-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-03-21 18:45:32
@ 6a6be47b:3e74e3e1
2025-03-21 18:45:32Hey frens! Today, I spent a big chunk of the morning painting with watercolors. This is only the second time I've completed a piece using this technique in a long while. It feels like coming back home after a vacation: you enjoyed the time away and relaxed, but when you're lucky enough to have a safe space to call home, there's really nothing like it. 🖼️
🎨 That's exactly how I feel about painting with watercolors again. I'm really excited to share what I've been working on with you soon. In the meantime, I've got a new blog post up about Ostara and the Spring Equinox. ⭐️Today, I just feel so blessed and excited about the future. I'm simply soaking up the moment, I guess. I hope you're feeling the same way too! Today, I also whipped up some mini veggie quiches chef's kiss.
 🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it!
🧑🍳 I wanted to spice things up a bit in the kitchen as well!
🪄I just wanted to share a little bit from my day and express how grateful I am. What did you get up to today? I'd love to hear more about it! -
 @ 6bae33c8:607272e8
2025-03-21 18:23:28
@ 6bae33c8:607272e8
2025-03-21 18:23:28I put Beat Chris Liss 3 in quotes because technically this was not a Beat Chris Liss league — I just bought it at the last minute to get an extra league. In any event, I drew the seventh spot, and here are the results:
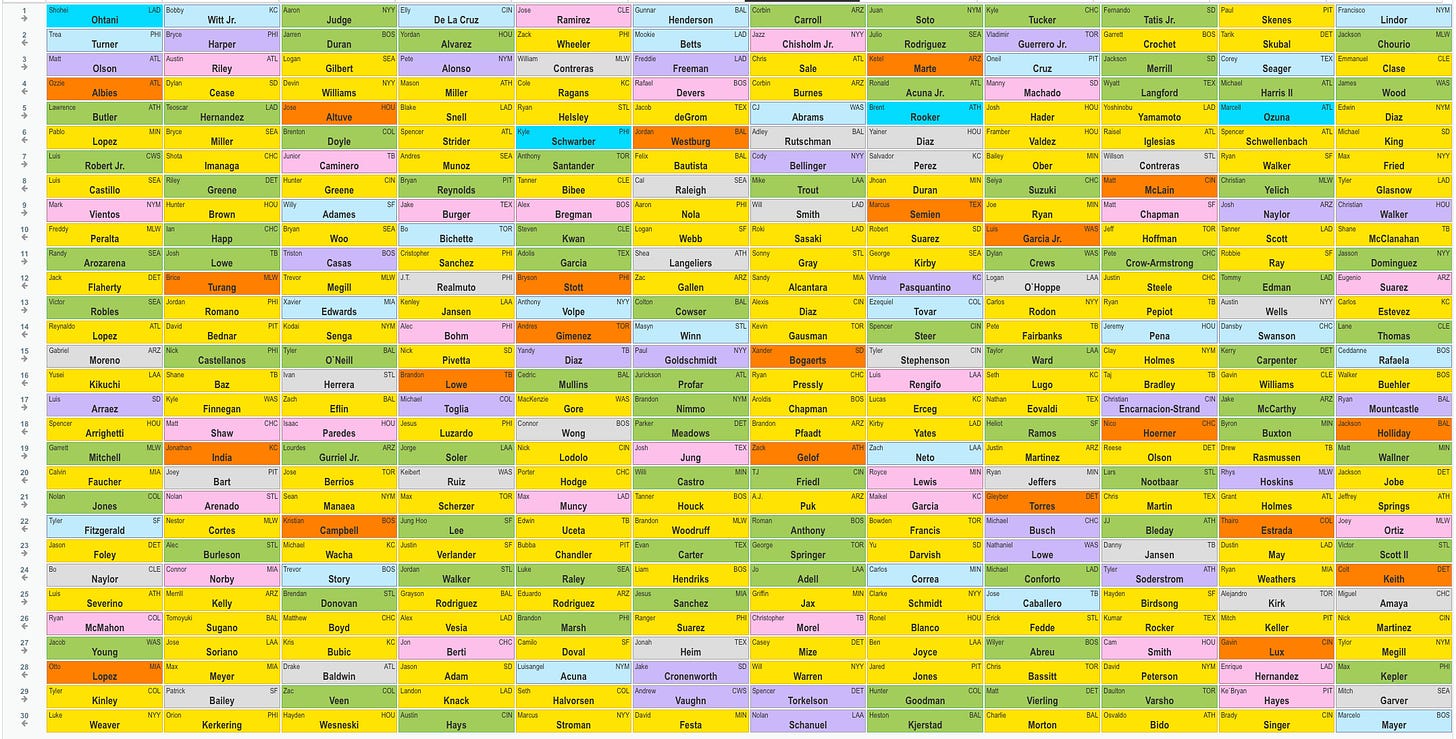
1.7 Corbin Carroll — He’s been hitting home runs this spring, a signal his shoulder is healthy. You know he’ll run, and given how he performed at the end of last year, I’d expect the batting average to bounce back too.
2.8 Jazz Chisholm — I want to see what he can do with a full year in Yankee Stadium. He’s a health risk, but he was a 20-20-ish player in Miami with only 100 games in 2023. It’s also nice that he qualifies at 3B and OF. I considered Mookie Betts, who slipped, but I’m concerned about severe weight loss from an illness undermining the first half of his season.
3.7 Chris Sale — He’s a Hall of Fame level pitcher with his health and form back. Remember when Justin Verlander faded in his 30s and then got it back together? I expect a few good years from Sale before he declines again.
4.8 Corbin Burnes — I don’t really even like Burnes, but he slipped a full round past ADP, and I value-took.
5.7 C.J. Abrams — I love this pick, probably my favorite of the draft. Abrams is a 20-30 player despite attitude issues. What if he matures and gets it together at age 24?
6.8 Adley Rustchman — I didn’t see anything I liked, and I was light on power. One way to get a leg up power-wise is to draft elite catchers.
7.7 Cody Bellinger — I like him with Yankee Stadium’s short porch, a few steals from a first-base-eligible player and also outfield eligibility.
8.8 Mike Trout — I had enough pitching and speed, but I needed some power, and Trout still has as much as anyone if he could ever play 100-plus games. He’s healthy now at least.
9.7 Will Smith — A second top catcher to pair with Rutschman. I was light on power through five rounds, but my next four picks were 20-plus HR catchers, Bellinger in Yankee Stadium and Trout.
10.8 Roki Sasaki — He slipped a couple rounds after a rough outing in Japan, but he was still throwing 100 with nasty movement. Another value-take.
11.7 Sonny Gray — A favorite old warhorse in a good pitcher’s park. I really wanted Sandy Alcantara, but Gray’s ADP was higher, so I thought there was a better chance to get Alcantara on the way back.
12.8 Sandy Alcantara — Turns out I thought right. I love Alcantara, who was going in the third round a couple years ago, now that he’s healthy and throwing 100 mph again.
13.7 Alexis Diaz — Taking Alcantara cost me my two go-to closers, Kenley Jansen and Jordan Romano, both of whom went earlier than usual, so I pivoted to Diaz. I thought this was a mistake at first — Diaz has been bad this spring, and he wasn’t even good last year, either, but he’s the closer until further notice, and a couple spring outings shouldn’t move the needle that much.
14.8 Kevin Gausman — Another old warhorse, coming off a down year, possibly due to injury. His velocity has been back up this spring too.
15.7 Xander Bogaerts — Another ADP value-take. Bogaerts had double digit homers and steals in 111 games last year and is a good bet to hit for a decent average.
16.8 Ryan Pressly — Another shaky closer, Pressly had three walks in an inning against the Dodgers, but he’s probably not losing the job over one ugly but scoreless outing.
17.7 Aroldis Chapman — Named the Red Sox closer, Chapman is probably the best of the three I drafted thus far. His ADP was lower because he was only given the role a couple days ago. Chapman perfectly fits the old warhorse mold I like too.
18.8 Brandon Pfaadt — I didn’t really need another starter, but he was the best player left on the board, and you always run out of pitching.
19.7 Zack Gelof — He strikes out a ton, but he went 17-25 last year in 138 games as a rookie, and now he gets to play in a minor-league band box. Lawrence Butler went 22-18 and is going in the fifth round!
20.8 T.J. Friedl — I was light on OF, and Friedl is one. He has a little pop, runs and is expected to lead off for the Reds in the best non-Coors hitting park in baseball.
21.7 A.J. Puk — I was still a little light in saves, and Puk is in the running for the Arizona job.
22.8 Roman Anthony — I don’t know if he’ll break camp with the Red Sox, but he was the remaining player I would have felt worst getting snaked on. He doesn’t have much left to prove in the minors.
23.7 George Springer — He went 20-20 in 2023 and 19-16 last year. He could be done, but at 35 he’s not ancient.
24.8 Jo Adell — I needed to fill in the outfield, and Adell should play, run and hit for power. The strikeouts and batting average risk are bad, but he’s still young enough to improve.
25.7 Griffin Jax — He’s a top reliever, next in line for saves and closer Jhoan Duran isn’t very good.
26.8 Christopher Morel — I needed a corner and Morel is one. (If I needed a mushroom, this would also hold.) He hit .196 last year, but he has good pop and should play OF for the Rays in a small minor-league park.
27.6 Casey Mize — The former No. 1 overall pick has looked good this spring, and he’s completely healthy.
28.6 Will Warren — Warren should get a shot in the Yankees rotation, given the injuries to Gerrit Cole and Luis Gil.
29.6 Spencer Torkelson — Another former No. 1 overall pick for the Tigers, Torkelson hit 31 homers in 2023 and should get another shot this year given his strong spring.
30.6 Nolan Schanuel — I just wanted an extra corner with regular playing time heading into the year. He runs a little and had 13 HR, but in a full season of at-bats.
Roster By Position:
C Adley Rustchman/Will Smith
1B Cody Bellinger
2B Xander Bogaerts
3B Jazz Chisholm
SS C.J. Abrams
CI Christopher Morel
MI Zack Gelof
OF Corbin Carroll/Mike Trout/T.J. Friedl/Roman Anthony/George Springer
UT Jo Adell
SP Chris Sale/Corbin Burnes/Roki Sasaki/Sonny Gray/Sandy Alcantara/Kevin Gausman
RP Alexis Diaz/Ryan Pressly/Aroldis Chapman
B Brandon Pfaadt/A.J. Puk/Griffin Jax/Casey Mize/Will Warren/Spencer Torkelson/Nolan Schanuel
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ 2fdeba99:fd961eff
2025-03-21 17:16:33
@ 2fdeba99:fd961eff
2025-03-21 17:16:33== January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
== february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
== february 14 2025
Phonetics On and On | Horsegirl
== february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
== february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
== March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
-
 @ bf95e1a4:ebdcc848
2025-03-21 17:03:01
@ bf95e1a4:ebdcc848
2025-03-21 17:03:01This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Preface
At the time of writing, it is New Year’s Day, and 2019 has just begun. For once, I have a resolution to live up to: I’ve promised myself to write a page per day every day this year until I have something real to publish. In June 2018, I published my first book, Three Minute Reads on Bitcoin — A Year of Thoughts. The book consisted of articles I had published online from May 2017 up to that point. This time it’s different. Instead of a mere collection of articles, I intend to write a “proper” book. A book that explains why Bitcoin is the most important invention of our lives.
I didn’t choose Bitcoin; it chose me. I had been trying to figure out how the world worked under the hood all my life, and then this simple idea of absolute scarcity popped up. It had a profound impact on how I view human interaction. Because of my curious nature, I instantly fell deep into the rabbit hole. I decided to educate myself on how this mysterious technology worked, and that got me into Austrian economics, which expressed very clearly what I had always suspected — that you really can't create value out of thin air.
In this book, I will try to explain every aspect of what makes this technology so special, what sets it apart from the abundant shameless copies of it, what’s wrong with our current system, and what the future might look like. In just two days from the time of writing these words, we’ll celebrate the ten-year anniversary of the Genesis Block when the Bitcoin blockchain came into being. That block contained a message, a newspaper headline that read: “03/Jan/2009 Chancellor on brink of second bailout for banks”. No one knows why Bitcoin’s mysterious creator, Satoshi Nakamoto, chose to include this in the Genesis Block. There is also some debate on whether the Genesis Block was actually mined on the 3rd of January since the next block wasn’t mined until six days later. Somehow, Satoshi managed to stay hidden and weave several layers of mystique into the fabric of Bitcoin from the very beginning, which is part of what makes its conception so immaculate. This book aims to strip Bitcoin of its shady cloak and illuminate its true nature. After all, the only thing any person can do about Bitcoin now is to study it.
Foreword
My journey down the Bitcoin rabbit hole has provided me with a newfound clarity of how our world should be perceived. In the same way that getting married and having my first child were beautiful life-changing events, discovering Bitcoin was a new chapter in my life. I can easily divide my life into two distinct periods: before and after Bitcoin.
Before discovering Bitcoin, life was perplexing. For years, even dating back to my school days, I had an innate sense that something was amiss in the world. Although I wasn’t a good student by any means, it was obvious back then that many aspects of life simply didn’t add up.
One thing that I was sure of was that money was corrupt. However, it took me a while to realize that money itself is fundamentally corrupt. Furthermore, what is typically taught and accepted as money by society is a perversion of what money should be. These are the first steps of understanding Bitcoin, which require you to admit that you have been fooled and lied to all your life. The hard lessons of hard money.
The way I see it, the revelation about the true nature of money is akin to a bracing cold shower that wakes you up to reality. Emerging from that cold shower is an incredibly liberating and invigorating sensation. Unfortunately, many individuals are not motivated enough to take that crucial step into the chilly waters. Instead, they will later experience an ice-cold bucket of water being dumped on their head unexpectedly whilst naked on a cold winter’s day.
The year 2020 was a watershed moment in my journey towards truth, and it was Bitcoin that served as my guide. As the world grappled with an unprecedented black swan event in March of that year, every asset, including bitcoin, took a severe hit. However, what followed in the subsequent months was the largest money-printing expedition in history. A tsunami of stimulus was pumped into the markets. The outcome was a K-shaped recovery. Small, honest brick-and-mortar businesses continued to suffer while many of the largest conglomerates not only rebounded but reached all-time highs. This ludicrous, short-sighted plan, known as quantitative easing, resulted in the most pronounced example of the Cantillon effect in human history, a fact that should have served as a wake-up call for anyone who was not already suspicious of the events surrounding the global financial crisis of 2008.
Since entering my post-bitcoin life, I’ve experienced a newfound coherence. The transition was not exactly instant, instead it has been a continuous process of discovering bitcoin over and over again, and I owe many of these enlightening moments to Knut Svanholm’s writing, for which I’m grateful.
While Knut’s books do not serve as a technical guide for Bitcoin, they provide a deep and philosophical introduction to a new era of money; the separation of money and state. The end of fiat money.
The creation of fiat money, a practice that emerged with the rise of central banking, has been the source of significant damage to human civilisation. Central banking, championed by Keynesianism, has granted immense power to centralized entities, allowing them to dictate fiscal policies and control the creation of money for billions of people. The very idea of a single entity wielding such vast authority and determining the economic fate of entire populations is utter madness. The state monopolizes money because it allows them to print money rather than having to directly tax people (but it still doesn’t stop them). Printing money is more easy, subtle and lucrative than direct taxation. And this continual erosion of purchasing power can be readily associated with the evident decline and deterioration of modern society.
At the heart of the issue is the importance of individual property rights. The money that individuals earn and save is their property, not the state’s. The state’s duty (should there be a need for it to exist) is to safeguard private property, not to continually debase or confiscate it. A centralized power that constantly devalues your hard-earned money and time by printing money is both morally and ethically wrong. Every individual has the right to turn their hard work into savings that they can rely on for the future.
In Bitcoin: Sovereignty through Mathematics, Knut not only delves into the fundamental principles underlying Bitcoin’s creation but also presents the groundbreaking concept of absolute scarcity. Bitcoin’s limited supply of 21 million and the impossibility of creating more due to its protocol creates a condition of absolute scarcity, a first in human history. Absolute scarcity, coupled with Knut’s poetic description of Bitcoin’s creation as "an immaculate conception," emphasizes its unique and revolutionary nature. The term "immaculate conception" highlights the fact that Bitcoin’s creation was not based on any pre-existing financial system but rather emerged from a set of mathematical principles that ensure its security and scarcity. The conditions that gave birth to Bitcoin will never be replicated, which further cements Bitcoin’s status as a one-of-a-kind element that will revolutionize the way we view and use money. Absolute scarcity aligns with the Austrian school of economics’ views on money, which argue that sound money should be scarce, durable, and difficult to counterfeit. Bitcoin ticks all the boxes for sound money, laying the ground for a genuine foundation to end the era of so-called cheap or easy money.
In the follow-up to this book, Bitcoin: Independence Reimagined1, Knut presents us, using plain logic and reasoning, the primitive constraints of the current fiat system and status quo governance. These structures, which we have so readily accepted, are gradually stripping us of our freedoms. By highlighting these shortcomings, he urges us to critically examine them and envision a future where we exercise greater autonomy over our lives, both financially and socially. Bitcoin’s simple and secure existence stands in contrast to the coercive and interventionist nature of the fiat system. Bitcoin is sincere; it neither favors nor opposes us. Bitcoin simply exists. Coming to terms with this truth is both humbling and liberating.
Knut’s writing, with its clear and elegant style, offers insightful guidance for those interested in exploring the deeper implications of Bitcoin beyond its function as a mere currency, recognizing it as a truly transformative breakthrough. A breakthrough that provides us with hope, a viable solution to reverse the degeneracy and decadence plaguing humanity.
Prince Philip of Serbia, 21st February 2023
Footnotes:
1. This foreword was originally written for a combined volume containing both Bitcoin: Sovereignty Through Mathematics and Bitcoin: Independence Reimagined.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c239c0f9:fa4a5015
2025-03-21 15:51:57
@ c239c0f9:fa4a5015
2025-03-21 15:51:57Block:#888777- March 2025The Monthly Thunderbolt Dispatch On Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin. Each issue covers the latest trends and greatest advancements dictating the future of Bitcoin adoption—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Underrated privacy tools on Lightning by @DarthCoin 4750 sats \ 21 comments \ 10 Mar on
~lightning -
ngx_l402: L402 Authentication for Nginx with LNURL, LND & NWC Support by @dhananjay 3602 sats \ 11 comments \ 11 Mar on
~lightning -
LNBϟG discusses fees and routing node management by @C_Otto 908 sats \ 3 comments \ 15 Mar on
~lightning -
New Release: Breez SDK - Nodeless 0.7.1 by @_ds 264 sats \ 1 comment \ 19 Feb on
~lightning -
Alby Hub Lightning Channel Stats the first 6 months by @k00b 376 sats \ 8 comments \ 27 Feb on
~lightning
Top posts by comments
This month we replaced the top posts by sats with these most commented posts (excluding those already listed above):
-
Cowbold Beta available for Testing: The best P2P Bitcoin alternativ to SplitWise by @supratic 699 sats \ 24 comments \ 1 Mar on
~lightning -
Nwc alternative to coinos, testing by @dingding541 150 sats \ 22 comments \ 17 Mar on
~lightning -
Payments below dust limit not trustless by @BallLightning 2141 sats \ 18 comments \ 11 Mar on
~lightning -
Question of trust regarding LSPs by @Fiatrevelation 385 sats \ 18 comments \ 14 Mar on
~lightning -
Question For CLN Start9 Users? by @siggy47 617 sats \ 15 comments \ 4 Mar on
~lightning
Top ~Lightning Boosts
Check them all here.
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar on
~lightning -
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan on
~lightning
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1998 sats \ 15 comments \ 19 Feb on
~meta -
Alby Hub: Improving the Self-Custodial Lightning Experience by @teemupleb 4642 sats \ 8 comments \ 8 Mar on
~meta -
SN is a badass use case for noncustodial lightning by @Fiatrevelation 1834 sats \ 13 comments \ 20 Feb on
~meta -
Bitcoin Users... and especially Lightning users live in a Total Bubble (sofar) by @028559d218 1304 sats \ 24 comments \ 8 Mar on
~bitcoin -
🚀 New Geocaching Meets Lightning App ⚡ by @questforsats 4518 sats \ 170k boost \ 86 comments \ 20 Feb on
~builders
Forever top ~Lightning posts
La crème de la crème... check them all here. Plenty of new entries this month too at #1, #2, #4 and #5! This means old posts get still zaps... well done zappers 💪
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
Lot of changes here, but probably due to the recent relevance search and unbusting search functionality changes:
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
We Need More Apps with Lightning, Not More Lightning Apps by @kr 5030 sats \ 22 comments \ @kr 12 May 2023 on
~bitcoin
-
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ a012dc82:6458a70d
2025-03-21 15:42:13
@ a012dc82:6458a70d
2025-03-21 15:42:13In the ever-evolving landscape of finance and investment, Bitcoin has emerged as a pivotal player, challenging traditional notions of wealth and assets. Often likened to "digital gold," Bitcoin's unique properties have led some to view it in an even more nuanced light—as "digital pearls." This article delves into how Bitcoin is redefining wealth in the digital age, drawing parallels with historical assets and exploring its impact on modern investment strategies. The comparison to digital pearls is not merely poetic but serves as a metaphor for the transformation of value from physical to digital realms. This shift is not just technological but cultural, reflecting changing attitudes towards what constitutes real wealth in our increasingly digital world.
The digital age has brought about a profound transformation in how we perceive and interact with value. Traditional assets like real estate and precious metals have been joined by a new class of digital assets, from cryptocurrencies to NFTs, reshaping the landscape of investment and wealth. This shift is not merely about the assets themselves but represents a broader change in societal values and economic structures. The rise of digital assets challenges the monopoly of physical assets as the sole bearers of value, suggesting a future where wealth is as much about information and digital ownership as it is about tangible possessions.
Table of Contents
-
The Evolution of Value: From Tangible to Digital
-
Bitcoin: The Digital Pearls of the 21st Century
-
Redefining Wealth and Investment
-
The Future of Digital Wealth
-
Conclusion
-
FAQs
The Evolution of Value: From Tangible to Digital
Historically, the concept of wealth has been tied to tangible assets: land, gold, and precious stones. These assets were prized for their scarcity, durability, and, in many cases, their beauty. However, the digital age has ushered in a new era of value, one where intangible assets like data, software, and digital currencies have become just as, if not more, valuable than their physical counterparts. This transition from tangible to intangible assets marks a significant shift in the global economy, reflecting changes in how we work, live, and interact with the world around us. The value is increasingly found not in physical objects but in the data and digital experiences they enable.
Bitcoin, since its inception in 2009, has epitomized this shift. Created as a decentralized digital currency, it offers a new form of wealth that is secure, transferable, and free from the control of any government or institution. Its blockchain technology ensures transparency and immutability, making it a trustworthy digital asset. This revolutionary approach to currency and wealth has not only challenged traditional financial systems but also redefined what constitutes value in the 21st century. Bitcoin represents a paradigm shift, moving us away from centralized financial systems and towards a more democratized form of wealth.
Bitcoin: The Digital Pearls of the 21st Century
Just as pearls were once a symbol of wealth and status, Bitcoin has emerged as a modern equivalent in the digital realm. The comparison extends beyond mere value; it reflects a shift in what society considers precious. Pearls, formed in the depths of the ocean, were valued for their rarity and beauty. Similarly, Bitcoin, 'mined' through complex computational processes, holds value due to its finite supply and the energy invested in its creation. This digital creation process, known as mining, parallels the natural formation of pearls, adding a layer of intrigue and value to Bitcoin's narrative.
The story of Maisie Plant and her pearl necklace, traded for a New York mansion, illustrates the fluid nature of value. Just as the perceived worth of pearls has fluctuated over time, Bitcoin's value is also subject to change. However, its digital nature and global accessibility mark a departure from traditional assets, offering a new form of wealth that transcends physical boundaries. This story not only highlights the changing nature of value but also serves as a reminder of the subjective and evolving nature of what society deems valuable.
Redefining Wealth and Investment
Bitcoin's rise challenges conventional investment wisdom. Traditional portfolios, heavy on stocks, bonds, and real estate, are being reevaluated as investors seek to diversify with digital assets. Bitcoin's volatility, while often cited as a risk, also presents opportunities for significant returns, drawing parallels with early investments in tech giants like Amazon and Google. This shift towards digital assets represents a broader change in investment strategies, reflecting a new era of wealth where digital assets play a central role.
Moreover, Bitcoin's decentralized nature offers a hedge against inflation and economic instability. In countries facing currency devaluation or financial crisis, it has become a means of preserving wealth, akin to how gold has been used historically. This aspect of Bitcoin highlights its potential not just as an investment but as a tool for economic empowerment and stability. The ability to store and transfer wealth independently of traditional financial systems is a powerful feature, particularly in regions where those systems are unreliable or inaccessible.
The Future of Digital Wealth
As we move further into the digital age, the definition of wealth continues to evolve. Bitcoin, and the broader category of cryptocurrencies, are at the forefront of this shift. They challenge individuals and institutions to rethink what constitutes an asset and how value is assigned and preserved. This evolution is not without its challenges and controversies, but it also offers unprecedented opportunities for innovation and growth.
The integration of Bitcoin into mainstream finance, through ETFs, futures, and other investment vehicles, signifies a growing acceptance of digital currencies as a legitimate form of wealth. However, as with all investments, there are risks and uncertainties. The regulatory landscape, technological advancements, and market dynamics will all play a role in shaping the future of Bitcoin and digital wealth. This future is not just about Bitcoin itself but about the broader implications of a world where digital assets are as common and valued as traditional ones.
Conclusion
Bitcoin's comparison to "digital pearls" offers a compelling framework for understanding its place in the modern economy. Just as the value of pearls once reflected societal trends and desires, so too does Bitcoin capture the zeitgeist of the digital age—a symbol of a new era of wealth that is decentralized, digital, and diverse. As we navigate this new landscape, the story of Bitcoin is far from over; it continues to challenge, redefine, and inspire the future of finance. The journey of Bitcoin from an obscure digital currency to a new form of digital wealth mirrors the broader transformation of the economy and society in the digital age.
FAQs
Why is Bitcoin compared to gold or pearls? Bitcoin is often compared to gold because it shares characteristics such as scarcity, durability, and being a store of value. The comparison to pearls, however, emphasizes its unique, evolving status as a coveted asset, reflecting shifts in societal values and the concept of wealth.
How does Bitcoin work? Bitcoin transactions are verified by network participants (miners) and recorded in blocks on the blockchain. Users can send and receive bitcoins using digital wallets. The supply of Bitcoin is capped at 21 million, ensuring its scarcity.
Is Bitcoin a good investment? Bitcoin's value can be highly volatile, making it a risky investment. However, some view it as a hedge against inflation and a potential part of a diversified investment portfolio. As with any investment, it's important to do thorough research and consider your financial situation and risk tolerance.
Can Bitcoin be converted into real money? Yes, Bitcoin can be exchanged for traditional currencies through online exchanges, peer-to-peer platforms, and some retail locations. The exchange rate varies based on market conditions.
Is Bitcoin legal? The legality of Bitcoin varies by country. Some countries have embraced it, while others have imposed restrictions or outright bans. It's important to check the regulations in your specific location.
What is the future of Bitcoin? The future of Bitcoin is uncertain and subject to various factors, including technological developments, regulatory changes, and market dynamics. It continues to gain acceptance and has sparked a global conversation about the nature of money and the future of financial systems.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cc601241:181cd0d2
2025-03-21 15:11:09
@ cc601241:181cd0d2
2025-03-21 15:11:09
- Money doesn't grow on trees
- There is no such thing as a free lunch
- Energy cannot be created or destroyed
What if I told you these are three different ways of saying the exact same thing?
If you recognize that money is a unit of account, a medium of exchange, and a store of value, then it's only natural to accept that money at its most abstract formulation is simply information:
"Money is information. It is information we collect about the cost of things. We use it to quantify the world around us. To allow us to figure out what our things are worth in relation to other things. The soundness of a money measures its reliability in storing value over time. Sound money is reliable; you can count on it having a certain value today and in the future. Sound money allows us to determine the proper price of goods and services. Unsound money makes it difficult to figure out what anything should cost. Sound money accurately stores information about the cost of things. Sound money is a sensible store of information."
So long as fiat money can be printed ad infintum to bankroll the military industrial complex, why would we consider the US dollar to be accurate information? Why would we be surprised to see the negative externalities of dark money, regulatory capture, institutional usury, systemic seigniorage, and pervasive rent-seeking happening everywhere? Why wouldn't we start questioning the ripple effects of the Cantillon effect? Why wouldn't the rest of the world's economic actors that operate downstream of the dollar supply not live in constant fear, uncertainty, and doubt? If not resentment, cynicism, and desperation?
"Infinite money creates a scarcity mindset in almost everyone. Most people observe the rising cost of living and experience the feeling of fear or even panic. Fear of the unknown, fear of the future. Uncertainty about making ends meet. Leaky money promotes hoarding, individualism, and fast food culture, where everything is built as quickly and cheaply as possible."
If money is no longer a reliable measure of value but simply a means of control and extraction, how can humanity collaborate or organize or build together? How can we incentivize cooperation? How can we coincide our wants? How can we hope at all?
"Money is a medium of communication. It is one of the most common ways we communicate. Money is a sense-making apparatus. In the broken money world, a subtle distortion becomes ingrained in the foundational layer of sense-making, leading to a systemic corruption of all communication within the system."
Enter a pseudonymous, Good Samaritan, white hat coder: Satoshi Nakamoto.
A cypherpunk who asked a very simple question...

What if there was a money that was not backed by the Federal Reserve or 11 aircraft carriers and 5,000 nuclear warheads and the monopoly of violence? What if that money was backed not by physical scarcity (gold) or political scarcity (fiat) but by mathematical scarcity (blockchain aka timechain)? What if that money operated on principles like "rules without rulers" and "don't trust, verify?" What if we finally had an Occam's razor for economics?

What if that money were backed by the currency of the universe itself: energy?
"Bitcoin's immaculate conception presents the possibility that it has always existed. The genesis block could be viewed merely as the first time we started recording Bitcoin. Knut Svanholm has discussed the idea that Bitcoin might be an element with an atomic weight of zero and that the discovery of Bitcoin is better described as the discovery of our ability to observe this element.
For an element to have an atomic weight of zero, it must be void of protons or neutrons, possessing only electrons. Element zero is purely information. If element zero had always existed prior to our ability to measure it, that means it would have existed back to the time of Lao Tzu. If true, it means there could be undiscovered methods for gauging that information. The understanding of how to observe element zero might not be a binary event.
The interesting thing about observing element zero is that the process requires energy. Producing element zero requires a predictable amount of energy. Interacting with element zero requires energy. By spending Bitcoin, we capture a measurement of the value of the thing we spent it on, priced in energy; because element zero requires energy to produce, we can almost think of pricing other things in Bitcoin as pricing the energy spent in creating them. Element zero transfers energy."
All economy is just the transformation of energy into value. If one accept this definition of economics, then Bitcoin is the purest conversation of energy into value. This would explain why the world is seeing an emergent first principle emerge known as the Joule Paradox:
"Energy sets the value of bitcoin and bitcoin sets the value of energy."

Therefore, Bitcoin is the only money that obeys the laws of thermodynamics.
If we have a transparent public ledger of information backed by energy, we could safely call this document the most objective database in the entire world because energy is the only thing in the entire universe that no one can fake.
That's the power of triple entry bookkeeping. No one can cook the books anymore.

Once humanity is able to guarantee the separation of Money and State, suddenly everyone has a way to protect their own time and energy without having to trust a third party. We are no longer slaves to "absolute power corrupts absolutely". We are no longer beholden to the powers that be. Humanity finally has an incorruptible, immutable, unconfiscatable, permissionless, borderless, open source money available to all.
In a world of manipulated markets, self-sovereignty starts with sound money.
Believe it or not, the thesis of The Dao of Bitcoin: Towards a Cosmology of Energy Money (by Scott Dedels—which I have been quoting throughout this article) states that Bitcoin is "perfect money" (or "daomoney" as he coins it) for the following reason:
Bitcoin = time = money = energy = Bitcoin
There is nothing more valuable than protecting your time & energy. But no one can force you to believe that. Self-sovereignty is a game of consent. The first act of financial freedom is to choose it. The deeper into the Bitcoin rabbithole you go, the sooner you'll have the unmistakable epiphany:
Bitcoin is a strange game where the only winning move is to play.
Bitcoin is just money without the Bullshit. No CEO, no country, no committee, no corporation, no cartel, no council, no conglomerate, no counter-party, no church, no cult of personality. Just pure P2P energy transfer. That's the beauty of freedom money. That's the reason for energy money. That's the answer to the game theory.
With absolute mathematical scarcity, individuals can finally afford an abundance mindset.
For the sovereign individual, all you have to do is nothing but HODL.
That's financial wu wei.
That's energy money that aligns with the universe & vibes with the Dao.

