-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 21ac2956:09d1e2df
2025-01-22 15:27:00
@ 21ac2956:09d1e2df
2025-01-22 15:27:00kakoi の仕様についてのメモ
キーボード操作
- 左手での操作に最適化
| キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする |
タイムライン
- kind:1, 6, 7, 16を取得して表示する
- フォロイーの名前の前には * が付く
フォローリスト(kind:3)
-
参照のみで更新はしない
-
F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存)
プロフィール(kind:0)
- F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存)
返信(NIP-10 kind:1)
- kakoi のタイムラインに流れるすべてのイベント種に返信可能とする
- スレッドを考慮せず、単一イベントへの単発返信とする
- e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定
json ["e", "返信先 event-id", ""]- p タグは 返信先 pubkey ひとつだけを指定
リポスト(NIP-18 kind:6 , 16)
- kakoi のタイムラインに流れるすべてのイベント種をリポスト可能
- kind:1はkind:6。その他はkind:16でリポストする
- e タグは relay-url に空文字を設定
json ["e", "リポスト元 event-id", ""]引用(NIP-18 kind:1)
- q タグは relay-url に空文字を設定
json ["q", "引用元 event-id", ""] -
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 84b0c46a:417782f5
2025-01-11 01:48:46
@ 84b0c46a:417782f5
2025-01-11 01:48:46nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0df2mwnp2q6hm6zjrthkmx3fudwsuwrmgnwrdavpzgjy8nnuqm5cqpd06k
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs2muhvnev5367ywuzkhell9my86jlnzhsnuszwl46tnc3fpsx9mtgjkqnu7
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsznnkrl8qdwzgp7ry2hc7a77kwhg440gv9xtmvyfawggrpz3rhwvcx4rckf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsyjf80k3djt96qncgvwl2yem09fdqcc0y9l8t657yc9qg2yhmg7kcnua8vn
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0s3lp0w0yclk64j0tpc5fvrulv78g2lfjz3gcgacw9mt6czek26qtqxuck
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqqs89tst72clc60wse3zq4qfs0976y7areffnhx26atvu6pv58hg6dsxvcc79
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr3mhxue69uhhxun5wfjkccte9e3j6um5v4kxcctj9ehx2aqqyp5k40r3ug02yz5y0tn67tm2lwevuwac54qyw3yyct8n8uzr7pjz2q92pyt
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyp9pennjwq2qk4dxpr440wxqm5cfwah4qccd8la62hantxdelkk82ty9mr8
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqsz9w30kxzjshwd8sq7jg2hsy2hwqg3zu7gyvxnsyrgfw0ur4rkhsg9v0re4
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqs8wkx2r8txt9q69c3zvpqs2em2s40nc8tajmcc5l8ngxn8v2ng3sc43xvzu
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyzdkacpjqvv2y79zgvufx9jh39rd7xa8v056rgn4xelmnmrq9u2tuguswek
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qy2hwumn8ghj7mn0wd68ytnyv96xztngv96hxqpqmdtjrs38fv8r20deplrlt8fma54gu43keuzquzks7673a27ud58slunr8y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhkummnw3ezucm0d4cxjmr994jhyun0wghxuet5qqsxzpx2r5hd36pruzn2e58wh947y2t0t205fp5xtstqp5wq0qgcjuq07rqlk
-
 @ c43d6de3:a6583169
2025-02-05 02:46:10
@ c43d6de3:a6583169
2025-02-05 02:46:10
Right this moment, 5.52 billion pairs of hands are within arm’s reach of the internet.
Hands stretch across pillows, eagerly reaching for phones first thing in the morning. Fingertips tap at keyboards and swipe across glowing glass.
The world has never been so connected. Billions of conversations are happening every second.
Yet, humanity has never been so quiet.
Hotel lobbies, waiting rooms, train stations, and airports — places once buzzing with the chatter of strangers — now lie quieter than libraries. Most libraries don’t exist in the physical sense anymore.
Humanity Has Gone Mute.

Small talk is disappearing. The tiniest thoughts are condensed into 280 characters to be posted on X, hoping to garner hearts, claps, zaps, or whatever gimmick social media platforms use to keep us tethered to their feeds. Instead of sharing these thoughts with the few souls occupying the same physical space as us, we broadcast them into the digital void.
Gone are the genuine, physical reactions — a smile, a laugh, maybe a headshake if a joke didn’t land.
Who needs small talk, right? Wasn’t it just that awkward thing people did before cellphones and the internet existed?
No. The silence is worse.
It’s the manifestation of relational decay.
That’s why people talked. People talked about the weather or about Mrs. Jones’ dog that always gets out. That’s what helped neighbors scale one another’s emotional fences and get to know one another. It was, and always will be, the first step to any meaningful relationship.
Today, small talk has been relegated to social feeds and forums. It’s easier to make a friend across the planet than to make one next door. People fall into the trap of chasing likes, followers, and fame, while their local connections — the ones critical to mental health and a sense of purpose — fade into the background.
Maybe I’m out of touch. Maybe I just don’t get out enough. But as a member of the Army Reserves, I’ve experienced something rare.
Once a month, I attend drill, and once a year, we’re sent on an annual training that can last up to thirty days. During those thirty days, we’re often shipped off to a place far from the internet. And in that time, something remarkable happens: small talk comes back to life.
It’s incredible to watch my fellow Soldiers connect.
The relationships we have before training versus after are night and day. And it all starts with small talk — simple jokes, shared gripes, and the mundane details that snowball into camaraderie.
When we’re forced to take that first step to avoid the boredom of silence, we discover one another’s existence. It’s a reminder that sometimes, the absence of convenience is what sparks true connection.
Small talk isn’t just filler. It’s the foundation of relationships. Maybe it’s time to put down the phone, look around, and say something — anything — to the person next to you.
While the world may feel quieter than ever, the potential for connection has never been stronger.
I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
Thank you for reading. If you liked this article let me know with a zap and share with friends you feel might enjoy it too!
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 1cb14ab3:95d52462
2025-02-05 00:14:34
@ 1cb14ab3:95d52462
2025-02-05 00:14:34Welcome to the first installment of my ‘Nostr Spotlight’, a series where I explore various Nostr clients (which I will refer to as apps for simplicity sake), review their features, and share tips on how to use them effectively.
For the first installment, I’m diving into npub.pro, an incredible service that lets anyone on Nostr create a fully functional website using their already-published notes.
What is npub.pro?
npub.pro is a simple—yet powerful— tool that takes your Nostr content and turns it into a website instantly. By filtering through hashtags or keywords, or hand-selecting which notes to feature, you can curate what appears on your site.
This allows for highly customizable and dynamic websites that anyone on Nostr can deploy. Whether you’re a blogger, photographer, journalist, artist—or just want to organize your notes into a cleanly setup website—this service opens up endless possibilities for showcasing your notes.
Who Should Use npub.pro?
This service is ideal for:
✅ Writers and bloggers who want a frictionless way to publish content.
✅ Artists and photographers looking to showcase their work.
✅ Journalists and researchers who need an easy way to organize articles.
✅ Anyone who wants a personal website without dealing with hosting or technical setups.
Why I Love npub.pro
I’ve personally deployed several websites using npub.pro, each serving a different purpose:
HesArt – My personal art portfolio.
https://image.nostr.build/6a7030a24a9c5d4a9e3a0854020e08740241e870e46083b6b326ca36d5dc681f.png
Hes – My main long-form writing site, featuring artist statements, travel guides, photo series, tech reviews, and economic essays.
https://image.nostr.build/7d088829dd2ec0f9702430f115e29d368da85a78227cf6524f8773216f6a102e.png
HesCooks – A collection of curated recipes.
https://image.nostr.build/840ffdc74ac618ddf9534d4ab77a09d02aee45eee8c332a6733bcea5b80a3d2a.png
HesCreates – A categorized and searchable archive of my notes.
https://image.nostr.build/4663c91f3c77ad59f0f291813c672395f8cc20c6806ca2afffb3e3d65b6c6f37.png
The ability to filter my Nostr content and instantly publish it as a website has made organizing my notes seamless and efficient. The opportunities are endless and I have several ideas for other websites I plan on deploying.
How to Get Started
1.Visit npub.pro.
2.Enter your Nostr private key (nsec) using an extension of bunker.
3.Choose your filters (hashtags, keywords, etc.) to curate what appears and select a pre-made theme.
4.Publish instantly – no extra setup needed!
It’s that simple.
Final Verdict:
5/5 Stars ⭐⭐⭐⭐⭐
npub.pro is an outstanding tool that makes publishing on the web effortless for Nostr users. It’s intuitive, versatile, and packed with potential use cases. Whether you need a blog, portfolio, or curated archive, this app delivers.
Highly recommended!
More from Hes
Note: This spotlight is not sponsored. I thoroughly enjoy the service and have received outstanding customer service from the team at npub.pro!
Stay tuned for more Nostr App Spotlights as I explore the best apps in the ecosystem!
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ 3b7fc823:e194354f
2025-02-03 14:51:45
@ 3b7fc823:e194354f
2025-02-03 14:51:45Protecting Email Communications: A Guide for Privacy Activists
Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights.
Why Encryption Matters
Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location.
Key Encryption Tools
There are several tools available for encrypting emails, catering to different skill levels and preferences:
- PGP (Pretty Good Privacy)
-
For Tech-Savvy Users: PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient.
-
GPG (GNU Privacy Guard)
-
Free and Open Source: GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution.
-
ProtonMail
-
End-to-End Encryption: ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content.
-
Tresorit
-
Secure Communication: Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists.
-
Claws Mail
- User-Friendly Email Client: Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features.
Steps to Encrypt Your Emails
- Choose a Tool:
-
Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface.
-
Generate Keys:
-
Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses.
-
Share Your Public Key:
-
Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform.
-
Encrypt and Send:
- When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content.
Minimizing Metadata
Beyond encryption, consider these steps to reduce metadata exposure:
- Use Tor for Sending Emails:
-
Routing emails through Tor hides your IP address and makes communication more anonymous.
-
Avoid Revealing Identifiers:
-
Use .onion addresses when possible to avoid leaving a traceable email account.
-
Choose Privacy-Friendly Providers:
- Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration.
Best Practices
- Avoid Using Real Email Accounts:
-
Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure.
-
Understand Legal Implications:
-
Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly.
-
Use Encrypted Backup Methods:
- Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised.
When Encryption Isn't Enough
While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists.
Conclusion
Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 78b3c1ed:5033eea9
2025-01-10 12:31:01
@ 78b3c1ed:5033eea9
2025-01-10 12:31:01※ライトニングノード保有者向け
Alby Hubをインストールした時なんもわからずポチポチしているとMegatlith LSPノードからインバウンドを購入してチャネルを開くことになります。2万sats(2024/12/4 午後7時時点で三千円ほど)かかります。
そこで誰もが思うに違いない 「高いなぁ。だれかタダで無料で私のHubにチャネル開いてくれないかなぁ...」
その願望をかなえる献身的なノードランナー(笑)がAlby Hubへチャネルを開いてあげるための手順書みたいなものがこの記事です。 ~~ppmをうんと高くしてぼったくってやりましょう!~~
※AlbyHubにオンチェーン資金が無くてもLNDから開く方法を発見しました。末尾に追記しました。
《これはアンカーアウトプットを利用するタイプのチャネル》 条件 ・チャネルを開く側 Clearnet IPアドレスで着信可能であること。Torノードは不可。ノードURIを公開していなくても良い。AlbyHubでピア登録できるClearnet IPアドレスと着信ポートがあればOK。
・開いてもらうAlby Hub側 オンチェーン資金25,000sats以上をデポジットしておく。ないと開けません。
手順
-
[Alby Hub側] オンチェーン資金をデポジット Hubログイン後の左メニューからNodeを選択。Saving BalanceのDepositを選択。するとbc1qではじまるオンチェーンアドレスが表示される。ここへ送金してオンチェーンをデポジットしておく。
-
[Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。 右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。
-
[開く側ノード] AlbyHubを確認、チャネルを開く ThunderhubやRide-The-Lightningなどを使い、Alby Hubのノードが表示されていることを確認。Hubにエイリアスは無いのでノードIDで表示される。 このノードに対してチャネルを開く。Private channelが望ましいと思われる。 6conf後に開設完了。
終わり!
メモ
- Alby Hubではbase feeは設定可能だがrateが設定できない。そもそもAlby Hubはルーティング向けノードとして設計されてない。セルフカストディアルウォレットです。
- public channelだとchannel_update, channel_announcementがゴシップされるまでHubへ送金できない(no route)。上記の通りウォレットとしてのノードならprivate channelだけにしてルートヒント付きインボイスが発行できるようにしとくのが望ましい。
- LDKにおいて相手からチャネルを開いてもらう場合にオンチェーン資金が必要。相手がチャネルリザーブ無しのチャネルでもOKなら不要。現にメガリスLSPからチャネルを開いてもらう時オンチェーン資金が0satsでも開けているのがその実例。
- オンチェーン資金が必要なのはチャネルタイプがanchorの場合。オンチェーン資金でアンカーアウトプットをCPFPするためみたい。anchorが登場する前のstatic-remotekeyのタイプならオンチェーン資金は不要。
<ここからが追加>
《これはアンカーアウトプットを利用しないタイプのチャネル》 LNDからチャネルを開くときにstatic remote keyを利用するタイプを指定します。
条件 ・チャネルを開く側 ※上記と同様。
・開いてもらうAlby Hub側 無し。 手順 1. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 2. [開く側ノード] AlbyHubを確認、チャネルを開く SSHログイン、UmbrelならLightningのターミナルで以下のコマンドを実行します。
<ノードID>は開きたいAlbyHubのノードIDで置き換えてください。 <チャネルサイズ>は開きたいチャネルの金額、例えば20万satsなら200000としましょう。 <手数料率>はチャネル開設のトランザクションに掛ける手数料率です。mempool. spaceなどで手数料水準を確認して指定しましょう。 --channel_type tweaklessがキモです。デフォルトだとanchorになります。RTLやTHで開くとこのanchorになります。なのでlncli openchannelでやります。
lncli openchannel --node_key <ノードID> \ --local_amt <チャネルサイズ> \ --sat_per_vbyte <手数料率> \ --private --channel_type tweakless終わり!
-
-
 @ dffd3ffc:5ade7be1
2025-01-04 12:58:17
@ dffd3ffc:5ade7be1
2025-01-04 12:58:17Nostr 利用開始から 1 年を迎えて
はじめに
みなさんこんにちは。おっぱぴぃです。
ハッカーのおもちゃとしての Nostr のススメ と Nostr の面白さをエンジニア目線で解説してみるをみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。
nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c
Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。
初投稿日

今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~
これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。
その日はNostr の Scrapbox(現 Cosense)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。
nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w
~~おまえ、このころから大欲情を…~~
のす会でのオン会(?)
Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。 過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、
nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc
その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。
nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5
こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。
初のオフ会参加
2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、ゴリラ.vim#30~四谷ラボコラボ~の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。
この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、
nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp
顔面が痙攣したり、
nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn
詫び菓子を貰ったり、
nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl
病院待合室みたいな場所で検尿コップで水飲んだりと
nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy
トラウマになりそうなオフ会でした。当時の様子はnosli でまとめています。
今振り返ってもくちゃくちゃの体験してるなと思いますが、 ~~クレーターを作りそうな青ウサギがいたものの~~
nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da
誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。
各種イベント参加
Nostr には四谷ラボ参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば…
- Bluesky Meetup in Tokyo Vol.2
- 技術書典 16 ⇒ 関わらせていただいたのぶこ本
- Nostrasia2024
など。
微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。 自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。 関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。
オフ会履歴
私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。

うわっ...私のオフ会参加、多すぎ…? ~~1 年間は52週しかないねんぞ~~
このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。
ちなみに、人単位でお会いした回数もまとめています。
 ※:Nostrasia などのイベントでお会いした回数は除いています。
※:Nostrasia などのイベントでお会いした回数は除いています。こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。
思い出深かった出来事
nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r
nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8
この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~
その後も酔ってる時を中心に結構誤字をやらかすので、那月さんによるまとめが作られています。
名前としては不名誉かもしれませんが、面白いのでOKです。
おわりに
振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。 Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。
Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。
これからもよろしくお願いします。
-
 @ fd78c37f:a0ec0833
2025-02-03 00:23:23
@ fd78c37f:a0ec0833
2025-02-03 00:23:23🔹 Pre-event buzz: Even before the event started, numerous calls came in to confirm the venue and ask if they could bring friends along. Upon arrival, many young attendees were eager to learn more about YakiHonne, reflecting the excitement and anticipation surrounding the meetup.


🔹 Engaging discussions: The event kicked off with an introduction to Nostr and YakiHonne’s core principles, sparking insightful conversations about what it truly means to have a decentralized social media platform.

🔹 Deep dive: Attendees raised many questions, particularly about YakiHonne’s decentralization model. The concept resonated with many, and a large number of participants expressed their support and interest in becoming part of the YakiHonne ecosystem in the future.

 The meetup wrapped up with light refreshments 🍹, networking 🤝, and a photo session 📸. Even after the event officially ended, conversations continued as people stayed behind to connect and explore further possibilities ✨.
The meetup wrapped up with light refreshments 🍹, networking 🤝, and a photo session 📸. Even after the event officially ended, conversations continued as people stayed behind to connect and explore further possibilities ✨.


