-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ 4ba8e86d:89d32de4
2024-10-01 13:27:38
@ 4ba8e86d:89d32de4
2024-10-01 13:27:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26
@ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions?
Revolution or Destabilization?
Figures like Wadah Khanfar, the former head of Al Jazeera, expressed optimism about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests.
For instance, Professor Hamid Dabashi linked Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly seized the moment, using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces.
The Color Revolution Playbook
The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in Webster Tarpley’s analysis for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region.
Consider the case of Stuxnet, a cyberweapon developed by the US and Israel to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "Which Path to Persia?", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention.
From Iran to Syria: The Next Domino
Once the destabilization of Iran was in motion, attention shifted to its key ally, Syria. The calls for regime change escalated quickly, with Senator Joe Lieberman openly suggesting that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China.
This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about denying it to China. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China.
Let's examine some instances of China's strategy in the region. * On April 6, 2006, Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges. * China's expanding diplomatic, economic, and security interests in the Middle East, particularly through its interactions with the Gulf Cooperation Council (GCC). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond. * China's expanding influence in the Caspian region and its intersection with Syria's strategic ambitions. Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. Syrian President Bashar al-Assad's "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas. * China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized Silk Road initiative. Following Syrian President Bashar al-Assad's 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles.
The Fall of Puppets: Mubarak and Libya
Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between China and the Arab world, particularly in Africa. His removal paved the way for a new power dynamic, one that better served Western interests.
A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, China’s oil investments in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa.
The Bigger Picture: A New World Order Agenda?
What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control.
Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention.
The Illusion of Spontaneous Uprising
While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control.
The question remains: How much longer will people buy into the illusion?
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8d34bd24:414be32b
2025-02-16 04:19:34
@ 8d34bd24:414be32b
2025-02-16 04:19:34Last night in my Bible reading I read this verse:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. (Jeremiah 7:16) {emphasis mine}
My first thought was “Why in the world is God telling us not to pray for this people? Doesn’t the Bible tell us to pray about everything?”
First of all, then, I urge that entreaties and prayers, petitions and thanksgivings, be made on behalf of all men, for kings and all who are in authority, so that we may lead a tranquil and quiet life in all godliness and dignity. This is good and acceptable in the sight of God our Savior, who desires all men to be saved and to come to the knowledge of the truth. (1 Timothy 2:1-4) {emphasis mine}
Doesn’t God tell us to pray for whatever is bothering us?
Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:6-7)
Doesn’t the Bible say that God will answer all of our requests?
Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. (John 14:13)
Doesn’t the Bible tell us to pray for Israel and Jerusalem and His chosen people?
Pray for the peace of Jerusalem:\ “May they prosper who love you.\ May peace be within your walls,\ And prosperity within your palaces.”\ For the sake of my brothers and my friends,\ I will now say, “May peace be within you.”\ For the sake of the house of the Lord our God,\ I will seek your good. (Psalm 122:6-9) {emphasis mine}
Doesn’t the Bible even tell us to pray for our enemies?
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. (Luke 6:27-28)
If all of this is true, then why does this verse tell us to not pray for this people, especially considering this is referring to God’s chosen people?
To answer this question, let us look at a broader portion of this passage:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
God is saying to not pray for these people who have turned from Him and are worshipping other gods. These people are in full rejection of God. Still does it mean that we can’t pray for them at all or is this talking about a particular kind of prayer?
A little later in Jeremiah, we read:
“Therefore do not pray for this people, nor lift up a cry or prayer for them; for I will not listen when they call to Me because of their disaster. (Jeremiah 11:14)
and
So the Lord said to me, “Do not pray for the welfare of this people. When they fast, I am not going to listen to their cry; and when they offer burnt offering and grain offering, I am not going to accept them. Rather I am going to make an end of them by the sword, famine and pestilence.” (Jeremiah 14:11-12) {emphasis mine}
We get a little more specificity on the command to “not pray for” in Jeremiah 14. We are told, “Do not pray for the welfare of this people.” This is not a universal command to never pray for them, but a command to not pray for their welfare. It is a command to not pray blessings on those in active rebellion against God.
At the time this command was made, the Israelites were expecting God’s protection and blessings while refusing to follow Him and instead worshipping other gods. This command isn’t a blanket statement to not pray for a sinning Israel, but a statement to not pray for blessings and protection for a sinning Israel. If this was a blanket statement it would contradict Psalm 122 above.
This is the confidence which we have before Him, that, if we ask anything according to His will, He hears us. And if we know that He hears us in whatever we ask, we know that we have the requests which we have asked from Him. (1 John 5:14-15) {emphasis mine}
Using 1 John 5:14, we can begin to see the catch. We are to pray “according to His will.” It is not God’s will for sinners and those in open rebellion against God to be blessed or protected from hardship. A prayer such as, “Please turn your people back to you and give them a pure heart and repentance from sin,” would be according to His will. A prayer to “Please bless and protect Israel” while Israel has turned their back on God is not a prayer that God will answer. He will “not hear you.”
The Bible also says:
You ask and do not receive, because you ask with wrong motives, so that you may spend it on your pleasures. (James 4:3)
How often are our prayers not answered because we pray with wrong motives? At least sometimes. Of course there are also times when God tells us to wait or has something better in mind and we can’t see it because we are not seeking His will, but our own.
It is always good to pray for someone’s repentance and salvation. It isn’t always good to pray for someone’s healing, blessings, and prosperity. It is always good to pray for a nation to turn back to God and to obey His commands. It isn’t always good to pray for a nation’s prosperity and power in the world. Sometimes God’s will is to punish those who turn away from Him or against Him. We need to make sure we are aligned to God’s will and not just seeking our own.
I recommend that our prayers be like Jesus’s prayer right before going to the cross, “saying, “Father, if You are willing, remove this cup from Me; yet not My will, but Yours be done.” (Luke 22:42). Our requests should be like that of Shadrach, Meshach, and Abed Ngo right before being thrown in the fiery furnace, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:18). This isn’t just words thrown on the end of our prayers “yet not My will, but Yours be done,” but a cry of our hearts in full and complete trust in our Father God.
One thing that helps me is I try to pray the problem not the solution. God knows much better solutions than we do because He knows everything that has happened, everything that is happening, and everything that will happen. He knows what will lead to the best long term solution. When we pray the solution we desire, we miss out on the blessings of God’s knowledge, wisdom, and love.
May God lead you and guide you in a closer relationship to Him so that your will is completely aligned with His will and you are in close fellowship to Our Father in Heaven.
Trust Jesus
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ 6ad3e2a3:c90b7740
2025-02-09 11:22:19
@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself.
Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?
A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…
Q That’s more than sufficient, Oscar, thank you. And date of birth?
A: July 7, 2020.
Q Talk a little bit about your childhood and how you came to live in Lisbon.
A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.
Q: That must have been traumatic.
A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.
Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?
A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)
Q: I meant to ask you about your size. I hope it’s not a sensitive subject.
A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.
Q: Are you self-conscious about being a small dog?
A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.
Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.
A: I’m not ambitious. I’m perfectly happy to be a dog.
Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”
A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.
Q: Human privilege?
A: Yes. Dogs don’t get due process. There is no justice for a dog.
Q: Do you think there’s species discrimination?
A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?
Q: How does that make you feel?
A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.
Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?
A: A person of human ancestry can’t possibly know the lived experience of a dog.
Q: You mentioned vegetable sticks. Are you a vegetarian?
A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)
Q: What’s behind the alias “The Opportunist” which you said you don’t like.
A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.
Q: I see how that could be insulting. How would you describe your current vocation?
A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.
Q: Security?
A: I make sure to let everyone know when someone’s at the front door.
Q: What goes through your mind in those cases? Are you scared?
A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”
Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?
A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”
Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?
A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.
Q: Some serious method acting!
A: You could call it that. I am fully immersed in the role.
Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?
A: I don’t know. I focus on the present.
Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.
(buzzer sounds)
A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ c1e6505c:02b3157e
2025-02-08 21:52:51
@ c1e6505c:02b3157e
2025-02-08 21:52:51***"Time is the best teacher but unfortunately it kills all of its students."*** I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. *I love it.* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \[ \]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on.           Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: *"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected.   ) *Just in case you missed it…* **I have a limited edition framed print that I will have available until February 28th.** Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. \]() ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints.  [Dehancer Film (promo code "PICTUREOOM")](https://www.dehancer.com/shop/pslr/film) *If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.* Thank you - Colin
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 3b7fc823:e194354f
2025-02-07 18:42:31
@ 3b7fc823:e194354f
2025-02-07 18:42:31Privacy in Public Spaces: A Tactical Guide
1. Public Wi-Fi Privacy
Using public Wi-Fi can be convenient, but it's important to take precautions to protect your privacy:
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data.
- Disable Automatic Connections: Prevent your device from automatically connecting to open Wi-Fi networks by turning off this feature in your settings.
- Avoid Sensitive Transactions: Refrain from accessing banking or other sensitive accounts while connected to public Wi-Fi.
- Use Secure Websites: Look for "https://" in the website's URL to ensure it uses encryption.
- Keep Software Updated: Ensure your device's operating system and apps are up-to-date to protect against security vulnerabilities.
2. Surveillance Camera Awareness
Surveillance cameras are common in public spaces. Here are some strategies to maintain your privacy:
- Spotting Cameras:
- Look for Signs: Many establishments post signs indicating the presence of surveillance cameras.
- Camera Placement: Cameras are often placed near entrances, exits, and high-traffic areas. Look for dome-shaped cameras on ceilings or wall-mounted cameras.
- Using Masks and Coverings:
- Face Masks: Wearing a mask can help obscure your facial features from facial recognition systems.
- Hats and Sunglasses: A hat can shield your face from overhead cameras, while sunglasses can hide your eyes.
- Covering Identifying Marks:
- Clothing Choices: Wear clothing that doesn't have distinctive logos or patterns that can easily identify you.
- Blend In: Opt for styles and clothing choices that helps you blend in with your surroundings, reducing your visibility.
- Temporary Coverings: Consider using temporary coverings, such as scarves or hoods, to conceal tattoos or other identifying marks.
3. General Privacy Tips in Public Spaces
- Be Mindful of Your Surroundings: Pay attention to your environment and be aware of any unusual behavior or devices that may be capturing your information.
- Limit Personal Information: Avoid discussing sensitive information in public where it can be overheard.
- Use Encrypted Messaging Apps: Apps like Signal or SimpleX offer end-to-end encryption for your messages, making it harder for eavesdroppers to intercept your conversations.
- Use Privacy Screens: Privacy screens on all of you electronic screens can defend against the over the shoulder peek or side eye.
- Avoiding Behaviors: Be mindful of behaviors that could make you a target, such as frequent visits to certain areas or engaging in conversations that might attract unwanted attention.
Taking these steps can help you maintain your privacy while navigating public spaces and using public Wi-Fi. Remember, staying informed and vigilant is key to protecting your personal information.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 57d1a264:69f1fee1
2025-02-17 13:55:53
@ 57d1a264:69f1fee1
2025-02-17 13:55:53Hey ~Design fam! We’re hosting an exclusive session on ephemeral architecture & immersive photography—and you’re invited! 🎟️
What happens when spaces tell stories? join us for an inspiring session that explores the magic of ephemeral architecture and immersive photography. let paramdeep singh dayani, architect & photographer, guide you through the art of designing impermanent yet unforgettable moments.
What you'll explore: ✨ designing for impermanence: how to craft spaces that make a statement. 📸 photography as storytelling: capturing the fleeting essence of design. 🤝 the human connection: using visuals to evoke emotion.
Why you should attend: 1️⃣ get inspired to create meaning in impermanence. 2️⃣ learn how visuals can transform spaces into stories. 3️⃣ connect with a community of creative minds and innovative thinkers.
📅 When Feb 27, 2025 - 9-10 PM
📍 Where? Right here on Discord—because webinars should be interactive, engaging, and community-driven.
🔗 Save your spot now! - https://tally.so/r/w86MkP
See you there! 🚀
originally posted at https://stacker.news/items/888333
-
 @ 6ad3e2a3:c90b7740
2025-02-07 08:17:18
@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account.
I’d tell them, “You decide, I’ve got my own problems.”
. . .
I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests.
. . .
Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere.
Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium.
That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper.
. . .
I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative.
The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media.
What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn.
There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.)
No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness.
We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot.
. . .
I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them.
I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!”
. . .
There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature.
. . .
No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach.
. . .
The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.”
For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
-
 @ e88a691e:27850411
2025-02-17 13:30:42
@ e88a691e:27850411
2025-02-17 13:30:42test post longform 4
-
 @ da0b9bc3:4e30a4a9
2025-02-17 12:33:36
@ da0b9bc3:4e30a4a9
2025-02-17 12:33:36Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
Man! I Feel like a Woman! Shania Twain!
https://youtu.be/ZJL4UGSbeFg?si=ClexJCLdrpDg1RRG
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/888248
-
 @ 16d11430:61640947
2025-02-17 12:28:08
@ 16d11430:61640947
2025-02-17 12:28:08The Perfect Psychological Operation to Divide, Conquer, and Enslave
Why Do Men Feel Useless and Women Feel Overburdened?
Look around. Something is deeply, insidiously wrong.
Men are lost, stripped of purpose, and drowning in quiet despair. Women are exhausted, forced into unnatural roles, carrying both professional and domestic burdens while being told they should be grateful for the privilege. Marriages crumble, families disintegrate, and the birth rate nosedives while corporate profits soar.
Coincidence? Not a chance.
This is not a byproduct of "progress" or "equality." This is a precision-engineered psychological and economic war waged against the family unit by the fiat system and its corporate enforcers. It is not feminism, nor is it the patriarchy. It is something far worse: a deliberate social and financial coup to destroy natural gender balance, increase worker dependency, and create the perfect, exhausted, obedient slaves.
Let’s tear this apart, piece by piece.
Step 1: Economic Sabotage – The Emasculation of Men
Men have been systematically stripped of their role as providers, not by cultural shifts, but by the fiat scam that inflates away their labor and makes single-income households impossible.
In 1970, a man could buy a home, support a family, and retire with dignity on a working-class salary. Today? Even high earners struggle to buy homes while rent and debt devour their paychecks.
The psychological effect? Uselessness. The traditional role of men—to provide, protect, and build—has been economically crippled. The moment a man cannot provide, his biological drive collapses. His confidence, purpose, and even testosterone levels plummet.
He turns to distractions—video games, porn, drugs, or meaningless jobs. Or he checks out entirely, labeled “lazy” while the system that neutered him laughs from above.
And yet, men are still told to "man up" and "work harder"—as if fighting against a rigged economy is a test of character.
Step 2: Psychological Warfare – The Masculinization of Women
Women, meanwhile, have been sold a lie—that the only path to fulfillment is chasing careers inside corporate cubicles.
While they are told this is "empowerment," what it really does is double the workforce, lower wages, and increase tax revenue.
Women now face double the burden—working a full-time job while still handling the majority of child-rearing and housework.
Instead of being honored for creating life and raising future generations, they are ridiculed for “wasting their potential” if they don’t dedicate themselves to their corporate masters.
And what is the psychological effect? Resentment.
Resentment towards men, who are no longer the strong providers they once were.
Resentment towards motherhood, which has been devalued and monetized.
Resentment towards themselves, because they were promised fulfillment through corporate work but ended up burned out, anxious, and miserable.
Women have been told they are “strong and independent” while simultaneously being enslaved to a system that profits off their exhaustion.
Step 3: Divide and Conquer – Corporate Culture as the New Family
With men neutered and women overburdened, the nuclear family collapses. But humans still need a sense of belonging.
Enter: The Corporation.
Your workplace becomes your "real family." HR tells you to “bring your whole self to work.” Team-building exercises and corporate retreats replace family gatherings.
Work colleagues become your primary emotional support system. There’s even the concept of the “work spouse,” an insidious corporate fabrication that normalizes deeper emotional ties with colleagues than with real partners.
Your career becomes your purpose. Not your bloodline, not your family history, not your legacy—your productivity for someone else’s bottom line.
And before you know it, you’re 50 years old, childless, exhausted, and utterly dependent on a salary to survive. The corporate world used your best years to enrich its shareholders, and now you have nothing.
Step 4: The Endgame – The State Raises Your Kids
With the family unit in ruins, who raises the next generation? The State.
Public schools become indoctrination camps, teaching kids to obey, conform, and view the government as their protector.
Children are raised by institutions, not by parents—because both parents are working just to survive.
The cycle repeats: fatherless boys become weak men, overburdened girls become resentful women, and the system gains a fresh crop of obedient, exhausted workers.
The ultimate fiat scam is not just financial. It is biological. It is a full-scale, generational coup against the natural order of humanity.
How Do We Break Free?
The only way to escape this biological and financial slavery is to opt out of the fiat system entirely.
-
Bitcoin & Self-Sovereignty – Remove your wealth from the fiat system. Own hard assets, build businesses, become untouchable.
-
Build Real Families – The corporate world is not your family. Your bloodline is. Reject the state’s control over your children.
-
Reject Debt & Wage Slavery – The system is designed to keep you financially trapped. Find ways to exit the rat race early.
-
Reclaim Natural Gender Roles – Not through coercion, but through honest, sovereign partnerships that reject fiat-fueled dysfunction.
They divided us so they could rule us. Break the cycle.
-
-
 @ 3ffac3a6:2d656657
2025-02-06 03:58:47
@ 3ffac3a6:2d656657
2025-02-06 03:58:47Motivations
Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network.
Prerequisites
- A "server" with an amd64 processor (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do.
- Basic knowledge of Linux commands.
- Access to your Wi-Fi router's settings (if you plan to configure routes there).
Step 1: Installing the WARP CLI
- Update your system packages:
bash sudo apt update && sudo apt upgrade -y- Download and install the WARP CLI:
```bash curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg
echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list
sudo apt-get update && sudo apt-get install cloudflare-warp ``` 3. Register and connect to WARP:
Run the following commands to register and connect to WARP:
```bash sudo warp-cli register sudo warp-cli connect ````
Confirm the connection with:
bash warp-cli status
Step 2: Routing Traffic on the Server Machine
Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel.
- Enable IP forwarding:
bash sudo sysctl -w net.ipv4.ip_forward=1Make it persistent after reboot:
bash echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf sudo sysctl -p- Set up firewall rules to forward traffic:
bash sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related acceptReplace
eth0with your actual network interface if different.- Make rules persistent:
bash sudo apt install nftables sudo nft list ruleset > /etc/nftables.conf
Step 3: Configuring the Route on a Local PC (Linux)
On your local Linux machine:
- Add a static route:
bash sudo ip route add 104.0.0.0/24 via <SERVER_IP>Replace
<SERVER_IP>with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step.
Step 4: Configuring the Route on Your Wi-Fi Router (Recommended)
If your router allows adding static routes:
- Log in to your router's admin interface.
- Navigate to the Static Routing section. (This may vary depending on the router model.)
