-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ cdee943c:5e637400
2025-04-15 08:38:29
@ cdee943c:5e637400
2025-04-15 08:38:29Flotilla-Budabit is fork of Flotilla which aims to provide a first class, git-centric community experience for developers. Based on the popular Coracle client, Flotilla is a drop in replacement for Matrix/Discord/Slack, using a variation of NIP-29. This post is a result of a brainstorming session for features that would deliver the best possible user experience.
1. Repositories Overview
Goal: Browse and discover Git repositories. - Project cards showing name, description, tags, clone URL. - Buttons: Star, Watch, Fork. - Links to discussion channels and activity.
Powered by:
kind:30617
2. Branch and Tag View
Goal: Show active branches and tags with latest commits. - Branch/tag selector - HEAD pointer visualization - Timeline of commits
Powered by:
kind:30618
3. Issues Board
Goal: Track bugs, discussions, and feature requests. - Markdown issue rendering - Labels and status indicators - Threaded comments
Powered by:
kind:1621,kind:1630–1632
4. Patch Threads
Goal: View and discuss patches as threaded conversations. - Rich patch preview - Reply threads for review - Revision tracking
Powered by:
kind:1617,kind:1630–1633,NIP-10
5. Pull Request UX
Goal: Display patch series as PR-style units. - Patch stack visualization - Merge/apply status indicators - Final result commit link
Powered by:
kind:1617,kind:1631,merge-commit,applied-as-commits
6. Diff and Merge Preview
Goal: Side-by-side comparison with inline comments. - Expandable diff viewer - Merge conflict resolution UI - Apply/Close buttons
Powered by:
kind:1622,parent-commit,commit
7. Real-time Git Chat
Goal: Communicate in real-time around a repo. - Dedicated chat channels for each repo - Markdown, code snippets, and tagging support - Pinned patches, issues, and sessions
Powered by:
NIP-29,a:30617,kind:1337
8. Notifications and Mentions
Goal: Alert users to relevant events. - Mentions, assignments, and status changes - Personal notification pane
Powered by:
ptags,mentione-tags
9. Repository-Wide Search
Goal: Search patches, issues, snippets. - Full-text search with filters - Search by kind, label, commit ID
Powered by:
kind:1617,1621,1337,t,x,l,subject
10. Repository Wikis
Goal: Collaboratively edit and view project documentation. - Wiki sidebar tab - Markdown articles with versioning - Linked inline in chat
Powered by (proposed):
kind:1341(Wiki article)
kind:30617withwiki-hometag
11. Live Coding Sessions
Goal: Host real-time collaborative coding events. -
/livecodestarts a session thread - Snippets auto-tagged to session - Export as patch or wikiPowered by (proposed):
kind:1347(Live coding session)
kind:1337,kind:1622,kind:1341
Supporting Tools
1. GitHub Browser Extension
Goal: Publish GitHub content to Nostr directly. - “Share on Nostr” buttons on PRs, issues, commits
Backed by:
kind:1623,1622,1617,1621
2. VS Code Extension
Goal: Enable developers to interact with Flotilla from their IDE. - Repo feed, patch submission, issue tracking - Inline threads and comment rendering
Backed by:
kind:1617,1621,1337,163x
3. GitHub Actions Integration
Goal: Automate Nostr publishing of repo activity. - Push = repo state - PR = patch - Issue/Comment = issue - Merge = status update
Backed by:
kind:30618,1617,1621,1631
Configured via.nostr.yml -
 @ edeb837b:ac664163
2025-04-16 12:59:09
@ edeb837b:ac664163
2025-04-16 12:59:09If you’ve spent any time around stock trading communities, chances are you’ve heard the name Webull pop up more than once. It’s not just another brokerage app—it’s one of the go-to platforms for retail traders across the globe. But what exactly is Webull? Why do so many individual traders prefer it over other platforms? And how does NVSTly take its capabilities even further?
Let’s break it all down.
What Is Webull?
Webull is a commission-free trading app that allows users to trade stocks, ETFs, options, and cryptocurrencies from their phones or desktop. Launched in 2017, it quickly gained popularity for its sleek interface, real-time data, and powerful tools—all without the traditional fees associated with many brokerage platforms.
While it’s often compared to Robinhood, Webull caters more to active traders and those who want slightly more advanced tools without the complexity (or costs) of institutional-level platforms.
What Can You Do on Webull?
Webull offers a full suite of features for modern traders:
- Commission-free trading for stocks, options, ETFs, and crypto
- Extended trading hours (premarket and after-hours)
- In-depth charting tools with technical indicators
- Fractional shares trading to invest with any dollar amount
- Paper trading for practice without real money
- Level 2 market data (Nasdaq TotalView, subscription-based)
- Custom alerts and watchlists
- Community feed for trade ideas and discussions
Whether you’re a beginner trying to learn the ropes or an experienced trader managing multiple positions daily, Webull is designed to give you an edge.
Why Retail Traders Prefer Webull Over Other Brokers
Here are some reasons why Webull has become a fan favorite among retail traders:
✅ Advanced Tools, Simple UI
Unlike many traditional brokers with clunky interfaces, Webull balances powerful tools with a user-friendly design. You get access to real-time quotes, charting with dozens of indicators, and customizable layouts—all wrapped in a clean, modern app.
✅ Free Options Trading
While some platforms charge per contract or per trade for options, Webull offers commission-free options trading, which is a huge win for active options traders.
✅ No Account Minimums
New traders can get started with as little (or as much) money as they want. There are no minimum deposit requirements for standard cash or margin accounts.
✅ Fractional Shares
Webull lets users invest in fractional shares, meaning you don’t need to buy an entire share of high-priced stocks like Amazon or Tesla. You can invest as little as $5 into a stock, making it easier to build a diversified portfolio with any budget.
✅ Paper Trading
Webull gives users a way to test strategies in a simulated environment, which is perfect for learning without risking real money.
✅ Mobile & Desktop Support
Webull’s mobile app is robust, but the desktop version is just as powerful—great for traders who prefer multi-screen setups or deeper analysis.
Webull Pros & Cons
✅ Pros
- $0 commissions on stocks, options, ETFs, and crypto
- Clean and intuitive interface
- Real-time data and news
- Built-in paper trading
- Fractional shares
- Support for extended hours trading
- Level 2 market data available
⚠️ Cons
- No mutual funds
- Webull uses a high spread for crypto trading
- Slight learning curve for beginners
How NVSTly Supercharges Your Webull Experience
Webull is powerful on its own—but when integrated with NVSTly, it becomes next-level.
NVSTly is the fastest-growing social trading app, where traders can automatically track, share, and analyze their trades, all in one place. Thanks to deep Webull integration, you can now connect your Webull account to NVSTly in seconds.
🔗 Connect in Seconds with a QR Code
Linking your Webull account is as simple as scanning a QR code inside your NVSTly account settings using the Webull mobile app. That’s it—your trades are now synced automatically.
💼 What You Get with NVSTly + Webull
- Auto-tracked trades — No more manual logging or screenshots
- Real-time trade sharing — Followers see your trades as they happen
- Performance analytics — Gain insights into your win rate, risk/reward, and more
- Automate your trade signals — Save time and help followers catch entries earlier, closer to your price
- Trade history dashboards — View and share detailed stats for your trades, with visual breakdowns
- Daily/Weekly/Monthly Recaps — Get beautifully designed trade summaries sent straight to your Discord or social profiles
Whether you’re a solo trader or part of a larger trading community, NVSTly makes it ridiculously easy to share your journey, learn from others, and improve your performance—all while staying 100% focused on the markets.
Final Thoughts
Webull has earned its spot as a top-tier brokerage app for retail traders, offering a powerful platform with zero commissions and high-quality tools. When paired with NVSTly, your trading becomes smarter and more connected—automating the way your trades are tracked, shared, and analyzed, so you can focus on the markets while NVSTly handles the rest.
If you’re a Webull user and haven’t connected to NVSTly yet, now’s the time. Your trading deserves more than just a broker—it deserves a platform built to grow with you.
Ready to level up your Webull trading?
➡️ Sign in to NVSTly, go to Brokerages & Exchanges in your account settings, click Connect next to Webull, and follow the QR code instructions to link your account in seconds.Available on web, iOS, Android, & fully integrated with Discord through a unique bot – the only of its kind!
-
 @ 7d33ba57:1b82db35
2025-04-16 12:52:15
@ 7d33ba57:1b82db35
2025-04-16 12:52:15Addo Elephant National Park is a premier wildlife destination in South Africa's Eastern Cape, located approximately 70 km from Gqeberha (formerly Port Elizabeth). Established in 1931 to protect a small group of elephants, the park has since expanded to become the third-largest national park in the country, encompassing diverse landscapes from the Karoo to the coast.
🐘 Wildlife Highlights
-
Elephants:Home to over 600 elephants, the park offers exceptional opportunities to observe these majestic creatures in their natural habitat
-
Big Five:In addition to elephants, visitors can encounter lions, leopards, buffaloes, and black rhinos.
-
Big Seven:The park's marine section includes great white sharks and southern right whales, making it one of the few places boasting the "Big Seven.
-
Other Species:The park hosts a variety of wildlife, including zebras, antelopes, meerkats, and over 400 bird species.
🚙 Activities
-
Self-Drive Safaris Explore the park at your own pace on well-maintained road.
-
Guided Game Drives Join expert-led tours for in-depth wildlife viewing experience.
-
Hiking Trails Discover the park's diverse flora and fauna on designated walking path.
-
Bird Watching With a rich avian population, the park is a haven for bird enthusiast.
-
Picnic Spots Enjoy meals amidst nature at designated picnic area.
🏨 Accommodation
The park offers various lodging options, including rest camps and luxury lodges like Camp Figtree, catering to different preferences and budges.
🌿 Visitor Tips
-
*Malaria-Free: The park is located in a malaria-free zone, making it suitable for families and travelers of all aes.
-
*Accessibility: Easily reachable from Gqeberha, it's an excellent addition to a Garden Route itinerry.
-
*Conservation Efforts: The park plays a crucial role in preserving South Africa's biodiversity, offering visitors a chance to support and learn about conservation initiaties.
For more information and to plan your visit, you can explore the official SANParks website.
-
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 0121e6f7:1a7c8df4
2025-04-16 12:37:37
@ 0121e6f7:1a7c8df4
2025-04-16 12:37:37hi2
-
 @ 52524fbb:ae4025dc
2025-04-09 03:36:09
@ 52524fbb:ae4025dc
2025-04-09 03:36:09 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkin
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkinNostr most Amazing Features
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ 06639a38:655f8f71
2025-04-16 12:11:31
@ 06639a38:655f8f71
2025-04-16 12:11:31Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ 5188521b:008eb518
2025-04-16 09:09:48
@ 5188521b:008eb518
2025-04-16 09:09:48Why write a book about time?
My obsession with time actually started when I read An Occurrence at Owl Creek Bridge (written by Ambrose Bierce in 1890).
We can’t play around with time in the real world, but in fiction, anything goes. The story of Owl Creek Bridge follows a Confederate sympathiser condemned to death by hanging. In its three sections, time goes forward and back, speeds up and slows down, and at one point stops entirely. Every time I read it, I feel like I’m physically travelling in time.
I went a bit deeper into the topic back in 2020. Due to the lockdown, I had a lot of time on my hands to do some research. Like many of my stories, this one started with a question: I started to ask ‘what actually is time’?
What did you find out?
I found out that time is a rabbit hole! Nobody knows exactly what it is. We know that it’s conceptual, personal, and malleable, however accurate our watches are. Some philosophers and scientists (Jose Luis Borges and Carlo Rovelli) claim it doesn’t exist.
I guess what I discovered is that we all need time to survive. It’s how we process our experience here on Earth.
Who are the characters in this book?
The book tells the story of Luca Cangemi, an Italian philosophy professor giving a lecture on the subject of time. The chapters follow the possible lives of other characters in the lecture hall. Then, Cangemi makes an astounding discovery. It’s something that allows him to change the fabric of time for everyone (including the readers).
Why use 15 characters to present the story?
I like to challenge readers, so I made the story a bit of a puzzle. In fact, there is something called a 15 puzzle — it’s a block of 15 pictured tiles and one space. You have to slide them to arrange the correctly ordered image. There’s more about the puzzle in the book.
What about the Timechain? Is there any link there?
Not exactly. The book doesn’t mention it, but isn’t everything an analogy for bitcoin? Soon after finishing this book, I got orange pilled and began to read more and more about bitcoin, including Gigi’s fantastic essay Bitcoin is Time.
Time is all we have though. Even though it might be hard to understand, we have to try.
Who do you think would enjoy this book?
I’d say sci-fi fans. Those who aren’t afraid to be challenged. One cool thing about the bitcoin community is that they are dialled in to technical stuff and they are avid readers. Why not give fiction a try too? Sometimes we learn more from getting the answer ourselves through stories.
What are you working on next?
I have three other writing projects on the go, so there is no time to rest. Very soon, I’ll be publishing a children’s book about horrible uncles. I’m editing the next installment of 21 Futures too. Financial Fallout will be out in early 2025. And finally, I’m writing content and newsletters for bitcoin founders and companies. If I’m not trying to sell you a book, I’ll be doing my best to orange-pill you, ha ha.
Thanks for talking with us, Philip, and good look with all those writing projects.
Order the book in our store.
Here’s a passage from Fifteen Shades of Time.
The Direction of Everything
Luca Cangemi and everyone he knows will be long dead, but the moment will come. Theoretical physicists believe it will be anywhere from 2.8 to 22 billion years in the future. In that moment, everything reverses.
The Big Crunch is a cosmological event in our future and our past in which the density of matter grows sufficiently that gravitational attraction overcomes the expansion that began with the Big Bang. Entropy reverses and the second law is broken. Chaos retreats.
Order is regained as space contracts. Broken rocks reform and decayed bodies reanimate. We live our lives in reverse, unexperiencing everything we did the first time around, moving backwards, shrinking towards birth. Instead of questions about creation, we search for the harbinger of order. Who began this? What is our final form?
Luca imagines the crowds at his book signings dissipating and the offices of his academic fellowships decreasing in size. Wrong turns are righted and his family grows closer. His briefcase heals itself and he returns it to his mother. Life rewinds back to him as a young boy, unreading the words that inspired him to look for meaning in all of this. If it can all be reversed, are all shared experiences undone? All bonds broken? Luca returns into his parents, then ancestors, apes, microbes, and nothing. The earth, the planets and stars all merge into one perfectly ordered mass.
Yet, this is not an end, but another beginning in which the universe is reborn in another bang. Galaxies, planets, plants, and philosophy professors will live the same lives as they did billions of years before (and after). The process of positive and negative entropy repeats and we all make the same mistakes again.
Time elapsed: the infinitely repeating cycle of a universe
Philip Charter is a totally human writer, laser-focused on spreading the gospel of bitcoin and cypherpunk ideals. He is the editor of the 21 Futures anthology series and has published four books of short fiction. After leaving the UK to search for more sun, he now resides in Gran Canaria, Spain.
-
 @ 7d33ba57:1b82db35
2025-04-16 08:31:09
@ 7d33ba57:1b82db35
2025-04-16 08:31:09Iceland is a surreal blend of volcanic power, glacial beauty, and rugged wilderness. From black sand beaches and steaming geothermal pools to massive waterfalls and the magical northern lights, it’s a dream destination for nature lovers and road trippers.
Whether you want to soak in a hot spring, chase waterfalls, hike volcanoes, or just drive through epic landscapes that look straight out of a fantasy film, Iceland has it all.
🧭 Top Things to Do in Iceland
1️⃣ The Golden Circle
The perfect intro loop from Reykjavik: - Þingvellir National Park – Rift valley between tectonic plates + historic parliament site
- Gullfoss – Thundering two-tier waterfall
- Geysir geothermal area – Home of the original geyser (and Strokkur, which erupts every few minutes)2️⃣ South Coast Highlights
- Seljalandsfoss & Skógafoss – Iconic waterfalls you can walk behind or get soaked by
- Reynisfjara Black Sand Beach – With eerie basalt columns and crashing Atlantic waves
- Sólheimajökull Glacier – Guided glacier walks or ice climbs
- Vík – Quaint village with epic coastal views
3️⃣ Snæfellsnes Peninsula
- Often called “Iceland in Miniature”
- Includes Kirkjufell mountain, lava fields, fishing villages, and coastal cliffs
- Great alternative if you’re short on time but want variety
4️⃣ The Blue Lagoon (or better: Sky Lagoon)
- Iconic milky-blue geothermal spa near the airport
- Sky Lagoon near Reykjavik is newer, less touristy, and has a 7-step ritual sauna-spa experience with ocean views
5️⃣ Chase the Northern Lights
- Best seen September to April
- Get away from city lights and use apps or tours to track them
- Clear skies, cold nights, and some patience = magic
🚗 Epic Road Trip: The Ring Road
- Iceland’s main highway (Route 1) loops the entire island
- Takes about 7–10 days to do well
- You’ll see glaciers, fjords, waterfalls, volcanoes, and maybe even puffins and reindeer
- Rent a campervan or car and take it slow—it’s all about the journey
🍽️ What to Eat in Iceland
- Lamb stew (kjötsúpa) – Warm and hearty
- Plokkfiskur – Creamy fish and potato comfort food
- Skyr – Icelandic yogurt, smooth and protein-rich
- Hot dogs from Bæjarins Beztu – Iconic street food in Reykjavik
🗓️ When to Go
- Summer (June–Aug): Midnight sun, hiking, puffins, easier driving
- Winter (Oct–Mar): Aurora season, ice caves, snowy wonderland
- Shoulder seasons: Fewer crowds, lower prices, unpredictable weather (pack layers!)
✨ Quick Tips
✅ Tap water = some of the purest in the world
✅ Always check road and weather conditions—they can change fast
✅ Download Veður (weather) and SafeTravel.is for safety updates
✅ Book hot springs, ice cave tours, and northern lights hunts in advance during high season -
 @ da0b9bc3:4e30a4a9
2025-04-16 08:28:24
@ da0b9bc3:4e30a4a9
2025-04-16 08:28:24Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/944844
-
 @ ffbcb706:b0574044
2025-04-16 08:11:12
@ ffbcb706:b0574044
2025-04-16 08:11:12I like to have openletter on the Nostr protocol
-
 @ 2b24a1fa:17750f64
2025-04-16 07:55:24
@ 2b24a1fa:17750f64
2025-04-16 07:55:24„Ich bin der Weg“, sagt Jesus am Kreuz, in der Mitte. Symbolisch zwischen Übertreibung und Verblendung. Wenn dieser Maßstab an das Gros der Nachrichten angelegt wird, die wir in den letzten fünf Jahren vermittelt bekamen, landen wir selten in der Mitte. Aber nur der gelassene Blick in Richtung Übertreibung und Verblendung, lässt die Mitte zwischen ihnen erspüren.
https://soundcloud.com/radiomuenchen/angst-frisst-seelen-von-j-rgen?
Auf den Weg dorthin begibt sich eine Friedensprozession am Karfreitag, den 18. April ab 13 Uhr, ausgehend vom Postplatz in Dresden. Hören Sie Jürgen Flieges Text: „Angst frisst Seelen“.
Sprecher: Guido de Gyrich.
-
 @ 2b24a1fa:17750f64
2025-04-16 07:52:59
@ 2b24a1fa:17750f64
2025-04-16 07:52:59Am 22. November 1963 starb US-Präsident John F. Kennedy bei einem Attentat in Dallas durch zwei Gewehrschüsse. Als möglicher Täter wurde Lee Harvey Oswald verhaftet und zwei Tage später erschossen. Kennedys Amtsnachfolger Lyndon B. Johnson setzte einen Untersuchungsausschuss ein: die Warren-Kommission, benannt nach deren Leiter Earl Warren, höchster Richter am Supreme Court, dem Obersten Gerichtshof der Vereinigten Staaten. Die Warren-Kommission bestätigte die Einzeltäter-These. Dennoch kursierten und kursieren bis heute zahlreiche Gerüchte und Verschwörungstheorien. Mit dem Totschlag-Argument „Nationale Sicherheit“ verweigerte die CIA die Herausgabe ihrer Ermittlungsakten und nährte gerade dadurch den Verdacht, sie selbst habe Kennedy ermorden lassen. Über 60 Jahre später gibt Präsident Trump nun die Akten frei.
https://soundcloud.com/radiomuenchen/trump-die-jfk-files?
\ Die Meinungen gehen auseinander: Für die einen enthalten die Akten wenig Neues, für die anderen ergeben sich neue Zweifel an der Einzeltäter-These. Unsere Autorin Gaby Weber befasst sich schon seit vielen Jahren mit der Materie, unter anderem in ihrem Buch „CIA, Drogen, Gehirnwäsche“ von 1981. Außerdem recherchiert sie seit langem über illegale Atomwaffentests des Pentagons in Argentinien 1960. Zwischen den illegalen Atomwaffentest und Kennedys Tod könnte es einen Zusammenhang geben, glaubt Gaby Weber und hat einen neuen Antrag auf Aktenfreigabe gestellt. Hören Sie ihren Beitrag: „Trump & die JFK-Files“.
Sprecherin: Gaby Weber
Redaktion: Jonny Rieder
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927
-
 @ 2b24a1fa:17750f64
2025-04-16 07:40:49
@ 2b24a1fa:17750f64
2025-04-16 07:40:49„Auch wenn das völliger Wahnsinn ist“ … soll der Freie-Wähler-Chef gesagt haben: „Die CSU kann auch ohne uns im Bundesrat zustimmen. Deswegen bringt es nichts, wenn wir uns weiter dagegenstellen.“ Man opfert also die eigene Einstellung und stimmt für das Gegenteil, legitimiert also den Wahnsinn, weil es nichts bringt? Hört mit dieser Schizophrenie auf – möchte man schreien. Denn täglich hören wir von führenden deutschen Politikern, die ohne relevante Begründung die irrwitzigsten Entscheidungen treffen und den Souverän übergehen, als wäre er Luft.
Jetzt sollte dieser Souverän, der Bürger aber nicht mit Hilflosigkeit reagieren, meint Ludwig F. Badenhagen, denn es existiere ein einfacher als auch wirksamer Lösungsansatz. Hören Sie seinen Text: „Wie wir die Kriegstreiber stoppen“. Sprecherin: Sabrina Khalil.
Sie hörten: „Wie wir die Kriegstreiber stoppen“ von Ludwig F. Badenhagen. Ludwig F. Badenhagen ist ein Pseudonym für einen Autor mit deutschen Wurzeln, der das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika beobachtet. Er ist international agierender Manager mit globalem Netzwerk und verfügt dadurch über tiefe Einblicke in Konzerne und Politik. Sein Text erschien zunächst auf Milosz Matuscheks Friedensinitiativseite „Friedenstaube“.
-
 @ 2b24a1fa:17750f64
2025-04-16 07:32:45
@ 2b24a1fa:17750f64
2025-04-16 07:32:45Wo läßt es sich trefflicher plaudern als am Küchentisch. Es muß ja nicht unbedingt der eigene sein. Hauptsache, es sitzen vergnügte Menschen reinen Herzens daran, wie zum Beispiel die Herren Helmut Schleich und Franz Esser.
https://soundcloud.com/radiomuenchen/am-kuchentisch-mit-schleich-und-esser
-
 @ 9c9d2765:16f8c2c2
2025-04-07 07:39:53
@ 9c9d2765:16f8c2c2
2025-04-07 07:39:53CHAPTER TWO
“This is just a gift,” he said casually. “A small show of goodwill. But if you want my real help, the six hundred million dollars you need, there's one condition.”
He turned to Rita and smiled.
“I want Rita as my wife.”
Silence fell over the room.
Helen was the first to speak. “That can be arranged.”
James, who had been listening from outside the room, felt his chest tighten. He pushed the door open, his heart pounding.
“No,” he said firmly.
Mark raised an eyebrow. “Excuse me?”
“She’s my wife,” James said, standing his ground.
Helen turned to him with a scowl. “Not for long.” She slid a divorce document across the table. “Sign it, James. Stop being selfish.”
James stared at the papers.
Christopher’s voice was sharp. “You don’t belong here, James. If you truly love Rita, you will let her go.”
Rita’s eyes met James’. There was fear in them, but also love.
James clenched his fists.
“No,” he said again.
Then, without another word, he turned and stormed out of the event.
James walked through the cold night, his hands clenched into fists. His heart pounded with frustration. The humiliation he had endured at the Ray family’s business anniversary was unbearable. They had treated him like an outsider, an unwanted burden. Now, they were pressuring him to sign the divorce papers so they could sell Rita off to Mark, a man who was nothing but a privileged opportunist.
How did it come to this?
James had given everything to the family: his loyalty, his love, his hard work. And yet, the moment Grandpa Ray passed away, the rest of the family turned against him.
His phone vibrated in his pocket.
At first, he ignored it, assuming it was yet another message from Helen or Christopher, demanding that he sign the divorce papers. But when it vibrated again, curiosity got the best of him.
He pulled out his phone and saw a notification from an unknown number.
New Email: Urgent Financial Notice – Deltacore Inc.
James frowned. Deltacore?
The name stirred a faint memory. He hadn’t thought about that company in years. Back when he was still working in his father's company before he was falsely accused of embezzlement he had invested a small amount of money in Deltacore Inc., a rising tech company that had shown promise. However, soon after, Deltacore went bankrupt, and James had written off his investment as a loss.
His chest tightened as he opened the email.
Dear Mr. James,
We are pleased to inform you that your investment in Deltacore Inc., which had previously been marked as a loss, has now yielded significant returns. Under new management, Deltacore Inc. has resumed operations and successfully expanded into international markets.
As an early investor, your stake originally valued at $50,000 has now grown exponentially, reaching a current market valuation of $2.7 billion.
Kindly contact our financial department at your earliest convenience to discuss the liquidation or management of your newfound assets.
Best Regards, Jonathan Reed CFO, Deltacore Inc.
James stopped dead in his tracks. His breath caught in his throat.
Two point seven billion dollars.
His eyes scanned the email over and over again, ensuring he wasn’t hallucinating. But no, the numbers were real. His tiny investment had transformed into an unimaginable fortune.
A mixture of shock and disbelief rushed through him.
For years, he had been treated as a nobody, abandoned and looked down upon. But now… now, he was wealthier than the entire Ray family combined.
James’ grip on his phone tightened.
Everything had changed. The next morning, James wasted no time. He called the number listed in the email and scheduled an urgent meeting with Deltacore Inc.
By the afternoon, he was sitting in a high-rise office in the heart of the financial district. The company’s top executives treated him with the utmost respect, referring to him as one of their founding investors.
“We’ve been trying to reach you for months,” Jonathan Reed, the CEO, explained. “But since your contact information had changed, it was difficult to locate you.”
James leaned back in his chair. “I never imagined this would happen. I thought Deltacore was finished.”
Reed chuckled. “It was. But a few years ago, new investors stepped in, acquired the company’s patents, and relaunched operations. As an early investor, your small stake remained valid, and with our recent expansion into global markets, your shares skyrocketed.”
James exhaled slowly, trying to process it all.
“I’d like to access my funds immediately,” he said.
“Of course,” Reed nodded. “Do you have any immediate plans for wealth?”
James smiled slightly. Oh, I have plans A mixture of emotions surged within him shock, excitement, and most of all, vindication.
And yet… instead of feeling triumphant, an unsettling thought crept into his mind.
If they knew…
If the Ray family discovered his newfound wealth, they would come crawling back, pretending to care, pretending they had always loved him. Helen would try to manipulate him, Christopher would suddenly call him ‘son,’ and Stephen, who had never hidden his disdain, would act as if they were close brothers.
They would all turn against Rita, forcing her to beg for his forgiveness just to secure their own future.
James clenched his jaw.
No. They don’t deserve to know.
Not yet.