YakiHonne Meetup was more than just a gathering—it was a step forward in shaping the future of decentralized social media! 🚀
YakiHonne #Nostr #DecentralizedSocialMedia
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 5a261a61:2ebd4480
2025-02-02 20:42:37
@ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to anything for 90 days is like trying to herd cats on espresso. You start strong, then life happens: kids, chores, or that one glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments.
The Game Plan
First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap).
Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment.
Reality check: some days will suck, and you'll want to skip. That's where having everything planned out helps. When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it.
Why It (Maybe) Works
Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment.
Current run
My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - 30 days: Tiny dopamine hit. (making little photoset of Her feet playing with my hardon… for science.)
- 60 days: Mid-tier flex. (cleaning mushed banana split off Her toes tongue only)
- 90 days: Go nuclear. (a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment?
TL;DR
90-day challenges are the BDSM of self-improvement: consensual, slightly painful, and weirdly addictive. Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr.
90days #FLR #LostCauseButStillTrying #femdom
-
 @ ddf03aca:5cb3bbbe
2025-02-02 13:09:27
@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes.
What’s New in v2.2?
While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please let us know. Here’s a rundown of the major updates:
- Enhanced Proof Creation: The way proofs are created internally has been revamped.
- User-Controlled Outputs: You now have full control over how outputs are created.
- Improved Bundling: We’ve switched our bundling tool to vite for faster and more modern builds.
- Updated Testing Tools: Our testing framework has migrated to vitest and msw, with added browser testing via Playwright.
New Flexibility with OutputData
In previous versions of Cashu-TS, the creation of outputs (or BlindedMessages) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic.
What’s Changed?
In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new
outputDataoption available on all output-creating methods, you can now bypass the automatic process and provide your own outputs.For example, you can create two proofs tied to different public keys in a single mint operation:
ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, });Customization Made Easy
The
outputDataoption now accepts anything that conforms to theOutputDataLikeinterface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like:```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array;
toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ```
Introducing OutputData Factories
While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support OutputData Factories.
A factory is simply a function that takes an amount and
MintKeysas input and returns anOutputDataLikeobject. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send:```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); }
function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); }
const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ```
Plus, you can now instantiate a
CashuWalletwith a defaultkeepFactory, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further.
Bundling Improvements with Vite
Starting with v2.2, we’ve transitioned from using
tscto vite for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits:- Modern Build Target: We’ve updated our build target to ES6.
- Updated Exports: The package exports now reflect the latest JavaScript standards.
- Standalone Build Soon: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML.
If you encounter any issues with the new bundling setup, please let us know.
A Nod to Vitest
In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to vitest combined with msw. This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx!
In Conclusion
Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library.
Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to reach out to us.
-
 @ 59cb0748:9602464b
2025-01-01 06:15:09
@ 59cb0748:9602464b
2025-01-01 06:15:09Nostrでお世話になっている方も、お世話になってない方も、こんにちは!
タコ頭大吉です!
NIP-23を使った初めての投稿です。
今回は、私がここ数ヶ月中にデザインをした三種類のビタキセケースの紹介記事になります!!
ビタキセを買ったもののあまり自分の好みに合う外観や仕様のケースがなく、いくつかプロトタイプを作りそれなりに時間をかけて考えたケース達です。
これら3シリーズに関しては、FDMタイプの3Dプリンタの精度、耐久性、出力後の作業性を考慮して一つのパーツで完結することに拘って設計をしました。
一定以上の充填率でプリントをすればそれなりに丈夫なはずです。
また、基本的に放熱性と保護性を両立できるように設計をしたつもります。
それぞれのモデルについて簡単に紹介をさせていただきますので、よろしければ各リポジトリに付属のREADMEを読んでいただいて自作、フィードバックをいただけましたら幸いです。
それでは、簡単に各モデルの紹介をさせていたきます。
AirLiftFrame
 最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
TwinAirLiftFrame
 ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
VoronoiShell
 AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
いずれカスタム方法やインサートナットや増設ファンの選定方法等を紹介したいのですが、今回はNIP-23になれるという意図もあるので紹介に留めます! また、他の関連OSハードウェアプロジェクトのケースもデザインできたらと思っております!
今後ともタコ頭をよろしくお願いいたします。
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 8d34bd24:414be32b
2025-01-30 23:35:39
@ 8d34bd24:414be32b
2025-01-30 23:35:39Sometimes I’m reading the Bible and see a connection and go off chasing a rabbit trail. I type up my idea to organize my thoughts and see if there is actual Biblical support for it. Although it feels a bit weird to share Biblical ideas that I’m not certain about, it also seems a waste of lots of work to not share my speculations. Feel free to give me feedback if you disagree, especially if you have Scripture or historical evidence showing I’m wrong.
In this case, I’ve seen a portion that seems to be prophecy about our future, but that doesn’t necessarily mean that this entire group of chapters is future predictions. Sometimes prophecy mixes events that happens soon after the prophecy with events that will not be fulfilled until the distant future (like prophecies about Jesus’s first and second comings). I try to be open about what ideas I feel I have strong Biblical evidence to support and when my ideas have some evidence, but not conclusive evidence. This is one of my more speculative posts, but I hope you will find it thought provoking.
I was recently reading Isaiah 18-22. I had always assumed these prophecies of warning were in reference to things that had happened in the distant past (not that I knew any particular historical fulfillment), but this time I saw some major parallels with Revelation.
Now behold, here comes a troop of riders, horsemen in pairs.” And one said, “Fallen, fallen is Babylon; And all the images of her gods are shattered on the ground.” (Isaiah 21:9) {emphasis mine}
From Revelation:
And another angel, a second one, followed, saying, “Fallen, fallen is Babylon the great, she who has made all the nations drink of the wine of the passion of her immorality.” (Revelation 14:8) {emphasis mine}
And he cried out with a mighty voice, saying, “Fallen, fallen is Babylon the great! She has become a dwelling place of demons and a prison of every unclean spirit, and a prison of every unclean and hateful bird. (Revelation 18:2) {emphasis mine}
Of course it is possible that Babylon and Babylon the great are parallel, but different nations, but the similarity of statement is hard to deny.
All you inhabitants of the world and dwellers on earth,\ As soon as a standard is raised on the mountains, you will see it,\ And as soon as the trumpet is blown, you will hear it. (Isaiah 18:3) {emphasis mine}
This passage talks about all inhabitants of the world seeing a standard raised. Until the past 20 years or so, this was not possible. Now that almost every person on earth has a smart phone, we can know what is going on around the world in real time. This passage also refers to “dwellers on earth” which is a phrase used numerous times in Revelation.
In Revelation 11, it speaks of the two witnesses who testify to Jesus and call down plagues on the earth. After their death:
And their dead bodies will lie in the street of the great city which mystically is called Sodom and Egypt, where also their Lord was crucified. Those from the peoples and tribes and tongues and nations will look at their dead bodies for three and a half days, and will not permit their dead bodies to be laid in a tomb. And those who dwell on the earth will rejoice over them and celebrate; and they will send gifts to one another, because these two prophets tormented those who dwell on the earth. (Revelation 11:8-10) {emphasis mine}
Both passages refer to those who dwell on the earth and both talk about every person on earth seeing what is happening. This doesn’t sound like a prophecy fulfilled in ancient times, but about a prophecy that could not be fulfilled until modern times.
If these prophecies are about the end times and if the end times are now or very soon, what could they be referring to? Isaiah 18 begins with:
Woe to the land of whirring wings\ along the rivers of Cush,\ which sends envoys by sea\ in papyrus boats over the water.\ Go, swift messengers,\ to a people tall and smooth-skinned,\ to a people feared far and wide,\ an aggressive nation of strange speech,\ whose land is divided by rivers. (Isaiah 18:1-2)
Cush was located where modern day Sudan is located on the western edge of the Red Sea. Right across the red sea is Yemen which has been involved in missile and drone strikes on ships in the Red Sea. Traditionally the “land of whirring wings” is interpreted to mean locusts, but could it be referring to modern technology like drones? Who is Cush sent to seek? Who are the people “over the water,” “tall1 and smooth-skinned,” “feared far and wide,” and “an aggressive nation of strange speech,\ whose land is divided by rivers.”? I wonder if it could be the US. The US is over the Atlantic Ocean, “feared far and wide,” “an aggressive nation of strange speech” (involved in the business of almost every nation on earth), and divided by the Mississippi River (and to a lesser extent the Missouri and Ohio Rivers). The US also likes to act as the world’s policeman and get involved in every international dispute in the world. If Sudan was in fear of attack by the Houthis in Yemen, it would be expected for the US to be called in and get involved.
At the end of this prophecy:
At that time gifts will be brought to the Lord Almighty\ from a people tall and smooth-skinned,\ from a people feared far and wide,\ an aggressive nation of strange speech,\ whose land is divided by rivers—\ the gifts will be brought to Mount Zion, the place of the Name of the Lord Almighty. (Isaiah 18:7)
This same nation will bring a gift to Mount Zion (Jerusalem/Israel). The US has been regularly giving Israel weapons to defend itself from attacks by the enemies around it. If this nation is the US, then this would make sense, especially with our change in leadership.
When I read Isaiah 19, it made me think of the Muslim Brotherhood takeover of Egypt starting in 2011.
“I will stir up Egyptian against Egyptian—\ brother will fight against brother,\ neighbor against neighbor,\ city against city,\ kingdom against kingdom.\ The Egyptians will lose heart,\ and I will bring their plans to nothing;\ they will consult the idols and the spirits of the dead,\ the mediums and the spiritists.\ I will hand the Egyptians over\ to the power of a cruel master,\ and a fierce king will rule over them,”\ declares the Lord, the Lord Almighty. (Isaiah 19:2-4)
The next part of this passage talks about the Nile drying up and the canals stinking and the fields becoming parched. I did a web search related to drought in Egypt and found an article about drought fears from 2020. The building of the Grand Ethiopia Renaissance Dam on the Blue Nile is causing a fear of major drought in Egypt. There are negotiations between Egypt, Sudan, and Ethiopia to deal with this, but it looks like an ongoing issue for Egypt. An interesting fact is that Ethiopia started building this dam in 2011 -- the same year of the Muslim Brother Hood overthrow of Egypt.
The biggest problem with my theory is Isaiah 20, which talks about Assyria leading Egypt and Cush (Sudan) away as captives. Assyria was located in what is currently Northern Iraq. It is hard to fathom Iraq conquering Egypt and Sudan. The area of Assyria did include a little bit of Turkey, which would be more believable as a conqueror.
Now we get back to the verses in Isaiah 21, which started this musing. First there is a description of terrorists attack:
A prophecy against the Desert by the Sea:
Like whirlwinds sweeping through the southland,\ an invader comes from the desert,\ from a land of terror.\ A dire vision has been shown to me:\ The traitor betrays, the looter takes loot.\ Elam, attack! Media, lay siege!\ I will bring to an end all the groaning she caused. (Isaiah 21:1-2)
Elam is the Eastern edge of Iraq on the Border of Iran and Media is in Iran. Could this be an attack from Iran that includes some of its Shia allies in Iraq? What kind of attack could it be – conventional or nuclear? Who are they attacking?
Look, here comes a man in a chariot\ with a team of horses.\ And he gives back the answer:\ ‘Babylon has fallen, has fallen.\ All the images of its gods\ lie shattered on the ground!’ ”\ My people who are crushed on the threshing floor,\ I tell you what I have heard\ from the Lord Almighty,\ from the God of Israel. (Isaiah 21:9-10)
In ancient times, Babylon was located in the location of modern Iraq, but if we look at the words “Babylon has fallen, has fallen,” and associate them with the almost identical words in Revelation, “Fallen, fallen is Babylon the great,” and we consider how Revelation also refers to “Mystery Babylon” then we are likely talking about an attack on a different nation. (Why would Babylon be a mystery if it was the same people in the same location? It would be a mystery if it was a country and peoples that didn’t exist at the time of the prophecy, but would have the spirit of Babylon in them.) If you take into account my arguments in “Speculation on Babylon the Great” and associate this nation with the people “over the water,” “tall and smooth-skinned,” “feared far and wide,” and “an aggressive nation of strange speech, whose land is divided by rivers.” then this could be an attack on the US (I’ll admit there is a fair amount of speculation here). Although the US has become quite anti-God and has been pushing a lot of evil around the world, it still has one of the largest populations of believers in the world. The statement “My people who are crushed on the threshing floor” also fits for the US.
I know some people won’t consider the possibility that the US could be Mystery Babylon or Babylon the Great because they can’t consider the US being an evil nation, but the US has been pushing many unbiblical ideas on the nations around the globe, like LGBTQ ideology and abortion. It is also possible I am looking too hard for my own country in the scriptures because if the US isn’t mentioned, then something has to happen to the US before the Tribulation occurs to make the US become unimportant in international affairs. We all have our biases.
I’d love to hear your thoughts on my speculations. I’d also like to hear whether people benefit from my speculations or prefer me to stick to the clear and more easily understood Bible passages and Bible truths.
Trust Jesus.\ \ your sister in Christ,
-
 @ 84b0c46a:417782f5
2024-12-26 10:28:26
@ 84b0c46a:417782f5
2024-12-26 10:28:26- lumilumi The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
Follow List ( kind3 ) organization tool.
- NAKE NIP-19, NIP-49 Encode/Decode Tool
- chrome extension
- firefox add-on
- nostviewstr
Addressable or Replaceable Event Editor ( いろんなリストエディター )
Addressable or Replaceable Event Recovery tool ( いろいろリカバリーツール )
Bookmark event ( kind:10003,30001,30003 ) recovery tool ( ぶくま復活させたいやつ )
プロフィールを編集するやつ - nostr-bookmark-viewer
Bookmark event ( kind:10003,30001,30003 ) Editor ( ぶっくまーくをみるやつ )
Broadcast an event from relay to relay ( イベントをブロードキャストするやつ )
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ ea30c5a8:f76a0295
2025-01-30 21:58:25
@ ea30c5a8:f76a0295
2025-01-30 21:58:25whats up yall doing some more testing using nostrmo, amber, citrine, pokey on my shitty android.
-
 @ 2cb8ae56:84d30cba
2024-12-21 11:27:14
@ 2cb8ae56:84d30cba
2024-12-21 11:27:14ども、薄味のキャルピスでございます。
当記事は、「Nostr Advent Calendar 2024」7日目の記事です。
この記事を読んでいる人でいないとは思いますが、Nostrとはなんぞやとお思いの方は以下をご覧ください。https://hello.nostrapp.me/
僕は「Nostrで過ごした2024年」というタイトルの通り、一年間を振り返ってみようと思います。
自己紹介
まず知らん人のために軽く自己紹介をします
「薄味のキャルピス」という名前で、色んな所にいるどこかの高校生です。 左利き、箸とベースとお盆は右手。
普段は学業の傍ら、画像を弄ったり作ったりしている上に、イヤホンを集めたりラジオにメッセージを送っています。
コーディングは出来ないテクノロジーまみれのガラクタ人間(→テックジャンカー)です
参加経緯とスタンス
なぜ参加したのかを思い出しながら書いていきます まず、どんな媒体でNostr(ノスター・ノストラ)の存在を知ったのかと言うと、ネットニュースです。
https://gigazine.net/news/20230425-nostr-intro/
こちらの記事で「そんなのあるんだ」と知り、4月1日ついにjoin!!!!
現時点での参加スタンスは「気楽に、素直に」という感じで参加しています
やりたいときにやりたいことをやるって言うリアルでは到底難しいことを、Nostrのなかでやっている気もします。
後述するNostrasia 2024の開催日「9月23日」を持って、Mastodon(マストドン)から乗り換え、上記のスタンスのもと、メインで精力的に活動しています。
Nostr活動年表
2024/04/01 Nostr Join!!!
2024/06/08 人生初オフ会「たくろうさんオフ」参加、LNアドレス追加。
2024/09/23 人生初小規模イベント「Nostrasia 2024」運営メンバーとして参加
2024/10/12 2度目のオフ会「デザイン談義」主催・参加
簡易的に各種紹介!
人生初オフ会「たくろうさんオフ」 渋三魚金でご飯→猿田彦珈琲でリラックス、Linux使ってると話を切り出す(唐突)→スクランブル交差点で解散。 ウォークマンの再生画面を送付した投稿を行う
人生初イベント「Nostrasia 2024」
あ、記事出したので見てください。初版
第二版
2度目のオフ会「デザイン談義」
秋葉原の「創作空間caféアトリエ あきば店」で行われたオフ会。 ちょくちょく内容を上げているので、見ていってください。 https://nostter.app/npub19ju2u4sduewta4hxl22kke7se8yxm2puytzw47lr6y999pxnpjaqtjjfxj/2024/10/12 終了後、e☆イヤホン 秋葉原店にて、BTR13の在庫状況を確認し、在庫がないため予約しました。 (10月24日到着) 雑多すぎますが、一応こんな感じで大丈夫かな?まとめ
僕がNostrに出会い、Nostrにのめり込むまでの話はいかがだったでしょうか。 Nostrに入る前、オフ会に参加するまでは「ネットにロクな人なんていない!」と思っていましたが、Nostrは違いましたね。 いい意味で期待はずれ、本当にいい人たちばかりで、とにかく自然体で接することができるSNSであると感じました。 そんな世界にぜひとも一回足を踏み入れてみてはいかがでしょうか? それではまた、来年のアドベントカレンダー、及び開催されましたら「Nostrasia 2025」でお会いしましょう。 -
 @ ec42c765:328c0600
2024-12-15 11:13:44
@ ec42c765:328c0600
2024-12-15 11:13:44てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
-
 @ ec42c765:328c0600
2024-12-13 08:16:32
@ ec42c765:328c0600
2024-12-13 08:16:32Nostr Advent Calendar 2024 の 12日目の記事です。
昨日の 12/11 は きりの さんの 2024年のNostrリレー運営を振り返る でした。
nostr-zap-view 作った
リポジトリ: https://github.com/Lokuyow/nostr-zap-view/
動作確認ページ: https://lokuyow.github.io/nostr-zap-view/それ何?
特定の誰かや何かに宛てたZap(投げ銭)を一覧できるやつ
を
自分のWebサイトに設置できるやつ
自分のサイトに設置した例 * SNSリンク集ページ(最下部): https://lokuyow.github.io/
おいくらサッツ(Zap一覧ボタン): https://osats.money/
今日からビットコ(最下部): https://lokuyow.github.io/btc-dca-simulator/なんで作ったの?
私の去年のアドベントカレンダー
【Nostr】Webサイトにビットコインの投げ銭ボタンを設置しよう【Zap】
https://spotlight.soy/detail?article_id=ucd7cbrql/
が前提になってるけど長いので要約すると * ZapするやつはあるけどZap見るやつがないので欲しい * ZapをNostr(の典型的なkind:1クライアント)内だけに留めるのはもったいない * Webサイトの広告うざいからZap(的な何か)で置き換わって欲しいお前だれ?
非エンジニア、非プログラマー
AIにコード出させてるだけ人作った感想
できた
作った感想2
完成してから気付いた本当に作りたかったもの
こういうところにそのままZapを表示できる感じにしたい
 (ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
(ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
もうZapっていう文字もビットコインっていう文字もNostrも出さなくていいし説明もしなくていいのでは感がある
イメージはWebサイトを対象にしたニコニ広告 + スーパーチャット + 祭りとか神社の奉納者一覧
で思ったのは
個人からの投げ銭なら推し活的なものにしかならないけど
企業がNostrにアカウントを作ってサイトに投げ銭をしたら企業の広告になるんでは!?
~~企業がNostrにアカウントを!?デリヘルしか見たことない!~~今後
思いつき、予定は未定
* ボタン→ダイアログ形式でなくバナー、Embed形式にしてページアクセスですぐ見れるようにする * 多分リレーに負荷がかかるのでなんかする * Zapの文字は出さず「Sponsored by」等にする * 単純な最新順でなくする * 少額Zapをトリミング * 一定期間(一か月など)ごとで金額順にソート * 多分リレーに負荷がかかるのでなんかする * 今は投稿宛てのZapをWebサイト宛てのZapと勝手に言い張ってるだけなのでちゃんとWebサイト宛てのZapにする * NIPの提案が必要 * ウォレットの準拠も必要 * リレー(wss://~)宛てのZapもできてほしい将来
インターネットのすべてに投げ銭をさせろ
おわり
明日は mono さんの Open Sats 申請編 です!!
-
 @ cc8d072e:a6a026cb
2025-01-30 17:20:24
@ cc8d072e:a6a026cb
2025-01-30 17:20:24Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later.
1. Shifting from Deterministic to Probabilistic Thinking
- Traditional software engineering deals with deterministic outcomes
- AI systems operate on probability rather than certainty
- Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes
- Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems
2. Understanding Core AI Concepts
(There are a lot of concepts to understand, but i will focus on the most frequently asked ones)
Memory Management
- Short-term Memory: Implemented through conversation context
- Long-term Memory: Implemented through vector databases (RAG - Retrieval Augmented Generation)
- Context length management is crucial due to LLM token limitations
Language Models and Fine-tuning
- Base models (like GPT) provide general intelligence
- Domain-specific knowledge can be added through:
- Fine-tuning with custom datasets
- Adding RAG layers for specific knowledge domains
3. Technical Framework Knowledge
Essential Tools and Frameworks
- Vercel AI SDK (if you are a typescript guy)
- LangChain (alternative option)
- Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm )
- Understanding of prompt engineering
Multi-Agent Systems
- Agents can communicate through natural language
- Inter-agent communication requires careful system design
- Implementation of thought processes and decision-making loops
- Safety considerations for system commands and operations
4. Language and Localization Considerations
- System prompts typically work best in English
- Multi-language support requires careful handling:
- Input translation to English
- Processing in English
- Output translation to target language
- Model performance varies across different languages
5. Safety and Error Handling
- Implementing validation layers for critical operations
- Understanding model limitations and potential errors
- Building feedback mechanisms to detect misunderstandings
Conclusion
Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications.
Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :))
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ f0c7506b:9ead75b8
2024-12-08 10:03:35
@ f0c7506b:9ead75b8
2024-12-08 10:03:35
-
Bazı şeyleri yapmak, söylemekten daha kolaydır.
-
Bütün güzel şeyleri bize toprak verir. Bütün güzel şeyler toprağa geri döner.
-
Eğer mevsimlere bakarsanız her mevsim meyve getirir. Yazın meyve vardır, sonbaharda da. Kış farklı meyveler getirir, ilkbahar da. Hiçbir anne çocukları için bu kadar çok çeşit meyveyle buzdolabını dolduramaz.
-
Kendimi bu hayattan kurtarmaya karar verdim. Ne için mi? Bu anlamanıza yardım etmeyecektir ve bunun hakkında sizinle konuşamam; anlayamazsınız. Anlamayacağınız için değil; çünkü benim hissettiklerimi hissedemezsiniz. Duygularımı anlayıp paylaşabilirsiniz, bana merhamet gösterebilirsiniz; ama acımı hissedebilir misiniz? Hayır. Acı çekersiniz ve ben de çekerim. Sizi anlarım. Acımı anlayabilirsiniz; ama onu hissedemezsiniz.
-
İnsanın devam edemeyeceği bir an gelir.
-
Birisine yardım etmek istediğiniz zaman bunu uygun biçimde yapmalısınız, bütün kalbinizle. Bu daha iyidir. Daha adil ve daha makul.
-
İntiharın en büyük günahlardan birisi olduğunu biliyorum. Fakat mutsuz olmak da büyük bir günah. Mutsuzken başka insanları incitirsiniz. Bu da bir günah değil mi? Başkalarını incittiğinizde bu bir günah değil midir? Aileni incitiyorsun, arkadaşlarını, kendini incitiyorsun. Bu bir günah değil mi? Size yakın olan insanları incitiyorsanız bu da büyük bir günahtır.
-
Yardım, mutlaka karşılığı ödenmesi gereken bir şey değildir.
-
Size başımdan geçen bir olayı anlatacağım: henüz yeni evlenmiştim. Belaların her türlüsü bizi buldu. Öylesine bıkkındım ki her şeye son vermeye karar verdim. Bir sabah şafak sökmeden önce arabama bir ip koydum. Kendimi öldürmeyi kafama koydum. Yola koyuldum. Dut ağaçlarıyla dolu bir bahçeye vardım. Orada durdum. Hava henüz karanlıktı. İpi bir ağacın dalı üzerine attım; ama tutturamadım. Bir iki kere denedim ama kâr etmedi. Ardından ağaca tırmandım ve ipi sımsıkı düğümledim. Sonra elimin altında yumuşak bir şey hissettim: Dutlar. Lezzetli, tatlı dutlar. Birini yedim. taze ve suluydu. Ardından bir ikincisini ve üçüncüsünü. Birdenbire güneşin dağların zirvesinden doğduğunun farkına vardım. O ne güneşti, ne manzaraydı, ne yeşillikti ama! Birdenbire okula giden çocukların seslerini duydum. Bana bakmak için durdular. "Ağacı sallar mısın?" diye bana sordular. Dutlar düştü ve yediler. Kendimi mutlu hissettim. Ardından alıp eve götürmek için biraz dut topladım. Bizim hanım hâlâ uyuyordu. Uyandığı zaman dutları güzelce yedi. Ve hoşuna gitti. Kendimi öldürmek için ayrılmıştım ve dutlarla geri döndüm. Bir dut hayatımı kurtarmıştı.
-
Bir türk, doktoru görmeye gider. Ve ona der ki: "Doktor bey, vücuduma parmağımla dokunduğumda acıyor, başıma dokunsam acıyor, bacaklarıma dokunsam acıyor, karnıma, elime dokunsam acıyor." doktor onu muayene eder ve sonra ona der ki: "vücudun sağlam; ama parmağın kırık!"
-
Hayat dümdüz ilerleyen bir tren gibidir; rayların sonuna geldiğinde son durağa ulaşır. Ve ölüm son durakta bekler. Elbette, ölüm bir çözümdür; fakat ilk olarak değil. Genç yaşta hiç değil.
-
Dünya göründüğü gibi değildir. Bakış açınızı değiştirmelisiniz ki dünya değişsin. İyimser olun. Her şeye olumlu tarafından bakın.
-
-
 @ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03
@ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03For me, it’s simple yet profound: a job and labor aren’t the same thing. You don’t have to struggle to perform a task or to meet someone else's unrealistic expectations. In fact, if you genuinely enjoy what you’re doing and believe in its purpose, the results will naturally be better—and everyone benefits.
I’m speaking from the perspective of someone who walked away from a "well-established career" multiple times. These days, I might be working more than ever, but I don’t feel tired, frustrated, or burned out. The radical change I made—leaving the "professional fiat world" behind—wasn’t easy, but I’ve never regretted it. Now, working fully in Bitcoin, I feel more motivated and satisfied than ever before.
Sure, it's not always straightforward.
This lifestyle definitely comes with its challenges. But those challenges don’t crush me. Just the opposite. When combined with a sense of freedom, they become opportunities for growth—something I truly value. It’s a completely different experience compared to most jobs rooted in the old system.
I’m not saying working in Bitcoin is all sunshine and rainbows, nor am I criticizing anyone still working in fiat. What I’m trying to emphasize is the core message of that quote:
Do what you love, and you’ll never work a day in your life...
Read it aloud and think about your last couple of jobs.
How did you feel? Did you find fulfillment and satisfaction, or was it more like a form of slavery that made you dread going to bed and waking up every morning?
I didn’t really have those feelings, except for one corporation at the beginning of my career, which gave me a hard time but also taught me valuable lessons. Aside from that experience, most of my jobs weren’t too bad—no need to complain. Still, I often questioned my situation: 'Seriously, why do I have to do this or that if I know it doesn’t make sense?'
Doing things you don’t believe in can lead to frustration, often in ways you might not even realize, yet every time, significantly affecting your well-being and the people around you.
Now, I hardly know what inner anger means.
I wake up happy, full of passion and ideas. I don’t track the hours as they pass; instead, I focus on all the tasks I complete and how they make a difference for me and others. Yes, I love what I do. And returning to the main point of this article, I shouldn’t even see it as work, even though in practice it definitely is.
The key here is a mix of independence, purpose, and self-determination. Bitcoin has helped me achieve that to a level that’s hard to break.
A Fresh Take on The Market
I also remember that 5-7 years ago, especially for non-devs, Bitcoin-based jobs weren’t as accessible as they are now (which is probably why I stayed in my traditional career for so long...). It’s really only in the last, maybe 2-3 years that things have changed. With so many areas expanding beyond just mining and tech-related stuff, and new interesting projects popping up regularly, there’s almost any position you can imagine to jump into.
According to a recent report by Bitvocation '69% of Bitcoin jobs are non-developer roles'. Also, more than half of available positions in 2024 offered remote opportunities, giving job seekers extra flexibility. Bitcoin is borderless—and so are many of the jobs in this space. If you’ve ever thought working in Bitcoin was out of reach, think again—and check this out "BITCOIN JOB MARKET DATA, 2024 Report".
One tip from my experience: a good option is to start with a part-time role while keeping your traditional fiat job for more stability, especially at the beginning. After a while, you’ll gain more confidence and see which direction you want to go. Or, if you position yourself so that you don’t need to earn a lot for the next 3-6 months, consider finding a project- or task-based Bitcoin job, maybe even just an internship. Meanwhile, you might decide to focus on building something unique on your own. It can feel amazing! You’ll gain valuable skills, sharpen your experience, and better understand which options work best for your future.
You see, just like in nature, balance is key. You don’t have to run before you can walk.
What I’m saying is this:
The choice is yours, as long as you plan ahead + learn, while staying true to your needs, beliefs, and priorities.
If you want it, do it. Starting a career in Bitcoin is possible, and I have a feeling this space will grow even faster in the next few years. Yes, there will still be ups and downs (hello, bear markets!), but if you plan thoughtfully, there’s not much to worry about.
We’re still early—Bitcoin is only 16 years old—but if you’ve been following this space, you’ve probably seen how dynamic and resilient it is. If you’ve ever thought about working in Bitcoin, now is the time to rethink the possibilities :)))
BTC Your Mind. Let it Beat.
Şelale
-
 @ 7cb5fba1:4ea55c0e
2025-01-30 05:36:08
@ 7cb5fba1:4ea55c0e
2025-01-30 05:36:08

Samira parties with customers at a brothel. She was married at 12, trafficked to a brothel two weeks later.

A madam counts money in a brothel


Mia, 15, sits with her new 27-year-old groom during their wedding. ‘My family has been saving for my wedding for a very long time. I am a girl, so they always knew they would need to give me away.' Five or six months ago, her parents found Mia a groom, a 27-year-old man who works in a garment factory. 'I am nervous,' Mia says, quietly. 'I think I will miss my family'

Yasmin waits for customers

A girl shows her self harm scars

Women wait for customers

Habiba waits for customers. The 14-year-old has been in a brothel for three years

‘I ran away from my husband after seven days. He was only about 15 or 16, but he raped me so violently that one morning, when I knew he was asleep, I slipped out of the house as quietly as I could, and ran,’ Samira says. ‘I ran back to my house, but I was too frightened to go inside because I was covered in blood and bruises. My mum died when I was 11, so my brother and sister had arranged the marriage because they could not afford to look after me any more, and I knew leaving my husband would make them angry. So I asked a rickshaw driver to take me across (the town) to my friend’s house, but he told me I should be ashamed of myself, and dropped me off at the brothel instead’

A customer enters Yasmin’s room

A police officer stops to speak to a woman outside a brothel

A customer fights with girls at a brothel
-
 @ 4c5d5379:3a4383ee
2024-12-01 03:21:49
@ 4c5d5379:3a4383ee
2024-12-01 03:21:49first header
I'm testing YakiHonne article.

にほんごだよ
header
header
header
header
header
header
ヘッダ
ヘッダ
ヘッダ
ヘッダ
ヘッダ
ヘッダ
-
 @ 6b0a60cf:b952e7d4
2024-11-17 07:02:11
@ 6b0a60cf:b952e7d4
2024-11-17 07:02:11ビットコインのウォレットは取引形態によって2種類に分かれます。
- オンチェーン(L1)
- 取引がブロックチェーンに刻まれるタイプ。時間がかかるし手数料が高い。
- ライトニングネットワーク(L2)
- ブロックチェーンに刻む前の少額決済を目的としたレイヤー。高速で手数料が安い。
NostrでZapを利用する場合はライトニングネットワーク(以下、LNと呼びます)のウォレットが使われますが、さらにその中でもZap対応/非対応で分かれることになります。
また、秘密鍵を誰が管理するかによっても2種類の呼び方に分かれます。
- カストディアル
- 秘密鍵をサービスの運営に預けるタイプ。
- ノンカストディアル/セルフカストディアル
- 秘密鍵(シードフレーズ)を自分で持っておくタイプ。
Nostrで人気があるWallet of Satoshi(以下、WoSと呼びます)はLNのカストディアルウォレットです。 今回はLNのセルフカストディアルウォレットであるPhoenixを使ってみて、その仕組みや注意点など、学んだことを記録したいと思います。
Phoenixでウォレットを作る場合、初回でシードフレーズ(12個の単語)が作られますので、大切に控えておきましょう。
WoSからPhoenixに送金してみる
メイン画面左下にあるReciaveからQRCode表示画面へ遷移します。そこでcopyボタンを押して
Lightning invoice(text)をコピーしましょう。
次に、WoSの画面からSendを選択し、クリップボードからの貼り付けを選択します。