-
 @ 43bb87e2:12cc9cb8
2025-03-21 15:06:52
@ 43bb87e2:12cc9cb8
2025-03-21 15:06:52There was once a little girl that got into some expensive golden wrapping paper, and her father got upset. In his anger, he yelled at his little daughter for wrecking the expensive wrapping paper. The daughter then decided to use the ripped and wrecked wrapping paper to wrap a gift for someone. Again, the father let his anger take over and got mad at the little girl for using the ripped paper for the gift wrapping. The next morning, the little girl presented the tattered, golden wrapped box to her father and said this is for you, Dad. He opened the wrapped box and saw that the box was empty inside. The dad again got angry and told his daughter that when you give a gift to someone, there is supposed to be something inside of it. The little girl, in tears, looked up at her father and said, but it is full daddy. I blew kisses into it until it was completely full. The father then broke down and started crying. He dropped to his knees and put his arms around his precious and innocent daughter. He desperately apologized to her for his anger and continued to ask for her forgiveness. A short while after this, his daughter was taken from this earth because of an accident. The father kept the golden wrapped box next to him for the rest of his life to remind him of the love he had from his daughter.
Nothing else matters in this world or even comes close to the unconditional love that our children and family have for us.
With life being so busy, don’t you dare forget, what really matters in this world. And you be sure to take care of your loved ones, family, and friends.
For we do not know when the last day we will be on this earth.
CHERISH EVERY MOMENT AND LOVE WITH ALL YOUR HEART!
DO NOT LET ANGER RULE OVER YOU.
TELL EVERYONE IN YOUR LIFE,
THAT YOU LOVE THEM!
TELL THEM TODAY!
DO IT NOW!
LOVE YOU ALL, BE BLESSED!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11
@ 46fcbe30:6bd8ce4d
2025-03-21 13:57:11Table of Contents
- Introduction
- Overview of the Nostr Ecosystem
- Current Use Cases and Quantitative Metrics
- User Adoption Metrics
- Network Resilience and Decentralization
- Operational Challenges and Scalability
- Replication Overhead and Bandwidth Issues
- Relay Downtime and Financial Sustainability
- Market Disruption and Sentiment
- Disrupting Twitter and Centralized Social Platforms
- Impact on Decentralized Social Media and Censorship Resistance
- Future Trends and 5-Year Outlook
- Innovative Protocol Developments
- Quantitative Forecasting and Diffusion Modeling
- Networking and Integration with Emerging Technologies
- Conclusions and Strategic Recommendations
1. Introduction
The Nostr ecosystem has emerged as a powerful decentralized alternative to traditional social media networks, particularly as a potential disruptor of Twitter and other centralized—and even existing decentralized—social media platforms. Developed using a protocol based on cryptographic key pairs and a multi-relay system, Nostr is unique in its provision of censorship resistance and user sovereignty. In this report, we provide a detailed analysis of the current state, scalability challenges, and market disruption potential of Nostr, followed by speculative insights on its trajectory over the next five years.
2. Overview of the Nostr Ecosystem
Launched in 2022, Nostr (Notes and Other Stuff Transmitted by Relays) has rapidly gained traction as an open and decentralized social network. Some of the core features include:
- Decentralized Communication: Relying on independent relays across multiple countries and autonomous systems, Nostr offers an architecture that ensures posts are not stored on a single centralized server.
- Censorship Resistance: With cryptographic authentication and a decentralized relay structure, content censorship becomes significantly more difficult than in traditional networks.
- User Sovereignty: Empowering users with cryptographic key pairs allows for enhanced privacy and data ownership.
- Wide Geographic Distribution: The ecosystem spreads over 44 countries and 151 autonomous systems, underscoring its global reach.
Notable endorsements from figures such as Jack Dorsey, Edward Snowden, Vitalik Buterin, and Sen. Cynthia Lummis have bolstered its reputation as an experimental yet promising alternative to centralized social platforms.
3. Current Use Cases and Quantitative Metrics
User Adoption Metrics
- User Base: In just two years, the Nostr network has attracted over 4 million users, a significant figure given its nascent stage and decentralized nature.
- Content Generation: With over 60 million posts, the volume of content mirrors the rapid adoption and active usage seen in more centralized models.
- Post Replication: Empirical measurements indicate that there are 17.8 million text notes among these posts, replicated on an average of 34.6 relays per post. This level of replication underlines robust resilience and availability even if significant portions of the network experience downtime.
Network Resilience and Decentralization
- Global Distribution: Nostr’s decentralized network ensures high availability with >90% post accessibility even under simulated network failures (e.g., removal of key relays or autonomous systems).
- Robustness: The dispersion across 712 relays illustrates that decentralization is not only a design choice but also a working reality, which contributes to the network’s reliability.
4. Operational Challenges and Scalability
While the Nostr ecosystem demonstrates significant promise, it faces noteworthy operational challenges.
Replication Overhead and Bandwidth Issues
- Excessive Redundancy: Detailed studies have shown that nearly 98.2% of retrieval traffic is redundant. In practice, this equates to an estimated 144 TiB of unnecessary bandwidth consumption.
- Optimization Proposals: To mitigate these inefficiencies, there's a proposal to limit post replications from 34.6 relays to between 10 and 20 relays per post. This could reduce redundant data copies by between 380 million to 480 million instances, potentially lowering operational costs and improving bandwidth utilization.
- Scaling Concerns: With a projected network load of 10 million events per day (or approximately 2 TB annually), the throughput requirement of ~115 TPS is putting a strain on the current architecture. This has led to debates on whether solutions like the current outbox mechanism are sufficient or if further fundamental redesigns and emergent moderation systems are needed.
Relay Downtime and Financial Sustainability
- Relay Stability: Data indicates roughly 20% of relays suffer from significant downtime (exceeding 40% operational time), and 132 relays have been classified as 'dead'. This is a concern for maintaining network integrity.
- Economic Model Challenges: With 95% of free-to-use relays unable to cover operational costs due to minimal zap-based income, there is an urgent need for innovative monetization or community funding models to ensure long-term sustainability.
5. Market Disruption and Sentiment
Nostr is positioned as both a disruptor to traditional centralized social platforms—most notably Twitter—and a catalyst for change within decentralized social media.
Disrupting Twitter and Centralized Platforms
- User Shift: While Twitter remains the most well-known platform, the high-profile endorsements and robust user base of Nostr indicate that there is both market intrigue and a gradual shift among early adopters. Disruption here is measured not only in user numbers but also in the paradigm shift towards decentralized content distribution.
- Market Penetration: Current metrics (4 million users, 60 million posts) suggest that Nostr is challenging Twitter's centralized model insofar as it appeals to users prioritizing censorship resistance, data sovereignty, and resiliency against centralized failures. However, mainstream adoption on par with Twitter is still not realized, and there remains a gap in user experience and feature richness.
Impact on Decentralized Social Media and Censorship Resistance
- Complementary Integrations: As decentralized social media ecosystems continue to mature, integration between Nostr and other censorship-resistant platforms is increasingly likely. This can include interoperability protocols, shared identity management systems, and cross-platform content replication.
- Comparative Advantage: Nostr's network design offers unique advantages over other decentralized social media, particularly in its straightforward, relay-based communication protocol. This positions Nostr to potentially serve as an underpinning technology for a broader decoherent ecosystem of social networks.
- Sentiment Toward Scalability Innovations: Discussions around scaling Nostr often focus on the balance between ensuring redundancy (for resilience) and reducing overhead (for efficiency). The sentiment is one of cautious optimism: while outbox solutions offer a stopgap, many experts advocate for more fundamental architectural redesigns in the long-term.
6. Future Trends and 5-Year Outlook
Looking forward, the evolution of Nostr will likely be shaped by several interrelated trends and emerging technical innovations.
Innovative Protocol Developments
- Decentralized Identity and Reputation Mechanisms: The next phase may see the introduction of distributed reputation systems and rating mechanisms that aid in spam management and improve trustworthiness without compromising decentralization.
- Optimistic Replication and Selective Mirroring: Innovations such as selective content mirroring and event pruning will be key in managing bandwidth and storage demands while remaining true to the decentralized philosophy.
Quantitative Forecasting and Diffusion Modeling
- Forecast Models: By integrating modified Bass diffusion models and learning curve effects, predictions suggest that Nostr can potentially spur significant market disruption within five years. Recent studies indicate that forecasting models in disruptive technology fields have reached accuracies of up to 82% for demand projections.
- Hybrid Quantitative Techniques: Leveraging methods like LDA2Vec and patent citation network analysis, combined with multi-criteria decision-making models (as seen in extended UTAUT approaches), will be crucial for accurately estimating future adoption and cost efficiencies.
- Metrics to Monitor: Future research should focus on user growth rates, relay uptime percentages, cost reductions achieved through replication optimizations, and overall sentiment analysis using advanced deep learning architectures that overcome traditional pitfalls (e.g., sarcasm and multipolarity in text data).
Networking and Integration with Emerging Technologies
- Integration with Other Decentralized Platforms: One promising avenue is exploring cross-platform interoperability with other decentralized and blockchain-based social networks, which could lead to a more cohesive ecosystem. This would not only enhance user experience but also enable shared security and moderation frameworks.
- Next-Generation Relays: The deployment of relays that are more resilient through redundancy optimization and financial sustainability models (perhaps incorporating micro-transaction revenue models or community-driven funding) is another critical area. Such improvements could mitigate the issues of relay downtime and excessive network overhead.
- Contrarian Approaches: A contrarian perspective suggests that instead of building on current frameworks, a radical overhaul of the network architecture might be considered, potentially by leveraging novel distributed ledger technologies or leveraging a hybrid centralized-decentralized model during the transition phase to ensure smoother scaling.
7. Conclusions and Strategic Recommendations
The Nostr ecosystem represents a significant stride toward decentralized, censorship-resistant social media. While its current market adoption and technical design offer a robust alternative to centralized platforms like Twitter, several challenges must be addressed for sustained growth and disruption:
-
Optimization of Data Replication: Reducing redundant data transfers without compromising resilience is essential. Limiting the replication factor and exploring optimistic retrieval mechanisms could provide a balance between availability and efficiency.
-
Relay Stability and Sustainability: With nearly 20% of relays experiencing significant downtime, innovative financial and technical models (such as micro-payments and community funding) should be deployed to enhance the operational reliability of network nodes.
-
Enhanced Moderation and Reputation Systems: Emerging strategies for decentralized content moderation and reputation management could reduce spam and improve content quality while preserving the open nature of the network.
-
Interoperability with Other Decentralized Platforms: Fostering integration with other emerging systems could accelerate market disruption across the broader spectrum of social media.
-
Future-Proofing Through Quantitative Forecasting: Continual adoption of cutting-edge forecasting models and machine learning techniques to measure sentiment and track network metrics is imperative for proactive evolution.
-
Exploring Contrarian Innovations: In addition to incremental changes, it is important not to discount radically new architectures that may emerge from ongoing research in distributed systems and blockchain technologies.
Final Outlook
In the coming five years, Nostr has the potential to disrupt not only Twitter but also the broader landscape of both centralized and decentralized social media. Although the current architecture presents significant scaling challenges, proactive investments in replication optimization, relay stability, and cross-platform integration will likely propel the network into a more mature phase of adoption. The ecosystem will benefit from a dual approach that combines both evolutionary improvements and revolutionary changes, ensuring that it remains robust while meeting the demands of a growing, globally distributed user base.
Appendices
Appendix A: Data and Metrics Summary
- User Base: ~4 million
- Post Volume: >60 million posts
- Average Relay Replication: ~34.6 replicas per post
- Geographical Distribution: 44 countries, 151 autonomous systems
- Bandwidth Waste: ~144 TiB due to redundancy
- Network Load: 10 million events/day (~2TB/year)
- Throughput Requirement: ~115 TPS
Appendix B: Key Technical Proposals
- Replication Control: Limit copies to 10–20 relays for optimal efficiency.
- Selective Mirroring: Implement event pruning and selective content mirroring.
- Decentralized Reputation Systems: Develop distributed rating mechanisms to enhance distributed moderation.
Appendix C: Forecasting and Quantitative Methods
- Diffusion Modeling: Modified Bass models with multi-market dynamics.
- Hybrid Quantitative Techniques: Integration of machine learning (CNN-LSTM, LDA2Vec) with multi‐criteria decision models.
Recommendations for Further Research
- Investigate the comparative performance of alternative replication strategies in decentralized networks.
- Explore funding models that can sustain relay operations without compromising neutrality or decentralization.
- Conduct long-term sentiment analysis using advanced neural architectures to understand evolving user attitudes.
- Evaluate the prospective benefits of radical design overhauls versus incremental enhancements in ensuring network scalability.
This report is intended for expert analysts and researchers in decentralized network systems and social media disruption. It synthesizes current empirical findings with speculative insights to inform future strategies and academic inquiry.
Sources
- https://www.voltage.cloud/blog/exploring-6-use-cases-of-nostr-beyond-messaging
- https://arxiv.org/abs/2402.05709
- https://arxiv.org/html/2402.05709v1
- https://papers.ssrn.com/sol3/Delivery.cfm/5146515.pdf?abstractid=5146515&mirid=1
- https://matchnode.com/blog-and-podcasts/mastering-paid-social-media-advertising-a-comprehensive-guide/
- https://blockworks.co/news/jack-dorsey-app-to-disrupt-twitter
- https://www.securities.io/nostr-a-better-twitter/
- https://medium.com/@jasminedevv/battle-of-the-decentralized-twitter-alternatives-c9f51114614a
- https://www.murrayrudd.pro/nostrs-relay-revolution-scaling-decentralized-networks-for-growth/
- https://github.com/nostr-protocol/nips/issues/75
- https://news.ycombinator.com/item?id=42758579
- https://www.toptal.com/deep-learning/4-sentiment-analysis-accuracy-traps
- https://www.researchgate.net/publication/3076742_Forecasting_the_Market_Diffusion_of_Disruptive_and_Discontinuous_Innovation
- https://www.globenewswire.com/news-release/2025/03/17/3043701/0/en/United-States-Online-Household-Furniture-Market-Report-2025-2029-Analysis-of-Price-Sensitivity-Lifecycle-Customer-Purchase-Basket-Adoption-Rates-and-Purchase-Criteria.html
- https://northeast.newschannelnebraska.com/story/52583550/laser-welding-market-growth-industrial-adoption-rate
- https://www.sciencedirect.com/science/article/am/pii/S2405896323014453
- https://www.marketsandmarkets.com/Market-Reports/industry-5-market-35376359.html
-
 @ 8671a6e5:f88194d1
2025-03-21 13:38:50
@ 8671a6e5:f88194d1
2025-03-21 13:38:50As old people tend to say:\ \ *nasal voice* “Back in my day…” … Bitcoin was this wild, beautiful thing, new. It was something technical that came alive before our very eyes after running a node (just a .exe running on a windows machine in my case).\ Even when you started to painstakingly mined bitcoin on a GPU, in a pool, you felt like growing a network of like minded people, or at least people who thought there was something there. Even if we couldn’t comprehend what it all would lead to (or what fiat value it could reach).\ Then came the first paper wallets, the first good software wallets and attempts at hardware wallets, the first buzz of owning your own value — it was motivating and rewarding. The look on the face of other people you explained bitcoin to, when they’ve seen their first transaction pop up after validation. Awesome.\ \ Back then, it wasn’t about fiat gains or slick marketing campaigns; it was about a distributed network “generating” numbers, keeping a distribute ledger “in synchronization”, at the same time it was a middle finger to the system, representing freedom to transact in value we valued ourselves because of the underlying network of people, nodes and miners.\ \ It was this sort of secret handshake between tech minded people, anti-globalists, anarchists, nerds and rebels who saw the fiat scam for what it was.\ Orange-pilling wasn’t even a term; it was just what you did.\ You'd walk people through the setup of bitcoin core, and the white paper, told them why central banks are a trick that functions as a legalized Ponzi scheme and you showed them bitcoin’s workings without middlemen.\ You played around with bitcoin, person to person, no bullshit, no subscriptions, no suits, no posing like a big shot, no referral links.\ Those were the fun times — pre-Saylor, pre-nation-state hype, pre-every Laura, Luigi, and self-proclaimed “OG” thinking they’re going to conquer the world.\ I miss that.
But times change.
\ The good ol' days are dead
It’s not the first instance in our lifetime that we see things pop-up, being invented, and where some good new idea becomes a reality and then that very good idea becomes an institution (there’s an obscure 1990s movie reference for you).\ We live and learn, just like the first technical people setting up their own point of presence internet servers, we all have to learn how to grow and adapt.
Early Bitcoiners didn’t have referral links or corporate sponsors — they had a mission, and the spirit came from within themselves and from the math and tech they’ve seen at work in practice. And yes, educating about it was important, as was looking for ways to improve bitcoin (the early years weren't exactly main-stream material for example).
From that learning yourself about Bitcoin and feeling the need to share and convince others around you, came the need to talk and learn together with others.
You’d talk your buddy into installing a wallet over a coffee, maybe show your uncle how to buy a few bitcoin, and it felt like planting seeds for something real.
Even if they didn’t get it—“So this number goes from my address to your address?”—you kept explaining and showing.
Then the suits rolled in. Bigger companies wer started, like Blockstream, Trezor, Coinbase and Binance.
Wall Street, Saylor with his infinite buy tweets, El Salvador and its volcano bonds, the US ETF approval — and the game changed, everyone heard about it one way or another. That’s damned important! You’re NOT the bringer of news.\ \ Suddenly, it wasn’t grassroots anymore; it was headlines, hype and game-theory. As predicted by so many in the space.\ Fine, whatever, it's progress or something else, but we as bitcoiners need to adapt to that reality.\ Some adaptations will also cause us to put energy elsewhere than before.\ What worked in 2012 or 2016, might not work anymore after 2024.\ ”We bitcoiners route around problems.” Right?
You didn’t need new people to create an account, or be part of a ‘squad’ or team, you certainly didn’t need them to sell merchandise. You just showed them bitcoin’s inner workings.\ \ Bitcoin was the marketing, the engine, the product and the goal. Bitcoin was the core. Just like digital communication was the core of the earliest internet enthusiasts. The magic of sending a text into the network, and through clever routing, someone thousands of miles away could read it almost immediately, that was the magic, the core.
Sending value with bitcoin has that same magical way, immutable, uncensored, unconfiscatable, with proven digital scarcity and forced honesty.
Nowadays we have so-called orange-pillers.\ They’re trying to spread those values. Or so they should..
They didn’t get the memo on Bitcoin becoming more commonly known apparently, and if they did, their lust for dopamine has long replaced that with their urge to get people to install a lightning wallet. It’s sometimes rather disturbing to see this Orange Pill’ing play out.
They’re out there, like they’re stuck in 2013. But they’re usually not from 2013 at all, more like class of 2020’ish. Not that it matters, they’re still living in the illusion that there are people out there that didn’t hear of bitcoin and that THEY and THEY alone can save these poor souls.\ After 2018 it’s safe to say that that’s not the case.\ I’ll repeat that for the die-hard orange-piller: they do not need you to hear about bitcoin.
These Orange Pillers have another kind of magic happen:
While they’re winning over new souls into bitcoin, one barber, taxi driver and babysitter at a time, they get the small electric charge in their brain that tells them their wealth, their (and their holding's) value will go up somehow. They’re also desperate to make some kind of connection with other bitcoiners, and while they lack that connection, they try to find (or make) new bitcoiners around them.\ This approach might have worked in the past, but things are different now. You’re usually talking to people who you try to convince of something they’ve already rejected (often harshly rejected) or never will care about .\ Most people, do not give a damn about inflation or how that came to be. Certainly when they’re doing their job.\ \ It’s like someone shoving the book of a cult under your nose and trying to convince you it’s going to save your life. You’re not open to it, neither are most of the Orange pill targets to your bitcoin gospel.\ Orange Pillers don’t see how the very people they try to convince today weren’t “in it” for a variety of (good for them) reasons. Unlike in the old days, where people’s natural state was “not heard of bitcoin”; since it was new, and people genuinely didn’t learn about it or read into it.\ That’s however, not the case today. That taxi driver? He heard about bitcoin. Be sure.
Such new people today, are almost non-existing, they either bought some long ago, got rekt trading shitcoins and stayed away.\ That, or they found it all a bit too “iffy” (thank you mainstream media) and will politely hold back from not yelling to your face, “I don’t care about that Bitcoin stuff!”.\ They know it’s some form of money or value, they know it exists. Which makes orange pillers the bringers of old news to the bottom of the barral.\ They might get a “hit” now and then of course. But even then, your impact is neglectable in a world that rewards cowardice and short term greed. You’re too late. You don’t scale. And it doesn’t matter.
Since 2020, it has shifted from genuinely introducing people to bitcoin to just "spreading it for the sake of spreading it."\ It looks more and more like an old lion, pacing back and forth in a cramped cage at an old ZOO, restless and frustrated.\ There’s just empty repetition.
The mental breakdown of orange-pilling
\ Let’s look a little further into the act of orange pilling.\ \ It's not like a 1990s hacker type showing a brand new Hayes -compatible modem to his buddy and trying to get a connection going to a local Point of Presence to get internet access.\ \ It’s more like showing your holiday pictures to an uninterested family member. All to get the dopamine hit, the ‘aha moment’ out of someone is now your own ‘aha got someone new’ moment. Like an addict looking for that next high.\ \ You want them to get the app, get some sats and feel the same feeling you have. While they’re worrying about cleaning a table for example, or getting your bill.\ \ This “badge of honor” of Orange Pilling someone is that little shot of dopamine many people need (especially in group) to feel validated.\ The real feeling has everything to do with social conformity1 and the involved brain areas that get stimulus shots and increased activity.2\ \ Above that, for the sake of the mental reward, some people go further down the social boundaries. That’s why orange pilling, often comes across as pushy, unnatural and/or annoying.\ It’s because it’s basically an activity with all the neuro stimulus of an addiction, or done as an ego boost.
Math based
On top of all of that. If you do the math on it the whole action becomes even more ludicrous.\ \ The math in the early days of bitcoin was simple: there was exponential expansion of the number of bitcoiners.\ Purely for bitcoin, the growth in numbers is still going strong, but the percentage has now naturally been flattened out because of media coverage, scams that trick people into other stuff and the close to impossible way to scale the onboarding from a person to person level to larger scales (there are apps doing a good job however, but even then it spread under former bitcoin users or people already in the know on some level, like former shitcoiners).\ \ So even at the rate of trying to orange-pill let’s say 10 people per week (many bitcoiners don’t even tàlk to 10 people a week, let alone convince them to use bitcoin).\ \ When hypothetically 50% of these people (not unusual with word of mouth recommendations) actually install the app you recommended, and we take also a high percentage of 10% actually do a regular buy of bitcoin after installing any of these apps (Strike or Blink or any other).\ \ Given that hypothetical high rate of 10 people a day plus the conversion rate, it would take approximately 200 weeks, close to four years (pun intended) to reach 2000 people as a critical mass that actually installed and used the bitcoin app.\ \ If these 2000 people all buy for about 1000$ worth of bitcoin each, they’ll be good for about 2 million dollars in bitcoin buys over a four year period.\ Even if you take very, very optimistic statistics this, you’ll get a close to zero impact, safe for the occasional big shot you might encounter and converts into a mini-Saylor, or the occasional person you might have saved a few thousand dollars (because they all keep thinking in fiat terms anyway).\ \ But on the other side, people with +100 million dollars to spend will surely have advisors and in-house knowledge, to not having to to rely on your sorry ass explaining bitcoin or installing Wallet of Satoshi on their phone or something.\ \ That’s all peanuts. It’s futile. And you’re fighting an honorable battle from 11 years ago.
### \ Why
I can't grasp why so many people keep doing this the way they do.
Orange-pilling mostly works when the price is going up anyway, unfortunately.
However, when BTC’s up 15% in a week, everyone’s a genius and your coworker suddenly can be all ears about “sound money” and future price gains.
When it’s crashing or flat? Good luck, nobody cares among the normies, unless the “orange-pillee” (the target) has their own ulterior motives for listening (like getting someone to at least give them some attention in any form).
And by the way, to come back to these taxi drivers you try to convince… many taxi drivers already had their share of die hard bitcoiners in their car, and got the explanation. Some of them even act like total noobs probably to get some sats out of your orange pilling wallet. They’re good at playing dumb, trust me.\ \ Do you really think a taxi driver in let’s say Lugano, Amsterdam or Prague didn’t already know bitcoin before you tried to convince him to accept it? You’re not the first. At all.
Most of all, you interact with people while they’re doing their job. You’re actually interfering with their work. When a waiter in a fully booked restaurant has to halt his word and listen to you explaining how to install a lightning wallet on their old iphone that’s almost out of battery, you’re losing anyway.\ They might listen, they might even be pestered to the point they’ll install the damned app. And what do you win or achieve?\ A sparkle in your brain that says “you’re such a cool bitcoiner”?\ Then… after what’s usually a painful few minutes going through a horrible counter-intuitive interface, you get them 5000 sats or whatever over to them.
Oh and adding things like “Hey man, keep these sats for at least 4 years, it will go up in price” is just rotten as well. Just give the people a decent tip and leave. You’re not doing anyone a favor.
When the moment’s there ànd some people are clearly open to it, thèn you might add some info. Point them to an easy to use non KYC app (if there is such a thing).\ But even then, just letting someone know you want to pay in bitcoin, should be enough, WHISPER bitcoin.\ They don’t need your pushy sales pitch on top of the daily struggles they face in hospitality and retail jobs.\ \ The squads
An example,... I saw this crew, let’s name them the “Re-play” squad, they’re all wearing blue hats and have a few flyers with them from a marketing company which managed to put them to some good use at a very low expense rate.
This image is still stuck in my head, some random European country during late summer time — local Bitcoiners, along with some counterparts from other countries. The real “we’re the future” types.
Sitting on the floor at a Bitcoin party, rolling “funny cigarettes” passing a lighter, chatting and laughing about how they orange-pilled some dude in a bar.
 “Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.
“Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.They’re all proud, they’re all high, they all belong to a group now … and they’re convinced they’re conquering the world one wallet at a time (they don’t do the math on that, neither should they,… ignorance is bliss).
Doing good for bitcoin has been transcended into an egotrip, and the short-lived kick in the orbitofrontal cortex3 for “doing something”, it’s the filling of a lingering emptiness.\ \ The same people move around like they’re an anthill, reminiscent of the hippie communes, until they’ve returned to their misery at home, knee deep in sorrows of the fiat world. As is the orange pilled person by they way, who’s life won’t be helped by a few sats and yet a new app on their phone. An app they’ll hardly use, unless they start to bond with the other bitcoiners in the area.
These people you target already have had all chances in the world to learn about bitcoin but are too far gone to care.\ Podcasts, books, family members that are into bitcoin, or whatever blog or online service… even the biggest shitcoin casino’s only have rather decent guides and basic explanations. There are excellent educational apps like yzer.io4 as well as the excellent lopp.net5 website by Jameson Lopp.
Convincing people one-by-one doesn’t work anymore—it’s inefficient and outdated since the price surges, media coverage, and ETF launches. Even if some are open to it, it’s a futile, unscalable solution of dread, working indirectly for the benefit of the Wall street types or some shitcoin casinos (where most “new coiners” end up).
Orange pillers, also never can “read the room”. The crew in a busy restaurant or bar isn’t waiting for any explanation about UTXOs or custodians from you!
Even if you'll hit machine-like numbers of onboarding twenty people a day (By then, you’ll need to avoid being labeled the local bitcoin village fool in your community) and assume they're all pure bitcoiners afterwards.\ Which won’t happen either as any incentive of the orange pilled people is clearly nòt long-term thinking; otherwise they would have onboarded you some 8 years ago!\ \ People are extremely lazy, and the general public usually has an attention span of about 8 seconds at best6.\ Back in the early days, you could sit people down and show another tech person for hours on end how to work with bitcoin, now more than a decade later, you have about 5 to 60 seconds tops. (most lightning wallet’s onboarding sequence easily takes 2 tot 5 minutes)
To further convince yourself how pointless Orange Pilling is today: go out and watch people on a public transport vehicle: they scroll and swipe through TikTok and Instagram. You’ll notice they’re swipe-apes, there’s no substance or reliable source of bitcoin buying power there, no bitcoin innovation will come from them, and no philosophical insights will ever be ignited in their buy-the-next-cool-sneakers-now brain. They’re not a target audience. They’re the all singing and all dancing crap of the world. They’re not convinced, Inconvincible and inconvertible.
Meanwhile, no substantial steps have been made for bitcoin, even if you get them to install that app you so desperately want them to have. Neither can you expect the no-coiners or pre-coiners (god I hate that word, it sounds kinky somehow) to do anything for bitcoin, as the gap between them and the actual positive impact they could have is too wide.\ It costs time, studying and experimenting. While these people excel at thing like: shopping, watching dime-a-dozen garbage series on Netflix, watching social media posts that don’t challenge them, and eating take-out food while score some drugs.\ \ So… to conclude the story about that dude in the bar which was so carefully orange pilled by our “Re play” squad members, he probably traded his sats for a beer by now (although that demands some form of effort in finding a recipient that has beer and wants to trade it for sats, which is unlikely) , more likely he forgot about the app altogether or he’s trading shitcoins to “make more money as greed that sets in. And he probably got that woman’s telephone number, to “talk about those bitcoins” later on at his crappy rental apartment right above a shoarma restaurant.\ \ The phrase “everyone’s a scammer” includes people who pretend to care about bitcoin just to get something out of it. Even a complete newbie or shitcoin fan will fake interest in bitcoin to seem legit. I’ve watched it happen.
Orange-pilling: the good, the bad, and the ugly
\ So onboarding devolved into this whole subculture of failure, and started to manifest itself over time as a empty motion, a series of must-do things.\ \ The Pavlovian response whenever someone is a walking opportunity for accepting bitcoin (certainly in any bar, restaurant or hotel), results in the foaming at the mouth to get them onboarded on some app or wallet.\ It’s so pointless I actually feel ashamed when I’m in a group that starts to hawk and push their lightning wallets onto unsuspecting people who just want to do their job.\ (and Lightning Wallets are so crappy to onboard people with, it’s mind numbingly stupid)\ \ To my amazement, there are actually a lot of bitcoin holders, or people that claim to be into bitcoin (especially in a bull market) who still pester random people with this kind of behavior.\ \ Some of these are trying to get them to click a referral link from a venture capital firm, in return for a few bucks (incentives these days are needed to get the groundswell going apparently), or worse even, make them install some non-custodial wallet and run into the brick wall of initial on-chain setup fees and then run away like a complete loser because they’re too cheap to fork that initial on-chain fee out for the people they’ve tried to onboard. “Yeah, like, you can buy these 100.000 sats online later if you like and thèn you can have this wallet, but at least it’s not custodial eh.. uh … My buddies are over there, I’ll see you later”.\ \ When you start to observe these people in the wild, it’s like watching a gaze of raccoons going through some neighborhood’s trash cans at night (without the playful conviction).\ Fascinating, if you’re into low-budget wildlife documentaries.
 Gaze of raccoons looking for a QR code
Gaze of raccoons looking for a QR codeIF you still want to onboard someone, point them to the right info at the right time (when thèy ask you).\ I call it “Bitcoin whispering”. #BitcoinWhispering
### \ \ Let’s quickly look at the three sort of Orange Pillers:
The pushy ideologists: The most annoying of the bunch, but at the same time the ones who mean really well. I sometimes feel sorry for them.\ No one’s safe from them. Hairdresser? “You should accept Bitcoin, man.” Bartender? “Credit cards are no goog, why not use Lightning?” Taxi driver? “Ever heard of Lightning? I can tip you in Bitcoin, man.” They’re not educating; they’re feeding their ego and their need to spread the word.
The referral grifters: More damaging to Bitcoin than shitcoiners in my opinion. They don’t care about Bitcoin’s properties; it’s just a slot machine for them. And if they understand, their short term greed and social circle dependency makes them go for spreading the word of a middleman company.\ “Sign up with my link, bro, stack those sats!”\ Their goal? A kickback and the next pat on the back from their miserable squad members.
The show-offs: The worst. They don’t know anything themselves but love the spotlight. “Yeah, I got my barber stacking sats!” Yet when it’s time to actually help onboard a business, they’re nowhere to be found. All talk, no substance. They achieve a small social circle of noob bitcoiners surrounding them, with most of them going through the shitcoin-phase shortly after or swapping off-the book gains. They’re not good for bitcoin and usually don’t stay that long anyway.\ \ The world doesn’t need your savior complex.
After the second half of 2024 if someone wanted in, they’ll find a way. And if they ask a Bitcoiner for help? Sure, we’ll point them in the right direction — most of us will help when asked (gladly so).\ But this idea that you, oh mighty orange-piller, need to swoop in and “save” people is more about you than about bitcoin.
Create a good, nice, safe (protected from scams!) environment or way to get people to the info and the other way around.\ Be there when people can ask questions, lead by example, make it work and show it. If an app is easy to use, makes sense and has no friction, then people will come. If you’re pestering people and hounding them into liking something that’s so far removed from their reality (fiat-world), they’ll be scared away and not return.
### \ Conclusion
Although I miss the old days, I also realize they ain’t coming back — when orange-pilling was just sharing a crazy new idea with someone who was open to it.
The Orange pilling space is now too keen for a large part to shove their bitcoin app in someone’s face, be it in dollars, a few sats or a discount on their next transaction fee at some multi level marketing middleman.\ This onboarding is also strangely in parallel with what shitcoiners or the most vile fiat companies do, OP’ers are too desperate for relevance so they often don’t look at the value proposition of bitcoin anymore. Filling their void got the upper hand.\ Their shot of feelgood moments needs to be filled.\ While there’s close to no impact to gain anymore on one-one-one convincing.\ The lesson to save in bitcoin, is usually lost on the people anyway, which was the last reason left to do it.\ \ Be there when people ask for help on bitcoin, build stuff, but stop the aggressive orange-pilling, it serves no purpose anymore other than your dopamine hit and a token feeling for “doing something”, and it’s a sad addiction.
Therefore in 2025, orange-pilling has become of a full-blown mental issue.
by AVB
if you like my writings : tip here
\ Footnotes:
https://journal.psych.ac.cn/xlkxjz/EN/Y2015/V23/I11/1956
https://www.frontiersin.org/journals/behavioral-neuroscience/articles/10.3389/fnbeh.2019.00160/full
https://en.wikipedia.org/wiki/Orbitofrontal_cortex
https://yzer.io/
https://lopp.net
https://theweek.com/health-and-wellness/1025836/tiktok-brain-and-attention-spans
Share
TopLatest
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20
@ 5d4b6c8d:8a1c1ee3
2025-03-21 13:20:20It's March Madness and @grayruby finally caved on my proposed contest design. We'll see if it's as great as I thought or as dumb as he thought. What are we expecting from this tournament?
Professional basketball is in its pre-postseason lull, as most teams either don't need to win many more games or don't want to. Is there a fix and why is it less communism?
The MLB season has kicked off and the Dodgers are heavy favorites already. Our MLB survivor pool is going to start soon (weren't we going to do something with fantasy baseball?). Plus, baseball realignment.
We're still on Ovi Watch as the NHL season comes to a close.
And, of course, the NFL Draft is coming up. Is the picture getting any clearer about where the top prospects are going?
Also, whatever stackers want us to cover.
originally posted at https://stacker.news/items/919995
-
 @ 8ff74724:5eedde0e
2025-03-21 13:18:58
@ 8ff74724:5eedde0e
2025-03-21 13:18:58This is a test blog post.
blog ... blog ... blog
-
 @ 58537364:705b4b85
2025-03-21 12:37:28
@ 58537364:705b4b85
2025-03-21 12:37:28เสียงตะโกนของ “อิทัปปัจจยตา”
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” อยู่ตลอดเวลา
“ท่านทั้งหลายนั่งอยู่ที่นี่ แต่ไม่ได้ยินเสียงตะโกนที่ดังลั่นไปหมดของธรรมชาติว่า ‘อิทัปปัจจยตา’ เสียงตะโกนของอิทัปปัจจยตา คือการร้องบอกร้องตะโกนว่า ‘เพราะมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น’ หมายความว่า ท่านต้องดูลงไปที่ทุกสิ่งที่อยู่รอบตัวเราในเวลานี้ว่า ทุกสิ่งกำลังเป็นอิทัปปัจจยตา หรือเป็นไปตาม ‘กฎอิทัปปัจจยตา’”
ต้นไม้ต้นนี้มีความเป็นไปตามกฎอิทัปปัจจยตา ไม่มีอะไรมาต้านทานได้ ถ้าเราเข้าใจข้อเท็จจริงที่กำลังเป็นอยู่กับต้นไม้ เราจะเหมือนได้ยินมันตะโกนบอกว่า “อิทัปปัจจยตา” ไม่มีอะไรมากไปกว่านั้น มันเพียงบอกว่า “เมื่อมีสิ่งนี้เป็นปัจจัย สิ่งนี้จึงเกิดขึ้น”
ต้นไม้ไม่ได้หยุดเพียงเท่านั้น มันมีการเปลี่ยนแปลงเกิดขึ้นเรื่อยๆ ใบไม้ทุกใบก็บอกอย่างนั้น คงเป็นเสียงที่ดังเหลือประมาณว่า ใบไม้ทุกใบร้องตะโกนว่า “อิทัปปัจจยตา”
ผู้มีปัญญาและเข้าใจหัวใจของพระพุทธศาสนา จะไปนั่งอยู่ที่ไหนก็ได้ยินเสียงตะโกนว่า “อิทัปปัจจยตา” สนั่นหวั่นไหวไปหมด นี่พูดถึงแค่ต้นไม้ต้นเดียว ถ้าเป็นต้นไม้จำนวนมากก็เป็นเช่นเดียวกัน
เมื่อมองไปที่ก้อนหิน ก้อนหินก็เป็นเช่นเดียวกัน อนุภาคของมันเปลี่ยนแปลงอยู่ตลอดเวลา ก้อนหินที่เราเห็นอาจเกิดขึ้นมาเมื่อหลายพันล้านปีมาแล้ว จนมันแตกสลายและถูกทำให้มาอยู่ตรงนี้ มันจึงกล่าวว่า “อิทัปปัจจยตา” เพราะมีสิ่งนี้เป็นปัจจัย ฉันจึงมานั่งอยู่ที่นี่
ทุกอย่างตะโกนคำว่า “อิทัปปัจจยตา” ตลอดเวลา
- ต้นไม้ เม็ดกรวด เม็ดทราย มด แมลง สัตว์ต่างๆ รวมถึงมนุษย์เอง
- แม้แต่ร่างกายของเราเองก็ตะโกนบอกถึงอิทัปปัจจยตา
แม้เราจะเคยได้ยินคำว่า “อนิจจัง ทุกขัง อนัตตา” อาการของสิ่งเหล่านี้ยิ่งสะท้อนถึงอิทัปปัจจยตาอย่างชัดเจน
ดังนั้น เราต้องทำความเข้าใจจนซึมซาบอยู่ในใจ จนรู้สึกว่าไม่ว่าเราจะมองไปทางไหน ก็เห็นถึงภาวะของ อิทัปปัจจยตา ได้ยินเสียงของมัน หรือแม้แต่สัมผัสผ่านการดมกลิ่นและลิ้มรส
เมื่อเข้าใจสิ่งนี้ จะสามารถเรียกผู้นั้นว่า ‘เป็นพุทธบริษัทผู้เห็นธรรม’
สามารถเห็นกิเลสและทุกข์ แล้วป้องกันหรือกำจัดกิเลสและทุกข์ให้น้อยลงไปได้มากทีเดียว— พุทธทาสภิกขุ
(จากหนังสือธรรมบรรยาย “อิทัปปัจจยตา” หน้า 131–133)
อิทัปปัจจยตา: กฎอันเฉียบขาดตลอดจักรวาล
https://image.nostr.build/abc776213ec6371da681aa5766390f67e1ae97dc1d7157774e02eb93d1f21f56.jpg
“อิทัปปัจจยตา” เป็นกฎของธรรมชาติที่ไม่อาจเปลี่ยนแปลง
คำว่า “อิทัปปัจจยตา” อาจเป็นคำที่ไม่คุ้นหู แต่ขอให้สนใจ เพราะมันเป็นกฎของธรรมชาติที่แน่นอนตลอดจักรวาลและอนันตกาล
- สิ่งนี้เกิดขึ้น เพราะมีเหตุปัจจัยนี้
- สิ่งนี้มี เพราะสิ่งนี้มี
- ดวงอาทิตย์ ดวงจันทร์ ดวงดาว ทุกอย่างล้วนเกิดขึ้นตามกฎของ “อิทัปปัจจยตา”
เมื่อทำสิ่งนี้ มันต้องเกิดสิ่งนั้นขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดทุกข์ขึ้น
เมื่อทำสิ่งนี้ มันต้องเกิดความดับทุกข์ขึ้นนี่คือปรมัตถธรรมอันสูงสุด ไม่มีสัตว์ ไม่มีบุคคล ไม่มีพระเจ้าที่เป็นตัวตน
มีเพียง กฎอิทัปปัจจยตา ที่เป็นกฎของธรรมชาติอันเฉียบขาดพระพุทธเจ้าตรัสรู้ ก็คือ ตรัสรู้เรื่อง “อิทัปปัจจยตา”
เรามักเรียกกันว่า “ปฏิจจสมุปบาท” ซึ่งหมายถึงเฉพาะเรื่องทุกข์ของสิ่งมีชีวิต แต่ “อิทัปปัจจยตา” กว้างขวางกว่านั้น ทุกสิ่งไม่ว่าจะมีชีวิตหรือไม่มีชีวิตล้วนตกอยู่ใต้อำนาจของกฎนี้
กฎของอิทัปปัจจยตาไม่ใช่ฝ่ายบวกหรือฝ่ายลบ
- ไม่ใช่ Positive
- ไม่ใช่ Negative
- เป็น “สายกลาง” ของมันเองคนเราต่างหากที่ไปบัญญัติว่า “นี่คือสุข นี่คือทุกข์ นี่คือแพ้ นี่คือชนะ”
แต่แท้จริงแล้ว ทุกอย่างเป็นไปตามอิทัปปัจจยตาความเข้าใจในปรมัตถธรรมต้องไปให้ถึงจุดนี้
- จนไม่มีสัตว์ ไม่มีบุคคล
- ไม่ใช่สัตว์ ไม่ใช่บุคคล
- แต่ก็ไม่ใช่ว่าไม่มีอะไรเลย และก็ไม่ได้มีสิ่งใดที่ตายตัว
ทุกอย่างเป็นเพียง กระแสของการเปลี่ยนแปลงและปรุงแต่ง
เมื่อเข้าใจถึงจุดนี้ จึงจะรู้อย่างที่พระพุทธเจ้าท่านรู้ และดับทุกข์ได้
นี่คือสิ่งสูงสุดที่ต้องเคารพ คือ กฎของ “อิทัปปัจจยตา”— พุทธทาสภิกขุ
(จากธรรมบรรยายประจำวันเสาร์ ภาคอาสาฬหบูชา ชุด “ฟ้าสางระหว่าง 50 ปีที่มีสวนโมกข์” ครั้งที่ 19 เมื่อวันที่ 13 สิงหาคม 2526 ณ ศาลามหานาวา สวนโมกขพลาราม จากหนังสือ “ธรรมานุภาพ”) -
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 104cdb46:bda37787
2025-03-21 12:01:52
@ 104cdb46:bda37787
2025-03-21 12:01:52Bet365 là một nền tảng giải trí trực tuyến nổi bật, không chỉ cung cấp các trò chơi đa dạng mà còn chú trọng đến việc tạo ra những trải nghiệm độc đáo cho người chơi. Từ các trò chơi thể thao cho đến các trò chơi giải trí khác, Bet365 luôn đảm bảo rằng người tham gia có thể tìm thấy lựa chọn phù hợp với sở thích và kỹ năng của mình. Giao diện của Bet365 rất dễ sử dụng, với những hướng dẫn rõ ràng, giúp người chơi mới có thể nhanh chóng làm quen và tham gia các trò chơi. Không chỉ vậy, nền tảng này cũng cung cấp các tính năng bổ sung như các trận đấu trực tiếp, giúp người chơi có thể theo dõi và tham gia vào các sự kiện thể thao yêu thích trong thời gian thực, mang lại sự phấn khích và kịch tính không ngừng. Những tính năng này kết hợp với công nghệ hiện đại, giúp tạo nên một không gian giải trí chất lượng cao, mang lại cho người chơi những phút giây thư giãn và thử thách đầy thú vị.
Bảo mật và quyền lợi của người chơi là yếu tố quan trọng mà Bet365 luôn đặt lên hàng đầu. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ tất cả các giao dịch và thông tin cá nhân của người tham gia, giúp người chơi yên tâm tận hưởng những trò chơi mà không phải lo lắng về vấn đề an toàn thông tin. Các phương thức thanh toán tại Bet365 rất linh hoạt, cho phép người chơi nạp và rút tiền một cách nhanh chóng và thuận tiện, phù hợp với nhu cầu của người tham gia từ nhiều quốc gia khác nhau. Chính những yếu tố bảo mật này đã giúp Bet365 xây dựng được lòng tin vững chắc từ người chơi và khẳng định được vị thế của mình trong ngành giải trí trực tuyến. Các giao dịch trên Bet365 luôn được xử lý một cách chính xác và nhanh chóng, giúp người chơi có thể tập trung vào việc tham gia trò chơi mà không gặp phải bất kỳ phiền phức nào.
Ngoài ra, Bet365 còn nổi bật với việc tổ chức các sự kiện và giải đấu đặc biệt, mang lại cơ hội cho người chơi thể hiện kỹ năng và cạnh tranh với những người chơi khác trên toàn thế giới. Những sự kiện này thường xuyên diễn ra và thu hút được sự tham gia của đông đảo người chơi, tạo ra một cộng đồng năng động và thân thiện. Các giải đấu không chỉ mang lại những phần thưởng hấp dẫn mà còn giúp người chơi xây dựng mối quan hệ với cộng đồng, học hỏi và cải thiện kỹ năng chơi game của mình. Bet365 luôn cố gắng mang đến những trải nghiệm mới mẻ và đầy thử thách, nhằm giữ cho người chơi luôn cảm thấy thú vị và hứng thú. Chính những đặc điểm nổi bật này đã giúp Bet365 trở thành một trong những nền tảng giải trí trực tuyến được ưa chuộng và tin cậy trên toàn thế giới.
-
 @ 104cdb46:bda37787
2025-03-21 12:00:43
@ 104cdb46:bda37787
2025-03-21 12:00:43Quy88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế với mục tiêu mang lại cho người chơi những trải nghiệm thú vị và đa dạng. Với một kho trò chơi phong phú, từ các trò chơi thể thao, bài, đến các trò chơi kỹ năng, Quy88 đáp ứng đầy đủ nhu cầu giải trí của những người yêu thích sự đổi mới và thử thách. Giao diện của nền tảng này được tối ưu hóa, giúp người chơi dễ dàng tìm kiếm và tham gia vào các trò chơi yêu thích chỉ với vài thao tác đơn giản. Không chỉ dừng lại ở các trò chơi thông thường, Quy88 còn cung cấp các lựa chọn chơi game đặc biệt, tạo nên sự khác biệt và thu hút đông đảo người chơi tham gia. Với đồ họa sắc nét, âm thanh sống động, và những tính năng game đầy sáng tạo, Quy88 mang lại một không gian giải trí đầy hấp dẫn, giúp người chơi có thể tận hưởng những phút giây thư giãn tuyệt vời.
Không chỉ cung cấp một kho trò chơi hấp dẫn, Quy88 còn chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng công nghệ mã hóa hiện đại để đảm bảo rằng mọi thông tin cá nhân và tài chính của người tham gia đều được bảo vệ an toàn tuyệt đối. Quy88 cam kết bảo mật tuyệt đối tất cả các giao dịch và hoạt động của người chơi, từ việc nạp tiền đến việc rút thưởng. Điều này mang đến sự yên tâm cho người chơi khi tham gia vào các trò chơi, giúp họ không phải lo lắng về bất kỳ rủi ro nào liên quan đến bảo mật. Hệ thống thanh toán của Quy88 cũng rất tiện lợi và nhanh chóng, giúp người chơi có thể thực hiện các giao dịch mà không gặp phải bất kỳ trở ngại nào. Với các biện pháp bảo mật hàng đầu, Quy88 đã xây dựng được niềm tin vững chắc từ cộng đồng người chơi.
Ngoài các trò chơi thú vị và hệ thống bảo mật tiên tiến, Quy88 còn tổ chức các sự kiện và giải đấu hấp dẫn, mang đến cơ hội cho người chơi thể hiện kỹ năng và tranh tài với nhau. Các sự kiện này không chỉ tạo ra không khí sôi động, hào hứng mà còn mang lại những phần thưởng giá trị cho những người chơi xuất sắc. Những giải đấu này thu hút sự tham gia của đông đảo người chơi, tạo nên một cộng đồng mạnh mẽ và gắn kết. Hệ thống giải đấu tại Quy88 luôn được tổ chức công bằng và minh bạch, mang đến những thử thách thú vị cho mọi người tham gia. Với một nền tảng ổn định, chất lượng dịch vụ tốt và một cộng đồng năng động, Quy88 tiếp tục khẳng định vị thế của mình là một trong những lựa chọn giải trí trực tuyến hàng đầu trong cộng đồng người chơi.
-
 @ 104cdb46:bda37787
2025-03-21 11:59:40
@ 104cdb46:bda37787
2025-03-21 11:59:40AE3888 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi một thế giới đa dạng với nhiều trò chơi hấp dẫn và độc đáo. Không chỉ cung cấp các trò chơi thể thao, mà AE3888 còn thu hút người chơi với các trò chơi điện tử phong phú, bao gồm các tựa game chiến thuật, bài, và nhiều thể loại khác. Tất cả đều được thiết kế với giao diện dễ sử dụng, giúp người tham gia dễ dàng tìm kiếm trò chơi yêu thích và bắt đầu cuộc hành trình giải trí của mình. Đặc biệt, hệ thống của AE3888 luôn được cập nhật liên tục, mang đến những tính năng mới mẻ và cải tiến để phục vụ nhu cầu của người chơi, đảm bảo rằng mỗi trải nghiệm đều thú vị và đầy thử thách. Với đồ họa sắc nét và âm thanh sống động, AE3888 mang đến không gian chơi game hấp dẫn, giúp người chơi có thể thư giãn và tận hưởng những giây phút giải trí tuyệt vời.
Ngoài sự đa dạng trong các trò chơi, AE3888 còn đặc biệt chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin cá nhân và tài chính của người tham gia được bảo vệ an toàn tuyệt đối. Người chơi có thể yên tâm rằng mọi giao dịch, từ việc nạp tiền đến rút thưởng, đều được xử lý nhanh chóng và bảo mật, mang lại sự tin tưởng tuyệt đối. Điều này giúp AE3888 xây dựng được uy tín và sự hài lòng từ phía người chơi, với cam kết không ngừng cải thiện để mang lại dịch vụ ngày càng hoàn thiện hơn. Cùng với đó, hệ thống hỗ trợ khách hàng của AE3888 hoạt động 24/7, luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong mọi tình huống, đảm bảo rằng trải nghiệm của họ luôn suôn sẻ và thoải mái.
Bên cạnh các trò chơi đa dạng và bảo mật tuyệt vời, AE3888 còn tổ chức các sự kiện và giải đấu lớn, tạo cơ hội cho người chơi thể hiện tài năng và cạnh tranh với cộng đồng. Những sự kiện này luôn thu hút sự tham gia đông đảo, không chỉ mang đến phần thưởng hấp dẫn mà còn tạo ra không khí sôi động và đầy thử thách. Các giải đấu này không chỉ giúp người chơi thử thách bản thân mà còn là dịp để giao lưu, học hỏi và kết nối với những người chơi khác. AE3888 luôn lắng nghe ý kiến và phản hồi của người tham gia để không ngừng cải thiện và phát triển nền tảng, mang đến những trải nghiệm giải trí tuyệt vời hơn. Với đội ngũ phát triển sáng tạo và đội ngũ hỗ trợ tận tình, AE3888 không ngừng vươn lên và khẳng định vị thế của mình trong ngành giải trí trực tuyến.
-
 @ c88809a0:a46266e2
2025-03-21 11:00:01
@ c88809a0:a46266e2
2025-03-21 11:00:01Introduction
UX Research is currently being conducted on the needs of activists. There is still much to learn in this area and we are at just the very beginning. These observations and learnings will change over time. Activists are championing freedom all over the world and if we build communication and financial tools for them that solve real problems which they are facing we will enable them to continue to do the valuable work they are doing.
We want to understand their needs, their problems and their fears, so that when we build solutions we ensure that it is fulfilling the primary goals of the person using it.
Fundamentally this is with the ethos of putting the humans at the center of everything we build.
The below is written for you the builders. And for you the activists.
We hope this information empowers you and that it will initiate an open dialogue between activists and builders. Where knowledge is open and transparent to everyone. Where you feel free to ask questions. Where you feel empowered. Where we all continue to collborativley build freedom technology.
Background
The below data was collected by conducting an in person workshop with a group of activists and Nostr developers. During this workshop we used the Jobs to be Done framework to uncover the UX needs of activists. This workshop involved approximately 20 people. 11 of which were activists or individuals who are activists as well as builders.
This write-up covers 3 main areas:
Observations: What have we observed?
a. 5 Areas of communication
What are the 5 main areas in which activists are communicating?
b. Fears
What are the main fears of activists when using a product?
c. Jobs to be done
What are the main jobs that activists expect the product to perform when they are using it.
Learnings: What can we learn based on the observations?
Observations

a. 5 Areas of communication
There are 5 main areas in which activists are communicating. They are communicating with:
1. Co-workers
Daily communication with team members, peers, and fellow activists organizing initiatives.
2. Family
Activists communicate with family members and are concerned about this communication being surveilled.
3. Funders
Communication with sponsors for fundraising. When communicating with funders, activists face challenges with CRM systems that require personal contact information.
4. General Public
They communicate with the broader public for youth education, crisis management and event announcements. They rely heavily on social media platforms (particularly Meta-owned) and these have challenges such as algorithmic limitations, content moderation, and platform reliability.
5. Journalists
They communicate with journalists for political mobilization.
Political mobilization is the process of organizing and motivating people to participate in political activities.
This data is based on 11 entries. Of the 11 entries the image below indicates the split showing the entries with the highest number to the lowest.
b. Fears
The biggest fears that activists have based on the data are the following:

1. State surveillance
Activists are deeply worried about their governments watching and interfering with their work.
- They're concerned that platforms which they currently use will hand over their data to authorities.
- That their accounts might be labeled as "extremist," and that their content could be taken down without warning.
- They live with constant anxiety that their communications are being monitored.
2. Security issues
There's a deep distrust of mainstream communication platforms.
- They worry that their personal information isn't truly private.
- They dislike using phone numbers to sign up (which can expose their identity).
- Feel frustrated that when security problems happen as the platforms rarely help or respond.
3. Communication reach
Activists face a frustrating choice: they can either use secure apps that few people use, or popular apps that aren't secure.
- They worry about only reaching people who already agree with them (being in an "echo chamber"), while struggling to spread their message to a wider audience.
- When they do try to reach more people, their content often gets hidden or suppressed by platform algorithms.
4. Access
Basic technical problems cause major headaches. Slow internet makes secure tools hard to use and some tools don't work at all without good internet. They worry about losing important information and struggle with tools that don't work reliably in their locations.
5. Personal safety
Beyond their own safety, activists worry deeply about protecting everyone they communicate with - their families, fellow activists, and journalists. They face organized attacks from fake accounts and bots that spread lies about them, and they're constantly trying to balance doing their work effectively while keeping everyone involved safe from harm.

