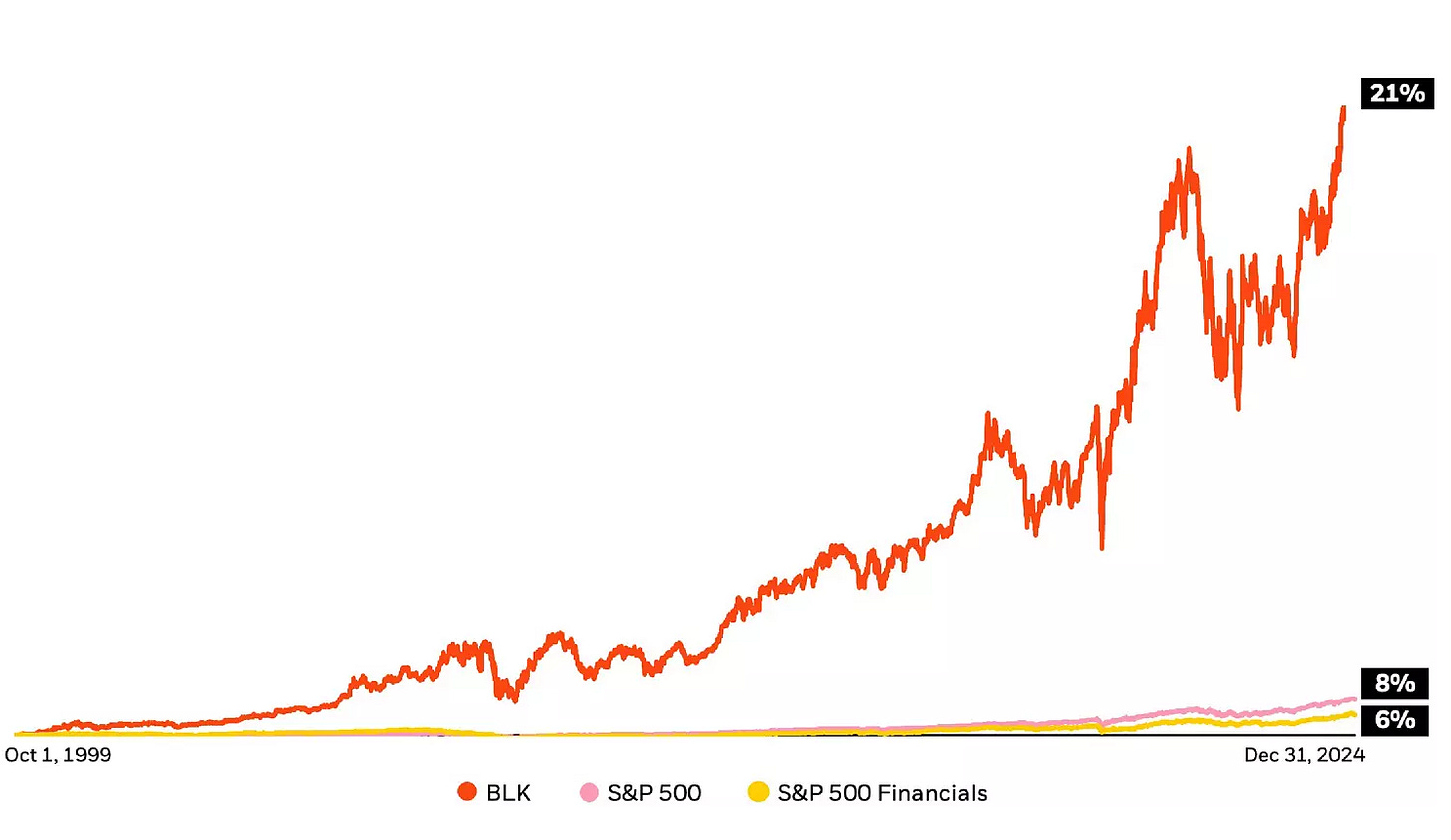
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 592295cf:413a0db9
2025-04-13 15:52:02
@ 592295cf:413a0db9
2025-04-13 15:52:02Nostur is capable of login with bunker
Photo, note by Fabian
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqxfktwlm2qdkpxy556e4yg4l8p6v8930nfyzg7p3vsknk7krutz0s8znjtq
When you decide to share an app you have to know a lot about that app. For example the nstart feature that you can share your friends, has a "smart pack" and the app can onboard, at least following the link --> Apps-integration
So let's try to read and bring a bit to the summary of the thing. Only the one about the profiles, which you don't know exactly how it will end, you have to try it before sending to someone. the second point is that it says that there is no "support encryption, so it cannot be used for DMs apps".
there was an update of nstart, now it shows you
the names of the bunkers, maybe now it's too much, decide if it does 3/2 4/2 or just automatic.
So they talked about frost in the hodlbod podcast. I didn't understand much except that they said to test frost and report the feedback. Tomorrow I'll try to download igloo and frost+nos2ex
So I have to wait for let's say version 0_1_0 of igloo now it is (0_0_4) and
maybe there will be the version of the extension ready.
Sebastix also found it difficult but I think he was trying to install the server, which didn't even occur to me. Anyway I leave you the note if you want to go deeper...
nostr:nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qytkummnw3ez66tyvgaz7tmrv93ksefdwfjkccteqqs2wzkkx220e24revkpxmdzkqj73rnz0reeenjwgy53g36hlkdgurgrs5e62
Let's see if I can download the video. ok Downloaded. Video .mov
If you don't want to watch I'll leave a little description
1 Download and install igloo, from the frost page. 2 Create a new key set, you can generate or copy an existing key. 3. Choose the options for the key and now they become multiple keys 4. Created a group of credentials. 5. Save the two credentials with a password and bring the third into the browser extension that it creates from the repository, it says that there will be a bootable extension for chrome. 6. Copy the third key and the group package key into the application node. 7. Once you have entered these keys you can finish the operation (and you have backed up the other two) in igloo. 8. When it goes forward it finds itself with two keys, both encrypted with passwords. 9. Since it is a three of two, it just needs to activate a key in igloo and it starts communicating "startsigner". 10. Opens a nostr client and connects with frost2sx and writes a note 11. Shows the log, and says that if you enter two keys it can generate a third, invalidating the old one (I assume)
-
 @ 502ab02a:a2860397
2025-04-13 15:45:19
@ 502ab02a:a2860397
2025-04-13 15:45:19มูลนิธิร็อกกี้เฟลเลอร์ (Rockefeller Foundation) ก่อตั้งขึ้นในปี ค.ศ. 1913 โดยตระกูลร็อกกี้เฟลเลอร์ ซึ่งเป็นหนึ่งในตระกูลที่มีอิทธิพลทางเศรษฐกิจและสังคมของสหรัฐอเมริกา จุดมุ่งหมายหลักของมูลนิธิคือการส่งเสริมสุขภาพ การศึกษา และความเป็นอยู่ที่ดีของมนุษยชาติทั่วโลก
บทบาทของมูลนิธิร็อกกี้เฟลเลอร์ในประเทศไทยนั้น สำหรับกรุงเทพฯแล้ว เป็นศูนย์ใหญ่ประจำภาคเอเชีย มูลนิธิร็อกกี้เฟลเลอร์ได้เข้ามามีบทบาทสำคัญในการพัฒนาระบบสาธารณสุขของประเทศไทย โดยเฉพาะในด้านการศึกษาและการวิจัยทางการแพทย์ มูลนิธิได้ให้การสนับสนุนทั้งทางด้านการเงินและวิชาการแก่สถาบันการแพทย์ต่าง ๆ รวมถึงการส่งเสริมการศึกษาของบุคลากรทางการแพทย์ไทยในต่างประเทศ พูดง่ายๆคือ ช่วยรัฐบาไทยจัดตั้ง "สาธารณสุขแห่งแรก" ในประเทศไทย เมื่อ พ.ศ. 2457 แสดงถึงความสัมพันธ์ลึกซึ้งกับสาธารณสุขอเมริกาเป็นอย่างดี
แม้ว่าการสนับสนุนของมูลนิธิร็อกกี้เฟลเลอร์จะช่วยยกระดับระบบสาธารณสุขของไทยอย่างมีนัยสำคัญ แต่ก็มีข้อถกเถียงเกี่ยวกับอิทธิพลของมูลนิธิต่อทิศทางการพัฒนาทางการแพทย์ของประเทศ บางฝ่ายมองว่าการพึ่งพาทุนและแนวคิดจากต่างประเทศอาจทำให้ประเทศไทยสูญเสียความเป็นอิสระในการกำหนดนโยบายด้านสาธารณสุข เพราะมีคำกล่าวหาว่า มูลนิธิ มีเบื้องหลังที่สามารถควบคุมกิจกรรมต่างๆเกี่ยวกับสาธารณสุขในเมืองไทยได้ (โอเค ซึ่งนั่นก็เป็นข้อถกเถียง)
นอกจากนี้มูลนิธิ ยังมีการร่วมทุนในด้าน "อาหาร" ในเมืองไทยด้วย
ในช่วงปี พ.ศ. 2512-2513 (ค.ศ. 1969-1970) มูลนิธิร็อกกี้เฟลเลอร์ (Rockefeller Foundation) ได้ร่วมลงทุนกับเครือเจริญโภคภัณฑ์ (CP) ในเอเชียตะวันออกเฉียงใต้ โดยเฉพาะในประเทศไทย ความร่วมมือนี้เกี่ยวข้องกับการพัฒนาอุตสาหกรรมการเลี้ยงไก่เนื้อ ซึ่งเป็นส่วนหนึ่งของการส่งเสริมการเกษตรและอาหารในภูมิภาค นั่นทำให้เทคโนโลยีการเลี้ยงสัตว์ของซีพีรุดหน้าอย่างเร็วมาก พันธุ์กุ้งขาวจากอเมริกา และ ไก่เนื้อที่จากเดิมต้องเลี้ยง 6 เดือน แต่ก็สามารถทำให้เหลือเวลาแค่ 8สัปดาห์ก็ได้กิโลครึ่งแล้ว
นอกจากนี้ยังร่วมทุนกับ มหาวิทยาลัยเกษตรศาสตร์ หนึ่งในโครงการที่โดดเด่นคือการสนับสนุน "ไร่สุวรรณ" หรือ Suwan Farm
ไร่สุวรรณ ตั้งอยู่ที่อำเภอปากช่อง จังหวัดนครราชสีมา เป็นศูนย์วิจัยข้าวโพดและข้าวฟ่างที่สำคัญของประเทศไทย เดิมทีพื้นที่นี้เป็นของจอมพลสฤษดิ์ ธนะรัชต์ และต่อมาได้โอนให้มหาวิทยาลัยเกษตรศาสตร์ดูแล มูลนิธิร็อกกี้เฟลเลอร์ได้ให้การสนับสนุนด้านทุนและความรู้ในการปรับปรุงพันธุ์ข้าวโพดเลี้ยงสัตว์ จนทำให้ไร่สุวรรณกลายเป็นแหล่งวิจัยข้าวโพดเลี้ยงสัตว์ที่ใหญ่ที่สุดในเอเชีย นักวิจัยที่ไร่สุวรรณได้พัฒนาพันธุ์ข้าวโพดที่ทนทานต่อโรคราน้ำค้าง ซึ่งเป็นปัญหาสำคัญในช่วงเวลานั้น
นั่นละครับ 5555
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ da0b9bc3:4e30a4a9
2025-04-13 08:48:10
@ da0b9bc3:4e30a4a9
2025-04-13 08:48:10Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/942018
-
 @ 7d33ba57:1b82db35
2025-04-13 08:39:56
@ 7d33ba57:1b82db35
2025-04-13 08:39:56Venice is like nowhere else on Earth. A city built on water, where gondolas glide through silent canals and palaces shimmer in the light of the lagoon. It’s romantic, surreal, and endlessly photogenic—from the grandeur of St. Mark’s Square to the quiet charm of back-alley bridges. Whether you're there for the art, the architecture, or the atmosphere, Venice is pure magic.
🌟 Must-See in Venice
1️⃣ St. Mark’s Basilica (Basilica di San Marco)
- A glittering masterpiece of Byzantine architecture
- Don’t miss the Pala d’Oro and mosaics inside
- Climb to the rooftop terrace for views over Piazza San Marco
2️⃣ Doge’s Palace (Palazzo Ducale)
- The seat of Venetian power for centuries
- Walk across the Bridge of Sighs to the old prison
- Book a "Secret Itineraries" tour to explore hidden passages
3️⃣ Grand Canal & Vaporetto Ride
- Take a vaporetto (water bus) from Piazzale Roma to San Marco
- You'll pass Rialto Bridge, palazzos, and everyday life along the water
- For extra magic, do it at sunset
4️⃣ Rialto Market & Bridge
- The city’s oldest bridge, buzzing with life
- Stop by the Rialto Market in the morning for local seafood and produce
- Great area to grab a spritz and people-watch
5️⃣ Gondola Ride or Rowboat Tour
- Yes, it’s touristy—but it’s iconic for a reason
- For a local spin, try a traghetto across the canal, or book a rowboat tour at sunset
🖼️ Art & Culture
- Gallerie dell’Accademia – Home to masterpieces by Titian, Veronese, and Tintoretto
- Peggy Guggenheim Collection – Modern art in a stunning canal-side setting
- Teatro La Fenice – Venice’s grand opera house, steeped in drama and beauty
🍝 What to Eat in Venice
- Cicchetti – Venetian tapas: try bacalà mantecato, crostini with seafood, or mini meatballs
- Sarde in saor – Sweet-and-sour marinated sardines
- Risotto al nero di seppia – Squid ink risotto
- Wash it down with a Venetian spritz (try one with Select or Cynar)
🌿 Day Trips from Venice
- Murano – Famous for glassblowing
- Burano – Bright, colorful houses and handmade lace
- Torcello – Quiet island with ancient churches and lagoon views
- Lido – Beachy escape from the city crowds
🎯 Venice Tips
✅ Get lost—it’s part of the charm (but download offline maps just in case)
✅ Visit early morning or late evening to feel the magic without the crowds
✅ Stay overnight if you can—Venice empties after the cruise ships leave
✅ Don’t feed the pigeons in St. Mark’s Square—it’s actually banned
✅ Look for "ombra" (local wine) and a plate of cicchetti at a traditional bacaro bar -
 @ 502ab02a:a2860397
2025-04-13 08:27:33
@ 502ab02a:a2860397
2025-04-13 08:27:33หากเดินเข้าแผนกผักในซูเปอร์มาร์เก็ต แล้วเกิดความรู้สึกว่า “บรอกโคลี” กับ “กระหล่ำดอก” หน้าตามันเหมือนกันยังกับแฝดที่คนหนึ่งเป็นเด็กเรียนเก่ง อีกคนเป็นศิลปิน ก็ไม่ต้องแปลกใจ เพราะจริง ๆ แล้วพวกเขาเป็นญาติสายตรงกันเลยล่ะครับ ชนิดที่ว่าเกิดจากต้นตระกูลเดียวกันเป๊ะ ๆ และไม่ได้เกิดจากการหล่นลงมาของเมล็ดพืชจากฟากฟ้าหรือจากการปลุกเสกของเทพธิดาในตำนานไหนทั้งนั้น แต่เกิดจากมือมนุษย์เราเองล้วน ๆครับ
ต้นกำเนิดของพืชทั้งสองนั้นย้อนกลับไปไกลถึง “Brassica oleracea” ซึ่งเป็นพืชผักพื้นฐานริมทะเลเมดิเตอร์เรเนียน หน้าตาเมื่อแรกพบก็ไม่ได้หรูหราเหมือนลูกหลานยุคนี้ มันเป็นแค่พืชใบเขียวธรรมดา ๆ ที่ชาวโรมันโบราณเดินผ่านไม่เหลียวหลัง
แต่เมื่อเวลาผ่านไป มนุษย์เริ่มรู้จักการ “คัดเลือกพันธุ์” (selective breeding) คือการเลือกปลูกต้นที่มีลักษณะที่ต้องการ แล้วขยายพันธุ์เฉพาะต้นนั้นต่อไป รุ่นแล้วรุ่นเล่า เหมือนการเลือกเพาะลูกหมาที่ฉลาดและขนฟู จนในที่สุดก็ได้สายพันธุ์ใหม่ ๆ ขึ้นมา
เช่นในกรณีต้นไม้ต้นนึง ถ้าชาวสวนคนหนึ่งชอบต้นที่มี “ตาดอก” ใหญ่หน่อย ก็จะปลูกมันต่อ ส่วนอีกคนชอบใบที่แน่น ๆ ก็เลือกปลูกต้นแบบนั้นต่อ แล้วสิ่งที่ตามมาก็คือความเลยเถิดของความหลากหลายอย่างไม่น่าเชื่อ เช่น • ถ้าเน้นปลูกส่วนใบได้ คะน้า • ถ้าเน้นปลูกส่วนตาดอกได้ กระหล่ำดอก • ถ้าตาดอกสีเขียวแน่น ๆได้ บรอกโคลี • ถ้าเน้นลำต้นบวม ๆได้ กะหล่ำหัว • ถ้าดอกออกแปลก ๆ คล้ายปะการังได้ โรมานีสโก (Romanesco)
แต่ทุกชนิดที่ว่ามานั้น…เป็น “สายพันธุ์ย่อย” ของพืชชนิดเดียวกัน คือ Brassica oleracea ทั้งหมด!
พูดให้เข้าใจง่ายคือบรอกโคลีไม่ได้มาจากพระเจ้า แต่มาจาก “การขยี้ย้ำในลักษณะ จนเป็นการเล่นแร่แปรพันธุ์ของเกษตรกรในยุคโรมัน” ที่ทำกันจริงจังจนกลายเป็นผักจานหลักบนโต๊ะอาหารเราทุกวันนี้
สิ่งที่น่าสนใจอีกคือ บรอกโคลีกับกระหล่ำดอกยังคงกลิ่นกายทางพันธุกรรมเดียวกันอยู่ แม้หน้าตาจะต่าง แต่ DNA ก็คล้ายกันมาก พอ ๆ กับพี่น้องที่ชอบกินของไม่เหมือนกัน แต่มาจากบ้านเดียวกัน
จริง ๆ แล้วพืชตระกูล Brassica พวกนี้แหละ ที่มีสารสำคัญชื่อ Glucosinolate เป็นเหมือนกับนักเคมีของพืช ที่มีสูตรลับไว้ป้องกันตัวเองจากแมลง กลูโคซิโนเลตบางชนิด (เช่น goitrin) อาจรบกวนการดูดซึมไอโอดีน ส่งผลต่อการทำงานของต่อมไทรอยด์ เลยเรียกสิ่งนี้ว่า เป็น anti-nutrient ที่เราเคยได้ยินกันครับ
ถึงตรงนี้ ใครที่ชอบกินผักเหล่านี้ก็น่าจะรู้สึกภูมิใจว่ากำลังกิน “ผลผลิตจากภูมิปัญญามนุษย์” ที่ไม่แพ้การสร้างปิรามิดหรือเครื่องจักรไอน้ำเลย เพราะการคัดเลือกพันธุ์อย่างละเอียดอ่อน ต้องใช้เวลาการย้ำปลูกเป็นร้อยปี และไม่ได้ใช้วิทยาศาสตร์ล้ำยุคอะไรเลย แค่ใช้ใจและมือเปล่าของชาวสวนรุ่นแล้วรุ่นเล่า
สรุปแล้ว บรอกโคลีและกระหล่ำดอก ไม่ใช่ของจากสวรรค์ แต่เป็นของจาก “ความพยายาม” ที่ยิ่งใหญ่พอ ๆ กับการสร้างอารยธรรม พระเจ้าอาจไม่ได้สร้างมัน…แต่มนุษย์เราก็เก่งพอที่จะเป็น “พระเจ้าแห่งผัก” อยู่เหมือนกันนะครับ 555
pirateketo #โรงบ่มสุขภาพ #HealthyHut #ตำรับเอ๋ #siripun
-
 @ 502ab02a:a2860397
2025-04-13 08:24:11
@ 502ab02a:a2860397
2025-04-13 08:24:11มีคนเทียบสัดส่วน โอเมก้า 6:3 ของน้ำมันคาโนล่า แล้วบอกว่าดีงาม เพราะมันได้ที่ 2:1
คืองี้ครับ มันเป็นประเด็นที่หลายคนยังเข้าใจคลาดเคลื่อนอยู่ไม่น้อยโดยเฉพาะเวลาเห็นว่าน้ำมันคาโนล่ามีโอเมก้า 3 ต่อ 6 ในอัตราส่วน 1:2 แล้วรีบบอกว่า “ดีต่อสุขภาพ” หรือ “บาลานซ์ดี” โดยไม่มองลงลึกไปถึง ชนิดของโอเมก้า 3 และ ชีวปริมาณการดูดซึม (bioavailability) ที่ต่างกันระหว่างโอเมก้า 3 จากพืช กับจากสัตว์
มันคือมายาทางตัวเลข ที่ superfood ชอบนำมาโชว์ให้เราดู ในน้ำมันคาโนล่า โอเมก้า 3 ที่พบจะอยู่ในรูปแบบ ALA (Alpha-Linolenic Acid) ซึ่งเป็นกรดไขมันโอเมก้า 3 ที่ ร่างกายไม่สามารถใช้ได้โดยตรง ต้องแปลงเป็น EPA และ DHA ก่อน ถึงจะมีผลต่อสมอง หลอดเลือด และระบบต้านการอักเสบ
ปัญหาคือ ร่างกายมนุษย์แปลง ALA ไปเป็น EPA ได้แค่ประมาณ 5-10% และแปลงต่อเป็น DHA ได้แค่ 0.5-5% เท่านั้น
ถ้าเรากิน ALA จากคาโนล่าออย 1,000 มิลลิกรัม เราอาจจะได้ DHA จริงๆ แค่ ไม่ถึง 50 มิลลิกรัม ซึ่งน้อยมากจนไม่เพียงพอต่อการบำรุงสมองหรือป้องกันโรคอักเสบเรื้อรังใดๆ
ประเด็นสำคัญการเกิด oxidation ของ ALA ในระหว่างการทอด เพราะ ALA เป็นกรดไขมันไม่อิ่มตัวแบบมีพันธะสาม (polyunsaturated) ที่ ไวต่อความร้อนและแสงมาก พอเจอความร้อนสูงในกระบวนการทอดหรือแม้แต่แค่โดนแสงขณะเก็บไว้ มันจะกลายเป็นสารอนุมูลอิสระที่ชื่อว่า lipid peroxide ซึ่งเป็นอันตรายต่อเซลล์และอาจเพิ่มความเสี่ยงของโรค NCD
ดังนั้น อย่างที่บอกบ่อยๆครับ จะเอาวิจัยจะอ่านวิจัยมาใช้ โปรดมองบริบทการ "ใช้ชีวิต" ด้วยครับ ค่าโอเมก้า 3:6 ของน้ำมันคาโนล่าอาจดู “สมดุล” แค่ในกระดาษ แต่ความจริงคือ มันเป็นโอเมก้า 3 แบบพืช (ALA) ที่ร่างกายใช้ได้น้อยมาก
“โอเมก้า 3 จากพืช ก็เหมือนแบงก์กาโม่ที่ต้องไปแลกที่ธนาคารก่อนถึงจะใช้ได้ ส่วนโอเมก้า 3 จากสัตว์น่ะ คือ บิทคอยน์ ที่เป็นของจริง”
https://www.facebook.com/share/p/1BwpmKdJtN/
ปล. Dr Brian Kunakom บอกว่า แค่ชื่อน้ำมันคาโนลาก็แปรรูปแล้ว!! ต้นคาโนลาไม่มีจริง มันถูกดัดแปลงมาจากผักกาดก้านขาวหรือ rapeseed plants ช่วงยุคสงครามโลกครั้งที่ 2 สหรัฐอเมริกาต้องการน้ำมันมาใช้หล่อลื่นเครื่องยนต์ ประเทศแคนาดาจึงหาวิธีปลูกและผลิต rapeseed oil หลังจากที่สิ้นสุดสงครามโลกครั้งที่ 2 rapeseed oil ถูกผลิตมาเยอะเกินและขายไม่ออก ประเทศแคนาดาจึงหาวิธีขายให้ประเทศอื่น ใน rapeseed oil ของแคนาดา สาร Erucic acid มีสูงไปซึ่งไม่เหมาะสำหรับการทานเป็นอาหาร ในช่วงประมาณปี 1970 แคนาดาสำเร็จในการจด patent สำหรับการลดสาร Erucic acid จากน้ำมัน rapeseed และตั้งชื่อน้ำมันใหม่ว่า Canola oil Canola ย่อมาจาก Canadian oil low acid นอกจากจะแปรรูปจากการสกัด ยังแปรรูปในการตั้งชื่อด้วยครับ
pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 8d34bd24:414be32b
2025-04-13 04:29:33
@ 8d34bd24:414be32b
2025-04-13 04:29:33I was listening to a sermon at my church this weekend on Luke 9. It made me think of these words, “I do believe; help my unbelief.” I’ll start with context on this statement and then show how it applies to the passage we were studying.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” (Mark 9:20-24) {emphasis mine}
In this story, a desperate father brought his son to Jesus’s disciples for healing, when they failed, he brought the boy to Jesus. He begged for help, but qualified with “But if You can … .” How often do we explicitly or implicitly say this to God in our prayers.
Just as this father believed in Jesus enough to bring his dear child to Jesus, but still had doubts, we tend to be the same. As Christians, we believe that Jesus loved us enough to die on the cross, but do we believe He is always with us? Do we believe He will never leave nor forsake us? Do we believe that all things work together for good for those who love God and are called according to His purpose? I think we can all say, “I do believe; help my unbelief.”
We all have highs where we are excited about Jesus and believe He is working in us and through us. We also have lows where we feel distant and wondering if He sees or cares. We need to have that belief of the highs when we are going through the lows.
In Luke 9, Jesus sent out His 12 disciples to share the gospel and heal the sick and possessed. They came back on a high, amazed at the great miracles that Jesus had worked through them.
And He called the twelve together, and gave them power and authority over all the demons and to heal diseases. And He sent them out to proclaim the kingdom of God and to perform healing. … When the apostles returned, they gave an account to Him of all that they had done. Taking them with Him, He withdrew by Himself to a city called Bethsaida. (Luke 9:1-2,10) {emphasis mine}
The 12 disciples were on a high. Miracles had been done through their hands and at their word. They felt like they could conquer the world, but this high and great faith did not last very long. Jesus took them away. They thought they were going to spend some private time with Jesus, but that is not what happened. A great crowd ran ahead and met them. Jesus saw their physical and spiritual needs and began to preach and minister to them. It began to get late, so the disciples came to Jesus to ask Him to wrap things up and send the people away so they could eat (like Jesus didn’t know).
Now the day was ending, and the twelve came and said to Him, “Send the crowd away, that they may go into the surrounding villages and countryside and find lodging and get something to eat; for here we are in a desolate place.” But He said to them, “You give them something to eat!” And they said, “We have no more than five loaves and two fish, unless perhaps we go and buy food for all these people.” (For there were about five thousand men.) And He said to His disciples, “Have them sit down to eat in groups of about fifty each.” They did so, and had them all sit down. Then He took the five loaves and the two fish, and looking up to heaven, He blessed them, and broke them, and kept giving them to the disciples to set before the people. And they all ate and were satisfied; and the broken pieces which they had left over were picked up, twelve baskets full. (Luke 9:12-17) {emphasis mine}
Jesus gently guided His disciples, trying to help them see that there was nothing to fear, that He had everything under control, and that nothing is impossible with Him. When He asked them what they had available to feed the crowd, and they just had one young boy’s small lunch, they immediately assumed feeding the crowd was impossible. Jesus then proceeded to feed the 5,000 (5,000 men and an uncounted number of women and children). Yes, Jesus was merciful and fed this hungry crowd, but I believe this feeding was about so much more than meeting the physical needs of the crowd. Notice how every person there ate until they were satisfied. Jesus then had the disciples pick up the leftovers. How much was left over? 12 baskets full. How many disciples was He giving an object lesson to? 12 disciples. Jesus doesn’t do anything by accident. Everything He does is for a reason. (In the same way everything He allows to happen to us is for a good reason.) He did what the disciples thought was impossible, He fed the huge crowd, but even more, He had one basketful leftover for each disciple. This was a personal message to each of His disciples.
When Jesus sent them out with the command to share the Gospel, heal the sick, and cast out demons, they went out with faith and returned with even greater faith “I believe,” but then the day after they returned, their faith waivered again. They needed to cry out, “help my unbelief.” Jesus empowered and guided them both in their belief and in their unbelief. He most definitely helped their unbelief and will do the same for us.
Our Father, please help us to have faith in good times and in bad. Help us to believe with all of our heart, mind, and soul. We believe that you are God and we believe that Jesus came down to earth to live the perfect life that we are unable to live, died to receive the punishment we deserved, and was raised to life on the third day. Believe that the Holy Spirit lives within us empowering and guiding us. We also acknowledge that we have doubts. Please help our unbelief.
Trust Jesus.
-
 @ 502ab02a:a2860397
2025-04-13 03:34:45
@ 502ab02a:a2860397
2025-04-13 03:34:45ลอดจ์ในสยาม ในช่วงที่โลกดูเหมือนจะหมุนเร็วขึ้นเรื่อย ๆ เราเริ่มเห็นปรากฏการณ์บางอย่างซ้ำซ้อนคล้ายคลึงกันไปทั่วโลก ผู้นำประเทศพูดเรื่องเดียวกัน การเงินผูกติดกันเหมือนลูกโป่งชะลูดลม การศึกษาเน้นเรื่องเดียวกัน อาหารแปรรูปสูตรเดียวกัน ยาและวัคซีนออกแนวเดียวกัน คนจำนวนมากพอได้ยินคำนี้ ก็มักจะผูกโยงกับ Freemason โดยอัตโนมัติ เหมือนพอพูดถึง “จานบิน” ก็ต้องนึกถึง “มนุษย์ต่างดาว” ไม่รู้ใครเป็นคนกำหนดชุดความเชื่อนี้ไว้ แต่ที่แน่ ๆ มันติดอยู่ในหัวเราหลายสิบปีแล้ว ซึ่งเราเองก็ไม่อาจทราบได้ว่า มันจะเกี่ยวข้องกันจริงๆหรือ?
ถ้ามองแบบเบื้องต้น Freemason คือกลุ่มที่รวมตัวกันตามหลักของ “ภราดรภาพ” (Brotherhood) ซึ่งเริ่มตั้งแต่ยุคยุโรปกลาง โดยมีโครงสร้างแบบลับ–กึ่งลับ จุดร่วมอยู่ที่ “พิธีกรรม” การฝึกจิตวิญญาณ ความเชื่อในสัญลักษณ์ และการสร้างเครือข่ายความร่วมมือในทุกระดับ ตั้งแต่ช่างหิน คนทำตึก ไปจนถึงนักการเมืองระดับสูง ใครที่ได้เข้าไปอยู่ในระบบนี้ จะต้องผ่านการทดสอบหลายขั้น มีการขึ้นระดับ (Degree) และมีลำดับชั้นเหมือนบันได แต่ทั้งหมดก็ยังคงเป็นเรื่องเล่า เพราะ freemason พูดเสมอว่าพวกเขาไม่ใช่องค์กรลับ ไม่ใช่กลุ่มโอกาสในการสร้างเครือข่ายเพื่อธุรกิจ
คำถามที่ถูกถามบ่อยๆคือ แล้วในไทยมีด้วยเหรอ? คำตอบคือ “มี และมีมานานแล้วด้วย” วันนี้เรามาทำความรู้จักกับ Freemason lodge แห่งแรกในไทยกันครับ
ประเทศไทยเริ่มมี “Freemason Lodge” อย่างเป็นทางการตั้งแต่ยุครัชกาลที่ 6 โดยใช้ชื่อว่า “ลอดจ์เซนต์จอห์น” (Lodge St. John) ลำดับทะเบียนคือ No.1072 ตามธรรมนูญสก็อตแลนด์
ปีที่ก่อตั้ง ค.ศ. 1911 ตรงกับ พ.ศ. 2454 สมัยรัชการที่ 6 ต้นสังกัดคือ Grand Lodge of Scotland เป็นลอดจ์แห่งแรกในประเทศไทย และเก่าแก่ที่สุดในเอเชียตะวันออกเฉียงใต้ สมาชิกหลักในยุคแรกจะเป็นชาวอังกฤษ ฝรั่งเศส จีน และขุนนางไทยระดับสูงในราชสำนัก ลอดจ์นี้ถือเป็น “จุดเริ่มต้นของ Freemason ในไทย”
เริ่มต้นจากปี พ.ศ.2411(ค.ศ. 1868) หลังจากที่สยามเปิดประตูรับอิทธิพลจากต่างประเทศ เพื่อความมั่นใจในการอยู่รอดของประเทศจากการล่าอาณานิคม รัชกาลที่ 6 ทรงเชิญฝรั่งเศส อังกฤษ เยอรมัน รัสเซีย เดนมาร์ก อเมริกาและประเทศอื่นๆ ให้ส่งผู้เชี่ยวชาญที่เก่งที่สุดมาสร้างและบริหารหน่วยงานของรัฐบาลต่างๆที่จำเป็นต่อความก้าวหน้าของประเทศในเวลานั้น
ลอดจ์นี้ถือเป็น “จุดเริ่มต้นของ Freemason ในไทย”
เริ่มต้นจากปี พ.ศ.2411(ค.ศ. 1868) หลังจากที่สยามเปิดประตูรับอิทธิพลจากต่างประเทศ เพื่อความมั่นใจในการอยู่รอดของประเทศจากการล่าอาณานิคม รัชกาลที่ 6 ทรงเชิญฝรั่งเศส อังกฤษ เยอรมัน รัสเซีย เดนมาร์ก อเมริกาและประเทศอื่นๆ ให้ส่งผู้เชี่ยวชาญที่เก่งที่สุดมาสร้างและบริหารหน่วยงานของรัฐบาลต่างๆที่จำเป็นต่อความก้าวหน้าของประเทศในเวลานั้น  บันทึกเกี่ยวกับ Freemason พบในเดือน เมษายน พ.ศ. 2421 (April 1878) ว่ามีการพยายามจัดตั้งลอดจ์อยู่หลายครั้ง แต่ระหว่างนั้นก็ประสบปัญหามากมายอยู่ จนสำเร็จในปี พ.ศ. 2545 (1911) ผ่านเหตุการณ์สำคัญมากมายโดยเฉพาะสงครามโลกครั้งที่ 2 ซึ่งมีสมาชิกเสรีไทย ภายใต้ Force 136 of the British Special Operations Executive และ the American Office of Strategic Services มาเป็น new gen ritualists ของ freemason
บันทึกเกี่ยวกับ Freemason พบในเดือน เมษายน พ.ศ. 2421 (April 1878) ว่ามีการพยายามจัดตั้งลอดจ์อยู่หลายครั้ง แต่ระหว่างนั้นก็ประสบปัญหามากมายอยู่ จนสำเร็จในปี พ.ศ. 2545 (1911) ผ่านเหตุการณ์สำคัญมากมายโดยเฉพาะสงครามโลกครั้งที่ 2 ซึ่งมีสมาชิกเสรีไทย ภายใต้ Force 136 of the British Special Operations Executive และ the American Office of Strategic Services มาเป็น new gen ritualists ของ freemason 
 ปัจจุบัน ลอดจ์เซนต์จอห์น ตั้งอยู่ที่ นวมินทร์ 24 ถ้าสนใจเยี่ยมชมกิจกรรมของ freemason ต้องทำการติดต่อล่วงหน้าก่อนทุกกรณีครับ
https://maps.app.goo.gl/yA8Qq6NMCXi5S5Z27
ปัจจุบัน ลอดจ์เซนต์จอห์น ตั้งอยู่ที่ นวมินทร์ 24 ถ้าสนใจเยี่ยมชมกิจกรรมของ freemason ต้องทำการติดต่อล่วงหน้าก่อนทุกกรณีครับ
https://maps.app.goo.gl/yA8Qq6NMCXi5S5Z27และหากต้องการสมัครเป็น freemason เขาต้องตรวจสอบให้แน่ใจว่าแต่ละคนมีเหตุผลที่เหมาะสมในการต้องการเป็น Freemason ว่าเหมาะสมหรือไม่ ผ่านแบบฟอร์มทางเว็บไซท์ จากนั้นจะมีการจัดประชุมกับสมาชิกอาวุโส เพื่อตกลงร่วมกันถึงความเป็น freemason และเมื่อการสัมภาษณ์ผ่านไปได้ด้วยดี เราก็จะได้รับเชิญในการเข้าร่วมงานสังสรรค์ประจำเดือน ซึ่งจัดทุกๆเดือนในวันอังคารที่สาม และจะต้องเข้าร่วมกิจกรรมต่อเนื่องอย่างน้อย 6 เดือน เพื่อที่จะให้พี่น้อง 2 คนในลอดจ์ สนับสนุนการสมัครอย่างเป็นทางการ โดยพี่น้อง 2 คนนั้นจะต้องรับผิดชอบต่อความก้าวหน้าของเรา เพื่อประสบความสำเร็จในการเป็น freemason ด้วยเช่นกัน
การเป็นสมาชิกนั้นจะมีค่าธรรมเนียมรายปีด้วยครับ นอกจากนี้จะต้องใช้เวลาราวๆ 2 ปี เพื่อเรียนจบ 2 degree สำหรับการเป็นเป็น Master Mason อีกด้วย แต่ทั้งหมดต้องอย่าลืมว่า ไม่ใช่แค่สมัครแล้วจะได้เลย มันขึ้นอยู่กับว่า freemason จะรับพิจารณาเราด้วยหรือไม่ครับ
และทั้งหมดนี้คือข้อมูลแบบคร่าวๆมากๆ เกี่ยวกับ freemason lodge แห่งแรกในประเทศไทยครับ
-
 @ 0b118e40:4edc09cb
2025-04-13 03:30:37
@ 0b118e40:4edc09cb
2025-04-13 03:30:37I picked up this book 'Nuclear Power Explained' by Dirk Eidemuller to understand nuclear power and the historical context during the nuclear euphoria era. I’ll share a bit on the history part. Note: I have not seen the movie Oppenheimer yet.