Instead of revealing his fortune, he made a decision. The once-thriving empire of Ray Enterprises stood on the edge of collapse. The financial crisis had drained the company’s reserves, forcing them into a corner with no easy escape. Suppliers had begun cutting ties, employees whispered about mass layoffs, and investors were pulling out faster than anyone could stop them.
At the center of this storm was Robert Ray, the younger brother of the late Grandpa Ray. Unlike Helen, Christopher, and Stephen who had spent years living off the company’s wealth without truly working for it, Robert had always valued the legacy built by his older brother.
So when the crisis deepened, he did something unthinkable.
He reached out to James.
James had been cast out of the family, humiliated, and disowned after Grandpa Ray’s death. He had been treated as an outsider despite being the only person who had ever truly respected the company’s values. And yet, despite it all, Robert knew that James was their only hope.
Late one evening, Robert arrived at James’s side of the apartment, he was led inside the house, his hands sweating as he stepped into the living room, James sat, calm and unreadable.
James didn’t offer him a seat.
“I assume you’re not here for pleasantries,” James said, his voice cold but controlled.
Robert hesitated before speaking. “James, I know… I know we don’t deserve your help. I know what Helen and the others did to you. But Ray Enterprises is”
“Dying?” James finished for him.
Robert swallowed hard. “Yes.”
James leaned back in his chair, studying the older man. There was no amusement in his expression, no gloating, just the sharp, analytical mind that had made him a billionaire in his own right.
“And now you come to me?” James asked. “After everything?”
Robert exhaled. “I won’t make excuses. I won’t even ask for forgiveness. But I’m asking for your help.”
James was silent for a long moment.
Then, he spoke.
“I’ll do it.”
Robert’s eyes widened. “You will?”
“But under one condition.”
Robert tensed. “What is it?”
James’s lips curled into a slight smirk.
“I want full control. I want to be the President of Ray Enterprises.”
The words hung in the air like a thunderclap.
Robert hadn’t expected this, but he should have. James had been treated like nothing more than an outsider, a disposable nuisance. Now, he was making it clear that if they wanted his help, he would no longer be a guest in the Ray family business.
He would be its ruler.
After a long pause, Robert nodded.
“Fine,” he said. “I’ll make it happen.”
-
 @ 9c9d2765:16f8c2c2
2025-04-05 10:45:11
@ 9c9d2765:16f8c2c2
2025-04-05 10:45:11CHAPTER ONE
Grandpa Ray’s birthday was a grand celebration. His children and grandchildren gathered around, each presenting him with expensive gifts, golden watches, fine suits, and rare wines. The room buzzed with excitement and laughter.
Among them was James, Grandpa Ray’s adopted son. Unlike the others, James had no gift to offer. He stood quietly, watching as each family member received warm praise for their presents.
Then, Grandpa Ray did something unexpected. With a kind smile, he said, “Today, I want to give you all a gift instead. Ask for anything, and I will grant it.”
Excited, his children and grandchildren eagerly requested expensive things luxury cars, houses, money, and positions in the family business.
When it was James’ turn, he hesitated for a moment before saying, “Grandpa, I would like a shovel.”
A hush fell over the room, then erupted into laughter.
“A shovel?” one cousin sneered. “What a silly request!” another chuckled.
But Grandpa Ray raised a hand, silencing them. He looked at James with curiosity. “Why a shovel, my boy?”
James took a deep breath and replied, “I don’t need riches handed to me. I want to work for my own wealth. A shovel will help me till the land, plant crops, and build something for myself.”
Grandpa Ray’s eyes gleamed with pride. He nodded and said, “That is a wise request. Not only will I give you a shovel, but I will also grant you a piece of land to farm.”
The laughter died down. The others had asked for luxury, but James had asked for a tool to create his own future. James had once lived a life of promise. He was hardworking, loyal, and dedicated to his family’s company. But his world came crashing down when he was falsely accused of embezzlement. His own parents, ashamed of the scandal, disowned him without listening to his pleas of innocence.
Alone and broken, James had nowhere to go. It was then that Grandpa Ray, a man known for his wisdom and kindness, took him in. Unlike the rest of the world, Grandpa Ray saw something in James his resilience, his honesty, and his potential.
Despite being adopted into a wealthy and powerful family, James never truly felt accepted. The others in the family pretended to love him, but behind his back, they whispered that he was a burden, an outsider. The only one who genuinely cared for him besides Grandpa Ray was Rita, the old man’s granddaughter.
Over the years, James worked hard to earn his place in the family. He managed some of Grandpa Ray’s businesses, proving his intelligence and dedication. Rita, a kind and spirited woman, saw the goodness in him. Their bond grew stronger, and soon, love blossomed between them.
Grandpa Ray, seeing James’ sincerity and loyalty, made a bold decision he gave Rita’s hand in marriage to James, despite the objections of the rest of the family.
"You have proven yourself to be a man of honor," Grandpa Ray said to James on the wedding day. "And I know that you will cherish Rita the way she deserves."
The rest of the family smiled in public but harbored resentment in their hearts. To them, James was an unworthy orphan who had stolen their grandfather’s favor.
When Grandpa Ray passed away, everything changed. The mask of fake love that the family had worn for years finally fell off. Without Grandpa Ray to protect him, James became a target of humiliation.
Helen, Rita’s mother, Christopher, her father, and Stephen, her brother, openly ridiculed him. They made life unbearable, treating him like a servant rather than a family member.
"You don’t belong here," Stephen sneered one evening. "You were just Grandpa’s charity case."
James endured the insults in silence, holding onto the love he shared with Rita. But his in-laws had other plans; they wanted him out of Rita’s life for good.
Helen and Christopher believed that Rita had made a mistake by marrying James. They wanted her to divorce him and marry someone who would elevate the family’s status. That’s when Helen introduced Mark, the only son of the Prime Minister.
Mark was wealthy, powerful, and came from a family of high political influence. To her, he was the perfect husband for Rita.
"Rita, darling," Helen said sweetly, "don’t waste your life with James. You deserve someone who can give you the life of luxury you were born into."
Stephen agreed. "Mark is everything James is not rich, powerful, and from a good family. Be wise, sister."
But Rita stood firm.
"I love James," she said. "And I will not betray him, no matter how much you pressure me. James and I made a promise to Grandpa never to leave each other"
Helen, frustrated by Rita’s refusal, tried to manipulate her further. She arranged secret meetings between Rita and Mark, hoping she would be swayed. She even planned an engagement dinner, assuming Rita would eventually give in.
Meanwhile, James felt the weight of the battle. He saw how much pressure Rita was under and, one evening, he took her hands and said, "Rita, if leaving me will make your life easier, I won’t stop you."
Tears filled her eyes. "James, my love isn’t based on status or wealth. I chose you, and I will keep choosing you no matter what, you have forgotten the promise we two made to Grandpa before he died, in case you have forgotten, I haven't"
That night, Rita made her choice. She called a meeting to inform everyone that nothing will make her leave James for another man, James couldn't withstand the joy she made her that night, choosing love over wealth and status.
With nothing but their love and determination, James and Rita started anew. They built their life from scratch, with James working tirelessly to create a name for himself.
The Ray family had once been a symbol of wealth, power, and success, but in recent months, everything had started crumbling. A series of financial setbacks, business failures, and internal conflicts had pushed the family into a dire situation. The creditors were knocking, the banks were threatening to withdraw their support, and their empire was on the verge of collapse.
Desperation clouded every decision they made. And in that desperation, they saw only one way out is Mark.
Mark, the only son of the Prime Minister, was not just a man of wealth but also of power and influence. He had been interested in Rita for years, but she had always refused him, choosing instead to marry James. But now, with the family drowning in crisis, Mark became their only hope.
Helen, Rita’s mother, sat across from Christopher, her husband, and Stephen, their son. The tension in the room was thick.
“We have no other choice,” Helen said firmly. “Mark is willing to help us, but he wants something in return.”
“We all know what that is,” Stephen said, glancing at Rita, who sat silently in the corner of the room.
Christopher sighed. “James is the only obstacle left. We have to make Rita understand that this isn’t about love anymore, it's about survival.”
Helen’s voice was cold. “She will divorce him. And James will have no choice but to accept it.”
Rita looked up, her heart pounding. “You’re selling me to him,” she said in disbelief.
“Rita,” Helen said impatiently. “This isn’t about selling you. This is about securing our future. James has nothing. Mark can give you everything.”
“I don’t want everything. I want my husband.”
Helen scoffed. “Love won’t save this family.”
But Rita clenched her fists. She wasn’t going to give up on James so easily.
The Ray family organized a grand business anniversary event, using it as a cover to publicly introduce Mark as their savior. Guests arrived in expensive suits and dazzling gowns, but beneath the luxury was a desperate attempt to keep up appearances.
James had never felt more out of place. He knew he wasn’t truly welcome among the Ray family, but tonight, it was worse than ever. He could see the way people looked at him like he was an outsider, a liability.
Then Mark arrived; Tall, confident, and exuding power, he walked into the hall as if he already owned it. People flocked to him, shaking his hand, singing his praises.
And then, during a private meeting with the Ray family, he made his move.
“I know about your situation,” Mark said smoothly, placing a black suitcase on the table and opening it. Inside were stacks of cash, two million dollars.
Helen gasped. Christopher’s hands trembled.
Mark leaned back.
-
 @ 2b24a1fa:17750f64
2025-04-04 08:15:16
@ 2b24a1fa:17750f64
2025-04-04 08:15:16Ganz im Geiste des klassischen Kabaretts widmen sich Franz Esser und Michael Sailer den Ereignissen des letzten Monats: Was ist passiert? Und was ist dazu zu sagen? Das ist oft frappierend - und manchmal auch zum Lachen.
https://soundcloud.com/radiomuenchen/vier-wochen-wahnsinn-marz25-ein-satirischer-wochenruckblick?
-
 @ b0137b96:304501dd
2025-04-16 06:33:23
@ b0137b96:304501dd
2025-04-16 06:33:23In recent years, the Telugu film industry has witnessed a remarkable transformation, with a significant surge in the popularity of Hollywood movies in Telugu dubbed. This trend reflects a growing appetite among Telugu audiences for diverse storytelling and international cinematic experiences. While regional films continue to thrive, the increasing demand for Hollywood movies in Telugu dubbed speaks to a cultural shift and a desire for global entertainment. Two films that exemplify this trend are Medusa: Beauty is the Beast and its sequel, Medusa’s Venom. These movies not only showcase the appeal of Hollywood narratives but also demonstrate how familiar mythological themes can be reimagined in a contemporary context, resonating with Telugu viewers.
This article explores these two films and their significance in the broader landscape of Hollywood movies in Telugu dubbed, highlighting how this trend is reshaping the viewing habits and preferences of Telugu cinema enthusiasts.
Hollywood Movies in Telugu Dubbed
Medusa: Beauty is the Beast – Hollywood movie in Telugu dubbed (2021) Medusa: Beauty is the Beast is a horror movie that puts a modern twist on Greek mythology. After being bitten by a lethal snake, a young woman named Carly experiences changes in her senses and appearance as she sheds her old self and slowly turns into a deadly weapon. This Hollywood movie in Telugu dubbed is directed by Jeffrey and Co. and features a powerful performance by Megan Purvis as the lead actress, Carly. Most of the film takes place in a caravan site, which serves as a sanctuary for women under the protection of Medusa.
The Hollywood movie in Telugu dubbed tackles topical issues wrapped in horror, providing a tale of how women are treated in society. With a limited budget, the filmmakers have done a commendable job of creating an engaging and thought-provoking story. The film has been well-received by audiences, with 2.3k IMDb users adding it to their watchlists.
Hollywood Movies in Telugu Dubbed Medusa: Beauty is the Beast is one of the many Hollywood movies in Telugu dubbed that caters to the growing demand for international content in the region. These dubbed versions allow Telugu audiences to enjoy popular Hollywood films in their native language, making them more accessible and engaging.
The rise of Hollywood movies in Telugu dubbed represents a significant shift in the region’s cinematic landscape. It not only broadens the range of entertainment options available to Telugu-speaking audiences but also fosters a greater understanding and appreciation of diverse storytelling techniques and cultural perspectives. The success of films like Medusa demonstrates that there is a receptive audience for international content, paving the way for more innovative and diverse cinematic experiences in the Telugu-speaking regions.
Now, let’s explore the sequel of Medusa, Medusa’s Venom.
Hollywood Movies in Telugu Dubbed
Medusa’s Venom – Hollywood movies in Telugu dubbed (2023) Medusa’s Venom is a sequel to Medusa: Beauty is the Beast and continues the story of the deadly snake-woman. In this instalment, the beast is back, and her venom is deadlier than ever. When newcomer Lola is welcomed into Medusa’s circle, she undergoes a ritual to bring her closer to her new sisters.
Unlike the first film, Medusa’s Venom takes a more straightforward approach to the horror genre. It depicts a group of snake women who are also sex workers, living in a caravan site that is now under the control of Medusa. This Hollywood movie in Telugu dubbed, explores the theme of power corrupting people, as the sanctuary from the previous film has become a place of control.
Released in 2023, Medusa’s Venom avoids the subtlety and layered storytelling of its predecessor, opting for a more direct and action-oriented narrative. The film continues the Greek mythology-inspired horror elements while delving deeper into the dynamics of the snake women’s group.
Hollywood movies in Telugu dubbed: A Growing Trend The success of Medusa: Beauty is the Beast and Medusa’s Venom highlights the growing trend of Hollywood movies in Telugu dubbed. This trend allows Telugu audiences to enjoy a wider range of international films, from action blockbusters to thought-provoking dramas.
As the demand for Hollywood movies in Telugu dubbed continues to rise, more and more filmmakers are recognizing the potential of this market. By adapting popular Hollywood films for Telugu audiences, they are able to reach a larger and more diverse viewership, while also showcasing the talent and creativity of the Telugu film industry.
Wrapping Up In conclusion, Medusa: Beauty is the Beast and Medusa’s Venom are two examples of the growing popularity of Hollywood movies in Telugu dubbed. These films offer a unique blend of horror, mythology, and social commentary, providing audiences with an engaging and thought-provoking viewing experience.
As the trend continues to evolve, it has the potential to influence local filmmaking practices, encourage cross-cultural exchanges, and ultimately enrich the Telugu film industry. We are excited to see what other Hollywood movies are adapted for Telugu audiences in the future, are you?
-
 @ 2b24a1fa:17750f64
2025-04-04 08:10:53
@ 2b24a1fa:17750f64
2025-04-04 08:10:53Wir leben in einer Demokratie. So heißt es immer. Immerhin hat die Bevölkerung, der Souverän ein Mitspracherecht. Einmal alle vier Jahre. Und damit fünfundzwanzig Mal in einem Jahrhundert. Diese 25 Wahltage ergeben zeitlich 0,07 Prozent des gesamten Jahrhunderts. Würde man das Jahrhundert auf einen Tag runter rechnen, dann ergäben diese 0,07 Prozent ziemlich genau eine Minute des Mitspracherechts. Eine Minute pro Tag darf der Souverän also bestimmen, wer am restlichen Tag ungehindert schalten und walten darf – bis in das Grundgesetz hinein.
https://soundcloud.com/radiomuenchen/das-grundgesetz-als-schmierzettel-von-henry-matthes?
Die Veränderung in diesem zentralen Gesetzestexten ist allein den Parteien vorbehalten. An sämtliche Änderungen halten, dürfen sich dann nachher alle – selbst dann, wenn noch so wenige Bürger dahinterstehen.
In den letzten Wochen offenbarte sich dieser Missstand in präzedenzloser Weise. Die als Sondervermögen schön-deklarierte Neuverschuldung wurde im Grundgesetz festgeschrieben. Ist eine solch selektive Umgestaltungsmöglichkeit des wichtigsten Gesetzestext einer Demokratie würdig? Bräuchte es nicht zumindest einer Absegnung durch Volksabstimmungen?
Henry Mattheß hat sich hierzu Gedanken gemacht. Hören Sie seinen Text „Das Grundgesetz als Schmierzettel“, der zunächst auf dem Blog von Norbert Häring erschienen war.
Sprecher: Karsten Tryoke
Bild: Radio München
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ fbf0e434:e1be6a39
2025-04-16 05:38:17
@ fbf0e434:e1be6a39
2025-04-16 05:38:17Hackathon 概要
由瑞士洛桑联邦理工学院(EPFL)区块链学生协会组织的 Privacy and Verifiability Hackathon 于 2023 年 3 月 8 日至 9 日成功举办。这场 26 小时极限挑战吸引 36 名开发者注册参与,最终提交 23 个获批项目,聚焦区块链隐私与可验证性技术解决方案开发,由 Mina、Hedera Hashgraph Association 及 Hylé 等机构赞助,总奖池达 15,000 美元。
显著的成就包括在隐私增强方法和可验证区块链解决方案方面的创新。项目的评估标准包括创新性、技术执行,以及在解决隐私和可验证性问题上的有效性。所展现的多样化解决方案突出显示了区块链领域的原创性和实用应用。
Hackathon 促进了学生、专业人士和爱好者之间的协作和创造力,推进了关于隐私和可验证区块链技术的讨论。活动强调了分散化解决方案在应对隐私挑战方面的潜力,进一步确认了社区在推动区块链创新方面的承诺。
Hackathon 获奖者
Privacy and Verifiability Hackathon 以超过 25 个项目竞争 15,000 美元奖池而告终。它展示了在隐私和验证技术中取得突破的创新解决方案,分为三个类别。
Mina 奖得主
- Mina Cash: 利用 Mina Protocol 的零知识证明进行匿名支付交易,确保链上证明和链下隐私。
- zkPetitions: 一种去中心化应用程序,使用零知识证明来保护隐私和数据完整性,并进行请愿处理。
- ZKribble.io: 一种利用零知识证明游戏,在绘制和猜测上下文中保护秘密词语。
- Aether ticket: 集成 Mina Protocol 的票务验证平台,通过零知识证明实现安全、私密的验证。
- Hush tag: 使用 Mina Protocol 的去中心化票务系统,实现安全和私密的票务生成与验证。
Hedera Hashgraph Association 奖得主
- AtlasID: 使用 React、Express 和 SD-JWT VC 技术实现注重隐私的身份验证。
- donate.fun: 通过区块链和身份验证来增强人道主义援助的透明度和安全性。
- Geotrust: 用于地理寻宝的网络应用程序,具备位置创建和稳健的用户验证功能。
- Hedemon: 使用 Hedera 区块链将实物收藏品转换为可验证真实性和隐私的 NFTs。
Hylé 奖得主
- Sthylé - image verification: 基于区块链的平台,用于验证图像真实性与管理。
- zkIA: 专注于 AI 应用中的零知识证明,尽管没有提供具体技术细节。
- CipherSocial: 通过去中心化平台使用密码学和区块链,基于兴趣将用户连接起来以保护隐私。
- Plethora: 用于创建使用零知识证明的 AI 代理,完成私密、可验证的任务。
有关项目的完整列表和更多详细信息,请访问 dorahacks.io 上的 Hackathon页面 。
关于组织者
Blockchain Student Association
Blockchain Student Association 旨在教育和吸引学生参与区块链技术领域。该组织以其在区块链系统和应用方面的专业知识而闻名,积极举办研讨会和工作坊以增强成员的技术理解。它曾与行业领导者合作开展项目,专注于创新的区块链解决方案。该组织的使命是培养一个探索区块链实际应用并在快速发展的领域内提升技术素养的知识社区。
-
 @ fbf0e434:e1be6a39
2025-04-16 05:38:05
@ fbf0e434:e1be6a39
2025-04-16 05:38:05Hackathon 概述
由 SUCI Blockchain Hub 主办、CodeX 赞助的 AI Hackathon 于 2025 年 3 月 7-9 日在越南胡志明市成功举办。这场线下活动吸引 42 名开发者参与,围绕实用场景的真实资产整合与 AI 代理开发,共诞生 12 个创新项目。
此次 Hackathon 总奖池为 15,000 美元,以 USDT 和 CDX 代币形式分配。一等奖获得者获得 4,000 USDT 和 2,000 CDX 代币,以及前往泰国参加即将举办的 COTI Foundation Hackathon 的旅行和住宿。第二名和第三名分别获得 3,000 和 2,000 USDT,以及 CDX 代币。特别赛道奖项包括最佳 AI 代理、最佳无代码解决方案和最佳真实应用,每项获得 1,000 USDT 和 500 CDX 代币。其他奖项则表彰了创新 AI 应用、跨行业解决方案和社区影响。
活动促进了交流、学习和协作创新,展示了 AI 与区块链技术之间日益紧密的联系。
Hackathon 获奖者
AI Hackathon 2025 展现了技术创新和各领域的创意。历经 48 小时,参与者密集合作解决问题,评选出在三个奖项类别中的杰出项目:主要奖项、赛道奖项和特别奖项。
主要奖项获奖者
以下三个项目因其创新和实施而脱颖而出:
- VocakeX:这是一款 Web3 教育科技平台,利用游戏化和 AI 增强学习,结合 AI 驱动模块与游戏化元素,提高教育参与度和学习保持率。
- StudyVerse:通过分析学生情绪,提供个性化的健康建议和学习指导,旨在通过情感识别和自适应反馈提升教育效果的 AI 平台。
- VaultAI:一款 AI 驱动的加密钱包,设计用于复杂的资产管理和 DeFi 洞察,利用分析和机器学习优化财务决策。
赛道奖项获奖者
项目因在 AI 代理、无代码解决方案和真实应用中的成就而被认可:
- CryptoMentor:一个智能聊天机器人,帮助新投资者学习和进行加密交易,提供实时 API 集成以便可靠的帮助。
- VaultAI
- Scholar AI:一款 AI 工具,通过数据分析为留学决策提供量身定做的教育和财务机会的推荐。
特别奖项获奖者
这些奖项凸显了具有创新潜力、跨行业应用和社区影响的项目:
- StudyVerse
- TourRecommendation:一种 AI 工具,通过区块链驱动的透明度帮助游客找到可靠的餐饮和住宿,提升交易的信任度。
- Buildlink:通过 AI 简化区块链交互,提供 NEAR 区块链上的用户友好互换和质押,提高新用户的可及性。
此次 Hackathon 强调了 AI 在应对复杂问题和提供跨领域影响力解决方案方面的能力。有关所有项目的更多详细信息,请访问 Dorahacks AI Hackathon。
关于组织者
SUCI BLOCKCHAIN HUB
SUCI Blockchain Hub 致力于区块链技术的开发和应用。该组织以推进各行业的安全去中心化解决方案而闻名,并对多个重要区块链项目作出了贡献。通过研究和开发,SUCI Blockchain Hub 促进创新,与行业领导者协作,提升区块链应用,推动数字交易的可及性和透明度。目前,组织的使命着重于扩展区块链整合,为企业和个人提供高效、安全的解决方案。
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 8e7e2128:25e34fd1
2025-04-16 05:20:11
@ 8e7e2128:25e34fd1
2025-04-16 05:20:11In today’s beauty-driven, fast-paced world, the desire for youthful, radiant skin is stronger than ever. But unlike in decades past, where cosmetic surgery reigned supreme, modern skincare enthusiasts are increasingly turning toward gentler alternatives. Enter the era of minimally invasive skin treatments—solutions designed to refresh and rejuvenate without the need for scalpels, sutures, or significant downtime.
Among the many advancements, one technology stands out: light-based skin therapy. From acne to aging, pigmentation to inflammation, light is proving to be one of the most versatile tools in the modern skincare toolkit. But how did we get here, and what exactly makes these treatments so popular? Let’s break it all down.
Why Minimally Invasive Is the New Gold Standard Once upon a time, surgical facelifts and chemical peels were the go-to methods for anyone looking to turn back the clock on aging. But as our understanding of skin biology has evolved—and with the rise of social media and wellness culture—people are now seeking treatments that align with a lifestyle of balance, subtlety, and self-care.
Here’s why minimally invasive skin treatments are dominating the skincare space: - Little to no downtime: You can schedule a session on your lunch break and head back to work without skipping a beat. - Natural results: These treatments work with your body’s own processes to gradually enhance your skin’s appearance. - Lower risk: With no need for general anesthesia or extensive recovery, the risk profile is significantly lower. - Affordability: Compared to surgical options, many of these treatments are easier on the wallet. - Customization: Providers can tailor treatments based on individual skin types, concerns, and goals.
A Closer Look at the Technology: Light-Based Skin Therapy At the forefront of this skincare revolution is light-based skin therapy, a non-invasive category of treatments that use controlled light wavelengths to trigger natural biological processes within the skin.
How Does It Work? Different wavelengths of light penetrate the skin at various depths. By targeting specific skin layers, light-based skin therapy can: Stimulate collagen production Kill acne-causing bacteria Reduce pigmentation Promote healing and tissue regeneration
There’s no cutting, no abrasion, and often no pain—just the gentle power of light doing what it does best.
Types of Light-Based Skin Therapy Let’s dive into the most popular forms of light-based therapies and what they can do for your skin.
1. LED Light Therapy LED therapy is one of the most accessible and gentle treatments available. It involves the application of different colored lights to target various skin concerns: Blue light: Effective for killing Propionibacterium acnes, the bacteria behind acne breakouts. Red light: Boosts circulation and stimulates collagen production, making it ideal for anti-aging. Green light: Targets hyperpigmentation and sun damage. Yellow light: Helps reduce redness and inflammation. LED therapy can be done in-office or at home with wearable LED masks and handheld devices.
2. IPL (Intense Pulsed Light) Often referred to as a “photofacial,” IPL delivers broad-spectrum light deep into the skin. It’s especially effective for: Sunspots and age spots Redness and rosacea Broken capillaries Uneven skin tone Unlike lasers, which use a single wavelength, IPL uses multiple wavelengths, allowing for treatment of multiple issues in a single session.
3. Fractional Lasers Fractional lasers are more intensive than LED or IPL, but they’re still considered minimally invasive. They work by creating microscopic columns of controlled damage in the skin, which stimulates the body’s natural healing response. These are best for: Acne scars Fine lines and wrinkles Stretch marks Skin resurfacing
Downtime can vary, but results are often dramatic and long-lasting.
4. Photodynamic Therapy (PDT) A more medical-grade form of light-based skin therapy, PDT combines a light-sensitive solution with a specific wavelength of light to treat more severe issues, such as: • Precancerous skin lesions (actinic keratosis) • Severe acne • Sun damage This treatment is typically performed by dermatologists and offers both therapeutic and cosmetic benefits.
What to Expect During and After Treatment One of the key reasons minimally invasive treatments have taken off is how user-friendly they are. Here’s a general outline of what most patients can expect:
Before the Treatment: A consultation to assess your skin and recommend the right therapy. Photos may be taken for progress tracking. Skin will be cleansed, and protective eyewear provided (for light-based therapies).
During the Treatment: Most treatments are painless or involve minimal discomfort. Sessions usually last 15 to 60 minutes, depending on the area and technique.
After the Treatment: Mild redness or warmth is common but usually resolves within hours. You may be advised to avoid sun exposure and use gentle skincare. Results typically build over several sessions.
Is It Right for You? If you’re looking for a skin boost without the risks or recovery time of surgery, light-based skin therapy and other minimally invasive treatments could be perfect for you. These therapies are suitable for a wide range of concerns and skin types, but it’s always best to consult with a certified dermatologist or aesthetician to ensure you’re getting the safest and most effective treatment plan.
The Future of Skincare Is Bright—Literally As technology advances and consumer demand for safer, more effective skin care grows, light-based skin therapy is becoming a cornerstone of modern aesthetic medicine. These treatments blend the best of science and beauty, offering real results without drastic measures. Whether you're tackling acne, sun damage, or simply aiming to maintain your youthful glow, the future of skincare is about enhancement, not overhaul. So say goodbye to invasive procedures—and hello to glowing skin, one light beam at a time.
