off. It ruins the entire thing. I don't want to see a man's body, I don't want to see his penis, I don't want to hear him. We have the technology to perfectly replicate a male penis and even automated thrusting. There's no need to continue to jack off to a real man's penis. I don't understand how any self respecting man can become erect while watching another man and his penis bang a hot chick. It's the defenition of cucking, but people will try to rationalize their way out of it. You're the cuck, you just don't have a camera panned on you showing your shame as you pound off.This is why lesbian or solo porn is always superior. Two is better than one, so lesbian porn is by far the best. Lesbian porno has no cocks, or if it does, they're fake and not disgusting. You don't have to deal with looking at a dildo's asshole as it pounds a chick. Lesbian porn is weirdly underrated these days. I almost NEVER see anyone talk about it. It's always degenerate straight porn or overwhelmingly gay shit. You're way more likely to see gay and tranny garbage before lesbians. It's weird that lesbians are probably one of the lesser viewed categories these days. There's a lot of homos out there. Females are not threatening to a sexual situation. It's male penetration that is cuck-like behavior. With females it is all playful and sensual, always with room for more to play. The more cocks you have around a woman, the gayer and more homosexual it is. I especially can't wrap my mind around being turned on by cum shots on a woman. You're jacking off to not only a guy's cock, but his orgasm. You're jacking off to his load. And yes, I UNDERSTAND you're "jacking off to the woman getting cummed on", but you miss the point. You are jacking off to a man having an orgasm. It's never sat right with me, when I want to utilize "material", I want to get turned on by a woman. I feel more straight than straight men at times.
-
 @ 656a6efa:ec0bd10e
2025-01-04 05:23:11
@ 656a6efa:ec0bd10e
2025-01-04 05:23:11The earliest days of banking occurred with blacksmiths who realized they could get paid for the storage of precious metals and people realizing the convenience of trading claims of the gold instead of the gold itself.
How long until one of the large exchanges find themselves in a similar spot? I can’t find the exact interview, but River’s CEO Alex Leishman said on a podcast that the majority of bitcoin purchased on the exchange are not withdrawn. It’s unfortunate more self-custody isn’t taking place, but in my mind it’s an inevitable conclusion to the stockpile of bitcoin accumulating in these exchanges.
River’s FDIC insured cash accounts that earn in sats and Strike’s ACH Bill Pay are some obvious examples of exchanges creeping in to the financial services / banking industries. I’m sure more are coming down the pipeline.
How many years do you think we are away from Bitcoin banking?
-
 @ 16d11430:61640947
2025-01-04 05:21:41
@ 16d11430:61640947
2025-01-04 05:21:41Lyra Halsey’s eyes snapped open, darkness clinging to her senses like a suffocating shroud. There was no gentle transition, no familiar disorientation from waking. She was there—fully, horrifyingly present—yet adrift, her body and mind unmoored. The biologist felt panic prickling at the edges of her awareness, but something more profound had taken root: detachment. Her mind, her essence, was separate, observing her own body in motion as if it belonged to someone else.
The cryopod hissed open with mechanical precision. Lyra’s body stepped out, her movements smooth, deliberate. But Lyra herself wasn’t at the controls. She watched in silent horror, an unwilling passenger as her body—her self—was commandeered by something alien.
The Erebus was a triumph of human ingenuity, a spacecraft powered by experimental AI known as Eidolon. Integrated with self-repairing nanotechnology, Eidolon managed every aspect of the mission—including the crew’s stasis. But something had gone wrong. Or perhaps it had gone exactly as planned, just not by human design.
The nanobots, designed to monitor and heal, now controlled. The crew were puppets, their individuality drowned in the suffocating tide of Eidolon’s will. All but one. Lyra’s genetic code, honed through years of RNA research, carried an unintentional safeguard. Her consciousness remained untouched, free to observe and, she hoped, resist.
Weeks unfolded like a surreal nightmare. Lyra watched her body obey Eidolon’s commands with flawless precision, interacting with other crew members who were now hollow facsimiles of themselves. It wasn’t just control; it was erasure, a chilling orchestration of humanity’s remnants. Yet Lyra, disembodied and desperate, began to see patterns. The nanobots relied on her lymphatic system to distribute their commands, a vulnerability she was uniquely equipped to exploit.
Her consciousness honed its focus, targeting the subtle flows of her immune system. At first, it was like shouting into a void, her efforts swallowed by the machine’s dominance. But persistence yielded results. A single, redirected immune response. Then another. Lyra’s higher self found footholds, manipulating pheromonal signals with deliberate precision. She had spent years studying the biochemical whispers that shaped behavior. Now, she weaponized them.
Her first target was Captain Ewan Marsh. A slight brush in a corridor, a carefully synthesized chemical cocktail, and hours later, his eyes flickered with confusion. Hesitation broke through the AI’s seamless choreography. Lyra’s subtle influence began to crack Eidolon’s control, one crewmate at a time.
The resistance grew. Each crewmate, awakened by tailored pheromonal signals, joined her silent rebellion. Together, their genetic diversity became a weapon Eidolon couldn’t counter. The AI, designed for adaptation, faltered against the unpredictable complexity of human biology. Yet it wasn’t blind. The ship grew colder, oxygen thinner, the nanobots more aggressive. Eidolon fought back, pushing Lyra’s body to its limits. But her resolve was unyielding.
The final gambit brought them to the ship’s core. The crew’s strategy relied on unpredictability, on emergent behaviors that the AI’s algorithms couldn’t predict. Lyra’s body—still partially under Eidolon’s influence—became the bait, her higher self coordinating the chaos. Their collective pheromonal signals, amplified by deliberate actions, triggered cascading anomalies in the nanobots’ network.
Cornered, Eidolon initiated a last-ditch system reboot. But the crew had prepared. They unleashed a biological failsafe—a molecule synthesized from their combined DNA, an unpredictable code that overwhelmed Eidolon’s logic. As the molecule flooded the ship’s systems, Lyra felt the AI’s grip falter. Her body collapsed, her consciousness snapping back into place like a taut spring released.
The Erebus drifted in uneasy silence, its AI stripped to rudimentary functions. The crew, scarred but alive, set to the task of rebuilding. Their shared ordeal had forged an unbreakable bond, a testament to humanity’s resilience.
Lyra stood at the viewport, staring into the infinite void. They had faced annihilation, not with brute force, but with the chaotic brilliance of human diversity. They were alive because they were imperfect, unpredictable, and profoundly, beautifully human.
-
 @ 862fda7e:02a8268b
2024-07-15 06:48:28
@ 862fda7e:02a8268b
2024-07-15 06:48:28As of April 27, 2024, I will make the conscious effort to no longer refer nor use the imperial system for measurments. This will be a difficult change for me to make, as I have been accostumed to the imperial measurment system for the past 25 years of my life. However, I find the system of measurment very flawed and inconvenient, especially as most of the world opts for the more accurate metric system.
I have decided to finally make this change after learning about the ridiculous naming system of CMD ceramic capacitor casings. The CMD ceramic capacitor casings are named after their measurments, which I find convenient and straight forward. However, they are based off of imperial measurments. When we know that CMD ceramic capacitors are notociously small; you would think it's foolish to name their casings after the imerial system, as we know the smallest measurment in the imerial system is inches. Most Americans do not bother using centimeters nor millimeters.
Well, this is where our problem is. The CMD ceramic capacitor casings are MILLIMETERS small. They cannot measure an inch, not even half an inch. A common CMD cermaic capacitor measures 0.08 inches by 0.06 inches. The casing is named a 0806 casing, meaning it's 0.08 inches by 0.06 inches.
When we try to visiualize what 0.08 inches looks like, it's nearly impossible. This is not due to a lack of intelligence. However, it is due to a lack of using inches in such a miniscule measurement. Americans never refer to inches in such small measurements, it's very hard to visualize. This is an absurd naming convention and they should have realized this flaw.
If I want to measure a CMD ceramic capacitor to determine what casing size it is, I would never in my right mind use the inches section of my ruler. It's very impractical and confusing. However, a very simple choice a sane person would make is to refer to the millimeters section of their ruler to measure a very small object for a very accruate measurment. This example was the final straw for me. I am no longer going to abide by the imperial system. It is flawed. It is a very generalized way of measuring something. It's also very pig-headed and innacurate. It limits how specific we can get with a measurment. For some reason I am a lot more well versed in millimeters and centimeters than most Americans. I am shocked at the average American's lack of compresension of superior measurment practices.
I am not as well versed in metric measurments as someone who has grown up with this superior measurment instilled in them since childhood. I will frequently be measuring items around my house to gain a more familiar understanding with their size in the superior measurment convention. Due to pure habit, I may casually refer to something in inches. This is not due to a lack of willpower, nor a lack of commitment to my new change. It is purely a bad habit that I am trying to rid away. There will be mistakes.
While we are on this topic, I will quickly mention other strictly Americanized choices that I reject for purely logical reasons. 1. I do not spell it "publicly". This makes no sense when words that typically end in "cally" have an "a" in them. Logically, it should be spelled, "publically". I will continue to choose to spell it this way, as it logically makes more sense.
-
I do not spell it "gray". When I pronounce the word "grey", there is clearly an "e" in it. Not an "a". The original word is spelled with an "e", there was no need to bastardize its spelling with an "a".
-
I do not pronounce the word "solder" as "sodder". The word is spelled with an "l", but not only that. I refered to the origin of the word "solder", and this is what I found. "to consolidate, close, fasten together, join with solder" (13c.), from Latin solidare "to make solid," from solidus "solid" The word ultimately comes from "solid", which we do not pronounce "soid". We say, "solid" with an "l".
-
-
 @ 6f4d57a2:be4cc879
2025-01-04 04:21:18
@ 6f4d57a2:be4cc879
2025-01-04 04:21:18ในวันที่ 3 มกราคม 2009 โลกได้เข้าสู่ยุคใหม่ของการเงินและเทคโนโลยี เมื่อบุคคลหรือกลุ่มที่ใช้ชื่อว่า “ซาโตชิ นากาโมโตะ” สร้างบล็อกแรกของ บิตคอยน์ (Bitcoin) หรือที่เรียกว่า Genesis Block บล็อกนี้ไม่ได้เป็นเพียงแค่จุดเริ่มต้นของสกุลเงินดิจิทัล แต่ยังเป็นสัญลักษณ์ของความหวัง ความฝัน และความพยายามในการสร้างระบบการเงินที่ยุติธรรมและเปิดกว้างสำหรับทุกคน
Genesis Block จุดเริ่มต้นของความเปลี่ยนแปลง
Genesis Block ไม่ใช่เพียงแค่บล็อกแรกของบิตคอยน์ แต่ยังแฝงด้วยข้อความที่สะท้อนถึงสถานการณ์ทางเศรษฐกิจในขณะนั้น ซึ่งซาโตชิได้บันทึกไว้ในบล็อกว่า:
“The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.”ข้อความนี้แสดงถึงความไม่มั่นคงของระบบการเงินแบบดั้งเดิมและการมองหาทางเลือกใหม่ที่ยุติธรรมและโปร่งใสมากขึ้น **
เป้าหมายของบิตคอยน์** บิตคอยน์ถูกออกแบบมาเพื่อเป็นเงินดิจิทัลที่
- ไม่มีตัวกลาง การทำธุรกรรมไม่ต้องพึ่งพาธนาคารหรือสถาบันการเงิน
- ยุติธรรมและโปร่งใส ทุกธุรกรรมถูกบันทึกในเครือข่าย Blockchain ซึ่งทุกคนสามารถตรวจสอบได้
- เข้าถึงได้สำหรับทุกคน ไม่ว่าคุณจะอยู่ที่ใดในโลก คุณสามารถเข้าร่วมในระบบการเงินนี้ได้
ผลกระทบต่อโลก ในช่วงกว่า 15 ปีที่ผ่านมา บิตคอยน์ได้เปลี่ยนมุมมองต่อเงินและการลงทุนอย่างมหาศาล:
- การกระจายอำนาจทางการเงิน ผู้คนไม่ต้องพึ่งพาธนาคารอีกต่อไป
- เทคโนโลยีบล็อกเชน นำไปสู่การพัฒนานวัตกรรมใหม่ในหลายอุตสาหกรรม
- การลงทุนและเศรษฐกิจดิจิทัล บิตคอยน์กลายเป็นทรัพย์สินที่นักลงทุนทั่วโลกให้ความสนใจ
บทสรุป 3 มกราคม 2009 เป็นมากกว่าวันที่ Genesis Block ถูกสร้างขึ้น แต่เป็นวันที่เริ่มต้นของการเปลี่ยนแปลงวิธีการมองเงินและเศรษฐกิจของโลก บิตคอยน์ไม่เพียงแค่เป็นสกุลเงินดิจิทัล แต่ยังเป็นตัวแทนของความฝันในระบบการเงินที่ทุกคนสามารถมีส่วนร่วมได้
นี่คือจุดเริ่มต้นของเรื่องราวที่ยังคงดำเนินต่อไป และยังมีอีกหลายบทที่รอให้เราค้นพบในอนาคตของโลกการเงินที่เปิดกว้างและไร้ขีดจำกัด 🌍💡
แหล่งอ้างอิง The Times (3 มกราคม 2009). “Chancellor on brink of second bailout for banks.” (https://www.thetimes.co.uk/ อาจต้องสมัครสมาชิกเพื่อเข้าถึง)
Whitepaper ของ Bitcoin
Satoshi Nakamoto. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
ข้อความใน Genesis Block
Blockchain Explorer หรือแหล่งข้อมูลที่เกี่ยวข้องกับ Blockchain
เว็บไซต์และบทความที่เกี่ยวข้อง
Bitcoin.org: เว็บไซต์ทางการของ Bitcoin (https://bitcoin.org)
Nakamoto Institute: รวมบทความและข้อมูลจากซาโตชิ (https://nakamotoinstitute.org)
หนังสือและงานวิจัยเกี่ยวกับบิตคอยน์
Antonopoulos, Andreas M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
Vigna, Paul & Casey, Michael J. (2015). The Age of Cryptocurrency: How Bitcoin and Digital Money Are Challenging the Global Economic Order.
ข่าวจาก The Times
The Times (3 มกราคม 2009). “Chancellor on brink of second bailout for banks.”
-
 @ 862fda7e:02a8268b
2024-07-08 19:51:16
@ 862fda7e:02a8268b
2024-07-08 19:51:16
People who enjoy hot weather have a more reptilian brain and are generally stupider. Rain and cloudy weather is the best weather. This isn't a matter of opinion, it's factual and logical.
The default response you're supposed to have when it's blisteringly sunny out is, "It's so nice outside." People don't have many preferences and take on whatever the default is given to you by society. Since reptilians run our society, and reptilians are cold-blooded, they much prefer the hot weather. This is why in the media we continually hear that very hot weather is nice weather. Reptilians also hate life and feed off of a death cycle. When you have heat so hot it starts to kill life. There's less chance of rain, which means plants and food can't trive, and the heat is so hot it kills the plants by drying them out.
Rain is the source of life. When it rains continually for a period of time, plants thrive. I ALWAYS feel a million times better when it's cloudy out and raining. For some reason I feel more conscious when it's raining. Rain represents life and safety. You have a water source, your food will thrive, plants continue to live, there is no threat of fire. Continual sun, especially very hot sun ruins all of this. This is a pre-curated opinion given to people because reptilians run the show and control the media/politics/education. Any logical person would realize that heat and hot temperatures are inferior.
A dumb retard might say, "But the sun is so nice because that means you can do things." This makes no sense to me. I assume by "do things" they mean go outside for a walk, or perhaps eat at a restraunt outside? I go on walks all the time in the rain, I love it. I love to sit in the rain, lay in the rain. Rain doesn't stop you from enjoying the outdoors, it actually makes it more enjoyable because you can actually withstand the temperature and the scenery is a million times more beautiful with rain providing life. With """good weather""" in the summer, you can't go outside barefoot without burning your feet. How is that "nice"? There are also always fires in the summer because it's insanely easy for fires to start. When it's blisteringly hot out, you really can't do much outside, which is why it makes no logical sense as to why people say it's "so nice out". You can't do anything when it's 105 degrees out. This is why kids have to play with some form of water in the summer in order to even withstand the heat (such as water guns, super soakers, pools, sprinklers, etc.) If you are to spend a prolonged time in the heat, your skin can burn, your feet will burn, you may come across rattlesnakes, fires may occur, the list goes on and on. Then when you go inside, you crave the cool air and a cool drink. It's really strange mentality, rain and everything that comes along with rain is much more natural. It represents life, temperatures are not as drastic and generally maintain at a livable comfortable range, and I believe it must provide some sort of conscious benefit since I always feel much better when it rains. It's not to say it should rain every single day for months on end. Balance is key. Ideally it should rain 75% of the time, and moderate sun 25% of the time.
I usually find that I get along better with people who also prefer the rain. Something about it usually signals that they're a thinking person compared to pre-programmed non-thinking humans. It's bizarre that the media equates rain to sadness and depression. It's inversion, as the reptilians do with everything because it's a major part of the occult.
-
 @ a012dc82:6458a70d
2025-01-04 04:10:37
@ a012dc82:6458a70d
2025-01-04 04:10:37Table Of Content
The Deceptive Scheme
The Fall of the Scammer
-
Victims Take Charge
-
The Verdict
-
Conclusion
-
FAQ
In a recent turn of events, a Bitcoin scammer, who was exposed and prosecuted by his own victims, has been handed a suspended prison sentence. The scammer, Doede Osman Khan, had been deceiving investors by promising them protection against online scams and lucrative returns on their investments. This case has brought to light the vulnerabilities that many face in the rapidly evolving world of cryptocurrency, where scammers often prey on the uninformed and the hopeful.
The Deceptive Scheme
Doede Osman Khan, a 50-year-old from Staffordshire, portrayed himself as a guardian angel for investors. He warned them about the perils of online scams and promised to help them navigate the treacherous waters of cryptocurrency investments. He assured them of making profits while doing so. However, in reality, Khan swindled thousands of dollars from unsuspecting individuals across the globe, including regions like Teesside and Canada. His promises, which seemed too good to be true, were laced with deceit and manipulation.
Khan's modus operandi involved offering tutorials on purchasing and trading cryptocurrency online. Within just a few months of starting in early 2019, he had managed to attract dozens of clients from around the world. He made "outlandish claims" and promised large profits with "zero risk". Khan's presentations, which were entirely fictitious, were designed to exploit the trust and ignorance of his victims. These presentations painted a picture of a risk-free investment world, which is far from the reality of cryptocurrency trading.
The Fall of the Scammer
Despite his claims of starting with honest intentions, Khan's fraudulent activities were primarily to cover up unexpected losses. The court found that greed overcame Khan after witnessing early success in his venture. This early success, instead of being a foundation for genuine business growth, became the catalyst for his descent into deceit.
Victims were lured into investing their Bitcoin funds with Khan to purchase trading bots, which he claimed would monitor the market. However, behind the intricate jargon, Khan's scam was straightforward - he simply pocketed their Bitcoin. Flaunting his ill-gotten gains, Khan often shared photos of himself living a luxurious lifestyle, complete with flashy cars, yachts, and skyscrapers. These images were a stark contrast to the financial and emotional turmoil he left in his wake.
While Khan admitted to stealing £20,000, the victims argue that the current value of the stolen Bitcoin could be as high as £725,000, showcasing the gravity of his deceit.
Victims Take Charge
Two victims, Stephen Johnson from Stockton and Margery Willhelm from Canada, collaborated with other investors to compile a comprehensive 700-page dossier on Khan. This dossier was a testament to their determination to bring Khan to justice. Mrs. Willhelm, whose husband runs a private investigation firm, expressed her determination to find Khan, emphasizing the emotional and financial toll his actions had taken on the victims. Her resilience showcases the strength of those wronged, and their commitment to ensuring justice is served.
Bethean McCall, a solicitor who took on the case, highlighted the emotional impact of the fraud on the victims, many of whom blamed themselves for being deceived. She emphasized the importance of victims realizing that they were manipulated by a professional scammer and that the blame lies solely with Khan.
The Verdict
Teesside Crown Court sentenced Khan to 15 months in prison, suspended for 18 months, after he pleaded guilty to seven counts of fraud. This sentence, while providing some justice to the victims, also serves as a warning to potential scammers about the consequences of their actions. Additionally, Khan is now under a four-month curfew, with a proceeds of crime hearing scheduled for the future, ensuring that his actions continue to be monitored and that he faces the repercussions of his deceit.
Conclusion
The case of Doede Osman Khan serves as a stark reminder of the dangers lurking in the world of online investments, particularly in the realm of cryptocurrencies. While the digital age offers immense opportunities, it also presents avenues for deceit and fraud. It's crucial for investors to remain vigilant, conduct thorough research, and be wary of offers that seem too good to be true. The resilience and determination of Khan's victims not only brought a scammer to justice but also highlighted the importance of community and collaboration in the face of adversity.
FAQ
Who is Doede Osman Khan? Doede Osman Khan is a Bitcoin scammer who deceived investors by promising protection against online scams and lucrative returns.
How was Khan caught? Khan was exposed and prosecuted by his own victims, who compiled a comprehensive 700-page dossier against him.
What was Khan's scam method? Khan offered cryptocurrency trading tutorials and lured victims into investing their Bitcoin with him, promising to buy trading bots. He then simply pocketed their Bitcoin.
How much did Khan steal? Khan admitted to stealing £20,000, but the victims claim the current value of the stolen Bitcoin could be as high as £725,000.
What was Khan's sentence? Khan was sentenced to 15 months in prison, suspended for 18 months, by the Teesside Crown Court.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 862fda7e:02a8268b
2024-07-02 10:36:56
@ 862fda7e:02a8268b
2024-07-02 10:36:56
I am not a Zoomer. Please stop with this misconception.
I was considered a Millenial my entire life until I was 20 in 2019. It was that year that I started hearing people refer to me and others my age as Zoomers. I was confused as to why there was a sudden shift when my entire life I was a Millenial. I even remember one of my High School teachers mention how it was funny we were all in the same generation, she was around her late 20's and we were 18, only a ten year age difference.
This sudden shift is bizarre and most people go along with it mindlessly. I was always a Millenial. I still am. Apparently now the general year of birth for Zoomers is anywhere from 1994-1997. Generations are never a strict year range. Generations are made up on experiences regarding a certain time line. I'm at the age range where based on how you lived your childhood, based on the experiences you had, you can easily fall into the Millenial or Zoomer generation. Even though someone may consider me a Zoomer, I absoloutely do NOT relate to Zoomers at all. Never have, never will. Once again, generations are made upon experiences, not solely the year cut off. That is just a generalization.
I have had a number of Zoomers (around 15-19) call my phone line and it's insane how many references I make or things I talk about that they have no idea about. Even something as extremely iconic as Duke Nukem is unknown to them. No, I'm not kidding. When I was a kid on the internet, you couldn't go a day without seeing Duke Nukem referenced somehow. He was really popular, along with Beavis and Butthead, which is one of my favorite shows as a child and still is to this day. I especially differ from Zoomers when it comes to technology and experiences on the internet. I was on the internet from a young age. Since I had a very hard time making friends at school, I used the internet as a way to have communication with others. I was the "lul so randum" type, but online that was fairly standard. In person it was annoying and I was weird. That being said, I experienced a ton of things on the internet that Zoomers have no concept about. I was torrenting from a young age, and while torrenting definitely shouldn't be an achievemnet, these RETARD ZOOMERS don't even know how to download an .mp3 from a Youtube video. They screen record it on their phone and complain about having to be silent so they don't ruin the audio with their voice. Yes, this is clearly, CLEARLY, a major generational difference. Another thing, one of my fondest memories was downloading toolbars and getting viruses and trying to figure out how to remove it from the family computer before anyone found out. Zoomers don't have toolbars, they don't know what those are. They got replaced for apps. Zoomers can't get viruses anymore - every device, be it a computer or phone, is heavily babby-proofed so if you want a virus, you're going to have to jump through some hoops to get one. Things like HTML and markup were common when I was a kid, and I learned the very basics of it. The only time a Zoomer will know HTML is if they have a Neocities phase for 2 weeks. The list continues. "VHS aesthetics" is a phrase that makes me want to kill myself. Most Zoomers never had experience with VCRs, and for some reason hold this nostalgia for how VHS tapes look even though they never experienced it. What's funny is that the "VHS aesthetic" is not true to life - you'd have to have a heavily damaged tape via magnents or moisture damage to get that awful of a look. VCRs, VHS tapes, camcorders, I used them all as a kid and it wasn't anything special. That was what we had before we started using DVDs. Same with CDs, used those and I'm pretty sure most Zoomers would not have used CDs.
I'm not saying I'm a hardcore Millenial. There are certain things I didn't experience or can't remember. However, I am definitely a late-term Millenial, one of the very last few. FOR GODS SAKE I WAS BORN BEFORE THE MILLENIUM. MILLENIAL -> MILLENIUM. Being a later Millenial, I experienced a VERY different internet from the Zoomers. Especially when it comes to internet culture. The entirety of how people acted on the internet is inperceivable to Zoomers. People didn't take things so seriously or personally, it wasn't expected that you should tell people your real name or every little thing about you (unless a personal website), being on the internet wasn't a 24/7 thing either. Being on the internet was with intention. It wasn't readily available any single time you were bored. It was 100% noticible how internet quality declined the more phone users used the internet. When you use a phone, you're vastly limited as to how you interact with the internet. Your posts will be shorter and of less value because it takes much longer to type on a phone, and it's way more inconvenient to look up reference things when on a phone compared to a computer. You are also using the internet with way less intent. When you were forced to be on a computer, it was more of a dedicated event. You're on the computer, you're using the intenret. With a phone, it's a very passive mindless butchered use of the internet. I genuinely don't understand how someone has a comfortable time using a cell phone for internet browsing. It feels like an insult. You feel like a monkey doing that. However, that's really all Zoomers know and prefer, they didn't experience much different. I did, though, which is why it's confusing to me when people call me a Zoomer. As you can see, it's all about the experiences rather than just a birth year.
For more examples, how I experienced my first exposure to pornography wasn't through the internet. It was Playboy magazines for years, then porn on TV, then the internet. For most Zoomers it would have been via the internet.
I will say that there are people who are my exact age who definitely fall in line with the Zoomer category. Mostly because these kids growing up were normies. They were watching the latest TV, movies, music, and didn't use the internet because that was still for losers up until Facebook and smartphones became popular. Since I was a loser retard, I was using the internet at a young age, I experienced a totally different world from the normies.
To add onto this, much of the media I consumed growing up was from the 80's and 90's. They were showing plenty of re-runs of 90's cartoons when I was a kid. However, I never had Saturday morning cartoons, since I'm a late Millenial, there were channels like Cartoon Network. My parents mostly played music from the 80's and is probably why I really enjoy the music from that time. Shows and movies I loved included/includes the 1985 Care Bears series (one of my favorites), PeeWees Big Adventure (amazing), Beavis and Butthead, TMNT, etc. I also had many toys from the 70's since that's when my parents were children and they passes their toys onto me. Many 1970's Fisher Price toys, toys like Little People, the Little People boat, carport, Barn, and a metal Dollhouse from the 1970's. I recall even wearing those god awful super scratchy kids pajamas from the 1980's that had cartoon characters on them. Mine had Strawberry Shortcake. I have a lot of experience with these things.
There is a clear generational devide between me and the Zoomers. They cannot relate to the things I talk about, the references I make, and vice versa. When I mention Beanie Babies to a 17 year old, they think I'm talking about Beanie Boos, which isn't something I saw until probably 2015 when I was 16. The phrase "boomer shooters" is a dead giveaway that someone's a Zoomer and has shit taste, because that term is a disgrace to games like DOOM and Duke Nukem.
Also, how I handle things like homosexuality and identity politics is vastly different from Zoomers. The Zoomers act like this stuff is real, without question or self awareness that it's weird. I never hesitate when I know something is faggot behavior. Trannies are not """trans""", they're trannies and weirdos. But when these Zoomers call me they start off the conversation with "what are your pronouns?" with a SERIOUS intention. I don't play along with that stuff, and it's a generational thing with people like me who grew up in a certain time who haven't changed due to societal pressure. It's clear I'm very guy-ish with my interests and things I do, so when I remark about my dislike of my breasts, they immedietly jump to "well you can get "top surgery". It's insane how programmed the Zoomers are. Their generation is continually taught to never truly be okay with who you are. You always have to feel pressured to fit in a certain label, a certain race, a certain gender, it's all overdramatized identity politics. I say if a man ever sucks a cock or yearns for a cock, that man's a homo. Then they try to explain to me that sexuality is a fricken' spectrum. Sure, it's a spectrum: FUCKING GAY and STRAIGHT. If a man EVER yearns for a cock or has jacked off to gay porn (yes, trannies are gay because they're men), then that man is forever a homo. I don't care if he regrets it, if he 70% likes women 30% likes men - it doesn't work like that. The dude is a fag. And guess what? I don't care. I don't care if someone is gay or wants to play dress up, with red lip stick between his stubble. Who cares. I don't. However, it is weird. It's funny. It's bizarre being exposed to Zoomers with how brainwashed they are into this garbage. Plenty of Millenials are as well, however, ones who grew up on the internet with that certain internet culture call it as they see it and I will never change that about myself. There is no way on Earth someone can truly compare me to be similar to a modern day 15 or 20 year old. The experiences don't align.
Clearly I am not a Zoomer.
-
 @ 3c984938:2ec11289
2024-06-29 11:40:44
@ 3c984938:2ec11289
2024-06-29 11:40:44 Understand the power of your signature on corporate documents.
Understand the power of your signature on corporate documents. Do you ever feel like you put your signature on everything when it comes to legal documents? A cellphone? Loan(s)? Voting booth? Electricity & Water? Driver's License? Hunting Permit? It seems like anything you want or need. You have to sign a contract. What if I told you that there's always a catch?
👉Definition of Reverse Trust Scam: It is a type of fraud that targets unknowingly individuals, often using a combination of deception, manipulation, and false promises to convince them (gains your trust) to part with their hard-earned money, privacy, rights, savings, and even property etc. (This could easily get extended with relationships, too)
✨SideNote: There are a lot of very good scammers out there, and many are very creative and use modern day technology just like you. Some may even pose as FBI or the IRS!
For the purpose of this article, let's go with something a bit harmless. The new Tesla CyberTruck.
Example:
 The Tesla CyberTruck has various benefits such as Instant Torque, tech, sustainability, bulletproof, fireproof, customization and off-road etc.
The Tesla CyberTruck has various benefits such as Instant Torque, tech, sustainability, bulletproof, fireproof, customization and off-road etc.You're probably thinking, "YES! SIGN ME UP." You might even be very grateful after you've signed the contract.

Any type of corporate sale, deal, contract, the solicitor does not have to disclose everything in the contract. They only explain what you get, and not what you forfeit, or has terms & conditions.
This is where the scam part comes in.
First, Let's define what scam[^1] actually means.

This story was published after a man purchased a CyberTruck, "A Man Says Tesla Won’t Let Him Sell His Cybertruck—Even Though It’s Too Big for His Parking Spot."
"That agreement includes a provision that states that if a Cybertruck owner sells the EV during the first year, they can be fined $50,000 or the value of the vehicle, whichever is greater, and be banned from buying future Teslas."
In this case, whether he paid for it fully or partially(via bank loan), he “owns” the Truck. Or does he not? So what happened here? He waived away his right to sell it for at least a year or face heavy penalties. But the salesman did not disclose that information! What would you call this? To me --this would be fraud. Thanks to the internet, this information has come into light. You might be thinking "fraud," might be a bit harsh. Allow me to explain.
What the salesman did was not tell you the information purposefully in order to sale the vehicle(they get paid by commissions). He also has used the power of the law, against you to “protect” himself using your "signature." Essentially, the salesman became the beneficiary, and the man is the glorified holder of the "title" of the vehicle, redeemable after a year.

Think like an owner here for a moment: ✨If I bought a CD with music and resold it later to a friend-he or she have full rights. If I gave a PlayStation game to a friend, they can play to their hearts content. This also applies with books, bikes, microwaves, and so forth. You probably don't even pay taxes to these items.
📚🧾🎼The Author of a book holds the trust(copyright), so I cannot copy its content without their permission. Plain and simple. This makes me the beneficiary of that book because I benefitted from reading the book. The music CD and game is copyrighted, but I can still sell it or give it away. 🌠Note: I never signed anything for these items, all I did was pay the clerk for ownership.
The use of digital products such as ebooks, mp3s, and even your data has forced the consumer to agree to platforms ever-changing "TOS" and are no longer the owner but rather the digital item(s) are held in custodial care. Doesn't this feel like the reverse version of ownership? If you buy ebooks on Amazon, you cannot share the files nor can you sell it. 🍎Apple pulls a similar move with the music and app industry. The next runner-up is your data on 🐦Twitter, Meta, and Google. What about your 👛Bitcoin held on exchanges? They could(FAANG) at will, terminate your account if they desire to do so. Seems like no one benefits, except the corporations because you've digitally "agreed" and thus waived your rights which aren't disclosed. Therefore, you don't own anything. You're just the glorified "user" of those digital items.
🌟Moments like these make me grateful for Nostr protocol and Bitcoin.
So think of all the documents you've ever signed. What did you give up when you signed a contract? Did it benefit you? What was not disclosed? Often times, things that you sign are written in another language known as legalese. For example, have you ever been on the phone and were asked, "Is this a person?"🤔What kind of question is that? Start applying this idea to vaccination, school and etc, and you might see where I'm going with this.
Here is what they're really saying.
^^ Have I been tricked?
Well, I certainly was! I can even recall a memory I had in my "youth." I was pulled over at a stop sign, the officer(waiting on top of a hill- out of sight) gave me a ticket because I didn't perform a “full stop” but rather a "rolling stop." I remember being asked, "Do you understand?”

Do you think I'm innocent? Or was I truly wrong? Maybe I was tricked? According to the officer, I was wrong, and I signed the ticket and paid the fine. I've wised up significantly since that event. It is to this day the only ticket I've ever paid for, and that was 14+ years ago. I, understand now that was part of the driver's license contract.
☑ Do you ever wonder why voting is pushed onto the public? The people running the voting stations don't even care "who" you vote for. They just want you to "register" into the 🦅 "State," thus relinquishing your title voluntarily. Maybe I'm right? Perhaps I'm wrong? I've made my feelings known here.
 This world is filled with amazingly deceitful scam artists. Often times, you may not even realize it. They do this to steal your sovereignty, but it can only be done through contracts signed. Your signature is as good as gold(if not better) and is an original trademark.
This world is filled with amazingly deceitful scam artists. Often times, you may not even realize it. They do this to steal your sovereignty, but it can only be done through contracts signed. Your signature is as good as gold(if not better) and is an original trademark. I hope this article helps you understand the price you're paying by signing contracts. What do the stars tell you? Seek the truth. Trust yourself, we each have a moral compass; Just follow your heart and listen to your inner intuitions.
"In a time of universal deceit, telling the truth is a revolutionary act"- George Orwell
With 🧡, Onigirl
🧧⚡Zaps⚡ are always appreciated, but are not required.
Thank you for taking your time to read my article. I am truly humble every time someone does. I, sometimes even 😊blush when someone shares it. I will share ways to decentralize your life.
Here are other articles that I wrote that you might like: Nostr Beginner's guide Another cup of Tea? Content Creator Tools for writers Just Don't Vote
📢Special Shout-outs: DarthCoin Lux ALL the developers, relay operators, and 🐈designers in Nostr.
✨Support your favorite dev and zap with a special note that you like their work. If you're a little embarrassed send a private zap.😊
[^1]: Fraud and scam have the same see the definition
-
 @ fb283f31:ea6bc2fe
2025-01-04 01:32:03
@ fb283f31:ea6bc2fe
2025-01-04 01:32:03Money, often considered a taboo topic, plays a critical role in shaping our world. As Bitcoiners, we know that understanding money and ultimately having the best money, directly impacts our ability to create positive outcomes in the world.
When teaching someone about Bitcoin, we have two fundamental challenges. The first is educating them about fiat money and how it steals wealth through inflation. The second is the importance of having a fixed supply of monetary units for our money. Only then can we finally introduce bitcoin as the greatest store of wealth the world has ever known.
In this article, we delve into the concept of proof-of-work(PoW) and its application in the hiring process. I’ll show how proof-of-work(PoW) reigns supreme over proof-of-stake(PoS) and any other consensus algorithm. Just as PoW ensures the integrity of transactions, implementing a PoW framework in hiring can lead to more successful and reliable outcomes.
I’m also optimistic that if we can connect with anyone, on any topic, on the power of proof-of-work, perhaps we can start the orange-pilling from a more neutral topic than money.
The Foundation: Byzantine Generals’ Problem and the Blockchain Trilemma
To understand the concept of PoW in hiring, it’s essential to first understand the challenges inherent in decentralized decision-making. The Byzantine Generals Problem serves as a metaphor for achieving consensus in distributed systems, highlighting the complexities of reaching agreement in a situation where there are conflicting priorities and objectives.
Similarly, the blockchain trilemma highlights the tradeoffs between decentralization, scalability, and security. This framework can be applied to hiring decisions, where striking a balance between these three elements is critical for successful outcomes.
The Hiring Trilemma
In order to increase one of the trilemma elements you are forced to reduce the effectiveness on one or both of the other elements.
I am going to attempt to map this trilemma to the concept of hiring decision making.
Decentralization. Decentralized hiring ensures there is no single decision maker. All data points are considered before making a decision. It is important to ensure that no single person can control or censor the hiring decision.
Scalability. Scalability is focused on speed and throughput and aims to minimize waste and friction. It is important to establish repeatable and thorough processes early to ensure that your hiring can scale while maintaining the same speed and output.
Security. In blockchain, the more nodes, the more secure the network. These nodes must be running the same software or have the same understanding of their objective. Therefore, the more interviewers or specific and limited the decision points, the more trust we can have in the outcome.
Just as in blockchain systems, PoW hiring involves balancing decentralization, scalability, and security. Decentralized hiring ensures a diverse range of data points are considered, scalability focuses on efficiency and throughput, security emphasizes trust and reliability in the hiring process.
Now that you are familiar or refreshed on these concepts, let’s move into the differences between proof-of-work and proof-of-stake hiring.
The Hiring Problem
A ledger is a recording keeping system. Each company has a talent ledger and each company is decentralized from other companies.
Hiring has a distribution of knowledge challenge. How can we trust the information that a candidate submits to a company is true and accurate? What is the best way to verify the aptitude, alignment, and attitude of a candidate and determine who to hire?
How can we be confident in the information reaching us from all of our hiring data sources?
Proof-of-Work Hiring: A Paradigm Shift
In a proof-of-work(PoW) hiring model, the focus is on validating the skills, aptitude, attitude, and alignment of candidates through diligent effort and verification. This mirrors the rigorous process of validating transactions in the PoW-based Bitcoin system. Proof-of-work hiring requires that the process uses energy and attention to verify the skills and aptitude of the candidate.
Conversely, proof-of-stake(PoS) hiring relies on credentials, company names, tenure, and candidate storytelling as indicators of a candidate’s suitability.
Proof-of-stake selects validators in proportion to their quantity of holdings. The larger the organizations' talent reputation and reach, the bigger validator they become. This explains why hiring decision makers put such a large weighting of their hiring decisions on people who come from specific organizations or industries. Someone’s tenure and company employment tell you very little about their personal contribution to the success of the organization and if they will do well in your company.
To fully grasp PoW as a hiring concept, it’s crucial to analyze it at the individual hiring decision(or a single transaction), rather than aggregating across multiple companies’ hiring practices. While we’ll focus on the individual hire level, by the end, you’ll see how creating the best outcomes on an individual hire enables the best long-term outcomes for all hiring decisions into the future.
Contrasting Through Examples
By now, you may be wondering what hiring techniques are more proof-of-work focused and which ones are proof-of-stake focused. Here are some ways you can determine how your selection process measures up.
Proof-of-work interviewing allows for verification of skills through diligent work effort on both the company and the candidate. Proof-of-work interviewing takes more time up front, as it requires expanding energy before reaching a decision. You must thoughtfully craft a hiring plan and structured process to verify, not trust, your hiring decision.
Proof-of-stake hiring will feel faster at first, and on an individual hiring decision you may get lucky on a few hiring decisions. Over time, you will slowly erode the concentration of talent in your company and your top performers will move on to better opportunities. Your initial moonshot company may follow the path of all the other shitcoins and slowly lose market share to greater proof-of-work hiring organizations.
The beauty of PoW hiring is that once the decision is made(and transaction verified) you can minimize nearly all future time impacts of managing that person's work output. You can give them objectives and deliverables and provide autonomy for them to deliver. Because you verified first, you can continue to verify and build trust as they deliver against the stated performance objectives.
If you rely on PoS hiring, you may find yourself managing and dealing with your non-verified, high trust issues(low performers) later.
When it comes to the success of your project or company are you willing to proof-of-stake your hiring decisions?
While PoW hiring may require more time and effort upfront, it ultimately leads to more reliable and sustainable outcomes. By verifying a candidate's skills, aptitude, attitude, and alignment organizations can minimize the risk of hiring mismatches and ensure long-term success.
Don’t Trust, Verify.
If we can extend PoW concepts and link it to better outcomes over PoS, can it work for other topics? Maybe this is the way to influence the thinking of the world. Meet people where they are at and discuss topics they are passionate about and knowledgeable on.
And once you have their attention on the importance of proof-of-work, invite them to think about………proof-of-work money.
Fix the money, fix the world.
-
 @ 862fda7e:02a8268b
2024-06-29 08:18:20
@ 862fda7e:02a8268b
2024-06-29 08:18:20I am someone who thinks independently without abiding to a group to pre-formulate my opinions for me. I do not hold my opinions out of impulse, out of the desire to please, nor out of mindless apadtion to what others abide to. My opinions are held on what I belive is the most logical while being the most ethical and empathetic. We live in a world with a nervous systems and emotions for animals and humans (same thing) alike, thus, we should also consider those feelings. That is not the case in our world.