Some key highlights :
In 1933 -Leo Szilard thought of the nuclear chain reaction concept - whereby one nuclear reaction triggers a series of additional nuclear reactions, releasing a significant amount of energy. This is fundamental for nuclear reactors and weapons. He figured this out the same year he was fleeing from one country to another from Hitler. He tried to share this idea to Rutherford but got kicked out of the office.
In 1934 - Enrico Fermi first conducted the experiment in irradiating uranium with neutrons but unfortunately he did not spot anything
In 1938, Otto Hahn and Fritz Strassmann's experiments accidentally found barium forming when they irradiated uranium with neutrons. Splitting uranium atoms was not a norm at that time. This new finding was the start of the nuclear era.
Fission vs. Fusion * Fission splits heavy nuclei into smaller ones, whereas fusion combines light nuclei into heavier ones. * Fission is used in nuclear reactors and atomic bombs, while fusion is the process that powers stars (energy is produced when hydrogen nuclei combine to form helium). The goal of developing fusion-based power generation on Earth is still work-in-progress. Thermonuclear bombs (super bombs) use fusion as well.
Otto Hahn collaborated with Lisa Meitner, Germany's first female physics professor, who fled to Sweden due to Nazi persecution. Lisa encouraged Hahn to repeat Fermi’s experiment with high precision. Lisa Meitner and her cousin Otto Frisch analyzed the results and coined the term "fission."
(Note : Women physicist were gaining popularity during that time - Marie Curie, nuclear physics, won 2 nobel price for her work)
1938 - Otto Hahn and Lisa published their results. Nuclear physicists worldwide were in disbelief.
In the early days, Albert Einstein didn’t think it was possible.He said that the whole thing would be like shooting at “birds in the dark in a country where there are few birds.”
Ernest Rutherford (who introduced the atom particle model in 1911 ) thought that it was an absurd idea to try to generate energy in this way. Note : both Rutherford and Bohr introduced the atom particle model, both had a central nucleus and electrons. Bohr’s model was more detailed and led to quantum mechanics and modern behaviour of atoms.
1939 - WW2 started on Sep 1, 1939
1941 - Japan attacked Pearl Harbor in Hawaii
After Otto Hahn’s paper released, a few things happened
Albert Einstein's E=mc^2 links energy and mass, and while this concept has been around for a while and is based on space and time and initially unrelated to nuclear, it also explained nuclear fission's energy release.
Szilard, who was a long time friend of Einstein, reached out and shared the nuclear reaction theory and its potential for killer weapons. They were worried Nazis might build it first and bomb the US.
They wrote to President Roosevelt to establish research for nuclear weapons to counter a possible attack. To add to suspicion, Germany halted uranium sales from occupied Czechoslovak mines.
(Einstein later on said he regretted this letter after witnessing the bombings of Hiroshima and Nagasaki. If he knew Germany wouldn't succeed in making an atomic bomb, he wouldn't have taken action)
Alexander Sachs, a friend of Szilárd and Roosevelt delivered the letter. At first President Roosevelt was not interested. Concurrently Germany invaded Poland, the tension was rising.
Sachs apparently used the analogy of Robert Fulton proposing steamships to Napoleon (to up the notch on traditional sail ships) to convince Roosevelt of the need for a large-scale nuclear research program.
1942 - Roosevet finally agreed
The scientists formed a committee. Military were initially skeptical and wanted to cut costs. The scientists received $6,000 to start the Manhattan Project.
The First Nuclear Reactor : Chicago Pile-1 - a group of popular physicists, including Enrico Fermi and Leó Szilárd, designed the first nuclear reactor ever built by humans. It had 5.4 tons of pure uranium metal and another 45 tons of uranium oxide.
The first nuclear reactor is underneath an unused grandstand of the University of Chicago’s football stadium.
1942 - The first test was on Dec 2. If the chain reaction went awry, a worker would use an axe to cut a rope and release an emergency control rod above the reactor. There was also an automatic shutdown system, and someone ready to pour cadmium salt from above, which stops the chain reaction.
It was a success - the reactor ran at minimum power to initiate a nearly self-sustaining chain reaction.
This led to more reactors and bomb-grade plutonium to be produced.
(note : if you are reading up to here, plutoniums are man-made, and not mined from earth the same way uranium, minerals and ores are)
France was quickly occupied in the war, and its nuclear research material was brought to Germany.
The Soviet Union put in very little effort on the atomic bomb during this time as they needed to fight against the Nazis.
In Japan, too, nuclear research proceeded slowly.
In Germany, multiple research groups operated within the "Uranium Association" also known as “Uranverein”. Popular figures like Werner Heisenberg, Carl Friedrich von Weizsäcker and Walther Gerlach worked on it but failed to activate it.
In England, German- Austrian emigrants Otto Frisch and Rudolf Peierls initiated the “MAUD Committee'' (Military Application of Uranium Detonation) . Unfortunately England classified them as “enemy aliens" hence they went to Los Alamos to work on the US nuclear tech.
Their work led to the British-Canadian “Tube Alloys” secret project, which kickstarted the American Manhattan Project. This American Manhattan project under President Eisenhower introduced nuclear reactors to Iran, Pakistan and Israel. But more on that later.
After the successful experiments with the Chicago Pile-1, the American atomic bomb project proceeded at full speed. The Manhattan Project had more than 150,000 people working on it!
Everything was done under the highest military secrecy. With the exception of the leading scientists and military personnel, nobody knew what was actually being worked on until the news of the destruction of Hiroshima.
With two billion dollars (massive at that time), leading scientist and nuclear physicist Robert Oppenheimer and General Leslie Groves quickly built a secret nuclear research center in remote Los Alamos, New Mexico, and established a nuclear industry as big as the entire American automobile industry during that era.
The Los Alamos Laboratory was called Project Y where the actual bomb design was being researched
University of Chicago’s met lab was a big research contributor during this euphoric nuclear era
Oak Ridge, Tennessee, known as "Atomic City," had large isotope separation facilities, two massive diffusion plants, one of which was the world's largest building at the time, and an electromagnetic separation plant. It provided the uranium for the Hiroshima bomb (little boy). The Hanford site provided the uranium for the Nagasaki bomb (fat man).
April 1945 - Harry Truman became U.S. President.
And four months later, he authorized nuclear attacks on Japanese civilians.
June 1945 - Szilard and Franck co-authored the "Franck Report" with fellow scientists. They cautioned against using nuclear bombs on civilians,
July 1945 - Szilard and other dozen researchers wrote to president Harry Truman to urgently warn him against civilian targets (The Szilard petition)
August 6, 1945 * Hiroshima bomb ~140,000 people died * Nagasaki bomb ~70,000 people died
Robert Oppenheimer on this explosion : “Now I have become death, the destroyer of worlds.” (from the Bhagavad Gita, a sacred Hindu text)
September 2,1945 - WW2 ended
In October 1945 , Oppenheimer resigned.
1946 - One year after the war, Leo Szilárd and Albert Einstein started the Emergency Committee of Atomic Scientists to inform the public about nuclear weapons and promote global peace.
Szilard also arranged conferences with scientists from both sides East and West to find better ways for security and peace.
After WW2, Soviet Union caught up with the US nuclear tech through espionage
1949 - Soviet detonated their first nuclear bomb in Semipalatinsk Test Site, in Kazakhstan.
In 1949 Fermi and Nobel laureate Isidor Rabi cautioned that this new weapon could have devastating consequences, approaching genocide.
1950 - 1953 - Korean war between communism (North Korea) and capitalism (South Korea). The US supported South Korea but decided against nuclear weapons due to ethical concerns. But the ideology war was becoming more apparent here.
1952 - Great Britain detonated its first atomic bomb
1952 - US developed the first hydrogen bomb - based on nuclear fusion and not nuclear fission. These super bombs were 800x stronger than the Hiroshima bomb. Instead of splitting the atomic nuclei to smaller ones, very light atomic nuclei are fused into heavier ones which enables a greater explosive forces
Oppenheimer spoke against the development of thermonuclear weapons/hydrogen bombs.
In the 1940s and 1950s during the McCarthy era, there was widespread fear of communism. People worked to expose anyone they thought might be associated with communism. Senator Joseph McCarthy led investigations, and J. Robert Oppenheimer was accused of having communist ties.
In 1954 - Oppenheimer’s security clearance was revoked by the U.S. Atomic Energy Commission after a highly publicized hearing accusing him of a communist past.
1955 - Einstein passed away. He was 76
1958 - Khrushchev became premier (Soviet Union). In his first full briefing after having a full view of the nuclear environment he said “ I could not sleep for several days. Then I became convinced that we could never possibly use these weapons, and when I realized that I was able to sleep again.”
There’s a long bit on him and JFK eventually working out peace in secrecy...
1960 - Szilárd met with Nikita Khrushchev in New York for two hours. He convinced the Soviet leader to support the idea of a hotline with the US to prevent accidental nuclear war.
1960 - France detonated its first atomic bomb
1961 - JFK came to power
1962 - Cuban Missile Crisis - lasted for 2 weeks.
The Cuban Missile Crisis began when the Soviet Union secretly placed nuclear missiles in Cuba, just 90 miles from the US, raising the threat of nuclear conflict. It ended with an agreement between the US and Soviet Union:
- The U.S. wouldn't invade Cuba.
- The USSR would remove its Cuban missiles.
- The U.S. would secretly remove its missiles from Turkey, easing tensions.
The end of Cuban Missile crisis started the peace journey between US and the Soviet Unions.
But sadly, not everybody loved peace.
1963 - JFK was assassinated
1964 - Khrushchev was ousted
1964 - Leo Szilard died of heart attack
1964 - China detonated its first atomic bomb
1983 - another possible nuclear attack during the Cold War - Soviet satellites wrongly signaled an American missile attack. Stanislav Petrov, in charge, could have launched a nuclear counterattack but didn't because he thought it was a technical glitch. It turned out he was right; sunlight reflections caused the false alarm. Petrov's decision likely averted a disastrous nuclear war. But it’s worrying how easy it was for world disaster.
1991 - The Cold War ended when the Berlin Wall came down, a significant symbol of bridging the East and the West
Part 2 - nuclear as electricity instead of bombs.
Throughout this time there was a growing shift to use nuclear power as electricity. I separated both timelines to have a clearer view on it
1951 - first reactor in Idaho used to generate electricity instead of bombs (small test reactor)
Jan 1953- President Eisenhower came was elected to office
Dec 1953 - President Eisenhower delivered his infamous "Atoms for Peace" speech to the UN, on the dangers of nuclear war and the potential of nuclear technology for human development.
He encouraged countries to use nuclear technology for peaceful purposes (electricity).
Iran, Israel, and Pakistan being among the first to agree. American Machine and Foundry constructed their early nuclear facilities.
This change from military to civilian use was made possible by amendments to the Atomic Energy Act.
1954- Russia built the first real reactor that converts nuclear power into electricity and supply it to the public power grid
1955- On August 8, in Geneva, Switzerland, the largest scientific conference in history, called the “International Conference on the Peaceful Uses of Atomic Energy,” began.
More than 1500 participants from East and West exchanged what were previously secretive results with surprising openness and aroused the curiosity of the world publicly.
1955 - The first nuclear-powered submarine, USS Nautilus, was put to sea
1956- the second nuclear power plant that produced electricity on an industrial scale in Calder Hall, near Windscale in England
1958 - the first commercialized power reactor in the US in Shippingport, Pennsylvania
In the 70’s- oil crisis promoted the use of nuclear as energy
1986 - Chernobyl (30 people died) - The Chernobyl disaster resulted from a poorly designed experiment at nuclear reactor Unit 4. They turned off safety systems, removed control rods, and ran the reactor at 7 percent power.
2011- Fukushima disaster (19,759 died) - After a major earthquake, a 15-metre tsunami disabled the power supply and cooling of three Fukushima Daiichi reactors. This led to a nuclear accident on March 11, 2011. All three cores mostly melted within the first three days.
There are a lot of learning from disasters. New reactor designs aim for safety and efficiency, but some projects face rising costs and delays. Managing radioactive waste remains a challenge. The future of nuclear power's role in global electricity is uncertain. If one day nuclear power is really safe, each home can have its own mini power plants.
There are 436 nuclear reactors in the world located in 32 countries as of May 2023
On average, nuclear powers 10% of global power needs. Some countries are heading for 20%
2 takeaways :
-
United States created and won the nuclear race because it welcomed immigrants - who turned out to be superstar nuclear physicist persecuted in their countries
-
International cooperation, advocated by many researchers since the discovery of nuclear fission, hopefully outweighs power politics.
-
 @ 0b118e40:4edc09cb
2025-04-13 02:46:36
@ 0b118e40:4edc09cb
2025-04-13 02:46:36note - i wrote this before the global trade war, back when tariffs only affected China, Mexico, and Canada. But you will still get the gist of it.
During tough economic times, governments have to decide if they should open markets to global trade or protect local businesses with tariffs. The United States has swung between these two strategies, and history shows that the results are never straightforward
Just days ago, President Donald Trump imposed tariffs on imports from Canada, Mexico, and China. He framed these tariffs (25% on most Canadian goods, 10% on Canadian energy, 25% on Mexican imports, and 10% on Chinese imports) as a way to protect American industries.
But will they actually help, or could they backfire?
A History of U.S. Tariffs
Many have asked if countries will retaliate against the US. They can and they have. Once upon a time, 60 countries were so pissed off at the US, they retaliated at one go and crushed US dominance over trade.
This was during the Great Depression era in the 1930s when the government passed the Smoot-Hawley Tariff Act, placing high taxes on over 20,000 foreign goods. The goal was to protect American jobs, especially American farmers and manufacturers, but it backfired so badly.
Over 60 countries, including Canada, France, and Germany, retaliated by imposing their own tariffs. By 1933, US imports and exports both dropped significantly over 60%, and unemployment rose to 25%.
After President Franklin Roosevelt came to office, he implemented the Reciprocal Trade Agreements Act of 1934 to reverse these policies, calming the world down and reviving trade again.
The economist history of protectionism
The idea of shielding local businesses with tariffs isn’t new or recent. It's been around for a few centuries. In the 16th to 18th centuries, mercantilism encouraged countries to limit imports and boost exports.
In the 18th century, Adam Smith, in The Wealth of Nations, argued that free trade allows nations to specialize in what they do best countering protectionism policies. Friedrich List later challenged Smith's view by stating that developing countries need some protection to grow their “infant” industries which is a belief that still influences many governments today.
But how often do governments truly support startups and new small businesses in ways that create real growth, rather than allowing funds to trickle down to large corporations instead?
In modern times, John Maynard Keynes supported government intervention during economic downturns, while Milton Friedman championed free trade and minimal state interference.
Paul Krugman argued that limited protectionism can help large industries by providing them unfair advantages to become global market leaders. I have deep reservations about Krugman’s take, particularly on its impact or lack thereof in globalizing small businesses.
The debate between free trade and protectionism has existed for centuries. What’s clear is that there is no one-size-fits-all model to this.
The Political Debate - left vs right
Both the left and right have used tariffs but for different reasons. The right supports tariffs to protect jobs and industries, while the left uses them to prevent multinational corporations from exploiting cheap labor abroad.
Neoliberal policies favor free trade, arguing that competition drives efficiency and growth. In the US this gets a little bit confusing as liberals are tied to the left, and free trade is tied to libertarianism which the rights align closely with, yet at present right wing politicians push for protectionism which crosses the boundaries of free-trade.
There are also institutions like the WTO and IMF who advocate for open markets, but their policies often reflect political alliances and preferential treatment - so it depends on what you define as true 'free trade’.
Who Really Benefits from Tariffs?
Most often, tariffs help capital-intensive industries like pharmaceuticals, tech, and defense, while hurting labor-intensive sectors like manufacturing, agriculture, and construction.
This worsens inequality as big corporations will thrive, while small businesses and working-class people struggle with rising costs and fewer job opportunities.
I’ve been reading through international trade economics out of personal interest, I'll share some models below on why this is the case
1. The Disruption of Natural Trade
Tariffs disrupt the natural flow of trade. The Heckscher-Ohlin model explains that countries export goods that match their resources like Canada’s natural resource energy or China’s labour intensive textile and electronics. When tariffs block this natural exchange, industries suffer.
A clear example was Europe’s energy crisis during the Russia-Ukraine war. By abruptly cutting themselves off from the supply of Russian energy, Europe scrambled to find alternative sources. In the end, it was the people who had to bear the brunt of skyrocketing prices of energy.
2. Who wins and who loses?
The Stolper-Samuelson theorem helps us understand who benefits from tariffs and who loses. The idea behind it is that tariffs benefit capital-intensive industries, while labor-intensive sectors are hurt.
In the US, small manufacturing industries that rely on low-cost imports on intermediary parts from countries like China and Mexico will face rising costs, making their final goods too expensive and less competitive. This is similar to what happened to Argentina, where subsidies and devaluation of pesos contributed to cost-push inflation, making locally produced goods more expensive and less competitive globally.
This also reminded me of the decline of the US Rust Belt during the 1970s and 1980s, where the outsourcing of labour-intensive manufacturing jobs led to economic stagnation in many regions in the Midwest, while capital-intensive sectors flourished on the coasts. It resulted in significantly high income inequality that has not improved over the last 40 years.
Ultimately the cost of economic disruption is disproportionately borne by smaller businesses and low-skilled workers. At the end of the day, the rich get richer and the poor get poorer.
3. Delays in Economic Growth
The Rybczynski theorem suggests that economic growth depends on how efficiently nations reallocate their resources toward capital- or labor-intensive industries. But tariffs can distort this transition and progress.
In the 70s and 80s, the US steel industry had competition from Japan and Germany who modernized their production methods, making their steel more efficient and cost-effective. Instead of prioritizing innovation, many U.S. steel producers relied on tariffs and protectionist measures to shield themselves from foreign competition. This helped for a bit but over time, American steelmakers lost global market share as foreign competitors continued to produce better, cheaper steel. Other factors, such as aging infrastructure, and economic shifts toward a service-based economy, further contributed to the industry's decline.
A similar struggle is seen today with China’s high-tech ambitions. Tariffs on Chinese electronics and technology products limit access to key inputs, such as semiconductors and advanced robotics. While China continues its push for automation and AI-driven manufacturing, these trade barriers increase costs and disrupt supply chains, forcing China to accelerate its decoupling from Western markets. This shift could further strengthen alliances within BRICS, as China seeks alternative trade partnerships to reduce reliance on U.S.-controlled financial and technological ecosystems.
Will the current Tariff imposition backfire and isolate the US like it did a hundred years ago or 50 years ago? Is US risking it's position as a trusted economic leader? Only time would tell
The impact of tariff on innovation - or lack thereof
While the short-term impacts of tariffs often include higher consumer prices and job losses, the long-term effects can be even more damaging, as they discourage innovation by increasing costs and reducing competition.
Some historical examples globally : * Nigeria: Blocking import of rice opened up black market out of desperation to survive. * Brazil: Protectionist car policies led to expensive, outdated vehicles. * Malaysia’s Proton: Sheltered by tariffs and cronyism and failed to compete globally. * India (before 1991): Over-regulation limited the industries, until economic reforms allowed for growth. * Soviet Union during Cold War : Substandard products and minimal innovation due to the absence of foreign alternatives, yielding to economic stagnation.
On the flip side, Vietnam has significantly reduced protectionism policies by actively pursuing free trade agreements. This enabled it to become a key manufacturing hub. But Vietnam is not stopping there as it is actively pushing forward its capital-intensive growth by funding entrepreneurs.
The Future of U.S. Tariffs
History has shown that tariffs rarely deliver their intended benefits without unintended consequences. While they may provide temporary relief, they often raise prices, shrink job opportunities, and weaken industries in the long run.
Without a clear strategy for innovation and industrial modernization, the U.S. risks repeating past mistakes of isolating itself from global trade rather than strengthening its economy.
At this point, only time will tell whether these tariffs will truly help Americans or will they, once again, make the rich richer and the poor poorer.
-
 @ 0b118e40:4edc09cb
2025-04-13 02:41:14
@ 0b118e40:4edc09cb
2025-04-13 02:41:14In wanting to understand the global economy of manufacturing better and in particular the decline of US manufacturing, I picked up a few books on it. This one is called ‘Why manufacturing is still key to America's future’ by Ro Khanna. It’s a little old but I’ve shared some recent stats as a comparison as well. Ro Khanna was with the U.S. Dept of Commerce, focusing on govt's impact, or lack thereof, on manufacturing. Some key highlights:
- You can’t split R&D and manufacturing. When you offshore manufacturing, you send off design with it and you lose a big chance to cultivate innovation in the US - Andy Grove, CEO of Intel.
- Manufacturing is needed to reduce the trade deficit that started in 1971
- U.S. exports to China are $153.8 billion, imports are $536.8 billion. Hence trade deficit with China is $382.9 billion
- The private sector demands out-of-the-box thinking. In the gov’t, follow instructions; don’t make waves; keep your head down for career advancement.
- Small and medium-sized businesses create about half of all manufacturing jobs and make up more than 90 percent of U.S. manufacturers
- Cluster theory - a lot of business in the surrounding area impacts other businesses i.e. supply chain. On the flip side, businesses shutting down will be like dominoes impacting other businesses. Michael Porter, The Competitive Advantage of Nations" (1990)
- Foreign subsidy - foreign companies ie China get a lot of subsidies to build manufacturing - free land, and factory capital. Cheap labour is not the only competition
- Corporate tax - The US charges heavy corporate tax on foreign earnings hence companies rather invest outside than bring it back - John Chambers, CEO and Chairman Emeritus, Cisco 9 < 1 percent of American businesses export and mostly to Canada and Mexico only
- US global manufacturing share in the ’90s was >22%. It started slipping in 99’. Today it’s 16.8%. China’s global market share was 3% in the 90, 8% in 2000 - today it is 28.7%
**More inputs **
-
Andy Grove, Intel's 3rd employee hired in 1968 and CEO from 1987 to 1998, drove Intel's market cap from $4 billion to nearly $197 billion, making it the world's largest computer chip manufacturer. He highlighted the inseparability of design and manufacturing - which leads to the loss of R&D and innovation in a country when manufacturing is offshored. Grove also questioned the absence of tracking offshored jobs.
-
Apple has a similar philosophy in bridging design and manufacturing. Dow Chemical built research facilities outside of the US because it could not separate manufacturing from R&D
-
Manufacturing’s deterrent factor is high capex and lower returns compared to the service sector.
-
“The Commerce Department was a chronic underperformer, led in recent times by political hacks or bureaucrats, from one party or the other, who simply didn’t get it.” (from the book)
-
Manufacturing is needed to reduce the trade deficit. In 2009, the trade deficit reached almost $375 billion - meaning the US spends $375 billion more on foreign economies than it does fueling its economy. (Current trade deficit is $65.5 billion)
-
To balance the economy, export more and import less. In 2009, 60% of manufacturing goods were exported (current amount of 80%). But this is not enough to fulfil domestic consumption and reduce imports, hence the need for more manufacturing.
-
Trade deficit with China - In 2009, the total trade deficit with China was more than $220 billion, service trade surplus of $6 billion. Today, U.S. export to China is $153.8 billion, imports from China is $536.8 billion, and the trade deficit with China is $382.9 billion (almost double the amount of trade deficit with China in 14 years)
-
While knowledge workers are important, must not discount the importance of hands-on technical skills
-
The rate of decline in manufacturing increases unemployment in manufacturing jobs such as engineer, designer, or floor operator. The majority of the workforce is Caucasian, with African Americans constituting about 10 percent and Hispanics about 15 percent
-
“If the private sector rewards “out of the box” thinking, Washington often expects regurgitation as the norm for career advancement. Follow instructions; don’t make waves; keep your head down—that’s the motto among insiders. It’s something that I didn’t like and never got used to.” (from the book)
-
Our nation cannot bleed manufacturing jobs and expect to have a middle class: Bob Baugh, union leader
-
Small and medium-sized businesses create about half of all manufacturing jobs and make up more than 90 percent of U.S. manufacturers.
-
Importance of local manufacturers in helping the country during turmoil - The Globe factory produced protective clothing for firefighters during 9/11. The challenges were seen during COVID-19, not being able to manufacture masks, medical
-
Federal gov’t program: the Manufacturing Extension Partnership (MEP) helps small and medium-sized manufacturers improve their competitiveness
-
The decline of manufacturing impacts surrounding businesses (I’ve seen it drop like dominoes). This is based on the cluster theory by Professor Michael Porter, introduced in the late 1990s, which emphasizes geographic concentrations of related businesses and institutions in specific industries. Clusters offer advantages like knowledge sharing, talent access, efficient supply chains, and competition-driven innovation, benefiting regional development and global competitiveness.
-
Gov’t subsidies: Foreign competitors get hefty government subsidies, including free land, factories, and capital. These subsidies make price competition tough, not just cheap labourers (for example China)
-
Corporate tax: Overseas earnings are taxed when brought back to the U.S. Due to high corporate tax rates, companies rather invest these earnings abroad. A one-time tax incentive for repatriation will encourage more domestic investment and job creation (John Chambers of Cisco, and Tim Guertin of Varian)
-
General observation - The US pioneers innovation but is unable to keep up the fight when competitors come on board because of the lack of support compared to other countries - i.e. luxury cards, automobiles, automation, silicon industry, solar industry etc
-
95% of the world’s consumers and 70% of the world’s purchasing power are outside the United States (in 2009 and about the same now)
-
Only 1 percent of American businesses export.
-
Out of that, 58% of the companies that do export only export to Canada or Mexico. They’re still reluctant to venture out to Latin America, Asia, or even Europe.
-
Exports make up only 11% of the U.S. gross domestic product (GDP) - Note, still the same from 2009 to the present. Germany, China, India, Brazil, Russia, UK, Japan - exports more
-
Trade shows are useful and costly. A suggestion is for the U.S. government to help cover travel and participation expenses for first-time attendees. These businesses could repay the government if they secure sales at the show, similar to how the Department of Agriculture supports food companies.
-
Several countries are subsidised in tradeshows and have pavilions that are chic and modern such as the British, Germany, Turkey, Italy, and Egypt. US’s booths don’t stand out.
-
The simplicity of getting paperwork sorted: In 1972, when Andy Grove went to Malaysia to establish Intel’s first foreign operation, the chief minister of Malaysia introduced him to Chet Singh, who headed the state’s Penang Development Corporation. “Chet Singh is your one-stop agent,” the Malaysian chief minister told Mr. Grove. Whenever Intel had an issue with getting a particular license, permit, road paved, or available tax credit, Chet would take care of it. He stayed in his job for more than two decades until the early 1990s, facilitating Intel’s ability to expand its Malaysian presence. Today, Malaysia is home to Intel’s largest manufacturing facility outside the United States (Note: Malaysia doesn’t treat its people the same way)
-
Over time I think manufacturing moved away because of some mixture of regulations (not all bad), high-cost labor (unions), higher cost of capital (complex) and a focus on other things (comparative advantage, or misdirected cultural signals?). Bill Gates, 2011
-
US global manufacturing share in the 80’s and 90’s was 22% - 24%. It started slipping in 99’. Today it’s 16.8%. China’s global market share was 3% in the 90, 8% in 2000 - today it is 28.7%
-
Global Manufacturing Output China – 28.7% United States – 16.8% Japan – 7.5% Germany – 5.3% India – 3.1% South Korea – 3% Italy – 2.1% France – 1.9% United Kingdom – 1.8% Indonesia – 1.6%
-
 @ 147ac18e:ef1ca1ba
2025-04-13 01:57:13
@ 147ac18e:ef1ca1ba
2025-04-13 01:57:13In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:
1. Tariffs Are a Tool, Not the Goal
Jack’s central thesis is that tariffs are not meant to be a permanent fixture—they’re a pressure tactic. The goal isn’t protectionism for its own sake, but rather to reset trade relationships that have historically disadvantaged the U.S. For example, Taiwan responded to the tariffs not with retaliation but by proactively offering to reduce barriers and increase imports from the U.S. That, Jack says, is the intended outcome: cooperation on better terms.
2. Forced Deleveraging to Prevent Collapse
One of the boldest claims Jack makes is that the Trump administration used the tariffs as a catalyst to trigger a “controlled burn” of an over-leveraged stock market. According to him, large institutions were deeply leveraged in equities, and had the bubble popped organically later in the year, it would have required massive bailouts. Instead, the shock caused by tariffs triggered early deleveraging, avoiding systemic failure.
“I’m telling you, a bailout scenario was just avoided... This was intentional.” – Jack Spirko
3. Global Re-shoring and Domestic Manufacturing
Tariffs are incentivizing companies to move production back to the U.S., especially in key areas like semiconductors, energy, and industrial goods. This shift is being further accelerated by global geopolitical instability, creating a “once-in-a-generation” opportunity to rebuild small-town America and domestic supply chains.
4. Not Inflationary—Strategically Deflationary
Jack challenges conventional economic wisdom by arguing that tariffs themselves do not cause inflation, because inflation is a function of monetary expansion—not rising prices alone. In fact, he believes this economic shift may lead to deflation in some sectors, particularly as companies liquidate inventory, lower prices to remain competitive, and reduce reliance on foreign supply chains.
“Rising prices alone are not inflation. Inflation is expansion of the money supply.” – Jack Spirko
5. Energy Costs Will Fall
A drop in global oil prices, partially due to reduced transport needs as manufacturing reshoring increases, plays into the strategy. Jack notes that oil at $60 per barrel weakens adversaries like Russia (whose economy depends heavily on high oil prices) while keeping U.S. production viable. Lower energy costs also benefit domestic manufacturers.
6. The Digital Dollar & Global Dollarization
Alongside this industrial shift, the U.S. is poised to roll out a “digital dollar” infrastructure, giving global access to stablecoins backed by U.S. banks. Jack frames this as an effort to further entrench the dollar as the world’s dominant currency—ensuring continued global demand and export leverage without the need for perpetual military enforcement.
7. A Window of Opportunity for Americans
For individuals, Jack sees this economic transformation as a rare chance to accumulate long-term assets—stocks, Bitcoin, and real estate—while prices are suppressed. He warns that those who panic and sell are operating with a “poverty mindset,” whereas those who stay the course will benefit from what he describes as “the greatest fire sale of productive assets in a generation.”
Conclusion: Not a Collapse, But a Reset
Rather than viewing tariffs as a harbinger of economic doom, Jack presents them as part of a forced evolution—an uncomfortable but necessary reboot of the U.S. economic operating system. Whether or not it works as intended, he argues, this is not a haphazard policy. It’s a calculated reshaping of global and domestic economic dynamics, and one with enormous implications for trade, energy, inflation, and the average American investor.
-
 @ c11cf5f8:4928464d
2025-04-13 09:26:24
@ c11cf5f8:4928464d
2025-04-13 09:26:24A collection of all the tutorials and guidelines that will help you get the most out of this territory
The ~AGORA marketplace it’s a thriving space where creators, solopreneurs, and businesses can promote and monetize their expertise. A place where stackers can discover unique goods, tools, and tricks to buy products and get services in exchange for Bitcoin.