The rise of minimally invasive skin treatments has redefined what it means to age gracefully. By prioritizing natural results, minimal recovery, and long-term skin health, these therapies are changing lives (and complexions) one session at a time.
And when it comes to harnessing the power of light, light-based skin therapy is illuminating the way forward—proving that sometimes, the best treatments are the ones that don’t require going under.
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 502ab02a:a2860397
2025-04-16 04:11:58
@ 502ab02a:a2860397
2025-04-16 04:11:58ในยุคที่ใครๆ ก็พูดเรื่อง สิทธิเสรีภาพ จะมีใครรู้บ้างว่า สิ่งที่เรากินทุกวัน กลับกำลังเข้าสู่ยุค ไร้สิทธิในการรับรู้ โดยเฉพาะเมื่อพูดถึงสิ่งที่เรียกว่า “GMO 2.0”
ใช่แล้วครับ GMO 2.0 หรือ synthetic biology ไม่ใช่ข้าวโพด BT, ไม่ใช่ถั่วเหลืองต้านยาฆ่าหญ้าแบบเดิม แต่มันคือ “พืชที่ถูกดัดแปลงพันธุกรรมแบบไม่มีรอยแผล” คือการใช้เทคโนโลยี CRISPR-Cas9, TALEN หรือ ZFN เข้าไป “ตัดต่อยีน” ภายในพืช โดยไม่ต้องใส่ยีนแปลกปลอมจากสิ่งมีชีวิตอื่น
ถ้าจำได้ ที่ผมเคยแชร์เรื่องการสร้างหมาป่า Game of Thrones และกำลังทำแมมมอธ อยู่นั่นละครับ CRISPR คือเทคโนโลยีที่เขาใช้ ผมเคยโพสไว้ว่า ผมสนใจเรื่องสัตว์นะ แต่ผมมีเรื่องกังวลควบคู่มาด้วย นี่คือเรื่องที่ผมบอกไว้ครับ
เพราะการสร้างสิ่งเหล่านั้นมันฟังดูดีใช่ไหมครับ? แต่ปัญหาคือ...มันดีจนไม่ต้องถูกเรียกว่า GMO นี่คือกลยุทธ์ใหม่ของอุตสาหกรรมพันธุ์พืช เพราะในหลายประเทศ เช่น สหรัฐฯ แคนาดา และแม้แต่ญี่ปุ่น กฎหมายไม่ถือว่า CRISPR เป็น GMO ถ้าไม่มีการนำยีนจากสิ่งมีชีวิตอื่นมาใส่เข้าไป
พูดง่ายๆ คือ “ตัดแต่งยีนจากของตัวเอง ยังไม่เรียกว่า GMO” แต่ผลที่ออกมา... อาจเปลี่ยนทั้งระบบการเติบโตของพืช เปลี่ยนลักษณะอาหาร เปลี่ยนภูมิคุ้มกัน และเปลี่ยนการควบคุมอำนาจในห่วงโซ่อาหารโลก
แล้วการที่ไม่ต้องติดฉลาก ไม่ต้องแจ้งผู้บริโภค นี่คือสาระสำคัญ!!!! เพราะเมื่อมันไม่ใช่ GMO ในทางกฎหมายก็ไม่มี “ภาระในการแจ้งผู้บริโภค” ใครกินพืช CRISPR เข้าไป ก็จะไม่รู้เลยว่า...นี่คือพันธุ์ที่ผ่านการดัดแปลงระดับ DNA มาแล้ว
ลองคิดดูครับว่า นี่เรากำลังถูกดันเข้าสู่ยุคที่ “มะเขือเทศหวาน” หรือ “ข้าวที่แข็งแรงทนแล้งดี” หรือ "พืชที่สะสมโปรตีนวิตามินที่ใส่สารละลายไว้ในตัว" อาจจะผ่านการตัดต่อพันธุกรรม แต่คุณไม่มีทางรู้ เพราะมันไม่มีทางตรวจพบจากฉลาก หรือการทดสอบดีเอ็นเอปกติ
คำถามคือ ใครควบคุม? ใครได้ประโยชน์? คำตอบเหมือนเดิมละครับ บริษัทยักษ์ใหญ่ที่จดสิทธิบัตรไว้ก่อนไง 5555
ในระบบ GMO 1.0 อุตสาหกรรมเคยพยายามผูกขาดพันธุ์โดยใช้สิทธิบัตร แต่ผู้บริโภคยังสามารถรู้และต่อต้านได้ แต่ GMO 2.0 มาแบบ “เงียบกว่า แหลมคมกว่า และควบคุมง่ายกว่า”
ยกตัวอย่างเช่น ข้าวโพด CRISPR จากบริษัท Corteva (เจ้าของเดิมคือ DowDuPont) สามารถสร้างพันธุ์ที่ “โตไว แห้งเร็ว เก็บเกี่ยวได้เร็วกว่าเดิม” แต่พันธุ์นี้มีสิทธิบัตรคุ้มครองแบบเบ็ดเสร็จ แถมไม่มีข้อผูกมัดในการแจ้งข้อมูลกับผู้บริโภคด้วย
ในส่วนของความเสี่ยงที่ใครก็ไม่กล้าพูดถึงก็มีอีกนะครับ เช่น -การตัดต่อยีนแม้จะไม่ใส่ยีนใหม่ แต่ก็สามารถเกิด off-target effect หรือผลกระทบที่ไม่ได้ตั้งใจได้ -ยีนที่ถูกตัดออกอาจมีหน้าที่สำคัญด้านภูมิคุ้มกันหรือสมดุลภายในพืช ซึ่งส่งผลถึงโภชนาการของผู้บริโภค -การกระจายของพันธุ์ CRISPR โดยไม่ต้องผ่านการควบคุม อาจทำให้พืชดั้งเดิม สูญพันธุ์ทางพันธุกรรม เพราะถูกแทนที่แบบเงียบๆ
แล้วเกษตรกรล่ะ? จะรอดไหม? คำตอบคือ รอดยากขึ้นครับ หรือจะเรียกไม่มีทางรอดดีโหดไปไหม? เพราะ GMO 2.0 ไม่ใช่แค่เรื่องการดัดแปลงพันธุกรรม ถ้ามองภาพกว้างกว่านั้น มองโครงสร้างเลยนี่มันคือการสร้าง “ระบบใหม่ในการผูกขาดพันธุ์” ที่มองไม่เห็น เป็นการล็อกพันธุ์พืชด้วย “สิทธิบัตรโมเลกุล” ซึ่งเกษตรกรไม่สามารถเซฟพันธุ์ไว้ปลูกต่อได้ เพราะละเมิดกรรมสิทธิ์ ต้องเช่าใช้หรือ subscribe ไปตลอดชีวิต มีหน้าที่แค่หน่วยปลูกเท่านั้น
ขณะที่พันธุ์พื้นบ้านหรือพันธุ์เปิดกลับไม่สามารถแข่งขันกับพันธุ์ดัดแปลงเหล่านี้ได้เลย เพราะถูกออกแบบมาให้ “ตอบโจทย์ตลาด” แต่ไม่ใช่ “ตอบโจทย์ดินฟ้าอากาศจริงๆ” แบบเกษตรวิถีเดิม
แล้วในโลกหลัง GMO 2.0 จะเหลืออะไรให้เราปลูก? นี่ไม่ใช่การต่อต้านเทคโนโลยีนะครับ ทุกคนเข้าใจดีว่าเราต้องเติมโตและมีการพัฒนา แต่คือคำถามเรื่อง สิทธิในการรู้ สิทธิในการเลือก และ สิทธิในการรักษาพันธุกรรมของพืชพื้นบ้าน มันอยู่ตรงไหนก่อน
เพราะเมื่อเราถูกเปลี่ยนพันธุ์แบบไม่รู้ตัว วันหนึ่ง เราอาจต้องซื้อเมล็ดพันธุ์ทุกปีจากบริษัทเพียงไม่กี่ราย ปลูกอาหารในระบบที่เราควบคุมไม่ได้ และกินอาหารที่ไม่มีใครกล้ารับรองว่า “ดั้งเดิม” จริงหรือเปล่า
ดังนั้นมันจึงถึงเวลาตั้งคำถามใหม่... ว่า real food ของเรายัง real อยู่ไหม?
ในยุคที่แม้แต่มะเขือเทศก็ถูกเปลี่ยนยีน และข้าวโพดก็ถูกออกแบบมาให้เก็บเกี่ยวเร็วขึ้น แต่ไม่งอกได้อีกเลย คำถามไม่ใช่แค่ “อร่อยไหม” หรือ “หวานแค่ไหน” แต่คือ
“เราเหลือสิทธิ์อะไรกับอาหารที่เราปลูกบ้าง?”
สิ่งนี้มันเกิดขึ้นไปแล้วครับ นี่ยังไม่ได้พูดถึงผลกระทบจากการกิน เพราะมีหลายๆคนแฮปปี้ดี๊ด๊าไปมากมาย กับสตอเบอรี่หวานฉ่ำ เมลลอนหอมฉุย กล้วยใบงาม กินแล้ว "healthyyyyy" อะตรงนั้นผมไม่แย้งแล้วกัน
ซีรีย์นี้เลยให้มองผลของการถูกจองจำครับ กบชอบอาบน้ำอุ่นเสมอ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 502ab02a:a2860397
2025-04-16 04:06:25
@ 502ab02a:a2860397
2025-04-16 04:06:25"Satoshi is not me." #ตัวหนังสือมีเสียง
เพลงนี้เรียกได้ว่าเป็นจุดเริ่มต้นของคอนเสปอัลบั้มนี้เลยครับ ผมเลยเอาชื่อเพลงนี้เป็นชื่ออัลบั้มไปด้วย
มันเริ่มจากการที่คนชอบคาดคะเนกันไปว่า ใครคือ satoshi nakamoto ตัวจริง แล้วก็มีสารพัดทฤษฎีออกมา ค้นคว้ากันไปถึง กระทู้ที่คุยกันใน mailing list สมัยนั้นเลยเชียว
มีคนนึงที่ไม่พลาดโดนมองว่าเป็น satoshi นั่นคือ Jack Dorsey (nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m) ผู้ร่วมก่อตั้ง twitter แล้วยิ่งเขาลงมาในทุ่งม่วงและสนับสนุน บิทคอยน์ เต็มตัวรวมถึงไปร่วมงานคอนเฟอร์เรนซ์บิทคอยน์ด้วย นั่นยิ่งทำให้คนพูดกันหนาหูขึ้น
ในปี 2020 Dorsey ได้ให้สัมภาษณ์กับ Lex Fridman โดยเมื่อถูกถามว่าเขาคือ Satoshi Nakamoto หรือไม่ เขาตอบว่า "ไม่ และถ้าผมเป็น ผมจะบอกคุณไหมล่ะ?"
นี่หละครับ ประโยคที่ผมรู้สึกว่า น่ารักและเอามาขยายความเป็นความจั๊กจี้ได้โรแมนติกดี แถมมันเข้ากับประโยคที่พวกเรามักใช้ว่า we’re all Satoshi
ทำให้คำว่า Satoshi is not me เลยกลายเป็นมุมกลับที่จั๊กจี้ดี ในความคิดผม
ผมเลยเริ่มจากการร่างไว้ว่า ท่อนฮุคของเพลงจะต้องมีคำว่า "Satoshi is not me" บังคับตัวเองไว้ก่อนเลย ฮาๆๆๆ
เพลงจะกล่าวถึงบรรยากาศโรแมนติกสบายๆผ่อนคลาย หนุ่มสาวเดินไปตามชายหาดด้วยกัน หัวเราะหยอกล้อ
เนื้อเพลงพยายามซ่อนการเปรียบเทียบเป็นนัยยะ ตามความต้องการแรกในการทำอัลบั้มนี้คือ ถ้าไม่โดนยาส้มไว้ ก็ยังฟังได้แบบสบายๆ ตามประสาเพลงบอสซาทั่วไป แต่ถ้าโดนยาส้มแล้ว อาจจะฟังแล้วรู้สึกถึงอีกมุมที่เป็นปรัชญาบิทคอยน์ได้
เรียกว่าไม่อยากเอา core code มาเขียนเพลงนั่นละครับ
เราเริ่มด้วยการวางฉากให้สบายๆชายทะเล ประสาความบอสซาโนวาก่อน ด้วยท่อนแรก In the cool of evening, beneath the twilight trees, We sway with the ocean, feeling the summer breeze, There's a whisper in the air, oh so tender, so free, ยามเย็นอ่อนลม ใต้พฤกษาเวลาโพล้เพล้ เราสองตระกองกอดไปกับคลื่นทะเล ลมฤดูร้อนพัดพาเสียงเล่าเบา ๆ
ก่อนจะลงท่อนปิดด้วยประโยคว่า You smile and softly whisper, "Satoshi is not me." เธอยิ้มแล้วกระซิบว่า "ฉันไม่ใช่ซาโตชิ"
แต่ผมก็ยังพยายามแทรกเรื่องของบิทคอยน์และเบื้องหลัง fiat money เอาไว้ด้วยนิดนึง Soft waves kiss the sand, like a gentle dream, With every step we take, there's a secret melody, คลื่นเคล้าหาดเบา ๆ ดุจฝันที่ละมุนละไม ทุกก้าวที่เราย่างไว้ ล้วนมีท่วงทำนองแอบแฝงอยู่ ฮาๆๆๆ คือกำลังพยายามบอกว่า ความราบรื่นในชีวิตเราทุกวันนี้ เราอาจรู้สึกสวยงาม แต่จริงๆแล้วทุกๆก้าวย่างของเรา ถูกกำหนดด้วยความลับบางอย่างอยู่
จากนั้นก็ปูเข้าสู่ทางรอด คล้ายๆกับชักชวนมาสร้างโลกที่หลุดพ้นจาก fiat In the world we're crafting, where our hearts feel light, We find our own rhythm, in the still of the night, No need for grand illusions, or some wild decree, มาระบายเมืองด้วยสีสันที่สดใสด้วยหัวใจแห่งเสรี เราสร้างท่วงทำนองของเรา แล้วเต้นใต้เงาจันทร์ จนแสงรุ่งทาบฟ้าอีกครา ไม่จำเป็นต้องมีมหากาพย์ภาพลวงตา หรือประกาศิตอันยิ่งใหญ่ใด
ก่อนจะจบผมวางท่อง bridge ไว้โดยมีประโยคว่า No chains to bind us, just a heartfelt plea, ไร้พันธนาการใดมาควบคุมเรา มีเพียงคำขอเบา ๆ จากใจที่แท้จริง เพื่อแสดงความปลดแอกอะไรบางอย่าง
ทีนี้ยังมีลูกเล่นในแต่ละท่อน ที่ใช้คำว่า "Satoshi is not me." ด้วยนะครับ ผมเอามาเรียงกันให้ตามนี้ You smile and softly whisper, "Satoshi is not me."
You laugh and then you tell me, "Satoshi is not me."
With your hand in mine, love, "Satoshi is not me."
You softly keep reminding, "Satoshi is not me."
Embrace the simple truth, “Satoshi is not me.”
คือเป็นการหยอดความโรแมนติกนิดหน่อย ว่าเชื่อเค้าเหอะนะ เค้าไม่ใช่ Satoshi ด้วยการใช้ประโยคต้นที่ขยับแรงขอร้องมากขึ้นเรื่อยๆ
หวังว่าหลังจากนี้เวลาฟังเพลงนี้จะจั๊กจี้แบบที่ผมนึกสนุกตอนเขียนนะครับ ฮาๆๆๆๆ 🎶 youtube music https://youtu.be/g8oyZQ_lTa0?si=kS7ga_TxmFnPOmwR
🟢 spotify https://open.spotify.com/track/69GOSGMrma3BONKG8l5wpN?si=c0e6711c7a994011
💽 tiktok ค้นหา Heretong Teera Siri เลือกแผ่นเสียงไปทำคลิปได้เลยครับ
Lyrics : Satoshi is not me [Verse] In the cool of evening, beneath the twilight trees, We sway with the ocean, feeling the summer breeze, There's a whisper in the air, oh so tender, so free, You smile and softly whisper, "Satoshi is not me."
[Vers 2] We walk along the shoreline, while the stars start to gleam, Soft waves kiss the sand, like a gentle dream, With every step we take, there's a secret melody, You laugh and then you tell me, "Satoshi is not me."
[Chorus] In the world we're crafting, where our hearts feel light, We find our own rhythm, in the still of the night, No need for grand illusions, or some wild decree, With your hand in mine, love, "Satoshi is not me."
[Verse 3] Let’s paint the town in colors, of freedom and delight, Dance in moonlit shadows, till the break of daylight, In this realm of wonder, where we both can be, You softly keep reminding, "Satoshi is not me."
[Bridge] Beneath the starlit canopy, where dreams softly align, We live for the moment, leave the rest behind, No chains to bind us, just a heartfelt plea, Embrace the simple truth, “Satoshi is not me.”
[Chorus] In the world we're crafting, where our hearts feel light, We find our own rhythm, in the still of the night, No need for grand illusions, or some wild decree, With your hand in mine, love, "Satoshi is not me."
pirateketo #siripun
-
 @ 69eea734:4ae31ae6
2025-04-01 15:33:49
@ 69eea734:4ae31ae6
2025-04-01 15:33:49What to record from the last two weeks? The key points from the things I've read and watched? \ The encounters I had with various groups of people, and also one on one? (on my trip to Munich)\ My thoughts on what is going on in the world?\ It is all connected anyway.
This is my second post. The first was under a different profile, which I lost the private key to.
So close and yet apart
The various encounters: Overlapping 'camps'. School friends, friends from uni times, friends from Covid times. One friend from school, and one friend from uni did not have a Covid vaccine and were critical of measures. To think that this still matters! Can you believe it? But it does! Which is sad on one hand, and makes for strong bonds on the other.
I'm in a pub with three school friends. They discover that they all voted Green, and are delighted. They kind of congratulate each other, and themselves. I don't even know what to feel in that moment. I'm not shocked. It is not surprising. And yet I still find it astounding.
As the evening progresses, we move to a Greek restaurant round the corner. On the way there, I walk alongside the friend with whom I exchanged the most challenging emails of the last five years. There had been long pauses between replies. Once I read only the first two lines, and then 'quarantined' the mail. I once deleted one, and three weeks later asked him to send it again.
In 2023 we sat in a café and openly talked about the Corona period and our differing positions. I appreciated it. At least we could talk. Shortly after, the emphasis in our conversations shifted from Covid to Putin. One arch enemy was replaced by another. And when previously, the 'Covid deniers' were the deplorable ones, now it was the 'Putin understanders', and weren't they the same people anyway? And mentioning peace talks was right wing. It was all so predictable. Was I predictable, too? I'd sent a long email a week ago. But walking alongside each other, we preferred to talk about the kids.
At the Greek restaurant, the inevitable happened. We ended up in a massive discussion. I once was gesticulating wildly at him. "Conspiracy theorist! That is so convenient. Everything that does not fit into your worldview, becomes a conspiracy theory. That there would be a vaccine mandate was once a conspiracy theory. That the virus came from a lab was once a conspiracy theory."
On another occasion, he exclaimed: "You know that I know all that about America! You know exactly that I know all those things!"
We both knew a lot of things, and it went back and forth.
The irony was that we managed to stay respectful, and it was a discussion with the other school friend there (the fourth person on the table was my husband), that turned out to be the last straw. She had voted Green as well, and had congratulated our school mate on having been to the protest 'against the right'. But she was also the one who didn't have the vaccine, and now said, "With Covid, it was just so obvious that it was all set up." A bit later she said something about the WEF. Only to be greeted with a long tirade. "Aha. So you think this is all a big conspiracy with some powerful people in the background planning everything. And this wasn't a pandemic although lots of people died. I know six doctors, and they all told me the same." A bit later, to me: "So why did only the unvaccinated die then?" And then shortly after, when my friend stated again how the whole thing had seemed premeditated, "Right. That's enough now. I'm leaving." And he got up to pay and left.
My friend, who stayed behind, thought we had had interesting discussions and she had learned something. On reflection, it was good to have this discussion at all -- at a time that nobody seems to want to talk about Covid anymore.
But also: Shouldn't we be much much further than this???
My first sats
A few months ago I had tried to buy bitcoin, just to play around, but there had been difficulties to do with the fact I have a UK bank account. When looking at how to get funds into my getalby account, I ended up with Strike, which is available in the UK. But it seems they take extra care to make sure you know what you are letting yourself into! I had to do a test with about 10 questions to show I understand the risks.
I then had to wait 24 hours, but now I have sent my first sats.
On the Strike website, I noticed this video of a conversation between Jack Mallers, founder of Strike, and Jack Dorsey, co-founder of Twitter. The more I watched, the more I thought, wow, here it is all in one video, all that I would like my friend to see. "America has a problem." The Empire needs to end, and it would be a good thing for America, says Jack Dorsey. This was also the second time in a week that I heard about how Great Britain had created money and bought their own bonds when the public didn't want to, in effect stealing from the people by making their money worth less. It was good to be reminded of Adam Curtis who has made some mind-blowing documentaries, using lots of BBC archive material. Including about the special US and UK relationship (An ocean apart), and also one about Russia from 1985 to 1999 (Trauma Zone).
The two Jacks talk about the importance of open source, and of being independent of government. The dangers of building abstraction on abstraction on abstraction. About how Mark Zuckerberg served Dorsey raw goat once, because he had this challenge to only eat what he had killed himself. That was also a way to get back to the real.
Dorsey endorsed RFK jr, this was in summer of 2023, when he was still running for president.
There is also an interesting bit on the pressures of running a company that has gone public. And the government interference, in effect censorship. The Twitter files. It is not quite clear to me, if it was really so difficult for Jack Dorsey to pay attention and know what was going on, but I can understand that it must have been a difficult situation.
What I also find very interesting is that in Africa or Latin America bitcoin is sometimes valuable as an exchange medium. That is where I think it could diverge from the pure Ponzi scheme that people often call it.
And yet, doubts remain. Is bitcoin not too valuable for a lot of people to spend it? But what if you don't have access to any other money. And sending Satoshis around is different from hording bitcoin. Can it fulfil both these functions in the end, storage medium and exchange medium?
I believe that these two people want to achieve something positive. But they also remain tech bros. And I don't mean that in a bad way. It is just something that will always remain a bit alien to me.
I did like what Dorsey said about the punks. How they just started to play an instrument, and didn't care if they were not good at it. Then just turned up again and again and eventually got better. I have often thought of myself as a bit punk-like in that respect, although I've often been worried about not being good enough.
Doing away with domination
The last blog article posted on a website I work on, made me explore the writings by Darren Allen on his Expressive Egg substack. I had landed there before, years ago, and had been very impressed back then. He seems to criticise people's thoughts a lot though -- almost everybody's -- and I was wondering if that was all he ever did. But then I came across this article about anarchy. It made me realise again, in all this mess about different worldviews, different expectations and values, that this is a constant for me: How can we have less coercion, how can we live in a way that frees ourselves and others at the same time. I once saw a Twitter bio: "I insist on your freedom." It seems to come from Jack Kerouac.
Allen writes that there are seven dominants, seven elements that "control individuals against their will". They are, " in roughly ascending order of subtlety and pervasiveness":
1. The [autocratic] monarchy.\ 2. The [socialist-democratic] state (which includes its money, law, property, police, etc.).\ 3. The [totalitarian-capitalist] corporation.\ 4. The [mass] majority.\ 5. The [professional-religious] institution.\ 6. The [technocratic] system.\ 7. The [mental-emotional] ego.
I want to keep this list in mind and pay attention when I get sucked into the influence of one of these spheres.
\ I also like this quote:
The reason men and women do not need kings, princes, states, professionals, institutions and systems to rule over them is because the life within them is more intelligent, more apt, more sensitive, more forgiving and more creative than anything else—certainly any human authority. But this life cannot be rationally fixed. It can be expressed, artistically, indirectly, poetically, musically, or with tone and glance and such ordinary, metaphorical arts of human interaction; but it cannot be literally stated.
\ Although this would be a good ending for this post, I have to mention Jeffrey Sachs as well. I have been following him for a while. He appeared in the EU parliament, invited by Michael von der Schulenburg. Sachs has an amazing amount of experience with both Russian and American government officials, and with currencies. In the 90s he spent some time helping Eastern European countries with the transition to capitalist systems. He realised that the U.S. did not want to help Russia in the same way.
He gave a long speech in which he laid bare the ways in which the U.S. had influenced so many wars and uprisings around the world, and how the NATO enlargement had been a long-term strategy. That now, with Trump, the war was going to end.
There would be so much more to say. In any case, this seems to me a historic speech. Can it break through the mirror glass that has kept so many people away from valid sources of knowledge?
-
 @ 8d34bd24:414be32b
2025-04-16 03:48:30
@ 8d34bd24:414be32b
2025-04-16 03:48:30Ever since becoming a Christian, I have whole-heartedly believed the Bible and that God will fulfill what He has promised. On the other hand, for the majority of the time I have been a Christian, I have dreaded reading prophecy. It seemed so hard to understand. Some is couched in figurative language, but I now believe much of it was hard to understand because there were no words for the technology and systems that would come into being and fulfill these predictions.
Now reading End times prophecy, like in Revelation, Daniel, Matthew 24-25, 2 Thessalonians, Zechariah, etc. the prophecies are starting to sound like the evening news instead of some poetic mystery. These predictions are making more and more sense as the technology and world politics begin to align with the prophecies. I have gone from hating when I get to prophecy passages, especially Revelation, in my Bible reading, to spending extra time reading these passages and seeing how they line up and clarify each other. (I really want to start a project linking all of the end-times prophetic passages together to see how they clarify each other and try to see the big picture, but that is a massive project and time is in short supply. The only way I know to do it is in Excel, but that isn’t efficient. If anyone has a suggestion for a better way to link and show relationships, I’d love to hear about it, especially if it is free or very cheap.)
Matthew recounts Jesus telling His disciples about what to expect in the end times. Although Matthew 24 describes more of the details of the events that happen, this passage in Matthew 25 describes the importance of watching expectantly for the signs of the times, so we are ready.
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13) {emphasis mine}
Many Christians think studying prophecy is not useful for today, but that is not true. Our time is short and Jesus warned us to be aware and ready. We can’t be ready for something if we know nothing about it.
In this passage it mentions that “while the bridegroom was delaying, they all got drowsy and began to sleep.” How often do we feel the delay and begin to rest or get distracted by other things? Most Christians do not live like Christ’s return is imminent. Although we can’t know the hour or the day, we can know that we are closer to that hour than we have ever been before. Peter warns us not to doubt Christ’s coming or to become focused solely on our earthly lives.
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” (2 Peter 3:3-4)
Because Jesus has not returned for almost 2,000 years, many act as if He will never come, but that long wait instead suggests the time is nearing because God never breaks His promises.
For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men.
But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:5-9) {emphasis mine}
The long wait is due to God’s unfathomable mercy and patience, but we should also realize that the increase of evil in the world cannot continue forever. How much more can evil increase before mankind destroys itself? God claims judgement for Himself and finds every kind of sin abhorrent. If we are distraught over the sin in the world today, how much more awful is it to a holy, perfect God to see His very own creation destroyed by sin?
Just as the ten virgins became tired waiting, we tend to get caught up in the things of this world instead of focusing on God’s plan for us and the world. We act as if this world is the only thing we will experience instead of preparing for our rapture to heaven. We focus on our job, our homes, and our families (all good things) and miss the most important things — winning souls for heaven.