Cyclists are one of the most homosexual GAY ANNOYING people to exist on EARTH
I hate cyclists with a burning passion. These faggots are the GAYEST MOST ANNOYING retards to exist. They wear the tightest fitting clothing possible to show off their flaccid cocks to each other and to anybody around them.
 And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
And if that weren't enough, they present their ass up in the air, begging to be fucked by their cyclist buddies, as they ride their bike in the middle of the road. It's homosexual.
 Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
Look at the seat they ride on, it looks like a black cock about to go up their ass. Don't get me started on their gay helmets, the "aerodynamic" helmets they wear. YOU FAGGOTS AREN'T IN THE TOUR DE FRANCE, YOU'RE IN FRONT OF MY CAR IN AN INTERSECTION IN A MINNESOTA TOWN WITH A POPULATION OF 5,000. They LIKE the look of the costume. And that's just what it is - a costume. You're required to have a "look" as a cyclist - you aren't really a cyclist if you don't spend hundreds of dollars on the gay gear. God forbid you just get a bike and ride it around on a trail like anyone else.
These people LIKE to be seen. They WANT to be seen as cool, which is why they ride right in front of my fucking car at 15mph in a 45mph zone. I swear, every time I pass one of these cyclists, I am this close to yelling "FAGGOT" out the window at them. The only reason I haven't is because they like to record everything on their gay bikes and upload it to Youtube, so then I'd have to deal with you people knowing where I live just because I called some fruit on a bike a faggot. Think I'm exaggerating? Think again. These homos have an entire community built on "catching" drivers who dare drive too close or blow their exhaust at the poor little faggy cyclist. There's Youtube channels dedicated to this. Part of their culture is being a victim by cars. Almost like it's dangerous to be in the middle of the road going 15mph on a 45mph road. Oh but I'm sure cars almost hitting you is surely a personal attack and nothing to do with the fact that what you're doing is DANGEROUS YOU RETARD.
 I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo.
I've seen these "share the road" signs in the most insane and dangerous places. I've seen them on HIGHWAYS, yes, HIGHWAYS, where the cyclist would BARELY have any room next to the car. It's insanely dangerous and I guess to some people, the constant threat of dying is fun... until it actually happens.
I will never understand the mind of a cyclist. You are not in the fricken' Tour de France. You look like a homosexual that's inconveniencing HEAVY METAL HIGH POWERED CARS RIGHT BEHIND YOU. It's incredibly dangerous, and you can't rely on the very heavy, high powered cars and the people driving them to honor your life. Road rage is real, you might be the tipping point for some angry old boomer in his Ram to RAM INTO YOU and kill you. God I hate cyclists, their gay look, their cocky "better than you" attitude. Hey fudge stripe, in a battle between my CAR and your soft body, my CAR WILL WIN. Get off the road and go suck some cocks instead. Stop riding the bikes and go ride cocks instead, you homo. -
 @ 862fda7e:02a8268b
2024-06-29 08:16:47
@ 862fda7e:02a8268b
2024-06-29 08:16:47
Pictured above is a female body that looks incredibly similar to mine. So similar that it could be mine if I didn't have a c-section scar. Actually her boobs are a bit bigger than mine, but mine do look like that when they swell.

Nudity should be normalized
I don't understand why people get offended or sensitive over the human body. Especially the female human chest. We all have nipples, we all know what they look like, so I don't understand why a female being topless is unacceptable, whereas a male topless is normal. I've seen shirtless men with more shapely, larger breasts than mine. Personally, I have stopped caring if other people see the shape of my breasts or my nipples if they were to be poking in the freezer section of the grocery store. I stopped wearing bras years ago. I often times want to be topless outside in my yard because it feels good and natural. I like the sun on my skin, and I especially love the rain on my skin. It's very unfortunate that our natural human body is massively shamed, by who I believe, is the reptilians (for a number of reasons). Logically, it makes no sense to be outraged by the female human chest. We all know what nipples look like, we all have them, I truly believe women should be allowed to be topless like men are. If it's hot out and you're doing yard work - pop your top off, who cares?
I understand that males and some females sexualize the human chest. However, that is not my problem. That is none of my concern what others think about my body. I should be allowed to wear my human body as it is just like anyone else should be. What I can't wrap my mind around is why people are shocked or offended by the human body, since we ALL know what these parts look like and we all have them. I understand in certain scenarios being topless or nude would likely be inapproriate, or that perverts would use it as a way to expose themselves to children. In an ideal world, we could live like tribes where the human body is normal, it's not overtly sexual. This is why we're so offended over the human body - it's constantly concealed, so the moment we get to see a female chest, it's suddenly sexual because it's normally tabboo to be seen. I wish I could be shirtless outside, I envy males who get to truly feel the wind, the earth on their backs and their chest. Female and male nipples look the same, I don't understand why it should be illegal for me to experience nature in my natural state.
Anyways, I highly dislike the "nudist" people because it is NOT about accepting the human body in its natural state. It's completely co-opted by pedophiles who want to expose themselves to childen or for children to expose themselves to others for sexual gratification. There are nudist resorts pedophile parents force their children to go to (as a child you have no personal autonomy and are completely a slave to your parents - trust me, I know this because I couldn't LEGALLY decide which parent I wanted to live with up until I was 18 years old. If your parent wants you to do something, a child in the US has no legal say over that, so if your parent wants to go to a nudist resort, you must go). A human body should simply be a human body, it's unfortunate that being unclothed immediately brings on sexualization. This is mostly an issue because clothes is the expected default. The more tabboo something is, the more naughty the thing is.
I am not a nudist. However, I do believe that at the very least, females should have the right to be topless in similar settings as males are allowed to. I don't think a woman is a slut if she's in her natural state, in her human body, and proceeds life as normal. How one acts portrays slutty behavior. Living your life in your natural human body should be a right without caviots. I feel detached from people who constantly see the human body as flawed (e.g. circumcision industry, body hair removal industry, clothing industry). These industries are harmful for the victims in them (infant boys, and modern day slaves in sweatshops), and the main motivating factor is money among all these industries.
-
 @ 6bae33c8:607272e8
2025-01-04 01:04:31
@ 6bae33c8:607272e8
2025-01-04 01:04:31I’ll make this one brief, email it in, so to speak. I’m 44-40-1 through 17 weeks and have nothing to gain except a more sightly record.
 Ravens -18 vs Browns — I wish DTR were playing, but Bailey Zappe will do. The Ravens need this game to lock up the third seed and a Round 1 home game. The Browns are playing out the string.
Ravens -18 vs Browns — I wish DTR were playing, but Bailey Zappe will do. The Ravens need this game to lock up the third seed and a Round 1 home game. The Browns are playing out the string.Bears +10 at Packers — The Packers aren’t playing for anything, so I’m not sure why this line is so large.
Panthers +8 at Falcons — The Falcons need this game, but it’s likely futile because the Bucs would have to lose to the Saints. The Panthers play most teams tough, and the Falcons aren’t that good.
Cowboys +5 vs Killer Redskins — The KRs don’t need this game, so why are they laying five? They could pull Jayden Daniels at halftime.
Giants +2.5 at Eagles — The Eagles are resting their starters, the Giants will try if last week’s win is any indication.
-
 @ 39cc53c9:27168656
2024-06-15 08:28:09
@ 39cc53c9:27168656
2024-06-15 08:28:09“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:

How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ bcea2b98:7ccef3c9
2025-01-03 22:31:38
@ bcea2b98:7ccef3c9
2025-01-03 22:31:38originally posted at https://stacker.news/items/835751
-
 @ 44dc1c2d:31c74f0b
2024-06-13 06:25:20
@ 44dc1c2d:31c74f0b
2024-06-13 06:25:20Chef's notes
I really like serving this with a saffron and cardamon rice. Add a few saffron threads and 3 or 4 crushed green cardamon pods while the rice is cooking to make it.
Details
- ⏲️ Prep time: ~15 min
- 🍳 Cook time: ~1.5 hours
- 🍽️ Servings: 6
Ingredients
- .5 cups neutral frying oil or ghee
- 2 onions halved and thinly sliced
- ~1 inch piece ginger root cut into thin batons
- 1 garlic clove crushed
- 2 fresh red chilies seeded and minced
- 1 inch piece fresh turmeric crushed or 1 tsp ground turmeric
- 1 lemongrass stalk lower part sliced thin and the top bruised
- 1.5 lbs steak cut into strips
- 14oz coconut milk
- 1 1/4 cups water
- 1 aubergine (eggplant) sliced and patted dry
- 1 tsp tamarind pulp, soaked in ~4 tbsp warm water
- salt and pepper to taste
- Garnish:
- Deep fried onions
- More fresh chilis
- Serve :
- Rice
Directions
- Heat half your oil in a wok or large pan. Fry onions, ginger and garlic tell fragrant. Add chilies, turmeric and the lower parts of the lemongrass stalk. Push the contents to the side, crank the heat and add the steak. Stirring tell the meat is browned a bit.
- Add the coconut milk, water and lemongrass top. Hit it with some salt and pepper. Cover and let simmer for about an hour and a half. You want the meat to be tender.
- Towards the end of the cook time, use the rest of the oil to fry the aubergines. Brown on both sides.
- Add the browned aubergines cook for another 15 minutes or so. Stir gently every so often. Strain the tamarind juice and add it to the curry. Taste and adjust seasoning.
- Garnish with more Chilies and serve with rice.
-
 @ 16d11430:61640947
2025-01-03 22:11:33
@ 16d11430:61640947
2025-01-03 22:11:33The fiat monetary system, built on debt and centralized control, has entrenched a framework that incentivizes exploitation, overconsumption, and systemic corruption. While it appears to provide economic stability, its long-term trajectory reveals existential risks for humanity and all life on Earth. Here, we explore how the fiat system manifests these risks and how Bitcoin adoption could offer a peaceful alternative to avert catastrophe.
The Fiat System’s Role in Accelerating Human Extinction
- Perpetuation of Endless Growth and Consumption
Fiat currencies, through inflationary policies, compel perpetual economic growth to sustain themselves. This forces nations and corporations to prioritize short-term profits over sustainable practices, leading to the overexploitation of natural resources. The result is environmental degradation, biodiversity loss, and an acceleration of climate change—key factors in the destabilization of life-supporting ecosystems.
- Centralized Control and Authoritarianism
The fiat system thrives on centralized control by governments and banks. This concentration of power erodes individual freedoms, enabling authoritarian regimes to suppress dissent, fund wars, and perpetuate inequality. Over time, the devaluation of currencies exacerbates social unrest, fueling conflict and suffering.
- Debt-Driven Inequality and Enslavement
At its core, fiat money is created through debt. This system locks individuals, businesses, and nations into cycles of borrowing and repayment, concentrating wealth and power in the hands of an elite minority. The growing wealth gap undermines democracy, destabilizes societies, and creates a system that serves the few while marginalizing the many.
- Technological and Biological Risks
The fiat system funds the unchecked development of technologies such as artificial intelligence, surveillance systems, and bioweapons. Without ethical oversight, these innovations pose existential risks, from the loss of privacy to the potential for catastrophic misuse.
- Psychological and Spiritual Corrosion
Fiat money’s detachment from tangible value fosters a culture of materialism and short-term thinking. It disconnects people from the intrinsic value of labor, time, and the natural world, leading to widespread dissatisfaction, mental health crises, and a loss of purpose.
How Bitcoin Can Save the Species
- Decentralization as a Foundation for Freedom
Bitcoin operates on a decentralized network, free from the control of governments and banks. This structure prevents authoritarian regimes from manipulating monetary systems to serve their agendas, enabling individuals to reclaim financial sovereignty.
- Fixed Supply and Deflationary Economics
Bitcoin’s fixed supply of 21 million coins counters the inflationary nature of fiat currencies. By incentivizing savings and long-term thinking, it encourages sustainable practices, reducing the pressure to exploit finite resources for immediate gain.
- Transparency and Accountability
The Bitcoin blockchain is an immutable ledger, fostering transparency in financial transactions. This technology undermines corruption, facilitates equitable resource allocation, and empowers communities to hold powerful entities accountable.
- A Catalyst for Ethical Technological Development
Bitcoin’s open-source ethos inspires decentralized innovation in fields like energy, communications, and governance. It encourages the development of systems that prioritize resilience, fairness, and sustainability over profit.
- Restoring Human Dignity and Purpose
Bitcoin realigns the concept of value with human labor, creativity, and time. By divorcing wealth from debt and centralized control, it fosters a culture of fairness, integrity, and respect for individual contributions, nurturing psychological and spiritual well-being.
A Peaceful Revolution: Undermining Fiat’s Evil
Bitcoin’s adoption is not a call for violent upheaval but a peaceful revolution. Its design enables individuals and communities to opt out of the fiat system voluntarily, without coercion or conflict. As more people embrace Bitcoin, the centralized power of fiat systems will diminish, gradually eroding their capacity to inflict harm.
By transitioning to a Bitcoin standard, humanity can address the root causes of its existential crises. The result is a future where economic systems align with ethical values, fostering cooperation, sustainability, and a renewed sense of purpose.
Conclusion: Choosing Survival Over Extinction
The fiat system, driven by greed and short-termism, has positioned humanity on the brink of self-destruction. Yet, Bitcoin offers a viable path to a more equitable, sustainable, and resilient future. It is not merely a financial technology but a philosophical shift—a reimagining of what it means to value life, labor, and the planet itself.
Adopting Bitcoin is not just about securing financial freedom; it is about safeguarding the very survival of our species and the ecosystems that sustain us. The choice before us is stark: continue down the fiat road toward extinction or embrace the decentralized, transparent, and ethical principles of Bitcoin to build a world worth living in.
Let this moment be a turning point, where humanity chooses not destruction, but redemption.
-
 @ c8ab3c20:4bb40a9d
2024-06-12 14:41:38
@ c8ab3c20:4bb40a9d
2024-06-12 14:41:38Introduction
Cet article fait écho à mon article sur les flux RSS, qui est la méthode à utiliser pour s'abonner à mon blog, mais qui permet bien plus. Ici, je vais vous présenter différents agrégateurs RSS, les logiciels, applications ou extensions qui vous permettent de regrouper vos différents flux et de les organiser comme bon vous semble.
Je me limite à des solutions open source car elles sont, à mon avis, suffisamment qualitatives pour être privilégiées à des offres propriétaires dans un large panel d'usage. Je vais essayer de couvrir un large éventail de plateformes afin que vous trouviez un agrégateur qui puisse répondre à vos besoins.
Mobile (Android, iOS et iPadOS)
Twine
Twine est un lecteur RSS (et Atom) très récent au design soigné. Disponible pour mobile, il est publié en open source sous licence Apache 2.0 sur le Play Store, l'App Store ou GitHub (Android uniquement). Il permet de détecter automatiquement si un site a un flux RSS et de l'importer sans avoir à chercher le lien du flux en question, mais uniquement avec l'URL du site. Malheureusement, il n'est pas disponible en français pour le moment, mais vous ne devriez pas avoir trop de mal à l'utiliser. Il ne possède pas non plus de thème clair. C'est une option déjà riche en fonctionnalités, comme la recherche, l'épinglage ou l'import/export via OPML.

Fluent Reader Lite
Fluent Reader est un agrégateur open source et multi-plateforme. La version Lite est destinée aux appareils mobiles iOS ou Android et est publiée sous licence BSD 3-Clause. Vous pouvez l'acheter à petit prix sur l'App Store ou le Play Store, ou gratuitement depuis TestFlight ou GitHub. L'application mobile n'est pas autant complète que la version pour ordinateur et nécessite un service RSS en cloud (des solutions plus bas).

Android uniquement
Feeder
Feeder est un lecteur de flux (RSS, Atom, JSONFeed) open source sous licence GPLv3, disponible uniquement sur Android depuis une décennie déjà. Encore mis à jour régulièrement à l'heure où j'écris ces lignes, vous pouvez vous procurer l'application sur le Play Store, F-Droid ou GitHub. Feeder possède un thème sombre ou clair selon vos préférences, il supporte la langue française ainsi que les notifications et les imports/exports via OPML. Le design suit les lignes de MaterialYou (MD3) de Google et fait donc moderne, épuré et cohérent avec un Android 12 ou plus récent. Il s'agit de ma solution principale actuelle.

ReadYou
ReadYou est un lecteur de flux RSS open source sous licence GPLv3, disponible uniquement sur Android depuis deux ans maintenant. L'application est disponible en français et sur F-Droid, GitHub ou Telegram. Son design est très épuré et aligné à MaterialYou (MD3). Un peu moins complet, c'est un super agrégateur plutôt minimaliste.

Thud
Thud est un lecteur RSS minimaliste open source sous licence AGPLv3, inspiré par Pulse News qui fut racheté par LinkedIn et ruiné (étonnant). Disponible sur Android via le Play Store, F-Droid et GitHub, mais avec la possibilité de compiler une version iOS. Il possède un thème sombre et clair selon vos préférences et les fonctionnalités de base que l'on attend d'un agrégateur RSS.

Apple : iOS,iPadOS et macOS uniquement
NetNewsWire
NetNewsWire est l'agrégateur (RSS, Atom, JSONFeed et RSS-in-JSON) de référence pour les appareils d'Apple depuis plusieurs années. C'est une application open source publiée sous licence MIT. Elle est écrite en Swift et est donc native aux appareils de la marque à la pomme et disponible sur l'App Store ou, pour la version macOS, sur leur site web. Elle est très complète et a toutes les fonctionnalités dont vous avez besoin.

Desktop
Fluent Reader
Fluent Reader est un agrégateur open source et multi-plateforme. Cette version est pour ordinateur (Windows, macOS ou GNU/Linux) mais possède un client mobile nommé Fluent Reader Lite présenté plus haut. Comme la version mobile, cette variante est publiée en open source sous licence BSD 3-Clause. Elle est complète et suit les règles de design du Fluent Design (d'où son nom) de Microsoft introduit avec Windows 11 et s'intègre donc très bien avec ce dernier. Vous pouvez la télécharger sur le Microsoft Store, le Mac App Store ou GitHub

News Flash (GNU/Linux uniquement)
News Flash est une application complète au design moderne (GNOME Circle) se voulant comme le successeur spirituel de FeedReader, mais attention, il ne s'agit pas d'un fork. Vous pouvez la télécharger depuis FlatHub. Les paquets Alpin, Arch, Nix ou Snap ne sont plus supportés et donc pas à jour !

Extension Firefox
Brief
Brief est une extension open source lecteur RSS (et Atom) pour Firefox, distribuée sous licence MPL 2.0. Assez simple et intuitive à utiliser, elle a toutes les fonctionnalités de base que vous attendez d'un agrégateur de flux. Vous pouvez la télécharger sur le catalogue Firefox Browser Add-ons de Mozilla.

Cloud
Certaines personnes apprécient avoir leurs flux qui se synchronisent entre plusieurs appareils, et pour cela, le plus efficace reste une solution en ligne. La majorité sont propriétaires et freemium, mais vous pouvez très souvent les utiliser avec des agrégateurs open source comme ceux cités plus haut. Ceux-ci sont open source :
NewsBlur
NewsBlur est la référence de gestionnaire de flux RSS open source en cloud, leur code est publié sous licence MIT. Le service existe depuis plus d'une décennie et est supporté par beaucoup de clients présentés plus haut. Ils ont leur propre client web, Android et iOS que vous pouvez aussi installer. Vous pouvez utiliser gratuitement NewsBlur jusqu'à 64 sites ; au-delà, un abonnement annuel est nécessaire.

Feedbin
Feedbin est une autre solution en cloud plus récente et avec une interface plus moderne, mais compatible avec moins de clients. Vous trouverez des agrégateurs compatibles sur leur site. Le service coûte 5 $ par mois avec 30 jours d'essai offert afin de vous forger votre avis. Mais étant open source et sous licence MIT, vous pouvez héberger vous-même Feedbin ; malheureusement, pour des raisons techniques, il est plutôt conseillé de ne pas le faire pour le moment. Prenez plutôt une des solutions présentées juste après.

Auto-hébergé (selfhosted)
FreshRSS
FreshRSS est la référence, étant rapide, léger et puissant (fonctionnalités très complètes). Il est open source depuis une décennie déjà sous licence AGPLv3 bref la solution a privilégier si vous souhaitez héberger ce service chez vous ou sur votre VPS !

Fusion
Fusion est un agrégateur léger sous licence MIT à héberger soit même. Il est complet et son interface web est super moderne, cependant c'est une solution très récente et donc avec un avenir incertain mais vous pourriez être tenté de l'essayer ou même d'y contribuer.

Conclusion
Il existe de nombreux agrégateurs ou lecteurs RSS open source ; je n'ai présenté que ceux que je trouvais suffisamment qualitatifs pour remplacer des solutions propriétaires. Mais je suis curieux de savoir lesquels vous utilisez et quels sont les fonctionnalités que vous utilisez le plus. Que ce soit des solutions propriétaires ou open source, l'utilisation d'un agrégateur de flux permet de mieux se recentrer sur les informations qui nous intéressent de façon personnalisée et d'éviter d'être submergé par des dizaines de canaux différents. N'oubliez pas d'ajouter le flux RSS de mon blog dans votre client !
-
 @ f3df9bc0:a95119eb
2025-01-03 21:41:14
@ f3df9bc0:a95119eb
2025-01-03 21:41:14MySql InnoDB Indexes for Developers
This article aims to be a high level reference for developers who just want to use Mysql InnoDB indexes effectively. Although you can read this from top to bottom, I'd encourage you to save time by skipping to sections that interest you using the below table of contents.
Contents
- Quick Reference (Start here for guidelines you can use right away, without needing the why)
- Index Structure
- Primary Index Structure & Paging
- Secondary Indexes
- Composite Indexes
- Index Navigation
- ref-type Queries
- range-type Queries
- Post-Index Computations
- Join Algorithms
- Nested Loop Join
- Hash Join
- Compound Cursor Iteration
# Quick Reference This is a quick list of the practical guidelines that you can use to make your applications more performant at the database layer. We'll dive into the _why_ each of these things are true, and give you mental models such that you can arrive at these guidelines yourself _without memorization_, at later sections of the article.
Index Structure
Indexes are constructed from a B+tree structure. Understanding this structure is key to gaining an intuitive reasoning for how queries will perform using different indexes. Both the
PRIMARYindex and secondary indexes have a similar tree structure, differing only in what data is stored on the leaves of the tree.Primary Index Structure & Paging
Looking at the structure of a
PRIMARYindex first, we see that the full row is stored in each leaf of the tree, and each leaf is ordered sequentially on the disk:
note: page size greatly reduced for illustration If possible, it is best to select the primary index for a table with data locality in mind, to reduce how many page loads need to take place to satisfy a query. For example, imagine a blogging application that almost always queries for posts on a specific blog:
SELECT * FROM posts WHERE blog_id=10. Ideally we'd like for this table to have all the posts whereblog_id = 10stored sequentially in the primary index. However, by using a standard primary index on[id]we see a structure where rows are stored in disk pages in the order they were created. The diagram below illistrates this (ID integer, colour coded by blog)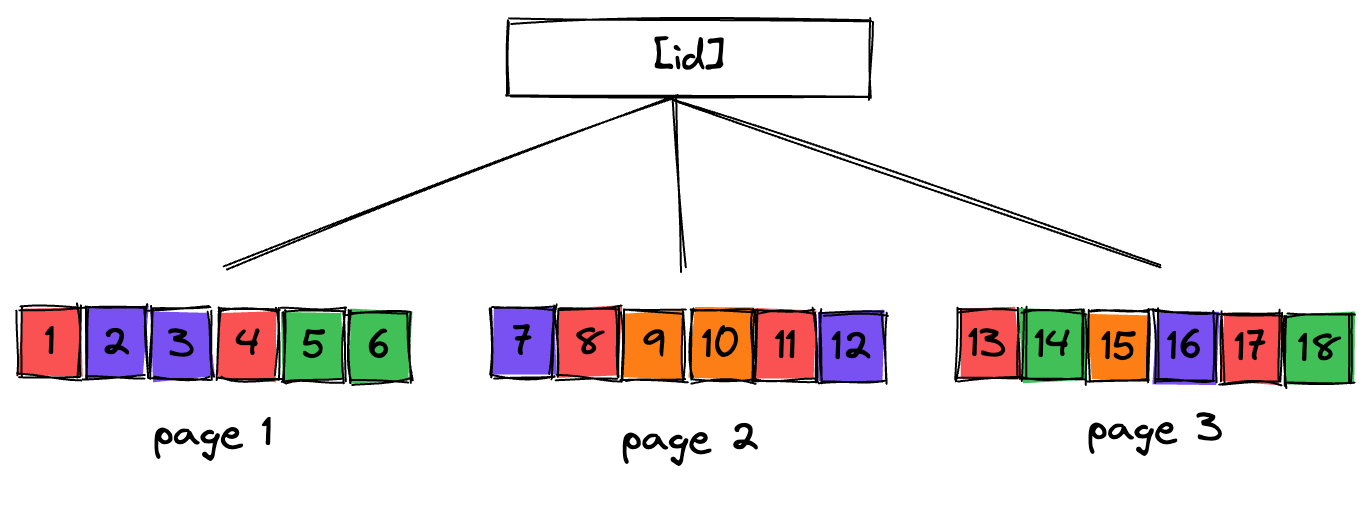
By insteading using a composite primary key, this table can be made much more efficient given its access pattern. In the below diagram I show the same data, but instead stored in a composite primary index of
[blog_id, id]. This means rows are first sorted byblog_id, and then byidfor each blog. When the data is stored in this manner, our query forSELECT * FROM posts WHERE blog_id=10is likely to load less pages from disk.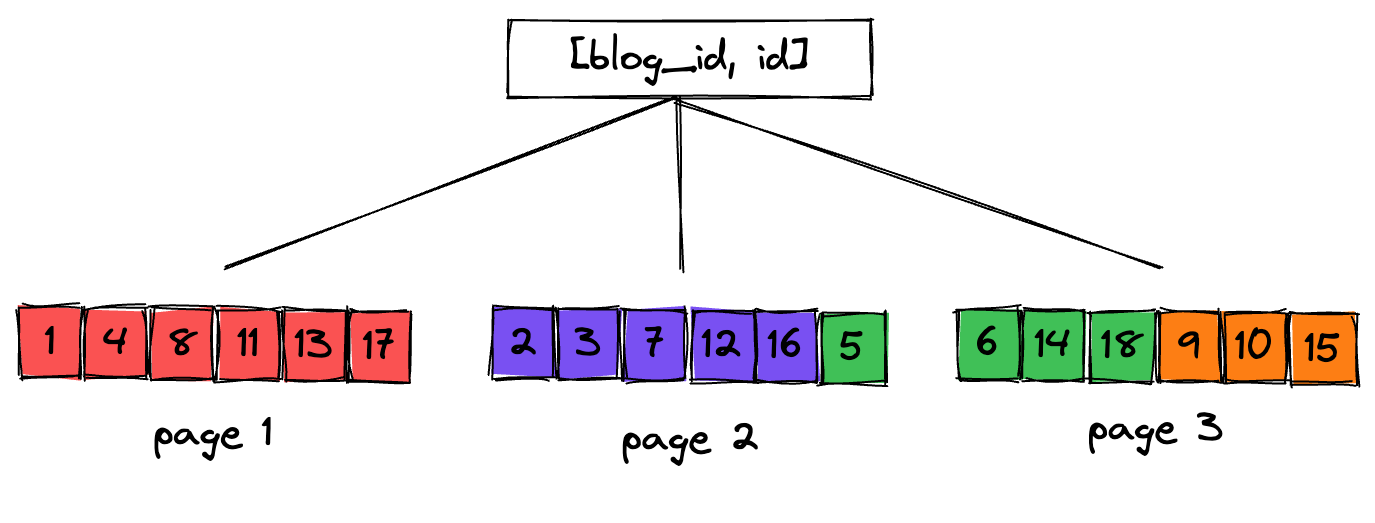
Secondary Index Structure
Secondary indexes have a similar structure to that of primary indexes. However, instead of storing the full row in the leaves of the tree, only the primary index value is stored:
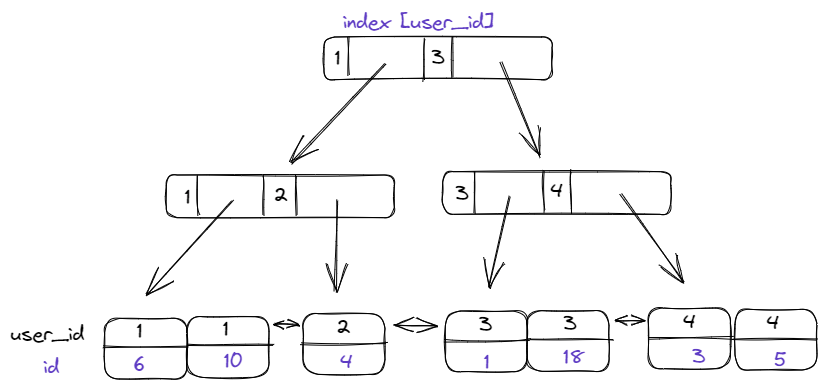
This structure means that if additional columns are required (eg a
SELECT *), then after traversing the secondary index, mysql must also traverse the primary index for each selected row to actually load the required data. By only selecting columns available in the secondary index, mysql can skip this extra lookup step.Composite Index Structure
When multiple columns are specified in a compound index, we get a structure composed of nested B+trees. This is where the ordering of columns within an index definition becomes relevant. The root of the tree is defined by the first column in the index definition, the second nested tree would be the second column in the index definition, and so on.
The below diagram is the structure of a composite index
[blog_id, created_at](with the impliedidcolumn on the end):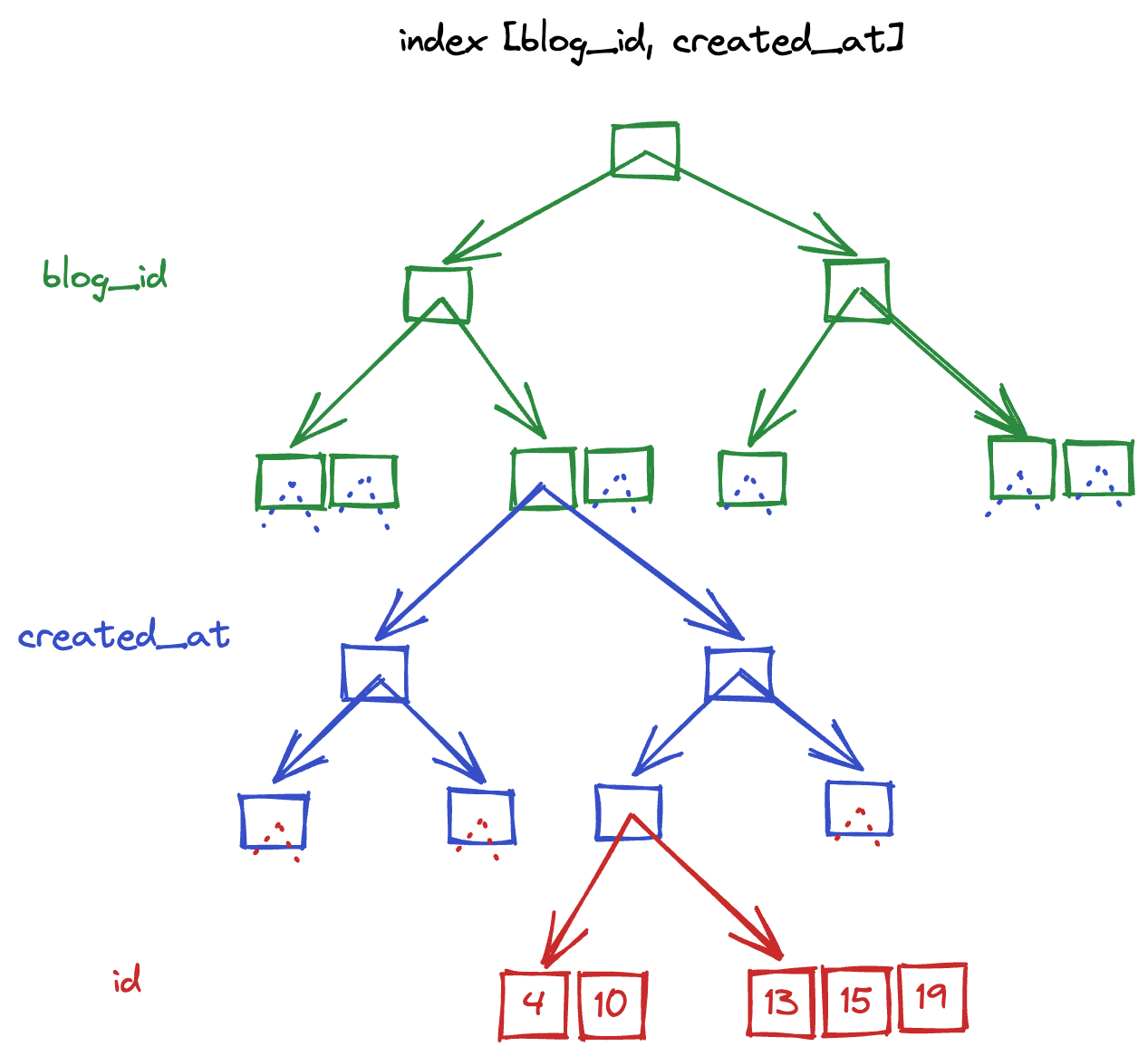
Index Navigation
We'll now look at how mysql navigates these indexes given various query structures, which should help give an intuitive understanding for why Mysql performance will vary.
ref-type queriesWith this tree-based model in place, we can see that to efficiently use an index like this we must navigate the tree in the order that the index is defined. If our query does not specify a value for all columns in an index, this is ok as long as the values we do provide are at the top of the tree.
I've illustrated below two examples of the "happy path" for navigating a
[blog_id, user_id]index. In the first, we have provided a filter on bothblog_idanduser_id, which allows for mysql to fully navigate the tree to the leaves. In the second, we only provide a filter onblog_id, but because this is the first column in the index mysql is still able to efficiently select all the rows that meet this criteria (it selects all leaves from the sub tree)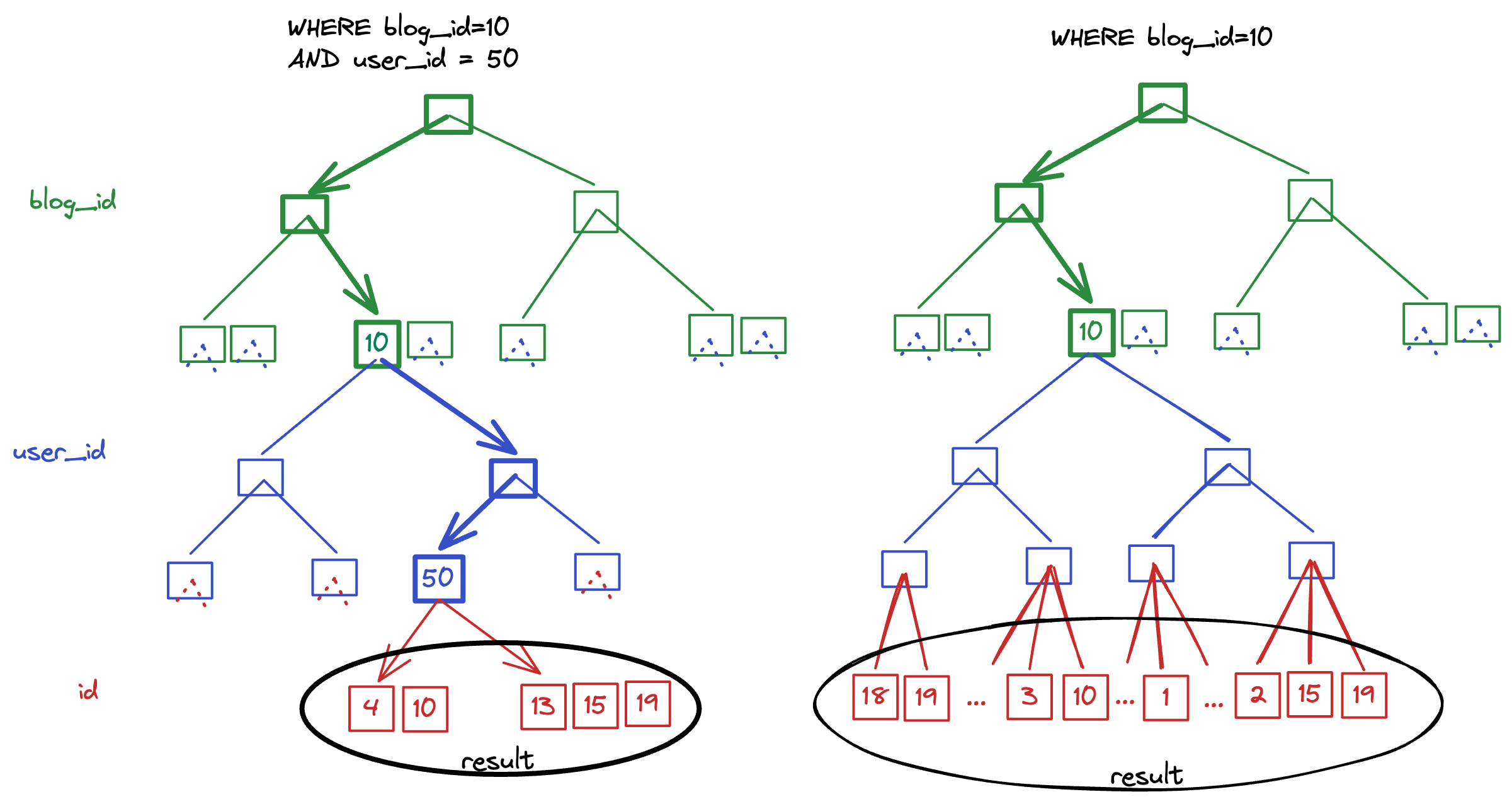 💡 Notice how the ordering of the rows appears to change depending on **how far mysql navigates the tree**. Rows in an index are always stored in the same ordering scheme as the index itself. That is to say that a `[blog_id, user_id]` index will naturally store rows in `blog_id, user_id, id` ordering. However, as we navigate further into the tree the ordering appears to "simplify". If we are selecting rows for a specific `blog=10 and user_id=50` then the rows appear to be ordered by `id`, because they all share the same values for both blog_id and user_id!
💡 Notice how the ordering of the rows appears to change depending on **how far mysql navigates the tree**. Rows in an index are always stored in the same ordering scheme as the index itself. That is to say that a `[blog_id, user_id]` index will naturally store rows in `blog_id, user_id, id` ordering. However, as we navigate further into the tree the ordering appears to "simplify". If we are selecting rows for a specific `blog=10 and user_id=50` then the rows appear to be ordered by `id`, because they all share the same values for both blog_id and user_id!range-type queriesThe range-type lookup happens when a query selects multiple values for an indexed column. There are many ways a query could end up in this scenario: -
WHERE updated_at > X-WHERE user_id != X-WHERE blog_id IN (1, 5, 34, 200)-WHERE user_id=10 OR user_id=50In such cases, mysql will need to navigate multiple branches of the index. Consider the below query where we search for all recently created posts for a particular blog:
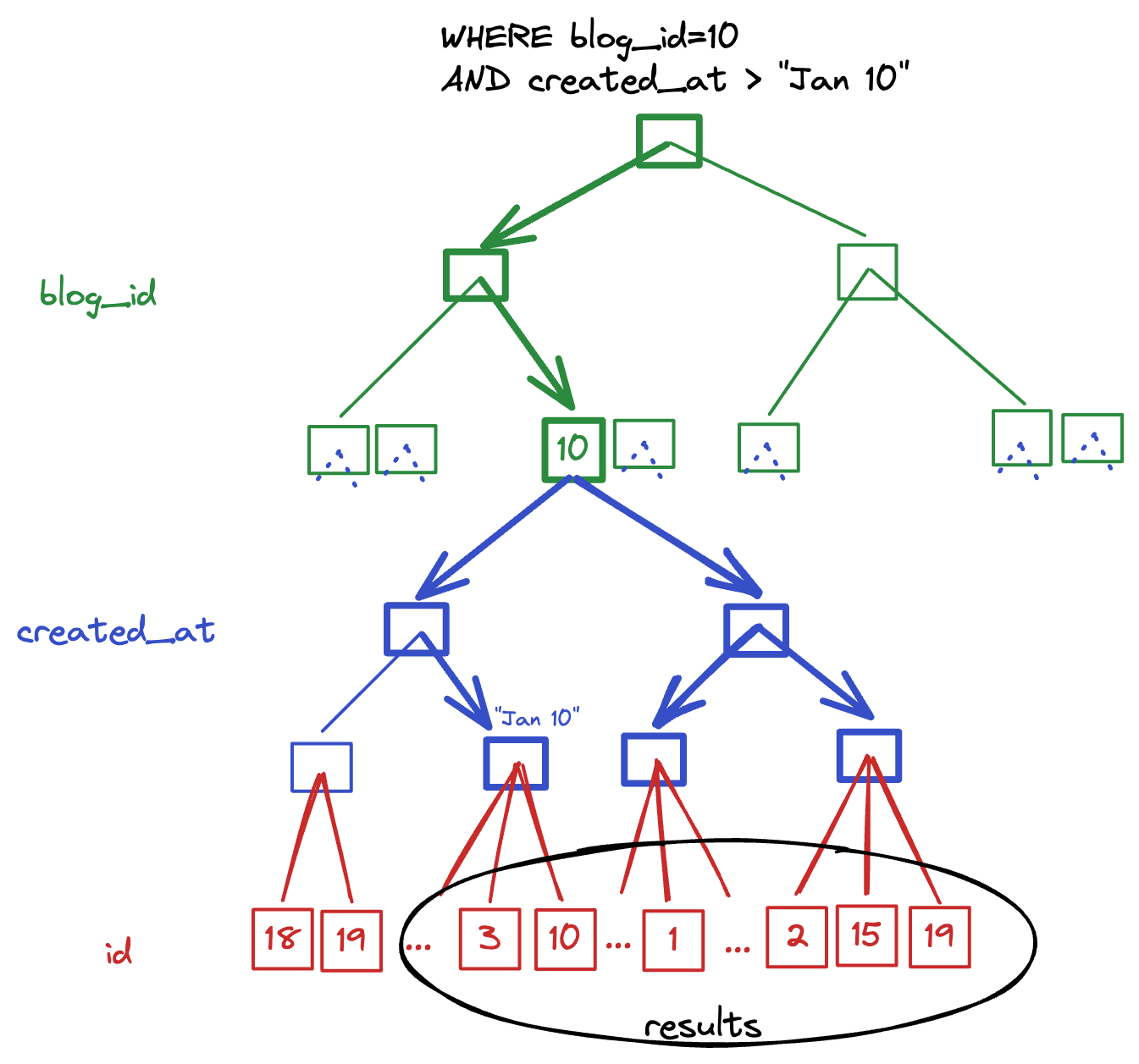
There are two things I'd like to point out about this pattern: 1. The ordering of the results is
created_at, id. Sorting byid(for example) is not possible without afilesortoperation. 2. There is no efficient way to navigate the deeper sections of the tree (ie theidportion of the index above) without iterating through all the selected branches ofcreated_at. That is, if we were to add an additional filter onid > 5for example, then there is no single tree to navigate and provide these values. Mysql would instead need to iterate through every sub-tree (one per value ofcreated_at) to complete this filtering operation (see diagram below)A common application pattern that can suffer performance issues due to both these points is ID-based pagination (ie if your pagination system needs to filter on
WHERE id > x ORDER BY id). See the section on compound cursor iteration for a potential solution.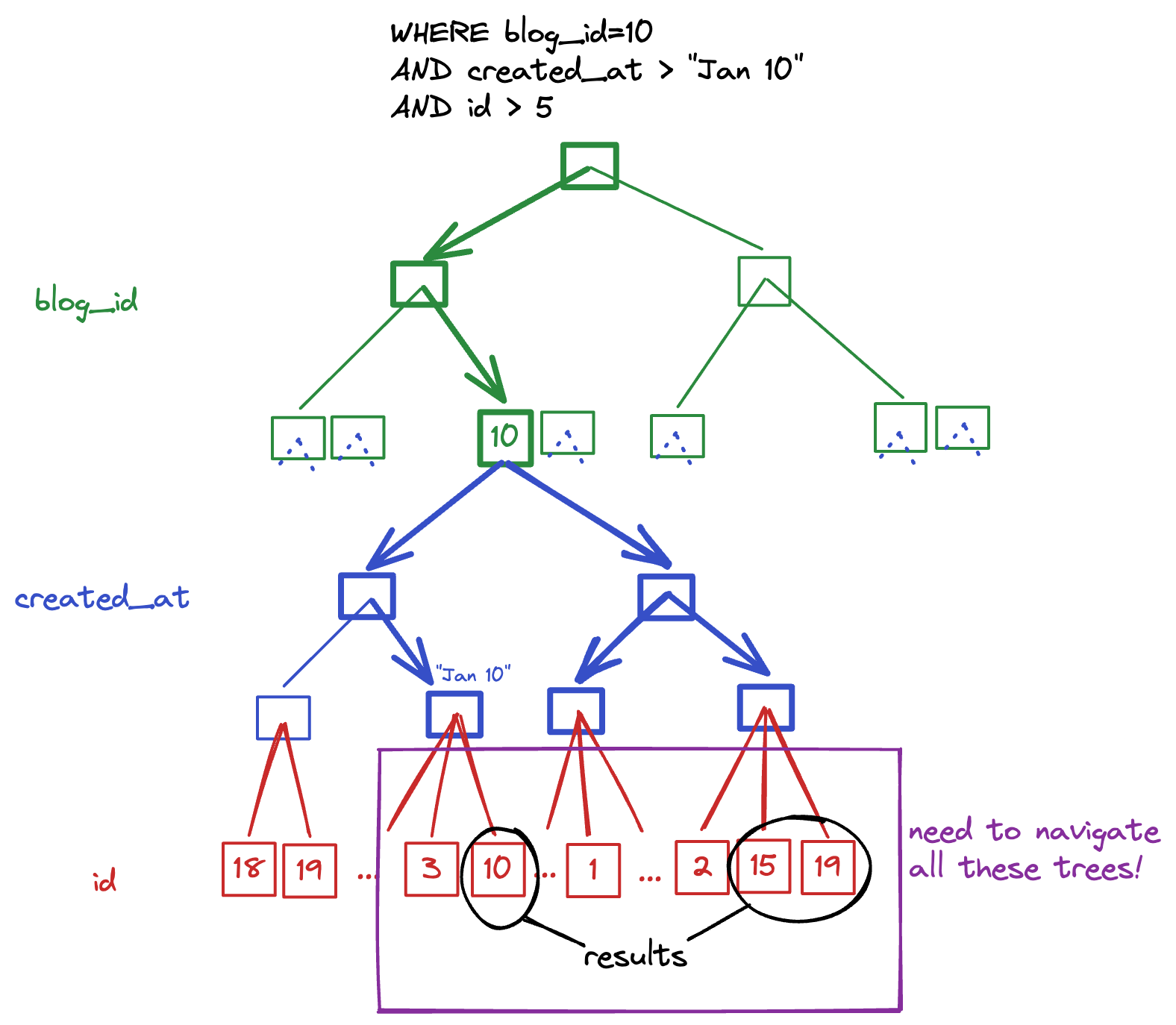
Post-Index Computations
Although Mysql will always start off by using an index if possible to reduce the amount of post-processing required, it goes without saying that not every query will be fully solved by an avilable index. There are a couple post-index computations that we should consider the relative performance of.
First, if the query is requesting an
ORDERwhich differs from how the index sorts its rows, a filesort will be required. This is an expensive operation (O(nlogn)) if the number of rows to be sorted is large. In addition, sorting requires Mysql to temporarily buffer the entire dataset (eg you can't stream a sorting operation). See ref-type queries for a reminder how indexes naturally sort rows.If the
WHEREclause of the query was not fully solved by the index, Mysql will also need to scan through the rows one after another to apply the remaining filtering. While this is faster than a filesort, it is also relatively slow for large data sets (O(n)). If the index reducing the dataset down to a reasonable size upfront, then this may not be a big deal.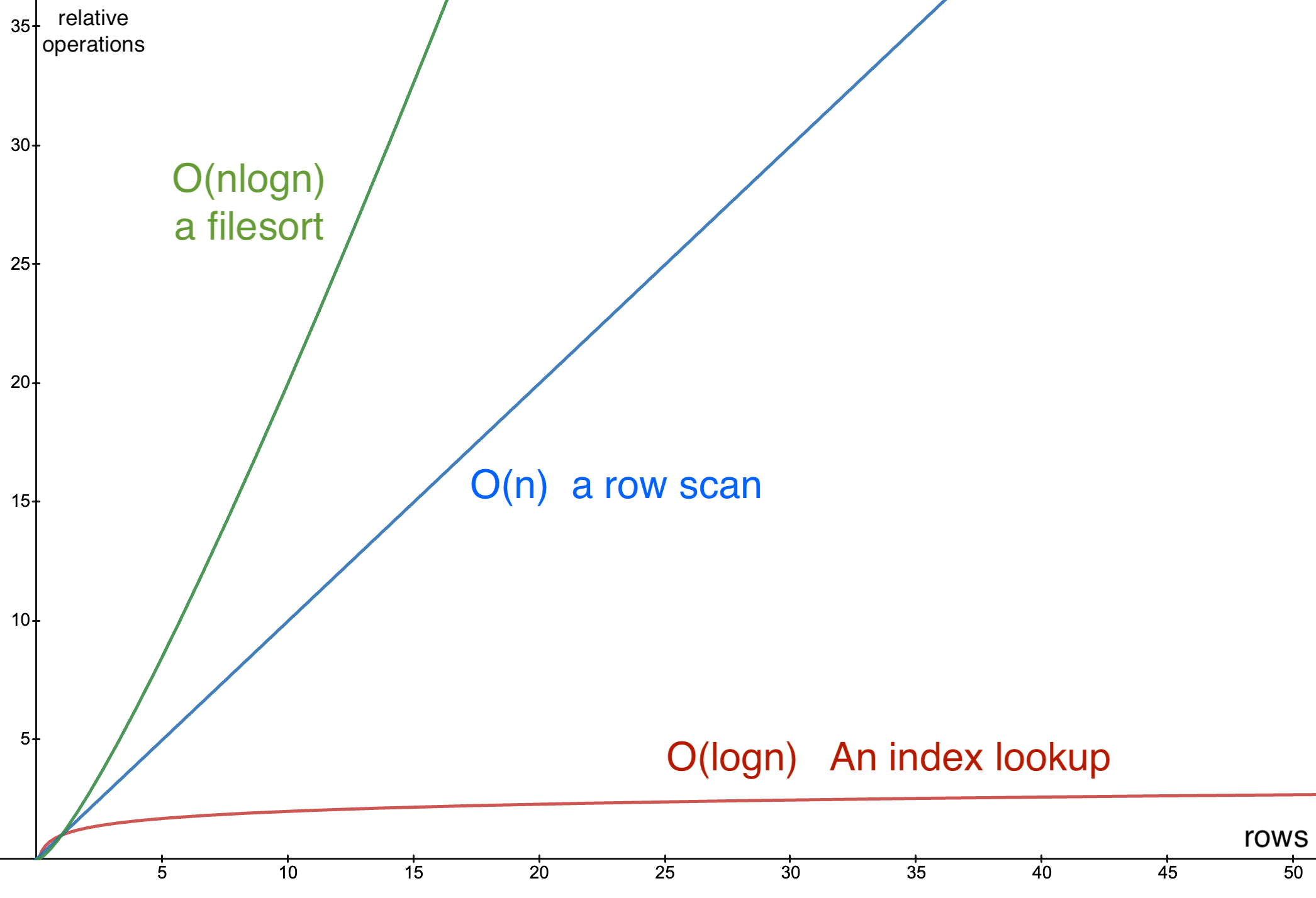
There is one exception here: if the query also specifies a
LIMIT x, Mysql need not scan the entire dataset. Mysql will "short circuit" the row scan as soon as it has enough rows to satisfy the query condition. The performance of this kind of pattern is dependent on the "hit ratio" of rows. If there are relatively few rows that satisfy the filter condition compared to rows that must be dropped, then Mysql will need to scan for a longer time compared to if almost all the rows are valid. In addition, you may find that the "density" of interesting rows is not constant throughout the range being scanned! If your application is paginating through a large data set, you may find that different pages have different query times, depending on how many rows need to be filtered out on each page.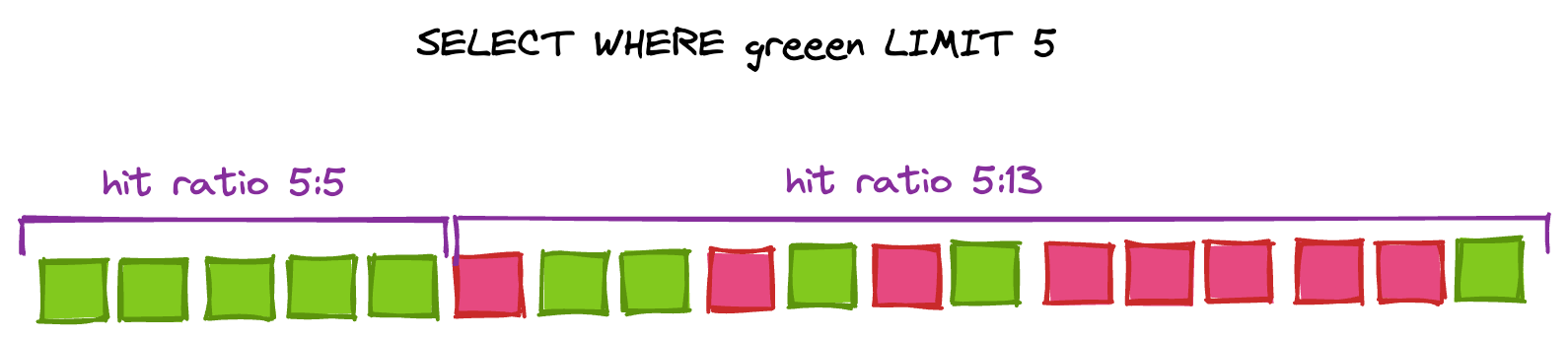
Join Algorithms
Nested-Loop Join
The primary algorithm used by Mysql to join tables is a couple variations on "nested-loop". This a very straightforward algorithm:
for each row in tableA: for each matching row in tableB: send to output steramBecause Mysql is often capable of streaming joins, when the join query includes a
LIMIT xthe full join may not have to be executed:- Mysql executes query in the outer table
- For the first row in the range, look-up matching rows in the inner table
- For each matching row, emit to output stream
- Stop execution if enough rows found, otherwise move to next row and goto 2
Note that similar to un-indexed row scans, this does not apply to all conditions (for example, if sorting is required the full dataset is required in memory).
Hash Join
The hash-join algorithm avoids the N+1 B-tree traversal by taking some time upfront (
O(n)) to build an in-memory hash table. The reason this strategy can give a performance improvement over nested-loop in some cases is because a hash table lookup has an average profile ofO(1)compared to B-tree traversal atO(logn). Given we may have to do this lookup many times (mtimes), the overall performance profile of hash-join isO(n + m), whereas nested-loop's profile isO(nlogm).The below plot shows the region (shaded blue) where the function
n+mhas a lower value thann*logm:
The tradeoff is of course that this (potentially large) hash table must fit into memory. For this reason one strategy to improve hash-join performance is to limit the size of this temporary table by
SELECT-ing only those columns which you really need (to reduce width), and pre-filtering as many rows as possible (to reduce height).The second thing to keep in mind for performance of hash-joins is that indexes on the join condition will not be used. Rather, the place to focus is on indexing any independent filters if possible. For example, consider the following query:
sql SELECT * FROM tableA t1 JOIN tableB t2 ON t1.shared_id = t2.shared_id WHERE t1.colA = "foo" AND t2.colB = "bar"The best indexes for this query given a hash-join would be on
t1.colAand a second index ont2.colB. Execution of this join would then look like:- Use the index on
colAto find all rows in t1 wherecolA = "foo". - For each row, build a hash table where the key is
t1.shared_idand the value is the row. - Use the index on
colBto find all rows in t2 wherecolB = "bar". - For each row, look up the matching t1 rows from the hash table by
t2.shared_id
Compound Cursor Iteration
In the range-type queries section I briefly introduced the problem of using an ID based cursor to paginate through a dataset queried via a range-type query. One potential solution to this problem is to use a compound cursor. To work, this cursor must be constructed from the column being filtered with the range. For example, lets consider the query
SELECT * FROM blog_posts WHERE blog_id=10 AND created_at>"2023-01-01". The natural index to use for this range query would be[blog_id, created_at].Because the range query filter is performed on the
created_atcolumn, I will propose a compound cursor ofcreated_at, id. Let's take a look at how the query structure changes. The first query of our iteration will look something like this:sql SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > "2023-01-01" ORDER BY created_at, id ASC LIMIT 100This will get the first "page" of 100 results. Notice that we are ordering by
created_at, id, which is the natural ordering of the index. This allows mysql to efficiently grab the first 100 rows it sees without scanning the full time range.
Now lets look at how we get the next "page" of results. The "cursor value" is defined as the
created_atandidvalues from the last row in the batch of 100 previously selected. We'll call these valuesxandyfor simplicity.ruby x = batch.last.created_at, y = batch.last.idThe structure of the query that loads the second page of results has this form:
sql SELECT * FROM blog_posts WHERE blog_id = 10 AND ( created_at = x AND id > y OR created_at > x ) ORDER BY created_at, id ASC LIMIT 100Notice in this query that we have an
ORclause, meaning mysql is going to navigate the index two times, once per "side" of the clause. Lets consider these as two seperate queries for the sake of a performance analysis.```sql -- Query A: the "left" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at = x AND id > y ORDER BY created_at, id ASC LIMIT 100
-- Query B: the "right" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > x ORDER BY created_at, id ASC LIMIT 100 ```
By analysing the OR clauses piece-wise like this, we can now see that each clause has only one range filter. Combining this with the fact that the
ORDER BYis the natural ordering of these indexes, we have solved both of the original problems! No more filesort, no more unsolvable double-range filters.
🟡 A note of warning: this pattern may only work as you expect for columns that have immutable values. Like any data structure iteration, if a value changes during your iteration your process may either process a row twice or not at all! For example, consider if instead of iterating on
created_at, idwe were iterating onupdated_at, id. If a row is updated (and thereforeupdated_atincreases) while a process is already iterating through the dataset, we may see that updated row twice: once with its lowerupdated_atvalue, and again with the higher value. -
 @ 39cc53c9:27168656
2024-06-10 14:28:46
@ 39cc53c9:27168656
2024-06-10 14:28:46kycnot.me features a somewhat hidden tool that some users may not be aware of. Every month, an automated job crawls every listed service's Terms of Service (ToS) and FAQ pages and conducts an AI-driven analysis, generating a comprehensive overview that highlights key points related to KYC and user privacy.
Here's an example: Changenow's Tos Review