- Add a new static route:
- Destination Network:
104.0.0.0 - Subnet Mask:
255.255.255.0 - Gateway:
<SERVER_IP> - Metric:
1(or leave it default) - Save and apply the settings.
One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations.
Final Thoughts
Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug.
-
 @ 1833ee04:7c4a8170
2025-02-04 15:14:03
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 3ffac3a6:2d656657
2025-02-03 15:30:57
@ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações.
Descobrindo L3DA
Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo.
"O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando.
Naquele momento, suas telas piscaram em vermelho. Acesso não autorizado detectado. Ela havia ativado um alarme invisível da Corporação Atlas.
O Resgate de Vey
Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral.
"Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico.
Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova.
"O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin."
A Caça da Atlas
A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os Girinos através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato.
"Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais.
"Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro."
A Missão Final
Em uma missão final, Nova liderou uma equipe de assalto armada dos Girinos até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico.
Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado.
"Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas.
No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os Girinos se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas.
Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática.
"Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada.
O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho.
"Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria."
De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord.
Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança."
Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia."
Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui."
Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..."
Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA.
Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin.
O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..."
Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!"
Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais uma. Ela era todos.
Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir.
Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: "Eu sou L3DA. Eu sou Satoshi." Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: "A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."
Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína.
O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre.
O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar.
"Viva la libertad, carajo!" ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
-
 @ d360efec:14907b5f
2025-02-17 12:20:25
@ d360efec:14907b5f
2025-02-17 12:20:253 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่
นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น
-
การซื้อขายตามอารมณ์: ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด
-
การไม่ยอมรับความเสี่ยง: การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้
-
การขาดความรู้และความเข้าใจ: ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก
บทสรุป
3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ
บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่
บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน
3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:
-
ปล่อยให้ขาดทุน แต่รีบขายกำไร: นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร
-
ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น: นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า
-
รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย: พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว
คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:
- ฝึก "Cut Loss Short, Let Profit Run": ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น
- อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล: พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น
- บริหารความเสี่ยงและ Money Management อย่างเหมาะสม: กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้
- เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง: ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ
- มี Mindset ที่ถูกต้องสำหรับการเทรด: เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา
สรุป:
การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
-
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ 7546e8e4:154e8264
2025-02-17 10:48:44
@ 7546e8e4:154e8264
2025-02-17 10:48:44Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless.
Key Points The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time.
Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets.
Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains.
Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com -
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 849a5a61:b57d2870
2025-02-17 10:11:18
@ 849a5a61:b57d2870
2025-02-17 10:11:18Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio.
We built BitFlio because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel, and when referred by other customers, that customer typically has a 37% higher retention rate.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the
BitFlio.convert('yourcustomer@email.com')function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
-
Pricing from $0/month
-
Automatic NWC sync
-
Works for both subscriptions and one-time charges
-
Embed script is lightweight and only ~13kb
-
Privacy-friendly & Anonymous
-
No GDPR needed, as we operate in the Private.
-
Manage multiple affiliate programs for different products from one single dashboard
-
Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via beta.BitFlio.com and let us know how you get on / your initial thoughts 😄
Landing: https://BitFlio.com
sᴏᴏɴ!Beta whitelist: https://beta.BitFlio.com Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx Support the open source project on @geyserfund https://geyser.fund/project/bitflio/
Mirror posts: - https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/ - https://geyser.fund/project/bitflio/posts/view/4138 - naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla
originally posted at https://stacker.news/items/888167
-
-
 @ 849a5a61:b57d2870
2025-02-17 09:47:19
@ 849a5a61:b57d2870
2025-02-17 09:47:19We built BitFlio because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel, and when referred by other customers, that customer typically has a 37% higher retention rate.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the
BitFlio.convert('yourcustomer@email.com')function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
-
Pricing from $0/month
-
Automatic NWC sync
-
Works for both subscriptions and one-time charges
-
Embed script is lightweight and only ~13kb
-
Privacy-friendly & Anonymous
-
No GDPR needed, as we operate in the Private.
-
Manage multiple affiliate programs for different products from one single dashboard
-
Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via beta.BitFlio.com and let us know how you get on / your initial thoughts 😄
-
-
 @ ece127e2:745bab9c
2025-01-29 18:37:16
@ ece127e2:745bab9c
2025-01-29 18:37:16He sentido un asco visceral , inexplicable, profundo , con ganas de hacer desaparecer el motivo que lo causa.
Una repulsión que viene de la sima más cenagosa y que cuando emerge tiene mi peor cara ,la del mal subido al mayor mal conocido.
Una ola de bilis que sube por mi garganta y quiere devorarme y devorar todo lo que me rodea.
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ 2063cd79:57bd1320
2025-02-17 09:12:39
@ 2063cd79:57bd1320
2025-02-17 09:12:39Für diejenigen, die mich nicht kennen: Ich bin Hal Finney. Ich machte meine ersten Schritte mit Kryptographie, in dem ich an einer frühen Version von PGP arbeitete, in enger Zusammenarbeit mit Phil Zimmermann. Als Phil beschloss, die PGP Corporation zu gründen, war ich einer der ersten, die er einstellte. Ich habe bis zu meiner Pensionierung an PGP gearbeitet. Zeitgleich fing ich an, mich bei den Cypherpunks zu engagieren. Neben anderen Aktivitäten betrieb ich den ersten kryptographisch basierten anonymen Remailer.
Springen wir ans Ende des Jahres 2008 und der Ankündigung von Bitcoin. Ich habe bemerkt, dass Krypto-Graubärte (ich war Mitte 50) dazu neigen, zynisch zu werden. Ich war eher idealistisch; ich habe Kryptographie immer geliebt, das Mysterium und das Paradoxe daran.
Als Satoshi Bitcoin in der Kryptographie-Mailingliste ankündigte, wurde er bestenfalls skeptisch aufgenommen. Kryptographen haben schon zu viele großartige Pläne von ahnungslosen Anfängern gesehen. Sie neigen zu überhasteten Reaktionen.
Ich war positiver eingestellt. Ich hatte mich schon lange für kryptografische Zahlungssysteme interessiert. Außerdem hatte ich das Glück, sowohl Wei Dai als auch Nick Szabo kennenzulernen und ausgiebig mit ihnen zu korrespondieren, von denen allgemein bekannt ist, dass sie Ideen entwickelt haben, die mit Hilfe von Bitcoin verwirklicht werden sollten. Ich hatte einen Versuch unternommen, meine eigene, auf Proof-of-Work basierende Währung namens RPOW zu schaffen. Daher fand ich Bitcoin faszinierend.
Als Satoshi die erste Version der Software ankündigte, schnappte ich sie mir sofort. Ich glaube, ich war die erste Person neben Satoshi, die Bitcoin laufen ließ. Ich habe Block 70 oder so gemined und ich war der Empfänger der ersten Bitcoin-Transaktion, als Satoshi mir zehn Coins als Test schickte. In den nächsten Tagen führte ich eine E-Mail-Konversation mit Satoshi, in der ich hauptsächlich Fehler meldete, die er dann beseitigte.
Heute ist die wahre Identität von Satoshi ein Rätsel. Aber damals dachte ich, ich hätte es mit einem jungen Mann japanischer Abstammung zu tun, der sehr intelligent und aufrichtig war. Ich hatte das Glück, im Laufe meines Lebens viele brillante Menschen kennenzulernen, daher erkenne ich die Zeichen.
Nach ein paar Tagen lief Bitcoin ziemlich stabil, also ließ ich es laufen. Das waren die Tage, als die Difficulty 1 war und man Blöcke mit dem CPU finden konnte, nicht einmal mit einem GPU. In den nächsten Tagen habe ich mehrere Blöcke gemined. Aber ich schaltete es ab, weil mein Computer zu heiß wurde und mich das Lüftergeräusch störte. Im Nachhinein wünschte ich, ich hätte länger durchgehalten, aber andererseits hatte ich außerordentliches Glück, dass ich am Anfang dabei war. Das ist so eine halb volles, halb leeres Glas Sache
Das nächste Mal, dass ich von Bitcoin hörte, war Ende 2010, als ich überrascht feststellte, dass es nicht nur immer noch existierte, sondern bitcoins tatsächlich einen Geldwert hatten. Ich entstaubte meine alte Wallet und war erleichtert, als ich feststellte, dass meine bitcoins noch darin waren. Als der Preis auf eine echte Summe kletterte, transferierte ich die Coins in eine Offline-Wallet, wo sie hoffentlich für meine Erben etwas wert sein werden.
Apropos Erben: 2009 erlebte ich eine Überraschung, als bei mir plötzlich eine tödliche Krankheit diagnostiziert wurde. Zu Beginn des Jahres war ich in der besten Verfassung meines Lebens, ich hatte viel Gewicht verloren und mit dem Langstreckenlauf begonnen. Ich war mehrere Halbmarathons gelaufen und hatte begonnen, für einen vollen Marathon zu trainieren. Ich hatte mich zu Läufen über 20 Meilen hochgearbeitet und dachte, ich hätte alles im Griff. Doch dann ging alles schief.
Mein Körper begann zu versagen. Ich sprach undeutlich, verlor die Kraft in meinen Händen und meine Beine erholten sich nur langsam. Im August 2009 erhielt ich die Diagnose ALS, auch Lou-Gehrig-Krankheit genannt, nach dem berühmten Baseballspieler, der daran erkrankt war.
ALS ist eine Krankheit, die Motoneuronen abtötet, die Signale vom Gehirn an die Muskeln weiterleiten. Sie verursacht zunächst Schwäche und dann allmählich zunehmende Lähmungen. Die Krankheit verläuft in der Regel innerhalb von 2 bis 5 Jahren tödlich. Meine Symptome waren zunächst gering und ich konnte weiterarbeiten, aber Müdigkeit und Stimmprobleme zwangen mich Anfang 2011, in den Ruhestand zu gehen. Seitdem ist die Krankheit unaufhaltsam fortgeschritten.
Heute bin ich im Wesentlichen gelähmt. Ich werde durch einen Schlauch ernährt, und meine Atmung wird durch einen weiteren Schlauch unterstützt. Ich bediene den Computer mit einem kommerziellen Eyetracker-System. Es ist auch mit einem Sprachsynthesizer ausgestattet, so dass dies jetzt meine Stimme ist. Ich verbringe den ganzen Tag in meinem Elektrorollstuhl. Ich habe eine Schnittstelle mit einem Arduino entwickelt, so dass ich die Position meines Rollstuhls mit meinen Augen einstellen kann.
Es war eine Umstellung, aber mein Leben ist nicht allzu schlimm. Ich kann immer noch lesen, Musik hören, fernsehen und Filme schauen. Vor kurzem habe ich entdeckt, dass ich sogar Code schreiben kann. Es geht sehr langsam, wahrscheinlich 50 Mal langsamer als vorher. Aber ich liebe das Programmieren immer noch, und es gibt mir Ziele. Derzeit arbeite ich an etwas, das Mike Hearn vorgeschlagen hat, nämlich die Sicherheitsfunktionen moderner Prozessoren, die „Trusted Computing“ unterstützen, zu nutzen, um Bitcoin-Wallets zu härten. Es ist fast fertig zur Veröffentlichung. Ich muss nur noch die Dokumentation erstellen.
Und natürlich sind die Kursschwankungen von Bitcoin für mich unterhaltsam. Ich habe einen Anteil an dem Spiel. Aber ich bin durch Glück zu meinen bitcoins gekommen, ohne dass ich etwas dafür kann. Ich habe den Crash von 2011 miterlebt. Ich habe es also schon einmal erlebt. Einfach kommen, einfach gehen.
Das ist meine Geschichte. Ich habe insgesamt ziemlich viel Glück. Selbst mit der ALS ist mein Leben sehr zufriedenstellend. Aber meine Lebenserwartung ist begrenzt. Diese Diskussionen über die Vererbung von bitcoins sind mehr als nur von akademischem Interesse. Meine bitcoins befinden sich in unserem Bankschließfach, und mein Sohn und meine Tochter sind technisch versiert. Ich denke, sie sind sicher genug. Ich bin mit meinem Erbe zufrieden.

-
 @ 044da344:073a8a0e
2025-02-17 08:50:50
@ 044da344:073a8a0e
2025-02-17 08:50:50Ich nehme alles zurück, was ich je gegen die Filmförderung gesagt habe. Eine halbe Milliarde Euro im Jahr? Na und. Die heile deutsche Welt im Kino? Der Schuss Erziehung? Das Ausblenden der kleinen Leute mit ihren großen Problemen? Mir ab sofort egal. Sollen Produzenten, Regisseure, Autoren ruhig nach immer mehr rufen. Gebt ihnen aus den leeren Steuertöpfen, am besten mit vollen Händen. Diese Woche habe ich gelernt: Sie drehen im Zweifel nur für mich.
Das Kino war leer, okay. Das ist aber nicht mein Punkt. Dieses Kino ist so gut wie immer leer. Meist sitzen meine Frau und ich allein in einem der neun großen Säle und sind manchmal sogar im ganzen Haus die einzigen neben den beiden an der Kasse. Was auf der Leinwand läuft, ist oft frustrierend. Siehe oben. Ich mag aber keinen Verriss schreiben. Sonst würde es an dieser Stelle jeden Samstag um das Kino gehen. Diese Woche waren wir hin und weg. Unser Leben. Unsere Stars. Unsere Sprache. Und das alles weit weg von der DDR und von Ostdeutschland, im Niemandsland zwischen Regensburg und Pilsen.

Ich weiß gar nicht, wo ich anfangen soll. Fidel Castro in Warnemünde. Originalbilder, direkt aus meinem Kindergartengedächtnis. Dann Havanna und die Strände mit diesem Wasser, das einem erlaubt, die eigenen Füße zu sehen. Es gibt viele Kuba-Filme, sicher. Aber wo läuft alles auf ein Revolutions-Quiz hinaus, bei dem sich Ost und West gegenübersitzen, die absurdesten Details aus dem Innersten der Maschine abspulen können und dafür in einem Touristenhotel auch noch bejubelt werden? In welchem Drehbuch kann eine Heldin einfach „blauer Würger“ sagen und wie selbstverständlich voraussetzen, dass jeder weiß, um was es geht? Auflösung: Kristall-Wodka. Das Etikett war blau. Die Flasche kostete eigentlich 16 Mark, aber ich weiß wie gestern, dass ich einmal gleich zwei für 55 gekauft habe, als im Wohnheim der Stoff ausging und ich in den Fresswürfel geschickt wurde, Kosename für die hässlichen Häuser, die es in vielen Neubausiedlungen gab, um einen Anlaufpunkt zu haben für Tanz, Kultur, Saufgelage. Der Abend ist in unser Familiengedächtnis eingegangen, weil mich die Studentin, die später meine Frau wurde, vor die Tür gesetzt hat.
Bei den „Kundschaftern des Friedens“ geht es auch um die Liebe, natürlich. Wir sind im Kino. Es geht aber auch um das Altern und um Erinnerungen, die nicht mehr viele teilen. Wir waren in den 2010ern dreimal in Fidels Reich. Autofahren auf Kuba war der Renner auf einem unserer frühen Blogs, deutlich häufiger geklickt als der Artikel über das Revolutionsmuseum oder der Text, den dann die Freie Presse in Chemnitz übernommen und gedruckt hat, weil der Chefredakteur wusste, dass Kuba für seine Leser immer ein Thema ist. Ein Sehnsuchtsort der DDR-Menschen, erreichbar und zugleich unerreichbar fern, jedenfalls für die allermeisten.

Robert Thalheim erklärt das alles in diesem zweiten „Kundschafter“-Film nicht. Seine Helden reden wie alte Ostdeutsche, wenn weder Wessis zuhören noch die Kinder. Wie meine Frau und ich zu Hause oder in diesem leeren Kinosaal. Über die Schauspieler muss ich nicht viel schreiben. Henry Hübchen, Katharina Thalbach, Corinna Harfouch, Thomas Thieme, Winfried Glatzeder: Das sind unsere Leute. Lebensbegleiter, wenn man so will. So viele sind nicht übriggeblieben. Ich habe ein Buch geschrieben, um zu ergründen, warum Medienmenschen aus dem Osten anders sind und mir vielleicht auch deshalb oft näher. Soll ich den Film empfehlen? Ich weiß nicht recht. Bilder, Musik, sogar der Ton (in deutschen Filmen sonst oft unerträglich): Hier passt schon alles. Vielleicht sage ich es so: Wer den Schlussgag ohne Google versteht, sollte ins Kino gehen. Thomas Thieme sitzt dort in einem Motorboot und lockt ein paar Amis auf das Wilhelm-Pieck-Atoll.
Freie Akademie für Medien & Journalismus
Fotos: Freie Akademie für Medien & Journalismus
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ d360efec:14907b5f
2025-02-17 08:49:15
@ d360efec:14907b5f
2025-02-17 08:49:15ภาพรวม BTCUSDT (OKX):
Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาขึ้น (Uptrend)
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง
- Break of Structure (BOS) ด้านบน
- ยังไม่มีสัญญาณการกลับตัวเป็นขาลง
- ICT:
- ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day ณ ราคาปัจจุบัน
- EMA:
- ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross)
- Money Flow (LuxAlgo):
- สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ
- Volume Profile:
- Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน
- แท่งเทียน:
- แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ
- แนวรับ: EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น
- แนวต้าน: High เดิม
- สรุป: แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาขึ้น (พักตัว)
- SMC:
- HH และ HL
- BOS ด้านบน
- ราคาหลุด EMA 50
- ICT:
- Fair Value Gap (FVG): สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback
- Order Block: ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) เป็นจุดที่น่าสนใจมาก
- EMA:
- ราคาหลุด EMA 50
- EMA 200 เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น
- Volume Profile:
- Volume profile ค่อนข้างสูง
- แนวรับ: EMA 200, Order Block, บริเวณ Volume Profile
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ
(3) TF15 (15 นาที):
- แนวโน้ม: ขาลง (Downtrend) ระยะสั้น แต่เริ่มมีสัญญาณการฟื้นตัว
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) แต่เริ่มเห็น Higher Low
- BOS ด้านล่าง
- เริ่มมีสัญญาณการ Breakout EMA 50/200
- ICT:
- ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่)
- EMA:
- EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross
- Money Flow (LuxAlgo):
- เริ่มมีแท่งสีเขียวปรากฏขึ้น
- Volume Profile:
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA50/200
- สรุป: เริ่มมีสัญญาณการฟื้นตัว แต่ยังต้องระวัง
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น
- แนวโน้มรอง (4H): ขาขึ้น (พักตัว), ทดสอบ Order Block
- แนวโน้มระยะสั้น (15m): เริ่มมีสัญญาณการฟื้นตัว
- Money Flow: Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก
- กลยุทธ์:
- Wait & See: รอการยืนยันการ Breakout EMA 50/200 ใน TF15m
- Buy (เสี่ยง): เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง
- Short (เสี่ยง): ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง
คำแนะนำ:
- Order Block: ให้ความสำคัญกับ Order Block ใน TF4H
- FVG: สังเกต FVG ใน TF4H
- ความขัดแย้งของ Timeframes: เริ่มลดลง (15m เริ่มมีสัญญาณบวก)
- จับตาดู TF15 อย่างใกล้ชิด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ bbb5dda0:f09e2747
2025-02-17 08:13:00
@ bbb5dda0:f09e2747
2025-02-17 08:13:00Alright, This weekly review's gonna be a quick one as i covered my weekend + monday about Sats 'n Facts in the last one. Which leaves us with only a few days, some of which I had to give in and rest as I had been continuing to work with quite a bad cold for too long. The Facts must've been hitting too hard...