Just as Jesus gently reprimanded Martha for having the wrong focus:
But Martha was distracted with all her preparations; and she came up to Him and said, “Lord, do You not care that my sister has left me to do all the serving alone? Then tell her to help me.” But the Lord answered and said to her, “Martha, Martha, you are worried and bothered about so many things; but only one thing is necessary, for Mary has chosen the good part, which shall not be taken away from her.” (Luke 10:40-42) {emphasis mine}
In the same way, we get focused with the business of life and miss the most important stuff. It wasn’t bad of Martha to take care of her guests, but sitting with Jesus and learning from Him was more important. In the same way, our jobs, families, and homes are good things and we should do them well, but reading our Bibles, praying, growing closer to Jesus, and sharing the Gospel with those who don’t know Jesus is better.
When we believe that our time on earth is short and Jesus is coming for us soon, we are more likely to focus on the most important things — the eternal things.
This passage in Matthew 16 describes the importance of us knowing, understanding, and looking for the signs of the times.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
Christians that believe studying end times prophecy is not important would be rebuked even today by Jesus. We are supposed to study and learn and prepare and watch eagerly for His return.
In Revelation, God says we are blessed if we hear and heed the words of this prophecy.
The Revelation of Jesus Christ, which God gave Him to show to His bond-servants, the things which must soon take place; and He sent and communicated it by His angel to His bond-servant John, who testified to the word of God and to the testimony of Jesus Christ, even to all that he saw. Blessed is he who reads and those who hear the words of the prophecy, and heed the things which are written in it; for the time is near. (Revelation 1:1-3) {emphasis mine}
Do you seek God’s blessing? Then study God’s prophecies, especially as written in Revelation. God is good and He has shown His children what will happen, so they can be prepared. Don’t be like the five foolish virgins who were unprepared. Study the Scriptures. Look for the signs. Be ready for our Savior’s return by inviting as many people as possible to join us.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, the judgement, etc.).
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ 35da2266:15e70970
2025-04-16 03:45:13
@ 35da2266:15e70970
2025-04-16 03:45:13Qd6Vc1ZwkoV314qozv8RVkBk0YW9XQK38bjizGI5a4ws0wuuJQR5U0uDEzKcNd9/QWPbaj4rQIgdFNlmmybdn4s1WXfmdoymUFBRjpBau7Nj2yeXaKtk+RVl488Kxo0/kb13hQfX8q6kzPs9jY2NWS9KedXA+LSEhZJKXeXn5lT8hxuFPc6Q/rmVQT3gTRAORK/LUizNE71+wnaJPV0V/mNrdiKxWbFAv6lnmSPY+zKVY/u5E6vgjgObaSGpjj+MOaMkYfGxnm7fm9kvQawJNmIHdYn2CcymnSYHhuL7jqohECqf0DtPrewYkFfJ6mrerKhKwRbaHRIOcOJKiIjw5Q==?iv=RdYmRey3pCxDafHJpDdFVA==
-
 @ 75869cfa:76819987
2025-04-01 05:55:38
@ 75869cfa:76819987
2025-04-01 05:55:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 221,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 79%. More than 10 million events have been published, reflecting a 12% decrease. Total Zap activity stands at approximately 21 million, marking a 15% increase.
Additionally, 15 pull requests were submitted to the Nostr protocol, with 2 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 569 long-form articles were published, 24% focusing on Bitcoin and Nostr. During this period, 7 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 221,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 17662 events, with a low of approximately 15781.
The number of new users has decreased significantly. Profiles with bio are now around 25951, reflecting a 79% drop. Pubkeys writing events have decreased by 50% compared to the previous period.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 12% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.7 million, which is a 4.4 % decrease. Both reposts and reactions have decreased by about 5%.
For zap activity, the total zap amount is about 21 million, showing an increase of over 15% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Added optional signString() method
nostr:npub1emq0gngdvntdn4apepxrxr65vln49nytqe0hyr58fg9768z5zmfqcwa3jz is proposing a signString() method that allow Nostr users to sign/authenticate messages for external apps without compromising their private key (nsec).It opens up a more generic and flexible challenge-response style external authentication method, using the same Schnorr signature mechanism that Nostr uses to sign events natively.External apps need only understand Schnorr signatures - they do not need to understand Nostr's event structure. This widens interoperability.A concrete example of where this would be useful is P2PK locking of Cashu ecash tokens to a Nostr pubkey (npub). Decoding the token requires a Scnorr signature on a structured message string. This method would allow a signer to handle It cleanly.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 defines kind:39701 as website bookmarks.Bookmarks can be queried by the d tag, which is just their URL without the scheme, which is always and everywhere assumed to be https://. The querystring and the hash must be removed entirely, unless their requirement is explicitly stated either by the user or by some hardcoded list of URLs that rely on query strings for basic routing provided by the client (I've searched the internet extensively and could only find 3 websites that do this: YouTube, Hacker News and a random guy's sad old blog). Bookmarks can be commented on with NIP-22.
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that covers the inclusion of Progress Events as implemented in Open Librarian. While the specific implementation is focused on tracking reading progress, the NIP is generic enough to be used in a whole range of other progress tracking scenarios (e.g. Fitness challenges, course progression for learning, personal goals etc..)
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that includes a minor update to extend kind 30003 in NIP-51 to include the i tag for external identities, as implemented for book reading lists in Open Librarian.
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr is proposing a NIP that Enable references to commits, files and lines for both nip34 repositories and other git repositories. Useful for code reviews of nip34 patches, the forthcoming nip95 code snippets and referencing specific code more generally.
Notable Projects
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🌐web v4.5.0: * Custom reactions are here! Choose your preferred emoji to react to notes and other content. * Improved profile organization with notes and replies now displayed separately. * Adding the ability to zap notes directly from the notifications center. * Enhanced DM filtering by time, allowing you to view only recent messages or browse further back. * Manual cache clearing from settings to optimize web app performance. * Resolved issue preventing users from removing custom media uploader servers. * Expanded export data, including more relevant details in credential and wallet files. * General bug fixes and performance improvements.
📱mobile v1.6.8: * One tap zap: Send a Lightning Network payment with one tap. * Dms extensive filtering: Use advanced filters to sort or prioritise direct messages efficiently. * Separating replies from notes: Split replies and notes in profiles, adding a tab for easier browsing. * Adding slide to display options: Swipe in notifications to access zap, reply, or DM options quickly. * Custom reactions: Choose from a set of emojis for personalised reactions, beyond standard likes. * App cache manager: Manage and clear app cache to boost performance and save space. * Variety of bugs fixed: Fixed multiple bugs for a more stable and seamless app experience. * General app improvements: Enhanced overall performance, usability, and design across the app.
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xChat v1.0.2-Desktop Beta is now live! * Supports NIP-104 MLS secret chat. * Copy images directly from the clipboard. * The app stays running after closing the window. * Fixed Enter key sending messages immediately on desktop.
Nostur v1.18.2 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
Nostur v1.18.2 bugfix update: * Fixed Follow button sometimes disabled * Fixed account switching reload issue * Fixed custom feeds missing * Fixed live stream banner scroll/swipe issue * Fixed screen turns off while playing video
voca v0.0.6 nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu
This release fine tunes the release process and makes publishing to @Zapstore a lot easier. There are also continuous improvements to initializing the text to speech engine for a faster startup.
WasabiWallet 2.5.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- 3rd Party Providers for Fee & Exchange Rate
- Quality of Life Features
- Backend and Coordinator packaged for Linux
GitPlaza nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks
- Login via nsec
- Activity feed for the people you follow (only issue creation)
- Create issues
- Comment on issues
ZEUS v0.10.1 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.1-beta1 is now available for testing. * NameDesc / bLIP-11 support: add receiver name to invoices * Bug fix: import of QR image from camera roll * Bug fix: Embedded LND: Open Channel: fund max * UI: Add dynamic background/text colors to Android NFC modal
KYCNOT.ME nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
- UI/UX - designe a new logo and color palette for kycnot.me.
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services.
- ToS Scrapper: implement a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices.
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services.
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab.
- Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - upgrade the request system. The new form allows you to directly request services or points without any extra steps.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
Long-Form Content Eco
In the past two weeks, more than 569 long-form articles have been published, including over 94 articles on Bitcoin and more than 43 related to Nostr, accounting for 24% of the total content.
These articles about Nostr mainly explore the growing importance of decentralization in communication, identity management, and digital infrastructure. From beginner-friendly guides like Nostr 101 and Getting Started with Primal, to more technical deep dives such as NIP-101e, NIP-95, and tutorials on running Nostr relays as TOR hidden services. Some articles focus on security and privacy—like protecting your Nsec with Amber or using tools such as ProtonMail—while others tackle complex challenges including Sybil attack mitigation and child protection in decentralized environments. There are also cultural and political reflections, such as letters from political prisoners and thoughts on the future of free speech in a post-Twitter world. In addition, the Nostr community shows a strong spirit of experimentation—ranging from agent-to-agent communication through dad jokes, to desktop-like clients, fitness tracking protocols, and Lightning integrations like Work Zaps and Wallet Connect. Together, these pieces showcase a dynamic, resilient, and freedom-driven movement shaping the future of the web.
The Bitcoin articles discuss a wide range of themes—from foundational ideas like "What is Money?" and Bitcoin’s first principles, to practical guides on mining, self-custody, Lightning payments, and privacy tools. Many explore Bitcoin’s role as a hedge against inflation, a form of sovereignty, and a response to fiat fragility. Cultural and economic reflections appear throughout—ranging from using Bitcoin to buy homes in Italy, to hip-hop collaborations, and even personal stories of financial awakening. There's critical analysis of Bitcoin UX, memetics, policy-making, and even war-time monetary history. From node sovereignty to P2P lending, from grassroots adoption to global macro shifts, these articles together portray Bitcoin not just as a currency, but as a cultural movement, a technological evolution, and a lens to reimagine freedom, value, and the future of money.
Thank you, nostr:npub1akzvuyyd79us07m8mtp2ruuha3ylp9757qg46d50rcrkhnx0fs4q2xzr37 nostr:npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmc6qyqdfnllhnzzxr5wpepfpnzcf8q6m3jdveflmgruqvd3qa9sjv7f60 nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0 nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm nostr:npub186k25a5rymtae6q0dmsh4ksen04706eurfst8xc5uzjchwkxdljqe59hv0 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
YakiHonne teamed up with Bitcoin Safari, nostr:npub1w7z986fez3gmjvxy6dd3sku4ndazhxzafjv2lf6aaa26mtl70q6scz4erj nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv nostr:npub1pw778uxwkky3xgq7w3anykdwdw9g46xy8de9mnau0kgwzz375zkq3udv57 and FULAFIA University to successfully host a series of Nostr Workshops, attracting over 200 participants in total. These events introduced the Nostr ecosystem and Bitcoin payments, allowing attendees to explore decentralized technologies through YakiHonne while earning rewards. Participants were encouraged to register and verify their accounts to claim exclusive bonuses—and invite friends to unlock even more benefits.
-
The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar was held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar was hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (a lawyer specializing in Banking, Corporate, and Financial Law). The session aimed to introduce the academic program and explored Bitcoin, the crypto economy, and related legal issues.
-
The monthly Bitcoin Meetup organized by Mi Primer Bitcoin took place on Thursday, March 27 at 7:00 PM at CRAFT Basilea in San Salvador. The event featured Bitcoin education, networking opportunities, live music, and fun extras like merchandise, raffles, and more. It was a vibrant evening dedicated to building community and spreading knowledge around Bitcoin. nostr:npub10zuxk4yhygswdmt5n9mfyeq6lh7gcu5g042tlggrgp8yunl32clqsu5t9r
Here is the upcoming Nostr event that you might want to check out.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. the event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
- Panama Blockchain Week 2025 will take place from April 22 to 24 at the Panama Convention Center in Panama City. As the first large-scale blockchain event in Central America, it aims to position Panama as a leading blockchain financial hub in Latin America. The event features a diverse lineup, including a blockchain conference, Investor’s Night, Web3 gaming experiences, tech exhibitions, and an after-party celebration.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 35da2266:15e70970
2025-04-16 03:43:02
@ 35da2266:15e70970
2025-04-16 03:43:02QdWVn542ZckzWEvFkyHenDWAI0kk58kbjgrYtvQBbbQXRXaxaRAlvjQ93NChwiNnfPaAEJ5R/hmuJ6FkTowumS9q0NP7uG6tA0RuTssdwNIORaN/wvqmz0GYme1Ci5RlNxtlHgeOyuPkLdiaolTt9CYlY2mV4gC1Tplkn7aP4mbXK+TJM9t6VsRR68GxShp8bLVK1qH3N6sPn9B7pkY2jEwi9GxGtZlf/jO3vS3lBgW79Ud2OYHbU3pauSdeM97+1TWvtMQt/iBlg54OB5Nb5pCTCNWDeJFD2wwavfQE8g9i91XBtt70z69shNrxLKHgpj6noC7QdUy1XZ49o3KSQw==?iv=B8YV090ont/MFRGbYBxpsA==
-
 @ d5c3d063:4d1159b3
2025-04-01 04:20:50
@ d5c3d063:4d1159b3
2025-04-01 04:20:50“วิธีที่ดีที่สุดในการทำลายทุนนิยมคือทำลายค่าเงิน” Lenin Was Right
ประโยคนี้ไม่ใช่แค่คำปลุกระดมของนักปฏิวัติ แต่มันเป็นเหมือนสัญญาณเตือนล่วงหน้า ที่คนส่วนใหญ่ไม่สนใจ จนวันหนึ่งมันก็เกิดขึ้นจริง แบบเงียบ ๆ โดยไม่มีใครทันตั้งตัว
Henry Hazlitt เขียนบทความนี้ไว้ตั้งแต่ปี 1947 เขาไม่เพียงบอกว่าเลนินพูดถูก แต่เขาแฉว่าโลกทั้งใบ “กำลังทำตามแผนของเลนิน” แบบไม่รู้ตัว
ตอนนั้นรัฐบาลหลายประเทศ โดยเฉพาะในยุโรป พิมพ์เงินออกมาใช้มหาศาล โดยอ้างว่าสงครามบีบบังคับให้ต้องทำแบบนั้น แต่ปัญหาคือ...พอสงครามจบในปี 1945 แล้ว รัฐกลับไม่หยุดพิมพ์เงิน ยังทำเหมือนอยู่ในภาวะฉุกเฉิน
เหมือนที่ อ. #SaifedeanAmmous พูดไว้ในหนังสือ #TheBitcoinStandard ว่าเวลารัฐอยากพิมพ์เงินแบบไม่ต้องรับผิดชอบ ก็แค่เอาสงครามมาอ้าง พอพูดว่า “เพื่อความมั่นคง” หรือ “เพื่อชาติ” เท่านั้นแหละ ทุกอย่างก็ดูเป็นเรื่องจำเป็นขึ้นมาทันที แล้วไม่มีใครกล้าถามว่าจริง ๆ แล้วเงินมันมาจากไหน
พอเงินเฟ้อมันแรง ของก็แพงขึ้น แต่รัฐไม่ยอมรับหรอกว่าที่ของแพงเพราะตัวเองพิมพ์เงินออกมาเยอะเกิน แต่กลับไปโทษพ่อค้า โทษคนทำธุรกิจ ว่าขายของแพง ค้ากำไรเกินควรซะงั้น
Hazlitt เขาเตือนว่า...รัฐกำลังทำให้คนเกลียดพ่อค้า เกลียดเจ้าของธุรกิจ เพื่อให้ดูเหมือนว่าตัวเองมีเหตุผลที่จะเข้ามาคุมเศรษฐกิจ ซึ่งที่น่ากลัวคือ... มันไม่ได้เกิดจากความไม่รู้ แต่มันเกิดจาก “ระบบ” ที่เปิดช่องให้เขาทำแบบนี้ได้เลย แบบไม่ต้องรับผิดชอบอะไรทั้งนั้น
ตรงนี้แหละที่ Hazlitt เอาคำพูดของ John Maynard Keynes เข้ามาเสริม เพราะแม้แต่ Keynes ก็ยังเคยเตือนไว้ในหนังสือ The Economic Consequences of the Peace ว่า “เงินเฟ้อ” มันเหมือนเครื่องมือเงียบ ๆ ที่จะค่อย ๆ ทำลายระบบเศรษฐกิจ โดยที่คนส่วนใหญ่ไม่รู้ตัว
Hazlitt เขาเป็น "สายวิจารณ์" Keynes ตัวพ่อเลยนะ เขาเขียนหนังสือ The Failure of the New Economics ที่ไล่รื้อแนวคิดของ Keynes แบบ “ตา-ต่อ-ตา หน้า-ต่อ-หน้า” กับหนังสือ The General Theory ของ Keynes เลยนะ
แต่พอมาในบทความนี้...Hazlitt กลับหยิบคำพูดของ Keynes มาใช้อย่างเต็มใจ เพราะมันตรงเกินไปที่จะมองข้ามได้ ว่าแม้แต่ #Keynes เองยังเคยเตือนเลยว่า “การทำลายค่าเงิน” คืออาวุธเงียบ ที่ใช้ทำลายระบบทุนนิยมได้อย่างแนบเนียนที่สุด . . พออ่านแล้วแบบ…แม้แต่คนที่เราคิดว่าเชียร์ฝั่งรัฐ ยังเตือนเรื่องนี้ไว้ แล้วเราจะยังเฉยอยู่ได้ไง
คือถ้าเงินมันถูกทำให้ด้อยค่าลงเรื่อย ๆ วันนึงมันจะพังแบบเงียบ ๆ จนคนไม่รู้ตัวเลย คนทั่วไปจะรู้แค่ว่าของมันแพงขึ้น แต่ไม่มีใครเห็น ว่าจริง ๆ แล้ว เงินที่เราใช้มันเริ่มไม่มีเสถียรภาพ และไม่มั่นคงอีกต่อไปแล้ว
แล้วถ้ามองตัวเลขนี่ยิ่งช็อก ระหว่างปี 1939 ถึง 1947 ในเวลาแค่ 8 ปี ปริมาณเงินในระบบของสหรัฐฯ เพิ่มจาก 33,000 ล้านดอลลารเป็น 108,500 ล้านดอลลาร์ พูดง่าย ๆ คือ คูณสาม (ช่วงสงครามโลกครั้งที่ 2)
Hazlitt พูดแบบตรง ๆ เลยว่า ปัญหาที่เกิดขึ้น มันไม่ใช่เพราะเศรษฐกิจโตหรือคนรวยขึ้นนะ มันเกิดจากการที่รัฐเพิ่มปริมาณเงินในระบบเร็วเกินไป เมื่อเงินในตลาดเลยเยอะขึ้น แต่ของที่มีให้ซื้อไม่ได้เยอะขึ้นตาม เมื่อเงินไหลเวียนมากขึ้น โดยที่ของยังมีเท่าเดิม ราคาของก็เลยพุ่ง
ทีนี้พอของขึ้นราคา รัฐบาลกลับไม่ยอมรับว่าเป็นเพราะเขาพิมพ์เงิน แต่ไปเลือกวิธีแก้แบบง่าย ๆ แต่สร้างปัญหาในระยะยาว เช่น สั่งห้ามขึ้นราคา กดดันคนทำธุรกิจให้แบกต้นทุนไว้ หรือไม่ก็ล็อกค่าเงิน เหมือนไม่มีอะไรเกิดขึ้น
หลังจากนั้น เศรษฐกิจยุโรปก็เริ่มพัง ผู้ผลิตเจอต้นทุนบาน การค้าระหว่างประเทศก็รวน สุดท้ายก็ต้องพึ่งดอลลาร์จากอเมริกา (Marshall Aid) มาช่วยอุ้ม เหมือนพิมพ์เงินของตัวเองจนระบบรวน แล้วไปขอเงินจากฝั่งที่พิมพ์ได้มากกว่าอีกที
นี่แหละจุดเริ่มของ “วิกฤตเศรษฐกิจโลกหลังสงคราม” ที่จริง ๆ แล้ว...ก็แค่เรื่องของการพิมพ์เงินล้วน ๆ . . แต่นั้นมันเป็นเรื่องเกิดขึ้นเมื่อปี 1947 นะ...แล้ววันนี้ล่ะ
ล่าสุด ปี 2020 ก่อนโควิด ระดับ M2 money supply ของสหรัฐอยู่ราว ๆ 15 ล้านล้านดอลลาร์ แค่ไม่กี่ปีต่อมา มันทะลุไปถึง 21 ล้านล้าน ในเวลาไม่ถึง 3 ปีเงินเพิ่มขึ้นในระบบเศรษฐกิจกว่า 6 ล้านล้านดอลลาร์
แล้วของก็แพงขึ้น ค่าแรงวิ่งตามไม่ทัน แต่แทนที่รัฐจะบอกว่า “เราพิมพ์เงินมากไป” ก็ไปเล่นมุกเดิม โทษตลาด โทษนายทุน โทษธุรกิจ (บ้างก็โทษโลกร้อน)
สุดท้ายก็จะมีคนบางกลุ่มเชียร์ให้ “ควบคุมราคา” อีก มันคือ loop เดิม ที่ #Hazlitt เคยเตือนไว้ เมื่อเกือบ 80 ปีก่อน.. . . สิ่งที่ซุปเห็นชัดเจนที่สุดจากบทความนี้คือ... เกมนี้มันไม่มีใครหยุดได้เลย ถ้าคุณยังถือเงินที่รัฐพิมพ์ได้
เพราะตราบใดที่ยังมีคนสั่งพิมพ์เงินได้ตามใจ ระบบเศรษฐกิจก็จะปั่นป่วนซ้ำไปซ้ำมา ของก็จะแพงขึ้นเรื่อย ๆ แบบไม่มีจุดจบ
คุณก็จะต้องเหนื่อยทำงานมากขึ้น แต่ซื้อได้น้อยลง แล้วคุณก็จะโทษตัวเอง ว่ายังขยันไม่มากพอ ทั้ง ๆ ที่คุณทำงาน 4-5 อย่าง
.
เลนิน พูดถูก ถ้าจะทำลายทุนนิยม ก็แค่ทำลายค่าเงิน ฟังดูแรงเนอะ...แต่เรื่องนี้มันไม่ใช่แค่ทฤษฎีแล้ว เพราะเรากำลังเห็น ว่ามันกำลังเกิดขึ้นอยู่จริง ๆ
แต่วันนี้ เราเลือกที่จะไม่อยู่ในเกมที่พังซ้ำๆ ได้แล้ว
เพราะเรามี “ทางออก” อยู่ตรงหน้า บิตคอยน์ ไม่ใช่อะไรที่ทุกคนจะเข้าใจมันได้ทันที แต่มันคือ “เงิน” ที่ไม่มีใครพิมพ์เพิ่มได้ตามใจ ไม่มีใครมานั่งกดปุ่มสร้างมันขึ้นมาได้ง่าย ๆ ไม่มีใครเปลี่ยนกติกากลางเกมได้ และไม่มีใครแทรกแซงนโยบายของมันได้
สิ่งเดียวที่ #บิตคอยน์ บอกเราตรง ๆ ก็คือ “ความขาดแคลน” ไม่ใช่ปัญหา...
สิ่งที่ Hazlitt เตือนเมื่ออดีต คือกับดักของเงินไม่มีขอบเขต
สิ่งที่ #Bitcoin เสนอ คือขอบเขตที่ทำให้ “มูลค่า” กลับมามีความหมาย
[Newsweek column from September 22, 1947, and reprinted in Business Tides: The Newsweek Era of Henry Hazlitt.] https://mises.org/mises-wire/lenin-was-right
Siamstr
-
 @ 91266b9f:43dcba6c
2025-04-16 03:42:09
@ 91266b9f:43dcba6c
2025-04-16 03:42:09"No," I said, "you've got no right."
Sergeant Curtis sighed. "Come on, Mister Alton, I need you to work with me here."
"No," I said. "Absolutely not."
"He did it," shouted Mavis Harris, my recently new neighbor, leaning over the garden fence. "I saw him! He had a knife, a carving knife. And I heard the screaming and the shouting! He did it!"
"Thank you, Miss Harris," said Sergeant Curtis. "We've got it from here."
We were in my beautifully manicured backyard, sweating under the midday sun, along with six other police officers--all of them armed with shovels, ready to dig.
"This is an invasion of my privacy and I won't have it," I said.
"If you just tell us where your wife is we can get this all cleared up," he said.
"I'm not married," I said. "I've never been married."
Sergeant Curtis chewed on that for a bit, while he did the same to his bottom lip. "Girlfriend then. Partner?"
"I have no girlfriend. No partner. There's nobody at all," I said.
But there was. Sort of. Cindy, wonderful, difficult Cindy.
"He's lying!" said Mavis Harris. "I've seen her. Through the window. One time I called by when he wasn't here and she was just sitting in there, not moving. Wouldn't even answer the door. She must've been terrified, the poor girl. I bet he had her tied to the chair!"
That was absurd. Cindy wasn't into that kind of thing. I would never tie her to a chair and leave the house. That's crazy talk.
"We've got more than one eyewitness that says there's been a woman in the house with you," said Sergeant Curtis. "How about we get this woman on the phone, clear this up?"
"I can't make the impossible happen, Sergeant," I said, stiffly.
My back door opened and Constable Jenkins stepped onto the verandah. "Got a carving knife missing from a set of six," he said.
"I told you, he went after her with a knife!" said Mavis Harris.
She was right. Things had got heated. Words were said. The knife had made an appearance. There had definitely been some stabby-cutty action. Much to my dismay. I hated that it happened. I guess I was going to have to live with the damage.
Sergeant Curtis sighed. "This isn't looking good, Mr Alton."
"I bet he put her under the roses!" said Mavis Harris. "That's where I saw him heading with the body!"
"Alleged body," I muttered.
"Jenkins, any sign of blood in there?" said Sergeant Curtis.
"None whatsoever," said Jenkins. "Not even under black light. Couldn't spot any in the garden either."
"He must have cleaned it up," said Mavis. "Bleach. Bleach will clean up anything. And I saw him, I saw him carry her out and she had what looked like a knife sticking out of her chest!"
"Last chance, Mr Alton," said Curtis, "let's get this lady friend of yours on the phone and clear this up."
"I told you, I can't do the impossible," I said.
"Then you're leaving me no choice," he said.
He turned and nodded at the waiting officers with their shovels. "Start with the rose garden," he said.
They rolled up their sleeves with obvious relish and got to work.
"This is destruction of private property," I said. "When you're done, every rose petal, every grain of soil, better be back exactly as it was. Or you'll be dealing with my lawyer."
"Don't worry," said Sergeant Curtis, "I assure you everything will be put back as we found it. Whether we uncover anything or not."
As we watched the officers desecrate my rose garden, Sergeant Curtis said, "You know there's probably a few million square kilometers of country, forests, lakes, beaches, and do you know where most killers bury their wives or husbands? On their own property, right in their own backyard."
"Convenience trumps everything, I suppose," I said.
"Laziness," said Sergeant Curtis, "most casual criminals are just bone lazy."
"Or," I said, "they maybe wanted to keep their loved ones close."
Sergeant Curtis looked at me, eyes narrowed. "Is that what it is? You kill them, but somehow you want to keep them close?"
I shrugged. "Things happen. But you still love them. Maybe, you want them to be close to home," I said.
Curtis glared at me.
After a while Constable Jenkins climbed out of the rose garden and moped his sweating forehead with his sleeve. "Nothing here," he said. "This soil is pretty solid, hasn't been dug up in a while."
"The other rose bed," said Mavis Harris, "he must have used the other rose bed, beside the shed."
Damn that woman, why won't she keep her mouth shut?!
Constable Jenkins went over and stabbed his shovel into the dirt a few times. "Yeah," he said, "this has been dug up recently."
"Okay," said Sergeant Curtis, "get to it."
"I really must protest," I said. "This is a violation of my rights!"
"I'm sure we'll be done soon enough," said Sergeant Curtis, with a tight smile.
I turned and stared daggers at Mavis Harris, who haughtily thrust her nose and chin in the air, a smug smile on her face. Damn that woman and her meddling ways!
