-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 16d11430:61640947
2025-01-26 01:03:44
@ 16d11430:61640947
2025-01-26 01:03:44The colonial fiat system—an intricate network of financial, social, and psychological constructs—relies on its ability to manipulate collective behavior, sustain economic dependency, and enforce systemic conformity. For the individual navigating this landscape, the brain becomes both a target and a tool. The question arises: how can the human brain, with its remarkable capacity for autonomy and adaptability, defend itself against the manipulative information siege of such a system? The answer lies in understanding and leveraging the brain's strengths to build defenses, foster resilience, and reclaim personal sovereignty.
Understanding the Siege: The Colonial Fiat System's Manipulative Arsenal
The fiat system exerts its control through psychological and informational tactics designed to overwhelm the individual mind:
-
Fear and Uncertainty: Constant narratives of inflation, economic crises, and scarcity exploit the brain’s amygdala, triggering anxiety and compliance.
-
Hyperconsumerism: By hijacking the brain’s reward pathways, the system fosters addiction to materialism, making individuals dependent on endless cycles of consumption.
-
Herd Mentality: Swarm consciousness, driven by social norms and media influence, suppresses critical thinking and reinforces collective conformity.
-
Short-Term Thinking: The system capitalizes on impulsive decision-making, eroding long-term planning and independence.
To resist these tactics, the individual brain must become a fortress—fortified by critical thought, emotional regulation, and intentional living.
Fortifying the Mind: Strategies for Resilience
- Cultivate Cognitive Autonomy
At the heart of resistance lies the brain’s ability to think independently. By engaging the prefrontal cortex—the seat of logic, reasoning, and decision-making—individuals can reclaim their mental autonomy.
Question Narratives: Evaluate the motives behind information presented by media, corporations, and governments. Ask: Who benefits from this message?
Strengthen Critical Thinking: Regularly challenge your own assumptions and seek out diverse perspectives to avoid echo chambers.
Learn the System: Understand how the fiat system functions, from its reliance on inflationary policies to its ties to debt-based economies. Knowledge dismantles manipulation.
- Master Emotional Regulation
The colonial fiat system thrives on fear, uncertainty, and the dopamine-driven cycles of consumerism. Emotional regulation shields the brain from these manipulative forces.
Practice Mindfulness: Techniques such as meditation and deep breathing calm the amygdala, reducing reactivity to fear-based propaganda.
Delay Gratification: Strengthen your ability to prioritize long-term rewards over impulsive consumption, engaging the brain’s executive functions.
Build Emotional Awareness: Recognize when your emotions are being manipulated, whether through scarcity marketing or fearmongering headlines.
- Rewire Reward Systems
The brain’s reward pathways, driven by dopamine, are a primary target of the fiat system’s consumerist messaging. Reclaim control by redefining what brings you fulfillment.
Seek Intrinsic Rewards: Shift focus from material possessions to meaningful activities, such as learning, creating, and connecting with others.
Limit Exposure: Reduce consumption of advertising and social media, which are designed to exploit your reward circuits.
Adopt Sound Money Principles: Embrace financial practices that align with long-term stability, such as saving in Bitcoin or other deflationary assets.
Adaptability: The Key to Outwitting the System
- Harness Neuroplasticity
The human brain’s neuroplasticity—its ability to rewire and adapt—offers a powerful tool for resisting the system’s influence.
Unlearn Dependency: Challenge habits and beliefs that tie your self-worth to fiat-driven success metrics, such as status symbols or debt-financed lifestyles.
Learn Decentralization: Educate yourself on alternatives to fiat systems, such as Bitcoin, decentralized finance, and peer-to-peer economies.
Adopt Resilient Skills: Develop capabilities that enhance your independence, such as critical financial literacy, coding, or permaculture.
- Reclaim Time and Focus
The fiat system thrives on distraction, keeping individuals too overwhelmed to question its constructs. Reclaiming focus is an act of rebellion.
Set Boundaries: Allocate time for deep work and personal growth, free from the constant noise of digital media.
Practice Digital Minimalism: Use technology intentionally, ensuring it serves your goals rather than consuming your attention.
Value Rest: Recognize that productivity is not your sole measure of worth. Rest and reflection strengthen your cognitive resilience.
A Community of Sovereignty: The Collective Defense
While the individual brain is formidable, collective resistance amplifies its power. The social brain network enables connection with others who share a vision of autonomy and decentralization.
Build Like-Minded Networks: Engage with communities that value critical thinking, self-reliance, and alternative systems.
Share Knowledge: Spread awareness of the manipulative mechanisms of the fiat system, empowering others to resist.
Collaborate on Solutions: From supporting decentralized technologies to creating resilient local economies, collective action dismantles dependency.
Finding Anchors: Philosophy, Purpose, and Meaning
The brain’s capacity for self-reflection and existential thought provides a deep well of strength. By anchoring your life to principles and purpose, you can resist the shallow incentives of fiat-driven systems.
Explore Philosophical Anchors: Ideas such as sound money, personal sovereignty, and ethical living provide a framework for resistance.
Seek Transcendence: Practices like spirituality, art, and nature connection foster a sense of purpose beyond materialism.
Define Success on Your Terms: Reject fiat-driven definitions of success, focusing instead on values like freedom, creativity, and meaningful relationships.
Conclusion: The Brain as a Bastion of Sovereignty
The colonial fiat system’s manipulative siege is formidable, but the human brain is a far greater force. Through critical thinking, emotional regulation, adaptability, and purpose, the brain has the power to resist the swarm consciousness that perpetuates systemic dependency. By building mental fortresses, individuals can reclaim their autonomy, foster resilience, and pave the way for a decentralized, self-sovereign future.
The battle for freedom begins not in institutions but within the neural networks of the individual brain. Each mind fortified against manipulation is a victory for personal sovereignty—and a step toward a world where human potential thrives beyond the shadow of fiat control.
-
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:31
@ 9e69e420:d12360c2
2025-01-26 01:31:31Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ d3052ca3:d84a170e
2025-01-25 23:17:10
@ d3052ca3:d84a170e
2025-01-25 23:17:10It seems to me that the primary opposition to ecash from bitcoiners comes from the belief that lightning will enable self-custodial micropayments for the masses. Many lightning enthusiasts see ecash as competition that will eliminate this technological outcome (whether they admit it or not).
I understand the motivation for this line of reasoning but I don't see things this way at all. Ecash is a superset of lightning. Cashu literally doesn't have a spec for on-chain transactions (yet!). Everything cashu accomplishes is built on the back of lightning. Standing on the shoulders of giants.
I don't believe that ecash will take away market share from self-custodial lightning because lightning is not a good technology for self-custody. The high overhead costs of running your own node create a natural incentive for a semi-centralized hub and spoke network graph. It just makes economic sense for many users to share a lightning node. It doesn't make economic sense for individuals to bear this cost alone.
This stacker news post is the best writeup on this topic: https://stacker.news/items/379225
It comes from a builder who struggled with these issues for years and learned the shortcomings of the tech first hand. Notice they experimented with ecash as a solution to these problems before they burned out and pivoted to save the company.
Ecash is a superset of lightning. It extends the capability and reach of the lightning network. Without ecash, I don't believe we can achieve bitcoin mass adoption. You can't jam a square peg into a round hole.
We still have a need for self-custody of "small" amounts of bitcoin. I put small in quotes because the block size limit and the fee market it creates impose a fundamental constraint on the minimum practical size of a UTXO. This limit is pegged to the unit of bitcoin. As bitcoin increases in value the minimum size for an on-chain transaction will grow in value as well. You can send $10 worth of bitcoin on-chain today but will this be true in 10 years when the price is much higher? 100 years?
If the current exponential trends hold, we will soon price out the majority of humanity from owning a UTXO. This is bad. Like really bad. "Bitcoin is a failure" bad. This is the motivation for my posts about scaling on-chain usage to 10 billion people. I believe we will need to radically rearchitect bitcoin to achieve this goal.
Lightning is not up to the task. We should leverage lightning for what it's good at: gluing together different self-custodial bitcoin service providers. We should leverage ecash for what it's good at: peer-to-peer electronic cash micropayments. IN ADDITION we also need to start seriously looking at new ideas for scaling self custody to "small" amounts of bitcoin. I am very optimistic that we can solve this problem. There are a number of promising avenues to pursue but I think first we need to move the Overton window ~~beyond the idea of mass adoption of self-custodial lightning~~ regarding on-chain scaling.
Edit: I think the original Overton window statement was incorrect. If on-chain fees stay low then self-custodial lightning or something similar is a much better prospect.
Just my 2 sats...let me know what you think. Keep it civil or be muted.
-
 @ 1cb14ab3:95d52462
2025-01-25 23:13:34
@ 1cb14ab3:95d52462
2025-01-25 23:13:34Tree branches. 4' x 4 [Castle Pines, USA. 2016]
Introduction
Sanctuary offers a layered view of resilience, juxtaposing the green expanses of the Sanctuary Golf Course with the majesty of Pikes Peak and the scars of past destruction. Framed by the lens, this work explores the tension between human intervention and nature’s cycles of renewal.
Site & Placement
Perched at Daniels Park in Castle Pines, the lens focuses on the rolling terrain of the golf course, leading the eye to the distant peak. The surrounding brush, which once burned in a major fire, adds depth to the narrative of renewal. A bench, positioned for an unobstructed view, invites visitors to sit and reflect on the land’s capacity to heal and endure.
Impermanence & Integration
As an ephemeral installation, Sanctuary embodies nature’s cycles of destruction and rebirth. The materials—branches and rock—will eventually decay and return to the earth, a process that mirrors the recovery of the landscape itself after fire. This impermanence underscores the delicate balance between human influence and natural forces.
Reflection
Sanctuary serves as a reminder of both the fragility and resilience of the world around us. It invites viewers to pause and consider the interplay of destruction and growth, human and natural, as they gaze upon a scene shaped by both time and transformation
Photos






More from the 'Earth Lens' Series:
Earth Lens Series: Artist Statement + List of Works
"Looking Glass" (Earth Lens 001)
COMING SOON: "Platte" (Earth Lens 004)
COMING SOON: "Grandfather" (Earth Lens 005)
COMING SOON: "Chongming" (Earth Lens 006)
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 37305b10:4676ca73
2025-01-25 23:32:19
@ 37305b10:4676ca73
2025-01-25 23:32:19This is some test content dsadfsadfasdfasdf
-
 @ 16d11430:61640947
2025-01-25 23:05:47
@ 16d11430:61640947
2025-01-25 23:05:47The entanglement of fiat currency, racial hierarchies, and colonialism is not merely a historical artifact but a systemic force that continues to shape the modern world. While colonialism has shifted from overt territorial domination to more subtle forms of economic and ideological control, its foundations remain deeply rooted in racialized exploitation and fiat-based financial systems. This article explores how fiat currency has historically been a tool of colonial power, how race has been weaponized to justify and sustain economic hierarchies, and how these forces persist in contemporary global structures.
The Role of Fiat in Colonial Domination
Fiat currency—money without intrinsic value, issued by centralized authorities—played a pivotal role in enabling colonial powers to exert control over colonized territories. By dismantling indigenous systems of trade and imposing fiat-based economies, colonizers centralized power, creating a structural dependence that persists to this day.
-
Monetary Imposition and Disruption: Colonial administrations replaced local barter systems and commodity currencies with fiat systems, compelling indigenous populations to use colonial currencies for taxes, goods, and services. This enforced participation in a colonial economic order undermined self-sufficient local economies. For example, the British introduction of the rupee in India dismantled complex indigenous trade networks, forcing economic realignment under colonial terms.
-
Taxation and Forced Labor: Fiat systems were weaponized to coerce colonized populations into labor. Taxes, often payable only in colonial currency, forced people to work within colonial enterprises to earn the money required. This dependency reinforced economic subjugation.
-
Inflation as Extraction: By manipulating fiat currency supplies, colonial powers extracted wealth from colonies. Printing excess money devalued local economies while enriching colonial elites. This strategy was less visible but equally exploitative compared to direct resource extraction.
Race as an Economic Justification
While fiat systems provided the mechanisms of economic control, racial ideologies provided the moral and political justification for colonial domination. Race became a lens through which economic inequality was normalized, rationalizing the exploitation of non-European populations.
-
Racialized Labor Exploitation: Under colonialism, racial hierarchies determined access to wealth and opportunities. Indigenous and enslaved peoples were systematically underpaid or unpaid, while Europeans occupied privileged economic positions. Racial ideologies framed these disparities as natural or deserved.
-
The Commodification of Racialized Bodies: Fiat systems also underpinned the commodification of human lives during slavery. Loans, bonds, and other financial instruments were issued based on the value of enslaved people, reducing human beings to economic units within racialized systems of extraction.
-
The Devaluation of Indigenous Economies: Indigenous systems of wealth and exchange were not merely disrupted but devalued, portrayed as primitive or inefficient compared to fiat-based systems. This cultural erasure further entrenched economic hierarchies tied to race.
Fiat Colonialism’s Modern Legacy
The relationship between fiat and racialized economic control persists in the global financial architecture:
-
Structural Dependence: Many post-colonial nations remain reliant on currencies introduced during colonial rule or tied to foreign powers. For example, the CFA franc in West Africa still links former French colonies to the French treasury, perpetuating neo-colonial dependency.
-
Global Financial Institutions: Organizations like the IMF and World Bank, operating within fiat systems, impose structural adjustment policies on Global South nations. These policies prioritize debt repayment to wealthy nations, often at the expense of local development. The racialized logic of colonialism reappears in these economic relationships, where predominantly non-European nations bear the brunt of austerity measures.
-
Racialized Access to Capital: In modern fiat economies, access to credit and capital is often disproportionately restricted for marginalized racial groups. This reinforces historical inequities rooted in colonial systems of economic exclusion.
Ideological Colonialism Through Fiat
Fiat currency is not merely a tool of economic exchange but a vehicle for ideological dominance. The imposition of Western fiat systems during colonialism also imposed Western economic values, undermining indigenous worldviews and institutionalizing a global hierarchy that remains intact today.
Monetary Sovereignty: By denying colonized nations the right to issue their own currencies, colonial powers stripped them of economic sovereignty. Today, this legacy continues as many nations remain economically constrained by foreign-controlled fiat systems.
Cultural Hegemony: Fiat systems have been a means of propagating cultural imperialism. Indigenous concepts of value and exchange, which often prioritized communal well-being over profit, were replaced by extractive models tied to fiat economies.
A Decolonial Perspective: Bitcoin and Alternatives
In the face of these enduring systems, decentralized financial systems like Bitcoin present a potential challenge to the colonial logic embedded in fiat systems:
-
Decentralized Sovereignty: Bitcoin operates independently of centralized authorities, offering nations and individuals the opportunity to bypass fiat dependencies. This could empower post-colonial states to reclaim economic autonomy.
-
Neutrality and Accessibility: Unlike fiat systems, which often reflect and reinforce racial and geopolitical hierarchies, Bitcoin is borderless and non-discriminatory, creating opportunities for marginalized groups to access capital and build wealth.
-
Transparency and Accountability: Blockchain technology ensures transparency, reducing the opacity that has historically allowed global financial institutions to exploit vulnerable nations through predatory practices.
Conclusion
The historical entanglement of fiat currency, race, and colonialism reveals how economic systems have been designed to sustain power imbalances. While colonialism has shifted in form—from direct rule to economic and ideological control—the core principles remain intact, with fiat currency serving as a critical mechanism for perpetuating these hierarchies.
Decolonizing the global economy requires dismantling these systems, recognizing their racialized foundations, and exploring alternatives that prioritize equity and autonomy. Bitcoin and decentralized technologies offer a potential pathway, though their success depends on a broader commitment to addressing the structural inequalities that fiat-based colonialism has left in its wake.
This is not just an economic imperative but a moral one: to imagine and build a world no longer bound by the exploitative legacies of fiat and race.