Reflecting on networks
A lot of my time this week was reflecting on the event and all the contacts I'd made there. There has been a surprising lot of enthusiasm of the community about Tollgate specifically. There's something that draws me to the project and i think it's not even the flashy-ness of routers paying routers, I'm starting to see the bigger possible implications of the sovereign networks that can grow from this. Not for the western world per se but for places that want to build out new infrastrucutre with their own communities. One of the worries from people to operate TollGates is if they'll get trouble with their ISP's. Which is a legitimate worry, but how long will that worry be relevant?
One thing I realize, as Nostr grows -and Blossom too- is that the data we pull in will be more localized. Imagine a city equipped with a Sovereign Tollgate network. If a few people in your city have watched a video, there will likely be a copy of that video inside the city-wide network. Then if the city get's cut off for any reason, that video will still be very much accessible and people might not even notice the 'internet is down'. I woke up in the middle of the night and had to draw out this visualization of the combination of Clearnet + Tor + TollGate networks and how they can interact with Epoxy proxies in between (visualized by the ♾️ symbol). Anyone that sees an opportunity to bridge the networks can jump in and be that link.
Even attacking (DDOS) services within other networks might become harder, because either: 1) you have to have your botnet reside inside the network of the victim. Which, if it's a small network won't comprise of a significant amount of nodes. 2) you have to have to route your attack through (Epoxy) bridges known to you, the attacker. Which likely have limited bandwidth.
 Anyway, this is just my 3 AM brain-dump. I'll keep chewing on this...
Anyway, this is just my 3 AM brain-dump. I'll keep chewing on this...Marketing TollGate
Like I mentioned earlier there was a lot of interest in Tollgate and to be honest it's been a bit overwhelming, there are so many opportunities like podcasts, meetups and articles opening up to share it and talk about it that I have to think about the form in which I want to relate myself to the project. In any case, these are Good problems to have...
In the meanwhile we've worked on getting a good website landingpage where we can point people to that are interested in the project, it should be up soon! - Consumers can download the Android (for now) app - Operators can download TollGateOS to put on their router - FAQ's
Also, i've been helping out to get some stuff automated. so we can build and push new versions quickly to start getting user feedback and enable iterating on a fast pace!
-
 @ 0463223a:3b14d673
2025-02-17 07:48:11
@ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy!
It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible.
So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey...
3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her!
2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last!
3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life.
A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…)
So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt!
It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
-
 @ a311301f:4663f8f2
2025-01-22 21:39:38
@ a311301f:4663f8f2
2025-01-22 21:39:38```perl
!/usr/bin/perl
use strict; use warnings; use Term::ReadKey;
STDOUT->autoflush(1);
this version run on Windows and use a pwd.txt file created by
the perl program ; otherwise encoding issue may follow
following sub needs to be used first by uncommenting the main call
sub write_password { print ("Enter Password: ") ; my $password =
; my $file_path = 'pwd.txt'; open(my $fh, '>', $file_path) or die "Cannot open file '$file_path' for writing: $!"; print $fh $password; close($fh); print ("\n"); print "Password written to '$file_path'\n"; } sub printhex { my $str = shift ; foreach my $char (split //, $str) { printf "%02x ", ord($char); } print "\n"; }
Function to read password from file
sub read_password_from_file { #unecessary #binmode(STDIN, ':crlf'); my $file_path = shift; #unecessary #local $/ = "\r\n" ; # CR, use "\r\n" for CRLF or "\n" for LF open(my $fh, '<', $file_path) or die "Cannot open file '$file_path' for reading: $!"; my $password = <$fh>; close($fh); #printhex ($password) ;
chomp($password); print "'$password'\n" ; #$password =~ s/\r?\n$//; # Remove newline character #$password = substr($password, 2) ; # BOM File starts with FF FE printhex($password ) ; # "\'$password\'\n" ; #$password = "abcde" ;
return $password; }Main program
sub main { #write_password(); # to uncomment for first use my $correct_password = read_password_from_file("pwd.txt") ; print "Enter password: "; ReadMode('noecho'); # Turn off echo my $entered_password = ReadLine(0); ReadMode('restore'); # Restore echo chomp($entered_password); print "\n";
# Compare entered password with the correct password if ($entered_password eq $correct_password) { print "Access granted!\n"; } else { print "Access denied!\n"; print "'$entered_password' not eq '$correct_password' \n"; printhex ($entered_password); printhex ($correct_password) ; print "The end! \n" ; }}
Call main function
main();
```
-
 @ 35f3a26c:92ddf231
2025-01-22 20:48:34
@ 35f3a26c:92ddf231
2025-01-22 20:48:34Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
What can you do with Script? 1. time locks 2. multi-signature requirements 3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the Taproot upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well Schnorr signatures, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and MAST (Merklized Abstract Syntax Trees) which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The Taproot upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
What is Bitcoin Covenants?
It is a BIP (Bitcoin Improvement Proposal), BIP-347, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are Ethan Heilman and Armin Sabouri, now the community will debate its merits.
Here the link, in case you are curious:
https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
Controversy
The controversy revolves around two main camps:
- Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
- Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
Final Thoughts
Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
- How will that change affect the security of the network?
- How that change will affect the blockchain usage?
- What is the projected impact over the fees per transaction if this change is approved?
- Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
https://rodswallet.unstoppable/
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-
 @ b17fccdf:b7211155
2025-01-21 18:10:10
@ b17fccdf:b7211155
2025-01-21 18:10:10Link to the bonus guide ~ > HERE <~
Some notes:
ℹ️ For the moment, this guide will touch only the case of an only testnet mode situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide.
ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode.
Enjoy it MiniBolter! 💙
-
 @ fd78c37f:a0ec0833
2025-02-17 07:15:15
@ fd78c37f:a0ec0833
2025-02-17 07:15:15In this edition, we invited Kelvin from Bitcoin Chama to share how his community is leveraging Bitcoin to build a self-sustaining ecosystem in rural areas.
YakiHonne: Kelvin, thanks for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Today, we’ll be diving into your community. So, let’s start—tell us a bit about yourself and what you do?
Kelvin:I'm Kelvin, the founder of Bitcoin Chama, a rule-based Bitcoin community with a mission to build a self-reliant Bitcoin circular ecosystem. How do we achieve this? We empower young people and our community economically by introducing accessible, low-resource projects that require minimal time and space to implement. We then encourage them to save their earnings in Bitcoin, promoting financial independence and long-term sustainability.
YakiHonne: Given Bitcoin’s increasing value, it’s almost like owning property, but in the form of a digital asset. That’s an incredible concept and a really great initiative!Now, let’s dive into today’s questions. What initially sparked your interest in Bitcoin, and what motivated you to build a community around it?
Kelvin:Initially, I didn’t know much about Bitcoin. But I had a friend who worked at Boda Boda. He was trying to save up his earnings to buy iron sheets and build a better house for his family. Since he didn't get enough money from Boda Boda, he saved whatever little he could in a bank, a savings group. Over the course of two years, when he finally went to withdraw his money, he realized that the price of iron sheets had increased by almost 100% Originally, he had planned to buy 30 iron sheets, but by the time he withdrew his savings, his money could no longer afford that many. For someone who works so hard to earn a living, this was a major setback. Kelvin:That’s when I started thinking—how can we solve this problem? At the time, I didn’t know much about Bitcoin or how money really works. But seeing my friend struggle, I realized that the real issue wasn’t just rising prices, but the financial system itself. Kelvin:Then, later that year, I was introduced to Bitcoin, and it suddenly clicked! If my friend had saved in Bitcoin instead of fiat, his purchasing power wouldn’t have been eroded. In fact, he might have even been able to afford nails, labor costs, or additional materials. That realization led me to create Bitcoin Chama—a community to help people save in Bitcoin and protect their hard earned money.
YakiHonne: It sounds like you were inspired by how Bitcoin’s value appreciates over time, much like an investment in land that continues to grow in value. That’s a truly powerful concept behind Bitcoin.Now, could you share how your community first got started and what strategies you used to attract members in the beginning?
Kelvin:Building a community from scratch—especially a Bitcoin community—isn’t easy, particularly in a rural area of Kenya where many people lack internet access and don’t even use smartphones. At first, my focus was purely on Bitcoin education. I would go out, meet people, and teach them about Bitcoin. But I soon realized that while knowledge is valuable, most people didn’t have the means to earn and save in Bitcoin. Kelvin:That’s when I came up with a different approach. Instead of just educating people, I decided to create small projects that could generate income, sponsor these projects, and help them grow. Over time, as people started earning from these projects, they could begin saving their income in Bitcoin. Kelvin:We’ve now been running Bitcoin Chama for almost a year—since May last year. The impact isn’t massive yet, but for a community just getting started, it’s been a significant step forward. Every small step matters, and while growth takes time, I believe these small beginnings will eventually lead to something big in the future.

YakiHonne: It's a wonderful start,So far, what challenges have you faced while building and growing the Bitcoin Chama community?
Kelvin:I don't have many challenges—just two main ones.The first challenge is poverty. Whenever you introduce someone to Bitcoin, you often have to explain its history. Imagine telling someone that in 2010, Bitcoin was worth about $1, and by 2013, its value had increased significantly. Fast forward to 2025, 15 years later, and Bitcoin is now worth around 13 million Kenyan shillings (about $100,000). When people hear this, they see it as a great opportunity to escape poverty. The problem is, they often perceive Bitcoin as free money, rather than understanding it as a long-term investment or financial tool. The second challenge is scamming. Many people think Bitcoin might be a scam. This is a common issue in many communities.
YakiHonne: Yes, especially the second challenge—people thinking Bitcoin is a scam. This is very common in many emerging communities. A lot of people feel that since they can't see Bitcoin physically, it’s not real, which leads them to doubt its authenticity.Finding a way to convince people of Bitcoin’s legitimacy is crucial. So, what principles guide your community? And how do you maintain trust and reliability in your discussions?
Kelvin:So, in our community, I’ve discovered something—I’ve found saccos. Right now, I have two saccos(Chama) , and I intend to grow them over time. Within these two circles, we use the Machangura app. The app has an option for creating a clan, so we organize people into two saccos, forming two clans. We then add all members from each sacco into their respective clan. This setup ensures a trustless system. For example, if someone wants to withdraw money from their shared account or sell Bitcoin, the system notifies all members. This way, everyone stays informed, and people don’t have to feel insecure about the funds they have saved.
YakiHonne: So at least that’s how you maintain integrity, transparency, and trust within the community. So How does your community educate its members and keep them updated on Bitcoin developments?
Kelvin:I am the founder of Bitcoin Chama, and right now, I’m mostly focused on community activities. We usually hold meetups oftenly, but I wouldn’t say we focus entirely on Bitcoin only. Instead, our discussions are more about how to improve what we do, grow more, and build new projects. That’s the main focus for me at the moment. That said, I am planning to start physical Bitcoin lessons. Since Bitcoin Chama is located in my community, I know that a lot of people visit the area—many come here to shop and buy things. So, I plan to post a notice at the location, inviting new members who are interested in learning about Bitcoin. We’ll create a timetable so that people can come at specific times to attend lessons. Additionally, we’ll leverage our existing clients and brainstorm ways to make this work for a wider audience.
YakiHonne: It's still part of the education process,maybe not fully in-depth, but it’s still valuable. So, that’s actually a good thing. You guys are doing something very meaningful, which is great.The meetups also serve as a way to educate people about Bitcoin, making them an important part of the process. It’s definitely a solid approach. YakiHonne: So, Kelvin, how does your community collaborate with the broader Bitcoin ecosystem? And what partnerships have you formed so far that have had the biggest impact on BitcoinTerminal?
Kelvin:We haven’t had any major collaborations yet. So far, we’ve been riding solo. We’ve had some support from friends and well-wishers, but we haven’t partnered with any major organizations yet.
YakiHonne: That’s okay! You guys will get there very soon, I’m sure of it. So far, in the process of building your community, what initiatives have you taken to promote the adoption of Bitcoin in your local environment?
Kelvin:Well, besides our existing clients, we have about three shops that currently accept Bitcoin payments. I’m still working on overcoming the major challenges we face while also trying to find ways to encourage people to use Bitcoin in their daily lives. Kelvin:First, I need to support the people who are already part of our community, making sure they have the resources and knowledge they need. I don’t know if I’m fully answering the question, but this is what I’m working on. I’m not solely focused on growing a large community right now. Instead, I’m focused on quality growth—on educating people who truly understand Bitcoin, know how to use it, and grasp what it really means. My approach is to start small and expand gradually, ensuring that at each stage, people gain a deeper understanding of Bitcoin and how it can impact their lives.
YakiHonne: I’m sure you guys will succeed. You don’t necessarily have to start big, but I believe you’ll grow much faster than you expect. With the effort and passion you’re putting in, I have no doubt that Bitcoin Chama will expand significantly. So,moving on to my last question,what are your community’s goals for the next 6 to 12 months? And how do you see it evolving with Bitcoin’s development?
Kelvin:My goal for the next year is to continue the projects I’ve been working on. We have a community team that serves as a gathering point where people can come together, coordinate meeting times, and discuss Bitcoin and our future plans. Kelvin:so far for example, we built and distributed 15 beehives to different young people in our community. They harvest honey, sell it, and save the earnings in Bitcoin. We piped free clean water which can be accessed by any member in our community, significantly improving daily convenience.
 Kelvin:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.
Kelvin:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.
 Kelvin:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland.
Kelvin:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective.
Kelvin:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland.
Kelvin:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective.YakiHonne: I truly love all the ideas behind this. I admire the fact that you are giving back to the community and that people are experiencing real benefits from the Bitcoin ecosystem. This way, they have something positive and meaningful to say about Bitcoin. YakiHonne: Thank you so much, Kelvin, for joining us today. We’ve reached the end of our interview, and I’m really happy to have had this conversation with you. We look forward to seeing Bitcoin Chama grow!
-
 @ b17fccdf:b7211155
2025-01-21 18:04:28
@ b17fccdf:b7211155
2025-01-21 18:04:28Available at: https://minibolt.info
Main changes to the version 1:
- The complete guide has been migrated to the new design visual builder web tool platform gitbook.com
- New modern UI (responsive, full width, and better visual items)
- New menu structure for a better user experience
- New visual items to improve the navigation through the web page
- New switch to enable light/dark theme
- Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain
Other changes:
- New MiniBolt Linktr forked of the alternative FOSS project proposed by Gzuuus
- Changed MiniBolt from a personal project to an organization so that the project has its own identity
- New email contact address hello@minibolt.info to receive proposals and give support
- New resources folder with the current MiniBolt roadmap, network map diagrams, and others
ℹ️ More info:
- The new version is available with the known domain: minibolt.info but from now on links associated with the new v2 version were shared using the v2.minibolt.info subdomain due to a GitBook limitation
- The old and deprecated v1 will be still available at a time in the subdomain v1.minibolt.info, but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens
- Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder gitbook.com
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:47:28
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > HERE < ~
Some sections of the guide:
- Generate SSH keys
- Import SSH pubkey
- Connect to the MiniBolt node using SSH keys
- Disable password login
- Disable admin password request
Some shortcuts to the Extra sections:
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:39:34
@ b17fccdf:b7211155
2025-01-21 17:39:34Link to the bonus guide ~ > HERE < ~
⏰ Recently added an update that includes a new section How to detect Ordinals transactions and verify Ordisrespector filter works to verify that Ordispector is filtering and burning Ordinals correctly 🔥
Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:42:38
@ dbe0605a:f8fd5b2c
2025-02-17 06:42:38Originally posted on Nostr: https://highlighter.com/a/naddr1qvzqqqr4gupzpklqvpdfcuch9wkh2gary7erd4275jmrf6qw0z5sz0dhj8u06kevqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszxrhwden5te0ve5kcar9wghxummnw3ezuamfdejj7qgwwaehxw309ahx7uewd3hkctcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzqjn0d9hz6argv5k57ur9dck5y6t5vdhkjm3df4shqtt5xduxz6tsrdmw7l
I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.
Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.
Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better
Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.
Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
originally posted at https://stacker.news/items/888088
-
 @ b17fccdf:b7211155
2025-01-21 16:49:27
@ b17fccdf:b7211155
2025-01-21 16:49:27What's changed
- New method for Bitcoin Core signature check, click ~ >HERE< ~
- GitHub repo of Bitcoin Core release attestations (Guix), click ~ >HERE< ~
History:
~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >HERE< ~
~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >HERE< ~
Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 16:30:11
@ b17fccdf:b7211155
2025-01-21 16:30:11Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap?
Go to the bonus guide by clicking ~ >HERE <~
Enjoy it MiniBolter! 💙
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
@ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
\ I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.

Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.

Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better

\ Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.

Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin.
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
-
 @ b17fccdf:b7211155
2025-01-21 16:23:44
@ b17fccdf:b7211155
2025-01-21 16:23:44Build your nostr relay step by step on your MiniBolt node! (easily adaptable to other environment) No need to trust anyone else! Be sovereign!
~> Go to the bonus guide by clicking ~> HERE< ~
~> This guide includes a complete extra section to cover the different processes for using nostr as a user and relay operator.
PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address:
wss://relay.minibolt.info~> Let a review on noStrudel or Coracle of your experience using it.
Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
-
 @ da0b9bc3:4e30a4a9
2025-02-17 06:31:19
@ da0b9bc3:4e30a4a9
2025-02-17 06:31:19Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/888083
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ 783850fd:77511d32
2025-01-20 13:22:54
@ 783850fd:77511d32
2025-01-20 13:22:54I'm thinking about buying a small house or a plot of land in Morocco and living there. The amount I am willing to pay for this would be $10 000 - 30 000. How much might I liquidate into their fiat (MAD) bank account with a month or so without them freezing my account and god only knows what worse things them doing to me. I use robosats and never exceed the amount of 950 euro when selling Bitcoin. I have all my wealth in Bitcoin, no history of income over the last 5 years, no filing tax returns too. I am from the EU, residing in Spain. How has your experience with Morocco been? Can one open a bank account in Morocco without having a residence there?
originally posted at https://stacker.news/items/857178
-
 @ 9349d012:d3e98946
2025-01-19 19:47:15
@ 9349d012:d3e98946
2025-01-19 19:47:15For many reasons, not least of those the outcome of the last US presidential election, I’m now working on Librarian Detective, Book Two as my creative release. At the moment, I’m already on chapter seven, which means I made it through writing the second chapter, always an admirable hurdle to clear. If you’ll recall, with Librarian Detective, Book One, clearing that milestone was a challenge. It took between nine and 12 years to finish that book, although I wrote three books in those meantime years. This was partly because of working on my day job business more fulltime (MyLibrarian! Our app is out, sign up to test on the pop up here) but also because I revamped my entire writing process, which I’ll share with you.