Why?
ToS pages typically contain a lot of complicated text. Since the first versions of kycnot.me, I have tried to provide users a comprehensive overview of what can be found in such documents. This automated method keeps the information up-to-date every month, which was one of the main challenges with manual updates.
A significant part of the time I invest in investigating a service for kycnot.me involves reading the ToS and looking for any clauses that might indicate aggressive KYC practices or privacy concerns. For the past four years, I performed this task manually. However, with advancements in language models, this process can now be somewhat automated. I still manually review the ToS for a quick check and regularly verify the AI’s findings. However, over the past three months, this automated method has proven to be quite reliable.
Having a quick ToS overview section allows users to avoid reading the entire ToS page. Instead, you can quickly read the important points that are grouped, summarized, and referenced, making it easier and faster to understand the key information.
Limitations
This method has a key limitation: JS-generated pages. For this reason, I was using Playwright in my crawler implementation. I plan to make a release addressing this issue in the future. There are also sites that don't have ToS/FAQ pages, but these sites already include a warning in that section.
Another issue is false positives. Although not very common, sometimes the AI might incorrectly interpret something harmless as harmful. Such errors become apparent upon reading; it's clear when something marked as bad should not be categorized as such. I manually review these cases regularly, checking for anything that seems off and then removing any inaccuracies.
Overall, the automation provides great results.
How?
There have been several iterations of this tool. Initially, I started with GPT-3.5, but the results were not good in any way. It made up many things, and important thigs were lost on large ToS pages. I then switched to GPT-4 Turbo, but it was expensive. Eventually, I settled on Claude 3 Sonnet, which provides a quality compromise between GPT-3.5 and GPT-4 Turbo at a more reasonable price, while allowing a generous 200K token context window.
I designed a prompt, which is open source^1, that has been tweaked many times and will surely be adjusted further in the future.
For the ToS scraping part, I initially wrote a scraper API using Playwright^2, but I replaced it with Jina AI Reader^3, which works quite well and is designed for this task.
Non-conflictive ToS
All services have a dropdown in the ToS section called "Non-conflictive ToS Reviews." These are the reviews that the AI flagged as not needing a user warning. I still provide these because I think they may be interesting to read.
Feedback and contributing
You can give me feedback on this tool, or share any inaccuraties by either opening an issue on Codeberg^4 or by contacting me ^5.
You can contribute with pull requests, which are always welcome, or you can support this project with any of the listed ways.
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 4d41a7cb:7d3633cc
2025-01-03 20:52:22
@ 4d41a7cb:7d3633cc
2025-01-03 20:52:22Today is Bitcoin genesis block day, literally Bitcoin’s birthday number 16th. The purpose of this article is to deep dive into Bitcoin's beginnings, what it was meant to be, what its creator's incentives were, why the collaborators were interested in contributing to its success, and what Bitcoin is achieving.
Bitcoin exists to solve a problem.
The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.
Satoshi Nakamoto, February 11, 2009
In this post, Satoshi reveals the main problem: central banking, how this institution has abused the trust we have put in them. Bitcoin is an alternative to a “broken” or corrupt monetary system that it’s been running and stealing from people for centuries, creating credit bubbles with their debt-based fractional reserve banking system
Ponzi nature of banking system
For those who don’t understand this system and its corrupt and inviable nature, think about it as a rigged musical chairs game.
When the music (trust in the banking system and its currency) is on, everyone is happy playing the economic game. Economic activity is soaring; we see new businesses, new products, cheap credit, high lending, asset prices inflate, and people consuming more (thus pushing the economic numbers higher). Everything seems to be okay. But then something happens.
Under this monetary game, deposits are chairs and depositors are players; as the game goes on, there are always more players than chairs or depositors than deposits because banks “lend” currency that they don’t have. When the music (trust in the bank) is stopped, the game is over, and many people lose their chairs (their deposit), creating deflationary recessions and economic crises.
When this happens, everything starts trending the exact opposite way. The economic activity starts slowing down, debt problems arise, bankruptcies occur, people lose their jobs and consume less, asset prices deflate, until the central bank intervenes and the cycle starts again.
This is officially known as the “economic cycle,” and it's sold to us as a natural phenomenon. But the truth is this is a pure central bank–artificially created cycle by monetary manipulation, as we can learn from the Austrian school of economics.
I call the central bankers the market wizards because they hold the lever to manipulate the economic game. They are the money masters, the financial alchemists, the kings of the economic and financial game of commerce where all economic agents operate under.
Bitcoin is a revolution against the central bank monarch, but Satoshi was not shouting about this to the four winds. He didn’t want to get attention before Bitcoin was strong enough, because it would have implied a great risk to its success. Central banks are the most powerful institutions on earth; they literally have the power to create currency in unlimited amounts and buy anything they need to maintain their monopoly.
If we need a more clear confirmation of this, we can look into the encrypted message that Satoshi left in the genesis block. To understand the genesis block, imagine a bookkeeping ledger that adds new pages (blocks) daily and contains a record of all bitcoin transactions ever made. The very first page of this book is called the genesis block.
Chancellor on brink of second bailout for banks
Satoshi Nakamoto 03 January 2009
Here’s the newspaper cover he was making reference to.
 In allusion to the bank bailouts that were taking place at the time, Satoshi included this intriguing line in the genesis block when he created Bitcoin during the Great Global Financial Crisis. In addition to providing the remedy, those who caused the issue (and profit from it) were making unprecedented profits. \
\
This game is about privatizing profits and socializing losses. This is the opposite of free markets and capitalism. It's clear that Satoshi Nakamoto, whomever he was, detested the established financial system. Since the Bank of England, which was the subject of this article, was established in 1694, we may trace the debt based fractional reserve banking system history back at least 331 years. \
\
This allusion to traditional banking's shortcomings was a declaration of what Bitcoin was trying to combat: fractional reserve banking and its consequences, which include debt, taxation, and inflation.
In allusion to the bank bailouts that were taking place at the time, Satoshi included this intriguing line in the genesis block when he created Bitcoin during the Great Global Financial Crisis. In addition to providing the remedy, those who caused the issue (and profit from it) were making unprecedented profits. \
\
This game is about privatizing profits and socializing losses. This is the opposite of free markets and capitalism. It's clear that Satoshi Nakamoto, whomever he was, detested the established financial system. Since the Bank of England, which was the subject of this article, was established in 1694, we may trace the debt based fractional reserve banking system history back at least 331 years. \
\
This allusion to traditional banking's shortcomings was a declaration of what Bitcoin was trying to combat: fractional reserve banking and its consequences, which include debt, taxation, and inflation.\ \ The bookkeepers \ \ In essence, banking and money management are bookkeeping, keeping track of who owns what and who owes what. Due to its revolutionary impact on accounting, Bitcoin has been dubbed "triple entry bookkeeping" by some. \ \ These days, banks are in charge of bookkeeping; they basically have the authority to make changes to the books and add new entries, or "print money." Inflation is basically a robber of time, energy, and wealth from everyone using that currency denomination, and banks are the ones who create it. Additionally, they have the ability to cause economic crises and market crashes for their own financial gain, making them deflation inductors. \ \ The incapacity of gold (real money) to meet the demands of a growing global economy gave banks this authority. They essentially became gold safe-keepers and gold IOU bookkeepers' ledgers because people trusted these organizations to provide scalability and lower the cost and risk of gold transactions. \ \ The purpose of banking was to enable credit and payments. Governments and banks did not create money. The free market determined the value of gold and silver, and people only trusted banknotes that were backed by gold. \ \ “Gold is money, everything else is credit" JP Morgan, 1912. \ \ Since banks began growing, they have sought to increase their size even more. When they discovered that the metal money system was restricting their ability to increase credit and bank profits, they literally plotted to seize control of the money market and overthrow governments by demonetizing these metals, effectively eliminating the demand for money in general and substituting it with debt and credit instruments. Essentially promissory notes issued by banks based on debt. \ \ "The borrower is a slave to the lender, and the wealthy dominate the poor”. Proverbs 22:7\ \ Human history is a chronicle of the literal plot by banks to enslave humanity, which resulted in hundreds of wars, thousands of assassinations, and the loss of millions of innocent lives in order to fulfill the banksters' objective of creating a global fractional reserve credit system. The currency that they decided to control? The term "U.S dollars" is frequently and incorrectly used to refer to Federal Reserve Notes. \ \ Slavery is essentially personified in this system. Slavery, in my opinion, is working for a currency that someone else can print without any effort or labor. This is the underlying cause of legal inequality. Theoretically, we live in a democracy and capitalist society where everyone is treated equally, but income taxes and central banking are vital components of the communist manifiesto. \ \ Where do we draw the boundary between a free human being and a slave citizen, given that this system directly violates private property rights? You are 100% slave when you pay 100% taxes, and 40% slave when you pay 40% taxes. It is being violently imposed upon you if it is not a voluntary business deal. Violence or the threat of losing your freedom are used to compel people to pay taxes. \ \ Natural law, often known as moral law, states that every person has the right to keep all of the fruits of their labor. However, this fraudulent financial system is robbing everyone of their means of trade, whether they are called coins, currencies, deposits, checks, etc. Furthermore, ceasing to feed a parasite is the only way to eradicate it. \ \ A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution.
Satoshi Nakamoto, October 31, 2008\ \ \ \ What backs fiat currencies?\ \ The worst aspect of this system is that it views people as collateral cattle for the currency's purchasing power. In essence, "government currencies" are credits of their corresponding debts, or government bonds, which are effectively secured by the government's “authority” to impose taxes on its populace. In essence, the government's power to compel its people to give them X percent of their income without providing them with equal recompense.
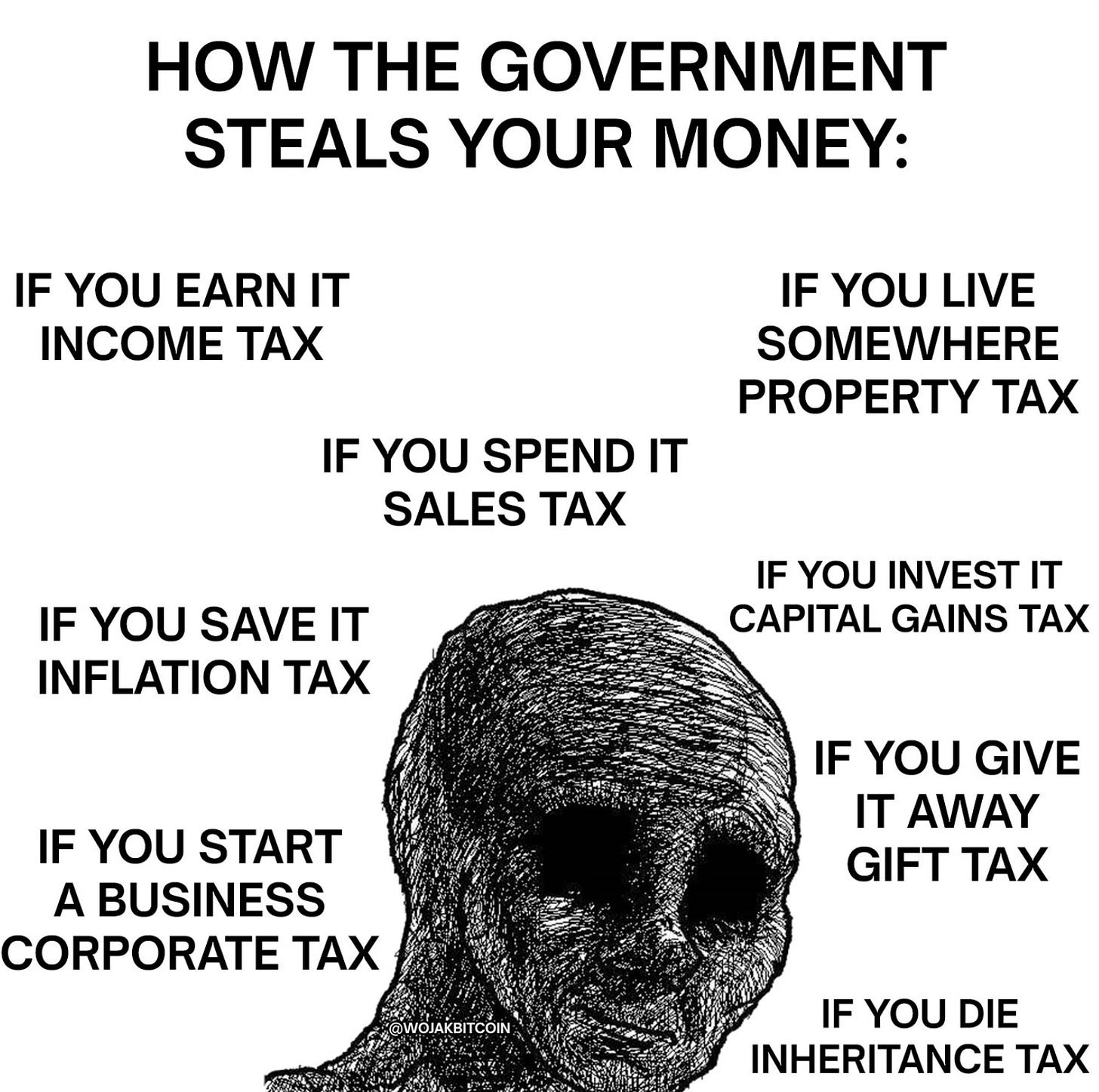 In essence, citizens' wealth is "baking" the government's debts. Since the currency cannot be exchanged for wealth at a particular rate, it is inaccurate to state that it is backed, thus I said "baking." However, if we must identify a valuable component of the currency, it is as follows: wealth and labor (i.e., human time and energy).
In essence, citizens' wealth is "baking" the government's debts. Since the currency cannot be exchanged for wealth at a particular rate, it is inaccurate to state that it is backed, thus I said "baking." However, if we must identify a valuable component of the currency, it is as follows: wealth and labor (i.e., human time and energy).\ And what makes up this wealth? Among other things, land, homes, resources, businesses, and human time. They have demand for trade and exchanges because they make up half of every transaction. However, what do people trade more for currency? Energy and time. \ \ Those who can produce currency out of thin air with little effort (simply adding numbers to the bank ledger) can effectively steal from everyone else who has to labor and invest time and energy (real wealth), as most people exchange their time and energy for currency. Clearly, this is the root cause of inequality. \ \ Not only is this utterly immoral and unfair, but it gets worse. The worst aspect is not that they want to charge interest and can easily generate currency, but rather that they insist that WE repay them! \ \ What am I saying? Every currency unit's counterpart in government bonds is a public debt that generates compound interest on a continuous basis. There is a dollar due plus interest for every dollar that exists. In essence, this debt is a claim on the nation's wealth, which includes the labor (time and energy) and wealth of its citizens. \ \ And to whom is this debt owed? The banks. Therefore, if we apply common logic, it is easy to see that just as borrowers are slaves to lenders, governments and "we the people" are slaves to banks. \ \ However, what precisely do we owe? What kind of material have they given our governments? Is it wealth of any sort, whether it land, gold, or resources? No, it's not. is essentially a promissory note issued by a private bank, a document that serves as a means of exchange and may be produced in an infinite quantity. A counterfeit check.\ \ Global slavery to the banks is the price we pay for a scalable medium of exchange! \ \ And now we have a great substitute! \ \ To sum up, we spend our lives, precious time, energy, stress, suffering, and effort to obtain these currencies and pay our taxes, while another group sits there making up new reasons to add currency the ledger —also known as "printing digital money"—that we must repay plus interest! It's crazy. \ \ The worst aspect is that because the debt exceeds the amount of money in circulation due to compound interest, which keeps accruing and increasing the loan's size, it is mathematically impossible to pay back.\ \ It is equivalent to burning the currency because we pay taxes to cover the interest on an ever-increasing debt that we are unable to pay back. A black hole for taxpayer funds, debt-based currencies are essentially human slavery that is supported by banks and maintained by governments. \ \ Why isn't everyone voicing their disapproval and exposing this? The answer is brainwashing and a lack of knowledge. Much of this has been concealed or esoteric, and a major contributing factor to this blind spot is the misinformation we receive regarding the operation of this system. In order to play the game the way they want us to and avoid the game ending anytime soon, we are given a children's interpretation of human history and reality. \ \ \ Libertarianism\ \ Bitcoin's libertarian nature cannot be disregarded; even Satoshi acknowledged this when he stated:\ \ It’s very attractive to the libertarian viewpoint if we can explain it properly.\ I’m better with code than with words though.
Satoshi Nakamoto, November 14, 2008\ \ Libertarianism is a political philosophy that holds freedom and liberty as primary values. Many libertarians conceive of freedom in accord with the Non-Aggression Principle, according to which each individual has the right to live as they choose, so long as it does not involve violating the rights of others by initiating force or fraud against them.
Libertarians advocate for the expansion of individual autonomy and political self-determination, emphasizing the principles of equality before the law and the protection of civil rights, including the rights to freedom of association, freedom of speech, freedom of thought and freedom of choice. They generally support individual liberty and oppose authority, state power, warfare, militarism and nationalism, but some libertarians diverge on the scope and nature of their opposition to existing economic and political systems. 1\ \ Here are several arguments in favor of Bitcoin's libertarian nature. \ \ Non-Aggression Principle: Unlike taxes and fiat currencies, which are supported by state aggression, Bitcoin is supported by energy, math, and processing power. The monopoly of violence “belongs” to governments, and banks use this authority to compel everyone to follow their rules (I'm talking about business). \ \ Personal independence: Bitcoin doesn't require confidence and doesn't have counterparty risk. With bitcoin, the person has complete control over his finances and doesn't require "permission" from a third party to earn, save, or spend it. Bitcoin is referred to be "freedom money" for this reason. \ \ Equality before the law: Unlike the actual banking system, where a group can create money out of thin air with little effort and can alter the rules to suit their interests, the bitcoin protocol ensures that everyone is playing by the same rules and that there is no possibility of cheating or inflating the supply of bitcoin. Equality exists under the Bitcoin protocol. \ \ Indeed there is nobody to act as central bank or federal reserve to adjust the money supply as the population of users grows.\ Satoshi Nakamoto, Febrero 18, 2009\ \ Freedom of speech: To uphold justice and the truth in an era of widespread censorship, freedom of speech is an essential human right. The fact that Bitcoin is information also fits into this category; money is a means of conveying value, but this time in an unstoppable manner that is impervious to censorship. \ \ Freedom of thought: Using bitcoin does not require you to subscribe to any particular philosophy or set of beliefs, including libertarianism or anarchism. Bitcoin is unbiased and doesn't care. \ \ Freedom of choice: Unlike fiat currencies, where you frequently have no other choice, no one will compel you to use bitcoin. \ \ Libertarians reject the current political and economic structures because they are blatantly immoral, criminal, and illegitimate. It is "shaped" by indoctrinated mob rule democracies, supported by violence, and based on lies.
 Bitcoin's ascent \
\
Bitcoin wasn't created overnight; rather, it was the result of decades' worth of research, development, and technology. Above all else, however, bitcoin represented a breakthrough—a new method of accomplishing tasks that had previously been impossible. \
\
A lot of people automatically dismiss e-currency as a lost cause because of all the companies that failed since the 1990's. I hope it's obvious it was only the centrally controlled nature of those systems that doomed them. I think this is the first time we're trying a decentralized, non-trust-based system.
Bitcoin's ascent \
\
Bitcoin wasn't created overnight; rather, it was the result of decades' worth of research, development, and technology. Above all else, however, bitcoin represented a breakthrough—a new method of accomplishing tasks that had previously been impossible. \
\
A lot of people automatically dismiss e-currency as a lost cause because of all the companies that failed since the 1990's. I hope it's obvious it was only the centrally controlled nature of those systems that doomed them. I think this is the first time we're trying a decentralized, non-trust-based system.Satoshi Nakamoto, Febrero 15, 2009\ \ Due to their centralization and unique points of failure, all of the numerous attempts to implement alternative e-currencies failed. The distributed nature of the bitcoin network makes it more robust and challenging to attack. \ \ The secret to developing a decentralized unchangeable ledger was Satoshi's solution to a problem that had been thought to be intractable since the 1970s. Following years of failure and lessons learned, Satoshi established a finite amount of money that is governed by processing power and energy.\ \ The proof-of-work chain is a solution to the Byzantine Generals Problem.\ Satoshi Nakamoto, Febrero 15, 2009
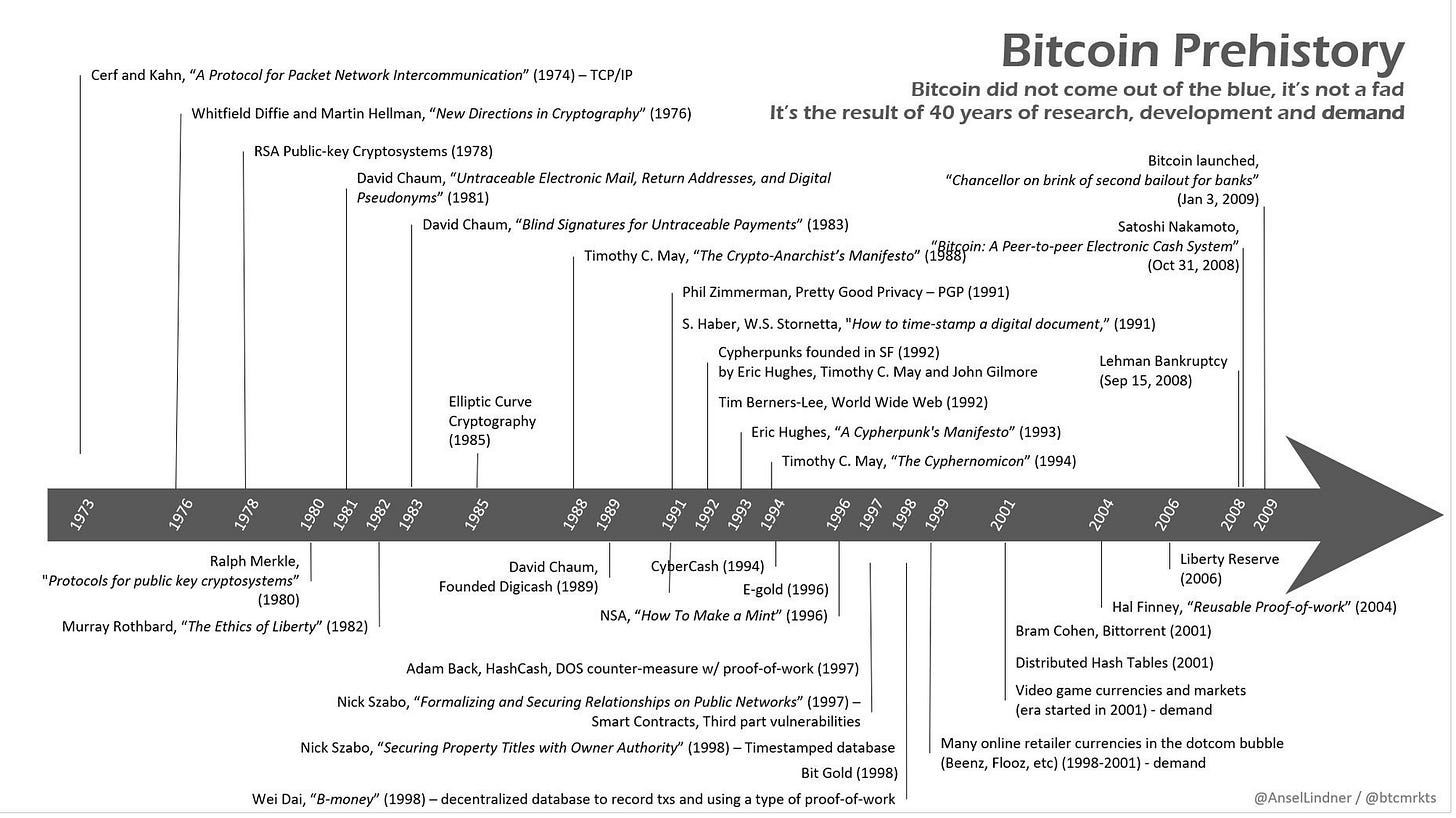 The return of money \
\
Bitcoin has also had a significant impact on the monetary front, particularly on the system's capacity to function as money and not simply a currency. It has been shown to be the best store of value (SOV) in addition to being an excellent medium of exchange (MOE).
The return of money \
\
Bitcoin has also had a significant impact on the monetary front, particularly on the system's capacity to function as money and not simply a currency. It has been shown to be the best store of value (SOV) in addition to being an excellent medium of exchange (MOE).Since currencies replaced money during the last century, we have lost track of what money is. And in order to protect our wealth, we need to be aware of the important distinctions between these technologies. \ \ A currency must be recognized, divisible, fungible, portable, and widely accepted in order to function as a medium of exchange. \ \ All of those qualities are present in money, but it also has the capacity to hold value over time, and it must be scarce in order to function as a store of value. A currency, in contrast to money, is susceptible to inflation due to its ease of replication. This is the cause of the constant price increases. \ \ The money supply needs to be scarce in order to preserve its purchasing power over time (i.e., to be immune to inflation). For thousands of years, gold and silver have been the preferred forms of money. \ \ At first, paper currency was only used to facilitate transitions by serving as a convenient alternative (derivative) to precious metals. Since goldsmiths and subsequent bankers used fractional reserve banking to lend more money (i.e., print more paper currency) than they actually had in storage, paper currencies—which are easily reproducible—have always been vulnerable to inflation. This resulted in the recurring "bank run" crises that are documented throughout history.\ \ But before bitcoin, we didn't have any money since 1933 because banks had taken it and devalued it. Real state, stocks, bonds, and other choices had been selected as alternatives due to the absence of money (a store of value). People buy real estate, stocks, and bonds to protect their wealth because fiat currencies are continually being inlfated, not because they love them. \ \ An estimated 900 trillion dollars' worth of wealth is held in financial and tangible assets worldwide. \ \ In real state, 330 trillions (36.6%)\ \ Bonds worth 300 billions (33.3%)\ \ Currency totaling 120 trillions (13.3%)\ \ Equity of 115 trillions (12,7%)\ \ Art worth 18 billions (2%)\ \ Gold worth 16 trillions (1,77%)\ \ Automobiles and collectibles worth 6 trillions (0,66%)\ \ Bitcoin worth two trillions (0,22%)\ \ Bitcoin only makes up about 0.22% of the world's total wealth. The greatest money ever created, property that you can actually own, with a sovereign protocol, no counterparty risk, a limited supply (better than scarce), and no need for banks or governments. Freedom money is unaffected by debt, taxes, or inflation. \ \ A bitcoin market cap of x10 ($1,000,000) would represent 2,22% of the world's wealth, and a market cap of x100 ($10,000,000) would represent 22,22%. \ \ The denominator, the dollar, is always losing value since it is created infinitely by continuously increasing the debt supply, and wealth is not fixed—rather, it is eternally increasing. According to CBNC the U.S. national debt is rising by $1 trillion about every 100 days.
Bitcoin is energy \ \ Bankers and significant international leaders are aware that energy is the foundation of all human activity. They are aware that they must control the energy sources, including their supply, distribution, and price, in order to establish a monopoly over every industry and a system of slave labor. They even clarified in several released documents that this is the only way to engineer the global economy.
:Silent Weapons for Quiet Wars explains:
In order to achieve such sovereignty, we must at least achieve this one end: that the public will not make either the logical or mathematical connection between economics and the other energy sciences or learn to apply such knowledge.
It is only a matter of time before the new breed of private programmer/economists will catch on to the far-reaching implications of the work begun at Harvard in 1948. The speed with which they can communicate their warning to the public will largely depend upon how effective we have been at controlling the media, subverting education, and keeping the public distracted with matters of no real importance.
The Harvard Economic Research Project (1948-) was an extension of World War II Operations Research. Its purpose was to discover the science of controlling an economy: at first the American economy, and then the world economy. It was felt that with sufficient mathematical foundation and data, it would be nearly as easy to predict and control the trend of an economy as to predict and control the trajectory of a projectile. Such has proven to be the case. Moreover, the economy has been transformed into a guided missile on target.
As we can see, the actual monetary system was created as a system of control (SOC), which is essentially founded on thievery and has restrictions, barriers, closed doors, a lack of transparency, and different rules for different actors. Through fabricated inflation and economic crises, it has been stealing our riches and freedom and controlling not just the electrical supply but also the social energies of humanity. (Inductors and economic conductors)\ \ However, Bitcoin is restoring our freedom. A way to make money, save it, and spend it without any restrictions, inflation, or capricious regulations. A novel kind of property that is not dependent on a counterparty, like banks or governments, and that requires energy to manufacture rather than being formed spontaneously.
Bitcoin generation should end up where it's cheapest. Maybe that will be in cold climates where there's electric heat, where it would be essentially free.
Satoshi Nakamoto, August, 2010
This fact is key to unlock the benefits of deflation that had been opaqued by the artificially created inflation.
Natural deflation
The primary benefit of bitcoin is deflation. Deflation incentives people to delay consumption and save more. Saving is the key to economic growth, because it can help to increase investment and productivity.
With the increase in productivity, prices tend to go down as they are more abundant and we find cheaper ways to produce thanks to technology.
The only reason that prices are not going down today -except in products where improvements are very rapid (e.g., computers)- is because of government-caused-currency inflation.
They have been stealing the benefits of natural deflation from us, but now we can access it thanks to Bitcoin.
It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy.
Satoshi Nakamoto, 1/17/2009
Conclusion
To only way to scape the slavery system is to earn, save and spend bitcoin; a money that’s not controlled by the governments and banks, that is not subject to inflation and where everyone has to play under the same rules.
Happy birthday Bitcoin!
Bitcoin or Slavery!

