-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 83279ad2:bd49240d
2025-04-20 08:39:12
@ 83279ad2:bd49240d
2025-04-20 08:39:12Hello
-
 @ c3f12a9a:06c21301
2025-04-19 10:09:45
@ c3f12a9a:06c21301
2025-04-19 10:09:45Satoshi’s Time-Traveling for Knowledge #4: Liberland 2024 – Freedom Under Siege
What is Liberland?
While digging through old decentralized forums archived on the Interchain, Satoshi came across a curious name: Liberland.
“A sovereign libertarian micronation on the Danube? Founded in 2015 via Terra nullius? Built on the principles of freedom, voluntaryism, and Bitcoin? And I’ve never heard of it?”
Intrigued, Satoshi began to research. The story was almost too good to be true. A 7-square-kilometer patch of unclaimed land between Croatia and Serbia, turned into a symbol of decentralized governance and individual liberty.
No taxes unless voluntary. Bitcoin as the national currency. A digital nation-state with thousands of registered e-citizens, and even its own constitution. And yet—no recognition, no borders, and no peace.His curiosity turned into determination. He calibrated the temporal coordinates on his chrono-node to the Danube River in 2024, a year rumored to be turbulent for the Free Republic of Liberland.
When he arrived, reality struck harder than the legend.
Freedom Under Siege
The nation was under siege.
The scent of burnt wood and trampled earth lingered in the air as Satoshi stepped into what remained of the Liberland settlement. Broken structures, crushed solar panels, and a few scattered personal belongings were all that testified to the once-vibrant hub of liberty pioneers.
He found a group of residents—mud-streaked, exhausted, but defiant—gathered around the remnants of a communal kitchen. One of them, wearing a weathered Liberland t-shirt and a crypto-wallet hardware device on a chain around his neck, greeted him:
"You're not with them, are you?"
Satoshi shook his head.
"Just... passing through. What happened here?"
The man’s voice trembled between rage and sorrow:
"On the International Day of Peace, no less. Croatian police raided us. Bulldozers came with them. Took everything—generators, comms gear, even our medical tents. Claimed it was 'illegal occupation of Croatian forestry land.' But no court, no hearing. Just force."
Satoshi listened, taking mental snapshots of their faces, their words, their pain. He thought about the dream—of a place built voluntarily, where people governed themselves, free from coercion.
But that dream was burning at the edges, like the collapsed tents scattered behind them.
Reflections Under the Stars
As night fell over the Danube, Satoshi sat alone, watching the stars reflect on the black water. Thoughts spiraled:
"Decentralization... is beautiful. But without protection, it's fragile."
He realized that so long as central authorities hold monopoly on violence and taxation, every independent effort to decentralize the world—from Bitcoin to Liberland—is at risk of being suppressed, ignored, or destroyed. Not because it’s wrong, but because it's inconvenient to power.
"Unless a major state like the USA decentralizes itself from within," he thought, "true decentralization will remain a resistance—never the standard."
He activated his chrono-node once more. Not in defeat, but with purpose.
The next destination? Unknown. But the mission was clearer than ever.
originally posted at https://stacker.news/items/947954
-
 @ 7d33ba57:1b82db35
2025-04-21 20:16:41
@ 7d33ba57:1b82db35
2025-04-21 20:16:41Helsinki, the stylish and compact capital of Finland, sits right on the edge of the Baltic Sea, blending Scandinavian design, sustainable living, and a love for nature. It’s a city of clean lines, calm energy, and a creative spirit—where you can go from a seaside sauna to a sleek design museum in minutes.