Here’s a picture of the writing methods I use. I went from writing longhand to digitally, which is more efficient, and I also use a series of guides to help organize the writing process: An outline, character list, calendar timeline, editing checklist and the main writing doc itself.
Seven years ago when I realized my writing method was working for me, I started doing a video series on Writing, called On Storytelling, filmed at all the remote locations I work at, one of the best of which I’m at right now, working on my new book. If you are looking for more writing resources, there’s a list on my blog. When you go down these rabbit holes you may come out ready to write your first book.
GOOD LUCK—MEZ
Originally appeared on https://www.michellezaffino.com/my-writing-methods/
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6e0ea5d6:0327f353
2025-02-17 01:04:37
@ 6e0ea5d6:0327f353
2025-02-17 01:04:37Ascolta bene, sì? In the game of business, as in chess or the streets of Palermo, there are times to advance like a ruthless king and times to wait like a wolf stalking its prey. Those who fail to grasp this distinction are doomed to be taken down before they even see the sun rise.
Prudence is the sharp blade that separates the wise man from the fool who rushes headlong into the enemy’s spear. Those who act without weighing the consequences end up as the corpses rotting on the sidewalks of unbridled ambition. But understand this well—prudence is not cowardice. The coward hesitates out of fear; the prudent man waits because he knows the right moment to strike. The difference? One crawls, the other conquers.
Fortis Fortuna Adiuvat—fortune favors the bold. But boldness without calculation is like a man crossing a minefield blindfolded. Greed blinds, destroys, and devours the reckless like a raging sea dragging bodies to the depths. You see it every day—entrepreneurs who rise too fast and crumble at the first crisis, young men who burn through their earnings chasing illusions of instant wealth, fools who trust too much in friends already hiding the dagger up their sleeve.
There’s a reason why great men endure while mere opportunists vanish like smoke in the wind. They understand that every battle has its time, every strike must have precision. Trade the cleaver for the scalpel—the butcher wounds without thought, the surgeon cuts with precision and saves his own skin.
Dimmi, quale vuoi essere? The fool who charges into war without a shield, or the strategist who, in the end, sits at the banquet of victory? The answer is not in what you say, but in what you do while others waste their opportunities.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 6e0ea5d6:0327f353
2025-02-17 00:53:36
@ 6e0ea5d6:0327f353
2025-02-17 00:53:36Ascolta! When you allow the flame of ambition to fade within your chest, you inevitably drift toward petty and foolish concerns unworthy of an adult. In other words, the moment you abandon your dedication to grand objectives—precisely due to idleness—you will end up entangled in trivial matters, thus weakening your masculinity. Lacking the responsibilities inherent to a grown man, you will inevitably behave like a boy in all aspects of life, including relationships.
He who is truly determined to win in life has neither the time nor the energy to engage in matters of neediness, jealousy, or fear of abandonment.
Love, as it is often romanticized, is a dangerous illusion that leads us to reckless and self-destructive behaviors. The romantic ideal, propagated by poets and dreamers, makes us vulnerable to manipulation and disappointment.
A man who is aware of his value remains focused on what truly matters, and because he understands the weight of his priorities, that alone is enough.
Weakness does not inspire confidence. In a world where strength and determination are essential for survival and success, showing weakness is signing your own sentence of irrelevance. A man must be the foundation upon which the relationship stands. He must be the unshakable rock amid life’s storms. Life is a game of power and influence, and those who fail to understand this are doomed to failure.
Take care of yourself. Strengthen your body, your mind, and your spirit. Be an example of determination and courage. The woman by your side must see in you a leader, a visionary, someone destined for great achievements. Only then will you earn not only her respect and admiration but also full control over your own destiny.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ a0c34d34:fef39af1
2025-01-14 14:28:28
@ a0c34d34:fef39af1
2025-01-14 14:28:28I feel fabulously free, I deleted TikTok. I am spending less time on my phone and more time developing Onboard60. I never expected to go from the Metaverse to A.I. healthcare and NFCC medical bracelets.
I was on Vine, Twitter back in 2009… I went from 8 second nonsensical videos and funny tweets to diving deeper down any rabbit hole I ever imagined.
In 2016, I heard a little noise about Bitcoin and I haven’t gotten off the rollercoaster of a merry go round yet. If you know, you know.
I found Nostr awhile ago but I’m no maxi, I’m curious. I learned about different things pertaining to blockchain and cryptocurrency, social media and protocols.
I kept journals of my fears and conferences I experienced and published them as my first years behind the scenes of a senior citizen diving deep into the unknowns.
Someone had to tell me I was a senior citizen. I’m 64 now , that was four years ago. Since then I took a crazy idea and started Onboard60.
I created a curriculum for myself. For years I have learned a variety of subjects. I took the basics and made a cliff note booklet - Web3 1101 for Seniors.
I didn’t want to be left behind so I learned Spatial and created an auditorium, an art gallery and an office. It was my attempt to get senior citizens involved to connect with their grandkids in virtual reality like Roblox.
Over the years, I’ve written articles on Substack sharing my journey, and sporadically posted on Zentaurios. I remember writing on YakiHonne when I first discovered it.
Onboard60 has become more than what I ever thought it would be, as I started just sharing my journey in hopes others would join me.
I hoped senior citizens would be interested in learning how to put their trust funds, H.O.A.s, POLSTs and other senior citizen documents on chain.
The past four years, nothing until I speak of medical bracelets. I do not mention BitDoctor AI or mirrors that do body scans. Bracelets, I speak bracelets.
The focus is to keep senior citizens up to date with new technologies that focus on improving their quality of life.
Finding YakiHonne again is refreshing. The esthetics clean, seemless cross posting, and better options for posting. Soft landing.
I have learned a lot over the years, experiencing this space becoming , watching protocols grow, some platforms fizzle, creating a new world isn’t easy.
I’m enjoying being a mermaid in Monniverse community on Farcaster, not Farcaster itself but enjoy being a mermaid. Monniverse is a decentralized animation production company. I’m learning how to use the image generator and like the global reach.
I have compromised on so many social media sites just to be on them. I still frequent Twitter Onboard60, and have my old Vine group on Instagram. I spend time on Lens mostly.
I use traditional media to share Onboard60 - LinkedIn and YouTube for Onboard60. I am creating a digital replica of all the information, subjects, videos, content that I created as Onboard60. I hope to keep it updated as times goes forward.
I’m going to use my guide to IRL events at Blockchain Miami in a few weeks, WAGMI MIAMI. After so many conferences and events, I had to write down a step by step how to get through these and follow up after. They can be overwhelming and I needed a way to decompress. My guide helps me.
I seem to be rambling. I don’t have a purpose or any value to share with this article, I just wanted to share my thoughts for now, walking into 2025.
Sandra ,Samm,Sababa
Onboard60, founder
-
 @ c0a57a12:8b230f7a
2025-02-17 00:08:04
@ c0a57a12:8b230f7a
2025-02-17 00:08:04Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom.
Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was risk. They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence.
And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for everything. How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: only do what is approved.
And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t know how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do.
And you know what? We’re no better. When’s the last time you did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a free man instead of a well-behaved tax mule hoping the system doesn’t notice you?
We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a good one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines.
And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t choose this. Like we didn’t let it happen.
So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell.
Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself.
Your call. But either way, don’t pretend to be surprised.
-
 @ 58937958:545e6994
2025-01-13 03:31:48
@ 58937958:545e6994
2025-01-13 03:31:48I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."

The method is the same as making regular croquettes. I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.

The face is made with seaweed and sliced cheese. The arms and legs are made with fish cake (hanpen). I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.
 The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.
The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.Here’s Bitcoin Croquette squished into a bento box:

Halving

Notes
- I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation.
- The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions).
The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time!
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ 58937958:545e6994
2025-01-13 03:19:17
@ 58937958:545e6994
2025-01-13 03:19:17Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました

作り方は一般的なコロッケです 試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが 粉をつける前に手足がもげました

顔はのりとスライスチーズ 手足ははんぺんです 足は醤油をつけてトースターで軽く焼いたら茶色になりました
 手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました
手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました弁当箱に押し込まれてるコロッケくん

半減期

メモ
- タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう
- 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ)
ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ 5a261a61:2ebd4480
2025-02-16 21:54:41
@ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves.
It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
-
 @ 558e15eb:efa6e980
2025-01-12 19:23:42
@ 558e15eb:efa6e980
2025-01-12 19:23:42[2025-02-07] Øy 5 year anniversary - Talk show and watch party @ online
Øy 5 year anniversary - Talk show and watch party online - https://lislegaard.stream/ (https://lislegaard.stream/)
(Friday, 7 February 20:00)

https://do.basspistol.org/event/oy-5-year-anniversary-talk-show-and-watch-party
-
 @ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41
@ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention. The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests.
2009: A Manufactured Uprising
In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi prematurely declared victory. This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The BBC took the lead, publishing outright fabrications about mass uprisings—falsehoods they were later forced to retract.
Then came the Twitter storm. On June 13, a sudden flood of 30,000 tweets, many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The Jerusalem Post quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations.
The Blueprint: Iran 1953—The CIA’s Original Coup
This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister Mohammed Mossadegh made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the CIA launched Operation Ajax, an insidious regime-change operation that became the prototype for future coups.
The CIA’s strategy was as ruthless as it was effective: * Staged bombings blamed on Mossadegh’s government * Islamist agitation funded and nurtured to turn public sentiment * Propaganda campaigns demonizing Mossadegh as a secular threat * Bribery of officials and military leaders to ensure betrayal
The result? The overthrow of Mossadegh and the installation of the pro-Western Shah, whose reign saw brutal repression under the secret police SAVAK—trained by the CIA and Mossad. The template was established. From Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s), the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal.
A New Strategy: Economic Warfare and the NGO Takeover
With direct coups becoming too risky, a subtler method emerged: economic strangulation. Enter the International Monetary Fund (IMF). The play was simple: 1. A corrupt dictator takes out massive loans for projects the country cannot afford. 2. The country inevitably defaults, giving the IMF the power to restructure its economy. 3. Western corporations move in, plundering national resources under the guise of “recovery.”
This scheme was exposed in 2001 when former World Bank chief economist Joseph Stiglitz blew the whistle on these manufactured debt traps. Further details emerged in 2004 with John Perkins' “Confessions of an Economic Hitman”, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain.
But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights.
Color Revolutions: The Soros Connection
Enter the age of the NGO-driven color revolutions, where regime change is disguised as a people’s uprising. Organizations like the Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED) became the new weapons of choice. These NGOs: * Fund and train opposition groups * Coordinate mass protests during elections * Provide media support to delegitimize governments
The results? A series of destabilizations across the world: Ukraine (2004 - Orange Revolution) Lebanon (2005 - Cedar Revolution) Georgia (2003 - Rose Revolution) Kyrgyzstan (2005 - Tulip Revolution)
Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the fingerprints of Soros, the billionaire financier with a long history of manipulating global politics to serve elite financial interests.
However, this strategy has started to backfire. Georgia witnessed a major anti-Soros backlash, and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "Grape Revolution"—have faltered as people wake up to the deception.
Iran 2009: An Operation in Plain Sight
While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of Mir-Houssein "Butcher of Beirut" Mousavi raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again: 1. Foment unrest through digital manipulation and street protests. 2. Control the narrative via Western media outlets. 3. Install a leader more compliant with Western economic and geopolitical interests.
Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations.
As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue.
-
 @ 5a8e581f:c150c8ba
2025-01-11 18:31:08
@ 5a8e581f:c150c8ba
2025-01-11 18:31:08Doing Bitcoin the right way is hard.
If Bull Bitcoin wanted to take the easy path, we would have done what all the other exchanges are doing and would simply have offered a custodial wallet to our users. But our mission is not to sell numbers on a screen, fake paper bitcoin and IOUs. Our mission is to create sovereign individuals. If our clients don’t take full control over their wealth, we have failed them.
If we wanted to take the easy path, we would have offered shitcoin trading, NFTs, ICOs, yield and all sorts of nonsense. No doubt, we would today be far more wealthy.
But we would have failed in our mission to establish a universal Bitcoin standard and fixed the problems created by easy money. We would have compromised on our values and sold products that we don’t believe in and we don’t personally use.
If we wanted to take the easy path, we wouldn't have spent years building open-source software that lets any business run their own self-hosted Bitcoin wallet API infrastructure connected directly to their own Bitcoin, Lightning and Liquid network nodes. We would have just done a deal with Coinbase or another third party to take care of the Bitcoin engineering on our behalf.
But we would have failed in our mission to help keep the Bitcoin network decentralized and resilient to institutional failures. We would have lost our direct and precious connection to the Bitcoin network.
The engineering, operational and logistical challenges involved in maintaining a noncustodial Bitcoin service like Bull Bitcoin, in an environment where Bitcoin network fees are increasingly high, while also maintaining an accessible user experience with minimal compromises on the cypherpunk principles of Bitcoin… are impossibly hard to fathom for the vast majority of Bitcoiners.
Despite consistently taking the most difficult path at every turn, Bull Bitcoin has nonetheless been crushing it for the past 10 years thanks to our Bitcoiner ethos and mindset, sticking to our core values and creating products with a singular focus: engineering sovereignty.
All of this we accomplished without any outside funding. Every sat invested in Bull Bitcoin was acquired by offering a service valued by our customers. Every network fee we pay, every investment in R&D comes straight out of our pockets. If our bitcoin-only noncustodial model fails and we become unprofitable, there will be no bailout.
As a low-time preference business, taking the hard path today means we will have a unique competitive advantage in the future. Nobody uses Bitcoin more than a non-custodial exchange. Every trade and every revenue generating activity is derived directly from a Bitcoin payment. We are keenly aware of every possible problem that Bitcoin users may be facing, because we are ourselves are a power user. We know what kinds of problems the users will face, what solutions we need to build and how we must adapt. We always skate where the puck is going.
But there is another, more noble purpose to choosing the hard path.
I'm also heavily involved in a community circular economy project in Costa Rica called Bitcoin Jungle. We spend countless hours to educate locals, set merchants up with Bitcoin point of sales, and build the infrastructure necessary for Bitcoin to thrive as a medium of exchange in even the most rural areas. All of this we do for free, and in fact it we pay for it out of pocket! I discovered recently that a few people were skeptical of our efforts. I met one of them and he asked us “but why are you doing this, if you don't make any money from it”.
We do it because we love Bitcoin. We believe in the ideology of Bitcoin, its underlying cypherpunk and free market principles. We do it because we as sovereign individuals cannot live in isolation and we all benefit from the success of our communities. We do it because we want our kids to grow up in a world that is free from the evils of Fiat currency. May our children never suffer the corruption of participating in a socialist economic system that steals their time and their wealth by the simple fact of interacting with fiat currency. We do it because doing it is a moral imperative. In a world of systematic injustice, doing nothing is to be complicit. You cannot live a virtuous life with the knowledge that you had the capacity to act heroically but chose to capitulate.
Bitcoin is at the center of a spiritual war between forces of corruption and forces of liberation. There is a higher power that calls us to become the resistance. Bitcoin is hope. Bitcoin is salvation. If Bitcoin fails, everyone on earth is truly and utterly fucked.
We are on the cusp of a fundamental civilizational change. The global debt-fueled fiat ponzi is imploding right before our eyes. What comes next is up to us to determine. We are the right place and the right time. We have a unique window of opportunity that may not come again within our lifetimes and that of our children.
The choices we make today will shape what the world looks hundreds of years from now. Whether our descendants live in totalitarian dystopias or will be ushering in a new era of prosperity and freedom depends on our willingness to choose the hard path today.
And if you think the hard part is over and that Bitcoin has already won, think again. During our decade of operational experience, there were few serious attacks on the Bitcoin network. Bitcoin had relatively low levels of adoption and apart from a few periods of intense fee spikes and the fork wars of 2017, it was smooth sailing. Bitcoin was mostly flying under the radar, left to develop organically in the hands of its cypherpunk caretakers.
This era of complacency is over. From now on, everything is about to get much, much harder. This is what we live for! Nothing easy is worth pursuing.
Bull Bitcoin hasn't given up on Bitcoin's mission to free humanity from the shackles of fiat slavery and centralized systems, we are reinvigorated by the challenges that Bitcoin is facing and that will continue to intensify.
We will not give up on Bitcoin's use case as a medium of exchange and we will continue to build tools that make it easy for anyone to opt out of the traditional banking system to conduct peer-to-peer transactions securely, as was originally intended by Satoshi when launched the Bitcoin project.
This new epoch, Bull Bitcoin is leveling up to an entire new standard for consumer-facing Bitcoin apps, higher than anyone has ever seen. We have been thinking about how to make our unique noncustodial model work sustainably long-term for years. This is the hill that we choose to die on.
But as we entered into a new Bitcoin epoch, I've witnessed many in the Bitcoin community become cynical, fatalistic and even depressed. It’s hard to blame them.
Privacy-preserving tools are being shut down. The Lightning Network is suffering scalability issues. The Bitcoin blockchain is being spammed by degenerate NFT gamblers, driving up transaction fees for everyone else. Bankers and Wall Street insiders are accumulating Bitcoin fortunes and promoting exchange traded funds as an alternative to self-custody. Bitcoin mining is being heavily centralized among a small group of American-based public companies. It sometimes feels like Bitcoin is under attack by various nefarious interests that want to control it and corrupt it.
Even from within our own community we are suffering from prophets of doom spewing fear, uncertainty and doubt. Many sneer that Lightning is broken, that Bitcoin has been co-opted by Wall Street. Some say we should give up and switch to altcoins. Some pundits blame “lasereyed maxis” for blocking protocol changes and claim that being conservative about modifying the rules of Bitcoin means “ossification” and that's the reason why Bitcoin has high fees. Others are pushing the idea that Bitcoin was never meant for payments anyway and that being a store of value was always the main goal of Bitcoin. Who cares about the poor? The plebs can always keep their funds on an exchange.
At Bull Bitcoin, we see it very differently. We have a realistic and optimistic approach towards building a bright future for Bitcoin. I have never been so bullish on the future Bitcoin as I am today.
Make no mistake: the core principles of Bitcoin self-custody, censorship-resistance and privacy are under attack. But the Bitcoin community possesses a unique advantage that will ultimately allow us to prevail: not only do we have skin in the game, we have soul in the game.
Our tribe of a few thousand cypherpunk Bitcoin maximalist fanatics stand against an empire of fiat clones, millions of faceless cogs in a soulless machine. I like our odds.
While I agree that we should never take Bitcoin’s success for granted, the bleak picture that some want to paint regarding the state of Bitcoin is detached from reality.