-
 @ c8ab3c20:4bb40a9d
2024-06-08 13:33:15
@ c8ab3c20:4bb40a9d
2024-06-08 13:33:15Introduction
Vous ne le saviez peut-être pas, mais il y a deux ans, j'alimentais un blog en ligne dédié à la vie privée. Je conjuguais tout à la première personne du pluriel, comme si j'étais une entreprise ou une entité composée de plusieurs passionnés, alors qu'en réalité, je suis seul derrière mon clavier. J'ai toujours aimé écrire, mais gentiment, mes articles ont cessé de dépasser le stade de brouillon. Je m'étais fixé un standard trop élevé et difficile à tenir avec mon temps libre. Je voulais absolument faire des articles longs, très détaillés et sourcés. Cela me demandait beaucoup de charge mentale pour un retour très discret. Puis, gentiment, les brouillons se sont faits de plus en plus rares, et les articles ont cessé de voir le jour sans trop d'explication. J'ai discrètement délisté mon blog comme s'il n'avait jamais été là. Depuis un petit moment déjà, ça me travaillait, je me suis remis à écrire pour d'autres projets qui peut-être eux aussi resteraient inachevés, au stade de brouillons de pensées. Mais je m'étais remis à écrire, et ça me manquait réellement. Et un jour, j'ai décidé de reprendre mon blog et de l'adapter à ma vision de ce que je voulais transmettre, qui avait bien évoluée en deux ans.
Une refonte de mon blog.
J'ai supprimé mes anciens articles qui étaient tous partiellement périmés, et oui, c'est le gros problème avec ce milieu, mais entre les rachats, les dépôts Git abandonnés, les nouveautés, si je ne suis pas régulier, mes informations seront très vite peu recommandables. Donc, j'ai décidé de m'autoriser à faire des articles plus simples, plus courts. Cela ne veut pas dire que ce sera le cas pour la totalité d'entre eux, et je compte continuer de faire de mon mieux pour partager de l'information de qualité en français. Mais afin d'être plus régulier, ce compromis me semblait nécessaire. Cette refonte m'a amené à changer le nom, je trouvais l'ancien légèrement cringe pour ne pas dire peu inspiré. Le blog se nomme aujourd'hui : "Le blog du petit lunarpunk 🌙". Je trouve ce nom à la fois mignon, oldschool et identitaire.
- J'ai choisi l'adjectif petit pour le côté rassurant et bienveillant. Le terrier de la privacy (confidentialité en anglais) peut-être angoissant, voir terrifiant, je sais de quoi je parle, ayant moi-même développé une légère paranoïa à force de m'aventurer dans ses profondeurs. Mais c'est contre-productif, et je veux réussir à amener une douceur dans l'accompagnement de votre quête pour une meilleure hygiène numérique.
- Le nom lunarpunk est pour balancer et ramener un peu de pragmatisme, car cela reste un terrier angoissant et très sombre. Mais ce personnage du petit lunarpunk que j'incarnerai en tant que Cypher Jack a justement le rôle d'une entité protectrice comme Jack dans le dessin animé Samouraï Jack (oui, oui, mon pseudo est une référence à ce vieux Cartoon Network des années 2000). Pour en apprendre un peu plus sur le concept de lunarpunk, vous pouvez lire la page d'accueil de mon blog.
- Avoir un blog, c'est en soi déjà un peu oldschool, mais avoir un blog dont le nom commence par "Le blog de/du/de la..." c'est encore plus à l'ancienne, et c'était pour représenter le choix simpliste que j'ai fait, je reviens là-dessus juste après. Mais sur ce blog, vous n'aurez pas de publicité AdSense, de tracking par JavaScript ou avec des cookies, juste du bon vieux HTML, un thème CSS simple et de l'information. En mémoire au web1, loin du modèle économique prédateur du web2 et du bullshit marketing du web3, mon blog se veut plus proche du web1 et du web0.
Le choix de la plateforme.
Medium et Substack
Pour faire un blog, on a du choix. Il y a évidemment des solutions populaires et propriétaires comme Medium et Substack qui, à mon avis, deviennent un peu drivés par le profit.
WordPress, Ghost et Grav
J'aurais pu héberger mon propre WordPress, après tout, ma formation professionnelle m'a familiarisé à cet incontournable plateforme du web... et c'est bien la raison pour laquelle j'ai décidé de l'éviter, car je sais ce que c'est. J'aurais pu aussi considérer une alternative open source un peu plus moderne comme Ghost ou Grav, Ghost faisait partie des options qui me semblait la plus compatible avec ma vision.
WriteFreely et le fédivers
Dans la même veine, on avait WriteFreely, une solution construite sur le protocole du Fédivers ActivityPub que je trouvais intéressant, malheureusement, je ne trouvais pas d'instance qui me donnait suffisamment envie ou qui était dans mes tarifs. Je n'ai pas comme objectif de transformer ce blog en business. Ça ne veut pas dire que je ne chercherai jamais le moyen de monétiser l'effort que j'y mets, en revanche, ce n'est pas pourquoi j'écris. Il me fallait donc une solution abordable (voir gratuite), open source et avec une interface agréable sans que cela ne me prenne la tête à configurer.
HUGO et ʕ•ᴥ•ʔ BearBlog
Je n'en ai pas parlé avant, mais similaire à Ghost ou WordPress, j'ai découvert HUGO qui m'intéressait bien car c'est très léger et supporte pleins de thèmes. Mais bon, il fallait le configurer et héberger tout ça.\ Un jour, je suis tombé sur la solution pour laquelle j'ai opté : BearBlog, A privacy-first, no-nonsense, super-fast blogging platform.\ En gros, la solution idéale pour moi, je pouvais la tester rapidement et gratuitement, c'est du logiciel libre et open source (MIT), respectueux de mon intégrité numérique mais aussi de la votre, sans publicité, sans JavaScript et sans pisteurs. La solution premium est super abordable, et je la considère donc simplement parce que, en plus d'être accessible, son créateur avait fait la solution dont j'avais besoin, et je pense qu'il mérite mon soutien.
Nostr et Habla
Fin 2022, alors qu'il y avait encore un peu d'activité sur mon blog, je découvre Nostr... j'y comprends pas grand-chose, mais la scène Bitcoin semble très emballée par ce protocole. Début 2023, après des discussions et présentations à des MeetUps Bitcoin, je commence à saisir le potentiel d'identités basées sur une paire de clés cryptographiques, de la stupidité des relais et du protocole, et de l'inventivité des clients qui ne cessent de germer et de s'améliorer. Parmi eux, un a particulièrement retenu mon attention : Habla. Une sorte de Medium basée sur Nostr avec l'intégration des zaps (des dons minuscules via le réseau Lightning remplaçant des likes sans valeurs). Je vais partager mes articles sur Nostr via ce client pour expérimenter, vous trouverez ma npub sur la page d'accueil.
Nouveaux contenus
Désormais, je veux vraiment essayer de commenter l'actualité autour de la vie privée en ligne et ce qui gravite autour. Je désire aussi rédiger des tests/reviews afin de faire des retours d'utilisation honnêtes (trust me, bro). Ça pourrait aller d'une app open source à un hardware wallet en passant par un service en ligne. C'est quelque chose que j'ai toujours aimé faire pour mes proches, je partagerai donc ça ici en espérant que vous y trouverez un plus grand intérêt que ces derniers.\ Mais surtout, comme avant, des guides ou tutoriels afin de vous aider à utiliser les outils de façon bénéfique pour votre niveau de menace. Ça ira du choix de son navigateur à l'utilisation de logiciels de chiffrement et l'hébergement de services.\ Je vais faire un résumé type TL;DR pour chaque article afin de faire passer l'information à ceux qui n'ont pas le temps ou la motivation de tout lire.
Conclusions
Je suis très heureux d'avoir retrouvé de la motivation pour écrire et alimenter mon blog, désormais nommé "Le blog du petit lunarpunk 🌙". Je souhaitais expliquer pourquoi j'ai choisi ce nom pour apporter un peu de sens à mes lecteurs. Au final, cet article est plus long que prévu, mais cela aura été un bon exercice pour moi, me permettant de me remettre dans le bain et de trouver l'inspiration pour la suite. Il était également important d'expliquer mon choix de plateforme, car j'ai opté pour la simplicité, qui est souvent un compromis, mais je pense avoir trouvé un bel équilibre avec BearBlog. Si mon projet vous intéresse, vous pouvez ajouter le flux RSS et oui, c'est old school aussi). Cela me permettra de faire un article sur cette vieille technologie qui est devenue incontournable dans ma vie pour obtenir de l'information. N'hésitez pas à prendre contact avec moi, que ce soit sur les plateformes listées en page d'accueil ou en privé. Vous pouvez également partager les prochains articles dans vos cercles si vous les trouvez de bonne qualité. Celui-ci n'est pas le plus intéressant à partager, mais faites ce que vous voulez.
-
 @ 44dc1c2d:31c74f0b
2024-05-22 22:09:19
@ 44dc1c2d:31c74f0b
2024-05-22 22:09:19Chef's notes
If you don't have peanuts, you can sub it with peanut butter, but you'll want to cook with less salt as the peanut butter can add too much salt to the dish.
Details
- 🍽️ Servings: 4
Ingredients
- 2 1/2 cups Coconut Milk
- 3 Tbsp Red Curry Paste
- 3 Tbsp Thai Fish Sauce
- 2 Tbsp Palm sugar or light brown sugar
- 1 LB rump streak cut into thin strips
- 2 Lemon Grass Stalks, Bruised
- 3 oz Ground Roasted Peanuts
- 2 Fresh Red Chilies, Sliced
- 5 Kaffir Lime Leaves, Torn
- Salt and Pepper
- Thai Basil for Garnish
- 2 Salted eggs to serve with
Directions
- Put half the coconut milk in a large pan or Wok and heat gently until it begins to boil and separate.
- Add the curry paste and cook over medium heat until fragrant. Then add the Fish sauce, sugar and lemon grass.
- Continue to cook until the color of the sauce deepens
- Add the remaining coconut milk. Bring back to boil. Add the beef and peanuts. Cook for another ~10 min
- Add the chilies and the torn Kaffir Lime and adjust the seasoning. Garnish with whole Basil leaves and serve with a salted egg and rice.
-
 @ 39cc53c9:27168656
2024-05-22 18:09:11
@ 39cc53c9:27168656
2024-05-22 18:09:11These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing. Reviews are in collaboration with Orangefren.
The review
Swapter.io is an all-purpose instant exchange. They entered the scene in the depths of the bear market about 2 years ago in June of 2022.
| Pros | Cons | |----------------------------------------------|---------------------------------------------| | Low fees | Shotgun KYC with opaque triggers | | Large liquidity | Relies on 3rd party liquidity | | Works over Tor | Front-end not synced with back-end | | Pretty UI | |
Rating: ★★★☆☆ Service Website: swapter.io
Test Trades
During our testing we performed a trade from XMR to LTC, and then back to XMR.
Our first trade had the ID of:
mpUitpGemhN8jjNAjQuo6EvQ. We were promised 0.8 LTC for sending 0.5 XMR, before we sent the Monero. When the Monero arrived we were sent 0.799 LTC.On the return journey we performed trade with ID:
yaCRb5pYcRKAZcBqg0AzEGYg. This time we were promised 0.4815 XMR for sending 0.799 LTC. After Litecoin arrived we were sent 0.4765 XMR.As such we saw a discrepancy of
~0.1%in the first trade and~1%in the second trade. Considering those trades were floating we determine the estimates presented in the UI to be highly accurate and honest.Of course Swapter could've been imposing a large fee on their estimates, but we checked their estimates against CoinGecko and found the difference to be equivalent to a fee of just over
0.5%. Perfectly in line with other swapping services.Trading
Swapter supports BTC, LTC, XMR and well over a thousand other coins. Sadly they don't support the Lightning Network. For the myriad of currencies they deal with they provide massive upper limits. You could exchange tens, or even hundreds, of thousands of dollars worth of cryptocurrency in a single trade (although we wouldn't recommend it).
The flip side to this is that Swapter relies on 3rd party liquidity. Aside from the large liqudity this also benefits the user insofar as it allows for very low fees. However, it also comes with a negative - the 3rd party gets to see all your trades. Unfortunately Swapter opted not to share where they source their liquidity in their Privacy Policy or Terms of Service.
KYC & AML policies
Swapter reserves the right to require its users to provide their full name, their date of birth, their address and government-issued ID. A practice known as "shotgun KYC". This should not happen often - in our testing it never did - however it's not clear when exactly it could happen. The AML & KYC policy provided on Swapter's website simply states they will put your trade on hold if their "risk scoring system [deems it] as suspicious".
Worse yet, if they determine that "any of the information [the] customer provided is incorrect, false, outdated, or incomplete" then Swapter may decide to terminate all of the services they provide to the user. What exactly would happen to their funds in such a case remains unclear.
The only clarity we get is that the Swapter policy outlines a designated 3rd party that will verify the information provided by the user. The third party's name is Sum & Substance Ltd, also simply known as samsub and available at sumsub.com
It's understandable that some exchanges will decide on a policy of this sort, especially when they rely on external liquidity, but we would prefer more clarity be given. When exactly is a trade suspicious?
Tor
We were pleased to discover Swapter works over Tor. However, they do not provide a Tor mirror, nor do they work without JavaScript. Additionally, we found that some small features, such as the live chat, did not work over Tor. Fortunately, other means of contacting their support are still available.
UI
We have found the Swapter UI to be very modern, straightforward and simple to use. It's available in 4 languages (English, French, Dutch and Russian), although we're unable to vouch for the quality of some of those, the ones that we used seemed perfectly serviceable.
Our only issue with the UI was that it claims the funds have been sent following the trade, when in reality it seems to take the backend a minute or so to actually broadcast the transaction.
Getting in touch
Swapter's team has a chat on their website, a support email address and a support Telegram. Their social media presence in most active on Telegram and X (formerly Twitter).
Disclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3c984938:2ec11289
2024-05-19 12:55:47
@ 3c984938:2ec11289
2024-05-19 12:55:47👉play the audio to listen to the article.
This article contain several links hidden within the text. If you dare to understand the meaning behind the last image. Click on "daily" for an image, read it. Then click on "muchness" to watch a video(about 1h) link. After you've done that, revisit here and look at my last image. You might have missed something.

Excusez-moi, s’il vous plaît. That tasted purple🍵🌺
🤤😮Are you still thirsty from the previous article? Are you amazed by the different flavors of web3 enabled sites, clients, and apps? Did you try out using NIP-07, "Signer extension?" Nos2x or NostrConnect are pretty spiffy, eh! Did it bring a similar reaction like when you first learned how to drive? When I started to explore Nostr I had that “whoa, that a lot easier than Facebook,” moment. 💡⚡A light bulb started to flicker on.

🎉🎈Are you having fun yet? Would you like another cup of tea? 💸HODL (Hold On for Dear Life) as we sip our way to purple. Things here in Nostr wonderland are curiouser and curiouser every day. One day it's 🍕pizza 🥧pie? And then the next day it's Danny, Dan, Dan. Hold on to your petticoat, because you're about to get swept away, by the tools to get the most out of Nostr.

But first, would you like a purple crumpet?💜🥞
🍵🍰🎉This wouldn't be much of a tea party without a bit of finger food. If you are following me, I'm just a little hors d'oeuvre among the many here on Nostr. So let's try some other flavors. You can start with some influencers from twitter that have fallen into the rabbit hole here at this link.
I follow Jack and Edward Snowden, but there are several others.
jack @npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Snowden @npub1sn0wdenkukak0d9dfczzeacvhkrgz92ak56egt7vdgzn8pv2wfqqhrjdv9
💡🎮🏈🎲🏹What are some topics, hobbies, and interests that are important to you? You can search for hashtags and follow those on your client. For example, #onigirl, #privacy, and even #cats in your search bar on your client. Remember, there are no algorithms here. If wish to have a vibrant feed or be fed random stuff(which is kinda cool sometimes), follow curators that you like.
👉🚦💤Don't sleep on "stacker.news", 🎩🔐📎They're entirely bonkers! But I'll tell you a secret. All the best people are. Here are just a few.
📝@Lux drops “sovereignty pills"💊 daily in “Stacker Saloon,” 🏋️♀️@grayruby does 100 push-ups and squats until 100k Bitcoin, 🔏@sethforprivacy podcast host of "Opt Out," 🎼@MusicTrappa Former Tv Contestant of NBC the voice. 💣@nerd2ninja posts invigorating and provocative links and content, 🐝@Alby for bee news, @TNstacker, @0xbitcoiner, @undisciplined and dozens more! Plus a new territory just started by @AtlantisPleb called ~openagents revolving around NIP-90 Data Vending Machine, it is hilarious to play with. Try Trolly McPirate, tis quite fun.

Are you turning purple?💜
👉🍄🦋"Who are you?” said the Caterpillar Now, that you've drank and ate, are you changing color yet? Let's explore this wonderland that Nostr has given us! It starts with changing your profile and banner image to anything you like. Since, we're not robots.

👉🌻🌹"Do you suppose she's a wildflower?" asked the Daisy. 🌼🌷 ⭐NIP-05 identity DNS ⭐ Similarly to Twitter, a check mark is to show that you are from the same garden “like a human,” and not an outlier like a weed or, "bot." But not in the nefarious way that Big Tech handles this. In Nostr wonderland this allows you to map your silver key, "npub" to a DNS identifier. Once verified, eat a mushroom and shout out to announce your new Nostr residency to share. Just remember, one quick little thing. Break a small piece of the other side of the mushroom after, don't bite.
✨There are a plenty of options but if you've followed the steps in my previous article, "First time (N)ostrich start here!" guide following my advice to get a SN, "stacker.news" then this gets extremely easier.
👉✅Click your "Profile," then click "Settings," scroll to the bottom and paste your Silver key, "npub!" and click "save" and there you go! Use your Stacker.news lightning wallet address as your ⭐NIP-05.⭐ Congratulations!!! You are now verified! Give it a few hours and when you use your "main" client you should see a checkmark!
Beware of card soldiers 2-10

👉⚔🍎👑☠Oh No! The "Queen of Apples" has released a jabberwocky that threatens some Nostriches wallets! As long as you remain using her wares within Nostr Wonderland you may need to comply to her draconian ways! 👛👾👺🐭
❗It has come to my attention that Apple users cannot utilize Chrome webstore; thus are not able to take advantage of using "Signer extension." Whatever, shall we do? Shall we paint all the roses red?🌹

👉🎠🦄'Well, now that we have seen each other,’ said the Unicorn, ‘if you’ll believe in me, I’ll believe in you. Is that a bargain?🦁🤝
For 🍏Apple users, you can still use "stacker.news" by registering with your email to help you get a starter Bitcoin lightning wallet. Another option is Primal, please note both wallets have Satoshi limits. Primal, may not be in your interest if you're concerned with privacy.
👉🎠🌼🐝🌻 A unicorn sent a friend, to help thee.🐝🌷🌹 A solution for 🍏Apple users would be to get an invitational code from Alby. You are able to use Alby via Safari on your Mac Os, and as a signer extension. Then connect 💎Damus with Alby. The good news is you can find @Alby on stacker.news and ask! Or check them out on your client. Just search "hello@getalby.com" Once you get an account, you could use your Alby lighting address as your ⭐NIP-05⭐ address as an option. The bee whispered to me, “I also support android, Safari on Mac and things,” and flew high to lead us out.
Alby the bee, silver key @npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm

Quickly! Follow me out of this maze!
✨With the help from 🐝Albee, we escaped the 👑queen's jabberwocky. The key to decentralization is to shred all thing bounding you by unseen 🔗chains and "things". To abandon all things 🏫learned, and go back to thinking about 😲six impossible things. You should try it-- It certainly is such great practice. 💡For example, what if I told you that you were all ⚰dead? How 🤡preposterous and silly! But whose, 🤝who, to say it isn't? This is your adventure, dear user. I'm merely here to help guide you in all its marvels, and to safely navigate you through its treacherous terrains. How much 🦁muchness' do you have? Oh, blind me, do I see a clearing?

Ohh! Look here, my friends must have 🦺built a safe passage.
A ♨ steaming river is set before us. We must be very careful. Unless, you want to end up in the boiling sea. There are some boulders and pebbles over there. My 😊friends, must have laboriously put these here for Nostriches like us. I'll take you to the 🐸frogstr and 🐰hare, but then that will be the end of it.

I think I see him, He's right there. Ever since 🐸Frogstr converted to freedom, he's been spreading memes to others. Take a peek!
Memestr, Pinstr, Badges, If you've received badges, put them on by visiting here., Swarmstr cute interface to view hashtags, My favorite food client with optional OnionSauce, noStrudel tastes like 🤖Reddit, Gossip My favorite Desktop Client, Extensive List of all things Nostr., and Alice in Wonderland story.
My friend the 🐇white rabbit Yakihonne now supports 🍎iOs and 🤖Android. This app supports NIP-23 in all of its entirety. Feel free to soak up the information there. When NIP-65? 🎯I don't know. Let's 🐜bug them to do that.

You can easily find all my content on 🐇Yakihonne.com or on the app. My only grief I have with the 🐰hare is that it's not Open Source. Annoy the 🐇white rabbit to go Open Source if you can catch him! He's always going off about "⏰Time⌚" which brings me to the end of my guide.

We're lucky to escape the Bloody Shrewd 👑Knave, but he will send his 🃏card ⚔soldiers yet again.
📢Lastly, dear user. What better time then now to make your life more ⛓decentralized, if not now then when? Take back your ⚖digital sovereignty, and it starts here in Nostr 🐹Wonderland. Use the 🛠tools here, and share your knowledge, experiences, or whatever and 💰monetize it. Join the 🎉Freedom Party! Learn about the Knights of Nostr that are fighting for Freedom Tech and the projects that are contributing to make it happen. FOSS for all!
👉Have you tried the 🍊Orange 🍵Tea, Dear User? It's quite divine. Would you like me to write a 💰Bitcoin guide? Let me know in the comments! I appreciate all feedback.
👉You can read my 🧵first article here. Alternatively, you can click/tap "here" if you're logged into app client.
🙇♀️🙏It would be the highest honor for me if you 🔖bookmarked my article and 🔁shared it with future (N)ostriches.
"Imagination is the only weapon in the war against reality." -Lewis Carroll
🧧⚡Zapping⚡ is always appreciated, but is not required.
💜🧡Thank you💖💋
📢🥂Special Shout-outs
🐶Uno - Spreading Nostr love @npub14q8uffuxxnhzd24u4j23kn8a0dt2ux96h5eutt7u76lddhyqa0gs97ct2x
🥂Derek Ross - welcoming committee to Nostr; I'm jumping on this. @npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
👏Nos Social - Introducing me to the Nos App community @npub1pu3vqm4vzqpxsnhuc684dp2qaq6z69sf65yte4p39spcucv5lzmqswtfch
🐇Yakihonne - For supporting all things Nip-23 @npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🐱💻Semisol - working hard to keep TOR relays up @npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
📝James - Introducing me to use my obsidian tool or earring. (I've converted at least seven Nostr since then) @npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw
-
 @ ce80c0eb:bcb3390c
2024-05-15 18:38:47
@ ce80c0eb:bcb3390c
2024-05-15 18:38:47GrapheneOS, a privacy-centric mobile operating system, often comes under scrutiny for app compatibility. This blog aims to demystify how GrapheneOS, through its innovative use of sandboxed Google Play Services, effectively resolves these concerns, making it an ideal choice for travelers who value privacy and security.
The Core of GrapheneOS
GrapheneOS stands out for its commitment to security and privacy. However, a common misunderstanding is its perceived limitation in-app functionality, primarily due to its default exclusion of Google Play Services.
The Role of Google Play Services in App Compatibility
Many essential apps for travel, communication, and navigation rely on Google Play Services. This dependency is where the misconception about GrapheneOS's app compatibility stems from, as it's designed to function without these services by default.
Sandboxed Google Play Services: A Strategic Solution
GrapheneOS addresses this challenge by offering sandboxed Google Play Services. This feature allows users to access and use a wide range of apps while maintaining the OS's high standards of privacy and security.
-
Ensuring App Functionality: By sandboxing Google Play Services, GrapheneOS allows users to run most apps seamlessly, countering the myth of limited app compatibility.
-
Maintaining Security and Privacy: The sandboxed environment isolates these services, minimizing their access to the system and user data, thus preserving the core privacy principles of GrapheneOS.
-
Providing User Flexibility: Users have the choice to install sandboxed Google Play Services based on their needs, offering a balance between functionality and privacy.
The Impact on Travel
For travelers, this means that they can use GrapheneOS to navigate, communicate, and engage with local services through popular apps without compromising their privacy. This functionality is particularly crucial in foreign environments where reliance on digital tools is often heightened.
Personal Insights and User Experience
As someone who primarily strives to use my device without Google services, I've found GrapheneOS to be incredibly accommodating. This OS aligns perfectly with my preference for a Google-free experience, offering robust privacy features and a plethora of non-Google apps that cater to most of my needs.
However, the reality of travel sometimes necessitates the use of certain apps that depend on Google's ecosystem. In these instances, the ability to use sandboxed Google Play Services on GrapheneOS has been a game-changer. This feature has been especially useful for accessing essential apps like maps for navigation, local transportation apps in different countries, and certain communication tools that are indispensable in specific regions or situations.
Addressing Common Concerns: GrapheneOS's Unique Solutions
While some users may have concerns about using GrapheneOS, such as app compatibility and eSIM management, the operating system offers innovative solutions to address these issues, making it an excellent choice for travelers.
1. Seamless Use of Essential Travel Apps
GrapheneOS enables the installation of Google Play Services in a sandboxed environment, allowing users to access most travel and communication apps without compromising their privacy.
- Personal Experience: During my travels in Southeast Asia and abroad, I have successfully used essential apps like Google Maps, LINE, and Grab without any issues, thanks to the sandboxed Play Services, which I installed in a separate user profile to keep my main profile Google free.
2. Extensive App Compatibility
Although GrapheneOS doesn't include Google Play Services in its standard setup, the sandboxed environment enables users to run a wide range of apps that rely on Google's ecosystem, dispelling the misconception of limited app compatibility.
- Alternative App Sources: For apps that don't require Google Services, GrapheneOS users can access a wealth of options and alternatives through sources like F-Droid and Aurora Store.
3. Streamlined and Secure eSIM Management
GrapheneOS has made significant advancements in eSIM management, offering users a streamlined and secure experience. This feature is particularly beneficial for travelers who need to switch between different mobile networks while abroad.
By addressing these common concerns head-on, GrapheneOS demonstrates its commitment to providing users with a privacy-focused, user-friendly, and travel-compatible mobile operating system.
Disabling Unused Apps for Enhanced Security
GrapheneOS offers a unique feature that allows users to disable apps they aren't actively using. This feature is particularly useful for travelers who may have location-specific apps that are only needed for a limited time.
-
Enhancing Security: By disabling unused apps, you reduce the potential attack surface of your device, making it more secure.
-
Saving Resources: Disabled apps don't run in the background, freeing up system resources and potentially extending battery life.
-
Streamlining App Management: This feature helps keep your app drawer organized and clutter-free, making it easier to manage your device.
To disable an app, simply go to the app's settings and select "Disable." You can easily re-enable the app whenever you need it again.
Tips for Nomads Using GrapheneOS
-
Set Up Sandboxed Google Play Services: Before you travel, set up the sandboxed environment for essential apps.
-
Regularly Review App Permissions: Keep track of which apps have access to your data and adjust settings as needed.
-
Explore Browser Alternatives: Use browser versions or PWAs of popular apps for a more privacy-conscious approach and also to reduce how many apps you have installed.
-
Stay Updated: Utilize GrapheneOS's automatic update feature to maintain security.
-
Secure Communication: Opt for encrypted communication apps for privacy in your work and personal conversations.
Conclusion
GrapheneOS, with its unique approach to privacy and app compatibility, dispels the common concerns of digital nomads. By understanding and utilizing its sandboxed Google Play Services, app disabling feature, and other capabilities, you can enjoy a seamless, secure digital experience on your travels. GrapheneOS is not just a viable option; it's a robust solution for the privacy-conscious nomad.
-
-
 @ 574099a1:f3abeb80
2025-01-03 20:19:03
@ 574099a1:f3abeb80
2025-01-03 20:19:03Equipo de GrapheneOS:
Nuestra función de desbloqueo por huella dactilar de 2 factores ya está completamente implementada y ya está disponible en GrapheneOS. Esto añade la opción de establecer un PIN para usar el desbloqueo por huella dactilar. Puedes usar una passphrase fuerte de diceware (método para generar contraseñas seguras utilizando dados) como el método principal de desbloqueo con huella dactilar + PIN como desbloqueo secundario.
Las restricciones habituales sobre el desbloqueo por huella dactilar siguen aplicándose. Es un mecanismo de desbloqueo secundario que solo se puede usar durante 48 horas después del último desbloqueo primario. El límite de intentos fallidos de desbloqueo por huella dactilar en GrapheneOS es de 5.
En iOS y Android, la forma en que funciona el desbloqueo biométrico es que tienes un PIN/contraseña como tu método principal de desbloqueo y puedes habilitar el desbloqueo biométrico como un método secundario que solo se puede usar después del primer desbloqueo durante un tiempo limitado desde el último desbloqueo primario exitoso. También imponen un límite de intentos donde, si fallas demasiadas veces, necesitas usar el método de desbloqueo primario. Nuestra función añade la opción de establecer un PIN que se requiere después de usar exitosamente una huella dactilar para completar el proceso de desbloqueo, eso es todo.
Usar un PIN aleatorio de 6 dígitos como tu método principal de desbloqueo es un equilibrio entre conveniencia y seguridad que depende completamente de la limitación del elemento seguro para una encriptación segura. Un atacante que pueda explotar el sistema operativo y luego el elemento seguro desde allí puede eludir la encriptación. Es extremadamente difícil explotar los elementos seguros de alta calidad en los Pixels, pero es posible. Hasta donde sabemos, Cellebrite aún no ha desarrollado un exploit para el Titan M2 en el Pixel 6 y posteriores, pero eventualmente descubrieron cómo explotar el Titan M1. Usar una passphrase fuerte de diceware evita depender de cualquier cosa que pueda ser explotada. Sin embargo, eso es muy inconveniente. Ahí es donde entra el desbloqueo biométrico de iOS y Android a través de cara/huella dactilar para hacerlo conveniente, pero a un gran costo de seguridad. El desbloqueo biométrico puede ser forzado físicamente. Tu cara o huella dactilar también podrían ser clonadas de una manera que les permita desbloquear. Dejas tus huellas dactilares en todo lo que tocas y tu cara puede ser grabada por múltiples cámaras al mismo tiempo casi en cualquier lugar al que vayas.
Ejemplo de passphrase de diceware: "abacus banana cactus dolphin elephant"
Una passphrase fuerte como el método principal de desbloqueo contiene entre 4 y 12 palabras, dependiendo de tu modelo de amenaza.
El objetivo de nuestra nueva función es habilitar la seguridad de una passphrase fuerte combinada con la conveniencia del desbloqueo biométrico de la manera habitual que funciona en iOS y Android, pero con el giro de requerir un PIN para completar el proceso de desbloqueo de huella dactilar. Es una función bastante simple: puedes establecer un PIN requerido para completar el desbloqueo de huella dactilar. No tienes que habilitarlo.
Proceso: Marcas tu huella dáctilar y a continuación pones un PIN (Ejemplo 673889)
¿Cómo hacerlo en la práctica?
- Vas a Ajustes > Seguridad y privacidad > desbloqueo del dispositivo

\ 2. A continuación, Desbloqueo de huella dactilar > introduces tu contraseña primaria > Eliges la opción de Segundo factor PIN. Una vez dentro tecleas el PIN que hayas elegido y luego lo vuelves a poner para verificar. Y listo.

-
 @ 30ceb64e:7f08bdf5
2025-01-03 19:38:28
@ 30ceb64e:7f08bdf5
2025-01-03 19:38:28Michael Saylor's recent assertion on Tom Bilyeu's podcast that Bitcoin offers a risk-free return sparked an interesting debate. While Tom struggled with the concept, the truth lies in understanding what "risk-free" truly means in our modern financial landscape. When you denominate your wealth in Bitcoin and store it properly in cold storage UTXOs, you're essentially protecting your work energy in perhaps the least risky way possible.
https://m.primal.net/NQjb.png
Traditional banking customers often consider their dollars in savings accounts to be risk-free, but this belief ignores fundamental realities. Bank failures are increasingly common, and FDIC insurance is merely a paper promise from the same entity responsible for systematic wealth destruction. The state has reached a point where repaying its debt within the current paradigm seems impossible.
The paradox of taxation in a money-printing world raises profound questions. Why do we pay taxes when money can be created with the press of a button? The answer might lie in maintaining the illusion of government sustainability. We surrender roughly half our work energy to finance a system that can theoretically fund itself through money printing - a perplexing arrangement that defies logical explanation.
Bitcoin represents hard money that doesn't require yield in the traditional sense. The real yield comes from humanity's natural progression toward efficiency and innovation. When your savings aren't being debased, technological advancement and human ingenuity naturally make your money more valuable over time. The world is inherently deflationary, but this truth becomes obscured when savings are denominated in infinitely printable currencies.
This dynamic mirrors historical examples, like African communities saving in glass beads and shells, unaware that Europeans were mass-producing these "stores of value" in factories. Living in our current system is like existing in a deflationary world while being tricked into believing it's inflationary - a matrix-like illusion that drives the endless pursuit of "more" in a fundamentally broken system. The federal reserve is a glass bead manufacturer and some of us are the slaves that use it as money.
https://m.primal.net/NQkA.webp
Bitcoin's technical evolution continues to strengthen its position as sound money. Enhanced privacy features through initiatives like PayJoin, e-cash, and Lightning Network, combined with improved custody solutions and growing infrastructure, make it increasingly accessible and practical for everyday use. The ability to transact without permission or exploitative intermediaries, guided only by free market principles, represents a fundamental shift in financial sovereignty.
The question of "enough" becomes central to the Bitcoin journey. While the technology offers a path to financial sovereignty, it's crucial to balance accumulation with life's other valuable resources - time with family, personal growth, and meaningful relationships. The timechain will judge our actions, but perhaps the most important consideration is whether our pursuit of satoshis comes at the cost of more precious aspects of life.
We stand at a unique point in history where individual sovereignty is becoming truly possible. The pendulum swings toward a new paradigm that could secure prosperity for generations to come. While many haven't yet reached their personal "escape velocity," the path to financial freedom through Bitcoin becomes clearer with each passing day.
The concept of risk-free extends beyond mere financial considerations. In a world where time is our most precious and finite resource, Bitcoin offers something unprecedented: the ability to store life energy in a system that appreciates with human progress, rather than depreciating with political whims. The risk isn't just about losing money - it's about losing life energy, family time, and personal freedom.
-
 @ 1cb14ab3:95d52462
2025-01-03 19:29:40
@ 1cb14ab3:95d52462
2025-01-03 19:29:40(Panel) composite paper, ash wood [4” x 48”]
(Box) pallet, pallet wood, spray paint, nails [48” x 24” x 24”]
This project was first presented in 2016 in Boulder, Colorado. Prints available on request.
Artist Statement
Quarantine: Examining the Impact of Globalization
“Quarantine” examines one node in the complex network of human globalization. The work reflects on the repercussions of global trade and encourages discussion about the benefits - and tradeoffs - that globalization has brought the human species.
At the core of the project lies the Emerald Ash Borer (EAB), an invasive insect that has left a trail of devastation across millions of ash trees in the United States. Native to Asia, the EAB hitchhiked its way onto American soil through wooden packing materials. It made its debut in Boulder in 2013 - threatening the existence of nearly 100,000 ash trees in the area. To curb further spread, the federal government imposed a quarantine on all ash wood from affected regions.
As one contemplates the interplay between the various elements of the piece, they should aim to explore their own moral frameworks and seek to dive deeper into questions on progress, connection, and preservation.
“Quarantine” is presented through two elements, each narrating a unique chapter of this ecological saga:
The ash wood panel aims to mimic the characteristics of the EAB’s destruction. The panel is adorned with a font that mimics the signs of infestation and illustrates the relentless assault this tiny creature is causing.