 金額を指定して送金します。
金額を指定して送金します。
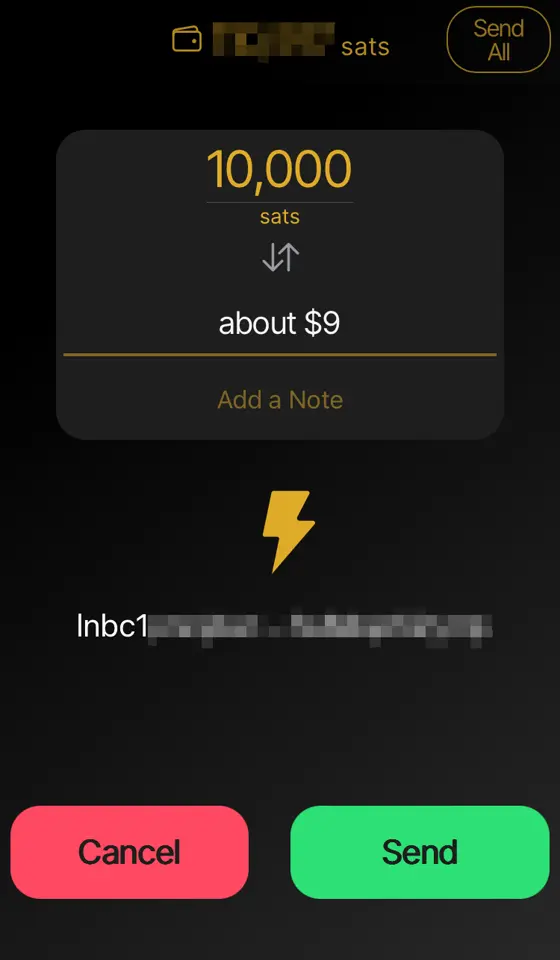
送金した額が満額届いてないんだけど?
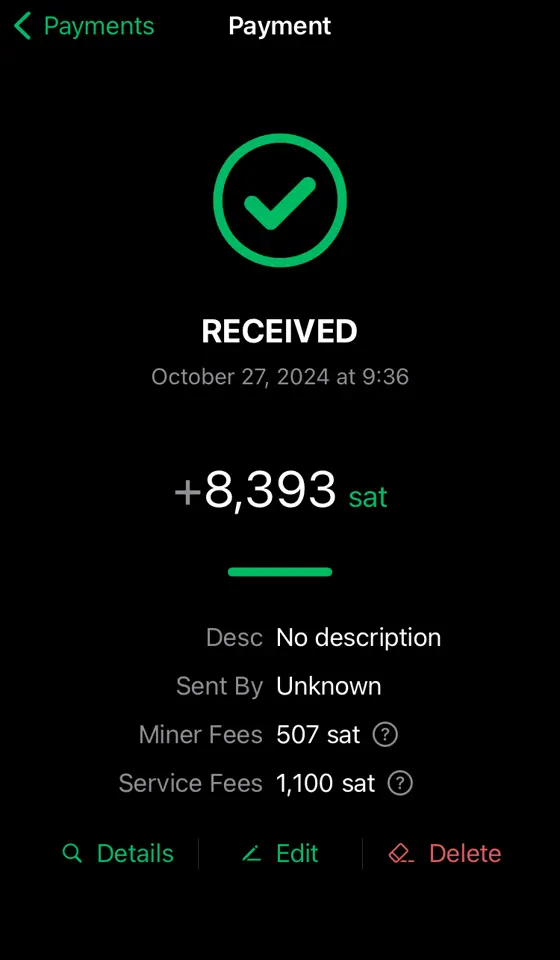
下の方に
Service Feesとありますが、これはPhoenix運営(ACINQ)へのお布施ですね。結構高く見えますが初回だけです。 またMiner Feesという項目は、mempoolのfeeに連動して変わるようですが、これはチャネルを太くする(送受信できる金額の上限を上げる)ために使われる手数料になります。財布が重たくなると手数料が取られる?
有り体に言えばそういうことになります。以下のように10,000satsをもらう度にチャネル拡張のための手数料が引かれています。
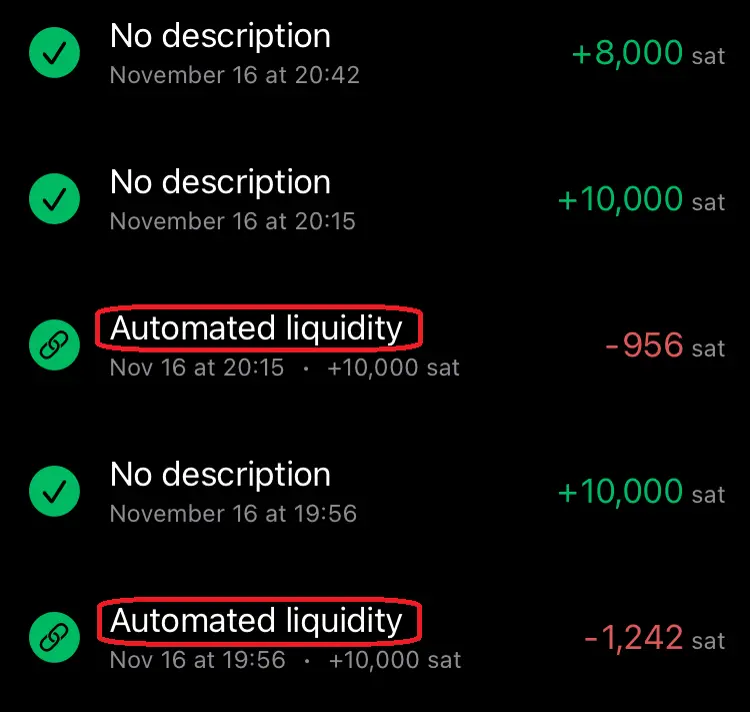
上記の8,000satsを受け取っている時には手数料が発生していませんね。これはチャネル拡張が必要ないギリギリの金額を狙って送金したためです。送金前は8,859satsの余裕がありました。送金後は1,719satsに減っています。(余裕分がぴったり8,000sats減るわけではないようです。このへんの仕組みはよくわかりません。) (画面は左上⚙️マークの設定からPayment channelsから。)
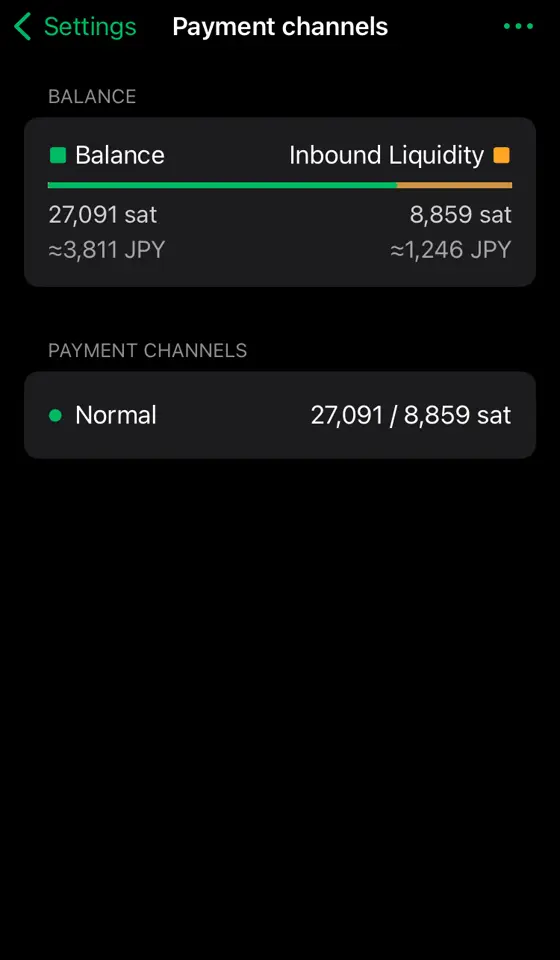
財布が軽くなると余裕が増える?
逆にPhoenixからWoSに5,000satsほど送金してみます。(手数料として24satsほど余計に抜かれました)
余裕(Inbound Liquidity)が5,883satsまで復活しています。受け取るばかりでなく、バランスよく送ることで財布を重たくしなければチャネル拡張せずに使い続けることができそうです。(太くしたチャネルは永遠に残るわけではなく、1年までらしいです)
自動でチャネル拡張にsatsを使われたくない!
自動チャネル拡張を設定で無効化できます。左上⚙️マークの設定から
Channel managementから。
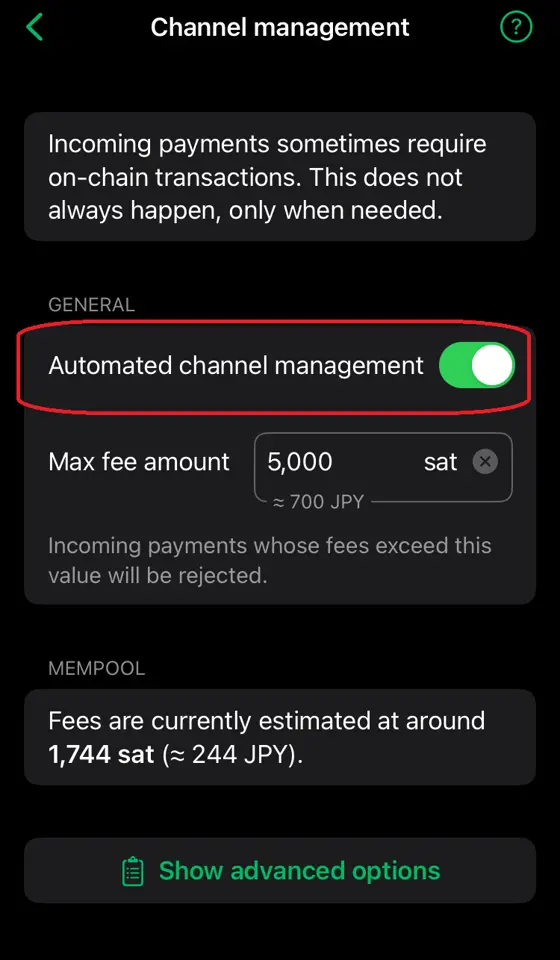
これでチャネル拡張が必要なほどの金額を送金しようとするとエラーになり失敗します。
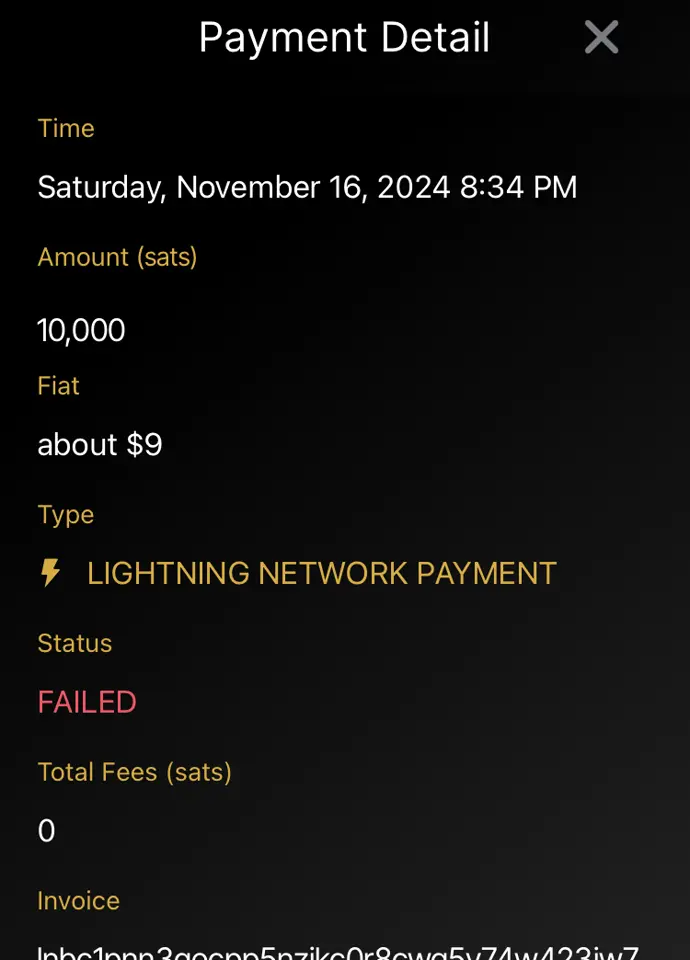
まとめ
セルフカストディアルウォレットならではの概念があり、謎の手数料が発生したりして怖いイメージがありましたが、どういう理由で手数料が発生するのかを知り、設定でのコントロールの仕方を習得することである程度怖いイメージを払拭することができました。 しかしカストディアルウォレット(特にWoS)の使いやすさを再認識することにもなりました。ただ自分で管理することの重要性も理解していますので、徐々に知識を深めていこうと思います。
参考/謝辞
- Phoenix wallet(フェニックスウォレット)の使い方!ビットコインのセルフカストディができるアプリを解説 - 知っとこ!ビットコイン図鑑
- nostr:npub10zeurmg22wc89l8m3npw9cyu45cun0lvs6w3ep69cdpa25pna65s0994qz 様
-
 @ 04c195f1:3329a1da
2025-01-29 08:16:38
@ 04c195f1:3329a1da
2025-01-29 08:16:38Over the past week, Sweden has been rocked by an unprecedented wave of domestic terrorism. Bombings, shootings, and gang-related violence have escalated to a level that even the most hardened observers find shocking. The Swedish people are waking up—sometimes quite literally—to explosions outside their homes, their neighborhoods resembling conflict zones rather than the peaceful Scandinavian society they once knew.
A Month of Terror
Since the beginning of the year, Sweden has witnessed at least 32 bombings, averaging more than one explosion per day. In a sign of how routine this has become, state media outlet SVT now maintains a "live ticker" tracking the growing number of explosions—reminiscent of the death and infection tickers used during the COVID-19 pandemic. The attacks have struck cities large and small—Stockholm, Uppsala, Helsingborg, and Örebro among them. Some explosions have targeted residential buildings, even bedrooms where children sleep. Others have been part of gang warfare, retaliation for unpaid debts, or attempts to intimidate rivals.
Just in the past 24 hours, five separate explosions have rocked Stockholm. A grenade attack forced a school into lockdown, while an explosion in Årstaberg destroyed the entrance of an apartment building. This is not the first time—and it certainly will not be the last.
Sweden’s Political Paralysis
Despite this unprecedented security crisis, the Swedish government refuses to take meaningful action. Prime Minister Ulf Kristersson recently acknowledged the situation, stating:
“The criminal gangs show total disregard for the public. This is domestic terrorism that we must fight with the full force of society. The police are working intensively to prevent and stop acts of violence. The police can now conduct preventive wiretapping, and security zones are in place. These are important tools. But more is needed.”
However, this is yet another attempt to address symptoms rather than causes—and it will fail to even achieve that. Last night, I participated in a livestream where former MP Jeff Ahl likened the government's approach to trying to stop arterial bleeding with a band-aid. A fitting description indeed.
Meanwhile, rather than declaring a national emergency, Sweden’s political elite have prioritized ideological pet projects. Minister Paulina Brandberg was busy opening a new DEI (Diversity, Equity, Inclusion) office at Chalmers University while bombs tore through Stockholm’s suburbs. Justice Minister Gunnar Strömmer held a crisis meeting with the police last week, only to suggest that the government might be able to stop the gangs in eight years—an admission of failure if ever there was one.
The Root of the Crisis
The media and political establishment refuse to address the root cause of this descent into chaos: mass immigration and the importation of criminal clan networks. The reality is undeniable:
-
Areas like Rinkeby and Botkyrka—once Swedish working-class neighborhoods—now have overwhelming non-Swedish majorities, with Rinkeby exceeding 95% and Botkyrka over 60%. These are just two examples of the hundreds of neighborhoods across Sweden where Swedes are now a minority, where criminal clans thrive, and where gangs have effectively taken control—not just of the streets but also of local commerce and entire business districts.
-
Organized crime syndicates, many with roots in the Middle East and North Africa, exert dominance over these areas, operating parallel societies with little to no interference from Swedish authorities.
-
Police estimate that 30,000 individuals are active in criminal gangs—when factoring in extended networks, the number may be in the hundreds of thousands.
-
Most of these people should never have been allowed into Sweden in the first place.
“We’re Used to It”
Perhaps the most chilling aspect of this crisis is the growing resignation among Swedes. After a bombing in Upplands-Bro last night, one resident summed it up:
“No, I’m not worried. I’m used to it.”
This normalization of terrorism is a direct consequence of decades of political negligence, ideological blindness, and a refusal to admit policy failure. Sweden’s leaders have deliberately ignored the warnings. They have allowed the chaos to fester. And now, they pretend to be shocked as the country spirals deeper into lawlessness.
What Comes Next?
Let’s be clear: these bombings will not stop. If history is any guide, Sweden’s authorities will issue statements, hold meetings, and maybe even arrest a few foot soldiers. But the broader networks, the root causes, and the state’s unwillingness to reclaim control over the country remain unchanged.
The question is not whether Sweden can recover. The question is whether Swedes are willing to demand real change. And if they do not, how much further can this country fall before it collapses altogether?
I will continue to report on this crisis—because while mainstream media acknowledges the violence, they refuse to confront its root cause. If we do not acknowledge the failure of multiculturalism and dismantle this ideological experiment, we will never resolve this crisis.
For near-daily updates, follow me on X, Telegram, and Nostr, where I report on these events as they unfold. Stay informed, stay vigilant, and if you value my work, consider subscribing and sharing this newsletter.
■
-
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 20e7c953:3b8bcb21
2025-01-29 05:53:46
@ 20e7c953:3b8bcb21
2025-01-29 05:53:46Thai Nostriches #Siamstr
Get Ready for Sats N Facts 2025! https://satsnfacts.btc.pub/ 🎉
Join us for a series of exciting events where Bitcoin, Nostr, and local Thai communities come together to innovate, create, and connect! Here’s the breakdown for the 2 main activities:
🛠 Hackathon Overview
https://satsnfacts.btc.pub/hackathon/
This is your opportunity to work alongside leading teams and individuals pushing the boundaries of Bitcoin and Nostr. Whether you're a developer, designer, an educator or a visionary, your contributions can help shape the future of decentralized technology.

What to Expect:
Participate in the sessions by pitching and listening to others ideas or setting up a spot in the schedule. The event is designed to be a “decentralized and collaborative” effort between all participants, with activities being put together with attendees’ feedback.
🤝 Introducing Potential 🇹🇭 Participating Teams
nostr:npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 – Bitcoin Education and Translations for the Thai community; this would be an ideal occasion in order to connect with international developers in order to curate and share insights within the #Siamstr community
Other Projects that are formally invited are:
nostr:npub1l8ktdyyhwxh4ty5cf48tl72g8ra286nr9klmvqznvk3aqyjkucgsem97q9 – Simplifying Bitcoin payments through intuitive tools
nostr:npub1nsxnfp5690uplzgkslthcvt6269htshqeymhghthenr9wnpt869q57q2hf – Innovating Lightning infrastructure and Bitcoin ATMs
nostr:npub16elg3wf8nffkymylw9kfwecc45j9c30lufrrzx2zf5vmxjlcgkkq3xc6d7 – Enhancing social innovation through Nostr-powered solutions
🎨 Art Exhibition

What else to expect?
A showcase of Bitcoin and Nostr-inspired works by local Thai artists like nostr:npub16unl8g9ucanlpfvp94sdjdv2f4mukm2ywmgrywnrfdgt98qwrrdq0qcn35 nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu and nostr:npub1uprlst7kjp0eyfxe4yn7q36gr885mjr9fm6ejfqt8pmdta7stv9s2xvysq - Huaiphueng Project community members.
Celebrate the creativity of our culture with a fusion of tech and art!
📍 Location: Weave Artisan Society, Chiang Mai
📅 Date: 8th - 10th February
🎟 How to Join: Register either as a Lead or Attendee, wait for confirmation from SnF team and get your ticket as a Thai National via Formstr at https://satsnfacts.btc.pub/#tickets
🌟 Why You Should Join:
If you are a Bitcoiner and Ostrich in Thailand the question should be re-formulated to... WHY WOULD YOU NOT JOIN ?
Support and grow the local ecosystem while having a great time with fellow international Bitcoiners.
✨ Mark your calendars and spread the word! Stay tuned through the links or connect with us on Nostr.
Let’s build a stronger Bitcoin & Nostr future at Sats & Facts ✌️
Pictures by nostr:npub15l5mxmljftnnqur8gf2nkjj2yuemqy2kuly7yc29lx7x598svx5s447rgk 👇


เราจะทำอะไรต่อไป ?
AND WE SAID;
ONWARDS
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ f240c9c2:6c0c0a86
2024-08-22 06:50:33
@ f240c9c2:6c0c0a86
2024-08-22 06:50:33⚠️一部のクライアントでは表示が崩れている場合があります。HablaやYakihonneから見てください
NIP-51のkind:30007に関するPull Requestが承認され、2024/08/20時点で本家NIPsにもマージされました。今後「リポスト」や「リアクション」などの特定のkind^1をミュートするためのセット^2が対応するクライアントで使えるようになります。
kind mute set(kind:30007)にて、
"d"タグには対応するイベントの種類の番号(リポストなら"6"、リアクションなら"7")を入れ、"p"タグにはユーザの公開鍵(pubkey)を入れるそうです。nostrクライアントのnostterは、これに対応したことで、Twitter(現:X)の「リポストをオフのする」機能のように"特定ユーザーのリポストをクライアント上で非表示にする"といったことができるようになりました。リアクションも同様に非表示にできます。 nostterでは、2024/07/29以降、ユーザーのプロフィール画面からこれらの設定を行えるようになっています。
2024/06/22 20時の時点では、nostter上ではこれを設定する画面が用意されていなかったので、別アプリを用いたり、イベントを自分で投げるなどして別途設定する必要がありました。 以下は、別アプリを用いて設定した際の手順です。
手順
kind:30007はのすとびうあというWebアプリで設定しました。 以下のようにのすとびうあのホーム画面「リストの種類」で30007を入力するか、

https://nostviewstr.vercel.app/<npub文字列>/30007にアクセスして設定画面にいけました^3。左下の方にある≡を押して

ポップアップの「編集」を押して

ここではリポストのミュートのため、IDの欄に対応するイベントの種類の番号である「6」を入れて

右下にある青いボタン押して

Userの欄にリポストをミュートするユーザーの公開鍵のnpub文字列を入れ、public(ミュート状況が公開される)あるいはprivate(非公開)のボタンを押したら

そのユーザーが追加されて設定完了!

この設定を行うことで、入力した公開鍵(ユーザー)のリポストをnostter上でもミュートできました🙌
リポストやリアクションがどのように表示されるかをユーザーがコントロールできると便利なので、今後いろんなクライアントで対応されればいいな〜と思います!
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 4c96d763:80c3ee30
2024-08-19 16:26:43
@ 4c96d763:80c3ee30
2024-08-19 16:26:43Changes
Rusty Russell (3):
- Makefile: fix missing dependencies on bolt11 headers.
- bolt11: update to latest version from CLN
- bolt11: remove unneeded fields.
William Casarin (1):
- ndb_filter_from_json
pushed to nostrdb:refs/heads/master
-
 @ 27676f17:0726572a
2024-06-21 23:13:04
@ 27676f17:0726572a
2024-06-21 23:13:04foobar
-
 @ 86cf3742:678e3ae8
2025-01-28 15:06:54
@ 86cf3742:678e3ae8
2025-01-28 15:06:54In this episode, we dive deep into the world of dairy farming with JR Burdick, a former conventional dairy farmer turned raw milk producer. JR shares his journey from following the traditional dairy farming system to becoming an independent raw milk seller, breaking away from industry norms and regulations. He recounts the challenges he faced, including dealing with stray voltage that decimated his herd, a lengthy legal battle with an electric company, and the emotional and financial toll it took on his family.
JR also discusses the impact of industry regulations, such as the mandatory check-off programs and the pressures from dairy cooperatives, which led him to question the sustainability and ethics of the conventional dairy system. His story is one of resilience and transformation as he navigates the complexities of direct-to-consumer sales, the challenges of marketing raw milk, and the importance of maintaining integrity in his farming practices.
Throughout the conversation, JR offers insights into the broader agricultural landscape, touching on issues like government subsidies, the consolidation of the dairy industry, and the role of technology and innovation in farming. He also shares his thoughts on the future of agriculture, the potential of Bitcoin as a financial tool for farmers, and the importance of preserving traditional farming knowledge.
This episode is a compelling exploration of the struggles and triumphs of a farmer who dared to defy the status quo and forge a new path in the world of agriculture.
-
 @ 3f770d65:7a745b24
2024-06-17 18:56:54
@ 3f770d65:7a745b24
2024-06-17 18:56:54Several months ago, nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s and I set out to do tackle a task that had never been done before throughout Nostr's short history. We decided adopt the "go big, or go home" mentality and give our best effort to Purple Pill all of the nostr:npub167n5w6cj2wseqtmk26zllc7n28uv9c4vw28k2kht206vnghe5a7stgzu3r conference.
We couldn't accomplish this monumental task without the help of the Nostr community. From every day Nostriches and plebs, to legendary developers putting their blood, sweat, and tears into building this new protocol, to several companies within the Nostr ecosystem, everyone was going to need to do their part to turn this dream into a reality.
The mission
For the original vision of Nostr at BTC Prague, we planned on supporting the smallest available booth and a small panel on the secondary stage. The plan was for any Nostr developer to contribute what they could and then use the Nostr booth as a central hub to onboard users to their applications, provide support to their users, and meet the community. I embarked on my first crowdfunding journey and was able to initially raise over 10M sats thanks to the greater Nostr community donating towards our efforts.
Shortly afterwards, I was approached by nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m from Satlantis. He had planned on doing a mainstage presentation at BTC Prague on his new Nostr powered application. He asked me if I wanted to combine our efforts to upgrade the Nostr booth to the largest booth possible to give Nostr an even larger presence. I reached out to Avi and several other trusted Nostriches to see their opinions on this potential upgrade and everyone seemed to agree that we should continue with the "go big, or go home" mentality and try our best to Purple Pill all of Prague.
Now with a larger goal at hand, we were able to garner even more support from the Nostr community in addition by adding Highlighter from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and Primal from nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr as larger contributors.
The final tallies for funds raised were 16M+ sats from the greater Nostr community and 38M+ sats raised from Satlantis, Primal, and Highlighter. (We did have to raise a little more than originally anticipated because the Bitcoin 58K Gang made the fiat value of Bitcoin dip down for a bit right when we were trying to finalize payment.)
Putting it all together
This support enabled us to secure one of the four large booths at BTC Prague and a main stage panel. Given that these three companies made significant contributions, enabling our acquisition of the largest booth, we decided that it was logical to feature these companies more prominently. However, it was crucial to strike a delicate balance here. While emphasizing that this booth represented the Nostr community and was a true community effort, we also wanted to acknowledge and showcase those who made it possible. These companies could have opted for smaller individual booths, but their collaboration in a unified space demonstrates Nostr's principles of openness and interoperability—demonstrating that everyone and everything can work together seamlessly.
Therefore, we included as many logos across the Nostr ecosystem as possible throughout our iconography.

And, we also had a dedicated area of the booth highlighting our larger contributors.

The results exceeded all expectations. For three days during the BTC Prague conference, the Nostr booth was continuously bustling with activity. Attendees ranged from individuals who had never heard of Nostr before to those who were curious, active users within the ecosystem, and developers creating the applications we use daily. It was a remarkable community effort, with unexpected volunteers stepping up to onboard new users and provide support. Recognizing our busy schedules and flocks of new Nostriches hatching, they chose to assist in our efforts, offering help, and answering questions. It was a truly inspiring experience. Despite the busyness, the enthusiasm and support of so many people made each day enjoyable and dynamic, ensuring there was never a dull moment and we were always surrounded by friends.
Booth takeaways
As this was our very first attempt at doing something like this, I'd like to do a personal post mortem and highlight many of our successes and even some areas where I feel we can improve upon in the future.
Several Nostriches went above and beyond, helping onboard people and answer questions for three days straight. nostr:npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 nostr:npub1spdnfacgsd7lk0nlqkq443tkq4jx9z6c6ksvaquuewmw7d3qltpslcq6j7 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1k6tqlj78cpznd0yc74wy3k0elmj4nql87a3uzfz98tmj3tuzxywsf0dhk6 nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1zga04e73s7ard4kaektaha9vckdwll3y8auztyhl3uj764ua7vrqc7ppvc were the lifeblood of the booth, always answering questions themselves or referring them to others if they were unable to help, didn't know the answer or were busy at the time. You all put in the work and deserve much credit and thanks. Even nostr:npub1995y964wmxl94crx3ksfley24szjr390skdd237ex9z7ttp5c9lqld8vtf was helping with onboarding!

Additionally, beyond general use case questions, we also had many developers stop by and answer many more technical questions for those wanting to learn a bit more too. nostr:npub1zach44xjpc4yyhx6pgse2cj2pf98838kja03dv2e8ly8lfr094vqvm5dy5 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft were often seen answering more technical questions on various developmental topics.


Identifying areas for improvement is challenging, as the entire team of Nostriches performed exceptionally well, exceeding expectations. The event was a whirlwind of activity, with constant engagement and zero downtime. Volunteers seamlessly rotated at the front counter answering questions and distributing items to attendees. (Thanks nostr:npub1cgcwm56v5hyrrzl5ty4vq4kdud63n5u4czgycdl2r3jshzk55ufqe52ndy . Your nostr.how and nostrapps.com business cards were a HUGE help here!)
Full disclosure, I personally didn't leave the booth for three days all that much for two reasons. 1) Because I love to #GrowNostr and talk to people and 2) Because I was worried that the booth would turn into a corporate Primal or Satlantis show. However, this wasn't the case. While these teams did have a large presence with many team members all wearing t-shirts, none of my fears became a reality. If people asked questions about Nostr in general, that was discussed. If people asked questions about Primal or Satlantis, that was discussed. I personally recommended numerous social apps, Damus, Amethyst, Primal, Nostur, Nos.social - all of them. The booth was a true decentralized effort and I absolutely did not need to worry as much as I did, but I felt like I had an obligation to fulfill and I wanted to be there to see it through.
If I had to choose an area that needed improvement, I'd say that the three Satlantis women that nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m brought with him were supposed to shadow some of us to learn more about Nostr, so that they could then use this information to do the initial intake booth questions before making the referral to those with more information, but this just didn't happen. We were all so busy. Sorry! It was just too hard to coordinate. Maybe in the future we can prepare a bit more in this area. Although, nostr:npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa did a fantastic job, jumping right in there head first!
Secondly, we could have improved our television capabilities. We rotated from showing the live dashboard from the booth's Zap.stream livestream, to showing Primal.net/explore Nostr statistics, to showing nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz 's Nostr Documentary on loop, to playing the Satlantis promotional video. The majority of the time our TV was playing the same Nostr Documentary. It's great! I love that video, but we may be able to work out a better schedule and rotation mechanism in the future to showcase more content equally. Plus, I don't want to always be on the TV. I don't want people getting the wrong idea.
Nostr takeaways
After speaking with hundreds of people at BTC Prague, I feel that I've discovered the best way to describe Nostr.
Nostr has a portable digital social identity, allowing you to be in control of your digital social identity for the very first time, allowing you to take your entire social graph with you, every time you use a different application from Nostr's ecosystem.
Nostr is the social glue that binds all of your apps together.
In general, at BTC Prague, while explaining Nostr to people, the digital social identity route was what clicked with the most people. From there, it's not a long stretch to understand building a reputation and web of trust either.
Many people do not use the "Other Stuff" and explaining to them how to use these applications is hard. People want a native application.
Damus, Primal, and Amethyst seem to be the number one apps that people are using, with maybe Primal being the number one altogether? This is probably due to Primal being available on Android, iOS, and the web. Also, many people don't know that Damus still supports Zaps via the Nostr script workaround. I had to show many how to enable Zaps.
Everyone wants Nostr at their conference
There is significant interest in featuring Nostr at various conferences. Although not everyone has reached out, numerous individuals at BTC Prague expressed enthusiasm about incorporating a Nostr booth, along with several Nostr talks and sessions, into their upcoming events. They recognize the critical role Nostr and free speech play globally and acknowledge Nostr's popularity within the Bitcoin community. However, they also understand that more work is needed, and we must continue our efforts to onboard and engage new users.