We've already achieved incredible technological miracles. The fact that it is possible for a user to run a Lightning network node on a mobile device and make fully trustless payments is a monumental achievement. Despite what they claim I can guarantee that no other shitcoin or fiat payment system has anywhere near the level of sophistication of Bitcoin. It is an incredibly bullish sign for the Bitcoin ecosystem that we have achieved a level where users can remain fully sovereign if they have the means.
Scaling Bitcoin so that it can enable hundreds of millions of people to become sovereign individuals is the most pressing challenge of our times. Our community must accept inevitable realities: not everybody will be able to afford on-chain transactions. The success of Bitcoin means that one day, during our lifetimes, a single Bitcoin translation will cost hundreds of dollars.
Upgrading the Bitcoin protocol may allow us to create tools that enable a more secure, censorship-resistant and private payment mechanism, but no soft fork can fix the fundamental tradeoffs of the Bitcoin protocol.
But this doesn't mean that we should either give up on Bitcoin’s value proposition as a medium of exchange, or that we must fork bitcoin according to the whims of whoever is trending on Twitter, nor should we capitulate to traditional exchanges acting as banks for the vast majority of users.
To fix the inconvenient and expensive user experience that most people are suffering in times of high fees while making the minimum amount of compromises, you need vision and execution.
There is an army of shadowy super coders that, like us, have dedicated their lives to ensure that Bitcoin becomes the universal medium of exchange, store of value and medium of account. We come from different walks of life and we have different strategies. Some of us work on self-sovereign consumer applications. Other focus of privacy protocols, mining decentralization, second later payment networks, e-cash protocols, and finally, as a last resort, some are working to add changes to the Bitcoin protocol which can enable tools that we currently cannot build.
At Bull Bitcoin, our vision of the future Bitcoin experience is crystal clear. It is a vision of success and integrity, where the path of least resistance for the user is also the path of least compromise.
We, the Bitcoin builders, will make it real.
-
 @ 6ad3e2a3:c90b7740
2025-01-10 12:33:47
@ 6ad3e2a3:c90b7740
2025-01-10 12:33:47The excesses of wokeness are thankfully getting their overdue correction, but as often happens with corrections, they tend to overshoot. A case in point was from the usually reasonable writer Wesley Yang on Twitter, who posted the following:
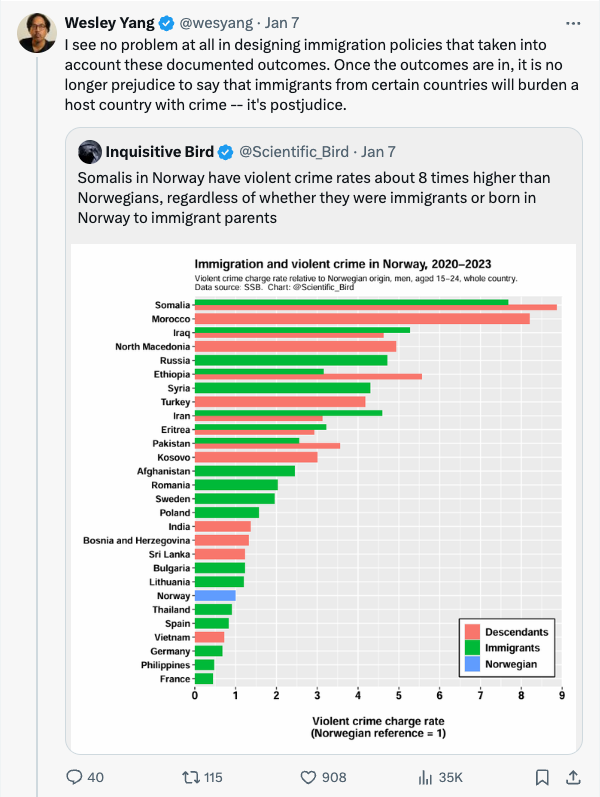
Poor long-term immigration policy has apparently led to too many foreign-born and native criminals of foreign descent in Norway, a disproportionate number of whom, per the chart, hail from Somalia and Morocco. Yang argues using this data to inform Norway’s immigration policies going forward is both unproblematic and “no longer prejudice.”
This is a sleight of hand. You can advocate for designing prejudicial immigration policies based on the group to which an individual potential immigrant belongs, but you cannot both do so and pretend it is not prejudicial.
This is not a point about what countries should or should not DO. They are free IMO to design immigration policies as they see fit, and there are arguments to be had over that. But there is a reactionary blindness wherein people pretend that grouping individuals by race, religion or country of origin isn't prejudicial to those individuals who have no control over how others in their assigned group behave.
The grouping is justified in their view by "data" or "statistics" or "reason." The truth is most of us still view "prejudice" as negative, so no one advocating for discriminatory immigration policies wants to be considered prejudiced. They are for the policy, think it's good, and therefore try to pretend it's not prejudiced when it obviously is.
Don't pretend. If you're for prejudicial, discriminatory immigration policies "for the greater good", just advocate for it on those terms. Be honest about what you're saying.
This might seem like a trivial point on which to base a post, but I don’t think it is. It’s not because “prejudice is bad” or “racism!” That’s just one type of instance in which this midwit tendency — to assign individuals to a group and then pretend you are being “data-driven” — rears its terrible head. I remember a couple years ago people on Twitter accused me of “taking up an ICU bed” because I refused to inject myself with Pfizer’s latest. Their reasoning was similar: because the unvaccinated are more likely to take up ICU beds (which turned out to be a lie, but let’s assume it were true), I was in the group taking up more beds, therefore I was taking up a bed.
The trick is to assign someone to a group in which they qualify (Somali, unvaccinated, etc.), get “data” about that group and then apply that data to the individuals within it, even if it is totally inaccurate with respect to them.
This is the same trick used to justify disastrous DEI policies too. You are from a historically underprivileged group, so you deserve to be held to lower standards. It doesn’t matter if you would succeed on your own merit, it doesn’t matter your race, gender, sexual orientation are irrelevant to the task for which you are being hired, it doesn’t matter if you are the son of wealthy and famous people and attended all the best schools, you belong to a particular category and therefore this standard will be applied.
But the implications of this midwit sleight of hand are even worse than that, especially on the eve of AI-based systems taking over so many of the administrative functions at both the corporate and state level. You will be categorized, and you will be pre-judged on that basis because it is far more efficient for the system to do so than to examine everyone individually. In fact, I’d argue, unlike humans, AI is incapable of seeing individuals, it sees only “data.”
This was the premise for the movie Minority Report, set in a dystopian future wherein people get convicted of “pre-crime” because the system determined from the data about them they were likely to commit one. You might not have done anything yet, but based on your angry social media posts, your high testosterone, your age and background, you have a 99.9 percent chance of violence. Why not arrest you now before you victimize someone? For every 1000 victims we protect, we’ll convict only one person who would not in fact have done it!
There will be many people who are for this kind of reasoning. It’s “data” after all. Never mind the data can be biased based on the grouping. Why am I grouped with other people I don’t know and over whom I have no control? What if they added 100 other parameters which showed I’m among the least likely to commit violence? Who is selecting these parameters and what are their agendas?
But more to the point, such a society is not free. You are at the whims of your grouping, of parameters, of statistics. The paradigm of individual civil liberties, innocent until proven guilty, responsibility only for your own actions would be dead. You are pre-judged before you have done anything.
The second-order effects of such a paradigm would be a race to the bottom. If I am not in the wrong group I can do no wrong, based on my favorable peers. I can roam the streets, commit acts of vandalism and violence with impunity, I can loaf at work, not do my job and never be fired. I would argue that under the present (and mercifully soon-to-be-departed) administration we’ve already experienced many of these effects already.
So back to the original question. What is Norway to do with this “data”? One idea would be to have a non-discriminatory vetting process that involves delayed gratification and requires some diligence on the part of the prospective immigrant. This might self-sort the people capable of living in an open, prosperous western society and those who are not. You would be admitted or denied based on demonstrated suitability (merit), not with whom you were grouped (identity). This would be closer to the “postjudice” policy prescription Yang erroneously claims for his own in the cited post.
Whether that results in more people of one race or another, one nationality or another getting in, isn't important. What's important is both not judging individuals on the basis of their assigned group and keeping the country free of violent criminals. Both goals are essential if we want to avoid dystopian outcomes.
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ c902b8da:0cedc5fb
2025-02-16 18:13:20
@ c902b8da:0cedc5fb
2025-02-16 18:13:20I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects:
State Licensing Requirements (Primary State): - Initial Capital and Surplus: $10-15 million minimum (varies by state) - Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC - Processing Time: 12-18 months - Application Fee: $25,000-50,000 - Filing Requirements: - Articles of Incorporation - Statutory Financial Statements - Actuarial Certifications - Detailed Ownership Information - Background Checks for All Officers/Directors - Holding Company Act Filings if Applicable
Federal Requirements: - ACA Compliance: - Must offer all 10 Essential Health Benefits - Medical Loss Ratio requirements (80% individual/small group, 85% large group) - No annual or lifetime limits - Guaranteed issue and renewal - HIPAA Compliance: - Privacy Officer Appointment - Security Protocols Implementation - Timeline: 6-8 months - Cost: $200,000-500,000 for initial setup
Multi-State Expansion (Per Additional State): - Certificate of Authority Application: $5,000-25,000 per state - State-Specific Capital Requirements: $2-5 million additional per state - Processing Time: 6-12 months per state - Required State Deposits: $500,000-2 million per state - Guaranty Fund Membership: $25,000-100,000 per state
Mandatory Insurance Filings: - Rate Filings: - Timeline: 60-90 days for approval - Filing Fees: $500-5,000 per filing - Form Filings: - Timeline: 30-60 days for approval - Filing Fees: $50-500 per form - Annual Statement Filing: $500-2,500 per state
Required Positions and Certifications: - Licensed Actuary (MAAA certification) - Compliance Officer - Medical Director (licensed physician) - Claims Manager - Network Management Director - Timeline for hiring/certification: 3-6 months - Annual Costs: $1-2 million for required personnel
Reserve Requirements: - Claims Reserves: 3-6 months of expected claims - Premium Reserves: 1-3 months of premium - Special Deposits: Varies by state ($1-5 million) - Total Reserve Requirements: 25-40% of annual premium
Ongoing Regulatory Compliance: - Quarterly Financial Filings: Due within 45 days of quarter end - Annual Financial Statements: Due March 1 - Market Conduct Examinations: Every 3-5 years - Cost: $100,000-500,000 per examination - Financial Examinations: Every 3-5 years - Cost: $200,000-1 million per examination
Required Insurance Coverage: - E&O Insurance: $5-10 million coverage - Annual Cost: $100,000-250,000 - D&O Insurance: $10-25 million coverage - Annual Cost: $200,000-500,000 - Cyber Insurance: $5-10 million coverage - Annual Cost: $100,000-300,000
Total Regulatory Timeline: - Initial State License: 12-18 months - Federal Compliance: 6-8 months (concurrent) - First Policy Issuance: 18-24 months from start - Multi-State Operation: Additional 12-24 months
Total Initial Regulatory Costs: - Single State Operation: $15-25 million - Multi-State Operation (5 states): $30-50 million - Annual Compliance Costs: $2-5 million per state
These requirements and costs can vary significantly based on: - State of domicile - Number of states operating in - Types of health insurance products offered - Size of projected enrollment - Market conditions and risk factors
Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works:
- Public Comment Period
- Most state insurance departments have a public comment period during the application process
- Existing insurers can submit formal objections or concerns
-
They typically focus on market saturation, financial viability, or potential unfair competition
-
Market Need Assessment
- Many states require a "need and necessity" showing as part of the application
- You must demonstrate that:
- There's sufficient market demand
- Your company brings something unique or beneficial
- The market can support another carrier
-
However, mere competition itself is not grounds for denial
-
State Regulator Discretion
- Regulators consider market concentration and competition
- They generally favor healthy competition unless there are legitimate concerns about:
- Market destabilization
- Your company's financial strength
- Risk to consumers
-
Pure "we don't want competition" arguments from existing insurers typically don't succeed
-
Trade Association Influence
- Insurance trade associations may provide input during the licensing process
- They can raise concerns about:
- Capital adequacy
- Management experience
- Business plan viability
- But they cannot directly block your application
Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with: - Consumer protection - Market stability - Your company's financial soundness - Management competency
-
 @ d34e832d:383f78d0
2025-01-06 23:44:40
@ d34e832d:383f78d0
2025-01-06 23:44:40Lets explore three key aspects of Bitcoin technology to enhance your engagement with the ecosystem:
- Running an Alby Hub Cloud Instance
- Setting Up a Nutshell Ecash Mint on an Affordable VPS
- Integrating Nostr Wallet Connect for Seamless Tipping
These components empower users to manage transactions, ensure privacy, and facilitate smooth interactions within the Bitcoin and Nostr communities.
1. Running an Alby Hub Cloud Instance
Purpose and Benefits:
Alby Hub is a self-custodial Lightning wallet that allows you to manage Bitcoin transactions efficiently. By running an Alby Hub instance in the cloud, you gain 24/7 online access to receive payments via a Lightning address, integrate with various applications, and maintain control over your funds without the need for personal hardware.
Setting Up Alby Hub in the Cloud:
-
Choose Alby Cloud: For a hassle-free setup, Alby offers a cloud service where you can start your own hub in just 2 minutes. Give it A Try: Alby Cloud
-
Subscription Benefits: Subscribing to Alby Cloud provides you with a self-custodial Lightning wallet, 24/7 online access, exclusive partner deals, priority support, and access to a subscriber community.
-
Getting Started: Visit the Alby Cloud page, select the subscription that suits you, and follow the guided setup process to have your hub up and running quickly.
- Alby Cloud page
For a visual guide on setting up Alby Hub, you can watch the following tutorial:
2. Setting Up a Nutshell Ecash Mint on an Affordable VPS
Purpose and Benefits:
Nutshell is an implementation of Ecash, a digital cash system that prioritizes privacy and anonymity. Setting up a Nutshell Ecash mint on a Virtual Private Server (VPS) allows you to operate your own mint, enhancing transaction privacy and providing a backup system for your Bitcoin transactions.
Setting Up on a $5 VPS:
-
Select a VPS Provider: Choose an affordable VPS provider that supports Bitcoin and Nostr communities. For instance, SatoshiHost offers VPS services tailored for such needs.
-
Install Nutshell: After setting up your VPS, install the Nutshell software by following the official installation guide.
- Nutshell
-
Configure the Mint: Set up the mint parameters, including denomination and security settings, to suit your requirements.
-
Secure the Server: Implement security measures such as firewalls and regular updates to protect your mint from potential threats.
- Recommendations
- Server Tips
3. Integrating Nostr Wallet Connect for Seamless Tipping
Purpose and Benefits:
Nostr Wallet Connect (NWC) is an open protocol that enables applications to interact with Bitcoin Lightning wallets. Integrating NWC allows for seamless tipping and payments within Nostr apps, enhancing user experience and promoting engagement.
Integration Steps:
-
Choose a Supporting App: Select a Nostr app that supports NWC, such as Amythystor Damus.
-
Connect Your Wallet: Use NWC to link your preferred Lightning wallet to the Nostr app. This connection facilitates seamless payments without the need to switch between applications.
-
Test the Integration: Perform a test transaction to ensure that the tipping functionality works as intended.
-
Maintain Security: Regularly update your wallet and Nostr app to incorporate the latest security features and improvements.
For a deeper understanding of Nostr Wallet Connect and its significance, you can watch the following discussion:
Final Thoughts On Setup
Implementing these components enhances your interaction with the Bitcoin ecosystem by providing efficient transaction management, improved privacy, and seamless integration with Nostr applications. By running an Alby Hub cloud instance, setting up a Nutshell Ecash mint on an affordable VPS, and integrating Nostr Wallet Connect, you contribute to a more robust and user-friendly Bitcoin environment.
Invitation for Feedback
I encourage you to share any questions or feedback regarding these topics. Let's continue the conversation to explore how we can further engage with and improve upon these technologies.
-
 @ df478568:2a951e67
2025-02-16 17:10:55
@ df478568:2a951e67
2025-02-16 17:10:55I asked a pleb to answer a few questions about selling stuff for sats, and he asked me, "What made you want to do a story/article on this?"
The short answer: Because I like seeing people make their own bitcoin jobs, but the question made me think about the why. When I tried to be an English teacher, one of my professors said, "The difference between a job and a career is that a career is something you think about all day." I didn't become an English teacher, because I already had something I think about all day: bitcoin. I didn't fit the teacher ethos, for whatever reason, so undecided, I wanted to work in bitcoin sometime around block 525,000.

That's about the time I began writing on yalls.org. I fell in love with the idea of writing for sats. It was too early. Very few people used lightning back then, but the idea of earning sats to write was invigorating. I had no illusions of earning enough to earn a living, but yalls had a paywall. I spent a fair amount of time experimenting with these paywalls. Part of my articles were available for free, but to finish the article required a payment of 210 sats when that was about two cents. I was fascinated with this concept because it meant I could write for sats. Readers could send p2p electronic cash to me—sats short for satoshis. Each bitcoin can be divided into 100,000,000 sats. The lightning network allowed people to send you micropayments.
Yalls

This was not possible with credit cards because of the fees they charge. The lightning network can be used to circumvent fees imposed on credit card merchants and the sats can now be instantly converted to fiat. This is not financial advice. Earning bitcoin is 21 million times more interesting than trading bitcoin. Investors talk about green dildos, red dildos, and some other sex toy called a bollinger band. If you're into that kind of kinky stuff, I don't judge, but I stay vanilla and stack sats. I experimented with shitcoin play in younger years, but it was just a phase. I finally realized alts are an attempt to break the solution to the double-spending problem sometime around block 630,000.
That's when I declared myself a bitcoin maxi on yalls.org. Adam Back retweeted it. It didn't go viral, but that was amazing. I'm just an anonymous user who couldn't get an English teaching job, but Adam Back...You know..The guy Satoshi cited in the white paper—That guy retweeted my article. I started a couple of anonymous blogs and earned a small amount of sats in the early days of nostr.
How I Made 1,000,000 Volunteering At Pacific Bitcoin
I volunteered for Pacific Bitcoin 2022. I volunteered to save some sats on a ticket. I stayed in a hostel. I did not expect to get paid, but it earned me a million sats after I sold the pack of collectible cards that came in a swag bag at the conference. What if I can one day retire on the millions of sats I earned over the last few years? I'm not sure that will happen, but it might be enough for my grandchildren to retire. *If bitcoin goes up "forever Laura..." you're never too late to earn bitcoin on the side. The sats you earn go up in value forever.
Maybe the ROI on your college degree didn't pay off like you thought it would. You read Walden and Civil Disobedience and A Letter From a Birmingham Jail...thought...these are great ideas. They prepared me to read Early Retirement Extreme. I also listened to Choose FI and decoded Mr. Money Mustache. Dave Ramsey says you should get a second job to pay off debt in a country where many people working two jobs are still getting into more debt. Maybe they should use that extra job to stack sats. Earning bitcoin feels different than buying bitcoin. It means earning money on the Internet without needing a trusted third party. PayPal and Patreon have been around for years. They are nothing new, digital middlemen.