-
-
 @ 1cb14ab3:95d52462
2025-01-25 22:51:08
@ 1cb14ab3:95d52462
2025-01-25 22:51:08Tree branches, Rock. 4' x 4 [Boulder, USA. 2016]
Introduction
From atop Flagstaff Mountain, Folsom frames Boulder’s iconic Folsom Field, a symbol of youth, learning, and community. This lens offers a moment of reflection on the brevity of the college experience and the transient nature of life, inviting viewers to connect with the campus and its fleeting but impactful moments.
Site & Placement
The lens is strategically placed to frame the stadium, blending the vibrant life of the campus with Boulder’s vast and enduring natural landscape. The bench, situated 6 feet from the lens, offers a space to sit and contemplate the juxtaposition of permanence and change, of structure and wilderness.
Impermanence & Integration
Constructed from branches and rock, Folsom is designed to fade into the mountain landscape after only a short time. Its impermanence echoes the fleeting nature of the college years, reminding viewers that growth and transformation are rooted in moments that pass all too quickly.
Reflection
Through its brief presence, Folsom captures the delicate interplay between human experiences and the enduring landscapes that frame them. It invites viewers to celebrate the vibrant present while acknowledging the inevitability of change.
Photos






More from the 'Earth Lens' Series:
Earth Lens Series: Artist Statement + List of Works
"Looking Glass" (Earth Lens 001)
COMING SOON: "Sanctuary" (Earth Lens 003)
COMING SOON: "Platte" (Earth Lens 004)
COMING SOON: "Grandfather" (Earth Lens 005)
COMING SOON: "Chongming" (Earth Lens 006)
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ d9cfbbde:e7cfd9fd
2025-01-25 22:47:10
@ d9cfbbde:e7cfd9fd
2025-01-25 22:47:10Testing if this can be edited after publishing...
-
 @ 16d11430:61640947
2025-01-25 22:32:58
@ 16d11430:61640947
2025-01-25 22:32:58In the world of fiat, bosses are no longer mere professionals managing resources and people. They are, in essence, Big Brother's appointed handlers, glorified totems of obedience whose primary role is to ensure the herd stays docile, compliant, and tethered to their assigned hamster wheels. They don’t just manage; they surveil. With Orwellian precision, their every motivational email, team-building exercise, and performance review is an insidious mechanism for upholding the grand illusion of "freedom within structure."
These citizen-handlers come cloaked in titles like "team leader" or "manager," but their true mandate is far more sinister. Their KPIs aren’t just productivity or revenue—it’s compliance. It’s ensuring that no one questions why a third of their paycheck evaporates into the shadowy depths of taxes and inflation, why corporate policies look more like legislation, or why time—the only non-renewable resource—is spent propping up systems designed to ensure it is wasted.
Their tools? The carrot and the stick, but reinvented for the modern serfdom. The carrot is a pay raise that barely outpaces inflation, a shiny "employee of the month" badge that says, "You’re a good hamster!" The stick? Passive-aggressive emails, whispered conversations about "alignment with company values," and the ever-present specter of "budget cuts," a euphemism for your expendability in the machinery.
Dark satire requires pointing out the absurdities they enforce with a straight face: They orchestrate pointless Zoom meetings that siphon hours of productivity but demand employees "turn on their cameras" as proof of existence. They impose performance reviews steeped in doublespeak, where "areas of improvement" mean "You’re not docile enough," and "leadership potential" is code for "You’re great at mirroring propaganda."
Their allegiance is not to you, nor even to the company. It’s to the system that birthed them—a system that thrives on mediocrity, rewards complicity, and punishes dissent. The fiat boss isn’t a mentor; they’re a handler armed with spreadsheets, PowerPoints, and policies designed to turn independent thought into a liability. They are the human interface of a system that cannot tolerate deviation, individuality, or questions like, "Why are we doing this in the first place?"
In their world, promotions aren’t about merit but about trust—trust that you will perpetuate the cycle without asking too many questions. "You’re like family here," they say, but families don’t dock your pay for being late. "We value innovation," they claim, while shackling creativity with bureaucratic hurdles. "We care about work-life balance," they insist, while quietly monitoring your Slack activity at 11 PM.
Ultimately, the fiat boss-handler is a tragic figure in this dark satire, a cog who believes they’re the engine, a shepherd who thinks they’re free while they guide the sheep. They are the unwitting enforcers of a dystopia where freedom is rationed, individuality is commodified, and dissent is erased—not by decree, but by performance improvement plans.
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 37305b10:4676ca73
2025-01-25 22:55:49
@ 37305b10:4676ca73
2025-01-25 22:55:49This is some test content
-
 @ 37305b10:4676ca73
2025-01-25 22:51:13
@ 37305b10:4676ca73
2025-01-25 22:51:13This is some test content
-
 @ 1ec45473:d38df139
2025-01-25 20:15:01
@ 1ec45473:d38df139
2025-01-25 20:15:01The probability of AGI ending us is negative.
A common tactic among doomers is to state something along the lines of the following:
"If we create AGI, there is some non-zero chance every year, that the AGI will end humanity. Whatever that chance is compounds every year, and is thus unacceptable."
The question I would ask the doomer is "How do you know that the chance of AGI ending humanity isn't negative?"
What does it mean for AGI to have a negative chance of ending humanity?
Setting aside AGI for a moment, what is the chance every year that humanity ends from other events, such as nuclear war, solar flares, super-volcanoes, asteroid hits, societal collapse, etc?
How do you even answer this question in a reasonable manner? Well lets look at past data.
Of all species that have existed 99% have gone extinct.
Of our closest 7 relatives from the genus Homo, 100% have gone extinct.
On a higher level looking at civilizational collapse. According to Wikipedia, virtually all historical societies have collapsed.
Looking out into the universe, we see no signs of life elsewhere, so if there was life in the past we can assume that they have gone extinct.
It would therefore be reasonable to say that the chance of our extinction is very high even without AGI, well above 90%. Maybe 99%.
You could argue the numbers but at least with these numbers we are using some past data to extrapolate the future, where the doomers are using no data whatsoever to support their numbers.
We can also state, that of all the species and societies that have collapsed in the past, they have done so because they did not yet have the knowledge on how to survive. They didn't know how to create antibiotics, or generate enough energy, or defend themselves from the environment.
What is AGI? AGI is a way to create knowledge. Most all societies in the past have collapsed because they didn't have the knowledge on how to survive, and the doomer argument is that we should slow down our ability to create knowledge, when we know that this has been precisely the problem in the past.
It is a certainty we will all die without more knowledge then we have now. The future death of our sun ensures that.
We have to create the knowledge on how to survive, and that is what AGI does - it creates knowledge.
AGI most certainly has a negative probability of ending humanity.
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ ec642f38:a8b07008
2025-01-25 22:43:05
@ ec642f38:a8b07008
2025-01-25 22:43:05This is some test content
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ 920165f0:049cf1bb
2025-01-25 21:29:02
@ 920165f0:049cf1bb
2025-01-25 21:29:02Periodically, alone, at a less-than-preferred time, you must sit with yourself. Or I suppose you could take a walk, but unless you can guarantee your solidarity, you will likely appear somewhere on the outskirts of normal. While your pride may shine about this little compliment now, it will at times irritate you and ask if you’re sure you want to continue. That’s how everyone gets swallowed. Don’t ask questions. Don’t pick up rugs. Don’t be unruly with yourself or those you love, quietly drift into a more compliant state.
This is why you must go off and write or speak aloud. You ought to answer the question often: would you prefer explore the many routes of numbing medications, or feel your face melting as you take your most prized possessions and hold them to the fire?
There are no lifetime passes on this route. You must renew every day. But you’ve snuck away for months or years this time, and now you have to pay for your absence. You are required to bring your sacrifices to the table in order to continue. Nobody makes it out of here with a neat note, without mistakes or drops of blood on the page. If so, it wasn’t done.
You sacrifice yourself—your rightness, defensiveness, and all forms of denial.
So we sit and write. We pace and speak. We come near pulling our eyes from their sockets. We face ourselves in this heap of trash left to us by our predecessors. It’s not to say they weren’t left it as well—it’s to say it’s yours now.
Whether or not you want to think is your decision alone. Hoping others will take responsibility is an irresponsible management of your own life. As you lift every corner, you’ll find this dirt scattered across your life. You’ll turn your head, cite a guilty party, anything but take ownership.
If you see it, it’s yours. Nothing here belongs to anyone else. That’s the guarantee of mulling around in the mind. You’ll always find this, or you can be sure you’re lying.
It sounds tricky, but it’s only tricky because you are playing the tricks. Let us be clear: any form of matter you see is your responsibility.
Can you breathe now? Not any easier.
If the world around you is so foolish and dumb, why haven’t you adjusted for it sooner? If you did, don’t you think you’d employ a new method of crossing paths with them, beyond disappointment and frustration?
Who is the lagging party?
If you’d notice this quirk—which you cannot stop seeing in the same boring way—you’d realize you see the game very well but haven’t bothered acknowledging the rules. You’ve taken every other route, exactly what someone does when they’re trying not to see what’s in front of them.
You may be aware of this in others, but that’s not sufficient for someone who sits down to attempt to think, for someone who puts himself at the stake. That kind of man is responsible for the game, what he sees, and the rules in which the game is played.
That kind of man abandons the point-keeping devices he’s clung to over the years. He finally realizes he’s been using a unique scoring system to quantify himself, and it’s outdated.
The game goes on. You have a clear score, a clear basis for winners and losers, but you are consistently wrong. Impossible, you say? You’re diligent and precise?
Give it up. Give up your metrics.
If you wish to play the game, know the rules. Sound the buzzer, set all to zero, and dissolve everything you know about keeping track of points. Acknowledge the layers built into the game, the veils you must pierce to be successful within it.
You are susceptible to thinking you’ve thought. You are susceptible to believing it’s all or nothing. You won’t give up a few marbles for a bar of gold.
There’s only one reason. You think very highly of your marbles.
And be it gold or anything else, you are sticking to your marbles for the sake of never changing.
So is it them who can’t change? Is it them who cannot see? Is it they who’ve lost their minds?
Maybe. Maybe.
But it’s also you.
And until you can read the room without defending something, until you learn to play the game as if you knew the rules, your efforts are as good as they’ve always been.
-
 @ 1ec45473:d38df139
2025-01-25 20:15:01
@ 1ec45473:d38df139
2025-01-25 20:15:01`` ______________ / /| / / | /____________ / | | ___________ | | || || | || #NOSTR || | || || | ||___________|| | | _______ | / /| (_______) | / ( |_____________|/ \ .=======================. | :::::::::::::::: ::: | | ::::::::::::::[] ::: | | ----------- ::: |-----------------------'```
-
 @ 1ec45473:d38df139
2025-01-25 20:15:01
@ 1ec45473:d38df139
2025-01-25 20:15:01Preston Pysh posted this event this morning:

Behind the scenes, the nostr event looks like this:
Event = { "id":"a6fa7e1a73ce70c6fb01584a0519fd29788e59d9980402584e7a0af92cf0474a", "pubkey":"85080d3bad70ccdcd7f74c29a44f55bb85cbcd3dd0cbb957da1d215bdb931204", "created_at":1724494504, "kind":1, "tags":[ [ "p", "6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb", "", "mention" ], [ "p", "77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c", "", "mention" ], [ "p", "c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1", "", "mention" ], [ "p", "50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63", "", "mention" ], [ "p", "20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5", "", "mention" ], [ "p", "273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2", "", "mention" ], [ "t", "BH2024" ] ], "content":"Awesome Freedom Panel with...", "sig":"2b64e461cd9f5a7aa8abbcbcfd953536f10a334b631a352cd4124e8e187c71aad08be9aefb6a68e5c060e676d06b61c553e821286ea42489f9e7e7107a1bf79a" }In nostr, all events have this form, so once you become familiar with the nostr event structure, things become pretty easy.
Look at the "tags" key. There are six "p" tags (pubkey) and one "t" tag (hashtag).
The p tags are public keys of people that are mentioned in the note. The t tags are for hashtags in the note.
It is common when working with NOSTR that you have to extract out certain tags. Here are some examples of how to do that with what are called JavaScript Array Methods:
Find the first "p" tag element:
``` Event.tags.find(item => item[0] === 'p')
[ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ]
```
Same, but just return the pubkey":
``` Event.tags.find(item => item[0] === 'p')[1]
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb'
```
Filter the array so I only get "p" tags:
``` Event.tags.filter(item => item[0] === 'p')
[ [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ], [ 'p', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', '', 'mention' ], [ 'p', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '', 'mention' ], [ 'p', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '', 'mention' ], [ 'p', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '', 'mention' ], [ 'p', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2', '', 'mention' ] ]
```
Return an array with only the pubkeys in the "p" tags:
``` Event.tags.filter(item => item[0] === 'p').map(item => item[1])
[ '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2' ]
```
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ 0d7bc80d:aaf2218d
2025-01-25 16:55:59
@ 0d7bc80d:aaf2218d
2025-01-25 16:55:59\ Volkesbewusstsein, as interpreted from Carl von Savigny’s legal philosophy, and utilized by Carl Schmitt in his own, refers to the common consciousness of the people.
For Savigny, this meant that the laws and boundaries of the state evolve organically out of the collective consciousness of the people in a given historical period. A blooming out of the shared cultural fabric of a society.
Schmitt’s interpretation is slightly more assertive, seen more as an imposition of the collective will in defining the sovereign and the state.
But what makes up the common consciousness of society in our time? How does that influence the formation of our state and its laws? My sense is that the thing most shared or collective about our current consciousness is the schizophrenic quality of it. Our cultural fabric is that of an insane asylum,. We swim deep inside the algorithmic passivity of our historical moment, and this has fragmented our consciousness.
The concept of the public sphere as conceptualized by Jürgen Habermas projects an idealized image of a bygone era of communal communication and a genuine shared experience of reality. The public sphere was an arena for dialogue, disagreement, and maybe even reconciliation. This ideal held that communication occurred outside the bounds of state and market manipulation and held to rational discourse as a means of discovering Volkesbewusstsein.
Habermas was aware and critical of the modern erosion of the public sphere due to mass media and its influences. And here we are now in our cultural moment. It’s become trite to remind ourselves of the algorithmic sway that we encounter on a daily basis through social media news feeds. But this is one of those realities we need to continually encounter to take seriously, because it backgrounds itself so well. We become passive automatons swayed for engagement. AI agents capturing our attention and manipulating the lizard brain.
We are all aware of this.
However, to what extent are we understanding the schizophrenic agency of the algorithmic hyper-agent? There’s undoubtedly intentional manipulation of information for explicit ends, not explicit to us necessarily, but to someone or some bureaucracy.
What happens though when we have a myriad of explicit algorithmic hyper-agents taking over the public sphere? I’m no clinician, but my diagnosis is schizophrenia at the level of our distributed cognition. We’re in a collective asylum and the guards are insane too.
What kind of heroes emerge out of that cultural fabric? Well, insane ones. And they will look perfectly sane in their response to a system of state sovereignty and laws that have emerged out of that asylum. And we’ll cheer it on as it feels like entropy towards collapse is the only thing that might save us. Not that we are always conscious of our entropic aims. But the walls are crumbling down, and everyone has a sledgehammer, so we decide to pick one up as well. We’d prefer to feel that we’re at least exercising SOME sort of agency, after all.
I find myself entirely addicted to my comforting insanity. Precisely because it gives me the illusion of agency, rather than the passivity that Habermas feared would be the destruction of the public sphere. I’m grateful that every now and then, I’m able to stand back and examine the frames I’m applying, or that have been applied for me, and recognize my passivity.
Perennially, it becomes apparent that we need to step outside of the passive sway of our screens and to engage in an algorithmic free salon. The idealized picture of humans in a communal space, with minimally distorted flows of information, in true dialogue. A mutual respect for each other and our different value judgements, with a shared commitment to orienting towards truth.