🧭 Top Things to Do in Helsinki
⛪ Helsinki Cathedral
- The city’s iconic white-domed landmark, perched on Senate Square
- Climb the steps for sweeping views over the city’s neoclassical heart
🏝️ Suomenlinna Sea Fortress
- A UNESCO World Heritage Site spread across several islands
- Explore old ramparts, tunnels, museums, and scenic picnic spots
- A short ferry ride from the city center, perfect for a half-day trip
🧊 Löyly Sauna
- One of Helsinki’s most famous public saunas, right on the waterfront
- Relax in the heat, then dip in the Baltic like a local
- Beautiful architecture and a must-do cultural experience
🏛️ Design District & Museums
- Wander the Design District for boutique shops, galleries, and Finnish fashion
- Visit the Design Museum, Kiasma (contemporary art), and Ateneum (classic Finnish art)
🌲 Nature + Nordic Calm
- Walk along the Esplanadi park or relax in Kaivopuisto by the sea
- Take a boat to the nearby archipelago islands for hiking, birdwatching, or quiet cafés
- Even in winter, the city feels clean, serene, and cozy
☕ Food, Coffee & Nordic Flavors
- Try karjalanpiirakka (Karelian pies), salmon soup, or reindeer meat if you’re adventurous
- Helsinki has a big coffee culture—Finns drink more coffee per capita than anyone!
- Cozy up in a café with a cinnamon pulla and watch the snow fall (or the summer sun glow at midnight)
🚲 Getting Around
- Easy to explore by foot, tram, or city bikes
- Excellent ferries and boats to nearby islands and Tallinn, Estonia
- Helsinki Airport is well-connected and just 30 mins from downtown
📅 When to Go
- Summer: Endless daylight, festivals, and outdoor dining
- Winter: Snowy streets, cozy interiors, and a shot at the Northern Lights if you head north
- Autumn: Ruska (fall colors) is stunning in the parks and forests
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 3ad01248:962d8a07
2025-04-21 19:40:22
@ 3ad01248:962d8a07
2025-04-21 19:40:22It has almost been a month since the Bitcoin friendly Trump administration has been in power. The Bitcoin price was riding high days before and after the election with Bitcoin reaching a new all time high of 109k. It sure seem like surely once Trump got into office the price would skyrocket and everyone finally would have lambos and girlfriends.
Sadly for the number go up crowd this didn't happen. There are no lambos to be found and no girlfriends. All we get is some sideways price action and a Strategic Bitcoin Reserve (BSR).
If you are in Bitcoin for the right reasons and understand what you hold, this is the perfect time to stack sats before the price goes parabolic. I say this because Bitcoin sure seems to be poised to make a massive run. If you look past the current price of Bitcoin you can see a storm of dollars flowing into Bitcoin from the traditional fiat economy. The signs are there if you start looking for them.
US States Creating Bitcoin Strategic Reserves
Guess how many states are considering creating a state level Bitcoin reserve of their own? Lots. Here is a list of states that are thinking about creating a reserve for their state:
- Alabama
- Arizona
- Florida
- Kansas
- Illinois
- Iowa
- Massachusetts
- Michigan
- Missouri
- Montana
- New Hampshire
- New Jersey
- New Mexico
- North Carolina
- North Dakota
- Ohio
- Pennsylvania
- South Dakota
- Texas
- Utah
- Wisconsin
- Wyoming
Each state is at some varying degree of interest in creating a reserve. Texas and Arizona are by far have made the most progress on making a Bitcoin reserve a reality. Texas is currently holding a public hearing on this at the time of this writing. There is strong political will to create a reserve so I definitely can see them being first movers on this and once Texas makes it a reality the other state will move in short order.
Arizona's strategic reserve bill passed the senate finance committee on a 5-2 which is a big deal in itself but still has a long way to go before it becomes policy. If it passes the Senate it still has to pass the Arizona House of Representatives and signed by Democrat Governor Katie Hobbs, so the odds of this becoming law is slim. Arizona Democrats seem to be anti-Bitcoin in general and any bills coming from Republicans will likely be shoot down or watered down.
Analysts believe that $23 billion could flow into Bitcoin from government reserves which equates to 247k Bitcoin going into government cold storage. I have reservations about governments creating BSR's but if we are going to have them I much rather them be at the state level where it can benefit citizens the most. Especially state pension funds that so many of our firefighters, police and first responders depend on for retirement.
We will probably see a state level BSR created by the end of the year if not sooner. Time will tell.
SAB 121 Repeal
What is SAB 121? SAB 121 or Staff Accounting Bulletin 121 made it problematic for financial institutions to custody digital assets such as Bitcoin for their customers. SAB 121 required institutions to record their holdings as a liability and not an asset.