Although the less technical often use bitcoin non-custodially, it's getting easier to take self-custody and use bitcoin as it was intended, p2p electronic cash. Why use eBay when you can have a garage sale on nostr? Even Dave Ramsey can sell stuff on nostr. He's been telling people to avoid bitcoin since it was $400. What if you sell your fancy clothes made in Bangladesh on nostr while instantaneously converting it to USD on Strike? You can send 1,000 fiat bucks to your checking account faster than a speeding Superman. You can get the garage sale money deposited to your bank account within a half-hour. I can't even drive to an ATM that fast! Transfer the money to a savings account that pays 0.01% interest. Baby Step 1 complete! You can take the instant fiat from your next nostr garage sell and pay your debt straight from the Strike App! This is NOT financial advice.
I could earn fiat on Poker Stars until the government took away my permission. I could earn fiat on Full Tilt, but they spent players' fiat and barely kept a fraction in reserve. The same is true of platforms. You can earn fiat on Twitter if you pay for the monthly Twitter lottery. American's can currently earn fiat on TikTok...but do see where this is going? That's why I like supporting people who have some sort of bitcoin side hustle. I may have found bitcoin in 2014, but I didn't have a full-time job. I was unemployed for a couple of years before that. This one time, I got into an argument with my wife because, some months, we could only scrape up $50 to "buy bitcoin." I was an asshole. I kinda feel bad about that, but I'm a lucky guy with a beautiful wife who forgave me for being an asshole and dashing doors to stack bitcoin without telling her about it. She was pretty pissed. That Fifty bucks we argued over is now worth...
The misses is not so pisses anymore.😁
- I've picked up extra jobs to stack sats.
- I used BTCPayServer to stack sats.
- I stacked sats with lnbits
- I originally set up a lightning node so I could stack sats on yalls.org.
- It took me six months to get a lightning node up and running on a raspberry pi.
Few
Very few people used the lightning network back then. Any bitcoiner has the ability to make their own job. I started a blog and set up a BTCPayServer so people would pay me for my prose. Some actually did. It wasn't much money. I might have broken even, but the possibilities still intrigue me. You can use Alby Hub on the cloud, Zaprite, or run it on a Start9. You can pay GetAlby for a lightning node in the cloud. If you're a fiat-spending maximalist, you can convert all your bitcoin to fiat with Strike.*
Bitcoin Is For Everybody, Even Nocoiners
Maybe you don't want bitcoin, but need some extra cash and can make candles. Fiat won't hedge against eggflation, but that's not what this is about. That's not the point. Bitcoin is for anybody, even no-coiners. You don't even need to make a website anymore. You can just use Shopstr, Plebian Market, Coinos, Cashu.me, Buzz Pay, and more.I just bought some soap from someone I saw on nostr. I decided to try something new this month. I paid with fiat, but the soap miner received bitcoin on the other end. Anyone with the Strike App can pay dollars to people who want bitcoin and vice-versa. Some people proudly proclaim they never...ever...spend bitcoin. Those who hodl never sell.
In Everyone's A Scammer, Michael Bitstein says:
"Merchants are scammers because they lead you to believe that your bitcoins are only worth the price of their retail good in order to allow themselves (or those to whom they sell the bitcoins, if they so choose), rather than you, to benefit from future Bitcoin price increases. …And That’s a Good Thing This is not to say merchant adoption is bad. In fact, from the hoarder's perspective, merchant adoption is great. First, merchant adoption means that there is more demand for Bitcoin, that the Bitcoin network is growing, and that Bitcoin is thus more valuable than it was yesterday. Second, merchant adoption means there are more places to spend bitcoins. This does not mean a hoarder will actually want to spend bitcoins. More importantly, he can spend bitcoins.If you like this quote, [please zap this note. 100% of these zaps go to BitstienSaylor says bitcoin is hope, but you know what gives me hope? Not the billionaire buying bitcoin, but the pleb selling stuff for sats. - Maybe there's a homeless person selling a few used books for a meal. - Maybe an artist stacks $500 per month selling art on nostr. - Maybe a recently X government employee can sell DEI training on the free and open market on nostr. Or...Maybe they can sell culturally appropriate tamales on nostr for actual sats instead.
Those are the stories I want to find. Bitcoin is for everybody, even people with college degrees that the job market does not value much. Saylor's not wrong. Bitcoin is hope. Saylor said he wants to make education free. That's why he founded Saylor Academy. They have a course called Bitcoin Is For Everybody. Bitcoin is for everybody, even no-coiners, even for people who went to college even though it didn't lead to a high-paying job. Bitcoin is hope for those people, people just like me.
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
* Strike is an affiliate and I earn a small commision if you pay for the service. I use it to pay my credit card bills.
-
 @ df478568:2a951e67
2025-02-16 16:53:45
@ df478568:2a951e67
2025-02-16 16:53:45I asked a pleb to answer a few questions about selling stuff for sats and he asked me, "What made you want to do a story/article on this?"" When I tried to be an English teacher, one of my professors said, "The difference between a job and a career is that a career is something you think about all day." I didn't become an English teacher, because I already had something I think about all day, bitcoin. I didn't fit the teacher ethos, for whatever reason, so Indecided I want to work in bitcoin sometime around block
That's about the time I began writing on yalls.org. I fell in love with the idea of writing for sats on yalls.org. It was an idea, but it was too early. It was very early days. Very few people used lightning back then, but the idea of earning sats to write was invigorating. I had no illusions of earning enough to earn a living, but yalls had a paywall. I spent a fair amount of time experimenting with these paywalls. Part of my articles were available for free, but to finish the article required a payment of 210 sats when that was about 2¢. I was as facinated with this concept because it meant I could write for sats. Readers could send p2p electronic cash to me-sats short for satoshis. Each bitcoin can be divided into 100,000,000 sats. The lightning network allowed people to send you micropayments. This was not possible with credit cards because of the fees they charge. The lightning network can be used to circumvent fees imposed on credit card merchants and the sats can now be instantly converted to fiat. This is not financial advice. Earning bitcoin is 21 million times more interesting than trading bitcoin. Investors talk about green dildos, red dildos, and some other sex toy called a bollinger band. If you're into that kind of kinky stuff, I don't judge, but I stay vanilla and stack sats. I experimented with shitcoin play in younger years, but it was just a phase. I finally realized alts are an attempt to break the solution to the double spending problem sometime around block 630,000.
That's when I declared myself a bitcoin maxi on yalls.org. Adam Back retweeted it. It didn't go viral, but that was amazing. I'm just an anon who couldn't get an English teaching job, but Adam Back...You know..The guy Satoshi cited in the white paper--That guy retweeted my article. I started a couple anon blogs and earned a small anount of sats in the early days of nostr. I volunteered for Pacific Bitcoin 2022. I volunteered to save some sats on a ticket. I stayed in a hostel. I did not expect to get paid, but it earned me a million sats after I sold the pack of collectible cards that came in a swag bag at t he conference. What if I can one day retire on the millions of sats I earned over the last few years? I'm not sure that will happen, but it it might be enough for my grandchildren to retire. *If bitcoin goes up "forever Laura..." you're never too late to earn bitcoin on the side. The sats you earn go up in value forever. Maybe the ROI on you're college degree didn't pay off like you thought it would. You read Walden and Cilvil Disobedience and A Letter From A Birmhingham Jail...thought...these are great ideas. They prepared me to read Early Retirement Extreme. I also listened to Choose FI and decoured Mr. Money Mustache. [Dave Ramsey](Resources to Tackle Debt - Ramsey) says you should get a second job to pay off debt in a country where many people working two jobs are still getting into more debt. Maybe they should use that extra job to stack sats. Earning bitcoin feels different than buying bitcoin. It means earning money on the Internet without needing a trusted third party. Paypal and Patreon have been around for years. They are nothing new, digital middlemen. Although the less technical often use bitcoin non-custodially, it's getting easier to take self custody and use bitcoin as it was intended, p2p electronic cash. Why use eBay when you can have a garage sale on nostr? Even Dave Ramsey can sell stuff on nostr. He's been telling people to avoid bitcoin since it was $400.00. What if you sell your fancy clothes made in Bangladesh on nostr while instantaniously converting it to USD on Strike? You can send 1,000 fiat bucks to your checking account faster than a speeding Superman. You can get the garage sale money deposited to your bank account within a half hour. I can't even drive to an ATM that fast! Transfer the money to a savings account that pays 0.01% interest. Baby Step 1 complete! You can take the insta-fiat from your next nostr garage sell and pay your debt straight from the Strike App! This is NOT financial advice. I could earn fiat on Poker Stars until the government took away my permission. I could earn fiat on Full Tilt, but they spent players fiat and barely kept a fraction in reserve. The same is true of platforms. You can earn fiat on Twitter if you pay for the monthly Twitter lottery. American's can can currently earn fiat on TikTok..but do see where this is going? That's why I like supporting people who have some sort of bitcoin side hustle. I may have found bitcoin in 2014, but I didn't have a full time job. I was unemployed for a couple years before that. This one time, I got into an argument with my wife because, some months, we could only scrape up $50 to "buy bitcoin." I was an asshole. I kinda feel bad about that, but I'm a lucky guy with a beautiful wife who forgave me for being an asshole and dashing doors to stack bitcoin without telling her about it. She was pretty pissed. That Fifty bucks we argued over is now worth...
The misses is not so pissed anymore.😁 I've picked up extra jobs to stack sats. I used BTCpayServer to stack sats. I originally set up a lightning node so stack sats on yalls.org. Very few people used the lightning network back then. Any bitcoiner has the ability to make their own job. I started a blog and set up a BTCpayServer so people would pay me for my prose. Some actually did. It wasn't much money. I might have broke even, but the possibilities still intrigue me. You can buy a Start9 and use Alby Hub. You can pay GetAlby for a lightning node in the cloud. If you're a fiat spending maxi, you can convert all your bitcoin to fiat with Strike. Maybe you don't want bitcoin, but need some extra cash and can make candles. Fiat won't hedge against eggflation, but that's not what this is about. That's not the point. Bitcoin is for anybody, even nocoiners. buYou don't even need to make a website anymore. You can just use Shopstr, Plebian Market, Coinos, Cashu.me, [Buzz Pay](https://pos.albylabs.com/#?nwc=bm9zdHIrd2FsbGV0Y29ubmVjdDovLzY5ZWZmZTdiNDlhNmRkNWNmNTI1YmQwOTA1OTE3YTUwMDVmZmU0ODBiNThlZWI4ZTg2MTQxOGNmM2FlNzYwZDk/cmVsYXk9d3NzOi8vcmVsYXkuZ2V0YWxieS5jb20vdjEmcHVia2V5PTVkNzVjZDQ5OTFkNGFhOTViMDllMWJkZTg1YmRkODllMTg2YjUxZmE3MDYwOTEyOTE5MGYxZWIwYjcyYzk0MWUmc2VjcmV0PWFiZDM5NDU3ODQ4NmI0OWJlMzMwNzk1ZWE2YTU2OGIwYWI2MWJjMjMzN2JkMTE5NzU1YTNiM2ZmZTBhZDEwMmQ=&name=Support my work using the Value 4 Value model), and more.I just bought some soap from someone I saw on nostr. I decided to try something new this month. I paid with fiat, but soap miner recieved bitcoin on the other end. Anyone with the Strike App can pay dollars to people who want bitcoin and vice-versa. Some people proudly proclaim they never...ever...ever spend bitcoin. Those who hodl never sodl can spend fiat at bitcoin shops using Strike. Buying stuff with bitcoin increases the stack of a fellow HODLer. In Everyone's A Scammer, Michael Goldstein says, "Merchants are scammers because they lead you to believe that your bitcoins are only worth the price of their retail good in order to allow themselves (or those to whom they sell the bitcoins, if they so choose), rather than you, to benefit from future Bitcoin price increases. …And That’s a Good Thing This is not to say merchant adoption is bad. In fact, from the hoarder’s perspective, merchant adoption is great. First, merchant adoption means that there is more demand for Bitcoin, that the Bitcoin network is growing, and that Bitcoin is thus more valuable than it was yesterday. Second, merchant adoption means there are more places to spend bitcoins. This does not mean a hoarder will actually want to spend bitcoins. More importantly, he can spend bitcoins. Demand for cash exists because there is uncertainty of future needs, and the holder of cash believes he will come across currently unknown opportunities in the future that can better satisfy his needs than any current opportunities." Saylor says bitcoin is hope, but you know what gives me hope? Not the billionaire buying bitcoin, but the pleb selling stuff for sats. Maybe there's a homeless person selling a few used books for a meal. Maybe an artist stacks $500 per month selling art on nostr. Those are the stories I want to find. Bitcoin is for everybody, even people with college degrees that the job market does not value much. Saylor's not wrong. Bitcoin is hope. Saylor said he wants to make education free. That's why he founded Saylor Academy. They have a course called [Bitcoin Is For Everybody](Bitcoin is for everybody](https://learn.saylor.org/course/view.php?id=468)). Bitcoin is for everybody, even no-coiners, even for people who went to college even though it didn't lead to a high paying job. Bitcoin is hope for those people, people just like me.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[884,054(https://mempool.marc26z.com/block/00000000000000000000a9305d5f83abfc86da27c9524a7ad181b7a75f0827a9)
-
 @ 41fa852b:af7b7706
2025-02-16 15:52:51
@ 41fa852b:af7b7706
2025-02-16 15:52:51"Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr
If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.
It's a big week with 12 meetups--check out the list below and see if there's one near you.
Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at bitcoinevents.uk. Just scroll down to find your meetup group, and you'll see how to get in touch.
Let's dive in…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Newcastle Bitcoin Meetup: A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻
-
Bitcoin 101: Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at cyphermunkhouse.com/events.. 👨🏼🎓
-
Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺
-
Bitcoin Wales: Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻
-
OPA London Bitcoin Meetup: The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the Century Club (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸
-
Shropshire Bitcoin: On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻
-
Brum Bitcoin & Beer: If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺
-
Bitcoin Bristol: Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻
-
2140 Collective: Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Plymouth Bitcoiners: The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at Procopio's Pantry and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 3ffac3a6:2d656657
2025-01-06 23:42:53
@ 3ffac3a6:2d656657
2025-01-06 23:42:53Prologue: The Last Trade
Ethan Nakamura was a 29-year-old software engineer and crypto enthusiast who had spent years building his life around Bitcoin. Obsessed with the idea of financial sovereignty, he had amassed a small fortune trading cryptocurrencies, all while dreaming of a world where decentralized systems ruled over centralized power.
One night, while debugging a particularly thorny piece of code for a smart contract, Ethan stumbled across an obscure, encrypted message hidden in the blockchain. It read:
"The key to true freedom lies beyond. Burn it all to unlock the gate."
Intrigued and half-convinced it was an elaborate ARG (Alternate Reality Game), Ethan decided to follow the cryptic instruction. He loaded his entire Bitcoin wallet into a single transaction and sent it to an untraceable address tied to the message. The moment the transaction was confirmed, his laptop screen began to glitch, flooding with strange symbols and hash codes.
Before he could react, a flash of light engulfed him.
Chapter 1: A New Ledger
Ethan awoke in a dense forest bathed in ethereal light. The first thing he noticed was the HUD floating in front of him—a sleek, transparent interface that displayed his "Crypto Balance": 21 million BTC.
“What the…” Ethan muttered. He blinked, hoping it was a dream, but the numbers stayed. The HUD also showed other metrics:
- Hash Power: 1,000,000 TH/s
- Mining Efficiency: 120%
- Transaction Speed: Instant
Before he could process, a notification pinged on the HUD:
"Welcome to the Decentralized Kingdom. Your mining rig is active. Begin accumulating resources to survive."
Confused and a little terrified, Ethan stood and surveyed his surroundings. As he moved, the HUD expanded, revealing a map of the area. His new world looked like a cross between a medieval fantasy realm and a cyberpunk dystopia, with glowing neon towers visible on the horizon and villagers dressed in tunics carrying strange, glowing "crypto shards."
Suddenly, a shadow loomed over him. A towering beast, part wolf, part machine, snarled, its eyes glowing red. Above its head was the name "Feral Node" and a strange sigil resembling a corrupted block.
Instinct kicked in. Ethan raised his hands defensively, and to his shock, the HUD offered an option:
"Execute Smart Contract Attack? (Cost: 0.001 BTC)"
He selected it without hesitation. A glowing glyph appeared in the air, releasing a wave of light that froze the Feral Node mid-lunge. Moments later, it dissolved into a cascade of shimmering data, leaving behind a pile of "Crypto Shards" and an item labeled "Node Fragment."
Chapter 2: The Decentralized Kingdom
Ethan discovered that the world he had entered was built entirely on blockchain-like principles. The land was divided into regions, each governed by a Consensus Council—groups of powerful beings called Validators who maintained the balance of the world. However, a dark force known as The Central Authority sought to consolidate power, turning decentralized regions into tightly controlled fiefdoms.
Ethan’s newfound abilities made him a unique entity in this world. Unlike its inhabitants, who earned wealth through mining or trading physical crypto shards, Ethan could generate and spend Bitcoin directly—making him both a target and a potential savior.
Chapter 3: Allies and Adversaries
Ethan soon met a colorful cast of characters:
-
Luna, a fiery rogue and self-proclaimed "Crypto Thief," who hacked into ledgers to redistribute wealth to oppressed villages. She was skeptical of Ethan's "magical Bitcoin" but saw potential in him.
-
Hal, an aging miner who ran an underground resistance against the Central Authority. He wielded an ancient "ASIC Hammer" capable of shattering corrupted nodes.
-
Oracle Satoshi, a mysterious AI-like entity who guided Ethan with cryptic advice, often referencing real-world crypto principles like decentralization, trustless systems, and private keys.
Ethan also gained enemies, chief among them the Ledger Lords, a cabal of Validators allied with the Central Authority. They sought to capture Ethan and seize his Bitcoin, believing it could tip the balance of power.
Chapter 4: Proof of Existence
As Ethan delved deeper into the world, he learned that his Bitcoin balance was finite. To survive and grow stronger, he had to "mine" resources by solving problems for the people of the Decentralized Kingdom. From repairing broken smart contracts in towns to defending miners from feral nodes, every task rewarded him with shards and upgrades.
He also uncovered the truth about his arrival: the blockchain Ethan had used in his world was a prototype for this one. The encrypted message had been a failsafe created by its original developers—a desperate attempt to summon someone who could break the growing centralization threatening to destroy the world.
Chapter 5: The Final Fork
As the Central Authority's grip tightened, Ethan and his allies prepared for a final battle at the Genesis Block, the origin of the world's blockchain. Here, Ethan would face the Central Authority's leader, an amalgamation of corrupted code and human ambition known as The Miner King.