The most basic way we can do this is to continually step back from the asylum, and find a quiet corner to discuss with other well intentioned patients how we might organically blossom out a new common consciousness. It’s hegemonic character, that which dominates it, need not be the assertion of one difference over the other, but the assertion that differences in value systems share some orientation.
All this must be, for now, done from the place of acceptance of our diagnosis. Our conversations in the public sphere will need to continually encounter and correct for our schizophrenia. But if enough of us pick up a hammer and start smashing it against the wall of the asylum, a new organic shared consciousness has a shot at arising.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ d57360cb:4fe7d935
2025-01-25 15:43:16
@ d57360cb:4fe7d935
2025-01-25 15:43:16Martial Arts has a way of imparting deep lessons on you, lessons that you feel deep to the core. Here are a few that have stuck with me. These lessons extend beyond the field of martial arts into every area of life, may you find value in them.
Static Vs Dynamic
The world is a dynamic and fluid domain, yet we think statically. This error makes us incompatible. When we think about the future and the past, they are fixed in our minds. We might have a grand plan for how we will beat our opponent or hold fear of a loss we suffered at the hands of another opponent. Because these are harbored in our minds, we are fixed in place entering a battle which is constantly moving.
To succeed one has to abandon the static and learn to dance. Let me explain this through the problem solving process.
Problem Solving
Imagine there's a giant wall in front of you and this wall is going to fall directly on top of you. Here you're faced with a problem, the wall falling and you also might have guessed the solution which is get out of the way. The usual approach people take in solving problems is they wait til the problem has already taken place and established itself to act.
Knowing fully the wall is falling they will wait til the wall has crushed them, only then they'll enact their plan to get out of the way. Their plan may very well work but not when the wall has already fallen, this renders their plan useless even though it is the correct solution. In their minds they see the problem and the solution only taking place when certain factors are met and conditions are perfect.
They will not act to evade a punch until hit in the face, they won't try to escape a choke until their opponent is squeezing the life out of them. This is the error of unskilled beginners yet it's a necessary path to the dynamic.
The best way to avoid danger is not going there in the first place
At a certain point you will get tired of getting hit in the face, getting choked out, and having the wall get crushed on you. You will see others using the very same solutions you're using and wonder why they succeed and you don't. The cogs in your brain come alive and you begin to think if the solution is to get out the way, I need to do it before or as the wall is falling not when it's already fallen. This takes you from the static to the dynamic, from thinking to feeling.
Instead of thinking and anticipating a punch and then moving, you no longer anticipate you immerse yourself in the chaos and are free to feel. You no longer wait for your opponent to have his hands around your neck to avoid getting choked, you avoid the situation altogether. You see the wall falling and you step out of the way, by nature another wall replaces it, this one is also falling and you maneuver out of its way. This is the great dance, this is the art.
Failure is Information
"The fool that persists in his folly soon becomes wise"
In life as in the arts you will continually face failures or walls. Most people view these as negative. Having a wall crushed on them they take it personally, blame themselves, how terrible they are and how much better their opponent is. These are your trusted guides they show you where you are fixed in place, they show you your inflexibility, your rigidity. They humble you over and over. It may take days, weeks, years or months for you to realize. In this way the end never arrives, the path of practice is the goal.
With diligence and patience the thing you once saw as a failure will become your wisest friend.
No opponent
Each person is going through this struggle internally. They face their own set of problems. In this way your opponents serve you as you serve them. The person that beats you down is not a rival, he's also not 'better' in any way he's exposed you and shown you the areas you have blindspots and weakness in. In the same way you serve that purpose for those just starting on the path. You may beat someone down and think you are 'better' than those you dominate. This is the wrong view you are a guide to those below you and student to those above you.
If you get caught up in your ego and status you will be blinded. One must leave the static world of victory and loss to find the dynamic.
Everything Bleeds
This was a post on material arts, but you could very well replace martial arts with any field and any set of problems. The incompatible mix of the static mind and dynamic world is found in every area of life. The lessons you learn from one area can be translated to another, these lessons are fundamental. In this way lessons bleed and overflow into everything you touch. You are the center of experience the things you devote time to in life are merely tools of expression.
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ 378562cd:a6fc6773
2025-01-25 15:19:53
@ 378562cd:a6fc6773
2025-01-25 15:19:53Top 20 U.S. Cryptocurrency Headlines:
-
SEC Reverses Crypto Accounting Rule, Easing Bank Participation The U.S. Securities and Exchange Commission (SEC) has overturned guidance that previously treated digital tokens as liabilities on bank balance sheets. This reversal is expected to facilitate banks in offering cryptocurrency custody services without facing significant penalties.
-
President Trump Signs Executive Order to Bolster Crypto Industry. President Donald Trump has issued an executive order titled "Strengthening American Leadership in Digital Financial Technology," aiming to position the U.S. as a global leader in the digital asset market. The order includes the creation of a task force to propose new crypto regulations and explore the establishment of a national digital asset stockpile.
-
Crypto Markets React to New Regulatory Initiatives. Following the administration's recent policy moves, the cryptocurrency market experienced a dip, with Bitcoin stabilizing around $105,000. The creation of a task force to propose new crypto regulations has introduced uncertainty, leading to profit-taking among investors.
-
Industry Celebrates Anticipated Deregulation Amid Caution. The cryptocurrency community is optimistic about the administration's supportive stance, including proposals for a U.S. Bitcoin reserve. However, experts caution that increased government endorsement could expose the financial system to significant risks if the market faces downturns.
-
White House Appoints David Sacks as Crypto and AI Advisor. The administration has appointed tech entrepreneur David Sacks as the White House's cryptocurrency and artificial intelligence advisor. Sacks will lead the newly formed Presidential Task Force on Digital Asset Markets, focusing on developing regulatory frameworks and exploring the creation of a national Bitcoin reserve.
-
Bitcoin Price Surges to All-Time High Amid Policy Shifts. Bitcoin has reached a record high of $109,000, driven by increased interest following endorsements from President Trump and tech entrepreneur Elon Musk. The launch of cryptocurrencies associated with both Trump and former First Lady Melania Trump has further fueled market enthusiasm.
-
Financial Institutions Show Renewed Interest in Crypto Services. Major financial firms, including Charles Schwab, are exploring deeper engagement in the crypto market following recent regulatory changes. Traditional banks are now better positioned to offer cryptocurrency custody services, reflecting a shift towards mainstream adoption.
-
Congressional Leaders Express Concerns Over Rapid Crypto Expansion. Some lawmakers have raised concerns about the swift regulatory changes favoring the cryptocurrency industry. They caution that rapid deregulation could lead to increased market volatility and potential risks to the broader financial system.
-
Crypto-Related Crimes Prompt Calls for Enhanced Security Measures. The recent kidnapping and assault of Ledger co-founder David Balland have highlighted the risks associated with the crypto industry. Security experts advise individuals involved in cryptocurrency to exercise discretion regarding their personal wealth and implement robust security protocols.
-
Stablecoin Development Encouraged Under New Executive Order. The administration's executive order promotes the development of dollar-backed stablecoins for global use, aiming to enhance the U.S. dollar's presence in the digital asset space while prohibiting the establishment of a central bank digital currency (CBDC) in the U.S.
-
Crypto Education Initiatives Launched to Foster Public Understanding. In response to the growing interest in digital assets, educational programs are being developed to inform the public about cryptocurrency investment risks and opportunities, aiming to promote responsible participation in the market.
-
Tech Companies Explore Blockchain Integration Amid Regulatory Clarity. With the recent regulatory developments, technology firms are increasingly considering blockchain integration into their operations, anticipating that clearer guidelines will support innovation in the sector.
-
Crypto Taxation Policies Under Review Following Executive Order. The Treasury Department is reviewing existing cryptocurrency taxation policies to align with the new executive order, potentially leading to revised guidelines that could impact investors and businesses.
-
Investment Funds Increase Crypto Holdings Amid Policy Support. Investment funds are bolstering their cryptocurrency portfolios, encouraged by the administration's supportive policies and the SEC's reversal of restrictive accounting rules.
-
Public-Private Partnerships Form to Advance Blockchain Research. New collaborations between government agencies and private companies are emerging to advance blockchain research and development, aiming to maintain the U.S.'s competitive edge in digital financial technologies.
-
Crypto Mining Operations Expand in the U.S.Cryptocurrency mining firms are expanding their operations domestically, attracted by the favorable regulatory environment and potential incentives outlined in recent policy initiatives.
-
Consumer Protection Agencies Advocate for Crypto Awareness. Consumer protection agencies are launching campaigns to raise awareness about the risks associated with cryptocurrency investments, emphasizing the importance of due diligence.
-
State Governments Explore Local Crypto Regulations. In light of federal initiatives, state governments are examining their regulatory frameworks concerning cryptocurrencies to ensure alignment and address local concerns.
-
Academic Institutions Introduce Cryptocurrency Courses. Universities and colleges are adding cryptocurrency and blockchain courses to their curricula, preparing students for careers in the evolving digital asset landscape.
-
Crypto Exchanges Enhance Compliance Measures. Cryptocurrency exchanges are strengthening their compliance protocols in anticipation of forthcoming regulatory recommendations from the Presidential Task Force on Digital Asset Markets.
Top 5 Worldwide Cryptocurrency Headlines:
-
Global Banks Anticipate U.S. Regulatory Changes. International banks are closely monitoring the U.S. regulatory shifts, assessing the potential global impact on cryptocurrency custody services and market participation.
-
European Union Debates Crypto Regulatory Framework. The European Union is engaging in discussions to establish a comprehensive regulatory framework for cryptocurrencies, aiming to balance innovation with consumer protection.
-
Asian Markets React to U.S. Crypto Policy Developments\ Cryptocurrency markets across Asia, including Japan and South Korea, are seeing increased trading activity following the U.S. administration's supportive stance on digital assets. Investors are optimistic about the ripple effects on the global crypto ecosystem.
-
India Announces Plans for Blockchain-Based Voting System\ The Indian government has unveiled plans to pilot a blockchain-based voting system aimed at enhancing election security and transparency. This initiative is part of India's broader efforts to explore blockchain technology in governance.
-
African Nations Embrace Bitcoin for Cross-Border Payments\ Several African countries are increasingly using Bitcoin to facilitate cross-border payments, citing its efficiency and reduced transaction costs. This trend reflects the growing adoption of cryptocurrencies in regions with limited access to traditional financial services.
-
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ 9e69e420:d12360c2
2025-01-25 14:32:21
@ 9e69e420:d12360c2
2025-01-25 14:32:21| Parameters | Dry Mead | Medium Mead | Sweet Mead | |------------|-----------|-------------|------------| | Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) | | Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) | | Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks | | Racking | Fortnight or later | 1 month or after | ~2 months and after | | Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 |
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ cffd7b79:dd8ca91f
2025-01-24 02:11:04
@ cffd7b79:dd8ca91f
2025-01-24 02:11:04Introductory
That right folks, it is called Satlantis. An upcoming game that is based on Minecraft. It uses a game engine called Launti/Minetest that has been in development since 2023, but it is unclear when it will be released. It is small team of bitcoin enthusiasts of 3-5 game developers.
Their Origin Story
It started out as a Minecraft server around 2018. It was prosperous with many players up to 100 players for just a SMP Server. Then on 2023, Mojang Studios contacted the owner of the server to shut it down due to have a play-to-earn function.
Their Discord Server
In their discord server, you can now earn their own currency called joules which can be earned by playing Counter Strike 2, Fortnite or Dead by Daylight. The joules then can be exchange for sats. If you wanna invest your sats into it, you can buy ASICs through the auction which is fueled by joules which gives you sats in return by the hour.
In Conclusion
From Minecraft to Minetest, it has great potential for such a game nowadays since not only its through some dApp currency scheme, but its straightforward process. if you want to see their site it is at Satlantis.net.
I am Chrissy Sage and I am out!
-
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ 0b14a03f:3f0257c2
2025-01-25 13:33:47
@ 0b14a03f:3f0257c2
2025-01-25 13:33:47Change doesn’t come from something external. The change comes from within. But people are so disconnected from themselves that they keep trying and trying with tools to connect without realizing that if there is no connection within, there won’t be a healthy and long-term connection outside.
Bitcoin has no name or last name because it’s not important who created it. What’s important is what it was made for. That’s written on its roots, in its essence. And that essence won’t be discovered if we keep trying to set it up in old avatars, systems, protocols, and connections.
Bitcoin is not a tool to get rich and be free. It’s a means to disconnect from a broken environment and find a safe place to pause, to feel, to see what’s really inside of ourselves, and to analyze if the world around us is not a consequence but a reflection of our internal disconnection.
Freedom will be a consequence, not a cause of a better future. We can be the artisans of that future by connecting with ourselves from within, as individuals first, and as a community after.
Community as in Common Identity. We need to find our identity, then share it, nurture it with others, and by doing so, be able to create a better world.
Don’t fall into old traps. After all, this is a journey from the mind to the heart.
Happy arriving!
Hug✨
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ bf47c19e:c3d2573b
2025-01-04 19:10:20
@ bf47c19e:c3d2573b
2025-01-04 19:10:20UTXO (Unspent Transaction Output) je Bitkoin koji nije potrošen, BTC koji se nalazi na svim adresama. Možemo ga porediti sa novčanicom u novčaniku i koja se mora u celosti potrošiti. Samo što kod BTC to može biti bilo koji iznos i taj iznos je uvek isti kao veličina poslednje transakcije minus naknada majnerima. Dok novčanice u novčaniku imaju tačno određene apoene, 100 dinara, 200 dinara, 500 dinara itd.
Kada plaćamo novčanicama nešto što košta 300 dinara, a u novčaniku imamo jednu novčanicu od 500 dinara, mi prodavcu moramo dati celu novčanicu od 500 dinara, a on nam zatim vraća kusur 200 dinara.
Kada plaćamo novčanicama nešto što košta 300 dinara, a u novčaniku imamo tri novčanice od 200, 200 i 100 dinara, mi prodavcu moramo dati ili dve novčanice od po 200 gde takođe dobijamo kusur ili dve novčanice od 200 i 100 dinara.
Ova analogija se može primeniti i na BTC i UTXO-ve koji funkcioniše na gotovo istom principu.
Ako plaćamo putem BTC nešto što košta 0.03 BTC, a u novčaniku imamo jedan UTXO od 0.05 BTC (a koji je nastao tako što je neko nama prethodno poslao 0.05 BTC u jednoj transakciji), naš novčanik ne šalje samo 0.03 BTC sa adrese, a da pritom 0.02 BTC ostane u novčaniku. Ne nego se iz novčanika šalje svih 0.05 BTC, 0.03 BTC ide prodavcu, a 0.02 BTC se vraća nama u novčanik kao kusur (change) na novu adresu formirajući novi UTXO od 0.02 BTC. Za slanje sredstava sa tog jednog UTXO-a plaćamo jednu transakcionu naknadu (fee) Bitkoin rudarima/majnerima. Neka bude $1 fee.
Ako plaćamo putem BTC nešto što košta 0.03 BTC, a u novčaniku imamo tri UTXO-a od 0.02, 0.02 i 0.01 BTC (koji su nastali tako što su nam prethodno poslate tri odvojene transakcije od 0.02, 0.02 i 0.01 BTC), naš novčanik automatski ili mi lično (putem opcije "coin control") sada moramo da odaberemo koja od ta tri UTXO-a, koje od te tri svojevrsne digitalne novčanice, ćemo poslati trgovcu. Dakle moramo da iskoristimo sredstva sa dva UTXO-a pošto nijedan pojedinačni UTXO nema dovoljno sredstava za plaćanje. I za slanje svakog od ta dva UTXO-a se majnerima plaća zasebna transakciona naknada koje zbirno koštaju duplo više nego u situaciji kada šaljemo sredstva sa jednog UTXO-a. Dakle plaćamo hipotetičkih $2 fee.