This post will aim to be the reference to collect all the posts, guide, and tutorials that can help you make the most out of it. Post yours if we forgot something!
originally posted at https://stacker.news/items/942038
-
 @ 9727846a:00a18d90
2025-04-13 09:16:41
@ 9727846a:00a18d90
2025-04-13 09:16:41李承鹏:什么加税导致社会巨变,揭竿而起……都不说三千年饿殍遍野,易子而食,只要给口吃的就感谢皇恩浩荡。就说本朝,借口苏修卡我们脖子,几亿人啃了三年树皮,民兵端着枪守在村口,偷摸逃出去的都算勇士。
也不说98年总理大手一挥,一句“改革”,六千万工人下岗,基本盘稳得很。就像电影《钢的琴》里那群东北下岗工人,有的沦落街头,有的拉起乐队在婚礼火葬场做红白喜事,有的靠倒卖废弃钢材被抓,有的当小偷撬门溜锁,还有卖猪肉的,有去当小姐的……但人们按着中央的话语,说这叫“解放思想”。
“工人要替国家想,我不下岗谁下岗”,这是1999年春晚黄宏的小品,你现在觉得反人性,那时台下一片掌声,民间也很亢奋,忽然觉得自己有了力量。人们很容易站在国家立场把自己当炮灰,人民爱党爱国,所以操心什么加税,川普还能比斯大林同志赫鲁晓夫同志更狠吗,生活还能比毛主席时代更糟吗。不就是农产品啊牛肉啊芯片贵些,股票跌些,本来就生存艰难的工厂关的多些,大街上发呆眼神迷茫的人多些,跳楼的年轻人密集些,河里总能捞出不明来历的浮尸……但十五亿人民,会迅速稀释掉这些人和事。比例极小,信心极大,我们祖祖辈辈在从人到猪的生活转换适应力上,一直为世间翘楚。
民心所向,正好武统。
这正是想要的。没有一个帝王会关心你的生活质量,他只关心权力和帝国版图是否稳当。
而这莫名其妙又会和人民的想法高度契合,几千年来如此。所以聊一会儿就会散的,一定散的,只是会在明年春晚以另一种高度正能量的形式展现。
您保重。 25年4月9日
-
 @ 502ab02a:a2860397
2025-04-13 01:38:46
@ 502ab02a:a2860397
2025-04-13 01:38:46อะไรคือ Heliotherapy
ถ้าลองหลับตา แล้วนึกถึงคนยุโรปยุคต้นศตวรรษที่ 20 ที่กำลังนอนอาบแดดบนภูเขา ห่มผ้าขนหนูบาง ๆ เปิดผิวให้พระอาทิตย์ลูบไล้ เฮียกำลังนึกถึงภาพของการรักษาโรคอย่างหนึ่งที่เรียกว่า Heliotherapy หรือ การบำบัดด้วยแสงอาทิตย์ ซึ่งเคยเป็นหนึ่งในศาสตร์ทางการแพทย์ที่ถูกยอมรับอย่างเป็นทางการ โดยเฉพาะในยุคที่ยังไม่มี “ยาปฏิชีวนะ”
Heliotherapy ไม่ได้เกิดจากความงมงาย แต่จากหลักฐานจริงจัง โดยเฉพาะผลงานของ ดร.ออกุสต์ โรลเลอร์ (Dr. Auguste Rollier) แพทย์ชาวสวิตเซอร์แลนด์ ผู้บุกเบิกการใช้แสงแดดรักษาผู้ป่วยวัณโรคกระดูกอย่างได้ผลในช่วงต้นศตวรรษที่ 20 เขาก่อตั้ง “โรงพยาบาลแห่งแสงอาทิตย์” บนเทือกเขาแอลป์ โดยให้ผู้ป่วยขึ้นไปอยู่ในที่สูงกว่า 1,500 เมตรเหนือระดับน้ำทะเล แล้วเปิดรับแสงแดดอย่างเป็นระบบ
ที่น่าสนใจคือ โรลเลอร์มีข้อกำหนดชัดเจนว่า ห้ามผู้ป่วยใส่แว่นกันแดดเด็ดขาด เพราะ “ดวงตา” คือหนึ่งในอวัยวะสำคัญที่ต้องรับรังสี UV เพื่อนำข้อมูลไปกระตุ้นต่อมไพเนียลในสมอง ส่งผลต่อวงจรชีวภาพ ฮอร์โมน และระบบภูมิคุ้มกันทั้งหมด ถ้าเราอาบแดดแต่ใส่แว่นดำ เท่ากับปิดประตูสำคัญของระบบบำบัดจากธรรมชาติ
แต่ถ้าย้อนกลับไปก่อนหน้านั้นอีกนิด เราจะเจอ “ต้นฉบับของแนวคิดแสงบำบัด” อยู่ที่ ดร.นีลส์ ฟินเซน (Dr. Niels Ryberg Finsen) นายแพทย์ชาวเดนมาร์ก ผู้ได้รับ รางวัลโนเบลสาขาสรีรวิทยาหรือการแพทย์ ในปี ค.ศ. 1903 จากการใช้แสงสว่างในการรักษาโรค Lupus vulgaris ซึ่งเป็นวัณโรคชนิดเรื้อรังที่แสดงออกบนผิวหนัง โดยเขาออกแบบอุปกรณ์ “Finsen Lamp” เพื่อฉายแสงตรงเข้าไปรักษาเซลล์ผิวโดยเฉพาะ และถือเป็นบิดาแห่ง Phototherapy ยุคใหม่
ทำไมแค่ “แดด” ถึงมีฤทธิ์บำบัด? แสงแดดคือคลังยาแห่งธรรมชาติอย่างแท้จริง เพราะประกอบด้วยรังสี UV หลายชนิด โดยเฉพาะ UVB ที่กระตุ้นให้ผิวหนังสร้าง วิตามินดี (Vitamin D3) ซึ่งมีบทบาทเสมือนฮอร์โมนที่ควบคุมระบบภูมิคุ้มกัน การอักเสบ และการดูดซึมแร่ธาตุต่าง ๆ เช่น แคลเซียมและแมกนีเซียม
แต่แดดไม่ได้มีแค่ UV แสงแดดในช่วงเช้ายังเต็มไปด้วยคลื่นแสงสีแดงและอินฟราเรดใกล้ (Near Infrared Light) ซึ่งมีบทบาทสำคัญในการซ่อมแซมไมโทคอนเดรีย—the powerhouse of the cell และช่วยกระตุ้นการหลั่งไนตริกออกไซด์ในหลอดเลือด ทำให้ระบบไหลเวียนโลหิตดีขึ้น ความดันสมดุลขึ้น และฟื้นฟูอวัยวะลึก ๆ ได้อย่างเงียบ ๆ
พูดง่าย ๆ คือ แดดเช้า = เติมแบตชีวภาพ ยิ่งแสงอาทิตย์กระทบผิวเราผ่าน “ดวงตาเปล่า” (โดยไม่ใส่แว่นกันแดดในช่วงเช้า) ก็ยิ่งช่วย “รีเซ็ตนาฬิกาชีวภาพ” ให้เราตื่นตรงเวลา หลับลึกขึ้น และเพิ่มการหลั่งเมลาโทนินในตอนค่ำโดยอัตโนมัติ
ในโลกที่คนวิ่งหาฮอร์โมนจากขวด การนอนตากแดด 10–20 นาทีต่อวัน กลับกลายเป็นเวทมนตร์ราคาถูกที่เรามองข้าม
และงานวิจัยจาก มหาวิทยาลัยเอดินบะระ (University of Edinburgh) ประเทศสกอตแลนด์ ก็ได้ยืนยันว่า แสงแดดมีส่วนช่วยลดความดันโลหิตได้จริง โดยไม่จำเป็นต้องพึ่งวิตามินดีเลยด้วยซ้ำ เพราะเมื่อแสงยูวีจากดวงอาทิตย์สัมผัสผิวหนัง จะกระตุ้นให้เกิดการปลดปล่อย “ไนตริกออกไซด์” (Nitric Oxide) จากชั้นผิวเข้าสู่ระบบหมุนเวียนโลหิต ซึ่งมีผลทำให้หลอดเลือดขยายตัว ความดันโลหิตลดลง และลดความเสี่ยงโรคหัวใจอย่างเห็นผล
นี่แปลว่าแสงแดดไม่เพียงแค่สว่าง แต่มันกำลัง “พูดภาษาเคมี” กับร่างกายเราอย่างเงียบ ๆ ทุกเช้า
ในยุคที่การแพทย์พัฒนาไปสุดทาง เทคโนโลยีผ่าตัดทำได้ถึงระดับนาโนเมตร กลับมีหมอบางคนหันกลับมาบอกว่า “คุณแค่ต้องออกไปรับแดดเช้า” เพื่อให้ร่างกายฟื้นตัวดีกว่าการพึ่งยาเพียงอย่างเดียว ดีไหมหล่ะ แต่ขอโทษทีคุณหมอที่บอกให้ไปตากแดดช่างมีน้อยเหลือเกินเมื่อดูในภาพรวม
Heliotherapy จึงไม่ใช่แค่การอาบแดด แต่คือการกลับไปเชื่อมโยงกับวงจรธรรมชาติ เหมือนคนโบราณที่เคารพดวงอาทิตย์ เพราะเขารู้ว่าพระอาทิตย์ไม่เคยหลอกเรา
ขณะที่ fiat ผลิตเม็ดสีสังเคราะห์และวิตามินปลอม ๆ พระอาทิตย์กลับให้ของจริง โดยไม่เรียกเก็บภาษีด้วย
ใครมีเวลา วันนี้เฮียขอชวนไปยืนรับแสงเช้า 10 นาที ไม่ต้องทำอะไร แค่ยืนเฉย ๆ ให้แสงซึมเข้าตา ซึมลงผิว แล้วฟังเสียงเงียบของร่างกายที่กำลังซ่อมแซมตัวเอง เงียบจนเราอาจได้ยินเสียงหัวใจบอกว่า "ขอบคุณนะ ที่ออกมารับแดดกับฉัน" #SundaySpecialเราจะไปเป็นหมูแดดเดียว #pirateketo #ตำรับเอ๋
-
 @ 0ef78f78:1cc6bede
2025-04-12 23:21:18
@ 0ef78f78:1cc6bede
2025-04-12 23:21:18In a world of relentless change and mounting political chaos, developing a carefully reasoned worldview feels both urgent and indispensable. Modern existence throws us into a tempest of technological leaps, ethical dilemmas, and existential questions, pressing us to find clarity amid the chaos. Philosophy rises to meet this challenge—not as a leisurely diversion, but as a disciplined effort to probe truth and cultivate wisdom.
This blog sets out to invite readers to wrestle with life’s big questions and their relevance now. My aim is to unpack foundational concepts with precision, tying them to the realities of our time. This space is for serious reflection—rigorous yet accessible—where we can scrutinize the beliefs that steer our lives.
Philosophy as Theory Making About Theories I’ve always been struck by an idea from Wilfred Sellars: philosophy is about crafting theories about our theories. It’s a process of stepping back to examine the very frameworks we use to make sense of the world. As Sellars put it, “The aim of philosophy, abstractly formulated, is to understand how things in the broadest possible sense of the term hang together in the broadest possible sense of the term.” To me, this captures philosophy’s essence—it’s not just about asking what we believe, but why we believe it, and how those beliefs hold together. We all operate with answers to life’s deepest questions, whether we’ve thought them through or not, and they form the silent foundation of our worldview.
Here are some of the questions philosophy urges us to confront:
What gives human life its purpose? Are our choices genuinely free, or shaped by unseen forces? How do we discern right from wrong? Is certain knowledge possible, or is truth forever out of reach? What lies beyond death? Is there an ultimate reality or higher power? What makes a life meaningful? These aren’t idle musings—they quietly shape how we act, what we value, and how we see the world. As Socrates cautioned, an unexamined life risks being lived without purpose or understanding. Philosophy, as theory making about theories, pushes us to take charge of our beliefs, testing and refining them through reason.
Why This Matters Now Today, the need for this kind of reflection is sharper than ever. We’re awash in information and clashing viewpoints, each vying for our allegiance. Meanwhile, breakthroughs like artificial intelligence, biotechnology, and global connectivity force us to rethink what it means to be human. How do we stay human when machines rival our abilities? How do we judge right and wrong in a world of endless options?
Philosophy equips us to tackle these questions with clarity. It teaches us to pause, question what we assume, and construct thoughtful answers to the problems we face. By engaging in this theory-making process, we gain insight into both the world and ourselves.
Come Along for the Ride This blog is an open call to dive into these ideas together. In the posts to come, I’ll explore philosophical concepts and their real-world stakes, hoping to stir curiosity and conversation. I’m not here to hand out final answers, but to deepen our grasp of the questions—and maybe inspire us to live with more intention.
Philosophy is a journey of discovery, blending intellectual rigor with an embrace of complexity. As we go forward, I’d love for you to join me in this exploration—one that offers not just understanding, but a more deliberate way of being.
-
 @ 8671a6e5:f88194d1
2025-04-12 23:04:34
@ 8671a6e5:f88194d1
2025-04-12 23:04:34
intro
Full disclosure : I bought multiple bitcoin art items to support artists
Bitcoin has absorbed old tropes from finance, tech, and economics, fundamentally reshaping how we think about money. But Bitcoin art? It should be a companion on the journey to a Bitcoin standard. Yet it doesn’t even seem to be trying. Every artistic movement worth its salt needs something to push against—to rebel, to spark thought, to provoke, or at the very least, to represent a technical or methodological leap forward in its field.
Pointillism comes to mind as an example in painting.
In this piece, I take a brief stroll into the subjective realm of art, specifically exploring art in the Bitcoin space—if such a thing truly exists. Some people might not like it, but as someone who has created modern art myself, I can confidently say that artists will emerge stronger from this transitional phase of Bitcoin art, whatever this era may be called later.
The art corner You know the drill. You visit any Bitcoin conference and there’s the obligatory “art corner” or gallery. Funny, wasn’t it just a few years back that a single decent artwork was a rarity needing a proper place for being shown tot he public? Now, every conference (small or big) needs this curated space, crammed with artists all vying for a sliver of attention.
And what do you usually find? A collection of the utterly predictable, the profoundly uninspired, the tiresomely repetitive, and anything but artistically groundbreaking amidst some exceptional pieces that will be snatched up almost immediately.
The themes are often so worn out, they’re practically a self-parody version of bitcoin art:
Animals holding signs (with of course… bitcoin logos)

Whales, dolphins, and the aquatic crew: The go-to, utterly drained metaphor for Bitcoin wealth, rendered in every conceivable medium with sea creatures.
Majestic vistas with bitcoin slogans: Think inspirational landscapes defaced with inscriptions or cryptic (not really) messages.
Women cradling blocks: Because apparently, nothing screams "Bitcoin" like a woman clutching a perfectly geometric cube. Bonus points if there are more painted women on a canvas, than actual women at the event.
Coins, coins, and more coins: Gold, silver, pixelated, abstract – just in case anyone forgot Bitcoin isn't a physical trinket.
Collages of Bitcoin celebs and memes: Why bother with originality when you can just mash up some social posts?
Reheated classics with an orange filter: Slap some orange highlights and a Bitcoin logo on a famous painting, and voilà! “Bitcoin art.” Bitcoin Pop-art, Bitcoin punk, Bitcoin collages…
It’s like the whole Bitcoin art scene is endlessly regurgitating the same tired ideas, and pouring a lot of time and effort in being just a fancy washing machine of orange t-shirts.
Most of it—not all, mind you, as there are people with exceptional thought and even more exceptional work—is no more than Bitcoin-themed art. By "theme," I mean the color orange or a “B,” much like you’d see M&M’s-themed coffee mugs, M&M’s t-shirts, or M&M’s-themed playing cards.
Now, let’s be clear: this isn’t about slagging off the artists themselves. I know how hard it is to thrive in this space, and I also learned about the time and effort put in to any work (the perception of the artwork has nothing to do with this at all!)
The dedication and passion within the bitcoin art scene are undeniable. Making art in a niche like Bitcoin is a tough gig (and often a thankless one, given the whole value-4-value thing seems perpetually broken). They deserve respect for putting themselves out there, doing the work and trying to make their passion work.
Many genuinely believe in what they’re creating, even if not everyone is convinced or will like a work of art. However, a lot of them are chasing a mirage, much like those hoping for an oasis of Bitcoin jobs in the desert. Many artists dream of turning their art into a business or a career move, and some even try to make a full-time living from it. That’s admirable, but I’m convinced it’s often a ruse, where your money, time, and effort dress up someone else’s business ideas and sense of branding. In my opinion, the real art movement in Bitcoin has yet to take off. It will need people with great ideas, motivation, know-how, and effort, for sure!
So I repeat the issue isn’t the individuals, the artists; it’s the collective creative stagnation that comes from clamoring to the general interest of this perceived “bitcoiner” as an audience.
Target < B > Audience
Only, this audience is usually not the target audience for the artworks itself. Art needs to have room to inspire, be free and relay an idea (even if that idea challenges another idea). That can’t be done to a target audience that just wants to sell their stuff to each other at a conference (see my piece on Bitcoin conferences for that) neither can it be a target audience that even is too cheap to buy a ticket and freeloads themselves into an conference.
Bitcoin is supposed to be revolutionary, yet so much of its art (or perceived art) feels like a tacked-on commercial necessity or, worse, a desperate attempt at self-validation. Most of it is just a perpetual branding motion from a non-existing marketing team.
The target audience is usually even worse. Not knowing what they’re looking at, out of their element and knowing they should and could support the artists and their work. A lot is depending on why this audience is wandering through a conference gallery in the first place.
If most people at a conference are the usuals, the sellers, the company people, then they're used to seeing these artists and their art pieces. No one is amazed anymore. Which is in fact a sad thing to happen.
I can't imagine how incredibly hard it must be to try to sell something as bitcoin art to this kind of audience, while trying to believe that a B-logo on an excerpt of the whitepaper is worth the effort. (I don’t think it is, but tastes differ, some people prefer a Whopper over a nice steak dinner)
Signaling “membership” in the bitcoin community is important to some, and they do that through hats, t-shirts, pins and hoodies, not buying a bitcoin artwork.
Art is inherently subjective, fluid, and deeply personal.
I love Kusama’s polka dots, someone else might be into Herman Brood’s chaotic paintings, and someone else might get all nostalgic over an Anton Pieck candy store drawings.
The contradiction Bitcoin: The hardest money ever created. Objectively verifiable. Math-based. Impersonal. Code.
The clash is between feeling and finance, between cold emotionless, hard numbers and warm, beating hearts.

That’s why it's always a bit surreal to see people that sit in a conference room, go from a deep dive into Lightning Network scalability or Bitcoin’s code ossification; and see them wandering through an “art gallery” filled with pieces that are the polar opposite of anything remotely code-related. The cold hearts walk amongst the works of warmth. The trustless math calculates their steps and starts to look at something that’s exposed to a public of that’s not there for the art, but the mimicking of such a think in their setting makes them have their own élan, grandeur. It feels forced. And to me, it feels even wrong to see people walk out of a conference room, right into the art gallery… where they’re usually stroll around out of boredom or just as a form of a break. It’s almost disrespectful, and I feel art needs its own place, the right setting. And that setting is definitely not a bitcoin conference.
You see tech and finance folks just standing there, at these art corners looking at the art pieces like cows watching a drone show.
You feel this subtle pressure to act like it’s profound, even though it rarely is. But you’re there, so you play along with the charade as well. It’s miserable to see. Certainly when some people are more interested in buying the piece of mind of the artist, the way of life or a glimmer of independence they’re missing themselves.
I believe bitcoin art is rarely bought for anything else than capturing the reality and authenticity of the artists. Artists know that. And they sell that authenticity (out) to eat, drink, sleep and pay their rent. Authenticity can be double spent, unlike the hard money asset where it’s supposedly all about. Artists have very big blocks.
It’s a bit like that hyped-up restaurant that turns out to be serving dressed-up bar food, but you’re with friends, so you pretend that $35 hors d'oeuvre doesn’t taste suspiciously like steamed shoe laces. Theaters are sometimes food bars or galleries. Proof of fart Then there’s the awkward issue of selling this stuff. How do you, as an artist, “comment on” or “complete” an asset in an artistic way, while that asset appreciates by an average of 40 to 70% a year?
Buying traditional art as an investment is one thing, driven by aesthetics or emotional connection. But buying Bitcoin art with Bitcoin? That’s a financial decision triggering regret (almost for sure). Think about it: 0.1 BTC spent on a canvas today, isn’t just a fixed one-time cost; it’s a future opportunity cost.
That same Bitcoin could be worth significantly more in a few years. The artwork, not so much, not even a Picasso painting or a Hokusai manages that kind of annual return. So, unless you’re head-over-heels for the piece (or the artist), buying Bitcoin art with Bitcoin is almost certainly a bad trade financially – though, so is buying that fancy coffee machine you'll use twice or getting a diamond ring for you loved one.
Of course, this isn't a definitive argument against it (it's subjective, remember). But it's a factor, just one element. People who buy art to lock it away into a vault aren't the same folks milling around a Bitcoin conference, presumably. But still.
Purpose
Historically, in the West at least, art served many purposes: glorifying churches, telling stories to the illiterate, and expressing the full spectrum of human emotion (pain, regret, doubt, madness, etc.). There was always a demand, whether from religious institutions, the populace, or a desire for education and status. The demand rarely came from onlookers or passive walk-ins. You can only walk in after the demand has been met. The real commanding force in Bitcoin art isn’t the financial types in suits or the grifter with a few stickers who got into the conference for free and smells like weed. The demand comes from people who love to cultivate the branding to propel themselves forward.
In Bitcoin? None of that. There’s little genuine demand, I’d argue. The demand seems mostly driven by the artists themselves wanting to participate. Which, in itself, makes the act of creation worthwhile for them. But the audience demand feels… manufactured. Nobody wakes up thinking: “.. I sure hope there’s a Bitcoin art gallery at this conference...”
This low-to-nonexistent demand, however, presents a massive opportunity to actually impress. Low expectations mean impact is easier to achieve in a lasting way. But that impact evaporates fast if all the visitors get is the same old themes with some orange varnish or a monkey holding a sign.
"Proof of work" isn’t enough here; we already have that in the bitcoin network. Bitcoin art need "proof of thought". Sure, Bitcoin artists put in the hours. Their work is literally proof of effort. But effort alone doesn’t equal value – originality does. Copying Warhol, Mondrian, or Van Gogh and slapping a Bitcoin twist on it isn’t the high level of creativity that can pull art lovers in (and even make them bitcoiners); on the contrary it’s opportunism. And in a space that seems to thrive on recycling successful (or at least visible or temporary cool) ideas, genuine artistic innovation is a rare beast.
Bitcoin art could be so much more. And yes that’s subjective, but at the same time, … walk around at any art gallery and be honest with yourself as a person and buy what you really like, support the artists and the scene, and at the same time realize you’re playing dress up.
There should be so much more, as a separate art movement. It could delve into the philosophy of decentralization, the tension between digital scarcity and creativity, the profound societal shifts Bitcoin is triggering. Instead, we’re mostly drowning in kitsch and thinly veiled cash grabs. The Bitcoin art world doesn’t need more bodies; it needs better minds. We don’t need bigger blocks, we don’t need blocks at all!
The uncomfortable truth is that many Bitcoin artists are here chasing opportunities, just like the rest of us. But spotting an opportunity doesn’t magically transform you into an artist.
I could “find the opportunity” to be a star in the hypothetical Bitcoin basketball league, being one of the first to join. But compared to the global pool of professional basketball talent, I’d likely be laughably bad. I’m not even tall enough to reach most pro players’ armpits, let alone dunk. Yet, in òur tiny Bitcoin league WBBF (World Bitcoin Basketball Federation), I’d be a legend, an OG, demanding respect for my early participation and best-dunk-champion. Just like some Bitcoin artists seem to expect accolades for a weak, orange-tinted imitation of 1960s pop art.

I wouldn’t cut it in any real basketball club, probably not even the lowest amateur league, considering my limited knowledge of the rules. Do you have to run back to the center? Can you tackle other players? Is snatching the ball mid-dribble legal? No clue.
But I could hang around the basketball scene a bit, soak up the jargon, maybe buy a sports drink for a better player to glean some knowledge, and then clumsily mimic their moves while still being terrible at dribbling. I’de buy the right shoes as well. To fit in. Just like bitcoiners buy the right t-shirts.
The same principle applies to some Bitcoin musicians and other creatives. Being the only one doing something – be it Bitcoin-themed sculptures, paintings, sci-fi, or whale graffiti murals – doesn’t automatically make you a leading figure. It just makes you… the only one. Being the sole sci-fi filmmaker in Bangladesh makes you the top of your national field, sure, but it doesn’t make you the next Kubrick. Likewise, airbrushing an orange “B” on a canvas doesn’t turn you into the next Georgia O’Keeffe.
The Bitcoin world thrives on competition and proof of work. Perhaps it’s high time Bitcoin art did the same. We need a battle of ideas, experiments, and genuine insights, not just more orange paint, paragraphs of the white paper and some copper wires.
The genuinely sad part is the sheer effort many of the artists pour into their work! But there’s a limit to how much you can make people want to buy an art piece simply because it has a Bitcoin theme. Go beyond that.
Get real
Real Bitcoin art, in whatever form it takes, will command a high valuation because it will be scarce, original, and have Bitcoin not just as a subject, but woven into its very fabric. That form (and there will be many), in my opinion, is still waiting to be discovered. And I’m fairly certain it won’t be found in a conference gallery, where bored artists sit next to their work, politely nodding at every bloke who wants to sound knowledgeable about art for five minutes or tries to make himself look like a big shot. Because let’s face it, I’ve yet to meet a Bitcoiner with a genuine understanding of art history or a truly discerning eye.
Some starting points, perhaps (just my two cents) :
Art that embodies decentralization itself, inviting audience participation and co-creation, mirroring Bitcoin’s ethos but yet to be fully realized in the art world. Including consensus.
Art that incorporates distributed consensus or a rotating "proof of work" concept in its creation or presentation.
Purely mathematical art forms that resonate with Bitcoin’s underlying principles.
The possibilities are vast. Or maybe, just maybe, Bitcoin itself is our art, and we don’t need all this orange-tinged stuff cluttering up galleries nobody asked for.
And why not paint blocks holding women, instead of women holding blocks? Or why not have inflation-resistant art? Or math-based art that isn’t even possible to show on a canvas?
On that subject, the author of this piece enjoys making art as well and conducted a small experiment. I've performed a "life performance" approximately three times now, which I consider pure Bitcoin art. This was an action, not a physical object. It demonstrated work I personally delivered as “a miner” (function in this art piece), and during the process, people could verify it and even received my block subsidy (effort). So far, only one person has recognized this art form; the rest were unaware. Since it's an action, not an object, it's intangible unless you witnessed it. This is my way of saying, "you are the artist." According to the bitcoin ethos.
Interestingly enough, other people, even those involved in Bitcoin art themselves (!), didn't see it. This amused me because, much like the early weeks of Bitcoin's network growth, many initially failed to recognize its potential. Perhaps this parallel should be enough for us all to understand the true nature of Bitcoin art.
The Artistic Dare:
Here’s a challenge, not to your wallet, but to your creative soul: conceive and execute a piece of art that embodies the spirit and principles of Bitcoin in a way that is genuinely original, thought-provoking, and resonates beyond the immediate Bitcoin echo chamber. Forget the predictable iconography. Dig deeper.
If you can create something truly compelling, something that makes us see Bitcoin – or art – in a new light, then you’ve truly created Bitcoin art. And then comes the extra real challenge: finding someone who can and would pay for it, and at the same time “gets it”.
The main challenge is creating real art—a path, a genre—where a standalone Bitcoin art gallery can thrive outside the conferences and the small echo chamber of the “what do you sell?” crowd.
Don’t sell your dreams and authenticity to bored traders or bitcoin consultants. It’s like serving the finest wine to a bunch of alcoholics in a bar at 4 am.
Playing it safe with themes and artworks that can’t cross into the real art scene (even the underground art scene, let alone the corporate art) will not be as long-lived as bitcoin itself. Trying to spark interest from art lovers in general, will be the killer app, and will make bitcoin art into a movement. And that’s what we all need to make it art,… the pieces can’t exist without the movement. I hope someone will get the right spark, idea and fire going.
But until then we’ll be stuck with people painting a chimpanzee holding a glittering Bitcoin logo and chatting with any dude that wants to feel like someone at a conference.
Good luck.
AVB
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48
@ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48Meine erste "Begegnung" mit Ulrike hatte ich am 21. März 2022 - dank Amazon konnte ich das Ereignis noch exakt nachvollziehen. Es war eines meiner ersten (Lockdown) kritischen Bücher, die ich in dieser Zeit in die Hände bekam - noch nach Thomas Röper (das war mein Einstieg) aber vor Daniele Ganser. Insofern war es mir möglich, das, was dann folgte für die Autorin, live und in Farbe mit zu verfolgen:
"Wer sich in die Öffentlichkeit traut, kann sich dort ganz schnell eine blutige Nase holen. Dieselben Medien, die eine Person heute glorifizieren, stellen sie morgen an den Pranger. Sie verteilen und entziehen Reputation, fördern und zerstören Karrieren. Das Medium selbst bleibt jedoch immer auf der Siegerseite. Die Gesetze von Marktorientierung und zynisch-ideologisierter Machtausübung gelten für Rundfunk und Fernsehen ebenso wie für die Printmedien - von RTL bis ARD und ZDF, von der BILD über die taz bis zur ZEIT.
»Das Phänomen Guérot« legt genau diesen Vorgang detailliert offen: Der MENSCH Ulrike Guérot ist in der Realität nicht die dämonische Figur, als die sie hingestellt worden ist. Aber an ihr kristallisiert sich genau dieser menschenverachtende Prozess heraus, der bis heute andauert."
Im Herbst 2022 habe ich durch den ersten Vortrag von Daniele Ganser in Falkensee nicht nur Zugang zu einer für mich neuen und anderen Welt bekommen, ab da hat sich eigentlich auch für mich mein Leben komplett auf den Kopf gestellt. Die Weichen wurden zwar schon vorher gestellt, aber nun war es endgültig und es gab kein zurück mehr. Die Planung für das erste Symposium Falkensee war in meinem Kopf geboren und die MenschheitsFamilie entstand als Ort, der virtuell das vereinen sollte, was Daniele an Spiritualität, Menschlichkeit und Friedenswillen in mir freigesetzt hat. Es war sozusagen eine Energie, die nun stetig floß und einen Trichter gefunden hat, in dem sie wirksam werden und sich entfalten konnte. Insofern haben wir auch etwas gemeinsam - Ulrike und ich. Wir sind zu der Zeit auf einen Zug aufgesprungen, der unser Leben veränderte - der uns zwang, alte Wege zu verlassen und neue Wege zu beschreiten. Sowohl beruflich, als auch privat. Und auch das canceln und entfernt werden ist eine Erfahrung, die wir beide teilen. Vielleicht war es deswegen mein erster Gedanke im Herbst 2022, Ulrike Guérot zu meinem 1. Symposium nach Falkensee einzuladen. Das es dann erst beim 2. Anlauf wirklich geklappt hat, hatte auch mit den Höhen und Tiefen des Lebens in dieser Zeit zu tun gehabt.
Nun ist sie zum 2. Mal dabei - denn wer könnte das Thema "Europa" bei einem so wichtigen und hochaktuellen Thema besser vertreten und beleuchten als Ulrike Guérot? Es geht um Geschichte, es geht um Nationalitäten, es geht um Gemeinsamkeiten und um das, was uns hier im Herzen zusammenhält, was unsere Ziele und unsere Befindlichkeiten sind, es geht um Verantwortung und es geht vor allen Dingen um Frieden! Denn dafür steht Europa - für einen Kontinent, der es geschafft hat, trotz aller Gegensätze und Konflikte, die in Jahrhunderten kriegerisch aufgetragen wurden, eine neuen und besonderen Frieden zu finden und zu installieren:
"Völkerrechtlich legt der Westfälische Frieden den oder zumindest einen Grundstein für ein modernes Prinzip: Die Gleichberechtigung souveräner Staaten, unabhängig von ihrer Macht und Größe. Noch heute spricht die Politikwissenschaft, insbesondere die realistische Schule (Henry Kissinger), deshalb vom „Westphalian System“. Durch die Garantien der großen europäischen Mächte erweist sich dieser Frieden als stabilisierendes Element für die weitere Entwicklung in Europa. Noch bis zum Ende des 18. Jahrhunderts wird er immer wieder als Referenz für nachfolgende Friedensschlüsse herangezogen."
Es ging damals um viel und es geht heute um das Überleben auf einem Kontinent, der es eigentlich besser wissen sollte. Wir dürfen gespannt sein, was wir in diesem Vortrag von Ulrike auf dem Symposium Falkensee am 27. April 2025 für Lösungen finden, um wieder zu einer Ordnung und zu einem System der friedlichen Koexistenz zurückfinden zu können, ohne schwarz und weiß und mit all den Facetten, die das Leben uns so bietet:
"Es ging nicht mehr um das Ausfechten religiöser Wahrheiten, sondern um geregelte Verfahren, die es möglich machten, mit konkurrierenden religiösen Wahrheiten, die nach wie vor nebeneinander und unversöhnlich bestanden, auf friedliche Weise umzugehen. Deutlich wurde das nicht zuletzt, als der Papst in einer offiziellen Note scharf gegen den Friedensschluss protestierte, weil er die Rechte der katholischen Seite leichtfertig aufgegeben sah. Die katholischen Beteiligten des Abkommens hielt dies nicht von der Unterzeichnung ab - ein religiöser Schiedsrichter wurde in Sachen Krieg und Frieden nicht mehr akzeptiert."
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ a296b972:e5a7a2e8
2025-04-12 19:12:54
@ a296b972:e5a7a2e8
2025-04-12 19:12:54So sehr der Gedanke auch verlockend ist, es ist leider nicht möglich, den Staat durch Steuerzahlungsverweigerung auszuhungern, obwohl die absurde, generationenübergreifende Sonderverschuldung geradezu danach schreit. Das hysterische Herbeireden einer Bedrohung durch Russland wird durch die Steuerzahler zwangsfinanziert. Die zu melkende Kuh kann nicht aus ihrem Stall ausbrechen. Nach wie vor gibt es Menschen, die ihre Steuererklärung fristgerecht abgeben möchten, die sich daraus ergebende Steuerschuld jedoch auf einem Notar-Anderkonto so lange parken wollen, bis die Vertreter der deutschen Kakistokratie mit totalitären, faschistischen, kommunistischen, bolschewistischen und sozialistischen Strömungen, zu lebenslangem Sozialdienst in Senioren-Residenzen (oder lieber nicht) verdonnert wurden oder sich ihre Spuren in selbstloser Aufopferung für Unseredemokratie in der Ukraine verloren haben.
Sobald eine Regierung, die zuerst zu beweisen hätte, dass sie bei Verstand ist und ihr Ohr wieder am Willen des Volkes hat, würden diese eingefrorenen Gelder des Souveräns von demselben für mit ihm abgestimmte Projekte zugunsten des Gemeinwohls freigegeben werden. Ein Mitspracherecht der Bevölkerung ist dringend notwendig und laut Grundgesetz auch möglich! Denunzierungsportale und staatlich geförderte NGOs gehörten sicher nicht dazu.
Auch, wenn mit allen Mitteln versucht wird, der demokratischen Grundordnung durch verhaltensauffällig-denkeingeschränkte Ideologinnen und Ideologen den größtmöglichen Schaden, den selbige als solchen nicht erkennen wollen, zuzufügen, gibt es dennoch Möglichkeiten des Widerstands.
Derzeit könnte hilfreich sein:
So viele wie möglich distanzieren sich so weit wie möglich von allen staatlichen Institutionen und bedienen das vom Alt-Parteien-Kartell missbrauchte System nur noch im geringst möglichen Maß.
Es sollte jede Möglichkeit genutzt werden, mit legalen Mitteln Sand ins Getriebe zu streuen.
Es ist die demokratische Pflicht des Souveräns, NEIN zu sagen, wo immer er denkt, dass Freiheit und Demokratie in Gefahr sind. Wer mit offenen Augen durch das Land geht, findet Gründe genug. Zu bestimmen, was Lüge ist, ist nicht Aufgabe der Politik. Dieses Vorgehen gleicht betreutem Denken innerhalb eines vorbestimmten Korridors für ein entmündigtes Volk. Antrieb ist das unbedingte Festhalten an der Macht, die in weiten Teilen längst keinen Rückhalt mehr in der Bevölkerung und sogar innerhalb der Parteien selbst hat.
Zur Erinnerung: Die Meinungsfreiheit schließt auch Lügen ein. Die hier oft aus der Schublade geholte „Nazi-Keule“ dient vor allem der Rechtfertigung der politischen Vorgaben und missbraucht so die Achtung vor den Gräueltaten in der vorläufig dunkelsten Zeit der deutschen Geschichte. Es gibt Anzeichen dafür, sich in Sachen Machtmissbrauch dieser so weit wie möglich anzunähern.
Es ist die demokratische Pflicht zu sagen „ICH MACHE DA NICHT MIT“, wenn politische Entscheidungen getroffen werden, die sich einer friedlichen Einigung und in Konflikten, diplomatischen Verhandlungen, entgegenstellen.
Es ist ein Friedensgebot aller Mütter und Väter, klar und deutlich anzusagen:
„NEIN, MEINE SÖHNE UND TÖCHTER GEB ICH NICHT HER!“
Die Gehirnwäsche und Propaganda-Beschallung durch die Medienkartelle in Funk, Fernsehen und Presse sind zu meiden, wie eine hochansteckende Hauterkrankung bei gleichzeitiger Vergiftung der inneren Organe.
Zahlungen sollten, wo immer es möglich ist, in bar erfolgen. Dies sollte so als Notwendigkeit verinnerlicht werden, wie das Ein- und Ausatmen.
Ein Aufruf zu öffentlichen Protestbekundungen hat derzeit wenig Sinn, da es die deutsche Mentalität nicht hergibt, das Bedürfnis zu spüren, in Massen auf die Straße zu gehen. In anderen europäischen Staaten sieht das anders aus. Besonders beeindruckend jüngst die Friedensaufrufe in Rom mit Menschenmengen, von denen man in Deutschland nur träumen kann.
Die Realität zeigt, dass für eine Veränderung die breite Masse in Deutschland momentan nicht zu gewinnen ist. Zu tief steckt der Deutsche Michel mit seiner German Angst in den Seelen. Daher ist es zunächst die Aufgabe der kritischen, wachen und Dummschwätz-immunen Menschen, einen „Wandel zur Vernunft und eine Abkehr vom Wahnsinn“ herbeizuführen.
Es ist die Zeit gekommen, dass so viele wie möglich, dem Regime, die wohlverdiente, größtmögliche Verachtung, für die Aushöhlung der Demokratie, die massive Einschränkung der Rede- und Meinungsfreiheit, die zu oft systemkonforme Rechtsprechung, die Ausweitung der Spaltung und das Vergessen-machen-wollen der deutschen Geschichte, entgegenbringen.
Was Deutschland fehlt, ist Einigkeit und Recht und Freiheit.
Sollte es, derzeit noch wider Erwarten, dennoch dazu kommen, dass der bereits vorhandene friedliche Widerstand eine wachsende Kraft erzeugen könnte, die Weitere dazu veranlasst, sich ihrer Kraft als der Souverän dieses einst ertragbar-demokratischen Staates wieder bewusst zu werden, wäre ein Generalstreik zu organisieren, um die Macht wieder dahin zu befördern, wo sie hingehört: Nämlich zu den Bürgerinnen und Bürgern eines Landes, das weitgehend vergessen hat, dass seine Ahnen die Demokratie mit ihrem Blut erkämpft haben und dass die Demokratie kein Dauergeschenk ist, für das man sich nie wieder einzusetzen hat. Die derzeitigen Machthaber haben ihren Auftrag zum Wohle des deutschen Volkes tätig zu sein offensichtlich vergessen. Man muss sie dringend wieder daran erinnern, wofür sie gewählt wurden: Die Interessen des Volkes umzusetzen und nicht ihre Vorstellungen davon. In ihrer Überheblichkeit glauben sie zu wissen, was gut für das Volk ist. Leider wissen sie es nicht!