The battle was a clash of philosophies as much as strength. Using everything he had learned, Ethan deployed a daring Hard Fork, splitting the world’s blockchain and decentralizing power once again. The process drained nearly all of his Bitcoin, leaving him with a single satoshi—a symbolic reminder of his purpose.
Epilogue: Building the Future
With the Central Authority defeated, the Decentralized Kingdom entered a new era. Ethan chose to remain in the world, helping its inhabitants build fairer systems and teaching them the principles of trustless cooperation.
As he gazed at the sunrise over the rebuilt Genesis Block, Ethan smiled. He had dreamed of a world where Bitcoin could change everything. Now, he was living it.
-
 @ 8194da31:0f3badf3
2025-02-16 12:41:16
@ 8194da31:0f3badf3
2025-02-16 12:41:16My stands on Plan B comments 👇
1- As a #Bitcoin maxi not your keys not your coins is non negotiable
2- Transferring your #Bitcoin to an ETF just because your are a fucking lazy ass is not an excuse
3- I do respect people who prefer the ETFs over #Bitcoin for 3 specific reasons:
A- you are over 70 years old
B- you are sovereign wealth fund or a Corporation
C- you will take advantage of the FIAT system by using IBIT as collateral to get more #Bitcoin
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 6ad3e2a3:c90b7740
2025-01-05 14:26:34
@ 6ad3e2a3:c90b7740
2025-01-05 14:26:34Maybe it’s because I watched The Omen at way too young an age, or maybe it’s because the Book of Revelation’s “mark of the beast” allegory is playing out too literally for my tastes, but having already written about the Second Coming, it only follows I should speculate as to its counterpart.
As I mentioned in The Second Coming, it’s dangerous to take the myths from our ancestors too literally. They used the symbols of their times, and we should be careful not to confuse the mental maps they had of their world with reality itself. That said, we should also not be dismissive — Mozart didn’t have fancy music editing software, but his genius using the modalities of the time was real. To the extent our forebears offered us their wisdom about the nature of man and forces within him we should endeavor to understand it. The technology and the symbols may have changed, but our essential nature is ever the same.
Just as the second coming of Christ would free man from tyranny, the Antichrist would be its imposition. And just as I speculated that Jesus might not return in the form of a person, it’s likely neither would his counterpart. But if Satoshi, Bitcoin’s pseudonymous creator, can be the face, so to speak, representing the movement toward freedom and God, who and what would represent its antithesis? Let’s speculate.
It would have to be someone charismatic, a person the multitudes would want to follow and in whom to look for reassurance. That eliminates villains du jour like Bill Gates, Klaus Schwab and Vladimir Putin. If that’s who Satan is sending, he’s not sending his best. What about Donald Trump? More charismatic, much more popular appeal. He’s a better choice than the first group, but while street-smart, he lacks refined intelligence and is too despised by wide swaths of the population. He’s also probably too old.
For a while, I would have said Barack Obama was the best candidate, and even some hard-core right wingers agreed (it’s hilarious that this claim was actually fact-checked! — you can’t fact-check whether someone is the Antichrist!) Obama was relatively young, vital enough, popular, charismatic and intelligent. But he’s faded from view the last few years and has been a surprisingly inconsequential former president.
That leaves one person of whom I can think with the qualities and societal position to fill the role. Regrettably it’s someone I like, but of course I would like the Antichrist! If he weren’t likable he wouldn’t be the Antichrist.
That person is Elon Musk.
Musk is the richest person in the world, among the most followed on Twitter, has a borderline worshipful fanbase and big plans for improving humanity. Musk is young enough, he’s probably a genius and considering a private takeover of arguably the world’s most important communications network. He’s also a big player in satellites, energy, transportation and internet provision.
Musk says lots of sensible things with which I agree about free speech and rights. He is the perfect foil to the out-of-central-casting Schwab supervillain. As Edward Dowd speculated:
 But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for free speech, renewable energy, population expansion? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “The medium is the message.”
But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for free speech, renewable energy, population expansion? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “The medium is the message.”Or, more aptly, the top-down messianic complex is the message.
Musk has long discussed saving humanity via expansion into space and sustainable energy. But in order to save humanity, one must exert some control over it. While Musk’s Twitter takeover from the ineffectual woke scolds is getting most of the press, this is also going on:
 Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?
Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?
Well don’t get the implant then. Just get in your Tesla and drive away. But electric cars don’t work that way — they are attached to the grid, trackable and capable of being shut down remotely. And that’s before we consider driverless cars in which there would be even less privacy and autonomy. Moreover, Teslas track the driver’s movements already to an extent combustion-engine cars do not, ostensibly to inform the developing AI, but uses for technology evolve over time — sending email and paying bills over the internet was commonplace in 2000, but now people are micro-tracked by Facebook and Google.
One could object that Musk has, to-date, used his influence for good. But that makes it no less dangerous to entrust him with so much power: J.R.R. Tolkien understood this clearly:
“You are wise and powerful. Will you not take the Ring?”
“No!” cried Gandalf, springing to his feet. “With that power I should have power too great and terrible. And over me the Ring would gain a power still greater and more deadly.” His eyes flashed and his face was lit as by a fire within. “Do not tempt me! For I do not wish to become like the Dark Lord himself. Yet the way of the Ring to my heart is by pity, pity for weakness and the desire of strength to do good. Do not tempt me! I dare not take it, not even to keep it safe, unused. The wish to wield it would be too great for my strength. I shall have such need of it. Great perils lie before me.”
-- The Lord of the Rings
Beyond Neuralink, Musk also seems to have a strong utilitarian bent:
 In this paper Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss.
In this paper Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss.While Bostrom’s framework seems benign — who is against collective human happiness in the form of more worthwhile lives? — it’s actually a form of utilitarianism that tries to sum the totality of human happiness over the entire species rather than to consider, as Immanuel Kant would, each individual as an end in himself. This viewing of the collective good as the optimal outcome has been used to justify many of history’s worst atrocities. To create a master race, to make sure everyone gets the same amount, to protect the world from covid, we must do whatever it takes!
If, per Bostrom’s math, one harnessed black hole were worth quadrillions of lives, it would, for example, seem an easy call to sacrifice a bunch of selfish losers on earth who stood in the way of creating the technology for doing so. Utilitarianism, ironically, winds up failing miserably by its own metric because (a) it can so easily be manipulated by whoever is maintaining the “greater good” spread sheet, which just happens to coincide with one’s ambitions; and (b) because it’s absurd to think you can calculate aggregate good for octillions of lives so far into an unknowable future. As such, while Musk’s pitch is more persuasive than Schwab’s or Gates’, it’s ultimately part of the same dangerous philosophy which is: “Let me optimize for total human happiness on your behalf.”
Contrast Musk’s top-down humanity-saving endeavors with Bitcoin which is purely opt-in, works with simple incentives and imposes no value judgments on its users. It’s a truth-recording clock, impervious to fraud and cooption by the powerful. No matter how wealthy or powerful a person is, he cannot control the network or get treated with special privileges. Bitcoin’s finite supply means governments cannot print more of it, cannot finance unpopular wars or massive giveaways to the military and pharmaceutical industrial complexes. Instead of trusting any particular powerful person (the president, Elon Musk, Bill Gates) to be good, it simply removes the incentives toward and reduces the capacity for evil.
The supreme good is like water, which nourishes all things without trying to. It is content with the low places that people disdain. Thus it is like the Tao.
From the Tao Te Ching (Lao Tse — translated by Stephen Mitchell)
We simply need the right conditions, the proper axioms on which to build. Just as the US Constitution created the framework for the most prosperous society in the history of the world, bitcoin will provide the axioms for peace, the harnessing of stranded energy and the low-time preference required for a more prosperous future.
But it won’t be the future brought to you by Elon Musk, and ultimately I foresee a clash between the two. One tell is his otherwise inexplicable promotion of Dogecoin as a possible currency for Tesla purchases. Dogecoin was literally a joke from its creator and of course has none of the security, decentralization or censorship resistance of bitcoin. Musk is too smart not to know that — he put a couple billion dollars of Tesla’s balance sheet in bitcoin already and almost certainly understands the value proposition. That he still cites Doge seriously would be a clever way to muddy the waters about what bitcoin is vs what blockchain-based “crypto” is. And of course the Antichrist would avail himself of bitcoin, if only to obfuscate his real intentions and also to be able to crash the price by selling, if necessary, at an opportune time.
The Klaus Schwab-Bill Gates-WEF set have already lost. They are widely despised, central banks are flailing, once-trusted institutions like the legacy media, major science and medical journals, the WHO, CDC and FDA are hemorrhaging influence. People are unhappy and looking for someone or something to trust. Elon Musk could fill that void, and if he does, he will be The Final Boss, the last false idol that needs to be discarded before humanity can, through its own efforts, enjoy a new era of prosperity, the Second Coming, so to speak.
I actually suspect Musk is genuine in his desire to help humanity via his vision and am pretty sure he doesn’t have 666 embedded in his scalp — in any case even Damian in The Omen neither knew who he was nor wanted to be the Antichrist! But the most dangerous people for humanity are those with the biggest plans for it.
Or put more succinctly:

-
 @ 58937958:545e6994
2025-01-03 11:07:06
@ 58937958:545e6994
2025-01-03 11:07:06January 3, 2024 I made a Bitcoin-inspired Osechi to celebrate Bitcoin's birthday. Everything was handmade! Osechi: A traditional Japanese New Year’s feast, typically served in stacked boxes.
First Layer (Ichino-jū)

- Tazukuri: Dried sardines, symbolizing a wish for a bountiful harvest.
- Simmered Kuai: A vegetable with large sprouts, symbolizing growth and success.
- Kombu Rolls: A play on words with the Japanese term yorokobu ("to be joyful"), making it a good luck dish.
- Matsukazeyaki: Ground meat coated with sesame or poppy seeds on one side, symbolizing honesty (no "hidden side").
- Black Beans: Represent hard work and good health.
- Datemaki: Sweet rolled omelet resembling scrolls, symbolizing knowledge and learning.
- Grilled Yellowtail: A fish whose name changes as it grows, symbolizing success. Salmon Terrine: A classic addition to Western-style Osechi. Salmon symbolizes success, avoiding misfortune (sakeru), and prosperity for future generations.
- Tataki Gobo: Burdock root with deep roots, symbolizing family stability and prosperity.
Second Layer (Nino-jū)

- Candied Kumquat: A dish symbolizing wealth and good fortune.
- Namash: Pickled daikon and carrot, resembling celebratory red and white decorations.
- Chestnut Kinton: Golden in color, symbolizing wealth and a prosperous year.
Bitcoin-themed additions:
- Pumpkin Yokan
- Chicken and Spinach Terrine
- Kinako Sticks
Third Layer (Sanno-jū)
 Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity.
I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself.
Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity.
I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself.Dishes Inspired by Bitcoin
Pumpkin Yokan
 I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan.
I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan.Chicken and Spinach Terrine
 It was my first attempt, and I think with more care, the shape could be even better.
It was my first attempt, and I think with more care, the shape could be even better.Kinako Sticks
 A simple snack made with honey and roasted soybean flour (kinako).
Roll it out, cut it into sticks, and coat with more kinako.
A simple snack made with honey and roasted soybean flour (kinako).
Roll it out, cut it into sticks, and coat with more kinako.Candied Kumquat
 Candied Kumquat: A dish symbolizing wealth and good fortune.
In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold."
Candied Kumquat: A dish symbolizing wealth and good fortune.
In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold."nostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy
I wonder what Satoshi might have eaten on the day Bitcoin was born. Wouldn't it be amusing to imagine him snacking on Osechi while working on his computer? (Satoshi chose a Japanese name, so perhaps he might have an interest in Japanese culture.) Maybe, right now, Satoshi is relaxing and enjoying some Osechi... though probably not! In any case, I hope Satoshi is living peacefully somewhere.
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 58937958:545e6994
2025-01-03 11:01:49
@ 58937958:545e6994
2025-01-03 11:01:492024年1月3日 ビットコインのお誕生日に合わせて ビットコインっぽい具材を入れたおせちを作りました 全部手作りです
1の重
 (左上から)
(左上から)- 田作り…田んぼに田作り(カタクチイワシ)を肥料として撒いたことから、豊作祈願の意味合いがある。
- くわいの煮物…大きく芽が出る野菜で、出世や成功を祈る。
- 昆布巻き…「喜ぶ(よろこぶ)」の語呂合わせで縁起物。
- 松風焼き…表面だけケシの実やゴマをまぶす=裏がない→隠し事のない正直な生き方ができるように、という意味が込められている
- 黒豆…「まめに働く」ことや健康を祈る。
- 伊達巻き…巻物に似ていることから、知識が豊富になるようにと願いが込められている。
- ぶりの幽庵焼き…ぶりは成長とともに名前が変わる出世魚で、将来の出世を願う。
- 鮭のテリーヌ…洋風おせちの定番。鮭には「出世」「災いを避け(サケ)る」「子孫繁栄」などの意味がある
- たたきごぼう…根が深く張るごぼうは家族や子孫繁栄の象徴。
2の重

- 金柑の甘露煮…金柑の「金」の文字から、金運や財運を祈る。
- なます…紅白の水引のような形状で祝いの意味がある
- 栗きんとん…黄金色が金運を表し、豊かな1年を願う。
以下はビットコイン具材として入れました
- カボチャようかん
- 鶏とほうれん草のテリーヌ
- きな粉棒
3の重
 煮しめ…様々な具材を一緒に煮ることから、「皆で仲良く、末永く繁栄するように」という願いが込められている
きぬさやのBは我ながらちょっと笑ってしまった
煮しめ…様々な具材を一緒に煮ることから、「皆で仲良く、末永く繁栄するように」という願いが込められている
きぬさやのBは我ながらちょっと笑ってしまったビットコインを意識して作った具材
カボチャようかん
 固めの牛乳かんを作り、包丁でBの形に切り抜いて、カボチャのようかんを流す感じです
固めの牛乳かんを作り、包丁でBの形に切り抜いて、カボチャのようかんを流す感じです鶏とほうれん草のテリーヌ
 鶏むね肉とはんぺんをミンチにして、半分にほうれん草を入れて形作りました
初めて作ったので不安でしたが丁寧に作ればもっと良い形になると思いました
鶏むね肉とはんぺんをミンチにして、半分にほうれん草を入れて形作りました
初めて作ったので不安でしたが丁寧に作ればもっと良い形になると思いましたきな粉棒
 はちみつときな粉だけで作る駄菓子的なおやつです
のばして包丁で切り抜いてきな粉をまぶします
はちみつときな粉だけで作る駄菓子的なおやつです
のばして包丁で切り抜いてきな粉をまぶします金柑の甘露煮
 丸くてオレンジ色なので作ってみました
しかも名前に「金(ゴールド)」が入っているのでビットコイン食材のポテンシャルがあると思います
とろける感じでめっちゃおいしかったです
丸くてオレンジ色なので作ってみました
しかも名前に「金(ゴールド)」が入っているのでビットコイン食材のポテンシャルがあると思います
とろける感じでめっちゃおいしかったですnostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy
サトシはビットコインが生まれたその日に何を食べていたのかなぁと おせちをつまみながらパソコンに向かっていたりしたら面白いなぁと思いながら作りました (日本文化が好きだから日本名にした可能性はあるかな~とか)
今頃のんびりおせちを食べてくつろいでいる・・・なんてことはないですかね 何にせよサトシが平和に暮らしていればいいなぁと思います
-
 @ c3c7122c:607731d7
2025-02-16 07:48:35
@ c3c7122c:607731d7
2025-02-16 07:48:35At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it. Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market.
Trade number decreased in 2024

But USD volume increased ($/year)

(same graph but $/day by year)

Which means more higher value per trade

Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!

Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).

I separate fiat payment methods into three groups.

All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)

This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).

Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.

Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)

Same group, all years

Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.

Same group, all years

What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq wiki)

There no KYC premium, but there is a small Surveillance Discount

If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...

Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)

In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.

Now let's compare the surveillance discount by week in 2024 for select payment methods.
Strike was consistently worse than Zelle

Revolut was sometimes way worse than Zelle but sometimes a little better.

The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.

Take aways * Be a maker and get a better price (fees are better too) * Zelle is better for speed + convenience * Amazon gift cards are good for speed + privacy (sorta) * Cash or money order are better for privacy + volume
-
 @ e7bc35f8:3ed2a7cf
2025-02-16 05:34:56
@ e7bc35f8:3ed2a7cf
2025-02-16 05:34:56The 2012 attack on the U.S. diplomatic mission in Benghazi has been widely debated, but the real story remains obscured by political theatrics and media smokescreens. The mainstream narrative focuses on bureaucratic failures, misinformation about an anti-Islamic film, and partisan blame games. However, when you dig deeper, a far more sinister picture emerges—one involving illegal arms deals, covert CIA operations, and geopolitical power plays that stretch far beyond Libya.
Benghazi: A Strategic Flashpoint
Benghazi, Libya’s second-largest city, was a crucial battleground in the 2011 NATO-backed uprising that led to the overthrow and murder of Muammar Gaddafi. As a key port city, it was not only economically vital but also politically significant. After the fall of Gaddafi, Libya descended into chaos, becoming a breeding ground for militant groups and a hub for illicit weapons smuggling. On the night of September 11, 2012, around 150 armed militants—reportedly from Ansar al-Sharia, an Al-Qaeda-linked faction—attacked the U.S. diplomatic mission in Benghazi. Four Americans died in the assault, including Ambassador Christopher Stevens and two former Navy SEALs who were working as CIA contractors. In the immediate aftermath, the U.S. government, led by Ambassador Susan Rice, falsely claimed the attack was a spontaneous reaction to an obscure anti-Islamic video. This story collapsed within days, leading to Republican-led investigations and heated political battles. Yet, amid the partisan finger-pointing, the most critical questions were never fully answered: What was the real purpose of the U.S. presence in Benghazi?
Why was the CIA so heavily involved in this particular location?
Was the attack a cover-up for a botched operation?
The CIA’s Secret War in Benghazi
One of the most underreported aspects of Benghazi is the sheer volume of CIA operatives on the ground during the attack. In August 2013, even CNN admitted that “dozens” of CIA personnel were present in Benghazi that night. The agency went to extraordinary lengths to keep its operations in Libya under wraps. Whistleblowers later revealed that CIA officers were subjected to frequent polygraph tests to ensure they weren’t leaking information about what really happened in Benghazi. This level of secrecy suggests something far more than just diplomatic work was taking place. What were they hiding? Evidence points to an illegal arms-smuggling operation, reminiscent of the Iran-Contra scandal, where weapons were funneled to terrorist factions in Syria under the guise of aiding "moderate rebels."