Naturally banks and other financial institutions didn't see an upside to custody digital assets if it meant taking on liability and having an administration that was hostile to crypto in general. Why take the chance to piss off the government and give them a reason to go after you is probably the reasoning of most bank executives. SAB 121 achieved the goal the Biden administration set out to accomplish, namely stymie Bitcoin adoption by banks and individuals as long as possible.
President Trump swiftly issued a executive order rescinding SAB 121 and with that ushering a new era in the realm of Bitcoin and digital assets in general. Financial institutions now have the ability to explore Bitcoin custody solutions that fit their customer's need without fear of having to record a liability on their books.
As more and more people and business learn about Bitcoin third party custody options are going to be popular. Think about it from a small business owner perspective for a second. They are in the business of selling their widgets for Bitcoin but they don't want to manage the complexity that comes with accounting, taxes etc.. In steps in their local bank that they have been with for years if not decades and starts providing Bitcoin management services. Small business owners would be all over that idea. In the long run I think the repeal of SAB 121 is going to be a bigger deal than states creating Bitcoin strategic reserves.
FASB
Financial Accounting Standards Board or FASB for short has applied fair value accounting rules on Bitcoin and other digital assets. This is a huge deal because it will allow business to realize profit and losses of Bitcoin based on market prices. It also makes it easier for investors who evaluate businesses that hold Bitcoin on their balance sheet. Overall it treats Bitcoin like any other asset that a business would hold.
This accounting rule change will pave the way for more businesses to put Bitcoin on their balance sheet further driving demand for Bitcoin.
Lightning Companies Leading The Way
We all know that L1 Bitcoin can not scale to the entire world and that in order to bring more people into Bitcoin that layer two solutions would have to be built. This has largely been done with the creation of the lightning network which enables seamless peer to peer micropayments in the blink of an eye.
Base layer Bitcoin will certain not be used to buy your daily coffees or gym memberships but lightning will be used for that purpose. Businesses small and large will demand one click on demand solutions to help them accept Bitcoin payments for their businesses. There are plenty of Bitcoin business ready to help business adopt a Bitcoin standard.
Businesses such as Opennode, Zaprite, Voltage, Breez make switching over to a Bitcoin standard easy for businesses to do.
So when you take a step back and really look at the Bitcoin ecosystem it is a lot more mature than most give it credit for and will slowly eat away at fiat currency dominance around the world.
The best thing that you can do is be patient, stack as many sats as you can and educate others about Bitcoin. We all know how fiat currencies end. Our time will come.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 000002de:c05780a7
2025-04-21 19:36:30
@ 000002de:c05780a7
2025-04-21 19:36:30When people typically use the analogy of digital gold to describe bitcoin they mean that it is a digital asset that functions in the market in a way very similar to gold. By this they mean it is a store of value, not really a medium of exchange. This framing is not popular with the bitcoin is money crowd because when people use the digital gold framing they typically mean bitcoin isn't money. Its just a store of value. A hedge against inflation. It would never be used as money. It isn't good for buying stuff. Some that say this I'm pretty convinced are simply pushing this idea because of fear of the state. Others seem to really mean it.
The other day I was thinking about this and something occurred to me. I thought I understood gold before I understood bitcoin. I imagine like most people are similar. The truth is reading "The Bitcoin Standard" taught me much more about gold than bitcoin. In fact, I didn't really learn much about bitcoin from the book. I'm not saying its not a great book about bitcoin but rather my ignorance of gold was much greater than I realized. I imagine I'm not alone in that.
I remember thinking about gold after reading it... gold is pretty cool. Its properties are kinda wild. Gold has been used as money far longer than paper money. Its absolutely absurd to compare gold to bitcoin. Bitcoin is so new! But gold has qualities that make it unique among precious metals. These are not all unique properties but these are some of its qualities that make it a good money.
- You cannot create it, you have to find/mine it.
- You cannot destroy it.
- It is fungible.
- Its authenticity can be verified.
- Its supply has a very small increase over time(for now).
- It has been used for thousands of years as both a store of value and medium of exchange.