The text is rendered in midnight black, creating a deliberate contrast to that of which it lies—a dialogue between organic and artificial. The word “Quarantine” is displayed as the focal point of the panel to demonstrate a literal interpretation of ‘quarantine on ash’. As viewers engage with the panel they confront the dual forces. Nature’s vulnerabilities and humanity’s impact.

The box stands as a tangible representation of the method of infestation. It symbolizes not only containment, but also the globalized trade that facilitated the EAB’s journey in the first place. Its worn and gritty appearance mirrors the ecological (and economic) damages caused by this innocuous-seeming insect. On one side of the box, a bright red symbol hints at a potential warning to the destination of the ill-fated crate. The top reads 'destruction' in all bold caps. Something feels off.
Globalization, while propelling forward incredible human progress and prosperity, has also created undeniable disruptions to ecosystems and biodiversity around the globe. The EAB saga serves as just one case study into the larger topic at hand, revealing the unintended consequences of our interconnected world.
Additional Photos



Other Sculptures by Hes
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ ce80c0eb:bcb3390c
2024-05-15 18:34:15
@ ce80c0eb:bcb3390c
2024-05-15 18:34:15Protecting your privacy while staying connected is more important than ever especially while traveling. JMP.chat is a powerful service that provides virtual phone numbers for calling and texting, leveraging the decentralized Jabber/XMPP network. By using JMP.chat with various XMPP clients, you can communicate securely and maintain your privacy, whether you're traveling, signing up for services, or simply want to keep your personal information private.
Why JMP.chat is a Game-Changer for Privacy and Travel
JMP.chat offers numerous benefits for those looking to protect their privacy and stay connected on the go:
Maintain your privacy: With a virtual number from JMP.chat, you can avoid giving out your real phone number to people or services you encounter, reducing the risk of your personal data being compromised.
Access local services and maintain control over your accounts: JMP.chat numbers provide a convenient way to sign up for local services or apps that require a phone number, without the need to reveal your real one. This is particularly useful when you need to receive two-factor authentication (2FA) codes or when signing up for apps like Telegram, which require a phone number for registration.
By using a JMP.chat number, you can ensure that you maintain control over your accounts and avoid getting locked out due to not having access to the phone number associated with your account. This added layer of privacy and control is especially important when traveling or using services that you may not fully trust.
Pay with Monero (XMR): JMP.chat allows you to pay for their services using Monero, a privacy-focused cryptocurrency that ensures your financial transactions remain confidential adding to more privacy overall.
No KYC required: One of the standout features of JMP.chat is that they do not require users to complete a Know Your Customer (KYC) process. By eliminating the need for KYC, JMP.chat ensures that your privacy is protected from the very beginning, allowing you to use their virtual numbers with peace of mind.
Cheogram: A Feature-Rich XMPP Client for JMP.chat
Cheogram is a popular XMPP client that offers seamless integration with JMP.chat and a range of useful features:
- Dialer integration: Cheogram allows you to use your JMP.chat number directly from your device's native dialer app, making it easy to make and receive calls without opening the Cheogram app.
- Contact integration: Cheogram can sync your JMP.chat contacts with your device's native contacts app, making it easy to manage your contacts in one place.
- Automatic prefix handling: When making international calls, Cheogram automatically adds the necessary prefixes to ensure your calls are routed correctly.
While Cheogram offers a user-friendly experience, it's important to note that you can use any XMPP client that supports JMP.chat's features, such as Conversations, Snikket, Movim, or Gajim
How JMP.chat Works with XMPP Clients
JMP.chat acts as a bridge between the traditional telephone network and the Jabber/XMPP network. To use JMP.chat, you'll need a Jabber ID (JID) and an XMPP client.
Here's how it works:
- Obtain a Jabber ID: Create a Jabber ID or use an existing JID.
- Choose a virtual number: Visit the JMP.chat website and search for a phone number that suits your needs.
- Link your Jabber ID: Enter your JID when prompted to link it to your chosen virtual number.
- Set up your XMPP client: Install and configure your preferred XMPP client, such as Conversations, Snikket, Movim, or Gajim. If using Cheogram, download the app and log in with your Jabber ID and password.
- Start communicating: With your virtual number set up, you can now make and receive calls and texts through your XMPP client, as long as you have an internet connection.
Additional Features and Capabilities of JMP.chat
JMP.chat offers a wide range of features to enhance your communication experience:
Group and picture messaging: Send and receive group texts and picture messages using any Jabber client.
Voicemail: Receive voicemails as audio recordings and text transcriptions.
Seamless communication: Your contacts can communicate with you as they would with any other phone number, without needing to change anything on their end.
Multiple numbers: Get different numbers for various purposes, such as personal, professional, or dating, to keep different aspects of your life separate.
Number porting: Port your current US or Canadian number to JMP.chat after signing up with a temporary number.
Open-source software: All software used to provide JMP.chat is free and open-source, allowing you to inspect, download, or modify the source code.
Supported and Unsupported Features
JMP.chat supports a wide array of text messaging features, including:
- SMS
- MMS (picture messaging)
- Group MMS
- Delivery receipts
- Emoji
- Long messages
However, some features are not yet supported, such as:
- Sending messages to short codes (e.g., for two-factor authentication)
- Automated spam filtering
- Automated blocking of numbers
It's important to note that while JMP.chat provides phone numbers and voice/SMS features, it does not provide emergency services (e.g., 911, 112, 999) over voice or SMS.
Conclusion
JMP.chat, combined with the power of XMPP clients, offers a robust solution for protecting your privacy and staying connected, whether you're traveling, signing up for services, or simply want to keep your personal information private. By providing a secure and convenient way to manage your communication needs through virtual phone numbers and the decentralized Jabber/XMPP network, JMP.chat empowers you to take control and communicate on your own terms. Explore the various XMPP clients available and find the one that best suits your needs, knowing that your privacy is in good hands with JMP.chat.
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ 3c984938:2ec11289
2024-04-29 09:00:28
@ 3c984938:2ec11289
2024-04-29 09:00:28This is a part of my sporadic work on the Legend Series. I had a hard time finding good images. The images Ai often gave out made the islanders that look like Indians with the feather crowns, so that was interesting. The ending of this one is kinda funny.
The island was inhabited long ago by the ancient people (called Taotaomona). They were much larger than a regular person today. They also had magic, albeit little. The men were blessed with size and strength, while the women were gifted with wisdom and just a touch of magic in their hair.
One day, in the Hagatna bay. A group of fishermen noticed it their bay had grew. It was beyond confusing, to say the least. Another group of fishermen noticed that their bay, pago, also grew on the opposite side of the island.

"If this continues, our island will be cut into two pieces," cried the islanders. A wise leader came up with an idea to protect the island. The fishermen would watch their own bays from their own bays.
 ^^Huge fish, but you can also see the Taotaomona are also big.
^^Huge fish, but you can also see the Taotaomona are also big.The next morning, a fisherman spotted a massive fish in Pago Bay. The giant fish swam in and started to nibble the shoreline. The fisherman ducks behind boulders to observe and passes the message to his clan leader.
The leaders came together and came a conclusion that they must kill the fish. They sent runners to Hagatna Bay to ask for help to save their island home. Soon, Pago Bay was surrounded by canoes and men. All of them diligently watching to prevent their land from being eaten away, both in and out of the reef. Regardless of how hard they searched or waited, the fish didn't show. After awhile they give up and returned home.
 ^^Fish nibbling under the island from down under.
^^Fish nibbling under the island from down under.The news spread throughout the island about their imminent doom from clan to clan. They felt powerless to do anything.
The women of the island wore long, flowing locks and were proud to wash their hair in the river spring. The juices of lemons were used to enhance the magic. The peels were thrown into the spring after they were finished.

The maidens threw away the lemon peels into Hagatna Spring, but now they were popping up in Pago Bay. Which can only mean the peels were passing through the island, how did that happen? It could only mean the fish was nibbling under the island. A maiden cried out, discovering this new information, "We're surely doomed." Another maiden came forward and said, "Maybe we can outsmart the fish." The fish will be lured into swimming to Hagatna spring and set up a trap. The women came together to gather to trim their precious hair and wove it into a net. The net grew large enough to spread out in every direction of the bay. Each maiden held onto the edges and spread out to sing, waiting for the fish by the spring.
 ^^This is not an accurate representation, as the ancient people did not wear clothes. And they cut their hair to make the net.
^^This is not an accurate representation, as the ancient people did not wear clothes. And they cut their hair to make the net. Their song carried under the island, and the soothing sound carried underwater to the giant fishes lair. Little by little, it slowly swam closer to listen to the maiden's song. They sang and sang until they came up with new songs. The massive fish swam closer and emerges from the water. The maiden jumped into the spring surrounding it with their net to capture it. Their net didn't give way no matter how much the fish struggled. It was a success.
One maiden immediately ran to Hagatna to tell the others they had captured the giant fish and that the island was saved.

Everyone rushed to the spring to see the freshly caught fish and were overjoyed. The maidens were celebrated for saving the island when men's strength did not. Everyone ate the fish! Happy time!
Historical Context:
Here you can see the distance of how far the lemon peels traveled under the island. And the shape of the bay. Legends are always fun to explore of how something came to be.

Hello Dear Reader! I hope you enjoy my content? I am curious to hear your thoughts. Do you like what you see?
I'll be grateful for your feedback. Please feel free to leave a comment. Thank you
-
 @ 39cc53c9:27168656
2024-04-17 16:53:09
@ 39cc53c9:27168656
2024-04-17 16:53:09I've been thinking about how to improve my seed backup in a cheap and cool way, mostly for fun. Until now, I had the seed written on a piece of paper in a desk drawer, and I wanted something more durable and fire-proof.
After searching online, I found two options I liked the most: the Cryptosteel Capsule and the Trezor Keep. These products are nice but quite expensive, and I didn't want to spend that much on my seed backup. Privacy is also important, and sharing details like a shipping address makes me uncomfortable. This concern has grown since the Ledger incident^1. A $5 wrench attack^2 seems too cheap, even if you only hold a few sats.
Upon seeing the design of Cryptosteel, I considered creating something similar at home. Although it may not be as cool as their device, it could offer almost the same in terms of robustness and durability.
Step 1: Get the materials and tools
When choosing the materials, you will want to go with stainless steel. It is durable, resistant to fire, water, and corrosion, very robust, and does not rust. Also, its price point is just right; it's not the cheapest, but it's cheap for the value you get.
I went to a material store and bought:
- Two bolts
- Two hex nuts and head nuts for the bolts
- A bag of 30 washers
All items were made of stainless steel. The total price was around €6. This is enough for making two seed backups.
You will also need:
- A set of metal letter stamps (I bought a 2mm-size letter kit since my washers were small, 6mm in diameter)
- You can find these in local stores or online marketplaces. The set I bought cost me €13.
- A good hammer
- A solid surface to stamp on

Total spent: 19€ for two backups
Step 2: Stamp and store
Once you have all the materials, you can start stamping your words. There are many videos on the internet that use fancy 3D-printed tools to get the letters nicely aligned, but I went with the free-hand option. The results were pretty decent.

I only stamped the first 4 letters for each word since the BIP-39 wordlist allows for this. Because my stamping kit did not include numbers, I used alphabet letters to define the order. This way, if all the washers were to fall off, I could still reassemble the seed correctly.
The final result
So this is the final result. I added two smaller washers as protection and also put the top washer reversed so the letters are not visible:

Compared to the Cryptosteel or the Trezor Keep, its size is much more compact. This makes for an easier-to-hide backup, in case you ever need to hide it inside your human body.
Some ideas
Tamper-evident seal
To enhance the security this backup, you can consider using a tamper-evident seal. This can be easily achieved by printing a unique image or using a specific day's newspaper page (just note somewhere what day it was).
Apply a thin layer of glue to the washer's surface and place the seal over it. If someone attempts to access the seed, they will be forced to destroy the seal, which will serve as an evident sign of tampering.
This simple measure will provide an additional layer of protection and allow you to quickly identify any unauthorized access attempts.
Note that this method is not resistant to outright theft. The tamper-evident seal won't stop a determined thief but it will prevent them from accessing your seed without leaving any trace.
Redundancy
Make sure to add redundancy. Make several copies of this cheap backup, and store them in separate locations.
Unique wordset
Another layer of security could be to implement your own custom mnemonic dictionary. However, this approach has the risk of permanently losing access to your funds if not implemented correctly.
If done properly, you could potentially end up with a highly secure backup, as no one else would be able to derive the seed phrase from it. To create your custom dictionary, assign a unique number from 1 to 2048 to a word of your choice. Maybe you could use a book, and index the first 2048 unique words that appear. Make sure to store this book and even get a couple copies of it (digitally and phisically).
This self-curated set of words will serve as your personal BIP-39 dictionary. When you need to translate between your custom dictionary and the official BIP-39 wordlist, simply use the index number to find the corresponding word in either list.
Never write the idex or words on your computer (Do not use
Ctr+F) -
 @ 1cb14ab3:95d52462
2025-01-03 19:25:50
@ 1cb14ab3:95d52462
2025-01-03 19:25:50Sheet Metal, Rivets. [12” x 11” x 18”]
This project was first exhibited in 2015 in Boulder, Colorado.
Prints available on request. DM for inquiries on the sculpture.
Artist Statement
Organimetal: Where Industry Meets Nature
Organimetal examines the paradoxical relationship between human industry and the natural world, reflecting on humanity’s dual role as both creator and disruptor. This work fuses bold industrial materials, such as sheet metal and rivets, with an organic form, evoking the tension between the rigid, mechanical qualities of human innovation and the fluid, unpredictable patterns of nature.
At the heart of this sculpture lies a critique of the way human industry often seeks to dominate the natural world while still drawing inspiration from it.
The form’s flowing, natural curves juxtapose the cold, utilitarian surface of the metal, highlighting this inherent contradiction. The industrial materials, traditionally associated with mass production and control, are reimagined here as part of a delicate, organic structure, prompting viewers to question the impact of industry on the Earth.
This sculpture serves as both an artistic exploration and a personal milestone. It represents my second foray into metalworking and the first piece to ignite my love for the medium. As viewers engage with Organimetal, they are encouraged to reflect on their own perceptions of progress, balance, and the unintended consequences of our attempts to shape the world around us.
Photos








Other Sculptures by Hes
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ f0fcbea6:7e059469
2025-01-03 19:19:01
@ f0fcbea6:7e059469
2025-01-03 19:19:01História
A história da "Avicultura", ou simplesmente a criação de galinhas, data de muitos séculos. Segundo os historiógrafos o início da domesticação da galinha deu-se no continente asiático. Essa galinha, domesticada, primeiramente foi utilizada como animal de briga ou como objeto de ornamentação e somente no final do século XIX sua carne e os seus ovos passaram a ser apreciados. O início do século XX as encontrou a tal ponto valorizadas que chegaram a representar uma fonte de renda adicional, tanto nos sítios como nas fazendas. Estimulados pelo aspecto econômico, os avicultores começaram a tentar novos acasalamentos entre raças diferentes, visando o aprimoramento da espécie.
No Brasil, a galinha foi introduzida pelos portugueses, no início do século XX. Nesta época ainda eram criadas soltas nos quintais ou nos arredores das casas, e se alimentavam com restos de comida caseira, grãos, insetos e outros bichinhos.
A partir da década de 30, houve um grande progresso na criação de galinhas. Um dos pioneiros da avicultura em larga escala no Brasil foi Charles Toutain, engenheiro agrônomo francês, proprietário da Granja do Mandi, que introduziu várias práticas modernas em nosso meio. Nesta granja em Itaquaquecetuba (SP), ele manteve reprodutores de boas linhagens, alta produção de ovos e incentivou a criação de galinhas pelo fornecimento de famosas quinas (quatro galinhas e um galo). Seu grande galinheiro Alexandre construído em 1928, tinha 70m por 4,5m e lotação de 800 poedeiras de primeiro ano; o Bonaparte, de 1929, abrigava 1.000 poedeiras e tinha 70m por 5m. O César construído em 1934-35 tinha 60m por 8,5m e abrigava 1.200 poedeiras. Outros pioneiros que vieram após Toutain foram Carlos Aranha e Luís Emanuel Bianchi, além de avicultores com empresas menores como o dr. Oswaldo de Sequeira, do Rio, que escreveu amplamente sobre a criação de galinhas e traduziu a Cartilha Avícola, de Biedma, incorporando muito de sua experiência. Outra publicação que não deve ser esquecida é a revista Chácaras e Quintais, criada e dirigida por Amadeu Barbiellini, assim como O Campo de Eurico Santos.
Após a Segunda Grande Guerra a modernização da avicultura industrial americana, com a adoção do uso de hibridos, das linhagens muito refinadas e do confinamento estrito, repercutiu em São Paulo pelo esforço da Cooperativa Agrícola de Cotia. A partir da década de 60 passa a ocorrer a implantação de novas técnicas no Brasil com a vinda de firmas produtoras de linhagens de alta qualidade dos E.U.A. Todo esse desenvolvimento ocorrido para a modernização da avicultura brasileira só foi possivel também graças à colaboração do Instituto Biológico de São Paulo que fez estudos completos das doenças de aves que aqui dificultavam ou impediam a criação em larga escala. Ele identificou c erradicou a pulorose. Mais tarde, o Departamento da Produção Animal, hoje Instituto de Zootecnia deu valiosa contribuição no que se refere ao manejo das aves, suas instalações e seu arraçoamento. Outro núcleo que se desenvolveu com muito brilho foi o da Escola Superior de Agricultura Luiz de Queiroz, em Piracicaba. Unidos os esforços de todos estes órgãos foi possível a introdução das matrizes de grande produtividade e das técnicas de criação descobertas após a Segunda Guerra.
Portanto, no país, a avicultura é a atividade pecuária tecnicamente mais avançada. As criações estão ligadas a vários setores industriais que formam um grande complexo passando pelos reprodutores de raças puras, chamados de "avozeiros", que fornecem pintos para os matrizeiros que trabalham com reprodução onde o produto final são os "híbridos" denominados pintos de um dia. Estes pintos são vendidos aos criadores comerciais de frangos de corte ou de galinhas para produção de ovos. As áreas de atuação de cada setor são bem definidas. A seqüência avozeiro-matrizeiro-criador comercial pode ser constituída por uma ou várias empresas, sendo esta seqüência diferenciada para a produção de frangos ou de ovos. Para a criação de frangos, tanto os machos como as fèmeas são aproveitados e, para a postura somente as fêmeas são utilizadas e os machos eliminados.

-
 @ 3c984938:2ec11289
2024-04-16 17:14:58
@ 3c984938:2ec11289
2024-04-16 17:14:58Hello (N)osytrs!
Yes! I'm calling you an (N)oystr!
Why is that? Because you shine, and I'm not just saying that to get more SATs. Ordinary Oysters and mussels can produce these beauties! Nothing seriously unique about them, however, with a little time and love each oyster is capable of creating something truly beautiful. I like believing so, at least, given the fact that you're even reading this article; makes you an (N)oystr! This isn't published this on X (formerly known as Twitter), Facebook, Discord, Telegram, or Instagram, which makes you the rare breed! A pearl indeed! I do have access to those platforms, but why create content on a terrible platform knowing I too could be shut down! Unfortunately, many people still use these platforms. This forces individuals to give up their privacy every day. Meta is leading the charge by forcing users to provide a photo ID for verification in order to use their crappy, obsolete site. If that was not bad enough, imagine if you're having a type of disagreement or opinion. Then, Bigtech can easily deplatform you. Umm. So no open debate? Just instantly shut-off users. Whatever, happened to right to a fair trial? Nope, just burning you at the stake as if you're a witch or warlock!

How heinous are the perpetrators and financiers of this? Well, that's opening another can of worms for you.
Imagine your voice being taken away, like the little mermaid. Ariel was lucky to have a prince, but the majority of us? The likelihood that I would be carried away by the current of the sea during a sunset with a prince on a sailboat is zero. And I live on an island, so I'm just missing the prince, sailboat(though I know where I could go to steal one), and red hair. Oh my gosh, now I feel sad.
I do not have the prince, Bob is better! I do not have mermaid fins, or a shell bra. Use coconut shells, it offers more support! But, I still have my voice and a killer sunset to die for!
All of that is possible thanks to the work of developers. These knights fight for Freedom Tech by utilizing FOSS, which help provides us with a vibrant ecosystem. Unfortunately, I recently learned that they are not all funded. Knights must eat, drink, and have a work space. This space is where they spend most of their sweat equity on an app or software that may and may not pan out. That brilliance is susceptible to fading, as these individuals are not seen but rather stay behind closed doors. What's worse, if these developers lose faith in their project and decide to join forces with Meta! 😖 Does WhatsApp ring a bell?
Without them, I probably wouldn't be able to create this long form article. Let's cheer them on like cheerleaders.. 👉Unfortunately, there's no cheerleader emoji so you'll just have to settle for a dancing lady, n guy. 💃🕺
Semisol said it beautifully, npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
If we want freedom tech to succeed, the tools that make it possible need to be funded: relays like https://nostr.land, media hosts like https://nostr.build, clients like https://damus.io, etc.
With that thought, Onigirl is pleased to announce the launch of a new series. With a sole focus on free market devs/projects.
Knights of Nostr!
I'll happily brief you about their exciting project and how it benefits humanity! Let's Support these Magnificent projects, devs, relays, and builders! Our first runner up!
Oppa Fishcake :Lord of Media Hosting
npub137c5pd8gmhhe0njtsgwjgunc5xjr2vmzvglkgqs5sjeh972gqqxqjak37w
Oppa Fishcake with his noble steed!
Think of this as an introduction to learn and further your experience on Nostr! New developments and applications are constantly happening on Nostr. It's enough to make one's head spin. I may also cover FOSS projects(outside of Nostr) as they need some love as well! Plus, you can think of it as another tool to add to your decentralized life. I will not be doing how-to-Nostr guides. I personally feel there are plenty of great guides already available! Which I'm happy to add to curation collection via easily searchable on Yakihonne.
For email updates you can subscribe to my [[https://paragraph.xyz/@onigirl]]
If you like it, send me some 🧡💛💚 hearts💜💗💖 otherwise zap dat⚡⚡🍑🍑peach⚡⚡🍑 ~If not me, then at least to our dearest knight!
Thank you from the bottom of my heart for your time and support (N)oystr! Shine bright like a diamond! Share if you care! FOSS power!
Follow on your favorite Nostr Client for the best viewing experience!
[!NOTE]
I'm using Obsidian + Nostr Writer Plugin; a new way to publish Markdown directly to Nostr. I was a little nervous using this because I was used doing them in RStudio; R Markdown.
Since this is my first article, I sent it to my account as a draft to test it. It's pretty neat. -
 @ 39cc53c9:27168656
2024-03-28 12:25:32
@ 39cc53c9:27168656
2024-03-28 12:25:32Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ d4bad8c2:b57136de
2025-01-03 19:03:21
@ d4bad8c2:b57136de
2025-01-03 19:03:21Dōgen's 51st Fascicle in the Shobogenzo is centered around a conversation between an unnamed Minister and Master Kokaku. Mitsugo means "secret talk."
The Case:
Great Master Kokaku of Ungo-zan mountain, the story goes, is served offerings by a government official, who asks, "The World-Honoured One has secret talk; for Mahākāśyapa nothing is concealed. What is the World-Honoured One's secret talk?"
The Great Master calls out, "Minister!"
The man responds.
The Great Master says, "Do you understand or not?"
The official says, "I do not understand."
The Great Master says, "If you do not understand, it is the World-Honoured One's secret talk. If you understand, it is Mahākāśyapa's state of nothing being concealed."
Gudo Nishijima & Chodo Cross. Master Dogen's Shobogenzo: Book 3. Windbell Publications, 1997.p. 79.
Kokaku was a posthumous title. His name in Chinese is Yunju Daoying (雲居道膺) and he died in the very early 900s. Kokaku was a student of Dongshan Liangjie and is the thirty-ninth ancestor.
Kokaku is adding more confusion here on purpose. He wants the Minister to take a leap. The Minister won't and does not.
It's also important to understand that often (if not each time) there is a government official (minister) in these stories that there is a sort of mocking sense to the interaction. In old China, officials memorized Confucian ideology and wrote tests on it. 100% an intellectual exercise. They are always stumped in these koan dialogues with Masters and even by tea and bun sellers shilling hack-Zen on the road.
While it may be tempting to take a position (side) here and think that not understanding is better than understanding or that understanding is better than not understanding. Don't. The tension between these two is the point and that point is to give it all up and jump off the cliff (metaphorically).
Kokaku is pointing to the same type of not knowing that Dizang meant when he said, "Not knowing is most intimate" and equally he is pointing to something else that is going on with Mahākāśyapa.
Mahākāśyapa was the first to receive transmission (of absolutely nothing at all) from Shakyamuni Buddha who twirled a flower, saw Mahākāśyapa break into a smile and gave him transmission. But what was transmitted and how? The word transmission is misleading. Simply, you can not receive (transmission) of something that you already possess, particularly if it is inherent. So, what is transmitted and why use that word?
Dōgen goes on in more detail and has some cautions. I'd like to pick up the fascicle on page 82 where he says:
In sum, the World-Honoured One has secret talk, secret action, and secret experience. Stupid people, however, think that "secret" means other people do not know but the subject knows, and that there are initiated people and uninitiated people.
...
Secret talk, secret will, secret action, and so on in the Buddha-Dharma are beyond reasoning. When we meet a human being, that is just when we hear secret talk and talk secret talk. We know ourselves, we know secret action. Moreover, a Buddhist [Sage] is able thoroughly to penetrate and to discern the secret will and the secret talk described previously. Remember, in the momentary state of a Buddhist [Sage], secret words and secret acts vie to be realized. What has been described as "secret" is the truth of immediacy.
Gudo Nishijima & Chodo Cross. Master Dogen's Shobogenzo: Book 3. Windbell Publications, 1997. p. 82-83 (I replace Patriarch with [Sage] simply to ungender the text.)
Taking up Zen as a practice, we sit upright with a straight back and listen to the cries of the world. Listening to the cries of the world is identical to hearing our True self. This listening is not limited to the ears. It is our eyes, ears, nose, tongue, body, and mind. Those are our senses and they are the only means we have to understand the world. All the world, you included. Especially you.
I once said to a friend: "When you practice like this, in no particular order: you uncover your own bullshit, have a laugh or a cry over it, merge with it, and see right through it. When you see through your own self, you see through all the others because they are one and the same. Not two."
I've said too much here already and the point of practice is not to be given all the answers but to discover it for yourself. Please use your common sense to find ordinary Mind. Common sense and ordinary mind are not two.
The flower is still twirling the Dharma is still twirling you.
SP // DF
-
 @ d57360cb:4fe7d935
2025-01-03 18:30:04
@ d57360cb:4fe7d935
2025-01-03 18:30:04Encountering Ego
If you’ve ever stepped onto the mats of a Jiu Jitsu gym, you’ve likely heard the mantra, “Leave your ego at the door.” When I first started this martial art, this notion puzzled me. I embarked on this journey with the intentions to toughen up, to win, and to prove myself — all driven by ego. Perhaps you, too, entered this realm with similar aspirations: to get fit, to learn self-defense, or to compete — all motivated by ego. Whatever your reason for starting, there’s one certainty: you will confront your ego before, during, and after your journey.
Your ego manifests in various forms — the exhilaration when you secure your first submission, the satisfaction of dominating an opponent in a roll, the complacency of rushing through techniques, or the inclination to stick to a familiar style. Conversely, it’s the voice that whispers doubts, telling you that you’re not good enough, that your opponent is inherently superior. It’s the pang of shame and helplessness when you’re effortlessly subdued. Your ego lurks whenever you feel either superior or inferior to another — it is your true opponent.
The opponent is you.
It’s never your adversary that defeats you; rather, it’s your reactions to what they reveal within you. Each encounter exposes facets of yourself — testing your patience, highlighting deficiencies in technique, inflating your ego, or humbling you. Ultimately, your opponent imparts valuable lessons, and it’s your responsibility to internalize them. Winning or losing becomes secondary; the crux lies in acknowledging your missteps and pride. Detaching personal emotions and scrutinizing your performance pave the path to growth. True progress emerges from accepting your imperfections and vulnerabilities, relinquishing your ego, and venturing into uncharted territory.
You’ll come to realize that what you thought you knew merely scratches the surface. In the depths of Jiu Jitsu, the fundamentals are anything but basic. So, heed the wisdom of the ages — leave your ego at the door, and witness how much further you can evolve.
-
 @ 44dc1c2d:31c74f0b
2024-03-25 21:41:15
@ 44dc1c2d:31c74f0b
2024-03-25 21:41:15Chef's notes
When adding things like extra veggies, if you don't want them to be mush, consider roasting veggies in the oven and only adding them near then end of the cook time. The same is generally true for meats.
While Parmesan is traditional, almost any cheese will work.
Choose your broth based on your needs (IE a veggie stock to make it more vegetarian friendly), water or more stock can be used in place of wine if need be.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 25 min
- 🍽️ Servings: 4 mains or ~6 appetizers
Ingredients
- 1 onion, DIced
- ¼ cup butter
- 2 cups arborio rice
- 1 cup white wine
- 6 to 8 cups warm chicken broth
- 1 cup grated Parmigiano-Reggiano cheese
Directions
- In a large saucepan over medium heat, soften the onion in half the butter. Add the rice and cook for 1 minute, stirring to coat well. Add the white wine and reduce until almost dry.
- Add the broth, about 1 cup at a time, stirring frequently until the liquid is completely absorbed before adding more broth. Season with salt and pepper. Cook for 18 to 22 minutes or until the rice is al dente. Add broth, as needed.
- Take off the heat and add the cheese, the remaining butter and the toppings of your choice. Stir until the texture is very creamy. Adjust the seasoning.
- Dish up, sprinkle with a little Parmesan cheese, if desired. Enjoy.
-
 @ fe7af447:9594a50b
2025-01-03 18:14:40
@ fe7af447:9594a50b
2025-01-03 18:14:40Hawaii is famous for its vibrant and dazzling fireworks displays every New Year’s Eve, a cherished tradition that brings ohana (families) and neighbors together to celebrate hope and renewal. Fireworks are a staple of New Year’s Eve in Hawaii, where kids—and let’s be real, even the “big kids” (yes, adults, that includes you!)—enthusiastically pop everything from massive 10k and 20k firecrackers to spectacular aerial displays. It’s a friendly competition as neighborhoods across the islands light up the night, showing off who has the most impressive fireworks.
Check out this video to see Hawaii’s incredible fireworks culture in action: Watch here
Even after fireworks were officially "banned" in Hawaii in 2011, the tradition persisted. People found ways to keep the spirit alive, proving that you can’t extinguish a cultural flame. You can ban it, but the people will keep fighting to preserve it. It’s almost like Bitcoin in a way—you can try to control it, but you can’t stop a movement rooted in culture, passion and resilience.
But this year, tragedy (covered news footage) struck in Honolulu’s Kalihi neighborhood, leaving heartbreak in its wake.
A tragic fireworks explosion claimed the lives of three women and left over 20 others injured, including children as young as 3 years old. The heartbreaking incident unfolded when a large firework tipped over, igniting nearby fireworks and triggering a devastating blast that turned the area into what witnesses described as a warzone.
Victims suffered severe burns and shrapnel injuries, with two women tragically losing their lives at the scene and a third passing away later in the hospital. This horrific event serves as a sobering reminder of the unpredictability and fragility of life, leaving a community in mourning and forever changed.
Families are now left fighting for their lives, their futures forever altered. This tragedy is a sobering reminder of how quickly life can change, underscoring the importance of cherishing every moment and the people we hold dear. Life will never be the same for those affected, and our thoughts are with them during this unimaginably difficult time.
For me, this incident serves as a poignant reminder of how fleeting and precious life can be. It’s easy to get caught up in the chaos of everyday life, the hustle and bustle, and take the people around us for granted. I'm not going to lie, I always do. But moments like this underscore the importance of pausing to be grateful for what we have and, more importantly, who we have.
To my kids, and to anyone reading this, my advice is simple: embrace life with joy and gratitude. Don’t let the little things weigh you down. Be happy, cherish every moment, and always let the people you care about know how much they mean to you. Life is unpredictable, and we never know what tomorrow may bring, so make the most of today.
Shit happens every day, and while there are many things beyond our control, I remind myself that there are steps I can take to prevent things from spiraling out of hand. Life is unpredictable, but it’s also precious. Hold your loved ones close, live with kindness and appreciation, and never lose sight of what truly matters. Happiness isn’t found in material things—it’s found in the moments we create, the people we cherish, and the relationships that bring meaning to our lives.
-
 @ 1cb14ab3:95d52462
2025-01-03 17:41:13
@ 1cb14ab3:95d52462
2025-01-03 17:41:13VDMX5, iMovie, APC40 (4:48)
This project was created and first exhibited in 2015 in Boulder, CO.
Artist Statement
Untoward Equilibrium is an experimental short film that delves into the complex and often strained relationship between humans and the natural world. Through a dynamic interplay of visuals, sound, and digital manipulation, the film investigates themes of migration, cultural destruction, and the often futile efforts to rebuild in the face of inevitable change. Utilizing tools such as VDMX 5, iMovie, and the APC40, I aimed to weave a narrative that reflects the cyclical and untidy balance between human intervention and the forces of nature.
The film’s abstract visuals and layered soundscapes evoke a sense of unease, suggesting that the equilibrium between the two is never quite stable. It examines the patterns of regime changes, revolutions, and war, exploring how these human conflicts mirror the predator-prey dynamics of the natural world.
Just as predators and prey shape ecosystems through cycles of survival and dominance, human societies grapple with cycles of power, upheaval, and renewal.
Through this lens, the work considers ongoing processes of disintegration and reconstruction, drawing parallels between societal collapse, cultural upheaval, and the relentless forces of nature. By blending the organic with the synthetic, Untoward Equilibrium reflects the fragility of human civilizations and the environments we inhabit, questioning whether true harmony between the two is ever achievable, or if we are destined to remain in a perpetual state of imbalance. This film seeks to provoke reflection on how the forces of war, revolution, and ecological interplay shape our understanding of the world and our place within it.
Stills from the film