Ako imamo preveliki broj manjih UTXO-va, odnosno UTXO-va na kojima se nalaze pojedinačno mala sredstva i treba da platimo nešto skuplje u jednoj transakciji, onda ćemo za svaki od tih UTXO-va platiti zaseban fee što može dovesti do toga da ukupan fee bude dosta skup.
Ko vodi računa o privatnosti i nikada ne prima sredstva na jednu istu adresu više od jednom, odnosno uvek generiše novu adresu pri primanju svake transakcije, onda će uvek imati situaciju "1 adresa = 1 UTXO" i onda je lakši upravljanje UTXO-vima (UTXO management). Mnogo je teže kada se sva sredstva primaju na jednu adresu koja bi imala veliki broj UTXO-va.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
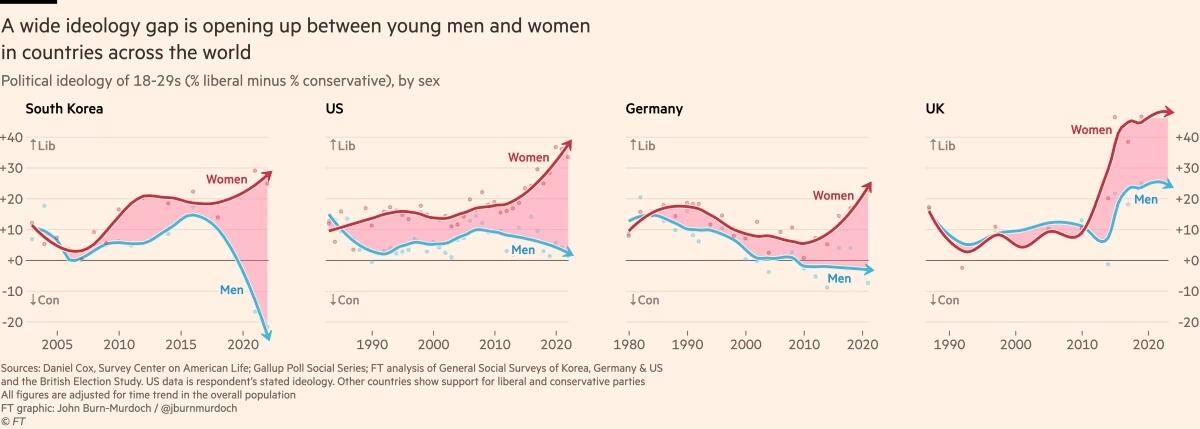
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ a012dc82:6458a70d
2025-01-25 13:09:46
@ a012dc82:6458a70d
2025-01-25 13:09:46The landscape of cryptocurrency is witnessing a potential paradigm shift with the growing interest of institutional investors in Bitcoin. The excitement surrounding the prospect of a spot Bitcoin Exchange-Traded Fund (ETF) is palpable, yet it brings with it a wave of concern. Arthur Hayes, a renowned figure in the cryptocurrency space and the founder of the Maelstrom Fund, stands as a vocal critic of this development. His insights offer a critical perspective on how institutional involvement could fundamentally alter the essence of Bitcoin, potentially steering it away from its founding principles of decentralization and autonomy. This article delves into Hayes' concerns, unraveling the complexities and potential repercussions of institutional custody on the future of Bitcoin.
Table Of Content
-
The Rising Concern of Institutional Involvement
-
The Scenario of Institutional Custody
-
The Essence of Bitcoin at Stake
-
Influence on Network Consensus
-
Long-Term Implications for Bitcoin
-
Conclusion
-
FAQs
The Rising Concern of Institutional Involvement
Arthur Hayes' apprehensions about institutional involvement in Bitcoin are rooted in a deep understanding of both the cryptocurrency world and traditional financial systems. The entry of large financial institutions like BlackRock into the Bitcoin space could signify a significant shift in the dynamics of cryptocurrency ownership and control. These institutions, often perceived as extensions of state interests, could bring a level of centralization and control antithetical to Bitcoin's decentralized ethos. The historical relationship between large financial entities and state mechanisms, and their potential influence on Bitcoin, raises critical questions about the future of this cryptocurrency. The impact of this shift on the broader crypto ecosystem, investor behavior, and Bitcoin's perception in the global financial landscape is profound and multifaceted.
The Scenario of Institutional Custody
The future that Hayes envisions, where significant portions of Bitcoin are locked away in institutional ETFs, is a stark departure from the current state of the cryptocurrency. This transformation could relegate Bitcoin from a vibrant, actively traded asset to a passive component of investment portfolios. Such a shift would not only alter Bitcoin's market dynamics but also its fundamental utility. The implications of this change are far-reaching, affecting everything from Bitcoin's liquidity to its role as a tool for financial freedom and empowerment. The prospect of Bitcoin becoming a mere line item in institutional balance sheets is a scenario that challenges the very ideals upon which the cryptocurrency was built.
The Essence of Bitcoin at Stake
The core of Hayes' argument lies in the potential loss of Bitcoin's identity. If Bitcoin becomes predominantly held in institutional ETFs, it risks becoming just another asset in the global financial system, losing its unique characteristics as a decentralized and autonomous currency. This transformation would affect the philosophical and practical aspects of Bitcoin, impacting principles of autonomy, privacy, and decentralization. The shift from a user-driven to an institutionally controlled asset could have profound implications for the future of Bitcoin, potentially undermining the trust and support of its community.
Influence on Network Consensus
Hayes raises a significant concern about the potential influence of institutional holders on Bitcoin's consensus mechanism and development path. The risk of having a large portion of Bitcoin controlled by entities with different priorities than the broader Bitcoin community is real and concerning. This influence could lead to a misalignment between Bitcoin's development and the needs of its user base, especially regarding crucial updates related to security and privacy enhancements. The integrity and future evolution of Bitcoin's technology could be at stake, raising questions about the true independence and resilience of this decentralized network.
Long-Term Implications for Bitcoin
While the short-term effects of institutional investment, such as price appreciation, are clear, the long-term consequences are more nuanced and complex. The potential trade-offs between short-term gains and long-term impacts on Bitcoin's utility and independence are a critical aspect of this discussion. The paradox of Bitcoin's growing acceptance by traditional financial institutions and the possible erosion of its foundational principles is a dilemma that the crypto community must navigate carefully. The future of Bitcoin, in this context, is not just about its price or market capitalization, but about its ability to retain its core values and functionality.
Conclusion
Arthur Hayes' insights provide a crucial perspective on the evolving landscape of Bitcoin in the face of institutional interest. As the cryptocurrency world grapples with these developments, understanding the balance between mainstream acceptance and the preservation of Bitcoin's core values is essential. This article reflects on the potential risks and implications of institutional custody of Bitcoin, offering a comprehensive analysis that underscores the importance of maintaining the decentralized ethos that has defined Bitcoin since its inception.
FAQs
What is the main concern raised by Arthur Hayes about institutional involvement in Bitcoin? Arthur Hayes expresses concern that institutional involvement, particularly through Bitcoin ETFs, could lead to centralization and control by large financial entities, undermining Bitcoin's decentralized ethos.
How could institutional custody of Bitcoin alter its market dynamics? Institutional custody could transform Bitcoin from an actively traded asset to a passive component of investment portfolios, affecting its liquidity and role as a tool for financial freedom.
What implications does institutional control have on Bitcoin's network consensus? Institutional control could influence Bitcoin's consensus mechanism and development path, potentially leading to a misalignment with the needs of the broader Bitcoin community, especially regarding updates related to security and privacy.
Are there long-term implications of institutional investment in Bitcoin? Yes, while institutional investment might boost Bitcoin's price in the short term, it raises concerns about the long-term impact on Bitcoin's utility, independence, and adherence to its foundational principles.
What is the essence of Arthur Hayes' argument against institutional custody of Bitcoin? Hayes argues that institutional custody risks turning Bitcoin into just another financial asset, losing its unique characteristics as a decentralized and autonomous currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 89ccea93:df4e00b7
2025-01-25 13:02:52
@ 89ccea93:df4e00b7
2025-01-25 13:02:52Meh.
I'm ambivalent.
For the cypher/crypto punks out there, the freedom fighters. You already didn't like what the government was doing before, why should this be any different?
For all those who preached hyperbitcoinization, but are now upset, it only makes sense for companies and countries to eventually want this thing on their balance sheet.
Soo.... Enjoy.
You got what you wanted... ?
I think.
For those who think this is the greatest thing since sliced bread...
Yeah, again, meh.
It'd probably be better for individuals to have it and the "State" to muddle through oblivious. I think by worshipping it, you're showing you literally ONLY care about the price, which is dumb. Price doesn't matter if you're cattle herded into a KYC-only pen. If you become a criminal for wanting to be outside the system.
But in the meantime, before the dystopia descends.
Just use it. Earn it. Save it. Spend it. Hodl it.
Whatever floats your boat.
But for the love of God, and I'm actually serious now, practice responsible Bitcoin ownership...
Don't tell eeeevveeeryyooonee you have it.
Hold the keys yourself.
Don't give your blood, voice, 3D picture, passport, first born, stool, DNA, SSN just to buy Bitcoin.
I bought some Bitcoin via Bisq the other day at BELOW market value. Peach and RoboSats at 0.5% above market value. So there's no excuse in my mind to use an centralized KYC exchange.
Inspired by this post by Rare Passenger.
originally posted at https://stacker.news/items/863448
-
 @ 54286b98:3debc100
2025-01-25 12:15:02
@ 54286b98:3debc100
2025-01-25 12:15:02The gift and the challenge? More time with my kids than most dads get. Days filled with them. It's a blast.
Diapers, potty training, sticky fingers, the easy stuff. Expected. A privilege, really.
But here's what I'm learning: Undivided attention. Presence. That's the hard part. The part that fades.
We walk. Parks, trails, anywhere but inside. They love it. S'mores, impromptu campsites, boats on the horizon, Florida beaches (no walking next to Florida freshwater for this dad, gators!). We read. We play hard. My oldest is discovering the magic of computers.
Mornings with my daughter. Just us. Quiet. Books. Connection. Then her brother wakes, and the day explodes with breakfast, more books, more play.
Knowledge, manners, a little discipline, and a lot of fun. That's the legacy.
But even with all this time, there's still work. Responsibilities. "Papa needs to work." "Papa, don't you want to play with me?" The hardest lesson: balance. Teaching them independence when all they want is connection.
The reminder: Even when life gets crazy, make the moments count. Be there. Truly be there. And trust that when I can't, they'll know it's not about them. It's about the work.
Love them. Cherish them.
Until the next one.
J
___
Feel free to follow me here on nostr or sign up on my website for my blog posts/newsletters, talking about crafting beauty in life, family, entrepreneurship, culture, woodworking & faith.\ https://www.javierfeliu.com/
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ 6f3670d9:03f04036
2024-12-29 08:20:22
@ 6f3670d9:03f04036
2024-12-29 08:20:22Disclaimer: - This will void your warranty - There might be differences between the Bitaxe and the Lucky Miner that might not cause issues or damage immediately, but might manifest long-term - Proceed at your own risk
A Different Pickaxe
You live in a place where it's difficult to get a Bitaxe. You have access to AliExpress. You look around. You find something called the "Lucky Miner LV06". A Bitaxe clone that uses the same mining chip as the Bitaxe Ultra (BM1366 ASIC). You buy one.
You plug it in, you enter your wallet address and other settings, and it starts mining. It works! Great!
But it's running a customized firmware. It's not AxeOS. Maybe there's something shady in the stock firmware. It's not open-source, after all. Also, AxeOS looks amazing... And that automatic pool fail-over feature is handy.
You think to yourself: "Maybe I can use the Bitaxe firmware on this?". Guess what? You're right!
Flashing From Web UI
What usually works for me is to: - Download the Bitaxe firmware files (
esp-miner.binandwww.bin) from GitHub (here). Version 2.4.1 seems to work well, as of this writing. - Then from the Lucky Miner web interface, upload the "Website" (www.bin) file. - Wait for a minute or two after it's done uploading. - Upload the "Firmware" (esp-miner.bin) file. - Wait another minute or two. - Unplug the power and plug it back in. - Set the "Core Voltage" and "Frequency" to the defaults. - Unplug the power and plug it back in again.If you're lucky (no pun intended), you'll have a working Lucky Miner with AxeOS. Update the settings and mine away!
However, often times I've been unlucky, like what happened while I was writing this article, ironically. The miner malfunctions for no obvious reason. It keeps rebooting, or it's not mining (zero/low hashrate), or the web interface is inaccessible. You name it.
The miner has become a "brick". How do you "unbrick" it?
When you brick a Bitaxe, you can recover it by flashing (uploading) a "Factory Image". The Bitaxe has a USB port that makes this easy. Follow the guide and it should come back to life again. Unfortunately, the Lucky Miner LV06 doesn't have a USB port. It has a serial port, though. We'll have to get our hands a bit dirty.
Flashing Using the Serial Port
We need to connect the serial port of the miner to a computer and run a program to flash (upload) the firmware file on the miner. Any 3.3v UART serial port should be sufficient. Unfortunately, PCs don't usually come with a UART serial port these days, let alone a 3.3v one. The serial port common in old computers is an RS-232 port, which will most probably fry your miner if you try to connect it directly. Beware.
In my case, as a serial port for my PC, I'm using an Arduino Due I had lying around. We connect it to the PC through USB, and on the other side we connect a few wires to the miner, which gives the PC access to the miner.
WARNING: Make sure your serial port is 3.3v or you will probably kill the miner. Arduino Uno is 5v not 3.3v, for example, and cannot be used for this.
Wiring
First, we need to open the Lucky Miner. Use a small flat screwdriver to gently push the two plastic clips shown in the picture below. Gently pry the top cover away from the bottom cover on the clips side first, then remove the other side. Be careful not to break the display cable.
Once the cover is off, you can find the miner's serial port in the top right corner (J10), as shown in the next picture. We'll also need the reset button (EN).
There are three screws holding the PCB and the bottom cover together. If you're confident in your ability to push the small button on the underside of the PCB with the bottom cover on, then no need to remove these. The following picture shows what we need from that side.
And the next picture shows the pins and USB port we will use from the Arduino.
Now, we need to connect: - The USB port on the Arduino labelled "programming" to the PC - Pin 18 (TX1) on the Arduino to J10 through-hole pad 5 (blue dot) - Pin 19 (RX1) on the Arduino to J10 through-hole pad 3 (green dot) - Any GND pin on the Arduino to J10 through-hole pad 4 (yellow dot)
I didn't need to solder the wires to the pads. Keeping everything stable, perhaps by putting a weight on the wires or a bit of tape, was sufficient in all my attempts.
Setting up the Arduino
To use the Arduino as a serial port for our PC, we'll have to make it pass-through data back and forth between the USB port and UART1, where we connected the miner.
The following steps are all done on a PC running Debian Linux (Bookworm), in the spirit of freedom and open-source.
First, we start the Arduino IDE. If the package for the Arduino Due board is not already installed, you'll see a small prompt at the bottom. Click "Install this package".
Click the "Install" button.
Once the package is installed, click "Close".
Next, we select the Due board. Click the "Tools" menu, select "Board", select "Arduino ARM (32-bits) Boards" and click "Arduino Due (Programming Port)"
Next, we select the port. Click the "Tools" menu again, select "Port", and click the port where the Arduino is connected. In my case it was "/dev/ttyACM0".
Now we need to upload the following code to the Arduino board. The code is actually the "SerialPassthrough" example from the IDE, but with the serial speed changed to match the miner.
``` void setup() { Serial.begin(115200); Serial1.begin(115200); }
void loop() { if (Serial.available()) { // If anything comes in Serial (USB), Serial1.write(Serial.read()); // read it and send it out Serial1 }
if (Serial1.available()) { // If anything comes in Serial1 Serial.write(Serial1.read()); // read it and send it out Serial (USB) } } ```
Copy/paste the code into the IDE and click upload. You'll see "Done uploading" at the bottom.