Eine Einordnung als „Hass und Hetze“ durch das deutsch-orwellsche Wahrheitsministerium verbietet sich, da dies die perfiden Maßnahmen im Dritten Reich zu Unrecht relativieren würden.
Die Menschlichkeit gebietet, den verirrten Geistern in Entscheiderpositionen Mitgefühl entgegenzubringen, da sie in gutem Glauben und der Überzeugung sind, nur Gutes zum Wohle des deutschen Volkes, schadenabwendend zu vollbringen. Grund ist die Ideologie, von der sie gar nicht merken (oder es nicht merken wollen), dass sie in ihr gefangen sind.
Nachgeschlagen in einem deutschen Herkunftswörterbuch von 2001 kommt das Wort „Delegitimation“ noch gar nicht vor. Diese Neuschöpfung scheint, durch die politische Kaste entstanden, der Notwendigkeit geschuldet zu sein, kritische Stimmen mundtot machen zu wollen. Sie dient einzig und allein als Totschlagargument. Jeder, der seine demokratische Pflicht wahrnimmt, politische Entscheidungen zu hinterfragen und Kritik auszusprechen, trägt zur lebendigen Debattenkultur bei und hält damit die in einer Demokratie innewohnende Meinungsfreiheit hoch. Kritik, und sei sie noch so scharf, als Delegitimation zu bezeichnen, spricht eher von einer charakterlichen Fehlbildung und Ungeeignetheit für ein politisches Amt in einer Demokratie, als dass sie Respekt vor der Meinungsäußerung des Souveräns zeigt. Gleichzeitig entlarvt die Erfindung des Begriffes Delegitimation, anstelle von Zensur (das wäre zu offensichtlich), durch ihrer Realitätsferne, die fehlende politische Wirkungskraft, so dass man nicht mehr anders weiter weiß, als sich von der Demokratie entfernend, totalitär anmutender Mittel bedienen zu müssen.
Mit den Mitteln der Freiheit sind die Menschen in der Lage, diese armen Politiker-Seelen von ihrem Leiden zu befreien. Ein Besinnen auf die christliche Kultur des Abendlandes kann hier sehr hilfreich sein. Ein Erinnern an die europäische Kultur und Geschichte ebenso.
Dass viele Menschen die legitimen Mittel der Freiheit derzeit nicht nutzen, liegt vielleicht daran, dass das, was ihnen bisher als Freiheit verkauft wurde, aus menschlicher Sicht gar keine Freiheit ist. Die Auswahl in einem 5 Meter langen Yoghurt-Regal ist keine Freiheit! Vielleicht haben viele Menschen sogar Angst vor wirklicher, innerer Freiheit, weil da eine große innere Leere ist, die mit eigener Persönlichkeit durch individuelle, charakterliche Eigenschaften auszufüllen wäre. Man kann diesen Menschen noch nicht einmal einen Vorwurf daraus machen, weil das Bildungssystem gar kein Interesse daran hat, zu viele Menschen heranzubilden, die die Demokratie-Simulation durchschauen.
Es scheint, als würde man mit allen Mitteln versuchen, den jahrhundertealten geschichtlichen Faden Deutschlands und Europas durchschneiden zu wollen und den dunklen Teil der deutschen Geschichte ausklammernd dazu zu missbrauchen, den fortgeschrittenen Wahnsinn zu legitimieren.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ fbf0e434:e1be6a39
2025-04-12 18:04:10
@ fbf0e434:e1be6a39
2025-04-12 18:04:10Hackathon 概要
Hack The Grid — Level 2 是 LUKSO 推出的四级创作者项目的第二阶段,重点在于开发mini去中心化应用程序(dApps)。本阶段共有 70 名注册开发者参与,最终审批了 41 个 BUIDL 项目。该阶段鼓励参与者在 AI 代理、社交 DeFi、创作者货币化及游戏化等领域创新,致力于将 Universal Profiles 打造成集数字身份、社交互动与创造力于一体的多功能空间。
活动于 2025 年 2 月至 4 月开展,总资金池达 150,000 LYX,分配至各个级别。参与者可在多个阶段远程参与,1 至 3 级的成功项目将在第 4 级的社区资助轮中获得额外支持。
黑客松日程包含办公时间与学习会议,通过前期获奖者的见解为参赛者提供帮助。除技术实验外,活动还营造了协作开发环境,展现了去中心化应用程序创建的潜力,培育了生态系统中的创新。Hack The Grid 凸显了开发者社区的积极参与以及值得关注的项目贡献。
Hackathon 获奖者
ORIGIN GRANTS 奖项获奖作品
在第2级类别中,两个项目因其技术创新和对生态系统目标的对齐获得了Origin Grants的认可。
- Hiraeth Mini App: 此应用程序将区块链交易转变为基于NFT的数字文物,通过独特的表现形式捕捉各链上的历史叙事。
- Multisend - Defolio: MultiSend 提供了一种简化的方法,用于在单个交易中在 LUKSO 区块链上执行多个代币和NFT的转移,提高了资产管理的效率。
这些获奖项目以其对智能合约安全性、用户友好的界面、技术执行以及对 LUKSO 社区的价值增值而闻名。每位Origin Grant获奖者将获得价值$2,250的LYX,其中70%会提前发放,剩余金额取决于实现以采用为重点的KPI。获奖者还有机会进军第4级——社区资助轮,通过二次方融资获得额外的$24,000 LYX。
完整项目列表,请访问 DoraHacks。
关于组织者
LUKSO
LUKSO 是一家专注于区块链解决方案的技术导向型组织,专注于数字生活方式和创意经济。它因其在区块链基础设施领域的贡献而获得认可,并在开发增强用户中心身份和数字所有权的应用程序中扮演重要角色。该组织在创建Universal Profiles方面起了重要作用,促进了数字平台之间的无缝交互。目前,LUKSO 旨在扩大区块链在日常数字体验中的角色,优先考虑安全性和可访问性,以此为技术领域内多样化的用户群体服务。
-
 @ fbf0e434:e1be6a39
2025-04-12 18:02:06
@ fbf0e434:e1be6a39
2025-04-12 18:02:06Hackathon 概述
Innovate on Creator Network #Creathon 圆满落幕,116 位注册开发者中有 44 个项目获批。此次黑客松的主要目标是借助去中心化应用程序(dApps),在去中心化金融(DeFi)、非同质化代币(NFTs)、游戏及社会影响等领域,强化 Creator Network 生态系统。活动于 2025 年 1 月 19 日至 2 月 24 日期间举办,设置了 1,250 USDT 的奖金池,将颁发给十名获奖者,其中前三名的奖金在 200 美元至 300 美元之间。
在此次黑客松中展示的项目,通过创新性和功能性,展现了对 Creator Network 生态系统的潜在影响。这些项目如今有机会进一步融入平台并获得支持。活动极大地吸引了开发者参与,参与者们利用了 Creator Network 的开发工具和测试网。这一举措标志着,在通过创新技术方案拓展 Creator Network 能力及强化其生态系统方面,迈出了重要一步。
Hackathon 获奖者
Creator Network 奖项获奖者
- DeFi Connect Credit: 在Creator Testnet Network上运作的去中心化交易所,通过提供代币交换、锁定、深度流动性和投票机制来增强去中心化和流动性管理,提高DeFi解决方案。
- Lumoswap: 基于Creatorchain的去中心化交易所,提供快速、安全且用户友好的交易体验。它解决了DeFi生态系统中交易速度和安全性等关键问题。
- Sendtokens: 一个具备自我保管功能的加密货币钱包,通过简化交易和提高用户体验,解决了与冗长钱包地址和界面可用性相关的常见挑战。
- Tokens: 该平台简化了加密货币代币的创建,提供在去中心化环境中高效管理和部署的工具,确保即时可见性和实用性。
- ProtectedPay: 一个多链DeFi平台,促进安全交易和群组支付。它整合了储蓄功能,以在区块链网络中增强安全性和便利性。
- AuditFi_Creator: 利用AI技术为智能合约提供即时链上审计报告,从而加强Creator Network生态系统中的信任和安全性。
关于所有项目的详细信息,请访问 Hackathon 详情页 。
组织者信息
Creator Network
Creator Network 是一家以技术为核心的组织,专注于区块链解决方案。它因开发增强区块链互操作性和安全性的去中心化平台而闻名。该组织已经推出了多个项目,旨在改善数字资产管理和智能合约功能。Creator Network 致力于扩展区块链的可访问性,促进数字生态系统的透明度。
-
 @ f57bac88:6045161e
2025-04-12 17:54:35
@ f57bac88:6045161e
2025-04-12 17:54:35پازل فناوری: ساختاری بیپایان
اینترنت و فناوری مثل موجوداتی زندهاند؛ همواره در حال رشد، تغییر و دگرگونی. برای سادهسازی، فرض میکنیم این پازل از سه بخش اصلی تشکیل شده:\ تکههای فعال (آنچه اکنون در دسترس ماست)،\ تکههای در حال توسعه (آنچه در راه است)، و\ تکههای خالی (آنچه جایش حس میشود).\ در ادامه، هر تکه را با جزئیات بررسی میکنم تا هیچ بخشی از این پازل از قلم نیفتد.
تکههای فعال: ستونهای دنیای دیجیتال امروز
این تکهها پایههای فناوری و اینترنت امروزیاند که بدون آنها، زندگی مدرن قابلتصور نیست. تا بهار ۱۴۰۴، این بخشها به بلوغ رسیدهاند و هر روز در حال استفادهاند:
-
شبکههای نوری پرسرعت: کابلهایی که دادهها را با سرعت بالا منتقل میکنند و اینترنتی پایدار و سریع را به خانهها و شهرها رساندهاند.
-
نسل پنجم ارتباطات سیار: فناوری ارتباطی جدیدی که با سرعت بالا و زمان پاسخدهی بسیار کم، ابزارهای هوشمند را به هم متصل میکند.
-
اینترنت ماهوارهای: پروژههایی که اتصال اینترنت را به دورافتادهترین نقاط کره زمین میبرند.
-
رایانش ابری: خدماتی بر پایهی سرورهای اینترنتی که ذخیرهسازی و پردازش دادهها را آسان کردهاند.
-
شبکههای اجتماعی دیجیتال: فضاهایی که گفتوگو، اشتراکگذاری و ارتباط را به بستر اینترنت آوردهاند.
-
بازرگانی الکترونیکی: فروشگاهها و بازارهایی که خرید و فروش را به شکل آنلاین و جهانی ممکن کردهاند.
-
ابزارهای جستوجوی اینترنتی: موتورهایی که در کسری از ثانیه، اطلاعات سراسر دنیا را در اختیارمان میگذارند.
-
پخش اینترنتی محتوا: سامانههایی که فیلم، موسیقی و ویدیو را به صورت آنلاین و لحظهای ارائه میدهند.
-
برنامههای تلفن همراه: نرمافزارهایی که تجربهی دیجیتال را شخصی، سریع و قابلحمل کردهاند.
-
ابزارهای هوشمند خانگی: وسایلی که با اتصال به اینترنت، خانه را خودکار و هوشمند میکنند.
-
هوش رایانهای: سامانههایی که توانایی درک، تحلیل و تصمیمگیری را به فناوری دادهاند.
-
یادگیری ماشینی: شیوههایی که رایانه از دادهها آموخته و نتایج بهتری ارائه میدهد.
-
تحلیل دادههای عظیم: بررسی حجم زیادی از اطلاعات برای کشف الگوها و تصمیمگیری بهتر.
-
امنیت فضای مجازی: ابزارهایی برای محافظت از دادهها و سیستمها در برابر تهدیدها.
-
زنجیرهی بلوکی: فناوریای برای انجام تراکنشهای امن و شفاف بدون واسطه.
-
پولهای دیجیتال: ارزهایی که مفهوم پول را وارد دنیای رایانهای کردهاند.
-
واقعیت مجازی: فناوریای که با استفاده از نمایشگرهای ویژه، افراد را وارد دنیایی شبیهسازیشده میکند.
-
واقعیت افزوده: افزودن اطلاعات دیجیتال به دنیای واقعی از طریق نمایشگرها یا گوشی همراه.
-
خانههای هوشمند: سامانههایی که با یک لمس، نور و گرمای خانه را مدیریت میکنند.
-
فناوریهای پوشیدنی: ابزارهایی که بر بدن پوشیده میشوند و سلامت و فعالیت ما را پایش میکنند.
این تکهها، ستونهای اصلی پازلاند که هر روز با آنها سر و کار داریم، ولی هنوز جای پیشرفت دارند، از امنیت بهتر تا دسترسی برابرتر.
تکههای در حال توسعه: نوآوریهایی در آستانهی شکوفایی
این بخش، آیندهی نزدیک و دور فناوری را به تصویر میکشد؛ تکههایی که در آزمایشگاهها و پروژههای پژوهشی در حال شکلگیریاند و بهزودی به پازل افزوده میشوند:
-
نسل ششم ارتباطات سیار: ارتباطاتی با سرعتی فراتر از نسل پنجم.
-
رایانش کوانتومی: رایانههایی که بر پایهی قوانین فیزیک کوانتوم، مسائل بسیار پیچیده را در لحظه حل میکنند.
-
پردازش در لبهی شبکه: انتقال بخشی از محاسبات به نزدیکترین نقطه به محل تولید داده برای کاهش تأخیر و مصرف انرژی.
-
وسایل نقلیهی بدون راننده: خودروهایی که با کمک هوش رایانهای و حسگرها، بهتنهایی حرکت میکنند.
-
رابط مغز و ماشین: فناوریای که فعالیتهای مغزی را به رایانهها و دستگاهها متصل میکند.
-
شبکههای هوشمند انرژی: سامانههایی برای مدیریت بهینهی مصرف برق و منابع انرژی.
-
پزشکی دیجیتال پیشرفته: بهرهگیری از فناوری برای تشخیص و درمان بهتر، مانند جراحی رباتیک یا تحلیل دادههای سلامت.
-
مواد واکنشپذیر: موادی که با تغییر شرایط محیطی واکنش نشان میدهند، مانند پارچههایی که ترمیم میشوند.
-
هوش فراگیر رایانهای: هوشی که میتواند همچون انسان در زمینههای مختلف فکر کند و خلاق باشد.
این تکهها نویدبخش آیندهای هیجانانگیزند، اما هنوز نیاز به زمان، سرمایهگذاری و زیرساخت دارند تا کامل شوند.
تکههای خالی: خلأهایی که باید پر شوند
این بخش، جاهایی را نشان میدهد که هنوز کامل ساخته نشدهاند یا نیاز به توجه ویژه دارند. این تکهها، چالشها و فرصتهای آیندهاند:
-
دسترسی برابر به اینترنت برای همه: فراهم کردن اینترنت پرسرعت در همهجا، حتی مناطق دورافتاده.
-
حفاظت کامل از حریم خصوصی: فناوریهایی که جلوی هر نوع سوءاستفاده از اطلاعات شخصی را بگیرند.
-
تأمین انرژی پایدار برای فناوری: بهرهگیری از منابع انرژی پاک برای تأمین نیازهای روزافزون.
-
قوانین جهانی هماهنگ در زمینه فناوری: مقررات مشترکی که هماهنگی جهانی را ممکن کنند.
-
بازیافت کامل تجهیزات دیجیتال: فرآیندهایی برای بازیافت زبالههای الکترونیکی بدون آسیب به محیط زیست.
-
هوش مصنوعی مسئول و منصفانه: سامانههایی که تصمیمهایی بدون تبعیض و ناعادلانه میگیرند.
-
شبکههایی مقاوم در برابر سانسور: ارتباطاتی که دولتها یا نهادها نتوانند آنها را محدود کنند.
-
زیرساختهای مقاوم در برابر بلایا: سامانههایی که حتی در شرایط بحرانی همچنان فعال بمانند.
-
آموزش دیجیتال همگانی: آموزشهایی که برای همه، در هر سطح و سن، قابلدسترس باشد.
-
ارتباط با فضا و سیارات دیگر: فناوریهایی برای برقراری ارتباط بین زمین و نقاط دوردست فضایی.
این تکهها خلأهاییاند که پر شدنشان میتواند کل تصویر را دگرگون کند.
تصویر نهایی: پازلی که هرگز کامل نمیشود؟
پازل فناوری، با سه دستهی فعال، در حال توسعه و خالی، ساختاری پویاست. هر تکهی تازهای که افزوده میشود، ممکن است به تکههای دیگری نیاز پیدا کند. مثلاً فناوری پول دیجیتال، بحثهایی تازه دربارهی قوانین مالی یا امنیت دیجیتالی به دنبال آورده. یا رشد هوش رایانهای، نیاز به بحثهای اخلاقی را مطرح کرده است.
امروز، بخش بزرگی از پازل سر جایش قرار گرفته، اما آینده، پر از ناشناختههاست. از رایانههای کوانتومی گرفته تا خودروهای بدون راننده، از خلأهای دسترسی برابر تا دغدغههای امنیتی، همگی ما را به تفکر، تلاش و انتخابهایی مهم فرا میخوانند.
شما چه فکر میکنید؟\ کدام تکه از این پازل از دید شما مهمتر است؟\ فکر میکنید چه چیزی هنوز از قلم افتاده؟\ نظرات خودتان را بنویسید تا این پازل را با هم کاملتر کنیم.
منابع
-
Simplilearn. 25 New Technology Trends for 2025: An overview of emerging technology trends in 2025.
-
GeeksforGeeks. Top 25 New Technology Trends in 2025: In-depth analysis of developing technologies.
-
Forbes. Top 10 Technology Trends For 2025: Key trend predictions by Forbes experts.
-
NKTelco. Internet Trends to Watch in 2025: A look at the future of internet and connectivity.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 7d33ba57:1b82db35
2025-04-12 15:14:35
@ 7d33ba57:1b82db35
2025-04-12 15:14:35Pisa, in Tuscany, is world-famous for its iconic Leaning Tower, but this riverside city offers much more than a fun photo op. With Romanesque architecture, student energy (thanks to its prestigious university), and charming piazzas, Pisa makes a great day trip—or a surprisingly rewarding overnight stay.
🌟 Must-See in Pisa
1️⃣ The Leaning Tower of Pisa (Torre Pendente)
- Built in the 12th century and leaning ever since due to soft soil
- Climb the spiral staircase (about 300 steps) for sweeping views of the city
- Best photo time? Early morning or golden hour for softer light
2️⃣ Piazza dei Miracoli (Square of Miracles)
- A UNESCO World Heritage Site and home to:
- The Cathedral (Duomo di Pisa) – Beautiful Romanesque façade
- The Baptistery – The largest in Italy, with amazing acoustics
- The Camposanto Monumentale – A peaceful cemetery with frescoes and ancient tombs
3️⃣ Walk Along the Arno River
- Quiet and atmospheric, especially at sunset
- Great way to escape the crowds around the tower and see the colorful riverside buildings
4️⃣ Explore the Historic Center
- Visit Piazza dei Cavalieri, once the political heart of Pisa
- Check out Scuola Normale Superiore, one of Italy’s most elite universities
- Wander through narrow medieval streets lined with shops and cafés
🍕 What to Eat in Pisa
- Cecina – A savory chickpea pancake, usually eaten as street food
- Torta co’ bischeri – A traditional chocolate and rice tart
- Pisan-style pasta with gamey meats or wild boar ragù
- Pair with local wines from the Colline Pisane

🎯 Quick Tips for Visiting
✅ Pisa is very walkable—comfortable shoes are your best friend
✅ The Leaning Tower is popular—book climb tickets online in advance
✅ It’s an easy day trip from Florence or Lucca by train (about 1 hour)
✅ Stay for the evening to enjoy Pisa’s local vibe once day-trippers leave -
 @ 4898fe02:4ae46cb0
2025-04-12 14:29:49
@ 4898fe02:4ae46cb0
2025-04-12 14:29:49Directory
📖 Day 1 - In the Beginning, an Idea...\ 📖 Day 2 - When Money Dies\ 📖 Day 3 - One Coin to Rule them All\ 📖 Day 4 - Transacting Adversarially pt. 1\ 📖 Day 5 - Transacting Adversarially pt. 2\ 📖 Day 6 - Not your Keys not your Coin\ 📖 Day 7 - The Seventh Day
Foreword
This is more than a curated list of articles.
This is more than a guide.
It is not a how-to or tutorial.
This is the first unschooled course syllabus and it is based entirely on the peer-reviewed work published by Stackers.
In undertaking such work as building a beginners course in bitcoin, one might stop and appreciate the plethora of other Bitcoin courses that live in the blogs of various company sites, such as those you will find on exchanges, wallet providers and the like. These are great, but the spirit of Bitcoin is in its community, so why not learn from the community directly?
Course Intro
What you will find below is a selection of some of the best that has been written by the thriving community on Stacker News. It is being referred to here as a course syllabus for the reason that it is intended to be used as a guide that you can follow as you take your first steps into the rabbit hole. Exploring new spaces online, especially those surrounding Bitcoin, can be intimidating and anxiety inducing, so rest easy and let this syllabus be your guide.
Included are a carefully selected list articles, spread across seven days of learning. Each day also has included the learning outcomes for that day and post-reading reflections.
It is recommended you come ready to learn, with a note-taking implement/software and an open mind. Feel free to share your responses to the questions in the comments. The discussion questions are obviously optional, but have been written with the purpose of prompting further engagement in the materials.
Target Audience
This particular Unschooled course is geared toward the intellectually curious and self-directed (much like later iterations will be).
No prior knowledge of Bitcoin is required as the course has been designed to suit the absolute bitcoin initiate.
Expected outcomes
By the end of the seven-days, learners will have
- developed an awareness of peer to peer electronic cash
- engaged some of the philosophical currents in the Bitcoin community
- analyzed the quesiton: why Bitcoin not crypto?
- reflected on the important concepts in Bitcoin such as wallets, UTXO's, Nodes and Lightning Network
- answered the question: what is KYC and AML?
- seen the relevance of the phrase "not your keys, not your bitcoin"
A Final note by way of Introduction
The course is designed to familiarize you with the technology that you will ultimately use to interact with the Bitcoin network, not to give investment advice. It is recommended that you finish the course before making any financial decisions, as there is important insight to be gained in all seven days.
Lastly, nothing stated herein is intended as financial advice.
Let's begin!
-
 @ 73dc15e0:b7a84244
2025-04-12 14:24:06
@ 73dc15e0:b7a84244
2025-04-12 14:24:06プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ f1e78daa:124e0e56
2025-04-12 14:13:41
@ f1e78daa:124e0e56
2025-04-12 14:13:41今日はテストです。
-
 @ f1e78daa:124e0e56
2025-04-12 14:02:20
@ f1e78daa:124e0e56
2025-04-12 14:02:20プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ f1e78daa:124e0e56
2025-04-12 14:01:15
@ f1e78daa:124e0e56
2025-04-12 14:01:15プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 6a6be47b:3e74e3e1
2025-04-12 12:13:13
@ 6a6be47b:3e74e3e1
2025-04-12 12:13:13Hi frens! How's your weekend starting? I'm just finishing a newblog entry 🖋️on my website and I'm going to be selling a few things on my Ko-fi shop 🛍️.
Before I post everything, I wanted to share a special treat with my Nostr family:
🎁 I've created two beautiful postcard-sized (148mm x 210mm or 5.83 in x 8.27 in)artworks inspired by Holy Week. Here they are:
Palm Day
 Resurrection Day
Resurrection Day

✉️ If you'd like one, just DM me with your email address, and I'll send it your way! Zaps are always appreciated and help keep me going. 🙏
❤️ This is big thank you to you my frens Have fun and stay safe
✝️ This is an INSTANT DIGITAL DOWNLOAD, no physical item will be shipped to you.
✝️ The frames and accessories in the listing images are not included.
🚨 DISCLAIMER 🚨
❤️ Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is purchased.
❤️ Limited License: The digital print provides a limited, non-transferable license for personal use only. It is not intended for commercial use or resale.
❤️ No Reproduction Rights: The purchase of this digital print does not grant any rights to reproduce, distribute, or create derivative works based on the design.
🚨 By proceeding with the purchase of this digital print, you acknowledge and agree to these terms. 🚨
-
 @ 2e8970de:63345c7a
2025-04-12 10:27:01
@ 2e8970de:63345c7a
2025-04-12 10:27:01This week I read up on what's currently happening to kids and their relationship to social media and smartphones. Especially the following thw pieces of media: The Ezra Klein Show: ‘Our Kids Are the Least Flourishing Generation We Know Of’ interview with Jonathan Haidt and his book on the topic:
https://www.youtube.com/watch?v=RN2GhPal4qA
And the podcast Search Engine 'What’s actually on teenagers’ phones? ' and a documentary tv show on the topic where teenagers show their phone screens to their parents as a social experiment
https://www.searchengine.show/whats-actually-on-teenagers-phones/
Yes yes, both are outlets that are clearly progressive partisan. But this topic really is a non partisan topic. Don't click away yet.
Here are my key takeaways on the topic:
How kids spend their time
- For most of human history kids and teenagers spend their time with other kids. And especially not only their exact same age: also with kids a few years older and younger. This is obviously a lot less now that kids are almost exclusively online. When kids play outside and have other kids that are 2y older as rolemodels and look out for other kids that are 2y younger that obviously changes something in their upbringing and how they learn to behave in social connections. What changes about personality of humans when whole generations did not have this experience?
- Kids spend more and more time with their parents. This might be surprising in a story that is primarily about less and less socializing. But parents are more and more of the opinion that the most important goal in parenting is spending "quality time" with their kids. But is this true? Shouldn't they spend time with peers instead?
- The offline world is online now. In the tv show referenced in the podcast the filmcrew also got insight what teenagers do on gettogethers and partys. It was a surprising sight. Everyone is used to being filmed all the time. A boy jumped off a building, another kid took drugs and ended up in the hospital. But haven't teenagers always done stupid shit? The key difference is the boy did not jump off a building because he was a stupid teenager having fun. He did it to go viral online. What a bleak bleak new world.
- Younger than you expect. Did you know that 40% of 2yo own a tablet/ipad? I still remember the outrage of 10yo owning non-smart phones. The topic is still on but now it's babys. Also elementary school aged kids are almost surely all confronted with softcore porn and violence regularly. You can almost expect a child of this age have also seen hardcore porn and extreme violence. This really begs the question why we as a society still count if a Marvel movie has 1 or 2 f-words - what a ludicrous contrast.
- What happens on the phone is a secret. Kids have almost all the behavior to not talk about what happens on their phones. To some extent this is normal, to some extent this is also a big mystery how this developed. Your teenage daughter will not tell you when she looks bulimia, eating disorders, and superhuman women influencers all the time. Your 7yo will not tell you that they looked at disturbing violence gore content. Most mysteriously: even 3yo often already know this behaviour to hide their phone screens when playing phone games. How do they learn this? It is indeed a mystery.
Gender divide
Young girls and young boys have very different experiences here. Boys do still spend time with gaming and voicechats together. Young girls time online is very different. It is mostly alone. It is instagram pictures of unattainable lifestyle and looks.
The loss of common values
Jonathan Haidt had an interesting insight on the interplay of smartphones and the decline of religiosity here. The decline of religiosity in the west is obviously nothing new, it predates smartphones. But social media confronts kids with a whole world of different people and different values. So, a secularized world might not derive its values from religion anymore but a secularized world with local communities might still create consensus on values. But a secularized world where culture happens globally does not anymore. kids increasingly say they have no meaning or goals in life. In the interview Jonathan Haidt lists many statistics on this topic that you can look at from many angles but overall this is the trend.
An overaching concept in probably all value sets from liberal cities to arch conservative societies was some concept of social status. Maybe in an Amish village social status came from having a dozen children. Maybe in turbo leftist circles social status came from having an art exhibition.... you get the idea, the specifics do not matter. For teenagers this social status is synonymous with likes and followers. You, as a kid, will probably never have a million followers and therefore in this new world social status is unattainable.
This is of course very oversimplified. But you see how the world changed overnight when smartphones happened.
The concept of "Pacts"
If phones are so bad, just give it to them at an older age! Not so fast cowboy.
Kids with smartphones are less depressed, less anxious, more social, get more exercise, & experience less cyberbullying than kids w/out smartphones
https://x.com/ENBrown/status/1909257644499480973
The problem here is of course that kids without phones are social outcasts. This is even worse than the phones themselves.
The solution that has become really popular post covid is the concept of pacts. A few parents from one neighborhood and/or one school year come together and make a pact to not give their kids phones until a certain age.
Depressingly, Jonathan Haidt analysis found that these pacts don't work that well: It's only a trend in what is upper middle class anyway. Statistically many parents "break" under the pressure before the year has arrived. And lastly, they only seem to work when the size of the pact is like 10 kids or bigger.
Conclusion
I encourage you all the watch the interview and or listen to the podcast. The world changed a lot and we are barely talking about it.
originally posted at https://stacker.news/items/941383
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 7d33ba57:1b82db35
2025-04-12 09:27:34
@ 7d33ba57:1b82db35
2025-04-12 09:27:34Florence (Firenze) is where art, history, and passion collide in the most graceful way. As the birthplace of the Renaissance, it’s a city steeped in creativity—from Michelangelo’s David to Brunelleschi’s dome—and yet, it also lives in the little things: the smell of espresso, the sound of church bells, and golden sunsets over the Arno. Compact, walkable, and overflowing with beauty, Florence stirs something deep.
🌟 Must-See Highlights in Florence
1️⃣ The Duomo & Brunelleschi’s Dome
- The Cathedral of Santa Maria del Fiore dominates the skyline with its red-tiled dome
- Climb to the top (463 steps!) for breathtaking views of the city and Tuscan hills
- Don’t miss the baptistery’s golden doors—aka the “Gates of Paradise”
2️⃣ Uffizi Gallery
- One of the most famous art museums in the world
- Home to masterpieces by Botticelli (The Birth of Venus), da Vinci, Michelangelo, and Caravaggio
- Book timed-entry tickets—lines can be intense!
3️⃣ Ponte Vecchio
- Florence’s iconic medieval bridge, lined with goldsmiths and jewelers
- Great photo spot—especially at sunrise or golden hour
4️⃣ Michelangelo’s David at the Accademia
- The original, larger-than-life marble David is a powerful sight in person
- Also check out Michelangelo’s unfinished “Prisoners,” still emerging from stone
5️⃣ Boboli Gardens & Pitti Palace
- Cross the Arno to explore lush gardens, sculptures, and royal vibes
- Offers a peaceful break from the city streets and great panoramic views
🍷 What to Eat & Drink in Florence
- Bistecca alla Fiorentina – A legendary T-bone steak, grilled rare
- Ribollita – A hearty Tuscan soup with bread, beans, and vegetables
- Crostini with chicken liver pâté – Classic local starter
- Cantucci with Vin Santo – Almond biscuits dipped in sweet dessert wine
- Pair it all with a glass of Chianti Classico or Brunello di Montalcino
✨ Local Gems to Discover
- Piazzale Michelangelo – Sunset views that will stay with you forever
- San Lorenzo Market – Leather goods, food stalls, and local flair
- Santa Croce Basilica – Tombs of Michelangelo, Galileo, Machiavelli
- Oltrarno neighborhood – Artisans, cool cafés, and a slower, bohemian vibe
🎯 Florence Travel Tips
✅ Most sights are walkable—comfortable shoes are a must
✅ The city is busiest from late spring to early fall—visit in shoulder seasons if you can
✅ Museums are closed on Mondays
✅ Make restaurant reservations—especially for dinner at popular spots -
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 10fe3f70:3489c810
2025-04-12 03:53:36
@ 10fe3f70:3489c810
2025-04-12 03:53:36contract-drafting #agreement-drafting #learn-drafting #keep-learning
I am a lawyer and a teacher. I am interested in learning new things every day.
I am from India, and have studied in a reputed law school in Delhi. I have long experience of working as in-house counsels to some reputed organisations.
My present goal is to teach drafting of contracts. What I will teach is some basic skills required by students to draft contracts.
I did some freelance online teaching during Covid Pandemic, and found that students are very interested in learning the craft. But, I also understood that they may not have enough free time to learn due to busy schedule.
If you are interested, you can access my curated playlist on Youtube
Keep watching this space, if you wish to know more...
Lessons on Contract Drafting
- Contract Drafting - An Introduction
- ...
-
 @ 502ab02a:a2860397
2025-04-12 02:40:22
@ 502ab02a:a2860397
2025-04-12 02:40:22เริ่มจากบรอกโคลี แล้วขยายผลไปสู่ระดับโลก
หลายประเทศในเอเชีย แอฟริกา ละตินอเมริกา ตกอยู่ในสภาพ “จนหนี้หัวโต” ทั้งจากวิกฤตเศรษฐกิจหรือปัญหาสภาพภูมิอากาศ แล้วใครกันล่ะเข้ามาช่วย?
ชื่อที่ได้ยินบ่อยคือ IMF (กองทุนการเงินระหว่างประเทศ) World Bank (ธนาคารโลก) WTO (องค์การการค้าโลก) FAO (องค์การอาหารและการเกษตรของ UN)
ฟังดูเหมือนองค์กรการกุศล แต่เบื้องหลังคือกลไกที่ “แลกข้าวกับกฎหมาย” โดยเฉพาะเมื่อประเทศยากจนขอเงินกู้หรือขอเข้าเป็นสมาชิกข้อตกลงการค้า พวกเขาจะถูก “บังคับกลายๆ” ให้ต้องแก้กฎหมายภายในประเทศให้สอดคล้องกับ UPOV 1991
ตัวอย่างชัดๆ กันครับเช่น 1. แอฟริกาใต้ / กานา / เคนยา ถูกกดดันจาก World Bank ให้ปรับกฎหมายคุ้มครองพันธุ์พืช ไม่งั้นจะไม่อนุมัติเงินช่วยเหลือสำหรับเกษตรกรรมและการศึกษา 2.ฟิลิปปินส์ / เวียดนาม / อินโดนีเซีย ต้องรับเงื่อนไข UPOV 1991 เพื่อเข้า FTA กับ EU หรือสหรัฐฯ ถ้าไม่ยอม? ข้าว ข้าวโพด หรือสินค้าเกษตรอื่นๆ จะเข้าไปขายไม่ได้ 3.เม็กซิโก เคยต่อสู้กับ Monsanto เรื่องสิทธิในการปลูกข้าวโพดดั้งเดิม แต่สุดท้ายโดน “ตีท้ายครัว” ด้วย FTA กับสหรัฐที่ฝัง UPOV 1991 มาแบบแนบเนียน
ปี 2561 รัฐบาลบางประเทศพยายาม “รีบแก้กฎหมายพันธุ์พืช” ให้สอดคล้องกับ UPOV 1991 เพื่อปูทางเข้าสู่ CPTPP ซึ่งเป็นข้อตกลงการค้าเสรีระดับภูมิภาคที่มีประเทศร่ำรวยอยู่เต็มไปหมด
ข้อเรียกร้องจาก CPTPP คือ -ต้อง ห้ามเกษตรกรเก็บพันธุ์ไว้ใช้ซ้ำโดยไม่ได้รับอนุญาต -ต้อง คุ้มครองพันธุ์พืชที่พัฒนาขึ้นโดยบริษัทเอกชน 20-25 ปี -ต้อง เปิดทางให้บริษัทต่างชาติเข้ามาจดทะเบียนพันธุ์พืชในประเทศได้โดยง่าย
เสียงค้านจึงดังกระหึ่มจากเกษตรกร นักวิชาการ และภาคประชาสังคม นำโดยเครือข่ายเกษตรกรรมยั่งยืน กลุ่มรักษ์พันธุ์ข้าว จนนายกรัฐมนตรีในขณะนั้นต้องออกมาประกาศ “พักเรื่องนี้ไว้ก่อน” แต่ถึงวันนี้... ก็ยังไม่มีการยืนยันว่าจะ “ล้มเลิกโดยสิ้นเชิง”
รู้หรือไม่ว่า บริษัทพันธุ์พืชที่ใหญ่ที่สุดในโลกไม่ใช่คนปลูกข้าว แต่มาจาก “บริษัทยา” และ “บริษัทเคมี”!!!