So why don't we use gold every day to buy goods. A common opinion is that it is because of greedy bankers and central planners but that's not the whole story. The truth is that gold died as a common money largely due to technology. Telecommunications and the speed of communication across great distances is what really supplanted gold as money. Gold was still used to back paper money(notes) but its use as the actual direct medium of exchange is largely dead. Bitcoin was not the first attempt to make digital money nor digital gold, but it has been the most successful by far.
So what am I saying? Bitcoin isn't digital gold but its a good analog. If you could make gold digital is would be great money. Bitcoin is a great store of value for the same reasons gold has been. Bitcoin however can be sent across great distances with ease and at the same time it can be stored for long periods of time at low cost. It is better than gold in both ways. As a store of value and medium of exchange. I can't send an oz of gold across the globe in seconds. I can't validate the authenticity of my gold with a simple computer.
My belief is that people that think bitcoin is only a viable store of value don't really understand bitcoin. Its true that currently under standard economic definitions bitcoin is not a generally accepted medium of exchange but that is only an issue of adoption and understanding. Bitcoin without lightning is still better than any fiat money. The dollar is only digital due to custodial services and trust in third parties. Our biggest problem with bitcoin as a medium of exchange is literally a lack of knowledge. This will be solved over time as people start to hold it to preserve their long term wealth. As fiat money dies and as regimes crack down on humans we will see a rise in desire for a new money. Sadly, I think most people will need to get wrecked before they get it.
My recommendation is to stop fighting over the "digital gold" label but instead agree and focus on the digital aspect. If gold was digital it would not have been supplanted by paper notes.
What do you think?
originally posted at https://stacker.news/items/951965
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 9063ef6b:fd1e9a09
2025-04-21 19:26:26
@ 9063ef6b:fd1e9a09
2025-04-21 19:26:26Quantum computing is not an emergency today — but it is a slow-moving tsunami. The earlier Bitcoin prepares, the smoother the transition will be.
1. Why Quantum Computing Threatens Bitcoin
Bitcoin’s current cryptographic security relies on ECDSA (Elliptic Curve Digital Signature Algorithm). While this is secure against classical computers, a sufficiently powerful quantum computer could break it using Shor’s algorithm, which would allow attackers to derive private keys from exposed public keys. This poses a serious threat to user funds and the overall trust in the Bitcoin network.
Even though SHA-256, the hash function used for mining and address creation, is more quantum-resistant, it too would be weakened (though not broken) by quantum algorithms.
2. The Core Problem
Bitcoin’s vulnerability to quantum computing stems from how it handles public keys and signatures.
🔓 Public Key Exposure
Most Bitcoin addresses today (e.g., P2PKH or P2WPKH) are based on a hash of the public key, which keeps the actual public key hidden — until the user spends from that address.
Once a transaction is made, the public key is published on the blockchain, making it permanently visible and linked to the address.

🧠 Why This Matters
If a sufficiently powerful quantum computer becomes available in the future, it could apply Shor’s algorithm to derive the private key from a public key.
This creates a long-term risk:
- Any Bitcoin tied to an address with an exposed public key — even from years ago — could be stolen.
- The threat persists after a transaction, not just while it’s being confirmed.
- The longer those funds sit untouched, the more exposed they become to future quantum threats.
⚠️ Systemic Implication
This isn’t just a theoretical risk — it’s a potential threat to long-term trust in Bitcoin’s security model.
If quantum computers reach the necessary scale, they could: - Undermine confidence in the finality of old transactions - Force large-scale migrations of funds - Trigger panic or loss of trust in the ecosystem
Bitcoin’s current design protects against today’s threats — but revealed public keys create a quantum attack surface that grows with time.
3. Why It’s Hard to Fix
Transitioning Bitcoin to post-quantum cryptography is a complex challenge:
- Consensus required: Changes to signature schemes or address formats require wide agreement across the Bitcoin ecosystem.
- Signature size: Post-quantum signature algorithms could be significantly larger, which affects blockchain size, fees, and performance.
- Wallet migration: Updating wallets and moving funds to new address types must be done securely and at massive scale.