Next we'll test if we're receiving data from the miner. We start by opening the "Serial Monitor" from the "Tools" menu in the IDE. Then we change the baudrate to 115200.
Set the Arduino and the miner in a comfortable position, make sure the wires are held in place and got a good contact on both sides, and the power is plugged in.
Now we'll put the miner in "download" mode. Press and hold the button on the underside (K1), press and release the reset button (EN), then release the other button (K1).
You should see some text from the miner in the serial monitor window, like in the picture below.
Congratulations! We know we're able to receive data from the miner now. We're not sure transmit is working, but we'll find out when we try to flash.
Flashing Using the Serial Port, for Real
To flash the Lucky Miner we'll need a software tool named esptool and the factory image firmware file.
I usually use "esp-miner-factory-205-v2.1.8.bin" for the factory image (this one) as a base, and then flash the version I want from the Web UI, using the steps I mentioned earlier.
For esptool, the documentation (here) shows us how to install it. To make things a little easier on our Debian Linux system, we'll use pipx instead of pip. The instructions below are adapted for that.
First we make sure pipx is installed. Run this command in a terminal and follow the instructions:
sudo apt-get install pipxThen we install esptool using pipx. Run the following in a terminal:
pipx install esptoolThe output will be something like this:
user@pc:~$ pipx install esptool installed package esptool 4.8.1, installed using Python 3.11.2 These apps are now globally available - esp_rfc2217_server.py - espefuse.py - espsecure.py - esptool.py ⚠️ Note: '/home/user/.local/bin' is not on your PATH environment variable. These apps will not be globally accessible until your PATH is updated. Run `pipx ensurepath` to automatically add it, or manually modify your PATH in your shell's config file (i.e. ~/.bashrc). done! ✨ 🌟 ✨We can see pipx telling us we won't be able to run our tool because the folder where it was installed is not in the PATH variable. To fix that, we can follow pipx instructions and run:
pipx ensurepathAnd we'll see something like this:
``` user@pc:~$ pipx ensurepath Success! Added /home/user/.local/bin to the PATH environment variable.
Consider adding shell completions for pipx. Run 'pipx completions' for instructions.
You will need to open a new terminal or re-login for the PATH changes to take effect.
Otherwise pipx is ready to go! ✨ 🌟 ✨ ```
Now, close the terminal and re-open it so that esptool becomes available.
Finally, to actually flash the miner, put the miner in download mode, then in the following command change the port ("/dev/ttyACM0") to your serial port, as we've seen earlier, and the file path to where your firmware file is, and run it:
esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.binIf everything went fine, the tool will take a few minutes to flash the firmware to the miner. You'll see something like this in the output:
``` user@pc:~$ esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.bin esptool.py v4.8.1 Serial port /dev/ttyACM0 Connecting..... Detecting chip type... ESP32-S3 Chip is ESP32-S3 (QFN56) (revision v0.2) Features: WiFi, BLE, Embedded PSRAM 8MB (AP_3v3) Crystal is 40MHz MAC: 3c:84:27:ba:be:01 Uploading stub... Running stub... Stub running... Configuring flash size... Erasing flash (this may take a while)... Chip erase completed successfully in 9.5s Compressed 15802368 bytes to 1320190... Wrote 15802368 bytes (1320190 compressed) at 0x00000000 in 152.1 seconds (effective 831.2 kbit/s)... Hash of data verified.
Leaving... Hard resetting via RTS pin... ```
And we're done! Hopefully the miner will be recovered now.
Hope this helps!
Stay humble,
dumb-packageA Warning About Beta Versions of AxeOS
For reasons unknown to me, while I was writing this article I wanted to try the testing version of AxeOS, which was v2.4.1b (beta). Flashing from Web UI went smooth, but the miner stopped mining. I flashed back to v2.1.8 using the serial port, a known good version for me, but it wouldn't mine, still.
Thankfully, v2.4.1 was released recently, and flashing it from the Web UI magically revived my miner. So, be warned.
Bonus: File Hashes
For convenience, these are the SHA256 hashes of the files I used in this article: ``` da24fceb246f3b8b4dd94e5143f17bd38e46e5285e807ebd51627cb08f665c0a ESP-Miner-v2.4.1/esp-miner.bin 16c5c671391f0e3e88a3e79ce33fad3b0ec232b8572fad5e1e0d1ad3251ab394 ESP-Miner-v2.4.1/www.bin
d5182a15b6fa21d7b9b31bff2026d30afed9d769781a48db914730a5751e20c6 esp-miner-factory-205-v2.1.8.bin ```
-
 @ 6b57533f:eaa341f5
2025-01-25 11:45:15
@ 6b57533f:eaa341f5
2025-01-25 11:45:15Page: cover
background: #000000 template: vertical
Welcome to NoStry
This is the first nostr-story ever posted!
Page: intro
background-image: https://nostr.build/i/nostr.png template: vertical
What is NoStry?
NoStry is a new way to tell stories on nostr, combining the best of social media stories with the decentralized nature of nostr.
Page: end
background: #333333 template: vertical
Join the Revolution
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ da0b9bc3:4e30a4a9
2025-01-25 10:38:21
@ da0b9bc3:4e30a4a9
2025-01-25 10:38:21Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/863327
-
 @ fbf0e434:e1be6a39
2025-01-25 09:28:25
@ fbf0e434:e1be6a39
2025-01-25 09:28:25Hackathon 概要
Request Network - Summer Hackathon 在2024年夏季结束,吸引了144名开发者参与,并审核通过了32个项目。该活动由Request Network举办,着重于利用其兼容EVM的基础设施开发Web3金融应用。在Hackathon期间,参与者有机会参加针对初学者和高级用户量身定制的工作坊。这些工作坊旨在提高开发发票、支付、会计和借贷应用的技能。
激励措施包括总奖金池15,000美元,分为发票、支付、会计和借贷应用等奖项类别。此外,Request Network基金会为提交至其资助计划的项目提供额外35,000美元。评审标准强调实用性、易用性、技术复杂性和创新性。
参与者可以访问丰富的资源,如视频教程、GitHub代码库,还可以通过专用的Discord热线获得支持。Hackathon强调了积极参与,促进了旨在提升区块链交易能力的应用程序的创建。2024年7月8日,获奖项目公布,展示了参与者的创造力和技术专长。
Hackathon 获奖者
Invoicing Prize Winners
- ChainPay - 该项目通过与QuickBooks集成,将Request Network的功能扩展至Web3支付组件。它解决了Sepolia Testnet上的智能合约调用问题,目标是提供全面的解决方案。
- PiperPay - 一个支持多种货币和代币的发票和支付管理系统。它通过智能合约代理和代币交换遵循Request Network标准。
- Wavein - 该项目通过Request Network和Superfluid为自由职业者提供实时支付,提供带转换功能的流线型支付流。
Accounting Prize Winner
- request-accounting - 基于区块链的会计应用程序,确保安全交易,同时集成与行业标准一致的高效财务管理。
Lending Prize Winners
- Invoice Lending (Factoring) - 该项目通过将发票铸造成NFT提供流动性,允许在Request Network上进行点对点发票融资。
- Invisy Network - 一个去中心化发票平台,利用NFT提升效率和透明度,提供实时发票流动性的市场。
欲了解完整项目列表,请访问 DoraHacks Request Network Summer Hackathon。
关于主办方
Request Network
Request Network是一个兼容EVM的基础协议,致力于推动包括发票、支付和会计在内的Web3金融应用的发展。通过向区块链交易附加额外数据,网络确保合规、对账和可追溯性。这使用户能够维护其财务数据的所有权,促进灵活的转移和选择性共享。关键举措包括支持未抵押贷款和增强区块链交易流程。Request Network致力于促进一个包容的金融未来,通过优化服务来实现数据所有权和金融操作的自动化。
-
 @ 6f3670d9:03f04036
2024-12-29 06:51:25
@ 6f3670d9:03f04036
2024-12-29 06:51:25This is my first long-form post. The starting line.
There's nothing of value here. Just using this as a marker.
I hope to post a lot more. Documenting how I made something work would be very useful to me, and hopefully others, but I've been too lazy to do that. Wish me luck!
Stay humble,
dumb-package -
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ ed84ce10:cccf4c2a
2025-01-25 09:28:20
@ ed84ce10:cccf4c2a
2025-01-25 09:28:20Hackathon Summary
The Request Network - Summer Hackathon concluded with 144 developers participating and 32 project submissions approved. Hosted by Request Network, the event focused on developing Web3 financial applications utilizing its EVM-compatible infrastructure. Throughout the hackathon, participants had the opportunity to attend workshops tailored to both beginner and advanced users. These workshops aimed to enhance skills in developing applications for invoicing, payments, accounting, and lending.
Incentives included a total prize pool of $15,000, divided into categories such as invoicing, payments, accounting, and lending applications. Additionally, the Request Network Foundation provided an extra $35,000 for projects submitted to their grants program. The judging criteria emphasized utility, ease of use, technical sophistication, and innovation.
Participants were given access to extensive resources such as video tutorials, GitHub repositories, and support through a dedicated Discord helpline. The hackathon highlighted active engagement, promoting the creation of applications intended to improve blockchain transaction capabilities. On July 8, 2024, the winning projects were announced, showcasing the creativity and technical expertise of the participants.
Hackathon Winners
Invoicing Prize Winners
- ChainPay - This project expands Request Network's capabilities into Web3 payment components by integrating with QuickBooks. It addresses smart contract call issues on the Sepolia Testnet and aims for comprehensive solutions.
- PiperPay - An invoice and payment management system that supports various currencies and tokens. It follows Request Network standards using smart contract proxies and token swaps.
- Wavein - This project facilitates real-time payments for freelancers through Request Network and Superfluid, offering streamlined payment streams with conversion features.
Accounting Prize Winner
- request-accounting - A blockchain-based accounting application that ensures secure transactions while integrating efficient financial management aligned with industry standards.
Lending Prize Winners
- Invoice Lending (Factoring) - This project provides liquidity by minting invoices as NFTs, enabling peer-to-peer invoice financing on the Request Network.
- Invisy Network - A decentralized invoice platform leveraging NFTs to enhance efficiency and transparency, offering a marketplace for real-time invoice liquidity.
For a complete list of projects, visit DoraHacks Request Network Summer Hackathon.
About the Organizer
Request Network
Request Network is an EVM-compatible infrastructure protocol dedicated to advancing Web3 financial applications, including invoicing, payments, and accounting. By appending extra data to blockchain transactions, the network ensures compliance, reconciliation, and traceability. This empowers users to maintain ownership of their financial data, facilitating flexible transfers and selective sharing. Key initiatives include supporting under-collateralized loans and enhancing blockchain transaction processes. Request Network is committed to fostering an inclusive financial future by streamlining services to enable data ownership and automation in financial operations.
-
 @ 37305b10:4676ca73
2025-01-25 08:51:09
@ 37305b10:4676ca73
2025-01-25 08:51:09This is a test long form article publish via Nostr Article Publish in Obsidian
-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ ec642f38:a8b07008
2025-01-25 08:31:58
@ ec642f38:a8b07008
2025-01-25 08:31:58This is my test document for nostr publish
Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan.
Add some text
this is is a test
-
 @ 37305b10:4676ca73
2025-01-25 08:27:44
@ 37305b10:4676ca73
2025-01-25 08:27:44This is my test document for nostr publish
Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan.
Add some text
this is is a test
-
 @ 16d11430:61640947
2025-01-25 08:12:55
@ 16d11430:61640947
2025-01-25 08:12:55In Australia, a country where the Union Jack flies as a silent yet potent reminder of its colonial origins, the lives of non-violent, non-agitating individuals remain deeply entangled in a system built on inequality. Beneath the surface of modern democratic institutions and peaceful imagery lies a historical and ongoing strategy to maintain systemic dominance, often underpinned by the latent threat of violence.
For those who do not agitate, who simply wish to exist in peace, the daily experience can be one of quiet oppression. The colonial legacy ensures that fairness and justice are privileges reserved for a select ingroup—those who align with the dominant cultural narrative. Meanwhile, others find themselves trapped in a system designed to perpetuate inequality, all while cloaked in the language of ethics, science, and progress.
The Mask of Fairness
Australia’s institutions present themselves as bastions of fairness, meritocracy, and equality. Yet, these ideals are often undermined by the foundational violence that protects and privileges the dominant cultural group. This violence need not always be explicit—it exists in the form of legal frameworks, economic systems, and cultural narratives that favor the descendants of the colonial ingroup while marginalizing others.
For Indigenous Australians, immigrants, and those outside the dominant culture, the system does not just fail to deliver fairness—it actively maintains their disadvantage. The history of dispossession, forced assimilation, and cultural erasure is not simply a relic of the past. It continues to inform how resources, opportunities, and power are distributed today.
Privilege and Forgiveness
One of the most insidious aspects of this system is the privilege afforded to the ingroup. Actions that would be condemned or punished when carried out by marginalized groups are often forgiven, excused, or even celebrated when done by those within the dominant cultural framework. This double standard perpetuates a sense of impunity among the ingroup, while reinforcing the notion that fairness is conditional and selectively applied.
For example, protests or acts of civil disobedience by marginalized groups are often met with harsh policing and public condemnation. Meanwhile, similar actions by those in the dominant culture—especially when framed as defending “traditional values” or “national identity”—are met with leniency, if not outright support.
The Union Jack as a Symbol of Violence
The Union Jack, emblazoned on Australia’s flag, serves as a subtle yet powerful symbol of this systemic violence. It is a constant reminder of the country’s colonial roots, a time when land was taken by force, and Indigenous peoples were systematically oppressed. Today, while the overt violence of colonization has shifted into the background, its legacy persists in the structural inequalities that shape everyday life.
For many Australians, the flag represents pride and progress. For others, it is a symbol of dispossession and exclusion. This dual meaning highlights the deep divisions in how fairness and justice are experienced, depending on one’s place within the colonial hierarchy.
The Control of Peaceful Imaginations
Non-violent individuals often turn to ideals of peace, ethics, and community as a way to navigate the unfairness of the system. However, the colonial strategy has long been to co-opt these imaginations, redirecting them to serve the interests of the dominant group.
For example, the rhetoric of multiculturalism and reconciliation is frequently used to promote the idea that Australia has moved beyond its colonial past. Yet, these efforts often fall short of addressing the structural inequalities that continue to disadvantage marginalized groups. Instead, they serve as a way to maintain the status quo, offering symbolic gestures rather than substantive change.
Unfairness as a Daily Reality
For non-violent, non-agitating individuals, the daily reality of unfairness can manifest in countless ways:
Economic Disparity: Wages, employment opportunities, and wealth distribution continue to favor the dominant cultural group.
Cultural Erasure: Indigenous languages, traditions, and histories are often sidelined in favor of a Eurocentric narrative.
Policing and Justice: Marginalized groups are disproportionately targeted by law enforcement and are less likely to receive fair treatment in the justice system.
While these injustices may not always involve direct violence, the threat of coercion and enforcement looms large. The institutions that govern daily life are protected not by a commitment to fairness, but by the implicit and explicit threat of violence to those who challenge the system.
A Call for Change
Addressing this systemic unfairness requires more than symbolic gestures or surface-level reforms. It demands a reckoning with the colonial legacy and a commitment to dismantling the structures that perpetuate inequality. For true fairness to be realized, Australia must confront the uncomfortable truths about its past and present, moving beyond the veneer of peaceful coexistence to create a society built on genuine equity and justice.
Until then, the Union Jack will remain not just a symbol of the past, but a reminder of the ongoing struggles faced by those who dare to imagine a fairer world.
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 37305b10:4676ca73
2025-01-25 07:58:12
@ 37305b10:4676ca73
2025-01-25 07:58:12This is my test document for nostr publish
Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan.