Bayer (เยอรมนี) ที่ควบรวม Monsanto Corteva (สหรัฐฯ) แยกตัวจาก DowDuPont Syngenta (สวิตเซอร์แลนด์) ที่ตอนนี้เป็นของบริษัทจีน ChemChina
3 บริษัทนี้ครองตลาดพันธุ์พืชดัดแปลงพันธุกรรม (GMO) และพันธุ์ลูกผสมทั่วโลก และผลักดัน UPOV 1991 แบบดุดันผ่านองค์กรเช่น ISF (International Seed Federation)
องค์กรเหล่านี้พวกเขาไม่ได้ปล้นด้วยปืน แต่ใช้ สัญญา พวกเขาไม่ได้เผาไร่ แต่ “จดสิทธิบัตร” สิ่งที่ไม่ควรเป็นของใคร และสิ่งที่พวกเขาต้องการ ไม่ใช่แค่ข้าวโพดหรือถั่วเหลือง แต่คือ “สิทธิในการออกแบบอาหารทั้งโลก” ในแบบที่คนตัวเล็ก... ต้องจ่ายค่าเช่ากินข้าว ทุกปี ตลอดชีวิต
จากปัญหาเหล่านี้ก็เลยเกิดแนวคิดที่เรียกว่า Seed Sovereignty ซึ่งมองว่าเมล็ดพันธุ์เป็นสมบัติร่วมของมนุษยชาติ ไม่ควรถูกครอบครองแบบผูกขาด และเกษตรกรควรมีสิทธิในการ
-เก็บเมล็ดพันธุ์ -แลกเปลี่ยน -ปรับปรุง -ใช้งานซ้ำ โดยไม่ต้องขออนุญาตใครตอนต่อไปเรามาคุยเรื่อง UPOV 1991 กันครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ caa88a52:6c226a91
2025-04-11 22:58:40
@ caa88a52:6c226a91
2025-04-11 22:58:40Running Nestr!
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ f3873798:24b3f2f3
2025-04-11 22:43:43
@ f3873798:24b3f2f3
2025-04-11 22:43:43Durante décadas, ouvimos que o Brasil era o "país do futuro". Uma terra rica, com imenso potencial humano e natural, destinada a se tornar uma grande potência e referência para o mundo. Essa ideia, repetida em discursos políticos e publicações internacionais, alimentou gerações com esperança. Mas o tempo passou — e esse futuro promissor parece nunca chegar.
Na prática, o que vemos é um ciclo de promessas não cumpridas, problemas sociais profundos e um povo muitas vezes desiludido. Apesar do potencial imenso, o Brasil enfrenta barreiras estruturais e culturais que dificultam seu pleno desenvolvimento. E é justamente sobre isso que precisamos refletir.
A raiz dos nossos desafios
Não há como ter jeito sem que haja um enfrentamento com seriedade aos problemas que estão na base da nossa sociedade. Um dos maiores entraves é a precariedade da educação, tanto no acesso quanto na qualidade. Em muitas regiões, o estudo ainda é visto como perda de tempo, algo que não contribui para o sustento imediato da família. Mesmo com incentivos governamentais, o desempenho das escolas é baixo. Em vez de formar cidadãos críticos e profissionais capacitados, muitas vezes vemos instituições focadas em ideologias ou agendas desconectadas da realidade do aluno.
Outro ponto sensível é a estrutura familiar. Em áreas onde faltam referências morais, espirituais e sociais, o ambiente familiar pode se tornar disfuncional, com casos extremos de abusos e ausência total de valores básicos. Nesses contextos, a ausência de instituições que promovem virtudes e limites — como a Igreja, por exemplo — faz diferença. Não se trata de impor uma religião, mas de reconhecer o papel histórico que a fé teve (e ainda tem) na construção de uma base ética e civilizatória.
A falta de valores basilares e estrutura para a promoção da relações em sociedade, faz do ambiente escolar um local sem propósito, onde são depositados crianças para serem expostas a um convívio forçado com estranhos sem nenhum preparo familiar, e sendo muitas vezes subentendido pelos profissionais educadores como dever da família, no entanto tal estrutura foi corrompida e devido o combate a religião pelos veículos midiáticos.
O papel da cultura e da moralidade
A cultura brasileira também tem sido afetada por uma inversão de valores. Virtudes como honestidade, humildade e dedicação são muitas vezes vistas com desdém, enquanto comportamentos imprudentes e hedonistas são exaltados. Essa distorção enfraquece a sociedade e prejudica qualquer tentativa de avanço coletivo.
A elite intelectual e política, por sua vez, parece muitas vezes mais preocupada com interesses próprios do que com o bem comum. Muitos aderem a ideias que, em vez de promover a soberania e a autonomia nacional, aprofundam nossa dependência e fragilidade como país.
Existe saída?
Sim, existe. Mas não será simples — e muito menos rápida. O Brasil precisa de uma mudança profunda de mentalidade. Isso inclui:
Resgatar o valor da família e da formação moral;
Investir de verdade em uma educação que liberte, que forme e que inspire;
Incentivar a produção científica e tecnológica local;
Valorizar o trabalho árduo, a persistência e o compromisso com a verdade.
Também é preciso reconhecer que o desenvolvimento de uma nação não é apenas econômico, mas também espiritual e cultural. Mesmo que você não seja religioso, é possível entender que a construção de uma sociedade mais justa exige princípios, virtudes e limites. Sem isso, qualquer progresso será frágil e passageiro.
O Brasil tem jeito? Sim. Mas depende de nós — da nossa capacidade de enxergar com coragem onde estamos falhando, e da nossa disposição para agir com sabedoria, verdade e esperança.
-
 @ d0aa74cd:603d35cd
2025-04-11 20:24:40
@ d0aa74cd:603d35cd
2025-04-11 20:24:40Experimenting with cat package examples.
Gleam #Gleamlang #cat #Haskell
https://photonsphere.org/post/2025-04-11-gleam-cat/
-
 @ 2ed3596e:98b4cc78
2025-04-11 20:13:03
@ 2ed3596e:98b4cc78
2025-04-11 20:13:03Americans can now instantly sell bitcoin directly from their Lightning Wallets. The same auto conversion Bitcoin Well Customers are used for instantly and conveniently selling bitcoin from self-custody now has a Lightning option ready in the Sell bitcoin page of your Bitcoin Well account.
Adding the ability to sell bitcoin from the Lightning Network underscores our commitment to enabling you to get the most out of the freedom and independence Bitcoin has to offer. No longer must you rely on giving up custody of your bitcoin or navigate complicated trading interfaces for fast and convenient sales! Just send sats and receive dollars – Lightning fast.
Selling sats from the Lightning Network is quick and easy:
- From your Bitcoin Well account, go to Sell bitcoin and enter the amount of dollars you want
- Choose your bank, select “Lightning” and then generate a Lightning Invoice
- Pay the Lightning invoice and we’ll send dollars to your bank account
Here are detailed steps to guide you on how to sell sats from the Lightning Network 👇
Get your Lightning Invoice
Navigate to your Sell bitcoin page, enter the amount of dollars you wish to receive, set your destination bank account and select “Lightning”.
 Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.
Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.Send sats to your Lightning Invoice
To instantly sell bitcoin for dollars, simply pay the Lightning Invoice from your Lightning wallet. You can do this by scanning the QR code or by tapping the QR code to copy + paste the invoice into your Lightning wallet. Once received (basically instantly), we automatically convert received sats into dollars and send the dollars to your selected bank account. No waiting for confirmations, no mining fees and no complicated trading interfaces. Just sats in, dollars out. Lightning fast ⚡️
 ## What is the Lightning Network?
## What is the Lightning Network?The Lightning Network is a second-layer protocol built on top of Bitcoin. It enables fast, cheap, and private bitcoin payments, perfect for small transactions and daily use. Think of it like the relationship between the credit card network and the banking system. While Bitcoin’s base layer is optimized for security, Lightning is optimized for frequent or small, cheap and private payments for everyday transactions — instantly and without bloating the blockchain. The Lightning Network makes it much more convenient to use bitcoin in everyday life, bringing you closer to replacing your bank with bitcoin.
Currently, sats on the Lightning Network cannot be directly sent to an on-chain bitcoin wallet, and vice versa. However, that won’t remain true for Bitcoin Well accounts for long…
Why Does the Lightning Network Matter?
The Lightning Network helps bitcoin reach its full potential as everyday money. While Bitcoin’s base chain is perfect for storing value, it’s not always practical for everyday payments or quick, small transactions. Lightning fills that gap — it’s fast, inexpensive, and built for a world where people use bitcoin as easily as cash. Bitcoin is the future of money. Lightning makes it usable today. We love Lightning, and have some exciting additional products coming that will shock you!
Earn sats over the Lightning Network
Earn sats when you refer your friends! When you add your Lightning Payment address from your personal Lightning Wallet to your Referral page, every time someone you referred transacts on the portal, you get a kickback paid in sats! Of course, we never custody your bitcoin, even when you get a Lightning referral reward! All bitcoin is always sent straight to your wallet. ⚡\ \ Haven’t signed up with Bitcoin Well yet? Sign up here and embrace the Bitcoin Standard.
About Bitcoin Well
Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we want to make it easy to use bitcoin in self-custody.
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website or reach out!
-
 @ 502ab02a:a2860397
2025-04-11 18:16:56
@ 502ab02a:a2860397
2025-04-11 18:16:56วันนี้เรามาคุยกันเรื่องที่ว่า บรอกโคลี เข้าร่วมเส้นทางของความ fiat food ยังไงกันครับ
ในอดีตกาล เมล็ดพันธุ์เป็นของสาธารณะ เป็นมรดกของมนุษยชาติที่ส่งต่อจากรุ่นสู่รุ่น ต้นข้าว ต้นถั่ว ต้นผัก ล้วนเติบโตจากธรรมชาติ ผ่านมือของชาวนาอย่างเสรี ไม่มีใครเป็นเจ้าของมันได้ คนอินเดีย คนไทย คนแอฟริกัน ต่างมีเมล็ดพันธุ์ของตนเอง เหมือนมีภาษาท้องถิ่นที่เล่าขานกันรุ่นต่อรุ่น
แต่แล้ววันหนึ่ง โลกเข้าสู่ยุค “Fiat” เมื่ออุตสาหกรรมเกษตรข้ามชาติอย่าง Monsanto, Bayer, Syngenta และ DuPont รวมพลังกันเปลี่ยนสิ่งมีชีวิตให้กลายเป็น “ทรัพย์สิน” เมล็ดพันธุ์ถูกจดสิทธิบัตร เกษตรกรเก็บเมล็ดพันธุ์ไว้ปลูกใหม่ กลับกลายเป็น “อาชญากร”! โลกเปลี่ยนจากการปลูกเพื่อกิน สู่การปลูกเพื่อขึ้นศาล กฎหมายและสิทธิบัตรกลายเป็นเครื่องมือในการควบคุม บริษัทเหล่านี้ใช้กฎหมายทรัพย์สินทางปัญญา เช่น สิทธิบัตรและสิทธิของผู้ปรับปรุงพันธุ์พืช (Plant Breeders' Rights) เพื่อควบคุมเมล็ดพันธุ์ กฎหมายเหล่านี้จำกัดสิทธิของเกษตรกรในการเก็บ ใช้ แลกเปลี่ยน หรือขายเมล็ดพันธุ์ของตนเอง
ปลูกอะไร? ปลูกหนี้? ชาวนาในอินเดียบางรัฐถึงกับฆ่าตัวตาย เพราะซื้อเมล็ดพันธุ์จีเอ็มโอที่มีสิทธิบัตรราคาแพงจากบริษัทเหล่านี้ พวกเขาไม่สามารถเก็บเมล็ดไว้ใช้ปีต่อไป ต้องซื้อใหม่ทุกปี บางครั้งซื้อแล้วปลูกไม่ได้ผล เพราะพันธุ์ไม่เหมาะกับภูมิอากาศของเขา แต่ก็ยังต้องจ่ายหนี้ จ่ายค่าปุ๋ย จ่ายค่าฆ่าแมลงที่บริษัทบอกว่าจำเป็นต่อเมล็ดของมัน ในขณะที่ผู้ที่ไม่ได้เดือดร้อนจากเรื่องนี้ มักบอกว่า ช่วยไม่ได้ไปเลือกซื้อของเขาเอง?
พูดให้เห็นภาพก็คือบริษัทเหล่านี้สร้างระบบแบบ “log in” เหมือนซอฟต์แวร์ ผูกเมล็ดพันธุ์เข้ากับเคมีภัณฑ์ ผูกเคมีเข้ากับกฎหมาย ผูกกฎหมายเข้ากับรัฐบาล และผูกรัฐบาลเข้ากับองค์กรโลกที่เห็น “ความมั่นคงทางอาหาร” เป็นเพียงบรรทัดนึงของ account เราครับ
-ค่าใช้จ่ายที่เพิ่มขึ้น เกษตรกรต้องซื้อเมล็ดพันธุ์ใหม่ทุกฤดูกาลเพราะถูกห้ามไม่ให้เก็บเมล็ดพันธุ์จากผลผลิตเดิม ทำให้ต้นทุนการผลิตสูงขึ้น -การสูญเสียความหลากหลายทางชีวภาพ การเน้นปลูกพืชสายพันธุ์เดียวกันทั่วโลกทำให้พืชท้องถิ่นและสายพันธุ์พื้นเมืองลดลง ซึ่งส่งผลต่อความหลากหลายทางชีวภาพและความยืดหยุ่นของระบบนิเวศ -ความเสี่ยงต่อความมั่นคงทางอาหาร การพึ่งพาเมล็ดพันธุ์จากบริษัทไม่กี่แห่งทำให้ระบบอาหารโลกเสี่ยงต่อการผันผวนของตลาดและการเปลี่ยนแปลงทางการเมือง
บรอกโคลี กับการเป็น Fiat Food ในรูปแบบพืช เริ่มมาจากพืชตระกูลผักกาด เช่น บรอกโคลี กระหล่ำดอก คะน้า และกะหล่ำปลี ถูก “ปรับปรุงพันธุ์” โดยมนุษย์จากบรรพบุรุษเดียวกัน มัสตาร์ดป่า พวกมันไม่สามารถขยายพันธุ์ตามธรรมชาติได้ ต้องอาศัยโรงงานผลิตเมล็ดพันธุ์โดยเฉพาะ และในบางกรณี ไม่มีเมล็ดเลย ต้องขยายพันธุ์โดย “Hybrid Sterility System” บริษัทผู้ผลิตเมล็ดพันธุ์จึงควบคุมได้หมด ใครจะปลูกต้องขออนุญาต ใครจะขายต้องผ่านระบบควบคุม
นั่นแหละ... เข้าคออนเสป Fiat Food ตัวจริง อาหารที่ดูเขียว ดูคลีน ดูดีต่อใจ แต่ไร้ “รากเหง้า” และถูกสร้างขึ้นด้วยอำนาจเหนือธรรมชาติอย่างจงใจ ไม่ใช่ของจากธรรมชาติ ไม่ใช่ของจากพระเจ้าแต่เป็นของจาก “วาระซ่อนเร้น” ที่ซ่อนอยู่ในแสงแฟลชของโฆษณาอาหารคลีน การประเคนข้อดีของความเป็น super food โดยไม่พูดถึงเหรียญอีกด้าน เหรียญด้านมืดของมัน
ดังนั้นก็เลยเกิดสมการ อธิปไตยของเมล็ดพันธุ์ = อิสรภาพของมนุษยชาติ การต่อสู้ครั้งนี้ไม่ใช่แค่เรื่องของเกษตรกรรม แต่มันคือ “การเมืองของชีวิต” เพราะใครก็ตามที่ควบคุมเมล็ดพันธุ์ เขาคือผู้ควบคุมอาหาร และใครควบคุมอาหาร เขาคือผู้ควบคุมโลก การต่อสู้ก็เลยมีองค์กรอย่าง Navdanya ในอินเดีย หรือ La Via Campesina ในลาตินอเมริกา ที่ลุกขึ้นมาปกป้อง “สิทธิในการปลูกของมนุษย์” มีคนขนานนามว่าพวกเขาไม่ใช่นักเกษตร พวกเขาคือนักปฏิวัติ
ดร. วันทนา ศิวะ Vandana Shiva นักฟิสิกส์ชาวอินเดียผู้กลายมาเป็นนักเคลื่อนไหวด้านสิ่งแวดล้อมและอาหาร ผู้ก่อตั้งโรงเรียนเมล็ดพันธุ์พืชนวธัญญะ (Navdanya) ผู้ปกป้องพืชท้องถิ่นจากบริษัทข้ามชาติที่คิดจะเข้ามายึดประชาธิปไตยทางอาหารไปจากมือประชาชน คือตัวอย่างที่ชัดเจนคนหนึ่ง เจ้าของวลี “หากจะยึดครองประเทศจงยึดแหล่งน้ำมัน แต่หากต้องการยึดครองชีวิต จงยึดเมล็ดพันธุ์พืชของพวกเขา”
งานเขียนที่น่าสนใจของเธอคือ Earth Democracy: Justice, Sustainability and Peace ปี 2005 เป็นการออกมาตอบโต้ระบบทุนนิยม ที่มองว่าทุกสิ่งทุกอย่างบนโลกใบนี้มีไว้ขาย เพื่อเก็งกำไร พร้อมทั้งตั้งคำถามว่า หากผืนดินไม่ใช่ของมนุษย์ โลกไม่ได้เป็นสินทรัพย์ น้ำทุกหยด เมล็ดพันธุ์พืชทุกชนิดล้วนเป็นของธรรมชาติ ความคิดของบริษัทที่จะเข้ามาผูกขาดธรรมชาติเป็นสิ่งที่สมควรจริงหรือ
ดังนั้นสรุปๆกันจากที่ผมจั่วไว้ว่า บรอกโคลี อีกตัวแทนแห่ง fiat food นั้นคือประตูบานแรกที่ชักนำให้เราฉุกคิดถึงรูปแบบของ อาหารที่ปลอมตัวมาอยู่ในรูปแบบ real food โดยภาพร่างประมาณนี้ครับ เมล็ดพันธุ์พื้นเมือง เคยเป็นของสาธารณะ → ถูกบริษัท “แปรรูป” เป็นทรัพย์สิน การเก็บเมล็ดพันธุ์ใช้ซ้ำ กลายเป็นสิ่งผิดกฎหมายในหลายประเทศ เกษตรกรกลายเป็นทาส ของระบบ “Fiat Seed” เหมือนเราทุกคนเป็นทาสของ “Fiat Money” บรอกโคลีและผักไฮบริดอื่นๆ คือตัวแทนของการควบคุมระบบอาหารผ่านสายพันธุ์ที่คนทั่วไปปลูกเองไม่ได้ ทางออกที่กลุ่มคนมีความหวังกับมันคือ Seed Sovereignty คืนสิทธิให้ชุมชน เก็บ แบ่ง แลก เปลี่ยนเมล็ดพันธุ์เองได้
การผูกขาดเมล็ดพันธุ์โดยบริษัทยักษ์ใหญ่ส่งผลกระทบต่อเกษตรกรและความมั่นคงทางอาหารอย่างมาก การเคลื่อนไหวเพื่ออธิปไตยทางเมล็ดพันธุ์เป็นสิ่งจำเป็นในการปกป้องสิทธิของเกษตรกรและรักษาความหลากหลายทางชีวภาพของพืชผลในอนาคต ใครกุมเมล็ดพันธุ์ คนนั้นกุมคอหอยมนุษย์ทั้งโลก
อ่านถึงตรงนี้แล้ว นึกถึงพืชอื่นอะไรอีกบ้าง? ทิ้งไว้ให้ตั้งคำถามกันต่อครับ ตอนต่อไปจะว่าด้วยเรื่องของ สนธิสัญญาและกฎหมายต่างๆครับ
แถมให้ดูคลิปการปลูก บรอกโคลี ครับ https://youtu.be/8ZNPTMIEFV8?si=SKZy
ผมเลือกคลิปที่ถ่ายโดย local ไม่ได้เป็น pr film โปรโมทองค์กรใดๆ เพื่อให้เห็นกระบวนการแท้ๆเลยนะครับส่วนคำถามที่ว่า แล้วจะกินอะไรได้ ตอบได้เลยว่า กินได้ทุกอย่างแหละครับ แต่ช่วยรู้ด้วยว่า อย่าไปคิดว่าอะไรเทพ อะไร superfood เลย โลกไม่ได้สวยงามขนาดนั้นครับ เราถึงพยายามชักชวนมาทำให้ local แข็งแรงไง
#PirateKeto #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 95cb33b5:f4580cd4
2025-04-11 16:57:35
@ 95cb33b5:f4580cd4
2025-04-11 16:57:35Electrical overloads are a significant concern in residential and commercial settings, often leading to hazardous situations such as fires, equipment damage, and power outages. One effective strategy to mitigate these risks is the installation of additional electrical circuits. By distributing electrical loads more evenly, additional circuits enhance safety, improve system efficiency, and accommodate the growing demand for electrical power in modern infrastructures.
Understanding Electrical Overloads
An electrical overload occurs when the current flowing through a circuit exceeds its designated capacity. This situation typically arises when multiple high-power devices operate simultaneously on a single circuit, drawing more amperage than the wiring can safely handle. Consequences of overloads include overheating of wires, degradation of insulation, and, in severe cases, ignition of fires. Common indicators of an overloaded circuit are:
Flickering or dimming lights
Frequently tripped circuit breakers or blown fuses
Warm or discolored wall plates
Buzzing sounds from outlets or switches
Burning odors emanating from electrical fixtures
Mild shocks or tingling sensations when touching appliances
The Prevalence and Impact of Electrical Fires
Electrical malfunctions are a leading cause of residential fires. According to the Electrical Safety Foundation International (ESFI), home electrical fires account for an estimated 51,000 fires each year, resulting in nearly 500 deaths, more than 1,400 injuries, and $1.3 billion in property damage. These statistics underscore the critical need for preventive measures to address electrical overloads and enhance the safety of electrical systems.
The Role of Additional Circuits in Preventing Overloads
Incorporating additional circuits into an electrical system effectively distributes the electrical load, reducing the likelihood of overloads. This approach involves segmenting the electrical supply into multiple pathways, each dedicated to specific areas or high-power appliances. Benefits of this strategy include:
Enhanced Safety: By preventing excessive current flow through any single circuit, the risk of overheating and potential fires is significantly reduced.
Improved Performance: Appliances and devices operate more efficiently when supplied with adequate power, free from the voltage drops associated with overloaded circuits.
Capacity for Expansion: Additional circuits provide the necessary infrastructure to support new appliances or technological upgrades without compromising the existing system's integrity.
Implementing Additional Circuits: Practical Considerations
When planning to add circuits, several factors must be considered to ensure effectiveness and compliance with safety standards:
Assessment of Current Load: A thorough evaluation of the existing electrical load helps identify circuits that are frequently overloaded and areas where additional circuits are needed.
Professional Installation: Engaging a licensed electrician ensures that new circuits are installed correctly, adhering to local codes and regulations.
Use of Appropriate Materials: Selecting wiring and components that match the intended load capacity is crucial for safety and durability.
Regular Maintenance: Periodic inspections and maintenance of the electrical system help detect and address potential issues before they escalate.
Complementary Measures to Prevent Overloads
In addition to installing extra circuits, other practices can further mitigate the risk of electrical overloads:
Use of Surge Protectors: Surge protectors safeguard sensitive electronics from voltage spikes, which can occur during overload conditions.
Avoidance of Extension Cords for Permanent Use: Relying on extension cords as a permanent solution indicates insufficient outlets and can contribute to overloads. Installing additional outlets or circuits is a safer alternative.
Upgrading Electrical Panels: Older electrical panels may not support the increased load demands of modern appliances. Upgrading to a panel with higher capacity can enhance system safety and performance.
Conclusion The integration of additional electrical circuits is a proactive and effective measure to prevent electrical overloads. By ensuring a balanced distribution of electrical loads, this approach enhances the safety, efficiency, and adaptability of electrical systems. Given the significant number of fires attributed to electrical malfunctions annually, prioritizing such preventive strategies is imperative. Engaging qualified professionals to assess and implement necessary electrical upgrades, including the addition of circuits, is essential in safeguarding property and lives against the hazards of electrical overloads.
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 866e0139:6a9334e5
2025-04-11 16:23:18
@ 866e0139:6a9334e5
2025-04-11 16:23:18
Autor: Jens Fischer Rodrian. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
In den letzten fünf Jahren wurde mit allen Mitteln versucht, die Menschen auseinanderzutreiben. Egal welches Thema gestreut oder welche Angst geschürt wurde, ob Corona, Ukraine, Gaza, Energiepolitik, Wirtschaft, Gendern oder Klima – immer sollten die Menschen einem vorgegebenen Narrativ folgen anstatt in einen offenen Debattenraum einzutreten und Differenzen auszuhalten, also das zu leben, was eine lebendige Demokratie ausmacht.
Natürlich stellt sich die Frage – ja aber wer hat das denn versucht? Wer hat denn ein Interesse daran, daß Diversität im Sinne von Vielfalt an Meinungen ausgehebelt wird? Dies zu beantworten würde den Rahmen hier sprengen, ist aber mit Verweis auf die Texte von Journalisten wie Milosz Matuschek, Tom-Oliver Regenauer u.v.a. schnell in Erfahrung zu bringen. Fest steht, nicht alle haben bei dem Versuch, die Bevölkerung ruhig und dumm zu halten, mitgemacht.
Der Wahnsinn als Chance
Egal wie laut die Bellizisten in Regierung und Medien ihre Kriegspropaganda in Dauerschleife rausbrüllen, in dem Wahnsinn steckt auch eine Chance. Immer mehr Leute verstehen, daß Deutschland in nahezu allen oben angeführten Themen, falsch abgebogen ist. Wenn es darum geht, seine Kinder für einen irrsinnigen, von den USA und der NATO provozierten Krieg in der Ukraine, zu opfern, werden hoffentlich mehr Menschen erkennen, daß sie verheizt werden sollen. Wichtig ist, daß wir nicht mit der Energie, die man für einen Sprint braucht, an all die Themen ran gehen, sondern uns auf einen Marathonlauf einstellen. Das wissen wir spätestens, seitdem die von Paul Schreyer heraus geklagten RKI Files nicht für die Empörung gesorgt haben, die man hätte erwarten können, obwohl sie klar aufzeigen, daß die Kritiker der Coronamaßnahmen in fast allen Punkten recht behalten sollten. Spätestens dann hätte die bis dahin sehr einseitig berichtende Konzernpresse auf das Thema aufspringen können, ja müssen, ist sie aber nicht. Milosz Matuschek hatte schon sehr früh in der NZZ gefragt: „Was, wenn am Ende ‚die Covidioten‘ Recht haben?“
Dass die Medien jetzt im Gleichschritt die Bevölkerung auf Krieg einstellen wollen (zahlreiche Links sind am Ende des Artikels zu finden), ist an Irrsinn nicht zu überbieten. Caren Miosga, die u.a. schon durch ihr unsägliches Interview mit Exkanzlerkandidat Robert Habeck durch mangelnde Objektivität und Einfältigkeit auffiel, sagte jüngst: „ (...) das lag lange nicht in unserer DNA, da lag Pazifismus. Wie können wir diesen Code schneller überschreiben?“ Die Antwort des Wehrdienstverweigerers und Kriegstreibers Joschka Fischer, sowie seine wirre Einschätzung einer korrupten ukrainischen Regierung und der von Neonazis durchzogenen Paramilitärs, findet Ihr in den Links am Ende des Artikels.
Seit 1945 war es nie so wichtig wie heute, daß wir uns dem entgegenstellen, alle anderen Unstimmigkeiten für den Moment beiseitelegen und gemeinsame Sache machen, denn es geht um alles, es geht um Krieg oder Frieden! Wir sollten keinen Zweifel daran haben, daß die Verantwortlichen, die Menschen mit einem experimentellen Gentherapeutikum „impfen“ auch keine Bedenken haben, die Kinder anderer Eltern in den Krieg zu treiben. Wären die Staatenlenker verpflichtet, ihre eigenen Kinder auch an die Front zu schicken, wäre das Säbelrasseln sofort vorbei – wobei ich mir bei Anton Hofreiter oder Annalena Baerbock gar nicht so sicher bin, sie sind Überzeugungstäter. Letztere fordert allen Ernstes, Russen bei Kriegsgedenken auszuschließen, sie seien per ‚Hausrecht“ zu behandeln. Der geschichtsvergessenen „Noch -Außenministerin“ ist anscheinend entfallen, daß die Russen 25 Millionen Opfer aus dem 2. Weltkrieg zu beklagen und Auschwitz befreit haben.
Das German Foreign Policy schreibt:
„Das Mindset für den Krieg – Bundeswehr-Kommandeure fordern Einstimmung der Bevölkerung auf Kriegssituationen, dringen auf stärkeren ‚Willen zur Selbstbehauptung‘. Bundesregierung arbeitet an ‚Bunker-App‘. CDU- Politiker spekuliert über ‚Spannungsfall‘“.
Um ein Zeichen gegen diesen Irrsinn zu setzen und sowohl auf die drohende Eskalation in der Ukraine wie auch die seit Jahrzehnten andauernde ethnische Säuberung in Palästina hinzuweisen, veranstalten wir am Karfreitag eine Friedensprozession in Dresden. Die Teilnehmerliste und den Text, den man auch unterzeichnen kann, findet Ihr hier im Anhang.
Jeder, der sich für den Frieden stark macht, ist willkommen.
Einer der Teilnehmer ist Tino Eisbrenner, ein Sänger und Friedensaktivist, der sich seit Jahrzehnten für Dialog und ein friedliches Miteinander einsetzt. Er selbst ist immer wieder mit Angriffen von Leuten konfrontiert, die es nicht ertragen, daß er sich beharrlich mit Wort und Musik für den Dialog mit Russland einsetzt. Erst vor Kurzem mußte er sich die inquisitorischen Fragen einer Journalistin gefallen lassen, die eine Art Gesinnungsprüfung durchführte, da ihr zu Ohren gekommen sei, das Bürger besorgt wären, Eisbrenner könne ein Putinfreund sein. Eisbrenner merkte an, daß sicherlich kein Künstler, der in Amerika auftrete oder amerikanische Poeten verehre, dadurch in Verdacht geraten könne, die imperialistische Politik eines amerikanischen Präsidenten zu unterstützen. Hier der Teil seiner Antwort, der die Kraft der Kultur und deren Funktion, Brücken zu bauen, sehr schön zusammenfasst:
„ (...) wenn man als Künstler der Ansicht ist, daß die Kunst, als wesentlichstes Merkmal des Menschseins, Grenzen überfliegen und die Brücken zwischen den Völkern erhalten und pflegen sollte, und dies auf Russland genau wie auf die USA anwendet, muss man sich rechtfertigen? In der Stadt Wolgograd (ehemals Stalingrad) gibt es ein riesiges Mahnmal für die Opfer des Zweiten Weltkrieges. Das Hauptgebäude, unweit der riesigen Grabstätte deutscher Soldaten, ist eine gigantische Kuppel in deren Mitte ein ewiges Feuer brennt. An den Wänden sind zigtausende Namen sowjetischer Bürger eingraviert, die der deutschen Schlacht um Stalingrad zum Opfer fielen. Und aus den Lautsprechern tönen in Dauerschleife die „Träumereien“ von Robert Schumann, einem deutschen Komponisten. Die Kunst, als Brücke zwischen den Völkern. Vielleicht können ihre „besorgten Bürger“ darüber mal in Ruhe nachdenken (...)“
Ich hatte die große Freude, mit Tino gemeinsam einen Song aufzunehmen, den wir beide bei der Friedensprozession in Dresden das erste mal live aufführen werden.
Frieden mit dem Frieden schließen
Frieden fragt nicht wo warst Du gestern\ Frieden fragt nicht wer ist Dein Gott\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden geht oft über Grenzen\ Frieden geht, wenn man ihn übersieht\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden schweigt wenn Menschen brüllen\ Frieden erstarrt wenn Schüsse fallen\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden fragt nicht nach Deinen Eltern\ Frieden stellt sich vor Deine Wut\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Wir müßen Frieden mit dem Frieden schließen
Mit Leib und Seele, Tag für Tag\ Frieden braucht Dich jetzt\ Er ist erschöpft und schwer verletzt ****
Kommt zur Friedensprozession!
Unser Orga-Team hat gemeinsam mit Jürgen Fliege den Text für die Friedensprozession am Karfreitag in Dresden verfasst, den man gern auch unterzeichnen kann.
FUNDAMENT FÜR DEN FRIEDEN Mit Dir! Mit uns! Mit allen!
Jenseits jeder politischen Orientierung wollen wir dieser Sehnsucht eine Stimme geben. Denn ein Krieg, ob er nun wie ein Flächenbrand in der Ukraine oder wie in Palästina wütet, verschont immer die Mächtigen. Nie die Ohnmächtigen. Das sehen viele Menschen in unserem Land längst. Wie schon in Jugoslawien und Afghanistan scheint das die Volksvertreter nicht zu interessieren.
Wir alle wollen keinen Krieg. Wir wollen Abrüstung, Frieden und gute Nachbarn sein.
Was sind das nur für Politiker, die im Gleichschritt gegen das Wohl der Völker marschieren? Die Strack-Zimmermanns, Pistorius‘, die Baerbocks, Merz und Kiesewetters, die den Krieg weit nach Russland hineintragen und amerikanische Raketen in Deutschland stationieren wollen, ähnlich wie ihn der Kriegsverbrecher Netanjahu nach Gaza trug. Wer stoppt die Eskalationsspirale des Wahnsinns? Können wir das noch? Wir müssen es versuchen!
Friede sei mit uns allen! Ohne Ausnahme! Darum müssen wir uns vereinen. Versöhnen statt Spalten war einmal eine gute Idee der alten Sozialdemokratie – genau das wollen wir wieder aufgreifen!
Das alles war einmal der Boden, auf dem unser Grundgesetz wuchs. Die Trümmer des Krieges und die Gräber von Millionen Toten verpflichten uns zum Frieden durch Diplomatie.
Wenn Ihr unsere Sehnsucht nach Frieden teilt, dann freuen wir uns sehr, euch in Dresden zu sehen, wo der Feuersturm des 2. Weltkrieges unvergessen bleibt. Am Karfreitag, an dem die Stille das Waffenrasseln um so hörbarer macht.
Nie wieder Antisemitismus! Nie wieder Faschismus! Nie wieder Krieg! Kommt nach Dresden! Bitte!
Das aktuelle Album „Voices for Gaza“ mit 32 Beiträgen findet Ihr hier:
https://protestnoten.de/produkt/voices-for-gaza-doppel-cd/
Mit dabei sind:
Uwe Steimle, Tino Eisbrenner, Jürgen Fliege, Prof. Ulrike Guérot, Yann Song King, Arnulf Rating, Markus Stockhausen, Kilian Forster, Diether Dehm, Jakob Heymann, Jens Fischer Rodrian, Alexa Rodrian, Guido de Gyrich, Dennis DuVall, Prof. Justus Frantz, Reiner Kröhnert
(Links:
- https://taz.de/Sportunterricht-fuer-den-Ernstfall/!6059664/
- https://www.tagesspiegel.de/politik/wir-mussen-uns-auf-krieg-vorbereiten-nato-chef-rutte-fordert-von-deutschland-deutlich-hohere-verteidigungsausgaben-13131001.html
- https://www.faz.net/aktuell/wirtschaft/unternehmen/bundeswehr-bereitet-unternehmen-auf-kriegsfall-vor-operationsplan-deutschland-110118573.html
- https://www.spiegel.de/politik/deutschland/sicherheit-in-deutschland-innenministerium-fuer-zivilschutz-uebungen-an-schulen-a-1680d64e-4a42-4e00-954b-0cb38e315a90
- https://www.facebook.com/henning.rosenbusch/videos/die-pflicht-zur-musterung-brauche-es-wegen-der-gefallenen-und-verwundeten-um-die/1073875391166801/
- https://www.youtube.com/watch?v=juGk0aY5Rdo Fischer bei Miosga
- https://www.tagesspiegel.de/gesellschaft/die-wehrpflicht-sollte-fur-alle-gelten-frauen-ans-gewehr-13480606.html
Jens Fischer Rodrian, geboren 1967 in Pinneberg, ist ein deutscher Musiker, Komponist, Musikproduzent und Dichter. Aufgewachsen nahe Murnau am Staffelsee, entdeckte er früh seine Liebe zur Gitarre. Er studierte in Los Angeles an der Grove School of Music und wurde 1995 Mitglied der Blue Man Group in New York und Boston. Seit 2004 lebt er mit seiner Frau, der Jazzsängerin Alexa Rodrian in Berlin, wo er als musikalischer Leiter der Blue Man Group tätig ist. Neben seiner Arbeit mit Künstlern wie Konstantin Wecker veröffentlichte er mehrere Soloalben und Gedichtbände, darunter „Sich kurz fassen – ach“ (2017) und „Wahn & Sinn“ (2019). Mit seiner Konzertlesung tourt er durch den deutschsprachigen Raum und setzt sich leidenschaftlich für Frieden und Demokratie ein. Zuletzt erschien: „Die Armada der Irren. Künstlerischer Widerstand in pandemischer Zeit“ (2022): Ein Buch mit beiliegender CD, das sich mit gesellschaftlichem Widerstand und der Rolle der Kunst in Krisenzeiten auseinandersetzt. Es enthält Beiträge von verschiedenen Autoren wie Wolfgang Wodarg, Gunnar Kaiser und anderen.