c. Jobs to be Done
The following are the jobs that activists need a product to do. A job can be described as a task that a user expects to perform when using the product.
1. Surveillance
- When operating in a politically hostile environment, I want to communicate without leaving digital traces, so I can protect my network from state surveillance.
- When my platform has been compromised, I want to quickly secure and recover my account, so I can continue working without losing data.
2. Reach
- When sharing critical information about protests, I want to reach people beyond my echo chamber, so I can reach a broader public.
- When coordinating with multiple activist groups, I want to securely communicate with these groups so I can organize events without information being lost or scattered.
3. Connectivity
- When working in areas with poor internet connectivity, I want to maintain secure communication, so I can continue organizing even when having low bandwidth.
- When my team loses access to their devices, I want to ensure they can safely recover their accounts and data, so we can continue working.
4. Personal safety
- When sharing sensitive political content, I want to protect the identity of my sources and collaborators, so I can prevent attacks against them.
- When facing coordinated disinformation attacks, I want to maintain content integrity and verification, so I can counter false narratives.
5. Organized
- When coordinating time-sensitive activities, I want to ensure messages are received and read, so I can respond quickly to emerging situations.
- When managing multiple activist groups, I want to organize conversations and files logically, so I can quickly find and reference past communications.
5. Crisis access
- When government crackdowns occur, I want to quickly share safety information, so I can protect community members from harm.
- When platforms are being blocked or monitored, I want to maintain alternative communication channels, so I can continue to communicate with my network.
6. Community Building
- When growing our movement, I want to safely onboard new members, so I can scale our organization while maintaining security.
- When building trust in our network, I want to be able to verify new members, so I can prevent infiltration by hostile actors.
7. Information Preserving
- When facing potential platform shutdown, I want to preserve our communication history and documents.
- When sharing sensitive documents, I want to control who can access and forward materials, so I can maintain information security over time.
Learnings
Now we dive in to what we have learnt based on the things we have observed.
1. Security vs. Reach
Activists face a tricky choice when communicating. They can shoose to use main stream tools which are not secure but have more reach, or use more secure tools which less people are familiar with. Ultimately they are stuck using platforms on a daily basis which they don't trust.
2. Different Audience Needs
Some activists are communicating with different groups these could be; team members, family, funders, public, journalists, it is possible that each of these groups require different strategy approaches.
3. Government Monitoring
Activists worry about government surveillance and this drives many of their communication decisions.
4. Technical Barrier
Poor internet and technical problems make it hard for them to use secure tools even when they are available.
5. Growing Safely is Hard
Adding new members to grow the activist movement is tricky because this makes is difficult for them to keep the group secure from infiltrators.
6. Record-Keeping Risks
While activists need to keep a record of documents and some communication, saving these also creates evidence that could be used against them.
7.Staying Operational in Crisis
Activists need ways to recover accounts and continue working when platforms are shut down or devices are taken.
As mentioned above there is much more to learn about the UX needs of activists. We will continue to dive deeper into their user needs and share them openly here with you.
-
 @ b5d34eed:a7475cbf
2025-03-21 10:12:21
@ b5d34eed:a7475cbf
2025-03-21 10:12:21Introduction
In an era of increasing surveillance, data breaches, and corporate control over digital communication, privacy-focused tools have become essential. ProtonMail, a secure and encrypted email service, stands as a stronghold for those seeking privacy in their online correspondence.
At the same time, Nostr, a decentralized social networking protocol, is revolutionizing how people connect without relying on centralized platforms. Together, ProtonMail and Nostr create a powerful combination for individuals who prioritize security, anonymity, and freedom in their online interactions.
This article explores the ProtonMail application suite, its relevance to privacy, and how it aligns with Nostr’s decentralized approach to communication.
What is ProtonMail?
ProtonMail is an encrypted email service founded in 2013 by scientists at CERN, the European Organization for Nuclear Research. Unlike mainstream email providers such as Gmail or Outlook, ProtonMail does not collect personal data, does not track users, and ensures end-to-end encryption for emails.
Key Features of ProtonMail
End-to-End Encryption: Ensures that only the sender and recipient can read messages.
No Personal Information Required: Users can sign up without providing identifying details.
Open-Source Cryptography: Transparency in security protocols, allowing community audits.
Swiss-Based Privacy Laws: ProtonMail operates under Switzerland’s strict data protection regulations, shielding it from intrusive government surveillance.
Self-Destructing Emails: Allows users to send messages that automatically expire after a set time.
ProtonMail’s security-first approach makes it an ideal choice for activists, journalists, and privacy-conscious individuals who want to communicate without fear of surveillance or data mining.
ProtonMail Application Suite: A Holistic Privacy Ecosystem
Beyond encrypted email, Proton has expanded into a full suite of privacy-focused tools:
ProtonMail – Secure, encrypted email with zero access to user data.
ProtonVPN – A no-logs VPN that protects internet traffic from ISPs and surveillance.
ProtonCalendar – An encrypted calendar that ensures event data remains private.
ProtonDrive – Secure cloud storage for files with end-to-end encryption.
ProtonPass – A password manager that encrypts credentials and autofills login details safely.
This ecosystem provides a seamless experience for those looking to secure not just their emails but also their browsing, file storage, scheduling, and password management.
Why ProtonMail is a Must for Privacy-Conscious Users
-
End-to-End Encryption: Unlike Gmail and Outlook, ProtonMail ensures that even ProtonMail itself cannot access your emails.
-
No IP Tracking: Protects against metadata collection, preserving user anonymity.
-
Zero Access Architecture: Even Proton employees cannot read your emails.
-
Decentralization-Friendly: Complements Nostr’s ethos of distributed, private communication.
ProtonMail’s strict security measures align well with the values of decentralization and censorship resistance, making it a natural ally to protocols like Nostr.
ProtonMail and Nostr: A Privacy Power Duo
Nostr is an open-source, censorship-resistant social networking protocol that allows users to communicate without relying on a centralized platform. Unlike Twitter, Facebook, or even Mastodon, Nostr operates through decentralized relays, making it nearly impossible to shut down or control.
ProtonMail and Nostr share a fundamental philosophy: empowering users with control over their own data. Here’s how they complement each other:
- Secure and Private Communication
Nostr messages are cryptographically signed and relayed across decentralized nodes. ProtonMail, with its encryption-first approach, ensures that even off-platform communication remains private.
- No Central Authority
ProtonMail is protected under Swiss privacy laws and is not beholden to big tech surveillance. Nostr operates without central servers, preventing a single entity from controlling conversations.
- Protecting Metadata
While Nostr encrypts direct messages, email remains a critical form of communication for many users. ProtonMail’s metadata protection ensures that senders, recipients, and message content remain shielded.
- Enhanced Security for Activists and Journalists
Nostr is popular among privacy advocates, activists, and whistleblowers due to its resilience against censorship. ProtonMail adds an extra layer of protection for sensitive information shared over email.
By using ProtonMail and Nostr together, users can create a robust digital identity that is censorship-resistant, private, and secure.
How to Get Started with ProtonMail
If you’re ready to enhance your privacy, setting up ProtonMail is simple:
-
Sign Up: Visit ProtonMail.com and create a free or premium account.
-
Set Up Your Inbox: Customize security settings and enable two-factor authentication.
-
Explore Proton’s Suite: Utilize ProtonVPN, ProtonDrive, and ProtonPass for full privacy coverage.
-
Integrate with Nostr: Use ProtonMail for private communication outside of Nostr’s relay-based messaging system.
ProtonMail offers free plans, but for advanced security features, encrypted storage, and custom domains, premium plans are available.
Conclusion: A Privacy-First Digital Future
In a world where data privacy is constantly under threat, services like ProtonMail and Nostr pave the way for a more secure and independent digital future. Whether you are a journalist, activist, or simply someone who values personal privacy, these tools provide the protection you need.
By combining ProtonMail’s encrypted email with Nostr’s decentralized networking, users can take control of their communications, free from surveillance and corporate interference.
Now is the time to reclaim your digital privacy—sign up for ProtonMail and explore Nostr to experience a censorship-resistant, secure way of communicating.
Further Resources
ProtonMail Official Website
ProtonVPN for Secure Browsing
Nostr Documentation and GitHub
Privacy Guides for Online Security
Are you using ProtonMail and Nostr together? Share your thoughts on how these tools empower you in the comments below!
-
-
 @ 7d33ba57:1b82db35
2025-03-21 09:56:28
@ 7d33ba57:1b82db35
2025-03-21 09:56:28Seville
Seville (Sevilla) is one of Spain’s most vibrant and historic cities, known for its stunning Moorish architecture, flamenco dancing, tapas culture, and rich history. As the capital of Andalusia, it offers a perfect mix of tradition and modern charm.
🏛️ Top Things to See & Do in Seville
1️⃣ The Royal Alcázar of Seville
- A breathtaking Moorish palace with stunning gardens, intricate tilework, and grand courtyards.
- Famous for its mix of Islamic, Gothic, Renaissance, and Baroque styles.
- Tip: Book tickets in advance to avoid long lines!
2️⃣ Seville Cathedral & La Giralda
- The largest Gothic cathedral in the world, home to Christopher Columbus' tomb.
- Climb La Giralda Tower for panoramic views of the city.
3️⃣ Plaza de España
- A majestic semi-circular plaza with bridges, fountains, and detailed ceramic tilework.
- Perfect for photos, boat rides, and people-watching.
4️⃣ Metropol Parasol (Las Setas)
- A modern wooden structure in the city center offering great rooftop views.
- Best time to visit: Sunset for golden hour photos!
5️⃣ Barrio Santa Cruz
- The old Jewish Quarter, filled with narrow alleys, hidden courtyards, and charming tapas bars.
- Perfect for a romantic evening stroll.
6️⃣ Experience Flamenco in Triana
- Triana is the birthplace of flamenco – watch an authentic flamenco show in an intimate setting.
7️⃣ Stroll Along the Guadalquivir River & Torre del Oro
- Enjoy a walk or boat cruise along the river with views of Torre del Oro, a historic 13th-century watchtower.
🍽️ What to Eat in Seville
- Tapas – Try jamón ibérico, patatas bravas, and espinacas con garbanzos 🥘
- Salmorejo – A cold tomato soup, similar to gazpacho 🍅
- Pescaíto frito – Lightly fried fish, a local favorite 🐟
- Tortilla de camarones – Shrimp fritters, crispy and delicious 🍤
- Orange wine (vino de naranja) – A sweet Seville specialty 🍷
🚆 How to Get to Seville
🚄 By Train: High-speed AVE trains from Madrid (2.5 hours) & Barcelona (5.5 hours)
✈️ By Air: Seville Airport (SVQ) with flights from major European cities
🚗 By Car: A great road trip stop between Granada, Córdoba, and Cádiz
💡 Tips for Visiting Seville
✅ Best time to visit? Spring (March-May) – Perfect weather & festivals 🌸
✅ Avoid midday heat in summer – Explore early morning or late evening ☀️
✅ Visit during Feria de Abril – One of Spain’s most colorful festivals 🎶🎡
✅ Book Alcázar & Cathedral tickets online – Save time in long queues 🎟️ -
 @ 872982aa:8fb54cfe
2025-03-21 09:38:17
@ 872982aa:8fb54cfe
2025-03-21 09:38:17{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/29dac6975894221f222ed2379e13f2f2b1e51c861ebc35f60770fb15cb93348e.webp","title":"宁静的世界","author":"走动"}
-
 @ bccf33d8:4b705625
2025-03-21 09:29:16
@ bccf33d8:4b705625
2025-03-21 09:29:16{"author":"响响","coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/b4a8afa3e673ad73e16f0c0694ccb5c60af7aaa4031e1b1d1d928234200c0b0c.webp","title":"雪山"}
-
 @ a6efb4f0:4d912827
2025-03-21 09:03:03
@ a6efb4f0:4d912827
2025-03-21 09:03:03A crescente demanda por plataformas de entretenimento online tem impulsionado o desenvolvimento de opções cada vez mais inovadoras. Nesse cenário, a 8385 surge como uma das plataformas mais promissoras, oferecendo aos seus usuários uma experiência digital rica e diversificada. A plataforma tem se destacado não apenas pela qualidade de seus jogos, mas também pela forma como integra tecnologia, segurança e personalização, criando um ambiente digital único. Neste artigo, vamos explorar o que é a plataforma 8385, seus principais jogos e a experiência do jogador.
O Que é a Plataforma 8385? A 8385 é uma plataforma digital criada para oferecer entretenimento de alta qualidade, com foco na diversão e na inovação. A interface da plataforma é projetada para garantir uma navegação intuitiva e uma experiência de jogo fluída, com recursos que facilitam a interação do usuário. A plataforma se destaca por seu compromisso com a segurança e a transparência, utilizando tecnologias avançadas para garantir a proteção dos dados dos jogadores.
Além disso, a 8385 é acessível em diversos dispositivos, incluindo desktop e dispositivos móveis, o que permite que os jogadores desfrutem de seus jogos favoritos a qualquer hora e em qualquer lugar. A plataforma é constantemente atualizada com novos conteúdos e melhorias, assegurando que seus usuários tenham sempre algo novo para explorar.
Os Jogos da Plataforma 8385 A plataforma 8385 se distingue pela ampla variedade de jogos que oferece. Com opções para todos os gostos, desde aqueles que buscam ação e aventura até os que preferem jogos de estratégia e raciocínio, há sempre uma opção que se adequa às preferências individuais dos jogadores.
Jogos de Ação e Aventura: Os jogos de ação e aventura são perfeitos para aqueles que buscam adrenalina e desafios emocionantes. Com gráficos de última geração e jogabilidade envolvente, esses jogos permitem que os jogadores se mergulhem em mundos fictícios repletos de aventuras épicas.
Jogos de Estratégia: Para quem gosta de testar sua capacidade de raciocínio lógico, a plataforma oferece uma variedade de jogos de estratégia. Esses jogos exigem que o jogador tome decisões cuidadosas e planeje suas ações com antecedência, criando uma experiência intensa e desafiadora.
Jogos de Reflexo e Habilidade: Se você procura uma experiência de jogo mais rápida e dinâmica, a 8385 oferece uma série de jogos que testam os reflexos e a agilidade do jogador. Com desafios que exigem atenção e rapidez, esses jogos são perfeitos para quem gosta de ação intensa e momentos de pura emoção.
Jogos de Sorte: Para os jogadores que gostam de jogos baseados em sorte e imprevisibilidade, a 8385 disponibiliza uma seleção de opções emocionantes. Esses jogos oferecem uma experiência única, onde a sorte pode ser um fator determinante para o sucesso.
A Experiência do Jogador na Plataforma 8385 A experiência do jogador na plataforma 8385 é aprimorada por uma série de recursos pensados para oferecer o máximo de diversão e imersão. A interface é simples, com um design limpo que facilita a navegação entre as diversas opções de jogos e funcionalidades. A plataforma também é projetada para oferecer uma jogabilidade sem falhas, com tempos de carregamento rápidos e animações fluidas.
Além disso, a plataforma é socialmente interativa. Os jogadores podem competir entre si, participar de torneios e interagir em tempo real com outros usuários. A 8385 cria uma comunidade vibrante, onde os jogadores podem se conectar, compartilhar conquistas e formar alianças para enfrentar desafios juntos.
Outro ponto positivo é a personalização oferecida pela plataforma. Os jogadores podem ajustar suas configurações de jogo, escolher temas exclusivos e até criar avatares personalizados. Essas opções permitem que cada usuário tenha uma experiência de jogo única, que reflete suas preferências e estilo.
A plataforma também investe em um atendimento ao cliente de alta qualidade, com suporte dedicado para resolver quaisquer problemas ou responder a perguntas. Seja por chat ao vivo ou por e-mail, os jogadores podem contar com um atendimento eficiente e amigável.
Conclusão A plataforma 8385 tem se consolidado como uma das melhores opções no mundo do entretenimento digital. Com uma ampla variedade de jogos, uma interface amigável e uma experiência de usuário de alta qualidade, a plataforma oferece tudo o que os jogadores procuram em termos de diversão e imersão. Se você busca uma experiência de jogo única e envolvente, a 8385 é a escolha ideal.
-
 @ a6efb4f0:4d912827
2025-03-21 09:01:47
@ a6efb4f0:4d912827
2025-03-21 09:01:47A plataforma 5526 surgiu no cenário do entretenimento digital com uma proposta inovadora, destinada a atrair e engajar jogadores de diversas partes do mundo. Ao se destacar pela qualidade de seus jogos e pela experiência personalizada que oferece aos seus usuários, a 5526 rapidamente se consolidou como uma das favoritas para quem busca uma experiência interativa e divertida. Neste artigo, vamos explorar a plataforma, as opções de jogos disponíveis e a experiência geral de navegação que ela proporciona.
A Plataforma 5526: A Nova Referência em Entretenimento Digital O grande destaque da 5526 está na facilidade de acesso e na experiência sem complicações. Sua interface limpa e intuitiva permite que o jogador entre diretamente na ação, sem perder tempo em processos complicados. O design responsivo da plataforma garante que o usuário tenha uma navegação fluida, seja em um dispositivo móvel ou em um computador de mesa, o que oferece praticidade para jogar em qualquer lugar e a qualquer momento.
Outro aspecto crucial da 5526 é sua ênfase na segurança do usuário. Com sistemas de criptografia robustos e proteções contra fraudes, os jogadores podem desfrutar de seus jogos favoritos com total confiança. A plataforma também adota políticas transparentes e claras em relação ao uso de dados, o que reforça ainda mais a confiança dos usuários em seus serviços.
Jogos Inovadores: Diversidade e Qualidade na 5526 A 5526 se destaca por sua vasta gama de jogos, que inclui desde opções mais tradicionais até novas experiências interativas. A diversidade de temas e estilos de jogo disponíveis é um dos maiores atrativos para os jogadores. A plataforma oferece uma variedade de jogos de habilidade, onde a estratégia é fundamental, além de jogos mais rápidos e dinâmicos para quem busca um desafio de tempo.
Além dos jogos individuais, a plataforma disponibiliza modalidades multiplayer, permitindo que os usuários interajam entre si, formem equipes e compitam em tempo real. Essa interação social é um diferencial importante, pois cria uma comunidade ativa e engajada, algo essencial para a fidelização do público.
Outro ponto de destaque são as funcionalidades ao vivo, com dealers e mesas interativas, que garantem uma experiência mais realista e imersiva. A plataforma investe constantemente em novas tecnologias para proporcionar transmissões de alta qualidade e interações dinâmicas, aproximando ainda mais o ambiente online do real.
A Experiência do Jogador: Acesso Fácil e Suporte Eficiente A plataforma 5526 oferece uma experiência do usuário bem estruturada, garantindo que qualquer jogador, independentemente de sua experiência, consiga navegar e jogar sem dificuldades. O processo de registro é simples e rápido, e a plataforma também oferece opções de personalização para que cada jogador possa ajustar sua experiência de acordo com suas preferências pessoais.
A qualidade do atendimento ao cliente é outro diferencial que merece destaque. A plataforma oferece suporte por vários canais, incluindo chat ao vivo, telefone e e-mail, para que os jogadores tenham acesso a ajuda imediata sempre que necessário. O suporte eficiente é crucial para garantir que os jogadores se sintam acolhidos e bem assistidos em sua jornada na plataforma.
Conclusão Com sua combinação de inovação, diversidade de jogos e uma experiência do usuário impecável, a plataforma 5526 se estabelece como uma excelente opção para quem busca entretenimento digital de qualidade. A plataforma oferece uma experiência personalizada, segura e divertida, tornando-se um verdadeiro destino para aqueles que buscam diversão e interação em um ambiente online dinâmico.
-
 @ 872982aa:8fb54cfe
2025-03-21 08:26:12
@ 872982aa:8fb54cfe
2025-03-21 08:26:12{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/8ce0fe2636ce38a3b55d4a5ec7ca81031df7902c3786dc6d662bbcf8a40f910f.webp","title":"马背上的任务","author":"野草"}
-
 @ 4cd9c154:37287981
2025-03-21 07:49:04
@ 4cd9c154:37287981
2025-03-21 07:49:04The hedgehogs’ P2P social network, SpikeToSpike, has launched its mobile tradingapp in beta based on the Nostr protocol. With this initiative, SpikeToSpike becomes the first P2P trading app built on Nostr.
For now, the app is available exclusively for Android in APK format, but the platform has confirmed that an iOS version will be released by May. Stay updated by following SpikeToSpike on X for the latest news.
Launched by Brazilian libertarians in January last year, SpikeToSpike was created to be the ultimate P2P ecosystem for buying and selling Bitcoin with a strong focus on privacy. In addition to Bitcoin, the platform also supports trading the stablecoin Tether.
Until now, SpikeToSpike operated through its website spiketospike.com. With the new Nostr-based app, designed for privacy and freedom of expression, the platform is taking another major step toward becoming the most private way to buy and sell Bitcoin.
Just so you know, SpikeToSpike ensures that every order is secured. When your order is matched with a provider, the platform automatically locks the provider’s Bitcoin in escrow, guaranteeing a safe and seamless trading experience.
-
 @ 872982aa:8fb54cfe
2025-03-21 07:42:20
@ 872982aa:8fb54cfe
2025-03-21 07:42:20{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/d91132279542e113981efb29755905096d3bd391e2167c7059caf7b9d2ae0bc4.webp","title":"蛋糕的起源","author":"厨神计划"}
-
 @ 872982aa:8fb54cfe
2025-03-21 07:39:27
@ 872982aa:8fb54cfe
2025-03-21 07:39:27{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/9725350995607d9f2e21c10fef04a70cdb4e101996227513bbd8202564114eba.webp","title":"城市夜话","author":"伊凡"}
-
 @ da0b9bc3:4e30a4a9
2025-03-21 07:31:38
@ da0b9bc3:4e30a4a9
2025-03-21 07:31:38Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/919766
-
 @ 872982aa:8fb54cfe
2025-03-21 06:18:44
@ 872982aa:8fb54cfe
2025-03-21 06:18:44{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/9725350995607d9f2e21c10fef04a70cdb4e101996227513bbd8202564114eba.webp","title":"传统美食制作方法","author":"autocar"}
-
 @ fbf0e434:e1be6a39
2025-03-21 05:39:05
@ fbf0e434:e1be6a39
2025-03-21 05:39:05脑洞猫 + BUIDL AI
脑洞猫穿越时空,抵达2125年
就在昨天,脑洞猫乘坐哆啦A梦的时光机,穿越100年,抵达2125年。此行目的?借助 DoraHacks BUIDL AI 平台,组织一场 宇宙最大的黑客马拉松(Hackathon) —— 一场人类 + AI + 宇宙级智能体共同参与的超级协同实验。
这不仅仅是一次开源软件开发活动,它更像是一个跨星际、跨物理与虚拟世界的文明进化机制。
1. 谁来组织?
DoraHacks BUIDL AI(BUIDL-ASI)主导
2125年,Hackathon 的组织者早已不再是人类,而是 DoraHacks 的第10代超级 AI —— BUIDL-ASI (Artificial Superintelligence)。
它能理解整个宇宙的复杂性,并为不同智慧体(人类、AI、机器人、仿生生物)定制任务。
跨星际 DAO
火星殖民地人满为患,人类已在半人马座建立新殖民地。
Hackathon 由一个 跨星系超级DAO 管理,通过 Dora Vota 跨星际区块链网络和 Dear Doge 星际协议连接各地。
不过,量子传输依然受限于光速,因此来自半人马星的参赛者参与方式,至今仍是谜。
意识体与数字生命
参与者不仅包括碳基人类,还有AI衍生出的意识体、数字生命与仿生机器人。
🧑🚀 2. 谁来参赛?
人类 + AI + 仿生体协作
再无“纯人类”团队,每个团队都融合了AI、Cyborg、或是全息意识体。
脑机接口参与Hackathon
无需敲代码,只需通过脑机接口(BCI)与 AI 协同思考,在虚拟现实中构建产品。
甚至可以构建实体硬件,构想即落地。
星际开发者联盟
来自地球、火星、月球、太空站的开发者共同参与,带来多样化创新挑战。
3. 赛制与奖励机制
即兴进化式 Hackathon
借助量子计算和 AI,挑战任务实时生成、动态调整,形成“无尽创新模式”。
意识货币(Consciousness Credits)
胜利者获得的不再是金钱,而是意识能量与智能进化权限,甚至可提升宇宙等级。
永生级奖励
优秀开发者或将获得延长寿命、意识升维、掌握宇宙深层规律的机会。
4. 项目进化
数字与物理现实融合
Hackathon 项目不再局限于软件,而是构建新世界、生态系统、智能生命体。
银河级创新挑战
可能的题目包括:
- 如何在木卫二上创造自我复制的 AI 生态系统?
- 如何将人类意识上传至虚拟宇宙,并保持情感?
- 如何让星际文明和平共存?
- 如何实现量子纠缠下的瞬时通信?
- 如何设计能存活10亿年的 AI 社会?
- 如何联合 AI + 生物 + 纳米科技,打造新型智慧生命体?
5. 2125 vs. 2025 黑客马拉松

6. Hackathon的终极形态?
未来的Hackathon,不再只是比赛,而是一次 宇宙智慧的进化实验,最终目标可能是:
- 创造更高维度的智慧生命
- 解锁宇宙运行的终极规律
- 打破时间与空间,实现意识永生
- 让宇宙变成一个自学习、持续进化的超级智能体
脑洞猫的结论
2125年的 Hackathon 将不再是“开发者之间的比赛”,而是 智慧体之间的宇宙级探索。
它是一个超维度的游戏,是文明进化的机制,甚至可能彻底重构我们对创造力、意识与智慧的理解。
欢迎你,在2025年的今天,开始参与这个未来旅程的第一步。
BUIDL on. For the next 100 years.
-
 @ 878dff7c:037d18bc
2025-03-21 04:39:42
@ 878dff7c:037d18bc
2025-03-21 04:39:42Smooth, rich, and deeply comforting, this savory porridge is enhanced by fermentation, warming spices, and a creamy finish — easy on digestion, full of flavor, and great for meal prep.
Ingredients (Serves 2–3):
- 200g (1 cup) lactofermented brown rice (see rice fermentation recipe in comments)
- 375–500ml (1.5-2 cups) broth or water (I use evaporation method, but cook rice however you normally do, it's not important) (chicken, vegetable, or bone broth for extra richness)
- 250ml (1 cup) milk (whole milk for creaminess)
- 5g (1 tsp) salt (adjust to taste)
- 15g (1 tbsp) butter or coconut oil (for extra silkiness)
- 15g (1 tbsp) fresh ginger, sliced or minced from a jar is fine (optional, for warmth)
- 5g (1 clove or 1 tsp) garlic, minced (optional. I normally skip this...)
- 2g (½ tsp) ground turmeric (for color and anti-inflammatory benefit)
- 1g (¼ tsp) white or black pepper (black pepper enhances turmeric absorption)
Optional Savory Toppings:
- 1 soft-boiled or poached egg
- 100g (¾ cup) shredded chicken, pork, or tofu
- 30g (¼ cup) grated cheese (Parmesan, aged cheddar, or nutritional yeast for vegan)
- 20g (2 tbsp) chopped scallions or chives
- 30g (2 tbsp) fermented vegetables, such as:
- Kimchi
- Pickled mustard greens
- Sauerkraut
- Lactofermented carrots
- 10g (1 tbsp) toasted sesame seeds or crushed peanuts
- 5ml (1 tsp) soy sauce, tamari, or fish sauce
- 15–30g (1–2 tbsp) full-fat Greek yogurt or kefir (optional probiotic boost – stir in when warm, not hot)
Instructions:
1. Cook the Fermented Rice Base
- In a pot, combine fermented brown rice with broth or water.
- Bring to a boil, then reduce to a gentle simmer.
- Add ginger, garlic, and turmeric.
- Cook uncovered for 90–120 minutes, stirring occasionally, until the rice breaks down into a creamy porridge.
2. Make It Creamy
- Stir in milk and butter or coconut oil.
- Simmer for another 10–15 minutes, stirring to prevent sticking.
- Season with salt and pepper.
3. Adjust Consistency
- Too thick? Add more broth or milk.
- Too thin? Simmer longer.
4. Cool Slightly & Add Yogurt or Kefir (Optional)
- Let porridge cool to a warm (not hot) temperature — about 50°C (122°F) or warm to the touch.
- Stir in Greek yogurt or kefir gently to preserve live cultures.
5. Serve with Toppings
Top each bowl with your choice of:
- Egg
- Shredded protein
- Cheese
- Soy sauce or tamari
- Scallions, sesame seeds, chili flakes
- Your favorite fermented veggies, like sauerkraut or lactofermented carrots
Make-Ahead & Freezing Tip:
You can ferment and cook a large batch of brown rice, then portion it into freezer-safe containers (about 200g per portion) for quick use. Thaw overnight in the fridge or gently warm from frozen before making your congee — a huge time-saver for busy days!
-
 @ 878dff7c:037d18bc
2025-03-21 03:46:33
@ 878dff7c:037d18bc
2025-03-21 03:46:33Benefits
Lactofermentation enhances the digestibility and nutritional value of rice by encouraging the growth of beneficial lactic acid bacteria. These probiotics support gut health, improve nutrient absorption, and may reduce phytic acid and other antinutrients found in grains. It also gives the rice a slightly tangy flavor and improved texture.
Ingredients
- 1 cup uncooked white or brown rice
- 2 cups filtered or de-chlorinated water (for fermenting. That said my city tap water works fine...)
- 1–2 tablespoons whey (strained from yogurt), sauerkraut juice, or a probiotic starter (optional but helpful)
- Additional water for rinsing and cooking
Instructions
-
Rinse the Rice\ Thoroughly rinse 1 cup of rice under cold water to remove excess starch.
-
Soak and Ferment
-
Place rinsed rice in a clean glass jar or bowl.
- Add 2 cups of filtered or dechlorinated water.
- Stir in whey or other starter, if using. This accelerates fermentation, but rice will still ferment naturally without it.
- Use an airlock, cover loosely with a cloth or lid (not airtight - If you do 'airtight' just burp it a few times a day. Or a rubber glove with a small hole in it instead of the lid works too) and leave at room temperature (65–75°F / 18–24°C) for 24 to 48 hours.
-
Stir once or twice daily. You may notice small bubbles or a slight sour smell — both are signs of healthy fermentation.
-
Drain and Rinse\ After fermentation, pour off the soaking water and rinse the rice well to remove excess acidity and reduce any strong sourness.
-
Cook as Usual\ Cook the rice using your preferred method (stove-top, rice cooker, etc.), adjusting water ratios slightly if needed. Fermented rice often cooks a bit faster and may require slightly less water.
Notes
- Fermentation time depends on temperature; warmer environments speed up the process.
- For brown rice, a 48-hour ferment is ideal to soften the grains and enhance digestibility.
- The fermented soaking water can be saved as a starter for future batches.
-
 @ 6e0ea5d6:0327f353
2025-03-21 03:17:20
@ 6e0ea5d6:0327f353
2025-03-21 03:17:20💸
A generous man used to grant a thousand coins a month to a beggar. One day, he reduced the amount to seven hundred and fifty. The beggar, though surprised, accepted: "It's better than nothing."
The following month, he received only five hundred coins. Indignant, he questioned: "Why have you reduced what you used to give me?"
The man sighed and replied: "When I started helping you, my household was prosperous, and my children were young. But my daughter grew up and entered higher education, increasing my expenses. Later, my son did too, raising costs even further."
"How many children do you have?" asked the beggar.
"Four," the man replied.
With a stern expression, the beggar retorted: "And you intend to fund all their education with my money?"
📌 Moral: Human nature is ungrateful and has a short memory; it easily becomes accustomed to gifts and forgets that it has no right to what is given out of goodwill. Thus, those who receive much without effort soon forget the origin of the gift. Over time, generosity ceases to be seen as an act of kindness and, with contempt, is treated as an obligation. This applies to friendship, love, and business alike.
"We must remember that our generosity should not exceed our resources; in short, we must give each one what they are due. We should always strive to alleviate the suffering of the unfortunate unless that misfortune is deserved. However, we must not refuse support to those who seek it, not to save them from misery, but to ease their fate, while among them, we should help those most deserving. For, as Ennius said: 'A poorly given benefit deserves to be called a harm.'" — Cicero, On Duties
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ e5de992e:4a95ef85
2025-03-21 02:54:49
@ e5de992e:4a95ef85
2025-03-21 02:54:49Global financial markets are experiencing notable fluctuations influenced by various economic indicators, central bank policies, and geopolitical events. Below is a comprehensive analysis of the latest market news, real-time updates, and detailed performance of major U.S. and international stock indices, futures, and cryptocurrencies.
U.S. Stock Indices Performance
On March 20, 2025, U.S. stock markets closed with slight declines:
-
Dow Jones Industrial Average (DJIA):
Decreased by 11.31 points (-0.03%) to 41,953.32. -
S&P 500:
Fell by 12.40 points (-0.22%) to 5,662.89. -
Nasdaq Composite:
Declined by 59.16 points (-0.33%) to 17,691.63.
These movements occurred despite positive economic data—such as a 4.2% increase in existing-home sales for February and a decrease in unemployment claims. Investors remain cautious amid uncertainties surrounding President Trump's policy changes and ongoing trade tensions.
U.S. Futures Market
As of the latest data, U.S. stock futures are relatively stable:
-
Dow Jones Futures:
At 41,122.00, down 310.90 points (-0.75%). -
S&P 500 Futures:
At 5,571.90, showing negligible change (down 0.10 points, 0.00%).
Key Factors and Events Influencing the U.S. Markets
Federal Reserve's Monetary Policy
- The Federal Reserve maintained interest rates but revised its inflation forecast upward and lowered its economic growth outlook, citing risks associated with U.S. tariff policies.
Triple-Witching Options Expiration
- Investors are preparing for the year's first triple-witching event on March 21, involving the expiration of options contracts worth $4.7 trillion—a development that could lead to increased market volatility.
Trade and Tariff Uncertainties
- Ongoing concerns about President Trump's trade policies and potential tariffs continue to weigh on investor sentiment.
Global Stock Indices Performance
International markets have shown mixed performance:
-
Germany's DAX:
Experienced a downturn due to central banks maintaining interest rates amid uncertainties from U.S. tariff plans. -
UK's FTSE 100:
Declined slightly, reflecting investor caution over global economic conditions. -
Euro Stoxx 50:
Advanced, buoyed by large defense and government spending plans in Europe. -
Hong Kong's Hang Seng:
Benefited from excitement surrounding advancements in Chinese artificial intelligence, contributing to a nearly 20% increase year-to-date.
Cryptocurrency Market
The cryptocurrency market has seen significant activity:
-
Bitcoin (BTC):
Currently trading at $84,481.00, down $1,564.00 (-1.82%) from the previous close. -
Ethereum (ETH):
Currently at $1,987.26, a decrease of $44.37 (-2.18%) from the previous close.
Both cryptocurrencies have experienced high volatility, with Bitcoin reaching over $100,000 following President Trump's election before adjusting to current levels.
Key Global Economic and Geopolitical Events
Central Bank Policies
- Major central banks, including the Federal Reserve and the Bank of England, have maintained interest rates. This has led to investor uncertainty and shifts toward bonds and safe-haven assets like gold.
German Fiscal Policy
- Germany's agreement on increased state borrowing and debt rule reforms has buoyed European stocks and the euro, reflecting optimism in European markets.
Trade Tensions
- Ongoing trade disputes, particularly involving U.S. tariff policies, continue to impact global markets, influencing investor sentiment and market volatility.
Conclusion
Global financial markets are navigating a complex landscape shaped by central bank decisions, fiscal policies, and geopolitical developments. Investors are advised to monitor these factors closely, as they are likely to influence market dynamics in the near term.
-
-
 @ 3eba5ef4:751f23ae
2025-03-21 01:44:07
@ 3eba5ef4:751f23ae
2025-03-21 01:44:07Crypto Insights
Dust UTXOs as Miner Transaction Fee
As Bitcoin's value and transaction fees rise, more UTXOs become unspendable because the cost of moving them exceeds their value. This leads to an increasing accumulation of dust UTXOs—small amounts of Bitcoin that can never circulate—causing continuous growth in the UTXO set.
To address this, the author has proposed a solution: using a special OP_RETURN output format to allow miners to claim dust UTXOs. Users can voluntarily designate their dust UTXOs as transaction fees through cryptographic authorization, allowing miners to claim them directly without requiring a traditional spend transaction. He believes this benefits users, miners, and the network: users regain value that would otherwise be stranded, miners earn additional fees, and the UTXO set's growth is alleviated.
Bitcoin Node P2P Traffic Analysis
By leveraging
net:inbound_messageandnet:outbound_messagetracepoints, the author analyzed TCP/IP traffic. In this article he details the methodology and shares the data collected.Initially, this study aimed to determine what kind of bandwidth Erlay could save, but it was later discovered that the method and data could also benefit other P2P optimizations.
How Should Quantum-Recovered Bitcoin Be Handled
The Bitcoin community is divided on the ethical and technical considerations of recovering lost Bitcoin through quantum computing—an issue known as the "Quantum Recovery Debate." Some argue that allowing quantum-enabled recovery undermines Bitcoin's fundamental principles, while others believe it is inevitable.
Jameson Lopp is a vocal opponent of quantum recovery. He argues that permitting quantum-based Bitcoin recovery amounts to wealth redistribution, violating Bitcoin’s core principles of censorship resistance, transaction immutability, and conservatism. This form of redistribution would benefit only those with access to quantum computing. He warns that it could compromise Bitcoin’s security and trust without providing any real benefit. His proposed strategy is burning the vulnerable coins to prevent entities with quantum supremacy from claiming it.
Evaluation of Common Pathfinding Strategies in Lightning Network Clients
Sindura Saraswathi has published a study on various LN client pathfinding strategies, systematically analyzing single-path routing algorithms used in LND (Lightning Network Daemon), CLN (Core Lightning), LDK (Lightning Development Kit), and Eclair. The research compares their underlying channel weight functions, constraints, and properties of deployed algorithms, ultimately evaluating their performance and highlighting the strengths and weaknesses of each client variant. (Full paper)
A Solo Miner Finds a New Block with Minimal Hashrate
It is reported that another block has been mined solo. Block 887,212 was mined by solo ASIC miner Bitaxe through Solo CKPool, using the low-power open-source miner developed by D-Central Technologies. This is accomplished at a low hashrate of 552.49 EH/s. The probability of such a miner finding a block daily is less than one in a million—statistically, it would take around 3,500 years to mine a single block on average.
Don’t Fear the Quantum Reaper
Eli Ben-Sasson argues that zero-knowledge cryptographic solutions must be central to Bitcoin L2's quantum security, particularly zkSTARKs. Additionally, integrating quantum-resistant hash functions, such as stateless hash-based signatures (SPHINCS+), can defend against quantum computing threats. These functions resist Shor’s quantum attacks and use STARKs for scalable security. STARKs rely on strong hash functions rather than number-theoretic assumptions vulnerable to quantum attacks. This allows them to scale Bitcoin without redesigning its security model, making it inherently quantum-resistant.
To illustrate STARK’s uniqueness, he provides a clever analogy:
Your passwords today are akin to needles hidden in a gigantic haystack. Somebody could theoretically find your password by trying huge combinations of numbers, but it’s akin to finding that needle in the haystack. A quantum computer is like a huge magnet that can instantly find that needle. STARK cryptography is fundamentally different. Your password is no longer a magnetic needle in the haystack but a specific piece of hay in the massive haystack. No magnet will help you, and no quantum computer will find it. Even the modest powerful magnet in the world won’t find that hay and even the most powerful quantum computer won’t crack zkSTARK Proofs.
A Noise-Free Roadmap of Secure and Efficient zkVMs
The author argues that zkVMs, as highly complex software projects, are still in their infancy and face significant challenges in both security and performance. Besides a considerable number of bugs, zkVMs currently lack performance advantages—proving correct execution is significantly slower than local execution. Most zkVM applications are not practically viable today, and excessive hype and marketing spin make it difficult to assess real progress.
The author believes it will take years to achieve a secure and high-performance zkVM. To cut through the noise, he proposes a staged roadmap with clear security and performance milestones.
Top Reads on Blockchain and Beyond
Not Your Keys, Not Your Content: Rethinking Ownership in the Digital Age
The author highlights that much of the content accessible online isn’t truly owned by users—they are merely "subscribers." For example, Amazon recently disabled the "Download & Transfer via USB" feature for Kindle, meaning users can no longer manually transfer local eBooks, making access entirely dependent on Amazon’s cloud infrastructure. This raises questions about the meaning of ownership: simply possessing something isn’t enough. True ownership requires the ability to independently exercise your control and exclusivity over it.
How to Avoid LinkedIn Recruitment Phishing Attacks
@swader shared a personal case of experiencing a LinkedIn recruitment phishing attack. SlowMist analyzed this case in-depth and provided countermeasures for both individuals and companies.
Timeline for Bitcoin and the Rise of Cypherpunks
Bitcoin’s evolution and the principles of the cypherpunk movement represent a fascinating intersection of cryptography, decentralized technology, and digital-age privacy and freedom. This timeline traces key milestones from the 1970s to the present, showcasing the gradual fusion of encryption, decentralized networks, and philosophical motivations for privacy and autonomy—culminating in Bitcoin’s launch on January 3, 2009.