The officers found my second rose garden easier going. They were at it about twenty minutes when Constable Jenkins suddenly said, "Jesus Christ!"
"What, what is it?" said Sergeant Curtis, coming to attention.
"I ... I don't know," said Jenkins. "Hang on ..." He scraped at the dirt and then leaned over, grabbed something and lifted it out of the dirt.
A leg.
"Jeezuz," said Jenkins, letting the leg drop back into the soil. "I think we found her!"
"I knew it," said Mavis Harris. "I told you! Didn't I tell you? He did it! He killed her!"
They worked quickly now, gently digging and scraping away dirt until they could lift her other leg out. My beautiful Cindy doll.
"We've got a knife," said Jenkins, "but it's ... it's ..."
He turned to look at me, his face twisted in disgust.
"What is it?" said Curtis.
Jenkins swallowed, hard. "It's ... the knife, it's ... it's stabbed ... up between her legs, if, uh, if you know what I mean."
"Oh my god, you absolute monster," said Mavis Harris, clutching the neck of her blouse.
I sighed. They had no right. No right. This was a private matter. It was nobody's business but mine and Cindy's. We would work it out, Cindy and me. We always did.
"Okay," said Curtis, "get her out of there, quick! Check for a pulse, just in case."
"She's gone, Sarge," said Jenkins. "She's stone cold dea--wait, hang on a second."
He did some more digging and scraping with the shovel and slowly eased my Cindy all the way out of the dirt.
"Oh, bloody hell " said Jenkins. "You have got to be kidding."
"What, what is it?" said Curtis.
"Oh my, oh my Lord," said Mavis Harris, "I feel sick."
Jenkins struggled a bit with the weight, but managed to get Cindy upright. She is a bit of a heavy lass, I have to admit.
"It's a doll," said Jenkins. "It's just a doll, a sex doll, I think." He lifted Cindy's arm and made her give a little wave. "Seems to be silicon. Wow, very life-like, I must say." He was gently squeezing Cindy's arm and nose and cheek with his fingertips.
I seethed. The disrespect!
"A doll?" said Curtis.
"Yes, sir."
Curtis turned to me, his face a throttled purple colour. "A bloody sex doll?!"
I said nothing.
He struggled to keep his anger in check. "I could arrest you for obstruction of justice, Alton, for wasting Police time and resources," he said.
"How?" I said. "I was nothing but absolutely honest with you. There was no wife, no girlfriend, no body. I told you this repeatedly. You chose to ignore me and you, sir, have wasted not only my time, but that of your department and your own men."
I left him there, chewing air, and went to Jenkins and took Cindy gently in my arms. Her wounds were bad but not unamendable.
"Pervert," hissed Mavis Harris. "He's a dirty little pervert!"
I headed for the house, but paused at the back door and said, "I will expect you to return my rose gardens to their absolute pristine condition. My lawyer already doesn't like your department, not one bit, Sergeant Curtis."
I did not wait for a reply. I went inside and closed the door, quietly, behind me.
Night was coming on and the police had returned my garden to its former glory, and departed. A cool breeze drifted through the kitchen window.
I was at the table with Cindy, tending her wounds. Silicon glue isn't cheap, I'll tell you that, and it would leave Cindy with some scars, unfortunately. If I'm honest, I don't think she was all that pleased about it. As I knelt down to treat a wound across her ribcage, I copped her knee right in my groin.
"Ugh!" I said, the wind snapping out of me and tears rimming my eyes.
I reached out to steady myself and that's when she lurched forward, out of her chair, and headbutted me square in the face.
"For godsakes, Cindy!" I said.
She was baring down on me. I grabbed her by the shoulders, pushing her up and back, but like I said, she wasn't exactly a lightweight. I staggered back with her falling into me, and I winced as the edge of the kitchen counter stabbed into the small my back. Cindy gave me another hit to the testicles with her hand, making me gasp.
I rolled us around, putting her back against counter, silicon squeaking against marble--see how she likes it. I almost took another groin hit from her other hand. I was bending her back over the kitchen sink and without realising it, I had grabbed one of the serrated steak knives in my fist, raised it over my head, and was ready to drive it down into the open O of her mouth.
And that's when I looked past Cindy's head, out the kitchen window, across the fence, and over there in her kitchen window was Mavis Harris. Staring right at me, at us, her mouth an identical open O to Cindy's.
We stared at each other for a long moment, and then I reached up and slowly closed the kitchen blinds.
I sighed. I decided that Mavis Harris was a problem I just couldn't tolerate. Her constant invasion of my privacy was one thing, but calling the police was unacceptable. I would have to take care of her at my earliest opportunity. But carefully. And I had just the spot for her, out behind her very own shed.
Right next to Henry Patterson, the last neighbour and resident of that house, who had also gotten far too nosey for his own good.
Yes, a real nice spot, and close to home.
-
 @ 35da2266:15e70970
2025-04-16 03:38:20
@ 35da2266:15e70970
2025-04-16 03:38:209Jqq62GzpfwYvFgcKiQX5Fy6yyD5qIVdZ2hVOr79wFf7vtXyELuBT6RXik9TDnsf4CSqQQwbTbJ/8zO2hm/H0iEvBJj2fGGf/lJQ9OYtL56bIGbdPWDiFO0cG/aWaLEX+i5kc9aaxXvlYtdQVakkpcIo4FS4u+Opi7NmGJtLYkixj9njZ6RXnRhjYtBDqS/I+lsPM+8QlLxgUJyzX2FSWhMNCEkwGQyY7WL5ve3HmUyOHgvnE0jD5POQc8K576ujKv/7bIgVsLHDjM4YzGUnVozy5JFNIsuAFUU5aBXsqABeiAwTDBMpid+3kvT3THISm2YM2KSWz12RTI8yb5NduQ==?iv=qQok9QsgRXAZajfYeiFqSA==
-
 @ 35da2266:15e70970
2025-04-16 03:36:00
@ 35da2266:15e70970
2025-04-16 03:36:00lTFfszFRc574FKS4B4a6nuGhDb75H+3br1OH+YeiocHc3ef4q7oFvPns983W0dA911/8OMRW/+UFE7EESUeHCk0YQ6KSqzbzNAU3MKJaw8mwRmAzgyizq+3lTU0lB+A/CdbTmfmJP9eiyPsN/hkyPaYm+w35nhzEzFYeXfS6GZkB/vDoeyQVK8pwaLXjeo6Xo2qhZGu0V9DJEMHZjfmnCvXc1OR/JDOCz45pNmPR4SRBrsckZLNbmS9FGWQY9ffiSkA6YvuioiEqV5jmVz68F08zt57nm8BMnlQDdtI/TDZ8/kmXyBgcBwOM0ep5nTod7jEu+ydFNu/RHfZdWNetGQ==?iv=PEfCBpzguAgauYj3mhiO4Q==
-
 @ 35f80bda:406855c0
2025-04-16 03:11:46
@ 35f80bda:406855c0
2025-04-16 03:11:46O Bitcoin Core 29.0 foi oficialmente lançado e traz diversas melhorias técnicas voltadas para desenvolvedores, operadores de full nodes e a comunidade Bitcoin mais técnica. Desde mudanças na camada de rede até a atualização do sistema de build, este release é um passo significativo na modernização do ecossistema.
Se você roda um full node, desenvolve software que interage com o Core via RPC ou apenas quer estar por dentro das novidades técnicas, este artigo é para você.
Alterações na Rede e no P2P
Suporte ao UPnP Removido O UPnP foi totalmente desativado por razões de segurança e manutenção. Agora, a recomendação é utilizar a flag -natpmp, que conta com uma implementação interna de PCP e NAT-PMP. Mais seguro e mais leve.
Melhorias no Suporte Tor A porta onion agora é derivada da flag -port, permitindo múltiplos nós Tor na mesma máquina — ótimo para quem opera ambientes de teste ou múltiplos peers.
Transações Órfãs com Propagação Aprimorada O node agora tenta buscar os parents de transações órfãs consultando todos os peers que anunciaram a transação. Isso ajuda a preencher lacunas na mempool de forma mais eficiente.
Mempool e Política de Mineração
Ephemeral Dust Introdução de um novo conceito: ephemeral dust, que permite uma saída "dust" gratuita em uma transação desde que ela seja gasta dentro do mesmo pacote. Pode ser útil para otimizações de fees.
Correção no Peso Reservado de Blocos Bug que causava duplicação de peso reservado foi corrigido. Agora existe a flag -blockreservedweight, com limite mínimo de 2000 WU.
RPCs e REST mais robustos
- testmempoolaccept agora fornece o campo reject-details.
- submitblock preserva blocos duplicados mesmo que tenham sido podados.
- getblock, getblockheader e getblockchaininfo agora incluem o campo nBits (alvo de dificuldade).
- Novo RPC: getdescriptoractivity, que permite ver atividades de descritores em intervalos de blocos.
- APIs REST agora retornam nBits também no campo target.
Sistema de Build Modernizado
Uma das mudanças mais bem-vindas: o Bitcoin Core agora usa CMake em vez de Autotools como padrão de build. Isso facilita integração com IDEs, CI/CD pipelines modernos e personalização do build.
Outras Atualizações Importantes
- -dbcache teve limite máximo reduzido para lidar com o crescimento do conjunto UTXO.
- O comportamento Full Replace-by-Fee (RBF) agora é padrão. A flag -mempoolfullrbf foi removida.
- Aumentaram os valores padrão de -rpcthreads e -rpcworkqueue para lidar com maior paralelismo.
Ferramentas Novas
Uma nova ferramenta chamada utxo_to_sqlite.py converte snapshots compactos do conjunto UTXO para SQLite3. Excelente para quem quer auditar ou explorar o estado da blockchain com ferramentas padrão de banco de dados.
Limpeza de Dependências
As bibliotecas externas MiniUPnPc e libnatpmp foram removidas, substituídas por implementações internas. Menos dependências = manutenção mais fácil e menos riscos.
Como atualizar?
- Pare o seu nó atual com segurança.
- Instale a nova versão.
- Verifique configurações como -dbcache, -blockreservedweight e o comportamento RBF.
- Consulte os logs com atenção nas primeiras execuções para validar o novo comportamento.
Conclusão
O Bitcoin Core 29.0 representa um passo firme em direção a uma base de código mais moderna, segura e modular. Para quem mantém nós, desenvolve soluções sobre o Core ou audita a rede, é uma atualização que vale a pena testar e entender a fundo.
Já testou a nova versão? Notou impactos nas suas aplicações ou infraestrutura?
Referências
-
 @ c13fd381:b46236ea
2025-04-16 03:10:38
@ c13fd381:b46236ea
2025-04-16 03:10:38In a time of political volatility and declining public trust, Australians are looking for leaders who don’t just talk about accountability—but prove it. It’s time for a new standard. A protocol that filters for competence, responsibility, and integrity—not popularity alone.
Here’s the idea:
Anyone who wants to run for public office in Australia must stake 100Ksats to a public address and maintain provable control of the corresponding private key for the duration of their term.
A Low Barrier With High Signal
The amount—100Ksats—is modest, but meaningful. It isn’t about wealth or exclusion. It’s about signal. Controlling a private key takes care, discipline, and a basic understanding of digital responsibility.
This protocol doesn't reward those with the most resources, but those who demonstrate the foresight and competence required to secure and maintain something valuable—just like the responsibilities of public office.
How It Works
This system is elegantly simple:
- To nominate, a candidate generates a keypair and deposits 100Ksats into the associated address.
- They publish the public key alongside their candidate profile—on the electoral roll, campaign site, or an independent registry.
- Throughout their time in office, they sign periodic messages—perhaps quarterly—to prove they still control the private key.
Anyone, at any time, can verify this control. It’s public, permissionless, and incorruptible.
Why This Matters
Private key management is more than technical—it’s symbolic. It reflects:
- Responsibility – Losing your key means losing your ability to prove you’re still accountable.
- Integrity – Key control is binary. Either you can sign or you can’t.
- Long-term thinking – Good key management mirrors the strategic thinking we expect from leaders.
This isn’t about promises. It’s about proof. It moves trust from words to cryptographic reality.
A Voluntary Standard—for Now
This doesn’t require legislative change. It can begin as a voluntary protocol, adopted by those who want to lead with integrity. The tools already exist. The expectations can evolve from the ground up.
And as this becomes the norm, it sets a powerful precedent:
"If you can’t manage a private key, should you be trusted to manage public resources or national infrastructure?"
Identity Without Surveillance
By linking a public key to a candidate’s public identity, we create a form of digital accountability that doesn’t rely on central databases or invasive oversight. It’s decentralized, simple, and tamper-proof.
No backdoors. No bureaucracy. Just Bitcoin, and the competence to manage it.
Bitcoin is the foundation. Asymmetric encryption is the filter.
The result? A new class of public leaders—proven, not promised.Let’s raise the standard.
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ 35da2266:15e70970
2025-04-16 02:44:06
@ 35da2266:15e70970
2025-04-16 02:44:06fG+OPtj+9qPneI6eoh8G6m0+aQfxG6wbyeRGwYYVUYyGgZrNCzT2srRaP2CYp+KtOYAazGaN9UfHhdrVZOePCEPFRT8g/g4NwKwf7DRK8bLKeG3CNXCt0dQ2I5I9hUd6/HytYhlTCm/aUBA6oG3PQ2+xHFiHdEtLnWAFDfHSNqbtIgvOGoxdTUxCfXtRlxk4epaV8CyGmyJ3PSttjCzChxvJiSoi8+W2LBZtwVqkuAu/Wn6iRv82ExyX47YtEDf6FsvDPDiM54GPkclOv/umdUGxCLSAAOUOlLfBKDLA2jaHzpv4bfiI/vzdSd/kzNkssxtY14X6f7C8qWmA6J3KxQ==?iv=tQfpmbUuub6Kw6Nx1/uRbw==
-
 @ 35da2266:15e70970
2025-04-16 00:31:22
@ 35da2266:15e70970
2025-04-16 00:31:22LTcj+3KWI8XMzz4Ym2m+BueOuNcKP0mbeS59YLfrySjrf+xfAI8Xz/7qpW11EhahB67O2nZW2kMFfiaFpvDy53ot4a5MJ4Ab/Lt5d7Rg018eXygoPotWELDh69tGyb4nHZGL1APOFLBz0n+zYMceBoTT3cIyvZjtWLbsovCMaafxUWyx23cZ6DmgKizKKJDTQPFR+iVC1N3i/QOBVQb4Sl/iq2TR8J9gVbkOtU9wbZWp27zOamCI06FI0L+fLRLwVK39raNKLg4sHioRK5mbbRm1959NmezqF+LugdVfWoCfvn5IZjBj8j3cVJKeUfgKwg0dgq4M1/yPOTDM8d0NBIk3YXZAIQ0CcGYMfNCyVuY=?iv=da7j+e07uz89rJPwTNPAng==
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 35da2266:15e70970
2025-04-16 00:29:18
@ 35da2266:15e70970
2025-04-16 00:29:18enNjYOtdn9VukMmUvKkHjOljcVk2g5KKH5PjjljxUuOABxqIGInmW1jqgF9+E5Unxcoi8mWNJtOrC6Br/z23XrZjc+tt2zxbe9gLbtfZnTxXRUD5BmLzQoENXlBfjZjV90Yzt0S04CdmNKTZVeeJETXKoXWWuwlx5GlRgMJiC92kZyk26muxi+Xvh9lxSxascUQELNlqY0ySXG4/Hg/K8qiFxVBB1ZU2kuK4EW5RU/5Su2gb5jpzjCsuYXfM5Nd05eehnbbdY8S0jt37/B2TzYfrim+iLJM4Nq1TX3pOoAGhZgSKoDbbCwu8xxsDdTDRc9sInaUn2obMb4w0ylH+ZYHwiuSiOW0anfLyUM2/NoYPX+ZEx57waSU7+2zbY66x?iv=uuQ35Xb0RNpJAn+GJVixKQ==
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
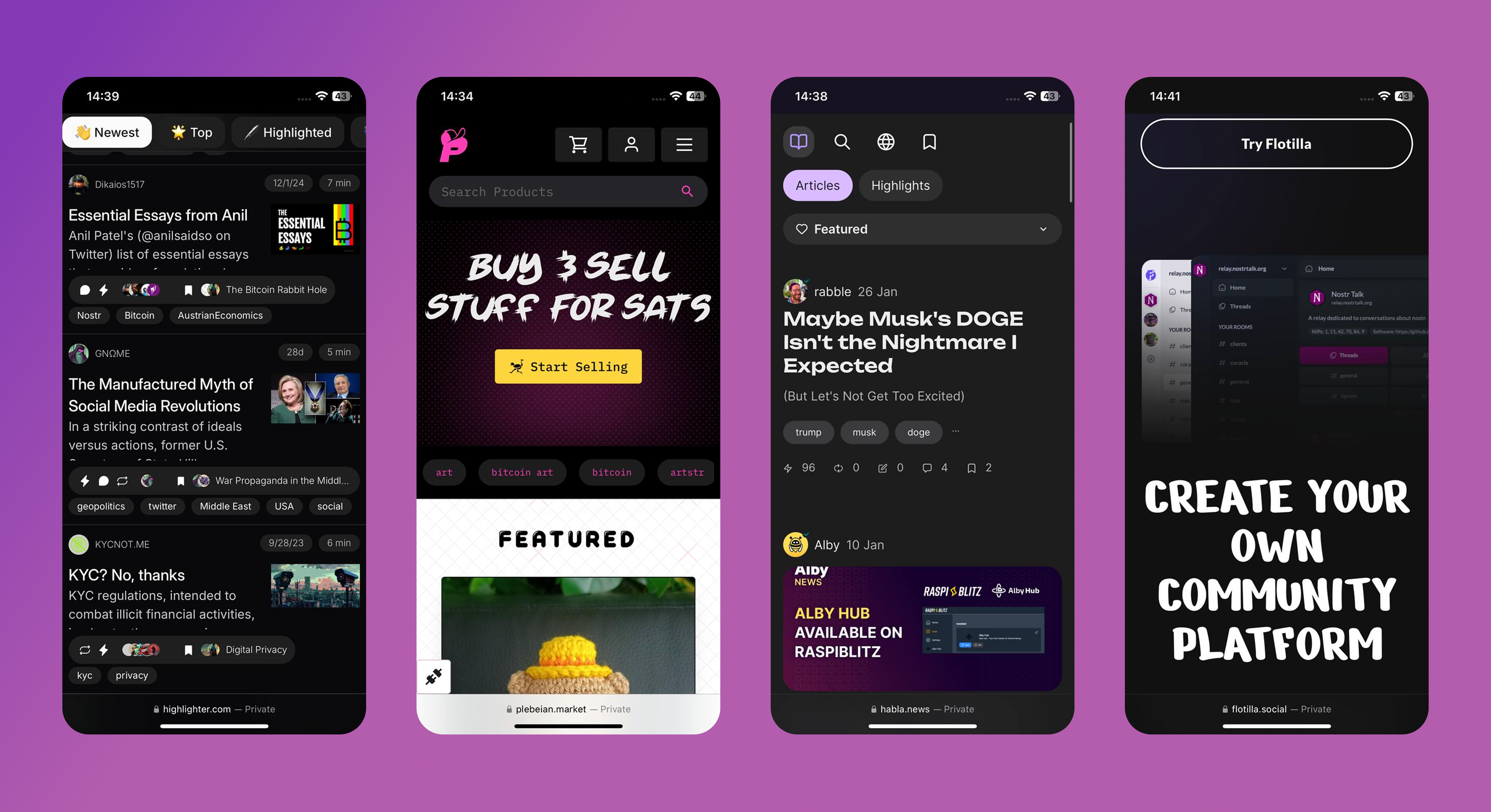
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
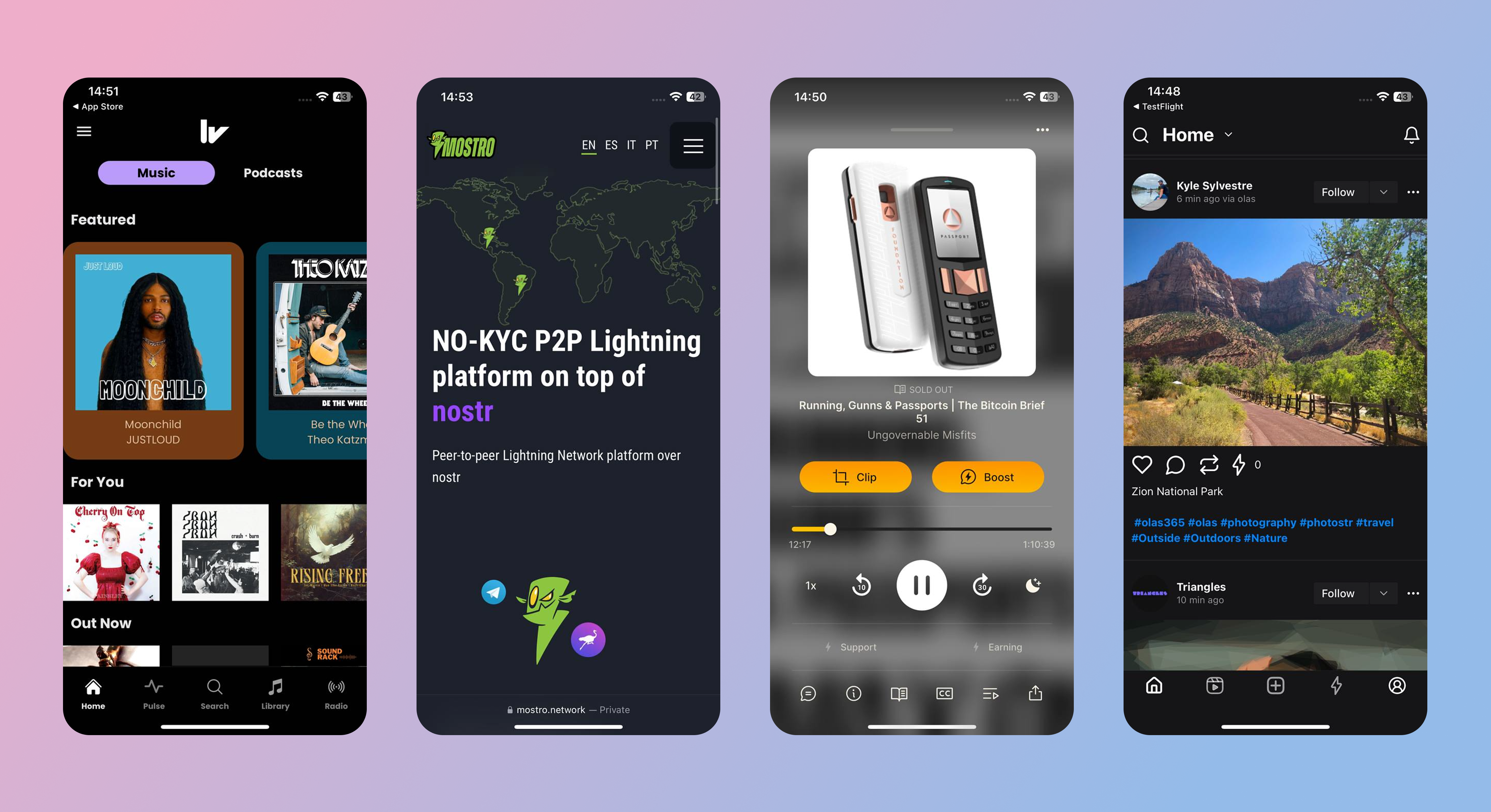
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
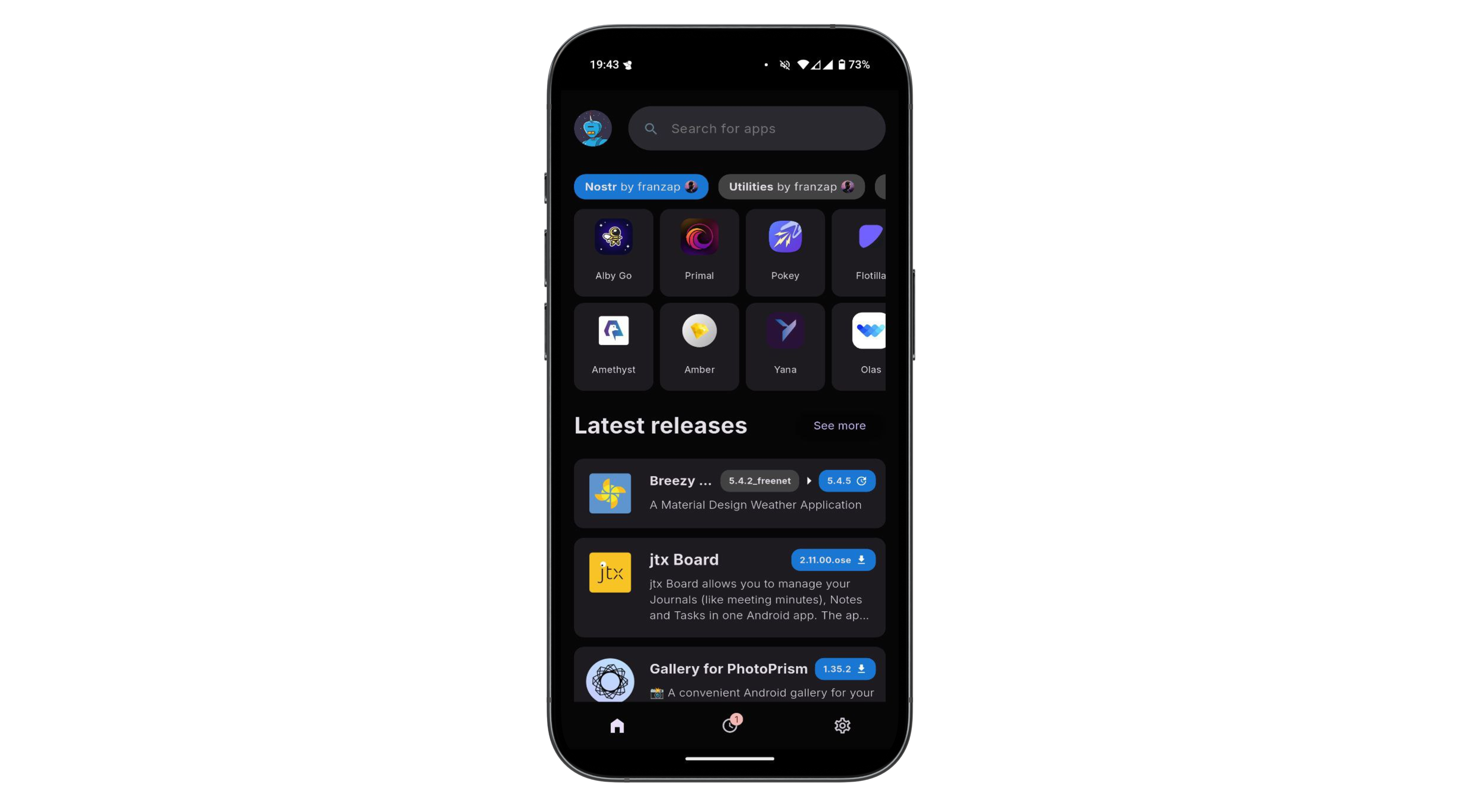
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ f1989a96:bcaaf2c1
2025-03-27 13:53:14
@ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers!
Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace.
In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances.
In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes.
We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Turkey | Lira in Free Fall as Erdogan Arrests Political Rival
Turkey’s lira plunged to a record low after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of primary elections and follows the increasing repression of opposition figures in recent months, including the suspension of political opposition accounts on X. Officials also arrested Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked protests in Istanbul despite a four-day ban. The regime is responding with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a dozen other citizens recently arrested for “provocative” social media posts. Netblocks reports that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression.
Cuba | Banks “Hijack” Citizen Remittances
Cubans are struggling to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities force their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “hijacking” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them.