I have two primary observations on this matter:
-
The community effort demonstrated here serves as a blueprint for success. We have proven that this approach to growing Nostr is effective, desired, and necessary. The engagement at our booth and attendance at our panels prove this with ease.
-
This fundraising initiative is likely a one-time effort. I cannot, in good conscience, continue to ask the community to bootstrap these endeavors. If we are to sustain these booths and promote Nostr at similar conferences, the conference organizers themselves must provide substantial support or discounts to foster broader Nostr adoption. While I understand that conferences entail significant operational costs, it is not feasible for Nostr developers and the broader Nostr community to finance these efforts continuously. Additionally, I would not feel comfortable requesting financial contributions from you all again for this purpose.
Looking forward
Will we do _this _again? I don't know. While our initial endeavor was a complete success, it would be unfortunate to cease our efforts just as we are gaining momentum.
Avi and I have a lot to discuss between ourselves and a lot to discuss with all of you.
Thank you all from the bottom of my heart. Thank you nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr for making all of this possible. Thank you to every single Nostrich that donated your hard earned sats to make this possible. Thank you to all of the developers that built all of this to make all of this possible. Thank you to everyone else <3
Keep building.
-
-
 @ b8851a06:9b120ba1
2025-01-27 11:58:53
@ b8851a06:9b120ba1
2025-01-27 11:58:53Trump's Blueprint for Gaza: The New Nakba
Trump’s offhand suggestion to “clean out” 1.5 million Palestinians from Gaza isn’t just reckless—it’s a thinly veiled blueprint for ethnic cleansing. The proposed forced displacement of millions isn't new; it’s the 21st-century sequel to the Nakba, designed to erase Palestine from the map.
Gaza: The Systematic Machinery of Destruction
The assault on Gaza isn’t chaos—it’s coordinated demolition:
- 47,306+ killed – lives extinguished with impunity.
- 111,483 injured – survivors burdened with physical and psychological scars.
- 92% of homes destroyed – families displaced, memories shattered.
- 60% of infrastructure dismantled – society intentionally crippled.
This is more than war—it’s annihilation by design.
A Second Nakba in Motion
The original Nakba (1948) was the template:
- 6 million refugees still barred from returning home.
- Generations of children growing up stateless, inheriting loss.
- Cultural heritage erased, lands stolen, and identities fractured.
Trump’s “solution” carries this legacy forward, pushing millions toward another endless exile.
The Humanitarian Collapse
If enacted, the mass displacement would trigger a humanitarian apocalypse across the region:
- Healthcare systems overwhelmed in neighboring nations.
- Schools collapsing under the weight of refugee students.
- Economic and social infrastructures stretched beyond capacity.
This isn’t just a Palestinian crisis—it’s a global one.
A Calculated Plan for Erasure
Make no mistake: the destruction of Gaza is deliberate. Israeli Finance Minister Avi Dichter’s chilling declaration of a "rolling Gaza Nakba" lays bare the intent: erase Gaza and its people from existence. The steps are cold, calculated, and systematic:
- Starvation as a weapon of war.
- Targeting hospitals to eliminate healthcare.
- Destroying water supplies to force displacement.
This isn’t collateral damage—it’s genocide.
Generational Wounds That Won’t Heal
The impact of this erasure will reverberate for centuries:
- Children growing up with inherited trauma.
- A culture erased piece by piece.
- Future generations left stateless, voiceless, and forgotten.
Every demolished building and every child killed are steps toward creating a permanent refugee underclass.
Silence is Complicity
The global silence is deafening. Trump’s “solution” isn’t a spontaneous idea—it’s the culmination of decades of dehumanization and demographic engineering. And every moment the world stays silent, the machinery of genocide moves forward.
Resistance is Survival
The choice is clear: submit to tyranny or resist. Every truth told, every act of defiance, every refusal to look away chips away at their plans. They want us silent. They need us indifferent.
But we’re not sheep—we’re the descendants of those who refused to kneel. - Share their crimes. - Expose their lies. - Refuse their narrative.
Because the battle for Palestine isn’t just about land—it’s about dignity, existence, and the refusal to be erased.
-
 @ 0463223a:3b14d673
2025-01-27 10:47:00
@ 0463223a:3b14d673
2025-01-27 10:47:00I wrote this article back in 2019 but I wanted to see how it stood up today. Since writing this I’ve been diagnosed with autism. However, I question this. For sure I’ve gone through lots of ups and downs in life. Some issues probably due to childhood trauma, others due to drugs etc. but I still ask if is a natural response to bullshit.
I don’t write this to belittle any problems anyone has and the autism spectrum disorder is real (but not disorder to me). When the whole population gets diagnosed as neurodivergent what next?
If you need help, get help. I write this as a person trying to get off the drugs prescribed to me many years ago. Something I’m finding difficult but I will do it…
From 2019
A large part of the adult population in the Western World are mad, mental, bonkers, have lost their marbles and are totally insane. Well, that’s at least according to the World Health Organisation A recent WHO report stated one in four people in the world will be affected by mental or neurological disorders at some point in their lives. And there’s a very high chance that you, the reader, are completely off your rocker. Mental Health is the buzzphrase of our times. It’s on the TV, the radio and all over the internet. The UK’s Prime Minister goes on TV to state how big the problem is and just how very seriously she takes it and we’re assured the government are working extremely hard to tackle it. However, the rhetoric never amounts to anything, as anyone seeking genuine help will attest. Help is hard to come by. Doctors prescribe pills to subdue the wrong thoughts, but nothing else. No long term solutions, just keep taking the pills. Hundreds of thousands of adults are medicated in this way and now, more worryingly, are many children. So it’s vital to talk about it. It’s permanently Mentalspeng Awareness Day or Tell Facebacon Your Neurologicalwankfuck Week. It’s even become quite fashionable, with regular treats from celebrities telling of their darkest moments and how they nearly didn’t get that huge Hollywood deal because they woke up feeling sad and unhappy one winter morning. If you’re a fruit-loop tell everyone. It will be ok… Tell them about the time you were going to drive your car off a cliff and ended up in hospital after a particularly long conversation with The Samaritans. Great stuff! Tell them about the regular, uncontrollable urges to slash yourself with a Stanley knife or any other sharp object close to hand. Awesome! Tell them about how you smash yourself repeatedly in the head, sometimes with a heavy object, as you can no longer deal with the stress and frustration of being disempowered by situations completely out of your control. Cool! Tell them how you feel trapped by an increasingly expensive housing market and how you have zero financial security. Brilliant! Or maybe just tell them that sometimes you can’t get out of bed and you don’t know why or that you panic uncontrollably for no reason. Skills! Tell the world! We’re so understanding of mental health issues these days, just raise more awareness and everything will be fine, we’re here for you man/woman! (and yes, we might need to sell this information on to the appropriate persons, future employers, insurance companies or government agencies etc.). After all, we’re all good people right? Tell everyone you’re mad and they’ll understand. They’ll think of the time you were a dick and they’ll say “Ahh, poor sod, you know he’s a mental don’t you”. Well frankly no. The world is full of cunts and whilst the people close to you will be sympathetic, as far as wider society goes, you’ll be marked, your position compromised and your word will not be trusted. I mean who knows, maybe you’re delusional, perhaps you’re about to rampage through town wielding a knife or driving your car into a crowded supermarket… But hold up…. One in every four of us is mental?! Is that really the case? Let’s think about this for a second. When did 25% of the population become a massive neurospeng? This wasn’t the case 30 years ago, a quarter of the population weren’t mad. There wasn’t the vast array of medications available these days; Prozac, Sertraline, Citralopram, Promethazine, Venlafaxine, Amiltryptaline, to name a few (there are many, many more). It’s clear that a lot of people aren’t feeling right but how come the suicide rates are higher now than they were 30 years ago? If we’re all so much more aware and well medicated, surely rates would be going down? Perhaps you were diagnosed as a mental because you responded negatively to events happening around you? Maybe you’re working increasingly longer hours for less money. Perhaps the terms of your work changed drastically and you no longer feel secure. Maybe you lost jobs because of funding cut backs. Perhaps you’re in despair because your friend took their own life when their job was cut in an austerity drive. Suicide is the most horrible thing which ever way you look at it. You strip a person of their purpose and they react with the most extreme act of self violence, causing an unbelievable amount of emotional distress for those left to pick up the pieces… And so we say, “Ahh but you understand, they were mad… They were fucking mental, they lost control of their senses, it such a terrible shame but they were mad you know”. Bullshit. The term Mental Health removes all responsibility from the structures creating an environment where people are deemed no longer of value or viable human beings. But maybe you were angry because you were told by politicians that you need to live within your means, whilst those in large financial institutions increased their wealth exponentially? The world economy crashed in 2008 and there’s no money. Eh? The governments of printed more and more money, but there’s no money for you, you cunt. Perhaps it was packed aboard a spaceship and is now hurtling towards Mars! (mad people tend to think like this, after all it couldn’t be that the money was stolen). Maybe you got angry with the blatant corruption from those in public life? Politicians shout loudly that they’re for the people but will pocket pay rises, local council officials bully members of the public and make threats to cut funding . This can be done with total with total impunity, as the structures put in place to control such actions cover up any wrong doing. You see the powerful can not and will not be challenged. There is no pathway to justice. When the fire at Grenfell happened, it was clear for all to see that the housing association, council and big business were at fault, but no, blame was heaped on the lone fire officer who had the awful task of managing two lowly fire engines in London’s biggest fire since World War II. At the time my local Member of Parliament response was “the flats were refurbished to a very high standard”. We shouldn’t lay blame at those in power, we cannot have any fault with the establishment. I bet that poor fire officer was a mental too… When discussing mental health we’re not talking about a brain injury or unfortunate illness. There’s extreme difficulty coping with the world but it’s not madness and it’s not a delusion. It’s a natural reaction to bullshit. We’re are completely surrounded by bullshit, on the internet bullshit, on the TV bullshit, in the work place bullshit, from our leaders bullshit etc. etc. The world is running on massive excess levels of bullshit. And this is the natural emotional response to bullshit. Mental Health is used to invalidate the anger, freeing the powerful from responsibility and laying blame squarely at the individuals door. In the meantime, piece by piece, the powerful steal everything we’ve ever owned. So next time someone says to you raise awareness about mental health, maybe tell them to fuck off. Either that or tell them you’re flying to the Moon to have tea with Kim Jong Un and Barney The Dinosaur. Fuck mental health. *Image used without permission of Barney The Dinosaur.
-
 @ 3bf0c63f:aefa459d
2024-06-07 15:27:10
@ 3bf0c63f:aefa459d
2024-06-07 15:27:10Report of how the money Jack donated to the cause in December 2022 is being spent.
Bounties given
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 97121c7b:30a10e4e
2025-01-27 06:18:42
@ 97121c7b:30a10e4e
2025-01-27 06:18:42here is where the content will be just a test
-
 @ 3c984938:2ec11289
2024-06-07 11:14:17
@ 3c984938:2ec11289
2024-06-07 11:14:17The Chamorros: People of my island
They islanders for centuries took care of the island. They fished, farmed, hunted, voyaged, made tools, art, had stories, had marriages within clans. Then, the Spanish came. When they first came, the Chamorros boarded their boat to greet the weird people(I'm sure they thought they were weird too). It started peaceful until the Spaniards coffer's slowly dried up. This led to the occupation of the island and grew oppressive. Eventually, The Spanish lost the war to the Americans. Guam was then sold to the American gov't as spoils of war, trading one oppressive regime for another.
The TakeOver Process-1
The TakeOver Process-2
The TakeOver Process-3
Get a job, you lazy islanders. We need to tax you, come work for us. This was the price to become American to the indigenous islanders.
Then the war came.
close up
Guam was hit first before Pearl Harbor(The international Date line puts Guam timezone first ahead) but after this, The Japanese invaded and then occupied the island. Note at the bottom, The American Naval governor surrendered. This led to the islanders thus to become slaves to the Japanese Empire.
Recall "Day of Infamy" by FDR
Life under Japanese Rule Note Northern Marianas islands are the smaller islands above Guam. See the next image below.
Map of the island geography. Guam is referred as NYC in the Marianas. The rest are really, really small.

Nearly 16k of indigenous islander died, by the end of the war less than 6kish Chamorro survived.
The Federal Government then claimed parts of the land and since then and haven't returned it. They've returned some of it. This was a long time ago, I think it's time to let it go. Some islanders demand war repatriations. It makes zero sense to demand money from future Americans to pay for those war repatriations. The enemy is not the people, it's those that wield the pen to create unreasonable bills and the ones that enforce it.
Final Words. The islanders lived peaceful. There was no room to be a bad person of the colony because that person was risked getting shunned. Often, they sent the bad natives (thus becoming 2nd class citizens) inland, barring them from getting access to the ocean. But the land is rich and fertile. Instead of saltwater fish, they had fresh water 🐟fish, 🐍eel, 🦐shrimp and 🦞crawfish and plenty of fruit to eat and farm.
They didn't ask to become Spanish or American. It was this way or the highway. When countries want to expand they need more territories, land, money and human capital(your life energy). History doesn't repeat, it just rhymes.
🦋The best way to combat this is go back to a similar economy that is less corruptible. I believe Bitcoin can do this. History gives clues. Don't trust, verify.
Thank you for joining me on this walk (lol, reading) through the museum, please comment if you enjoyed this.
-
 @ 59c2e15a:d25e6e8d
2025-01-27 02:29:42
@ 59c2e15a:d25e6e8d
2025-01-27 02:29:42Note: I originally wrote these essays on bitcoin and yoga in 2022 after completing my yoga teacher training and going deep down the bitcoin rabbit hole. I then published them to my Ghost blog in 2023. I decided to repost them here on Nostr to start 2025 to further spread the wisdom and timelessness that bitcoin and yoga share. I split my original essay into seven parts, and I will add an eighth comparing yoga and Nostr. I hope you enjoy part one - namaste!
Part I: Bitcoin and Yoga Shared Values
Part II: Mythical/Mystical Origins
Part III: Evolution of Money and Yoga
Part IV: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 1-2)
Part V: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 3-8)
Part VI: Bitcoin is Dharma
Part VII: Himalayan Kriya Yoga
Introduction
With each passing day, month, and year, it feels as though our human civilization is becoming more dysfunctional, untethered, and unsustainable. Individuals are working harder, longer hours, yet most remain stuck in place, goals farther from reach. We live in a world where many have outsourced the most critical task that has enabled humans to prosper – critical thinking. I challenge each one of you to remove preconceived notions you might have about Bitcoin or Yoga before reading this series. I invite you to enter with an open mind. Think for yourself – you are welcome to agree or disagree with the information and arguments I put forth.
I also encourage you to go beyond thinking – feel. Use your intuition to understand if the way you’re living your day-to-day life feels good to you, or if you have sense, an inner knowing that something is off with our society today – that there can be a better way. If you open your heart and mind to receiving new information, there is potential to motivate yourself to change your thoughts and behaviors for more aligned action towards individual sovereignty. Every individual can choose freedom and independence. Yet it has become increasingly difficult to live a life of freedom due to the fiat system of inflation and the many distractions that keep us from going inward. After deep study and reflection, I believe bitcoin and yoga both provide the individual control over their own life journey, and frameworks to understand our connection to self and others.
I'm excited to share what I have found in my own personal experience, and hope to spark curiosity within you to follow your passion. This writing is intended for anyone seeking tools to lead a life of freedom, make positive changes and deepen your understanding of self. In addition, it is written for yogis who want to learn about bitcoin, bitcoiners who want to learn more about yoga, and anyone who is interested in a fundamental understanding of these topics that I believe contain the potential to transform your life.
Part I: Bitcoin and Yoga Shared Values
Bitcoin and yoga share many fundamental values with one another and provide deep wisdom on guiding individuals towards living better and more meaningful lives. Ultimately bitcoin and yoga share the goal of individual liberation, freedom from suffering, and a deep inner, lasting peace in Being. In yoga, this state is called moksha or samadhi. I believe everyone has a true essence, an inner being that knows what is best. However, our external environment and our own conscious mind push us away from this serenity, leading to regrets about the past or anxieties about the future. This perspective of linear time and our own individual stories and identity damage our ability to stay present in the Now, leading to endless distractions. In similar ways, bitcoin and yoga provide us insight for an individual’s path to inner peace, as well as for humanity’s path to collective peace and prosperity.
Energy
At the most elemental level, energy is the force underlying both bitcoin and yoga. Energy is the universal currency of life. We would not exist without energy. We require physical energy to fuel our cells and bodies to perform essential tasks like breathing, circulation, digestion, and movement. We perceive many forms of energy such as light or sound waves, yet there are many energy wavelengths we are not able to or are not trained to perceive.
Bitcoin is powered by physical energy in the real world in a process that secures the network and unlocks new bitcoin for distribution, a process commonly referred to as mining. Interestingly, 100 years ago, Henry Ford pushed for an energy-linked currency measured in kilowatt hours that could bring peace after a brutal World War, as seen in the New York Tribune headline and article December 4, 1921: ‘Ford Would Replace Gold with Energy Currency and Stop Wars’ (i). It took another century, but mankind has finally developed a digitally-native currency tied to the physical world through energy expenditure – bitcoin.
Yoga is similarly rooted in energy that individuals tap into through breathwork, physical movement and meditations practices. This life-force energy is known in Sanskrit as prana. Prana is not bound by time or space, and it flows through individuals in over 72,000 nadis, or channels. There are three main nadis - the first is ida, our left side body which corresponds to the feminine, receiving energy, or the moon. On the right side is pingala, relating to our masculine, giving energy, or the sun. The central nadi runs through our shushumna, linking our seven main energetic centers, known as chakras. These chakras run from the base of the tail bone, up through the spine and the top of the head. Each chakra has a name, a color and key characteristics that can often become blocked through negative emotion, trauma or stress in the body. Different yogic practices target these energy centers to unlock what is stuck and enable energy to more freely flow through us in an open exchange with the earth and out the universe. This energy is ever-present; one need only to tap into this energy, feel it and utilize it for the strengthening of one’s inner being that then radiates outwards on others in your life. The energetic experience and upward surge can also be referred to as kundalini energy, a creative power of divine feminine energy that originates in the muladara chakra at the base of the spine.
 Depiction of our chakras and nadis (image source)
Depiction of our chakras and nadis (image source)Proof of Work
In both Bitcoin and Yoga, "proof of work" is required to operate, practice and move forwards. In the Bitcoin network as described in the original white paper, miners contribute tangible energy towards running a hashing algorithm on a computer – SHA256 – to earn the right to add the next block to the blockchain and collect both the coinbase and transaction fee reward (ii). The work is difficult to produce but easy to validate by others. Miners are collecting all of the valid peer-to-peer transactions being propagated to the network and establishing them as truth into the distributed ledger. The rules in bitcoin’s code incentivize honest behavior from miners through unforgeable costliness – if a miner were to lie about any of the transactions it includes in a block, independent nodes in the network would reject the block, and the miner would have lost all the real resources it expended to solve the proof of work calculation.
 Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.
Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.In yoga, dedicated work is needed to learn the asanas, postures, and practice for oneself; you won’t just be able to go upside down or flow through sun salutations without first learning proper alignment and breathing techniques. An individual needs to conscious decision to work on a daily yoga practice that requires energy to flow. There are several ways to work on your yoga practice beyond physical movement; these include bhakti yoga (devotion/prayer), jnana yoga (study/wisdom), karma yoga(selfless action) and raja yoga (ashtanga). Raja yoga includes ashtanga, the eight limbs or paths of yoga that Patanjali detailed \~2000 years ago that we will explore in more depth in part IV. These ancient margas (paths) and subsequent development of these ancient teachings provides individual with ample opportunity to dedicate and work towards individual enlightenment.
Decentralization
Next, there are no external barriers preventing an individual from participating in Bitcoin or yoga. Bitcoin does not discriminate and can be accessed by anyone around the world. Yoga provides a way of life full of mindfulness and appreciation. The only barriers are internal blockages, or unwillingness to ask questions, learn and take responsibility for oneself and state of being. Therefore, Bitcoin and yoga can both be defined as decentralized. There are no centralized gatekeepers preventing one from accessing the Bitcoin network or using bitcoin as money; anyone can spin up a node, download a wallet or mine bitcoin. There are over 16,000 nodes geographically distributed around the world voluntarily running the bitcoin core software code establishing the payment network, validating transactions and storing the entire transaction history of bitcoin (iii). It costs as little as a few hundred dollars and requires less than 600 gigabytes of storage to run a node – in 2023 you can find mobile phones with that much storage. No one can prevent you from sending a peer-to-peer transaction or storing your own wealth with 12 words in your head – you need only decide to take true freedom into your own hands and learn how to do so (iv). The common maxim is “don’t trust, verify”. You don’t need someone else’s permission to participate in bitcoin or trust anyone else (eg, banks) to hold your wealth.
 Geographic distribution of reachable bitcoin nodes (source: bitnodes)
Geographic distribution of reachable bitcoin nodes (source: bitnodes)Similarly, no one can stop an individual from practicing yoga, learning yogic philosophy or connecting with one’s truest self and inner guru. Anyone can choose to follow the path of yoga, focus on ones breath or develop a strong asana practice. There are many different ways to learn and interact with yoga, with experienced teachers willing to share their lessons to students all over the world. One need to simply find yoga studio, enroll in a teacher training or and engage with a teacher to experience yoga for themselves. Yoga looks and feels different depending on what country you are in or in which lineage you are being taught. Tapping into these profound lessons, as fundamental as controlling ones own breath, requires only an individual desire and the conscious decision to act. There’s no CEO or central authority dictating how Bitcoin or yoga has to be. Individuals have the freedom to express themselves voluntarily guided by frameworks we will dive into deeper.
Low Time Preference
Another core value that bitcoin and yoga share is low time preference. In Austrian economics, time preference refers to individual decision making. An individual with a low time preference makes decisions with greater consideration of the future, quieting immediate cravings and desires to pursue a higher goal (v). In bitcoin and money, lower time preference decisions include putting off consumption to save value for the future. Unfortunately, our fiat (by government decree) system induces individuals to make high time preference decisions, heightening consumerism and poor habits today that we see rampant in our society. There is a disincentive to save, as inflation of the money supply leads to debasing value of the dollar and other fiat currencies, decreasing individuals purchasing power of cash they hold onto and don’t spend soon. For example, the purchasing power of your dollar today will be cut in half over the next decade at current levels of inflation. In many ways, bitcoin is time, described brilliantly by Gigi, as it creates a decentralized clock that establishes consensus with each block (vi).
In contrast, the hard cap supply of 21 million bitcoin enables individuals to save with the knowledge that governments and central banks will not be able to debase their hard-earned value. This allows for one to plan with greater certainty, making investments that have a longer payoff period rather than chasing quick, material gains. Likewise in yoga, developing your own practice will not bear fruit right away; it takes discipline and time to continuously improve and strive towards a better future self. For example, in modern Ashtanga yoga taught by Pattabhi Jois, there is a set sequence of asanas that one studies and repeats each practice. It may even take months to have find the right alignment of body and breath for a single pose! The hours-long sequence requires dedication to practice and learn. The dedicated yogi understands that wholehearted commitment today will pay off for one’s mental, physical and spiritual health in the years to come. The ability to develop a calm mind can also be beneficial when people don’t initially understand or are intimidated by bitcoin. This approach can also enable you to stay grounded and discover the signal through the noise when learning about bitcoin.
 Sequence of asanas in Jois' Ashtanga Yoga (image source)
Sequence of asanas in Jois' Ashtanga Yoga (image source)Union
Yoga comes from the Sanskrit word “yuj”, which means ‘to join’ or ‘to unite’. Yoga represents the union of the mind, body, and soul of an individual. Yoga provides a pathway to individual sovereignty through disciplined practice and purpose. Yoga unites an individual internally and to one’s community, fostering connectedness and support (vii). Similarly, bitcoin provides a pathway to individual sovereignty in many ways. Bitcoin empowers the individual authority with property rights over one’s value, which in turn frees individuals from outside control (government or otherwise). Bitcoin’s technology enables one to hold their own wealth and life’s energy in a self-custodial fashion. Bitcoin is money that can be stored forever and transmitted through space at the speed of light on layer two via the Lightning Network.
Bitcoin is an open economic network with the potential to unite eight billion people together in a way our current unfair and fragmented financial system could never do. In many countries, a majority of people are unbanked, while intermediaries take a cut of the value to transfer slow, legacy payments like Western Union. While tens of millions people around the world have so far interacted with bitcoin – we are still early – similar to the internet of the mid-nineties. Bitcoin eliminates counter party risk associated with non-bearer assets, such as fiat currency (e.g., dollars, euros, yen). Bitcoin’s supply schedule is set and eliminates inflation time theft that fiat currency wages on individuals, which leads to anxiety and depression or feelings of hopelessness. Fiat is money enforced by the monopoly on violence that modern nation states grip tightly.
In contrast, bitcoin and yoga empower the individual to remove the shackles and embrace personal responsibility to improve ones life. Bitcoin and yoga also connect people directly to each other and tap into truth, ones inner being, bringing peace in the present and ultimately offer hope for a better future for each person, your community, and the world. Bitcoin and yoga have the power to unite humanity in love.
In the next section, we will explore both yoga and bitcoin's mystical and mythical origins.
Note: Bitcoin with a capital "B" generally refers to the protocol/network; bitcoin with a lower case "b" refers to the money/currency.
References:
i. Redman, Jamie, How Henry Ford Envisaged Bitcoin 100 Years Ago — A Unique 'Energy Currency' That Could 'Stop Wars', News.Bitcoin.Com, October 11, 2021 <https://news.bitcoin.com/how-henry-ford-envisaged-bitcoin-100-years-ago-a-unique-energy-currency-that-could-stop-wars/>
ii. Nakomoto, Satoshi, Bitcoin: A Peer-to-Peer Electronic Cash System, bitcoin.org, October 31, 2008 <https://bitcoin.org/bitcoin.pdf>
iii. https://bitnodes.io/
iv. Hall, Stephen, What is a bitcoin seed phrase and how does it work? Unchained.com. December 17, 2021 <https://unchained.com/blog/what-is-a-bitcoin-seed-phrase/>
v. Ammous, Saifedean, Making Time Preference Low Again, The Bitcoin Times, Austrian Edition (V). November 8, 2022 <https://bitcointimes.io/making-time-preference-low-again/>
vi. Gigi, Bitcoin is Time, dergigi.com. Jan 14,2021 <https://dergigi.com/2021/01/14/bitcoin-is-time/>
vii. 200 hour yoga teacher training. House of Om, Bali, Indonesia. <https://houseofom.com/>
-
 @ 4c96d763:80c3ee30
2024-05-31 07:05:51
@ 4c96d763:80c3ee30
2024-05-31 07:05:51Here's a quick script for generating git shortlog longform notes on git push. It currently powers the Damus Code nostr account:
Let's say you are hosting a bare git repository on a server at
git/project. You can add apost-receivehook that generates a longform note when you push to the server:In
server:git/project/hooks/post-receive:```bash
!/usr/bin/env bash
commit_body="" last="" project="my-project" # update this with your project name sec="abcdef..." # update this with your secret key branch="master"
while read oldrev newrev refname; do branch=$refname last=$newrev relays="wss://relay.damus.io wss://nos.lol" commit_body=$(git shortlog $oldrev..$newrev | awk -f /home/user/markdown-shortlog.awk) done
if [[ $branch == "refs/heads/master" ]]; then
nostril --content "# Changes
$commit_body" \ --envelope \ --kind 30023 \ --tag title "$project" \ --tag summary "Latest codebase changes to $project" \ --tag t gitlog \ --sec $sec \ | nostcat --connect-timeout 1000 $relays fi ```
you'll need nostril, nostcat, and
markdown-shortlog.awk:```awk /^[^ ]/ { if (author) { print "" } author = $0 print "## " author }
/^ / { print "-" substr($0, 6) } ```
Now when you push, it will generate a longform note that looks something like this:
Example
William Casarin (10):
- fix warnings
- readme: add usage
- textmode: fix coloring of abbreviated names
- profiling: update puffin version
- refactor: move note into its own widget
- refactor: rename widgets to ui
- ui: simplify note widget
- get all missing ids from all timelines
- initial inline note previews
- fix until filters
kernelkind (6):
- Add custom visual themes
- Add modular custom text styles
- Apply app style to AccountLoginView
- Add MobileAccountLoginView
- Refactor 'ui tests' conception to previews
- Use custom style in app
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ f77dfdcf:17e93422
2024-05-29 04:06:39
@ f77dfdcf:17e93422
2024-05-29 04:06:39Proof of Work เป็น concept ที่คนที่เคยศึกษาการทำงานของ bitcoin อาจจะเคยได้ยินผ่านหูมาบ้าง แต่จริง ๆ แล้ว สิ่งนี้สามารถนำมาประยุกต์ใช้กับชีวิตประจำวันของเราได้อย่างเป็นธรรมชาติมาก
Proof of Work สำหรับ bitcoin เอาแบบสั้น ๆ คือ การที่เราเจอ ตัวเลขที่ถูกต้อง (Proof) ซึ่งได้จากการขุด ที่จะเกิดขึ้นได้โดยการใช้พลังงานและเวลาของเครื่องขุดในการคำนวณตัวเลข (Work)
ยิ่งมี Proof of Work ใน chain เยอะขึ้น ก็ทำให้ transaction มี confirmation มากขึ้น
ถ้าจะให้เขียนให้ครบจบตรงนี้ คนอ่านน่าจะตาลอย แนะนำให้ลองอ่านต่อใน Inventing Bitcoin ดูครับ
พอเราซูมออกมาเป็นภาพกว้าง ๆ Proof of Work จะหมายถึง “หลักฐาน” ที่เกิดขึ้น จากการทำ “งาน”
งาน (Work)ในที่นี้ คือ การลงทุนทาง “เวลา” ไปกับการทำส่ิง ๆ หนึ่ง ซึ่งจะได้ผลตอบแทนเป็น Proof of Work ในรูปแบบใดรูปแบบหนึ่ง
Proof ที่พูดถึง ไม่จำเป็นต้องเป็นชิ้นงานที่มองเห็นหรือจับต้องได้ มันอาจจะหมายถึงทักษะ ความรู้ หรือ ประสบการณ์ ก็ได้
ตัวอย่างในชีวิตประจำวันชัด ๆ เลยก็อย่างเช่น
- การที่บางคนที่มีหุ่นดี สุขภาพแข็งแรง มีกล้ามเนื้อกำยำ ก็เป็น Proof of Work ของการออกกำลังกาย กินอาหารที่ดี และความมีวินัย
- การที่เราเรียนรู้เรื่องใหม่ ๆ แล้วเรารู้สึกว่ายังไม่แน่ใจกับสิ่งที่รู้ เราเลยศึกษาเพิ่ม สิ่งนี้ก็เป็นการเพิ่ม Proof of Work ตัวเรา ซึ่งคือ knowledge ของสิ่งนั้น ทำให้เรามั่นใจในองค์ความรู้นั้น ๆ มากขึ้น และสามารถนำไปส่งมอบ valueให้กับคนอื่น ๆ ได้
- หรือจะเป็นการฝึกทักษะการทำงาน ถ้าเรารู้ว่ายังไม่เก่ง Work ที่เราจะทำเพิ่ม ก็คือการหมั่นฝึกฝน และ Proof of Work ที่ได้ คือ ทักษะที่ดีขึ้นของเรา พอมองแบบนี้ เราจะชั่งน้ำหนักได้ง่ายขึ้น ว่าเราอยากจะลงทุนเวลาของเราไปกับ Proof of Work แบบไหน เพราะทุกคนย่อมอยากได้ผลตอบแทนที่คุ้มค่าจากการลงทุน
แต่มันมีข้อสังเกตอยู่อย่างหนึ่ง คือ เราต้องมองให้ออก ว่าอะไรเป็น Proof of Work จริง ๆ ของแต่ละสิ่ง
อย่างบางที เราบอกว่า เราเข้าใจเรื่องนี้นะ เพราะเราเคยเรียนคลาสนี้มา และเราอาจจะคิดว่าเอารูปถ่ายหรือประกาศนีย์บัตรมันเป็น Proof of Work ได้ แต่จริง ๆ แล้วไม่น่าใช่ มันคือ Proof of อะไรไม่รู้
อ่ะ ๆ มันอาจจะเป็น Proof ว่าเราเคยไปเรียนมาจริง อันนี้ยอมรับได้ แต่ไม่ใช่ว่ามันจะเป็น Proof ว่าเราเข้าใจเรื่องนั้นได้โดยตรง
เพราะ Proof ของ Work ที่เรากำลังพูดถึง มันคือ knowledge ที่อยู่ในหัวเรา ถ้าเราอยากโชว์ว่ามี Proof of Work จริง ๆ เราต้องเอาสิ่งที่ได้เรียนรู้ มาแชร์ให้คนอื่นฟังได้
และสังเกตดี ๆ จะเห็นว่า Proof of Work ที่ได้พวกนี้ มันเป็นสิ่งที่จะติดไปกับตัวเราทั้งหมดเลย มันจึงเกิดเป็น quote ที่ว่า
“You are your Proof of Work”
ซึ่งสื่อว่า สิ่งที่เราเป็น ล้วนเป็น Proof of Work มาจากสิ่งที่เราทำทั้งสิ้น และยิ่งเรามี Proof of Work เยอะขึ้น เราก็จะยิ่งเติบโตขึ้นเรื่อย ๆ
บางทีเราสามารถมองได้ด้วยตาเปล่าด้วยซ้ำ ว่าใครมี Proof of Work ที่มากหรือน้อย เพราะมันจะมันสะท้อนออกมาในรูปแบบของความมั่นใจ
พอรู้จักสิ่งที่เรียกว่า Proof of Work แล้ว สุดท้าย เราต้องกลับมาถามตัวเอง ว่าสิ่งที่เราทำอยู่ มันกำลังให้อะไรกับเรา กำลังสอนอะไรกับเรา หรือมันจะมอบ Proof of Work ที่เราต้องการ สำหรับเป้าหมายของเราในอนาคตหรือเปล่า
พิจารณามันให้ดี และอย่าลืม
หมั่นสร้าง Proof of Work ให้กับตัวเอง
Reference
https://youtu.be/E0LYMhjHnBU?si=AY6ySrTy5t-OgYFT
-
 @ 378562cd:a6fc6773
2025-01-26 18:51:00
@ 378562cd:a6fc6773
2025-01-26 18:51:00Here is the best list I could compile.... I hope I didn't miss anything but please let me know if I did in the comments.
- Withdrawal from the Paris Climate Agreement\ Directed the U.S. to exit the Paris Climate Agreement, citing economic priorities over global climate commitments.
- Withdrawal from the World Health Organization\ Initiated the process to withdraw the U.S. from the WHO, criticizing its handling of global health crises.
- Declaration of National Emergency at the Southern Border\ Declared an emergency to allocate military resources for border security and wall construction.
- Attempt to End Birthright Citizenship\ Proposed ending birthright citizenship for children of non-citizens in the U.S.; pending legal challenges.
- Mass Pardon of January 6th Defendants\ Pardoned approximately 1,500 individuals charged in the Capitol riot, sparking significant debate.
- Reinstatement of the Mexico City Policy\ Prohibited U.S. foreign aid from funding organizations that provide or promote abortions.
- Energy Policy Shift Favoring Fossil Fuels\ Ordered an expansion of fossil fuel production on federal lands and offshore, reversing previous restrictions.
- Rescission of Diversity, Equity, and Inclusion Programs\ Ended DEI initiatives within federal agencies, focusing on merit-based policies.
- Establishment of the Department of Government Efficiency\ Created a department tasked with reducing bureaucratic waste and improving federal operations.
- Designation of Mexican Drug Cartels as Terrorist Organizations\ Labeled certain cartels as foreign terrorist organizations to enhance enforcement measures.
- Mandate for Federal Employees to Return to Offices\ Ended remote work policies for federal employees, requiring a full return to physical offices.
- Artificial Intelligence Investment Initiative\ Repealed previous AI orders and allocated $500 billion to advance AI development in the U.S.
- Pardon of Ross Ulbricht\ Granted a full pardon to Ross Ulbricht, founder of the Silk Road online marketplace.
- Reversal of Electric Vehicle Targets and Renewable Energy Permits\ Halted permits for renewable energy projects and reversed EV adoption targets.
- Declaration of National Energy Emergency\ Declared an emergency to boost domestic energy production and enhance energy independence.
- Declassification of Assassination Files\ Ordered the release of government records related to the assassinations of JFK, RFK, and MLK Jr.
- Pardons for Anti-Abortion Protesters\ Pardoned individuals convicted of offenses related to anti-abortion protests, including clinic blockades.
- Strengthening American Leadership in Digital Financial Technology\ Promoted U.S. leadership in blockchain and digital assets while fostering innovation and regulatory clarity.
- National Hiring Freeze and IRS Agent Reassignment\ Froze federal hiring and proposed reassigning 90,000 IRS agents to border security roles.
- Trade Reform and Tariff Implementation\ Imposed tariffs on imports from Mexico, Canada, and China, aiming to boost U.S. manufacturing and tax revenue.
- Investigation into Weaponization of the Justice System\ Initiated a probe into federal, state, and local agencies to assess potential misuse of the justice system.
- Suspension of CBP One Program\ Terminated the system allowing asylum seekers to schedule appointments at legal ports of entry.
- Demand for Increased NATO Defense Spending\ Called on NATO allies to increase defense spending to 5% of GDP for equitable burden-sharing.
- Trade Tariff Threats Against Mexico and Canada\ Announced intentions to impose a 25% tariff on imports from Mexico and Canada to protect U.S. industries.
- Suspension of Foreign Aid, Including to Ukraine\ Halted all foreign aid programs, notably affecting assistance to Ukraine.
- Launch of Mass Deportations Using Military Aircraft\ Initiated large-scale deportations of undocumented immigrants utilizing military resources.
- Executive Order Recognizing Only Two Genders\ Stated that the federal government will recognize only two genders, male and female, eliminating DEI mandates.
- Ending Illegal Discrimination and Restoring Merit-Based Opportunity\ Prohibited private organizations from conducting Diversity, Equity, Inclusion, and Accessibility (DEIA) employment programs for jobs created by federal contracts.
- Designation of Ansar Allah as a Foreign Terrorist Organization\ Initiated the process of designating Yemen's Ansar Allah (the Houthis) as a Foreign Terrorist Organization.
- Rescission of Executive Order 11246\ Revoked the 1965 order that prohibited federal contractors from employment discrimination based on race, color, religion, sex, sexual orientation, gender identity, or national origin, and mandated affirmative action programs.
-
 @ 7bdef7be:784a5805
2024-05-28 13:47:50
@ 7bdef7be:784a5805
2024-05-28 13:47:50I wrote Oracolo (see the announcement below) because I was brainstorming about Nostr "long format" and thinking about how to promote it. There seems to be little love for this format, why?
Long posts should have interesting value because the author usually put effort into them, and are produced for a long-term fruition. In the end, blogging was one of the most productive strands on the web, and still holds considerable importance.But in standard (kind-1) social clients they are rather hidden. I think many people don't even know they exist, they probably intuit something just because they see a particular formatting. This is quite evident if you compare the responses/zaps/reactions of the short notes with the long ones, the latter have far fewer interactions, a fact that I read as less exposure to readers.
Interlude: don't know what this "long format" stuff is?
Check https://habla.news or https://highlighter.comI think the situation can be largely improved with some adjustments in kind-1 clients:
- Add a tab/section to the user's profile, next to the usual posts/responses, that lists only the long format notes;
- Highlight/pinning recent long notes in the user's profile to give them visibility; the user picture could also have a special mark that alerts about fresh content available;
- In the feed show the preview of long notes with a special design, and allow the user to read them in a separate/immersive view (or just link to njump.me);
- In an appropriate context (es. at the footer of a long note) invite the user to discover long format and post his own content;
- Offer a filtered feed that display only long format notes;
Finally, we should probably also evaluate and agree on a new labeling in clients, because “long notes” is self-explanatory but also a bit confusing next to "plain notes”. Perhaps “articles” might be a better term.
If clients bring more interaction on articles, content creators are naturally incentivized to invest their time in this area, thus increasing the production of in-depth content that may be of interest even to those who are not as involved in social media dynamics.
Memo for kind-1 clients: interoperability is our superpower and currently your are the main entrance to Nostr, so don't be fearful or lazy, please embrace it.
nostr:nevent1qqsrrcl7sfaxd505lyezj7u54tpdg93x0swpcpe0xj5adax5l6xz3yspzamhxue69uhky6t5vdhkjmn9wgh8xmmrd9skctcpr3mhxue69uhkxmm4de68y6t9wvhxv6tpw34xze3wvdhk6tcppemhxue69uhkummn9ekx7mp0aagyzp
nostrdesign
-
 @ fd78c37f:a0ec0833
2025-01-26 12:07:12
@ fd78c37f:a0ec0833
2025-01-26 12:07:12ETHOS & PURPOSE🌐
SATS'N'FACTS emphasizes Creativity, Privacy, FOSS Advocacy,with a focus on Local Community, Decentralization, and Health Balance. It is dedicated to nurturing an environment where decentralization and open collaboration thrive, providing space for deep technical discussions, hands-on learning, and meaningful networking, all with the goal of strengthening the Bitcoin community in Asia.
They aspire to redefine boundaries and usher in a new era of design and development excellence that leaves an indelible mark on the bitcoin environment. A three-day event dedicated to fostering innovation, and freedom within the Bitcoin Developer Community in Asia.
LEADS🧑💼
Enthusiast developers and builders from around the globe, will attend this first installments of the SATS’N’FACTS. Including nostr:npub1nvfgglea9zlcs58tcqlc6j26rt50ngkgdk7699wfq4txrx37aqcsz4e7zd nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6 nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv nostr:npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef nostr:npub13rvvn5g23anm09kwnya8qvzqejxfajfa56rnn47ck5l96ke6cq4sdcd4e0 nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr nostr:npub10xk2rsg9l9ksht66egss98z7mzhetf8d7q4476d9cm6vsfv3a00qld5tdf nostr:npub19x0h8jm3mnwzhv4tpq62zta05er0qlyge73m0pwsp7h666khkd9qev2ree and more.
AGENDA📝
The event is designed to be a “decentralized and collaborative” effort between all participants, with activities being put together with attendees’ feedback. So no agenda, but here some guidance to make sure this event will be joyful and constructive:
🗓️8ᵗʰғᴇʙ Doors Opening:
- [ ] Event Opening
- [ ] Welcome session and intros
- [ ] Presentations and open discussions
- [ ] Initial networking and collaborative sessions
- [ ] Hackathon begins
🗓️9ᵗʰғᴇʙ :
- [ ] Hackathon continues
- [ ] Attendee-led sessions
- [ ] Recording room open for voluntarily podcasting and interviews
- [ ] Peer-to-peer learning and networking
🗓️10ᵗʰғᴇʙ Closing UP:
- [ ] Hackathon wrap-up
- [ ] Pitching contest and project presentations
- [ ] Networking
- [ ] Closing remarks and final session
MERCH🛍️
Their event merch is not just cool—it’s a must-have! T-shirts 👕, bags 🎒, stickers 🖼️, caps 🧢...Get yours and carry the event vibe wherever you go!