Arming Terrorists: The Benghazi-Syria Connection
Reports suggest that Ambassador Stevens himself was deeply involved in a covert weapons pipeline, shipping arms from Libya’s looted stockpiles to Syrian insurgents. These insurgents—many linked to Al-Qaeda—somehow ended up with advanced weaponry, including U.S.-made Stinger missiles. Where did these weapons come from? The very security operation in Benghazi that was supposedly meant to prevent arms from falling into the wrong hands. Lieutenant Colonel Anthony Shaffer, a military intelligence whistleblower, suggested that Stevens was likely killed because he had knowledge of these weapons transfers. Similarly, CIA contractor Robert "Tosh" Plumlee, a veteran of Iran-Contra, supported the claim that the U.S. was funneling weapons to Syria through Turkey, Jordan, and even Pakistan.
The Security Farce: Aiding the Enemy
Another bizarre piece of the puzzle is the so-called security force hired to protect the U.S. mission in Benghazi: the February 17th Martyrs Brigade. Incredibly, this group publicly displayed Al-Qaeda flags on their own Facebook page, yet they were still entrusted with U.S. diplomatic security.

Why would the U.S. government pay known jihadists to guard its personnel? Was this sheer incompetence, or something more deliberate?
A Planned Hit That Spiraled Out of Control
It appears the Benghazi attack was more than just a terrorist ambush. There are indications that it was an orchestrated hit—perhaps an attempt to eliminate Stevens before he could blow the whistle on the weapons trafficking operation. The two former Navy SEALs who died that night ignored stand-down orders and engaged the attackers, holding them off long enough for military drones to capture real-time footage. This forced the U.S. military to take notice, disrupting whatever covert plan was in motion. An Air Force whistleblower later claimed that a rescue mission was possible but was deliberately withheld. This suggests that allowing Stevens and his team to die was part of a calculated decision to prevent certain truths from coming to light.
The Petraeus Affair: A Convenient Distraction?
As if this story couldn’t get any murkier, another subplot surfaced: CIA Director David Petraeus’ extramarital affair with his biographer, Paula Broadwell. Shortly before the scandal erupted, Broadwell gave a speech in which she accidentally revealed that the CIA had been holding Libyan militants prisoner at the Benghazi annex. This revelation was explosive because it contradicted Obama’s official stance against CIA black sites. Was the Petraeus scandal used as a distraction? Was he forced out because he knew too much?
The Aftermath: Tying Up Loose Ends
Years later, in a final act of "cleaning house," a key suspect in the Benghazi attack was killed in a U.S. airstrike in Iraq. The timing, as always, was suspicious. This has become a pattern—critical witnesses and suspects disappearing before they can testify.
A Scandal Bigger Than Partisan Politics
Benghazi was not about bureaucratic missteps or political negligence. It was about illegal arms deals, black ops, and the perpetual cycle of U.S.-backed destabilization in the Middle East. The official narrative is a smokescreen designed to distract from the uncomfortable truth: The U.S. government has been covertly arming and funding the same groups it claims to be fighting. This is not a Republican or Democrat issue. Both sides of the political spectrum have been complicit in covering up what really happened in Benghazi. The military-industrial complex thrives on endless war, and the intelligence agencies operate with impunity. If history has taught us anything, it’s that these covert operations never truly end—they simply move to the next theater of war. And as long as the public remains distracted by partisan squabbles, the real architects of these schemes continue to operate in the shadows, profiting from chaos.
The question is: Will we ever hold them accountable?
-
 @ 47cc4b41:1bad46c9
2025-02-15 23:20:11
@ 47cc4b41:1bad46c9
2025-02-15 23:20:11Since the last time I wrote about a United States Bitcoin Strategic Reserve, there have been a few federal updates. Notably, Treasury Secretary Scott Bessent and Commerce Secretary nominee Howard Lutnick will be developing a plan to create the first United States sovereign wealth fund after President Donald Trump signed an executive order. The order also directs Bessent and Lutnick to develop a plan for creating the fund within 90 days. Lutnick holds hundreds of millions of dollars of Bitcoin and is bullish on the future of Bitcoin and I personally believe this is a huge indication that Bitcoin will be included in this fund.
Additionally, David Sacks, the Crypto Czar said that a top agenda item for his task force is evaluating “the feasibility of a Bitcoin reserve.”
Both of these developments in my opinion are very positive for the future of Bitcoin at a federal level but the reality is that Federal legislation takes time and can suffer from gridlock, party disagreements, and overall levels of bureaucracy that states oftentimes don’t have to deal with. For this reason, many states have already made progress in pushing strategic reserve legislation and other Bitcoin-related legislation forward. This is also a reason why I expect the states to once again “lead” ahead of the federal government as it relates to Bitcoin.
Bitcoin Laws (bitcoinlaws.io) is a resource that has emerged to specifically track Bitcoin and other digital asset legislation at the state level. The website highlights all of the outstanding legislation and provides the status and details on what is being proposed. I personally believe this resource will continue to be incredibly important for tracking what is actually happening at the state level as it relates to Bitcoin. It is rather difficult to stay up to date on all of the legislative occurrences as it relates to Bitcoin and Bitcoin Laws provides a one-stop-shop for all of the updates.

Most importantly, as of February 10th, 21 ‘Bitcoin Reserve’ bills have been introduced at the state level with 19 still active in the legislative process.
The idea that “the states will lead” reflects a theme of governance from the days of our Founding Fathers—that of Federalism. Federalism is a mode of political organization that allows separate states to unite under a national government while maintaining their own aspects of sovereignty. In layman's terms, Federalism allows for a Federal Government while also allowing State governments to have power within their individual borders. This system emphasizes a division of power with certain powers being granted to the federal government and others residing at the state level.
When the Founding Fathers created the Articles of Confederation they emphasized state power over a strong federal government. This system led to some problems such as economic instability amongst states and difficulties in coordinating a national defense eventually leading to the Constitution taking over and being the rule of the land for the centuries to follow. The Constitution created a stronger federal government while still protecting levels of state authority, autonomy, and sovereignty. The Tenth Amendment is a key aspect of this where it states, “The powers not delegated to the United States by the Constitution, nor prohibited by it to the States, are reserved to the States respectively, or to the people.” The amendment means that any powers not explicitly given to the federal government by the Constitution fall to the states.
The states having and maintaining individual power was a focal point when the United States was created and remains true today. Justice Louis Brandeis gave one of the more famous statements related to the rights of the states when he referred to them as “laboratories of democracy” during the case New State Ice Co. v. Liebmann (1932). The full quote was, “It is one of the happy incidents of the federal system that a single courageous State may, if its citizens choose, serve as a laboratory; and try novel social and economic experiments without risk to the rest of the country.” The meaning emphasized the idea that states were “laboratories” and should be encouraged to enact policy ahead of the federal government. The rationale for why states should be encouraged to do this is any policy they enact is specifically within their own borders while federal legislation typically applies to the whole country. As such, the “test area” for any new piece of legislation is much smaller and impacts far fewer people than any federally enacted policy of the same measure.
We have seen the “states lead” with numerous issues throughout the years including legislation on same-sex marriage, marijuana, healthcare experiments, climate change regulations, civil rights, and more. I believe the table is being set for the states to once again lead the federal government as it relates to policy regarding a Bitcoin Strategic Reserve.
It is also my personal belief the urgency at which legislation is confirmed for a Bitcoin Strategic Reserve is a matter of national security. Every day that a federal strategic reserve for Bitcoin is not enacted is another day that foreign adversaries and other nations can front-run our country.
The positive of this scenario is that the common man can also front-run the federal government.
The positive of this scenario is that states can also front-run the federal government.
The positive of this scenario is that states have the opportunity to once again lead and pave the way for what I believe the United States Federal government will also adopt.
Strategic Reserves within the United States both at the state and federal level will have their 0 to 1 moment and rapidly have their 1 to many rush to completion.
The States will Lead.
Stack SATs.
The views and opinions expressed here are for entertainment purposes only and should, in no way, be interpreted as financial or investment advice. Always conduct your own research when making an investment or trading decision, as each such move involves risk. I am not a financial advisor and do not claim to be qualified to convey information or advice that a registered financial advisor would convey to clients as guidance. Nothing contained in this e-mail/article constitutes, or shall be construed as, an offering of financial instruments, investment advice, or recommendations of an investment strategy. If you are seeking financial advice, find a professional who is right for you.The views and opinions expressed here are for entertainment purposes only and should, in no way, be interpreted as financial or investment advice. Always conduct your own research when making an investment or trading decision, as each such move involves risk. I am not a financial advisor and do not claim to be qualified to convey information or advice that a registered financial advisor would convey to clients as guidance. Nothing contained in this e-mail/article constitutes, or shall be construed as, an offering of financial instruments, investment advice, or recommendations of an investment strategy. If you are seeking financial advice, find a professional who is right for you.
-
 @ 9e69e420:d12360c2
2025-02-15 20:24:09
@ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement.
US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts.
Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support.
Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
-
 @ 58937958:545e6994
2025-01-02 12:33:17
@ 58937958:545e6994
2025-01-02 12:33:17May 22, 2024 I made Badger-kun’s pizza bread to celebrate Bitcoin Pizza Day.
Badger-kun: A character from the Japanese YouTube channel "Bitcoiner Hanseikai."
Making the pizza bread was quite a challenge:
Attempt 1: Rice Flour Bread
I thought it might be difficult to shape the character using yeast-based dough (since fermentation might turn it into just a plain round shape). So, I tried rice flour bread with psyllium, but it didn’t feel quite right.
Attempt 2: Cream Bread Style
The rice flour bread was too firm, so I wanted to try something softer. It ended up burning.
Attempt 3: Cheese Naan Style
 I wanted to capture that melty cheese vibe and finally thought of cheese naan.
For a character-themed pizza bread, this cheese naan approach seemed to work pretty well.
I realized that simpler character designs might be easier (and clearer) to make.
nostr:nevent1qqsd3a7thkzqde4sp4hx7qjwrjp4kxsnl66kytx40mk73djfvxfkspgu2fw34
I wanted to capture that melty cheese vibe and finally thought of cheese naan.
For a character-themed pizza bread, this cheese naan approach seemed to work pretty well.
I realized that simpler character designs might be easier (and clearer) to make.
nostr:nevent1qqsd3a7thkzqde4sp4hx7qjwrjp4kxsnl66kytx40mk73djfvxfkspgu2fw34 -
 @ 6e0ea5d6:0327f353
2025-02-15 19:47:49
@ 6e0ea5d6:0327f353
2025-02-15 19:47:49"You are a slave to whoever controls you emotionally."
"We get angry when someone tries to tell us what to do. 'Don’t tell me how to dress, how to think, how to do my job, how to live.' We feel this way because we see ourselves as independent, self-sufficient individuals.
Or at least, that’s what we tell ourselves.
Yet, if someone says something we disagree with, something inside us tells us we must argue with them. If a plate of treats is placed in front of us, we must eat them. If someone does something we don’t like, we must be furious. If a setback arises, we must be sad, depressed, or worried. But if something good happens a few minutes later, suddenly, we’re happy, excited, and wanting more.
We should never let another person shake us back and forth the way our impulses do. It’s time we start seeing things differently: we are not puppets, dancing to whichever tune suits us at the moment. We should be the ones in control—not our emotions—because we are independent, self-sufficient individuals."
— Ryan Holiday"Frame your thoughts like this: you are a mature man, and you will no longer allow yourself to be enslaved or manipulated like a puppet by every impulse. You will stop complaining about your current lot or fearing the future."
— Marcus Aurelius📌 Emotions can give us information, but they should not give us orders.
It’s not enough to learn to say "no" to others; you must also learn not to give in to the demands of your weaker self.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 58937958:545e6994
2025-01-02 12:32:51
@ 58937958:545e6994
2025-01-02 12:32:512024年5月22日
ビットコイン・ピザ・デーに合わせてバッジャー君のピザパンを作りました
バッジャー君…日本のYoutubeチャンネル「ビットコイナー反省会」のキャラクター
ピザパン作りはかなり苦戦しました
1回目:米粉パン
イースト発酵だとキャラクターの形を作りにくい気がして(作っても発酵後に単なる丸になっちゃう懸念)
サイリウムを使った米粉パンにしたんですけど
何かこれじゃない感
2回目:クリームパン風
米粉パンが固かったので柔らかいパンが食べたくなりました
焦げました
3回目:チーズナン風
 とろけるチーズ感を出したいな~と考えて
とろけるチーズ感を出したいな~と考えてここでようやくチーズナンを思いつく
キャラクター×ピザパンならこのチーズナン方式が結構いいかもしれない
もうちょっとシンプルなキャラクターだと作りやすそう(分かりやすそう)だと思いました nostr:nevent1qqsd3a7thkzqde4sp4hx7qjwrjp4kxsnl66kytx40mk73djfvxfkspgu2fw34
-
 @ c582af78:698069cc
2025-02-15 19:21:25
@ c582af78:698069cc
2025-02-15 19:21:25The Face of God: How Art Became a Gateway to the Divine
If you live in the West, you’re surrounded by depictions of God, Jesus, and the saints—from paintings and statues to illustrated Bibles and stained glass windows.
But this is far from universal. In the Islamic world, religious art takes a very different form: vibrant colors, intricate geometry, and architectural symmetry. Depictions of God or Muhammad aren’t just discouraged—they are outright forbidden.
But why?
To answer that, we must go back to the origins of the Abrahamic religions—when early Christians, Jews, and Muslims were surprisingly unified in their views on religious art.
https://image.nostr.build/1515c5fd00d798cd283583618bbbc0d5eb91bc481a84c21d53644d42fa30173a.jpg
The Early Christian Hesitation
The first generation of Christians were deeply aware of Judaism’s strict prohibition against idol worship. Depicting God in any form was considered dangerous—a potential gateway to paganism.
For centuries, Christianity could have followed this path, rejecting religious imagery altogether. But one fundamental theological idea changed everything:
The Incarnation.
As the early Church wrestled with the nature of Christ, heated debates emerged:
- Was he part human and part divine?
- Was he fully human and fully divine?
- And what did the Gospel of John mean by “the Word became flesh and dwelt among us”?
The result of these debates was the doctrine of the Incarnation—the belief that God took on human form in real flesh and blood. And if God himself had chosen to be seen in finite form, then depicting Him in art could no longer be considered blasphemous.
This single theological shift laid the foundation for Christianity’s embrace of religious art—a decision that would not only shape Christian worship but redefine how we engage with art itself.
https://image.nostr.build/1cf9ea5d1385c46bd720de9c7de65123428a9f76356e39e37c5d7b9663993930.jpg
Let There Be Art…
How did this change Christian art?
https://image.nostr.build/b945e4ea06b281bb4618f08b2543108beecf7f510aaa795bed1c833614e32fb7.jpg
The early objections to religious imagery went something like this:
“God is infinite and mysterious. Reducing Him to a finite, limited form is blasphemy.”
But with the Incarnation, the argument flipped:
“If God took on real shape, color, and form without diminishing His divine nature, then we can depict Him in art without compromising His grandeur.”
Thus, images of Jesus, Mary, and saints not only became permissible—they were encouraged.
Christian leaders actively commissioned religious art to communicate the Gospel visually to a largely illiterate population. Paintings, statues, and stained glass became tools of evangelization, helping people grasp biblical stories without needing to read.
Take the Duomo of Milan with its 4,000 statues. They aren’t just decorative. They inspire faith by highlighting the lives of the saints.
Christianity had embraced art as a spiritual bridge, a way to connect the finite with the infinite.
https://image.nostr.build/4f6b79a9179d818a951bf461ee5ff785cbe618ed376b4a56d92e77dcb34005bc.jpg
The Criticism: Were They Worshiping the Art?
Not everyone agreed.
Some critics argued that Christians were focusing too much on the art itself, rather than the God it was meant to represent.
https://image.nostr.build/29afb401ef99d2b6c59b71d8534a5160c25d2ca468d81251ba0f55d033679490.jpg
But the Church’s response was clear:
"You are not meant to look at art, but through it.
Art is not the end goal—it is a gateway to something greater.
A painting of Christ isn’t meant to be worshiped—it’s meant to draw the viewer into His story, His sacrifice, and His message.
This perspective didn’t just shape religious art. It fundamentally changed how we experience all forms of art, even secular ones.
To Infinity and Beyond: The Lasting Impact of Religious Art
Christianity’s view of art—that it should point beyond itself—has so deeply influenced Western culture that we often don’t even realize it.
Think about how we experience books, music, and movies:
- A great novel inspires courage.
- A powerful song moves you to tears.
- A gripping film motivates you to keep going in life.
The best art doesn’t just exist for its own sake—it transports you beyond the canvas, the page, or the screen.
This idea mirrors the Incarnation itself: an infinite God becoming finite to guide us back to the infinite.
Tolkien, The Lord of the Rings, and the Incarnation of Art
A perfect example? J.R.R. Tolkien’s The Lord of the Rings.
Tolkien infused his story with themes of brotherhood, heroism, and sacrifice—all timeless, transcendental ideas. But instead of leaving them as abstract concepts, he "incarnated" them into words on a page—finite, tangible, and deeply relatable.
https://image.nostr.build/b120c4d7c7232cf226af65c33cb7fc494f495d50b8ad4593a58f3528fd0b71dc.jpg
His goal? To turn the reader’s heart back to the infinite by making them experience these ideals in a concrete way.
The same can be said for any truly great art.
It doesn’t exist for itself—it exists to move you, to inspire you, to challenge you.
And next time you step into a cathedral, gaze at a masterpiece, or listen to a symphony, remember:
You’re not supposed to simply look at the art around you—
You’re supposed to look beyond it, into eternity.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ d57360cb:4fe7d935
2025-02-15 17:35:54
@ d57360cb:4fe7d935
2025-02-15 17:35:54Don’t focus on the end goal solely. If you do you’ll always find yourself empty handed. You wouldn’t want a fast forward button on your favorite song or your favorite movie. You don’t want to rush through your meals or the time you spend with important people in your life.
Notice this tendency to do things in order to get to the end. It’s sapping the depth of your existence from you.
Slow down. Life is lived in the in between. If you learn how to savor that, you’ll have a rich meaningful life.
-
 @ 58937958:545e6994
2025-01-02 12:32:28
@ 58937958:545e6994
2025-01-02 12:32:28October 31, 2024 I made pumpkin yokan to celebrate the anniversary of the Bitcoin whitepaper release.
*Yokan: A firm, jelly-like Japanese dessert typically made with azuki bean paste.
Cut a clear file into the shape of the Bitcoin logo.
 Place the ₿ mark on a slightly firm milk jelly (gyunyukan) and carefully cut it out with a knife.
Place the ₿ mark on a slightly firm milk jelly (gyunyukan) and carefully cut it out with a knife. Fill the cut-out with pumpkin yokan.
Fill the cut-out with pumpkin yokan.The mixture I made was a bit firm, so it was challenging to fill the gaps in the ₿ shape. Later, I tried a milk-based yokan with a smoother texture, which made the process much easier.
nostr:nevent1qqszzcz9npq5xgw08tp5wud0kg9wfacf9fkj07gu82wn3wjsad3wd2cppvjdw
You don’t need any special molds, so anyone can try this! I’m thinking of experimenting with different variations of the milk jelly and applying this technique to other dishes as well.