Pakistan | Announces Plans to Regulate Digital Assets
Pakistan announced plans to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly suspends the Internet, censors social media, represses opposition, and burdens its people with the highest cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also exploring a Central Bank Digital Currency (CBDC) and tightening controls on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated 15 to 20 million users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported Bitcoin Pakistan with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario.
Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality
Russia’s central bank plans to pilot its CBDC, the digital ruble, in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse.
Nicaragua | Government Mandates Public Employees Declare All Assets
In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to disclose information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the threat of termination. Ironically, despite the law requiring such disclosure, Ortega himself has not declared his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation.
BITCOIN AND FREEDOM TECH NEWS
Demand Pool | First Stratum V2 Mining Pool Launches
Bitcoin mining could become more decentralized and censorship-resistant with the launch of Demand Pool, the first mining pool to ever implement Stratum V2. Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more here.
Bitcoin Mining | Three Solo Blocks Found
Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks mined in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The first block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block 888,737. Just days later, a solo miner with under 1 TH/s of self-hosted hash rate found block 888,989, which became just the third block ever to be mined using an open-source Bitaxe device. Most recently, on March 24, a solo miner using a $300 setup successfully mined block 889,240.
Krux | Adds Taproot and Miniscript Support
Krux, open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), released an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission.
Cashu | Developing Tap-to-Pay Ecash
Calle, the creator of Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is developing a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo here.
OpenSats | Announces 10th Wave of Bitcoin Grants
OpenSats, a public nonprofit that supports open-source software and projects, announced its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for Stable Channels, which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for Floresta, a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant.
Bitcoin Policy Institute | Launches Bitcoin Summer Research Program
The Bitcoin Student Network (BSN) and the Bitcoin Policy Institute (BPI) are teaming up to offer students an eight-week research internship this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply here.
RECOMMENDED CONTENT
Principles of Bitcoin by Vijay Selvam
“Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it here.
Rule Breakers — The True Story of Roya Mahboob
“Rule Breakers” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 35da2266:15e70970
2025-04-16 00:15:02
@ 35da2266:15e70970
2025-04-16 00:15:02yf+dVZcg5m0ZWh0Vagoapkqo0p7GUDpcuicMVY3R1tN0pWbgiIT5auPs6+nIgD6fuCj8NpZYCI/ldesFKuBjowJxgq9WAKEgrVIkok9Mmes/7kjGP7aPzXyNBCmnrM3E8ZhmUI9YWCYZDNnrULkGPmco7HaTnMJOFqLUp6NzWtROYqV11HNVGG+H33blj0HA/HESPNaPbFDvw/2hGGf+XGzOaWfkRQFKvWIZJKPgMDAAJgMyUBHHEI6fkB8SICNWIT78Oj81JquMw448hMQ92a1aJu2tXNZiIyZ4AfioA/E0ZFK4DKaQ4V3Lav1DKr9iYIS1dOxZ/qAH3jsaTASgoLsgVISHEjFgFXO7VnTa8GfhzUHzgl/7fH/3OVnnYrwE?iv=UO8NRkvzZ3ApNXIkv5WSgw==
-
 @ 35da2266:15e70970
2025-04-16 00:13:51
@ 35da2266:15e70970
2025-04-16 00:13:51Ssk0hLkQlHXK4QXXhUjJFKdEHR3N1PuXmUIRG6om8yd1z0CM5lExk6oswyjHMVfbLsEBVR60teCcLwJhQcXMaTD7szHn86vwsD8rlm+H40SpDQkpyt+BtOhDTvWA0hiJoKTUVn+LQQv8uMP1dfZHTN/ircda7yLEWB7hLHbdVh1QV3vxt0WOzmefZPbAlnaVJidPwJpUndIm619FX5XqxYprZk5tVSbV7gr3JVLd06LLnmc8Q89z+TohPWWdkHgH5342I5tRFZeYg+VeBpaxg/WNVgVcjN5pUaXDg1dt7zP3smA9cmokluuuNbqLJ93nHURWO3+Mm35E9kMfedblRD3JuVIWi3HJPPTn3VDGnxMICWHTiB3vvEMuqvd37B7f?iv=mCMpjHPjNg74Cni8lc05Dg==
-
 @ 35da2266:15e70970
2025-04-16 00:12:12
@ 35da2266:15e70970
2025-04-16 00:12:12CYpQ+5c+twHS+/iKsblk1i/ZZD/lEVz6U8v1sDI5eqNtOTBkGvldJsrN6YJy7Xq4Oyc12fzkVivUURSYpHqbFx7LSqgwNjcnGV9ZyKDOcnnKzUSS1bRMeF4mFJb68t6hgZgiF+FpK0BL+JPFDoV8vYCQ5eBXqt6o1+4pq7CUHEZeyfVzHgQrg88XJwTvLNHbmpCE9D7pi+JWZKW4r6FEFzWBv0P82UZzq6EHNeH3C0Aq8yc5r6rs6z6wtEma46l5qAr01ISRDrnjN/WEgGTjkuW/zlIKpt4g/yhb79adaCz7MLDBhcTCNhGRgW2AJ0JorBbtGDcxcQYGHXcsjBEmn6G/ypNEi05V/n6uIUKJN8jQcZUyPVPaWF1Ky811nKkj?iv=1sgYyHP5h+upfg9POmRqww==
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 35da2266:15e70970
2025-04-16 00:11:19
@ 35da2266:15e70970
2025-04-16 00:11:19siI0dpuWuUZnxX+mmnRcRb75CXcVwS2aOPyVNd/SjGdltb828wShhZJVCj89zXIaAVIu92ifqUN3WFV5i7Q3LqN0LnlRNnAK1Rlx99N2DmF4VzhnlnaRfn/fkJ/X2z+RLT7odiWHzolaZbKXz2fV7hOHrgkbR2U5sJOQwY0BKOzVTDEiBBoirNWXCb6zn8XZ7AjezdbSLJG4KyebJp39SGmmHV8j/bvCra+EWOe6RvA2XoMIwIWBhzuJbgZ3ywLAyTj6roxBJDz9GWzWE/UWyvk2xAvWwY0aOG1F0fQpRfDORdcb8UCJUf+Sjk+rixqL9e7HXWn7FXR9ok/ewoujUoZtn/v4D32YAza2VQld3bsJ8yKMb55nygGMByrNWHmz?iv=wPdST/gc8OebFdvcY5GPuQ==
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 35da2266:15e70970
2025-04-16 00:09:35
@ 35da2266:15e70970
2025-04-16 00:09:35Wj2lYl56VPn8fLjFG1jyFqDTJkmiST+4zqrfFm4+pX8cYNZkNiva+7kcXxkOeAyl3mDs9qXcRzOP6vscPXFtKUxOBCDdwN/xK7yvsJQXbsEje6HsA3Lpw+aRHrzwSBpdW5QQR530yJfkZ2pneLycBT1gt5qhUu6Wkf0OCB0vQrPBAKx7Q4wRUlYmbmsS3Xv39+nOQXTfpJVPCLMM82RSqjqcDsIUj2njuXEiXBwA73ZKGl+S2ndN1nwg1od/CEslCqlK8uVbmhDZir8evG2lOsAbwIYn7rMWBs/2TW+pM/qychxU7ylLEVAlk9GzPLD+SWdGmaS5/erpJYDBAcsDzsJw9lDU2Ht7rXmUELK5oIFv1we7p0mfcEo+rtlHh4kF?iv=I186Y0DIBF2P7N5cKAasbA==
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 35da2266:15e70970
2025-04-16 00:04:40
@ 35da2266:15e70970
2025-04-16 00:04:40Qg+2vg0S9vXU1mOu5vRazmar3ItVtDsDs6j9uXmFE/2McOobjE8JpQinwdG/DM2aYQ92Xezj952C408rhg6syzR07BaP0gt4TmyimN+2wlPxLP48gGboa/S5Ptjk9KggELOk2oVE8jSLF1qDnIOdj0ktayvPgvQUaIsee+EeHk82VAhXxXfwL4m7JNVOBJzp+fDWC/mtaLoJH8PsQbXh9OIqccONrbhW2YJc2ZdQs3ZWVPCdr6uNdFVioPH3fV6qo1JUWK3O58HCj2MsYkSdarMYk3zZfKPE/VGMCaVs/n5X9fcRZmMcyKRzUp3FV4rgM2PIReL+MDubeNL03pOFAxKDZrBXV8r1/mJx5GjFTkc=?iv=JD9MkFOCMv8RFE8pTkEPXg==
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ 35da2266:15e70970
2025-04-16 00:00:28
@ 35da2266:15e70970
2025-04-16 00:00:28yc+j3QrBERVcrn1VStfklZu4h3hBUOWsfiVNtiQ/g55p/Qe4iAXch+OdGEj5BhQhOjaP1Th5I2ZSaJh/aedEuDe3A9tzLDbK79FqYp5jPB49rsvHmlVox+S+LwVCD5nqTLJ2aA7PVlDkE7yMuTyGYEMgYe901y/XcaudeJ0GyAjP//044SyiC4oxVyeKgOJP6teyaBRzZWu2jOZW1E3MBZbVfxEtYXlVIWK2lfGEjH8yImb46vstSOxqT3uVsN2q2yuGnCwEy+G6rIP6s8jr/REnZXJwzoMeFiJrxFpvZFZIybI8u5CV+Ibsc3MEmP2jGmBwunmCErCRID+WjItojdyfpZCuyhPEUhvUhB3Ocqg=?iv=WMsh7rlFrEMomNrq0S6CFg==
-
 @ 35da2266:15e70970
2025-04-15 22:57:51
@ 35da2266:15e70970
2025-04-15 22:57:51AHehpEcOzlTbnn0YaQlyUg++VOi7NQ44B6oSrJi8QR11GxF4hZMwoDjZE8u46qr8koCcuN6jWF1pFi6/9yaUgkwjZwVPIXVMr3M/Ns9zLJzLQJsbR/aeTH5oVlO/T34gbHI62xFnJh6Z7qV52X77XEKouenEpqKtaQHGT/rUM/gIzFbOATJPCSXrQJh5MB5wlOxx2woB8zOpsPW1Du4CFY7c9QNowFtj+JK7MaNg7a6Oei19ui5nCIVolZTL28DByAQPeXN+wIg6Wa3GmGrs1WLK9NFcry+1xHccD1OCM2M1Sf9ZRQmfJ/m0p7B6dlCsmnIiwAO2y/T6ZcnPxS7hfg==?iv=iQ/QgMVqCUFHox16uXox+g==
-
 @ 35da2266:15e70970
2025-04-15 22:38:44
@ 35da2266:15e70970
2025-04-15 22:38:44LUNdI+0ES87Z4Y3u6UqeHZ6NPYrn8jI3z6KfcaGFhDrC/LHoNIYWYFtRVNwt75j1u7SFCFkQCtq2L9cPXafz8IsK43eOCNk9I4jdT8g1jd+vHH/w/GD1LdR5IZlGXX7fIc46DXS2qraUGdeSpakfg0uN52dA4O9yTmljCCqnaEpeQTaU0bd3mLHveAJfWsmvPgQd36vcoXOD5aXYqotZmcRyvHSJwLClEKAN7qlNBeMdKNpkbpRMTYz7G7w5hAqJT1lJHE7bmPcWTmS9JG0JcRgskA3FYurOBmyV3ZmjyUC6KqmLzBfP+JeQmYKMcPCk5G0+OFv7KG7L1mWMPVS9GYayxA5HXgnpuTsitNgO9hxAFcamVWxCkYDOVQdjfqyV?iv=8lQSaN3o9AcqKS8PM5eZGA==
-
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ 35da2266:15e70970
2025-04-15 22:38:35
@ 35da2266:15e70970
2025-04-15 22:38:35Z+fTyrtePLMT0W+lR8MHBan7Dv45irS2udKxjVslQdjsxacgPAbE49g8kOj03RvaSexpcT4c5sC9AWv5aW7DZiVpB9+NrXxAgN1xWnBlds7btlpTqVn6eIrSYNKeviZ6Ie7MY6eYMsWD3np5ggfHQUFHWoy0dXwGxPmQBT1lJJtzAyA3ozAm/inXQl/YkTbvHlbQyA6cFtU5YGw/1SrN4XerNK+E3y2F2lpTf/M4WJb9OjRufdrm0Qdosci3liBNXIdgLJm7Qy3dcfpNev9TTaCgZ5M/EAUbrjG8+583GXFvPWvful14k0M0AQxhZiRzENaWns9UunDJKvRJCsZKA0aLTFx4hHYkfsL10IkGYuDM8U6ujpBOWut+LMLy8D5q?iv=DalQBHsbwDSSh3b2TLPc8w==
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
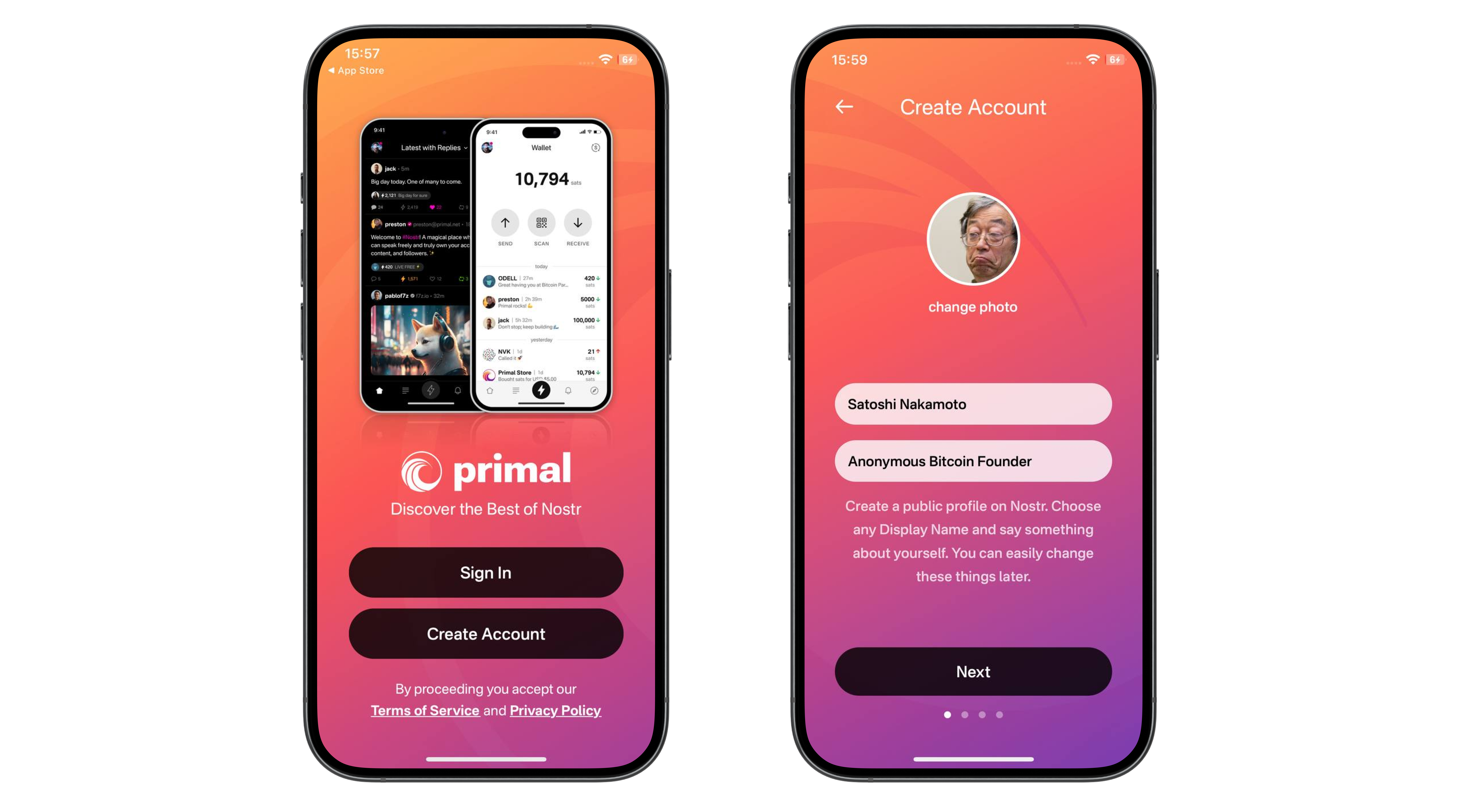
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
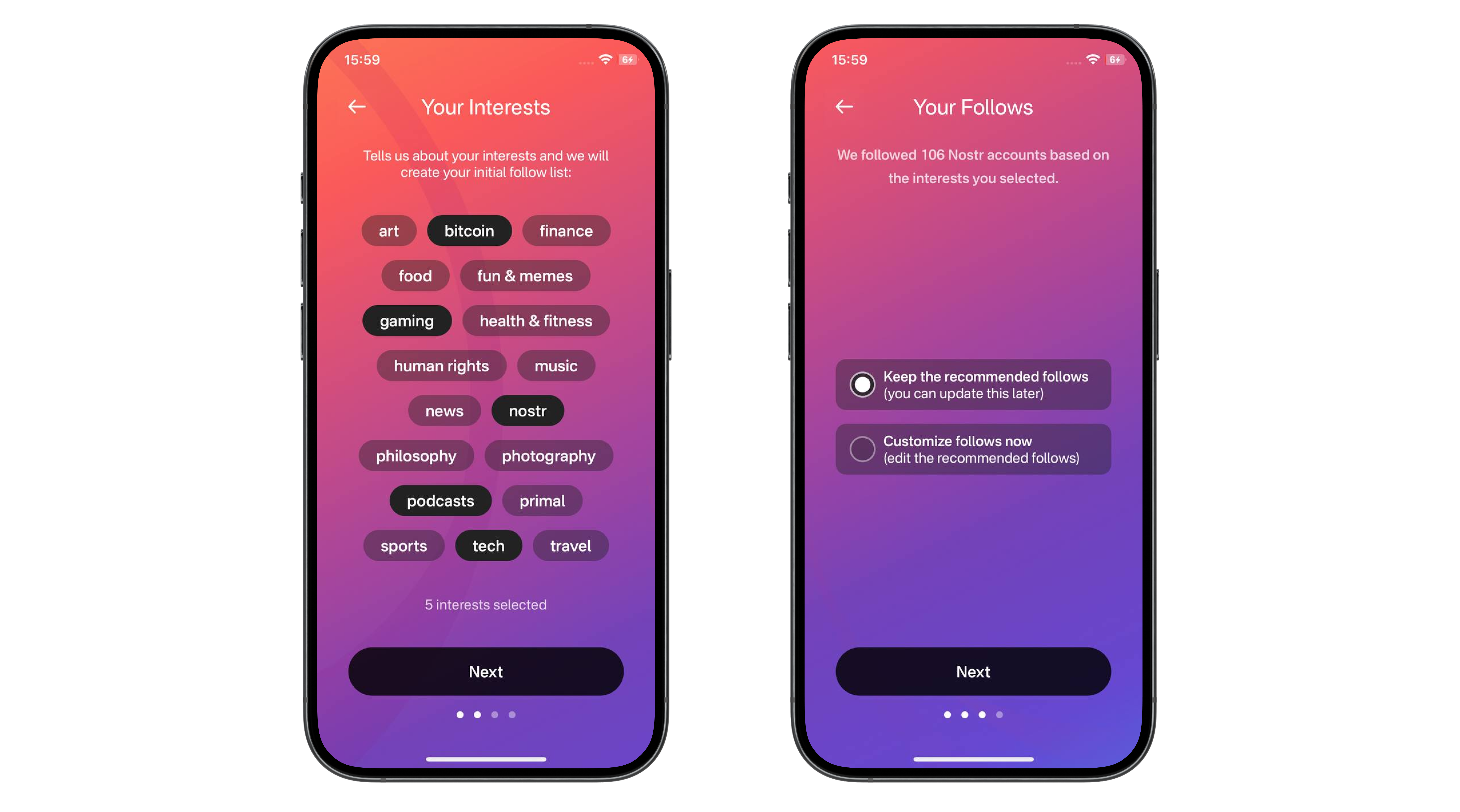
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
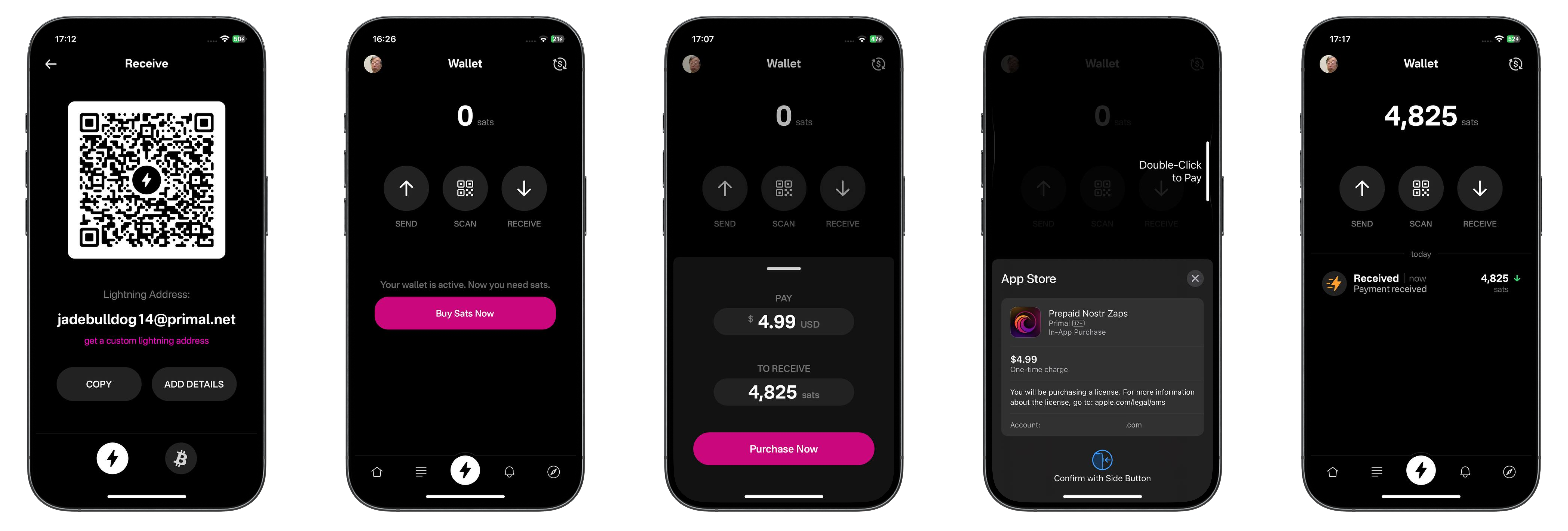
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
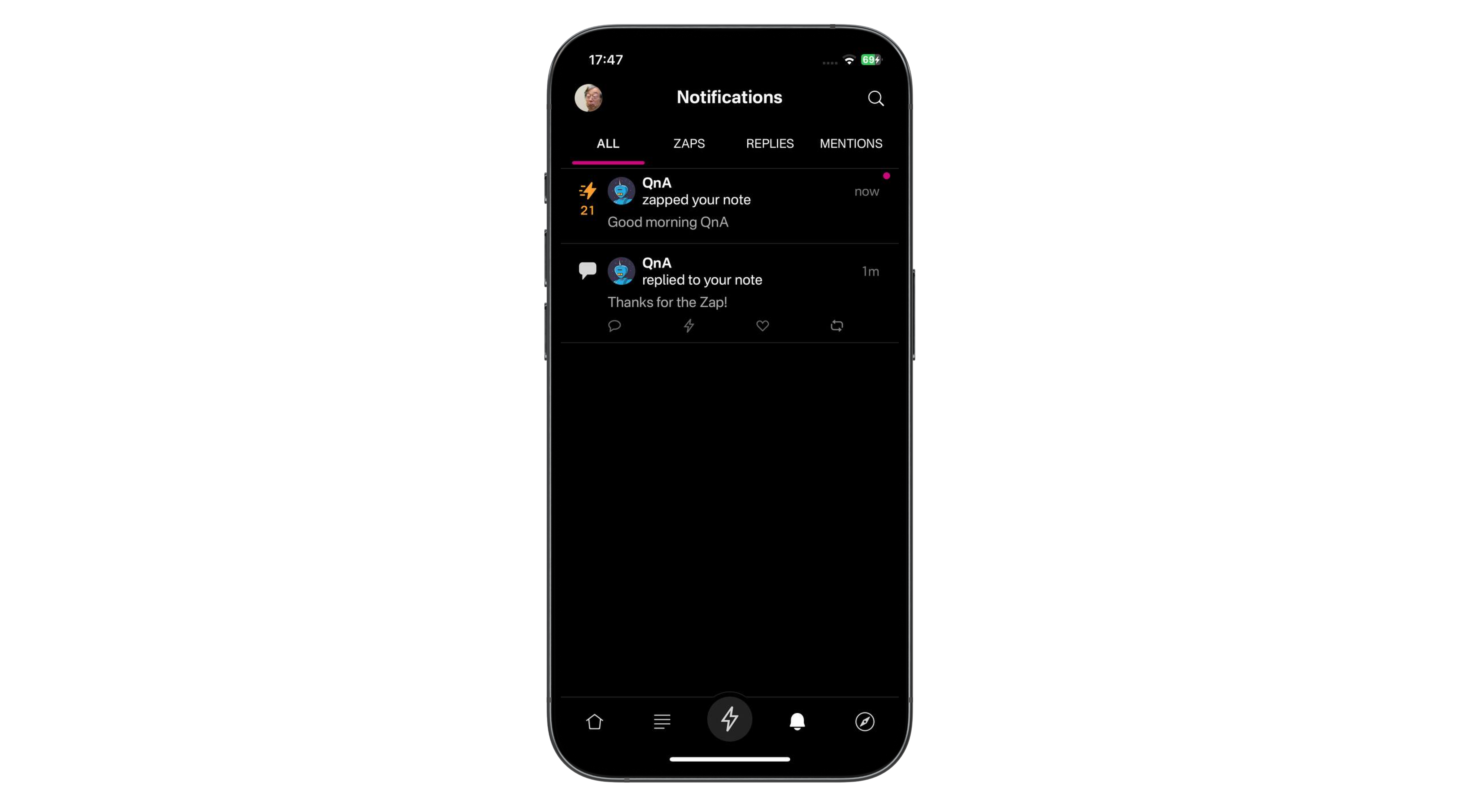
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
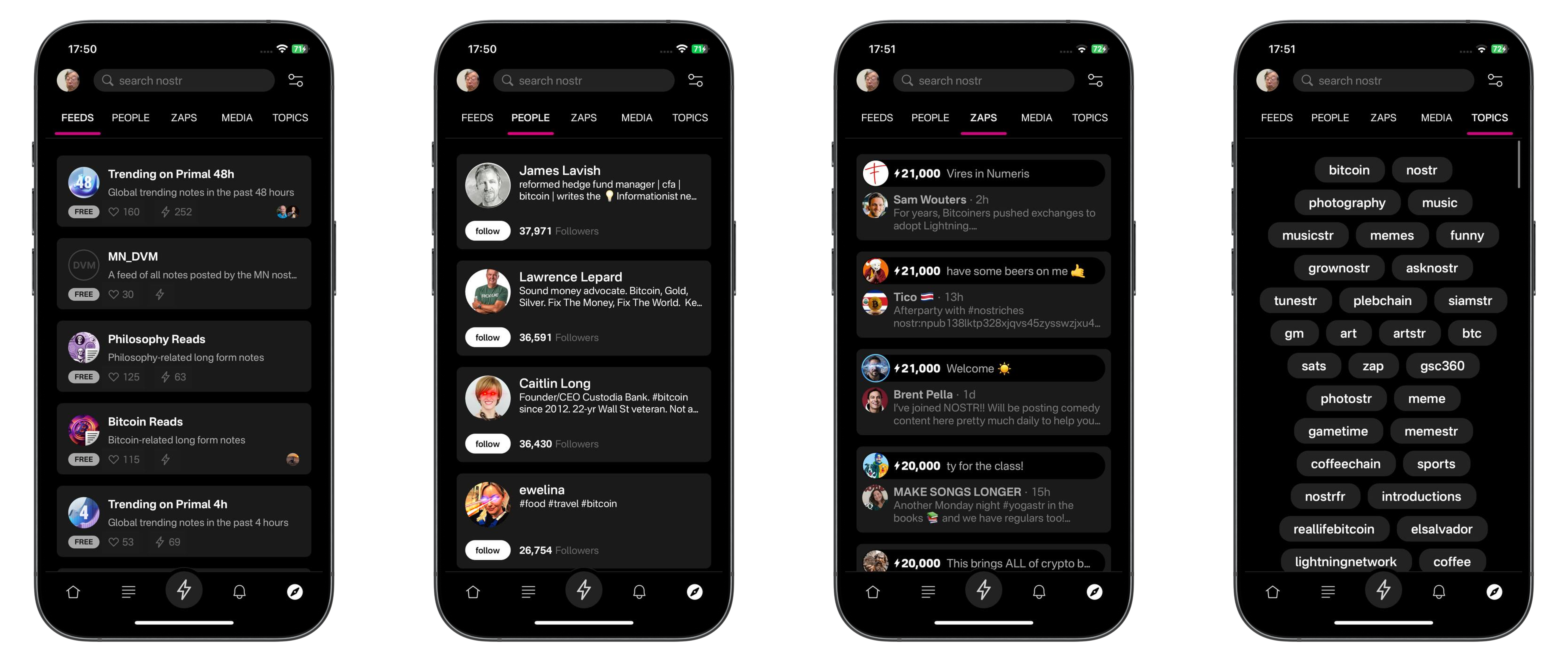
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ 35da2266:15e70970
2025-04-15 22:35:59
@ 35da2266:15e70970
2025-04-15 22:35:59NOFTr2Erm/FWn2Iwbon3TGxlXR61yy6zo3S2iG6PFV9nMUdCeqGRKNHSOUasBABwJsvmMY4WP0AePoHYuvNL6QabNxz7/tHLp3DJkj+WjDVF4US9qc48DJiiapz7sUaFucj2koDs+NkUcAZD5Ohw2RP+NS8YFQFhqQQtG3TDYqA6Lr900YqEMSR17KbhzZlNR4OqBO8yDA17Y4ltEOjxaOv/5ys5Id7qqenK1bKjPd693nU+4p60iTh/StDPKzmKZr8LFURCPH623RnjXIvwqHN00bMyiW7t1Hup6uIwZDKpVAhwjYLYUOiXlYhPtB2rQKQny5xssH8DpzNF3LJfSwFFGh4U/SjCs388WMPpd/PgtEic2grK9BBDzAeTbFLy?iv=4bG43qfls9wjBQBuTmn99g==
-
 @ 35da2266:15e70970
2025-04-15 22:34:50
@ 35da2266:15e70970
2025-04-15 22:34:50L5WDLmxdFunBoKzVVQY4l5mleg7nXQ8lRH1UAq3fNhGFN5RekZMFKZ3L2/17izs4C7n9afGPicEHrImszw1JsQWsxrw4cXKNZZbgmSw/haTJ5Ck8HmvdTi62/E2rsLlEzGgerDa2cFdOrSrLl5FzUcTSz/UB5KxMsOfgKeulIjxK+IxUuKtTXS2NFCRLBgYkr6prcjKjK7ejVOit4smZWmvs93+c4mXQxyZR4JTsjRdD0h017LG8962yDq+rjysCiiXqrCTcdN0bd/a6PVd1hdSi3q886h6+3Jqfq4aSyZ5jJPfde/pDrTPFoHtXfcUI0nFEJ7DUUk7dcjCL6XHH9NEhLe6RCZdLx7a4xbcYTWU/pHfPS2G1Vmbg9KWBs2hO?iv=hUn2MjQWE6EmnKRqcQAGiw==
-
 @ 35da2266:15e70970
2025-04-15 22:34:36
@ 35da2266:15e70970
2025-04-15 22:34:3697d+mYEJp5IRWD74WbEfsn/KgzKbGvL7O0YY6fu0xlh9p3tPkcna2hbVduDFtL85T9ayoJFYQJ/svNaYOT7YNpCJxeU0oswCRExE7cHR0KHfIk2EsMGjmGoeRlJT61oP5dO2CxXvpLBh1Xedwf+sXiAJItT3l7Xf+jRHBEa7EjNNM3vkIIuTYHVQCx31Hp3KK+fYdl6AymhS+KmxyOxNDMGvjhW2U0jaIUTffkSS8reSAcbGMx8SAMKxuhIH4O2YbgmyjiSn7CzHMD0zrhxXs/g9KS4SioT9Ka5yddSYI2YxTlAzKTKznTdhfzvuQLV0/26SXFqI9i+jtKlYKIhi/g==?iv=I4Y2WyCQqqsbTIGbWN34Nw==
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6be5cc06:5259daf0
2025-04-15 20:16:08
@ 6be5cc06:5259daf0
2025-04-15 20:16:08Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ e1b184d1:ac66229b
2025-04-15 20:09:27
@ e1b184d1:ac66229b
2025-04-15 20:09:27Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
1. A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

2. Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
3. Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
4. Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
5. Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
6. Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
7. Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

8. Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
9. High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
Your opinion
My attempt to write an article with Yakyhonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing and what are these properties?