Other Fun Activities🎡
In addition to the exciting conference, they've prepared a variety of enriching experiences for you—live art and craft activities🎨, art exhibitions🖼️, creative workshops✨, and Thai massage 💆……, and more.

How to join the Event🎡
If you're in Asia this February, don't miss out—join them in the vibrant city of Chiang Mai, Thailand 🇹🇭 for an unforgettable experience!
📅 Time:8—10th February 2025 📍Location:12/8 ถ.วัวลาย ซอย 3 ตำบลหายยา, เมืองเชียงใหม่ 50100 🇹🇭ไทย 💺Book your seat: https://formstr.app/#/fill/b3b9bd115fe936848a5e03134fefff945287285d51b1dee4731fef6a1070c597 🎤Submit an idea: https://formstr.app/#/forms/cf02333ea3c0d0c21080df599373e289fa343a55e63a1abdc7f633d1594078ff 🎫Buy your ticket: https://satsnfacts.btc.pub/p/ticket/
-
 @ 6ad08392:ea301584
2024-05-27 18:31:39
@ 6ad08392:ea301584
2024-05-27 18:31:39Release announcement & short overview
Two years, six drafts, and 125,000 words later, and The Bushido of Bitcoin is almost complete.
Before the book’s release in Q3 of this year I will be doing a few things:
- Making it available for pre-order on Geyser. For the general paperback, digital and audio copies, it will save you roughly 50%. I will also include some limited edition options, like a short run of 21 leather-bound versions of the book. More on that in the coming weeks.
- Drip-feeding snippets from the book, in the form of quotes, lessons, etymology progressions and insights, across all my socials. On Substack I’ll do longer form posts, on Twitter & Nostr, I’ll keep them more succinct, and finally, I’m reviving my Instagram to wrap the insights in beautiful, shareable, bite-size visuals.
- Jumping on a bunch of podcasts, both Bitcoin and not Bitcoin-related to dig into the content of the book. I’ve recorded with Breedlove already. Many more to come - and who knows, I may even revive my old Wake Up Podcast and do a few short episodes there too.
I want to treat this book as both an ongoing work and a piece of art. So alongside the book, I’m also going to produce some pieces of visual and physical art. The video trailer, alone, I promise will blow your mind., as will the warrior-samurai artwork I’m going to have commissioned in collaboration with some soon-to-be-announced artists. I’ll probably even do a tradings cards pack with Bitcoin Trading cards next year, and some other collaborations along the way.
In any case, it’s been an incredible journey writing this book and I’m honoured to have had people like John Carter help me edit it, and Ross Stevens agreeing to do the foreword. I can’t wait to have the final version completed and in your hands.
For those who might be wondering what I am talking about…
**What is The Bushido of Bitcoin? **
This is a book I’ve been writing for almost two years now. Its genesis was a conversation I had with Erik Cason on my old Wake Up Podcast - also called “The Bushido of Bitcoin.” It was Episode 65: you can check out here. The inspiration for that episode came from a shared love of the book by James Clavell, called: Shogun (now a HBO series - which it seems they didn’t make woke..thank God), and of course we related the idea of Bushido (Way of the warrior: Code of Virtue) back to Bitcoin.
I felt that this was a seed of an idea, well worth watering. So after that, I decided to go on a history binge and start collecting ideas. What ensued was a real journey. I must’ve listened to a thousand hours of history books and Dan Carlin podcasts in the first six months and the concept began to form. But before I tell you what the concept is - let me tell you what it’s not.
This is NOT another book about the history of money, nor does it make an Austrian case for sound money, or an economic case for Bitcoin as sound money. Neither is it concerned with how Bitcoin works, or any of the technicals. We have enough of those books, and I don’t think I will add anything new to that corpus of knowledge. What this book IS about, is something so much deeper and more profound: The behaviour, virtue, culture and civilisation of greatness.
The book seeks to answer the question: “What happens when Bitcoin wins?” What happens to those who rise to the top, and become the socio-economic elite of the world?
- Will we become a new parasitic class?
- Will we become self-indulgent degenerates? Or..
- Will become men and women of virtue?
The latter is not a given, and it’s certainly not enough to just say “Bitcoin Fixes This.” To become men and women of stature and character requires actively developing the virtues which give rise to a culture of excellence. This is the only way to reclaim and rebuild civilisation - complaining and wishing about the past won’t cut it.
Over the coming weeks, I will introduce you to the Ten Virtues that make up The Bushido of Bitcoin. The book of course is more complete, but I will hold nothing back. We’ll follow the historical and etymological genesis of these virtues with an in-depth analysis on how they were embodied by the greatest leaders and warriors throughout history. We’ll also draw lessons from this analysis that will help us navigate the road ahead.