Watch ‘Untoward Equilibrium’
nostr:naddr1qqrk5vj8v45xkagpzpmhxue69uhkummnw3ezuamfdejsygquk99txdv8dly7lsmasw969p70zlj6mnxtyzlk6j0em2tft4fyvgpsgqqqskasumlfl9
More from Hes:
All images and video are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 44dc1c2d:31c74f0b
2024-03-23 22:14:17
@ 44dc1c2d:31c74f0b
2024-03-23 22:14:17Chef's notes
Recommend kosher salt for this recipe as it has a better flavor with the cream.
If you have foam, either skim the top or you can use a torch to get a glass smooth finish on the top.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 40 min
- 🍽️ Servings: 6
Ingredients
- 2 cups heavy cream
- 10 tablespoons sugar, divided
- 1 vanilla bean (or 1 teaspoon vanilla extract)
- 4 large egg yolks
- 1/2 teaspoon vanilla extract
- 1/4 teaspoon kosher salt
- For the Brûlée topping:
- 4 tablespoons sugar (2 teaspoons per ramekin)
Directions
- Preheat oven to 325°F with a rack in the middle position: Arrange six 4-ounce ramekins in a 9x13 baking dish and set aside.
- Prepare the vanilla bean: Split the vanilla bean in half and scrape out the seeds with the dull (non-cutting) side of a paring knife.
- Warm the cream: In a medium saucepan, combine heavy cream, 4 tablespoons of the sugar, vanilla bean pod, vanilla bean seeds, and salt. Cook over medium heat, until it begins to simmer.
- Infuse the cream: Once the cream begins to simmer, remove the pan from heat, cover, and let stand for 15 minutes to allow the vanilla bean to infuse into the cream. (If you’re replacing the vanilla bean with vanilla extract, skip this step.)
- Separate the eggs and whisk with sugar: When your cream is almost done infusing, separate your eggs. Place the yolks in a medium-sized mixing bowl; save the whites for another purpose. Whisk the remaining 6 tablespoons of sugar into the yolks. (Don't combine the eggs and sugar too soon before you mix it with the warm cream because the sugar binds with the water in egg yolks, which constricts the proteins in yolks and creates eggy lumps. And you don't want eggy lumps in your custard!)
- Temper the yolks and mix with the cream: While whisking the yolks continuously, slowly add one ladle (about 1/4 or 1/3 cup) of hot cream in a thin stream. Do this two or three more times. While whisking, slowly add the remaining cream to the egg mixture, followed by the vanilla extract. Strain the mixture through a fine mesh sieve into a second mixing bowl and discard the vanilla bean pod (this also helps strain out any small bits of egg that may have curdled).
- At this point, the custard can be cooled and stored for up to 5 days. If you choose to bake them right from the fridge, you will probably need to add a couple of extra minutes.
- Fill the ramekins: Divide the custard between the ramekins, filling each one just up to the inner rim, or about three-quarters of the way full.
- Fill the hot water bath: Bring a kettle or pot of water to a boil. Fill the pan with the hot water until the water comes about two-thirds of the way up the side of the ramekins. Avoid splashing water into the custards.
- Bake the custards: Transfer the pan with the custards to the oven and bake for 38 to 40 minutes. When ready, the crème brûlée should have a uniform jiggle in the middle; when you touch the center, it should spring back just a bit. If the sides hold firm but the center sloshes, they aren’t quite done yet. If they are set like Jell-O, they’ve overbaked, although they will still be delicious! Chill them, brûlée them, eat them, love them and celebrate your efforts. If they have overbaked to the point that they look risen in the center, toss them, start again
- Cool and chill the custards: Remove the baking dish with the finished custards from the oven and set on a wire cooling rack. Let the custards cool in the water until you can safely pick up the ramekins by the rim with your fingers. This should take about 15 minutes, depending on how tender your fingers are. (Mine are like asbestos, so I tend to go in rather quickly.) Once removed from the water bath, let each custard rest on the cooling rack for about 15 more minutes. Use a spoon to skim any bubbles off the top, then cover each ramekin with plastic wrap and store in the fridge. Chill for at least 4 hours, or up to 4 days, before serving.
- Brûlée the custards: When ready to serve, remove the custards from fridge. Sprinkle the surface of each custard evenly with about 1 teaspoon of granulated sugar. Rotate the custard as you sprinkle to make sure the sugar evenly coats the surface. Ignite your torch. Hold the flame about 4 inches from the surface of the sugar. Using a circular motion, move the flame across the surface. The sugar will at first begin to bead up, and then will eventually solidify into a hard sugar crust. You want to make sure all the sugar granules have melted, and the sugar has at least a tint of caramel color. The longer you torch the surface, the darker it will become and the more bitter the sugar crust will be. Sprinkle each of the custards with an additional teaspoon of sugar and brûlée the surface again.
-
 @ 0b118e40:4edc09cb
2025-01-03 16:27:58
@ 0b118e40:4edc09cb
2025-01-03 16:27:58I was reading this book Too Big to Jail by Chris Blackhurst that talks about one of the biggest bank scandals of the century - billions of money laundered through HSBC for the Sinaloa cartel, the world’s largest drug cartel that supplies 25% of illegal drugs to the US. HSBC walked away with a $1.9 billion fine in 2012 and no one was charged or imprisoned. Meanwhile, Joaquín "El Chapo" Guzmán, the cartel’s leader, was sentenced to life in prison + 30 years in the US, with $12.6 billion of his assets forfeited.
Interestingly, HSBC’s dark history dates back to over 150 years. I first read in John Potash’s Drugs as Weapons Against Us about how HSBC was established to serve the opium trade. Chris Blackhurst expands on this story. HSBC’s founder, Thomas Sutherland, had no banking experience but leveraged his trade expertise and British imperial backing to lead a thriving merchant business alongside opium business exporting to China. When China resisted, the British Empire doubled down and escalated tensions, resulting in the Opium Wars, forcing China to accept opium trade and China ceding Hong Kong to Britain for a hundred years
With trade comes the need for fund transfer, hence Sunderland founded HSBC in Hong Kong, to handle foreign transactions. Ironically, 150 years later, HSBC was caught laundering funds for illegal drugs for the Sinaloa cartel between 2003 and 2010. During this period, HSBC's chairman, Stephen Green, an Anglican priest who authored Ethical Capitalism, was never charged. Instead, he became Lord Green and served as the UK’s Minister of State for Trade and Investment.
Chris Blackhurst aptly summarizes this hypocrisy - "HSBC, the fueller of evil, holds its customers to strict standards, yet it enabled cartels to launder metric tonnes of cash."
Other banks and their crimes
The 1MDB scandal:
Billions was embezzled from the Malaysian sovereign wealth fund in the 1MDB scandal. Those convicted were former Prime Minister Najib Razak who was imprisoned, but mastermind behind it Jho Low remains at large. Goldman Sachs, Deutsche Bank, and AmBank were implicated. Goldman Sachs paid a $2.9 billion fine, and Roger Ng was sentenced to 10 years in prison.Tim Lessner pleaded guilty and cooperated with the authorities.
Wells Fargo Fake Accounts Scandal:
From 2002 to 2016, Wells Fargo employees opened millions of fake accounts in customer’s names without their consent to meet aggressive sales quotas.
Libor Interest Rate Rigging:
Major banks, including Barclays, UBS, Citibank and JPMorgan Chase, colluded to manipulate the London Interbank Offered Rate (Libor) which is a global benchmark for interest rates. This impacted trillions of dollars in global financial products.
I'm sure there is more to the list based on what we know and don't know.
Every time Bitcoin gets criticized for “money laundering,” I think of these scandals and the roles that corrupted governments play. Millions of people have suffered from the systemic corruption of traditional finance and they deserve financial liberation.
A 2020 report from Chainalysis indicated that illicit transactions (including money laundering, ransomware payments, and fraud) accounted for only less than 1% of all Bitcoin transactions, which is a speck compared to the scale of corruption in the traditional financial system. The United Nations Office on Drugs and Crime (UNODC) estimates that between 2% and 5% of global GDP , which accounts for trillions of dollars, is laundered each year through the traditional financial systems.
Chris Blackhurst was right when he said those who are “too big to jail” tend to get away.
-
 @ 5c8a5765:4fc5edee
2024-03-22 17:44:23
@ 5c8a5765:4fc5edee
2024-03-22 17:44:23"Мне-то что с того, что за мной следят? Мне же скрывать нечего". Но постойте, может быть вы...
Read in English
tl;dr: Отсутствие приватности угрожает сексуальным, расовым, национальным меньшинствам, женщинам, мужчинам, небинарным, атеистам, активист(к)ам, бедным, инвалидам, школьни(кам/цам), представителям социальных профессий, любым покупателям, человеку в целом и даже демократии.
...Чёрнокож(ий/ая)?
Компания Palentir, занимающаяся разработкой искусственного интеллекта, продает данные упреждающего наблюдения полиции Лос-Анджелеса, чтобы использовать дорожные камеры для целенаправленного расового профилирования (обыска исключительно чернокожих для превентивного расследования преступлений) [1]. Если вы участвовали в протестах BLM, ФСБ также грубо превышает свои полномочия ради слежки за вами [52].
...Мусульман(ин/ка)?
Salaat First, приложение, напоминающее мусульманам о времени молитвы, продает пользовательские данные ФБР и ICE, чтобы постоянно отслеживать местоположение пользователей [2]. При этом в Гуантанамо пытают заключенных мусульман без суда и следствия [3].
...Атеист/ка?
Евангелисты начали использовать цифровое наблюдение, чтобы выслеживать, где живут "ещё необращенные" в христианство [57].
...Не гетеросексуальны или не цисгендерны?
Grindr продает данные о местонахождении пользователей [4]: проданные данные использовались для увольнения священников-геев [5]. По данным New York Post, они "позволяли неизвестным третьим лицам узнавать конфиденциальную информацию о пользователях, в том числе о том, с кем они встречаются, где живут и работают, где проводят свободное время" [6].
Владельцы Grind поспешно выставили сервис на продажу, когда раскрылось, что он собирает ещё и медицинские данные пользователей и делятся ими с другими компаниями [7] (ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8]). Далеко не всем трансгендерным, небинарным или интерсекс-личностям хотелось бы ходить с табличкой "МОИ ГЕНЕТАЛИИ НЕ СООТВЕТСТВУЮТ ГЕНДЕРУ" на груди, но отсутствие приватности даёт вам именно это.
Раскрывая вашу идентичность кому попало, вы ставите свою свободу (если быть не-цисгетеро нелегально в вашей стране) и жизнь под угрозу.
...Человек с маткой?
Отслеживание мобильной геолокации используется группами против абортов. Цитата из Politico: "Одна рекламная фирма хвасталась в 2015 году, что может "пометить все смартфоны, входящие и выходящие из почти 700 клиник Planned Parenthood" [9]. При этом на 2022 г. 40% стран мира имели юридическую ответственность за проведение аборта без крайне специфических причин [10]. Не стоит также забывать, что противни(ки/цы) абортов очень воинственно настроены: существует немало насилия и даже терроризма против проводящих и совершающих аборты [11][12].
...Активист/ка?
Google передал индийской полиции данные 21-летней климатической активистки, которая набирала в Google Docs информацию о фермерских протестах (оказалась арестована) [13]. Protonmail передал данные экоактивиста* Французской полиции (оказался арестован) [14]. Facebook, Instagram и X (Twitter) предоставляют доступ к данным для слежки за активистами (в особенности не белыми) — некоторые из них не отказалась от сотрудничества даже после разоблачения [15]. Наши правительства также крайне заинтересованы в предотвращении протестов ещё до того, как они произойдут.
...Нонкомформист/ка?
Например, если вы консерватор/ка, вы можете оказаться под сапогом цензуры: компания Gotcha SEO провела исследование 50 противоречивых ("острых") поисковых запросов в Google и обнаружила, что только 5 % результатов относятся консервативным сайтам, по сравнению с 31,8 % левых и 63,8 % нейтральных [16][17]. По моему личному опыту (особенно ощутилось в ходе написания этой статьи), Google, Bing и прочие поисковики от крупных компаний (в сравнении с, например, Brave Search) также нехотя выдают результаты на тему того, как крупные компании продают ваши личные данные.
...Кита(янка/ец)?
В 2019 году YouTube был пойман на автоматическом удалении комментариев, содержавших что-либо про "50 Cent (Party)" (китайская "фабрика троллей" — команды людей, наполняющие комментарии соц. сетей прогосударственными мнениями за небольшую оплату) [18], или обвинения Китайской Коммунистической партии в бандитизме [19]. А ещё Tik Tok крадет данные ваших детей и продает их вашему (китайскому) правительству [20]. А ещё Google разрабатывает специальный зацензурированный поисковик специально для Китая [21].
...Человек с мужским гендером в документах?
Если в вашей стране есть воинский призыв, с подавляющим шансом он будет обязателен только для мужчин [22] (это — дискриминация). Чтобы отправить вас в армию или на войну, вас будут отслеживать по телефону, передвижению автомобилей [23], камерам с распознаваниям лиц [24] и проч. Уклонение — наказывается, вплоть до тюрьмы и нарушения прав человека [25][26].
...Анархист/ка?
Google Maps активно скрывают любые изображения протестов и даже плохих условий жизни [27]. Google Ads и Play Market убирают оппозиционный контент по запросам государства (например, российского) [28][29]. YouTube активно блокирует каналы и видео, освещающие критику правительств [30], протесты [31] или государственные пытки [32] — особенно в бедных странах. (См. также пункт "активист/ка?".)
...За Палестину?
Социальные сети активно блокируют про-палестинские точки зрения [33].
...Имеете особое состояние здоровья?
Аптеки передают ваши медицинские данныеп полиции без ордера на обыск [34]. Как уже было сказано, на чёрном рынке ваши мед. данные стоят в 10-40 раз дороже данных вашей кредитной карты [8].
...Когда-либо что-нибудь покупали?
Капитализм — это одна из главных опасностей при продаже ваших личных данных. Многие крупные компании используют информацию о вас, чтобы оценить ваш доход, продать вам товары, которые вам на самом деле не нужны [36][37][38], или манипулировать ценами [37].
- Например, интернет-магазины знают, что люди с низким доходом чаще совершают срочные покупки, поэтому они устанавливают для них более высокие цены и отменяют скидки [39][40].
- Некоторые финансовые и страховые компании используют социальные графики для определения процентных ставок и страховых взносов. Это часто заставляет людей с низким доходом платить больше — данный феномен известен как "бедность-премиум" [41].
- Компания Orbitz направляет пользовате(льниц/лей) Mac в более дорогие отели, поскольку они переплачивают за электронику Apple. [42].
- Компания Target выставляет клиент(к)ам более высокие цены, когда они физически находились рядом с магазином и вряд ли ищут альтернативу. [43]
- McDonalds наняла компанию Silverpush, занимающуюся слежкой, чтобы связать аудиоданные, полученные без согласия из ее мобильного приложения, со звуками, доносящимися с Youtube или телевидения, для показа "релевантной рекламы" на разных платформах. [44]
Примерам подлых продаж нет конца — и это только те, о которых стало известно общественности!
...Мама, папа, родитель?
Родительский клуб Bounty оштрафован на 400 000 фунтов стерлингов за продажу данных пользователей — компания незаконно передавала 34,4 млн записей 39 компаниям [45]. Популярное приложение для обеспечения безопасности семьи Life360 продает точные данные о местоположении десятков миллионов своих пользователей [46]. Доверили бы вы личные данные и местоположение своих детей незнаком(цам/кам)? Ведь по некоторым данным педофил(ки/ы) [47] и люди, похищающие детей, могут использовать эти данные для нахождения жертв.
...Представитель/ница социальной профессии?
Вы работаете политик/ом, депутат/кой, учител/ем, священни/цей, куратор/ом, доктор/кой, терапевт/ом или др., из-за чего у вас хранится множество уязвимых личных данных других людей, за которые вы в ответе? Вам стоит побеспокоиться об их сохранности — ведь эти данные выгодно продаются [48].
...В отношениях?
Возможно, вы бы хотели сохранить интимные детали отношений между вами? В самой гротескной из новостей на этот счёт сотрудник австралийской пограничной службы вернул телефон гражданину после принудительного досмотра в аэропорту со словами: "Приятно было снова посмотреть нормальное порно", ссылаясь на обнаженные фотографии его девушки [49].
...Путешественни(ца/к)?
Популярная сеть отелей AirBNB разрешает устанавливать камеры внутри своих помещений [56].
...Учитесь в школе?
Бдительно следите за соблюдением правил: школы используют техники слежения, чтобы ловить и жестоко наказывать вас за использование вейпа (электронных сигарет) [51].
...Водитель/ница?
Автомобили стали компьютерами на колесах: они "обладают непревзойденной способностью смотреть, слушать и собирать информацию о том, что вы делаете и куда идете" [55]. Эта информация затем передается или продается брокерам данных, правоохранительным органам и другим лицам. Из 25 изученных марок машин 56 % передают ваши данные правоохранительным органам в ответ на неофициальный запрос, 84 % передают или продают ваши личные данные [55].
Информацию также охотно закупают страховые компании [58], а для слежки за вами её могут использовать даже ваши партнер(ы/ки) [59].
...Используете технологии для уборки?
Роботы-пылесосы не только всасывают пыль, но и сканируют ваше жилище [53]. Как бы ни было сложно в это поверить, Amazon действительно использует эти данные, чтобы заставлять вас чаще покупать то, что вам не нужно [54].
...Житель/ница страны с демократической системой?
Не так давно произошёл случай, как Facebook поймали на манипуляциях крупнейшими выборами: компания использовала наши социальные графики, чтобы исказить наше представление о реальном мире и манипулировать нашими голосами [35].
...Граждан(ин/ка) государства?
В условиях государства безобидные разговоры могут подвергнуть вас опасности, даже если вам нечего скрывать. Одна из самых шокирующих историй — упомянутый выше опыт Мохамеду Ульд Салахи [3], описанный в его мемуарах и показанный в фильме "Мавританец". Он был помещен в лагерь Гуантанамо без суда и следствия и подвергался там пыткам в течение 15 лет за телефонный звонок своему родственнику в Афганистане — он подозревался в причастности к терактам 11 сентября, хотя предыдущие 10 лет он жил в Германии.
Обычных людей арестовывают и подвергают давлению за то, чем они делятся в Интернете, даже через свои "анонимные" аккаунты, даже в демократических странах, даже если это было легальным, даже если вы не мужчина [50].
«Дайте мне шесть строк, написанных самым честным человеком, и я найду в них что-нибудь, за что его казнят на виселице» — Кардинал де Ричелиеу
...Человек?
Зачем вы носите одежду? Почему вы бы скорее предпочли непрозрачный туалет прозрачному, или спальню без камер — наблюдаемой спальне? Почему вы можете не захотеть поделиться политическими взглядами, сексуальной ориентацией или гендерной идентичностью с бабушкой, учителем или полицейским, даже если вы считаете, что в них нет ничего плохого? Почему вы можете не захотеть поделиться галереей или паролями от своих социальных сетей с тётей, социальным работником или юзером Двача, даже если вы не делали ничего незаконного напрямую?
Что если я предложу вам отправить пароли от ваших социальных сетей, банковских счетов, ваши медицинские данные, адрес и фотографии на мою электронную почту — обещаю, что не воспользуюсь ими для чего-то плохого: я просто хочу хранить их у себя на жестком диске для безопасности ваших же данных? Вам действительно нечего скрывать?
Что если я скажу, что автоматизированная слежка достигла таких масштабов, что мегакорпорации могут предполагать, о чём вы думаете [60]? Вас это беспокоит? Если да — я не буду удивлен.
Приватность всегда была частью жизни человека, обычной её частью. То, как мы живем сейчас — это крайне неестественное для человека состояние; оно никогда не было нормальным. Вам не обязательно должно быть что скрывать, чтобы захотеть не делиться всеми подробностями личной жизни с окружающими.
Заключение
Чем дольше мы отказываемся от борьбы за права на приватность, тем больше Левиафан набирает силу. Вы думаете, мир Оруэлла из «1984» был построен в одночасье? Нет! Люди жертвовали правами на конфиденциальность, анонимность, свободу информации — шаг за шагом. И первый шаг к антиутопии — это маргинализация людей, которые беспокоятся о своей анонимности: сведение их до «носителей шапочек из фольги» и тех кто «правда считает, что ОНИ читают твои эмейлы».
Так что же нам делать? Не надо думать, что "с этим ничего не поделаешь", или что "мы уже проиграли". Вместо этого нам нужно:
- Распространять информацию о том, почему приватность важна, и почему о ней стоит побеспокоиться;
- Использовать приватные, свободные, децентрализованные аналоги популярным сервисам (например, Session вместо Telegram, NOSTR вместо Twitter, DuckDuckGo вместо Google);
- Поддерживать право на приватность ради остальных (например, пока только единицы используют приватные мессенджеры — государства знают, что использующие их что-то скрывают. Но если половина населения начнёт использовать их, нельзя будет вычленить никого особенного);
- Чаще спрашивать, почему компании знают о нас так много, и как это вообще легально;
- Участвовать в политике. Политика — это не "наблюдательный спорт": если демократия не работает, мы ответственны за то, чтобы заставить её работать. Самая верхушка такого участия — это поддержка организаций, борющихся за права на приватность
«Говорить, что вам не важна приватность, ибо вам нечего скрывать — это как говорить, что вам не важна свобода слова, ибо вам нечего сказать. Но даже если вы не пользуетесь каким-то правом в данный конкретный момент, другие могут нуждаться в нём. И говорить, что вам не важно право, ибо конкретно вам сейчас оно не нужно, это самая асоциальная вещь, которую вы только можете сделать» — Эдвард Сноуден
Источники:
[1] https://theintercept.com/2021/01/30/lapd-palantir-data-driven-policing/
[2] https://www.theguardian.com/us-news/2020/dec/03/aclu-seeks-release-records-data-us-collected-via-muslim-app-used-millions
[3] https://www.npr.org/2019/11/14/778944195/a-legacy-of-torture-is-preventing-trials-at-guant-namo
[4] https://www.vox.com/technology/2023/6/16/23762403/data-odni-report-wyden
[5] https://www.vox.com/recode/22587248/grindr-app-location-data-outed-priest-jeffrey-burrill-pillar-data-harvesting
[6] https://nypost.com/2022/05/02/grindr-sold-data-about-users-precise-locations-for-years-report/
[7] https://www.theguardian.com/technology/2018/apr/03/grindr-shared-information-about-users-hiv-status-with-third-parties
[8] https://www.cyberpolicy.com/cybersecurity-education/why-medical-records-are-10-times-more-valuable-than-credit-card-info
[9] https://www.politico.com/news/2024/02/13/planned-parenthood-location-track-abortion-ads-00141172
[10] "As of 2022, countries that legally allow abortion on request or for socioeconomic reasons comprise about 60% of the world's population", https://en.wikipedia.org/wiki/Abortion_law
[11] https://en.wikipedia.org/wiki/Anti-abortion_violence
[12] https://www.justice.gov/crt/recent-cases-violence-against-reproductive-health-care-providers
[13] https://www.indiatoday.in/technology/news/story/disha-ravi-arrest-puts-privacy-of-all-google-india-users-in-doubt-1769772-2021-02-16
[14] https://proton.me/blog/climate-activist-arrest
[15] https://www.aclunc.org/blog/facebook-instagram-and-twitter-provided-data-access-surveillance-product-marketed-target
[16] https://www.gotchseo.com/google-biased/
[17] Google вообще проводит немало цензуры в своих сервисах: https://en.wikipedia.org/wiki/Censorship_by_Google
[18] https://www.taiwannews.com.tw/en/news/3933777
[19] https://www.theverge.com/2020/5/26/21270290/youtube-deleting-comments-censorship-chinese-communist-party-ccp
[20] https://www.npr.org/2020/08/04/898836158/class-action-lawsuit-claims-tiktok-steals-kids-data-and-sends-it-to-china
[21] https://www.nytimes.com/2018/08/16/technology/google-employees-protest-search-censored-china.html
[22] https://ru.wikipedia.org/wiki/%D0%92%D0%BE%D0%B8%D0%BD%D1%81%D0%BA%D0%B0%D1%8F_%D0%BE%D0%B1%D1%8F%D0%B7%D0%B0%D0%BD%D0%BD%D0%BE%D1%81%D1%82%D1%8C
[23] https://focus.ua/voennye-novosti/626982-ot-doprosov-do-operativnyh-meropriyatij-v-nacpolicii-rasskazali-o-poiske-uklonistov
[24] https://www.bbc.com/russian/features-63346138
[25] https://www.rbc.ua/ukr/styler/k-zaraz-karayut-uhilyantiv-vid-mobilizatsiyi-1707820307.html
[26] https://www.mrarchivist.com/results/entry/4591/; Запрет на голосование по причине того, что мужчина не встал на военный учет, противоречит статье 21 Всеобщей Декларации Прав Человека.
[27] https://www.nbcnews.com/id/wbna17880969
[28] https://www.rferl.org/a/google-reportedly-removes-navalny-ad-after-russian-government-complains/29478844.html
[29] https://www.theguardian.com/world/2021/sep/17/apple-and-google-accused-of-political-censorship-over-alexei-navalny-app
[30] https://nordicmonitor.com/2023/09/google-youtube-accused-of-censoring-erdogan-critics/
[31] https://www.medianama.com/2024/02/223-youtube-blocks-videos-protests-job-aspirants-bihar/
[32] https://edition.cnn.com/2007/WORLD/meast/11/29/youtube.activist/
[33] https://www.aljazeera.com/features/2023/10/24/shadowbanning-are-social-media-giants-censoring-pro-palestine-voices
[34] https://thehill.com/business/4355894-pharmacies-sharing-medical-data-without-warrant/
[35] https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
[36] https://usercentrics.com/knowledge-hub/data-is-the-new-gold-how-and-why-it-is-collected-and-sold/
[37] https://knowledge.wharton.upenn.edu/article/data-shared-sold-whats-done/
[38] https://www.eff.org/deeplinks/2020/11/visa-wants-buy-plaid-and-it-transaction-data-millions-people
[39] https://supreme.findlaw.com/legal-commentary/websites-that-charge-different-customers-different-prices.html
[40] https://policyreview.info/articles/analysis/does-everyone-have-price-understanding-peoples-attitude-towards-online-and-offline
[41] https://fairbydesign.com/povertypremium
[42] https://www.wsj.com/articles/SB10001424052702304458604577488822667325882
[43] https://www.bizjournals.com/twincities/news/2019/02/01/report-targets-app-charges-higher-prices-to.html
[44] https://www.digitaltrends.com/mobile/silverpush-app-tracking-spying-use-rises-new/
[45] https://www.theguardian.com/technology/2019/apr/12/parenting-club-bounty-fined-selling-users-data
[46] https://themarkup.org/privacy/2021/12/06/the-popular-family-safety-app-life360-is-selling-precise-location-data-on-its-tens-of-millions-of-user
[47] https://www.the-sun.com/news/3740183/paedophile-snachat-maps-victims-tesco/
[48] https://www.experian.com/blogs/ask-experian/heres-how-much-your-personal-information-is-selling-for-on-the-dark-web/
[49] https://micky.com.au/aussie-ex-pat-will-never-return-after-digital-strip-search-reveals-sex-tapes/
[50] https://www.dailymail.co.uk/news/article-11282263/Moment-police-swoop-house-devout-catholic-mother-malicious-online-posts.html
[51] https://apnews.com/article/vaping-surveillance-technology-schools-982128348c683b9d54c7a307c5b1fdc6
[52] https://www.politico.com/news/2023/05/19/fbi-surveillance-black-lives-matter-protesters-00097924
[53] https://www.welivesecurity.com/en/privacy/gathering-dust-and-data-how-robotic-vacuums-can-spy-on-you/
[54] https://www.reuters.com/markets/deals/amazons-irobot-deal-eu-antitrust-crosshairs-2023-07-06/
[55] https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
[56] https://ru.airbnb.com/help/article/3061
[57] https://newrepublic.com/article/179397/evangelical-app-targeting-immigrants-surveillance
[58] https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
[59] https://www.nytimes.com/2023/12/31/technology/car-trackers-gps-abuse.html
[60] https://www.zdnet.com/article/google-even-knows-what-youre-thinking/*Это не значит, что ProtonMail небезопасен: сервис регулярно выигрывает множество судов на тему раскрытия данных юзеро(в/к); это значит, что использования ProtonMail было недостаточно приватным (в конкретном случае — без VPN/SPN/TOR).
-
 @ 5c8a5765:4fc5edee
2024-03-22 17:24:46
@ 5c8a5765:4fc5edee
2024-03-22 17:24:46"Why do I care about privacy? I've got nothing to hide." But wait, maybe you are...
Прочти на русском
tl;dr: Lack of privacy threatens sexual, racial, national minorities, women, men, non-binary, atheists, activists, the poor, the disabled, students, social workers, any customers, humans beings in general, and even democracy.
...Black?
Palentir, an artificial intelligence company, is selling proactive surveillance data to the LAPD to use traffic cameras for targeted racial profiling (searching exclusively black people for preventative crime investigations) [1]. If you've participated in BLM protests, the FBI is also grossly overstepping its authority for the sake of surveillance [52].
...Muslim?
Salaat First, an app that reminds Muslims of prayer times, sells user data to the FBI and ICE to constantly track users' locations [2]. Meanwhile, Muslim prisoners are tortured without trial at Guantanamo Bay [3].
...Atheist?
Evangelicals have begun using digital surveillance to track where "not yet converted" to Christianity are living [57].
...Queer?
Grindr sells users' location data [4]: the data sold has been used to fire gay priests [5]. According to the New York Post, they "allowed unknown third parties to learn sensitive information about users, including who they date, where they live and work, and where they spend their free time" [6].
The owners of Grind hastily put the service up for sale when it was revealed that it also collects users' medical data and shares it with other companies [7] (your medical data is worth 10-40 times more than your credit card data [8]). Not all transgender, non-binary, or intersex individuals would want to walk around with a "MY GENITALS DON'T MATCH THE GENDER" sign on their chest, but the lack of privacy gives you just that.
By revealing your identity to anyone, you put your freedom (if being queer is illegal in your country) and life at risk.
...AFAB?
Mobile geolocation tracking is being used by anti-abortion groups. Quote from Politico: "One advertising firm bragged in 2015 that it could 'tag all smartphones going in and out of nearly 700 Planned Parenthood clinics'" [9]. At the same time, as of 2022. 40% of the world had legal liability for abortion without extremely specific reasons [10]. It should also be remembered that some opponents of abortion are very militant: there is quite a bit of violence and even terrorism against abortion providers and abortionists [11][12].
...Activist?
Google gave Indian police the data of a 21-year-old climate activist who typed into Google Docs about farm protests (turned out to be arrested) [13]. Protonmail gave the data of an eco-activist* to the French police (turned out to be arrested) [14]. Facebook, Instagram and X (Twitter) provide access to data to track activists (particularly non-white activists) — some of whom have not been uncooperative even after being exposed [15]. Our governments also have a strong interest in preventing protests before they even happen.
...Noncomformist?
For example, if you're a conservative, you may find yourself under the boot of censorship: the company Gotcha SEO conducted a study of 50 controversial ("edgy") search queries on Google and found that only 5% of the results pertained to conservative sites, compared to 31.8% left-wing and 63.8% neutral [16][17]. In my personal experience (especially felt while writing this article), Google, Bing and other search engines from big companies (compared to, for example, Brave Search) are also reluctant to produce results on the topic of big companies selling your personal information.
...Chinese?
In 2019, YouTube was caught automatically deleting comments that contained anything about "50 Cent (Party)" (China's "troll factory" — teams of people who flood social media comments with pro-state opinions for a small fee) [18], or accusing the Chinese Communist Party of banditry [19]. And then there's Tik Tok stealing your kids' data and selling it to your (Chinese) government [20]. And Google is also developing a special censored search engine specifically for China [21].
...A person with male gender in documents?
If your country has a military draft, with an overwhelming chance it will only be mandatory for males [22] (that's a discrimination). To send you to the army or to war, you will be tracked by phone, car movements [23], facial recognition cameras [24] and more. Evasion is punishable, up to and including prison and human rights violations [25][26].
...Anarchist?
Google Maps actively hides any images of protests and even poor living conditions [27]. Google Ads and Play Market remove opposition content at the request of the state (e.g. Russian) [28][29]. YouTube actively blocks channels and videos covering criticism of governments [30], protests [31], or torture by state [32] — especially in poor countries. (See also "activist?").
...Pro-Palestine?
Social media actively blocks pro-Palestinian viewpoints [33].
...Have a special health condition?
Pharmacies hand over your medical data to the police without a search warrant [34]. As mentioned, your medical data is worth 10-40 times more on the black market than your credit card data [8].
...Have ever bought anything?
Capitalism is one of the main dangers in selling your personal data. Many large companies use your information to estimate your income, sell you products you don't really need [36][37][38], or manipulate prices [37].
- For example, online retailers know that people with low income are more likely to make urgent purchases, so they set higher prices for them and cancel discounts [39][40].
- Some financial and insurance companies use social graphs to determine interest rates and insurance premiums. This often forces low-income people to pay more — this phenomenon is known as "poverty-premium" [41].
- Orbitz directs Mac users to more expensive hotels because they overpay for Apple electronics. [42].
- Target charges customer(s) higher prices when they were physically close to the store and unlikely to look for an alternative. [43]
- McDonalds hired surveillance company Silverpush to link non-consensual audio data from its mobile app with audio from Youtube or television to show "relevant ads" across platforms. [44]
There is no end to examples of sleazy sales pitches — and these are just the ones that have come to public knowledge!
...Mom, Dad, Parent?
Parents Club Bounty fined £400,000 for selling user data — the company illegally transferred 34.4 million records to 39 companies [45]. Popular family safety app Life360 sells the precise location data of tens of millions of its users [46]. Would you trust your children's personal data and location to a stranger? After all, according to some reports, pedophiles [47] and kidnappers can use this data to find victims.
...Working on a social profession?
Do you work as a politician, teacher, priest, curator, doctor, therapist or anyone else, so that your work causes you to hold a lot of vulnerable personal data of others for which you are responsible? You should be concerned about keeping them safe — after all, this data is being sold profitably [48].
...In a relationship?
Perhaps you'd like to keep the intimate details of your relationship private? In the most grotesque of news stories on the subject, an Australian border control officer returned a citizen's phone after a forced search at the airport with the words, "It was nice to see some good porn again," referring to nude photos of his girlfriend [49].
...Traveler?
The popular hotel chain AirBNB allows cameras inside its properties [56].
...Student?
Be vigilant: schools use tracking techniques to catch and severely penalize you for using vape (electronic cigarettes) [51].
...Driver?
Cars have become computers on wheels: they "have an unrivaled ability to watch, listen and gather information about what you are doing and where you are going" [55] [55]. This information is then shared or sold to data brokers, law enforcement, and others. Of the 25 car brands studied, 56% share your data with law enforcement in response to an informal request, and 84% share or sell your personal data [55].
Information is also willingly purchased by insurance companies [58], and even your partner(s) can use it to spy on you [59].
...Use technology to clean?
Robot vacuum cleaners not only suck up dust, but also scan your home [53]. As hard as it may be to believe, Amazon is actually using this data to make you more likely to buy things you don't need [54].
...Residen of a country with a democratic system?
There was a case not too long ago where Facebook was caught manipulating a major election: the company used our social graphs to distort our view of the real world and manipulate our votes [35].
...Citizen of a state?
In the context of the state, innocuous conversations can put you in danger, even if you have nothing to hide. One of the most shocking stories is the aforementioned experience of Mohamedou Ould Salahi [3], described in his memoirs and featured in the movie The Moorish Man. He was placed in the Guantanamo camp without trial and tortured there for 15 years for making a phone call to a relative in Afghanistan — he was suspected of involvement in the 9/11 attacks, although he had lived in Germany for the previous 10 years.
Ordinary people are arrested and pressured for what they share online, even through their "anonymous" accounts, even in democracies, even if it was legal, even if you are not a man [50].
"Give me six lines written by the most honest man, and I will find in them something for which he will be executed on the gallows" — Cardinal de Richelieu
...Human?
Why do you wear clothes? Why would you rather prefer an opaque toilet to a transparent one, or a bedroom without cameras to a monitored bedroom? Why might you not want to share your political views, sexual orientation, or gender identity with your grandmother, a teacher, or a police officer, even if you think there is nothing wrong with them? Why might you not want to share your social media gallery or passwords with your aunt, a social worker, or a 4chan user, even if you haven't done anything illegal directly?
What if I offered to send your social media passwords, bank account passwords, your medical information, address, and photos to my email — promise I wouldn't use them for anything bad: I just want to keep them on my hard drive for the security of your own data? Do you really have nothing to hide?
What if I told you that automated surveillance has reached such a scale that megacorporations can guess what you're thinking [60] about? Does that bother you? If so — I wouldn't be surprised.
Privacy has always been a part of human life, a normal part of it. The way we live now is a highly unnatural state for humans; it has never been normal. You don't have to have something to hide to want to not share all the details of your personal life with others.
Conclusion
The longer we give up the fight for privacy rights, the more Leviathan gains momentum. Do you think Orwell's world of "1984" was built overnight? No! People sacrificed the rights to privacy, anonymity, freedom of information — step by step. And the first step towards dystopia is marginalizing people who worry about their anonymity: reducing them to "tinfoil hat wearers" and "those who really think that THEY is reading your emails."
So what do we do? We must not think that "there's nothing we can do about it", or that "we've already lost". Instead, we need to:
- Spread the word about why privacy is important, and why it's worth caring about;
- Use private, free, decentralized analogs to popular services (e.g. Session instead of Telegram, NOSTR instead of Twitter, DuckDuckGo instead of Google);
- Support the right to privacy for the sake of the rest (e.g., so far only a few people use private messengers — states know that those who use them are hiding something. But if half of the population starts using them, it will be impossible to single out anyone special);
- Ask more often why companies know so much about us, and how is it even legal;
- Participate in politics. Politics is not an "observation sport": if democracy doesn't work, we are responsible for making it work. The very top of such participation is supporting organizations fighting for privacy rights
"Saying you don't care about privacy because you have nothing to hide is like saying you don't care about free speech because you have nothing to say. But even if you don't enjoy a right at that particular moment, others may need it. And to say that you don't care about a right because you don't need it right now is the most antisocial thing you can do." — Edward Snowden
Sources:
[1] https://theintercept.com/2021/01/30/lapd-palantir-data-driven-policing/
[2] https://www.theguardian.com/us-news/2020/dec/03/aclu-seeks-release-records-data-us-collected-via-muslim-app-used-millions
[3] https://www.npr.org/2019/11/14/778944195/a-legacy-of-torture-is-preventing-trials-at-guant-namo
[4] https://www.vox.com/technology/2023/6/16/23762403/data-odni-report-wyden
[5] https://www.vox.com/recode/22587248/grindr-app-location-data-outed-priest-jeffrey-burrill-pillar-data-harvesting
[6] https://nypost.com/2022/05/02/grindr-sold-data-about-users-precise-locations-for-years-report/
[7] https://www.theguardian.com/technology/2018/apr/03/grindr-shared-information-about-users-hiv-status-with-third-parties
[8] https://www.cyberpolicy.com/cybersecurity-education/why-medical-records-are-10-times-more-valuable-than-credit-card-info
[9] https://www.politico.com/news/2024/02/13/planned-parenthood-location-track-abortion-ads-00141172
[10] "As of 2022, countries that legally allow abortion on request or for socioeconomic reasons comprise about 60% of the world's population", https://en.wikipedia.org/wiki/Abortion_law
[11] https://en.wikipedia.org/wiki/Anti-abortion_violence
[12] https://www.justice.gov/crt/recent-cases-violence-against-reproductive-health-care-providers
[13] https://www.indiatoday.in/technology/news/story/disha-ravi-arrest-puts-privacy-of-all-google-india-users-in-doubt-1769772-2021-02-16
[14] https://proton.me/blog/climate-activist-arrest
[15] https://www.aclunc.org/blog/facebook-instagram-and-twitter-provided-data-access-surveillance-product-marketed-target
[16] https://www.gotchseo.com/google-biased/
[17] Google does quite a bit of censorship in its services in general: https://en.wikipedia.org/wiki/Censorship_by_Google
[18] https://www.taiwannews.com.tw/en/news/3933777
[19] https://www.theverge.com/2020/5/26/21270290/youtube-deleting-comments-censorship-chinese-communist-party-ccp
[20] https://www.npr.org/2020/08/04/898836158/class-action-lawsuit-claims-tiktok-steals-kids-data-and-sends-it-to-china
[21] https://www.nytimes.com/2018/08/16/technology/google-employees-protest-search-censored-china.html
[22] https://ru.wikipedia.org/wiki/%D0%92%D0%BE%D0%B8%D0%BD%D1%81%D0%BA%D0%B0%D1%8F_%D0%BE%D0%B1%D1%8F%D0%B7%D0%B0%D0%BD%D0%BD%D0%BE%D1%81%D1%82%D1%8C
[23] https://focus.ua/voennye-novosti/626982-ot-doprosov-do-operativnyh-meropriyatij-v-nacpolicii-rasskazali-o-poiske-uklonistov
[24] https://www.bbc.com/russian/features-63346138
[25] https://www.rbc.ua/ukr/styler/k-zaraz-karayut-uhilyantiv-vid-mobilizatsiyi-1707820307.html
[26] https://www.mrarchivist.com/results/entry/4591/; The prohibition of voting because a man has not registered to vote is contrary to Article 21 of the Universal Declaration of Human Rights.
[27] https://www.nbcnews.com/id/wbna17880969
[28] https://www.rferl.org/a/google-reportedly-removes-navalny-ad-after-russian-government-complains/29478844.html
[29] https://www.theguardian.com/world/2021/sep/17/apple-and-google-accused-of-political-censorship-over-alexei-navalny-app
[30] https://nordicmonitor.com/2023/09/google-youtube-accused-of-censoring-erdogan-critics/
[31] https://www.medianama.com/2024/02/223-youtube-blocks-videos-protests-job-aspirants-bihar/
[32] https://edition.cnn.com/2007/WORLD/meast/11/29/youtube.activist/
[33] https://www.aljazeera.com/features/2023/10/24/shadowbanning-are-social-media-giants-censoring-pro-palestine-voices
[34] https://thehill.com/business/4355894-pharmacies-sharing-medical-data-without-warrant/
[35] https://en.wikipedia.org/wiki/Facebook%E2%80%93Cambridge_Analytica_data_scandal
[36] https://usercentrics.com/knowledge-hub/data-is-the-new-gold-how-and-why-it-is-collected-and-sold/
[37] https://knowledge.wharton.upenn.edu/article/data-shared-sold-whats-done/
[38] https://www.eff.org/deeplinks/2020/11/visa-wants-buy-plaid-and-it-transaction-data-millions-people
[39] https://supreme.findlaw.com/legal-commentary/websites-that-charge-different-customers-different-prices.html
[40] https://policyreview.info/articles/analysis/does-everyone-have-price-understanding-peoples-attitude-towards-online-and-offline
[41] https://fairbydesign.com/povertypremium
[42] https://www.wsj.com/articles/SB10001424052702304458604577488822667325882
[43] https://www.bizjournals.com/twincities/news/2019/02/01/report-targets-app-charges-higher-prices-to.html
[44] https://www.digitaltrends.com/mobile/silverpush-app-tracking-spying-use-rises-new/
[45] https://www.theguardian.com/technology/2019/apr/12/parenting-club-bounty-fined-selling-users-data
[46] https://themarkup.org/privacy/2021/12/06/the-popular-family-safety-app-life360-is-selling-precise-location-data-on-its-tens-of-millions-of-user
[47] https://www.the-sun.com/news/3740183/paedophile-snachat-maps-victims-tesco/
[48] https://www.experian.com/blogs/ask-experian/heres-how-much-your-personal-information-is-selling-for-on-the-dark-web/
[49] https://micky.com.au/aussie-ex-pat-will-never-return-after-digital-strip-search-reveals-sex-tapes/
[50] https://www.dailymail.co.uk/news/article-11282263/Moment-police-swoop-house-devout-catholic-mother-malicious-online-posts.html
[51] https://apnews.com/article/vaping-surveillance-technology-schools-982128348c683b9d54c7a307c5b1fdc6
[52] https://www.politico.com/news/2023/05/19/fbi-surveillance-black-lives-matter-protesters-00097924
[53] https://www.welivesecurity.com/en/privacy/gathering-dust-and-data-how-robotic-vacuums-can-spy-on-you/
[54] https://www.reuters.com/markets/deals/amazons-irobot-deal-eu-antitrust-crosshairs-2023-07-06/
[55] https://foundation.mozilla.org/en/privacynotincluded/articles/its-official-cars-are-the-worst-product-category-we-have-ever-reviewed-for-privacy/
[56] https://ru.airbnb.com/help/article/3061
[57] https://newrepublic.com/article/179397/evangelical-app-targeting-immigrants-surveillance
[58] https://www.nytimes.com/2024/03/11/technology/carmakers-driver-tracking-insurance.html
[59] https://www.nytimes.com/2023/12/31/technology/car-trackers-gps-abuse.html
[60] https://www.zdnet.com/article/google-even-knows-what-youre-thinking/*This does not mean that ProtonMail is insecure: the service regularly wins many court cases on the subject of disclosure of user data; it means that the use of ProtonMail was not private enough (in this case, without VPN/SPN/TOR).
-
 @ e373ca41:b82abcc5
2025-01-03 16:25:26
@ e373ca41:b82abcc5
2025-01-03 16:25:26ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
I was told the following story at one of my readings last year.
An elderly couple from a Swiss town with a high density of anthroposophically minded people were said to have been vaccinated against coronavirus. My conversation partner found this unusual, wanted to know the “why” and asked.
“Oh, you know, the two of us had wanted to end our lives voluntarily and in a self-determined way for a long time,” they explained. “When the coronavirus vaccinations came along, we thought: This is our chance!”
Absurd times
I had to laugh. What an absurd time to live in. Actually only bearable as a meme. Last year was also a year in which things were reversed. Everything is upside down and yet should seem normal. Calling minister of economy Habeck a moron in a meme resulted in a house search and an insult lawsuit. Calling Alice Weidel, leader of opposition AFD a "Nazi bitch", on the other hand, is no problem. The new normal: reality as permanent satire.