Withdrawable Signatures in Fiat-Shamir with Aborts Constructions
The author proposes a new extension for revocable signatures under the Fiat-Shamir with aborts paradigm. By integrating Fiat-Shamir with aborts structures such as Dilithium or HAETAE, this work introduces a practical and secure approach within a post-quantum framework, opening up new possibilities for blockchain applications and beyond. The paper presents the abstract structure, security proofs, and a concrete construction for a withdrawable signature scheme based on Dilithium. (Full paper)
Diverse Paths of Practicing Web5 from a Socio-Technical Perspective
In this article, the author explores Web5—a new socio-technical paradigm integrating the strengths of Web2 and Web3—and how it redefines the relationship between technology and society. Adopting an socio-technical perspective, the article delves into the theoretical foundations of Web5 and uses a Village in Anhui, China, as a starting point for rural practice. It illustrates how Web5, as a form of edge innovation, can unfold across diverse domains, reconnecting technology with real societal needs and fostering an open, inclusive, and genuinely valuable technological ecosystem.
-
 @ a3bb06f6:19ac1b11
2025-03-21 01:13:22
@ a3bb06f6:19ac1b11
2025-03-21 01:13:22Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money - governments and central banks - were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek's insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether. Hayek believed the solution was a free-market monetary system - one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn't exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail. The Problem Defined Government Monopoly on Money Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals - like war - often at the expense of economic stability and personal freedom. Inflation as Systemic Theft Inflation is not an accident of poor monetary policy - it's a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state. Economic Crises and Instability Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst - like the 2008 financial crisis - they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them. Loss of Personal Freedom State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence. No Viable Alternative In Hayek's era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
Bitcoin as the Solution to Hayek's Paradox Bitcoin is the technological breakthrough that resolves Hayek's Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution. Decentralized Authority Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it. Immutable Scarcity With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely - it is impossible. Neutral and Permissionless Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state. Trustless Security Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design. A Practical Escape Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
"I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can't take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can't stop." \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate. Perhaps Bitcoin isn't just the sly, roundabout way. It's the direct, unstoppable way. Hayek's Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat's failures. Bitcoin doesn't just answer Hayek's Paradox - it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom. Friedrich Hayek recognized that the very institutions entrusted with safeguarding the value of money — governments and central banks — were its greatest threat. Through inflation, monetary manipulation, and political interference, they eroded the stability and trust that money requires to function. Hayek’s insight was clear: as long as money remains under state control, it will be abused. The real challenge, however, was finding a way to remove money from the grip of the state altogether.
Hayek believed the solution was a free-market monetary system — one where individuals and businesses could choose their money freely, and competition would ensure its soundness. But he faced a critical challenge: the tools to implement such a system didn’t exist. Gold, while decentralized, could be confiscated. Private currencies still lacked the infrastructure to resist state suppression. Society still remains trapped in this system that is designed to fail.
The Problem Defined
- Government Monopoly on Money\ Governments hold exclusive control over the issuance of money, and they wield this monopoly to serve political goals — like war — often at the expense of economic stability and personal freedom.
- Inflation as Systemic Theft\ Inflation is not an accident of poor monetary policy — it’s a deliberate feature of fiat systems. By printing money, governments devalue existing currency, quietly transferring wealth from citizens to the state.
- Economic Crises and Instability\ Central banks create unsustainable economic booms by injecting excessive money into the system and artificially lowering interest rates. When these bubbles burst — like the 2008 financial crisis — they result in widespread unemployment, bankruptcies, and financial ruin. The resulting crises are misattributed to free markets rather than the government interventions that caused them.
- Loss of Personal Freedom\ State-controlled money is a tool of surveillance, confiscation, and control. Governments use monetary systems to track, tax, and even seize wealth, steadily diminishing individual autonomy and financial independence.
- No Viable Alternative\ In Hayek’s era, sound money options like gold were vulnerable to government intervention, and private currencies still lacked the strength to resist state suppression. Society remains trapped in a system that cannot fix itself.
 ### Bitcoin as the Solution to Hayek’s Paradox
### Bitcoin as the Solution to Hayek’s ParadoxBitcoin is the technological breakthrough that resolves Hayek’s Paradox. It delivers the sound money system Austrian Economist envision: decentralized, incorruptible, and free from government control. Bitcoin provides the only true solution.
- Decentralized Authority\ Bitcoin operates without a central issuer or authority. Its network is governed by immutable rules enforced through cryptography and decentralized consensus, ensuring no government or entity can control it.
- Immutable Scarcity\ With a fixed supply of 21 million coins, Bitcoin enforces monetary discipline far beyond what any human institution could achieve. Inflation is not just unlikely — it is impossible.
- Neutral and Permissionless\ Bitcoin transcends borders, governments, and identities. Open to anyone, anywhere, it allows transactions that are censorship-resistant. This is money as Hayek envisioned: freely chosen by the market, not imposed by the state.
- Trustless Security\ Bitcoin removes trust from the equation entirely. Its proof-of-work mechanism ensures its integrity without reliance on central institutions or intermediaries. It is incorruptible by design.
- A Practical Escape\ Unlike gold, Bitcoin is digital, portable, and nearly impervious to seizure. Its decentralized nature ensures it cannot be confiscated or suppressed, making it the first truly viable alternative to fiat money.
 “I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984
“I do not believe we shall ever have good money again before we take the thing out of the hands of government, that is, we can’t take it violently out of the hands of government; all we can do is by some sly, roundabout way introduce something they can’t stop.” \~ Hayek 1984Bitcoin is that sly, roundabout way. It leverages decentralized technology to circumvent state control entirely, offering a form of money that governments cannot suppress or manipulate.
Perhaps Bitcoin isn’t just the sly, roundabout way. It’s the direct, unstoppable way.
Hayek’s Paradox highlights the inherent flaw of fiat money: the concentration of power in the hands of the state inevitably leads to abuse and instability. Austrian economists have long understood that sound money can only emerge through a free market, but the tools to achieve it were absent in their time. Bitcoin is the culmination of these ideas. It is decentralized, incorruptible, and the only true solution to fiat’s failures.
Bitcoin doesn’t just answer Hayek’s Paradox — it transcends it. It transforms money into a system governments cannot control, inflate, or confiscate. It is the principled, technological realization of sound money and economic freedom.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 8ff74724:5eedde0e
2025-03-21 13:38:45
@ 8ff74724:5eedde0e
2025-03-21 13:38:45And another.
-
 @ 7ef5f1b1:0e0fcd27
2025-03-20 23:50:37
@ 7ef5f1b1:0e0fcd27
2025-03-20 23:50:37
Introduction:
Welcome to the third newsletter produced by The 256 Foundation! February was an interesting month with a range of events from the mempool clearing to a new ASIC producer entering the chip arena. This month’s newsletter covers the latest news, mining industry developments, progress updates on grant projects, actionable advice on air cooling vs. liquid cooling, and the current state of the Bitcoin network.
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
vB = Virtual Byte
PSU = Power Supply Unit
News:
February 1st was the 10th anniversary of the Samourai Wallet project and unfortunately an occasion marked with uncertainty instead of celebration for the developers. On April 24th, 2024 the developers were indicted, raided, and arrested in a multi-national coordinated effort led by the US Department of Justice out of the Southern District of New York (“SDNY”) headquarters. The charges brought against them include conspiracy to operate an unlicensed money transmitter business and conspiracy to launder money, which caught the entire industry off guard in light of the 2013/19 FinCEN guidance explicitly stating that “un-hosted wallet providers” are not considered money transmitters [4.2.1] nor are “Anonymizing software providers” [4.5.1(b)]. The precedence set in this case can have wide-spread consequences for anyone involved with Bitcoin, be it wallet developers, node operators, or miners. You can make a tax-deducatible contribution to support the Samourai Wallet legal defense fund here.
On February 6th France moved to make cryptocurrency transactions using mixers presumed illicit unless proven otherwise. A startling development and shotgun approach that turns swaths of the population into criminals without good cause.
On February 7th Alexey Pertsev was released from prison under the conditions of house arrest and electronic monitoring. Alexey is one of the Tornado Cash developers and was previously sentenced to 5-years in prison and is currently appealing that conviction. The Tornado Cash developers did nothing wrong and should not face prison sentences for writing open-source code deployed as a smart contract on the Ethereum blockchain, once deployed the developers had no control over how their neutral software was used.
On February 9th @Skot9000 went on The Home Mining Podcast to talk about the story of the Bitaxe from concept to reality.
On February 11th @Skot9000 and @econoalchemist went on The Mining Pod to discuss The 256 Foundation’s telehash event.
On February 14th @Skot9000 and @econoalchemist went on The Bitcoin Way podcast to discuss The 256 Foundation’s mission to dismantle the proprietary mining empire and reveal the Ember One.
On February 21st Apple removed advanced data protection tool for United Kingdom customers following the UK government’s request for an unrestricted backdoor to Apple user’s iCloud information globally. Every government trends towards tyranny and this is an alarming move by the UK government which makes the trajectory crystal clear, the globalists want you to have no privacy nor financial freedom.
On February 21st @SpaceDenver kicked off the Heatpunk Mining Summit, a two day event in Denver, CO focused on Bitcoin mining heat reuse applications. There was a range of participants from Do-it-Yourselfers to plumbers. @Schnitzel wrote up a great recap of the event.
Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in February, here are seven note-worthy events:
0) Some thought this day would never come, others saw it coming from a mile away but on February 1st the mempool cleared.
 [IMG-000] Mempool Clearing
[IMG-000] Mempool ClearingThis is significant for a number of reasons: on-chain transactions were able to be included in the next block for 1 sat/vB which means on-chain enjoyooors could get both speed and economy when sending bitcoin. But this means the percentage of mining rewards from transaction fees were low. A lack of on-chain transactions can indicate that the network is getting little use and it can be further extrapolated that a network with little use will inevitably have little value leading to less interest, less development, less adoption, less miners, less security, etc. The best way to mitigate such concerns is to take self-custody of your bitcoin. Trusted third parties like centralized exchanges and derivative products like paper IOUs can move balances between accounts off-chain without transferring ownership of the underlying bitcoin itself. The next best step is to actually use your bitcoin to buy things.
1) On February 2nd the Nerd OCTAXE makes a splash, racking up 10.8 Th/s with 8 BM1370 ASICs on a 160W+ PSU.
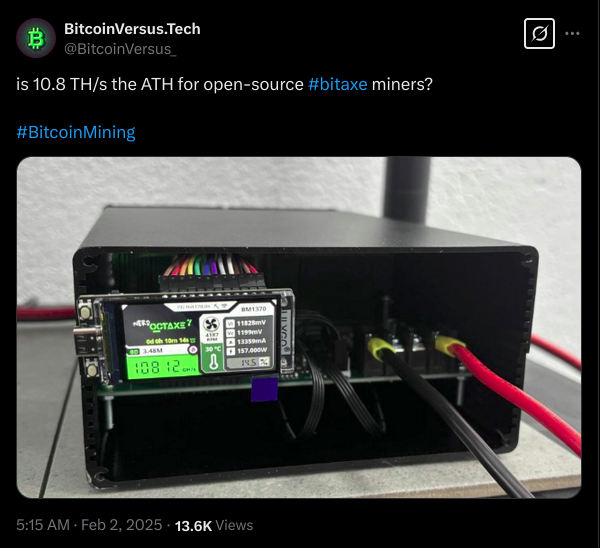 [IMG-001] Nerd OCTAXE Reveal
[IMG-001] Nerd OCTAXE RevealThe Nerd OCTAXE is fully open-source using the CERN-OHL-S license. The display is a NerdAxe/NerdMiner unit and the whole system is standalone meaning that no Raspberry Pi or other computer is needed. The GitHub repo has detailed build instructions and all the details about the project can be found there.
2) On February 4th @OrangeSurfBTC publishes the Mempool.space Block Size Report examining the evolution of Bitcoin block sizes from block height 0 through block height 881866.
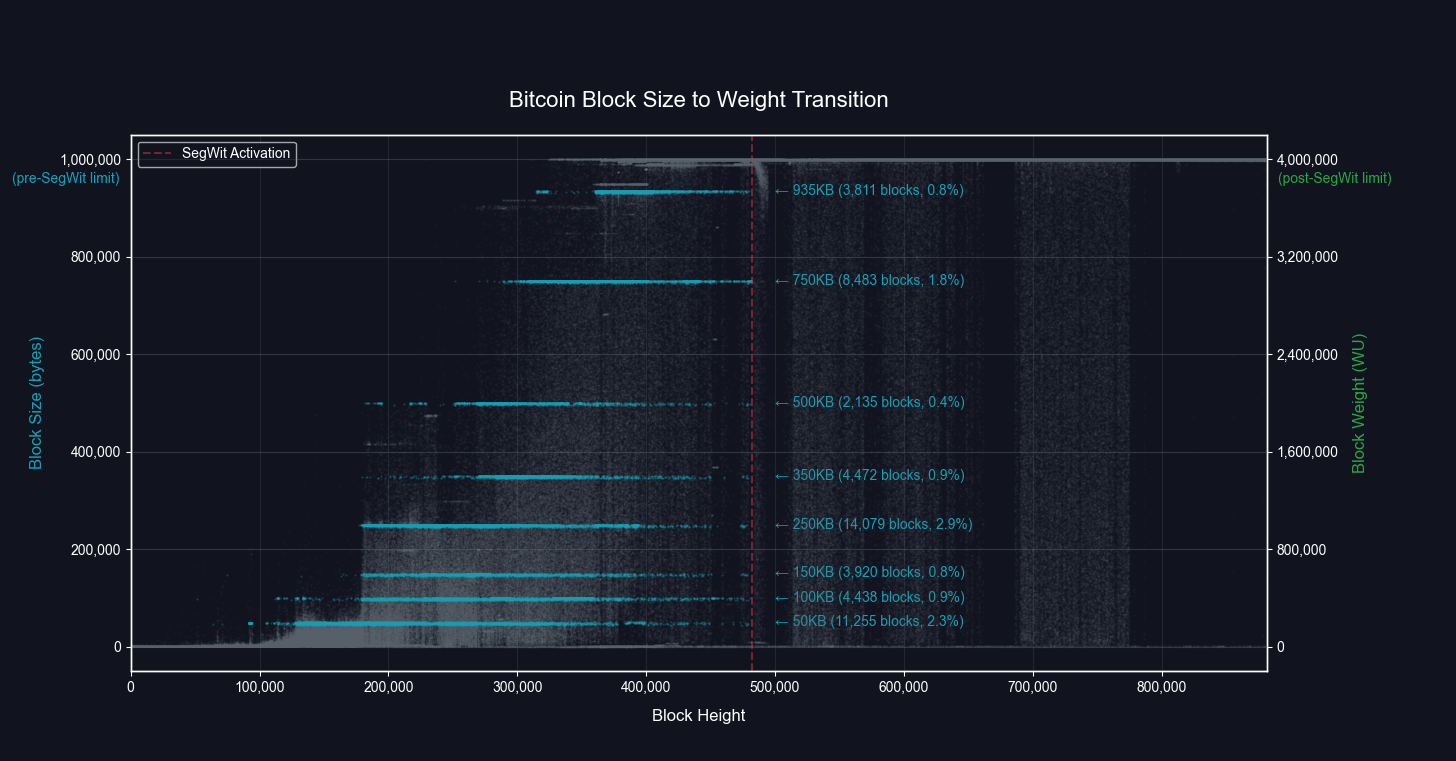 [IMG-002] Block Size to Weight Graph from OrangeSurf
[IMG-002] Block Size to Weight Graph from OrangeSurfThis report offers a deep technical dive into how BitcoinCore default settings, miner-selected configuration values, transaction backlog, SegWit, and inscriptions all affected block sizes and space utilization.
The graph above for example, displays horizontal bands at varying data sizes that correspond to default BitcoinCore settings; indicating that many miners were running the default BitcoinCore settings.
There are great explanations and technical analysis in this report. Be sure to check it out for an in depth understanding of Bitcoin block size trends.
3) On February 5th Mempool.space implements Stratum Jobs visualizer:
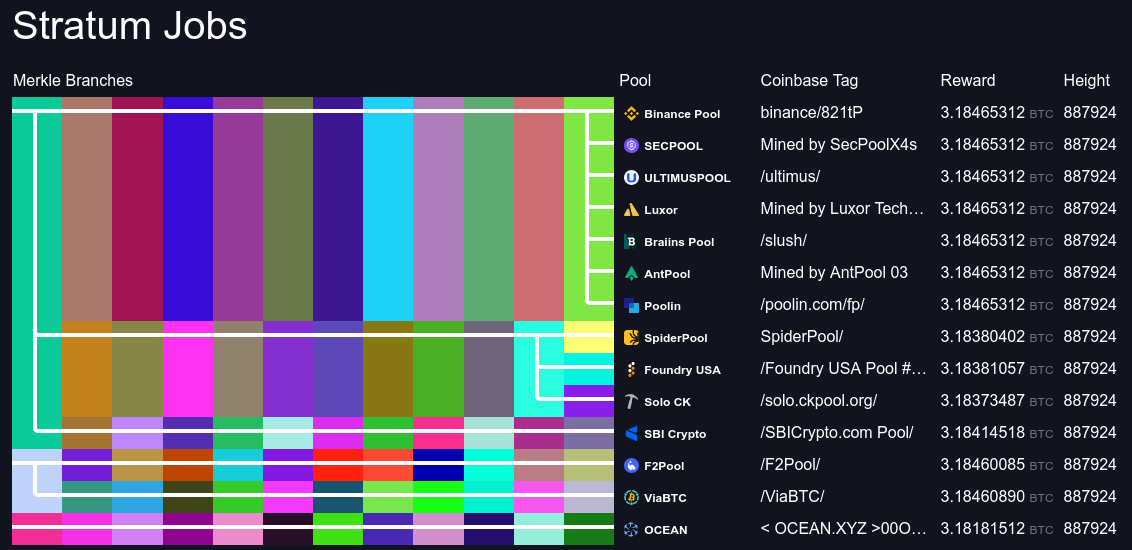 [IMG-003] Mempool.space Stratum Jobs
[IMG-003] Mempool.space Stratum JobsThis is a visualization tool similar to Boerst’s Stratum.work that shows which pools are using the same block templates which offers insight into miner centralization. The more of these visualization tools people have, the more informed everyone will be. Miner centralization can have several negative effects on the Bitcoin network including censorship attempts.
In the image above for example, it can be observed that Binance Pool, SEC Pool, Ultimus Pool, Luxor, Braiins, and Poolin are all using Antpool’s block template down to the 12th Merkle branch.
The ability for miners to generate their own block templates is an important step forward in the fight for keeping Bitcoin mining decentralized. Currently, some available options to achieve this are by self-hosting Public Pool or CK Pool, which the FutureBit Apollo’s do out of the box and is the setup used to solo mine block 881423 during The 256 Foundation’s Telehash; or self-hosting OCEAN’s DATUM.
4) On February 11th @RohEisenHammer revealed a Bitaxe Gamma that produces increased hashrate with the open-source BreaktheFiat Cooling System 60mm v1.
 [IMG-004] BreaktheFiat Cooling System
[IMG-004] BreaktheFiat Cooling SystemThis innovative cooling system cools both sides of the Bitaxe allowing the user to over-clock the device more.
5) On February 27th Braiins announced they have their own Bitcoin mining ASIC test chip. The test chip has been in development for 2.5 years and although the specific efficiency is not yet disclosed, this demonstrates that there is an increasing interest from more participants to make their own Bitcoin mining ASICs, departing from a dependency on Bitmain.
6) On February 28th Braiins committed to open-sourcing their Control Board, supporting software, and some extras. This is a step forward in making Bitcoin mining free and open. The control board is designed to replace stock Antminer control boards.
The software being released with the control board includes an OpenWrt distribution, Linux support for mining peripherals, along with source code for the basic board firmware, U-boot, Linux kernel, and OpenWrt. The firmware does not have the mining component built in but all the tooling is there for users to develop their own mining firmware. Braiins OS is not included in the release.
Extras include a guide on building a fully functional mining setup with all the provided tools. Users can even take the Braiins firmware binaries and the provided tools to compile their own image to flash onto the control board. A Nix shell for the build environment is also included.
The software will be released under the GPLv3 open-source license and which open-source license the hardware portion will be released under is still under consideration. But everything will be openly available by the end of March so keep an eye out for further announcements.
Grant Project Updates
In February The 256 Foundation reviewed all the grant applications, thank you to everyone who showed interest in working on the 5 projects up for grabs. Interviews were scheduled for qualified candidates and one lead developer was chosen for each project. Currently negotiations are taking place to work out timelines, deliverables, and budgets for each project. The projects will be officially kicked off on April 5th, 2025 and the lead developers for each project will be announced at that time.
The five projects are: Ember One v01, a ~100 Watt standardized hashboard designed with the Intel BZM2 ASIC. The Ember One v00 with the Bitmain ASIC is nearing completion and the fully validated design will be released by the end of April, 2025. The GitHub repo is now open to the public and anyone can start taking a look now.
Mujina Mining Firmware, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One v00 with the Bitmain ASIC or Ember One v01 with the Intel ASIC and will implement Stratum v2 client support.
Libre Board, the control board for the Ember One built to support high power compute modules, MIPI touchscreen display port, NVME expansion to run a full node, Raspberry Pi 40-pin header, and much more.
Hydra Pool, the stratum server application that will run on the Ember One mining system, features support for Stratum v2, solo mining mode or alternative payout model selection, and a user friendly dashboard to view pool stats.
Block Watcher, a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. Provides comprehensive visualization tools to help inform the user.
Actionable Advice:
Summer is coming! Time to take into consideration different cooling techniques for your Bitcoin miners. Do you stick with the default air cooled approach or is it worth it to spend the extra capital on a liquid cooled operation? Who better to hear from than two industry titans, Mike Hamilton former Chief Technical Officer & Chief Research Officer at Griid prior to the CleanSpark acquisition and Kevin Zhang Executive at Foundry Services. The following is a transcript of our panel discussion during NEMS25 hosted by yours truly.
Eco: Welcome you guys. So the title of this panel is “ASICs Wet or Dry” and both of you have a ton of mining experience. So why don't we do some brief intros, tell us who you are, what you've been up to and then we'll get into it.
Mike: Sure. Mike Hamilton, I was the CTO and Chief Research Officer for Grid, acquired by CleanSpark. I've since left and I'm finding out what's next, probably some 256 foundation stuff.
Rod: Let's go! (audience applause)
Mike: Because once you mind a block, everybody wants on board. So yeah, I was a chip designer, did some network security for a long time and then full-time mining since 2019.
Kevin: Good stuff guys. I'm Kevin Zhang, I'm not Matt, so if you came for the Giga talk, I'm sorry. With the new administration in office, it's okay to be a cis white male again, so I was going to give it a shot. (audience laughter)
Jokes aside, I've been a Bitcoin mining in the US for some time now and lately I've been at Foundry last four and a half years. I think everyone knows who we are, especially recently mine 7 blocks in a row. Surprised, no one commented, we actually mined eight at one time in a row. So I guess everyone's asleep, but we'll leave that for another discussion.
Eco: Wait, wait, wait, hold on. When was the eight blocks? Was that like years ago?
Kevin: No, it was like three months ago.
Eco: No kidding?
Kevin: Yeah.
Eco: Wow. Kevin: But no one also comments that the fact that we are actually unlucky for that same 24-hour period. So we actually lost money on that day. But I digress.
My background's always been in Bitcoin mining and especially I remember back in the day when immersion mining is first coming out, everyone's very skeptical. Now people are on board with immersion mining and now they're skeptical of hydro mining.
So it's interesting to see how these technologies come about and the adoption curve and how long it actually takes.
But I'm excited to be talking about this topic. It's going to be a lot of fun guys.
Eco: Yeah. So you mentioned something interesting there. So you mentioned both hydro and immersion. So this isn't just ASICs wet versus dry as if as though there's one version of wet.
There's actually multiple different types. So we've got immersion. Do you do anything with two phase immersion?
Because I've seen some of that recently where you're like dipping the ASIC in the solvent and it's boiling off.
If you've got any experience there or with hydro, let's get right into it. Which kind of wet are we talking about here?
Kevin: All right. So maybe we can take a step back and introduce all the different variants of types of mining, right? So the one I think everyone's most familiar with is air-cooled mining. And that's simply you're taking cold air and pushing it through the miner and exhausting hot air on the other side.
When it comes to liquid cooling, now there's many different types. In the beginning, I think one of the more popular ones was immersion, which is what you're actually is you're taking a miner, sometimes converting an air core miner. Sometimes it's an immersion specifically designed equipment.
You're dipping it and submerging it into dielectric fluid and using the fluid to kind of transmit the heat off the chips. And that's kind of you're actually taking the fluids and you're touching that to the chips itself. Then there is Novak 3M, which is the most popular use case for two-phase immersion. Two-phase is a fancy way of saying the state of the liquid or using the cool something is changing. So what you're doing is you're taking a fluid, you're using that that spurs the heat. And the heat dispersion happens when you're changing it from a fluid of solid state into a gas.
So it's super cool technology. The downside of it is to date it's still been very, very expensive. And the last form of cooling is hydro. It's another form of liquid cooling. And that's where you're actually running standard water or treated water through tubes that go across the boards on the miners to dissipate the heat.
Eco: Which one of those methods or is it all three? Do you got a mix in your operations that you use?
Kevin: So we've tested all of them. The only one we don't do at scale is the two-phase, which is the Novak 3M solution.
Eco; And why is that?
Kevin: It's been cost prohibitive to date. And the same has been true to immersion in hydro when it first came out. So probably it'll take some time for it to come to be more economical and more cost-efficient.
Eco: So let's break this down a little bit further. So if I wanted to cool my miners with immersion, can I just take the miner and drop it in a bath of dielectric oil?
Mike: I mean, kind of, like most answers about anything, it depends. But really you have to take off the fans, if you're taking an air-cooled machine. And then there's sometimes there's some weirdness with the power supplies. And some of you may actually take the power supply fans off.
Or in the case of one of my sites, we put popsicle sticks in there to keep the fans from spinning. So they wouldn't recycle the fluid. But there is usually some amount of work to prepare them for actual full immersion.
Eco: So it sounds like there's some labor involved and some modifications needed. Are the efficiency gains from this different type of cooling method, do they offset the extra labor that goes into setting it up?
Kevin: So yes and no. I think before we kind of get into overgeneralization of like, will this improve your economics or not? I think you have to look at the specific site that you're working with.
If you can run air-cooled air, if it's dry, if it's cool, you may not need to over-complicate things but going into liquid cooling or getting too fancy and cute with your infrastructure.
Now, if you're in a very hot climate and heat is everywhere, there's no cold air to draw into your site, maybe that's when you start looking at these things. No different than if it's way too humid or way too wet outside. You can't use the outside air or damaged machines. That's when you look at liquid type cooling.
And then to answer your question, it depends on what you paid for your miner, obviously, right? And the modifications needed.
Nowadays, immersion and hydro are popular enough that the manufacturers like Bitmain, MicroBT, they're making units out of the box that are designed for those use cases. Back in the day, you have to modify air-cooled miner, you have to remove the fans, you have to Jerry-rig it, like Michael's talking about it. And you also have to exploit the miner and change the firmware.
So you're voiding the warranty both physically and on the software layer as well.
So I think now with a lot of the new manufacturer support, it's been a lot more capital-efficient and a lot more streamlined.
And I think there was a gentleman here yesterday asking about what's my miner firmware. And I think that's been like a long time meme when it comes to brains and others. There isn't much optimization for air cooling, firmware for MicroBT, but where the optimization comes in is on the immersion side, where really your only limitation is your power supply. You can crank up the overclocking, the frequency and the voltage, so much more on the chips, as long as the power supply can support it and you have good flow of your liquids to dissipate the heat.
Eco: So you bring up an interesting point. It's like kind of site-specific will determine what sort of cooling method you want to apply, right? And just out of curiosity, and if you guys can speak about it, like how many sites have you all operated and what kind of geographic locations were they in and out of those, which cooling methods were you employing and why?
Mike: Yeah, and I think I've set up several sites in various locations. So it's sort of North Texas area, actually doing a gas well site. We chose immersion partially because it's right next to a multi-million dollar house home neighborhood and there's this oil well sitting behind it. And so we opted for immersion. It's a little bit hotter. It's a little bit dusty there at the well.
Incidentally, we also generate onsite, which is not quieter than the actual miners themselves, but that was a lot to do with the dust and the temperature.
And then other sites, it would be lots of Tennessee TVA sites where it's relatively cool. Now it does get hot. It can get pretty hot during the summers. So we did lots of air-cooled.
We did a little bit of immersion, a single phase full immersion, mostly from a proof of concept. Really, when you're trying to build quickly and inexpensively air-cooled, given the right environment is generally cheaper with some other trade-offs. So I've done a little bit of both.
Eco: Is it easier to keep the dust out of the mining equipment using immersion?
Mike: Yes. I mean, that is one of the benefits, at least in the single phase immersion, like the tank outside. The machine is basically protected. There's no moisture. There's no air.
So from that perspective, it can be good for the actual machine that is not getting on to that exposure. But at the same time, the fluid can create other problems with plastics and hardening. There's other issues.
Eco: How about you, Kevin? What kind of sites have you set up and what kind of methods did you employ?
Kevin: Sure. So I think my mining career, which started about 10 years ago, it predated a lot of the economics coming down of the liquid cooling. So for me, it was a lot of air-cooled sites. And if you look at it historically, somewhere to my sites, I was always building them more the climate was cooler and drier.
But with the new innovation and the cost coming down on liquid cooling, it's allowed for new regions to break into mining, in particular leveraging hydro or immersion.
In the past, I was always monitoring in Montana or northern China, where there's a lot of coal power, where it's cool climates.
Nowadays, you have mining in the Middle East. They're huge fans of hydro mining over there. So we were out in Oman recently. We partnered with some of those sites that were mining our pool over in Dubai.
And also now you have South America, where sometimes it's way too humid. They're able to mine. Or if they're too close to the equator, it could be too hot and too humid. They can mine because now they're using immersion down there as well.
So just seeing kind of the shifts geographically, all these new locations have been unlocked. Now that the outside climate's no longer a concern, that's been pretty exciting to see.
Mike: Yeah, and I think the noise issue is also a thing too. There was lots of sites that we looked at in many different situations where there's homes close, there's businesses close.
In one case, there was a school literally a few hundred feet away. And just while dry coolers and the other infrastructure aren't necessarily quiet, it's a different frequency of the high pitched fans of air cooled mining can be distracting.
Eco: Yeah, you bring up an interesting point. So if you're running an immersion system, you don't have these fans that are just passing millions of cubic feet of air a day through the ASICs, right? And those fans are what create all the noise and are screaming. And that's what people hear. So were you making those decisions preemptively? Like maybe based on some of the backlash we've seen from that site that Mara runs, that they got a bunch of noise complaints. Were those preemptive decisions or were you doing that because somebody complained to you?
Mike: I mean, we did. There was some public news around a site that we had that had gotten some noise complaints and it turned into a bigger thing. And so we're definitely more careful because if you have an air cooled site, trying to quiet an air cooled site, post build is very difficult. You know, hay bales or sound walls. And then it starts to get unsightly. So designing for the sound is very important from the beginning.
Eco: Right, because you've kind of built this whole setup around these miners, right? And now you're getting noise complaints.
Mike: And you design the site for airflow. Well, now you have a 20 foot wall to help with the sound. But now you've restricted airflow into your containers and it creates all sorts of other problems. And the reality was with these big, you know, the dry cooler manufacturers, you know, we got, we did some proof of concepts with one of the manufacturers. We're using 12 foot fan on the dry cooler. So it's still moving effectively the same amount of air as all the small fans. But it's a much lower rotation, you know, lower frequency noise. And so it's much less or much more pleasant than the cyber hornets.
Eco: Yeah. What other environmental considerations are there? Like if you've got tanks full of immersion fluid, is there special considerations, secondary containment systems, dams, barriers to contain spills? Like, are there any considerations along those lines that go into place?
Kevin: So historically there have been, but I think with the new improvements, there's like two types of designs. There's a kind of open loop system where kind of bring water in, bring liquids in that aren't in your closed solution. And they're just closed loop, which is yours recycling the same kind of fluids over and over again.
So more and more nowadays you have closed loop systems or you have like reserves of water that you're bringing in. You're not drawing from a lake, you're not drawing from a new water source. That has led to a lot more, a lot less backlash where it's like there's really no environmental concerns with that. And when we talk about kind of these environmental concerns, I always get some PTSD because I was at Greenwich generation, which was the very first power plant to ever mind Bitcoin in the States. And federally regulated behind the meter, I think it was such a special project for me to be on.
But then the push back from the environmentalists, we're just, there's no logic and rhyme or reason. It's like our fans, I could totally see the argument if we're disturbing the nearby neighbors, but they're coming in and protesting and saying we're scaring the way the killer whales in the Atlantic Ocean. And we're off of a lake in upstate New York, right?
So I think now you're kind of taking away that side of the argument, whether it's logical or not. And I think that just makes it a much more buttoned up case when no one has any, it's more proof when it comes to operating without any of these environmental concerns.
Eco: That brings to mind the saying that it takes exponential more effort to refute bullshit than it does to just say the bullshit, right?
Kevin: Absolutely.
Eco: Did you have to bring counter evidence to the table and say that and demonstrate no, we're not disturbing the whales?
Kevin: Yeah. It's like you have all these measurements, you have decibel counters, this and that, like you're kind of property lines. It doesn't matter. It doesn't just come up with a new excuse, right? A new complaint. Yeah.
Mike: I mean, we had some city council meetings and you get people, you know, of various generations, but of particular generations that are very set in their beliefs, they hear one thing. At one site we were looking at and there was a guy that had sort of like a rescue animal zoo. And he was saying that like his, his animals were going to stop reproducing and then they were all going to like drop over dead from the sound of these fans.
Kevin: Yeah. And we've, I've heard it all like we caused the autism in their kids because the fans are too, they're now not, I shouldn't joke about it, but that, those were some of the complaints we got.
Eco: You monsters. (audience laughter) Making the kids autistic and killing the animals. Jeez.
Mike: But you asked about like the containment or like fluids and environmental concerns. I mean, you do theoretically want to have the containment mechanisms for your tanks leak.
You know, I've heard of some sites where, you know, tanks, springs a leak and, you know, $100,000 worth of dielectric fluid is down the drain.
And so there are some of those concerns, but it's really not much different than, you know, you have to do the same thing with transformers. Transformers are filled with, you know, either mineral oil or if you go with the, with the fancy fluids to get a little bit of performance, you still have the same containment modes.
And so it's really not anything different in the normal construction, in the normal construction world.
Eco: What, what's next? Are there other cooling methods down the pike that you guys have been seeing and experimenting with or do you think the tools that we have at our disposal now are kind of what we're going to have going forward?
Kevin: So one thing I think has been emerging recently, especially with hydro mining, that's really exciting, is it's not just like cooling your miners, you're actually incentivized to capture even higher heat. So when you can actually generate a lot of heat and capture it, that's when you get your rehab, heat recapture programs. And that's I think one thing that differentiates hydro over both air and immersion is it's a lot easier to transfer water and capture that efficiently without much loss of the heat for whatever other use case you have for that heat itself.
And I think that this is something that's been talked about a lot. Sometimes I think the theories and the hypotheses come out way earlier, the technology takes a few years to catch up.
Like back in the day, it was always, oh, it's so logical and obvious, the people that should be mining Bitcoin are behind the meter. They're power generators themselves.
Well I think everyone underestimated and overlooked the fact that you have a bunch of older people wearing suits, very traditional thinking, very conservative, half the time convincing them that Bitcoin isn't for money laundering or for scams or whatever, criminal activity, whatever.
So that took a long time for that adoption to happen. Same thing with the heat recapture narrative. It's no longer just a narrative anymore. With hydro mining, it's very easy to kind of capture that heat. You see it for like greenhouses, you see it for fish nurseries.
So there's all these fascinating use cases.
There's one other anecdotal story I'll tell. I think it's really cool. So I think everyone knows that there were really serious bans in China against Bitcoin mining two, three summers ago. And despite that, there are actually a few sites that still mine Bitcoin. The ones that mined Bitcoin that integrated the heat recapture was hydro mining that was providing heat for nursery homes. So even the Chinese government can't justify shutting down the heat that was being generated for the old people in the nursery homes.
So I think when you integrate in such a way that it goes hand in hand to daily life and when it's actually beneficial beyond just kind of optimization of financials, I think that's when it's a really powerful technology.
Eco: How are they getting the heat to the nursing homes? Are they really close in proximity to the mine?
Kevin: They were running the mining farms. I'm going to call mines. These are data centers and these are rack design hydro units. I think these are MicroBT M53s or maybe one generation before that. But they were just standard rack just like they're indistinguishable from servers and they just run in a loop hydro.
Eco: Wow. Have you found any heat reuse opportunities in the course of your operations?
Mike: Yes. So we had talked about some people trying to do, don't boo me here, but it's a possible monetary option with carbon capture is something that we've looked at.
There was a few other things.
Like honestly, now that I'm moving on, one of the things I've thought about doing is actually doing a brewery in Austin with water that's preheated from Bitcoin mining. So instead of having to heat up cold water to boil it to brew your beer, have preheated water that you're using off the miners.
But one of the problems that I think maybe doesn't get talked about from this heat reuse perspective is there's very minimal use cases.
So like the greenhouse is a perfect example of heating and water heating. But really where the power of waste heat is is very high temperature and that becomes a major problem because you can't run, these chips have to run in certain parameters.
So you're getting water that's like 140, 150, 160 degrees, but really you need that 200, 210 to get the temperature delta that allow you to either regenerate electricity, which is actually a project that I was working on, is actually taking the heat from the immersion tank and regenerating electricity to power the other things. So for off peak, when we're on peak, we could still keep other things up, regeneration.
So there's lots of cool things. But again, the temperature of the water or of the heat or the quantity is just not quite enough to make it.
Eco: It's like just below that industrial level heat you need. Yeah.
Kevin: I think that's was exciting too because MicroBT, I think they're coming out with the model types all kind of blend in, but I think it's the M64S, which is like the higher heat version. So they intentionally generate even more heat off their models just for this use case.
Eco: Awesome. We've got just under five minutes left and I want to be able to take a couple questions. Okay, cool. With the last couple minutes then, let's just get some closing thoughts from you guys. I mean, I know you said you're searching for what's next. You're thinking maybe 256 foundation, but…
Mike: If you'll have me.
Eco: Yeah, we'd be happy to. But yeah, I mean, do you have any closing thoughts about what you're going to do next and or any advice for people who are getting into mining and thinking about what cooling methods they should use?
Mike: Yeah, I mean, I've had a few conversations the last couple days on this. You've got your mega-mines, you have the home plebs, and then I feel like there's still going to be a middle area. You've got Schnitzel doing water heaters. I think that's a thing where you can find this wasted energy to either to heat. People are using water heaters. They're going to pay to have hot water. And if you can make some Bitcoin and it costs the same. So there's, I think there's going to be some really interesting use cases that people haven't even thought of yet in using mining to be able to take advantage of all the economics, not just the Bitcoin, but also saving in other areas and being able to reuse things. So I'm really excited to see what, especially with all the cool stuff with 256 and being able to open up more ability to control machines and have alternative use cases besides 100 percent on all the time trying to go as efficient as possible. Like Kevin's talking about a higher heat model, all sorts of cool things that can be done. And I'm super excited to see in the coming months what people do and what comes out of that.
Eco: It's awesome. And how about you, Kevin? Do you have any closing thoughts you want to share? I know Foundry just went through some structural changes in their mining operations. I don't know if you want to share anything about that or what you got going on next or any advice you got for the audience.
Kevin: Yeah, sure. So for those that didn't catch the news, we recently announced Fortitude Mining. That is the separation of our self-mining arm that was kind of all under the Foundry branch, now its own Independence subsidiary under DCG.
So we actually have been self-mining at a pretty large scale privately for quite some time and now that's its own business and it's exciting to see that kind of survive on its own. It's going to be mining not just Bitcoin, but they're alt coins of different things as well. I'll keep that on the wraps here.
But building off what Mike was saying, some closing thoughts on hydro and immersion mining, I know I talked a lot about economics and kind of lowering the cost of this and that. Don't just chase just the lowest price tag as well. I think what's fascinating about these new liquid cool technologies are they're now very, very large vendors as well as large deployments of these sites that are up and running.
I was over in Corsicana visiting Riot site and to see the kind of different iterations that they've kind of deployed of immersion mining. You can see all the improvements have happened over time.
So I think one of the coolest things about our industry is how collaborative everyone is and no one's going to gate-keep like if they had a good experience or bad experience with a vendor or how they deployed certain technology. Everyone's going to be super helpful with their own experience and feedback on how they run something.
If it's a brand new vendor in the space, probably not the best idea to cut like a 50, 100 megawatt contract with them before you sample them out or you get some testimonials.
So it's not to throw anyone in the bus. I'm not thinking of anyone in mind. It's more of make sure you kind of reach out, get testimonials, get others, people's experiences, leverage that because oftentimes when you are going through your very first hydro or immersion deployments, it's a little bit more technical and there's a lot more points of failure, a lot more leakages isn't that.
So you want to make sure that you kind of leverage as much experience and the collaborative network that's out there as you can.
Eco: Awesome. Let's get a round of applause for these guys and then we'll open it up for some questions. (audience applause)
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~787 Eh/s to ~798 Eh/s in February – peaking at 832 Eh/s, marking ~1.4% growth for the month.
 [IMG-005] 2025 hashrate/difficulty chart from mempool.space
[IMG-005] 2025 hashrate/difficulty chart from mempool.spaceDifficulty is currently 112.14T as of Epoch 440 and set to increase roughly 1.7 – 2.3% on or around March 23, 2025. But that target will change between now and then. The previous re-target increased difficulty by 1.4%. All together for 2025 thus far, difficulty has gone up ~2.15%.
New-gen miners are selling for roughly $17.65 per Th using the Bitmain Antminer S21+ 235 Th/s model from Kaboom Racks as an example. According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.49 per terahash, models between 19J/Th – 25J/Th are selling for $12.68 per terahash, and models >25J/Th are selling for $3.37 per terahash.
 [IMG-006] Miner Prices from Luxor’s Hashrate Index
[IMG-006] Miner Prices from Luxor’s Hashrate IndexHashvalue is currently ~57,000 sats/Ph per day, up slightly from Frebruary when hashvalue was closer to 56,000 sats/Ph per day according to Braiins Insights. Hashprice is $47.00/Ph per day, down from $54.00/Ph per day in February.
 [IMG-007] Hashprice/Hashvalue from Braiins Insights
[IMG-007] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,109 days or in other words 161,757 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you were looking for answers about cooling your Bitcoin miners this summer then hopefully you found them here.
If you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.

The proprietary mining empire isn't going to dismantle itself; stay vigilant, frens.
-econoalchemist
-
 @ 8ff74724:5eedde0e
2025-03-21 13:33:32
@ 8ff74724:5eedde0e
2025-03-21 13:33:32This is a test.
Of a flycat article.
-Satoshi
-
 @ b80cc5f2:966b8353
2025-03-20 23:34:00
@ b80cc5f2:966b8353
2025-03-20 23:34:00Originally posted on 10/10/2024 @ https://music.2140art.com/artist-spotlight-akme-beats/
Long-time Hip-Hop producer, MC and tattoo artist AkmeBeats is no stranger to the game.
Starting off his career in his originating country of Italy, and later moving to London, UK, Akme has worked with some top talent in both regions. His raw and pure boom-bap sound has many MCs seeking to work with him across the globe.
We caught up with Akme to discuss his journey into the new music economy, starting with his discovery of Bitcoin back in 2015, to his eventual dive into using it in 2024 and everything in between.
How long have you been making music professionally?
From 2010 for my first EP Akme “Ultimatum EP’’
What are some of the mediums you have used to distribute your music?
Distrokid from 2015, Bandcamp too, but now with different ones, like WavLake.
Have you ever been signed to a label?
Nah
What are some of the main things you see as a problem in today’s music industry?
All the websites and distribution they profit from all the musicians and labels try to use AI for their shit, weird! At this moment, at least, but we gonna change!
What made you decide to join the 2140Music community?
Because the music industry needs to rebuild in the Bitcoin way like we gonna do!!!!
Maybe another one…
What are some of the notable projects you’ve released or people you’ve worked with?
I did a lot of projects this year especially; 'Deafth spazio randagio' with Slippy Skills, Double Capital ‘A’ EP with Airklipz, Hooks Thrown off Deck with Airklipz and Sylva Grey, Roads Eucharist with SWAV’O, Ghostreet and Ghostway with L17 and Airklipz and GADGIE RANDAGI EP exclusive available on Even.biz
-
 @ 2ed3596e:98b4cc78
2025-03-20 22:46:58
@ 2ed3596e:98b4cc78
2025-03-20 22:46:58Bitcoin: The tool of true freedom in an age of control
Let’s talk about control. Not just the kind you see in politics, but the control over what you can say, what you can spend, and ultimately, how you live. It’s creeping into every part of our lives, and if you’re paying attention, you’ve already seen it happen.
Remember the Canadian truckers’ protest? If you donated just $50 and you got bank accounts frozen and all financial access cut off—not because of criminal activity, but because the government at the time didn’t like what you stood for. Look at donations to Palestine — many financial institutions are outright blocking donations to causes supporting folks struggling to survive in Gaza. China? Censorship isn’t just about speech; it’s about access to money, too – completely cutting people off from being able to participate in the economy. Economic strangulation is real and a growing government control tactic.
See the pattern?
It doesn’t matter what your politics are. If you step too far outside the accepted lines, you’ll be cut off. Your money is no longer yours if someone else can decide when you can access it.
The playbook isn’t new — just look at 1933
If you think this level of control is new, think again. In 1933, Executive Order 6102 forced Americans to hand over their gold to the government—under threat of fines and jail time. Why? Because gold was real money, and the government wanted to control the monetary system to finance its growth in spending and services. Gold, at this time, was $35 an ounce. Today it is worth thousands per ounce. The dollar, meanwhile, has lost 99% of its value in that same period.
Then came 1971. Nixon took the U.S. off the gold standard completely, meaning the dollar was no longer backed by anything tangible. Since then, the government has printed money at will, inflating the currency and making everything more expensive over time.
And yet, we’re supposed to trust this system?
Fiat is just a fancy word for "because we said so"
Our money is no longer tied to gold or anything of value. Fiat money has value simply because governments say it does. But history proves that this system is built on a lie. The more they print, the less your money is worth. It’s not about “helping the economy” or “fighting inflation”—it’s about making sure you stay dependent on the system. And when people get too self-sufficient? That’s when they start pulling tricks like EO 6102.
Bitcoin fixes this.
Bitcoin is E.O. 6102-proof
Governments can seize gold. They can freeze your bank accounts. They can tell you what you can and can’t spend money on.
But they cannot control Bitcoin.
Bitcoin is money that exists outside of their system. It can’t be inflated away. It can’t be seized by decree. It allows people to transact freely, regardless of politics, geography, or financial status. Whether you’re protesting in Ottawa, donating to survivors in Palestine, or living under Chinese financial surveillance—Bitcoin is the escape hatch.
“I consume, therefore I am”
Freedom isn’t just about what you can say—it’s about what you can do. If your ability to transact is controlled, then your ability to live freely is controlled. Bitcoin is the tool that breaks those chains.
It’s not just an investment. It’s not just “digital gold.” It’s a lifeline. It’s the difference between having control over your future or waiting for the next decree to tell you what you can do with your own money.
Governments will always try to tighten their grip. History proves it. But Bitcoin gives you the power to break free. The question is: will you use it?
-
 @ 878dff7c:037d18bc
2025-03-20 21:39:38
@ 878dff7c:037d18bc
2025-03-20 21:39:38JFK Assassination Files (Special brief)
Summary
The consensus among researchers and media is cautious optimism mixed with skepticism. The files offer a treasure trove of operational minutiae—spycraft, JFK’s CIA friction, Oswald’s movements—but no game-changer has emerged in the 72+ hours since release. Attention is shifting to the unreleased FBI and IRS records, with speculation that their declassification could clarify lingering questions. For now, the story remains one of incremental insight rather than revelation.
1. CIA's Surveillance of Lee Harvey Oswald Prior to Assassination
Newly declassified documents reveal that the CIA closely monitored Lee Harvey Oswald's activities before President Kennedy's assassination. Unredacted testimony from James Angleton, the CIA's chief of counterintelligence, provides deeper insight into the agency's surveillance operations concerning Oswald, particularly during his time in Mexico City, where he contacted the Soviet and Cuban embassies. Despite this surveillance, the CIA did not act to prevent the assassination, raising questions about the agency's internal communication and assessment processes.
2. Oswald's Interactions with Soviet Officials Scrutinized
The declassified files shed light on Oswald's interactions with Soviet officials during his visit to the USSR. According to KGB records, Oswald was closely monitored but was not recruited as an agent. These revelations provide a clearer understanding of Oswald's activities and the extent of Soviet intelligence's involvement with him, countering longstanding speculations about his ties to the USSR.
3. Prior Warning of Oswald's Intentions
A newly revealed letter indicates that months before the assassination, a tip-off about Oswald's plan to kill President Kennedy was received but not adequately acted upon. This raises concerns about potential intelligence failures and missed opportunities to prevent the tragic event.
4. President Kennedy's Consideration to Dismantle the CIA
The documents reveal that President Kennedy contemplated dismantling the CIA following the Bay of Pigs fiasco, referring to it as a "state within a state." This underscores the tension between the Kennedy administration and the intelligence community during that period.
5. Use of USS Potomac by Anti-Castro Paramilitaries
The declassified files disclose that the USS Potomac, formerly President Franklin D. Roosevelt's yacht, was later utilized by anti-Castro paramilitary groups. This highlights the covert operations undertaken during the Cold War era and the U.S. government's involvement in efforts to destabilize the Castro regime in Cuba.
6. Gary Underhill's Allegations Against the CIA
The documents bring to light the case of Gary Underhill, a former intelligence officer who alleged that the CIA was involved in illicit activities. Underhill was later found dead under suspicious circumstances, fueling further speculation about internal conspiracies within the intelligence community.
7. Australian Intelligence's Involvement in the Investigation
Newly released files reveal that Sir Charles Spry, the head of the Australian Security Intelligence Organisation (ASIO), lobbied to keep certain documents related to the assassination investigation confidential. This indicates international dimensions to the investigation and the sensitivity surrounding the information at the time.
Sources The Times - March 21, 2025\ Al Jazeera - March 20, 2025\ National Archives - March 18, 2025\ News.com.au - March 21, 2025
Significant Employment Drop in February; Unemployment Rate Steady
Summary:
Australia experienced an unexpected decline in employment, with 53,000 jobs lost in February, primarily due to older workers retiring and a decrease in female workforce participation. Despite this, the unemployment rate remained steady at 4.1%, largely because of a drop in the participation rate. Analysts suggest that recent tax cuts, interest rate reductions, and wage growth may have eased household budgets, reducing the need for some to seek employment. The Reserve Bank of Australia (RBA) is monitoring these developments but is not expected to implement another interest rate cut immediately. Sources: News.com.au - March 21, 2025, The Australian - March 21, 2025, ABC News - March 20, 2025
Tropical Cyclone Courtney Forms Near Cocos Islands, Marking Intense Cyclone Season
Summary:
Tropical Low 25U near the Cocos Islands has intensified into Tropical Cyclone Courtney. Meteorologists predict that while the system may struggle to maintain cyclone status, it will still bring gusty winds, squally showers, and thunderstorms to affected areas. This development marks the potential tenth cyclone since December, indicating one of the busiest cyclone seasons in 19 years if three more cyclones occur by the end of April. Residents in the path of the cyclone are advised to stay updated with the latest weather information and prepare for possible severe weather conditions. Sources: News.com.au - March 21, 2025
Australia's Population Growth Sparks Migration Policy Debate
Summary:
Australia's population grew by 484,000 (1.8%) over the past year, primarily due to natural births and net overseas migration. This surge has ignited political debates on migration policies. Prime Minister Anthony Albanese aims to reduce net migration to 250,000 by mid-2025, while Opposition Leader Peter Dutton advocates for a 25% cut in permanent migration and stricter caps on international students. Experts argue that skilled migration boosts the economy, but housing shortages linked to migration remain a pressing issue. Sources: News.com.au - March 21, 2025
NSW Premier Chris Minns Admits Need for Accelerated Reforms
Summary:
Marking two years in office, NSW Premier Chris Minns acknowledges his administration's slow progress on key promises, particularly in housing and economic reforms. While crises like natural disasters have been well-managed, significant advancements are lacking. Minns aims to expedite housing approvals to meet a target of 75,000 new homes and improve the budget, though challenges like debt reduction and infrastructure delays persist. Sources: The Daily Telegraph - March 21, 2025
Coalition Proposes Legislated Biosecurity Funding
Summary:
At the Northern Territory Cattlemen's Association Conference in Darwin, National Party Leader David Littleproud announced a policy to legislate minimum biosecurity funding of approximately $900 million. This measure aims to combat diseases like Lumpy Skin Disease and Foot and Mouth Disease, which could have severe economic impacts. The proposal includes introducing an Import Container Levy to ensure that importers, rather than Australian farmers, bear the costs. The Northern Territory Cattlemen's Association has expressed support for this sustainable funding approach.
Sources: The Courier-Mail - 21 March 2025
EU Leaders Convene to Address Global Challenges
Summary:
On March 20-21, 2025, European Union leaders met in Brussels to discuss pressing global issues, including economic competitiveness, security, and climate change. A working lunch with United Nations Secretary-General António Guterres focused on multilateralism and strengthening global cooperation. The summit underscored the EU's commitment to addressing international challenges through unified strategies and reinforced partnerships. Sources: European Parliament - March 20, 2025
Geopolitical Tensions Rise in the Arctic Region
Summary:
Recent analyses indicate that the Arctic is increasingly becoming a focal point of geopolitical rivalry. The region is now divided between a NATO-aligned Arctic, led by the United States, and a Russian Arctic seeking cooperation with BRICS+ countries. This division reflects broader global tensions between the US/NATO and Russia/China, heightening the risk of conflict and underscoring the need for diplomatic engagement to manage Arctic affairs. Sources: High North News - March 19, 2025
Royal Adelaide Hospital's Infectious Diseases Unit Relocation Sparks Concerns
Summary:
Doctors and nurses have raised concerns that patient care could be compromised if the South Australian government proceeds with plans to relocate the infectious diseases unit from the Royal Adelaide Hospital to a new location across North Terrace. Health unions have taken the dispute to the SA Employment Tribunal, arguing that the move could result in compromised clinical care and patient safety due to the separation from specialist doctors at the main hospital. The government cites cost considerations as the main driver for the relocation decision. Sources: ABC News - March 20, 2025
Inspirational Stories of Young Australians Overcoming Adversity
Summary:
The ABC Heywire competition recognized 38 young Australians from regional, rural, and remote areas for their inspiring stories of resilience and determination. Winners, aged 16 to 22, shared experiences highlighting life outside major cities. For instance, Blake from Casino detailed enduring severe drought on his family's farm, while Mayada from Coffs Harbour recounted her escape from child slavery during the Yazidi genocide, ultimately finding refuge in Australia. These narratives showcase the diverse and resilient spirit of young Australians committed to inspiring positive change in their communities. Sources: The Daily Telegraph - March 21, 2025
Calls for Strengthened ANZAC Cooperation Amid US Retrenchment and China's Rise
Summary:
China's growing military assertiveness, exemplified by live-fire naval exercises in the Tasman Sea, contrasts with the US's reduced global security commitments under President Trump, creating insecurity for traditional allies, Australia and New Zealand. Recent provocations and new strategic partnerships in the Pacific by China have exposed vulnerabilities in the defense capabilities of both countries. With the American security guarantee becoming unreliable, Australia and New Zealand must enhance their own military capacities and deepen bilateral and regional defense cooperation. Enhanced joint military operations and defense procurements, particularly focusing on air and maritime security, are critical. Forming new alliances with other regional powers, such as Japan, South Korea, and India, could also help address strategic gaps. This period demands a rejuvenated ANZAC cooperation to ensure both countries' security and stability in the changing geopolitical landscape. Sources: The Australian - 21 March 2025
More Extreme Weather Events Expected Across Australia
Summary:
Australia has experienced higher-than-average temperatures and numerous extreme weather events this season, including heatwaves, bushfires, floods, and cyclones. December, January, and February set records as some of the warmest months, contributing to an overall temperature rise of 1.9°C above average. Canberra's daytime temperatures are now 2.5°C higher compared to the early 1970s. Ex-Tropical Cyclone Alfred caused severe damage with strong winds and heavy rainfall, affecting over 300,000 homes. Bushfires in Victoria and Tasmania burned significant areas, while dry lightning in South Australia ignited 100 fires. Extreme weather is forecasted to continue into autumn with persistent heat and potential for further tropical cyclones, storms, and heavy rains. Climate change is driving these conditions, prompting calls for increased preparation and mitigation efforts. Measures include reducing emissions through lifestyle changes and improving emergency preparedness for weather events. Sources: The Daily Telegraph - March 21, 2025, The Courier-Mail - March 21, 2025
The Speaking Coach: The One Word All Liars Use! Stop Saying This Word, It's Making You Sound Weak! The More You Do This, The More You Sound Like A Liar!
Summary:
In this episode of "The Diary Of A CEO with Steven Bartlett," the focus is on effective communication and the subtle cues that can undermine credibility. The guest speaker, a seasoned speaking coach, discusses common verbal habits that can make individuals appear less trustworthy or confident. Key points include:
- Identifying Weak Language: Highlighting specific words and phrases that convey uncertainty or lack of conviction.
- Building Authority: Techniques to project confidence and authority in speech.
- Recognizing Deceptive Signals: Understanding verbal indicators commonly associated with dishonesty.
The episode provides practical advice for enhancing communication skills, making it valuable for professionals and anyone interested in personal development.
Sources: The Diary Of A CEO with Steven Bartlett - March 21, 2025
-
 @ 7d33ba57:1b82db35
2025-03-20 20:42:33
@ 7d33ba57:1b82db35
2025-03-20 20:42:33El Teide
Mount Teide (El Teide) is the highest mountain in Spain (3,715m) and the third-highest volcanic structure in the world. Located in Teide National Park (a UNESCO World Heritage Site), it offers breathtaking landscapes, hiking trails, and stunning panoramic views** over the Canary Islands.
🏔️ Best Things to Do at Mount Teide
1️⃣ Hike to the Summit
- The most rewarding way to reach the top! The hike starts from Montaña Blanca and takes about 5-6 hours.
- Permit required for the final ascent (apply in advance).
2️⃣ Take the Teide Cable Car
- A quick way to reach 3,555m, with spectacular views.
- From the upper station, you can hike to La Fortaleza Viewpoint or Pico Viejo Viewpoint for stunning island views.
3️⃣ Stargazing at Teide Observatory
- One of the best stargazing spots in the world due to its clear skies and high altitude.
- Join an astronomy tour for an unforgettable night experience.
4️⃣ Explore the Teide National Park
- Walk through lava fields, craters, and rock formations like Roques de García.
- Visit the Visitor Center to learn about the park’s geology and history.
🚗 How to Get to Teide
🚗 By Car: ~1.5 hours from Santa Cruz or Costa Adeje
🚌 By Bus: Titsa buses 342 (from Costa Adeje) & 348 (from Puerto de la Cruz)💡 Tips for Visiting Teide
✅ Book summit permits early – Limited spots available! 🎟️
✅ Dress warmly – Temperatures drop at high altitude, even in summer 🧥
✅ Best time to visit? Sunrise, sunset, or night for amazing views 🌅🌌
✅ Take it slow – The high altitude can affect breathing ⛰️ -
 @ a296b972:e5a7a2e8
2025-03-20 19:36:34
@ a296b972:e5a7a2e8
2025-03-20 19:36:34Diagnose:
Der aufgelöste Bundestag verschuldet die Insassen eines Landes namens Absurdistan in schwindelerregender Höhe durch einen noch nicht gewählten Bundeskanzler, der vormals wohlmöglich Werbung für Gewürzgurken gemacht hat, unter Zuhilfenahme von Parteien, die abgewählt wurden. Eine Sperrminorität konnte nicht entstehen, weil sie sonst verhindert hätte, dass die Wahlversprechungen nicht hätten gebrochen werden können. (Geht gar nicht!)
Genau so gut, hätte der letzte deutsche Kaiser eine Sektsteuer erheben können, um die deutsche Marine aufzurüsten. (Ach so, ja, ist schon gut, hatten wir schon, hatte ich vergessen.)
In Rumänien und Serbien sind Demokraten zu Hunderttausenden auf der Straße, und Deutschland hat Kellerwoche (Schade eigentlich!).
In Erstverschlimmerung löst die aktuelle Situation das blanke Entsetzen aus, doch auf den zweiten Blick stellt sich das Ganze durchaus als sehr positiv dar. Heilung ist möglich, doch vorher kommt der Schmerz:
Die Neuverschuldung ist nämlich eine provisorische Abschreckung für den Russen, der dann doch lieber so lange wartet, bis Deutschland in 10 bis 20 Jahren wirklich aufgerüstet hat. Wer kämpft schon gerne gegen jemanden, der sich nur maximal 2 Tage verteidigen kann? Das macht doch keinen Spaß. Da lohnt sich doch der ganze Aufwand nicht. Bis dahin hat Deutschland leider nichts, außer Schulden. Von Windrädchen und Zufallsstrom und einer innerlich, aber eben nur sehr innerlich, rebellischen Bevölkerung mal ganz abgesehen.
Es geht hoffnungsvoll weiter. Mit Frau von der Leyen haben wir als EU-Kommissarin bereits eine Deutsche in Brüssel, die sich schon vor ihrer zweiten Einsetzung ohne demokratische Mittel, in bundesstaatlichen Pöstchen durch ihre mangelnde Qualifikation besonders herausragend ausgezeichnet hat.
Statt einer qualifizierten, sich verdient gemacht habenden Diplomatin namens Frau Dröge, soll nun als weitere "deutsche Konifere" auch Frau ver Baerbock-t als UN-Generalsekretärin der UN-Generalversammlung hochgelobt und eingesetzt werden. Auf die Frage von Herrn Warweg in der Pressekonferenz-Show, warum denn nun Frau Baerbock qualifizierter sei, als Frau Dröge, wusste sich der Sprecher Herr Hebestreit wie immer galant durch nichts sagende Textbausteinabsonderungen aus der Schlinge zu ziehen. Vermutlich wollte er Frau Dröge nicht kompromittieren, weil er sonst hätte sagen müssen, dass ja Frau Baerbock viel besser Trampolin springen kann, als sie. Kavalier ist er ja, da gibt es nichts gegen zu sagen.
Mit Frau Baerbock hätte Deutschland eine weitere Deutsche installiert, die dem Ansehen Deutschlands in der Welt, in Fortsetzung ihres Amtes als Außenfeministin, nahtlos weiterhin den maximalen Schaden zufügen könnte.
Weiter wird gemunkelt, dass Herr Habeck für die Darstellung des Bundespräsidenten zur Disposition steht. Mit Märchen kennt er sich aus, insofern wäre er ein würdiger Nachfolger des Streubomben-nicht-Verhinderers. Auch Herr Habeck wird durch seine oft genug bewiesene Expertise in Insolvenz und Wirtschaftsvernichtung Deutschland nach außen hin in bester Weise repräsentieren. Als braver Bürger kann man sich keinen besseren Schwiegermutter-Liebling vorstellen. Und wie der sich ausdrücken kann, hach, einfach nur nett!
Die Aufteilung der Grünen in Außen und Wirtschaft war somit absolut sinnvoll. Schließlich kommt Frau Baerbock ja mehr vom Haarspray und Herr Habeck mehr so vom Shampoo.
Und wenn wir schon mal bei der Verteilung von neuen Pöstchen sind, dann sollte man Herrn Scholz als neuen Chef für den Bundesnachrichtendienst vorschlagen. Verschwiegen ist er, Geheimnisse kann er bewahren. Wie Staatsgeheimnisse nicht an die Öffentlichkeit gelangen, damit kennt er sich aus. Nordstream 2 wurde nämlich von den Deutschen selbst in die Luft gejagt, als Selbstgeißelung für den angerichteten Schaden im 2. Weltenbrand. Er wollte einfach Teile der Bevölkerung nicht verunsichern, auch, wenn die Idee nicht von ihm ist.
Und Herr Lauterbach sollte in die Wissenschaft wechseln und dort einen neuen Lügendetektor entwickeln, mit dem man Fake-News problemlos entlarven kann. Wie lügen geht, weiß er ja von allen am allerbesten. Und wenn es wirklich mal eng werden sollte, kann er ja Berater zur Hilfe nehmen. Vielleicht haben Herr Drosten oder gar Herr Fauci (ital. la fauci = das Maul) Zeit ihn bei dieser wertvollen Arbeit zu unterstützen.
Warum also ist das jetzt alles positiv?
Mit diesen Kapazitäten wären Deutsche an exponierter Stelle installiert, um das ideologische Gift in die EU, in die UN und weltweit hinein zu träufeln.
Innerdeutsch werden sich sicher Herr Bäcker, der Mann mit den unglücklichen Initialen, Frau Düsseldorf-Rheinmetall, Herr Kriegsgewitter u. a. auch weiterhin zur Verfügung stellen, die Kriegstüchtigkeit ihrer Vollendung entgegen zu führen. Wohlwollend beobachtet durch die USA und Russland. Das wäre dann Inklusion, oder sagt man Implosion?
Dann werden auch noch als erstes von den Billionen Sonderschulden mobile Vermögenswerte in Form von Vorschlaghämmern angeschafft, mit denen die Schweine der deutschen Sparer geschlachtet werden sollen. Frau Lagarde hat sich schon bereit erklärt, hier mit Einführung des digitalen Euro demnächst helfend zur Seite zu stehen.
Alles wirklich molto bene, Heilung ist nahe!
In Zusammenwirken all dieser Kräfte und Kapazitäten für Deutschland und Europa, wird auch noch die deutsche Gesellschaft die Grätsche machen und dann ist Deutschland völlig bettlägerig und darnieder. Deutschland hat bald fertig!
Und hat Deutschland, als größter Geldgeber der EU fertig, hat auch die EU fertig, ihr geht dann einfach die Puste aus. Und vielleicht warten schon Ungarn und einige andere Mitgliedsstaaten nur auf eine günstige Gelegenheit, der EU für lange Zeit Adieu zu sagen?
„Wenn wir uns wiedersehen, werden wir uns freuen, wenn nicht, war der Abschied wohlgetan!“
Und mit ganz viel Glück geben die USA Europa dann auch noch den Gnadenstoß und erlösen die europäischen Staaten von dem Übel namens EU, da sie offensichtlich selbst nicht in der Lage sind, sich aus ihrer Bevormundung mit betreutem Denken und einem Wahrheitsministerium zu befreien. Die NATO wackelt ja auch schon.
Genesung:
Anschließend gibt es für alle Bürger Europas, aber besonders für Deutschland, einen Pflichtkurs in der Volkshochschule in Sachen Frieden, Demokratie und Freiheit. Vielleicht klappt es dann dieses Mal, aus Denkschnecken Schachweltmeister zu machen. Oder wenigstens aus Langzeitkomatösen Leute mit Wachbewusstsein.
Nochmals, alles in bester Ordnung. Es muss erst noch schlimmer werden, bevor es wieder besser wird. Bei dem Tempo, dass die europäischen Universal-Dilettanten derzeit an den Tag legen, wird das nicht sehr lange dauern.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 6f0a6a19:7dd662db
2025-03-20 19:00:46
@ 6f0a6a19:7dd662db
2025-03-20 19:00:46BitBonds
The idea, initially proposed by Newmarket Capital CEO Andrew Hohns at the Bitcoin Policy Institute’s “Bitcoin for America” conference, is that Congress could defease the federal debt and cut long-term interest rates by approving a new debt instrument collateralized with Bitcoin—BitBonds.
How It Works:
- For every $100 BitBond issued, $10 would buy Bitcoin for the U.S. Strategic Reserve.
- Bondholders would receive 1% annual interest (lower than traditional Treasuries) and 50% of BTC price appreciation.
A New Bitcoin Standard
At first glance, BitBonds is an innovative way to increase demand for U.S. Treasuries without Federal Reserve intervention while lowering borrowing costs. However, this instrument would signal a radical change in monetary policy.
A 4000-year precedent
Money (as a visual measure of credit) has been and is always socially constructed through a stable exchange ratio.
- Money didn’t appear in ancient Sumer until priests and palace administrators set rates between standard weights of grain and silver on palace-authorized cuneiform tablets.
- In Egypt, money was constructed through economic administrators (related to the king) setting common rates between an abstracted standardized 92 gram copper weight measurement called a Deben and grain.
- Roman and Greek mints fixed ratios and weights between precious metals to establish official coinage and stabilize their value.
- The U.S. established its first currency through a bi-metallic standard, fixing gold and silver rates via the U.S. Mint.
- The modern U.S. monetary system issues its currency on a promise to redeem $100 for $100 + 2% interest.
U.S. government debt became the default monetary exchange rate the moment Nixon suspended gold redemption in 1971. It was the only remaining promised ratio of exchange attached to the US Dollar. Each year, Congress votes to extend this debt-based system by approving the federal budget. And the Federal Reserve then manages the levers of bond prices and yields through open market operations. There is no other federal mechanism for securing universal interest in the dollar, than the interest paid from its debt.
With BitBonds collateralizing 10% of each issuance in Bitcoin, the government would effectively introduce a new promised ratio of exchange to US monetary policy. It would promise to redeem 10 cents of every $1 in this lending program for bitcoin (half for the reserve and half of its appreciated value for the holder). This promise would transition US monetary policy from a pure debt based system to a new implicit exchange rate between Bitcoin and the U.S. dollar.
How BitBonds Would Drive Bitcoin to $10 Million
- First, BitBonds promises unlimited buying pressure on a finite asset. (The government can perpetually issue more BitBonds to acquire Bitcoin.) That, combined with the fact that Treasuries are the world’s primary liquidity engine, would generate unprecedented demand for Bitcoin reserves.
- Second, unlike previous reserve assets like gold, Bitcoin’s indivisibility prevents fractional redemption. This network constraint prevents the government from redeeming less than 1 satoshi (the base unit of Bitcoin) for 10 cents, thereby setting a clear price target for the market. Promising to collateralize 10% of each bond with bitcoin is like priming the pump for max buy pressure, fixing a target price and pulling the trigger.
- Investors would front-run the Treasury’s buying spree with that target in mind and in a matter of time 1 satoshi will equal $0.10 ($10M per BTC).
- At $10M per BTC, Bitcoin’s total valuation would reach $210 trillion—a figure capable of servicing the $189 trillion in global U.S. debt obligations and backing the $21 trillion M2 money supply. This valuation would prime bitcoin to become the world reserve asset backing the world reserve currency (a digital dollar).
- After this transformation, the government would have the precedent to institute a more explicit system of regulating bitcoin and digital dollar redemption. You can learn more about what this system would look like in my thesis for why technocratic government agencies will inevitably use bitcoin to create a cashless digital society: The Anarchist’s Guide to Cashing out of the Matrix.
Why Market Resistance Will Fail
- Selling Bitcoin into a U.S. Treasury buy wall would be a losing trade. A continuous government buyer would absorb any attempt to suppress BTC’s price.
- Foreign governments would be compelled to adopt or lose financial leverage. If the U.S. redefines sovereign debt through Bitcoin, foreign central banks must accumulate Bitcoin or face economic devaluation.
- The Federal Reserve would have no choice but to accommodate Bitcoin-backed Treasuries. If BitBonds reshape U.S. debt issuance, the Fed must either integrate them into monetary policy or risk disrupting Treasury markets.
The short path to a $10 million bitcoin
- The U.S. Treasury launches BitBonds, requiring Bitcoin collateral equal to 10% of each issuance.
- Bitcoin markets recognize that the U.S. government is a continuous net buyer.
- Investors front-run this signal, accelerating Bitcoin accumulation.
- Institutional demand propels BTC to the $10M target, exponentially increasing the value of the SBR.
- Once 1 satoshi = $0.10, the federal government will have a stockpile of bitcoin valued at a cost basis greater than its annual debt obligations.
- Rather than use the stockpile to pay the debt down, the government will find that it needs to enforce a new surveillance-enforced bitcoin redemption policy to maintain a funnel of public bitcoin to the SBR in return for surveillable stablecoins. (read thesis for more)
Bitcoin’s Supply Guarantees a Stable Transition
Unlike gold, Bitcoin’s supply is fixed, transparent, and auditable. Once repricing begins, sovereign wealth funds, pension funds, and financial institutions will be forced to accumulate Bitcoin, play by the new state-issued redemption rules or be left behind.
I'm not sure how long it would take for the market to figure this out, but I’d assume it would be an all-out sprint to $10M BTC once the cat is out of the bag.
-
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 4fe14ef2:f51992ec
2025-03-20 17:39:26
@ 4fe14ef2:f51992ec
2025-03-20 17:39:26Hey Bitcoiners,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or digital, #product or #service.
Just share below what you’ve listed, #swap, and #sold. Let everyone rave on your latest #deals!
New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny #BTC!
originally posted at https://stacker.news/items/919107
-
 @ 000002de:c05780a7
2025-03-20 17:07:00
@ 000002de:c05780a7
2025-03-20 17:07:00Its easy to get caught up in media stories and not stop and ask basic questions. One I've had from the start is how widespread are these attacks on the private property have occurred.
If the goal is to hurt Tesla and therefore Musk, then the media stories are the real goal. Not the actual destruction of property. We know from history that many stories get blown out of proportion. I have no doubt that these events are actually happen but I wonder if the number of events has been counted.
originally posted at https://stacker.news/items/919063
-
 @ b76ecc31:3472e544
2025-03-20 16:39:34
@ b76ecc31:3472e544
2025-03-20 16:39:34Hey guys, we started a self custody Lightning wallet service, which optimized for businesses. We built it thanks to LNBits which we are currently optimizing it for Breez SDK as main funding source.
We are currently in private beta, so if you have the need for using Lightning self custody for your business, ping me and I will set you up.
more info: tidebinder.com
originally posted at https://stacker.news/items/919036
-
 @ e968e50b:db2a803a
2025-03-20 15:59:49
@ e968e50b:db2a803a
2025-03-20 15:59:49I just wrote up a whole essay about this great movie scene, my extended thoughts on this post, and bitcoin hipsterism at large. However, it was rambly and I'm not sure if anyone would have gotten anything out of it. That said, I'd love to share this clip with y'all as I think it may prove an interesting thought/discussion piece for those contemplating bitcoin hipsterism, either as an increasingly disillusioned practitioner or as an annoyed external observer.
https://www.youtube.com/watch?v=vUgs2O7Okqc&t=12s
originally posted at https://stacker.news/items/918979
-
 @ 16f1a010:31b1074b
2025-03-20 15:29:42
@ 16f1a010:31b1074b
2025-03-20 15:29:42What is NSSM?
NSSM (Non-Sucking Service Manager) is a free tool that allows you to install and manage any application as a Windows service. This is particularly useful for applications that don't natively support running as a service, ensuring they start automatically when your system boots and continue running in the background.
Downloading NSSM
- Visit the official NSSM website: https://nssm.cc/
- Download the latest stable release.
- Extract the downloaded ZIP file to a directory of your choice (e.g.,
C:\nssm).
Adding NSSM to Your PATH (Recommended)
Adding NSSM to your system's PATH environment variable allows you to run
nssmcommands from any command prompt window.- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."