What lies before us may be a “clown world” but hope is far from lost. We’ve been here before. Many times, and against greater odds. This is our generation’s opportunity for a re-conquista.
The Bushido of Bitcoin is written to remind you there is something greater inside of you, and the only way through hell, is forward. I hope you find value in the up-coming content, and that should you pick up a copy of the book, it greatly inspires you.
Thankyou Aleksandar Svetski
Per-order the book here: https://geyser.fund/project/bushidoofbitcoin Get a free introductory chapter here: BushidoOfBitcoin.com Follow my work here: Linktree.com/Svetski
-
 @ 362ebffa:492e2719
2024-05-27 12:51:14
@ 362ebffa:492e2719
2024-05-27 12:51:14Consciousness is the subjective experience arising from the brain (as the viewer, the beholder) While reality encompasses both the objective external world and our subjective perception of it.
The two are deeply interconnected, with consciousness shaping our experience of reality and reality influencing the state and content of our consciousness.
Therefor we do live in various bubbles of reality, my reality (my perception of reality) is my own.
What do you think?
-
 @ 3c506452:fef9202b
2025-01-24 20:27:49
@ 3c506452:fef9202b
2025-01-24 20:27:49Kia ora ano e te iwi whanui!
Often I pose the question to myself "How would I say this if I had no knowledge whatsoever of English?" That's basically what guides my sentence formation whenever I speak Maori.
Since the arrival of Tauiwi into our turangawaewae, our reo has shifted, largely due to intermingling with the English language, and an entire generation or two completing losing the reo.
Great efforts have been made to secure our language from total extinction, and the number of te reo speakers seems to be on the rise.
What I do notice though is that most of the time when I do hear te reo being spoken, it's cadence follows that of the English language.
Vowels are clipped, consonants are aspirated, and English thought patterns are disguised via the Maori language.
Regardless, I still appreciate and prefer the reo to be spoken rather than it not be spoken at all.
I once heard someone remark that"Maori sounds like Hawaiian with a New Zealand accent. Hilarious!"
So, how do I personally tackle this and try make my own reo sound more Maori?
Here's how:
-
Read Nupepa Maori - When the written word came to us, we dove straight in. Nupepa Maori gives great insight into how the language was used using the new medium of pen and paper.
-
Listen to the older videos of Wakahuia Docos - Wakahuia has been running for a long time and I find listening to our old people of those times a good way to hear the differences between how the reo sounds today, and how it sounded a little while back.
-
Listen Radio Kahungunu archives - They have a really nice archive of a talkback radio show.
-
People to listen for - I personally try to find anything by Timoti Karetu, Quinton Hita, and Julian Wilcox as I really enjoy the sound of how they speak the reo.
-
Listen to Cook Island Maori, Gagana Tokelau and Hawaiian (Keao Nesmith, Niihau dialect, Kaalala, Kanahele Collection) - Listening to other polynesian languages gives a good general gist of the sound of polynesian languages. I try to emulate a similar sound whenever I speak te reo.
No reira, ko tena tena, I hope that 2025 will be a good year for Te Reo Maori!
Nga rauemi:
Nupepa Maori
Wakahuia
Radio Kahungunu
Quinton Hita
Julian Wilcox
Timoti Karetu
Kanahele Collection
Ka Alala
Gagana Tokelau
Kuki Learning -
-
 @ 2ecde0a6:10022dcb
2024-05-25 20:28:41
@ 2ecde0a6:10022dcb
2024-05-25 20:28:41Opinion about KeepKey (hardware)
KeepKey is a hardware wallet with a high level of security and supports more than 40 different crypto assets.
The device provides a PIN code and recovery seeds. It has a feature where it switches your PIN code numbers from time to time, making it impossible for malware to copy our code. Also, the device has a system for trade where you have to press and hold to confirm the transaction to avoid external hacks.
KeepKey has only one button to manage it. This button is used for turning the device on and off. All the other processes can be managed through the mobile app. That includes entering your PIN code and setting up the recovery seed, which makes it very simple to use, unlike other complex wallets. The device has a wide screen that allows you to see the entire cryptocurrency address without the need to scroll back and forth. But it's easy to break or scratch if you don't have a protecting casing.
Its price is around $80.
But you have to remember that the device is a little big and heavy, compared to other hard wallets, so it's difficult to carry around with it.
WalletScrutiny #nostrOpinion
-
 @ 39cc53c9:27168656
2025-01-24 20:10:32
@ 39cc53c9:27168656
2025-01-24 20:10:32Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-24 00:08:49
@ 5d4b6c8d:8a1c1ee3
2025-01-24 00:08:49@grayruby and I wanted to do some Jokic appreciation, since he isn't going to be MVP this year, despite having one of the best seasons in NBA history.
Here's my case for Jokic being the best player in NBA history.
Jokic is averaging 30/13/10 while shooting damn near 50% from 3.
Context
Some reference points to add context to those figures - Shaq never averaged that many points in a single season, despite being considered the most dominant scoring big of all time by many people. - Steph has never shot as high of a percentage from 3, despite being universally recognized as the best shooter of all time. - Dirk never matched any of those four numbers in any season, despite being considered the best stretch-big ever. - Neither Duncan nor Robinson ever averaged that many rebounds. - Neither Jerry West nor Bob Cousy ever averaged so many assists.
Best of the best
Looking at the best seasons ever played, as measured by Win Shares per 48 minutes, Jokic is currently having the second best season ever. Only Kareem's legendary 71-72 season is higher.
The best 20 seasons are accounted for by just 9 players: - 5 are from Jokic - 4 from Lebron - 3 for Kareem - 3 for Jordan - 1 for Wilt - 1 for Steph - 1 for Durant - 1 for Robinson - 1 for SGA
Jokic does winning basketball stuff at a higher rate than anyone but Kareem and he's already done it more often than Kareem, despite still having several years left in his prime.
Scalable Skills
Jokic, like most of those other top players, is an elite scorer. However, what's so special about him is how scalable his skills are.
Being a dominant scorer is one of the least scalable skills: as in, there are steeply diminishing marginal returns to adding elite scorers to NBA rosters (there's only one ball, after all).
Shooting, passing, and rebounding are highly scalable. Shooting ability improves offensive spacing, making life easier for teammates. Passing generates better scoring opportunities for teammates. Rebounding is a team effort.
Because Jokic is so great at the most scalable skills, it's relatively easy to build a great roster around him. Lots of different kinds of players thrive, because he can make up for almost any shortcomings they might have. This is why he's the only NBA Champion who had zero All Star or All Defense teammates.
Conclusion
When we consider the totality of what it means to be good at basketball, it would be hard to argue that someone else has ever been better at it than The Joker.
originally posted at https://stacker.news/items/861853
-
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 3c827db6:66418fc3
2024-05-20 12:25:27
@ 3c827db6:66418fc3
2024-05-20 12:25:27With the previous articles, we found the disconnect between paid-for work and paid-for time. We also understood that if you want to get paid you have to provide work that is valuable for others. So when the person consumes the benefit of your work, the exchange happens value for value - work for sats. But what happens if the benefit that the consumer experiences is not a momentary but a continuous process? There are a few examples of this. I will start with the one that is not that captivating but still valuable.
Streaming services, like other industries, grapple with the limitations of the fiat payment system. The burden of fees and the absence of suitable technology for streaming payments have compelled them to adopt similar mitigations as other industries. This translates to charging users on a monthly basis.
With the Lightning Network, we have the technology to stream sats for content. No longer confined to monthly subscriptions, you pay for what you consume in real time. Whether you watch sporadically or binge extensively, streaming payments allow for a more personalized and efficient payment model. This way the creator of the content and the user have a direct connection for each minute the content is broadcasted. With streaming payments now you can say goodbye to subscription payments.
Unveiling A New Era Of Fair Compensation And Accountability In Movie Production
Imagine you've created a movie or documentary. Traditionally, you'd charge people for a ticket, essentially asking them to pay upfront for future value, creating a slight disconnect. Now, with streaming payments using sats, consumers can pay as they watch. If your movie sucks, they might only pay for the first 30 minutes. However, you still receive value, and viewers won't feel overcharged for something they didn't enjoy. If your movie is great they not only stream sats the whole time but at the end, they leave a tip.
On the receiving side of the movie most people involved in it received a salary for doing their job. As we already know this is not aligning the whole structure in the same direction. Some people do not care at all how good the movie is if they have already been paid and do not receive a bonus further. Some people might care about reputation in the market but very few just want to do the best job. Again, we went through this, and as you are guessing you just do a split payment in the backend where all the people in the credits actually receive sats or even milisatoshis based on their contribution. This was something I did not expect that Bitcoin would disrupt. This way the reputation is directly linked to the payment and a lot more people will fight to have the best movie. You can be someone who contributed to a project and wants to stay anonymous for whatever reason but still receive money - Lightning instant settlement is the way to do it.
These concepts should not be new if you read through the last 3 articles. In addition, people in the Bitcoin space are familiar with the Value for Value (V4V) podcasting and that is very close to what I am describing above. While the technology for podcasting is already in place, it's surprising how few podcasts leverage this technology to implement split payments effectively. They give that responsibility to some hosting service that decides to take a 5% split for themselves and the other 95% goes to the wallet of the show. Why not do the split the proper way? The hosting service provides value so they should get a percentage but if you are 3 people involved in the production of the podcast you should have that 95% split so it goes to those individuals. There's no excuse, especially for Bitcoin podcasts, not to make this effort and implement split payments appropriately.
The Dynamic Future Of Pay-as-you-go In Content Consumption
In this example, the pay-as-you-go model holds true for continuous experiences, like streaming. Now, let's revisit the movie example. If you're a theater, you are essentially the hosting provider for the movie. The quality of the theater experience can vary; one theater might have uncomfortable chairs, while another boasts luxurious massage chairs. The theater with subpar seating might receive a 3% share of the movie's streaming sats revenue, while the one with comfortable massage chairs might earn 5% for each sat stream paying for the movie. Furthermore, if a viewer activates the massage function of the chair, additional sats are streamed for each second that the function is on. I do not know the exact payment dynamics between theaters and movie studios but I bet there are prepayments and funds held at multiple points in the fiat payment process. With the adoption of the Lightning Network, theaters no longer have to prepay for movies to be projected on their screens. They can now observe which movies are most popular in real time and adjust their projections accordingly to optimize revenues. This benefits the consumer and optimizes profits for themselves and the creators of the movie.
Now you see the content gets its value stream for the continuous experience and everyone in the film industry will fight to give the best experience for the most amount of time. The better the experience the more sats flow their way. Due to the highly subjective nature of content, where one person might deem a movie subpar, another might label it as their favorite. This subjectivity is why I believe most content streaming will not have a predetermined price. Even movies may adopt the V4V model, similar to what Adam Curry is pioneering in podcasting. For instance, you watch a movie, and during the credits, a prominent QR code appears, allowing you to decide how much you want to send to the creators of the movie. You will listen to a song or a podcast the same way. Whether you predefine a streaming rate per minute or request payment at the end, both options are technically possible. However, the market will ultimately determine which option prevails as the better one.
Also, why not have a bidding competition for any event that has assigned seats? The person who bids the most for a ticket gets to be in the first row of the concert or a sports stadium. This way the subjectivity is left for all the viewers to decide how valuable it really is. This way it ensures a full stadium also because if there is no value in attending the event people are not going to bid for the seats or just pay 1 sat for it.
Revolutionizing Taxi Transactions For Drivers And Passengers Alike
The continuous experience or service for streaming could be anything in the physical realm. I will take a look at how instant settlement could look like in transportation services. One such transportation service is the taxi service. Even though Uber decentralized the taxi companies which is great they did nothing about decentralizing the payment process. Lightning Network fixes that and more.
With a streaming payment option for each meter of movement, taxi drivers no longer need to wait until the end destination to receive their payment. In a world of instant settlement, payment occurs as you go, eliminating the risk for the taxi driver regarding whether the passenger will pay at the end of the journey. While this might not be a groundbreaking improvement, there are several additional benefits to consider.
Why do most taxis operate with cash? Taxi drivers in most places need a POS device for the customers to be able to pay for a better user experience (UX). It may be a better UX but on the other hand, it creates problems for the drivers either way:
- They have to acquire clunky devices.
- They must pay payment processing fees, negatively impacting their margins.
- Operating solely with cash exposes them to the honeypot problem, carrying a substantial amount of money, and making them vulnerable to theft.
With an app tailored for the taxi experience and integrated with the Lightning Network, these issues become irrelevant. There is no need for additional equipment, no payment processing fees for receiving money, and no exposure to visible cash, reducing the risk of being a target for theft. Now you can have a better UX with better security and better margins - an additional benefit is that it will be paid with Bitcoin. Not only that but just like the example with the movie theater chairs drivers will be incentivized to make the travel experience even better. They can offer - to watch a movie, video games like PlayStation, or massage chair. If you choose to use those extra experiences on top of the travel experience you have to increase the sats streaming their way.
An additional benefit for the travel experience of customers arises when multiple passengers in a taxi have different destinations. Traditionally, the taxi meter ticks for the entire journey, and when the first person is dropped off, determining a fair amount for their portion becomes complex. However, with the Lightning Network, it's conceivable to streamline this process. Imagine a scenario where three passengers enter a taxi, each with distinct destinations. Each person scans a QR code upon entering, linking their streaming sats to the taxi app. The app manages split-receiving, dynamically adjusting the distribution of streaming payments based on how many people are in the taxi. As passengers are dropped off one by one, the app seamlessly adjusts the split-receiving, providing a fair and efficient payment solution for each individual's share of the journey.
Optimizing City Transportation With Streaming Sats
The proposed model of split-receiving through QR codes and streaming sats can extend beyond taxi services to other modes of transportation, such as buses. The idea is to calculate the average cost per mile (or meter/foot) for providing the transportation service, including factors like fuel, maintenance, and driver salary, and add a margin for profit. Passengers entering the vehicle scan a QR code, and the app dynamically adjusts the streaming payments based on the number of people on board.
For buses, this model allows for real-time adjustment of streaming payments as passengers enter and exit. If there are 30 people on the bus the split is between them. At the next stop, 10 people are dropped off and 5 people get on board - now the sats stream is divided by 25 people. As the number of people on the bus changes at each stop, the streaming sats are proportionally divided among the passengers. This approach can lead to more efficient and flexible city transportation. Late-night buses will be more expensive for the passengers because of the fewer riders, while buses during peak hours may offer a more cost-effective traveling experience as payments are shared among more passengers.
This system encourages transportation optimization around events, such as concerts or sports games, where private buses or minivans wait to fill up before departing. Routes can be dynamically adjusted because you will have a system tracking how many people are in the vehicles at what time and at what location on the map. Importantly, this data remains anonymous, as no KYC information is required for the Lightning Network payments.
The Streamlined Pay-from-a-distance
Now with this streaming money feature, it can be applied differently. Let’s go back to the taxi service for a moment. The pay-from-a-distance feature that is available in the Lightning Network can significantly enhance the experience of ordering a taxi. Instead of the traditional model where drivers wait patiently and charge fixed fees when passengers enter the car, this model introduces streaming sats from the moment the passenger accepts the ride. Here's how it works:
- The passenger places an order in the app, specifying the destination. Nothing new here.
- Drivers see the order and can apply for it, similar to platforms like Uber.
- Streaming sats start the moment the passenger accepts the driver, and streaming payments commence. This fee will be less than the actual transportation but the user is still paying for the service of the car coming to him and not the other way around.
- The taxi arrives at the passenger's door, and the streaming payments continue. There is a fee for waiting at the door per minute.
By shifting the waiting cost to the passenger, there's a strong incentive for both parties to be prompt, and the system becomes more efficient. Additionally, the passenger's responsibility to follow the car reduces operational costs related to alerting passengers via message or a call. Any inefficient time management becomes a cost for the passenger. This model aligns incentives for both drivers and passengers, creating a more seamless cost and time-effective taxi experience.
The concept of paying from a distance can be creatively applied to various scenarios, providing convenience and peace of mind. For instance, when it comes to sending your child somewhere with a taxi, traditional concerns about trusting them with money or the driver's reliability may arise. However, with the ability to stream sats for the ride, you gain real-time visibility on your device, tracking your child's journey and ensuring they reach the intended destination safely. This pay-from-a-distance feature extends beyond transportation and can be applied to other continuous services. For example, daycare services charge per minute, allowing you to stream payments in real-time, ensuring accurate and fair compensation for the duration your child spends there. Additionally, you can send a present to a friend, such as a massage session, and pay for it in a streaming fashion, covering the cost continuously based on the duration of the service. The flexibility of streaming payments not only offers real-time tracking and control but also opens up new possibilities for various services where charging per minute or duration is relevant. Those services can be paid on the spot or from a distance. image2
I know that now it looks like we are going backwards from the original point of never paying money for time. The key distinction here is that you may be paying for time past for the service but in that time you get a continuous stream of value (work done) so you are streaming value back to pay for it. In some cases the time spent is actually an accurate measure of the work done.
It's true that developing apps with such functionalities is technically feasible, and there might be entrepreneurs and developers willing to explore these possibilities. However, a significant challenge arises when considering custodial control over users' funds. Small startups might find it financially burdensome and complex to operate as custodians, potentially steering away from such responsibilities. This will take not only high responsibility but also a very big financial wall and expertise to obtain the licenses that comply with the ever-changing regulations. On the other hand, large tech companies with substantial resources could afford to take on the role of custodians, presenting both a business opportunity for them and a risk for the users. The move by some tech giants, like X(formerly Twitter), to obtain such licenses can be seen as a strategic measure for self-preservation over their own finances. This is also an opportunity to consolidate control over not only user data but user finances within their platforms.
The Breez SDK offers a powerful solution, empowering developers to create diverse applications without having to worry about payment intricacies. Its non-custodial nature is a key advantage, eliminating the need for licenses. The infrastructure of it is made in such a way that it is peer-to-peer so no one is holding money for someone else. The app developers focus on the experience within the app and just plug in the code. This combination of features gives startups a competitive edge and reverses the advantage held by large tech companies. While they go through the complex process of getting a license the startup can integrate the global payment network (the Lightning Network) in one day. Even if certain tech giants choose to lock users' funds within their applications, alternative options will continue to be developed, and users will have the freedom to opt-out. Just like people are choosing Bitcoin over fiat.
Now who is ready to give all of us those experiences in their app?
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ b804f68e:2fb0fa1f
2024-05-20 06:07:22
@ b804f68e:2fb0fa1f
2024-05-20 06:07:22Consistently writing on SN and Obsidian has underscored for me the critical role of application in the learning process. Writing allows me to visually process, reflect, analyze, and organize the myriad ideas generated within my brain. Through this ongoing practice, I can physically sense my improvement in articulating thoughts to others and myself, both in writing and speech. However, both forms of expression still require significant practice, especially the latter.
Before I began writing regularly, I didn't fully appreciate the importance of purposeful learning. Previously, I viewed reading a book, watching an educational video, or listening to a podcast as the primary components of learning. But these activities are merely the initial stimuli that prepare our brains for deeper engagement, much like a warm-up before a workout. True learning extends beyond passive consumption; it involves actively practicing and applying what we've learned, reflecting on our experiences, and continually revisiting the material to fill in gaps and deepen our understanding. Sharing and discussing our insights with others further enriches this process, as it exposes us to diverse perspectives and feedback we might not have considered on our own. For me, writing acts as the bridge that connects acquired knowledge to practical application.
After writing on SN consistently for over a month, I've come to realize what it truly means to learn and acquire knowledge. Writing daily has exposed gaps in my understanding, often revealing that I lack the depth of knowledge I assumed I had. When I reach the limits of what I know, I'm compelled to research further, which reinforces and expands my comprehension.
Even if you never write publicly, I believe everyone can benefit from the act of writing. The more I write, the more intentional my learning process becomes, and the more organized and structured my thoughts are.
-
 @ f1989a96:bcaaf2c1
2025-01-23 14:40:18
@ f1989a96:bcaaf2c1
2025-01-23 14:40:18Good morning, readers!
In Iran, officials are accused of exploiting a recent currency devaluation to profit at the public’s expense. The regime raised the rial’s official exchange rate from 550,000 to 640,000 per dollar to maximize its profit when selling the $5 billion it had withdrawn from the National Development Fund. This move effectively stole one quadrillion rials ($23 billion) from citizens, fueling inflation and devastating the public’s already-slim purchasing power.
In Nicaragua, dictator Daniel Ortega dissolved 15 more nonprofit organizations since the start of the year. This brings the total to more than 5,400 NGOs shut down since 2018. Ortega frequently uses financial repression to wield power over citizens, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle civil society groups.
In open-source software news, Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, a new home mining device designed for individuals to mine Bitcoin. It features a touch screen that displays mining metrics, network data, and Bitcoin news. Innovations like this help democratize access to mining and strengthen the overall Bitcoin network, making an especially big difference for people who wish to mine in difficult political environments. \ \ Meanwhile, Bitcoin developers are exploring rewarding mining pool participants with ecash shares. This model lets miners receive earnings instantly and trade them on open markets without revealing personal details. This could make mining more attractive for dissidents whilst helping strengthen Bitcoin’s overall decentralization.
Finally, we feature the release of Evan Mawarire’s book “Crazy Epic Courage,” in which the Zimbabwean pastor and activist recounts his inspiring journey of a peaceful uprising against Robert Mugabe’s dictatorship and hyperinflation. We also include a Bitkey wallet tutorial from renowned Bitcoin educator Ben Perrin, aka BTC Sessions, who walks users through setting up cold storage and best practices for safe transactions.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Iran | Regime Profiting From Currency Devaluation
In Iran, Hossein Samsami, a member of the parliament’s economic committee, accused the government of exploiting foreign currency exchange rates to profit at the expense of ordinary citizens. The regime recently increased the rial’s official exchange rate from 550,000 to 640,000 rial per dollar — a move Samsami explained “was to sell the $5 billion it had taken from the National Development Fund at the highest price.” By manipulating the exchange rate, the regime effectively stole one quadrillion rials ($23 billion) from citizens. This deliberate devaluation will drive up inflation, deplete savings, and push basic goods further out of reach. Iran’s multi-tiered exchange rate system has long fueled corruption, allowing regime insiders to profit from the gap between the artificially low official exchange rate and the higher free-market rate. To block any financial escape, the regime has tried to close onramps to Bitcoin.
Nicaragua | Regime Dismantles More Nonprofit Organizations
Since the start of 2025, the Nicaraguan regime dissolved an additional 15 nonprofit organizations (NGOs), including Save the Children and the Dominican Nuns Foundation of Nicaragua. This latest wave of repression brings the total to more than 5,400 NGOs shut down since 2018 under dictator Daniel Ortega. Ortega uses financial repression as a weapon, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle these groups. Deprived of resources and funding, these organizations are forced to close, leaving vulnerable communities without aid. These crackdowns come as part of Ortega’s broader strategy to stifle dissent, dismantle civil society, and consolidate his grip on Nicaragua.
Nigeria | Political and Bitcoin Activist Faces Regime Censorship
James Otudor, an activist and founder of Bitcoin Calabar, a Nigerian Bitcoin circular economy, described what he believes is a deliberate campaign to silence his Bitcoin advocacy. After filing a lawsuit against the Nigerian regime to defend citizens’ rights to own, use, and trade Bitcoin, Otudor was interrogated by the Department of State Security (DSS) about his funding sources and financial activities. Despite providing proof of legitimate earnings, he reports facing a series of suspicious and coordinated attacks — including the theft of his lawyers’ documents, the suspension of his social media accounts, and disruptions to his phone and internet services. These actions represent the extent to which authoritarian regimes like Nigeria will go to block financial tools that operate beyond their control.
United Arab Emirates | AI Ambitions and Authoritarian Control
The United Arab Emirates (UAE) is accelerating its bid to lead the global artificial intelligence race, with reports suggesting that intelligence chief Sheikh Tahnoun is in talks with the United States to acquire NVIDIA’s proprietary AI chips. At the center of this push is G42, an AI conglomerate heavily invested in data analytics, satellite imagery, and predictive surveillance. These technologies enable the UAE to expand domestic surveillance and control to suppress dissent with unprecedented precision. As an authoritarian regime with an appalling human rights record, the UAE has long used technology to surveil activists, journalists, and civil society. Now, it aims to take surveillance and repression to new heights.
Uganda | Civic Group Calls for the End of Trials of Civilians in Military Courts
On Wednesday, Jan. 15, Agora Discourse, a civic group co-founded by activist and Oslo Freedom Forum speaker Agather Atuhaire, launched a Change petition calling for the end of trials of civilians in military courts in Uganda. The next day, police officers harassed and roughed up Agather Atuhaire as she delivered a physical copy of the petition, addressed to Chief Justice Owinyi Dollo, at Uganda’s Supreme Court in the capital, Kampala. Alongside this physical repression, Uganda employs financial repression — freezing the bank accounts of civil society organizations to diminish civilian voices and their right to association and organization. This petition aims to rally international pressure against the regime’s practice of using military courts to target dissidents. If you have a moment, please consider reviewing and signing the petition here.
RECOMMENDED CONTENT
“Crazy Epic Courage” by Evan Mawarire
Zimbabwean pastor and activist Evan Mawarire never set out to become a revolutionary — he simply wanted to speak the truth. But when a video of him draped in a Zimbabwean flag went viral, it ignited a nationwide movement that would challenge Robert Mugabe, one of Africa’s longest-standing autocrats and a thief who looted Zimbabwean wealth via hyperinflation. In his newly released book, “Crazy Epic Courage,” Mawarire details how an ordinary citizen can become the voice of a nation. From arrests and exile to global advocacy, his journey is a testament to risking everything for what is right. Read the full book here.
BITCOIN AND FREEDOM TECH NEWS
This week’s Bitcoin news focuses on Bitcoin mining updates. To learn more about Bitcoin mining, we recommend checking out this explainer article and video.
Mostro | Implements Key Management to Boost Privacy
Mostro, a peer-to-peer (P2P) Bitcoin exchange built on Nostr, introduced advanced key management to improve user privacy. Created by Venezuelan developer Francisco Calderon, Mostro — specifically designed to aid people under tyranny — enables individuals to buy and sell Bitcoin without sharing excessive personal information. This adds another layer of privacy critical for human rights defenders, journalists, and nonprofits operating under authoritarian regimes. As a past recipient of HRF’s Bitcoin Development Fund, Mostro continues to advance private Bitcoin access for those who need it most.
Bitcoin Safe | New Bitcoin Wallet Designed for Non-Technical Users
Bitcoin Safe is a new open-source Bitcoin wallet designed to make self-custody simple even for non-technical users, something that really comes in handy for human rights activists. The wallet guides users through the setup process, with step-by-step instructions for both single-signature (where one private key is used to control your Bitcoin) and multi-signature wallets (which require multiple private keys for added security). Bitcoin Safe also includes features to manage Bitcoin efficiently, such as automatically combining unused Bitcoin (known as Unspent Transaction Outputs or UTXOs), speeding up stuck transactions with fees (known as Replace-By-Fee or RBF), and letting users choose specific coins to spend. With support for more than 10 languages, Bitcoin Safe can lower the barriers to self-custody.
Solo Satoshi | Introduces Bitaxe Touch
Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, the first Bitcoin home miner with a built-in touchscreen. Scheduled for release in early 2025, the device enables users to monitor key metrics, including Bitcoin’s price, mining performance, power consumption, incoming transactions, and real-time temperature data. It also features a Bitcoin news feed, offering a comprehensive overview of the mining experience. Built using an open-source Bitaxe 601 Gamma, the Bitaxe Touch is designed to simplify Bitcoin mining for individuals. By empowering more people to mine Bitcoin independently, devices like this reduce reliance on large mining pools, strengthening Bitcoin’s decentralization and resistance to censorship.
Mining Pools | Rewarding Miners with Tradeable Ecash Shares
Bitcoin developers are exploring a new way to reward miners using tradeable “ecash shares.” In Bitcoin mining, individuals often join “mining pools” — groups of Bitcoin miners that work together to verify transactions, solve blocks, and share rewards. They do so because pooling resources increases their chances of earning Bitcoin. However, miners in these pools can wait days or weeks for payouts (depending on the pools’ payout structure), and miners often suffer violations of their privacy. With ecash shares, miners could receive their earnings immediately and sell them on an open market (without having to reveal their identity, shielding them from a dictator’s watchful eye). This system could also make it easier for small mining pools to get started and grow. Smaller pools often struggle to attract miners because payouts are uncertain. By using ecash shares, these smaller pools could temporarily operate as clients of larger ones to ensure steady income in the early stages.
F2Pool | Monitoring Global Censorship Risks
Bitcoin developer b10c revealed that F2Pool, one of Bitcoin’s largest mining pools, may be filtering transactions. Over the past weeks, b10c’s miningpool-observer detected 15 transactions from certain addresses that were not mined in the first eligible block. While all transactions were eventually confirmed — proving the Bitcoin network’s overall censorship resistance — F2Pool appears to have excluded some despite negligible fee differences, raising concerns of potential censorship. Notably, no other pools filtered these transactions, revealing the strength of this decentralized software network. However, these observations warrant ongoing monitoring so that the public understands such risks before they metastasize.
Mi Primer Bitcoin | Releases 2025 Bitcoin Diploma
Mi Primer Bitcoin, a nonprofit advancing open-source Bitcoin education, released its updated 2025 Bitcoin Diploma. This 176-page open-source workbook serves as a 10-week educational program and is used by more than 56 projects in 30 countries. The diploma covers topics like the history of money, Bitcoin’s technical and practical applications, and its implication for financial freedom and human rights. The latest edition features enhanced infographics and refined content for improved clarity. Available in multiple languages, the Bitcoin Diploma is a powerful resource for fostering financial literacy and global Bitcoin adoption and is taught by civil society groups even under dictatorships like the one in Cuba.
RECOMMENDED CONTENT
Bitkey Wallet Tutorial by BTC Sessions
In this tutorial, renowned Bitcoin educator Ben Perrin (BTC Sessions) demonstrates how to set up and use the Bitkey hardware wallet on a mobile device. He guides viewers through the process of storing, sending, and receiving Bitcoin, with a focus on user-friendliness and secure practices. He also reveals secret techniques to make the most out of one’s hardware wallet. Don’t miss the full tutorial — watch it here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 93eeb56c:9469e39a
2025-01-22 17:08:44
@ 93eeb56c:9469e39a
2025-01-22 17:08:44💀 Introducing No Good Kid
After 15 years of working as a graphic designer, marketer, and brand therapist, I recently started to feel the urgency to start a project of my own.
I feel out of tune with the state of mainstream marketing today—sterile aesthetics, overstated presentations, and endless battle for attention on centralized social media.
So, I’m introducing No Good Kid. And as you can guess from the title, No Good Kid targets both creators and audiences who don’t exactly fit the status quo.
No Good Kid is the creative’s alter ego. It’s an identity that can be shared and serves as a label under which we can collaborate to create cool projects.
🪩 What is it?
I think of it as an identity—the creative’s alter ego, if you will—that can be shared among creators and serve as a label under which we can collaborate and create.
And the result can be anything, from a marketing campaign to original music production. There are no borders. If the party is right, anything can happen.
In the spirit of gamma personalities, there will be no agency, leader, or hierarchy.
My hope is that the projects will reflect values such as freedom and solidarity. But it’s entirely up to the creators.
Feel free to use the No Good Kid identity, share your project, or reach out if I can help.
🔥 Projects released so far

whistleblower10
In 2024, I crafted a campaign for Amnesty International CZ which led to Amnesty accepting Bitcoin donations for a limited time.
whistleblower10 website→\ project design→

The Nocoiner Syndrome
By the end of last year, The Nocoiner Syndrome was published by Institute of Cryptoanarchy—a research paper written by Peter Horváth that rebutted the ECB’s statement about Bitcoin being on “the road to irrelevance.”
Institute of Cryptoanarchy website→\ project design→
☮️ Vision
There is no need to place a label on this project. I want No Good Kid to be a tool to connect beliefs and hopes with skills in the name of freedom.
Let me know what you think of the idea, or if you have a project in mind.
Be well, and stay no good.
dworis 💀
🥁 Follow No Good Kid:
https://nogoodkid.com/ npub1j0ht2m9jgs6mccyvkffd2dlnfusmqfx9mjlwg6fsmfwxm9rfuwdq40w6rf npub1uwglfjet0m2regqhmgeygc2tc75ngezl8fhftgzhaqas9rjeny8sdztml4
---
🔥 Thanks for reading
Enjoyed this article?
⚡️ Zap some sats
literalpersian75(at)walletofsatoshi.com💀 No Good Kid projects & portfolio
https://nogoodkid.com/👥 Let’s connect on Nostr
npub1j0ht2m9jgs6mccyvkffd2dlnfusmqfx9mjlwg6fsmfwxm9rfuwdq40w6rf -
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-22 16:20:47
@ 5d4b6c8d:8a1c1ee3
2025-01-22 16:20:47I just completed my 5th steps challenge on Workit (only available on iOS, sorry).
This challenge was 10k steps every day for two weeks. Of course, these were the coldest two weeks of the year, so many of those steps were indoors.
The buy-in/stake was 25k sats and the payout was 28,608, which was a little less than I expected. I don't think the winners of the bonus rewards have been announced yet, so there may still be another 40k coming my way (but, probably not).
So far, I've netted over 50k on these challenges. What a great way to stay healthy, while stacking sats.
originally posted at https://stacker.news/items/860122
-
 @ ec965405:63996966
2024-05-18 18:02:00
@ ec965405:63996966
2024-05-18 18:02:00Re #introductions
For the next couple of months, the team at nos.social, led by @Rabble@nos.social, is supporting me in building engaging social media for my community with their new Nostr client. I'm an activist who is dedicating this season of my life to learning how computers and the Internet work. After stumbling across Nostr last year in search of better social media experiences, I entered a blogging contest with https://nostr.build and won a creator account. My interest and enthusiasm for this protocol has only grown.
RE #introducciones
Durante los próximos meses, el equipo de nos.social, liderado por Rabble@nos.social, me ayudará a crear una experiencia atractiva para mi comunidad con su nuevo cliente de Nostr. Soy un activisa dedicado a aprender cómo funcionan las computadoras y el Internet. Despues de encontrar a Nostr el año pasado en la busqueda de mejores experiencias en las redes sociales, participé en un concurso de blogs con [[nostr.build]] y gané una cuenta de creador. Mi interés y entusiasmo por este protocolo no ha hecho más que aumentar.
Liberation Tech
The world is having a moment right now. Social media is evolving into a tool for collective liberation. It couldn't have come at a better time. We have an opportunity to reconstruct a digital public commons. Tools like Nostr are blueprints for building resilient social media and represent a rejection of the factory of manufactured consent that defines our current political realities. A liberated fifth estate built on open protocols could channel people power into material improvements within our lifetimes. We are not going back to the way things used to be.
Tecnología de Liberación
Actualmente estamos viviendo un momento critical. Las redes sociales se estan evolucionando hacia una herramienta para nuestra liberación colectiva. No podría haber llegado en mejor momento. Tenemos una oportunidad de reconstruir la plaza digital del pueblo. Herramientas como Nostr son modelos para construir redes sociales resistentes y representan un rechazo a la fábrica de consentimiento manufacturado que define nuestras realidades políticas actuales. Un quinto estado liberado, basado en protocolos abiertas podría canalizar el poder del pueblo hacia un cambio material en el transcurso de nuestras vidas.
Explore my Asteroid
I host my main web page from an asteroid with Uberspace, a small team of supportive technologists who provide an affordable Linux server that runs on renewable energy. On it I run a personal relay for on-boarding my community to Nostr as well as learning to code. Find resources and more about what I'm working on at https://miguelalmodo.com.
Explora mi asteroide.
Mi pagina web principal se encuentra en un asteroide con Uberspace, un equipo chiquito de tecnólogos solidarios que ofrecen un servidor Linux barata que funciona con energía renovable. En él, gestiono un relevo personal para incorporar a mi comunidad a Nostr, además de aprender a programar. Encuentra rescursos y mas sobre lo que estoy creando en https://miguelalmodo.com
-
 @ 3efdaebb:3e0d2681
2025-01-22 01:08:58
@ 3efdaebb:3e0d2681
2025-01-22 01:08:58Hey Nostr! It’s App Store release day for Damus. Thanks again to our loyal Purple subscribers for helping us continue to improve the UX and pointing out important changes and fixes. Highlights of Version 1.12:
Added
- Render Gif and video files while composing posts (Swift Coder)
- Add profile info text in stretchable banner with follow button (Swift Coder)
- Paste Gif image similar to jpeg and png files (Swift Coder)
Changed
- Improved UX around the label for searching words (Daniel D’Aquino)
- Improved accessibility support on some elements (Daniel D’Aquino)
Fixed
- Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino)
- Fix non scrollable wallet screen (Swift Coder)
- Fixed suggested users category titles to be localizable (Terry Yiu)
- Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu)
- Fixed right-to-left localization issues (Terry Yiu)
- Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu)
- Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu)
- Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino)
- Fixed non-breaking spaces in localized strings (Terry Yiu)
- Fixed localization issue on Add mute item button (Terry Yiu)
- Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu)
- Fixed localization issues in RelayConfigView (Terry Yiu)
- Fix duplicate uploads (Swift Coder)
- Remove duplicate pubkey from Follow Suggestion list (Swift Coder)
- Fix Page control indicator (Swift Coder)
- Fix damus sharing issues (Swift Coder)
- Fixed issue where banner edit button is unclickable (Daniel D’Aquino)
- Handle empty notification pages by displaying suitable text (Swift Coder)
-
 @ 76c71aae:3e29cafa
2024-05-16 04:48:42
@ 76c71aae:3e29cafa
2024-05-16 04:48:42The Curious Case of DSNP: Years of Effort, Minimal Output
It's been a while since I looked at DSNP. There’s news that its backer, Frank McCourt, is trying to put together a team to buy TikTok. That’s insane. The DSNP and Project Liberty team are well-meaning, but they’re even less equipped to run a social network or protocol than Elon Musk at his lowest point when he was firing engineers based on how many lines of code they’d written.
To check what’s happened with DSNP since I last looked a year ago, I just read the entire spec, and there's not actually that much to it. The amount of time and money spent on developing so little is quite stunning. While the spec is fine, it is minimal.
Key Features and Odd Choices
DSNP allows users to have a key pair, write content into a datastore, follow people, and sign messages. However, the protocol seems to mix up layers, specifying the wire protocol, signing system, and at-rest specification format that clients and user data servers might use (pds in atproto, instance in fedi, relay in nostr). They use the ActivityStreams 2.0 schema, which is a good choice. Many new protocols have created their own schemas, but I appreciate DSNP's use of the standard. I wish more protocols had not tried to reinvent the wheel in this respect.
Encrypted Direct Messages and Metadata Privacy
There’s mention in the whitepaper about encrypted direct messages, suggesting it’s possible to hide metadata using techniques from Ethereum’s Whisper. Although the specs or code about DMs don't elaborate much on this, it’s good to see an attempt to hide metadata. However, there’s nothing about double ratchet encryption, forward secrecy, or any advanced encryption techniques. So, overall, it feels quite basic.
Data Storage and Interesting Choices
For storing user data and posts, they're using Apache Parquet, a file format from Hadoop. This is probably the only neat or interesting aspect. I've been searching for a supported data format like Parquet for a while because I think it can facilitate privacy-preserving contact discovery, so it’s cool to see its inclusion here.
Minimal Data Types and Following Options
DSNP supports very minimal data types: post, follow, reaction, profile, and, oddly, location. You can follow publicly or privately, the latter being a neat feature that Scuttlebutt had but most of the current generation of emerging social protocols don't.
Lack of Comprehensive Features
There does not appear to be any client app or server code, which might not be needed. There is an SDK for some core functions, but that’s it. Their documentation lacks information on user discovery, algorithms, or anything beyond the basics.
The Verdict: A First Draft After Years of Work
It feels like someone spent millions and ended up with a naive first draft, despite working on this for years. It’s similar to the early sketches of Farcaster and Lens, but those protocols have grown significantly over the past couple of years, with real users, lots of functionality, and apps.
DSNP remains as vaporware today as it was four years ago. These clowns have wasted tens of millions of dollars on nothing. Some academics have happily taken the money to fund their research labs. Consultants have written and thrown away countless prototypes nobody’s ever used.
There are lots of serious projects to build decentralized social media protocols. All these folks had to do was either work with others or even copy them. This stuff is all open source. Yet DSNP keeps sending folks to conferences without talking to anybody or attending any talks.
It’s a shame because they’ve got their hearts in the right place. The Unfinished conferences are really well put together with lots of great speakers. They hired the supremely talented and savvy Karl Fogel and James Vasile to help them make their code and process open, but you can’t fix DSNP.
Fundamentally, software and specs are a social enterprise, even more so if you’re working on social protocols. But these folks… they’ve never figured out how to play well with others. The money and good intentions couldn’t overcome their fundamental failure to have the humility to learn and play well with others.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 16d11430:61640947
2025-01-21 20:40:22
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
- Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
- Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
- Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
- Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
- Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
- Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
- Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
- Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-
 @ cff1720e:15c7e2b2
2025-01-21 19:28:49
@ cff1720e:15c7e2b2
2025-01-21 19:28:49Introduction
The aim of ELI5 (explain me like I'm 5) is to explain difficult things simply. This is urgently needed in our high-tech world, because only by understanding the technologies can we use them properly and develop them further.
I'm starting my series with Nostr, a relatively new internet protocol. What the hell is an Internet protocol? In formal terms, it is an international standard that has ensured that the Internet has been working pretty well for over 30 years. It is the language in which computers communicate with each other and which you also use every day, probably without realizing it. http(s) transports your request to a server (e.g. Amazon), and html ensures that a nice page is created on your screen from the data supplied. A mail is sent to the mail server with smtp and retrieved from it with imap, and since everyone uses the standard, this works with every app on every operating system and with every mail provider.
And with an e-mail address like roland@pareto.space, you can even move at any time, no matter where. Cool, that's state of the art! But why doesn't this work with chat, for example, is there no protocol? Yes, it's called IRC (Internet Relay Chat → remember the name), but it's hardly ever used. The reasons for this are not technical, but rather apps such as Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok and others have deliberately created incompatibilities and user dependencies in order to maximize profits.

Since the standard protocol is not used, each app has its own, and we need a handful of apps to exchange information with everyone we know. A mobile phone number is a prerequisite for every account, allowing app manufacturers to track users comprehensively and earn up to USD 30 per account per month by selling the information. The user is no longer the customer, he is the product! Advertising SPAM is the least of the problems with this business model. Servers with millions of user data are a “honey pot”, so they are often hacked and the access data sold. In 2024, the Twitter account of then President Joe Biden was also hacked and no one knew who had written the messages (nor did they before), meaning that the authenticity of the content is not guaranteed with any of these providers. In the same year, the founder of Telegram was taken into custody in France because he refused to build backdoors into his software. Now, to protect “our democracy”, practically anyone can read what information they exchange with whom, e.g. which shampoo certain politicians use.

Why Nostr?
And anyone who actually believes they can practice freedom of expression on social media will quickly find themselves in the situation of Donald Trump (who was president at the time), whose Twitter account was shut down in 2021 (cancel culture). The user data, i.e. their profile, contacts, documents, images, videos and audio files - no longer belong to them anyway but are the property of the platform operator; read the terms and conditions. But no, not a good idea, there are hundreds of pages and they are constantly being changed. So everyone uses apps whose technology they don't understand, whose rules they don't know, where they have no rights and which steal the results of their actions. What would the five-year-old say if his older sister offered to “manage” all his toys and then hand them over if he was good? “You must be crazy”, and with that the toddler proves he has more sense than the majority of adults.
Conclusion: no standards, no data, no rights = no future!