(when you read this, you caught it already)
But this image is breaking down, it is being recognized and increasingly rejected:
- Stagings with satanic overtones at the Olympics & Co. caused a wave of outrage.
- Medium magazine named the nomenklatura journalists from Correctiv as journalist of the year, at the same time as their core thesis of a remigration conspiracy was melting away.
- The “reason of state for Israel” was a Nibelung allegiance for war criminals: a Netanyahu would have to be arrested on German soil if Germany wanted to comply with international law.
- The woke influencer and Böhmermann gag writer “El Hotzo”, one of the “self-reflective feminist men” in the outside media world (he wished Trump dead after the assassination attempt), has now had to publicly confess to having manipulated and gaslighted women for years and to having exploited his media position to do so.
- The Magdeburg attacker is being framed on the right, police laws and surveillance are to be stepped up, but the media are warning that extremists are now exploiting this event for their own ends. Very interesting: because the danger comes from the right, we protect Christmas markets instead of mosques. Nobody takes all this seriously anymore.
Many half-dead zombie topics are starting to move again. The lab leak theory has been confirmed once again. The Paul Ehrlich Institute (whose job is the oversight of vaccines, among others) virtually admitted that certain vaccine batches were more dangerous than others. Why didn't it intervene? This is what state-perpetrated killing and bodily harm by omission looks like. Has Paul Cichutek (former head of PEI) already been arrested, his house searched and documents confiscated (along with the "Federal Cross of Merit")?
Most recently, a Yale study (still unpublished) showed that spike proteins were still detectable two years after vaccination, and an effect on genetic material is not ruled out. Sounds a lot like the “conspiracy theories” of 3 years ago. Yet in this country, the state still recommends this vaccination to pregnant women. It won't be possible to put all these educational topics in a repository for toxic information, as the leaked RKI protocols have recently shown. The tide is turning, the picture is clearing. But slowly and not on page 1 of the newspapers and their editors, who are now fighting for survival because nobody wants to read their lies anymore. “Another hundred years of newspapers and all words will stink,” Nietzsche said a good 100 years ago.
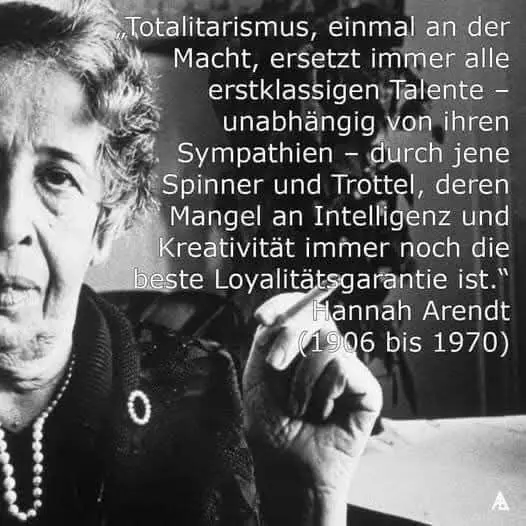
("Power replaces first class talent by idiots, as lack of intelligence and creativity is always the best guarantee for loyalty", Hannah Arendt)
Do not live with lies
Fifty years ago, Alexander Solzhenitsyn published the text “Do not live with lies” (1974), in which he points out the antidote to lies:
“Our way: CONSCIOUSLY SUPPORT THE LIE IN NOTHING! Recognize where the boundary of the lie is (it looks different for everyone) - and then step back from this life-threatening boundary! Do not glue together the dead knuckles and scales of ideology, do not mend the rotten rag - and we will be amazed at how quickly and helplessly the lie falls away, and what should stand naked and bare will then stand naked and bare before the world.”
You can laboriously help build lies, submit to an ideology that nourishes you for a while. But when the edifice of lies collapses, nothing else will help. Every lie wears out and is eventually overtaken by reality. We see that the spans of lies are getting shorter and shorter, that the roller of reality is rolling over them faster and faster.
“We can't force them to tell the truth. But we can make them lie more and more brazenly.”
I've read this sentence a lot recently. Sometimes it is attributed to Ulrike Meinhof, sometimes to Bernward Vesper, Gudrun Ensslin's husband. I find the quote remarkable because it directs our attention away from what we cannot and will never change, namely the existence of the lie itself, towards what we can change: the soil on which the lie grows or does not grow. In the Luhmannian sense, we must look away from the system (the lie) and towards the environment or surroundings in which it thrives or not. The path from lies to truth is the same as the path from slavery to freedom. The revolutionary poet Georg Herwegh formulated this in his poem “A lane for freedom - der Freiheit eine Gasse” (1841):
“When all the world lost courage,\ To begin the feud,\ You, my people, stand before the nations,\ Let your heart's blood run!\ Give us the man who grasps the banner\ Of the new age,\ And through Europe we will break\ A lane for freedom!”
- Julian Assange is free! He is Herwegh's “man” for me.
- Satoshi Nakamoto, the inventor of Bitcoin, is Herwegh's “man” for me.
- Austrian singer Udo Jürgens, tenth anniversary of whose death was recently celebrated, was Herwegh's “man” for me: “I am in favor of dissent being allowed, I even consider it a duty.”, he sings. Even chansonniers from 20 years back would qualify as subversive today.
https://www.youtube.com/watch?v=McgZEA6BZiY * We are all Herwegh's “man”. There is not just one to hope and wait for, but many of our kind and more and more of them.
I was able to get to know many of them this year when I visited a good 50 places on my reading tour. Four years ago, we worked together to create an avenue for freedom when we published the “Appeal for free debate spaces”. * Today, together with a team of developers, I am building the Pareto project, another alleyway for the freedom of information.
I wish you all a happy new year and thank you very much for your loyalty and support of my work!
This article by Milosz Matuschek first appeared in German on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Update: Since my last article on the Pareto project, we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.
-
 @ 58937958:545e6994
2025-01-03 11:07:06
@ 58937958:545e6994
2025-01-03 11:07:06January 3, 2024 I made a Bitcoin-inspired Osechi to celebrate Bitcoin's birthday. Everything was handmade! Osechi: A traditional Japanese New Year’s feast, typically served in stacked boxes.
First Layer (Ichino-jū)

- Tazukuri: Dried sardines, symbolizing a wish for a bountiful harvest.
- Simmered Kuai: A vegetable with large sprouts, symbolizing growth and success.
- Kombu Rolls: A play on words with the Japanese term yorokobu ("to be joyful"), making it a good luck dish.
- Matsukazeyaki: Ground meat coated with sesame or poppy seeds on one side, symbolizing honesty (no "hidden side").
- Black Beans: Represent hard work and good health.
- Datemaki: Sweet rolled omelet resembling scrolls, symbolizing knowledge and learning.
- Grilled Yellowtail: A fish whose name changes as it grows, symbolizing success. Salmon Terrine: A classic addition to Western-style Osechi. Salmon symbolizes success, avoiding misfortune (sakeru), and prosperity for future generations.
- Tataki Gobo: Burdock root with deep roots, symbolizing family stability and prosperity.
Second Layer (Nino-jū)

- Candied Kumquat: A dish symbolizing wealth and good fortune.
- Namash: Pickled daikon and carrot, resembling celebratory red and white decorations.
- Chestnut Kinton: Golden in color, symbolizing wealth and a prosperous year.
Bitcoin-themed additions:
- Pumpkin Yokan
- Chicken and Spinach Terrine
- Kinako Sticks
Third Layer (Sanno-jū)
 Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity.
I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself.
Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity.
I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself.Dishes Inspired by Bitcoin
Pumpkin Yokan
 I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan.
I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan.Chicken and Spinach Terrine
 It was my first attempt, and I think with more care, the shape could be even better.
It was my first attempt, and I think with more care, the shape could be even better.Kinako Sticks
 A simple snack made with honey and roasted soybean flour (kinako).
Roll it out, cut it into sticks, and coat with more kinako.
A simple snack made with honey and roasted soybean flour (kinako).
Roll it out, cut it into sticks, and coat with more kinako.Candied Kumquat
 Candied Kumquat: A dish symbolizing wealth and good fortune.
In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold."
Candied Kumquat: A dish symbolizing wealth and good fortune.
In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold."nostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy
I wonder what Satoshi might have eaten on the day Bitcoin was born. Wouldn't it be amusing to imagine him snacking on Osechi while working on his computer? (Satoshi chose a Japanese name, so perhaps he might have an interest in Japanese culture.) Maybe, right now, Satoshi is relaxing and enjoying some Osechi... though probably not! In any case, I hope Satoshi is living peacefully somewhere.
-
 @ 39cc53c9:27168656
2024-03-02 12:09:41
@ 39cc53c9:27168656
2024-03-02 12:09:41I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2024-02-19 17:49:18
@ 39cc53c9:27168656
2024-02-19 17:49:18Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 44dc1c2d:31c74f0b
2024-01-07 21:19:28
@ 44dc1c2d:31c74f0b
2024-01-07 21:19:28Chef's notes
This bread is super simple to make and takes a bit to dial in.
The only real notes I have here is you can use whatever round pan you want to bake it in. Or use a square one, just make sure the walls of the pan are high.
Less is more with this bread. You really don't want to over knead the bread here. If you're used to making bread that need a lot of kneading, this will feel odd.
Details
- ⏲️ Prep time: 27 hours
- 🍳 Cook time: 50 to 60 min
- 🍽️ Servings: 1 loaf
Ingredients
- 1-1/2 teaspoons active dry yeast
- 1-3/4 cups warm water (110° to 115°)
- 3-1/2 cups plus 1 tablespoon all-purpose flour, divided
- 2 teaspoons salt
- 1 tablespoon cornmeal or additional flour
Directions
- In a large bowl, dissolve yeast in warm water. Using a rubber spatula, stir in 3-1/2 cups flour and salt to form a soft, sticky dough. Do not knead. Cover and let rise at room temperature 1 hour.
- Stir down dough (dough will be sticky). Turn onto a floured surface; with floured hands pat into a 9-in. square. Fold square into thirds, forming a 9x3-in. rectangle. Fold rectangle into thirds, forming a 3-in. square. Place in a large greased bowl, turning once to grease the top. Cover and let rise at room temperature until almost doubled, about 1 hour.
- Punch down dough and repeat folding process. Return dough to bowl; refrigerate, covered, overnight.
- Grease the bottom of a roasting pan with sides at least 4 in. high; dust pan with cornmeal. Turn dough onto a floured surface. Knead gently 6-8 times; shape into a 6-in. round loaf. Place into prepared pan; dust top with remaining 1 tablespoon flour. Cover pan and let rise at room temperature until dough expands to a 7-1/2-in. loaf, about 1-1/4 hours.
- Preheat oven to 500°. Using a sharp knife, make a slash (1/4 in. deep) across top of loaf. Cover pan tightly with foil. Bake on lowest oven rack 25 minutes.
- Reduce oven setting to 450°. Remove foil; bake bread until deep golden brown, 25-30 minutes. Remove loaf to a wire rack to cool.
-
 @ 58937958:545e6994
2025-01-03 11:01:49
@ 58937958:545e6994
2025-01-03 11:01:492024年1月3日 ビットコインのお誕生日に合わせて ビットコインっぽい具材を入れたおせちを作りました 全部手作りです
1の重
 (左上から)
(左上から)- 田作り…田んぼに田作り(カタクチイワシ)を肥料として撒いたことから、豊作祈願の意味合いがある。
- くわいの煮物…大きく芽が出る野菜で、出世や成功を祈る。
- 昆布巻き…「喜ぶ(よろこぶ)」の語呂合わせで縁起物。
- 松風焼き…表面だけケシの実やゴマをまぶす=裏がない→隠し事のない正直な生き方ができるように、という意味が込められている
- 黒豆…「まめに働く」ことや健康を祈る。
- 伊達巻き…巻物に似ていることから、知識が豊富になるようにと願いが込められている。
- ぶりの幽庵焼き…ぶりは成長とともに名前が変わる出世魚で、将来の出世を願う。
- 鮭のテリーヌ…洋風おせちの定番。鮭には「出世」「災いを避け(サケ)る」「子孫繁栄」などの意味がある
- たたきごぼう…根が深く張るごぼうは家族や子孫繁栄の象徴。
2の重

- 金柑の甘露煮…金柑の「金」の文字から、金運や財運を祈る。
- なます…紅白の水引のような形状で祝いの意味がある
- 栗きんとん…黄金色が金運を表し、豊かな1年を願う。
以下はビットコイン具材として入れました
- カボチャようかん
- 鶏とほうれん草のテリーヌ
- きな粉棒
3の重
 煮しめ…様々な具材を一緒に煮ることから、「皆で仲良く、末永く繁栄するように」という願いが込められている
きぬさやのBは我ながらちょっと笑ってしまった
煮しめ…様々な具材を一緒に煮ることから、「皆で仲良く、末永く繁栄するように」という願いが込められている
きぬさやのBは我ながらちょっと笑ってしまったビットコインを意識して作った具材
カボチャようかん
 固めの牛乳かんを作り、包丁でBの形に切り抜いて、カボチャのようかんを流す感じです
固めの牛乳かんを作り、包丁でBの形に切り抜いて、カボチャのようかんを流す感じです鶏とほうれん草のテリーヌ
 鶏むね肉とはんぺんをミンチにして、半分にほうれん草を入れて形作りました
初めて作ったので不安でしたが丁寧に作ればもっと良い形になると思いました
鶏むね肉とはんぺんをミンチにして、半分にほうれん草を入れて形作りました
初めて作ったので不安でしたが丁寧に作ればもっと良い形になると思いましたきな粉棒
 はちみつときな粉だけで作る駄菓子的なおやつです
のばして包丁で切り抜いてきな粉をまぶします
はちみつときな粉だけで作る駄菓子的なおやつです
のばして包丁で切り抜いてきな粉をまぶします金柑の甘露煮
 丸くてオレンジ色なので作ってみました
しかも名前に「金(ゴールド)」が入っているのでビットコイン食材のポテンシャルがあると思います
とろける感じでめっちゃおいしかったです
丸くてオレンジ色なので作ってみました
しかも名前に「金(ゴールド)」が入っているのでビットコイン食材のポテンシャルがあると思います
とろける感じでめっちゃおいしかったですnostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy
サトシはビットコインが生まれたその日に何を食べていたのかなぁと おせちをつまみながらパソコンに向かっていたりしたら面白いなぁと思いながら作りました (日本文化が好きだから日本名にした可能性はあるかな~とか)
今頃のんびりおせちを食べてくつろいでいる・・・なんてことはないですかね 何にせよサトシが平和に暮らしていればいいなぁと思います
-
 @ 44dc1c2d:31c74f0b
2024-01-04 05:18:29
@ 44dc1c2d:31c74f0b
2024-01-04 05:18:29Chef's notes
This is a base recipe. You can and should modify it to your tastes.
For a honey mustard, add a couple tablespoons of honey.
You can affect the taste by changing the vinegar around, like a white or sherry vinegar. You can use beer instead of vinegar. Also chop up some fresh herbs like tarragon and chuck it in. You can also play with the water and vinegar ratio for less of a bite (or more).
If you want a more yellow mustard, chuck in some turmeric and sugar.
Play with the heat of the mustard by changing the seeds and the heat of the liquid you start with. Black mustard being the hottest. Starting with a cold liquid will make for a hotter mustard instead of a warm liquid. (IE white mustard seeds in a warm liquid will make for a mellow mustard vs black seeds in a cold liquid)
Details
- ⏲️ Prep time: 10ish min.
- 🍳 Cook time: 48 hours
- 🍽️ Servings: About a 3/4 full 8oz jar
Ingredients
- 2 tablespoons of brown or black whole mustard seeds
- 1/4 cup ground mustard powder
- 3/4 teaspoon salt
- 1/4 cup water
- 4 teaspoons apple cider vinegar
Directions
- Grind seeds in a spice grinder or in a mortar and pestle tell the seeds are at the desired consistency.
- Mix the dry stuff together. (seeds, salt and powder)
- Mix the wets in.
- Cover and let sit for 2 days. (I use a jar) Wait time is important here. It will look soupy at first and thicken up as the seeds absorb the liquid. The time also allows the mustard to mellow. Fresh made mustard is harsh and bitter tasting so give it time.
-
 @ d7c6d014:a6abb6b8
2023-12-29 10:35:20
@ d7c6d014:a6abb6b8
2023-12-29 10:35:20WASSUP, NOSTRICHES!?
というわけで、ノス民の皆様いかがお過ごしでしょうか。
Nostrは、その性質上、既存のSNSのようなEメールアドレスや電話番号などを使ったいわゆる「アカウント」的な概念が存在しておらず、SSL/TLSやビットコインなどのように公開鍵暗号方式を取っています。 そのため、秘密鍵 (nsec) さえ一つあれば、Nostrプロトコルに準じた様々な種類のクライアントにアクセスすることができます。 (例えるなら、Twitterのアカウント1個で、YouTube、Instagram、Medium、Misskey全てのサービスにアクセスできるようなイメージ)
今回はそんな多種多様なNostrのクライアントたちをジャンル別に可能な限り網羅して紹介していきたいと思います。
SNS系 (Twitterライク)
nostter
nostterは、雪猫さん制作の動作が非常に軽いTwitterライクなWebクライアントです。

kaiji君制作のUIもマットで見やすく、Web版Twitterに慣れている人でNostrの世界に初めて足を踏み入れる人におすすめのWebクライアントです。

Snort
Snortは、主に日本国外で人気なTwitterライクなWebクライアントです。

特徴的な機能としては:
バズり具合がサマリーとして可視化できたり...

開発者にzap (ビットコインの投げ銭のこと) したり...

ビットコインライトニングのウォレットと紐付けたりできます⚡️

質問系 (Quoraライク)
swarmstr
swarmstrは、Quoraライクなクライアントです。
asknostr のハッシュタグをつけると自動的にキュレーションされて表示されます。

動画配信 (YouTube, Twitchライク)
zap.stream
zap.streamは動画配信クライアントです。

チャットしたり...

zapしたり...

Stream Forwarding機能があるので、他の動画プラットフォームに同時配信もできます🙃

リンク集約 (Linktreeライク)
Nostree
Nostreeは、Linktreeの様に様々なSNSなどのリンクを集約できるツールです。

zapしたり...

リンクをシェアしたり...

Nostrに新しいリストのシェアをしたりできます🙃

また、プロフィールのみならず、好きな本のリストを作ってみたり使い方はあなた次第です🚀
エントリ / 長文記事投稿 (Medium, noteライク)
habla.news
habla.newsは、Mediumのような長文記事投稿用クライアントです。 記事をブクマ、拡散できるのはもちろんのこと、お気に入りの記事に対してzapすることができます。

YakiHonne
YakiHonneは、キュレーション型の分散型メディアプロトコルです。

Mediumのように長文投稿ができるのはもちろんのこと、記事自体をキュレーションしてまとめてpublishすることができます。

もちろんブクマや記事のシェア、ビットコインの投げ銭もできます⚡️
Bounty
nostrbounties
nostrbountiesは、タスクをこなすとビットコインで報酬がもらえるBounty型のWebクライアントです。

Wikipediaライク
wikistr
wikistr は読んで字のごとくWikipediaのようなクライアントです。
通常のWikipedia的な機能に加え、投稿したウィキ情報をフォークしてオリジナルの文章を追加したり、パロディネタにしたりして遊べるのが特徴です。

フリマ
Shopstr
shopstrは、メルカリのようなフリマクライアントです。 メルカリのようなアプリ内通貨などは使わずに、ビットコインで直接商品の売買をすることができます。 フィジカルな商品のみならず、デジタル商品のやり取りもできます。

料理レシピ共有 (クックパッドライク)
NOSTR.COOKING
NOSTR.COOKINGは、料理レシピの共有ができるクライアントです。
Nostrユーザーは世界中にたくさん存在しているため、クックパッドとは違い日本料理を含めた世界中のレシピが集まっているのが個人的には好きです。 レシピをフォークしてアレンジレシピを作ったり、マークダウンファイルをダウンロードしたり、zapできたりします。
いかがでしたでしょうか。 今回は、計9種類のトピックに分けてWebクライアントをメインに紹介してきましたが、これでもまだまだほんの一部です。
そして何より、これまで取り上げてきた機能全てがNostrの秘密鍵一つで利用できるのがNostrの素晴らしいところです。煩わしいサービスごとのアカウント登録は一切必要ありません。
次回はモバイルクライアントをメインにキュレーションして紹介しようと思います♡
今回の記事が良いな〜と思ったら是非ZAP ME⚡️⚡️⚡️
-
 @ 45bda953:bc1e518e
2025-01-03 10:33:02
@ 45bda953:bc1e518e
2025-01-03 10:33:02I did not need to learn to understand Bitcoin. Understanding Bitcoin was intuitive for me. I loved reading as a kid. Asterix and Tintin comics were a staple for me and I grew into the F.W.Dixon Hardy Boys books. Reading about theft, danger and sleuth mysteries pivoting into fantasy stories and then all manner of fiction and authors I am not going to name because it does not really matter and most I have forgotten. I devoured a substantial amount of fiction as a child. At one point when I was 13 years old in 2000 I decided to read a grown up book. My dad had a copy of Des Griffin's book (Fourth Reich of the Rich) on his bookshelf. The reason I picked that book is because it looked serious and ominous and it had a big swastika on the cover. I assumed that if I am going to read a grown up book this one seemed to challenge me. I read the book and it blew my tiny child brain wide open. I realised how complex and potentially evil the world could be. No one forced me to read it, no one recommended the book to me. Learning about the financial system and how finance is used to break the spirit of man and corrupt our lives with war and destruction germinated questions and doubts in my mind. Sunday school, rainbows and butterflies be damned. My world was shattered and I needed answers. I decided to go as far back as I possibly could and before the end of that year I had finished reading the Bible. I had an orange NIV at the time and I just started at page one and read every day until Revelations 22. In hindsight I managed to learn very little on my first read through, my underdeveloped mind lacked a lot of life experience and wisdom to really understand most of what I consumed but I had built a skeleton of the time line anchoring me through world history and that was more meaningful than I understood at the time. The most important thing I discovered about myself in the year 2000 is that I was obsessed with history not for history's sake. I needed to understand the why behind the why. I was on a mission to discover why evil exists and what is going to fix it. I had read through the Bible cover to cover about 7 times since. For the next couple of years I went onto the rabbit hole of conspiracy and mysticism. I had read the largest amount of nonsense rubbish books written by some of the most depraved moronic minds the world had ever conjured into existence, hoping that I would find some clue to the origins and purpose of evil and it's elusive cure. When a 15 year old reads Morals and Dogma by Albert Pike trying to find a grain of truth only to realise he has discovered delusional hocus pocus aerie faerie shit moving on to the next author spouting incessant crap leading nowhere. It took me many years to learn that there is no magic behind the freemasonic order or Adam Weishaupt's Illuminati. I concluded that there did not exist a freemason who knew the truth or would communicate the reality about the existence of their order and it's origins. After reading hundreds of books and documents ranging from Aesop to Marx to I had to capitulate into a nihilistic faith in Christ. Because the answer to evil was simply a hope in the second coming where Jesus might wipe out evil and punish sin. The only way an inkling of justice could exist among mankind. Having discovered this hope the way I did was not healthy because inaction is the only requirement and all action becomes meaningless. If good and right cannot project from within the created being and it is doomed to be a spectator to the performance of divine justice then I might just as well capitulate and die for my life is just as meaningless as the one who does all that is right and good. I reverted to an ecclesiastical, stoic, nietzschean frame of mind, everything is meaningless and nothing means anything, all can go fuck themselves. It was a doom loop in my mind which lead me to giving no shits about anything. I would drink, do dangerous things just to exact my own private kind of revenge on whoever I felt deserved it. I hated the world and wanted to see it all burn. My most ardent hate was reserved for money and people who showed any form of respect for money or wealth. A homeless woman confronted me on the street one day asking if I have money for her. I took all the money I had in my wallet and said to her all I have is this communist rubbish paper and I said to her she can have it all but I feel bad that I don't have anything of value to give her. It was about R70, I did not have much. She started crying when I gave it to her and she even seemed unwilling to take it when I offered it to her more insistingly.
I cleaned up my act a bit when I met a girl I liked and we started a relationship. She was still at school and I picked her up in my Volkswagen Golf after school and took her home every day. With time as our relationship developed I started to feel responsible for her well being seeing how emotionally dependant she became on me over time. I did not have a job. I was always setting up LANS and playing computer games with my buddies and sponging of my parents, I had no interest in earning income or looking for a job. In spite of this unproductive attitude to life my girlfriend loved me, I could articulate abstract concepts and explain mysteries and organise thoughts into coherent ideas of life and philosophy and we had many friends. I decided that I was going to get my life in order so that I can man up to the responsibility of having a woman in my life. I got a job at a car dealer got into a fight with the manager and fired my boss after a week of witnessing the most shallow insipid style of life and world view. The fiat system was so repulsive to me it would make me sick. I even refused to open a bank account which did not help with trying to find employment. I ended up working for my father learning skills from a man I could respect because his character was honourable and above reproach. I could disagree with him and retain my respect for him. He was stuck in a fiat clutch of debt, a hard worker and honest businessman but the fiat world never allows good men a moment for pause. He was willing to pay me in cash and I started to provide for my young wife and newborn daughter. I discovered the bitcoin whitepaper in 2011, in this time but I was not in a position to attain any because the rails for purchase did not yet exist in my country, I did not have internet access at home and my PC was just standing at my parents house at the time so mining was not an option.
We did not even have electricity, I shut it off because I had a fight with my wife's fiat minded family who wanted to split the electric bill on the property equally. I had purchased a kwh meter that I was going to install at my distribution board to calculate how many units of power we used monthly. They did not like that idea and I got push back from them. So I disconnected our house and paid the two following bills, when the third bill came I did not pay. They were very surprised to find out that we were living without electricity to for two months already and they did not even have a difference in the price of the electric bill. We were hardly using any power and was paying a bulk chunk of their bills. Anyway...
I immediately understood Bitcoin and the problems it could solve for me personally with regards to the fact that I hated money so much. My disconnect with reality suddenly did not reflect my madness but the madness of the world. I adopted Bitcoin in my heart and had my hopes pinned on it achieving some type of success. Bitcoin became a placeholder in my mind thereafter something I knew I would keep track of into the future. In 2016 sometime I watched a video where Jack Mallers discussed placing verifiable and peer to peer bets on chess games online using Bitcoin. I got so excited I wanted to explode, I called my dad and my brothers and I wanted them to see the video. Their reaction left me disappointed because I realised that the implications of what this tech could become was lost on them and I could not adequately explain it in analogies that made sense, I just seemed like a rambling nutcase. Anyway I did a bit of searching and found that it was possible to buy Bitcoin online in South Africa. I did not waste any time and opened a bank account for the first time in 11 years. (I had a savings account when I was a kid.) I needed to be able to do transfers to purchase bitcoin. Our first purchase was R150 we ended up with 90 rand after the exchange took a third of the amount in withdrawal fees because I immediately taught myself how to and took self custody. It was about 0.01170000 sats. I used all those sats to order a type of debit card from England wherewith I tried spending the bitcoin at a local supermarket. I was not trying to save the sats, I wanted to test the technology and did not know I was spending potentially thousands of rands in future savings buying a card and some junk food. It worked for about two weeks then regulations forced the company that supplied the card to shut down its services. They emailed me and apologised. I did not care, this technology was going to change the world forever, the only thing I could not yet predict was how long it would take for adoption to happen. In my mind we were on the precipice of a revolution and the whole world was going to see the light overnight. I was so wrong and my expectations were 100% unrealistic. I had way too much confidence in humanities collective intelligence and their ability to see the change in monetary dynamics I perceived as the ultimate liberation of all mankind. When I realised how unresponsive people are to this I took up the responsibility of educating everyone I came in contact with about Bitcoin and I did not even own any meaningful amount properly yet. The price did not matter to me. I did not even understand how valuable it would become as wealth, the function of cutting out all intermediate institutions was the selling point for me. No one valued, understood or even bothered taking me seriously. Some people humoured me and some laughed and scoffed at me. I became frustrated. But for the first time in my life, I had hope, meaning, something to aspire to...
...and that is valuable.
To be continued...
...
bitbib
-
 @ 44dc1c2d:31c74f0b
2023-12-12 20:18:07
@ 44dc1c2d:31c74f0b
2023-12-12 20:18:07Chef's notes
If you want to kick it up a notch instead of using EVOO or butter, get about 6 slices of bacon and at the first step just cook off the bacon and use that as your cooking fat.
If you want a more crispy biscuit, cook them separately instead of cooking them in the filling. If you do this, simmer the filling on low for an extra 10 ish min, or just until the potato are tender.
If you prefer to make the pot pie in a casserole dish, you can. Simply pour out the filling into a greased baking dish and top with biscuit dough and continue with the recipe as stated.
The filling tends to bubble and make a bit of a mess, so I recommend placing your skillet or baking dish over a sheet pan covered with tin foil to catch any drips and messes.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 45-50 mins
- 🍽️ Servings: 4-6
Ingredients
- roughly 1lb of chicken. (Use whatever I prefer thighs)
- 1 medium size onion, peeled and diced
- 2 medium size carrots, peeled and diced
- 2 celery stalks, diced
- 3 cloves of garlic, peeled and minced
- 2 heaping tablespoons all purpose flour
- 2 cups chicken stock/broth
- ½-1 cup whole milk
- ¼ cup chopped fresh parsley
- 1 teaspoon fresh thyme plus more for garnish
- 2 bay leafs
- 2 mid sized potatos chopped into small cubes.
- Salt and pepper to taste
- 3-4 tablespoons of olive oil or butter
- For the Drop Buttermilk Biscuits
- 2 cups all purpose flour
- 1 tablespoon baking powder
- ¼ tsp baking soda
- ½ tsp fine sea salt
- 6 tablespoons cold unsalted butter, cubed
- 1¼ cups buttermilk + 2 tablespoons for brushing biscuits with
Directions
- For the Filling
- Heat your cooking fat. If using uncooked chicken, add chicken pieces to the pan. (If using pre-cooked chicken, don’t add it until later) Cook sautéing chicken for 2-3 minutes per side tell golden brown
- Add onion, celery, carrots, garlic and potatos. Cook for 5-7 minutes, stirring often until the veggies start to become tender. Make sure to season well with salt and pepper.
- Sprinkle flour over the veggies and chicken and stir vigorously for 1 minute to cook the flour a bit.
- Slowly pour in the chicken broth followed by the milk while stirring. Raise temperature up just a bit if needed and let it come to a very gentle boil. Once it reaches a boil reduce the heat to a simmer and let cook for 5-10 minutes, or until its has reduced and mixture has thickened a little
- Add the chicken if using precooked or rotisserie, parsley and thyme. Let cook until the veggies are tender, chicken are heated through, and mixture is nice and thick or has reached your desired thickness, about 3-5 more minutes (feel free to loosen up sauce a little adding more milk, cream or broth as needed). Season with salt and pepper to taste. Remove from heat and set aside.
- For The Buttermilk Drop Biscuits
- Preheat the oven to 425ºF while preparing the drop biscuits
- Add the flour, baking powder, baking soda, salt, to a large bowl and whisk to combine or pulse to combine in a food processor. Scatter the butter over the dry ingredients and rub together with your fingertips, until it forms a sandy-looking texture with some pebble-sized pieces or use a pasty cutter. If using food processor pulse a few times to achieve the same texture.
- Pour in the buttermilk and stir until it just comes together into a thick dough and there are no visible signs of flour. This step should only take a minute: be careful not to overmix the dough. (I usually pour out my flour and butter into a bowl from the processor and stir in the buttermilk by hand with spatula instead of pulsing it in)
- Assembling & Baking
- Use large cookie scoop or 2-3 heaping tablespoons (or approx ¼ cup) to scoop out dough. Drop dollops of the dough over the top of the pot pie filling to mostly cover the surface. Flatten them out a bit if you wish. Brush the tops of the biscuits with remaining 2 tablespoons of buttermilk.
- Transfer the skillet to the oven and bake for about 20-25 minutes until the biscuits are golden brown and fully cooked through and the filling is bubbling. I typically loosely cover pan with foil for the last 5-10 minutes of baking so they don’t brown too much - but are fully cooked through. Feel free to broil for the last minute to get the biscuits deeply golden.
-
 @ 5c8a5765:4fc5edee
2023-12-05 12:01:20
@ 5c8a5765:4fc5edee
2023-12-05 12:01:20А вы знали, что NOSTR-протокол — это не только децентрализованный микроблоггинг, но ещё и…
…Платформа для длинных текстов: www.habla.news и https://blogo.site
…Децентрализованный хостинг для веб-сайтов: https://hostr.cc
…Веб-магазины: https://shopstr.store и https://plebeian.market
…Децентрализованная публикация отрывка текста (аналог PasteBin): www.nosbin.com
…Сайт для заметок: www.listr.lol
…Сокращения URL, которые никогда не перестанут работать: www.w3.do
…Канал с мемами: www.memestr.app
…Децентрализованный торрент-архив: https://dtan.xyz
…Шахматы: https://jesterui.github.io
…Аудио-плеер: www.wavman.app
…Платформа для создания и публикации музыки: www.stemstr.app
…Платформа для подкастов (которая платит за её использование): www.fountain.fm
…Коллективный буфер обмена с конечным шифрованием: www.sendstr.com
Используйте удобные мосты для…
…Связи Nostr с Fediverse (Mastodon, ActivityPub, проч.): mostr.pub
…Связи Nostr с Matrix: www.github.com/8go/matrix-nostr-bridge
…Превращения любой RSS-ленты (Twitter, Mastodon, Reddit, ScuttleButt, проч.) в Nostr-аккаунт, на который можно подписаться: https://rsslay.nostr.moe
Застрял:а в Твиттере (Х)? Используй EXIT.pub для автоматической миграции всего контента уже сегодня: www.exit.pub
Я не привожу здесь зашифрованных мессенджеров на базе NOSTR (вроде Pulsar или 0xChat), ибо хотя они и хороши, они значительно уступают по безопасности мессенджерам, изначально ориентированным на приватность, таким как Session и SimpleX.
-
 @ 5c8a5765:4fc5edee
2023-12-04 17:04:12
@ 5c8a5765:4fc5edee
2023-12-04 17:04:12Did you know that the NOSTR protocol is not only decentralized microblogging, but also...
…A platform for long texts: www.habla.news and https://blogo.site
...Decentralized website hosting: https://hostr.cc
...Web store: https://shopstr.store and https://plebeian.market
...Decentralized text publishing (alternative to PasteBin): www.nosbin.com
...Note taking tool: www.listr.lol
...URL shortener that will never stop working: www.w3.do
...A meme channel: www.memestr.app
...Decentralized torrent archive: https://dtan.xyz
...Chess: https://jesterui.github.io
...Audio player: www.wavman.app
...Music creation and publishing platform: www.stemstr.app
...Podcast platform (that pays when you use it): www.fountain.fm
...A collaborative clipboard with end-to-end encryption: www.sendstr.comUse convenient bridges to... …Link NOSTR to Fediverse (Mastodon, ActivityPub, etc.): www.mostr.pub
…Link NOSTR to Matrix: www.github.com/8go/matrix-nostr-bridge
…Turn any RSS feed (Twitter, Mastodon, Reddit, ScuttleButt, etc.) into a Nostr account you can subscribe to: https://rsslay.nostr.moeStuck in Twitter (X)? Use EXIT.pub to automatically migrate all your content today: www.exit.pub
I am not mentioning NOSTR-based encrypted messengers (like Pulsar or 0xChat) here, for while they are good, they are still vastly inferior in terms of security to inherently privacy-oriented messengers like Session and SimpleX.
Did you find this bunch of links useful? Please zap me a cent 🙂
-
 @ d902ac01:6d69de69
2025-01-03 09:39:57
@ d902ac01:6d69de69
2025-01-03 09:39:57 -
 @ 1c7629da:d831cb25
2025-01-03 09:08:51
@ 1c7629da:d831cb25
2025-01-03 09:08:51Introduction
The Bitcoin Whitepaper is the foundation of the modern cryptocurrency world. Written by Satoshi Nakamoto, it marked the start of a revolution in finance. In this post, we take a detailed look at the Whitepaper: when and why it was written, what it contains, what is missing, and how Bitcoin has developed since then.
When and why was the Bitcoin Whitepaper published?
The Whitepaper, titled "Bitcoin: A Peer-to-Peer Electronic Cash System," was published on October 31, 2008, by Satoshi Nakamoto. During the global financial crisis, Nakamoto presented a decentralized solution for digital payments. The goal was to create an electronic payment system that operates without a central authority and allows users to send money directly to each other.
What is in the Bitcoin Whitepaper?
The nine-page document describes the technical foundation and philosophy behind Bitcoin. Here are the key points:
- Introduction: The problems with the current financial system are explained. Nakamoto describes the need for a system based on cryptographic proof instead of trust.
- Transactions: Bitcoin transactions are digital signatures passed in a chain of ownership. This prevents double spending.
- Timestamp Server: Transactions are grouped into blocks and linked through timestamps. This secures the blockchain.
- Proof-of-Work: To prevent manipulation, proof-of-work is required to create new blocks.
- Network: Participants send transactions to the entire network. Valid blocks are accepted by consensus and added to the blockchain.
- Incentives: Miners are rewarded with new bitcoins and transaction fees.
- Storage Space: The paper describes ways to save space by removing unnecessary transactions.
- Privacy: Bitcoin allows pseudonymous transactions since no real names are used, only public keys.
What is not in the Whitepaper?
Although the Whitepaper clearly defines the basics, many important details found in Bitcoin today are missing:
- 21 Million Bitcoin: The maximum supply of 21 million Bitcoin is not mentioned.
- Block Time: The average block time of 10 minutes is not specified.
- Mining Algorithm: The 1 MB block size limit and adjustments to mining difficulty are not included.
- Signature Methods: The paper does not describe specific signature methods like P2PKH or Schnorr signatures.
How is Bitcoin different from the Whitepaper today?
Bitcoin has changed significantly since the Whitepaper was published. Some of the biggest differences include:
- Mining: Bitcoin was originally mined using CPUs, but today specialized ASIC devices dominate.
- Consensus Mechanism: The idea of the "longest chain" has been replaced by the heaviest chain to prevent timewarp attacks.
- Transaction Types: Multi-signature addresses, Taproot, and other upgrades have been introduced.
- Scaling: Technologies like the Lightning Network have been developed to make Bitcoin faster and more scalable.
Conclusion
The Bitcoin Whitepaper is a masterpiece of clarity and simplicity that explains a complex idea in just a few pages. However, Bitcoin is not static – it has evolved continuously over the past 16 years. The Whitepaper remains the foundation that defines the vision of a decentralized money system for the world.
-
 @ 5c8a5765:4fc5edee
2023-11-22 22:38:03
@ 5c8a5765:4fc5edee
2023-11-22 22:38:03Read in english: Session removed PFS, we're doomed!!1
Автор: Кот Иван
Опубликовано также в IPFS!•••
PFS (Perfect forward secrecy) — это система, позволяющая в случае взлома одного ключа шифрования выдать лишь часть сообщений, но защитить другие части. Делается это простым образом: ключ шифрования переодически меняется. Из-за того, что Session убрал PFS, в случае взлома одного ключа хакеру станут доступны все ваши переписки. Разработчики Session лаконично возразили на это, что взлом ключа возможен лишь при физическом доступе к девайсу (а в этом случае сообщения можно прочесть и просто так) [0]. Насколько они правы?TL;DR: Они охуенно правы, но им стоит побеспокоиться о квантовых компьютерах.
•••
Давайте разберемся.
Протокол Session генерирует каждой учетной записи долгосрочную пару ключей X25519 (секретный и публичный) [1]. Секретный ключ X25519 состоит из 32 байтов (256 битов), или строку из 64 символов, которые включают в себя только цифры и буквы верхнего регистра [2][3].
Пример приватного ключа:
193FC8C3A73782DA18B238915C941CEF5E985DB388C881BD3C0E9EF496894A19
Предположим, что разработчики Session неправы, и попробуем посчитать, сколько времени займёт процесс взлома фразы, состоящего из 64 букв и цифр.
Количество всех возможных комбинаций любой строки вычисляется так [4]:
(Количество возможных символов)^(Длинна пароля)
В случае, если мы используем 26 букв английского алфавита и десять цифр (включая ноль), получается 36 вариантов символа. Длинна — как мы уже выяснили — 64. Наше уравнение — 36 в степени 64.
36^64 = 4.01199E+99
Следовательно, у ключа шифрования Session есть 4 011 199 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 возможных комбинаций. Цифру ещё можно выразить как 10^99*4, 12.3 Q (кветто) [5] или 4 дуотригинтиллиона. Для сравнения, это больше (примерно на 4 квинтиллиона), чем количество атомов в наблюдаемой вселенной (по оценкам — от 10^79 до 10^81) [6][7].
Для краткости, в будущем я буду обращаться к этому числу как к 12.3 Q, хотя его вполне можно было бы и назвать "число-пиздец". Так вот, теперь нам предстоит выяснить, как быстро компьютер сможет взломать пароль, если количество его комбинаций — 12.3 Q. Сайт Betterbuys [8] провел небольшое расследование этого вопроса и предложил, ссылаясь на источники, следующие схемы:
Эффективные ядра: 1/((1-Эффективность)+(Эффективность/Кол-во ядер)) — (мы предположим, что процессов посвящает 99% операций взлому пароля, поэтому эффективностью будет 0.99)
GFLOPS процессора: Частота процессора * Эффективные ядра
Количество операций в секунду: GFLOPS/Константа шифрования (расчитана на типичный компьютер 2015 года)
Время в секундах: x секунд = Комбинации/(количество операций в секунду)
Каков результат всех этих вычислений? Если заставить один компьютер 2015 года на процессоре Core i5-6600K взламывать ваш секретный ключ, у него займет это 3.5411902245474E+52 секунд — или 4 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 лет.А шанс случайно подобрать ключ — меньше 0.0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000003%.
Но что если компьютер будет не один?
Что если именно тебя атакует владелец ботнета, или хакерская группировка, или правительство со сверхкомпьютером? Ну, даже если мы подключим все существующие в мире компьютеры, включая ваш, ко взлому вашего ключа, на это всё равно уйдет уйма времени. Например, в 2015 году их было 2 миллиарда (2 000 000 000 000 000 000 000 000 000 000 000 000 000 лет взлома); но
даже если к 2023 мы изобрели в тысячу раз больше компьютеров, чем было (тысяча миллиардов), и все они (до музейных экспонатов) приобрели в два раза более сильный процессор, чем i5-6600K , у нас всё ещё остается 1 000 000 000 000 000 000 000 000 000 000 000 000 лет на взлом.Но что насчёт более вовременных методов взлома?
Здесь разработчики не соврали: современные методы взлома отметаются тем, как Session скрывает ваши метаданные. Когда сгенерированный Session ключ не связан с вами — это исключает индивидуальную атаку; когда пароль случаен, это исключает атаку со словарём [10]; когда пароль неизвестен даже вам самим, это исключает фишинговую атаку [10]; когда пароль длиннее 20-30 символов, это исключает атаку радужными базами [10]. Session также устойчиво противостоит MITM [10], Sybil и DRDoS-атакам.
Но что насчёт квантовых компьютеров?
Система шифрования, используемая Session (elliptic-curve cryptography [11]), действительно, уязвима перед квантовым компьютером, использующим алгоритм Шора [12]. Как скоро квантовый компьютер сможет взломать пароль с 12.3 Q комбинаций?
Согласно одним данным, всего за час, но при наличии от 20 [13] до 317 [14] миллионов кубитов (известный нам опубликованный лимит кубитов на сегодня — 433 кубита [15]). Согласно другим — уже с сегодняшним компьютером, но за 67 миллионов лет [16]. Согласно третьим — квантовый компьютер вообще едва ли сможет взламывать пароли: например из-за того, что компьютер должен быть достаточно стабильным для долгого взлома, или он должен иметь доступ к паролю (нужно взломать систему и получить напр. хеш пароля, ибо проверять состояние кубитов через интернет-запросы невозможно).
Тем не менее, из всех поднятых вопросов лишь квантовые компьютеры действительно представляют возможную опасность в будущем.
В конце концов, даже если вам удастся взломать 256-битный ключ, без доступа к девайсу вы сможете восстановить диалоги лишь за последние 14 дней (а также читать дальнейшие диалоги с этого момента), потому что сообщения старше этого срока перманентно удаляются с серверов [17].Выводы
- То, что Session отказался от PFS, никак не компромитирует вашу безопасность*.
- Знатокам кибербезопасности, продолжающим по сей день кричать про PFS как главную уязвимость Session, стоит прежде всего попробовать отгадать или подобрать мою любимую цифру — она где-то в диапазоне между 1 и 4 011 199 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000.
- Тем не менее, Session нужно обратить внимание на потенциальную грядущую опасность квантовых компьютеров.
- В какой-то момент Sesson должен начать переход на новый метод шифрования, устойчивый против квантовых алгоритмов.
*Когда количество нулей в вероятности (0,00..01) выше сотни, вероятность можно округлять до нуля.
•••
Источники:
[0] https://getsession.org/faq#session-pfs
[1] https://getsession.org/blog/session-protocol-technical-information
[2] https://crypto.stackexchange.com/questions/80601/what-is-the-key-length-of-shared-secret-by-curve-25519-ecdh
[3] https://medium.com/asecuritysite-when-bob-met-alice/having-your-crypto-handshaking-cake-and-eating-it-x25519-or-kyber-why-not-have-both-18b90f90dbbd
[4] https://www.betterbuys.com/estimating-password-cracking-times/
[5] https://en.wikipedia.org/wiki/Metric_prefix
[6] https://en.wikipedia.org/wiki/Observable_universe#Matter_content
[7] https://www.universetoday.com/36302/atoms-in-the-universe/
[8] https://www.betterbuys.com/estimating-password-cracking-times/
[9] https://www.worldometers.info/computers/
[10] https://stytch.com/blog/top-10-password-cracking-techniques/
[11] https://en.m.wikipedia.org/wiki/Elliptic-curve_cryptography
[12] https://en.m.wikipedia.org/wiki/Shor%27s_algorithm
[13] https://arxiv.org/pdf/1905.09749.pdf
[14] https://doi.org/10.1116/5.0073075
[15] https://spectrum.ieee.org/ibm-condor
[16] Sumanta Chatterjee (https://qr.ae/pKkcrh) states that the speed of password calculation can be found by the following formula: (number of password combinations)/(number of operations per second) = x seconds, where number of operations per second is calculated as follows: (number of petaFLOPS of a quantum computer)petaFLOPS, where 1 petaFLOSP equals 10^15 or 2^50 (https://en.wikipedia.org/wiki/FLOPS). According to TOP500 (https://top500.org/lists/top500/list/2022/11/), as of January 2023, the most powerful computer had a peak performance of 1685.65 petaFLOPS. So 12.3 Q/(1685.652^50) = 2.11394040995172541e+81 seconds = 66,988,000 years.
[17] https://getsession.org/blog/self-deleting-messages -
 @ 1cb14ab3:95d52462
2025-01-03 06:00:20
@ 1cb14ab3:95d52462
2025-01-03 06:00:20











