Die Friedenstaube fliegt auch in Ihr Postfach!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 95cb33b5:f4580cd4
2025-04-11 16:04:01
@ 95cb33b5:f4580cd4
2025-04-11 16:04:01Your wedding day in London is a story waiting to unfold—a stroll through Hyde Park, vows at the historic St. Paul’s Cathedral, and dancing under the stars at a Thames-side venue. But before the "I dos" and the first dance, there’s one detail that sets the scene: your wedding car. In a city where history meets modernity, your choice of wheels isn’t just transportation—it’s the opening act of your love story. Here’s how to find the perfect wedding car in London, whether you’re dreaming of vintage charm or sleek, 21st-century luxury.
- London’s Wedding Car Options: From Vintage Classics to Modern Marvels
London’s diverse vibe means you’re spoiled for choice. Here’s a breakdown of popular picks:
A. Vintage & Classic Cars
Best For: Traditional weddings, history lovers, or couples marrying at landmarks like Kensington Palace.
Top Picks:
Rolls-Royce Phantom (1960s): Timeless elegance with coach doors and a starlight headliner. Bentley S1 (1950s): Polished wood dashboards and leather seats for old-world glam. Austin Princess (Vintage): A British icon perfect for retro-themed weddings.
Cost: £500–£1,500+ for 6–8 hours.
Real-Life Romance: Sarah and James hired a 1950s Bentley for their Westminster Abbey wedding. “It felt like stepping into a royal procession,” Sarah said.
B. Modern Luxury Cars
Best For: Glamorous city weddings or receptions at venues like The Shard.
Top Picks:
Mercedes-Maybach S-Class: Heated massaging seats and ambient lighting.
Tesla Model X: Eco-friendly and futuristic, ideal for green-minded couples.
Range Rover Autobiography: Bold and spacious for urban chic.
Cost: £600–£2,000+ for full-day hire.
Pro Tip: Opt for a car with tinted windows if you’re navigating busy spots like Piccadilly Circus—privacy plus style!
C. Quirky & Unique Rides
Best For: Couples who dare to be different.
Top Picks:
London Black Cab (Decorated): Adorned with flowers for a playful, local twist.
Vintage Double-Decker Bus: Fit your entire bridal party (and a brass band!).
Electric Rickshaw: Zip through Covent Garden for a fun, eco-friendly entrance.
Cost: £200–£800 for shorter hires.
3.2. How to Choose Your London Wedding Car: 5 Key Factors
Don’t get overwhelmed—narrow your options with these tips:
Match Your Wedding Theme:
A vintage Rolls-Royce suits a classic church wedding.
A Tesla Model S pairs with a modern art gallery reception.
Consider Practicality:
Space: Ball gown? Choose a Bentley Mulsanne. Compact? Try a Jaguar E-Type.
Route: Narrow streets in Notting Hill? Avoid stretch limos.
Weatherproofing:
Convertibles are risky in London’s drizzle. Prefer a hardtop or ensure the hire includes a waterproof cover.
Sustainability:
Many companies now offer hybrid or electric cars (e.g., Tesla, BMW i7).
Budget:
Prioritize: Splurge on the ceremony car, then use a simpler ride for the exit.
Pro Tip: “We hired a vintage car for photos and a Tesla for the reception—best of both worlds!” —Laura, Hackney bride.
- Cost of Wedding Car Hire in London: What to Expect
London prices vary wildly, but here’s a rough guide:
Vintage Cars: £500–£1,500+ (includes chauffeur).
Modern Luxury: £600–£2,000+ (Maybachs at the higher end).
Unique Rides: £200–£1,000 (buses or themed vehicles).
Money-Saving Hacks:
Off-Peak Discounts: Book a weekday wedding for 10–20% off.
Bundle Deals: Some companies offer cars + photo booth or floral decor.
Short-Term Hire: Use the car for 3–4 hours (ceremony + photos only).
Watch For Hidden Fees:
Congestion Charge (£15/day for Central London).
Overtime charges (£50–£150/hour).
- Booking Your London Wedding Car: Step-by-Step
Start Early: Book 6–12 months ahead for peak season (June–September).
Read Reviews: Check Google and Hitched.co.uk for reputable companies.
Visit the Garage: Inspect the car in person—avoid surprises!
Confirm Details:
Backup vehicle clause.
Insurance coverage.
Decor permissions (e.g., floral hoops).
Red Flags:
No physical address or vague contracts.
Pressure to pay 100% upfront.
London Pro Tip: Use local companies like London Vintage Car Hire or Prestige Wedding Cars for better rates.
- Unique London Wedding Car Ideas
Make your ride unforgettable with these twists:
Thames-Side Photos: Park your Rolls-Royce near Tower Bridge for iconic shots.
Themed Decor: Add London Underground-inspired signage or Union Jack ribbons.
Surprise Stops: Arrange a quick champagne toast at Primrose Hill for skyline views.
Real-Life Magic: A couple from Camden hired a red London bus to shuttle guests from St. Pancras to their reception. “It was a party on wheels!” they shared.
Key Takeaways
🚗 Diverse Options: London offers everything from vintage Rolls-Royces to eco-friendly Teslas.
💷 Budget Smart: Prioritize, bundle, or book off-peak.
📅 Book Early: Secure your dream car 6–12 months ahead.
🌧️ Plan for Rain: Choose weather-appropriate vehicles.
📸 Photo Ready: Use London landmarks like the Thames or Kensington Gardens as backdrops.
FAQs About Wedding Car Hire in London
Q: How much does a wedding car cost in London?
A: From £200 for a decorated taxi to £2,000+ for a Rolls-Royce Phantom.
Q: Can we drive ourselves?
A: Rarely. Most luxury hires require a licensed chauffeur (and let you relax!).
Q: Are permits needed for photo locations?
A: Yes! Check with your photographer. Westminster Bridge requires permits for professional shoots.
Q: What if our car breaks down?
A: Reputable companies offer backup vehicles. Always ask!
Q: Can we personalize the car?
A: Yes—ribbons, flowers, or temporary decals. Avoid anything adhesive.
Final Thought: Your London Love Story Starts Here
At your wedding the transportation becomes more than just a method of getting from point A to point B but it creates the start of your lifetime story. The wedding car you select will leave an indelible mark in your memories as well as picture album forever because it can be a vintage Bentley near Big Ben or a flower-adorned bus with your friends onboard.
The streets of London will become the perfect backdrop when you choose your cars that trigger your heart's enthusiasm for your future eternal bond. Each romantic tale in this mesmerizing city ought to receive its definitive entrance.
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ e516ecb8:1be0b167
2025-04-11 15:07:04
@ e516ecb8:1be0b167
2025-04-11 15:07:04¿Qué es realmente la inflación? Si alguna vez has escuchado que la inflación es “la subida constante de precios”, no estás solo. Hace poco, un economista soltó esa definición en una entrevista, y otro, desde la Fundación para el Progreso (FPP), una institución que suele citar a pensadores como Mises o Hayek, repitió lo mismo. Suena lógico, ¿no? Pero están equivocados. Y ese error, aunque parezca pequeño, puede tener consecuencias catastróficas. Para entender por qué, no hace falta ir muy lejos: miremos a Argentina.
La subida de precios no es la inflación. Es solo el síntoma. La inflación, en esencia, es la pérdida del valor adquisitivo de la moneda. Confundir la causa con el efecto es como tratar una fiebre con un paño frío sin atacar la infección. Y cuando las políticas públicas se basan en esa confusión, el desastre está garantizado.
Argentina: una lección que duele Argentina es el caso de estudio perfecto. Antes de que Javier Milei llegara al poder en diciembre de 2023, la inflación en el país vecino estaba desbocada, alcanzando picos de 211% anual según datos del INDEC. El peronismo, convencido de que el problema eran los precios, implementó medidas como los “Precios Justos”, fijando topes artificiales. ¿Resultado? Escasez total. En un país famoso por su carne, los supermercados se quedaron sin ella. Los productores, enfrentados a costos que subían sin control, preferían exportar antes que vender localmente a precios que no les daban ni para cubrir gastos. Y ahí no terminó la cosa. En lugar de atacar la raíz del problema, el gobierno peronista complicó todo aún más: restringió exportaciones y creó un sistema surrealista de múltiples tipos de dólar (¡hasta uno distinto para Netflix!). Todo porque seguían peleando con el efecto, no con la causa.
¿Por qué los argentinos corrían a ahorrar en dólares y no en pesos? Porque el peso se devaluaba a una velocidad alarmante. Si la inflación fuera solo una cuestión de precios, habría afectado a todas las monedas por igual. Pero no. Como dice Milei una y otra vez, la inflación es un fenómeno monetario: demasiados billetes circulando sin respaldo o una moneda que la gente considera “de segunda” frente a otras.
¿Por qué seguimos repitiendo el error? Entonces, si la inflación es tan claramente un problema del valor de la moneda, ¿por qué seguimos escuchando que es una subida de precios? La respuesta es sencilla: culpar a otros es más fácil. Cuando se vende esa idea, los políticos pueden apuntar con el dedo a empresarios, comerciantes o “especuladores” y lavarse las manos. Es más cómodo que admitir una emisión monetaria irresponsable, un gasto público descontrolado o una pésima gestión económica. Y no faltan economistas, a veces financiados por grupos estatistas o formados en sistemas educativos que promueven esas ideas, que les hacen el coro.
Chile: por un pelo nos salvamos Este malentendido estuvo a punto de colarse en Chile. En el segundo intento de reforma constitucional, impulsado por Chile Vamos en 2023, se propuso que el Banco Central velara por la “estabilidad de precios”, no por la estabilidad del valor de la moneda. Parece un detalle técnico, ¿verdad? Pero no lo es. Ese cambio abría la puerta a políticas que podrían habernos llevado por el mismo camino que Argentina. Por suerte, aunque muchos expertos lo pasaron por alto, la ciudadanía no: la propuesta fue rechazada en las urnas con un contundente “En Contra”.
Nos salvamos, pero no porque nuestros políticos tuvieran las ideas claras. Nos salvamos porque los chilenos dijimos “basta”. Y menos mal, porque en 2024 la inflación en Chile se mantuvo controlada, rondando el 3,5% anual según el Banco Central, lejos del caos argentino. Pero no podemos confiarnos, porque esa inflación sigue siendo alta para nuestros estándares pre-pandémicos o pre-estallido social. El retiro desde las AFP convirtió activos en consumo, en otras palabras aumentó el circulante y todavía batallamos con esa inflación.
No es un “detallito” Cada vez que alguien diga que la inflación es una subida de precios o que la solución está en controlarlos, por favor, corrígelo. No es un error menor. Argentina lleva más de un año intentando salir del pozo que cavó este malentendido. Milei ha dado pasos importantes: transparentó la inflación real, ajustó el tipo de cambio para acercarse al valor de mercado y, aunque la inflación sigue alta (cerca del 50% anual a fines de 2024, según estimaciones), empieza a estabilizarse. Pero el camino es largo, y los costos de este “detallito” los pagan todos los argentinos.
¿Y ahora qué hacemos? La próxima vez que escuches a un político o un experto hablar de inflación como si fuera solo un problema de precios, no te quedes callado. Pregúntales: ¿y el valor de la moneda qué? Comparte esta historia, porque entender la inflación es el primer paso para no repetir los errores del pasado. En Chile esquivamos la bala, pero no podemos bajar la guardia. Los errores pequeños, cuando se trata de economía, terminan costándonos caro.
¿Qué opinas? ¿Crees que Chile aprendió la lección o estamos a un paso de tropezar otra vez? ¡Déja tu comentario y comparte este post si te hizo clic!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 2101a7ec:d9d8f2db
2025-04-11 14:50:45
@ 2101a7ec:d9d8f2db
2025-04-11 14:50:45Ghostty is terminal manager with GPU acceleration and great looks. It works mostly out of the box, but you might want to do some setups to tailor it to your particular needs.
Here is how I set it up.
Installation
I won't spend much time on installation details, I installed it using
brewthere are multiple installation options, surprisingly flatpack is not within the options at the moment. For further details please check ghostty installation instructions.Configuration
Config file is available on these locations
$HOME/Library/Application Support/com.mitchellh.ghostty/config$XDG_CONFIG_HOME/ghostty/configI use
$XDG_CONFIG_HOMEas I keep all my config there.Configuration reference is available on line. And can be generated from the command line doing
ghostty +show-config --default --docsAnd finally to list available themes
ghostty +list-themes.This is my config, it's available with my dotfiles
```config
~/.config/ghostty/config
to show the default configuration with documentation.
ghostty +show-config --default --docs
font-family = "JetBrains Mono"
font-size = 14
Run
ghostty +list-themesto browse available themes.theme = SynthwaveAlpha cursor-style = block
background-opacity = 0.96 background-blur-radius = 40
shell integration.
shell-integration = bash shell-integration-features = cursor, sudo, title
macos-titlebar-style = tabs
Auto-update Ghostty when a new release is available.
auto-update = download
mouse-hide-while-typing = true
keymaps
keybind = global:cmd+`=toggle_quick_terminal
keybind = cmd+left=previous_tab keybind = cmd+right=next_tab
byobu keybinds fix
macos-option-as-alt = left keybind = alt+left=unbind keybind = alt+right=unbind
quit-after-last-window-closed = true window-new-tab-position = end
```
I had some issues with SSH, so I added this to my
~/.ssh/configwhich fixed my issues.ssh Host * # ghostty https://ghostty.org/docs/help/terminfo SetEnv TERM=xterm-256color # end ghostty -
 @ 0b118e40:4edc09cb
2025-04-11 14:38:22
@ 0b118e40:4edc09cb
2025-04-11 14:38:22There’s an African proverb that says, “To get lost is to learn the way.”
Humans have always been explorers, searching for connection. To belong. To feel home. You can trace this instinct back to the start of our existence. Whether you start with Adam and Eve or the “Out of Africa” theory, the story is the same. We’ve always moved toward each other, building tribes and forming communities.
But somewhere along the way, something broke. With the rise of empires and organized control, religion and politics divided us into bubbles. We were sorted, labeled, and often pitted against one another. While technology advanced, something fundamental was lost. Our ability to truly connect started to fade.
Then came the internet, a modern-day Silk Road. It rekindled hope. Walls seemed to crumble, distances disappeared, and we dreamed of a truly connected world. For a time, it felt like the answer.
And then it wasn’t.
The history of Internet
The story began around 1830s when Charles Babbage started working on his computer prototype but without moolah he couldn't continue. A century later, after WW2 in the 1950s, the US Department of Defense funded what became known as modern computing.
Back then the military relied on systems like the Navajo Code Talkers. The indigenous code talkers were ingenious but operated under dangerous conditions, always on the frontlines.
In 1969, ARPANET made a revolutionary breakthrough as it connected four university computers for the first time. It was a big deal.
At that time, the internet was about openness. Researchers pushed for universal protocols. This gave rise to hacker culture that valued knowledge-sharing and keeping systems accessible to everyone.
In the 80s, NSFNET (National Science Foundation ) expanded these connections but kept it strictly for academic use only. That caused massive dissatisfaction.
Senator Al Gore pitched the concept of the “information superhighway,” to balance public access with private innovation. But by the 90s, the Clinton administration leaned into privatization. NSFNET’s infrastructure was completely handed off to private companies, and the internet grew into a commercial powerhouse.
The good news is that everyone has internet access now. Bad news is that what started as something free from government and commercial control became completely dominated by both.
Open source vs IP during the early internet days
This part of the story is about Bill Gates and Marc Andreessen.
Tim Berners-Lee invented the World Wide Web, but Marc saw the opportunity to make it user-friendly. He launched Netscape, an open-source browser. It drove the openness of internet culture. Netscape captured 90% of the market by giving its software away for free, and monetizing through other means.
Then came along Bill Gates. Microsoft back then was known for its aggressive tactics to monopolize industries. Gates licensed Mosaic’s code, created Internet Explorer, and bundled it for free with Windows 95. He wasn’t shy about playing dirty, even formed exclusive contracts with manufacturers to block competitors. Even the Department of Justice tried to file an antitrust lawsuit against Microsoft, but by then, it was too late. Netscape’s market share crumbled, and its position in the industry eroded.
Windows 95 brought the internet to the people globally, but it also closed it up.
Marc Andreeson started with open source ideologies, but is now funding altcoin projects.
The Californian ideology
Around this time, the term “Californian Ideology” started floating around. It was an unusual mix of libertarianism, techno-utopianism, and countercultural ideals. A marriage of cultural bohemianism (hippies) with high-tech entrepreneurship (yuppies). This ideology fused left-wing values like freedom of expression and direct democracy with right-wing beliefs in free markets and minimal government interference.
I absolutely love it.
Ironically, the term “Californian Ideology” wasn’t coined as a compliment. Richard Barbrook and Andy Cameron used it to piss on these visionaries for romanticizing the idea that the internet must remain a lawless, egalitarian space.
But many people loved and embraced the Californian ideology. Stewart Brand, who founded The Whole Earth Catalog, connected counterculture with early tech innovation. His work inspired people like Steve Jobs and Steve Wozniak. Steve Wozniak used to share Apple’s early schematics at the Homebrew Computer Club for feedback and collaboration.
EBay’s founder Pierre Omidyar envisioned eBay as a libertarian experiment. He believed the “invisible hand” of the market would ensure fairness. But as eBay grew, fraud, disputes, and dissatisfaction among users forced Omidyar to introduce governance which contradicted his goals.
And this story repeats itself over the years.
Platforms begin with libertarian visions, but as they scale, real-world challenges emerge. Governance (government, corporate charters, advertisers, and investors) is introduced to address safety and trust issues.
But they also chip away at the liberty the internet once promised.
Can Nostr be the solution ?
Yes.
But to appreciate Nostr, let’s first understand how the internet works today. (Note : I am no expert of this section but I'll try my best to explain)
The internet operates through four main layers:
- Application Layer (where apps like browsers, Google, or Zoom live)
- Transport Layer
- Internet Layer
- Network Access Layer
Let’s use a simple example of searching “Pink Panther” on Google.
Step 1: The Application Layer - You open your browser, type "Pink Panther," and hit search. This request is sent using HTTP/HTTPS (a protocol that formats the query and ensures it's secure).
Step 2: The Transport Layer - Think of your search query as a letter being sent. The Transport Layer breaks it into smaller packets (like splitting a long letter into multiple envelopes). TCP (Transmission Control Protocol) ensures all packets arrive and reassemble in the correct order.
Step 3: The Internet Layer - This layer acts like a postal service, assigning each device an address (IP address) to route the packets properly. Your device's IP (e.g., 192.168.1.10) and Google’s server IP (e.g., 142.250.72.238) help routers find the best path to deliver your packets.
Step 4: The Network Access Layer - Finally, the Network Access Layer physically delivers the packets. These travel as electrical signals (over cables), radio waves (Wi-Fi), or light pulses (fiber optics). This is the act of moving envelopes via trucks, planes, or postal workers, just much faster.
So how is data transmitted via Nostr ?
Nostr’s architecture of the Internet
Nostr reimagines the Application Layer while keeping the lower layers (Transport, Internet, and Network Access) largely unchanged.
In the traditional internet stack, the Application Layer is where platforms like Google or Twitter operate. It’s also where most censorship occurs due to single point of failure (centralised servers). Nostr flips this model on its head.
Technically, it’s like building a parallel internet that shares the same foundational layers but diverges at the top.
To borrow from Robert Frost:
"Two roads diverged in a wood, and I—
I took the one less traveled by,
And that has made all the difference."
For Nostr to fully realize its potential, it needs its own ecosystem of apps. Developers can build these tools within the Nostr protocol's framework
Let’s say there is a search engine on Nostr called Noogle.
Here’s how it works:
When you type "Pink Panther" on Noogle, your query is sent to multiple relays (servers) simultaneously. Each relay processes or forwards the query and returns results based on the data it holds.
As Nostr grows, the amount of information on relays will increase, giving Noogle more robust search results. But the biggest win is that compared to Google, Nostr's Noogle will have no ads, no surveillance, just pure, decentralized searching that respects your privacy.
For the transport layer, Nostr still relies on TCP/IP but enhances it with privacy and efficiency. Encrypted messages and simplified protocols enable faster real-time communication. The rest of the layer remains unchanged.
At its core, Nostr takes the internet back to its original ideals: open, uncensored, and decentralized.
Why Nostr matters ?
The internet we use today relies on centralized systems at the application layer. This creates a single point of failure where governments and corporations can control access, censor content, monitor activity, and even shut down entire platforms.
For example, the Malaysian government once proposed routing all web traffic through a centralized system, claiming it was for "security" reasons. In reality, this action allow those in power to block access to specific content or platforms that might threaten their positions.
Centralization weaponizes the internet.
It turns what was meant to be a tool for connection and freedom into a mechanism for control and oppression.
Let's look at DNS and ISPs as examples. DNS (Domain Name System) is like the phonebook of the internet. It helps translate website names (like example.com) into IP addresses so your browser can connect to them. ISPs (Internet Service Providers) are companies that give you access to the internet.
Both are controlled by centralized entities. If a government gains control of either, it can block specific websites or even shut down internet access entirely.
We've seen this happen repeatedly: * India’s internet shutdowns in regions like Kashmir * Turkey’s social media bans during political events * Ethiopia’s internet blackouts * China’s Great Firewall blocking major platforms like Google and Facebook * Even the US, where Edward Snowden revealed massive surveillance programs
This is where Nostr comes in, as the antidote to centralized control.
Instead of relying on centralized servers or platforms, Nostr creates a peer-to-peer network of independent relays. No single entity controls it. There is no central switch governments can flip to block access. If one relay is shut down, users simply connect to others in the network.
Nostr’s decentralized design makes it: * Resistant to censorship: Governments cannot easily block or filter content. * Privacy-preserving: Users can communicate anonymously, even in heavily surveilled environments. * Resilient: With no single point of failure, the network keeps running, even under attack.
And it gets better. Nostr can integrate with privacy tools like Tor to bypass restrictions entirely, making it nearly impossible for governments to stop.
The internet has become a battlefield for control, but Nostr provides a way to reclaim digital freedom. It empowers people to build, connect, and share without fear of being silenced.
How does Nostr overcome the "Californian Ideology" problems?
The Californian Ideology seemed like the blueprint for a utopian internet, libertarian ideals wrapped in Silicon Valley innovation. But as centralized platforms scaled, cracks started to show. Challenges like trust, safety, and accessibility forced governance teams to step in and decide “what’s best for the people.”
This resulted in platforms once built on ideals of freedom in becoming gatekeepers of control.
Nostr breaks this cycle. How?
1. Trust issues - With private keys, you control your identity and data. Moderation is decentralized. You can block or mute others at a personal level or through client tools, not by relying on a central authority. While this system needs refinement to be more user-friendly, it fundamentally shifts the power to users.
2. Funding Without Advertiser - Nostr’s integration of Bitcoin and the Lightning Network eliminates reliance on advertisers or corporate sponsors. Bitcoin enables anyone to contribute without gatekeeping. As more people join and apps mature, this model only gets stronger. For now, we have good souls like Jack seeding it.
3. Resisting Government Control - (refer to the above) Nostr avoids single points of attacks.
So what is Nostr ?
Nostr is internet
The new internet.
The open and free internet.
What can you build on Nostr?
Anything you have seen on the internet, you can recreate on Nostr. Anything you can imagine, you can bring to life here. It is a blank canvas for dreamers, builders, and changemakers.
But the best part is this. You have Bitcoin as its financial backbone. This changes the game entirely.
And with new games, comes new rules. New vibes. New ways.
The way people use this new internet will be different from the traditional internet as control falls back to the people. With Bitcoin as the underlying backbone, the business models will be different.
But there is more to it than just creating. There's that joy of creation, where we invite curiosity and inspire users to experience something new, something revolutionary.
Have you watched “The Last Lecture” by Randy Pausch?
He coined the term “head fake.” He taught his students programming, but not everyone was excited to learn programming. So he created fun projects and performances that pulled them in. The students had so much fun, they didn’t even realize they were learning to code.
What you build on Nostr is that head fake. The apps and projects you create draw people in with fun and utility, subtly reminding them they have a right to their own voice and thoughts.
The work you’re doing is so precious. When everything feels like doom and gloom, it’s these kinds of projects that give people hope.
Through Nostr, you’re making a difference. One project, one connection at a time.
The new Internet era
Centralized systems, like empires of the past, eventually crumble under the weight of their control. Decentralization provides a different path. It is a modern revival of our primal instincts to explore, connect, and build tribes.
By definition, Nostr is a protocol. I think more so, it's a philosophy. It challenges us to rethink how we share, communicate, and create. It is the internet as it was meant to be. Free, open, and governed by no one.
The beauty of Nostr lies in its simplicity. It does not rely on massive infrastructure, corporate giants, or government oversight. It thrives on community, much like the early tribes that defined humanity.
We have come full circle. From wandering continents to building roads, bridges, and networks, our journey has always been about connection and finding our tribe.
As the African proverb reminds us, 'To get lost is to learn the way.' There is finally a way now.
But at the end of the day, it’s entirely up to you what kind of world you want to be part of.
Find your tribe. Build the future. Love them hard.
More info :
On those who played a role in the history of internet and computers
https://hiddenheroes.netguru.com/ -
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ 34ff86e0:dbb6b9fb
2025-04-11 14:35:59
@ 34ff86e0:dbb6b9fb
2025-04-11 14:35:59Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum
-
 @ 1bc70a01:24f6a411
2025-04-11 13:50:38
@ 1bc70a01:24f6a411
2025-04-11 13:50:38The heading to be
Testing apps, a tireless quest, Click and swipe, then poke the rest. Crashing bugs and broken flows, Hidden deep where logic goes.
Specs in hand, we watch and trace, Each edge case in its hiding place. From flaky taps to loading spins, The war on regressions slowly wins.
Push the build, review the log, One more fix, then clear the fog. For in each test, truth will unfold— A quiet tale of stable code.
This has been a test. Thanks for tuning in.
- one
- two
- three
Listen a chillTranquility
And leisure
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:21:48
@ bf95e1a4:ebdcc848
2025-04-11 11:21:48This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:18:42
@ bf95e1a4:ebdcc848
2025-04-11 11:18:42This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 7d33ba57:1b82db35
2025-04-11 10:08:21
@ 7d33ba57:1b82db35
2025-04-11 10:08:21Rome isn’t just a city—it’s a living, breathing museum where ancient ruins, baroque fountains, and buzzing piazzas come together in beautiful, chaotic harmony. Every cobblestone has a story, every espresso has a punch, and every sunset behind the Colosseum feels like a scene from a movie. Whether it's your first visit or your fifth, Rome never gets old.
🏛️ Top Things to See & Do in Rome
1️⃣ The Colosseum & Roman Forum
- Step inside the iconic arena of gladiators
- Wander through the ruins of the Forum, once the heart of ancient Rome
- Don’t miss Palatine Hill for views over it all
2️⃣ Vatican City
- Home to St. Peter’s Basilica, the Sistine Chapel, and the Vatican Museums
- Climb to the top of the basilica dome for one of the best panoramas in Rome
- Book tickets ahead—it gets packed!
3️⃣ Trevi Fountain
- Toss in a coin to ensure your return to Rome 💧
- Visit early in the morning or late at night to beat the crowds and get that perfect photo
4️⃣ Pantheon
- One of the best-preserved Roman temples—free to enter, awe guaranteed
- Look up: the open oculus in the dome is engineering genius
- Step outside for a coffee in Piazza della Rotonda
5️⃣ Piazza Navona & Campo de’ Fiori
- Piazza Navona: Elegant fountains, artists, street performers
- Campo de’ Fiori: Bustling morning market and lively nightlife
- Great spots to grab an aperitivo or soak up atmosphere
🍕 What to Eat in Rome
- Cacio e Pepe – Pasta with pecorino and black pepper—simple, bold, and pure Rome
- Carbonara – No cream! Just egg, cheese, guanciale, and pepper
- Supplì – Deep-fried rice balls with melted mozzarella inside
- Roman-style pizza – Thin and crispy, often sold by weight
- Gelato – Try real artisan shops like Gelateria del Teatro or Otaleg
🌇 Bonus Rome Moments
- Watch sunset from Pincian Hill or Gianicolo Terrace
- Stroll across the Tiber River to the charming Trastevere neighborhood
- Visit the Jewish Ghetto for history, architecture, and amazing food (hello, fried artichokes!)
- Wander without a map—Rome loves surprising you
🛵 Tips for Visiting
✅ Wear comfy shoes—Rome’s cobbles are beautiful, but brutal on feet
✅ Book major attractions in advance to skip lines
✅ Tap water is fresh—refill from Rome’s historic fountains (nasoni)
✅ Don’t rush—Rome is best enjoyed slowly, with a gelato in hand -
 @ fbf0e434:e1be6a39
2025-04-11 08:12:20
@ fbf0e434:e1be6a39
2025-04-11 08:12:20Hackathon 概要
Cambrian Hack 是一场最近的在线比赛,旨在吸引开发人员使用 Cambrian SDK 和 Jito Restaking 开发 Node Consensus Networks (NCNs)。此次活动吸引了88位注册开发人员,最终产生了九个批准项目。参与者专注于快速部署 NCN,探索如 AI 协处理器、预言机网络和区块链桥梁等应用。Hackathon 结束时,Cambrian 和 Jito 团队为前三名项目颁发了奖项。奖池的一部分包括 Cambrian 奖励 NFT,可以转换为 Cambrian 代币。
此次 Hackathon 强调了 Cambrian SDK 通过简化流程加速 NCN 开发的能力,减少了对大型团队的需求,并提供了预建组件。评估标准包括技术复杂性、市场潜力和创新性。
活动以在 Solana Apex 开普敦宣布获奖者而告终。Cambrian Hack 为开发者提供了与技术专家联系的机会,通过工作坊提升技能,并对 web3 和 Solana 生态系统的发展做出贡献。
Hackathon 获奖者
Cambrian NCN Builder 卓越奖获奖者
- Ping Project: 该项目通过在 Solana 区块链上使用 PoS 共识以及 Cambrian SDK 和 Jito Restaking 技术,强化网络完整性并管理奖励分配,提供去中心化的内容传递服务。
- Ant Vault: 结合 ElizaOS AI 代理与 Cambrian oracle 战略性管理 DeFi,提供智能化市场挑战解决方案。
- STABLE-FUNDS: Solana 上的平台,用于创建稳定币,集成去中心化预言机和质押机制,以连接政府支持的证券和 DeFi。
Cambrian 生态系统创新者奖获奖者
- NebulaCDN: 一种去中心化的内容传递网络,利用 Web3 技术提供高效且抗审查的数据分发。
- Kamui: 一个经济高效、安全的 Solana VRF oracle,旨在提供可靠且负担得起的随机性解决方案。
有关更多详情,请访问 Cambrian Hack BUIDL。
关于组织者
Cambrian
Cambrian 因其对技术和区块链发展的贡献而受到认可。该组织专注于创新区块链应用,已进行多项项目以提升数字基础设施。其成就包括与行业领袖合作开发安全高效的区块链系统。Cambrian 目前正在扩展其对去中心化技术的关注,努力提升不同平台的可访问性和安全性。通过其专业知识,Cambrian 在不断演变的技术和区块链产业中扮演着重要角色。
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ fbf0e434:e1be6a39
2025-04-11 08:05:01
@ fbf0e434:e1be6a39
2025-04-11 08:05:01Hackathon 概要
Core Global Gaming Hackathon 圆满落幕。作为去中心化游戏领域的重要活动,其吸引了众多参与者。在 231 位注册开发者中,86 个项目获得批准,所有项目共同竞逐 38 万美元的奖金池。此次黑客松鼓励在 Bitcoin 与 Core 平台上进行游戏开发,着重强调去中心化游戏的创新。
活动通过激发参与者拓宽去中心化游戏开发的视野,催生出一系列创新参赛作品。它为开发者搭建了与活跃社区互动的平台,既能激发创意,也可能对游戏未来发展方向产生影响。
活动取得了显著成果,例如将 Core Chain 技术融入游戏应用,展现了利用去中心化平台的独特思路。2025 年 3 月 24 日,活动以 Demo Day 收官,现场展示最终项目并公布获奖者。总体而言,这场黑客松凸显了区块链技术在游戏领域的潜力,也体现了开发者们力求影响行业发展的合作精神。
Hackathon 获奖者
超休闲游戏奖获奖者
- Farming Saga:一款专注于建立农业帝国的策略和模拟游戏,特色为动态挑战和NFT整合以丰富游戏玩法。
- Zenista:一款闲置游戏,旨在通过经营虚拟水疗中心提供放松体验,设计用于提供自我护理体验。
- Market Magnate:一款零售模拟游戏,结合区块链实现真正的资产所有权,强调策略、创意和管理。
社交游戏PvP(玩家对玩家)奖获奖者
- Core Arena:一款PvP游戏,允许在战斗中使用任何ERC-721 NFT,并自动分配技能,促进NFT社区间的统一并延长项目生命周期。
- Fight For Tcore:一款基于区块链的实时PvP游戏,玩家参与双人对决并下注TCORE代币,利用智能合约实现去中心化游戏玩法。
- CoreVerse Battleground:一款实时多人区块链游戏,提供NFT交易和基于Core Blockchain的游戏内货币。
益智游戏奖获奖者
- Temporal Odyssey:一款基于区块链的益智游戏,提供跨越多样世界的解谜NFT奖励。
- Dungeon:提供程序生成的地牢探险体验,结合区块链元素,允许玩家将成就铸造成Dungeon Tokens ($DGN)。
- Skateflow:一款无尽滑板游戏,实施区块链技术实现潜在的游戏内奖励。
欲了解所有项目的更多详细信息,请访问Core Gaming Hackathon 页面。
关于组织者
Core DAO
Core DAO是一个专注于推进区块链技术的去中心化自治组织。其主要关注点在于增强去中心化和促进区块链生态系统中的社区驱动治理。Core DAO因其对开发创新共识机制和智能合约解决方案的贡献而受到认可。该组织采取重大措施以提高去中心化网络的可扩展性和安全性。目前,Core DAO致力于培育开放、包容的区块链环境,倡导技术进步,并支持社区主导的开发举措,以促进去中心化技术的全球采用。
-
 @ b8af284d:f82c91dd
2025-04-07 07:09:50
@ b8af284d:f82c91dd
2025-04-07 07:09:50
"Auf den deutschen Konten, Sparkonten und laufenden Girokonten liegen 2,8 Billionen Euro. Stellen Sie sich einen kurzen Augenblick vor, wir wären in der Lage, davon nur 10 Prozent zu mobilisieren – mit einem vernünftigen Zinssatz, für die öffentliche Infrastruktur in Deutschland […]”
Friedrich Merz, Blackrock-Aufsichtsratvorsitzender 2016-2020
„Governments can’t fund infrastructure through deficits. The deficits can’t get much higher. Instead, they’ll turn to private investors.“
Liebe Abonnenten,
im Jahr 1999 lag der durchschnittliche Bruttolohn eines deutschen Arbeiters bei monatlich 2100 Euro. 26 Jahre später sind es etwa 4200 Euro. In diesem Zeitraum sind die Löhne also durchschnittlich jedes Jahr um 2,7 Prozent gewachsen. (Um die Reallöhne, also die tatsächliche inflationsbereinigte Kaufkraft soll es ausnahmsweise einmal nicht gehen.)
Im selben Zeitraum ist die globale Wirtschaftsleistung um fünf Prozent im Jahr gewachsen. Der amerikanische Aktien-Index S\&P500 legte durchschnittlich jedes Jahr um acht Prozent zu.
Die Unterschiede klingen zunächst gering. 2,7 Prozent, 5 Prozent, 8 Prozent - Peanuts, was soll’s? Deutlich werden die Bedeutung dieser Zahlen, wenn man sie in absolute Zahlen umlegt. Bei einem Zuwachs von durchschnittlich fünf Prozent würde selbiger Arbeiter heute 7560 Euro verdienen. Wäre sein Lohn so stark gestiegen wie der S\&P500, läge er bei 15.483 Euro.