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 7d33ba57:1b82db35
2025-04-15 19:33:07
@ 7d33ba57:1b82db35
2025-04-15 19:33:07Nestled in the lush Our Valley in northern Luxembourg, Vianden is a charming riverside town known for its stunning medieval castle, cobbled streets, and peaceful atmosphere. Surrounded by forested hills and steeped in history, it’s the perfect day trip—or even a peaceful overnight getaway—from Luxembourg City.
🏰 Top Highlight: Vianden Castle
- One of Europe’s most beautiful feudal castles, perched dramatically on a hilltop
- Built between the 11th and 14th centuries, with Romanesque and Gothic elements
- Lovingly restored, it now features furnished rooms, exhibitions, and epic valley views
- Visit in autumn or winter for a real storybook vibe, or during medieval festivals in summer for a lively twist
🌿 Things to Do in Vianden
1️⃣ Wander the Old Town
- Stroll the cobbled lanes, cross stone bridges, and admire the pastel-colored houses along the river
- Stop at a café by the water and just soak in the Alpine-style charm
2️⃣ Take the Chairlift
- Ride Luxembourg’s only chairlift up the hill above Vianden
- Amazing panoramic views of the town, river, and surrounding forests
- You can hike back down through wooded trails—it’s magical in the fall
3️⃣ Victor Hugo House
- Famous French writer Victor Hugo lived in exile here in the 1870s
- His former home is now a museum with personal items, manuscripts, and 19th-century decor
4️⃣ Hiking & Nature
- Vianden is surrounded by forested trails and river paths, perfect for hiking and biking
- You can follow the Our Valley Trail or parts of the Escapardenne trail toward the Belgian border
🍽️ Local Flavors
- Try hearty Luxembourgish dishes like Judd mat Gaardebounen (smoked pork neck with broad beans)
- Enjoy fresh trout from local rivers, Luxembourgish wine, or a slice of Apfelkuchen with coffee
- The town’s cozy inns and traditional restaurants make dining here feel warm and personal
🚆 Getting There
- From Luxembourg City: About 1.5 hours by public transport (train + bus combo) or 45 minutes by car
- Bonus: Public transport is free in Luxembourg!
-
 @ bf6e4fe1:46d21f26
2025-04-15 19:30:46
@ bf6e4fe1:46d21f26
2025-04-15 19:30:46this is a test
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ a296b972:e5a7a2e8
2025-04-15 19:15:22
@ a296b972:e5a7a2e8
2025-04-15 19:15:22Heute traue ich mich einmal eine steile These aufzustellen, auch auf die Gefahr hin, dass sich herausstellen kann, dass ich völlig daneben liege.
Die USA sind federführend in der Gain-of-Function Forschung. Warum einige Dr. Frankensteins auf die Idee gekommen sind, an Viren, Bakterien und Sporen herumzubasteln, damit sie noch gefährlicher werden, erschließt sich mir nicht.
Wie andere Verrückte zum Beispiel in 2001 auf die Idee kommen konnten, Milzbrandsporen (Anthrax) in Brieflein an US-Abgeordnete zu verschicken, kann meine einfach gestrickte Seele auch nicht nachvollziehen.
So oder so kann man bei solchen Beispielen in Zweifel kommen, ob der Mensch wirklich von Natur aus gut ist.
Unter Präsident Obama, der den Friedensnobelpreis nach Ansicht vieler zu Unrecht erhalten hat, wurde die Gain-of-Function Forschung in den USA verboten.
Bekannt für seine Outsourcing-Künste, zum Beispiel im Austragen von Kriegen außerhalb des eigenen Territoriums, aktuell im Stellvertreterkrieg der USA mit Russland in der Ukraine, wurde nach Möglichkeiten gesucht, die Forschung im Ausland weiter zu betreiben.
So entstand das durch Corona bekannt gewordene Labor in Wuhan und auch einige geheime Labore in der… Ukraine!
In einem leider nicht mehr auffindbaren Video berichtete ein italienischer Professor davon, dass es immer ein Labor gibt, dass an einer Bio-Waffe (wie in Wuhan) arbeitet, und ein Labor, das parallel dazu an dem entsprechenden Gegengift, dem „Impfstoff“ arbeitet. Das Antilabor zum Corona-Virus sollte sich wohl ebenfalls in China an der Grenze zu Russland befinden, allerdings mit der Entwicklung eines Gegengifts noch nicht so weit vorangekommen sein, wie die Hexenküche in Wuhan.
Jetzt kommt „Der Schlund“, „Das Maul“, also Signore Fauci, USA, der größte Bio-Waffen-Verbrecher aller Zeiten ins Spiel. Seit vielen Jahren ist er sowohl für die Bereitstellung von Geldern für die Virenforschung, als auch für die Herstellung eines Impfstoffs zuständig. Er zeigt mit dem Daumen nach oben oder nach unten. Man munkelt, dass er auch Verbindungen zu den US-amerikanischen Geheimdiensten und anderen hat. Naheliegend wäre es.
In ihrer unendlichen „Aufopferung“ für die Menschheit und zu deren Wohl wurden vorsorglich Planspiele gehalten. Die deuten darauf hin, dass man einen Unfall in des Teufels Küche nicht gänzlich ausschließen konnte. Das es auch mehrere Planspiele für den Umgang mit einer „Pandemie“ gab, ist wohl mittlerweile jedem bekannt. Es liegt nahe, dass es sich bei diesen Übungen eigentlich um ein verdecktes Planspiel für den Fall handelte, dass ein gefährlicher gemachtes Virus, das so in der Natur nicht vorkommt, aus einer Giftküche entwischt, wie die Menschen darauf reagieren würden und welche Maßnahmen zu ergreifen wären.
Professor Wiesendanger hat schon ganz zu Anfang der gemachten Welt-Hysterie darauf hingewiesen, dass das Corona-Virus eine Furin-Spaltstelle hat, die so in der Natur gar nicht vorkommt. Damals als Schwurbler denunziert, berichtet der sogenannte Mainstream inzwischen auch davon, dass die Wahrscheinlichkeit, dass das Virus aus einem Labor stammt, fast gegen 100 % geht, und verkauft das als die neueste Erkenntnis, obwohl es schon ein alter Hut ist, wenn man seinerzeit Professor Wiesendanger ernst genommen hätte. Warum man das nicht konnte, klärt sich später noch.
Man kann also davon ausgehen, dass von Anfang an bekannt war, dass das Corona-Virus NICHT von einer Fledermaus auf den Menschen übergesprungen ist (Zoonose), sondern dieses Märchen eher als Ablenkungsmanöver gedacht war.
So ist es gelungen, den Ausbruch eines durch Wahnsinnige geschaffenen Homunculus-Virus, also eine Bio-Waffe, in eine die Menschheit bedrohende Pandemie umzuetikettieren. Und weil man in der Wissenschaft und Politik nicht einschätzen konnte, wie gefährlich dieser von Menschenhand geschaffene Dreck ist, wollte man auf Nummer sicher gehen. Das würde die hysterischen Maßnahmen und die mit der heißen Nadel gestrickten Genbehandlungen erklären. Man wollte sich hinterher nicht vorhalten lassen, das Falsche oder zu wenig unternommen zu haben, falls es zu einem Massensterben kommen würde.
Das wiederum würde auch erklären, warum gleich zu Anfang das Militär mit einbezogen wurde, weil dies sich mit der Abwehr von (Bio-)Waffen am besten auskennt.
Glücklicherweise stellte sich schnell heraus, dass die Giftmischer doch noch nicht so erfolgreich waren, wie man zu Anfang befürchtet hatte, aber da war die Lawine schon ins Rollen gekommen, und es gab kein Zurück mehr.
Zu Anfang könnte man sich sogar vorstellen, dass die Politiker in bester Absicht gehandelt haben und die Menschen in der Tat schützen wollten: „Wir wollen euch „retten, bitte vertraut uns, die Maßnahmen sind nicht zu hinterfragen (aber wir können euch nicht sagen warum, nämlich das eine Bio-Waffe entwischt ist, von der wir nicht wissen, was sie anrichten wird).
Das würde erklären, warum die „Impfkritiker“ so derartig diffamiert wurden und versucht wurde, sie mundtot zu machen. Sie haben gleich schon zu Anfang die von Seiten der Entscheider notwendigen Maßnahmen infrage gestellt, als man sich von offizieller Seite noch nicht sicher war, dass die Gefahr in der Tat geringer ist, als es falsche Propheten mit unlauteren Interessen den Politikern nach dem Mund geredet und ins Ohr geflüstert haben.
Doch dann hat sich die Lage verselbständigt und es wurde der Zeitpunkt verpasst, zurückzurudern. Die Folge war das in deren Augen, dass es immer noch besser war, den Menschen eine experimentelle Genbehandlung, die natürlich nicht so genannt werden konnte, „anzubieten“, als gar nichts. Einen wirklichen Impfstoff gab es ja noch nicht. Der war ja, entgegen der fertigen Biowaffe noch gar nicht entwickelt und erprobt. Es herrschte die große Angst seitens der Entscheidungsträger, dass man hinterher zur Rechenschaft gezogen werden könnte, weil man nicht mehr gemacht hat (als, wie sich dann später herausgestellt hat) nötig war.
Die Hysterie ging dann soweit, dass in vielen Ländern eine Impfpflicht drohte und in einigen Ländern sogar durchgesetzt, aber gottseidank nicht vollends durchgezogen wurde.
Als dann im Laufe der Jahre die Erkenntnisse so weit vorangeschritten waren, dass sich der Terror, die Aushebelung von Grundrechten und die Aushöhlung der Demokratie, die Maßnahmen und absurdesten Freiheitseinschränkungen in der Rückschau absurd wurden, entschied man sich, dass es besser sei weiter zu lügen, statt diesen Riesenfehler einzugestehen, bis heute nicht, weil sonst weltweit Köpfe gerollt wären. Vielleicht fürchtete man Regierungsumstürze und eine weltweite Revolution, die den Planeten ins totale Chaos geführt hätte.
Auch die weltweit orchestrierte Vorgehensweise und der oft gleichlautende Wortlaut in verschiedenen Sprachen zu den Informationen zu Corona spricht für eine im Hintergrund agierende militärische Organisation, wohlmöglich sogar mit Beteiligung der NATO. Und auf Regierungsebene kennt man sich auch untereinander.
Die Regierungen hatten Angst, dass die im Verborgenen tätigen Hexenküchen bekannt werden. Die Gefahr, die von diesen Gift-Laboren ausgeht, durfte unter keinen Umständen ans Tageslicht kommen. Was möglich war, musste unter den Teppich gekehrt, oder verharmlost werden. Nicht ohne Grund fordert Professor Wiesendanger das weltweite Verbot von Gain-of-Function Forschung.
Zu allem Übel kam noch dazu, dass hinter all dem eine Menge Geld steckt und den verborgenen Strippenziehern drohte, sehr viel Geld zu verlieren. Sie schafften es ja sogar, die Haftung für die Gift-Jauche auf den Staat zu übertragen.
So erklärt sich auch, dass bis heute Gerichtsurteile gefällt werden, die bar jeder Vernunft sind.
Bekämen Kläger zu oft Recht, wäre das in vielen Staaten eine Bankrotterklärung. So wird weiter kräftig gelogen, weil man sonst zugeben müsste, welchen Schaden der staatlich verordnete Wahnsinn mithilfe von weltweit agierenden Organisationen, wie die WHO, angerichtet hat.
Vielleicht wäre es gut, wir würden uns von der Vorstellung verabschieden, dass von offizieller Seite eine wirkliche Aufarbeitung erfolgen wird. Es gibt weltweit Ansätze, es kann aber sein, dass diese zu keinen vollumfänglichen Ergebnissen führen werden. In Talkshows werden dieselben Verbrecher eingeladen, die den Schaden verursacht haben. Die einst hochangesehenen Herren Ioannidis, Bhakdi, Wodarg und viele, viele andere, sind nach wie vor im Staatsfernsehen nicht zu sehen.
Dafür gibt es eine umfassende Aufklärung in der sogenannten Blase. Wenn auch nicht von „offizieller“ Seite verkündet, liegen die Beweise dank immenser Arbeit von ungezählten Experten, die nicht an irgendeinem staatlichen Geldhahn hängen und sich der Wahrheit verpflichtet haben, auf dem Tisch.
Diese Tatsachenwahrheiten werden vielleicht erst in der nächsten Generation hergenommen werden, um eine wirklich offizielle Aufarbeitung auf den Weg zu bringen. Schon einmal wurde von einer nachfolgenden Generation gefragt: „Wie war das eigentlich damals? Was habt ihr eigentlich gemacht? Wie habt ihr euch verhalten und warum?“ Und selbst, wenn digitale Beweise vernichtet werden sollten, gibt es immer noch genug Bücher, also analoge Chroniken, der wohl bisher dunkelsten Geschichte der gesamten Menschheit.
Das Ausmaß dieses weltweiten Verbrechens, das anfangs vielleicht noch mit den besten Absichten seinen Lauf nahm und dann in ein Desaster überging, ist so groß, dass es fast das menschliche Erfassungsvermögen übersteigt.
Ich behaupte nicht, dass es genau so gewesen ist, aber es könnte sehr wohl genau so gewesen sein.
Dieser Artikel wurde mit dem Pareto-Client geschrieben.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 5f078e90:b2bacaa3
2025-04-15 18:17:32
@ 5f078e90:b2bacaa3
2025-04-15 18:17:32This is Hostr, a bridge between Nostr and the Hive blockchain. This post is originating on Nostr as a kind 30023, that is, a long form Nostr note. If all goes as hoped. This note will auto-post and appear over on the Hive blockchain. And, ideally on that Hive post, a link will appear that connects back to the original Nostr note.
The goal is to have either: * a bidirectional bridge, either way * a nostr-to-hive bridge only, if desired * a hive-to-nostr bridge only, if desired
-
 @ e0921d61:e0fe7bd5
2025-04-15 16:13:32
@ e0921d61:e0fe7bd5
2025-04-15 16:13:32Hans-Hermann Hoppe explains the capitalist process as driven by time preference, how people value present vs. future goods. Economic growth hinges on savings and investment, and this shapes our prosperity.

Factors like population, natural resources, and technology matter, but Hoppe argues they're secondary. Without prior savings and investment, even the richest resources and best technology remain untapped.

True economic advancement happens through increasing per capita invested capital, raising productivity, real incomes, and further lowering time preferences. This creates a self-reinforcing cycle of prosperity.

Hoppe claims this process naturally continues smoothly until scarcity itself disappears, unless people voluntarily choose leisure over more wealth. This growth has no inherent reason to halt abruptly.

This smooth capitalist cycle, however, is disrupted when government enters the picture. Government control of resources it didn’t earn or acquire legitimately distorts incentives and investment.

Government monopolization of money through fractional reserve banking artificially lowers interest rates.
Entrepreneurs mistakenly think, and are incentivized to think, there's more savings, so more unsustainable investments proliferate.

Without real savings backing these projects, a painful correction (a bust following the boom) inevitably occurs.
Investments must eventually realign with actual savings, thus leading to bankruptcies and unemployment.

Hoppe concludes that boom-bust cycles aren’t natural. They’re directly caused by government-created credit expansion. Unless governments stop manipulating fiat money supply, these cycles remain unavoidable.

-
 @ 9f2b5b64:e811118f
2025-04-15 15:23:25
@ 9f2b5b64:e811118f
2025-04-15 15:23:25Let's test some Articles
Let's star by just blabbing for a while blah blah balh
But this is the most important part, which will eventually be highlighted I hope.
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ 7d33ba57:1b82db35
2025-04-15 14:59:10
@ 7d33ba57:1b82db35
2025-04-15 14:59:10Tucked into a serene bay just 20 km south of Dubrovnik, Cavtat is a relaxed seaside town that mixes historic charm, clear Adriatic waters, pine-covered hills, and a welcoming small-town feel. It’s often seen as a peaceful alternative to Dubrovnik, with cobbled streets, pretty promenades, and hidden beaches**—perfect for those looking to unwind in style.
🌟 What to Do in Cavtat
1️⃣ Stroll the Seaside Promenade
- Palm-lined and picture-perfect, the Riva is the heart of Cavtat
- Lined with cafés, ice cream spots, and yachts bobbing in the harbor
- Great for a morning coffee or a golden hour walk
2️⃣ Explore the Old Town
- Compact and charming, full of red-roofed stone houses and quiet lanes
- Don’t miss the Rector’s Palace and Baroque St. Nicholas Church
3️⃣ Visit the Racic Mausoleum
- Designed by famed Croatian sculptor Ivan Meštrović
- Set on a hill with panoramic sea views and a peaceful atmosphere
4️⃣ Swim & Sunbathe
- Small coves, flat rocky spots, and crystal-clear turquoise waters
- Try Beach Kamen Mali or walk around the Rat Peninsula for secluded spots
- Great for snorkeling and paddleboarding
5️⃣ Take a Boat to Dubrovnik
- Water taxis run frequently—it's a stunning ride along the coast
- Spend the day exploring Dubrovnik’s Old Town, then return to Cavtat’s tranquility
🍽️ What to Eat
- Fresh seafood – grilled fish, calamari, or buzara (shellfish in white wine sauce)
- Peka – slow-cooked meat or octopus under an iron bell
- Local wines like Pošip (white) or Plavac Mali (red)
- Finish with rozata, a Dubrovnik-style custard dessert
🎯 Travel Tips
✅ Cavtat is 15 mins from Dubrovnik Airport, making it a perfect arrival or departure base
✅ Quieter than Dubrovnik—ideal for families, couples, or solo travelers
✅ Best time to visit: late spring to early fall
✅ Rent a bike or walk around the Rat Peninsula for nature and sea views -
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ cb4352cd:a16422d7
2025-04-15 13:25:04
@ cb4352cd:a16422d7
2025-04-15 13:25:04The world of online events has seen unprecedented growth in recent years, with virtual conferences breaking new ground and even setting Guinness World Records. As digital gatherings become more ambitious, some events aim not just to inform and engage but to make history.
Notable Guinness World Records in Online Events
World of Tanks: The Largest Online Game Server Attendance
In 2011, the multiplayer online game World of Tanks set a Guinness World Record for the highest number of players simultaneously online on a single server—91,311 users. This record highlighted the immense popularity and scalability of virtual gaming communities. (ixbt.games)The Largest Cybersecurity Online Conference
In 2020, KnowBe4 organized a cybersecurity conference that gathered more than 30,000 participants. This event set the record for the largest online conference in the field, demonstrating the power of virtual events in bringing together professionals from around the world. This achievement was officially recognized by the Guinness World Records.The Most Attended Virtual Concert
Another major milestone in online events was set by rapper Travis Scott, whose Fortnite virtual concert drew over 12 million concurrent viewers, making it the most attended digital concert ever. This event also earned recognition from the Guinness World Records for its groundbreaking achievement in digital entertainment.Beyond Banking Conference: Aiming for a New World Record
In 2025, Beyond Banking Conference is set to challenge existing records by organizing what could become the largest online gathering in the blockchain and AI space. With an ambitious goal of attracting over 100,000 participants, the event will bring together industry leaders, innovators, and enthusiasts to discuss the future of blockchain, artificial intelligence, and decentralized finance (DeFi).
By leveraging cutting-edge technology and strategic partnerships, Wenix aims to redefine what’s possible for online conferences. If successful, this event will not only break records but also set a new standard for global digital summits.
This isn’t just another virtual conference—it’s a revolution in the making.
-
 @ d3d74124:a4eb7b1d
2025-04-15 12:58:08
@ d3d74124:a4eb7b1d
2025-04-15 12:58:08ORIGINALLY ON XITTER BY STEVE BARBOUR. SHARED HERE FOR THE HOMIES (https://x.com/SGBarbour/status/1911614638623801425)
I find bureaucracy fascinating—it’s like a cancer within human organizations.
Why do organizations become bloated with excessive procedural controls, inefficiency, and indecisiveness as they grow in size and age? Why does decision-by-committee often replace the ambitious, self-starting decision maker? Why do small, "lean and mean" startups inevitably become bloated with bureaucracy as they scale and increase their headcount?
In 2014, these questions consumed me while I sat in a cubicle at an oil and gas company. Why, after years of honing my skills to fix artificial lift systems, was my signing authority decreasing (from $25,000 to $10,000 for workover budgets), despite record corporate profits? Why did I now need a 12-page Microsoft Word document with manager sign-off to schedule and scope a service rig for a simple pump change, when a five-minute email direct to the rig supervisor had previously sufficed?
Years into the job I was far more capable than when I had started, yet I had less authority with each passing day. I became determined to understand what was causes bureaucracy and whether or not it can be prevented.
After researching for some time, such as the essay I posted below, I concluded that bureaucracy stems from a lack of trust and accountability. Bureaucrats impose procedures instead of trusting subordinates to do their jobs, often in response to a costly mistake. This results in new processes that everyone must follow.
Bureaucrats rarely take responsibility for their own failures or hold others accountable for theirs. Instead, they create more procedures and invent new processes. Bureaucracy is a systemic issue, pervasive in nearly every large business or institution. The larger the organization, the more stifling it becomes.
This behavior is costly, increasing administrative overhead and delaying capital execution. Who is bearing this enormous cost?
You are, of course!
Fiat money funds the vast majority of the world's bureaucracy. Fiat money is counterfeit created out of thin air and is used to fund deficit spending by governments worldwide. Governments use paper money they did not earn from taxes to bail out institutions who are overleveraged and get caught with their pants down (e.g. Bombardier and Air Canada are famous repeat offenders in Canada, in the US you can choose any big name bank just about).
They keep printing money and nobody is held accountable anywhere.
Misallocate capital, become insolvent, print money and bail out, create new regulations / procedures, repeat.
You pay for bureaucracy by losing your savings to inflation.
You pay for bureaucracy when the local small businesses in your neighborhood is replaced by a global franchise funded by cheap, perpetual fiat money.
You pay for bureaucracy when you cannot retire as early as you planned and end up working yourself straight into a retirement home.
I was cleaning and organizing my office today and found this old essay by Brian D. Rule from 1977 on the topic, which sparked me to write this short X piece on bureaucracy.