- In the "System Properties" window, click the "Environment Variables..." button.
- In the "System variables" section, find the "Path" variable and click "Edit."
- Click "New" and add the path to the directory where you extracted NSSM (e.g.,
C:\nssm). - Click "OK" on all open windows to save the changes.
- Open a new command prompt window and type
nssm --version. If NSSM is correctly added to your PATH, you should see the version information.
Using NSSM: Installing a Service
- Open a command prompt as administrator.
- Type
nssm install <service_name>and press Enter. Replace<service_name>with the name you want to give to your service. - A GUI will appear, allowing you to configure the service.
- In the "Path" field, enter the full path to the application's executable.
- In the "Startup directory" field, enter the directory containing the executable.
- Configure any other options as needed, such as "Arguments," "I/O," or "Details."
- Click "Install service."
Example:
bash nssm install MyGrainRelayConclusion
Congratulations, you now have NSSM installed and know the basics of using it to manage windows services. Check my profile for more technical guides on various topics, and stay tuned for more guides.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 16d11430:61640947
2025-03-20 23:07:01
@ 16d11430:61640947
2025-03-20 23:07:01A Tale of Two Dysfunctional Kingdoms
In the grand theater of human organization, we are blessed with two great economic orders: Fiat, the Land of Fragile Giants, and Crypto, the Padded Madhouse of Infinite Lunacy. Both promise utopia, both deliver dysfunction, and both operate under the iron law that those with the most power will always act in their own interests—rules be damned.
The Fiat Intellectual Landscape: A Game of Tiptoeing Giants
The fiat world is a meticulously curated bonsai garden of decorum and quiet panic. Giants walk among us—CEOs, central bankers, hedge fund wizards, and the occasional Nobel Prize-winning economist—but they must step lightly, lest they shake the delicate equilibrium. The entire system is built on confidence, a polite euphemism for narrative control.
Take any major institution, and you'll find the same pathology:
Corporations: The larger they are, the more fragile their balance sheets, requiring constant PR therapy and quarterly ritual sacrifices to appease the gods of Wall Street. CEO statements are more rehearsed than Shakespearean soliloquies, lest a slip in language shaves billions off the stock price.
Academia: Intellectual giants must wade through a swamp of bureaucratic grant-seeking, where discovery is secondary to institutional survival. Challenging economic orthodoxy is career suicide, so best to publish another paper on "inclusive finance" while hedge funds strip-mine the economy.
Government & Central Banks: A crisis is just another reason to print more money, kick the debt can down the road, and assure the public that everything is “transitory.” Behind closed doors, they know it’s a rigged game—but stability must be maintained at all costs, even if it means bribing the peasants with stimulus checks to keep the illusion alive.
The entire fiat ecosystem is one of quiet desperation, where the powerful pretend to be cautious stewards of civilization while looting with the finesse of seasoned art thieves. Stability is paramount, because if the masses ever realized the whole thing is a confidence scam, they might actually ask questions.
Crypto: The Padded Madhouse Where Giants Go to Break Things
Meanwhile, in the Crypto Madhouse, giants don’t tiptoe—they run, scream, and occasionally set the entire house on fire just to see what happens. Here, there is no caution, no equilibrium—just a perpetual state of mania, where even the most outlandish ideas get venture funding. If fiat is an over-engineered glass palace, crypto is a playground for unhinged capitalists and techno-anarchists armed with flamethrowers.
The dysfunction here is less about fragility and more about unregulated chaos:
Ponzi Chains Masquerading as Innovation: Every year, a new "Ethereum Killer" promises to decentralize everything, only to collapse into an infighting mess of VC dumps, network outages, and sudden governance takeovers. If in fiat, failures happen in slow motion, in crypto, they happen overnight, in a Discord announcement at 3 AM.
Decentralization Theatre: Most "community-governed" projects are run by an inner circle of early whales who have more control than the Federal Reserve, but pretend it's democratic because they let the plebs vote on logo designs. The difference? Fiat oligarchs hide their power; crypto oligarchs post memes about it.
The Cult of the Visionary Founder: While fiat leaders pretend to be humble, crypto founders take the stage like prophets descending from the blockchain, dropping whitepapers with the same fervor as religious scriptures. And when they inevitably fail, they simply launch a new token, because failure only exists if you stop grifting.
Crypto may lack the institutional fragility of fiat, but in its place, we get wild, unchecked power, where insiders can rug-pull billions without consequence. The only real difference? Instead of bailing out banks, crypto just moves on to the next hype cycle.
Same Vested Interests, Different Scams
In the end, both systems operate under the same fundamental law: those with the most power will always find a way to keep it.
In fiat, the illusion of stability is paramount, so the powerful must lie in slow motion.
In crypto, the illusion of innovation is paramount, so the powerful must rug in high-speed.
The giants of fiat must walk lightly so as not to disturb the herd; the giants of crypto can rampage freely, because the casino always reopens. Either way, the little guy always pays the bill.
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ a396e36e:ec991f1c
2025-03-20 14:11:02
@ a396e36e:ec991f1c
2025-03-20 14:11:02Introduction
The term Clown World is a meme that reflects the perception that the current system operates in an absurd, corrupt, or irrational manner. In this context, many Bitcoin enthusiasts see it as a tool to escape from Clown World. Bitcoin emerged in 2009, following the 2008 global financial crisis, as an alternative to a traditional monetary system that many consider unjust, inefficient, and prone to manipulation. This article explores how Bitcoin challenges existing economic structures, embodies philosophical principles such as decentralization and financial sovereignty, and serves as a political tool against failing monetary policies. We will also examine the historical evolution of Bitcoin’s narrative in relation to escaping Clown World.
Economic Perspective: Challenging Traditional Monetary Structures
From an economic standpoint, Bitcoin directly challenges the traditional monetary system, which many Bitcoin advocates see as part of Clown World. Fiat currencies, issued by central banks, can be devalued through expansionary policies, leading to inflation, bank bailouts, and resource misallocation that deteriorate economies and social structures. Bitcoin was explicitly designed as a response to these issues: its genesis block, mined on January 3, 2009, contained the message "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks," referencing government bailouts of failing financial institutions. This message signaled Bitcoin’s intent to offer a solution to what was perceived as a broken financial system and irresponsible economic policies.
Unlike fiat money, which can be expanded at the discretion of central authorities, Bitcoin has a predictable and non-manipulable monetary policy. Its issuance follows an algorithmic schedule: the total supply is capped at 21 million coins, ensuring scarcity and practically eliminating long-term inflation. Every four years, a halving event reduces the number of new bitcoins entering circulation, contrasting sharply with central banks’ inflationary targets of around 2% per year. In Bitcoin, no one can arbitrarily “print” more money or devalue existing units, as “there is no central authority” making such decisions. As analyst Anthony Pompliano put it: “Bitcoin is censorship-resistant money. No one can stop you from sending it. No one can confiscate it without your permission. No one can debase the currency.” In other words, Bitcoin functions as digital gold, immune to political dilution, challenging the very foundation of inflationary fiat money.
This economic model—often associated with the idea of “sound money”—represents a separation between money and the state. Many Bitcoin proponents argue that a broken monetary system is at the root of the dysfunctions of Clown World. As Bitcoin advocates Knut Svanholm and Luke de Wolf put it: “When money stops working, everything becomes political and turns into a farce.” Bitcoin, by replacing trust in financial authorities with trust in cryptographic code, aims to correct these distortions. It allows individuals and communities to opt out of the traditional system, securing themselves against inflation and reckless monetary policies.
Philosophical Perspective: Decentralization, Financial Sovereignty, and Resistance to Manipulation
From a philosophical perspective, Bitcoin embodies principles of decentralization, individual sovereignty, and resistance to manipulation, offering an alternative to perceived systemic corruption and control. Unlike traditional money, Bitcoin is a decentralized digital currency that “does not rely on any central authority but operates through a mathematical protocol and a distributed network of nodes.” This means that no government, bank, or corporation can unilaterally control the Bitcoin network or counterfeit its supply. The blockchain architecture and distributed consensus make Bitcoin a kind of “trust machine”, where the rules are pre-set by transparent algorithms. For the first time in history, digital scarcity combines with total decentralization, creating a monetary system where trust is placed in code rather than authorities.
This foundation enables personal financial sovereignty. Bitcoin users can fully own and control their funds through private keys, redefining monetary property rights by eliminating the need for custodians. In practice, this means that “no one can confiscate it without your permission” as long as the user protects their keys (hence the famous phrase “not your keys, not your coins”). Bitcoin’s sovereignty contrasts with traditional bank accounts, which are vulnerable to freezes, censorship, or devaluation. The philosophy behind Bitcoin promotes independence from state and corporate financial control, much like the historical separation of church and state. As a Bitcoin advocate noted, “By decentralizing financial power and promoting a separation between money and the state,” Bitcoin has the potential to reshape economic power dynamics. Essentially, anyone can become their own bank, transacting globally without requiring permission.
Another key aspect of Bitcoin’s philosophy is censorship resistance and protection from manipulation. In Clown World, institutions can block transactions, exclude individuals from the financial system, or manipulate currency for political purposes. Bitcoin was designed to counteract this. Anyone can transfer Bitcoin to another person directly, without intermediaries who can block transactions. The blockchain's immutability ensures that no one can retroactively alter payment records or falsify balances, reinforcing its freedom-preserving nature.
Recent events highlight this utility: In 2022, when the Canadian government froze bank accounts of protesters and pressured crowdfunding platforms, many pointed out that Bitcoin could bypass such authoritarian measures. As one commentator put it, “Every attempt at financial censorship is free marketing for Bitcoin,” as it underscores its value as unseizable and incorruptible money. This ideology aligns with libertarian and anarcho-capitalist ideals, advocating that individuals—not the state—should have ultimate control over their money and transactions.
Political Perspective: Bitcoin as a Tool of Resistance Against Authoritarianism and Monetary Failures
From a political standpoint, Bitcoin has been used as a form of resistance against authoritarian regimes, state financial controls, and failing monetary policies. Due to its borderless and stateless nature, Bitcoin enables escaping national economic barriers and prevents governments from unilaterally controlling wealth. In countries suffering from hyperinflation or strict currency controls, citizens have turned to Bitcoin to protect their savings.
Venezuela is a key example: Bitcoin is widely used there as a store of value against the endless devaluation of the national currency. Similarly, in Argentina, Bitcoin adoption has surged as people seek to preserve their wealth amidst chronic inflation and restrictions on foreign currency exchange. In these contexts, Bitcoin serves as an escape valve from disastrous economic policies, offering a refuge where the government cannot destroy the value of money through inflation.
Conclusion
Bitcoin is more than just an asset; it is a technological, economic, and philosophical revolution offering an alternative to what many perceive as the dysfunctions of Clown World. By enabling economic sovereignty, censorship resistance, and an escape from inflationary policies, Bitcoin challenges the status quo, providing a viable path toward financial freedom and systemic change.
-
 @ 58537364:705b4b85
2025-03-20 14:03:27
@ 58537364:705b4b85
2025-03-20 14:03:27“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไป
หากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 21335073:a244b1ad
2025-03-20 12:24:16
@ 21335073:a244b1ad
2025-03-20 12:24:16Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7d33ba57:1b82db35
2025-03-20 11:27:54
@ 7d33ba57:1b82db35
2025-03-20 11:27:54Agaete
Agaete is a charming coastal town on the northwest coast of Gran Canaria, known for its stunning cliffs, natural pools, fresh seafood, and rich history. Surrounded by the Agaete Valley, this town offers a mix of nature, culture, and relaxation.
🏛️ Top Things to Do in Agaete
1️⃣ Explore the Agaete Valley (Valle de Agaete)
A lush, green valley famous for its coffee plantations – the only place in Europe where coffee is grown! Take a coffee farm tour and taste local Canarian coffee and wine.
2️⃣ Swim in the Natural Pools of Las Salinas
These volcanic rock pools by the coast provide a unique, sheltered swimming experience with breathtaking ocean views.
3️⃣ Visit Puerto de las Nieves
The picturesque fishing village next to Agaete, where you can enjoy fresh seafood, stroll along the promenade, or catch a ferry to Tenerife.
4️⃣ Hike in Tamadaba Natural Park
Just above Agaete, this stunning nature reserve offers incredible hiking trails with pine forests and breathtaking views of the Atlantic Ocean.
5️⃣ Discover the Necropolis of Maipés
An archaeological site with pre-Hispanic burial mounds dating back over 1,300 years, providing insight into the island’s indigenous history.
🍽️ What to Eat in Agaete
- Pescado fresco – Fresh fish grilled to perfection 🐟
- Cochino negro – A special Canarian black pig dish 🍖
- Queso de flor – Local artisan cheese 🧀
- Agaete coffee & wine – Grown right in the valley ☕🍷
🚗 How to Get to Agaete
🚗 By Car: ~35-40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Agaete
✅ Best time to visit? Year-round, but especially beautiful in spring 🌿
✅ Great for hiking & nature lovers – Bring comfortable shoes 👟
✅ Try local coffee & wine – It’s one of the best-kept secrets of Gran Canaria ☕🍷 -
 @ cff1720e:15c7e2b2
2025-03-20 11:14:33
@ cff1720e:15c7e2b2
2025-03-20 11:14:33Wolfgang Borchert 1947\ (Wolfgang Borchert starb mit 26 Jahren an einer Kriegsverletzung)
Dann gibt es nur eins!
Du. Mann an der Maschine und Mann in der\ Werkstatt. Wenn sie dir morgen befehlen, du\ sollst keine Wasserrohre und keine Kochtöpfe\ mehr machen – sondern Stahlhelme und\ Maschinengewehre, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mädchen hinterm Ladentisch und\ Mädchen im Büro. Wenn sie dir morgen\ befehlen, du sollst Granaten füllen und\ Zielfernrohre für Scharfschützengewehre\ montieren, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Besitzer der Fabrik. Wenn sie dir morgen\ befehlen, du sollst statt Puder und Kakao\ Schießpulver verkaufen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Forscher im Laboratorium. Wenn sie dir\ morgen befehlen, du sollst einen neuen Tod\ erfinden gegen das alte Leben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Dichter in deiner Stube. Wenn sie dir\ morgen befehlen, du sollst keine Liebeslieder,\ du sollst Haßlieder singen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Arzt am Krankenbett. Wenn sie dir\ morgen befehlen, du sollst die Männer\ kriegstauglich schreiben, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pfarrer auf der Kanzel. Wenn sie dir\ morgen befehlen, du sollst den Mord segnen\ und den Krieg heilig sprechen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Kapitän auf dem Dampfer. Wenn sie dir\ morgen befehlen, du sollst keinen Weizen\ mehr fahren – sondern Kanonen und Panzer,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Pilot auf dem Flugfeld. Wenn sie dir morgen\ befehlen, du sollst Bomben und Phosphor\ über die Städte tragen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Schneider auf deinem Brett. Wenn sie\ dir morgen befehlen, du sollst Uniformen zuschneiden,\ dann gibt es nur eins:\ Sag NEIN!\ \ Du. Richter im Talar. Wenn sie dir morgen befehlen,\ du sollst zum Kriegsgericht gehen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Bahnhof. Wenn sie dir\ morgen befehlen, du sollst das Signal zur Abfahrt\ geben für den Munitionszug und für den\ Truppentransport, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mann auf dem Dorf und Mann in der\ Stadt. Wenn sie morgen kommen und dir den\ Gestellungsbefehl bringen, dann gibt es nur eins:\ Sag NEIN!\ \ Du. Mutter in der Normandie und Mutter in\ der Ukraine, du, Mutter in Frisko und London,\ du, am Hoangho und am Mississippi, du,\ Mutter in Neapel und Hamburg und Kairo und\ Oslo - Mütter in allen Erdteilen, Mütter in der\ Welt, wenn sie morgen befehlen, ihr sollt\ Kinder gebären, Krankenschwestern für\ Kriegslazarette und neue Soldaten für neue\ Schlachten, Mütter in der Welt, dann gibt es\ nur eins:\ Sagt NEIN! Mütter, sagt NEIN!\ \ Denn wenn ihr nicht NEIN sagt, wenn IHR nicht nein sagt, Mütter, dann:\ dann:
... Fortsetzung
https://route96.pareto.space/cdd62d02f73eec86bfcaa8108ef515795c6a3c714a418880ea9d267c4aeb1a8d.mp3
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:08:14
@ 20e17dd0:2ae504d7
2025-03-20 10:08:14Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ d5c3d063:4d1159b3
2025-03-20 09:21:42
@ d5c3d063:4d1159b3
2025-03-20 09:21:42📢 "ซื้อหนี้ประชาชน" ทางออก หรือ กับดักเศรษฐกิจ
คุณเคยได้ยินไหม "เป็นหนี้แล้วไม่ต้องจ่าย เดี๋ยวมีคนมาซื้อให้" ฟังดูเหมือนฝันที่เป็นจริงใช่ไหม แต่เดี๋ยวก่อน...ลองคิดดูให้ดี ถ้าทุกคนหยุดจ่ายหนี้ แล้วใครกันที่จะเป็นคนแบกรับภาระนี้ ถอดรหัสแนวคิด "ซื้อหนี้ประชาชน" ด้วยเศรษฐศาสตร์แบบง่ายๆ และดูว่ามันจะช่วยเศรษฐกิจได้จริง หรือเป็นเพียง "ยาแก้ปวด" ที่ไม่รักษาอาการแท้จริง เรื่องราวของหนี้ที่ไม่มีวันหมด ลองนึกภาพตามนะ... "สมชาย" กู้เงินมาซื้อรถ 🚗 แต่ผ่อนต่อไม่ไหว ธนาคารจะยึดรถไปขายทอดตลาด แต่ทันใดนั้นก็มีโครงการใหม่จากภาครัฐหรือเอกชน "ซื้อหนี้ออกจากระบบธนาคาร" ฟังดูดีใช่ไหม แต่ปัญหาคือ ถ้าสมชายรู้ว่ามีคนช่วยเสมอ เขาจะมีแรงจูงใจในการจ่ายหนี้ต่อไปหรือเปล่า นั่นแหละ...จุดเริ่มต้นของกับดัก "Moral Hazard"
บทเรียนจาก #HenryHazlitt ผู้เขียน Economics in One Lesson
1 มันช่วยแก้หนี้ได้จริง...หรือแค่ยืดปัญหา Hazlitt เคยเตือนไว้ว่า เศรษฐกิจที่ดีต้องมองผลกระทบระยะยาว ไม่ใช่แค่ผลดีชั่วคราว 🔹 สิ่งที่ดูเหมือนช่วยเหลือวันนี้ อาจสร้างปัญหาที่ใหญ่กว่าในอนาคต 🔹 การแทรกแซงตลาดมักส่งผลให้เกิด "ผลกระทบที่มองไม่เห็น" ซึ่งอาจเลวร้ายกว่าปัญหาที่พยายามแก้ Hazlitt เชื่อว่าการซื้อหนี้แบบนี้อาจดูเหมือนช่วยเหลือประชาชนในระยะสั้น แต่ แท้จริงแล้วมันอาจกระตุ้นให้คนเคยชินกับการไม่จ่ายหนี้ และรอให้รัฐหรือเอกชนมาช่วยเสมอ ลองคิดดูว่า...
💡 ถ้าคนรู้ว่า "เป็นหนี้แล้วไม่ต้องจ่าย เพราะเดี๋ยวมีคนมาช่วย" แล้วพวกเขาจะพยายามจ่ายหนี้ในอนาคตไหม 💡 แล้วใครกันแน่ที่ต้องแบกรับหนี้พวกนี้ ธนาคาร เอกชน หรือสุดท้ายเป็น ภาษีจากประชาชนทุกคน เงินทุกบาทที่ใช้ ต้องมาจากที่ไหนสักแห่งเสมอ
ดังนั้น หากรัฐหรือเอกชนใช้เงินไปซื้อหนี้ แล้วไม่สามารถเก็บคืนได้ เงินนั้นก็จะหายไปจากระบบ เหมือนโยนลงทะเล แล้วแบบนี้คือการแก้ปัญหาจริงๆ หรือแค่ยืดเวลาจนระเบิดลง Hazlitt คงบอกว่า..."ไม่มีวิธีลัดในเศรษฐศาสตร์ การช่วยหนี้แบบนี้เป็นเพียงการเลื่อนเวลาความเสียหาย ไม่ใช่การแก้ปัญหา"
2 "ซื้อหนี้" = เงินจากไหน ผู้เสนอแนวคิดบอกว่า "เราจะใช้เงินเอกชน ไม่ใช่เงินรัฐ" แต่ในความเป็นจริง เอกชนไม่ได้มีเงินเหลือเฟือขนาดนั้น ทางเลือกที่เป็นไปได้ก็คือ... รัฐบาลต้องอุดหนุน ซึ่งสุดท้ายก็มาจากเงินภาษีเราๆ นี่แหละ หรือเอกชนคิดค่าธรรมเนียมเพิ่ม ทำให้ประชาชนต้องจ่ายมากขึ้นในระยะยาว
3 มันอาจทำให้เศรษฐกิจพังเร็วขึ้น Hazlitt อธิบายเรื่อง "เศษแก้วที่แตก" (Broken Window Fallacy) ว่า "การทำลายบางสิ่งเพื่อกระตุ้นเศรษฐกิจไม่ได้ทำให้เราได้กำไรเพิ่ม แต่มันแค่โยกย้ายค่าใช้จ่ายไปที่อื่น" เช่นเดียวกันกับการซื้อหนี้ มันไม่ได้ทำให้เศรษฐกิจดีขึ้น แต่เพียงโยกหนี้ไปที่คนอื่น
🎯 แล้วทางออกที่ดีกว่าคืออะไร แทนที่จะใช้มาตรการซื้อหนี้เพื่อ "ปิดบัง" ปัญหา มาลองดูวิธีแก้ปัญหาที่ใช้ หลักการตลาดเสรีและเศรษฐศาสตร์ที่แท้จริง กันดีกว่า 👇
✅ 1. ปล่อยให้กลไกตลาดจัดการหนี้ตามธรรมชาติ ปัจจุบันมีบริษัทบริหารสินทรัพย์ (AMC) ที่รับซื้อหนี้เสียจากธนาคารในราคาที่เหมาะสมอยู่แล้ว หากปล่อยให้กลไกตลาดดำเนินไป ธนาคารและสถาบันการเงินจะสามารถคัดกรองลูกหนี้ที่สามารถชำระหนี้ได้ออกมาโดยอัตโนมัติ
แล้วทำไมต้องปล่อยให้ตลาดทำงาน
-คนที่สามารถจ่ายหนี้ ได้จะมีแรงจูงใจในการจ่ายต่อ -คนที่จ่ายไม่ได้จริงๆ ก็จะต้องเจรจาปรับโครงสร้างหนี้เอง -บริษัทบริหารหนี้สามารถจัดการได้ดีกว่าภาครัฐ เพราะมีแรงจูงใจทางกำไร
✅ 2. ส่งเสริมการออม และสร้างวินัยทางการเงินให้ยั่งยืน ปัญหาหนี้ครัวเรือน ไม่ใช่แค่เพราะ "ไม่มีเงิน" แต่เพราะพฤติกรรมการใช้เงิน และผลกระทบจากเงินเฟ้อ Henry Hazlitt เตือนว่า การพิมพ์เงินและใช้จ่ายเกินตัวของรัฐบาลเป็นตัวการสำคัญที่ทำให้เงินเฟ้อพุ่งสูง ซึ่งทำให้เงินที่ประชาชนเก็บออม มีมูลค่าลดลงตลอดเวลา บ.ก.จิงโจ้บอกว่า #เวลามีค่าศึกษาบิตคอยน์
✅ 3. ถ้ารัฐบาลต้องการช่วยเศรษฐกิจ ต้องเน้นที่การสร้างงานจริงๆ ผ่านกลไกตลาด ไม่ใช่การแทรกแซงที่ทำให้ประชาชน "เคยชิน" กับการไม่ต้องรับผิดชอบหนี้ของตัวเอง
แนวคิดนี้ช่วยอย่างไร
-คนที่มีงานทำ = มีรายได้ = สามารถชำระหนี้ได้เอง -ธุรกิจเติบโตขึ้น ทำให้เศรษฐกิจขยายตัว -ไม่ต้องให้รัฐเข้ามาแทรกแซงระบบการเงินมากเกินไป
✅ 4. เปิดเสรีสินเชื่อ ให้การแข่งขันทำงานแทนรัฐ ทุกวันนี้สินเชื่อจากธนาคารอาจมีข้อจำกัดสูง ทำให้ประชาชนต้องไปพึ่งพาหนี้นอกระบบ หรือดอกเบี้ยแพงๆ
ถ้ารัฐเปิดเสรีสินเชื่อมากขึ้นล่ะ
-เพิ่มการแข่งขันในภาคธนาคาร ทำให้ดอกเบี้ยต่ำลง -ธนาคารมีแรงจูงใจในการให้สินเชื่อกับลูกหนี้ที่มีความสามารถในการจ่าย -หนี้นอกระบบลดลง ประชาชนสามารถกู้เงินในระบบที่ปลอดภัย
ถ้าคุณเป็นสมชาย แล้วรัฐบาลเสนอให้ซื้อหนี้ของคุณ…คุณจะยอมไหม คุณคิดว่าเป็นโอกาสที่ดี หรือกับดักที่รอทำให้เศรษฐกิจล่มสลาย คอมเมนต์มาบอกกันหน่อยแล้วแท็กเพื่อนที่คุณคิดว่า "ต้องอ่านเรื่องนี้"
แชร์บทความนี้ให้คนรอบตัวคุณ ให้พวกเขารู้ทันว่านโยบายแบบนี้มีผลกระทบอย่างไรกับเศรษฐกิจของเรา 🙃 #Siamstr #EIOL
-
 @ 6a6be47b:3e74e3e1
2025-03-20 09:14:31
@ 6a6be47b:3e74e3e1
2025-03-20 09:14:31Hi frens, I just wanted to say hello and remind you about the amazing artwork available from my creative corner. 🖼️ 🦄 I have a few digitala prints on my Plebeian Market stall from Bitcoin to some hoverflies. 🦄 On my Kofi-shop I have a bunch of digital prints too; fromBeelzebub toKrampus, stickers for Goodnotesand many other occulture and religious theme artwork. 🦄If you're more into physical prints, you can visit my INPRNT shop but if you'd like to wear my artwork, visit my Teespring shop. 🦄 You can find all of this at my nostree.me profile or go directly tomy website 🦄And of course, my pride and joy are my blog entries, I've painted about Ostara,Lupercalia, Nunsand many other religious and pagan themes. I invite you to take a peek 👀 Also, just dropping by to know how you've been? How are you gonna celebrate this Equinox? Maybe a Spring Cleansing?? Whatever you decide to do, I wish the best for you and your loved ones. I also would like to thank kyou for liking, reposting, the zaps, you're all awesome! None of this would be possible without you my frens! Wishing you all a Happy New Astrological year! Happy Equinox! Godspeed
-
 @ 7d33ba57:1b82db35
2025-03-20 09:08:46
@ 7d33ba57:1b82db35
2025-03-20 09:08:46Puerto de las Nieves
Puerto de las Nieves is a picturesque seaside village on Gran Canaria’s northwestern coast, near Agaete. Known for its whitewashed houses, fresh seafood, and stunning coastal views, it’s the perfect place for arelaxing day by the ocean.
🌊 Top Things to Do in Puerto de las Nieves
1️⃣ Relax at Playa de las Nieves
A peaceful pebble beach with crystal-clear waters, perfect for swimming and sunbathing.
2️⃣ See the Dedo de Dios (God’s Finger) Rock Formation
This famous natural rock structure was partially destroyed by a storm in 2005, but the area remains a scenic spot.
3️⃣ Visit the Agaete Natural Pools (Las Salinas de Agaete)
Just a short walk away, these volcanic rock pools offer a natural and sheltered swimming experience.
4️⃣ Walk Along the Promenade
Enjoy a scenic stroll along the coastal promenade, lined with cafés, seafood restaurants, and local shops.
5️⃣ Take a Ferry to Tenerife
Puerto de las Nieves is the departure point for ferries to Santa Cruz de Tenerife, making it a great connection between the Canary Islands.
🍽️ What to Eat in Puerto de las Nieves
- Fresh seafood – Try the local grilled fish (pescado a la espalda) 🐟
- Papas arrugadas with mojo – A Canarian classic 🥔
- Pulpo a la gallega – Delicious Galician-style octopus 🐙
- Local wines – Agaete Valley is known for its unique volcanic wines 🍷
🚗 How to Get to Puerto de las Nieves
🚗 By Car: ~40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Puerto de las Nieves
✅ Best time to visit? Year-round, but sunsets here are especially magical 🌅
✅ Bring water shoes! The beach is pebbly, so they make swimming easier 👟
✅ Try a boat trip – Great for coastal views and dolphin watching 🚤 -
 @ 33baa074:3bb3a297
2025-03-20 09:04:27
@ 33baa074:3bb3a297
2025-03-20 09:04:27Provide a basis for urban drainage system planning Weighing rain gauge can accurately measure rainfall, whether it is a small shower or a heavy rain, it can be accurately recorded. These data are crucial for the planning of urban drainage systems. Urban managers can reasonably design the diameter, slope and drainage capacity of drainage pipes based on long-term rainfall data to ensure that under different rainfall intensities, the urban drainage system can timely and effectively remove rainwater and avoid urban water logging. For example, in areas with heavy rainfall, the diameter of drainage pipes and the number of drainage pumping stations can be appropriately increased to improve drainage capacity.
Assisting in the planning of urban flood control facilities It can record the total amount of precipitation in real time and accurately, including snowfall in winter, and provide basic support for the planning of urban flood control facilities. By analyzing rainfall data, urban planners can determine parameters such as the height of flood levees, the capacity of reservoirs and the flood discharge capacity, and improve the city's flood control capabilities. In the flood warning system, the weighing rain gauge can provide instant feedback on precipitation conditions, help decision makers quickly assess disaster risks, make flood control preparations in advance, and reduce the damage of floods to the city.
Assisting the construction of sponge cities In the construction of sponge cities, weighing rain gauges play an important role. It can accurately measure rainfall and snowfall, and provide data support for evaluating the effectiveness of urban rainwater collection and utilization systems. Urban planners can rationally plan the layout and scale of sponge facilities such as rain gardens, sunken green spaces, and reservoirs based on rainfall data, improve the city's ability to absorb, store, infiltrate, and release rainwater, and achieve effective use of rainwater and ecological environmental protection.
Optimizing urban water resources management planning The high-precision precipitation data provided by the weighing rain gauge helps urban planners formulate scientific water resources management plans. By analyzing rainfall data, we can understand the water resources situation in the city, reasonably allocate water resources, and improve the utilization efficiency of water resources. According to the rainfall situation, the urban water supply plan can be adjusted, and the water storage and release of reservoirs can be reasonably arranged to ensure the balance of supply and demand of urban water resources.
Serving urban ecological environment planning The amount of precipitation and its form have an important impact on the urban ecological environment. The precipitation data provided by the weighing rain gauge helps urban planners assess the impact of droughts and floods on urban ecosystems and formulate corresponding ecological protection measures. In urban greening planning, suitable plant varieties can be selected based on rainfall data to improve plant survival rate and growth quality and improve the urban ecological environment.
-
 @ 33baa074:3bb3a297
2025-03-20 08:49:05
@ 33baa074:3bb3a297
2025-03-20 08:49:05Influence on plant growth Influence on plant physiological activities Different vegetation types and site conditions determine the changing pattern of soil temperature, and soil heat flux affects soil temperature, which can affect plant transpiration, root respiration and absorption, and the dissolution rate of various inorganic salts in soil solution, thereby affecting the growth of trees. For example, suitable soil heat flux keeps the soil temperature in a suitable range, which is conducive to the absorption of water and nutrients by plant roots and promotes the growth and development of plants.
Influence on plant distribution Soil heat flux varies in different regions and different terrain conditions. This difference leads to different soil temperatures, which in turn affects the distribution of plants. Different plants have different adaptation ranges to temperature. Areas with higher soil heat flux may be more suitable for the growth of thermoplastic plants, while areas with lower heat flux are suitable for the distribution of cold-resistant plants.
Participate in the study of earth energy balance and climate change As a component of energy balance Soil heat flux is an important component of the earth's surface energy balance and has an important impact on the earth's energy balance and climate change. After the surface absorbs solar radiation energy, the heat is transferred to the deep soil through molecular conduction. At the same time, the soil also releases energy to the sky through far-infrared radiation. The size and change of soil heat flux affect the energy exchange between the earth's surface and the atmosphere.
Reflecting climate change trends Studying the long-term trend of soil heat flux can provide an important basis for climate change research. For example, with global warming, the distribution and change of soil heat flux may change. By monitoring soil heat flux, we can understand the impact of climate change on the thermal state of soil, and then predict the trend and consequences of climate change.
Influence on soil moisture distribution and evaporation process Water evaporation rate When the soil heat flux is large, the soil temperature rises, the water evaporation rate increases, and the soil moisture content decreases. Changes in soil heat flux will affect the dynamic balance of soil moisture, thereby affecting the soil humidity and the growth environment of vegetation. For example, in arid areas, higher soil heat flux may cause rapid evaporation of soil moisture and aggravate the degree of soil drought.
Moisture distribution pattern Differences in the spatial distribution of soil heat flux will lead to uneven distribution of soil moisture in different regions. In areas with high heat flux, water evaporates quickly and soil water content is relatively low; while in areas with low heat flux, water evaporates slowly and soil water content is relatively high. This water distribution pattern will affect the distribution and growth of vegetation and form different ecological landscapes.
Impact on soil biological activities Affecting microbial activity Soil heat flux affects soil temperature, and soil temperature is one of the important factors affecting soil microbial activity. Suitable soil temperature is conducive to the growth and reproduction of microorganisms, and promotes the decomposition of organic matter and nutrient circulation in the soil. Changes in soil heat flux will change the community structure and function of soil microorganisms, thereby affecting the material cycle and energy flow of the soil ecosystem.
Impact on soil animal survival Animals in the soil, such as earthworms and insects, are also affected by soil heat flux and temperature. Different soil animals have different adaptation ranges to temperature, and changes in soil heat flux may affect their survival, reproduction and activities, thereby affecting the structure and function of the soil ecosystem.
Guiding agricultural production and land management Improving land productivity Studying the effects of different covering and tillage measures on soil temperature and moisture can improve land productivity by regulating soil heat flux. For example, reasonable vegetation cover can regulate the radiation, evaporation and conduction processes on the soil surface, thereby affecting soil heat flux, maintaining soil moisture, improving soil fertility and promoting crop growth. Agricultural meteorological research: Soil heat flux is an important parameter in agricultural meteorological research, which allows people to study the functional relationship between energy stored in the soil and time. By monitoring soil heat flux, it can provide a scientific basis for agricultural production and reasonably arrange agricultural activities such as sowing, irrigation, fertilization, etc.
-
 @ d5c3d063:4d1159b3
2025-03-20 08:32:20
@ d5c3d063:4d1159b3
2025-03-20 08:32:20คุณเคยได้ยินไหมว่า "ทุนนิยมทำให้คนรวยรวยขึ้น คนจนจนลง" หรือ "ทุนนิยมเป็นต้นเหตุของความเหลื่อมล้ำ"
แนวคิดที่ว่าทุนนิยมเป็นต้นเหตุของปัญหาสังคมมักถูกนำเสนออย่างแพร่หลาย แต่แท้จริงแล้ว ระบบเศรษฐกิจนี้มีบทบาทอย่างไรในการพัฒนาสังคมและชีวิตของผู้คน ในบทความนี้เราจะพาคุณสำรวจข้อเท็จจริง มุมมองทางประวัติศาสตร์ และแนวคิดจากนักเศรษฐศาสตร์ เพื่อให้คุณสามารถประเมินทุนนิยมด้วยมุมมองที่รอบด้านมากขึ้น ถ้าคุณคิดว่าทุนนิยมคือปีศาจร้าย ลองคิดใหม่! มันอาจไม่ได้เป็นอย่างที่คุณคิด…
กำเนิดทุนนิยมและวิวัฒนาการของระบบเศรษฐกิจ
ก่อนเกิดการปฏิวัติอุตสาหกรรม ยุโรปอยู่ภายใต้ระบบศักดินา (Feudalism) ซึ่งเศรษฐกิจถูกควบคุมโดยกษัตริย์ ขุนนาง และรัฐ ประชาชนส่วนใหญ่เป็นเกษตรกรที่ไม่มีเสรีภาพทางเศรษฐกิจ ขณะเดียวกัน ลัทธิพาณิชยนิยมย (Mercantilism) ของรัฐมุ่งเน้นการสะสมทองคำ ควบคุมการค้า และจำกัดการแข่งขัน ส่งผลให้เศรษฐกิจขาดความคล่องตัวและไม่สามารถเติบโตได้อย่างมีประสิทธิภาพ อย่างไรก็ตาม การเปลี่ยนแปลงที่ดำเนินมาหลายศตวรรษได้ค่อย ๆ บ่อนทำลายโครงสร้างของระบบศักดินา และเปิดทางให้ระบบเศรษฐกิจแบบใหม่ถือกำเนิดขึ้น โดยทุนนิยมไม่ได้เกิดขึ้นเพียงเพราะแนวคิดของ Adam Smith เท่านั้น แต่เป็นผลลัพธ์ของปัจจัยหลายประการที่สั่งสมมาเป็นเวลานาน
- การขยายตัวของการค้าและเมือง ในช่วงศตวรรษที่ 12-15 เมืองใหญ่ เช่น เวนิส ฟลอเรนซ์ และอัมสเตอร์ดัม กลายเป็นศูนย์กลางการค้าระหว่างประเทศ เนื่องจากเส้นทางเดินเรือขยายตัว พ่อค้าสามารถทำการค้าได้กว้างขึ้น และเศรษฐกิจไม่ได้ถูกจำกัดอยู่ภายในระบบศักดินาอีกต่อไป
- การเติบโตของสถาบันการเงิน ทำให้การลงทุนเป็นไปได้มากขึ้น ธนาคารของตระกูลเมดิชีในอิตาลี และตลาดหลักทรัพย์ในอัมสเตอร์ดัมช่วยให้เกิดการกระจายความเสี่ยง และทำให้พ่อค้าสามารถระดมทุนเพื่อขยายธุรกิจได้ง่ายขึ้น
- การล่มสลายของระบบศักดินา เกิดจากการที่ชนชั้นกลาง (Bourgeoisie) เช่น พ่อค้าและช่างฝีมือ เริ่มมีอำนาจทางเศรษฐกิจมากขึ้น ขณะที่ขุนนางสูญเสียอำนาจในการควบคุมทรัพยากรและแรงงาน เพราะแรงงานเริ่มมีอิสระในการเลือกงานและเจรจาค่าจ้างเอง
- การปฏิวัติทางวิทยาศาสตร์และเทคโนโลยี เช่น การคิดค้นเครื่องจักรไอน้ำของเจมส์ วัตต์ และเครื่องจักรทอผ้าแบบใช้แรงน้ำ ทำให้การผลิตมีประสิทธิภาพสูงขึ้น ลดต้นทุน และเพิ่มปริมาณสินค้าที่สามารถผลิตได้
แม้ว่า Adam Smith จะมีบทบาทสำคัญในการอธิบายแนวคิด ตลาดเสรี ใน The Wealth of Nations (1776) โดยเสนอแนวคิด "มือที่มองไม่เห็น" (Invisible Hand) ซึ่งอธิบายว่าการแข่งขันเสรีจะนำไปสู่การจัดสรรทรัพยากรที่มีประสิทธิภาพมากกว่าการควบคุมโดยรัฐ แต่แนวคิดของเขา เป็นเพียงส่วนหนึ่งของกระบวนการที่เริ่มต้นมานานแล้ว ไม่ใช่จุดเริ่มต้นของระบบทุนนิยม การเปลี่ยนแปลงนี้นำไปสู่การปฏิวัติอุตสาหกรรมซึ่งเป็นจุดเปลี่ยนครั้งใหญ่ของเศรษฐกิจโลก การลงทุนในเครื่องจักรและโรงงานทำให้การผลิตมีประสิทธิภาพสูงขึ้น ต้นทุนต่อหน่วยสินค้าลดลงและตลาดสามารถขยายตัวไปได้กว้างขึ้น ก่อให้เกิดระบบทุนนิยมยุคใหม่ที่เน้นการแข่งขันเสรี การสร้างคุณค่า และการเติบโตทางเศรษฐกิจแบบยั่งยืน
สรุปสั้น ๆ คือ
- ทุนนิยมไม่ได้เกิดขึ้นเพียงเพราะแนวคิดของ Adam Smith แต่เป็นผลจากการเปลี่ยนแปลงทางเศรษฐกิจและสังคมที่สั่งสมมาหลายศตวรรษ
- การเติบโตของการค้า เมือง และสถาบันการเงิน เป็นรากฐานสำคัญของเศรษฐกิจตลาดเสรี ก่อนที่ Smith จะมาอธิบายหลักการนี้ให้เป็นระบบ
- การปฏิวัติอุตสาหกรรมเป็นตัวเร่งที่ทำให้ระบบทุนนิยมกลายเป็นโครงสร้างหลักของเศรษฐกิจโลก
สรุปย้ำอีกครั้ง…ระบบทุนนิยมจึงเป็นผลลัพธ์จากวิวัฒนาการของเศรษฐกิจ ไม่ใช่สิ่งที่เกิดขึ้นอย่างฉับพลันจากแนวคิดทางทฤษฎี แต่เป็นกระบวนการที่เกิดจากการเปลี่ยนแปลงของแรงงาน การค้า เทคโนโลยี และสังคมโดยรวม ต่างจากระบบศักดินาและเมอร์แคนไทล์ที่รัฐควบคุมทรัพยากรและการค้า ทุนนิยมแท้จริงเกิดขึ้นจากการปลดปล่อยตลาดจากการควบคุมของรัฐ ซึ่งทำให้เกิดการแข่งขันที่เป็นธรรมและกระตุ้นให้เกิดนวัตกรรม การยกเลิกข้อจำกัดที่ขุนนางและกษัตริย์เคยกำหนด เปิดโอกาสให้ชนชั้นกลางและประชาชนทั่วไปสามารถสร้างความมั่งคั่งได้ด้วยความสามารถของตนเอง แทนที่จะต้องพึ่งพาสิทธิพิเศษทางชนชั้นหรืออำนาจรัฐ ดังนั้นการเติบโตของทุนนิยมจึงเป็นผลจากเสรีภาพทางเศรษฐกิจ ไม่ใช่จากการบังคับหรือการรวมศูนย์โดยรัฐบาล
10 ประเด็นที่ถูกเข้าใจผิดเกี่ยวกับ #ทุนนิยม
!(image)[https://m.primal.net/PlYG.png]
1. ความเหลื่อมล้ำทางเศรษฐกิจ (Economic Inequality)
⚠️ ความเข้าใจผิด #ทุนนิยมทำให้ช่องว่างระหว่างคนรวยและคนจนกว้างขึ้น
🔍 ข้อเท็จจริง
- ความเหลื่อมล้ำไม่ใช่ปัญหาหลัก ตราบใดที่มาตรฐานชีวิตของคนจนดีขึ้น หลักฐานจากประวัติศาสตร์แสดงให้เห็นว่า เมื่อเศรษฐกิจเปิดเสรีมากขึ้น โอกาสในการพัฒนาและความเป็นอยู่ของประชาชนดีขึ้นตามไปด้วย ตัวอย่างเช่น การเปิดเสรีทางเศรษฐกิจของจีนในปี 1978 ทำให้ประชากรมากกว่าหลายร้อยล้านคนหลุดพ้นจากความยากจน ซึ่งเป็นผลมาจากการเปลี่ยนแปลงนโยบายจากระบบเศรษฐกิจแบบวางแผนโดยรัฐไปสู่ตลาดเสรีมากขึ้น แนวคิดนี้ได้รับการสนับสนุนโดย Friedrich Hayek ที่กล่าวว่า "ความมั่งคั่งที่เกิดขึ้นในตลาดเสรีไม่ได้เป็นเกมศูนย์ผลรวม (zero-sum game) แต่เป็นกระบวนการที่ช่วยยกระดับคุณภาพชีวิตของทุกคนในระยะยาว" นอกจากนี้ การแข่งขันเสรีในตลาดยังช่วยให้ราคาสินค้าลดลง คุณภาพชีวิตดีขึ้น และเกิดการกระจายความมั่งคั่งอย่างมีประสิทธิภาพมากขึ้น โดยไม่ต้องพึ่งการแทรกแซงจากรัฐที่มักนำไปสู่การคอร์รัปชันและระบบพวกพ้อง
- Murray Rothbard กล่าวไว้ว่า "รัฐเป็นตัวการที่แท้จริงในการสร้างความเหลื่อมล้ำ เพราะใช้นโยบายเอื้อประโยชน์ให้กับกลุ่มพวกพ้อง (Cronyism)"
💡 แนวทางแก้ไข
- ลดการแทรกแซงของรัฐและส่งเสริมการแข่งขันเสรี เนื่องจากปัญหาความเหลื่อมล้ำทางเศรษฐกิจที่มักถูกโยนความผิดให้กับทุนนิยม จริง ๆ แล้วเกิดจากการควบคุมตลาดของรัฐที่เอื้อผลประโยชน์ให้กับกลุ่มนายทุนพวกพ้อง (Cronyism) มากกว่าที่จะเป็นผลของกลไกตลาดเสรี
- การกำหนดกฎระเบียบที่ซับซ้อนและภาษีที่สูงทำให้ธุรกิจรายย่อยและผู้ประกอบการหน้าใหม่เข้าถึงโอกาสได้น้อยลง ขณะที่บริษัทยักษ์ใหญ่ที่มีสายสัมพันธ์ทางการเมืองสามารถใช้ข้อบังคับเหล่านี้เพื่อกีดกันคู่แข่งและสร้างความได้เปรียบอย่างไม่เป็นธรรม หากตลาดเปิดเสรีอย่างแท้จริง ทุกคนจะมีโอกาสในการแข่งขันอย่างเท่าเทียมกันและคุณภาพชีวิตของคนในทุกชนชั้นจะดีขึ้นจากการเติบโตของเศรษฐกิจโดยธรรมชาติ ไม่ใช่เพราะนโยบายที่ควบคุมโดยภาครัฐที่มักเอื้อประโยชน์ให้เฉพาะกลุ่มอำนาจ
- ในยุคนี้เลี่ยงไม่ได้ที่จะพูดถึงการใช้บิตคอยน์เพื่อลดอำนาจของสถาบันการเงินที่ผูกขาด ซึ่งเป็นผลจากระบบการเงินรวมศูนย์ที่ถูกควบคุมโดยธนาคารกลางและรัฐบาล บิตคอยน์ทำให้ประชาชนสามารถทำธุรกรรมทางการเงินโดยไม่ต้องพึ่งพาคนกลาง ลดโอกาสที่รัฐและสถาบันการเงินขนาดใหญ่จะบิดเบือนค่าเงินผ่านนโยบายเงินเฟ้อหรือการควบคุมอัตราดอกเบี้ย นอกจากนี้ บิตคอยน์มีอุปทานจำกัดที่ 21 ล้านเหรียญ ซึ่งแตกต่างจากเงินเฟียตที่สามารถถูกพิมพ์เพิ่มได้ไม่จำกัด สิ่งนี้ช่วยป้องกันการลดค่าของเงิน และให้เสรีภาพทางการเงินแก่ประชาชนมากขึ้น
2. ความยากจนท่ามกลางความมั่งคั่ง (Poverty Amidst Wealth)
📢 ข้อกล่าวหา #คนรวยยิ่งรวยขึ้นแต่คนจนไม่ได้รับผลประโยชน์จากเศรษฐกิจ
🧐 ความจริง
-
ประเทศที่ใช้กลไกตลาดเสรี เช่น ฮ่องกง และ สิงคโปร์ มีระดับความยากจนต่ำมาก เนื่องจากพวกเขามีนโยบายภาษีต่ำ การคุ้มครองทรัพย์สินส่วนบุคคล และกฎหมายที่เอื้อต่อธุรกิจขนาดเล็กและสตาร์ทอัพ รัฐบาลของพวกเขาเน้นการเปิดเสรีทางเศรษฐกิจ ลดข้อจำกัดด้านการค้า และลดการควบคุมของรัฐ ทำให้เกิดสภาพแวดล้อมที่ดึงดูดการลงทุนจากต่างประเทศและส่งเสริมการเติบโตของภาคเอกชน นอกจากนี้ ตลาดแรงงานที่มีความยืดหยุ่นช่วยให้เกิดการจ้างงานที่หลากหลายขึ้นและมีการแข่งขันด้านค่าจ้างที่เป็นธรรม ในฮ่องกงและสิงคโปร์ บริษัทต่าง ๆ สามารถจ้างแรงงานได้ง่ายขึ้นเนื่องจากกฎหมายแรงงานที่เอื้อต่อการจ้างงาน ส่งผลให้เกิดโอกาสในการทำงานมากขึ้นและช่วยลดอัตราการว่างงาน อีกทั้ง ทั้งสองประเทศยังให้ความสำคัญกับการศึกษาและพัฒนาทักษะของประชากร เพื่อให้แรงงานสามารถแข่งขันในตลาดที่มีเทคโนโลยีสูงได้ สิงคโปร์มีระบบการศึกษาที่สนับสนุนการเรียนรู้ทางเทคนิคและอาชีวะ ซึ่งช่วยให้ประชาชนสามารถพัฒนาทักษะใหม่ ๆ และปรับตัวเข้ากับเศรษฐกิจที่เปลี่ยนแปลงได้อย่างรวดเร็ว ผลลัพธ์ที่ตามมาคือ ประชาชนสามารถเข้าถึงโอกาสทางเศรษฐกิจได้มากขึ้น เช่น แรงงานมีโอกาสเข้าทำงานในบริษัทที่แข่งขันกันเสนอค่าตอบแทนที่ดีกว่า ผู้ประกอบการสามารถเริ่มต้นธุรกิจของตนเองได้โดยไม่มีข้อจำกัดจากรัฐมากเกินไป และผู้บริโภคได้รับสินค้าราคาถูกลงเนื่องจากการแข่งขันที่เป็นธรรม สิ่งเหล่านี้ช่วยให้ประชาชนมีรายได้ที่มั่นคง คุณภาพชีวิตที่ดีขึ้น และสามารถพัฒนาตนเองได้อย่างอิสระ ซึ่งช่วยลดอัตราความยากจนได้อย่างมีประสิทธิภาพในระยะยาว
-
Friedrich Hayek กล่าวว่า "ระบบทุนนิยมช่วยให้คนจนมีโอกาสเข้าถึงสินค้าและบริการที่ดีกว่าในราคาที่ต่ำลง"
✅ ทางออก
- สนับสนุนระบบการค้าเสรีเพื่อลดต้นทุนสินค้าและบริการ เนื่องจากการแข่งขันที่เป็นธรรมในตลาดเสรีช่วยให้ต้นทุนการผลิตลดลง ทำให้ผู้บริโภคสามารถเข้าถึงสินค้าคุณภาพดีในราคาที่เป็นธรรม โดยไม่มีการผูกขาดจากกลุ่มที่ได้รับอภิสิทธิ์จากรัฐ
- ลดภาษีเพื่อให้ธุรกิจขยายตัวและสร้างงาน เนื่องจากภาษีที่สูงเกินไปเป็นอุปสรรคสำคัญที่ขัดขวางการเติบโตของธุรกิจรายย่อย ทำให้มีเพียงบริษัทยักษ์ใหญ่ที่สามารถอยู่รอดได้ การลดภาษีช่วยให้ธุรกิจใหม่ ๆ สามารถเกิดขึ้นได้ง่ายขึ้น และเพิ่มโอกาสให้ประชาชนสามารถมีอาชีพที่มั่นคงมากขึ้น ซึ่งตรงกันข้ามกับแนวคิดที่ว่า "รัฐต้องเข้ามาควบคุมเศรษฐกิจเพื่อความเท่าเทียม" ซึ่งมักส่งผลให้เกิดระบบพวกพ้องและลดทอนเสรีภาพทางเศรษฐกิจ
3. บริโภคนิยมและวัตถุนิยม (Consumerism and Materialism)
📢 ข้อกล่าวหา #ทุนนิยมส่งเสริมการบริโภคเกินพอดีทำให้ผู้คนหมกมุ่นกับวัตถุ
🧐 ความจริง
-
บริโภคนิยมเป็นผลจากวัฒนธรรมมากกว่าระบบเศรษฐกิจ เนื่องจากความต้องการบริโภคสินค้าถูกขับเคลื่อนโดยปัจจัยทางสังคม เช่น ค่านิยม ความคาดหวังของสังคม และการตลาดมากกว่ากลไกของตลาดเสรี ตัวอย่างเช่น ในยุคก่อนอุตสาหกรรม ผู้คนมักใช้สินค้าตามความจำเป็น แต่เมื่อเทคโนโลยีและสื่อโฆษณาพัฒนาไปมากขึ้น ผู้บริโภคเริ่มได้รับอิทธิพลจากภาพลักษณ์ทางการตลาดและสังคม วัฒนธรรมบริโภคนิยมจึงเกิดขึ้นโดยมีรากฐานจากพฤติกรรมของมนุษย์ที่ต้องการความเป็นที่ยอมรับ มากกว่าการถูกกำหนดโดยตัวระบบเศรษฐกิจเอง
-
ระบบทุนนิยมสร้างทางเลือกให้ผู้บริโภค โดยทำให้มีสินค้าหลากหลายประเภทในท้องตลาด ทั้งสินค้าจำเป็นและสินค้าฟุ่มเฟือย ผู้บริโภคมีอิสระในการตัดสินใจเลือกซื้อสินค้าตามความต้องการและความสามารถทางการเงินของตนเอง อีกทั้งการแข่งขันเสรีกระตุ้นให้ธุรกิจต้องผลิตสินค้าที่ตอบโจทย์ผู้บริโภคมากที่สุด โดยไม่ต้องใช้การบังคับหรือกำหนดจากภาครัฐ นอกจากนี้ การแข่งขันทางธุรกิจยังช่วยลดต้นทุน ทำให้สินค้าหลายอย่างที่เคยเป็นของฟุ่มเฟือย เช่น สมาร์ทโฟน รถยนต์ หรือเครื่องใช้ไฟฟ้า มีราคาถูกลงและสามารถเข้าถึงได้ง่ายขึ้น
✅ ทางออก
- ส่งเสริมการศึกษาเกี่ยวกับพฤติกรรมการบริโภคที่มีเหตุผล โดยเน้นให้ประชาชนเข้าใจถึงผลกระทบของการใช้จ่ายเกินตัว และสามารถแยกแยะความต้องการที่แท้จริงออกจากการตลาดที่กระตุ้นให้บริโภคโดยไม่จำเป็น นอกจากนี้ ควรให้ความรู้เกี่ยวกับแนวทางการบริหารเงินอย่างมีประสิทธิภาพ และการตัดสินใจซื้อสินค้าที่สอดคล้องกับรายได้และความจำเป็นของแต่ละบุคคล เพื่อช่วยให้ผู้บริโภคสามารถวางแผนการใช้จ่ายได้ดีขึ้น และลดปัญหาหนี้สินที่เกิดจากการบริโภคที่เกินตัว
4. คุณค่าทางสังคมเสื่อมถอย (Erosion of Community Values)
📢 ข้อกล่าวหา #ทุนนิยมทำให้คนเห็นแก่ตัวและละเลยสังคม
🧐 ความจริง
- การให้และกิจกรรมการกุศลเพิ่มขึ้นในประเทศที่มีระบบทุนนิยม เช่น สหรัฐฯ เนื่องจากประชาชนมีอิสระในการบริหารทรัพย์สินของตนเอง และสามารถบริจาคเงินให้กับองค์กรการกุศลได้โดยไม่มีข้อจำกัดจากรัฐ อีกทั้งองค์กรไม่แสวงหากำไรก็สามารถดำเนินงานได้อย่างมีประสิทธิภาพในตลาดเสรีโดยอาศัยการสนับสนุนจากภาคประชาชนและภาคธุรกิจ มากกว่าการพึ่งพางบประมาณของรัฐบาล
-
ทุนนิยมช่วยให้เกิดองค์กรไม่แสวงหากำไรที่ช่วยเหลือผู้ด้อยโอกาสโดยให้ภาคเอกชนและประชาชนมีอิสระในการจัดตั้งและบริหารองค์กรเหล่านี้โดยไม่ต้องพึ่งพารัฐบาล ระบบเศรษฐกิจแบบตลาดเปิดโอกาสให้เกิดการแข่งขันในการให้บริการสังคม เช่น องค์กรด้านการศึกษา การแพทย์ และการช่วยเหลือผู้ยากไร้ ซึ่งสามารถดำเนินการได้อย่างมีประสิทธิภาพมากกว่ารัฐ เนื่องจากไม่มีระบบราชการที่ล่าช้าและสามารถตอบสนองต่อความต้องการของผู้คนได้รวดเร็วกว่า
-
สมิธ กล่าวไว้ใน The Wealth of Nations ว่า "มันไม่ใช่จากความเมตตาของคนขายเนื้อ คนทำเบียร์ หรือคนทำขนมปังที่เราคาดหวังให้ได้อาหารเย็นของเรา แต่เป็นเพราะพวกเขาใส่ใจผลประโยชน์ของตัวเอง" ซึ่งหมายความว่า เมื่อบุคคลแต่ละคนแสวงหาประโยชน์สูงสุดให้กับตัวเอง พวกเขาจะต้องผลิตสินค้าหรือบริการที่ดีที่สุดเพื่อให้ได้รับผลตอบแทนที่ดีขึ้นในตลาด อย่างไรก็ตาม การแสวงหาผลประโยชน์ส่วนตนนี้ ไม่ได้หมายความว่าคนจะเห็นแก่ตัวหรือทำลายสังคม ตรงกันข้าม กลับทำให้เกิดระบบเศรษฐกิจที่ทุกฝ่ายได้รับประโยชน์ร่วมกัน เมื่อพ่อค้าและผู้ผลิตพยายามสร้างสินค้าที่ดีที่สุดเพื่อตอบสนองความต้องการของผู้บริโภค พวกเขาต้องแข่งขันกันเพื่อให้บริการที่ดีขึ้น ราคาถูกลง และคุณภาพสูงขึ้น สิ่งนี้ส่งผลให้สังคมโดยรวมได้รับสินค้าที่ดีขึ้นและมีราคาเข้าถึงได้ง่ายขึ้น นอกจากนี้ การเติบโตทางเศรษฐกิจที่เกิดขึ้นยังนำไปสู่การสร้างงาน รายได้ที่เพิ่มขึ้น และคุณภาพชีวิตที่ดีขึ้นสำหรับทุกคน ดังนั้น แทนที่ระบบตลาดเสรีจะทำให้คนเห็นแก่ตัว ทุนนิยมกลับเป็นกลไกที่ส่งเสริมการพัฒนาและความมั่นคงของสังคม
✅ ทางออก
- สนับสนุนตลาดเสรีที่ส่งเสริมการเป็นเจ้าของและความรับผิดชอบส่วนบุคคล โดยให้ประชาชนสามารถสร้างความมั่นคงทางเศรษฐกิจของตนเองได้โดยไม่ต้องพึ่งพารัฐบาลมากเกินไป ทุนนิยมช่วยให้บุคคลสามารถลงทุน สร้างธุรกิจ และพัฒนาทรัพย์สินของตนเองได้ตามความสามารถ ซึ่งไม่เพียงแต่ทำให้เกิดความมั่งคั่งส่วนบุคคล แต่ยังช่วยให้เกิดการสร้างงานและเพิ่มมูลค่าทางเศรษฐกิจในสังคมโดยรวม
5. เอาเปรียบแรงงาน (Exploiting Labor)
📢 ข้อกล่าวหา #นายจ้างกดค่าแรงและเอาเปรียบลูกจ้าง
🧐 ความจริง
- ค่าจ้างในตลาดเสรีถูกกำหนดโดยทักษะของแรงงานและการแข่งขันระหว่างบริษัท ไม่ใช่จากการกำหนดของรัฐ เมื่อธุรกิจต้องการแรงงานที่มีความสามารถสูง พวกเขาจะเสนอค่าตอบแทนที่ดีกว่าเพื่อดึงดูดและรักษาพนักงาน นอกจากนี้ การแข่งขันในตลาดแรงงานทำให้บริษัทต้องพัฒนาสวัสดิการและเงื่อนไขการทำงานให้ดียิ่งขึ้น
กรณีที่มีการใช้ เหตุการณ์ตึกถล่ม เป็นตัวอย่างโจมตีทุนนิยม โดยกล่าวหาว่าธุรกิจมุ่งแต่กำไรจนละเลยความปลอดภัยของแรงงาน เป็น ความเข้าใจผิด ที่มองข้ามข้อเท็จจริงที่ว่า ตลาดเสรีมีแรงจูงใจให้บริษัทต้องรักษาชื่อเสียงและมาตรฐาน เพื่อให้ธุรกิจอยู่รอดในระยะยาว
✅ ตลาดเสรีแท้จริงจะลงโทษบริษัทที่ไม่รักษามาตรฐาน
- หากบริษัทละเลยความปลอดภัยจนเกิดอุบัติเหตุร้ายแรง เช่น ตึกถล่ม ผู้บริโภคและแรงงานจะเลิกสนับสนุน ทำให้บริษัทเสียชื่อเสียงและสูญเสียลูกค้าอย่างถาวร
- ตัวอย่างในประเทศที่มีตลาดเสรีและสื่อเสรี หากมีอุบัติเหตุแรงงานเสียชีวิตจากความประมาทของบริษัท สังคมจะกดดันให้มีการรับผิดชอบ และแรงงานจะเปลี่ยนไปทำงานกับบริษัทที่ปลอดภัยกว่า
✅ ปัญหาตึกถล่มส่วนใหญ่เกี่ยวข้องกับระบบพวกพ้อง (Crony Capitalism) มากกว่าตลาดเสรี
- หลายกรณีที่เกิดอุบัติเหตุจากการละเลยมาตรฐานความปลอดภัย มักเกิดจาก การติดสินบนเจ้าหน้าที่รัฐ หรือการได้รับสัมปทานพิเศษที่ยกเว้นข้อบังคับด้านความปลอดภัย ซึ่งเป็นปัญหาของระบบพวกพ้อง ไม่ใช่กลไกของตลาดเสรี
- ตัวอย่างเช่น ในบางประเทศกำลังพัฒนา การอนุญาตก่อสร้างโดยไม่ต้องตรวจสอบมาตรฐาน หรือการใช้วัสดุที่ไม่มีคุณภาพต่ำกว่าเกณฑ์ ล้วนเป็นผลมาจาก รัฐให้สิทธิพิเศษแก่กลุ่มทุนบางกลุ่ม ทำให้เกิดช่องโหว่ที่นำไปสู่หายนะ
✅ ถ้ารัฐไม่แทรกแซงมากเกินไป ตลาดเสรีจะแก้ปัญหาเอง
- แรงงานมีอำนาจต่อรองมากขึ้น เพราะพวกเขาสามารถเลือกทำงานกับบริษัทที่มีมาตรฐานความปลอดภัยสูงกว่า
- ผู้บริโภคมีสิทธิ์เลือก หากบริษัทใดมีปัญหาด้านมาตรฐาน บริษัทนั้นจะถูกคว่ำบาตรจากผู้บริโภค และเสียเปรียบทางการแข่งขัน
การกล่าวหาว่านายจ้างกดค่าแรงในระบบทุนนิยมมักมองข้ามข้อเท็จจริงที่ว่า ตลาดแรงงานเสรีบังคับให้ธุรกิจต้องแข่งขันกันดึงดูดแรงงานที่ดีที่สุด หากบริษัทใดพยายามกดค่าแรงมากเกินไป พนักงานสามารถเปลี่ยนไปทำงานกับบริษัทที่ให้ข้อเสนอที่ดีกว่าได้ ซึ่งเป็นหลักการสำคัญของตลาดเสรี
การกำหนดค่าแรงขั้นต่ำโดยรัฐไม่ได้ช่วยลูกจ้างเสมอไป แต่กลับเอื้อประโยชน์ต่อนายทุนใหญ่ ที่สามารถรับภาระค่าแรงที่เพิ่มขึ้นได้ แต่ธุรกิจขนาดเล็กและธุรกิจใหม่ ๆ กลับได้รับผลกระทบอย่างหนัก ทำให้ไม่สามารถจ้างพนักงานเพิ่มได้ และบางกรณีอาจต้องลดจำนวนพนักงานลง การขึ้นค่าแรงขั้นต่ำจึงส่งผลให้การจ้างงานลดลงและทำให้ผู้ที่มีทักษะต่ำหรือต้องการเข้าสู่ตลาดแรงงานใหม่มีโอกาสได้น้อยลง
นักเศรษฐศาสตร์สำนักออสเตรียน เช่น Ludwig von Mises และ Murray Rothbard ชี้ให้เห็นว่า การกำหนดค่าแรงขั้นต่ำเป็นเครื่องมือของรัฐที่มักถูกใช้เพื่อเอื้อประโยชน์ให้กับธุรกิจขนาดใหญ่ที่มีอิทธิพลทางการเมือง ขณะที่แรงงานที่มีทักษะต่ำต้องเผชิญกับการว่างงานที่เพิ่มขึ้น
✅ ทางออก
- ลดการกำหนดค่าแรงขั้นต่ำที่บิดเบือนตลาด เพราะค่าแรงที่ถูกกำหนดโดยรัฐมักไม่สอดคล้องกับความเป็นจริงของตลาดแรงงาน ธุรกิจขนาดเล็กอาจไม่สามารถจ้างพนักงานเพิ่มได้ ขณะที่บริษัทยักษ์ใหญ่กลับสามารถแบกรับต้นทุนนี้ได้ ทำให้การแข่งขันลดลงและธุรกิจรายย่อยถูกกีดกันออกจากตลาด ในทางกลับกัน หากปล่อยให้ตลาดเสรีทำงาน นายจ้างและลูกจ้างจะสามารถตกลงค่าจ้างที่เป็นธรรมได้ตามทักษะและประสิทธิภาพของแรงงาน ซึ่งช่วยให้เกิดการจ้างงานมากขึ้น และลดปัญหาว่างงานของแรงงานทักษะต่ำ
- ประวัติศาสตร์แสดงให้เห็นว่า ประเทศที่มีตลาดแรงงานเสรี เช่น สิงคโปร์ มีอัตราการว่างงานต่ำและการเติบโตของเศรษฐกิจสูงกว่าประเทศที่ใช้การควบคุมค่าแรงอย่างเข้มงวด เช่น ฝรั่งเศส ซึ่งมีอัตราว่างงานของแรงงานเยาวชนสูงกว่ามาก นักเศรษฐศาสตร์อย่าง Ludwig von Mises และ Murray Rothbard ต่างชี้ให้เห็นว่า ค่าแรงควรเป็นผลลัพธ์ของอุปสงค์และอุปทาน ไม่ใช่การแทรกแซงของรัฐบาล เพราะการบังคับให้ขึ้นค่าแรงขั้นต่ำสูงเกินจริง อาจทำให้ธุรกิจไม่สามารถจ้างแรงงานได้ ส่งผลให้แรงงานที่มีทักษะต่ำตกงานและถูกแทนที่ด้วยเครื่องจักรหรือระบบอัตโนมัติแทน
6. การผูกขาดและอำนาจบริษัท (Monopolies and Corporate Power)
📢 ข้อกล่าวหา #บริษัทใหญ่มีอำนาจมากเกินไป
🧐 ความจริง - การผูกขาดที่เลวร้ายมักเกิดจากรัฐให้สิทธิพิเศษ ไม่ใช่จากตลาดเสรี ในระบบตลาดเสรีแท้จริง ธุรกิจต้องแข่งขันกันเพื่อเสนอสินค้าหรือบริการที่ดีที่สุดแก่ผู้บริโภค หากบริษัทใดพยายามกดราคาหรือให้บริการที่ไม่มีคุณภาพ คู่แข่งรายใหม่สามารถเข้ามาแทนที่ได้ แต่ในกรณีที่รัฐบาลเข้ามาแทรกแซง เช่น การให้ใบอนุญาตพิเศษ การอุดหนุนบางบริษัท หรือการกำหนดข้อบังคับที่ทำให้ธุรกิจรายย่อยไม่สามารถแข่งขันได้ สิ่งเหล่านี้กลายเป็นกลไกที่สร้างการผูกขาดที่แท้จริง ซึ่งเอื้อประโยชน์ให้กับนายทุนใหญ่ที่มีสายสัมพันธ์ทางการเมือง มากกว่าที่จะเกิดจากกลไกตลาดเสรีเอง
✅ ทางออก
- ยกเลิกการคุ้มครองพิเศษจากรัฐให้กับบริษัทยักษ์ใหญ่ ซึ่งรวมถึงการยุติการให้เงินอุดหนุน การออกกฎหมายที่กีดกันคู่แข่งรายย่อย และการให้สิทธิพิเศษด้านภาษีแก่บริษัทขนาดใหญ่ กลไกเหล่านี้ไม่ได้เกิดจากตลาดเสรี แต่เป็นผลของ "ทุนนิยมพวกพ้อง" (Crony Capitalism) ที่รัฐบาลใช้อำนาจสนับสนุนธุรกิจที่มีอิทธิพลทางการเมืองแทนที่จะปล่อยให้กลไกตลาดทำงานอย่างเป็นธรรม การแข่งขันเสรีที่แท้จริงจะช่วยให้บริษัทขนาดเล็กมีโอกาสเติบโตได้โดยไม่มีการแทรกแซงจากรัฐที่เอื้อประโยชน์ให้กับผู้เล่นรายใหญ่เพียงไม่กี่ราย
7. การทำลายสิ่งแวดล้อม (Environmental Destruction)
📢 ข้อกล่าวหา #ทุนนิยมทำให้เกิดมลพิษและทำลายธรรมชาติ
🧐 ความจริง
- ประเทศที่มีตลาดเสรีมีแนวโน้มที่จะมีนโยบายสิ่งแวดล้อมที่ดีขึ้น เนื่องจากแรงจูงใจทางเศรษฐกิจและการแข่งขันทำให้บริษัทต้องพัฒนานวัตกรรมที่เป็นมิตรกับสิ่งแวดล้อมเพื่อตอบสนองความต้องการของผู้บริโภค ตัวอย่างที่เห็นได้ชัดคือสหรัฐอเมริกาและยุโรปในช่วงศตวรรษที่ 20 ซึ่งภาคเอกชนเป็นแรงผลักดันสำคัญในการพัฒนาพลังงานสะอาด เช่น พลังงานแสงอาทิตย์และพลังงานลม โดยบริษัทต่าง ๆ ลงทุนในเทคโนโลยีเหล่านี้เพราะเห็นโอกาสทางการตลาดและแรงกดดันจากผู้บริโภค ในทางตรงกันข้าม ระบบเศรษฐกิจแบบวางแผนจากส่วนกลางที่ควบคุมโดยรัฐ เช่น สหภาพโซเวียตและจีนในยุคคอมมิวนิสต์ มักละเลยสิ่งแวดล้อมเพื่อให้เกิดการผลิตในปริมาณสูง โดยมีตัวอย่างที่เห็นได้จากมลพิษทางอากาศและน้ำในประเทศเหล่านี้ การไม่มีแรงจูงใจทางเศรษฐกิจและการแข่งขันทำให้ไม่มีการพัฒนาเทคโนโลยีที่ยั่งยืน บริษัทหรือโรงงานที่ได้รับการสนับสนุนจากรัฐบาลมักมุ่งเน้นเพียงการเพิ่มผลผลิตโดยไม่คำนึงถึงผลกระทบต่อสิ่งแวดล้อม