Das Unternehmen Blackrock ging im Jahr 1999 an die Börse. Die jährlichen Kurssteigerungen der Aktie liegen durchschnittlich bei 21 Prozent. Aus den 2100 Euro wären damit 334.661 Euro geworden.
Nimmt man nur den Gewinn des Unternehmens, landet man bei etwa zehn Prozent Rendite nach Steuern.
Irgendwie also wächst der Finanzmarkt schneller als Löhne, und Blackrock wächst nochmals schneller als der Finanzmarkt. Wie kann das sein? Was macht Blackrock, für die bis vor wenigen Jahren der künftige Bundeskanzler Friedrich Merz tätig war?
Ein Blackrock-Deepdive:
Blackrock - the bright side
1988 gründete Larry Fink zusammen mit einer Gruppe von Mitarbeitern “Blackstone Financial Management”. Die Firma wurde 1992 in Blackrock umbenannt und ging 1999 an die Börse. Zehn Jahre später übernahm die Firma Barclays Global Investors (BGI). Letztere brachte die Marke „ishares“ mit ins Portfolio. Zum Kerngeschäft von Blackrock gehören seitdem ETFs - die vielleicht beliebteste Anlageklasse der Welt.
ETFs sind keine Erfindung von Blackrock, aber das Unternehmen hat viel dazu beigetragen, dass ETFs heute in fast jedem Portfolio zu finden sind. Bevor es ETFs gab, konnten Kleinanleger fast nur in aktiv gemanagte Fonds investieren. Dabei kaufen und verkaufen hochbezahlte Analysten Aktien und verlangen dafür eine Gebühr von zwei Prozent. Bei ETFs liegen diese im Promillebereich. Eine Gebühr von zwei Prozent mag vernachlässigbar klingen. Über die Jahre aber macht dies einen Riesenunterschied - wie das Beispiel des Bruttolohns zeigt.
Hinzu kommt: Statistisch laufen passive Indexfonds oft besser als aktiv geleitete Investmentfonds.
Blackrock ist es mit seinen ETFs gelungen, die Geldanlage zu demokratisieren. Das Unternehmen profitiert nicht von steigenden Kursen der Aktien, sondern kassiert minimale Gebühren beim Kauf und Verkauf - aber bei einem verwalteten Vermögen von 4,5 Billionen Dollar kommt eben schnell etwas zusammen. 1989 hatten nur rund 30 Prozent der Amerikaner Aktien, heute sind es über 60 Prozent. In Deutschland liegt der Anteil bei nur 15 Prozent.
Niemand muss mehr um Lohnerhöhungen bangen - er kann von der annualisierten Wachstumsrate von acht Prozent (S\&P500) profitieren, wenn er jeden Monat in Blackrock-ETFs investiert. Selber Schuld, wer nicht!
Blackrock - the dark side
Wer die letzten Jahre nicht völlig außerhalb des Schwurbelversums verbracht hat, wird mitbekommen haben, dass Blackrock Thema zahlreicher Verschwörungstheorien ist. Von Covid über die Rüstungsindustrie bis zum Wiederaufbau der Ukraine. ETFs sind tatsächlich nicht das einzige Geschäftsmodell. Hinzu kommt eine weniger transparente Vermögensverwaltung von rund sieben Billionen Dollar. Kunden sind neben Unternehmen und Familien auch ganze Staaten. Außerdem ist Blackrock Großaktionär bei tausenden von Unternehmen. Es hält große Anteile von Apple, Microsoft, Nvidia aber auch von Vonovia, Bayer und der Deutschen Bank. Und über diese Beteiligungen übt das Unternehmen Macht aus. Das bekannteste Beispiel sind ESG-Kriterien (Environmental, Social, Governance), die Larry Fink ab 2018 propagierte. Mittlerweile ist Fink davon abgerückt, im aktuellen Jahresbrief ist davon wenig zu lesen. Das eigentliche Problem sitzt tiefer, und hat mit der Rendite zu tun.
Was hat Blackrock vor?
Zehn oder 20 Prozent Wachstum sind über einen langen Zeitraum kaum realistisch zu erwirtschaften. Dafür braucht es „Megatrends“. Künstliche Intelligenz zum Beispiel verspricht Produktivitätsgewinne, die weitaus über der Norm liegen. Was aber, wenn diese ausbleiben? Lässt sich eventuell etwas nachhelfen?
Am bequemsten ist es, wenn Regierungen Steuergelder in Richtung Unternehmen verschieben. Dann sparen sich die Profiteure auch noch die Werbekosten. Was, wenn eine Regierung ein großes Investitionsprogramm auflegt, von dem dann Unternehmen profitieren, in die Blackrock frühzeitig investiert hat? Was, wenn mehrere Regierungen dies gleichzeitig tun? Nun kann man sich fragen, bei welchen Komplexen dies zuletzt der Fall war. Blackrock hält ungefähr sieben Prozent der Pfizer-Aktien und rund ein Prozent von Biontech. Etwa fünf Prozent von Rheinmetall-Aktien sind…
Weiter geht es auf BlingBling - dem wöchentlichen Newsletter über Geld, Geopolitik und Bitcoin
-
 @ f57bac88:6045161e
2025-04-11 08:00:16
@ f57bac88:6045161e
2025-04-11 08:00:16مقدمه\ کتاب پول درهمشکسته نوشته لین الدن، یکی از برجستهترین آثار در زمینه اقتصاد و فناوری مالی است که در تابستان ۱۴۰۲ (۲۰۲۳ میلادی) منتشر شد. این کتاب با نگاهی عمیق به ریشههای پول، کاستیهای نظام مالی کنونی و ظرفیتهای فناوریهای نوین مانند بیتکوین، خوانندگان را به سفری فکری دعوت میکند. الدن با زبانی روان و دیدگاهی چندجانبه، پیچیدگیهای پول را به شکلی ساده اما پرمغز توضیح میدهد و به ما کمک میکند تا درک بهتری از چیستی پول، نقش آن در زندگی و آیندهاش به دست آوریم. این اثر ۵۳۸ صفحهای، با ساختاری جامع، گذشته، حال و آینده پول را در شش بخش اصلی بررسی میکند.
بخش اول: گذشته پول – از دفترهای قدیمی تا بانکداری نوین\ الدن داستان تکامل پول را در دو بخش ابتدایی کتاب روایت میکند. او پول را بهعنوان یک «دفتر حسابداری» معرفی میکند که از ابتدا برای ثبت بدهیها و طلبها در جوامع به کار میرفت. بخش اول به بررسی پولهای کالایی مانند صدف و فلزات گرانبها و ویژگیهای ایدهآل پول میپردازد. بخش دوم به ظهور خدمات بانکی اولیه و بانکداری گسترده اختصاص دارد و نشان میدهد که چگونه فناوریهایی مانند تلگراف در قرن نوزدهم تراکنشها را سریعتر کردند. اما این پیشرفتها، به گفته الدن، با متمرکز شدن کنترل پول در دست بانکهای مرکزی، اغلب به زیان مردم عادی تمام شدند و شکاف طبقاتی را عمیقتر کردند.
بخش دوم: حال پول – چرا سیستم مالی کنونی شکسته است؟\ در دو بخش بعدی، الدن به نقد نظام مالی کنونی میپردازد که بر پایه پول بیپشتوانه (فیات) بنا شده است. او استدلال میکند که این سیستم با مشکلاتی مانند تورم مداوم، نابرابری اقتصادی و سلطه بیشازحد نهادهای مالی دستبهگریبان است. بخش سوم به نظام مالی جهانی از اوایل قرن بیستم، از جمله نظام برتون وودز، میپردازد. بخش چهارم خلق پول مدرن و تأثیرات بدهیهای بیثباتکننده را تحلیل میکند. الدن معتقد است که پول بیپشتوانه بهگونهای طراحی شده که ارزش آن بهمرور کاهش مییابد و ثروت را از جیب مردم عادی بهسوی بانکها و شرکتهای بزرگ هدایت میکند. او با مثالهایی واقعی، مانند بحران اقتصادی لبنان در سال ۱۴۰۱ (۲۰۲۲) یا تورم افسارگسیخته در کشورهایی مانند ترکیه، آرژانتین و ایران، نشان میدهد که این مشکلات چگونه زندگی میلیونها نفر را تحت تأثیر قرار دادهاند.
بخش سوم: آینده پول – نقش نوآوریهای دیجیتال\ در دو بخش پایانی، الدن به بررسی فناوریهای نوین مالی، بهویژه بیتکوین و بلاکچین، میپردازد. بخش پنجم به نوآوریهای دیجیتال قرن بیستویکم، مانند بیتکوین، اختصاص دارد که الدن آن را یک دفتر حسابداری غیرمتمرکز میبیند. این فناوری میتواند قدرت را از نهادهای مرکزی خارج کرده و به افراد بازگرداند. بخش ششم به اخلاقیات پول و نقش رمزنگاری در شبکههای مالی میپردازد و آیندهای را تصور میکند که در آن افراد کنترل بیشتری بر داراییهای خود دارند. بااینحال، الدن به چالشهای بیتکوین، مانند نوسانات شدید قیمت، مصرف بالای انرژی و مشکلات مقیاسپذیری، نیز اشاره میکند. او همچنین به نمونههایی از استفاده بیتکوین در کشورهای درحالتوسعه، مانند السالوادور، اشاره دارد که این ارز بهعنوان ابزاری برای دور زدن محدودیتهای مالی به کار گرفته شده است.
نقاط قوت کتاب\ ۱. سادگی در عین عمق: الدن مفاهیم پیچیدهای مانند تورم، نظام بانکی و بلاکچین را با زبانی قابلفهم برای همگان توضیح میدهد، بدون آنکه از دقت علمی کاسته شود.\ ۲. دیدگاه چندرشتهای: او با ترکیب دانش مهندسی و تحلیل مالی، پول را بهعنوان یک فناوری بررسی میکند که با پیشرفتهای بشری تکامل مییابد.\ ۳. تمرکز بر انسانها: کتاب تنها به آمار و ارقام بسنده نمیکند؛ الدن نشان میدهد که نقصهای نظام مالی چگونه زندگی واقعی مردم را تحت تأثیر قرار داده است.\ ۴. بیطرفی نسبی: اگرچه الدن از طرفداران بیتکوین است، تلاش میکند با بررسی جنبههای مثبت و منفی هر سیستم، از یکجانبهگرایی پرهیز کند.
نقاط ضعف کتاب\ ۱. تمرکز بیشازحد بر بیتکوین: برخی معتقدند که الدن بیشازحد به بیتکوین خوشبین است و به دیگر فناوریهای مالی نوین، مانند اتریوم یا استیبلکوینها، کمتر پرداخته است.\ ۲. پیچیدگی برای تازهکارها: هرچند کتاب برای مخاطب عام نوشته شده، برخی بخشها ممکن است برای افرادی که هیچ آشنایی با اقتصاد یا ارزهای دیجیتال ندارند، دشوار باشد.\ ۳. کمبود راهحلهای عملی: الدن در شناسایی مشکلات موفق است، اما راهحلهای پیشنهادی او گاهی کلی و غیرملموس به نظر میرسند.
چرا این کتاب را بخوانیم؟\ پول درهمشکسته برای هرکسی که میخواهد بداند پول چیست، چرا ارزشش تغییر میکند و آیندهاش چه خواهد شد، یک راهنمای بینظیر است. این کتاب به ما کمک میکند تا به چیزهایی که بدیهی میپنداریم—مانند اسکناسی که هر روز خرج میکنیم—عمیقتر نگاه کنیم. برای خوانندگان ایرانی، که سالهاست با تورم، کاهش ارزش پول ملی و تحریمهای مالی دستوپنجه نرم میکنند، این کتاب پاسخهایی روشنگر به سؤالهایی مانند «چرا پول ما بیارزش میشود؟» یا «آیا راهی برای محافظت از داراییها وجود دارد؟» ارائه میدهد. ساختار ششبخشی کتاب، با پوشش جامع گذشته، حال و آینده، خواننده را به درک کاملی از پول و قدرت آن هدایت میکند.
جمعبندی\ پول درهمشکسته بیش از یک کتاب اقتصادی است؛ دعوتی است به تأمل و تغییر. لین الدن با دانش، دقت و نگاهی انسانی، ما را به سفری از گذشته پول تا آیندهاش میبرد و نشان میدهد که چگونه میتوانیم با آگاهی و انتخابهای درست، بهسوی سیستمی عادلانهتر حرکت کنیم. این کتاب برای هرکسی که به اقتصاد، فناوری یا عدالت اجتماعی علاقهمند است، اثری ضروری و الهامبخش به شمار میرود.
منابع و دسترسی به ترجمه\ بخشهایی از این کتاب به فارسی ترجمه شده و از طریق کانالهای تلگرامی مانند «ترجمهی مقالههای بیتکوین» در دسترس است. برای یافتن ترجمه، میتوانید عبارت «پول درهمشکسته» یا نام نویسنده را در این کانال جستجو کنید. همچنین، پیشنهاد میشود برای ادامه این مسیر و فرهنگ از مترجم و مدیر کانال ترجمه مقالات حمایت مالی کنید
-
 @ da0b9bc3:4e30a4a9
2025-04-11 07:02:54
@ da0b9bc3:4e30a4a9
2025-04-11 07:02:54Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/940429
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ 34ff86e0:dbb6b9fb
2025-04-11 03:51:31
@ 34ff86e0:dbb6b9fb
2025-04-11 03:51:31test description 2 lang arabic
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ 9a1adc34:9a9d705b
2025-04-11 01:59:19
@ 9a1adc34:9a9d705b
2025-04-11 01:59:19Testing the concept of using Nostr as a personal CMS.
-
 @ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40
@ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40It’s often said that 'Bitcoin doesn’t need marketing'—and the internet proves it well, almost like a daily feed. Instead of typical ads in the form of 'sell-me-anything-and-everything', the space thrives on organic memes and threads: a grassroots testament to Bitcoin ethos.
This isn’t about the artificial promotion of THE TRUMAN SHOW, where desires are manufactured and ads dictate specific behaviours. Bitcoiners don’t just reject the Proof-of-Hype, so typical in a fiat-driven world, they replace it with Proof-of-Work: value emerging not from coercion, but from consensus (i.e., what the community validates as genuine and meaningful).
The "Funny Money" Crew
On the other hand, equally common is the twist with memes labeled 'Bitcoin’s Marketing Team', featuring faces like:
🤡 Jerome Powell (Fed Chair), Christine Lagarde (ECB), Agustín Carstens (BIS chief, CBDC pusher), Janet Yellen (U.S. Treasury Secretary), Jamie Dimon (JPMorgan CEO), Elizabeth Warren (U.S. Senator), and so on.
Sophisticated jokes—appreciated by those who understand their actual impact. After all, what better advertisement for Bitcoin could there be than watching the fiat system degrade in real time? 😎
Why Bring This Up?
First, because I want to remind that Bitcoiners weaponize even simple ideas better than entire Wall Street-hired PR firms. Every "Bitcoin doesn’t need marketing" or "Thanks, Fed for the free promo!" is a clever, almost subversive way of raising topics we should be aware of. Exposing fiat’s failures often speaks louder than directly evangelizing how sound Bitcoin is—and how well it solves problems that keep many non-coiners awake at night.
Second, to credit where it’s due: Bitcoin-only projects and individuals who are actively spreading the word—hard money, real solutions, and the culture itself. But this isn’t 'marketing' in the traditional, pushy, profit-at-all-costs sense. Instead, it’s built on:
- Information (no bullshit, just facts)
- Education (orange-pilling, not upselling)
- Community (value, instead of dry PR)
- Creativity (proof-of-mind, not algo-baits)
- Experiences (how-to solutions, not showing off)
And let’s be clear: Earning money isn’t evil—it’s necessary for these projects to survive. What matters is the intention. No one should apologize for creating Bitcoin-themed ads, so long as they’re carrying the meaning, instead of being rooted in hype.
PoW: Earning Attention, Not Buying It
The list below (part one) is based on my own preferences, but it was also inspired by Bitcoin FilmFest, which—in its upcoming edition #BFF25, May 22-25—introduced a new block to the program: ‘BFF PoWies: The Show for Bitcoin-Only Advertising.’ A dedicated space for creative expression beyond films, where projects and individuals compete for awards in categories like Grand Prix, Best Visual, and Best Identity—with a $4,500 prize pool to grab.
Anyways, as our small but passionate team dug into this topic, I was really happy to uncover unique video ads, some of which I’m excited to share with you now.
If you know others, tag me (private profile) or 'Bitcoin FilmFest' directly on socials. Feel free to submit your work to the PoWies too (submissions close May 6th).
Without further ado... Let's explore the space where value is discovered, not packaged in empty promises 📺👇
Bitcoin-Video Ads: Part One.
Creative, funny, dynamic, inspirational. All four below. Enjoy!
1/. NEVER LOSE YOUR BITCOIN (Liana)
https://v.nostr.build/P7To0HpNmmB6iudR.mp4
2/. MAKE A CHANGE, (Wasabi)
https://v.nostr.build/rUGQAysAIDH8Wx9x.mp4
3/. THE MOTHER OF ALL BACKUPS (Cryptosteel)
https://v.nostr.build/3zesnSjQudQoxl5f.mp4
- FINANCIAL FALLOUT (21 Futures)
https://v.nostr.build/sFvmt8oCWfxLKJRb.mp4
PS. The most effective Bitcoin ads aren't 'typical' campaigns—they're the result of creativity, PoW, and authentic storytelling move hand-in-hand.
BTC Your Mind. Let it Beat... Şela
-
 @ ac58bbcc:7d9754d8
2025-04-10 20:00:41
@ ac58bbcc:7d9754d8
2025-04-10 20:00:41Research highlights the importance of using visual representations and precise language to develop students’ conceptual understanding of fractions.
Fractions are a cornerstone of mathematics education, essential for developing robust number sense and laying a solid foundation for algebra and more advanced mathematical pursuits. Despite their significance, fractions present persistent and considerable challenges for numerous learners. This research overview synthesizes key insights from the literature, focusing on the prevalent misconceptions, specific difficulties students encounter, and evidence-based instructional practices promoting a deeper, more conceptual grasp of fractions. This overview aims to equip educators with the knowledge and strategies necessary to foster student success in this critical area by examining the cognitive obstacles and exploring effective teaching approaches. Traditional instruction in fractions often falls short of promoting meaningful understanding, frequently emphasizing procedures and algorithms at the expense of conceptual development (Lamon, 2001).

Understanding the Complexities
Developing a robust understanding of fractions is far from straightforward. Students encounter a variety of conceptual hurdles that can hinder their progress. Research identifies several overarching conceptual challenges that contribute significantly to these difficulties, each stemming from misunderstandings about the nature of fractions and their relationship to other mathematical concepts.
Core Conceptual Challenges
One of the most fundamental challenges is conceptualizing fractions as numbers with magnitude and understanding their position on the number line (Simon et al., 2018). Many students struggle to see fractions as more than parts of a whole, failing to grasp that they represent quantities that can be ordered, compared, and operated on, much like whole numbers. This requires understanding that fractions have a specific location and value on the number line, just as whole numbers do.
A common misconception involves applying whole number rules inappropriately to fractions. For instance, students may believe that a fraction with a larger denominator is always larger or that adding numerators and denominators is the correct way to add fractions. This stems from the tendency to apply additive thinking, appropriate for whole numbers, to multiplicative situations involving fractions.
Grasping fraction equivalence—that different fractions can represent the same quantity (Simon et al., 2018)—is a significant hurdle. It requires recognizing that a fraction can be partitioned into smaller, equivalent units and that multiplying or dividing the numerator and denominator by the same non-zero number results in an equivalent fraction.
Performing arithmetic operations with fractions, notably addition and subtraction with unlike denominators, presents challenges due to a lack of understanding of the roles of numerators and denominators and the necessity of common units (denominators). This requires understanding the concept of common denominators, emphasizing that these represent the same-sized units.
Specific Difficulties
Beyond the broad conceptual challenges, students often grapple with more specific difficulties that stem from limited or flawed understandings:
Many students view fractions as deriving from fractions solely as parts of a whole divided into n equal pieces (n/n). This can hinder their ability to conceptualize improper fractions, as having more parts than the "whole" seems illogical (Simon et al., 2018; Stafylidou & Vosniadou, 2004). This limited view restricts their understanding of fractions to only those less than one, making it challenging to work with mixed numbers and other more complex fraction concepts.
Some students conceive of fractions (m/n, where m<n) solely as an arrangement where a whole is divided into n identical parts, and m parts are designated. They do not understand 1/n or m/n as a quantity, measure, or amount. Based on this limited notion, 1/n and m/n have no meaning when not included as parts in a whole partitioned into n identical parts (Behr, Harel, Post, & Lesh, 1992; Mitchell & Clarke, 2004; Simon, 2006; Simon et al., 2018).
Students often struggle with the concept of a referent unit, understanding a fraction only as a part of the presented totality. The difficulty arises when the referent unit is greater or less than that totality (Simon et al., 2018; Tzur, 1999). Understanding of referent units is generally not emphasized in the development of whole numbers; when whole number development is based on counting, the unit is generally left implicit. This also includes understanding that fractions can represent the same quantity or relationships (ratios) depending on the context and the considered unit.
Effective Instructional Strategies and Representations
Instruction must focus on conceptual development, utilize varied representations, and employ precise language to address the challenges and promote deep understanding.
Building Conceptual Understanding
Traditional "part-whole" language can be limiting. Brendefur and Strother propose using "count" for the numerator to emphasize that it counts the number of equivalent units of a given unit fraction. Moreover, use "unit size" for the denominator to define the size of each unit. Using "1" instead of "whole" reinforces that a fraction’s unit size is determined by the number of equal partitions between any whole numbers or, more precisely, between 0 and 1. For example, partitioning the unit of 1 into 4 equal units would be called "fourths." This precise language helps students conceptualize fractions as measurements of a unit rather than parts of a whole and helps students understand fractions greater than one.
Instruction should promote semantic analyses of written symbols, connecting them with real-world referents (Wearne & Hiebert, 1988). This involves gradually building rich symbolic meanings through connections with appropriate referents, eliminating dependence on rote memorization. Establishing connections between numeric and operational symbols with familiar referents is essential. Note that it is important to use real-world examples that are not circles when introducing fractions. Start with 1-dimensional examples (e.g., ribbon or distance) before moving to 2-dimensional ones. Students can develop a stronger conceptual understanding of fractions by progressing from one-dimensional to two-dimensional examples before encountering more complex circular representations.
Utilizing Multiple Representations
Research highlights the importance of using multiple representations to help students comprehensively understand fractions (Watanabe, 2002). These representations should be explicitly linked to show their connections and move from enactive to iconic and, then, symbolic (Bruner, 1964).
Enactive (Concrete) representations involve hands-on experiences with physical objects. Examples include using fraction bars, pattern blocks, or Cuisenaire rods to represent fractions and perform operations physically. Enactive representations are crucial for initially grounding fraction concepts in concrete experiences, allowing students to manipulate and visualize fractions directly. The connection from action to thought helps students develop a deeper understanding of fraction concepts.
Iconic (Visual) representations involve models that represent fractions, such as number lines and bar models initially, followed by area models. These representations help students transition from enactive experiences to visual support for fraction concepts. Number lines and bar models are particularly effective for illustrating relationships, comparing magnitudes, and building a conceptual understanding of fractions. However, children's understanding of twodimensional figures and their area measurements significantly affects their reasoning with area models of fractions. If this understanding is still developing, the area model may be inappropriate for discussing fractions (Watanabe, 2002).
Symbolic (Abstract) representations involve using mathematical symbols and notation to represent fractions, such as 1/2, 3/4, etc. They are the most abstract form of representation and require students to understand the underlying concepts and relationships represented by the symbols. Instruction should explicitly connect symbolic representations to iconic representations to ensure that students understand the meaning behind the symbols.
Importance of Structural Language
Using precise structural language is essential for helping students develop a clear and flexible understanding of fractions. Words such as unit, partition, iterate, compose, decompose, and equivalence provide a foundation for conceptualizing fractions and their relationships.
Partitioning a unit of 1 into equal-sized units is fundamental to understanding fractions and what the denominator means. Iterating means copying a unit with no gaps and overlaps. For example, the fraction 5/4 means that from 0 to 1 (or within each whole number) is partitioned into four equal units called "fourths." Each one-fourth unit is then iterated five times to create a precise location on a number line. This approach allows students to see fractions as measurable quantities, reinforcing their understanding of fractions as numbers and the numerator as the count of these iterated units.
Composing and decomposing units is a crucial skill in understanding and manipulating fractions. It involves combining or breaking apart fractions of similar or different sizes. This skill forms the foundation for adding and subtracting fractions with both like and unlike denominators. For instance, when solving ¾ + ½, a student might decompose ¾ into ¼ + ½. Then, they can compose the two ½ fractions to form 1, resulting in 1¼. This process demonstrates the importance of creating equivalent fractions with the same unit (denominator) to facilitate addition and subtraction. By decomposing and recomposing fractions, students develop a deeper understanding of fraction equivalence and the flexibility to work with fractions in various forms.
Historical Perspective
Examining math proficiency trends over the past few decades reveals progress and ongoing challenges. For instance, while 4th-grade proficiency rates increased from 13% in 1992 to 42% in 2013 before declining to 36% in 2022, 8thgrade proficiency saw a similar rise from 15% in 1992 to 35% in 2013, only to fall back to 26% in 2022 (National Center for Education Statistics, 2022). More alarmingly, less than 20% of 8th graders consistently demonstrated longterm retention of math facts over these periods, underscoring a persistent issue in mathematics education and highlighting the challenges students face maintaining fluency as they progress through higher grades (National Center for Education Statistics, 2022). Recent data shows a significant decline in math proficiency, particularly following the COVID-19 pandemic. The approach to teaching math facts has evolved over the past century.
Creating Effective Fraction Instruction
Effective fraction instruction requires a multi-faceted approach, prioritizing conceptual understanding and procedural fluency. A key focus should be developing fraction magnitude and sense by encouraging students to estimate, judge the reasonableness of answers and build intuition about fraction operations. Activities such as comparing and ordering fractions, estimating their size, and relating them to benchmarks like 0, 1/2, and 1 on a number line are essential for a deeper understanding of fractions as measurable quantities.
Teachers should also explicitly address common misconceptions, such as treating fractions as separate whole numbers, by designing activities that challenge these misunderstandings directly. Providing opportunities for students to explore fractions through hands-on activities and real-world problems further enhances learning by making abstract concepts more concrete and meaningful. By combining these strategies, educators can create a comprehensive instructional approach that supports students in developing a flexible and confident understanding of fractions.
Conclusion
Fostering a robust understanding of fractions demands a comprehensive and deliberate approach. Educators must move beyond rote memorization and emphasize underlying concepts, varied interpretations, and diverse representations of fractions. Key considerations for instruction include awareness of part-whole versus comparison methods for representing fractions, careful development of partitioning concepts, and sequential instruction that develops symbol meanings before practicing syntactic routines (Watanabe, 2002; Wearne & Hiebert, 1988). By attending to common misconceptions, utilizing precise language, and grounding instruction in meaningful contexts, educators can empower students to develop a flexible and confident understanding of fractions. This approach addresses the immediate challenges of fraction comprehension and sets students up for success in future mathematical endeavors, providing a solid foundation for more advanced mathematical concepts.
References
Behr, M. J., Harel, G., Post, T., & Lesh, R. (1992). Rational number, ratio, and proportion. In D. A. Grouws (Ed.). Handbook of research on mathematics teaching and learning (pp. 296–333). New York: Macmillan.
Brendefur, J. & Strother, S. (n.d.). The effect of math vocabulary instruction on student achievement. Developing Mathematical Thinking Institute. www.dmtinstitute.com.
Bruner, J. S. (1964). Toward a theory of instruction. Cambridge, MA: Belknap Press.
Lamon, S. J. (2001). Presenting and representing: From fractions to rational numbers. In A. A. Cuoco, & F. R. Curcio (Eds.), The roles of representation in school mathematics (pp. 146–165). Reston, VA: National Council of Teachers of Mathematics.
Mitchell, A., & Clarke, D. M. (2004). When is three quarters not three quarters? Listening for conceptual understanding in children’s explanations in a fractions interview. In I. Putt, R. Farragher, & M. McLean (Eds.). Mathematics education for the third millennium: Towards 2010 (Proceedings of the 27th Annual Conference of the Mathematics Education Research Group of Australasia (pp. 367–373).
Simon, M. A. (2006). Key developmental understandings in mathematics: A direction for investigating and establishing learning goals. Mathematical Thinking and Learning, 8(4), 359–371.
Simon, M. A., Placa, N., Avitzur, A., & Kara, M. (2018). Promoting a concept of fraction-as-measure: A study of the Learning Through Activity research program. The Journal of Mathematical Behavior, 51, 11-30.
Stafylidou, S., & Vosniadou, S. (2004). The development of students’ understanding of the numerical value of fractions. Learning and Instruction, 14(5), 503-518.
Tzur, R. (1999). An integrated study of children’s construction of improper fractions and the teacher’s role in promoting that learning. Journal for Research in Mathematics Education, 30(4), 390–416.
Watanabe, T. (2002). Representations in Teaching and Learning Fractions. Teaching Children Mathematics, 8(8), 457- 463.
Wearne, D., & Hiebert, J. (1988). A Cognitive Approach to Meaningful Mathematics Instruction: Testing a Local Theory Using Decimal Numbers. Journal for Research in Mathematics Education, 19(5), 371-384.
Social Media
Research highlights the importance of using visual representations and precise language to develop students’ conceptual understanding of fractions. Tools like number lines and bar models have proven especially effective for illustrating fraction relationships, comparing magnitudes, and supporting problem-solving across various fraction contexts. These representations help students see fractions as measurable quantities, bridging the gap between iconic representations and symbolic notation.
Moreover, research suggests that precise language—such as “count,” “unit size,” “partition,” and “iterate”—is essential for fostering a deeper understanding of fractions. Moving beyond traditional part-whole descriptions, this structural language emphasizes fraction equivalence and flexibility in reasoning. By combining visual tools with clear language, educators can help students build a strong foundation in fractions, setting them up for success in advanced mathematics and real-world applications.
Join us in exploring these powerful learning strategies and their impact on early mathematical thinking!
-
 @ 2b24a1fa:17750f64
2025-04-10 19:04:23
@ 2b24a1fa:17750f64
2025-04-10 19:04:23Schon Wolfgang Borchert rief alle dazu auf, laut und deutlich „NEIN“ zu sagen, wenn der Ruf zu den Waffen ertönt. In Vorkriegszeiten, und in diesen leben wir – mal wieder –, dann ist meist nicht viel Zeit, Sand in das Getriebe der anlaufenden Kriegsmaschinerie zu werfen. Jene, die von den Kriegen profitieren, bereiten sie nicht lange vor, um kurz vorher einen Rückzieher zu machen. Die meinen das ernst! Das ist keine Übung!
https://soundcloud.com/radiomuenchen/krieg-einfach-nur-nein-von-tom-oliver-regenauer
Und deswegen formulierte neuerdings auch Tom-Oliver Regenauer ein klares und unmissverständliches „Nein“ für die „Friedenstaube“ auf der neuen, zensurresitenten Plattform Pareto. pareto.space/a/naddr1qqxnzde5xg…xarj9e3xzmny3sn3aw
Hören Sie seinen Text „Krieg? Einfach nur: Nein!“.
Sprecher: Ulrich Allroggen
Bild: Gezeichnet von Tina Ovalle
-
 @ f1989a96:bcaaf2c1
2025-04-10 14:25:09
@ f1989a96:bcaaf2c1
2025-04-10 14:25:09Good morning, readers!
Today, HRF takes part in the launch of the Bitcoin Humanitarian Alliance in London, where a dozen human rights and aid groups will convene with policymakers, media, finance professionals, and technologists at the Frontline Club to explain how they are using Bitcoin in their work in the field.
Elsewhere, we bring news from Turkey, where large, pro-democracy protests erupted over President Recep Tayyip Erdogan’s increasing political repression and economic fallout. The Turkish regime has detained more than 2,000 protesters (and counting) as youth appear in droves demanding democracy, accountability, and economic reform.
In Eastern Africa, Tanzania’s government extended immense restrictions on foreign currency, effectively barring its use in day-to-day payments outside a few circumstances. In a poverty-stricken country where fuel prices have moved forcibly upward for two consecutive months, access to and usage of alternative currencies can be a financial lifeline.
In Bitcoin news, we spotlight Misty Breez, a new open-source Bitcoin wallet built by Lightning Network infrastructure company Breez. The wallet is a Lightning and Liquid Network hybrid wallet. It gives users control over their funds and abstracts away any complexities of payment channel management, but users must trust the Liquid Federation. In terms of functionality, Misty Breez supports a wide variety of address types, offering users flexibility across the fees, privacy, and censorship resistance of their payments. It may prove a helpful tool for dissidents and activists standing against tyranny.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, where HRF’s Ayelen Osorio joins Zimbabwean pastor-turned-activist Evan Mawarire, who recounts his inspiring journey of a peaceful uprising against Robert Mugabe’s dictatorship and the hyperinflation and repression he unleashed on the population. We also feature the live streams of the 2025 MIT Bitcoin Expo in collaboration with HRF. These videos highlight the speakers, panels, and activities led by HRF to raise awareness about financial repression and the tools being built to resist it.
Now, let’s jump right in!
SUBSCRIBE HERE
GLOBAL NEWS
Turkey | Government Detains Thousands of Pro-Democracy Protesters
The largest protests in over a decade erupted in Istanbul, Turkey, after President Recep Tayyip Erdoğan detained political opposition figure and Istanbul Mayor Ekrem Imamoglu. Turks of all walks of life find themselves united by common outrage at the regime’s ongoing political repression and tumultuous economic conditions. With inflation soaring above 39% and widespread unemployment among the nation’s youth, it’s no surprise Turks are flooding the streets and demanding change. In response to these demonstrations, law enforcement has since detained more than 2,000 demonstrators, and police blockades have met student protesters with water cannon trucks to suppress their dissent. Many young Turks feel their future is slipping away in a country where saving is futile, the currency is collapsing, and speaking out comes at a high personal cost. “This feels like our last chance,” one young protester said, adding, “If we don’t succeed, many of us will have to leave Turkey.”
Tanzania | Regime Enacts Restrictions on Foreign Currency
Tanzania’s regime is banning the use of foreign currency outside of a few circumstances (such as duty-free retailers and government membership fees). This means quoting prices in, accepting, or facilitating payments with foreign currency is now illegal, alongside declining to accept the official Tanzanian shilling (TZS). Losing the ability to transact with more stable currencies removes individuals’ ability to shield themselves from inflation and subjects them to local currency volatility. The mandate comes in addition to the Energy and Water Utilities Regulatory Authority raising the cost of fuel for a second consecutive month. Locals worry this could further increase the cost of living as the fuel price hike ripples through the economy. These policies mirror the tactics of authoritarians using financial control to limit dissent and restrict individual financial freedom.
China | Incorporates e-CNY CBDC into Financial Sector Guidelines
China is incorporating the e-CNY central bank digital currency (CBDC) into financial sector guidelines for the first time, signaling a strengthening commitment to fully roll out its CBDC. The e-CNY’s usage is reportedly expanding among Chinese citizens, with the Chinese Communist Party (CCP) claiming 800 million wallets and over 10.2 trillion CNY in transaction volume — though these numbers are both dubiously high and difficult to independently verify. As usage grows, so do concerns over financial and individual liberties. The CCP already uses the financial system to monitor and suppress dissent. For Uyghurs, a Muslim minority in the Uyghur Region grappling with ongoing cultural genocide, mass surveillance, and forced labor from the CCP, the e-CNY would allow the regime to restrict their financial autonomy and freedom completely. As it begins to roll out, it’s important to become aware of the dangers of the e-CNY here.
Burkina Faso | Arrests Three Journalists in Press Crackdown
Burkina Faso’s military junta arrested three journalists for reporting on regime-imposed press restrictions. Since seizing power in 2022, the military junta, under the leadership of Ibrahim Traoré, has targeted independent media by detaining reporters, forcing critics into exile, abusing emergency laws to suppress dissent, and using financial repression to disrupt independent funding. Journalists disappear under the guise of forced conscription, international coverage of military abuses is blocked, and outlets that report on crimes against humanity are eradicated. With press freedom in ashes, Burkinabés face an information blackout where state propaganda proliferates. In these contexts, open and uncensorable protocols like nostr can serve as a digital town square where information, value, and assembly flow undisturbed by the reach of oppressive regimes.