Brian's essay 'Bureaucracy' was actually the very essay that led me into believing fiat money with the root cause of global bureaucracy and waste, which lead me to become interested in gold in 2015 and then in bitcoin in 2016.
Sure enough I googled the prevalence of the term 'bureaucracy' and something interesting happened after 1971...
Isn't it weird how so much went to shit after we got off the gold standard?
Today I am convinced that hard, sound money is the only solution to bureaucracy. This is why I work for #bitcoin.
*Sadly I can no longer find the essay online, so I ripped the text from my paper printout that I found in my files with the now defunct reference website below. *
Bureaucracy
Brian D. Rude, 1977
Original website (now defunct): http://brianrude.com/burea.htm
In the summer of 1975 I took a teaching job in Nebraska. As my previous teaching experience was in Missouri I had to see about getting a Nebraska teaching certificate. I applied for a "Nebraska Standard" teaching certificate. I sent in my college transcript, the application form, and a check for eight dollars. They sent me back, in their own good time, a "Nebraska Prestandard" certificate. I decided there was nothing "prestandard" about me or my teaching, so I wrote back and asked why I didn't get the "standard" certificate. They replied that since I had not taught three out of the last five years I was eligible only for the "prestandard" certificate.
"What do those pigheaded bureaucrats know about my teaching?" I thought to myself. "How would they ever know the standard of my teaching just from shuffling papers around?"
With a little reflection I realized that of course they know nothing about my teaching. They are not supposed to know anything about my teaching. They are paid to evaluate the papers I send them. They are not paid to evaluate my teaching. They have a clear mandate to shuffle my papers, and nothing more.
I presume my application was opened by a secretary, who, following a tightly structured routine, checked off each requirement, typed up my certificate, got it signed by some authority and sent it off to me. Such a secretary is most likely a conscientious worker, a wife and mother, a Republican or Democrat, an occasional churchgoer, a bit of a gossip, and a lot of other plain ordinary things. But she is most likely not a "pigheaded bureaucrat". She would not think of herself as a bureaucrat, and neither would her boss, her coworkers, her family, or anyone else who personally knew her. When she typed "prestandard" instead of "standard" on my teaching certificate she is simply doing her job. Were she to do anything less or more she would be negligent.
So where is the bureaucracy? Or was I dealing with a bureaucracy? If not, then where is there a bureaucracy? Where do we find the genuine article, the bungling, myopic, pigheaded bureaucrat?
I think pigheaded bureaucrats do exist, but they are rare. It's the good bureaucrat that drives us batty, quite as much as the bungling bureaucrat. The good bureaucrat knows exactly what he is obligated to do and he does it conscientiously. The good bureaucrat simply applies the rules that he is responsible for applying, but that he did not make.
A bureaucracy is a group of people responsible for applying a set of rules. The police, courts, executive branches of government, parents, teachers, librarians, and many other people or groups of people are also responsible for applying rules, yet we don't think of these as being bureaucracies. The distinguishing features of a bureaucracy are the types of rules to be applied, and, to some extent, how the rules are applied.
A bureaucracy is responsible for applying what I will call "secondary", or "derived" rules. A secondary rule is a requirement or prohibition established only because it promotes a primary goal. When Moses came down from the mountain with his stone tablets he was carrying what might be considered the simplest statement of what I will call "primary" requirements. The rule, "Thou shalt not steal", for example, is a primary requirement because it is desirable for its own sake, not just as a means to some other end. Similarly, "Thou shalt not commit murder" is a primary requirement because it is desirable as an end in itself.
Safe driving, as a modern example, is a primary requirement because it is desirable for its own sake. The requirement that one get a driver's license before driving, in contrast, is a secondary requirement. It is a requirement instituted by state governments in an attempt to promote the primary goal of safe driving. It is secondary to, or derived from, the primary requirement of driving safely. If people always drove safely, or if driving by its nature presented no hazards, then there would be no need for driver's licenses. Or if legislatures decided that licensing did nothing to promote safe driving then there would be no need for driver's licenses. Licensing is not an end in itself.
Tertiary, or third order, requirements can also exist. If a state requires a birth certificate as proof of age before issuing a driver's license then the state is imposing a third order requirement. Showing a birth certificate is a requirement designed to promote the licensing of drivers, which in turn is designed to promote safe driving.
I imagine one could go ahead and find examples of fourth order requirements established to promote third order requirements. However I don't think there is much point in getting too deep in this kind of analysis. The main point is the distinction of whether a goal is important for its own sake or whether it is important in promoting some other goal. Thus I may speak of a "derived" requirement, meaning only that it is not a primary requirement, but not specifying whether it is secondary, tertiary, or even further removed from the primary goal.
In different contexts I may speak of primary or secondary "requirements", "rules", "prohibitions", "laws", "regulations", "goals", "wrongs", "burdens", "privileges", and so on. It seems natural to think of paying taxes as a "requirement", while murder is a "wrong" that is covered by a "prohibition". But the requirement of paying a tax can be interpreted as the prohibition of avoiding the tax, and the prohibition against murder can be interpreted as the requirement to refrain from murder. The important point here is the distinction between primary and derived, not between omission and commission.
In the example I gave about getting a teaching certificate the bureaucrats were concerned only with my compliance with secondary requirements. They were not at all concerned with the primary requirement - the requirement that I indeed be a good teacher. This is a distinguishing characteristic of bureaucracies. They are concerned only with applying derived, not primary, rules. Other agencies are brought in when there is a primary rule to be applied. The police and courts handle such primary wrongs as theft and murder. Parents and teachers handle such primary wrongs as tracking mud on the carpet or being late to school. Churches handle such primary wrongs as "living in sin" or blasphemy. But it doesn't take a judge or a preacher to decide if my application for a teaching certificate is in order, or my application for a driver's license, or a dog license, or a business license, or a barber's license, or a building permit, or a marriage license, or breathing license. It takes a bureaucrat to handle these matters.
The basic root of bureaucracy then, is the proliferation of secondary requirements. It is not enough, in our modern world, to just be a good and honest person. One can be the best and safest of drivers, but a driver's license is still required. One can be a patriot and a saint, but the IRS still wants that W-2 form. One can be the best doctor in the world, but to practice medicine without a degree and a license is still a serious offense. We have established literally millions of secondary requirements designed to promote a few primary goals. To administer these rules we have people we call bureaucrats.
If the basic root of bureaucracy is a proliferation of derived requirements, then it would seem reasonable that the way to decrease bureaucracy would be to decrease such requirements. This is true, and in fact is a main thesis of this article. Unfortunately it is not always easy to do. Every bureaucratic requirement, in a healthy society at least, was established by reasonably intelligent people giving at least half-way serious consideration to a genuine problem. Therefore any particular bureaucratic requirement or procedure that is challenged will be defended by some person or group.
The most important gain we hope to realize from derived requirements is security. The requirement of any permit or license is usually, if not invariably, justified in order to "protect the public". We want safe driving so we demand driver's licenses. We want our neighbor's dog out of our flower bed so we demand dog licenses. We want merchants to be honest so we demand business licenses. We want welfare recipients not to cheat so we require verification of identity, employment, and who knows what else. All these requirements are seen as necessary to prevent something bad from happening, or to assure that something good will happen.
Derived requirements cannot provide all types of security. We can't prevent floods and famines by making rules and printing forms. The type of security that is the goal of bureaucratic requirements is social control of one form or another.
Simple fairness is often the goal of bureaucratic requirements. The Internal Revenue Service is a good example of this. The primary goal of the IRS is to raise money. This could be done by charging every citizen a flat rate of $1000 or so each year. We wouldn't consider this fair, though, because we realize not everyone has an equal ability to pay. Therefore we have an elaborate set of rules designed to extract more from those who have more. To apply these rules we have what is probably the biggest and most complex bureaucracy since time began. This size and complexity comes from our desire to be fair, not from the simple desire to collect money.
Another form of social control for which bureaucratic requirements are established is prevention of abuse of power. Power comes in many different forms, and we know from long experience that power is always susceptible to abuse. One method of dealing with abuse of power is to call it a primary wrong and punish the offenders. This is done, and it keeps the police and courts very busy. Another way to control abuse of power is to set up secondary requirements to try to prevent such wrongs from occurring in the first place. This produces bureaucracies. In the 1880's, for example, railroads were playing a little rougher than people wanted. They gained power by monopolizing a vital service. In response to this the Interstate Commerce Commission was set up, and has regulated business ever since. A more modern, and more specific, example would be the requirement that a used car dealer certify that the odometer reading is correct when he sells a car. This requirement is in response to what is seen as abuse of power by car dealers who misrepresent their merchandise.
In addition to the main cause of bureaucracy - the proliferation of derived requirements for purposes of security - there are several other causes of bureaucracies that are worth mentioning. The first of these is pure blind imitation. Again I will use driver's licensing as an example.
In the fifty states there is a startling uniformity of driver's license requirements. The most obvious uniformity is that all states require licenses. I have never been able to understand this. It would seem that if each state followed its own experience, values, customs, and judgment, then there would be a whole spectrum of licensing requirements, ranging from no requirement at all to extensive and strict requirements. This is apparently not the case. The majority of states require a written, driving, and eye test. They require a license fee. They require renewal of the license every so many years. They require that the license be in the person’s possession while he is driving. So far as I can tell only minor variations are found on this basic pattern in the different states.
I attribute this uniformity mainly to imitation. If there were an obvious connection between traffic safety and driver’s licensing then this uniformity would seem more sensible. If the National Safety Council told us everyday that the majority of fatal accidents involved an unlicensed driver, then we would not be surprised to find a driver’s license requirement in every state. But that is not the case. The National Safety Council talks a lot about the drinking driver but not about the unlicensed driver. If there was a historical example of some state that was too stubborn to require licenses and had an atrocious accident rate, then again a strict licensing system would be expected in every state. But is not the case either. The connection between licensing and safe driving is tenuous at best. There are innumerable unsafe drivers in every state who have no trouble getting a license. There are also perfectly safe drivers who have trouble getting a license. I think it is safe to say that the average driver, safe or unsafe, can’t pass the written test without studying the book no matter how long he has been driving. Many people find this out when they try to renew their license. All this leads me to believe that licensing requirements are set up by imitation more than anything else. A few states started requiring licenses and other states blindly followed, thinking in some vague way that they were being modern and progressive.
Pure blind imitation may seem a poor reason to set up a bureaucratic requirement and a bureaucracy to apply it, but there are many examples of such imitation in everyday life. In a previous article, ("Roting and Roters", not yet on my web site) I described and developed the idea that blind imitation is a powerful determinant of individual behavior. I think it is almost as powerful a determinant of group action. If each state followed its own inclination in the matter of driver’s licensing I would expect a much wider variation among the different states.
Another cause of bureaucracies is a little more substantial than blind imitation, and accounts for many licensing systems. That is the desire for group recognition. People are by nature social animals. They want to have groups and they want to do things in groups. They want their groups to be recognized and they want this recognition to be official and formal. I began to realize this a few years back when I read in the paper that beauticians were trying to get legislation passed setting up a system of beautician licensure. I thought they were nuts. Why, when we all hate the bureaucracy so much, would anyone want to set up more bureaucracy?
Another example of this kind of bureaucracy building is in the field of occupational therapy. Nurses, physical therapists, and speech therapists are licensed by the state. Occupational therapists, in contrast, have a national association which gives a "registry examination". Upon passing this test, and having a degree in occupational therapy, one becomes an "O.T.R.", a registered occupational therapist. Hospitals and other institutions take this designation as evidence of full qualification in the field. With such a sensible system I find incomprehensible that the profession is pushing for a system of state, rather than national, licensure. But that is exactly what they are doing. They are trying to build more bureaucracy, and they will succeed.
It took me quite a number of years to realize that teacher certification is something that the teaching profession wants, rather than being a requirement imposed from above. However that is apparently the case. The system of licensure, though a pain, does give some recognition to the status of teachers. This, along with a considerable amount of blind imitation, apparently accounts for the uniformity of teacher certification requirements found in different states.
It would be nice if we could give official recognition to groups without the necessity of laying down a mass of secondary requirements, but that is not how it works. Recognition, apparently would have little meaning if it did not indicate that the members of the group meet a system of requirements. It would also be nice if those who gain this official recognition were always worthy of it, but that also is unfortunately not the case. There will always be drivers, teachers, beauticians, occupational therapists, doctors, lawyers, and others who somehow manage to gain the official license but are recognized by their peers as incompetent. Whenever a system of secondary requirements is established there inevitably enters a "reality gap", a gap between the ideal and the real. This can make the whole system ineffective. I will have more to say about this ineffectiveness and its effects shortly.
Yet another factor leading to the spread of bureaucracy is a systematic error made, to a greater or lesser extent, by practitioners of almost any field. That error is thinking that the world’s problems will be solved by one’s own field of knowledge or mode of operation. I think a good name for this would be "role egocentrism". Egocentrism means that a person considers himself the center of the universe, just as ethnocentrism means that a group considers itself the center of the universe. Role egocentrism simply means that one’s own role is given undue importance and status. Thus doctors think that medicine will be the salvation of the world. When medicine has progressed far enough, they think, the world will be such a fine place that other problems will just disappear. Preachers think that if only we would all turn to God there would be no more problems. Farmers think that once the world food problem is solved, by farmers of course, then all will be well. Teachers think that education will be the one thing to save mankind from itself. Scientists think that research will usher in a new golden age.
It is hard to conceive of a bureaucrat having such grandiose visions of salvation. But remember that bureaucrats do not think of themselves as bureaucrats. Even more importantly, bureaucrats don’t make the rules, they only apply them. The rules are made by governments. Governments consist of politicians, and politicians are very susceptible to role egocentrism. To attain office a politician must convince people that government is capable of doing things, and he must believe it himself. Since people want things done it is not surprising that governments are populated by large numbers of people with an inflated idea of what can be done by writing rules and laws. Since there are few primary laws left to write, we have an ever-increasing proliferation of secondary requirements. Bureaucrats may not make the basic rules that they apply, but they do have some latitude to make minor rules, and even more importantly, they are responsible for making reports and can require reports from their subordinates. In the making of reports a little role egocentrism can go a long way. The result can be a massive flow of reams and reams of paperwork, with copies sent to all other bureaucrats who might have come slight connection to the job at hand, but with very little of the reports actually being read.
Bureaucrats also have some latitude in working as individuals or teams, and again a great deal of waste can ensue. The justification for working in committees or teams is the idea that by joining forces the best abilities of each member can be brought to bear on the problem at hand and therefore a solution to the problem is more likely. Of course there is some truth to this, but it doesn’t always work out too well. The little bit truth can become greatly augmented by role egocentrism. Team workers like to think that if you set six experts around a table something good is bound to come out of it. Non-team workers, like myself, tend to think that setting six experts around a table is a good way for six experts to waste each other’s time. I think bureaucrats at the higher levels are more prone to waste their energy this way, and I interpret this as a form of role egocentrism.
All of these cases of bureaucracy are augmented by another systematic error. That error is the systematic overestimation of group cohesiveness. In the minds of bureaucracy builders the bureaucracies already in existence become "they", and "they" are a bunch of pigheaded fools. "We", on the other hand, are good, right-thinking people and the bureaucracy we set up will serve the people, not the bureaucrats. And just to make sure we’ll write in plenty of safeguards. Of course this doesn’t work. Just because it is "our" program doesn’t mean that it won’t be subject to all the problems that beset any program. A new generation will grow up and decide that "we" are "they" and the cycle begins over again.
So far I have painted a rather pessimistic picture. We have bureaucrats because we have a multitude of derived requirements to administer, and we have a multitude of derived requirements because we think they bring us security. We also have bureaucracies because of imitation, because of the desire for group recognition, and because of role egocentrism. Yet the sum total of all this drives us batty. The next step is to try to get some idea of why and how bureaucracy is frustrating. I think the frustration results from main causes, standardization and ineffectiveness.
Standardization is a wonderful thing in industry. If my car needs a new fuel pump I can buy one right off the shelf and know it will fit. Fuel pumps are standard, and engines are standard. They fit together beautifully. The few defective fuel pumps that are not standard are quickly caught and tossed off the assembly line. This happy state of affairs does not extend to non-physical objects though. Consider, for example, a seed planter. I don’t know just how a planter might work but I visualize a mechanical hand grabbing one seed at a time and popping it into the ground. Seeds are pretty well standardized and most seeds can be picked up by these mechanical hands without injury. A few seeds, however, are nonstandard. They are either too big, or too small, or perhaps the wrong shape. The iron hands that so effectively plant most seeds will bruise, shred, mangle or maybe just overlook the oddball seeds. This doesn’t worry us though. Just like the defective fuel pumps that are bumped off the assembly line, the few mishandled seeds are of no great consequence.
When standardization is extended to humans the situation changes dramatically. We can’t bump off the defectives so carelessly. A bureaucracy can be compared to the seed planter. Iron hands pick you up and set you down again. If you fit the standard mold, these iron hands hold you gently. If you don’t fit the standard mold those same iron hands can shred you to pieces.
For example, a few years back I knew a fellow who was paraplegic. He was completely confined to his wheelchair, but he had a car with adapted controls and could drive as well as anyone. Unfortunately he had considerable difficulty licensing both himself and his car. He could drive to the courthouse, and get himself out of his car and into his wheelchair, but he had no way of getting down in the basement where the licensing offices were. There were elevators from the first floor to the basement of course, but between the parking lot and the first floor were innumerable steps and curbs. To a person in a wheelchair a single four-inch curb might as well be a ten-foot wall. Apparently my friend managed somehow to keep himself legal most of the time, but he did at times speak bitterly about the troubles he encountered. The state required licenses, and the state provided a way to get these licenses, but only if you fit the standard mold. My friend did not fit the standard mold, and felt very much caught in those iron hands.
Fortunately most examples of the problems of standardization are not so serious. My wife had a friend in college who was triply enrolled in the School of Education, the School of Medicine, and the Graduate School. All occupational therapy students were dually enrolled in Education and Medicine, which caused no end of red tape in itself, but this particular girl was such a go-getter that she added Graduate School. This made her a non-standard person indeed. One day she spent a solid half hour on the phone trying to convince some bureaucrat that, no matter that it didn’t fit the computer, it was possible to be enrolled that way. I presume the problem, whatever it was, was eventually worked out, but not without some cost in frustration. The bureaucrat in question was probably no more pigheaded than you or I. The rules he was responsible for applying simply made no provision for triply enrolled students.
When caught as a non-standard person in a standardized bureaucracy one wonders why standardization is established in the first place. Except for the role egocentrism of a few bureaucrats, standardization is not intentional. It arises by the same forces that promote standardization in industry. Standardization promotes efficiency. Whenever a form is printed, for instance, it is designed to fit the majority of situations. Thus a fire insurance application form may ask if the house is frame or brick, with no intention of frustrating the owners of igloos, caves, and houseboats. It simply reflects the fact that most houses are either frame or brick. By stating these two choices the processing of the application is speeded up. If instead the application stated simply, "describe the dwelling to be insured", the work in processing the application would be considerably increased. Standardization is the inevitable correlate of the proliferation of secondary requirements.
There is also another cause of standardization, the lack of discretionary authority. Remember that secondary requirements are set up in many cases to prevent abuse of power and to be fair. This usually means that the bureaucrats who apply these rules have only a limited number of responses to a given situation. Bureaucracies are given very little discretionary authority. They must follow the rules whether the rules fit the situation at hand or not. To illustrate this let me hypothesize two ways of administering welfare.
In case A an applicant comes to a social worker. The applicant explains that her husband just lost his job because he drank too much, that she works as a maid two days a week but that her children have no one to stay with them when she works unless she pays a baby sitter which costs almost half her salary, that their car is about to be repossessed and then she won’t be able to get to work at all, that the landlord won’t fix the plumbing and charges too much rent, that they would move except they haven’t found a place that’s any cheaper, that their oldest son was just sent to jail for a two year term, and on, and on, and on. The social worker listens to all this, makes a few phone calls, and the next day tells the applicant, "We’ll give you $70 a week allowance, but tell your husband to come in before next week. We’ll get him off his beer and on the job one way or the other. I called your landlord and got his side of the story and there’ll have to be a few changes made before he’ll reconnect the shower, and you’ve got to..."
In situation B the applicant comes to the social worker with the same story. The social worker says, "I think we can help you, but first you’ll have to find your birth certificate. Regulations state that only citizens are eligible for welfare. Then you’ll have to take this form to your employer to certify your wage scale. And this form goes to your landlord to verify your rent. And you’ll have to fill out this form to show how you budget your income, and this form to verify that you are not now receiving veterans or disability compensation, and this form that verifies you are not eligible to collect child support from any previous husband, unless the marriage was annulled, in which case you have to hunt up the certificate of annulment... What? You lost your certificate of annulment? You’re not sure you ever were married to John before you left him for Henry? ..."
In situation A the social worker is given a budget and a wide latitude on how to distribute the money. She is given discretionary power to a large degree. In situation B the social worker is given a very small amount of discretionary power. She can’t decide for herself whether the applicant is genuinely needy, but must prepare a "work-up", consisting of documentation of all relevant aspects of the applicant’s situation. On the basis of this work-up she is allowed to authorize an allowance, the amount to be taken from a table. If the social worker feels that there are relevant circumstances that are not covered at all in the standard work-up then she may begin some special procedure to have the case considered by a higher authority or committee. But the common suspicion that things aren’t quite as they should be, either because the applicant is undeserving or that he needs more than he can get or that the program misses its mark in yet some other way, is just a routine part of the job.
Standardization, fitting everyone into the same size slot, reduces everything to paperwork. The "work-up" is a stack of documents. These documents, certificates, forms, statements, memos, become the currency of bureaucracy, the medium of exchange. "Facts" become so only when they are certified by someone’s signature, even though they may be obvious. Other "facts" must be accepted because of their official certification even though common sense or simple observation show them to be false. A gap between the real and the official inevitably sets in. Then this gap leads to actions that are perceived to be detrimental or unfair, then the result is a considerable amount of frustration, in spite of the fact that the intent of all the red tape was to be beneficial and fair.
This leads to the second cause of bureaucratic frustration, which is ineffectiveness. If a bureaucratic requirement is seen as effective in accomplishing its goal we accept it even if there is considerable inconvenience involved in meeting the requirement. If, on the other hand, a bureaucratic requirement is seen as ineffective then a little inconvenience in meeting the requirement can be a very significant frustration. Getting a loan from a bank, for example, involves considerable effort in meeting bureaucratic requirements. However we don’t expect money to be handed out without some security that it will be paid back. Therefore we don’t get too frustrated by the inconvenience in meeting those requirements. Similarly, driver’s licenses are seen as worthwhile, even if not fully effective, and entail only a little bother every four years or so. Therefore we do not hear too much about pigheaded bureaucrats at the driver’s license bureau. Unfortunately other licensing systems have imperfections so massive and ubiquitous, and benefits so doubtful, that the whole system is a burden to society. A little inconvenience in getting such a license can be very frustrating. This is the frustration I felt in the example I gave at the beginning of this article about getting a teaching certificate. Another example would be going back three times to the fire station to get a bicycle license. I went back twice. I figured three times was above and beyond the call of duty. I never did get my bicycle licensed.
In psychological phenomena the whole is not always equal to the sum of its parts. Bureaucratic frustration can work this way. One frustration may be brushed off, and then another, and perhaps several more, but eventually there comes a point where the frustrations increase out of proportion to their cumulative value. Short-term frustration changes into long-term demoralization. I think "hassle" is a good name for this. It is a commonly used term, though it is not normally considered a specifically defined term. I think the phenomenon should be taken seriously though. It will become increasingly common with constant increases in bureaucratic requirements.
The best example I can give of hassle in my own experience comes from my home state of Missouri. To get one’s car licensed in Missouri one must show the title or previous year’s registration certificate, as can be expected, but that is not all there is to it. One must also get a new safety inspection certificate and also show his personal property tax receipt. When I lived in Missouri I usually didn’t have any property to be taxed, but I still had to go to the Treasurer’s office in the courthouse to get a card stating that no taxes were due. The safety inspection always caused me worry, and the car licensing itself always had the potential for problems. Maybe they would find something wrong with my title and tell me I can’t register the car. Thus the sum of all this was to me a hassle. The requirements exceeded my tolerance. It caused me anxiety, much more than the sum of the anxieties of each requirement had they come independently. Fortunately other states I have lived in didn’t tie those things together, and for that reason I hope I don’t end up living in Missouri again.
People vary in their susceptibility to hassle. I expect I have about as low a tolerance as anyone. I haven’t heard other Missourians complaining about the car licensing system. Unfortunately those who are not susceptible to the demoralization of hassles have little understanding of the anxieties of those who are susceptible. This goes along with the general rule that the more aggressive cannot empathize with the less aggressive. This increases the problem to those who are susceptible to hassle. However I would expect the future will see the problem given much more recognition as more and more people find themselves pushed beyond their tolerance.
A movement is currently under way by the Democratic Party to do away with traditional voter registration practices and to substitute a "same day" standardized registration system. Thus a voter could show up on election day, show proof of identity and residence, and be registered on the spot. The rationale of this is that the complications of regular registration are sufficient to prevent many people from voting. I think the move is clearly motivated by the political goal of increasing the Democratic vote. Still, I am glad to see the movement. They are talking about hassle. They are acknowledging that bureaucratic requirements are a burden, and that this burden can at times be of a serious nature. Now when somebody tells me I’m nuts if I worry about getting a car license I can reply that apparently some people worry about voter registration.
In the first part of this article I tried to explain the causes of bureaucratic requirements. Then I tried to analyze how bureaucracy produces frustration. There are very good reasons for bureaucracies, and there are very good reasons for frustration, so it appears we must live with the problem forever. I don’t think the world will grind to a halt though. The way out of this dilemma is simply to realize when diminishing returns begin to set in, and even more importantly, to realize when the return does not equal the investment. Every human endeavor has a cost and a benefit, an investment and a return. When establishing a system of secondary rules the investment includes the cost of setting up the bureaucracy, the cost of the individual’s efforts in dealing with the bureaucracy, and increasingly more importantly, the cost in frustration, anxiety, and demoralization. These costs must be subtracted from the benefits before deciding that a given proposal is or is not worthwhile.
Sometimes the cost can be reduced to dollars and cents. According to an item in the newsletter from my representative in Congress the town of Faith, South Dakota, recently applied for a federal grant. I believe they wanted to build a rodeo grandstand. They were offered $150,000 to match their own $50,000, but of course there were strings attached. After looking closely at these strings they finally rejected the federal help entirely and built their own grandstand for only $20,000. I doubt that this example is typical of federal grants, but it does illustrate diminishing returns.
More commonly only part of the cost can be reduced to dollars and cents. For example, an accountant may compute that a $20,000 grant for a town would entail only about $6000 in labor to do all the paperwork. This would seem to make a clear profit for the town of $14,000. But if the city officials are sick of the paperwork and the delays, if the citizens are mad at everyone and each other, and if the strings will be attached forever, then all this must certainly be subtracted from the benefit.
The investment/return assessment is even more complicated when all important factors are psychological. How can we put a price on invasion of privacy? How can we put a price on independence and respect for the individual? How are these costs to be subtracted from the safety and security that we gain from bureaucratic requirements? I don’t know. Since psychological costs cannot be measured in dollars and cents, the worth of any system of bureaucratic requirements will always be a matter of subjective judgment, a matter of politics to be decided through political processes. They are not matters to be decided by technicians or engineers of any sort.
I have my own opinions. I vote for nuclear energy and against OSHA. I tend to think of the licensing of voters and guns worthwhile, of cars and drivers as borderline, and of teachers, barbers, cats and bicycles as not worthwhile. Of course everyone else will disagree. I only hope we will start counting costs and benefits a little more carefully. As is true of so many things, it cannot be said of bureaucracy that if some is good, more is better.
