Add some text
this is is a test
-
 @ ae6ce958:d0f02c7d
2025-01-25 06:54:35
@ ae6ce958:d0f02c7d
2025-01-25 06:54:35In the age of precision technology, photonic measurement systems like LiDAR play a critical role in transformative industries such as autonomous vehicles, medical imaging, and telecommunications. These systems rely on the precise behavior of sensors and software to ensure accuracy and reliability in complex, real-world environments. DamageBDD, with its innovative approach to Behavior-Driven Development (BDD), provides a platform for enabling a large number of people to participate in defining, testing, and refining the behavior of such systems.
By democratizing the process of behavior definition, DamageBDD unlocks new possibilities for collaboration and innovation. This article explores how DamageBDD can be applied to photonic measurement systems, demonstrating its potential to involve diverse stakeholders and enhance the quality of these technologies.
Why Involve Large Numbers of People in Defining Behavior?
- Diverse Perspectives: A wide range of participants, including developers, domain experts, end-users, and testers, brings diverse perspectives to defining system behavior. For example:
A developer might focus on system performance.
A medical professional might prioritize safety in imaging technologies.
An end-user might emphasize usability and intuitive interfaces.
-
Real-World Scenarios: Large-scale participation ensures that real-world scenarios are thoroughly explored and represented. For instance, in autonomous vehicles, scenarios such as heavy rain, fog, or crowded urban streets can be identified and tested by people from various geographies and climates.
-
Collective Intelligence: Crowdsourcing behavior definitions can leverage collective intelligence to anticipate edge cases and improve system robustness.
DamageBDD in Photonic Measurement Systems
DamageBDD’s unique ability to verify behavior at scale makes it an ideal platform for optimizing photonic measurement systems like LiDAR. Here’s how DamageBDD can be applied:
- Defining Behavior Using Real-World Scenarios
DamageBDD allows participants to write clear, human-readable scenarios that define expected behavior for photonic measurement systems. These scenarios are stored immutably on-chain, ensuring traceability and accountability.
Example:
Feature: LiDAR distance measurement Scenario: Accurate measurement in clear weather Given a reflective object is placed 10 meters from the sensor When the LiDAR system emits a pulse Then the system should report the distance as 10 ± 0.1 meters
Scenario: Measurement in foggy conditions Given a reflective object is placed 10 meters from the sensor And fog reduces visibility by 50% When the LiDAR system emits a pulse Then the system should report the distance as 10 ± 0.5 meters
With DamageBDD, such scenarios can be written by both technical and non-technical participants, enabling large-scale participation in defining behavior.
- Automating Behavior Verification
DamageBDD’s platform integrates seamlessly with testing frameworks, enabling automated verification of defined behaviors. This ensures that photonic measurement systems consistently meet the specified criteria across a wide range of scenarios.
Example: A team testing a LiDAR system can run automated tests against a DamageBDD-powered test suite. If a test fails—say, the system misreports distances under foggy conditions—it is flagged on-chain, triggering iterative improvements.
- Leveraging Crowdsourcing for Edge Cases
DamageBDD enables stakeholders to contribute new test cases and scenarios directly to the platform. For photonic measurement systems, this could involve:
Community members submitting scenarios involving unique environmental conditions (e.g., desert sandstorms or arctic snow).
Engineers proposing tests for hardware variations or upgrades.
Example: A developer in a tropical region might contribute the following scenario:
Scenario: Measurement in heavy rain Given a reflective object is placed 5 meters from the sensor And rainfall intensity is 50 mm/hour When the LiDAR system emits a pulse Then the system should report the distance as 5 ± 0.3 meters
By involving a global community, DamageBDD ensures comprehensive testing and improved resilience.
- Creating Incentives for Participation
One of the standout features of DamageBDD is its ability to incentivize participation through tokenized payouts. Contributors who define or verify behavior are rewarded in Damage Tokens, creating a self-sustaining ecosystem that encourages ongoing collaboration.
Example:
A developer contributes a new test case for low-light conditions.
A tester verifies the scenario by running it against a live system.
Both participants receive tokens for their contributions, fostering continued engagement.
- Ensuring Transparency and Accountability
With DamageBDD, all behavior definitions, tests, and results are immutably recorded on-chain. This ensures that:
Every contribution is traceable to its author.
Changes to system behavior are documented over time, creating an auditable history.
Example: When a new feature is added to a LiDAR system (e.g., enhanced fog detection), its behavior is verified through DamageBDD. The on-chain record shows:
Who defined the behavior.
When it was tested.
How it performed against previous versions.
This transparency builds trust among stakeholders and accelerates adoption.
Scaling to Other Photonic Applications
The principles outlined above can be applied to other photonic measurement systems, such as:
Medical Imaging: Ensuring MRI or CT scanners meet safety and accuracy standards across diverse patient demographics.
Telecommunications: Optimizing fiber-optic networks for different bandwidth and latency requirements.
Astronomy: Enhancing telescopes to accurately measure cosmic phenomena under varying atmospheric conditions.
In each case, DamageBDD enables mass participation, rigorous testing, and continuous improvement.
Conclusion
By enabling large numbers of people to define and verify behavior, DamageBDD revolutionizes how we approach photonic measurement systems and other complex technologies. Through its emphasis on collaboration, transparency, and tokenized incentives, DamageBDD not only improves the quality of these systems but also democratizes their development.
As industries continue to adopt precision technologies, DamageBDD provides a scalable framework for ensuring they meet the needs of diverse stakeholders. From LiDAR in autonomous vehicles to medical imaging and beyond, the potential for innovation is limitless when empowered by DamageBDD.
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 89ccea93:df4e00b7
2025-01-25 04:26:01
@ 89ccea93:df4e00b7
2025-01-25 04:26:01Here's a list of the services I use.
I plan to make a blog post for each on
expatriotic.memy previously defunct blog that is going live again.Stay tuned.
Networking
Flint Router Mullvad Tor Little SnitchBuying & Selling Bitcoin
Bisq Robosats Peach Hodl HodlPrivate email
Tuta Addy.io ProtonWallets
Ashigaru Stack Duo Cake Sparrow Envoy Zeus CoinosSwapping Bitcoin
Trocador basicswapdex unstoppable-swapnoKYC
```kycnot.me```Spending Bitcoin
Wise Bitrefill Bitpay PayWithMoon Coinsbee The Bitcoin Company CoinCards.comPhone
Graphene OS Minimalism Obtainium FOSS apps Signal for DMs Telegram for Groups Silent.LinkServer
DIY with Debian Start9 Dojo Ronin Dojo Monero NodesPodcasts
The Ungovernable Misfits News Network The Watchman Privacyoriginally posted at https://stacker.news/items/863051
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 16d11430:61640947
2025-01-25 04:19:41
@ 16d11430:61640947
2025-01-25 04:19:41In the grand tapestry of global history, few nations have endured and overcome with the resilience and grace of India. The centuries-long oppression wrought by colonialism not only plundered our material wealth but also sought to erode the dignity of our civilization. Today, while the political shackles have been cast off, the shadow of colonial mind games persists, manifesting as ridicule and prejudice toward the Indian diaspora. Yet, as heirs to an ancient and resilient culture, the diaspora must rise above this insidious narrative, reclaiming its agency and asserting its rightful place in the world.
The Colonial Playbook: Divide, Deride, and Demean
The strategy of the colonial enterprise was never limited to economic exploitation; it sought to demean the very essence of the colonized. Our history, culture, and achievements were systematically denigrated while a manufactured narrative of inferiority was imposed. That very playbook, though subtler in its contemporary iteration, remains at work today.
The Indian diaspora, as ambassadors of a thriving civilization, often finds itself targeted by the remnants of colonial prejudice—mocked for its accents, cuisine, and customs, and vilified for its success. Whether it is the ridicule of our English, tainted by colonial imposition, or the disparagement of our efforts to succeed in foreign lands, these tactics are nothing more than the echoes of a bygone era attempting to assert relevance in a world that has moved on.
A Legacy of Survival and Triumph
To endure is deeply etched into the DNA of the Indian psyche. We have weathered invasions, famines, and systematic subjugation with a fortitude that no conqueror could extinguish. The Indian diaspora, spread across continents, is the living embodiment of this indomitable spirit. It has flourished in the face of adversity, not by seeking vengeance, but by cultivating excellence in every field—science, medicine, literature, and technology—while retaining its cultural roots.
Today, Indian-origin CEOs helm some of the world's largest corporations. Indian doctors, engineers, and academics enrich societies across the globe. Yet, the colonial mind games persist, attempting to reduce these achievements to the stereotype of "over-ambition" or "cultural overreach." Such narratives are designed to diminish, to perpetuate the myth of the colonial superior.
Reclaiming the Narrative
The time has come for the Indian diaspora to reclaim the narrative, not with the bitterness of retribution but with the quiet confidence of a civilization that has seen the rise and fall of empires. The response to colonial mind games must be rooted in three key principles:
-
Pride in Heritage: The richness of Indian culture, from its philosophical traditions to its scientific advancements, is unparalleled. The diaspora must take pride in these achievements and articulate them with clarity and confidence.
-
Mastery of Communication: The colonial critique often begins with language. To counter this, the diaspora must wield English—not as a colonial relic, but as a tool reappropriated and mastered, blending it seamlessly with the wisdom of Sanskrit, Tamil, Hindi, and other mother tongues.
-
Unified Solidarity: The diversity of the Indian diaspora—spanning religions, languages, and regions—is its greatest strength. By standing united, the diaspora can amplify its voice and counter attempts to divide and diminish it.
The Enduring Legacy of Dharma
India's approach to the world has never been one of conquest but of engagement. From the dissemination of Buddhism to the world to the shared wisdom of yoga and Ayurveda, India's influence has always been through persuasion, not coercion. The diaspora must embody this dharmic ethos, rising above pettiness and prejudice, offering the world not retaliation, but enlightenment.
Victory Through Resilience
The colonial mind games that seek to ridicule and undermine the Indian diaspora are, in truth, a recognition of its success. They arise from the insecurities of those who once sought to subjugate, now witnessing the rise of a civilization they sought to diminish.
The Indian diaspora must endure not by stooping to the tactics of its detractors but by transcending them. The answer to colonial prejudice lies in excellence, unity, and an unshakable belief in the values that have guided India for millennia.
As we stride confidently into the future, let us remember: the spirit of India is not one of vengeance but of vindication. The triumph of the Indian diaspora will not be in silencing its critics but in rendering them irrelevant through the brilliance of its achievements and the dignity of its conduct. The time for enduring is over; the time for overcoming is now.
-
-
 @ 28cac85f:54300cac
2025-01-25 03:47:46
@ 28cac85f:54300cac
2025-01-25 03:47:46Reduction in Crime and Incarceration Rates: The war on drugs has often led to mass incarceration, particularly affecting minority communities. By decriminalizing drugs, the focus shifts from punishment to treatment, reducing the number of people in prison for drug possession. Portugal saw a significant decrease in drug-related incarceration following decriminalization. The proportion of the prison population held for drug offenses has decreased from over 40% in 2001 to around 15.7% by 2019, reducing the burden on the criminal justice system.
Public Health Over Criminal Justice: Treating drug use as a public health issue rather than a criminal one allows for better health outcomes. Portugal's model emphasizes harm reduction strategies like needle exchange programs, which have lowered rates of diseases like HIV and hepatitis C among drug users. There was a significant increase in the number of people entering drug treatment programs, with treatment admissions rising by about 60% from 1998 to 2011. New infections from needle sharing decreased dramatically, with HIV cases among drug users falling from an all-time high in 2000 to much lower rates by 2015.
Focus on Addiction Treatment: Legalization or decriminalization can free up resources (both financial and human) for addiction treatment rather than law enforcement. Portugal invested in treatment facilities and outreach programs, leading to an increase in people seeking help for addiction.
There has been a marked reduction in drug-related mortality. Overdose deaths dropped significantly from around 400 annually before decriminalization to much lower numbers in subsequent years.
Reducing Stigma: By removing criminal penalties, the stigma associated with drug use is diminished, encouraging more users to seek help without fear of legal repercussions. This can lead to earlier interventions in addiction. Drug use is now more widely seen as a health issue rather than a criminal one, which has helped reduce stigmatization and encourage people to seek help.
Economic Benefits: The costs associated with drug enforcement are substantial. Redirecting these funds towards education, prevention, and treatment can be more cost-effective in the long run. Additionally, regulated drug markets could generate tax revenue, although this aspect is more relevant if drugs are fully legalized rather than just decriminalized. The reduction in incarceration for drug offenses has potentially saved costs, allowing reallocation of funds towards health services and treatment.
Impact on Drug Market Violence: Much of the violence associated with drug markets stems from their illegal nature, leading to turf wars among dealers. Legal regulation can potentially reduce this violence by cutting out the black market.
Empirical Evidence: Portugal's experience since decriminalizing personal drug use in 2001 has shown positive trends. Drug-related deaths decreased, and there was no significant increase in drug use among the population, countering fears that decriminalization would lead to rampant drug use.
Human Rights Perspective: The criminalization of drug use has been criticized as a violation of human rights, disproportionately affecting the poor, minorities, and those with mental health issues. A health-centric approach respects human dignity and focuses on recovery.
Let's do this here in the US, why not?
-
 @ 16d11430:61640947
2025-01-25 03:04:45
@ 16d11430:61640947
2025-01-25 03:04:45In the dystopian wasteland of tech we call the "crypto space," where tokenomics is a euphemism for Ponzi schemes and the word “decentralized” is abused like a buzzword-shaped piñata, software engineers—real ones—struggle to survive. I’m not talking about the low-effort devs churning out Solidity copy-pasta for the next Insert-Adjective-Coin. No, I mean the overexperienced, underpaid, and utterly exhausted professionals who used to build things that mattered—systems that could scale, products that solved problems, applications that didn’t have to slap "on-chain" on their name to justify their existence.
Now? Honest conversations about software design, scalability, or—God forbid—ethics, are impossible. Why? Because the room is full of crypto zealots whose job descriptions boil down to "pump my bags or GTFO."
Enter the Zealots: The New Pyramid Architects
Walk into any crypto meeting, and you’ll find the same characters. The "visionary" founder with a LinkedIn bio that could double as a scammer’s résumé. The "community manager" whose job is to slap rocket emojis on tweets about nothing. And the "blockchain developer" who doesn’t know the difference between O(n) and "Oh, nice, this whitepaper has pretty graphs."
Now, try having an honest discussion with this crowd.
You: "This app doesn’t need a blockchain. A SQL database would handle this faster, cheaper, and more securely." Them: "Actually, by using our Layer 2 token, we're decentralizing freedom, empowering communities, and disrupting the financial matrix." Translation: "Our tokenomics scheme will siphon liquidity from suckers while pretending to solve a non-existent problem."
If you dare to mention Bitcoin—real Bitcoin, not some Frankenstein monstrosity glued to a shitcoin L2—you’ll get branded a heretic. "But Bitcoin can’t do smart contracts!" they cry, as if adding complexity to simplicity is a virtue, not a design flaw.
The Tokenomics Scam: Why Engineers Hate Their Lives
Here's the dirty secret: most crypto projects are not software projects. They’re marketing scams with some code sprinkled on top. The goal isn’t to build something robust or meaningful—it’s to create just enough technical smoke and mirrors to dupe investors into buying the token.
For a software engineer, it’s soul-crushing work. You’ll spend 80% of your time wrestling with poorly documented APIs on some vaporware blockchain, 15% explaining to your PM why "put it on-chain" is a stupid idea, and the remaining 5% wondering why you didn’t just go into carpentry instead.
Bitcoin: The Elephant in the Room
Every real engineer knows that Bitcoin works. It’s simple. It’s secure. It’s elegant. But because it doesn’t have a flashy CEO or a billion-dollar marketing budget, the average crypto enthusiast treats it like a relic. "It’s too slow," they’ll say, without understanding why Proof-of-Work exists. "It’s too basic," they’ll argue, as if simplicity is a flaw and not the reason Bitcoin has remained unbroken for over a decade.