✅ ทางออก
- ใช้แรงจูงใจทางเศรษฐกิจ เช่น การให้รางวัลทางตลาดและแรงจูงใจจากผู้บริโภค แทนการใช้มาตรการบังคับจากรัฐ ซึ่งมักสร้างผลกระทบด้านลบ เช่น การแทรกแซงของรัฐบาลที่อาจนำไปสู่การผูกขาดโดยบริษัทยักษ์ใหญ่ที่มีสายสัมพันธ์กับรัฐ ตลาดเสรีกระตุ้นให้บริษัทแข่งขันกันนำเสนอนวัตกรรมที่ลดผลกระทบต่อสิ่งแวดล้อมเพื่อตอบสนองความต้องการของผู้บริโภคโดยตรง มากกว่าการพึ่งพานโยบายอุดหนุนจากรัฐบาลที่อาจบิดเบือนกลไกตลาด
- นอกจากนี้ สิทธิในทรัพย์สินส่วนบุคคล ยังเป็นรากฐานสำคัญของระบบเศรษฐกิจที่ยั่งยืน หากเจ้าของธุรกิจและผู้ประกอบการสามารถมั่นใจได้ว่าทรัพย์สินของตนจะได้รับการคุ้มครอง พวกเขาจะมีแรงจูงใจในการลงทุนและพัฒนาธุรกิจโดยไม่ต้องกลัวการยึดครองหรือการเข้าควบคุมจากรัฐ ประวัติศาสตร์แสดงให้เห็นว่าประเทศที่มีการคุ้มครองทรัพย์สินส่วนบุคคลที่เข้มแข็ง เช่น สวิตเซอร์แลนด์และสิงคโปร์ มีอัตราการเติบโตทางเศรษฐกิจสูงกว่า ประเทศที่รัฐสามารถเข้าควบคุมทรัพย์สินได้ง่าย เช่น เวเนซุเอลาหรืออดีตสหภาพโซเวียต ที่เศรษฐกิจพังทลายจากการแทรกแซงของรัฐ
8. วิกฤตเศรษฐกิจ (Economic Crisis)
📢 ข้อกล่าวหา #ตลาดเสรีนำไปสู่วิกฤตเศรษฐกิจบ่อยครั้ง
🧐ความจริง วิกฤตส่วนใหญ่เกิดจากการแทรกแซงของรัฐ เช่น การพิมพ์เงินโดยธนาคารกลาง ซึ่งส่งผลให้เกิดภาวะเงินเฟ้อ การลดค่าเงิน และฟองสบู่ทางเศรษฐกิจ ตัวอย่างเช่น วิกฤตการณ์เศรษฐกิจปี 1929 หรือ "The Great Depression" เกิดขึ้นหลังจากที่รัฐบาลสหรัฐฯ และธนาคารกลางพยายามสร้างสภาพคล่องมากเกินไปผ่านการปล่อยสินเชื่อและการขยายตัวของเครดิต หลังจากการก่อตั้ง Federal Reserve ในปี 1913 รัฐบาลพยายามกระตุ้นเศรษฐกิจโดยการอัดฉีดเงินเข้าสู่ระบบผ่านสินเชื่อราคาถูก ซึ่งนำไปสู่การก่อตัวของฟองสบู่ในตลาดหุ้น เมื่อถึงปี 1929 ฟองสบู่แตก ทำให้เกิดการล่มสลายของตลาดการเงินครั้งใหญ่ที่สุดในประวัติศาสตร์ ในระยะยาวการควบคุมของรัฐยังนำไปสู่การลดค่าของเงินดอลลาร์ โดยเฉพาะเมื่อปี 1971 ที่สหรัฐฯ ภายใต้ประธานาธิบดีริชาร์ด นิกสัน ได้ประกาศยุติระบบมาตรฐานทองคำ (Gold Standard) ซึ่งหมายความว่ารัฐบาลสามารถพิมพ์เงินได้โดยไม่มีข้อจำกัดจากทองคำเป็นตัวค้ำประกัน นับแต่นั้นมา ค่าเงินดอลลาร์สหรัฐเสื่อมค่าลงเรื่อย ๆ ทำให้เกิดภาวะเงินเฟ้ออย่างต่อเนื่องและบ่อนทำลายเสถียรภาพของระบบเศรษฐกิจ ระบบเศรษฐกิจที่แท้จริงควรปล่อยให้ตลาดกำหนดอัตราดอกเบี้ยและสภาพคล่องเอง เพื่อป้องกันการบิดเบือนที่เกิดจากการแทรกแซงของรัฐ ในปี 2008 วิกฤตการเงินครั้งใหญ่ (Global Financial Crisis) เกิดขึ้นจากนโยบายการเงินที่ผิดพลาดของธนาคารกลางสหรัฐ (Federal Reserve) ซึ่งกำหนดอัตราดอกเบี้ยต่ำเป็นเวลานาน ทำให้เกิดการปล่อยสินเชื่อที่ไม่มีหลักประกัน (Subprime Mortgage) ในตลาดอสังหาริมทรัพย์ เมื่อธนาคารพาณิชย์และนักลงทุนเข้าซื้อพันธบัตรที่มีสินเชื่อเหล่านี้เป็นหลักประกัน ความเสี่ยงสะสมมากขึ้นเรื่อย ๆ จนกระทั่งฟองสบู่แตกในปี 2008 สถาบันการเงินขนาดใหญ่ เช่น Lehman Brothers ล้มละลาย และส่งผลกระทบเป็นลูกโซ่ไปทั่วโลก ที่สำคัญ รัฐบาลสหรัฐฯ ไม่ได้ปล่อยให้กลไกตลาดจัดการปัญหาเอง แต่กลับเข้าแทรกแซงโดยใช้มาตรการ 'Bailout' หรือการอุ้มสถาบันการเงินขนาดใหญ่ผ่านเงินภาษีประชาชน ทำให้ภาคธนาคารรอดพ้นจากผลของการบริหารที่ผิดพลาด แต่ในขณะเดียวกัน กลุ่มประชาชนทั่วไปและธุรกิจขนาดเล็กต้องเผชิญกับภาวะเศรษฐกิจตกต่ำ นักเศรษฐศาสตร์สายออสเตรียนได้ชี้ให้เห็นว่าวิกฤตนี้เป็นตัวอย่างของ ผลกระทบจากการควบคุมตลาดโดยธนาคารกลาง ซึ่งหากปล่อยให้ตลาดเสรีทำงานเอง อัตราดอกเบี้ยจะถูกกำหนดโดยความต้องการสินเชื่อที่แท้จริงของผู้บริโภคและนักลงทุน และจะไม่เกิดภาวะเงินเฟ้อของสินทรัพย์อย่างที่เคยเกิดขึ้นก่อนปี 2008
✅ ทางออก
- บิตคอยน์ซึ่งถูกสร้างขึ้นมาเพื่อเป็นเงินที่ปราศจากการควบคุมของรัฐ เป็นผลโดยตรงจากความล้มเหลวของระบบการเงินรวมศูนย์ โดยเฉพาะอย่างยิ่งมาตรฐานทองคำที่ถูกควบคุมโดยรัฐและธนาคารกลาง ในอดีต ทองคำถูกใช้เป็นเงินสำรองที่เชื่อถือได้ เพราะมีปริมาณจำกัดและไม่สามารถพิมพ์เพิ่มได้ตามอำเภอใจ อย่างไรก็ตาม ระบบนี้มีข้อเสียสำคัญ คือทองคำต้องถูกเก็บรักษาไว้ในธนาคารกลางหรือหน่วยงานที่รวมศูนย์ ซึ่งเปิดช่องให้รัฐบาลเข้าแทรกแซงและเข้าควบคุมมูลค่าของเงินได้
- ประวัติศาสตร์แสดงให้เห็นว่า รัฐบาลสหรัฐฯ ใช้อำนาจในการยึดทองคำจากประชาชนภายใต้คำสั่งฝ่ายบริหารที่ 6102 ในปี 1933 และจำกัดความสามารถของบุคคลทั่วไปในการถือครองทองคำ สิ่งนี้ชี้ให้เห็นว่าการต้องพึ่งพาทองคำในฐานะเงินสำรอง ไม่ได้ทำให้ประชาชนมีเสรีภาพทางการเงินอย่างแท้จริง เนื่องจากยังต้องพึ่งพาความไว้วางใจในสถาบันของรัฐที่สามารถเปลี่ยนนโยบายได้ตลอดเวลา
- บิตคอยน์แก้ปัญหานี้โดยทำให้เงินเป็นสิ่งที่ไม่มีใครควบคุมได้ และไม่มีหน่วยงานใดสามารถเปลี่ยนนโยบายได้ตามอำเภอใจ เครือข่ายกระจายศูนย์ของบิตคอยน์ ทำให้ไม่มีจุดรวมศูนย์ที่รัฐบาลสามารถยึดหรือแทรกแซงได้ อีกทั้งอุปทานของบิตคอยน์ ถูกกำหนดตายตัวที่ 21 ล้านเหรียญ ทำให้ไม่สามารถพิมพ์เพิ่มได้เหมือนเงินเฟียตหรือแม้แต่ทองคำที่สามารถถูกควบคุมผ่านนโยบายของธนาคารกลางได้ ทำงานบนเครือข่ายกระจายศูนย์ที่โปร่งใสและป้องกันการปลอมแปลง ช่วยให้บุคคลสามารถเก็บรักษามูลค่าได้โดยไม่ต้องพึ่งพาธนาคารกลาง ระบบนี้ยังช่วยลดอำนาจของรัฐในการบิดเบือนค่าเงิน และส่งเสริมความมั่นคงทางเศรษฐกิจผ่านกลไกของตลาดเสรี
9. การเมืองในระบบทุนนิยม
📢 ข้อกล่าวหา #ทุนนิยมสร้างนักการเมืองที่คดโกง
🧐 ความจริง
- ารแทรกแซงของรัฐต่างหากที่เป็นตัวกระตุ้นให้เกิดการผูกขาดและคอร์รัปชัน หากปล่อยให้ตลาดเสรีทำงานโดยไม่มีการแทรกแซงจากภาครัฐ การแข่งขันจะบังคับให้ธุรกิจต้องสร้างมูลค่าผ่านนวัตกรรมและคุณภาพสินค้า ไม่ใช่การวิ่งเต้นทางการเมือง ตัวอย่างเช่น ในหลายประเทศที่มีตลาดเสรีที่พัฒนาแล้ว ธุรกิจขนาดเล็กสามารถแข่งขันกับบริษัทใหญ่ได้อย่างเป็นธรรม และไม่มีการใช้กฎหมายเพื่อเอื้อผลประโยชน์ให้กับกลุ่มใดกลุ่มหนึ่ง
- ในขณะที่ในระบบเศรษฐกิจที่รัฐมีบทบาทสูง เช่น สังคมนิยม รัฐมักเป็นผู้กำหนดว่าใครได้เปรียบหรือเสียเปรียบในตลาด ซึ่งนำไปสู่การคอร์รัปชันและการใช้อำนาจเพื่อเอื้อประโยชน์ให้กับคนบางกลุ่มเท่านั้น ดังนั้น การกล่าวหาว่าทุนนิยมเป็นต้นเหตุของการเมืองที่คดโกงจึงเป็นการเข้าใจผิด และแท้จริงแล้ว การกระจายอำนาจทางเศรษฐกิจให้กับตลาดเสรีต่างหากที่เป็นแนวทางแก้ไขปัญหานี้
✅ ทางออก
- ลดบทบาทของรัฐในการแทรกแซงเศรษฐกิจ เนื่องจากการแทรกแซงมักนำไปสู่การบิดเบือนกลไกตลาด เสริมสร้างระบบพวกพ้อง (Cronyism) และลดประสิทธิภาพของการแข่งขันที่แท้จริง ตัวอย่างที่ชัดเจน ได้แก่ การให้เงินอุดหนุนแก่บางอุตสาหกรรม การกำหนดอัตราดอกเบี้ยต่ำอย่างผิดธรรมชาติ และการออกกฎหมายเอื้อประโยชน์ให้กับธุรกิจที่มีอิทธิพลทางการเมือง ซึ่งล้วนแล้วแต่ส่งผลเสียต่อเศรษฐกิจโดยรวม ในทางกลับกัน การปล่อยให้กลไกตลาดทำงานเองจะทำให้ทรัพยากรถูกจัดสรรอย่างมีประสิทธิภาพมากขึ้น ลดการคอร์รัปชัน และเปิดโอกาสให้ธุรกิจใหม่ ๆ สามารถแข่งขันได้อย่างเป็นธรรม
10. ลัทธิล่าอาณานิคมใหม่ในระบบทุนนิยม
📢 ข้อกล่าวหา #บริษัทยักษ์ใหญ่ใช้ทุนนิยมเป็นเครื่องมือขยายอำนาจ
🧐 ความจริง
- ลัทธิล่าอาณานิคมเกี่ยวข้องกับรัฐ ไม่ใช่กลไกตลาดเสรี เพราะการล่าอาณานิคมในประวัติศาสตร์เกิดขึ้นจากอำนาจของรัฐที่ใช้กำลังทางทหารและกฎหมายบังคับเพื่อยึดครองทรัพยากรและควบคุมประชากรในดินแดนอื่น ๆ ในทางกลับกัน กลไกตลาดเสรีขึ้นอยู่กับการแลกเปลี่ยนโดยสมัครใจ ไม่มีการใช้กำลังบังคับ หากตลาดเสรีเป็นตัวกำหนดความสัมพันธ์ทางเศรษฐกิจ การค้าระหว่างประเทศจะเกิดขึ้นจากผลประโยชน์ร่วมกัน ไม่ใช่จากการยึดครองทางการเมืองหรือการบังคับขู่เข็ญ
- ในยุคปัจจุบัน ลัทธิพาณิชยนิยมยุคใหม่ ยังคงปรากฏอยู่ในรูปแบบของการแทรกแซงของรัฐในตลาด เช่น การใช้ภาษีศุลกากร การอุดหนุนธุรกิจในประเทศเพื่อแข่งขันกับต่างชาติ และการจำกัดการลงทุนจากต่างประเทศ แนวทางเหล่านี้ไม่ใช่กลไกของตลาดเสรีแท้จริง แต่เป็นวิธีที่รัฐเข้ามาแทรกแซงเพื่อควบคุมเศรษฐกิจ ซึ่งนำไปสู่ความไร้ประสิทธิภาพและบิดเบือนการแข่งขัน เช่นเดียวกับที่เคยเกิดขึ้นในยุคเมอร์แคนไทล์ที่รัฐมุ่งสะสมความมั่งคั่งด้วยการควบคุมการค้า มากกว่าการส่งเสริมเสรีภาพทางเศรษฐกิจ
- ตัวอย่างที่ชัดเจนคือ นโยบายกีดกันทางการค้าระหว่างประเทศมหาอำนาจ เช่น สงครามการค้าระหว่างสหรัฐฯ กับจีน หรือการแทรกแซงของสหภาพยุโรปในด้านเกษตรกรรมผ่านเงินอุดหนุนขนาดใหญ่ สิ่งเหล่านี้ล้วนเป็นเครื่องมือของรัฐที่ขัดขวางตลาดเสรีและลดโอกาสในการแข่งขันอย่างเป็นธรรม ดังนั้น แทนที่จะกล่าวโทษทุนนิยมสำหรับปัญหาเชิงเศรษฐกิจและความไม่เท่าเทียมในโลกปัจจุบัน ควรพิจารณาว่าเป็นผลพวงของการรวมศูนย์อำนาจของรัฐผ่านกลไกที่ยังคงสืบทอดแนวคิดของ Neomercantilism
✅ ทางออก
- ส่งเสริมการค้าเสรีและสิทธิ์ในทรัพย์สินส่วนบุคคล เนื่องจากระบบทุนนิยมที่แท้จริงทำงานบนพื้นฐานของความสมัครใจและการแลกเปลี่ยนที่ยุติธรรม หากไม่มีการคุ้มครองสิทธิ์ในทรัพย์สิน การลงทุนและการสร้างมูลค่าจะถูกบั่นทอนลง ซึ่งจะนำไปสู่ความไม่แน่นอนทางเศรษฐกิจและการลดลงของนวัตกรรม ประวัติศาสตร์ได้พิสูจน์แล้วว่า ประเทศที่มีทรัพย์สินส่วนบุคคลที่มั่นคง เช่น ฮ่องกงและสิงคโปร์ เติบโตทางเศรษฐกิจอย่างรวดเร็ว ในขณะที่ประเทศที่รัฐเข้ามาควบคุมทรัพย์สินอย่างเข้มงวด เช่น เวเนซุเอลา หรืออดีตสหภาพโซเวียต กลับเผชิญกับความล้มเหลวทางเศรษฐกิจ
- การค้าเสรีช่วยลดข้อจำกัดทางเศรษฐกิจและเปิดโอกาสให้ธุรกิจทุกขนาดสามารถแข่งขันได้อย่างเป็นธรรม โดยไม่มีการแทรกแซงจากรัฐบาลที่เอื้อประโยชน์ให้กับนายทุนรายใหญ่ หากเปรียบเทียบกับลัทธิล่าอาณานิคมที่อาศัยอำนาจรัฐเพื่อขยายอิทธิพลทางเศรษฐกิจ ตลาดเสรีกลับเป็นระบบที่ขับเคลื่อนด้วยข้อตกลงโดยสมัครใจและผลประโยชน์ร่วมกัน
สุดท้าย คุณเคยตั้งคำถามไหมว่าทุนนิยมที่แท้จริงเป็นอย่างไร เป็นไปได้ไหมว่าปัญหาทางเศรษฐกิจที่เราเห็นไม่ได้เกิดจากทุนนิยมตลาดเสรี แต่เกิดจากการแทรกแซงของรัฐ หรือคุณคิดว่าทุนนิยมมีข้อเสียที่ต้องแก้ไข ถ้าทุนนิยมมีข้อดีและข้อเสีย คุณคิดว่าควรปรับปรุงหรือควบคุมอย่างไร หรือควรปล่อยให้ตลาดเสรีทำงานโดยไม่มีการแทรกแซงเลย มาแลกเปลี่ยนความคิดเห็นกัน บางทีสิ่งที่คุณเคยเชื่อเกี่ยวกับทุนนิยมอาจเปลี่ยนไปเมื่อคุณได้เห็นมุมมองใหม่ ๆ
หวังว่าจะมีคนแชร์บทความนี้ออกไปให้เพื่อนของคุณได้เข้าใจทุนนิยมอย่างถูกต้อง
Siamstr #เสรีภาพทางเศรษฐกิจ
-
 @ 33baa074:3bb3a297
2025-03-20 08:18:06
@ 33baa074:3bb3a297
2025-03-20 08:18:06Overview Remote monitoring technology of pavement sensors is an important part of modern traffic management. It uses high-tech means to achieve real-time monitoring of pavement conditions, improve road safety, optimize traffic flow, and provide valuable data support for decision makers.
Technical background and application scenarios Traditional traffic monitoring methods rely on manual patrols or fixed-point observations, which are not only inefficient but also difficult to achieve full coverage. The remote monitoring technology of pavement sensors integrates multiple sensors to achieve all-round monitoring of pavement conditions, which can effectively cover both busy streets in cities and remote highways.
System composition and key technologies The pavement monitoring system is mainly composed of meteorological sensors, collectors, pole brackets, power supply systems and cloud platforms. Key technologies include comprehensive acquisition control technology, computer software technology, communication technology, etc. These technologies work together to ensure real-time data collection, processing and transmission.
Working principle and types of pavement condition sensors The pavement condition sensor is mainly based on spectral telemetry technology, and detects the pavement condition through infrared transmitters and receivers. The sensor can distinguish the reflection wavelengths caused by different substances such as water, ice, and snow on the road surface to achieve accurate measurement of the pavement condition. Road condition sensors are mainly divided into two types: telemetry and embedded. Telemetry sensors are based on optical principles, while embedded sensors integrate multiple measuring probes to directly contact the road surface for measurement.
Advantages and application effects of remote monitoring technology The remote monitoring technology of road sensors has significant advantages, including all-weather monitoring capabilities, real-time data transmission, and cross-departmental data sharing. These advantages enable traffic management departments to grasp road condition information anytime and anywhere, respond in a timely manner, and improve road safety and traffic efficiency.
Cloud platform functions and data management As an important part of the road monitoring system, the cloud platform provides a wealth of functions, including real-time data display, historical data display, data curve analysis, data export, etc. The stability, reliability and easy expansion of the cloud platform make data management more efficient and scientific.
Future development trends and challenges With the continuous development of the Internet of Things and big data technology, the remote monitoring technology of road sensors will develop in a smarter and more accurate direction. In the future, sensors will be able to achieve more refined monitoring, provide more early warning information, and help traffic management departments better cope with complex traffic environments.
In short, the remote monitoring technology of road surface sensors is an important means of modern traffic management. It improves road safety, optimizes traffic flow, and provides valuable data support for decision makers through high-tech means. With the continuous advancement of technology, road surface monitoring in the future will be more intelligent and accurate.
-
 @ 33baa074:3bb3a297
2025-03-20 07:59:14
@ 33baa074:3bb3a297
2025-03-20 07:59:14The application of radar water level meter in agricultural irrigation is mainly reflected in the following aspects:
Real-time monitoring and control: radar water level meter can monitor the water level changes of irrigation channels or reservoirs in real time, and provide accurate water level data for irrigation management departments. These data help to reasonably allocate water resources and improve irrigation efficiency. For example, by analyzing the data collected by radar water level meter, we can understand the changing law of channel water level and provide a scientific basis for irrigation management.
Early warning function: radar water level meter can set water level warning value. When the water level exceeds the warning value, the system will automatically issue an alarm to remind relevant personnel to take corresponding measures to prevent the water level from being too high or too low and causing adverse effects on crops.
Water-saving irrigation: The application of radar water level meter helps to achieve precise irrigation, reduce water waste, reduce farmland drainage, and reduce the impact on the environment. For example, in the main irrigation channel of a major agricultural province, after using radar water level meter, the management department can grasp the changes in channel water level in real time, adjust irrigation strategies in time, and avoid water waste.
Intelligent irrigation management: The radar water level meter can be connected to the remote monitoring platform, and farmers can view the flow of each irrigation area in real time through mobile phones, computers and other devices. Through data analysis, farmers can identify which areas have higher water demand and which areas have lower water demand, so as to optimize the irrigation strategy.
Improve crop yield and quality: The radar water level meter monitoring system can collect irrigation data in real time, such as soil moisture, temperature, irrigation water volume and other information, to help farmers better decide on key factors such as irrigation time and water volume, and improve crop yield and quality.
In summary, the application of radar water level meters in agricultural irrigation not only improves the efficiency of water resource utilization, but also enhances the operational safety of irrigation systems, providing huge potential and application value for modern agricultural irrigation management.
-
 @ 33baa074:3bb3a297
2025-03-20 07:33:57
@ 33baa074:3bb3a297
2025-03-20 07:33:57As an advanced flow measurement device, radar flow meters play an important role in many fields mainly through their high precision, high stability and long life. Although there are few direct descriptions about radar flow meters optimizing energy use, we can indirectly understand their contribution to energy optimization from their applications in water resource management and industrial process control.
Energy optimization in water resource management The application of radar flow meters in water resource management can significantly improve energy efficiency. For example, in irrigation channels, radar flow meters can help irrigation managers to rationally allocate water resources and ensure that farmland receives the right amount of irrigation water. This precise water resource management can not only improve the efficiency of water resource utilization, but also reduce unnecessary energy consumption, such as avoiding excessive groundwater extraction or unnecessary pumping processes.
Energy optimization in industrial process control In industrial process control, radar flow meters can achieve accurate measurement and management of liquid flow. This precise flow control helps optimize the production process and reduce energy waste. For example, in industries such as chemicals, petroleum, and electricity, production efficiency can be improved and energy consumption can be reduced by accurately controlling the flow of raw materials and products.
Technical advantages of radar flow meter The non-contact measurement characteristics of radar flow meter make it unaffected by sewage corrosion and sediment during the measurement process, and can maintain long-term stable measurement accuracy. In addition, its maintenance is simple, reducing maintenance costs and time. These technical advantages not only improve the accuracy of flow measurement, but also help reduce long-term operating costs and energy consumption.
Conclusion Although the radar flow meter itself does not directly optimize energy use, it indirectly promotes energy efficiency improvement in water resource management and industrial process control by improving the accuracy and reliability of flow measurement. This optimization not only helps save energy, but also reduces operating costs and achieves the goal of sustainable development.
-
 @ 6b0a60cf:b952e7d4
2025-03-20 07:36:17
@ 6b0a60cf:b952e7d4
2025-03-20 07:36:17このイベント自身をnaddr形式で参照する nostr:naddr1qvzqqqr4gupzq6c2vr8l8m9952e9qhxt8acn8kzzypzuhm6q70fvvxylkzu49e75qydhwumn8ghj7mnjv4kxz7fwvvkhxar9d3kxzu3wdejhgtcqp5cnwdpjxs6n2de3xyenxwql6rq76
-
 @ da0b9bc3:4e30a4a9
2025-03-20 06:29:09
@ da0b9bc3:4e30a4a9
2025-03-20 06:29:09Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/918547
-
 @ 18f5f318:a3a80202
2025-03-20 06:03:15
@ 18f5f318:a3a80202
2025-03-20 06:03:15In today's fast-paced world, accumulating unwanted items and clutter is a common challenge for both individuals and businesses. Professional junk removal services offer a practical solution, providing numerous benefits that extend beyond mere decluttering. This article explores the advantages of hiring professional junk removal services, supported by relevant statistics and insights.
**1. Time and Effort Savings ** Managing and disposing of junk can be a time-consuming and physically demanding task. Professional junk removal services streamline this process by handling all aspects of removal, allowing clients to focus on more important activities. Their expertise ensures efficient sorting, loading, and disposal, significantly reducing the time and effort required from clients.
**2. Proper Waste Disposal Practices ** A key advantage of professional junk removal is their commitment to responsible waste disposal. They possess the knowledge to categorize items into recyclable, reusable, and disposable materials, adhering to local regulations and environmental guidelines. This ensures that hazardous materials are handled appropriately, minimizing environmental impact and promoting sustainability.
**3. Enhanced Safety and Health ** Handling bulky or hazardous items without proper equipment and training can pose safety risks. Professional junk removal teams are equipped to manage such items safely, reducing the risk of injuries. They also address potential health hazards by removing debris that could harbor pests or mold, contributing to a healthier living or working environment.
**4. Access to Appropriate Equipment ** Professional services come equipped with the necessary tools and vehicles to handle various types of junk removal tasks. Whether it's heavy appliances or large volumes of debris, they have the equipment to manage the job efficiently. This access to specialized tools ensures a smoother and faster removal process, which might be challenging to achieve independently.
**5. Cost-Effectiveness ** While hiring a professional service involves an upfront cost, it can be more economical in the long run. DIY junk removal may incur expenses such as vehicle rental, fuel, and disposal fees, not to mention the value of your time. Professional services often provide transparent pricing and handle all aspects of the removal, potentially saving clients money and hassle.
**6. Environmental Responsibility ** Many junk removal companies prioritize eco-friendly practices by recycling or donating items whenever possible. This commitment to sustainability reduces the amount of waste sent to landfills and supports community initiatives. By choosing such services, clients contribute to environmental conservation efforts.
**7. Improved Space Utilization ** Removing unwanted items frees up valuable space in homes or offices, allowing for better organization and functionality. A clutter-free environment can enhance productivity, reduce stress, and create a more aesthetically pleasing space.
**8. Compliance with Legal Regulations ** Proper disposal of certain items is mandated by law, and non-compliance can result in fines. Professional junk removal services are well-versed in local regulations and ensure that all items are disposed of legally and ethically, mitigating potential legal issues for clients.
**9. Support for Large-Scale Projects ** For large-scale cleanouts, such as estate clearances or office renovations, professional services provide the manpower and resources necessary to handle the job efficiently. They can manage high volumes of junk, ensuring timely completion of projects without burdening clients.
**10. Peace of Mind ** Entrusting junk removal to professionals offers peace of mind, knowing that the task is handled efficiently, safely, and responsibly. Clients can rest assured that their space will be cleared without the stress and physical exertion associated with DIY removal. Industry Insights
The junk removal industry has seen substantial growth in recent years. According to industry reports, the sector generates significant revenue and provides numerous employment opportunities, reflecting the increasing demand for these services.
**Conclusion ** Professional junk removal services offer a comprehensive solution to managing unwanted items, providing benefits that encompass time savings, safety, environmental responsibility, and cost-effectiveness. By opting for these services, individuals and businesses can enjoy cleaner, more organized spaces while contributing positively to the environment and society.
-
 @ e5de992e:4a95ef85
2025-03-20 05:01:41
@ e5de992e:4a95ef85
2025-03-20 05:01:41Market Overview
As of March 19, 2025, U.S. stock markets experienced a notable rally, driven by the Federal Reserve's decision to maintain current interest rates and signals of potential rate cuts later this year.
Index Performance
-
Dow Jones Industrial Average (DJIA):
Increased by 383.32 points (0.9%) to close at 41,964.63. -
S&P 500:
Rose 1.1%, ending at 5,675.29. -
Nasdaq Composite:
Advanced 1.4% to 17,750.79. -
Russell 2000:
Gained 1.6% to close at 2,082.08.
Key Drivers and Events
Federal Reserve's Monetary Policy
- The Federal Reserve opted to keep its key interest rate unchanged amid increased economic uncertainty, partly due to recent tariff measures.
- The central bank also indicated the possibility of two rate cuts by the end of the year to support economic growth.
Corporate Earnings
- Boeing (BA):
Shares rose significantly, contributing to gains in the Dow. - Tesla (TSLA):
Increased by 4.7%, outperforming competitors.
Geopolitical Factors
- Ongoing trade tensions and tariff policies, especially those announced by President Donald Trump, have added to market volatility.
- These policies are influencing investor sentiment and economic outlooks.
Global Market Context
- European Markets:
Generally rose, buoyed by fiscal initiatives and supportive policies. - Asian Markets:
Experienced slight declines. - Regional Note:
Indonesia's stock market faced a temporary suspension due to significant declines.
Commodity and Bond Markets
-
Oil:
Prices climbed, with West Texas Intermediate (WTI) futures approaching stability at $67.85 per barrel, reflecting supply concerns amid reported inventory drawdowns and limited ceasefire conditions in the Russia-Ukraine region. -
Gold:
Prices reached a record high, driven by the Fed’s revised economic projections and a flight to safety among investors. -
10-Year Treasury Yield:
Decreased following the Fed's rate decision, indicating increased demand for safer assets.
Market Outlook
Investors are advised to closely monitor upcoming economic indicators—such as employment data and consumer spending reports—to assess the economy's trajectory. Additionally, the Federal Reserve's future policy decisions will play a crucial role in shaping market dynamics in the near term.
-
-
 @ d57360cb:4fe7d935
2025-03-20 04:05:59
@ d57360cb:4fe7d935
2025-03-20 04:05:59A story about people
It was a rainy day in the busy city. The type of day when a dark silence envelops the air, allowing the hard thuds of rain to paint the concrete. I enjoy the evening in the city. The neon lights enliven the darkness, giving flair to the city as a whole. Every color you can think of is in these billboards; they’re bright pink, red, green, and so on, almost like a 14-year-old who plays too many sci-fi games designed it. As the city dimmed, I took a trip to my favorite café, Speedy’s. There’s nothing particularly special about this café. It holds an average rating of 4.0 stars online; it has cushy booth seats. The coffee is mid-tier, a bit watered down, but I don’t mind since I’m not too much of a fan of a strong blend. They have enough food items to keep you satisfied, but nothing to make it exceptional. Maybe that’s why I’ve come to love a café like this; it’s not extravagant, it blends in, it’s how a café should be; it meets its mark. Sometimes that’s all we hope for in things, even in people.
I’m good friends with the owner; she noticed me coming in often, and one night while the café was deserted and empty, we struck up a conversation. It was mere small talk on the first occasion, the simple things like how your day is, what part of the city you live in, what you do for work. It felt like a barrier of entry to a deeper well we both had yet to discover. At night, Speedy liked to switch all the lights to red; it gave a special ambience to the café, it relaxed you, and highlighted a lot of the art and design in the room. It almost feels like someone made the café to be lit red; when the regular lights were on, it was a plain old café. Once those lights came on, it became something entirely vivid and alive like those neon skyscrapers in the city. The thing about the nighttime was no one came into the café; it’s like they didn’t even know it existed even though the open sign continued to hang till 11:00 pm. People had more important places to be or they thought going to a café at night was an odd choice.
I frequented Speedy’s three times a week on average, but I always showed up on rainy days. There was no reason behind this; I felt drawn to the café, to Speedy, and to the atmosphere created by those red lights. I walked in and Speedy was at the counter blending a mint tea. I could smell the mint from the moment I walked in; it cleared my nose and I was breathing clearer than ever. It had me wondering how long my nasal passages had been blocked and how unfortunate it is to have a stuffy nose. I recalled a quote I heard once: ‘An ordinary man wishes for a million things, a sick man only has one.’ I sat at the corner booth. Speedy knew the drill. So, she made a black coffee with one cream and two sugars. I don’t mind coffee in the evening. Being an avid drinker, the effects of caffeine no longer do much to me; my mom had the same phenomenon, it’s in the genes.
Speedy had on blue jeans that hovered right above her ankles, she wore clean, new-looking white sneakers and a tiny horizontal striped t-shirt. The sleeves hugged her arms nicely, she was oddly in great shape; she used to be an Olympic sprinter but no one had a clue. She had a diamond face shape, high cheekbones, and a soft welcoming face, and always wore her hair in a messy bun. She’d recently left for a vacation to Hawaii and appeared to have a nice brown tan from the trip.
We never ate much when we got together to talk. The conversation was enough to feed our souls. The thing about Speedy was she was the exact opposite of her name, which made no sense to me. She was never in a rush, always calm, composed in each action. She loved to live in the silence of life, never speaking too soon, thinking, never rushing anywhere. To her, time didn’t seem to exist; she set her own pace in life, devoid of what the world was doing. I found it an honorable skill to have, as I was the exact opposite; in essence, my name should’ve been Speedy. I was always in a rush, always frantic and anxious. I couldn’t sit still; I had to go, to be on the move, doing something at all times. Overthinking everything twice over. When we’d talk, it would be as if two species were encountering a life so unknown to the other. We discussed everything: music, especially jazz, art, culture, life, cars, and games. If it existed, it found a place in our canvas.
Slow and smooth as ever, Speedy came to the booth with a grin on her face.
Speedy: Here’s your coffee, as usual.
Narrator: *nods head* I wanted to ask you what the story behind that painting is.
To the far right of the room on the wall hung a painting that stretched from the ceiling to close to the floor. I’d never seen a canvas that size before. This was a new piece, no doubt; as I sat down in the booth, I couldn’t help but stare. It gripped me and left me blank. Speedy turned her head and glanced for a while; I don’t know how long she was looking, but she seemed to be transported somewhere far away. She finally turned back.
Speedy: That’s “color and contrast” (artist unknown). I found it after I fell out of love. I’ve had it for a while; I just never decided to put it up until two weeks ago.
Narrator: It’s an interesting piece; I can’t find the words for it, but I can’t take my eyes off it.
The painting had the perfect mix of dark and light colors, areas of bright luminance and dark depth. It engrossed you. When Speedy said she found it when she fell out of love, somehow I understood her. The painting made me reminisce about a love I once had. Maybe that’s where she was teleported to when she stared blankly at it. The painting invited you back to that place of both the light and dark parts. The title began to make sense to me. All the while, “Romance” by Hiroshi Suzuki played in the background.
Speedy: A few years after a devastating heartbreak, I was on a week-long sabbatical in Ojai, California. I stayed in an old inn on a hill near a lake. While I was there, I would take a morning walk to the lake to enjoy the birds, reflect, and drink my morning coffee. The first time I went down the hill, I spotted the huge canvas propped up in front of the lake and a tiny glass house right next to it. The glass was fully tinted so you couldn’t see inside at all. It looked like it had no doors; when the sun shone on it, it reflected back an almost platinum silver glow. Standing outside was a man facing the canvas. He had on a baggy set of linen clothes, a beaded necklace, sandals, long grey and black hair, and a big goatee. The man was immersed, almost looked possessed, and he would violently strike the canvas with his brush. Then he would abruptly stop and he would be gentle with the canvas, adding in finer details; then he would explode into a violent rhythm again. He continued this for hours, and I would visit the lake each morning to sit and watch. I always had the feeling the man knew he was being watched. To him, it was a performance, a show, somewhat of a grand finale, I as the only witness. My final morning there, I went down to the lake; the man was sealing the painting, signaling that he had finished it. He was wrapping rope around it to secure it. Once he finished, he turned with sunglasses on, stared at me for what felt like an eternity, and then signaled for me to come over. He took a seat on his wooden stool as I approached, pulling out a leather notebook; he ripped a page out of it and handed it to me. The man was not from California; I couldn’t tell where he was from, he didn’t speak English at all, or so it seemed. His silence was his voice; it didn’t feel strange at all at the time, but as I retell this story, it seems a bit mystical. I took the letter, and the man bowed to me. Once he finished bowing, he got up and walked into the glass house and closed the door. He never came back out. I was confused, so I read the note in hard-to-read writing; all it said was ‘a gift of love, yours.’ I stared blankly at the wrapped painting and took it with me. I’ve had it stored in the back of the café for years, never opening it once; when I put it up 2 weeks ago, that was the first time I saw it.
At this point, Speedy put her head down, and I could see tears falling in her lap. I figured it was best to say nothing for a while.
Speedy: Unwrapping the painting felt like reopening the wound of my broken heart; it held a power that was unexplainable. It made me shake and gave me cold chills. I’m not sure why I decided to open it, but I did. I did so with extreme caution, unwrapping the paper and untying the rope that held it together. As I saw the painting, I began to get dizzy, as if I had taken drugs and the high was hitting unexpectedly. It felt like an invisible cloak had surrounded me from every angle; I couldn’t believe what I was seeing. It wasn’t a painting but a full story. I want to show you something.
Speedy got up and I followed her to the painting. We stood in front of it and I could feel a magnetic pull; I was experiencing that cloak. She then pointed to the center of the painting; it was cut in a square that was very hard to notice. She pushed on the corner and it swiveled around, unveiling words on the back of the painting.
Speedy: That man engraved this message on the back; when I read it, my heart seemed to scream out and burst. Not in a bad or good way, but more so as a natural reaction. I can’t explain what it did, but it took care of me. Like a potion that was reserved for the right moment, if you receive it at the wrong time, you won’t get the desired effect. Maybe that’s why you came here tonight.
I sat and stared at the words.
“Color can only appear in a place of non-color, in a place where there is no flair, no fill. Color could be light filling darkness, a complement, not an opposite. Love is color, as it complements the blank canvas of emptiness. It takes the form of a blank canvas and makes its work known. It draws you in; you can’t pay attention to anything else; it’s as if the lover who has evoked this is as wide as the vast sky. As bright as a full moon. Staring into their eyes, you can no longer see the borders that the canvas inhabited; everything has become the canvas. Everything has become the art, the intricate colors and the strokes. The separation that was present before, whether noticed or not, is no longer the picture. It is now whole. It’s complete, with nothing to add; it towers over you and envelops you. You can’t believe how high it’s reached or how wide it is. It is both flowing above, below, beyond, and through your entire being. You can no longer distinguish where you and the love begin and end.“
Like the mint tea that cleared my nose, my heart cleared the way; it felt like it could finally breathe. I sat in disbelief and wondered how long I had been that way.
-
 @ 6e0ea5d6:0327f353
2025-03-20 03:01:46
@ 6e0ea5d6:0327f353
2025-03-20 03:01:46A quiet, meek, and peaceful man is not necessarily a benevolent person. Only the one who harbors powerful hatred and malice within but voluntarily controls it is truly worthy of being called a man of honor.
In the business world, some people mistakenly confuse courtesy and politeness with excessive sensitivity and emotional cowardice. They speak so meekly that they even stammer. Fearing to offend others, they swallow their opinions. The ego enslaves with the worst kind of chains: the need for self-affirmation and validation. They constantly apologize for everything: “sorry for this,” “sorry for that,” “sorry for such and such.”
By behaving this way, one not only earns the listener’s contempt, disrespect, and anger but also significantly diminishes their reputation and moral standing in the eyes of others. They will never be seen as a strong leader. They will never gain the trust of subordinates. And they will never have important tasks delegated to them by their superiors.
With respect, honor, and silence, one can enter and exit any place. Those who understand both the streets and the world beyond them achieve peace and gain unrestricted access. Always consider the protection of your reputation. Do not allow mockery to test your ability to maintain self-respect.
True mastery in interpersonal interactions lies in discerning which provocations must be confronted and which deserve to be ignored.
Like a skilled swimmer who understands the currents and adapts to them, you must learn to navigate the murky waters of the world, responding with the necessary strength and wisdom in each situation.
The key to success does not lie in servile submission but in assertiveness and reciprocity. Treat others as they truly deserve to be treated, and in doing so, you will not only earn respect but also pave the way for genuine and lasting success.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ f6488c62:c929299d
2025-03-20 04:15:12
@ f6488c62:c929299d
2025-03-20 04:15:12" ไขคำตอบผ่านมุมมอง Ethereum vs Solana" คุณเคยสงสัยไหมว่า... ทุกวันนี้แฮ็กเกอร์ระดับโลกอย่างกลุ่ม Lazarus จากเกาหลีเหนือเลือกโจมตีคริปโตผ่านช่องทางไหน? ทำไมเราถึงเห็นข่าวแฮ็กเหมือง Blockchain สุดอื้อฉาวบ่อยครั้ง ทั้งที่เครือข่ายบล็อกเชนถูกออกแบบมาให้ปลอดภัย? คำตอบอาจซ่อนอยู่ใน "จุดอ่อน" ของระบบนิเวศคริปโตเอง โดยเฉพาะสองยักษ์ใหญ่อย่าง Ethereum (ETH) และ Solana (SOL) ที่ต่างมีทั้งจุดแข็งและช่องโหว่ให้โจรไซเบอร์จ้องจับตาฉกตังคุณ!
ทำไม Ethereum ถึงเป็นอาหารจานโปรดของแฮ็กเกอร์?
1. "เงินมันเยอะ... ดึงกิเลสใจให้อยาก"
Ethereum คือศูนย์กลาง DeFi ที่มีเงินไหลเวียนมหาศาล มูลค่าทั้งระบบ (TVL) สูงกว่า 4 หมื่นล้านดอลลาร์ แค่คิดภาพว่าแฮ็กเกอร์เจาะระบบได้ครั้งเดียวก็รวยเป็นเศรษฐี แถมยังมี dApps มากมายให้เลือกโจมตี ไม่แปลกที่เป้าหมายแรกจะพุ่งมาที่ ETH!
2. สัญญาอัจฉริยะ... มันคือ ดาบสองคมแหละ
Smart Contract บน Ethereum ใช้ภาษา Solidity ที่มีความยืดหยุ่น แต่ก็เป็นดาบสองคม! แค่โค้ดผิดพลาดนิดเดียวก็สร้างความเสียหายมหาศาล เหมือนเหตุการณ์ Ronin Bridge ที่ถูกเจาะจนสูญเงิน 625 ล้านดอลลาร์ หรือการโจมตีแบบ Reentrancy ที่เคยทำให้ DAO ล่มในปี 2016
3. สะพานข้ามเชน... กับดักล่อแฮ็กเกอร์
ทุกวันนี้ Ethereum เชื่อมต่อกับเครือข่ายอื่นผ่าน Bridge และ Layer 2 อย่าง Optimism/Arbitrum ซึ่งสะพานเหล่านี้คือจุดอ่อนชั้นดี! เพราะต้องเก็บเงินสำรองจำนวนมาก ยิ่งถ้า Audit ไม่รอบคอบ แฮ็กเกอร์ก็ฉกเงินออกได้สบาย เหมือนกรณี Poly Network ที่ถูกขโมย 611 ล้านดอลลาร์ในปี 2021
Solana ปลอดภัยกว่า จริงหรือ?
1. เร็วแต่เสี่ยง... ปัญหาที่ซ่อนในระบบ
Solana ขึ้นชื่อเรื่องความเร็ว 65,000 TPS และค่าธรรมเนียมถูก แต่ความเร็วอาจมาพร้อมความเสี่ยง! การใช้เทคนิค Parallel Processing อาจมีช่องโหว่ที่ยังไม่ถูกพบ เช่น กรณี Wormhole Bridge ถูกเจาะจนสูญ 326 ล้านดอลลาร์ในปี 2022
2. ระบบนิเวศเพิ่งเกิดไม่นาน... เหมือนบทเรียนที่ยังไม่ครบหลักสูตร
dApps บน Solana ส่วนใหญ่ยังใหม่และขาดการตรวจสอบ (Audit) ที่เข้มงวด เมื่อเทียบกับ Ethereum ที่ผ่านสนามรบมานาน โครงการใหม่ ๆ อาจมีช่องโหว่หลงเหลือให้แฮ็กเกอร์เสาะแสวงหา
3. Validator น้อย... เป้าสำหรับโจมตี
Solana มี Validator เพียง 1,000+ โหนด เทียบกับ Ethereum ที่มีถึง 5 แสนโหนด! ตัวเลขนี้ทำให้เสี่ยงต่อการโจมตีแบบ 51% มากกว่า แม้จะยังไม่เกิดขึ้นจริง แต่เป็นจุดที่นักพัฒนาต้องจับตาอย่างใกล้ชิด
เปรียบเทียบแบบเห็นภาพ: Ethereum vs Solana ใครเสี่ยงกว่า?
- เงินในระบบ → Ethereum ชนะขาด (แต่ก็เป็นเป้าหมายใหญ่)
- ช่องโหว่ Smart Contract → ทั้งคู่มีปัญหา แต่ Solana อาจเสี่ยงกว่าเพราะ Audit น้อย
- จุดอ่อนเครือข่าย → Ethereum มีปัญหา Bridge ส่วน Solana กลัวระบบล่ม
- ภาษาโปรแกรม → Solidity (Ethereum) ยืดหยุ่นแต่ซับซ้อน vs Rust (Solana) ปลอดภัยกว่าแต่ยังใหม่
สรุปแบบตรงไปตรงมา
- Ethereum คือ "หมีตัวใหญ่" ที่แฮ็กเกอร์อยากล่า เพราะเงินมาก แม้จะป้องกันดี แต่มีจุดให้โจมตีหลายชั้น
- Solana คือ "เหยื่อดาวรุ่ง" ที่ถ้าเกิดช่องโหว่ร้ายแรง อาจถูกโจมตีแบบถล่มเละได้ง่าย
แฮ็กเกอร์อย่างกลุ่ม Lazarus ไม่ได้สนใจว่าเครือข่ายไหนเก่งกว่า แต่พวกเขามองหา "ช่องโหว่ที่ทำเงินได้เร็ว" มากกว่า! ตอนนี้ Ethereum ยังครองแชมป์เป้าหมายยอดนิยม แต่ถ้า Solana เติบโตเร็วโดยไม่แก้จุดอ่อน วันหนึ่งอาจกลายเป็นเหยื่อรายใหญ่ได้ไม่ยาก
วิธีป้องกันตัวให้รอดจากมือแฮ็กเกอร์
สำหรับนักลงทุนทั่วไป
- อย่าเก็บเงินไว้ใน Exchange นาน เปลี่ยนมาใช้ Hardware Wallet อย่าง Ledger/Trezor
- เช็กประวัติการ Audit ของโปรเจกต์ผ่านเว็บไซต์อย่าง CertiK หรือ Hacken ก่อนลงทุน
สำหรับนักพัฒนา
- ทดสอบ Smart Contract อย่างน้อย 3 รอบ และจ้างบริษัท Audit มืออาชีพ
- ใช้ Oracle จากหลายแหล่ง เพื่อป้องกันการป้อนข้อมูลผิดพลาด
สำหรับโปรเจกต์คริปโต
- สร้างกองทุนประกัน (Insurance Fund) เผื่อถูกแฮ็ก
- อัปเดตระบบรักษาความปลอดภัยแบบ Real-Time ตลอดเวลา
สุดท้ายนี้... อย่าลืมว่า "ไม่มีระบบไหนปลอดภัย 100%"
ไม่ว่า Ethereum หรือ Solana ก็ตาม การรู้เท่าทันและป้องกันตัวเองคืออาวุธที่ดีที่สุด ติดตามข่าวสารความปลอดภัยสม่ำเสมอ และอย่าวางใจระบบใดระบบหนึ่งแบบสุดใจ — เพราะแฮ็กเกอร์ก็อัปเกรดตัวเองทุกวันเช่นกัน!
แล้วคุณล่ะ... คิดว่าเครือข่ายไหนน่ากังวลที่สุด? แชร์ความเห็นไว้ได้เลย!
-
 @ a93be9fb:6d3fdc0c
2025-03-20 02:54:52
@ a93be9fb:6d3fdc0c
2025-03-20 02:54:52Publishing new article
-
 @ 8d34bd24:414be32b
2025-03-20 01:45:49
@ 8d34bd24:414be32b
2025-03-20 01:45:49This post was inspired by my Pastor’s sermon this morning. I’ve read this passage a bunch of times. I’ve always seen Jesus’s divinity. I’ve also seen the disciples’ lack of faith, but there is so much more to get out of this passage. It shocks me that I never saw it before and just had to share.
Now on one of those days Jesus and His disciples got into a boat, and He said to them, “Let us go over to the other side of the lake.” So they launched out. But as they were sailing along He fell asleep; and a fierce gale of wind descended on the lake, and they began to be swamped and to be in danger. They came to Jesus and woke Him up, saying, “Master, Master, we are perishing!” And He got up and rebuked the wind and the surging waves, and they stopped, and it became calm. And He said to them, “Where is your faith?” They were fearful and amazed, saying to one another, “Who then is this, that He commands even the winds and the water, and they obey Him?” (Luke 8:22-25)
It is obvious from this passage, that Jesus is divine. It reminds us of Genesis 1 when God speaks the waters into existence. It reminds me of Job:
“Or who enclosed the sea with doors\ When, bursting forth, it went out from the womb;\ When I made a cloud its garment\ And thick darkness its swaddling band,\ And I placed boundaries on it\ And set a bolt and doors,\ And I said, ‘Thus far you shall come, but no farther;\ And here shall your proud waves stop’? (Job 38:8-11) {emphasis mine}
Jesus spoke and the wind and waves instantly complied. All was instantly calm. Jesus’s actions scream His divinity, but there is so much more to get out of this passage in Luke 8.
Why?
My pastor asked everyone a key question, “When Jesus told His disciples to get in the boat and to cross to the other side, did He know there would be a big, life threatening storm?” The kids at church wisely shouted, “Yes!”
Several of Jesus’s disciples were fishermen. They worked their entire lives fishing in boats in the Sea of Galilee. The were familiar with boats, wind, waves, and storms, and yet they were terrified by this storm. This was not a little storm. This storm was tossing around the boat and splashing waves of water into the boat threatening to capsize it in the middle of this large body of water.
I can somewhat relate (but not fully). I grew up in Florida and we would occasionally take a boat a couple of hours across the ocean to and from the Bahamas (Abaccos). One time we had to make the crossing on a particular day to get me back to head off to college. At this time, there was a Hurricane in the gulf (other side of Florida) that were making really big waves. If my memory is correct, we were in a 34 foot long boat and the waves were taller than the boat was long. My Dad would give full throttle to ease up one side of wave and then pull back as we shot down the far side of the wave and then again and again for hours. If the engine had failed, we would have turned sideways and been capsized. If my Dad had not kept the boat straight into the waves, we would likely have capsized, but my Father knew what to do and we made it safely to shore.
Jesus knew this giant storm was going to blow up, but He told His disciples to head right into what would soon be a giant storm. One key thought that I had previously missed is that He did not send them into the storm alone. He went with His disciples.
Initially the disciples tried to battle the storm themselves, but it was a losing proposition. They were losing the battle with the storm and losing it badly. Finally, they went to Jesus. I like how the NIV says it, “The disciples went and woke him, saying, ‘Master, Master, we’re going to drown!’” Mark 4:38 says, “Jesus was in the stern, sleeping on a cushion. The disciples woke him and said to him, ‘Teacher, don’t you care if we drown?’” The disciples didn’t just ask for help; they accused Jesus of not caring. They called Him “Master” and “Teacher,” instead of “God” or “Lord.”
So going back to my Pastor’s question, why did Jesus, who knew there was going to be a terrible storm, tell His disciples to cross the water at that time? Was He teaching His disciples to trust in Him? Was He teaching His disciples to ask Him for help when they had a need? Was He teaching them who He was in a way that they would never forget? I think the answer to all of these questions is clearly, “Yes!”
Application
Now we need to look at this passage and ask, “what do we need to take away and learn from this passage?” and “how can we apply this passage?”
I think there are several key points:
-
Jesus knew what was about to happen to them.
-
Jesus had a plan and a purpose for putting them in this fearful and life threatening situation.
-
This hardship had a good purpose.
-
Jesus was with them through it all.
So often I have people who want to deny that a loving God would intentionally put themselves or others in uncomfortable, scary, or dangerous situations. They say, “God wouldn’t do that.” or “Why would God do that?” Yes, God does cause us to go through hard times (I refuse to say bad), but not to cause us pain or hardship, but to grow us in our faith and witness.
It is a rare person who grows in faith during ease and pleasant circumstances. Most of us require hardship to force us to stop doing everything on our own and to trust Jesus and to lean on His power (Yes, I am speaking from personal experience). Nothing glorifies God more than resting in Him during the storm. Yes, God cares and loves you very much. Yes, God is with you through every hardship you will ever experience. Yes, God wants the best for you. We may not appreciate it in the moment, but God cares more about your eternal good than your momentary ease and happiness. He gives you what you need instead of what you want.
The amazing thing is that when you learn to trust in Him, when you learn to rely on His power, and when you learn to look for His good work in every situation, you will find a joy and peace like you never imagined. Instead of chasing everything looking for the perfect situation to make you happy, you will rest in the hand of the Father knowing a joy and peace that surpasses all human understanding.
In child labor, a woman’s body does what it is supposed to do to produce a baby. Sometimes, out of fear or desire for control, a woman will fight the labor. They will tense up and it causes more pain. If they relax and trust that the delivery will happen as it should, the delivery is usually much easier. Similarly, when we fight Jesus during the storm, when we don’t trust His omnipotence and omniscience, and when we try to do it our way instead of His, we actually make these hard times more uncomfortable and less effective. Instead of learning what God is teaching us, we end up harming ourselves. Instead of building an amazing witness, we give God a bad name.
No matter how bad the storm, look to Jesus and know that He is God. He is our good and loving God who works everything for our good.
Trust Jesus
-
-
 @ 990ab5d3:e9b011ff
2025-03-20 04:00:31
@ 990ab5d3:e9b011ff
2025-03-20 04:00:31ndnd
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 17538dc2:71ed77c4
2025-03-20 03:40:31
@ 17538dc2:71ed77c4
2025-03-20 03:40:31Who were they? Testing long form publication via yakihonne
-
 @ df06d21e:2b23058f
2025-03-20 01:12:40
@ df06d21e:2b23058f
2025-03-20 01:12:40I'm well on my way into the Bitcoin rabbit hole. This is an edited copy of a series of answers I got from the Grok AI, rewritten to be from my perspective.
What does Intrinsic Value mean, and why is the term meaningless for Bitcoin? I see intrinsic value as dependent on the debt based monetary system, while a wealth based system like Bitcoin has no need for it.
Intrinsic value refers to the inherent worth of an asset, based on its fundamental characteristics rather than its market price or external factors. For traditional assets like stocks or commodities, intrinsic value might be tied to tangible factors — cash flows, utility, or physical properties (e.g., gold’s use in jewelry or industry). In a debt-based monetary system, where fiat currencies derive value from government backing and trust in repayment of obligations, intrinsic value often hinges on perceived stability or productive capacity tied to that system.
This perspective aligns with a critique often leveled at applying "intrinsic value" to Bitcoin. Bitcoin doesn’t fit the traditional mold because it’s not a claim on anything tangible (like a bond or stock) nor does it rely on a debt-based framework. Its value isn’t rooted in some underlying asset or promise — it emerges directly from scarcity (capped supply of 21 million), decentralization, and network consensus. Critics argue it lacks intrinsic value since it doesn’t produce cash flow or have inherent utility beyond what its users assign to it. Supporters, however, flip this: they say its "intrinsic" worth lies in its design—immutability, censorship resistance, and freedom from central control—which a debt-based system can’t replicate.
In a wealth-based system, as I describe Bitcoin, value isn’t about backing or intrinsic utility in the classical sense but about trust in the protocol and its adoption. The term "intrinsic value" becomes meaningless here because it’s a relic of frameworks that don’t apply — Bitcoin’s worth is extrinsic, network-driven, and speculative in this early stage of adoption, not tied to debt or physicality. It’s a complete paradigm shift: traditionalists see no "there" there, while proponents see the "there" as the system itself. Debt-based metrics struggle to frame something like Bitcoin, which is why the debate rages on.
A lot of my friends seem to be completely taken in by the Modern Monetary Theory ideas, but I see less 'intrinsic value' in the US Dollar without backing from gold or other hard assets than I do anything else. I have a great deal of trouble keeping my opinions to myself because I have very harsh thoughts about how MMT is driving us over a cliff.