How does Nostr work?
The developers of Nostr realized that the server-client concept had turned into a master-slave concept. The master is synonymous with centralization and becomes the “single point of failure”, which inevitably makes systems dysfunctional. In a distributed peer2peer system, there are no longer any masters but only equal nodes (relays) on which the information is stored. By storing information redundantly on several relays, the system is more resilient in every respect. It is not only nature that has successfully used this principle for millions of years, the Internet was also designed in this way (the ARPAnet was developed by the US military for use in war situations with massive disruptions). All nostr data is stored on relays and the user can choose between public (usually free) and private relays, e.g. for closed groups or for the purpose of data archiving. As documents are stored on several relays, unique document names (URIs = identifiers) are used instead of URLs (locators), making broken links a thing of the past, as are deletions / losses.
Each document (called an event) is signed by the owner, making it authentic and tamper-proof and can only be deleted by the creator. A key pair consisting of a private (nsec) and public key (npub) is used for this, as known from mail encryption (PGP). This represents a Nostr identity that can be supplemented with a picture, name, bio and a readable Nostr address (e.g. roland@pareto.space ), which is all that is needed to use all the resources of the Nostr ecosystem. And this now consists of over a hundred apps with different focuses, e.g. for personal encrypted messages (DM → OxChat), short messages (Damus, Primal), blog posts (Pareto), meetups (Joinstr), groups (Groups), images (Olas), videos (Amethyst), audio chat (Nostr Nests), audio streams (Tunestr), video streams (Zap.Stream), marketplaces (Shopstr) and much more. Registration is done with a single click (single sign-on) and ALL user data is available to the apps (profile, data, contacts, social graph → followers, bookmarks, comments, etc.), in contrast to the fragmented data silos of the present.
Summary: one open standard, all data, all rights = great future!

Why is Nostr the future of the internet?
“Don't build your house on someone else's property” also applies to the Internet - for all app developers, artists, journalists and users, because their data is also valuable. Nostr guarantees ownership of the data and overcomes its fragmentation. Neither use nor creative freedom is restricted by excessive license and usage conditions. Passive users become active participants through interaction, co-creators in a sharing economy (Value4Value). Open source finally restores trust in software and its providers. Open standards enable developers to cooperate more and develop faster, while guaranteeing freedom of choice for users. Which brings us back to our five-year-old for the last time. Children love Lego more than anything, especially the maxi box “Classic”, because it allows them to live out their imagination to the full in terms of combinations. Adults then give them the far too expensive theme packs, with which you can only build one solution according to the instructions. “What's wrong with my parents, when did they take a wrong turn?” the children rightly ask themselves. But the image can be polished up again if they show their children Nostr, because even five-year-olds understand the advantages.
The new Internet is decentralized. The new Internet is self-determined. Nostr is the new Internet.

\ More infos: https://nostr.net/\ Quick start: https://start.njump.me/
-
 @ 20986fb8:cdac21b3
2024-05-14 04:27:58
@ 20986fb8:cdac21b3
2024-05-14 04:27:58Relay is the soul of the decentralized Nostr network. In previous articles, we discussed who would bear the ongoing operational costs of Relay. To ensure a thriving storage network, Relay needs to be incentivized. In order to achieve better decentralization of media, YakiHonne has launched the Relay's early incentive plan to support the development of 50 Relays for a period of 6 months.

The details of the grant program are as follows:
- Grant amount: A total of $50,000, with each grant ideally being $1000.
- Application period: From May 15, 2024, to December 31, 2024.
- Applicants: Existing Relay node hosts or new hosters, with a funding ratio of 20 existing Relay nodes and 30 new Relay nodes.
Relay operational requirements:
-
The minimum requirements for Relay deployment are according to [1]:
-
1.1. High performance Intel
- 1.2. 1 vCPU
- 1.3. 2048 MB Ram
- 1.4. 50 GB NVMe SSD
-
1.5. OS Ubuntu 22.04 LTS
-
There are no restrictions on storage service providers, and you can choose any stable provider.
-
There are no restrictions on the location of Relays, but it is recommended to have geographical diversity to maintain a balanced distribution of Relays.
- Relays need to operate continuously for the next 6 months with downtime not exceeding 30 minutes.
- You can choose from the already existed relays implementations: nostr-rs-relay based on Rust, nostr-ts-relay akk nostream using Typescript, or strfry using C++.
- Relay models can be of any type: thematic Relays relying on keyword filtering for specific topics, invitation-only Relays that restrict publishing permissions through public keys, or paid and free public Relays corresponding to paid publishing and fully open modes, respectively. However, to maintain a balanced incentive, the proportion of paid and invitation-only Relays will not exceed 20%.
- Monthly reports on Relay stability and availability need to be shared to maintain good operational status.
Application process:
You need to submit a proposal including whether you are already hosting a Relay, the name of the existing Relay, specifications of the Relay hosting service, possible service provider choices, Relay development environment, Relay model, and more details to help you secure funding.
Submission: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Grant Evaluation and Disbursement:
Within one week of receiving the application, we will provide feedback on the grant decision. The grant amount will be disbursed in two installments, with 50% being provided initially and the remaining 50% being disbursed after 3 months.
Rewards:
In the early incentive program, nodes that contribute consistently to improving Relay performance, expanding functionality, and ensuring stability will receive special rewards and have the opportunity to earn more income.
The goal of this incentive program is to further decentralize Nostr, enhance its performance, and promote the development of Relay functionality. Through the early incentive program, we aim to explore sustainable incentive models for Relays and lay the foundation for their sustainable development.
-
 @ 1bc70a01:24f6a411
2024-05-13 09:49:18
@ 1bc70a01:24f6a411
2024-05-13 09:49:18Thought 1: Content Creation, Discovery & Remixing
Recently I’ve been thinking about ways we could highlight nostr’s unique properties while at the same time attracting creators to the platform.
There’s been a lot of discussion about what might spark nostr’s next wave of growth. I pointed out that people come for either other people, or for content. But, I also failed to realize that people also seek ways to express themselves via new tools that enable easy or unique ways of expressing yourself.
One thing we can say with certainty is that people are not coming to nostr for other people. While generally following influencers is a proven growth strategy - after all, many of us followed Jack, we still have a catch 22 problem of lacking audience and incentives for those creators to come here. Even if we managed to convince some large influencers to try the platform, it is not likely that they would stay. They’d need to be really passionate about nostr’s principles and vision to buckle in for the long term.
Problem: creators and influencers won’t come to nostr unless they can grow their audience, and nostr lacks the audience. We’ve seen this play out with Matt Taibi. He joined nostr but was reluctant to stay because there’s little incentive to share with a small audience when Twitter/X can bring in many more eyeballs.
Possible Solution: Instead of brining creators to the platform, enable some of the current passionate user base to become decent creators themselves. We don’t need influencers with giant audiences, we just need good content that keeps people around. If we apply the 80/20 rule (Pareto’s principle), it turns out we don’t need that many creators to have a great flow of content. Enabling just a handful of people to create great content might just do the trick.
How to get there: focus on creating tools that enable expression of creativity. One such tool is Pinstr, but its value is largely untapped. On its own, pinstr is nothing interesting, it’s practically a clone of Pinterest. But, given the interoperable nature of nostr, it would be interesting to see pinned boards / content surfaced within kind 1 clients. People could then explore the board or that user’s other boards further by making their way to Pinstr.
How do we encourage more people to curate interesting pins? How about a pin extension that makes it easy to do so?
How do we enable people remixing other pins? Allow them to re-pin the content to their own boards. These are all mechanics that made Pinterest interesting, but lack in pinstr (as far as I’m aware).
Other ways that we might encourage content creation:
- Multi-account support. Can we make it SUPER easy to switch between identities when posting some curated content? Yes we can. (Select a different identity when posting)
- Surfacing “Other stuff” with a call to action to do that thing. For example, if someone shares a list, a kind 1 client should be able to render that list in a way that’s easy to browse, share and encourages to create your own list. If someone shares a music playlist (hopefully via native nostr kind), a person should be able to see the playlist and be encouraged to create their own. Watch stream? > prompt to start your own
- Gif / meme discovery with a call to action to create your own. (Plebhy, Memester)
- Styling tools (more complex) to style media, add soundtracks etc (perhaps via integration with Wavlake or other nost-native music events).
-
Content scheduling - help existing users become power users. Instead of posting everything at once, allow users to schedule it out for even distribution. Tools like Shipyard enable this already, but having this ability in-client might make it more accessible and useful.
-
Content pinning extensions - bring the outside world to Nostr. How can people 1-click pin content to nostr without having to switch tabs constantly?
-
App discovery - I think this is already in the works, but being able to surface other apps within kind 1 clients would be super interesting.
- Enable surfacing of highlighted content and paid content - with highlights, nudge people to read more of the content if it comes from within one of the nostr clients. With paid content, indicate that it is premium content and encourage creation of premium content “Become a creator” or “Join creator studio”.
- Encourage people to write long-form opinion content. When reading a long form article, perhaps have a call to action to start your own nostr publication. “Publish on Nostr and earn”
- Surface and encourage audio creation - we don’t have a nostr podcast client yet, but if there was one, kind 1 clients could surface that content automatically and encourage people to start their own podcasts, audio diaries, audio chats (nostr nests) or audio stories. Kind 1 clients could surface audio clips with waveforms and subtitles built in, or create a framework by which other developers could create this type of interaction with your kind 1 client. Can users create their own clip playlists from audio content fetched from the nostr podcast app? Why not?
The common objection to all of this might be that “you can already do all of this just by copying links”. Yes, and no. Copying links does share content - albeit in a boring preview way. It does not enable interactivity, nor prompt people to create that type of content. I think this is where nostr could shine.
Thought 2: Interoperability
One of the greatest strengths of nostr is the ability to display events across clients. I think of kind 1 clients as the glue that holds together the “other stuff”. The other stuff apps can be used to create the stuff, and kind 1 can enable discovery of said stuff, while encouraging to visit those tools to create their own.
Traditional social media platforms are encourage to put up walls and discourage leaking of users to other places. The more time a user spends on a website or app, the better for that company. But, with nostr, there’s a virtuous positive loop that does not punish leaking of attention, but instead, rewards it. The more content people create, the more interesting your kind 1 discovery client becomes.
How to get there: It’s going to take a lot of work to integrate the other stuff, but it’s already under way. As a client developer, partner up with other stuff clients to figure out how to best support them. Open up nostrapps.com to see what exists, and how your client can accommodate the surfacing of that stuff with minimal effort (since our resources are so scarce). Tap into product designers to help conceptualize and visualize interactions and growth loops. #nostrdesign is ready to help with this.


Type of content kind 1 clients could surface and create loops for:
- Playlists
- Pin boards (pinstr)
- Audio chats (nost nests, corny chat)
- Highlights (highlighter)
- Payments
- Fundraisers (Heya, Geyser)
- Communities
- Events (Flockstr)
- Streams (zapstream)
- Long form content
- Job posts / boards
- Recipes (zap cooking)
- Lists
- Torrents (Stan)
- News feeds
- Calling functionality
- DMVs
- Podcast clips, playlists
- Audio clips
- Marketplace items (Shopstr, Creatstr, Plebeian Market)
- Paid content (highlighter)
Recap
- Build tools to aid content creation
- Surface “other stuff” in kind 1 clients
- Prompt people to create their own stuff
I’m probably missing a ton, or not thinking of unique experiences that are just under the nose. What am I missing? What other cool interactions could be enabled by nostr’s interoperabilit
-
 @ 7dc16771:70ed704f
2024-05-11 06:01:39
@ 7dc16771:70ed704f
2024-05-11 06:01:39『マーダーボット・ダイアリー』マーサ・ウェルズ著・中原尚哉訳・東京創元社
「マーダーボット」と呼ばれる主人公“弊機”は保険会社に所属する人型警備ユニット。顧客に貸し出される警備システムの「構成機体」でありながら、自分で統制モジュールをハッキングして、“自由”な存在になっている。でも彼がその“自由”を使って行うのは大好きな連続ドラマ『サンクチュアリムーン』を繰り返し繰り返し見ること。――とにかく“弊機”が可愛い! 一人称を“弊機”と訳した訳者さんがすごい! 人間の作ったドラマにどハマりしながら「人間とは付き合いたくない」と思ってる自意識過剰な引きこもりオタbotによる一人称日記形式のSF小説。安倍吉俊さんの表紙イラストも可愛いので是非!
アーケードゲーム・タイポグラフィ ビットマップ書体の世界 (大曲都市・著/グラフィック社)
パックマンのフォントを覚えているでしょうか?
本書は、70〜90年代のアーケードゲーム黄金期に生まれた様々なゲームのために作られた、個性豊かなフォントを取り上げています。 そこはわずか8✕8ピクセルの小さな文字の世界。その中で工夫を凝らされた数百にも及ぶフォントにはひとつとして同じものはなく、視認性と世界観の演出を追求した試行錯誤と進化の歴史を感じることでしょう。
いわゆる8bit風、ピクセルアートがひとつのジャンルとして市民権を得て久しいですが、キャラクターや背景だけではなく、フォントにもこんな奥深い世界があることを感じてほしいと思います。
ネガティブ・ケイパビリティ 答えの出ない事態に耐える力 (帚木蓬生/朝日選書/朝日新聞出版)
本書は、医師たちが「ネガティブ・ケイパビリティ=答えの無い状況を耐える力」を発見するまでの道程からはじまります。以降、それが「医療」、「創作」、「教育」、および平和の源泉たる「寛容」の点から、実践的にも極めて重要である理由を述べています。
本書は読み物として面白いだけでなく、文献の列挙など参考書としても役に立つ様に書かれています。物語作家であり、現役医師でもある帚木氏ならではです。多くの人に一読をお薦めできます。
面白く読め、困難に直面した際に誰もが持つ根源的な力について、理解を助けてくれます。豊富な解説は、現代的な問題を俯瞰する際に、辞書的に参照することもできる一冊です。
王様のプロポーズ 極彩の魔女 (橘公司/富士見ファンタジア文庫)
この物語の始まりは不意に誘 (いざな) われた異世界、目の前で殺されたのは世界最強の魔女。 彼女に託された最後の魔法を受け取り、その犯人に迫っていく。 一見するとシリアスに感じられるストーリーに色を付けるのは主人公の一途さ。一目惚れから始まった彼女への恋愛感情はどこまでも愚直であり、故に周りから奇異の目で見られ滑稽なやり取りが発生することもある。しかし一途であるために犯人が露見した場面で主人公の決意がより重いものとなり、それまでの伏線の美しさが強く感じられる。
「人生が整うマウント大全」著:マウンティングポリス 技術評論社
登頂者(マウンティングピープル)たちの能力バトル開幕ッッ!お前の“普通”で相手を殴れーーーー!
強者は何気無い発言の全てが他者を傷つけていることに向き合え。弱者はマウントの型を取り入れて精神武装を身につけろ。
書籍の半分を占める圧倒的なマウンティング実例で、今日から実践可能な知識をインプット可能。マウンティングする“剛”の技だけではなく、マウンティングを受ける“柔”の技も身につく、全方位に特化した業界トップのハウツー本。
5年間Twitterでマウント警察をし続け、“体系的な学問”としてのマウントフルネスをぶち上げた筆者に涙が止まらない、感動の一冊。
-
 @ 50809a53:e091f164
2025-01-20 22:30:01
@ 50809a53:e091f164
2025-01-20 22:30:01For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video:
https://youtu.be/XRpHIa-2XCE
Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey.
We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/
It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited.
Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of.
I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo.
See: https://obsidian.md/publish
THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL.
Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions.
LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option.
But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to:
- Text
- OPML
- HTML
- and, PNG, for whatever that is worth.
Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here:
https://i.postimg.cc/qMBPDTwr/image.png
This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market.
On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack
So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance.
The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr".
These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion.
With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web.
I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever!
So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution.
So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope.
Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience.
Zim-Wiki is foundational. The user constructs pages, and can then develop them into books.
LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after.
https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF.
I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you!
One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/
On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental.
Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/
You might notice they advertise that "This is the future of bookmarks."
I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/
WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate.
This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note.
WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction.
That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration.
HedgeDoc: https://hedgedoc.org/
I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way:
- A nostr client that allows the cataloguing and management of relays locally.
- A LogSeq alternative with Nostr interoperability.
- HedgeDoc + Nostr is #3 on my list, despite being the easiest option.
Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/
Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..."
Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS:
https://denizaydemir.org/
https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/
https://subconscious.network/
Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy.
About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander.
Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr.
My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/
With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr.
Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian
-
 @ 9d92077c:38d27146
2025-01-20 20:46:31
@ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks.
—-
The Importance of Key Recovery on Nostr
One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation.
While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity.
—-
Proposed Solution: The Excalibur System
The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition.
1. Primary and Secure Keys
Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a
set_secure_keyevent.2. Key Transition Event
Upon detecting a compromise, the user activates the secure key by publishing a
key_transitionevent.This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata.
3. Social Graph Transition
Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data.
Followers are notified of the transition and encouraged to follow the secure key.
4. Unified Identity View
Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity.
Clients display a unified profile view, differentiating old and new events.
5. Seamless Transition for Existing Accounts
Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process.
6. Endless Security Chain
Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new
set_secure_keyevent.This ensures an endless chain of security, preventing future compromises from leaving users vulnerable.
Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently.
7. Insurance Model for Relays
Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations.
Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services.
This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network.
—-
Implementation Framework
Cryptographic Foundations
- The secure key must be pre-announced and linked to the primary key using a signed
set_secure_keyevent. - During key transition, the key_transition event includes a signature proving the association.
Relay Behavior
- Relays index the key_transition event and re-link historical data to the secure key.
- Events from the old key are tagged as "deprecated" but remain accessible.
Client Behavior
- Clients validate the
key_transitionevent and update social graphs automatically. - Followers are notified and prompted to follow the secure key.
- Profiles display both old and new events under a unified identity.
- Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly.
—-
Benefits of Excalibur
Resilience: Users can recover from key compromise without losing their digital identity or network.
Trust: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system.
Sustainability: The insurance premium model incentivizes relay adoption and ensures fair resource allocation.
User-Friendly: Automated transitions reduce the complexity for end users, making Nostr more accessible.
Adaptability: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability.
—-
Call to Action
The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality.
Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
- The secure key must be pre-announced and linked to the primary key using a signed
-
 @ 6b9da920:7841cc6e
2024-05-10 23:07:42
@ 6b9da920:7841cc6e
2024-05-10 23:07:42Here is a simple chart for developers to understand when to "Nostr Native" and when to "Nostr Integrated"
Definition:
Nostr Native: Uses relays as the only network layer and storage layer and business logic is 99%+ client side.
Nostr Integrated: Has in-house solutions and only connects partially to Nostr.
Both categories could be open sourced or close sourced.
| Features | Benefit From Network Effect | Don't benefit from Network Effect | | --- | --- | --- | | Contribute To Network Effect | All in Nostr Native | Recommend Writing to Nostr | | Harm Network Effect| Don't Write to Nostr and could read from Nostr | Should be in-house solution and not write to Nostr |
Category 1
If we think we should be all-in Nostr Native no matter what (like 99%+), we are limiting ourselves to only features that both benefit from Nostr and contribute to Nostr. This is a totally valid proposition as long as developers are consciously aware that they are indeed making a product within this category.
Pretty much all public facing social features fall into this category.
But, there are many products that need features that fall into other 3 categories.
Category 2
For features that benefit from Nostr but harms it, you are basically stealing data from Nostr without contributing back. My advice to is not write to Nostr at all and only read from Nostr if you have to do it, but you should minimize this product design in general.
Pretty much any massivly bot/batch job/pipeline generated data fall into this category. Machine generated data do not necessarily mean spam data. In the data engineering & machine learning world, it's very common to generate intermediate data in data pipelines for downstream analytics. This kind of data is huge and can also be purely textual. Don't write to Nostr relays.
Category 3
Is it even possible to have features that don't benefit from the network effect of Nostr and can contribute to it?
I can't think of any. But if it exists, consider writing to Nostr even if you don't use relays as the primary storage.
Category 4
These are features that don't benefit from Nostr and also harm Nostr if writing to it.
Slack style internal organization communication falls into this category. In fact, we want to actively prevent these features from having network effects because having these data in an open network might reduce their security.
Writing them to Nostr also harms the network because these data, encrypted or not, only have semantic meaning within the organization. Posting them to Nostr reduces the overall signal(value) density of the network.
Outtro
It is very common and almost inevitable for a single product to have both lots of category 1 and lots of category 4 and some % of category 2 & 3.
Using this chart, you will know how to make wise engineering decisions that help your product design instead of harming it and help the network at the same time.
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 6f7db55a:985d8b25
2025-01-19 19:46:30
@ 6f7db55a:985d8b25
2025-01-19 19:46:30This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
-
 @ e70d313e:573808ed
2024-05-10 21:24:41
@ e70d313e:573808ed
2024-05-10 21:24:41Kevin F. Boehnke, Assistant Professor of Anesthesiology, University of Michigan for The Conversation

Cannabis – also known as marijuana – is an ancient medicinal plant with promising new medical applications. Nancy Honey/Image Source via Getty Images The U.S. Drug Enforcement Agency announced in late April 2024 that it plans to ease federal restrictions on cannabis, reclassifying it from a Schedule I drug to the less restricted Schedule III, which includes drugs such as Tylenol with codeine, testosterone and other anabolic steroids. This historic shift signals an acknowledgment of the promising medicinal value of cannabis.
The move comes in tandem with growing interest in the use of psilocybin, the active component in magic mushrooms, for treatment of depression, chronic pain and other conditions. In 2018 and 2019, the U.S. Food and Drug Administration granted a breakthrough therapy designation to psilocybin, meant to expedite drug development given that preliminary studies suggest it may have substantial therapeutic value over currently available therapies for treatment-resistant depression and major depressive disorder.
Both of these developments represent a dramatic change from long-standing federal policy around these substances that has historically criminalized their use and blocked or delayed research efforts into their therapeutic potential.
As an assistant professor of anesthesiology and a pain researcher, I study alternative pain management options, including cannabis and psychedelics.
I also have a personal stake in improving chronic pain treatment: In early 2009 I was diagnosed with fibromyalgia, a condition characterized by widespread pain throughout the body, sleep disturbances and generalized sensory sensitivity.
I see cannabis and psilocybin as promising therapies that can contribute to bridging that need. Given that an estimated 50 million Americans have chronic pain – meaning pain that persists for three months or more – I want to help understand how to effectively use cannabis and psilocybin as potential tools for pain management.
Cannabis versus other pain medications
Cannabis, also known as marijuana, is an ancient medicinal plant. Cannabis-based medicines have been used for at least 5,000 years for applications such as arthritis and pain control during and after surgery.
This use extended through antiquity to modern times, with contemporary cannabis-based medications for treating certain seizure disorders, promoting weight gain for HIV/AIDS-related anorexia and treating nausea during chemotherapy.
As with anything you put in your body, cannabis does have health risks: Driving while high may increase risk of accidents. Some people develop cyclical vomiting, while others develop motivation or dependence problems, especially with heavy use at younger ages.
That said, lethal overdoses from cannabis are almost unheard of. This is remarkable considering that nearly 50 million Americans use it each year.
In contrast, opioids, which are often prescribed for chronic pain, have contributed to hundreds of thousands of overdose deaths over the past few decades. Even common pain medications like nonsteroidal anti-inflammatory drugs, such as ibuprofen, cause tens of thousands of hospitalizations and thousands of deaths each year from gastrointestinal damage.
Furthermore, both opioids and nonopioid pain medications have limited effectiveness for treating chronic pain. Medications used for chronic pain can provide small to moderate pain relief in some people, but many ultimately cause side effects that outweigh any gains.
These safety issues and limited benefit have led many people with chronic pain to try cannabis as a chronic pain treatment alternative. Indeed, in survey studies, my colleagues and I show that people substituted cannabis for pain medications often because cannabis had fewer negative side effects.
However, more rigorous research on cannabis for chronic pain is needed. So far, clinical trials – considered the gold standard – have been short in length and focused on small numbers of people. What’s more, my colleagues and I have shown that these studies employ medications and dosing regimes that are far different from how consumers actually use products from state-licensed cannabis dispensaries. Cannabis also causes recognizable effects such as euphoria, altered perceptions and thinking differently, so it is difficult to conduct double-blind studies.
Despite these challenges, a group of cannabis and pain specialists published a proposed guideline for clinical practice in early 2024 to synthesize existing evidence and help guide clinical practice. This guideline recommended that cannabis products be used when pain is coupled with sleep problems, muscle spasticity and anxiety. These multiple benefits mean that cannabis could potentially help people avoid taking a separate medication for each symptom.
Traditional hurdles to studying cannabis
Since the Controlled Substance Act was passed in 1970, the federal government has designated cannabis as a Schedule I substance, along with other drugs such as heroin and LSD. Possession of these drugs is criminalized, and under the federal definition they have “no currently accepted medical use, with a high potential for abuse.” Because of this designation and the limits placed on drug manufacturing, cannabis is very difficult to study.
State and federal regulatory barriers also delay or prevent studies from being approved and conducted. For example, I can purchase cannabis from state-licensed dispensaries in my hometown of Ann Arbor, Michigan. As a scientist, however, it is very challenging to legally test whether these products help pain.
Reclassifying cannabis as a Schedule III drug has the potential to substantially open up this research landscape and help overcome these barriers.

Psilocybin occurs naturally in many species of fungi, primarily mushrooms. Raphael Rangel / 500px via Getty Images The emerging role of psychedelics
Psychedelics, such as psilocybin-containing mushrooms, occupy an eerily similar scientific and political landscape as cannabis. Used for thousands of years for ceremonial and healing purposes, psilocybin is also classified as a Schedule I drug. It can cause substantial changes in sensory perception, mood and sense of self that can lead to therapeutic benefits. And, like cannabis, psilocybin has minimal risk of lethal overdose.
Clinical trials combining psilocybin with psychotherapy in the weeks before and after taking the drug report substantial improvements in symptoms of psychiatric conditions such as treatment-resistant depression and alcohol use disorder.
Risks are typically psychological. A small number of people report suicidal thoughts or self-harm behaviors after taking psilocybin. Some also experience heightened openness and vulnerability, which can be exploited by therapists and lead to abuse.
There are few published clinical trials of psilocybin therapy for chronic pain, although many are ongoing, including a pilot study for fibromyalgia conducted by our team at the University of Michigan. This treatment may help people develop a healthier relationship with their pain by eliciting greater acceptance of it and decreasing rumination often related to negative thoughts and feelings around pain.
As with cannabis, some states, such as Colorado and Oregon, have decriminalized psilocybin and are building infrastructure to increase accessibility to psilocybin-assisted therapy. One recent analysis suggests that if psychedelics follow a similar legalization pattern to cannabis, the majority of states will legalize psychedelics between 2034 and 2037.
Challenges ahead
These ancient yet relatively “new” treatments offer a unique glimpse into the messy intersection of drugs, medicine and society. The justifiable excitement about cannabis and psilocybin has led to state policies that have increased access for some people, yet federal criminalization and substantial barriers to scientific investigation remain. In the years ahead, I hope to contribute toward pragmatic studies that work within these difficult parameters.
For example, our team developed a coaching intervention to help veterans use commercially available cannabis products to more effectively treat their pain. Coaches emphasize how judicious use can minimize side effects while maximizing benefits. Should our approach work, health care providers and cannabis dispensaries everywhere could use this treatment to help clients in chronic pain.
Approaches like these can supplement more traditional clinical trials to help researchers determine whether these drug classes offer benefit and whether they have comparable or less harm than current treatments. As our society connects to the rich history of healing using these ancient drugs, these proposed changes may offer safer and substantive options for the 50 million Americans living with chronic pain.