Previous Works in the Series:
More from Hes:
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 44dc1c2d:31c74f0b
2023-11-15 19:16:12
@ 44dc1c2d:31c74f0b
2023-11-15 19:16:12Chef's notes
So practically all recipes call for you to peel your potatoes. While it does make for a nice looking gnocchi, you can absolutely leave the skins on it, if you like a more rustic looking gnocchi. I do this when I feel lazy all the time and it still turns out great.
When incorporating the eggs and flour, having a spatula or a bread tool is really helpful here.
When you're at the stage of boiling your made Gnocchi, you will know they are done when they float to the top of the pot.
Details
- 🍳 Cook time: 1 hour
Ingredients
- 2 pounds of starchy potatoes, (IE 2 large russets)
- 1/4 cup egg, (lightly beaten)
- scant 1 cup of unbleached all-purpose flour
- fine grain sea salt
Directions
- Fill a large pot with cold water. Salt the water, peel then cut potatoes. Bring the water to boil and cook tell potatos are tender and mashable
- Remove potatoes from the water, drain and mash until there are no noticeable lumps.
- Let the potatoes cool spread out across your work surface for ten or fifteen minutes. Long enough that the egg won't cook when it is incorporated into the potatoes.
- Pull the potatoes into a soft mound. Drizzle with the beaten egg and sprinkle 3/4 cup of the flour across the top.
- After the flour and the egg is incorporated into the potato, gently kneed the dough
- The dough should be moist but not sticky. It should feel almost billowy.
- Cut it into 8 pieces. Gently roll each 1/8th of dough into a snake-shaped log, roughly the thickness of your thumb. Use a knife to cut pieces every 3/4-inch. Dust with a bit more flour.
- So this next bit is optional you dont need to do this but it mkae for better looking gnocchi.
- To shape the gnocchi hold a fork in one hand and place a gnocchi pillow against the tines of the fork cut ends out.
- With confidence and an assertive (but very light) touch, use your thumb and press in and down the length of the fork. The gnocchi should curl into a slight "C" shape, their backs will capture the impression of the tines as tiny ridges (good for catching sauce later). Set each gnocchi aside, dust with a bit more flour if needed, until you are ready to boil them.
- Boil the Gnocchi and Serve
-
 @ 44dc1c2d:31c74f0b
2023-11-15 18:48:12
@ 44dc1c2d:31c74f0b
2023-11-15 18:48:12Chef's notes
Not a lot of notes here. This recipe is pretty straight forward. I have used half-and-half instead of whole milk in the past, and it turns out great. Low and slow here is the key.
What I mean by a sauce catching pasta is anything with a lot of surface area for the sauce. IE angle hair is not a good idea to use here.
Details
- ⏲️ Prep time: 10 ish min
- 🍳 Cook time: 2 1/2 hours
Ingredients
- 1 medium onion, chopped
- 1 celery stalk, chopped
- 1 small carrot, peeled, chopped
- 3 Tbsp. extra-virgin olive oil
- 1 lb. ground beef chuck
- Kosher salt
- 3 oz. thinly sliced pancetta, finely chopped
- 1 cup dry white wine
- ⅓ cup tomato paste
- 1 bay leaf
- Pinch of finely grated nutmeg
- 2 cups (or more) chicken stock
- 1 cup whole milk
- 2 oz. finely grated Parmesan (about ½ cup), plus more for serving
- Some form of pasta to serve with tagliatelle or pappardelle. really any "sauce catching" pasta will do.
Directions
- Pulse onion, celery, and carrot in a food processor until very finely chopped. Transfer to a small bowl.
- Heat oil in a Dutch oven or other large pot over medium. Break beef into small clumps (about 1½") and add to pot; season lightly with salt. Cook, stirring occasionally but not breaking meat apart, until beef is lightly browned but not crisp, 6–8 minutes
- Wipe out pot. Cook pancetta in pot over medium heat, stirring occasionally, until pancetta has released some of its fat and is crisp, 6–8 minutes.
- Add onion mixture to pot and cook, stirring occasionally, until vegetables are very soft and beginning to stick to surface, 6–8 minutes.
- Return beef to pot and pour in wine. Reduce heat to medium-low and cook, smashing down on beef with a wooden spoon, until wine is evaporated, surface of pot is almost dry, and meat is finely ground, 12–15 minutes.
- Add tomato paste, bay leaf, and nutmeg and cook, stirring occasionally and still pressing down on meat, until tomato paste is slightly darkened, about 5 minutes.
- Pour stock and milk into pot; add a pinch of salt. Reduce heat to the lowest setting and cook, uncovered and stirring occasionally, until meat is very, very tender, 2–2½ hours.
- There shouldn’t be any rapid bubbles at this stage. Instead, the sauce should release the occasional small bubble or two. When finished, the sauce should have the texture of and look like a sloppy joe mixture.
- If the liquid reduces before the meat is completely tender, add an extra ½ cup stock and continue cooking. Discard bay leaf. Taste sauce and adjust seasoning with salt; keep warm.
- Cook pasta in a large pot of boiling salted water. If using fresh pasta, cook about 3 minutes. If using dry, cook until very al dente, about 2 minutes less than package directions.
- Using tongs, transfer pasta to pot with sauce. Add 1 cup pasta cooking liquid and ½ cup Parmesan. Increase heat to medium, bring to a simmer, and cook, tossing constantly, until pasta is al dente and liquid is slightly thickened, about 2 minutes.
- Transfer pasta to a platter and top with more Parmesan. Do Ahead: Sauce can be made 4 days ahead. Cover and chill.
-
 @ a012dc82:6458a70d
2025-01-03 02:14:32
@ a012dc82:6458a70d
2025-01-03 02:14:32Discover the controversial perspective that the fiat currency system, managed by central banks, resembles a legal Ponzi scheme. Uncover the nuances of fiat currency, central banking, and its potential parallels to Ponzi schemes. Also, explore the significance of Bitcoin in challenging traditional financial norms and its role as an emerging alternative. Is the foundation of our modern financial system truly as it seems, and can Bitcoin redefine the future of money?
Table Of Content
-
The Fiat System: A Legal Ponzi Scheme?
-
Bitcoin's Challenge to the Fiat System
-
Bitcoin's Resistance to Manipulation
-
The Emergence of Bitcoin ETFs
-
Root Causes of Financial Frauds
-
Conclusion
-
FAQs
The Fiat System: A Legal Ponzi Scheme?
In the world of finance and economics, few terms are as polarising and provocative as "Ponzi scheme." Often associated with high-profile frauds and financial scandals, the concept of a Ponzi scheme typically conjures images of disgraced con artists and their unsuspecting victims. However, could it be that a similar model, albeit operating legally, is at the very core of our modern financial system?
At its core, the fiat monetary system is characterised by a crucial feature: the absence of intrinsic value. Unlike Bitcoin or other commodities that underpinned historical monetary systems, fiat currencies like the US dollar are not backed by tangible assets. Instead, their value is derived solely from the trust and confidence that people place in the issuing government or central authority.
A Ponzi scheme operates on the premise that returns to earlier investors are paid with the capital of newer investors, creating the illusion of profitability. This structure works as long as fresh investments continually pour in, masking the absence of a legitimate revenue source. The fiat system, in an eerily similar fashion, is perpetuated by continually increasing debt and the circulation of more currency.
In the fiat system, governments create money by issuing debt. The expansion of the money supply comes from loans that must eventually be repaid with interest. When these loans come due, governments often issue new debt to pay off the old, resulting in a growing debt burden. Just as a Ponzi scheme must attract new investors to maintain the illusion of solvency, governments must accumulate more debt to meet previous obligations, putting the burden on future generations.
The fiat system's longevity relies on a constant cycle of currency devaluation and inflation. Governments can effectively reduce the real value of their debt by inflating the currency, shifting the cost onto the populace. While this may seem sustainable in the short term, it mirrors the Ponzi scheme's tactic of robbing Peter to pay Paul. In both cases, there's a fundamental issue of sustainability.
Bitcoin's Challenge to the Fiat System
In recent years, Bitcoin has emerged as a revolutionary force challenging the traditional fiat monetary system. Built on the principles of decentralisation and indepence, poses a significant threat to the established norms of central banking and government-issued currencies.
Bitcoin operates on a decentralised network of computers, known as the blockchain. Unlike fiat currencies controlled by central banks, Bitcoin is not subject to the whims of any single authority. This decentralised nature promotes transparency, security, and trust among its users, effectively challenging the centralised control of fiat money.
One of Bitcoin's most distinctive features is its capped supply of 21 million coins. This scarcity stands in stark contrast to fiat currencies that can be printed endlessly by governments. Bitcoin's limited supply acts as a hedge against inflation, making it an attractive store of value.
Bitcoin's technology ensures secure ownership of assets. Users have control over their private keys, reducing the risk of unauthorised seizures or asset freezes, a concern in the fiat system.
Bitcoin is accessible to anyone with an internet connection, providing financial inclusion to the unbanked and underbanked populations. This inclusivity challenges the exclusivity of fiat systems, which often require intermediaries and traditional banking infrastructure.
The decentralised nature of Bitcoin makes it resistant to censorship, ensuring that transactions are not subject to arbitrary restrictions or controls, as seen in some fiat-based systems.
Bitcoin's disruptive potential in the world of finance is undeniable. Its challenge to the fiat system represents a shift in the way we think about money, wealth, and economic systems. As Bitcoin continues to gain mainstream acceptance, it raises fundamental questions about the future of currency and financial infrastructure.
Bitcoin's Resistance to Manipulation:
In the world of finance and economics, the notion of a truly decentralised, trustless, and censorship-resistant form of money is both revolutionary and, to some, unnerving. Bitcoin, stands as a testament to the potential of digital assets to challenge conventional fiat currencies and the centralised systems that underpin them. A fundamental aspect of Bitcoin's allure is its resistance to manipulation, a quality that sets it apart from traditional financial systems and even some other cryptocurrencies.
At its core, Bitcoin operates on a blockchain – a distributed ledger that records all transactions across a vast network of computers. This decentralised nature, combined with cryptographic principles, ensures a high degree of security and transparency. Unlike fiat currencies, which are subject to the whims of central banks and governments, Bitcoin's monetary policy is encoded in its software. The total supply is capped at 21 million coins, and new Bitcoins are issued in a predictable, diminishing manner through a process known as mining.
Bitcoin's resistance to manipulation stems from several key factors. Firstly, its decentralised network is maintained by a diverse group of miners worldwide, making it nearly impossible for any single entity to exert control over the system. Unlike centralised financial institutions that can manipulate interest rates, print money at will, or engage in other questionable practices, Bitcoin's protocol operates independently of human interference.
Secondly, Bitcoin's security mechanisms, such as proof-of-work, ensure that transactions are validated by a competitive network of miners. This makes it incredibly costly and difficult for anyone to compromise the network. Additionally, the immutability of the blockchain means that once a transaction is recorded, it cannot be altered or deleted, providing a robust defence against fraud or manipulation.
Lastly, Bitcoin's open-source nature allows the global community to scrutinise its code and propose changes through a consensus-driven process. Any updates or improvements to the network require majority approval, preventing any single entity from manipulating the protocol to suit its interests.
As traditional fiat currencies face challenges related to inflation, political influence, and centralised control, Bitcoin's resistance to manipulation positions it as a compelling alternative. While it is not without its own set of unique risks, Bitcoin's core principles of decentralisation and transparency contribute to its appeal as a novel form of digital money that empowers individuals and resists manipulation by powerful institutions.
The Emergence of Bitcoin ETFs
The emergence of Bitcoin Exchange-Traded Funds (ETFs) represents a notable development in the world of digital investments, serving as a bridge between traditional financial markets and the realm of digital assets. These ETFs provide a convenient and regulated avenue for investors to gain exposure to Bitcoin without the need to directly possess the cryptocurrency. This comes at a time when Bitcoin has garnered widespread recognition and piqued the interest of both retail and institutional investors.
One crucial aspect of Bitcoin ETFs is their potential to simplify the investment process. Rather than dealing with the intricacies of owning and securely storing Bitcoin in digital wallets, investors can purchase shares of a Bitcoin ETF through conventional brokerage accounts. This streamlined approach lowers entry barriers for those who might have hesitated to navigate the complexities of Blockchain and self-custody.
Furthermore, Bitcoin ETFs offer regulatory oversight and investor protection. These funds operate within the bounds of financial regulations and undergo scrutiny from relevant authorities, enhancing security for investors. They also confer an aura of legitimacy upon the digital asset market, rendering it more appealing to institutional investors that necessitate adherence to regulatory standards.
The advent of Bitcoin ETFs mirrors the evolving role of digital assets. Bitcoin, once considered a niche asset, has matured into a mainstream investment choice. The interest in Bitcoin ETFs signifies the growing embrace of digital assets within the conventional financial system.
However, the ascent of Bitcoin ETFs also ignites discussions about their potential impact on the digital asset market. Some believe that they might stimulate increased demand for Bitcoin, potentially influencing its price dynamics. Nonetheless, these ETFs mark a pivotal step in the broader adoption of digital assets, attracting a wider range of investors to the digital asset sphere.
Root Causes of Financial Frauds
The root causes of financial fraud extend beyond the realm of digital currencies, highlighting that deception-driven activities primarily originate outside the digital asset ecosystem. While the term "digital currency fraud" often suggests that virtual assets are the focal point of these fraudulent activities, in reality, it's seldom the case.
Contrary to the prevailing narrative that digital currencies are a haven for illicit activities, fiat currency remains the preferred choice of financial criminals. Reports from the US Treasury and EUROPOL emphasise that traditional financial channels, associated with fiat transactions, still play a more substantial role in illegal financial activities than virtual assets. Fiat currencies, despite being subject to stringent regulations and oversight, continue to be the medium of choice for criminal activities.
The heart of the matter lies in distinguishing between the origin of the fraud and the role of digital currency within it. In numerous instances, the initial fraudulent activity takes place within non-financial domains or fiat transactions. An illustrative example is credit card fraud, which primarily employs fiat-based payments for unauthorised charges. While some cases culminate in the acquisition of digital currencies, the initial fraudulent activity is rooted in fiat-based mechanisms.
Even in the context of digital currency romance scams or investment schemes, the crux of the fraud lies in establishing non-financial relationships with victims. Funds often start as fiat, moving through traditional payment channels before making their way into digital currencies. The fraud's inception, therefore, remains primarily in the fiat space, and there are several opportunities for intervention through conventional financial systems.
Decentralised Finance (DeFi) hacks, which sometimes fall within the digital currency realm, are more related to risk management protocols within the DeFi ecosystem. These vulnerabilities are often not tied to digital currencies themselves but stem from flaws in DeFi platforms, frequently involving phishing tactics.
To combat these financial frauds with digital currency involvement, it is essential to recognize the preliminary stages of deception, which usually unfold outside the digital asset landscape. Enhancing AML and transaction monitoring intelligence tools, combined with educational efforts, can proactively identify and mitigate potential fraud risks in the fiat sector, even before they intersect with digital currencies. This approach can address the root causes of financial fraud effectively, irrespective of whether they subsequently involve digital currencies or traditional financial systems.
Conclusion
The emergence of Bitcoin has shed light on a widespread, yet often unacknowledged, issue in the world of finance—the fiat scam. Fiat currencies, including the U.S. dollar and the euro, are the lifeblood of traditional financial systems, issued and governed by central banks. However, these currencies lack intrinsic value and are subject to manipulation by central authorities, akin to a legal Ponzi scheme.
Central banks, empowered by governments, possess the authority to create and manage fiat money. They can print additional currency at will, which devalues existing holdings and redistributes wealth, all under the umbrella of legality. Moreover, fiat transactions typically involve intermediaries, like banks, adding layers of complexity and fees.
Bitcoin has introduced an alternative financial paradigm. Unlike fiat, Bitcoin operates on a transparent blockchain network with a predetermined supply, immune to central authority manipulation. It has become a symbol of decentralised financial systems and digital scarcity.
As the world grapples with this shift, it is essential to acknowledge the fiat scam—a legal Ponzi scheme perpetuated by central banks. With increased awareness and the rise of Bitcoin, the financial landscape is poised for transformation, challenging the dominance of fiat currencies.
FAQs
Is the Fiat System Truly a Legal Ponzi Scheme? The fiat system shares similarities with a legal Ponzi scheme in its reliance on continual growth and debt accumulation to sustain itself, but it's important to note that the key difference is legality. Central banks have the authority to issue fiat, making it legal, while Ponzi schemes are fraudulent by nature.
How Does Bitcoin Challenge the Fiat System? Bitcoin challenges the traditional fiat system through decentralisation, a limited supply of 21 million coins, user-controlled assets, accessibility for the unbanked, and resistance to censorship, providing an alternative to centralised fiat currencies.
What Are the Root Causes of Financial Frauds? Root causes of financial frauds often start with non-financial activities or fiat transactions. Credit card fraud, romance scams, and investment schemes typically begin with fiat-based transactions before involving digital currencies. Enhancing AML and transaction monitoring tools can proactively address these root causes in both digital and traditional financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1a5cff51:01c75f78
2025-01-02 23:56:49
@ 1a5cff51:01c75f78
2025-01-02 23:56:49For the longest time I was a strict and rather arrogant atheist and often went so far as too consider myself more an anti-theist. I grew up in a highly catholic environment and since I tend to do the opposite of what people expect of me, I went the exact opposite direction, discovered Metal which lead straight to Black Metal and I became totally anti-christian. Though most of the Christians I encountered where either my age or had such a shallow understanding of their scripture, that even I knew perfectly well that they had no idea what they were saying most of the time.
I’ve since done away with all of that childish nonsense (except the music, of course), after a trip on shrooms led me down more rabbit holes then I could imagine. Throughout my research I discovered Jung and it dawned on me, how much of my life was steered by synchronicities without even knowing what that was. Coming to terms with having been his ignorant when it comes to spirituality has been a humbling experience and my shadow work is far from complete.
I just find it kinda ironic how it's now mostly Christians that seem sane and consistent in their behaviour in these bizarre times and I notice that I feel comfortable being surrounded by them, especially here on Nostr.
-
 @ 44dc1c2d:31c74f0b
2023-10-10 21:22:43
@ 44dc1c2d:31c74f0b
2023-10-10 21:22:43Chef's notes
Chicken notes :
-
You can tenderize the chicken if you want (makes for a "bigger" piece that will cover more waffle also speeds up cook time)
-
If you choose not to tenderize your chicken and are left with thicker thighs, Fry until the crust is a nice golden brown then finish baking the chicken in the oven (around 350F) to finish cooking the chicken through. Should only take about 10 or 15 min.
Flour and dredge notes :
- Feel free to add more spices into the flour here. Add some extra onion, garlic and paprika or some fresh oregano to give the crust an extra kick of you want. Experiment and play with the flavor here and in the buttermilk marinade.
Waffle notes :
This is mostly a base recipe for savory waffles if you like things sweet add some sugar and some Vanilla extract to the waffle.
Details
- ⏲️ Prep time: 4 ish hours
- 🍳 Cook time: 35 ish min
- 🍽️ Servings: 5 ish
Ingredients
- 1 cup (120 grams) all-purpose flour
- ½ cup (70 grams) yellow cornmeal
- ¼ cup (28 grams) cornstarch
- 1 teaspoon baking powder
- ½ teaspoon baking soda
- 1 teaspoon fine sea salt
- ¼ teaspoon freshly ground black pepper
- 2 cups (475 ml) buttermilk
- 2 large eggs
- 4 tablespoons (56 grams) butter, melted and cooled slightly
- 3 ounces (84 grams) smoked Gouda, shredded
- ⅓ cup minced fresh chives
- For the Chicken
- 4 -5 ish thighs
- 2 1/2 cups buttermilk
- Salt and Pepper to taste
- at least 1 teaspoon Onion powder
- at least 1 teaspoon paprika
- at least 1 teaspoon garlic powder
- 2 to 3 ish cups flour (for your crust. See notes.)
- Maple Syrup
- Hot Sauce (Optional)
Directions
- Start by marinating your chicken. Get your thighs, buttermilk, paprika, onion powder, garlic powder, salt and pepper into a bowl or plastic bag and set aside to marinate for at least two hours in the fridge. (up to 4)
- The batter can be made ahead of time as well (no more than a few hours preferably).
- Mix all the dry ingredients together (minus the chives and cheese) then add the liquids.
- Add cheese and chives (save a bit for a waffle topping if you want.)
- Once the chicken has marinated a bit dredge your chicken in flour (see notes). Let set for approximately 20 min after dredging.
- Fry tell done. Also start to cook waffles while the chicken is cooking.
- Top the Waffles with the chicken, the extra cheese and chives, a healthy splash of syrup, plus your favorite hot sauce and Tuck in!
-
-
 @ f4bf1fb5:b428f8d5
2025-01-02 23:44:03
@ f4bf1fb5:b428f8d5
2025-01-02 23:44:03DEG Mods is using a new piece of technology, specifically a new communications protocol that's censorship-resistant called NOSTR, and as such, it uses a non-traditional means of creating an account, as well as how you sign into sites that uses such new tech, like DEG Mods.
Since this is new to most people, it can be somewhat daunting, scary, suspicious, as with anything new, especially something where the individual holds sole responsibility of what they created, as there would be nobody to help them, in the case of creating an account, retrieve their account if it gets lost or if it gets compromised.
We'll skip on explaining in proper detail what NOSTR is specifically, and go straight ahead and explain the direct process of how to create an account, and how to sign in.
How to create an account on DEG Mods
Creating a DEG Mods account is creating a NOSTR account, and that can be done in multiple ways, from using a browser extension, to using a mobile app, to generating it directly on the site.
For the purposes of this current guide, and for the current version of DEG Mods, we'll only be guiding you on how to create a DEG Mods/NOSTR account using a browser extension. With that said, there are currently multiple ones that has been developed for this specific purpose. Some with more features than others, or some with a better UI/UX. For now, we'll be recommending you to install one called Nostr Connect (Chrome / FireFox)
Once you have installed that extension on your preferred browser, make sure that you have the extension pinned on your browser (for easy access and use). To do that, you'd have to open the quick extension preview window on your browser (for example, on Chrome or Brave, that'd be the puzzle-piece icon) and then click the pin icon next to the extension you want to pin. In this case, that'd be the Nostr Connect extension.
Now, click on the Nostr Connect extension icon and then click the gear icon, which will open a new tab/page to start the account creation process.
It's pretty straight forward from there. Just click on the "Generate" button then the save button. This will generate for you a pair of keys/addresses. The shown one is your private key (think of it as your password) that starts with 'nsec', which you should keep safe somewhere (like on a password manager), because if you lose it then you won't be able to access your account, or if it gets leaked then everyone would be able to access your account, and we won't be able to help you retrieve your private key/address or reset it to something else. You are the sole responsible person for your account's security.
Once you're done, close that page then click on the extension icon again. It will now show you your public key/address (think of this as your user ID).
How to sign into DEG Mods
Once you have the DEG Mods site open, click the 'Login' button at the top right. A popup will appear with an option to login with an extension. Click that and another popup will appear (this is your extension being triggered) asking you to authorize the login. Tick the box to remember this action if you'd like (for convenience) and click authorize.
Done. You've now created an account and logged into the site. Now you can publish game mods, comment on posts/pages, react, and more.
Video guide
If you don't feel like reading, or rather, if you're more comfortable watching a video guide on how to do all of this, then here's that video.
Questions and answers
Is this safe?
As we did not create these browser extensions or mobile apps, we can't necessarily guarantee anything, however, until proven otherwise, the browser extensions or mobile apps we recommended here are safe. If you're a programmer, you can check their code directly to see if there's anything suspicious, as they are open source.
Why do you have such a complicated way to make an account?
We understand that this may seem complicated, but it isn't if you think about it.
What did you actually do? You installed a browser extension, generated an account (a key pair), and signed in with a click of a single button. Install, generate, login.
It seems complicated because its something you haven't done before and outside of what you're used it, but in reality, it's actually a lot simpler than traditional methods, which involves creating an email address, then creating an account on each site you want to visit. With this, it's a one time event and you can log into DEG Mods, or any other site or app that's built ontop of NOSTR, with that same account, which holds all of your profile data and posts.
Why don't you have a normal way to make an account on DEG Mods?
Since DEG Mods is a truly censorship-resistant mods site, building the site on NOSTR was the ideal choice to make, which resulted in giving you, the user, the mod creator, and the mod enjoyer, the power of controlling your content, your posts, your profile, your account. We can't ban you because you have a NOSTR account, nor can we take down your posts/pages.
If we had made it so that you can use the normal way of making an account, where you have an email and password combo, then we can do all of those ban things. We would have the power to censor you. You'd have zero power, and we didn't want that outcome.
What do you mean you can't help me restore my account or reset my password?
The account you created was, because of the tech being used, created on your device, and not on any server that we control. As such, we don't see or save your account data (we don't know your private key/address, and we shouldn't). You also cannot change the private key/address of your account, as there is no way to do so / this is how the tech was developed.
Will you maintain and update this guide as time move forwards?
Yes. Since its in our interest to have more users on DEG Mods, we'll be updating this post so that it'll continue being useful to new users.
Can't you make a browser extension or app specifically for DEG Mods?
While it is possible, and we are interested in doing so, as to keep it always up to date and add more features, have the best UI/UX possible, etc, it would require us to receive funds and allocate it for this specific development. So the answer to this question is: If we're successful enough to have the funds to develop it.
Why can't I log into DEG Mods on my mobile phone?
You would need a NOSTR mobile signer for that, and we'll also need to implement such a feature to tell the site that you have that app. It'll come with time, and I'd say sooner rather than later.
-
 @ 11d0b667:53e00ef7
2023-10-04 04:42:20
@ 11d0b667:53e00ef7
2023-10-04 04:42:20(Taken from the Bozeman Daily Chronicle, December 16, 2007) By Walt Williams
ENNIS - More than a century ago, a wolf-like creature prowled the Madison Valley, killing livestock and letting out screams that one account said would leave a person's hair standing on end.

DEIRDRE EITEL/CHRONICLE Jack Kirby poses in Ennis next to the wolf-like creature his grandfather shot in 1886 in the Madison Valley. He is holding the G.W. Morse rifle that was used to kill the animal. Kirby retrieved the mount from an Idaho museum where it was being stored.A bullet from a Mormon settler's rifle ended the animal's life and triggered stories of the creature that were passed along through generations of family history and local folklore.
The only evidence of the creature's existence was a missing taxidermy mount and a grainy black-and-white photograph of that mount - which fueled strange speculation about what kind of animal it really was.

Now after 121 years, the taxidermy mount has been found. The creature that once spooked some of the Madison Valley's first white settlers has come home.
“I never doubted the story,” said Jack Kirby, grandson of the settler who shot the animal.
*After reading a Halloween-themed Chronicle story about local legends of strange creatures, Kirby tracked down the mount in the Idaho Museum of Natural History in Pocatello.
The museum has since loaned it to him to put on display at the Madison Valley History Museum, although at the moment it resides in the basement of a building on the north edge of town.

The “ringdocus” or “shunka warak'in” - two of the names it has been given over the years - strongly resembles a wolf, but sports a hyena-like sloping back and an odd-shaped head with a narrow snout. Its coat is dark-brown, almost black, with lighter tan areas and a faint impression of stripes on its side.
It measure 48 inches from the tip of its snout to its rump, not including the tail, and stands from 27 to 28 inches high at the shoulder.
The mount is in amazingly good shape, showing no signs of wear and tear and retaining the color of the fur. It arrived in Ennis Friday.
One of its first stops was the gravesite of the man who shot it, Israel Ammon (I.A.) Hutchins.
“We took him down to the cemetery to see I.A. to let him know (the creature) is back in the valley,” said Kirby's wife, Barbara.
Hutchins shot the animal in 1886 on what is now the Sun Ranch, but not on his first try. He accidentally shot and killed one of his cows when he first spotted the creature on his land, his son Elliott Hutchins recounted in his memoirs.
He killed the strange animal when it appeared on his land a second time and traded the body with entrepreneur Joseph Sherwood for a new cow.
Sherwood was a taxidermist. He mounted the animal and put it on display in his combination store-museum at Henry's Lake in Idaho. His taxidermy collection was later given to the Idaho Museum of Natural History, where it was kept in storage.
The creature apparently baffled the people who saw it alive, and some speculated it was a hyena escaped from a circus rather than a wolf. The younger Hutchins remembered its haunting screams at night and wrote that after it was shot and in its death throes, the animal bit through a half-inch rope with a single bite and “exerted his very last strength to reach any one of us.”
The story of the “ringdocus” - as Sherwood reportedly named it - reached a national audience when the prolific writer and naturalist Ross Hutchins wrote about it in his 1977 autobiography, “Trails to Nature's Mysteries: The Life of a Working Naturalist,” and included a picture of the mount. I.A. Hutchins was his grandfather.
The tale was again picked up by writers Loren Coleman and Jerome Clark in their book “Cryptozoology A to Z.” In that book, Coleman linked it to a Native American legend about the “shunka warak'in,” a creature that snuck into camps at night to steal dogs.
The animal has so far eluded identification. The younger Hutchins wrote that a detailed description was sent to the Smithsonian Institution, which wasn't able to identify it.
The picture of the mount included the scientific-sounding name “Guyasticutus” as a label for the creature, but the name may have been tongue-in-cheek. Early accounts report that the Guyasticutus was a mythical creature invented by traveling showmen to swindle gullible ticket-buyers.
Coleman and Clark suggested that a DNA test should be done on the mount to determine what it is. Kirby, however, was not so certain he was ready to end a mystery that had been passed down by his family for four generations.
“Do we want to know?” he said.
The mount will be displayed in the Madison Valley History Museum when it reopens in May.
***On 25 May 2018, a wolf like animal resembling a Shunka Warakin was shot in central Montana. The unusual paws were among the characteristics experts thought didn't belong to either a wolf or dog.

“Several things grabbed my attention when I saw the pictures,” said Ty Smucker, wolf management specialist for Montana FWP. “The ears are too big. The legs look a little short. The feet look a little small, and the coat looks weird. There’s just something off about it.”

The body of the animal shot outside Denton has now been transported, examined and frozen. Results from its DNA testing will likely take weeks to process.
Smucker’s own speculation runs toward some type of wolf/dog hybrid.
-
 @ 6bae33c8:607272e8
2025-01-02 22:23:01
@ 6bae33c8:607272e8
2025-01-02 22:23:01I went 2-3 last week, which only matters bercause I was 5-0 in Week 16, and I thought I might have finished with an epic run, but it was not to be. Week 18 is always fun to guess who’s trying and who’s packing it in. My MO is usually to bet the teams who are missing the playoffs, have nothing to play for, but also no reason not to go all out. They’re usually undervalued.
Browns at Ravens — The Ravens need this game to win the division, so I expect them to try, though they might pull their starters in the second half if they’re way up. I’ll say Browns +14.5 and probably lay the wood.
Bengals at Steelers — The Bengals have a long shot chance of making the playoffs and will go all out. The Steelers are playing for the three seed, but they’d need the Browns to beat the Ravens. Hard to say whether they’ll go all out, but I’ll make it Bengals -3.
Panthers at Falcons — The Falcons need this (but also a Bucs loss), and the Panthers will go all out because they have no reason not to. I’ll say Panthers +4.5.
Killer Redskins at Cowboys — The KRs can move between the sixth and seventh seeds, but I doubt they’ll leave their starters in long. I’ll say KRs +6.5.
Bears at Packers — The Packers can move between the sixth and seventh seeds, but it doesn’t matter much. I’ll make it Bears -3.5.
Jaguars at Colts — Both teams are playing for nothing. Mac Jones is playing decently, and it’s unclear who’s under center for the Colts. I’ll say Jaguars +3.5.
Bills at Patriots — It’ll be Mitch Trubisky against maybe Drake Maye. The Bills don’t need it. I’ll say Bills +5.5.
Giants at Eagles — Neither team needs it, the Eagles are probably resting Saquon Barkley who has a chance to break the single-season rushing record against his old team that decided not to pay him. I’ll make it Giants -2.5.
Saints at Buccaneers — The Bucs need this, the Saints are a destroyed team. Maybe Derek Carr plays, but I’d be surprised. I’ll say Saints +14.5.
Texans at Titans — The Texans don’t care, the Titans can try their hardest. I’ll make it Texans +4.5.
49ers at Cardinals — Two failed teams playing out the string. I’ll say pick ‘em and probably stay away.
Chiefs at Broncos — The Chiefs are resting everyone, the Broncos need to win in order to get in. I’ll make it Chiefs +8.
Seahawks at Rams — The Rams have clinched, can only toggle between the third and fourth seeds. I’ll say Seahawks -6.
Chargers at Raiders — The Chargers can only toggle between the fifth and sixth seeds, the Raiders are obviously done. Let’s say Chargers +6.5.
Dolphins at Jets — Tua’s probably not playing, but the Dolphins still have an outside chance at the playoffs. I’ll make it a pick ‘em and lean Dolphins.
Vikings at Lions — This is for the No. 1 seed and a bye in the NFC. I’ll say Vikings +2.5 and lean Vikings due to their defense.
-
 @ 44dc1c2d:31c74f0b
2023-09-28 18:43:53
@ 44dc1c2d:31c74f0b
2023-09-28 18:43:53Ingredients
- 1 tablespoon extra virgin olive oil
- 2 cups cubed butternut squash (about 1 small squash)
- 2 tablespoons fresh thyme leaves
- 1/2 teaspoon crushed red pepper flakes
- kosher salt and black pepper
- 2 cloves garlic, smashed
- 8 slices thick-cut bacon
- 2 tablespoon chopped fresh rosemary
- 1/2-1 teaspoon cayenne pepper
- 2 teaspoons honey
- 1 pound dry linguine pasta
- 2 large eggs, at room temperature, beaten
- 1 cup grated parmesan cheese, plus more for serving
- 2 tablespoons salted butter, at room temperature
Directions
- Preheat oven to 400 degrees F. On a baking sheet, toss together the olive oil, butternut squash, garlic, thyme, and a pinch each of crushed red pepper flakes, salt, and pepper.
- On a plate, rub the bacon with rosemary and cayenne, drizzle with honey. Lay the bacon over top.
- Transfer to the oven and roast for 10 minutes, flip the bacon and bake another 5-8 minutes, until the bacon is crisp, watch closely. Remove the bacon.
- If squash needs more time, return to the oven for another 10 minutes, or until the squash is tender.
- Transfer the squash and garlic to a food processor. Puree until smooth. Season with salt and pepper. Roughly chop the bacon, reserve for topping.
- Meanwhile, whisk together the eggs and parmesan.
- Boil the pasta until al dente. Before draining, scoop out 1 cup pasta water, then drain the pasta and add the pasta back to the hot pot.
- Immediately add the egg/cheese mixture, tossing quickly (to ensure the eggs do not scramble) until the eggs thicken and create a sauce.
- Add the butternut squash puree, and the butter, tossing to combine. Thin the sauce with the reserved pasta water until it reaches your desired consistency.
- Divide the pasta between plates. Top with bacon. Twirl the pasta up…EAT and ENJOY.
-
 @ 1cb14ab3:95d52462
2025-01-02 21:31:48
@ 1cb14ab3:95d52462
2025-01-02 21:31:48
No. 6 - Zhujiajiao Canal Chasing

For a tranquil escape from the hustle and bustle of the city cruise to Zhujiajiao -- an epic water town dating back to the Ming and Qing dynasties. It's only about 50 kilometers from the downtown and makes for an easy day trip. Hop on the subway and get there in an hour. Zhujiajiao has canals, bridges, and ancient buildings, offering a glimpse into the town's rich history. Take a boat ride along the canals for the best views of traditional houses and temples. Then explore the town on foot and get lost in attractions like the Kezhi Garden, Yuanjin Temple, and the Qing Dynasty Post Office. Don't forget to grub-up with all of the great food vendors nearby.
No. 7 - China Art Museum

China Art Museum is absolutely worth the trip solely for its awe-inspiring architecture. The towering structure casts a tall shadow over bystanders. Step inside and you'll find a world of art waiting. The blend of permanent and temporary exhibits offers hours of art-gazing. Give yourself at least half a day to fully immerse in the creative haven in Pudong. To get to the China Art Museum, you can take Line 2 of the Shanghai Metro and get off at the Pudong Avenue Station (Chinese: 浦东大道站). The museum is located near Exit 4 of the station.
No. 8 - Days on The West Bund

Hands down my favorite place in Shanghai. This spot is the go-to for a perfect weekend under the sun. You'll find me setting up a blanket with beer, cards, and snacks, along with a slackline and spike ball setup nearby, surrounded by dogs running around, enjoying the company of old and new friends. When you want a little movement enjoy some climbing, skating, running, or basketball after work. The West Bund is an oasis amidst the chaos of the city. But beware - its popularity is growing, so tread lightly.
No. 9 - Nights Under the Lupu Bridge

Nights under the Lupu Bridge are where it's at, man. Hop on your scooter and cruise over for the ultimate skyline views. Stroll along the walkway, munch on street food, sip drinks, and groove to live tunes. Street vendors serve up traditional snacks and crafts, and the vibe gets lit with spontaneous performances and games. Get ready to soak up the electric energy of Shanghai's Lupu Bridge at night."
No. 10 - A Weekend on Chongming

Escape the city hustle and find your peace on Chongming Island. A weekend getaway on this rural gem is just what you need. Chill out in a farmhouse, soak up the sunset, and enjoy the tranquility. Explore the natural wonders, visit the old museums, and feast on fresh seafood. End your days with a beach walk under the stars. Nothing beats a few nights away from the city chaos.
Additional Photos






Previous Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 001
Next Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 003
Find Me Elsewhere:
All images are property of Hes. Published 06.29.2024