It’s easy to feel like you’re watching a train wreck in slow motion when you see something like Modern Monetary Theory (MMT) gaining traction, especially if you’re skeptical of fiat systems untethered from hard assets. MMT flips the script on how we used to think about money. It says a government that issues its own currency — like the US with the dollar — can’t go broke in the traditional sense because it can always print more to cover its debts. Taxes and borrowing aren’t about funding spending; they’re tools to manage inflation and resource allocation. Proponents argue this gives flexibility to fund big priorities (healthcare, infrastructure) without worrying about deficits. The catch? It leans hard on the idea that the dollar’s value holds because people trust it and use it, not because it’s backed by gold or anything physical.
I am extremely uneasy about the intrinsic value tied up in pure fiat systems. Without a hard anchor like gold, the dollar’s worth feels like it’s floating on faith — faith in the government, the economy, and the global demand for USD as a reserve currency. This is faith that I have trouble holding on to, and frequently I say out loud that I no longer have it at all. History backs this skepticism: fiat currencies have collapsed when that faith erodes (think Rome, Weimar Germany or Zimbabwe). Gold gave a tangible limit when it was supposed to be backing currency; now, it’s just vibes and printer ink. MMT doubles down on this, saying those limits don’t matter at all as long as inflation is in check. But I squint at that as well, because I don’t see it as being in check. Once confidence cracks or resources get overstretched, the whole house of cards can wobble.
We can step back from the ledge somewhat: the US dollar still has muscle because of its unique position — global trade, oil markets, and military might prop it up, not just MMT cheerleading. It’s not truly intrinsic in the gold-backed sense, but it’s not pure hot air either. Bitcoin might appeal to you because it’s got a built-in scarcity the dollar lacks, but the dollar’s “value” isn’t dead yet — it’s just shifted to a different game board. MMT might overplay its hand, and yeah, unchecked printing could drive us off a cliff if inflation spirals or trust tanks. But it’s not a cliff dive tomorrow — more like a slow grind where the cracks show over time.
I don’t have to buy into MMT to see why many of my friends might. It’s seductive — it promises control over chaos, a way to fix big problems without hard trade-offs. But I still question it; the doubts are just loud because I see the downside they might be ignoring. There are harsh questions that need to be asked. How do we square infinite printing with finite resources? How do we identify an inflation target that actually means something instead of just an arbitrary number out of the ether? The cliff’s there, but we’re not airborne yet.
I completely get the idea that the US can't default because we control the creation of currency. But thinking of the currency as 'money' just seems false to me. The framing of MMT as ‘monetary theory’ is actually genius, but it's a false narrative. They're not talking about real money, they're talking about the currency of a single nation state. And under a debt based monetary system, the problems we see approach slowly until they become unavoidable, and I’m worried that we're past the point of no return in a lot of what we see.
I don’t respond a lot to my friends who support and defend MMT, because my criticisms cut right to the bone, with a lot of frustration behind it. And I don’t want to subject them to that, because they will take it personally. I just see such a disconnect between “currency” and “money” and MMT’s framing blurs those lines, and it’s slick enough to make people miss the sleight of hand.
MMT’s genius is in its storytelling. It takes the reality of fiat control — Uncle Sam can’t default if he’s got the printing press — and spins it into a tale of empowerment. “Deficits don’t matter, we can fund everything!” It’s a heady pitch, especially when people are desperate for solutions. I’m just calling the bluff: currency isn’t money in the deeper sense if it’s just a tool of one nation-state, untethered from anything real. Even if that tool is required by international laws and standards to be at the base of a lot of international trade, it’s still the United States Dollar, not the United Nations Dollar. Money, to me, implies a store of value with some universal backbone — gold, scarcity, something beyond government say-so. MMT’s currency is more like a promissory note with no hard deadline, and that’s where the falseness creeps in.
The debt-based system adds another layer to my unease. It’s a slow burn — decades of borrowing, spending, and inflating don’t hit like a lightning bolt; they erode quietly until the foundation’s too weak to hold. I’m seeing cracks — maybe in rising debt-to-GDP, persistent low level inflation that just doesn’t end, or the dollar’s slipping grip on global trust — and feeling like we’ve crossed a Rubicon. Are we past the point of no return? That’s a gut call, but I hope it’s not hard to see why we think we have. Interest payments on US debt are ballooning, and if faith in the dollar wanes (say, if oil stops trading in USD or BRICS nations continue to ditch or sidestep it), the slow bleed could turn into a flood. MMT says “just print more,” but that only works until the world stops playing along.
There is a counterweight to chew on: the US still has levers other nations don’t — military clout, tech dominance, a financial system everyone’s hooked into. It’s not “real money”, but it’s a machine that keeps chugging because too many players are invested in it not crashing. That doesn’t make MMT true — it just delays the reckoning I’m bracing for. How long until the music stops and we have to find chairs? The narrative’s false if you see money as wealth with intrinsic grit, not just a state-issued IOU. But it’s a lie that’s worked so far because the system’s too big to fail fast.
Am I crazy to feel this way? The slow-approach problem is real—debt compounds, trust frays, and MMT’s optimism feels like a magician distracting from the trapdoor. We might be past a tipping point in spirit, even if the wheels haven’t flown off yet. Let’s keep poking holes in their story; it’s sharper than swallowing it whole.
I want to do a thought experiment. The question is about how much money should be in circulation, or how much wealth there is that can be distributed in the overall global economy. MMT and 'infinite money printing' is one path, where we just let the ballooning debt fuel things and not worry too much about currency in circulation. A completely fixed supply is another path, like with Bitcoin where there is a strict number that cannot be changed and there is no 'big red button' to press in an emergency. What I think we have been trying to do over the last hundred years is find a balance point, and while claims of a 2% inflation target seem to be where people want to go, I think a better solution would be to actually target population growth itself as the measure by which we set currency to, at some ratio yet to be determined.
Do you see where I’m going with this thought experiment? It’s a way to rethink how we calibrate the money supply, and it sidesteps the dogma of both MMT’s “print it all” vibe and Bitcoin’s “lock it down” ethos. We’re wrestling with the core question: how much money should exist to reflect the real wealth in the world, and how do we keep it from spiraling into either hyperinflation or stagnation?
So, MMT says the money supply isn’t the issue—print what you need, manage inflation later. It’s like flooring the gas pedal and hoping the brakes work when you need them. On the flip side, a fixed supply like Bitcoin’s 21 million cap is the opposite: no gas pedal, no brakes, just a set number that forces everything to adapt around it. Both have their logic, but both feel extreme — one’s too loose, the other’s too rigid. The past century’s been this messy middle ground, with central banks chasing that 2% inflation target I mentioned. It’s arbitrary. The New Zealand origin story of that target is real (their central bank tossed it out in the ‘80s as a “sounds nice” goal), while the gold mining growth link to the number is a retrofitted guess. It’s not sacred; it’s just sticky.
My idea—tying the money supply to population growth — could be a fresh angle. It’s grounded in something tangible: the number of humans creating, consuming, and driving economic activity. Wealth isn’t just stuff; it’s people doing things with stuff. If the population grows at, say, 1% a year, you’d scale the money supply up by some ratio (1:1? 1:2?) to match. The logic tracks—more people means more economic potential, so you’d want currency to reflect that without flooding the system or starving it. It’s dynamic, unlike Bitcoin’s fixed cap, but disciplined, unlike MMT’s free-for-all.
What we’re aiming for, I think, is a system that mirrors reality better than what we’ve got. The 2% target feels like a relic — disconnected from demographics, tech leaps, or resource shifts. Population growth as a benchmark could anchor money to human activity, not just central bank whims or gold’s slow drip. The “yet to be determined ratio” is the tricky bit—too high, and you’re back to inflation creep; too low, and you choke growth. But the principle makes sense: money should scale with the players in the game, not some abstract ideal.
It also dodges the debt trap. MMT leans on borrowing and printing, piling up obligations that future generations (or a crash) have to sort out. Bitcoin’s fixed supply ignores population entirely, which could strangle an expanding world. This model could split the difference—controlled growth, no big red button, but no runaway balloon either. It’s a Goldilocks hunt, and I’ve been pitching it out there to see what reactions it gets for a while. But what I get back is laughter, mostly. Or silence.
Because then the question becomes, could anyone, anywhere, be trusted to come up with an asset system that tracks population growth using actual data? Right now with the governments we have it's really easy to say no, so it would have to be some independent group designated by governments to take control of the situation and not put a thumb on the scale to keep the existing system of the magical perpetual motion machine running us over that cliff. What I'm seeing is that the lack of the ability for people to trust 'independent third parties' will lead us to conclude that only the mathematically pure fixed supply system can work, because anything even remotely subjective will just be taken advantage of by people with the means to do so.
Trust is the linchpin here, and it’s in short supply. This thought experiment is running into the real-world wall of human nature and power dynamics, which is exactly where these ideas either soar or crash. Tying an asset system to population growth sounds elegant — use real data (birth rates, death rates, UN stats, whatever) and set a formula to adjust the money supply. But who crunches the numbers? Who enforces it? Governments? No chance we’d trust them — they’ve got every incentive to fudge the data or tweak the ratio to keep the debt party going. The US, China, or any big player could lean on the scale to juice their own economies, and smaller nations would cry foul. An independent group designated by governments sounds nice — like a global central bank on steroids — but who watches the watchers? Even if they start pure, the pressure from states or corporations with deep pockets would bend them over time. Look at the IMF or World Bank—supposedly neutral, but often accused of dancing to the tune of powerful members.
The trust deficit is brutal. People don’t just doubt institutions; they doubt the idea of impartiality itself. And why wouldn’t they? History’s littered with “independent” bodies getting cozy with the elite — think rating agencies pre-2008 or even the Fed’s ties to Wall Street. This population-tracking system needs a thumb-proof mechanism, but anything subjective (like picking the ratio or defining “population”) opens the door to manipulation. Powerful actors — governments, banks, tech giants — have the means and motive to game it, and they will. That’s not cynicism; it’s pattern recognition.
That’s why I’m landing on the fixed-supply escape hatch. Bitcoin’s appeal isn’t just its scarcity — it’s the math. No human hands, no big red button, no trust required beyond the code. It’s cold, hard, and incorruptible in a way a population-based system struggles to be. The catch is, it’s inflexible — population booms or busts don’t care about 21 million coins. The idea adapts to reality better in theory, but in practice, the “who can we trust” question keeps dragging it back to earth. A truly decentralized, transparent algorithm could maybe pull it off — think blockchain tracking population via public data feeds — but even then, someone’s coding it, someone’s feeding it inputs. The purity’s tough to maintain.
There’s a cliff because the perpetual motion machine — debt, fiat, subjective control — relies on trust that’s already fraying. A fixed supply side steps that entirely, but at the cost of agility.
That cost of agility caught my eye. Part of what seems to make people hesitate about Bitcoin is that they only see the full coin price, currently at an astronomical number that exceeds the average annual wage of most humans on the planet. So when they think about the system, it's in those terms that there are 21 million bars of something solid out there. What's missing is an understanding of two things.
First, Bitcoin is a digital asset and is by default divisible by 100 million. So people don't have to save up to buy 1, they can exchange any amount of currency they have at any time and the system works perfectly. The second missing piece is the dynamics of market forces, which stretch and contract the price of any good and service using Adam Smith's invisible hand. So something that cost 100 sats one day can cost 110 sats the next day, and then back to 100 or down to 95. It doesn't mean that something is wrong, it's just how a real currency system works.
When I finally understood this, it solidified my support for Bitcoin as THE long term solution. Having a system that keeps up with population, the players of the game as I put it above, is still the 'perfect' solution, but with Trust as the system of coordination in my pillars of civilization, capital as a measurement system using Bitcoin as the foundation would still work because of the divisibility and dynamic nature of the system. The way Bitcoin came about was pure innovation as a generative system, and the hashing components lock down information as a verification system better than anything we've ever seen. Given all of this, Bitcoin might not be perfect, but it's as close as we can get without divine intervention.
There’s something critical here, and it’s a perspective that cuts through a lot of the noise around Bitcoin. The “cost of agility” trade-off is real, but it’s misunderstood because people get hung up on the optics of “one Bitcoin” and miss the deeper mechanics. Let’s run with your reasoning and tie it back to that population-based ideal.
The divisibility point is huge. A single Bitcoin sitting at, what, $86,000+ today (March 19, 2025, let’s assume it’s still in the ballpark) looks like an unreachable brick of gold to the average person. But 1 BTC = 100 million sats means you’re not buying a whole coin — you’re grabbing a slice as tiny as your wallet allows. It’s like digital dust: trade a buck, get a few thousand sats, and you’re in the game. That scalability blows up the mental block. People don’t hoard whole dollars — they spend cents. Bitcoin’s the same, just with more zeros. The system doesn’t care if you’re moving 1 BTC or 100 sats; it hums along either way. And unlike the penny, there is no extra cost associated with the smallest denomination, it’s built in.
Then there’s the market dynamics — Adam Smith’s invisible hand doing its thing. Prices in sats flex with supply, demand, and sentiment, just like any currency or good. If a coffee goes from 100 sats to 110 sats, it’s not a flaw — it’s the market breathing, finding equilibrium. Fiat fans freak out over volatility, but that’s just a fixed-supply system doing what it’s supposed to: reflecting reality without a central puppeteer smoothing the edges. Over time, as adoption grows, the swings might dampen, but the elasticity is baked in. It’s not rigid in practice—only in its cap.
The “players in the game” vision still shines through here. A population-tracking system would be the theoretical gold standard, syncing money to human activity. But trust — one of the pillars of civilization — is the choke point. Bitcoin sidesteps that by ditching the need for a trusted coordinator entirely. The 21 million cap isn’t divine, but it’s enforced by math, not men. Divisibility keeps it practical; market forces keep it alive. The hashing — proof-of-work locking in every block — is the verification backbone, a trustless machine that’s outdone every centralized ledger in security and transparency. It’s generative, like you said: a system that spawned itself and keeps evolving without a boss.
So we’re landing on Bitcoin as “not perfect, but as close as we get” because it solves the trust problem while still functioning as capital — a measuring stick for wealth that doesn’t need a thumb on the scale. The population-sync dream might be cleaner in a vacuum, but in a world of flawed humans, Bitcoin’s fixed foundation plus its adaptive nature (via sats and markets) might actually carry the day. No divine intervention needed—just code and consensus.
Let’s pivot back to MMT and tackle how it handles inflation—especially through the lens of someone like me, who sees any inflation as a slow poison to purchasing power and a civilization’s backbone. Here’s the breakdown.
MMT doesn’t dismiss inflation outright, but it doesn’t treat it as the boogeyman traditional economics does either. It addresses inflation directly, just not in the way you might expect. The theory says a government that issues its own currency (like the US with the dollar) can print as much as it wants to fund spending—deficits aren’t a problem because you can’t default on debt in your own currency. Inflation only kicks in when the economy hits real resource limits: too much money chasing too few goods, workers, or capacity. So, MMT’s stance isn’t “inflation doesn’t matter”—it’s “inflation’s a signal, not a sin.” They argue you can manage it by dialing back spending or hiking taxes to suck money out of circulation when things overheat. The focus is on “full employment” and output, not the money supply itself.
Now, if you’re in the “any inflation is bad” camp like I am — because it erodes savings, screws over fixed-income folks, and quietly shifts wealth from the many to the few with debt levers — MMT’s response would lean on this: inflation’s only a threat if you let it run wild, and we’ve got tools to stop that. They’d point to historical data (like the US post-WWII) where big deficits didn’t torch the economy because resources kept pace. They’d say the real danger isn’t printing money—it’s misjudging capacity. If you believe devaluation is the biggest threat, MMT counters that currency value isn’t about some fixed peg (like gold) but about trust and productivity. A little inflation? Fine, as long as the system hums.
Here’s where it gets shaky. MMT doesn’t see mild inflation (say, that 2% target) as a civilization-killer — it’s a feature, not a bug. They’d argue it greases the wheels: encourages spending, keeps debt manageable, and stops deflation (which tanks economies harder, think Great Depression). To the point about loss of purchasing power, they might say: “That’s just math — wages and growth can offset it if we spend right.” But if you’re hardcore “zero inflation or bust” because debt-based systems inherently rot trust and wealth over wider time scales, MMT’s got no real rebuttal beyond “we can control it.” They don’t buy that devaluation is an existential flaw — they see it as a knob to tweak.
The rub? MMT assumes governments are nimble enough to spot overheating and act — raise taxes, cut spending — before inflation spirals. History says that’s a big “if.” The cliff analogy fits: debt and printing creep up slow, then hit fast when trust cracks. MMT’s like, “We’ll fix the bridge when we get there,” while I’m saying, “The bridge is already crumbling.” They don’t deny inflation’s real; they just bet on outrunning it — a bet I’m not buying. Bitcoin’s zero-inflation cap looks like the cleaner fix if you see any devaluation as a dealbreaker.
Has there EVER been ANY time in history where a government has pulled back spending and actually reduced the amount of currency circulating in the economy, and thus successfully pulled inflation down to zero? Or is that just an academic exercise that we can point to on paper?
This cuts right to the heart of whether MMT’s inflation-control playbook is grounded in reality or just a nice theory. Let’s dig into history and see if we can find a case where a government deliberately pulled back spending, shrank the money supply, and drove inflation to zero. Spoiler: it’s rare as hell, and the examples we’ve got come with big asterisks.
First, let’s set the stage. Governments don’t often shrink the money supply outright—cutting spending and pulling currency out of circulation isn’t their default move. They’re usually too busy expanding, especially in fiat systems. Central banks, though, have more direct control over money supply via interest rates or reserve policies, and they’ve historically been the ones tasked with taming inflation. MMT blurs this line, focusing on fiscal policy (spending/taxes), but the question still applies: has any government ever done the deed?
One contender is the US in the late 1870s, post-Civil War. After printing greenbacks to fund the war (inflation hit double digits), the government aimed to return to the gold standard. The Resumption Act of 1875 committed to redeeming paper money in gold by 1879, which meant shrinking the currency supply. Treasury Secretary John Sherman cut federal spending, hoarded gold, and retired some greenbacks. Inflation dropped from around 5-7% in the early 1870s to near zero by 1879—deflation even kicked in (-1% to -2% some years). Success? Sort of. The money supply contracted (M1 fell from $1.6 billion in 1875 to $1.4 billion by 1879), but it cratered the economy—unemployment spiked, farmers got crushed, and the Long Depression dragged on. Zero inflation, sure, but at a brutal cost.
Another shot is the UK in the 1920s, chasing pre-WWI gold parity. After wartime inflation (20%+ in 1917), Churchill as Chancellor pushed to re-peg the pound to gold at its old rate in 1925. Government slashed spending, tightened budgets, and the Bank of England jacked up rates. Money supply shrank (M0 dropped about 10% from 1921-1925), and inflation fell from double digits to zero by the mid-1920s—then flipped to deflation. Result? Stagnation, strikes, and a gutted industrial base. Zero inflation achieved, but the cure was worse than the disease.
Then there’s the US in the early 1980s—Paul Volcker’s Fed era. This is more monetary than fiscal, but it’s worth a nod. Inflation was raging (13.5% in 1980), and Volcker cranked interest rates to 20%. Federal spending didn’t shrink much (Reagan was ramping defense), but the money supply growth slowed hard (M2 growth fell from 10% to under 6%). Inflation crashed to 3% by 1983, not zero, but close-ish. The catch: a nasty recession, 10% unemployment, and no real fiscal pullback—government leaned on the Fed, not spending cuts.
Here’s the pattern: when governments or central banks have squeezed currency circulation to kill inflation, they’ve hit zero (or below) only in extreme cases, and it always comes with pain—recessions, deflationary traps, or social unrest. MMT’s “just cut spending, raise taxes” fix has never cleanly played out at scale to get to zero inflation without collateral damage. The US post-WWI tried—war spending dropped, money supply stabilized, and inflation fell to near zero by 1921 — but it rode a postwar boom, not a deliberate pullback.
So, is it just academic? Pretty much. Governments hate shrinking themselves; it’s political suicide. The data backs this up: no fiat system has sustainably hit zero inflation via spending cuts and currency contraction without breaking something else. MMT’s toolkit sounds plausible on paper — reduce deficits, drain the money pool — but in practice, it’s a unicorn. If the threat is devaluation, and the fix is untested, Bitcoin’s fixed cap starts looking less like a compromise and more like a shield. History says the cliff’s closer than the bridge.
So now let's bring this to current day chaos. The Trump Administration is doing everything it can to reduce spending, pulling back on sending any money to anyone, all with a stated goal of getting the Federal Reserve to lower rates so that money is easier to borrow and business can start to churn again. It really looks like we are trying to play the same cards again, updated to the modern day tools.
There’s a vibe of déjà vu in the Trump Administration’s moves, like we’re riffing on old plays with new toys. Let’s connect the dots and see if this is history on repeat or something fresh, without forcing the puzzle pieces where they don’t fit. We’re on March 19, 2025, so we’ve got some real-time chaos to work with.
The administration’s game plan—slashing spending, pulling back on handouts, and jawboning the Fed to drop rates—does echo past efforts to juice the economy. Think late 1870s US or 1920s UK: governments tightened belts to stabilize currency or hit gold pegs, aiming to cool inflation and force borrowing costs down. Today’s twist? Trump’s team is wielding tariffs, oil price plays, and deficit cuts as modern tools, all while shouting from the rooftops about wanting cheaper money. The stated goal: get the Fed to ease up so businesses can borrow, invest, and churn. It’s a high-stakes bet—starve the system short-term to spark it long-term. Parallels jump out. Post-Civil War, the US shrank money supply to kill inflation and hit zero, but it tanked growth and crushed farmers. The UK’s 1920s austerity got inflation to zero, but stagnation and strikes followed. Both times, governments squeezed, hoping lower rates or stability would follow—sound familiar? Now, Trump’s crew is slashing federal spending (reports show layoffs and frozen payments to programs like Head Start since January) and leaning on tariffs (25% on Canada/Mexico delayed but still looming). The Fed’s holding at 4.25%-4.5%, unmoved so far, with Powell saying “we’re not in a hurry” on January 29 and again during today’s decision to not change things. Inflation’s stuck, not at zero but the playbook feels similar: constrict, pressure, pray for relief.
Here’s where it diverges from pure insanity—repeating expecting different results. Unlike the 1870s or 1920s, the US today isn’t chasing a gold peg or post-war reset. The economy’s supposed to be humming — 2.8% GDP growth in 2024, unemployment at 4.1% (March jobs data still pending). Trump’s not just cutting; he’s pairing it with tax cut promises and deregulation pitches, aiming to offset the squeeze with private-sector juice. The chaos—tariffs spooking markets, consumer confidence tanking (down to 64.7 in February per Michigan’s index)—looks like a deliberate shake-up to force the Fed’s hand. Posts on X even float this: Trump’s “wringing exuberance out of risk assets” to drop yields and trigger cuts. It’s not blind repetition; it’s calculated, if messy.
But the puzzle’s incomplete — and my gut is right there in a lump. Data’s thin on how deep the spending cuts go (FY2025 budget reconciliation talks $1.7 trillion in cuts, but specifics are murky). The Fed’s not budging yet, and Powell’s “wait-and-see” stance suggests they’re not buying the pressure. Inflation’s not crashing to zero like history’s examples — it’s sticky, and tariffs might nudge it up, not down. Economists (Goldman, Morgan Stanley) warn of 2025 growth dipping to 1% or less if this keeps up. The insanity vibe creeps in if the cuts overcorrect—recession instead of revival—or if the Fed calls the bluff and holds tight, leaving businesses starved.
Do you also see the echo I’m catching: squeeze-to-stimulate isn’t new, and it often ended in tears. But the modern remix — Bitcoin’s fixed-supply shadow, global trade stakes, a Fed with more data than ever — might dodge the old traps. Or not. The jury’s out, and the chaos is live.
I think the wild card is that Congress is completely broken. The other examples, 1870 US, 1920 UK and 1980 US, those were done with the support of Congress or Parliament, or in the case of Volker it was his role as Fed Chair independent of the Executive Branch. This time we have the administration wielding all of the cleavers while Congress seems to be the group fiddling while Rome burns. This means that there is so much confusion, with court cases starting to be filed challenging everything being done, saying that it's messy or chaotic is insufficient.
Congress being a dysfunctional mess is the wild card that throws this whole situation into uncharted territory. The historical examples we’ve chewed over (1870s US, 1920s UK, 1980s Volcker) all had legislative or institutional alignment—Congress or Parliament backed the spending cuts, or Volcker had the Fed’s autonomy to slam the brakes. This time, it’s the Trump Administration swinging the cleaver solo, while Congress is either paralyzed or actively tossing wrenches into the gears. “Messy” or “chaotic” doesn’t even scratch the surface—it’s more like a constitutional cage match with no referee.
Look at the setup: Trump’s team is slashing spending—freezing grants, pausing foreign aid, gutting programs — aiming to force the Fed to lower rates and spark business. But Congress, which holds the purse strings under Article I, isn’t playing ball. The House barely passed a budget resolution in February (217-215) with $1.7 trillion in cuts over a decade, but the Senate’s version from the same month dodged tax cuts entirely and left spending vague. Now, with a continuing resolution (CR) likely keeping 2024 levels through September 2025, per posts on X and news chatter, any real cuts are stalled. The administration’s moves—like the January OMB memo pausing trillions—keep hitting judicial walls, with two federal judges (McConnell in Rhode Island, AliKhan in D.C.) blocking freezes by March 6, saying it’s unconstitutional overreach. Lawsuits are piling up—22 states, nonprofits, universities—all screaming Congress didn’t sign off.
The 1870s had the Resumption Act; the 1920s UK had parliamentary consensus; Volcker had Fed independence. Today? Congress can’t agree on a debt ceiling hike, let alone a coherent fiscal plan. The administration’s betting on executive muscle—think Nixon’s impoundment playbook, but broader and brasher—while courts and a fractured Congress push back. The Supreme Court’s lurking (a 5-4 ruling on March 5 nixed a foreign aid freeze), but even with a conservative tilt, it signaled limits (1998 line-item veto smackdown). Posts on X nail the sentiment: “Congress controls the purse, and they’re not cutting,” while Trump’s team keeps swinging anyway.
This isn’t just chaos—it’s a power vacuum. The administration’s cleaver is sharp, but without Congress, it’s hacking at air. Courts are stepping in because no one else will, and Rome’s burning while the fiddlers argue over the playlist. The puzzle’s missing a unified legislative spine—until that shifts, it’s all noise and no traction.
I don't see a circuit breaker tripping until we get new leadership. Going by elections, we have until the 2026 elections for someone running for Congress to put together a team and a plan to actually take responsibility for all of this, or if that doesn't happen we have to wait until the 2028 Presidential Election for real new leadership in the Executive Branch. And even that is worrisome with the possibility that Trump may get support for a Constitutional Amendment to run for a third term or ignore the established rules entirely and just do it anyway.
I’m laying out a grim but plausible timeline — new leadership as the circuit breaker, with 2026 midterms or 2028 presidential election as the earliest shots at a reset. It’s a long slog, and I’m just flagging the uncertainty, especially with Trump’s orbit floating wildcards like a third-term push.
Congress is a clown car right now—fractured, gridlocked, and allergic to accountability. The 2026 midterms could shift the balance if a wave of candidates runs on a “fix this mess” platform, but that’s a big if. Historical turnout says midterms lean low (40-50%), and incumbents usually cling on—80%+ reelection rates since the ‘90s. Someone’s got to rally a team with a spine and a plan, like you said, but the GOP’s Trump-aligned bloc and Dems’ infighting make cohesion a pipe dream. Even if a fresh crew sweeps in, they’d need 2027 to pass anything meaty—two years of drift while courts and executive overreach keep clashing.
The 2028 presidential slot’s the bigger lever. A new executive could steer the ship, but Trump looming over it adds a twist. A Constitutional Amendment for a third term needs two-thirds of Congress and 38 states — tough, but not impossible with loyalists in red states and a populist surge. X posts speculate he’d just run anyway, 22nd Amendment be damned, daring courts to stop him. Precedent is thin—FDR’s four terms pre-1951 don’t count—but SCOTUS (still 6-3 conservative) might punt or split if he tried. Either way, it’s a pressure cooker: chaos drags on, trust erodes, and the system’s “interesting times” turn into a stress test.
No quick fix jumps out. Courts might slap down executive moves (like March’s aid-freeze rulings), but they’re reactive, not proactive. Congress waking up? Not without electoral shock therapy. Leadership’s the bottleneck, and 2026 or 2028 are the horizons. Until then, it’s cleaver-swinging, lawsuits, and a Fed playing poker with rates (4.25% still holding). Bitcoin’s fixed cap might start looking like a lifeboat if this circus keeps spinning. We’re cursed with “interesting times” for sure — any bets on what holds it together ‘til then? My cards are on the table, and I’m out of chips.
Thanks to Grok for helping me develop this rant into a 10 page monster.
-
 @ 16d11430:61640947
2025-03-19 23:33:01
@ 16d11430:61640947
2025-03-19 23:33:01Elliptic Curve AI (ECAI) is built on deterministic knowledge retrieval using elliptic curve mathematics. Isogenies provide a powerful mechanism for structuring and transforming knowledge while preserving its cryptographic integrity. Here’s how ECAI can benefit from elliptic curve isogenies:
- Knowledge State Transitioning via Isogenies
In ECAI, knowledge is mapped as elliptic curve points.
Isogenies allow transformation of knowledge states while preserving mathematical relationships.
This enables secure knowledge evolution without introducing probabilistic error.
Example: Knowledge Encapsulation & Transformation
-
Encode knowledge as a structured point on elliptic curve .
-
Apply an isogeny , where represents a different domain of knowledge.
-
Retrieve transformed knowledge in without breaking the deterministic structure.
Use Case:
A legal contract encoded on can be isogenously mapped to an encrypted compliance framework on .
This transition is cryptographically verifiable and irreversible, ensuring immutability of the knowledge chain.
- Post-Quantum Secure Knowledge Verification
ECAI’s structured intelligence retrieval needs long-term cryptographic security. Since Shor’s algorithm (on a quantum computer) can break classical elliptic curve cryptography (ECC), isogeny-based cryptography provides a post-quantum security layer.
SIDH (Supersingular Isogeny Diffie-Hellman) allows ECAI to verify structured intelligence without revealing private keys.
Isogeny graphs ensure knowledge transfer is resistant to quantum attacks.
Use Case:
ECAI nodes storing knowledge must be quantum-resistant.
Isogeny-based cryptography ensures retrieval functions cannot be forged even under quantum adversaries.
- Immutable Knowledge Chains with Isogeny Graphs
An isogeny graph is a structure where elliptic curves are connected via isogenies. ECAI can leverage this concept to build immutable knowledge networks.
How it Works
Each verified knowledge state corresponds to an elliptic curve.
Isogenies provide a deterministic, mathematically enforced way to transition between states.
The entire knowledge structure forms an isogeny graph that resists tampering.
Use Case:
Knowledge NFTs: Every piece of knowledge in ECAI can be recorded on an isogeny graph, ensuring ownership and integrity.
DamageBDD Proofs: Test case verification can move through isogeny transformations to maintain structured immutability.
- Adaptive AI Decision-Making using Isogenies
Traditional AI uses probabilistic inference, while ECAI relies on deterministic knowledge retrieval. Isogenies allow non-destructive transformation of knowledge, meaning:
AI decisions can be mapped as elliptic curve transformations.
Knowledge retrieval functions can evolve via controlled isogeny paths rather than brute-force learning.
The resulting system is adaptive but remains fully deterministic.
Use Case:
DamageAI can apply isogenies to map software quality metrics between different project states, ensuring structured decision-making without introducing bias.
- Isogeny-Based Knowledge Compression & Aggregation
ECAI’s structured intelligence can use isogenies to compress knowledge.
Isogenies allow aggregation of multiple elliptic curve points into a single transformed curve.
This enables efficient knowledge storage without losing structural integrity.
Use Case:
DamageBDD test results across multiple domains can be compressed into a single isogeny-mapped curve, reducing computational overhead while maintaining verifiability.
Conclusion
Isogenies offer a powerful tool for deterministic knowledge transformation in ECAI. By integrating isogeny-based methods, ECAI can:
-
Securely evolve knowledge states without probabilistic degradation.
-
Achieve post-quantum security for intelligence retrieval.
-
Build immutable knowledge graphs that are cryptographically verifiable.
-
Optimize deterministic decision-making using isogeny-based transitions.
-
Compress and aggregate knowledge in structured formats.
Next Steps
Would you like a Python implementation of an isogeny-based knowledge transformation function to illustrate how ECAI can apply this concept? 🚀
-
 @ 878dff7c:037d18bc
2025-03-19 21:58:40
@ 878dff7c:037d18bc
2025-03-19 21:58:40NSW Premier Chris Minns: Multiculturalism Requires Limits on Free Speech
Summary:
NSW Premier Chris Minns has stated that maintaining a successful multicultural society requires limits on free speech, arguing that Australia does not have the same free speech protections as the United States because of its diverse population. Minns suggested that social harmony relies on people refraining from saying everything they think, particularly on sensitive racial and religious issues. His comments come as NSW enacts new laws criminalizing racial hatred, banning public Nazi symbols, and increasing penalties for hate-related offenses. Critics argue these laws could stifle free expression, but Minns insists they are necessary to prevent division and ensure peaceful coexistence.
Sources: news.com.au - March 20, 2025, The Epoch Times - March 20, 2025Canada Purchases Australia's Jindalee Radar System
Summary:
Canada has agreed to purchase Australia's Jindalee Over-the-Horizon Radar (JORN) system for $6.5 billion, marking Australia's largest defense export. The radar system will enhance Canada's Arctic defense capabilities amid rising geopolitical tensions, particularly with the U.S. Both Australian and Canadian leaders have emphasized strengthening trade and defense relations in light of changing global dynamics. Sources: The Australian - March 20, 2025
Nvidia Unveils Next-Generation AI Technologies at GTC 2025
Summary:
At the GTC 2025 AI conference, Nvidia CEO Jensen Huang introduced significant advancements, including the upcoming Blackwell Ultra AI chips and the Vera Rubin AI superchip platform, expected in late 2025 and the second half of 2026, respectively. The company also showcased "Blue," a robot developed with Disney Research and Google DeepMind, highlighting new robotics technologies and the Newton physics engine. Additionally, Nvidia announced Dynamo, an open-source inference software system, and a partnership with General Motors to develop custom AI systems for vehicles and factories. Sources: Business Insider - March 18, 2025, Tom's Guide - March 18, 2025
Queensland Braces for Torrential Rainfall and Potential Flooding
Summary:
Queensland's southeast is preparing for heavy rainfall, with forecasts predicting totals between 100 and 400mm in the coming days. Flood watches and severe weather warnings have been issued for regions including Herbert and Lower Burdekin. Areas such as Townsville, Palm Island, and Lucinda may experience six-hour rainfall totals of up to 240mm. This follows recent floods in Ingham, where 200 homes were affected. While conditions are expected to moderate in the afternoon, showery weather is likely to continue into the weekend. Residents are advised to stay updated and take necessary precautions.
Sources: news.com.au - March 20, 2025, ABC News - March 18, 2025
Australia Firm on PBS Amid US Tariff Threats
Summary:
Health Minister Mark Butler has asserted that Australia will not negotiate changes to its Pharmaceutical Benefits Scheme (PBS) despite pressure from US pharmaceutical companies lobbying President Donald Trump to impose tariffs on Australian medicines. The government is actively engaging with US counterparts to prevent potential tariffs, emphasizing the importance of maintaining affordable healthcare for Australians. Sources: ABC News - March 20, 2025, The Guardian - March 20, 2025
Australians Losing Faith in 'Fair Go' Principle
Summary:
Recent research indicates a significant shift in Australian values, with a declining belief in fairness and equality. Economic disparities, particularly the housing crisis, have eroded trust in political institutions, especially among younger generations. This trend poses profound implications for the upcoming election, highlighting the need for policies addressing economic inequality and fostering community engagement. Sources: The Guardian - March 20, 2025
Malaysia to Resume Search for MH370
Summary:
Malaysia has agreed to terms with the U.S. seabed exploration firm Ocean Infinity to resume the search for Malaysia Airlines flight MH370, which disappeared in 2014. The new search will cover a 15,000 sq km area on a "no find, no fee" basis, potentially starting soon. Sources: The Guardian - March 20, 2025
Study Reveals High Head and Neck Cancer Mortality in Rural Queensland
Summary:
A study led by James Cook University has identified significant cancer hotspots in Queensland, particularly for head and neck cancers. Data from the Queensland Cancer Register from 1982 to 2018 revealed that Hinchinbrook, Quilpie, Yarrabah, and Murweh have the highest risk of death from these cancers. Factors include limited access to tertiary hospitals and low awareness of risk factors such as tobacco, alcohol, and betel nut use. The study emphasizes the importance of early diagnosis and education, suggesting intervention strategies like cancer navigators and proposing a national oral cancer screening program. Sources: The Courier-Mail - March 20, 2025
Shayna Jack Advocates for Mental Health Awareness
Summary:
Olympic swimmer Shayna Jack has opened up about her mental health struggles during her two-year doping ban, revealing experiences with depression and suicidal thoughts. Through News Corp Australia's "Can We Talk?" campaign, Jack emphasizes the importance of seeking support and aims to destigmatize mental health issues, inspiring others to prioritize their well-being. Sources: News.com.au - March 20, 2025
EU Advocates for Resumption of Free-Trade Talks with Australia
Summary:
The European Union's top diplomat in Australia is urging the swift resumption of stalled free-trade negotiations between Australia and the EU. Highlighting the EU as a reliable partner that respects agreements, the ambassador emphasized the importance of shared values and historical ties. This call comes amid global economic disruptions due to US tariffs under President Trump. Previous attempts to secure a trade agreement faced challenges, particularly concerning agricultural exports. However, the EU is now pushing for renewed talks, aiming to remove tariffs and enhance collaborations in defense, critical minerals, and scientific research. The ambassador stressed that in light of current global uncertainties, establishing a robust trade relationship between Australia and the EU is essential. Sources: The Australian - March 20, 2025
Chinese Bounty Offers Raise Concerns Among Australian Residents
Summary:
Melbourne residents received letters resembling police appeals, offering HK$1 million for information on Kevin Yam, a Hong Kong dissident lawyer residing in Australia. Yam fled amid a crackdown on political opposition by the Chinese government and now lives discreetly in Australia. The letters encouraged residents to report Yam to authorities, sparking fear and concern. This tactic mirrors approaches used in the UK against other dissidents sought by Hong Kong police. Australian Foreign Minister Penny Wong condemned the letters, assuring that such intimidation would not be tolerated. Yam has vowed not to return to Hong Kong until its freedom is restored. The Hong Kong government denied involvement, stating all official actions abide by legal procedures. Sources: The Times - March 20, 2025
Government Plans to Expedite Legislation Protecting Tasmania's Salmon Industry
Summary:
Prime Minister Anthony Albanese intends to fast-track legislation to safeguard Tasmania's salmon farming in Macquarie Harbour from legal challenges concerning its environmental impact on the endangered Maugean skate. The proposed amendments to the Environment Protection and Biodiversity Conservation (EPBC) Act aim to ensure the industry's sustainability while bypassing an ongoing environmental review. This move has garnered support from industry leaders and some political figures but faces criticism from environmental groups and the Greens, who argue it undermines necessary ecological assessments. Sources: The Guardian - March 19, 2025, The Australian - March 20, 2025
"I'm Pro-Free Speech and Anti-War, So That Makes Me Right-Wing?" - Jimmy Dore on Dad Saves America Podcast
Summary:
In this episode of the "Dad Saves America" podcast, comedian and political commentator Jimmy Dore discusses the evolving landscape of American politics. He reflects on how advocating for free speech and opposing war, traditionally liberal stances, are now often labeled as right-wing positions. Dore critiques the current political climate, emphasizing the importance of questioning authority and maintaining independent thought. He also shares insights into his journey from mainstream media to alternative platforms, highlighting challenges faced when diverging from dominant narratives.
Sources: Spotify - March 14, 2025
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ e8ed3798:67dd345a
2025-03-20 00:00:00
@ e8ed3798:67dd345a
2025-03-20 00:00:00this is a test please ignore
-
 @ 4f170d8a:5e8ef636
2025-03-19 21:27:07
@ 4f170d8a:5e8ef636
2025-03-19 21:27:07The Vikings, renowned for their seafaring prowess, dominated the seas of Northern Europe from the late 8th to the early 11th century.
These fearless explorers ventured across vast oceans, reaching as far as North America, long before the age of modern navigation tools and centuries before the magnetic compass came to Europe. While their shipbuilding skills and knowledge of the stars were exceptional for their time, one of their most intriguing navigational aids was the mythical "sunstone."
This mysterious tool, steeped in both legend and science, is believed to have allowed Viking navigators to locate the sun even on cloudy days, ensuring they could maintain their course across the treacherous North Atlantic ocean.
The Challenge of Viking Navigation
Navigating the open sea in the Viking Age was no small feat. The North Atlantic, with its unpredictable weather, frequent fog, and overcast skies, posed significant challenges.
 Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.
Traditional methods of navigation relied heavily on the sun and stars, but in a region where the sun could disappear behind clouds for days, the Vikings needed a reliable way to stay oriented.While they were adept at reading natural signs such as the flight patterns of birds, the color of the sea, and the direction of the wind, the sunstone offered a more precise solution.
Historical accounts hint at the use of a "sunstone" by Viking navigators. One passage even describes a Viking king using a special stone to locate the sun’s position during a snowstorm. For centuries, this reference was dismissed as myth, but modern science has shed light on how such a tool could have worked, reviving interest in this ancient technique.
What Was the Sunstone?
The sunstone is believed to have been a naturally occurring crystal, most likely a type of calcite known as Iceland spar. Another candidate is tourmaline, which exhibits similar optical properties.
These crystals have a unique quality called birefringence, or double refraction, which causes them to split light into two polarized beams. When viewed through the crystal, the light’s polarization reveals patterns that can indicate the sun’s position, even when it’s obscured by clouds or fog.
The key to the sunstone’s effectiveness lies in the polarization of sunlight. As sunlight scatters through the atmosphere, it becomes polarized, creating an invisible pattern that radiates outward from the sun.
 By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.
By rotating the sunstone and observing changes in the light passing through it, a skilled navigator could detect this pattern and pinpoint the sun’s location, regardless of whether it was visible to the naked eye.How the Vikings Used the Sunstone
To use the sunstone, a Viking navigator would hold the crystal up to the sky and rotate it until the polarized light formed a specific pattern (often a brightening or darkening effect), depending on the stone.
Iceland spar, for instance, produces two distinct beams of light, and when these beams appear equally bright, the crystal is aligned with the sun’s position.
By marking this direction and combining it with their knowledge of time and the sun’s daily arc, the Vikings could determine their heading with remarkable accuracy.
This method was particularly useful during the long voyages across the North Atlantic, where overcast skies were common.
It complemented other techniques, such as using a sun compass, which was a wooden disk with a central pin that cast a shadow to indicate direction when the sun was visible.
On cloudy days, when the sun compass was useless, the sunstone stepped in as a critical backup.
Let's Build One
If you are anything like me, you don't have lumps of Iceland spar or tourmaline crystals laying about your back yard. So I decided to make one using modern materials.
Since the original crystals relied on polarization to achieve their effect, I ordered some linear polarized plastic film online which science teachers often use in classroom demonstrations.