This article is from The Conversation, a nonprofit news organization dedicated to sharing knowledge with the public.
Kevin F. Boehnke receives funding from the National Institutes of Health, the State of Michigan Veteran Marijuana Research Program, and has received grants from Tryp Therapeutics and Journey Biosciences. He is affiliated with Doctors for Drug Policy Reform as an unpaid expert. He also has received honoraria for speaking at conferences as well as for participating in a podcast on fibromyalgia from the European Medical Journal funded by Viatris Inc.
-
 @ 97c70a44:ad98e322
2024-05-09 17:25:22
@ 97c70a44:ad98e322
2024-05-09 17:25:22#lastword
A few weeks ago, Mike proposed the addition of a feature to nostr. The content of the proposal itself isn't important, but the resulting conversation illustrated something important about nostr development that I wanted to draw attention to.
If you're interested, you can find the issue here. The idea was basically a tag that disabled comments to a reply, for when you wanted to gracefully exit a conversation that had outlived its usefulness.
While I definitely sympathize with the experience of getting stuck in an unproductive argument and being unable to leave because you have to have the last word, I do think it's better to take responsibility for leaving the conversation, rather than make other people do it for you. You can either outlast your opponent, let them have the last word, or tell them "I don't want to talk about this any more, I'm not going to reply".
This is just my opinion, and it's really not important whether I'm right or not. What was interesting was how Vitor responded:
I am not sure if the NIP review process should consider "what's good for the user" in the discussion. That kind of nanny state thinking is what went wrong with regular social media in the first place.
Permaculture and Ethics
What it sounds like (although I have a hard time believing this is actually his position), is that Vitor is dismissing the relevance of an ethical framework in designing a protocol, preferring to stick to the mechanics of what is being suggested. As Vitor says, "Clients can do whatever they want, of course." This is true, but ignores the question of why a client developer might want to do any particular thing.
In a recent Thank God for Nostr episode, I interviewed Scott Mann of the Permaculture Podcast. When I asked him his opinion on how to manage decentralized protocol design and build effective consensus, here's what he had to say:
[You] don't need to frame it as a software development project, or even a protocol. I would look at it as a distributed community-based and community-supported project, whatever that is. Because permaculture is such a large umbrella, I like to go up to that 50,000 foot view and pull away from what the details are. Because the details are what we're going to build our solutions from.
And that's one of the things I didn't mention earlier — there's kind of a hierarchy within permaculture that goes, at the top are the ethics of permaculture: earth care, people care, fair share. Beneath that are the principles, then usually we have strategies and techniques.
But there's a dividing line between ethics and principles and the strategies and techniques, that we start at that top, and use the ethics to decide whether or not we're even going to launch a project.
He goes on to say:
I'm going to use the principles and see how can I apply those principles to my research and original design. To make sure that whatever I'm creating creates some kind of a surplus, to have a refinement process in place before I even launch, like what is that going to look like, even if I have to change it later, just having some of these building blocks in place.
And then once I've done that and have gone deep into my research into what this might look like, how I might launch it, that's where I would start going into strategies and going ok, how do I want to market this? How do I want to get this out to the people who are going to use it, how do I want to maintain this, how do I want to do distributed decision making, and then as I start to think about distributed decision making, looking at what is the form that I want to use for that?
Scott's thesis is that ethics and principles should be in the front of your mind both as you're considering a project, and as you continue to build it out. This not only makes sense as something to do if you want to succeed, it's categorically true. Action can't happen without agency, and it is your agency that informs what you choose to do, and how you plan to go about it.
The word "ethics" comes from the Greek ēthos, meaning "moral character". In other words, your ethic is who you are. Your values, hopes, preferences, faults all factor in to your actions.
This is not always clear, because in fiat-world, many people suspend their values in order to "get something done". If you want to protect your savings, you invest it in index funds, propping up the stock price of companies that hate you. If you want to make money, you go work at a job where you're berated quarterly for being racist. People think that they can exercise their own values in their private life, while actively undermining those values with the majority of their time and purchasing power.
But this is not how people with integrity act. And I think if you can say one thing about nostr — both its developers and the community at large — is that they have a very high level of integrity. In other words, their actions are clearly informed by their ēthos.
This is a very good thing. What is the point of building an entirely new internet if we're not going to impose our values upon it? What an absolute waste of effort.
A Nostr Manifesto
This is not to say that any one developer has the right to imposing his own vision on the protocol because of his own personal values and reasons for contributing, which is what I think Vitor was being cautious about. But there are lines I think we can draw as a community that can't really be crossed without excluding yourself from what I might call the "nostr group ethic".
So what are those boundaries? What is a nostrich? Here are some values I've observed to be generally shared among nostr developers and users. Not everyone would full agree with these (including myself), but I think they're a fair characterization of the community.
- Free speech absolutism. No central entity should be able to globally censor any content. This comes with the trade-off of objectively evil content continuing to exist. This trade-off is acceptable, both because of the value of free speech, but also because evil will continue to exist regardless of attempts to suppress it.
- Empower individuals over institutions. No centralized entity can be trusted to safeguard the interests of the individual. Institutional incentives are asymmetric and easily corrupted. Better to have many subjective views of the world, than a single, centrally managed view of the world.
- Advertising-based business models should be viewed with great skepticism and caution. Advertising is a system of incentives that is central to the institutional corruption we see around us. Broadly, this includes paid ads, monetization of engagement, public/private partnerships, and "crypto".
There are others that are shared by many within nostr, although not as widely agreed upon. Two I can think of are:
- Economic activity should be voluntary. Software and content should be free, and creators should be amply rewarded via zaps or other value-for-value models.
- Social media should support real life community and relationships, not detract from them. We should all take time to touch grass.
I'm personally skeptical of the first of these, and strongly in support of the second. Much of my energy as a nostr developer has gone into attempting to subvert and reform traditional patterns of social media to not only support, but also resemble relationships that exist in the analog world God made, and placed us in.
This particular principle is the one at play in the conversation I linked to at the top of this post. My comments weren't an accusation that anyone was acting "unethically" in a universal sense, only that the proposed feature was incompatible with my vision for what nostr should be.
But of course, my vision is not shared by everyone, and the principle of "support real life" is clearly subservient to core ethic #2, which admits the value of a diverse set of opinions about the world. I have no right (or ability) to invalidate anyone else's core principles. But by the same token I'm free to express my own, and attempt to convince other people to share them. This is the basic value proposition of freedom of speech itself.
Ethical Cohesion
I would go further, and say that not only is it permissible to talk about ethical reasons for building one thing or another on nostr, it's essential. By having these conversations we fuse our individual ethics into a shared ethic. By calibrating our moral compasses to point in (roughly) the same direction, we also decrease the friction involved in getting something done.
I think this was a significant part of the idea behind Sovereign Engineering — get a bunch of people in a room together sharing meals and going on hikes, and the work will accelerate! This is also the way a church works. By meeting weekly together we strengthen our shared identity and build one another up through our activity. In fact, this is the basic definition of a community as Scott Mann puts it. In his words, a community can provide:
a series of connections, and a knowledge base, and a skillset that we can't fulfill as an individual, while having a social relationship with people in such a way that we can call on them for help.
So maybe, as I've said before, the real protocol is the friends we made along the way. Disagreement and discussion is a healthy thing for a community to have, and we should never stop asking "why?"
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 97c70a44:ad98e322
2024-05-08 16:52:50
@ 97c70a44:ad98e322
2024-05-08 16:52:50I think there's been an inflection point recently in NIPs that are being proposed. Some examples:
- Products with pubkeys: https://github.com/nostr-protocol/nips/pull/1225
- Shared-ownership events: https://github.com/nostr-protocol/nips/pull/1192 and https://github.com/nostr-protocol/nips/pull/1015
- Spreadsheets: https://github.com/nostr-protocol/nips/pull/1189
- Relational databases: https://github.com/nostr-protocol/nips/pull/1168
- Relay-specific notes: https://github.com/nostr-protocol/nips/pull/1146
- Editable notes: https://github.com/nostr-protocol/nips/pull/1090
- Restricted events: https://github.com/nostr-protocol/nips/pull/1083
- Relay-based access control: https://github.com/nostr-protocol/nips/pull/1030
- Protected events: https://github.com/nostr-protocol/nips/pull/1029
- Closed groups: https://github.com/nostr-protocol/nips/pull/875
Some of these I like, some I don't. But most of them go beyond adding new features to nostr (for example audio, video, speedruns, resumes, etc), and begin to change how nostr actually works.
Nostr can be an everything app, but I think that means something very specific. Nostr can represent data types from pretty much any domain, but it can't actually support all the semantics needed to build any arbitrary system.
I would suggest conservatism in what we build on nostr, but of course anyone can build whatever they want. But I do think it's possible to identify things that nostr is good at, and things it's bad at, and play to nostr's strengths.
Nostr's strengths:
- Being able to model any data type orthogonally to the rest
- Single-owner, self-authenticating, atomic data types
- Potential for robust content dispersal and retrieval if we can flesh out NIP 65 etc.
Nostr's weaknesses:
- Mutable state, non-atomic state
- Shared ownership, key delegation/rotation
- Privacy — metadata will always leak, lack of consistency makes key rotation harder
- Consistency — not everyone has the same view of the world
- Transactionality — nostr isn't good for updating multiple pieces of data in lockstep
It happens that the original use case of nostr — public broadcast social media — benefits greatly from nostr's strengths, and isn't bothered by any of nostr's weaknesses. Blob storage like what blossom is building also works well in this paradigm. A lot of the use cases @PABLOF7z has identified work beautifully well because of the single-owner public-read nature of nostr, which makes forks easy to model.
But things like access control, relational data, collaborative document creation, heavier datasets, or anything that requires a solution to the double-spend problem become very awkward (or impossible) to model on pure nostr. A simple example of this is lists. Not only is it common for a single user to mess up his follow lists because of a lack of consistency between clients or devices, but commonly requested features like shared ownership lists immediately result in a huge increase of complexity, either on the key management side or on the data structure side. Both of these problems are difficult to solve on nostr due to lack of consistency — keys can't always be reliably or safely shared, and linked data structures spanning multiple events by different authors can be hard to assemble reliably.
I think the danger here is that if we as a developer community fail to realize the limitations of nostr and try to adapt the protocol to fit every possible use case, on an ad-hoc basis, we're going to end up with a tragedy of the commons, where no developer can comprehend what must be done to get his work done, and all kinds of weird artifacts appear for end users that no one can explain.
Here are some suggestions I have for preventing this from happening. I realize no one is going to follow them. But maybe they can be helpful for avoidance of wasted time.
- Don't overload event kinds. Many people (including myself) have tried to extend kind 0 with attributes for forms, products, and groups, but that leads to madness. Instead, create a new metadata event signifying a different kind of agent.
- Don't model things as replaceable events if you can avoid it. This creates the problem of shared mutable state, which nostr doesn't have a good story for resolving. They also have a hard limit on how big they can be.
- Use different keys for different things. For domains where some kind of access control needs to be implemented, not tying everything to your main pubkey makes it possible to create and burn keys as needed. Incidentally, this can help users maintain better privacy. An example of this is private groups, which have a dedicated key separate from the group creator's own key.
- Event ownership should always be (is) single-key. If you need shared ownership, figure out a way to share keys. More work needs to go into key invalidation and rotation for this to really work.
- Explore the fork model — this is "my" version of the same thing, and coexists with rather than supersedes the original. This has potential not just for groups or wiki entries.
- Distinguish between different ways to use relays. Relays may be used as indexers (holding specific event types or supporting different features like search/count), repositories (holding many diverse events, to be used with filters), or curated feeds (to be used without filters, or with only a few filters).
These are just suggestions, and many of them may be wrong. Nostr development is hard, and getting harder. Keep it simple.
-
 @ cff1720e:15c7e2b2
2025-01-19 11:10:21
@ cff1720e:15c7e2b2
2025-01-19 11:10:21Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards die dafür sorgen dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache in der sich die Rechner miteinander unterhalten und die auch sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt, der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers, lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen wenn ihm seine ältere Schwester anbieten würde alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays) auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic” weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
-
 @ 6ad3e2a3:c90b7740
2024-05-01 11:57:07
@ 6ad3e2a3:c90b7740
2024-05-01 11:57:07I remember reading a while back about how Omega 6 fatty acids found in seed oils (soybean, sunflower, corn, vegetable, etc.) promote inflammation while Omega 3s like the kind found in wild salmon or grass-fed beef reduce it. Of course, both are essential. If you were unable to produce inflammation, then you might bleed to death from a cut, rather than having it clot into a scab.
The problem was the proportion we consume of each has changed drastically over time. Our ancestors apparently had somewhere between 3:1 and 1:1 Omega 6 to Omega 3, while the standard American diet has between 30:1 and 10:1. That’s a lot of excess inflammation.
And it’s no surprise then that most of our modern diseases are inflammatory in nature — diabetes, cancer, auto-immune disease, heart attacks and strokes are all diseases of a body that’s too inflamed, hyper-responsive, over-sugared, clotting internally. Few people die of too little blood sugar anymore, at least in the calorie-abundant West.
. . .
I listened to a Jocko Willink podcast a few years ago wherein he told the story of a soldier who survived years in a Vietnamese prison camp. The takeaway was that while he was ardently optimistic about his ultimate fate, he remained steadfastly agnostic about the particulars. He said the soldiers who were sure they’d be home for Christmas, for example, were always the first to break when Christmas came and went.
The key was to be generally optimistic only. Think of it as the difference between someone who thinks God will help him pick the right lottery numbers vs one who believes whatever happens to him is in his best interests because God only provides exactly what he needs to learn. The latter is probably going to make it, the former not so much. . . .
The phenomenon of hyper-inflammation is not restricted only to the alimentary diet and the physical body. We are overstimulated by information too. In particular, the amount of threatening news we consume from all over the world is far in excess of what we’ve evolved to process. As such, despite being physically more secure than ever before, we’re in a state of chronic mental inflammation. There’s a word for chronic mental inflammation: “anxiety.”
. . .
I used to think I could overcome fears and other negative emotions by imagining the undesirable outcomes in detail and allowing myself to become okay with them. For example, if someone said something negative about me, I thought I could go over the slight repeatedly and in detail and have it not bother me one bit. But I came to realize the thinking of the slight was itself the being bothered by it. I couldn’t both think I had gotten over it and really get over it. I had to choose to think about it and not be over it, or not to think about it and actually get over it. I couldn’t have it both ways.
. . .
Even if you see through the fears endlessly promulgated by legacy institutions: climate change, terrorism, covid, the unvaccinated, Trump, Putin, the insurrectionists!, you are tuned into a new set of anxieties: CBDCs, the WEF, the WHO, GMOs, mRNA mandates, the impending collapse of the financial system. I’ve come to realize lately that even being aware of all the so-called real threats is also mentally inflammatory.
. . .
If being agnostic as to specific positive outcomes was the key to survival in the prison camp, perhaps it follows one should be agnostic as to negative ones too. While it’s easy to see the folly in the poor, tortured soldier clinging to the hope of being home for Christmas, it’s harder to see it in the anxious housewife fretting over the lives for her children in the face of near-certain climate doom. But it’s essentially the same error — being overly certain about the future outcome on which the hope or fear rests.
The alternative is to be on guard generally about threats of ruin, but agnostic about the specifics. It could be a car crash, a heart attack, a nuclear war, financial collapse, virus or dystopian new world order. You can read the signs, but you never really know. What makes the future the future is precisely this quality. You can protect yourself generally by taking care of your health to the best of your ability, putting your finances on solid ground to the greatest extent practicable and, it might turn out, decreasing your exposure to an information diet that leads to chronic inflammation of mind.
. . .
In the information age, there is a fine line between head-in-the-sand denial of real threats and inflammatory paranoia, one the new media (social algorithms) are designed to make ever more difficult to walk. You need the capacity to defend yourself against acute threats, to clot the cut so to speak when they arise, and yet chronic inflammation will kill you if you try to stay on high alert for every potential attack vector.
You have to choose, it seems, between being prepared generally, trusting yourself to face unknowable threats with the best acute response you can muster, and being specifically armed in advance, at the cost of making yourself sick.
There is no guarantee you survive, but that was ever the case, no matter your preparations.
-
 @ 9349d012:d3e98946
2025-01-18 20:15:22
@ 9349d012:d3e98946
2025-01-18 20:15:22For many reasons, not least of those the outcome of the last US presidential election, I’m now working on Librarian Detective, Book Two as my creative release. At the moment, I’m already on chapter seven, which means I made it through writing the second chapter, always an admirable hurdle to clear. If you’ll recall, with Librarian Detective, Book One, clearing that milestone was a challenge. It took between nine and 12 years to finish that book, although I wrote three books in those meantime years. This was partly because of working on my day job business more fulltime (MyLibrarian! Our app is out, sign up to test on the pop up here) but also because I revamped my entire writing process, which I’ll share with you.
Here’s a picture of the writing methods I use. I went from writing longhand to digitally, which is more efficient, and I also use a series of guides to help organize the writing process: An outline, character list, calendar timeline, editing checklist and the main writing doc itself.
Seven years ago when I realized my writing method was working for me, I started doing a video series on Writing, called On Storytelling, filmed at all the remote locations I work at, one of the best of which I’m at right now, working on my new book. If you are looking for more writing resources, there’s a list on my blog. When you go down these rabbit holes you may come out ready to write your first book.
GOOD LUCK—MEZ
Originally appeared on https://www.michellezaffino.com/my-writing-methods/
-
 @ 9349d012:d3e98946
2025-01-18 20:13:04
@ 9349d012:d3e98946
2025-01-18 20:13:04For many reasons, not least of those the outcome of the last US presidential election, I’m now working on Librarian Detective, Book Two as my creative release. At the moment, I’m already on chapter seven, which means I made it through writing the second chapter, always an admirable hurdle to clear. If you’ll recall, with Librarian Detective, Book One, clearing that milestone was a challenge. It took between nine and 12 years to finish that book, although I wrote three books in those meantime years. This was partly because of working on my day job business more fulltime (MyLibrarian! Our app is out, sign up to test on the pop up here) but also because I revamped my entire writing process, which I’ll share with you.
Here’s a picture of the writing methods I use. I went from writing longhand to digitally, which is more efficient, and I also use a series of guides to help organize the writing process: An outline, character list, calendar timeline, editing checklist and the main writing doc itself.
Seven years ago when I realized my writing method was working for me, I started doing a video series on Writing, called On Storytelling, filmed at all the remote locations I work at, one of the best of which I’m at right now, working on my new book. If you are looking for more writing resources, there’s a list on my blog. When you go down these rabbit holes you may come out ready to write your first book.
GOOD LUCK—MEZ
Originally appeared on https://www.michellezaffino.com/my-writing-methods/
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ 955e5a04:c03b3cc3
2024-04-29 13:36:19
@ 955e5a04:c03b3cc3
2024-04-29 13:36:19"If the things that cause you unease or disturb your peace don't come to you, but you, in a certain way, go to them, remaining unmoved, then judgment must cease warring against them. And thus, you will no longer desire them nor flee from them henceforth." –Marco Aurelio
"In this meditation, Marco Aurelio reflects on how our emotional reactions are influenced by our desires and aversions, rather than external circumstances.
Here's an interpretation for each line, based on all the principles applied in Stoicism and his Meditations, this is in the 11th book:
"If the things that cause you unease or disturb your peace don't come to you": Marco Aurelio points out that the things that cause us emotional distress don't actively pursue us, but it's our own reactions to them that create that distress. "But rather, you, in a certain way, go to them, remaining unmoved": Suggests that it's us who, in some way, seek out those disturbing emotions, even when external circumstances remain unchanged. "Therefore judgment must cease warring against them": Here, Marco Aurelio advocates for ceasing to fight against those disturbing emotions with the power of judgment or reason. Instead of resisting them, he suggests we should accept them as part of our human experience. "And thus, you will no longer desire them nor flee from them henceforth": By freeing ourselves from the struggle against those emotions, we cease to desire or fear them in the future. By accepting them peacefully, we lose interest in them and no longer actively pursue or avoid them."
Embrace inner strength. Master reactions. Find peace. That's the true path to empowerment and serenity.
-
 @ 76c71aae:3e29cafa
2024-04-27 02:17:10
@ 76c71aae:3e29cafa
2024-04-27 02:17:10Why are there 5.5 million people with Bluesky accounts and about 800k to 1.3M on Nostr?
Some of it boils down to social dynamics and chance. It's akin to how immigrants often cluster in the same neighborhoods. Most people are simply following their communities, and their primary decision is driven by where their community is heading.
Why did the communities choose Bluesky over Nostr, Mastodon, Farcaster, or the several dozen centralized and decentralized alternatives?
That’s a more pertinent question. Firstly, very few people actually make these decisions, and most simply follow them. Secondly, the choices aren't primarily based on the technology or the features of the apps or protocols.
Bluesky had certain advantages and disadvantages. It received a fair amount of press as a Twitter spinoff. However, it was late to launch, only preceded by Threads, which had Meta’s platforms for promotion.
In terms of initial marketing, I’d say Bluesky and Nostr were about equal, both often pitched as a ‘Jack Dorsey thing’, which wasn’t true in either case. The press loves stories about people and drama over networks and systems. Social media is vast and complex, and its technology even more so, which is why it’s often presented through personalized narratives about the creators.
Under the hood, Bluesky’s atproto and Nostr are very similar technologically. Both were inspired by Secure Scuttlebutt. Bluesky has adopted a cathedral model of open source, akin to how Android is open source but controlled by Google. Meanwhile, Nostr developed under the bazaar model of open source, created by a community rather than a company.
This company model gives Bluesky some advantages; for instance, they could launch with an invite list, a classic tactic to make something feel more desirable. Even then, most Bluesky users haven’t posted a single thing, and when they had a million registered users, they had fewer than 1500 Daily Active Users (DAU) see bluesky stats.
Bluesky is a lot easier to try than Nostr. The ways keys and content signing work in Bluesky and Nostr are overwhelmingly similar, except that Nostr doesn’t tell you where to store your keys and in Bluesky, you put them on your PDS server, which Bluesky provided free by default for all new users.
This means for Nostr, you have to figure out what to do with your nsec and npub, then how to get a nip-05 for a Nostr name which makes sense. If you want to log in with a username and password, you need to find and set up a nip-46 service. Not all apps support that, so you’re copying and pasting around an nsec. If you want to use a web app, you need to go find and choose one of several browser extensions and set that up. This is easy and natural for folks with experience in crypto but really foreign for everyone else.
Maybe a million people have figured out how to get started on Nostr; it’s definitely possible. And some apps like Primal and Nos have integrated name services as part of the signup, which makes it cleaner.
Once you’re on Nostr, people often discuss zaps, a functionality that may not work as expected. You’ve got to learn how to set up a wallet, what lightning and Bitcoin are. Some get really into it, we’ve seen folks get into Bitcoin through Nostr, but for many, it’s a confusing hurdle.
Bluesky provides a neat way to get into a single default app and gives you a username. Sure, you can change it—I self-host my DID at rabble.nz—but apparently less than 1% of Bluesky users do that, just like most Nostr users have chosen to use a cloud service for their nip-05 Nostr name.
Why else has Bluesky grown bigger than Nostr? It's their approach to positioning the protocol. They’ve set up default moderation controls and a trust and safety team. Initially, they didn’t have these, and when users demanded action and the company refused, growth stalled and usage dropped last July. The Bluesky team didn’t post for about a month, and there was a real question about whether Bluesky would survive.
The user community wanted pretty heavy-handed moderation. The Bluesky team was committed to building a decentralized protocol that didn’t do that. The compromise was that Bluesky would be slow about opening up open federation over atproto until the Bluesky apps, protocol, and company-hosted services could have a trust and safety team and a moderation bot. Their moderation bot is fancier than @reportinator, but it’s the same idea, but with a bigger team of humans reviewing reports. And if you’re using the Bluesky-provided PDS, there’s no way to block or unfollow their default moderation bot. We don’t make everybody on Nostr follow nostr:npub14h23jzlyvumks4rvrz6ktk36dxfyru8qdf679k7q8uvxv0gm0vnsyqe2sh .
That compromise worked for the community and company, and the user base started growing again. The negative press about Bluesky's content ceased and those upset by the policies left, some migrating to Nostr. Bluesky was able to position itself as the socially responsible social media protocol that was easy to use. Jack deleted his Bluesky account, signaling to the world and press what we already knew: he is much more interested in Nostr’s approach to bottom-up development by community and support for lightning payments.
During this period, Nostr's growth really stalled. There are a few reasons for this. We'd saturated the community of folks who both love Bitcoin and dislike Elon enough to leave Twitter. Additionally, our new user experience pushed people to view a global feed dominated by a single topic of conversation.
Nostr has positioned itself strongly as a protocol for those who are freedom-loving, anti-censorship Bitcoin enthusiasts. The easiest Nostr client for new users, Primal, markets itself as a Bitcoin wallet first, and only secondarily as a social media app. People view Nostr as a Web3 project. We’ve had individuals visit the Nos.social website and decline involvement, saying they dislike Web3 because they perceive it as a planet-harming scam (let's not argue the carbon emissions of mining here). We never mention Web3 or any cryptocurrency elements on the Nos website, yet all decentralization has been associated with dubious schemes.
As Nostr’s growth has stalled, the ecosystem has matured and flourished. Nostr boasts technology and apps that other platforms envy. I often hear Bluesky and Fediverse developers express admiration for the cool things Nostr is doing with technology and apps, but since their communities don’t use it, they don’t either.
Just look at the articles my posts last week about Nostr vs. ActivityPub kicked off: Extending ActivityPub and Nomadic Identity is Coming to ActivityPub
I suspect what’s holding back Nostr is twofold. First, how we talk about Nostr. We discuss it in political and ideological terms—we're against censorship, for free speech, value-for-value, etc.—but not about the types of content and people on Nostr, how to find your friends, or the interesting stuff you followed elsewhere. Nor do we talk about how you can use all these cool apps with the same identity and content. It's a hard concept to grasp, and I find myself constantly having to explain it.
The biggest issue people see with Nostr is its perceived association with Bitcoin enthusiasts plus those who’ve been deplatformed elsewhere, often for contentious reasons. I’m not saying the deplatforming was justified, but the perception among those unfamiliar with arbitrary bans and sanctions on platforms is that those who've been deplatformed had it coming—that they were all conspiracy theorists, bigots, or harassers. Some were, some were not, but it's perceived that way by many.
The way we talk about Nostr and onboard new users doesn’t help. The goal of the creator and journalism projects we just launched was to both diversify the content on Nostr for new users and to demonstrate to those creators and journalists that micropayments and paid content on Nostr are viable alternatives/additions to how they publish on social media elsewhere. It is value-for-value without the label, because our theory is that people want the functionality but aren't so keen on the cultural ideology.
This is all solvable. We can: - Make it easier to set up a nip-05 for new users. - Ensure that nip-05 also functions as an nsec bunker for easy login, if users desire. - Add Webfinger files so your nip-05 name functions as a Fediverse name (it’s pretty easy to do; we're experimenting with it on nos.social). - Show users a variety of content types when they join. - Help users find communities, perhaps encouraging groups/channels the way Farcaster does. - Make it easy to find and choose moderation settings, offering more middleware services like Reportinator but with different content labeling ideas. - Change our marketing to attract these new users, focusing on what they can see and who they can connect with, less on Bitcoin, technology, or evading censorship. - Develop apps that offer new functionalities, drawing people in instead of being mere clones with or without certain features.
It always takes a long time for people to figure out what the native mediums are on a technology platform. Initially people would make a phone call to listen to a concert, the first radio stations had people just reading the newspaper, and the first tv broadcasts were either a camera pointed at radio announcers or a single camera shot of a play. People always do the same things, we're the same humans that evolved a couple hundred thousand years ago, same brains, same bodies. What's changed is the way we do things with technology, so what fundamental human thing can we do new and different now that we've got these social protocols and tech?
Addressing the app design and technology will help, but actual growth will come when people discover us, join, find connections, and genuinely want to invite others to join them. Nostr users are incredibly welcoming to new users. However, we also have a subset of users who engage in sexist, racist, and homophobic harassment. This harassment drives people away from Nostr and deters them from recommending it to others. If we don't provide better tools for users to protect themselves from this harassment, they'll leave and find social spaces where they feel safe. Some might abandon public social media altogether, or just switch to Bluesky, which promises to eventually open up their network and has just announced support for uploading images, coming soon.
We're way ahead of the other protocols in some areas and way behind in others. We've got enough momentum and users to figure this out, but we're not there yet.
-
 @ 6b9da920:7841cc6e
2024-04-25 06:43:22
@ 6b9da920:7841cc6e
2024-04-25 06:43:22When I was a corporate programmer, I never had the chance to directly work with designers because I was a backend developer and more importantly, individual contributors usually have no sayings on what designers should be. Usually, the project manager discusses with designers and decides what should be done and we as programmers just receive the decisions.
In this context, programmers are not treated as engineers because real engineers have to influence the design.
I have the chance to work on designs and with designers for the first time in my life since I started Nostr last year. It has been a huge learning journey for me.
At first, I simply saw UI designers as some kind of painter that drew the shapes I want as the product creator. I have worked with several different designers to come up with UIs or graphics in a side gig, ad-hoc way, either paid or as a community effort.
I need to thank @Karnage and nostr:npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk who have volunteered to help me a bit.
However, the problem unveiled itself shortly. I never finished their design! Roughly 12 months ago, I asked @Karnage to do a redesign of Blowater. He finished it in like a week. But I still have not implemented 30% of what he designed!
Why?
The surface reason is that there are designs that I don't like or visuals that simply goes against the functionality intention. I, as the product creator, did not communicate clearly with the designer what functionalities I want. Therefore, many changes, iterations are needed.
The root reason is, in an exploratory project, designers can't be treated as ad-hoc helpers or outsourced laborers. They have to participate in the core process to shape the product. They can't just do the UIs, they have to actively get involved into the design of the whole product, from functionalities to UIs. This is what I did not understand back then and it took me 12 months to realize. While a designer does not need to spend 40 hours working on a single project. They still need to be considered as a full-time team member instead of an occasional helper.
To address the title, moving forward, I either have to become a UI designer myself, or I have to work with a designer who shares similar visions and is willing to work with me as a long term collaborator. I will never outsource ad-hoc design works again.