Meanwhile, these same zealots will praise the latest shitcoin L2 that "fixes" Bitcoin by adding layers of complexity that require endless token sales to function. Never mind that these systems are riddled with attack vectors. Never mind that the "innovation" usually amounts to reinventing centralized finance, only worse. It’s not about building better systems; it’s about spinning a better narrative.
The Undervalued CTO: A Study in Pain
And where does that leave the senior engineer, the architect, the CTO who’s been around long enough to smell the bullshit from a mile away? Stuck in endless meetings where you’re forced to explain to the same wide-eyed MBAs why the laws of physics and computer science apply to blockchains, too. Worse, your paycheck is probably being paid in tokens that are only worth something if you can stomach shilling them to the next sucker.
The most depressing part? The zealots don’t even know they’re part of the scam. They’ve convinced themselves that they’re "building the future" when all they’re really building is a pyramid, one token sale at a time.
A Modest Proposal: Burn It All Down
Here’s an idea: let’s strip crypto down to what works. Keep Bitcoin. Scrap everything else. Rebuild the internet of value on solid foundations, not speculative hype. Let engineers, not marketers, lead the way.
Until then, we’ll keep trudging along, writing code for projects we don’t believe in, pretending that decentralizing dog grooming or tokenizing air molecules is the next big thing. Because, let’s face it, in crypto, the only thing that scales reliably is bullshit.
-
 @ 228dde34:b5d0345e
2025-01-25 01:59:57
@ 228dde34:b5d0345e
2025-01-25 01:59:57By Jonathan Tan
Lead Editor
Hype Issue #60
JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.

The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in anNBC article.
The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recentsurveyconducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years.
This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth.
How to lose thousands before adulthood
“I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.
 In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.
In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain.
“I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says.
The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble.
“The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.”
But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”
 A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.
A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares.
And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites.
First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions.
But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place.
“I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says.
Consequences, consequences
Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable.
“The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.
 The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.
The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling.
Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares.
Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life.
What can be done?
The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions.
In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023.
However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry.
Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden.
“GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in a Straits Times article.
Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, in a Straits Times article.
Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution.
“Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling.
“A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ df476244:6804e458
2025-01-24 23:44:38
@ df476244:6804e458
2025-01-24 23:44:38Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by viewing the raw basic.md file.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is [an example](http://example.com/ "Example Title") inline link.This is an example inline link.
[This link](http://example.net/) has no title attribute.This link has no title attribute.
Reference-style links use a second set of square brackets, inside which you place a label of your choosing to identify the link:
This is [an example][id] reference-style link.This is an example reference-style link.
Then, anywhere in the document, you define your link label like this, on a line by itself:
```
```
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ bcea2b98:7ccef3c9
2025-01-24 23:21:05
@ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ 7ed7d5c3:6927e200
2024-12-03 15:46:54
@ 7ed7d5c3:6927e200
2024-12-03 15:46:54Shall I compare thee to a summer’s day? Thou art more lovely and more temperate; Rough winds do shake the darling buds of May, And summer’s lease hath all too short a date;
Sometime too hot the eye of heaven shines,
And often is his gold complexion dimm’d;
And every fair from fair sometime declines,
By chance or nature’s changing course untrimm’d;
``` But thy eternal summer shall not fade Nor lose possession of that fair thou owest; Nor shall Death brag thou wander’st in his shade, When in eternal lines to time thou growest;
So long as men can breathe or eyes can see, So long lives this and this gives life to thee. ```
-
 @ 16d11430:61640947
2025-01-24 22:19:20
@ 16d11430:61640947
2025-01-24 22:19:20The legacy of Thomas Babington Macaulay’s education policies in colonial India has left a profound and complex impact on generations of Indians who were groomed to serve as intermediaries between the British colonial authorities and the native population. Dubbed "Macaulay’s Little Englishmen," these individuals faced unique psychosocial challenges stemming from their dual identity—educated and acculturated in the ways of the British yet tied to their Indian heritage. Straddling these two worlds, they often became objects of suspicion and alienation, regarded as potential double agents in a deeply divided society. This article explores the psychosocial effects of such an upbringing, which left these individuals feeling unmoored, mistrusted, and culturally disoriented.
The Double Bind: Torn Between Two Worlds
The fundamental conflict for Macaulay's "Little Englishmen" lay in their hybrid identity. Educated to think, speak, and act like the British, they were expected to serve the colonial administration, often as clerks, teachers, or intermediaries. However, this acculturation came at a cost: alienation from their own cultural roots. Their mastery of the English language and exposure to Western philosophy, law, and governance set them apart from the masses, who viewed them as traitors to their native heritage.
At the same time, these individuals were never fully accepted by the British elite. Despite their fluency in English and adoption of British customs, they were often treated as inferior, excluded from the corridors of real power. This dual rejection—by their own people and their colonial masters—created a profound sense of isolation and a fractured sense of self.
The Suspicion of Betrayal
The psychosocial burden of living as a cultural and social hybrid was compounded by the pervasive suspicion they faced from both sides.
-
From the British: While Macaulay’s education system intended to create loyal intermediaries, the British often doubted the loyalty of these individuals. Were they truly assimilated into the colonial ideology, or were they secretly harboring nationalist sentiments? This doubt meant that, despite their qualifications, many were confined to subordinate roles, denied the trust and respect they sought from their colonial employers.
-
From their own people: Within Indian society, these individuals were often perceived as sellouts or traitors who had traded their cultural identity for material gain. They were seen as collaborators in the colonial machinery that oppressed their own people. This mistrust led to social ostracization and an enduring sense of guilt and shame, as they were caught between the expectations of their colonial education and the loyalty to their heritage.
Psychosocial Consequences
The experience of living under constant suspicion and alienation had deep psychological and social repercussions:
-
Identity Crisis: The duality of their upbringing created a fractured identity. They were neither fully British nor fully Indian, leading to feelings of dislocation and an inability to fully belong to either world. This liminal state often resulted in a lifelong struggle with self-perception and cultural loyalty.
-
Chronic Anxiety: The need to constantly navigate the expectations and suspicions of both the British and Indian communities induced chronic stress. They had to carefully monitor their behavior, speech, and actions to avoid appearing disloyal to either side. This vigilance contributed to anxiety, self-doubt, and a lack of authentic self-expression.
-
Social Isolation: Alienated from their own communities and never fully accepted by the British, many of these individuals experienced profound loneliness. They lacked meaningful social support, as their education and socialization had placed them in a unique and isolating position.
-
Internalized Inferiority: The colonial education system, designed to instill admiration for British culture and disdain for indigenous traditions, often led to internalized feelings of inferiority. Many came to view their own heritage as backward or uncivilized, perpetuating a cycle of cultural self-erasure.
-
Moral Conflict: Being agents of a colonial system that oppressed their own people created a moral dilemma. Many felt complicit in the exploitation and subjugation of their fellow Indians, leading to guilt and cognitive dissonance. This internal conflict was particularly pronounced during the rise of the Indian independence movement, when calls for loyalty to one’s nation clashed with their colonial upbringing.
The Broader Implications
The psychosocial effects of being “Macaulay’s Little Englishmen” extend beyond the individual level, influencing broader societal dynamics. The creation of a class of culturally alienated intermediaries contributed to the perpetuation of colonial hierarchies, even after independence. The mistrust they experienced on both sides foreshadowed the postcolonial identity crises faced by many nations grappling with the legacy of colonization.
Furthermore, the notion of being a "double agent" has parallels in modern postcolonial societies, where individuals educated in Western systems often face similar suspicions of disloyalty or cultural inauthenticity. The scars of Macaulay’s experiment in social engineering are still visible in the struggles of postcolonial nations to reconcile traditional identities with the legacies of colonial modernity.
Conclusion
The psychosocial toll of being "Macaulay’s Little Englishmen" highlights the deep and lasting consequences of cultural alienation and identity manipulation. These individuals lived as bridges between two worlds, yet they were mistrusted and misunderstood by both. Their experiences serve as a poignant reminder of the human cost of colonialism and the complex legacy of cultural hybridity in a divided world. The story of Macaulay's "Little Englishmen" is not just a tale of alienation—it is a testament to the resilience of those who navigated impossible contradictions, often at great personal cost.
-
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ fd208ee8:0fd927c1
2024-11-28 12:50:49
@ fd208ee8:0fd927c1
2024-11-28 12:50:49GitHub is a software project graveyard
I think the main reason why we have so many lone wolf devs is an economic one. The fact that most FOSS devs aren't being paid for their code is making this worse, not better, as they work for fame, not fortune.
Nobody wants to use joint-repos because they don't want to give up or share the property rights to the contents. But because anything someone else does in a repo you own, also belongs to you, people are disincentized from contributing to your repo.
GitHub, especially, has incentivized this splintering and isolation. Everyone wants to have all changes in their own repo because they can profit best on repos listed directly under their own name, so long as they become popular. Maximize your 🟩 and ⭐ , like chips you can cash in for a prize.
And because forking other people's repos is the norm, rather than teamwork, requests for changes are usually ignored or responded to with "fork it, bro." Go away. Leave me alone. My repo is none of your business.
Too autistic, even for me
So, the developers separate their efforts into a million tiny repos that are mostly redundant with other ones, there's little interaction, progress is often surprisingly slow and stalls for months at a time, it's hard to keep track of what other people are doing (so that you can review and test changes), most of the effort is headed straight for the bin, people build the same things over and over, and communication is extremely limited.
This is a work environment that is unattractive for anyone who isn't autistic and/or highly introverted. Half of the fun of open-source development used to be the esprit de corps. Much has been said about #Bluesky, but it all misses a major point: that's where you go, if you want to work with other people, to build something large, polished, and impressive. It doesn't actually matter how many developers Nostr has, if they all only stare at their own plates.
Your repo coulda been a file folder.
Ironically, git was developed for collaboration on large projects with a distributed team. Now, everyone uses it for projects they work on alone. They put those projects on the Internet to market them. It's a cheap gimmick, not an earnest attempt at collaboration. Collaboration begins at the beginning.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
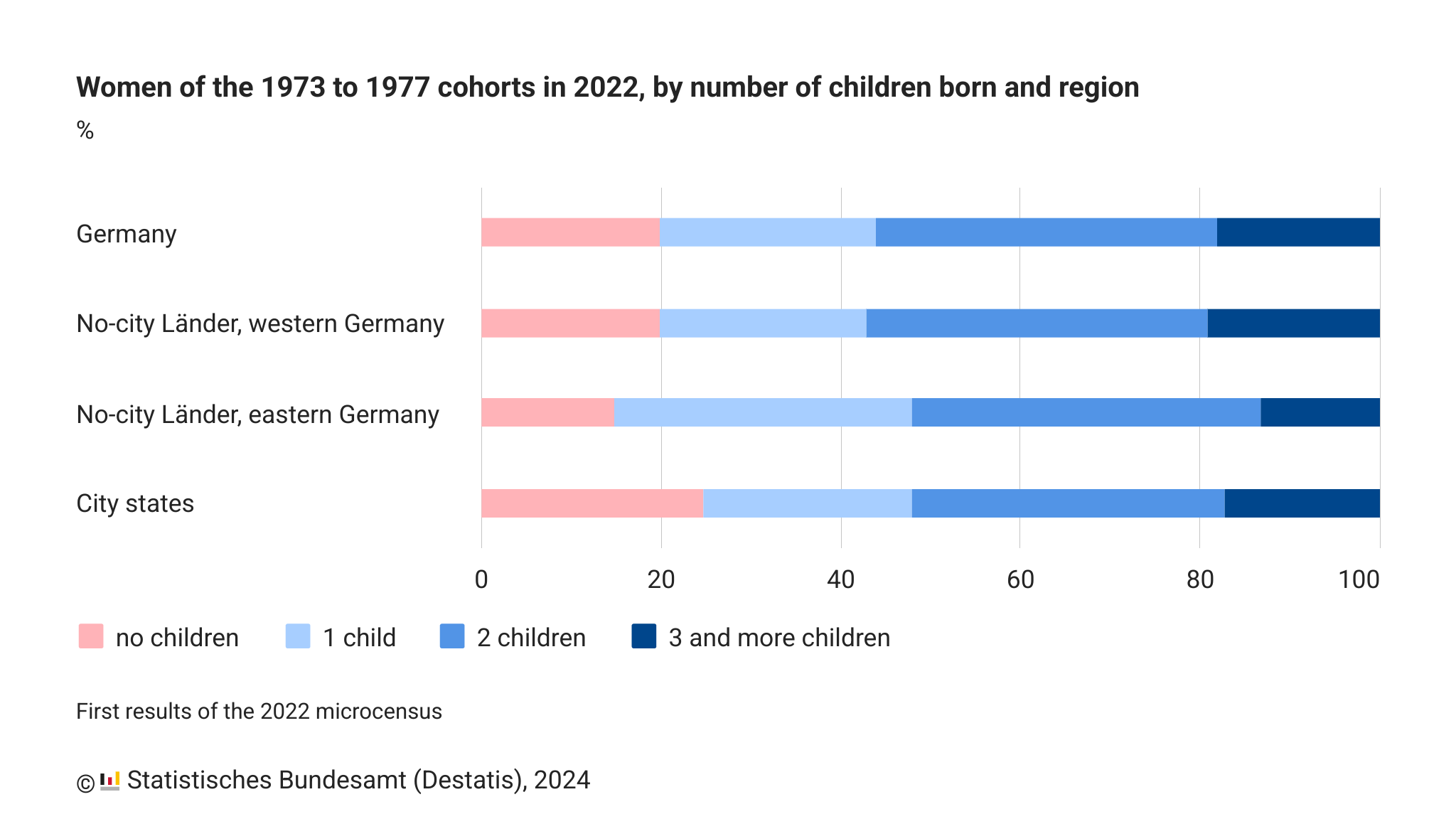
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
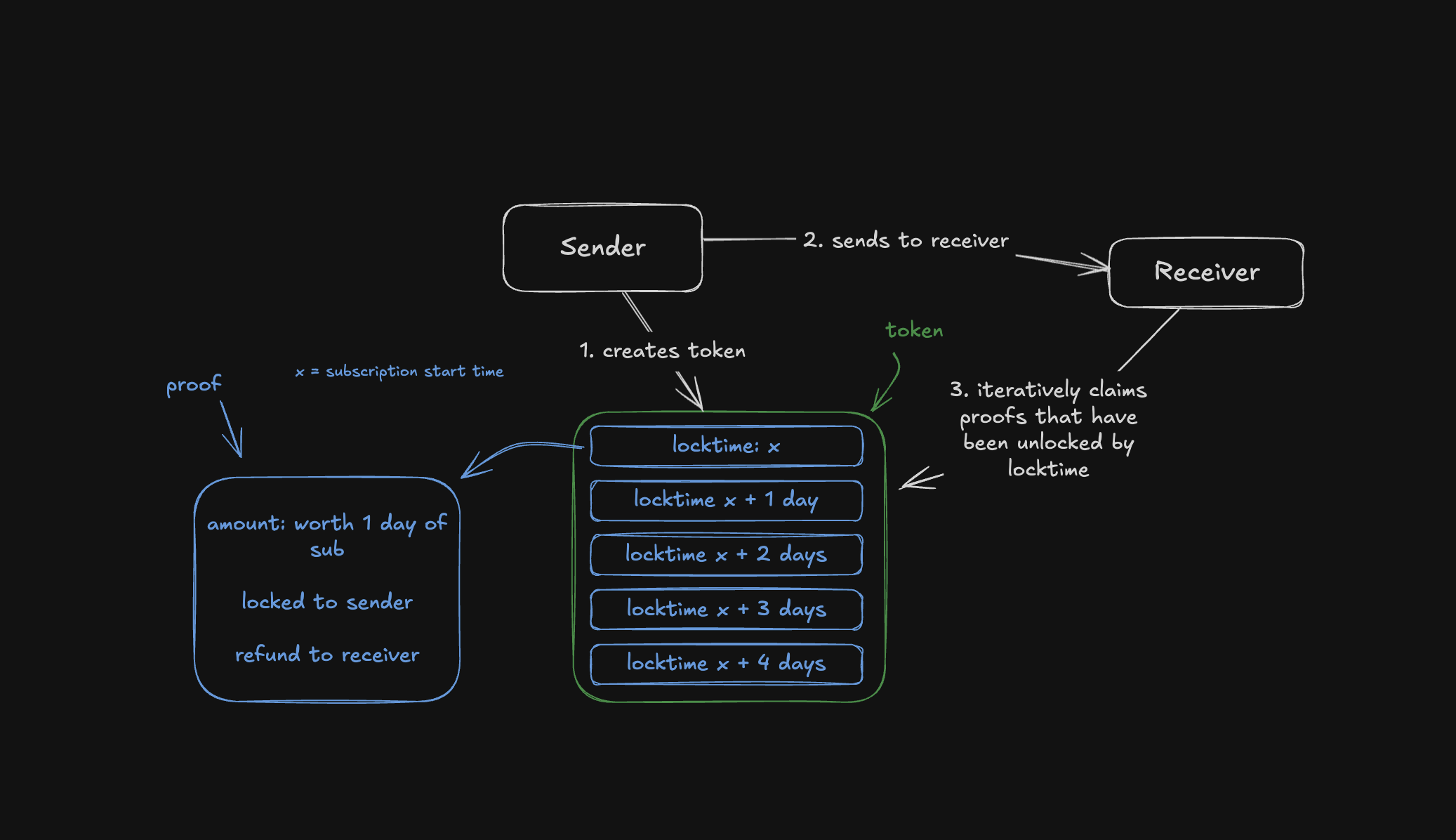
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 01d0bbf9:91130d4c
2024-11-19 14:46:24
@ 01d0bbf9:91130d4c
2024-11-19 14:46:24The Bitcoin community thrives on open-source innovation, but Coinkite’s move against BTClock risks stifling progress and alienating its core supporters.