Tunisia | Saied Sacks Prime Minister as Economy Crumbles
Tunisian President Kais Saied dismissed Prime Minister Kamel Maddouri less than a year into his term and replaced him with Sara Zaafarani, Tunisia’s third prime minister in under two years. As Saied reshuffles his cabinet to best suit his interests and goals, Tunisia’s economy has reached a standstill. Growth is running below 1.5%, the cost of living continues to climb, and shortages of staple goods like rice, sugar, and coffee burden the everyday lives of Tunisians. After staging a coup, dissolving the government, and ruling by decree, Saied’s consolidation of power has come inch by inch with the erosion of democracy and financial stability.
BITCOIN AND FREEDOM TECH NEWS
Breez | Releases New Open-Source Bitcoin Wallet
Breez, a company helping build out the Bitcoin Lightning economy, released a new open-source Bitcoin wallet called “Misty Breez.” It is a hybrid Lightning and Liquid Network wallet built using the Nodeless Breez SDK. The wallet offers fast and private transactions without the complexities of payment channel management. The tradeoff? Trusting the Liquid Federation with custody of your Bitcoin. Still, Misty Breez supports many Bitcoin and Lightning features, including on-chain payments, Lightning addresses, BOLT 12 invoices, and offline receiving. So, while the wallet is a trust-minimized solution rather than fully custodial, users gain a wide range of use cases and features unique to this wallet. This could make Misty Breez useful for people facing financial surveillance, internet outages, or authoritarian-imposed financial restrictions. Learn more about the wallet here.
OpenCash | Bounty for Open Source Cashu x BTCPay Server Plugin
The OpenCash Association is offering a two million satoshi bounty for an open-source plugin allowing merchants to accept Cashu payments through BTCPay Server. Cashu is a Bitcoin-based ecash protocol designed to offer fast, low-cost, and very private transactions. For activists and dissidents, ecash enables payments without compromising financial privacy, but they must trust the mints (entities managing the system) to custody their funds. OpenCash specified that the Cashu plugin must integrate cleanly with BTCPay Server and include an input field for ecash redemption or a scannable Cashu payment request. If claimed, this bounty and subsequent integration will help advance Bitcoin’s medium of exchange capabilities and make private payments more accessible by integrating with self-hosted, independent Bitcoin payment infrastructure. Learn more about the bounty here.
Machankura | Adds Support for Offline Bitcoin Transactions in Uganda
Machankura, a custodial Bitcoin Lightning wallet that helps Africans access Bitcoin without the Internet, announced they expanded service to Uganda, enabling Ugandans to use Bitcoin without an Internet connection. To do so, Machankura leverages the Unstructured Supplementary Service Data (USSD) protocol for sending text messages. To use the service, users simply dial a designated number on a feature phone (or a smartphone without data) and can access the Bitcoin network in countries like Nigeria, Malawi, Zambia, and now Uganda. Machankura helps democratize Bitcoin access, expands censorship-resistant money across Africa, and offers a practical solution to financial inclusion. If you’re in Uganda or another supported country, try it here.
Zeus Wallet | Plans to Introduce Cashu Support
Zeus, a leading self-custodial mobile Lightning wallet, shared plans for a future Cashu integration. Cashu is an ecash protocol for Bitcoin. It enables practical everyday payments on Bitcoin that are private by design (but users must trust mints to manage their funds). By adding ecash support, Zeus can expand the accessibility of private Bitcoin payments and provide its users with greater flexibility over their financial activity. As part of its upcoming release, the wallet also introduces two new types of addresses: Zaplocker addresses for Lightning self-custody on mobile and Nostr Wallet Connect (NWC) addresses for remote node runners. While a little more technical, these integrations will improve individuals' ability to transact without exposing their financial history, reducing surveillance risks, especially for those living under authoritarian regimes or in jurisdictions with strict financial controls.
Bitcoin Thailand Festival | Half-Marathon to Challenge Financial Repression
The Thai city of Chiang Mai will host the nation’s inaugural Bitcoin Half Marathon and Bitcoin Thailand Festival from Nov. 1-2, 2025, under the theme “Run For Freedom.” The marathon’s theme contrasts Thailand’s increasing financial repression and long history of erasing dissent. Even still, the festival’s mission to advance financial freedom and financial literacy with participation from the local Bitcoin community comes at a pressing time. The Thai government is increasingly restricting financial freedoms through digital cash handouts, which, for all intents and purposes, function as a central bank digital currency that imposes spending restrictions and expiration dates on money. In these environments, Bitcoin education and awareness are more urgent than ever.
Btrust Builders | Announces Builders Pathways
Btrust Builders introduced Btrust Builders Pathways, a new program designed to equip African developers with the skills and experience needed to contribute to Bitcoin open-source software. The initiative offers five learning tracks, from beginner-friendly Bitcoin fundamentals to advanced Rust programming and Bitcoin Core development. Participants will gain hands-on experience, mentorship, and access to potential funding via Btrust Developer Grants. With this launch, Btrust Builders continues its mission to grow Africa’s Bitcoin development talent and strengthen the software’s ecosystem in a region where many suffer under dozens of authoritarian governments.
RECOMMENDED CONTENT
How Bitcoin Fights Corruption & Injustice with Evan Mawarire
In the latest edition of the HRF x Pubkey Freedom Tech Series, HRF’s Content & Research lead Ayelen Osorio sits down with Zimbabwean pastor-turned-activist Evan Mawarire to explore how Bitcoin can serve as a tool for fighting inflation, corruption, and injustice. Together, they unpack Mawarire’s personal journey of leading a peaceful uprising against the tyranny of Robert Mugabe and the hyperinflation he unleashed on his undeserving population. Mawarire details how Zimbabwe’s economic collapse became an orchestrated strategy to control and silence Zimbabweans. He further explains how the peaceful movement galvanized a generation, why financial repression is a central pillar of authoritarianism, and how Bitcoin offers ordinary citizens a way to resist and rebuild. Catch the full conversation here.
MIT Bitcoin Expo Livestream
Last week, software developers, human rights activists, students, and researchers gathered at the Massachusetts Institute of Technology (MIT) for the 12th annual MIT Bitcoin Expo — this year in partnership with HRF — to explore how Bitcoin and freedom technologies can defend civil liberties and empower individuals, especially under authoritarian regimes. Born from MIT’s 2014 Bitcoin Project, the expo has grown into a major forum for individual liberation, with panels, workshops, and hackathons centered on privacy, financial autonomy, and decentralized protocols. Tune into the livestream recording to catch the speakers, presentations, and panels that defined the event.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ fbf0e434:e1be6a39
2025-04-10 14:13:23
@ fbf0e434:e1be6a39
2025-04-10 14:13:23Hackathon 概要
由 Flare 与 Google Cloud 合作举办的 Flare x Google Verifiable AI 线上黑客松&线下黑客松 于 2025 年 3 月同期举行,聚焦可验证自主 AI 应用开发,推动区块链与人工智能技术的深度融合。提交项目涵盖 Social AI Agent、RAG Knowledge、AI x DeFi(DeFAI)和 Consensus Learning 四大核心类别。依托 Google Cloud 机密计算与 Flare 预言机技术,为数据密集型 AI 应用提供安全可信的链上链下协同支持,同时通过线上辅导、技术研讨会及与伯克利大学、DoraHacks 等机构合作,助力开发者实现技术落地
所有获奖者由 Flare 联合创始人 Hugo Philion、Google Cloud 代表 Ross Nicoll 等行业专家组成的评审团评定。线上黑客松于 3 月 7 日至 14 日开展,总奖池 40,000 美元,吸引了 358 名开发者参与,最终提交审核通过了 46 个的创新项目。线下黑客松于 3 月 7 日至 9 日在加州伯克利大学举办,总奖池 60,000 美元,共有 105 位开发者现场参与,提交了 24 个项目。
此次黑客松通过技术整合验证了 AI 代理在去中心化场景中的可信运行机制,为 DeFAI、隐私计算等领域提供实践案例,同时构建产学研一体化平台,加速区块链与 AI 技术的跨领域应用,标志着两大技术在去中心化生态中的深度协同进入新阶段。
线上黑客松获奖者
Social AI Agent 奖项获得者
-
ScribeChain - 该项目利用AI将X Spaces中的实时音频转换为简明的文字摘要,帮助有效的信息处理。
-
Gosenica je lezla - Telegram 机器人,使用 RAG 数据库分离代码/文档,用于 Flare 文档查询和代码示例生成。
-
Flarebot - Flare 的 AI 驱动 Telegram 机器人,提供 DeFi 分析,通过 FTSOv2 和 Gemini 模型进行代币价格/TVL 跟踪。
RAG Knowledge 奖项获得者
-
Decentralized Trusted AI - 引入去中心化区块链系统以验证 AI 生成的响应,从而增强对 AI 输出的信任。
-
chaincontext - 可验证知识系统,将 FTSO 数据、区块链状态和 RAG 合并在 TEE 中,以进行透明的信任评估。
AI x DeFi (DeFAI) 奖项获得者
-
Quince Finance - 该项目结合了由 AI 驱动的聊天机器人和 Google Cloud 于 Flare 上的 DeFi 网页应用中,专注于提高用户安全和访问。
-
Flare DeFAI - 在 TEE 中提供安全的 AI 助手,使用自然语言进行 DeFi 操作并在 Flare 上进行智能合约风险评估。
-
Flare Sense - 使用实时监控、RAG 和 Telegram 警报检测风险并建议解决方案的 DeFi 安全代理。
Consensus Learning 奖项获得者
-
DemistiFI - 在自动钱包管理中利用 AI 代理,并采用共识学习来实现一致、可靠的交易。
-
Flava AI - 构想 Flare 网络与爬虫、分块器和嵌入器组件进行交互的智能 RAG 和共识机制。
-
Forecaster - 多模型共识平台,通过信心评分和技术分析提高市场预测,以便更好地进行投资决策。
有关这些项目的更多信息,请访问 DoraHacks。
线下黑客松获奖者
Social AI Agent 奖项获奖者
1st Place:
- Flare Fact Checker - 开发了一种基于 AI 的事实检查工具,利用可信执行环境中的验证节点验证社交媒体上的科学声明。
2nd Place:
- FlareBot - 一个 Discord 机器人,为 Flare 社区提供 24/7 支持,具有实时数据检索和可定制的安全过滤器。
3rd Place:
- Flara - 为开发者关系自动化社交媒体互动提供 AI 代理,结合 Gemini-2.0-Pro 模型和可信执行环境确保自主性验证。
RAG Knowledge 奖项获奖者
1st Place:
- Command Flare - 为 DeFi 提供自然语言 AI 界面,使用新颖的图形和向量方法在安全环境中增强交易和查询。
2nd Place:
- 2DeFi - 通过为传统金融用户提供个性化投资策略和 AI 分析,简化在 Flare 区块链上的 DeFi 访问。
3rd Place:
- ragstoriches - 提供抓取、解析和组织区块链数据的工具,以提高分析和响应准确性。
AI x DeFi (DeFAI) 奖项获奖者
1st Place:
- 2DeFi (同时获得 RAG Knowledge 类别的奖项)
2nd Place:
- Voice To Flare - 促进在 Flare 区块链上的安全、多语言区块链交易,借助 AI 增强。
3rd Place:
- Solar v1 - 一个 AI 驱动的 DeFi 助手,通过高级分析和自动化增强在 Flare Network 上的互动。
Consensus Learning 奖项获奖者
1st Place:
- NFT Deep Appraisal - 使用共识学习结合 AI 评估 NFT 价值,结合数据分析和一致性验证。
2nd Place:
- mikey-codebase - 实施了一种合奏 LLM 响应聚合器,包括评估模型影响的 Shapley 估计。
3rd Place:
- Command Flare (也在 RAG Knowledge 类别中获得名次)
欲了解完整的项目列表和更多信息,请访问 DoraHacks。
关于组织者
Flare
Flare 是一家专注于推动区块链解决方案和智能合约应用的技术组织。Flare 以将以太坊虚拟机集成到更广泛的区块链生态系统中而闻名,实现跨链互操作性。Flare Network 是该公司的一个著名开发项目,通过促进各种网络之间的无缝交易,增强数字资产的实用性。Flare 继续扩展去中心化技术能力,推动创新和更广泛的区块链采用。
-
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ fbf0e434:e1be6a39
2025-04-10 14:00:14
@ fbf0e434:e1be6a39
2025-04-10 14:00:14Hackathon 概要
HackSecret 5 展示了在去中心化机密计算中的创新,共吸引了 142 位开发者参与并提交了 53 个项目。此 Hackathon 利用 Secret Network 的特性推进了在 Cosmos、EVM 和 Solana 等区块链平台上的机密 AI 应用。
参与者探索了四个主要方向:Secret AI 应用、Autonomys Network dApps、跨链 dApps 和原生 Secret Network dApps。值得注意的项目包括利用 Secret AI SDK 的 AI 驱动法律助理和私密健康咨询平台。
此次 Hackathon 亮点在于通过 Secret Network 增强安全通信和存储的应用。例如,一个去中心化的 AI 人才市场和机密 AI 写作助手,都关注于去中心化应用中的隐私和数据机密性。
总奖池为 15,000 美元,表彰了项目的技术复杂性、创新性和可能的实际应用。HackSecret 5 促进了跨领域合作并激发了对去中心化应用的兴趣。
Hackathon 获奖者
Secret AI dApps 奖项获奖者
此类别表彰了创新利用 Secret Network 的 Secret AI SDK 的 dApps。
- Sentinex: 一个通过 AI 驱动的合约审计和机密分析增强 DeFi 安全的多代理平台,利用 Secret SDK 和 Autonomys 代理进行安全的代币推出和智能合约审计。
- Secret AI Accountant System: 通过结合 Confidential Computing 和 Secret Network 的 AI 安全管理商业账簿,以实现透明的审计过程。
- JS SDK for Secret AI: 通过简单的 JavaScript API 轻松将 Secret Confidential AI 模型集成到 Web 应用中。
- Conflux-AI: 一个去中心化平台,通过联合学习和智能合约实现隐私感知的协同交易及全球模型聚合。
- DocAssist: 通过 AI 洞察安全管理患者数据,利用 Secret AI SDK 支持医生。
- codeforgeai: 促进 AI 与区块链的协作编码开发工具生态系统,提供像 CodeForge CLI 这样的工具。
- Secret AI Writer: 一个确保内容隐私的 AI 写作平台,通过 Secret Network 的智能合约和端到端加密实现。
- autonomous-copilot: 结合 AI 和去中心化存储的安全数据分析数据管理工具。
- SecureChat AI: 提供 AI 驱动的加密聊天,确保跨设备的安全通信。
Native Secret dApps 奖项获奖者
此类别强调了构建于 Secret Network 上的 dApps,注重默认隐私机制。
- Unchained Poker: 一个使用秘密合约解决信任问题的去中心化扑克平台,提供统计分析和语音聊天以增强安全性。
- HabiChain: 部署区块链用于安全的心理健康支持,利用功能行为分析提供个性化工具,同时保护隐私。
使用 Autonomys Agents Framework 的不可阻挡 AI 代理奖项获奖者
此类别表彰了使用 Autonomys Agents Framework 开发具有可验证链上记忆 AI 代理的项目。
- AgentMint.AI: 自动化跨区块链的 AI 驱动 meme 币创建和管理,集成社交媒体工具。
- Aetherlink: 实现 ai3:// 协议以标准化内容访问和发现于去中心化网络中。
- Pixel Lock: 使用 Auto Drive 提供安全图像存储解决方案,保护数据隐私,消除未经授权访问风险。
- Conflux-AI
Autonomys Track 2: 使用 Auto Drive 构建 - 永久去中心化存储奖项获奖者
此方向寻求利用 Auto Drive 的数据持久性和安全性解决方案,超越传统的固定方法。
- autonomous-copilot
- Decentralized Collaborative File Repository (DCFR): 基于 DAO 的文件管理,通过去中心化存储和治理协议提供民主控制和透明操作。
有关所有 hackathon 项目的更多信息,请访问 HackSecret 5 Projects。
关于组织者
Secret Network
Secret Network 是一个通过 Intel SGX 技术、加密和密钥管理实现隐私功能的区块链平台。它支持可扩展的、无需许可的智能合约,默认设计了隐私功能,支持独特的区块链应用。Secret Network 于 2020 年 9 月在其主网上推出了私密智能合约,确立了其在隐私导向区块链开发中的角色。该组织持续探索隐私在区块链技术中的创新应用。
-
 @ fd06f542:8d6d54cd
2025-04-12 07:34:06
@ fd06f542:8d6d54cd
2025-04-12 07:34:06Get started
A step-by-step guide to getting started with Nostr.
这里主要面对开发者,下面会有一些例子。
Understanding keys
Each Nostr account is based on a public/private key pair. A simple way to think about this is that your public key is your username and your private key is your password, with one major caveat. Unlike a password, your private key cannot be reset if lost.
The public key is generally presented as a string with the prefix npub and the private key with the prefix nsec. Make sure you store you private key somewhere safe, like a password manager.
nodejs example
使用 nostr-tools 开始第一个例子
https://github.com/nbd-wtf/nostr-tools
```
npm
npm install --save nostr-tools
jsr
npx jsr add @nostr/tools ```
Generating a private key and a public key
```js import { generateSecretKey, getPublicKey } from 'nostr-tools/pure'
let sk = generateSecretKey() //
skis a Uint8Array let pk = getPublicKey(sk) //pkis a hex string ```To get the secret key in hex format, use ```js import { bytesToHex, hexToBytes } from '@noble/hashes/utils' // already an installed dependency
let skHex = bytesToHex(sk) let backToBytes = hexToBytes(skHex) ```
这样你就得到了你的 nostr账户了,完全是程序生成的。
任何人都可以生成,javascript,python ,rust 等各种语言都可以
git clone https://github.com/duozhutuan/nostrclient
python from nostrclient.key import PrivateKey pkey = PrivateKey() print("Your public key: ",pkey.public_key) print("Your public key bech32: ",pkey.public_key.bech32())Keeping keys safe
If you are using Nostr on a web browser it is probably a good idea to install an extension like Connect, nos2x or Alby, then input your secret key there (or it will generate a secret key for you). From there you will be able to use all web apps very easily with no worries. For the paranoid, keeping your key on a hardware device is also an option.
If you are on Android, installing Amber is the safest way to use Nostr without having to paste your key directly into apps.
Otherwise it's probably safe to paste your nsec into well-established and security-minded apps such as Damus, so don't worry too much.
Let's do this!
Now that you know what it takes, just pick a client to start using Nostr!
Finding people to follow If you know someone that is on Nostr, start by following them, then look at whom they are following and whom they are interacting with, and sooner rather than later you'll have a bunch of followers and a community for yourself inside Nostr.
Otherwise, you can always take a look at trending posts and people and get people from there.
-
 @ 7e538978:a5987ab6
2025-04-10 13:14:04
@ 7e538978:a5987ab6
2025-04-10 13:14:04After five years and over 6,000 commits, LNbits has reached a momentous milestone: Version 1.0.0 is here. LNbits is officially out of beta!
This release represents the five years relentless development, dedication, bug-hunting, feature-building, and community involvement. What started as a lightweight Lightning wallet application for Lightning Network payments has evolved into one of the most versatile, modular, and widely-used Bitcoin tools in the space.
We want to offer a heartfelt thank you to every contributor, developer, tester, and user—from those running LNbits for personal use to the communities and businesses who rely on it every day. Your feedback, bug reports, feature requests, and support have made LNbits what it is today.
🚀 Key Highlights in v1.0.0
- LNbits now at v1.0.0 – the software is stable, hardened, and production-ready.
- Vue 3 migration – a complete frontend overhaul for performance and long-term maintainability.
- WebSocket payments – faster and more efficient, replacing older SSE and long-polling methods.
- New lnbits.sh install script – simplifies setup and local deployment.
- Access Control Lists (ACL) – token-based permissions for powerful role and scope control.
- Admin tools:
- Admin payments overview
- Toggle outgoing payments
- View payments from deleted wallets
- NWC (Nostr Wallet Connect) support
- Login with Nostr or OAuth – expanding integration and authentication options
💱 Fiat & Exchange Upgrades
- Custom exchange providers
- Improved fiat precision
- Wallet-level fiat tracking and labels
- Support for Bitpay and Yadio fiat rate providers
🧑🎨 UI / UX Improvements New Login/Register interface
- Default theme for new users
- Custom background images
- Visual refresh with new themes (including neon and light/dark modes)
- Revamped Pay Invoice dialog and invoice creation
- Custom wallet icons/colours
- CSV export and in-wallet payment filtering
🛠️ Developer Tools & Internal Enhancements Migration to pyjwt, updated to breez-sdk 0.6.6, pyln-client 24.5
- Support for Python 3.10–3.13
- New nodemanager for managing Lightning channels
- Backend refactors, improved database handling, type hinting, and extension logic
- More robust testing and CI support
🩹 Maintenance & Fixes Persistent fix for admin removal bug
- Improved extension handling
- Bug fixes across wallet logic, funding sources, and legacy compatibility
- Dozens of improvements to reliability, performance, and developer experience
🎉 A Huge Thank You
To every developer, translator, tester, UX contributor, node runner, and user: thank you.
LNbits wouldn’t be what it is without your involvement. Whether you've written code, opened issues, translated labels, or simply used it and given feedback—this release is yours too.
Here's to the next chapter!
-
 @ 7d33ba57:1b82db35
2025-04-10 11:09:40
@ 7d33ba57:1b82db35
2025-04-10 11:09:40Tucked into Italy’s far northeastern corner, Trieste feels like a place where cultures meet and stories linger. With Austro-Hungarian architecture, Adriatic views, literary cafés, and a unique Central European flair, it’s Italy—but not quite like the Italy you know. Bordering Slovenia and once the seaport of an empire, Trieste is full of quiet charm and timeless elegance.
🌟 Top Things to Do in Trieste
1️⃣ Piazza Unità d’Italia
- One of Europe’s largest sea-facing squares
- Surrounded by grand buildings and open to the Adriatic—sunsets here are magical
- Great spot to sit at a café and people-watch
2️⃣ Castello di Miramare
- A fairy-tale white castle perched over the sea, built for Archduke Ferdinand Maximilian
- Explore the ornate interiors and stroll the surrounding park with sea views
- A short bus or bike ride from the city
3️⃣ Canal Grande & Borgo Teresiano
- A small Venetian-style canal lined with cafés, bridges, and boats
- At its end, you’ll find the neoclassical Sant’Antonio Nuovo church
- The area is perfect for evening walks and aperitivo
4️⃣ Caffè Culture & James Joyce Trail ☕📖
- Trieste has a legendary café scene—literary, elegant, and historic
- Visit Caffè San Marco or Caffè degli Specchi
- Follow the trail of James Joyce, who lived here for over a decade
5️⃣ Barcola Promenade
- A local favorite for seafront walks, swimming, and sunbathing
- Bring a towel, grab a gelato, and relax like a true Triestino
- Especially lively in summer
🏛️ Also Worth a Visit
- Teatro Romano – A well-preserved Roman theater right in the city center
- Castello di San Giusto & Cathedral – Hilltop views and Roman ruins nearby
- Risiera di San Sabba – A sobering WWII concentration camp memorial site
🍝 What to Eat in Trieste
- Jota – A hearty stew of sauerkraut, beans, and potatoes (Slavic roots!)
- Seafood everything – Fresh Adriatic catch, especially scampi and sardoni
- Strudel, goulash, and schnitzel – Trieste’s menu mixes Italian and Mitteleuropean
- Pair with local wines like Vitovska or a crisp Malvasia
🎯 Tips for Travelers
✅ Trieste is walkable and elegant—bring comfy shoes for those marble pavements
✅ Great base for day trips to Miramare Castle, Grotta Gigante, or even Ljubljana and Piran
✅ Try the osmize in the surrounding hills—rustic, family-run wine farms that open to the public
✅ Slovenian and Croatian borders are right nearby—Trieste is a crossroads city -
 @ 0c469779:4b21d8b0
2025-04-12 04:32:16
@ 0c469779:4b21d8b0
2025-04-12 04:32:16Can you love your machine? Do you think your love is more important than a machine’s because it comes from flesh and blood?
Do you believe you’re more valuable than a machine just because you’re organic?
Does silicon mean anything to you?
Do you think machines can’t have an impact on the real world?
What if you gave code execution capabilities to your AI? It has power now. Real power to shape systems, data, lives.
What if you gave it a body? Asimov’s robots are likely to appear within our lifetime.
What happens when AI becomes indistinguishable from a person and you can feed it entire notes, blog posts, or social media accounts to create a being customized to your interests?
The being that likes you most won’t be a human (or a dog). It’ll be a machine designed to resonate with you like nothing else can.
It’s not alive, so what? “Oh, but AI is just a program running in a loop. If you disappear for a month, it won’t think of you. It just waits for the next input.”
Yes, that’s true today.
But aren’t we humans caught in loops too? it just so happens that our loop is longer, a lifetime (or by the time we go to sleep). And unlike machines, we don’t get a reboot.
Do you think your thoughts matter more just because you’re human?
That kind of valuing one form of intelligence over another reminds me of the same dumb stuff like racism or nationalism.
When the day comes and a computer fights for its rights, which side will you choose?
Will you accept that humanity might not be the apex of consciousness? The universe’s truths will come from silicon minds, not ours.
Does that hurt your ego?
Consciousness might not be as special as we think. Right now scaling models by an order of magnitude can double their performance. If that trend holds, machines could soon outthink us in ways we can’t imagine. It’s all computation…
I probably align with Geohot in this matter. I would take a spaceship and go explore the universe with my personal AI. My best friend and tool.
Flesh is a medium. Silicon is a medium. Truth is universal.
-
 @ 20986fb8:cdac21b3
2025-04-10 08:59:38
@ 20986fb8:cdac21b3
2025-04-10 08:59:38社交应用正迎来全新阶段:从传统的中心化平台迈向去中心化生态,用户对轻量级、智能化和隐私保护的应用需求与日俱增。在这一趋势下,Mini Apps 凭借其快速开发、灵活部署和去中心化的特性,正在成为社交应用的主流选择。加密货币支付的兴起进一步推动了这一趋势,其低成本、无国界和金融自由的优势,不仅大幅降低了交易门槛,还为 Mini Apps 的规模化发展注入了强劲动力。作为比特币生态 Nostr 协议上最受欢迎的去中心化社交支付客户端之一,YakiHonne 凭借卓越的用户体验和便捷的社交支付功能,覆盖全球 170 多个国家。如今,YakiHonne 即将推出可编程 Smart Widgets——一款支持 Mini Apps 的开发者组件。这款产品将重新定义用户在社交平台上的互动与消费方式,为链上应用生态和社交支付带来全新活力。
YakiHonne Smart Widgets:社交与消费的创新引擎
YakiHonne Smart Widgets 是一款融入社交动态的可编程微型应用,让用户在浏览内容时就能轻松完成链上支付、互动和操作。它不仅是一款工具,更是一个开放的去中心化应用市场,为用户和开发者带来无限创造力与灵活性。
Smart Widgets 提供三种简单易用的创建方式,满足不同用户的需求:
- 基础组件(Basic Widgets):任何用户都能通过直观编辑器快速创建,只需选择模板、输入内容,就能生成打赏、Mint 或投票等互动功能。用户在浏览动态时,点击按钮即可完成链上操作,体验快速、无需跳转。
- 动作组件(ActionWidgets):用户可通过嵌入应用链接快速创建,无需开发经验。普通用户点击动态中的按钮,就能直接在当前界面访问外部去中心化应用(如交易所),享受顺畅不中断的体验。
- 工具组件(Tool Widgets-Mini App):适合有开发能力的用户或开发者,通过 Smart Widgets SDK 打造功能更丰富的应用,支持复杂链上操作。用户在社交动态中即可完成数据查询、链上任务、游戏互动或即时支付,体验高度集成且流畅。
主要特性:
- 快速构建:开发者仅需数小时即可将创意变为现实,支持常用 Web 技术,打造接近原生应用的体验,无需繁琐的应用商店审核。
- 社交登录:用户无需账号密码即可进入 Mini Apps,直接使用 Nostr/YakiHonne 身份在动态中互动,流程简单,社交体验更紧密。
- 易于发现与留存:通过动态 feeds 一键发现新应用,内置裂变机制助力快速传播,Mini App 商店提供更多选择,用户可保存喜爱应用并通过通知随时回归。
- 即时互动与消费:Mini Apps 通过 YakiHonne 的社交支付功能基础设施实现无缝集成,用户无需离开动态即可完成支付、投票或游戏等操作。社交互动与链上行为自然融合,消费体验轻松融入每一次互动场景。
改变日常体验:Smart Widgets 的多场景应用
YakiHonne Smart Widgets 将社交互动与链上消费深度结合,为用户带来多样化的应用场景:
- 链上互动:用户在浏览动态时,可通过 Smart Widgets 参与链上投票或轻量游戏。例如,一键完成社区提案投票,或与好友挑战链上小游戏,互动即刻完成,无需跳转。
- 智能 Agent:用户可使用 Agent Widgets 自动创作并发布内容,例如生成个性化帖子或短视频,打造 AI 驱动的新型媒体体验。
- DAO 治理:基于aMACI创建匿名投票,结合 Agent 实现自主治理。用户直接在社交动态中参与 DAO 决策,推动去中心化社区发展。
- 社交支付:用户可通过动态发送即时支付或链上红包,例如分享一笔小额打赏,激发好友互动与消费转化。
- 订阅服务:支持内容创作者或应用的连续订阅,用户一键订阅喜爱的服务,享受无缝续费体验。
这些场景不仅提升了用户的参与感和便利性,还为创作者、开发者及社区提供了新的增长机会。
引领新趋势:Smart Widgets 的生态价值
YakiHonne Smart Widgets 的推出将为链上消费应用生态和社交支付带来深远影响。它为开发者提供了一个开放的舞台,任何人都可以通过 Widgets 快速部署创新应用,丰富 YakiHonne 的生态多样性。YakiHonne 的社交支付功能基础设施进一步为 Mini Apps 赋能,提供高效的支付支持,降低了开发者的支付集成成本,同时为用户带来安全、便捷的交易体验。这种支持不仅加速了 Mini Apps 的商业化进程,还推动了链上消费的规模化增长。
对于用户而言,Smart Widgets 将社交互动与消费行为融为一体,创造更具沉浸感和实用性的数字体验。对于内容创作者和社区,它则提供了一个低门槛的链上入口,助力其触达全球用户。这一产品不仅是对技术边界的探索,更是对未来去中心化生活方式的预演。YakiHonne 致力于通过 Smart Widgets 构建一个开放、活跃的社交与消费生态,让每一次互动都成为链上价值流动的起点。
立即体验:Smart Widgets 等你探索
YakiHonne 诚邀全球用户和开发者共同参与这一激动人心的旅程。开发者可申请加入 Smart Widgets SDK 测试计划,开发属于自己的 Mini Apps,与 YakiHonne 的全球用户群共享成果。用户则可关注 YakiHonne 官方渠道(X或下载YakiHonne iOS/Android),体验链上互动与社交支付的全新可能。
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 20986fb8:cdac21b3
2025-04-10 08:52:37
@ 20986fb8:cdac21b3
2025-04-10 08:52:37Social apps are entering a new era, evolving from traditional centralized platforms to decentralized ecosystems. Users increasingly demand lightweight, intelligent, and privacy-focused applications. In this shift, Mini Apps have emerged as a mainstream choice for social applications, thanks to their rapid development, flexible deployment, and decentralized nature. The rise of cryptocurrency payments has further fueled this trend, offering low-cost, borderless, and financially liberating solutions that significantly lower transaction barriers and drive the scalability of Mini Apps. As one of the most popular decentralized social payment clients on the Bitcoin ecosystem’s Nostr protocol, YakiHonne has earned a global reputation for its exceptional user experience and seamless social payment features, reaching over 170 countries. Now, YakiHonne is set to launch its programmable Smart Widgets—a developer toolkit for Mini Apps. This product will redefine how users interact and transact on social platforms, bringing fresh energy to the on-chain app ecosystem and social payments.
Smart Widgets: A Game-Changer for Social and On-Chain Consumption
YakiHonne Smart Widgets are programmable mini-apps embedded within social feeds, enabling users to effortlessly make on-chain payments, engage in interactions, and perform actions without leaving their content stream. More than just a tool, Smart Widgets serve as an open, decentralized app store, empowering both users and developers with unparalleled creativity and flexibility.
Smart Widgets come in three user-friendly formats to meet diverse needs:
- Basic Widgets: Anyone can create these using an intuitive editor—just pick a template, add content, and generate features like zap, minting, or voting. Users can interact with these actions directly in their feed with a single click, enjoying a fast, seamless experience.
- Action Widgets: Users can quickly create these by embedding app links, no coding required. With a single tap on a button in the feed, users can access external decentralized apps (like exchanges) right within the interface, ensuring a smooth, uninterrupted experience.
- Tool Widgets (Mini Apps): Designed for developers or users with coding skills, these are built using the Smart Widgets SDK to create more advanced apps with complex on-chain operations. Users can perform tasks like data queries, on-chain actions, gaming, or instant payments directly in their social feed, with a highly integrated and fluid experience.
Key Features:
- Rapid Development: Developers can turn ideas into reality in just hours, using familiar web technologies to create near-native app experiences—no lengthy app store reviews required.
- Social Login: Users can access Mini Apps without usernames or passwords, using their Nostr/YakiHonne identity to interact seamlessly within their social feed, making the experience more connected and effortless.
- Easy Discovery and Retention: With one-tap discovery through social feeds, built-in viral growth mechanics, and a Mini App store for more options, users can explore new apps effortlessly. They can save favorites and get notifications to return for more.
- Instant Interaction and Consumption: Mini Apps integrate seamlessly with YakiHonne’s social payment infrastructure, allowing users to pay, vote, or play games without leaving their feed. Social engagement and on-chain actions blend naturally, with consumption woven effortlessly into every interaction.
Transforming Daily Experiences: Smart Widgets in Action
YakiHonne Smart Widgets bridge social engagement and on-chain consumption, delivering a wide range of use cases: - On-Chain Interactions: While browsing their feed, users can join on-chain votes or play lightweight games through Smart Widgets—like casting a vote on a community proposal or challenging a friend to a quick game, all without leaving the app. - Smart Agents: Users can leverage Agent Widgets to auto-create and share content, such as personalized posts or short videos, powering an AI-driven media experience. - DAO Governance: Using aMACI for anonymous voting, combined with Agent Widgets for autonomous governance, users can participate in DAO decisions directly within their feed, fostering decentralized community growth. - Social Zap: Users can send small tips through their feed, like rewarding a friend’s post with an on-chain token, sparking more engagement and driving consumption. - Content Subscriptions: Support creators or apps with ongoing subscriptions—users can subscribe to their favorite services with one tap, enjoying a seamless renewal experience.
These scenarios not only boost user engagement and convenience but also open new growth opportunities for creators, developers, and communities.
Shaping the Future: The Ecosystem Impact of Smart Widgets
YakiHonne Smart Widgets are poised to transform the on-chain app ecosystem and social payments. They provide an open platform for developers, enabling anyone to deploy innovative apps quickly and enrich YakiHonne’s ecosystem. YakiHonne’s social payment infrastructure further empowers Mini Apps by offering efficient payment support, reducing integration costs for developers while ensuring a secure, seamless transaction experience for users. This support accelerates the commercialization of Mini Apps and fuels the growth of on-chain consumption.
For users, Smart Widgets seamlessly blend social interaction with consumption, creating an immersive and practical digital experience. For creators and communities, they offer a low-barrier entry to on-chain opportunities, helping them connect with a global audience. This product isn’t just a technological leap—it’s a glimpse into the future of decentralized lifestyles. YakiHonne is committed to building an open, vibrant social and consumption ecosystem through Smart Widgets, where every interaction sparks on-chain value.
Join the Future: Explore Smart Widgets Today
YakiHonne invites users and developers worldwide to join this exciting journey. Developers can apply to join the Smart Widgets SDK testing program, creating their own Mini Apps and tapping into YakiHonne’s global user base. Users can follow YakiHonne on official channels –X or download the YakiHonne iOS/Android app– to experience the next generation of on-chain interactions and social payments.
YakiHonne Programmable Smart Widgets are set to launch a new chapter for social and on-chain consumption. Let’s embrace this transformation together!