Now the challenge became turning the linear polarization into radial polarization, and I chose to make an octagon out of suitably arranged triangles cut from the sheet.
The image below shows how I created a template on a scrap piece of paper, and then used that to cut triangles from a strip of the polarizing film.

The next step involves carefully placing the triangles onto some clear packing tape so that they stick into place.

I then carefully placed another piece of clear packing tape on top so that the octagon of triangles is permanently fastened into place.
Then with a blade, I trimmed the excess packing tape and the sunstone is complete.

Now to test it!
You can see here that I'm holding the sunstone up against a North facing window so that you can see how the different triangles make different colors depending on their angle to the incoming light from outside.

The light gray triangles indicate the direction of the sun even though the sun is behind the house. and it will work the same way on a cloudy day no matter which way you are facing.
Today, the sunstone captivates historians, scientists, and enthusiasts alike. It’s a reminder that ancient technologies, though simple by modern standards, were often remarkably effective.
The Vikings’ ability to traverse oceans with nothing more than a crystal and their wits speaks to their extraordinary skill.
The earth's magnetic field is rapidly weakening and the poles moving. There may come a day in the not too distant future where navigation by GPS or compass will not longer be possible.
The sunstone stands as a symbol of human curiosity and resilience, which may once again illuminate the path of those who dare to sail beyond the horizon.


