Open-source projects like BTClock typically aim to promote innovation and accessibility within the Bitcoin community. Suing the programmer for trademark infringement seems like an overly aggressive move by Coinkite, given the values that Bitcoin and its ecosystem often stand for: decentralization, collaboration, and open innovation.
Why It’s Problematic:
-
Chilling Effect on Open Source:
-
Actions like this discourage developers from creating alternative solutions or building on existing ideas, which stifles community-driven progress.
-
Open-source projects thrive on shared knowledge, and this lawsuit could set a precedent for others to clamp down on grassroots efforts.
-
Reputation Risk for Coinkite:
-
While Coinkite has long been respected for products like the Blockclock and Coldcard, this move could alienate its core audience—Bitcoiners who value freedom and decentralization.
-
By targeting an open-source developer, Coinkite risks being perceived as prioritizing profits over community principles.
-
Trademark Infringement Question:
-
If the issue is solely over the name "BTClock," a fair resolution could involve renaming the project rather than pursuing legal action.
- Lawsuits should ideally be a last resort, not the first response.
A Better Approach:
- Coinkite could have worked with the BTClock developer to address concerns without legal action—perhaps through dialogue or collaboration.
- Open acknowledgment of BTClock’s differences (lower cost, open-source) would have shown confidence in their own premium product, while still respecting community-driven alternatives.
What NVK and Coinkite Should Do
Even now, NVK could mitigate the damage:
- Withdraw the Lawsuit: Openly acknowledge the backlash and frame it as a misunderstanding or a "necessary step" that they’re now reconsidering due to the community’s response.
- Collaborate with BTClock: Find a way to coexist, perhaps by licensing certain Blockclock-specific elements if truly necessary, while leaving room for BTClock’s open-source innovation.
-
-
 @ 893a31fa:256af11f
2025-01-24 20:48:36
@ 893a31fa:256af11f
2025-01-24 20:48:36Over the past 4 years, we have lived through and witnessed unprecedented suppression of ideas from public/private partnerships in the United States. This broke our nations' ability to think and agree on a narrative for our reality. Now, I know Trump is back in office, Ross is free and things are looking great for our future. But why do the ideas and policies of our politicians in power matter so much? And why, at the same time, do the ideas of the individuals subject to them matter so little? I believe it's because we have built our lives and our incomes on platforms rather than protocols. We didn't read the fine print. We opted not to own anything and tried to be happy anyway. We need an exit. Bitcoin gave us an exit for our value and time. Now we need to build more exits that we can rely on.
Video as a medium for learning and communicating information has surpassed every classroom you’ve ever stepped into. More people now learn critical skills, spark new ideas, create culture, and discover hidden talents by watching videos online than anywhere else. Yet, this same medium is stuck in the iron grip of corporate gatekeepers, who control what you see and hear through hidden algorithms.
Day after day, our viewing habits are corralled by these profit-driven, ad based platforms. They shape our conversations to keep us engaged with their content, so we scroll passed more ads. They push us toward self-censorship so they don't loos their advertisers, and they feed us the content they deem acceptable for our consumption while hiding or downplaying content they deem of lesser value. It’s not an outright dictatorship. It’s quieter and more insidious, with the algorithm’s interests taking priority over our own, even our hobbies and interests are manipulated by this effect.
The Path to Exit
Without an exit, platforms don’t have to earn your loyalty, they own it. People have tried to escape. Over the years, we’ve seen platforms like Odysee (LBRY), PeerTube, BitChute and others promise “decentralization,” only to falter because of complicated Ponzi token schemes, clumsy technical demands, or the same old centralization in a new package. LBRY uses similar technology, but is overly complex and doesn't allow for the exit from one client to another in a user-friendly way. And the Odysee company ends up seeding most of the content anyway. "Use our servers and not Google's!", they say in the end. No matter how high-minded the pitch, these efforts never truly replaced the major players, so we come crawling back. Because the exit wasn't real enough. The transition wasn't easy enough. The alternative wasn't strong enough.
Why do the giants hold power? Because you can’t just walk away when there’s nowhere else to go. This is The Exit Problem in action. Freedom requires an alternative, a place you can migrate to without sacrificing your content or your community. That’s the gap bitvid is aiming to fill. By building a genuinely competitive system, using only open standers, it gives us a real choice: stay in the walled garden or exit to a network that respects our sovereignty. The only thing is, it requires personal responsibility. As a Bitcoiner, this appeals to me. With great power comes great responsibility. And that's ok, because as you will see, if you can keep a computer with some hard drive space turned on and connected to the internet 24/7 then you can host your own video content. And your community of fans can help you host it too!
Digitally Free
To really understand bitvid, forget any idea of it being “just another video platform.” Think of it as a framework or blueprint. It’s designed to let you share and watch video without kneeling to corporate or government control. It's designed to keep your content available so long as 1 person in the world wants it to exist.
The main idea? User sovereignty. You, not Big Tech, hold all the control. bitvid relies on a marriage between two distributed technologies, Nostr and WebTorrent. Nostr supports open, resilient note-sharing (which extends to things identity, and subscription management), while WebTorrent provides the engine for the peer-to-peer video file distribution. Put them together, and you get a system that bypasses central servers and choke points of control. Instead, viewers connect to each other directly, using magnet links for streaming directly into their browsers window.
This system’s open design encourages multiple clients to eventually be created and different approaches to flourish. Eventually, you can choose the one that best aligns with your values and preferences. This competition keeps everyone honest, making it impossible for any single entity to seize control.
I have a temporary whitelist and blacklist built into my version of the client, but you can fork the code and remove that whitelist or blacklist and host on your own domain if you want. or even post content from a static version on your desktop. This system is designed to be modified, improved and forked into as many clients as we need to explore all the ways we want to search and filter the content we post. It's just like Nostr in that way.
bitvid’s Core Ideas
Right now you see a basic and buggy proof-of-concept client showing how everything could eventually fit together. But that’s just step one. I hope and believe that others will quickly follow, either contributing to my initial design or creating a new client, customizing the features and interface for different audiences and use cases.
Exit as a Feature: Your content and online persona aren’t locked into any one client. If you eventually find a particular client goes off the rails in a way you don't like, you can take your subscriptions and block lists along with your identity elsewhere, with minimal hassle. Nostr allowed users to move text notes to different relays at will. Now, bitvid extends that capability to video. If a client blocks your content, host your own version, or shift to a new client altogether. Likewise, if a client does not block enough of the content you don't want to see, then you can do the same. Nobody can yank your channel offline from a distant control room or force you to stay and watch the feeds you dislike.
The Living System: There’s no single server that can crash and kill bitvid or its content. So long as one person in the world is seeding a video, and the Nostr note that contains the magnet link is accessible on some relay, then it will live on. If a client decides to censor it, another can flip the switch back. It’s a swarm that endures, so long as WebTorrent peers keep it alive.
Decentralized Streaming Infrastructure: By using WebTorrent, we turn viewers into seeders also. When you watch a video, you help distribute it. This crowdsourced approach makes the entire network sturdier and harder to silence. And it should function even better as more users and content come online.
User Sovereignty
Peer-to-peer technology comes with tradeoffs. Yes, this requires personal responsibility, and yes, it may be slower than YouTube. But that’s the price of freedom, and for those who value sovereignty, it’s a price worth paying. Because those inconveniences pale in comparison to the freedom you gain when nobody can arbitrarily cut you off because they dislike your message or wanted to tamp down your ideas. The reason this matters is that users become the infrastructure. Instead of expecting a hosting provider to store all videos, you and I take on that role ourselves. Videos stay accessible as long as a handful of us continue to seed them. The network’s future is in our hands, not behind a server farm in Silicon Valley.
With bitvid, we also open the door to parallel realities. Different communities can adapt the codebase to fit their needs, whether that means specialized niches, curated libraries, or completely uncensored environments. You decide which universe you want to inhabit, rather than letting one corporate platform and algorithm decide for you. Developers who share a vision of open content can build new tools, refine user experience, or implement creative incentives for people to seed, like Bitcoin zaps. Meanwhile, creators will need a little nudge to get onboard. That’s why bitvid needs to emphasize creator education, helping them to understand how to seed videos, manage magnet links, and fully embrace this new direct P2P approach.
Mind Meets Reality
The ability to discuss and share ideas without a corporate overlord quietly steering your every view or suppressing your voice and thought is an important next unlock for our culture in America. Now is the time to build this kind of system without fear or hesitation. Nostr's simplified design allows for fast experimentation and Bitcoin's Lightning Network and other tools like Cashu allows for various types of incentive structures to be created. Videos carry messages, and messages can change minds, cultures, and entire nations as we have seen. This is why controlling them has been so profitable in the past.
bitvid offers a peaceful revolution. You don’t need to file a lawsuit or beg a faceless megacorp for your right to speak. You can simply leave, and bring your videos with you. This freedom to exit is what truly unravels the power of centralization. The result? Independent communities that thrive on their own terms, unburdened by what has been... All it takes is a choice. Step off the corporate treadmill and connect to a network that puts you in the driver’s seat. It’s a quiet shift, but its implications are enormous. When enough people choose freedom, the old guard starts to fade. Who happens to sit in the Oval Office will matter less. And we as a nation can determine our own relationships with reality.
Help Me Build
So, where does this all go next? Are we standing on the brink of a major transformation in how we share and consume video? All I know right now is that bitvid is not anywhere near ready to achieve all these lofty goals, yet. bitvid is a simple idea. Just a proof of concept really. Showing everyone that this just might work. But it’s only going to be as strong as the community that adopts it and can improve it.
Want to shape the future? Jump in with me. Take a look at the code I have so far, help me fix bugs and add features! Propose fresh ideas for how videos should be shared and monetized with Zaps or Cashu. I'm just one inexperienced developer trying to make something cool. I'm actualy just a Graphic Designer. So I need your help. Let's take this idea to its logical extreme end and see if we can foster a new way to share video online. Spread the word, get in touch with me on Nostr if you want to help out or get on the whitelist and start seeding your own content.
By stepping into bitvid, you exercise The Path to Exit. You’re not just joining some new platform, you’re helping craft an ecosystem that thrives on competition and free choice, an ecosystem that can’t be dictated from above. Peer-to-peer torrent sharing isn’t some dusty relic of the 2000s. It’s the best hope for an engine of real independence. Now you can’t be shut down at the flip of a corporate switch.
So, build or watch it grow, either way, bitvid needs the participation of people who believe we deserve better than the status quo. If you’re fed up with censorship, stifling algorithms, and one-size-fits-all platforms, take the leap. Every seed, every new client built, and every viewer who opts in tightens the screws on centralized control of ideas and culture.
Together, we will reclaim our minds and our culture from the gates of centralized control.
-
 @ 3c506452:fef9202b
2025-01-24 20:27:49
@ 3c506452:fef9202b
2025-01-24 20:27:49Kia ora ano e te iwi whanui!
Often I pose the question to myself "How would I say this if I had no knowledge whatsoever of English?" That's basically what guides my sentence formation whenever I speak Maori.
Since the arrival of Tauiwi into our turangawaewae, our reo has shifted, largely due to intermingling with the English language, and an entire generation or two completing losing the reo.
Great efforts have been made to secure our language from total extinction, and the number of te reo speakers seems to be on the rise.
What I do notice though is that most of the time when I do hear te reo being spoken, it's cadence follows that of the English language.
Vowels are clipped, consonants are aspirated, and English thought patterns are disguised via the Maori language.
Regardless, I still appreciate and prefer the reo to be spoken rather than it not be spoken at all.
I once heard someone remark that"Maori sounds like Hawaiian with a New Zealand accent. Hilarious!"
So, how do I personally tackle this and try make my own reo sound more Maori?
Here's how:
-
Read Nupepa Maori - When the written word came to us, we dove straight in. Nupepa Maori gives great insight into how the language was used using the new medium of pen and paper.
-
Listen to the older videos of Wakahuia Docos - Wakahuia has been running for a long time and I find listening to our old people of those times a good way to hear the differences between how the reo sounds today, and how it sounded a little while back.
-
Listen Radio Kahungunu archives - They have a really nice archive of a talkback radio show.
-
People to listen for - I personally try to find anything by Timoti Karetu, Quinton Hita, and Julian Wilcox as I really enjoy the sound of how they speak the reo.
-
Listen to Cook Island Maori, Gagana Tokelau and Hawaiian (Keao Nesmith, Niihau dialect, Kaalala, Kanahele Collection) - Listening to other polynesian languages gives a good general gist of the sound of polynesian languages. I try to emulate a similar sound whenever I speak te reo.
No reira, ko tena tena, I hope that 2025 will be a good year for Te Reo Maori!
Nga rauemi:
Nupepa Maori
Wakahuia
Radio Kahungunu
Quinton Hita
Julian Wilcox
Timoti Karetu
Kanahele Collection
Ka Alala
Gagana Tokelau
Kuki Learning -
-
 @ a311301f:4663f8f2
2025-01-24 19:44:24
@ a311301f:4663f8f2
2025-01-24 19:44:24Needed to change the /tmp part replacing it with a call to $ENV in Powershell %TEMP% is now $env:PATH
Here is the Windows compatible program:
```perl
!/usr/bin/perl
use strict; use warnings;
my $filename = '/tmp/1.txt';
my $temp_dir = $ENV{'TEMP'} // '/tmp'; print ("temp: ", $temp_dir, "\n"); my $filename = "$temp_dir/1.txt";
if (-e $filename) { open(my $fh, '<', $filename) or die "Cannot open '$filename': $!"; while (my $line = <$fh>) { if ($line =~ /\$/) { print $line; } } close($fh); } else { open(my $fh, '>', $filename) or die "Cannot create '$filename': $!"; print $fh "This is a sample line with a \$ character.\n"; close($fh); }
```