- User experience: Any major cryptographic upgrade must remain simple enough for users to avoid security risks.
4. The Path Forward
The cryptographers worldwide are already working on solutions:
- Post-Quantum Cryptographic Algorithms are being standardized by NIST, including CRYSTALS-Dilithium, Kyber, FALCON, and SPHINCS+.
- Prototypes and experiments are ongoing in testnets and research networks.
- Hybrid signature schemes are being explored to allow backward compatibility.
Governments and institutions like NIST, ENISA, and ISO are laying the foundation for cryptographic migration across industries — and Bitcoin will benefit from this ecosystem.
5. What You could do in short term
- Keep large holdings in cold storage addresses that have never been spent from.
- Avoid reusing addresses to prevent public key exposure.
References & Further Reading
- https://komodoplatform.com/en/academy/p2pkh-pay-to-pubkey-hash
- https://csrc.nist.gov/projects/post-quantum-cryptography
- https://www.enisa.europa.eu/publications/post-quantum-cryptography-current-state-and-quantum-mitigation
- https://en.bitcoin.it/wiki/Quantum_computing_and_Bitcoin
- https://research.ibm.com/blog/ibm-quantum-condor-1121-qubits
- https://blog.google/technology/research/google-willow-quantum-chip/
- https://azure.microsoft.com/en-us/blog/quantum/2025/02/19/microsoft-unveils-majorana-1-the-worlds-first-quantum-processor-powered-by-topological-qubits/
- https://www.aboutamazon.com/news/aws/quantum-computing-aws-ocelot-chip
```
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ c239c0f9:fa4a5015
2025-04-21 17:42:49
@ c239c0f9:fa4a5015
2025-04-21 17:42:49Block:#893398- April 2025The Monthly Thunderbolt Dispatch on Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Use RIZFUL as your BTCPay Server lightning node via NWC by @supratic 10.2k sats \ 2 comments \ 14 Apr
-
c-otto.de routing node history with a bit of data by @C_Otto 6301 sats \ 31 comments \ 23 Mar
-
Phoenix Wallet available again in the US by @Scoresby 4696 sats \ 29 comments \ 8 Apr
-
Short Text Note: Cashu is coming to ZEUS. by @supratic 5270 sats \ 13 comments \ 1 Apr
-
Hydrus - Automating lightning liquidity management by @aftermath 2281 sats \ 9 comments \ 27 Mar
Top posts by comments
Excluding the ones already mentioned above, you can see them all here (excluding those already listed above):
-
Liquidity squeezing from your node by @k00b 644 sats \ 20 comments \ 5 Apr
-
ZEUS starting to open up Cashu test builds to community sponsors. by @supratic 499 sats \ 14 comments \ 6 Apr
-
Ask Node Runners: What is the longest lived LN channel you have? by @DarthCoin 276 sats \ 12 comments \ 10 Apr
-
What's the best way to accept lightning payments on Wordpress + WooCommerce? by @Jon_Hodl 1879 sats \ 12 comments \ 10 Apr
-
Lightning node over tor by @BallLightning 219 sats \ 9 comments \ 28 Mar
Top ~Lightning Boosts
Check them all here.
-
Missing r/place? LNboard.com is the Lightning Network's Anarchy Art Gallery by @f0e6f4f43b 905 sats \ 40k boost \ 20 comments \ 2 Apr
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar
-
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb
-
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
I made a game with Lightning where you can earn some sats by @stacks 4732 sats \ 46 comments \ 17 Apr on
~bitcoin -
"Lightning self custody works for 100 million users" "But it needs 10 billion!!" by @standardcrypto 2998 sats \ 22 comments \ 24 Mar on
~bitcoin -
24 Hours of Lightning: Watch LNboard.com's First Day Unfold by @f0e6f4f43b 809 sats \ 8 comments \ 2 Apr on
~bitcoin -
Lightning Payments Tour by Yopaki by @PlebLab 355 sats \ 0 comments \ 11 Apr on
~builders -
👀 My Bitcoin Startup Company Portfolio through Lightning Ventures. 👀 by @BlokchainB 965 sats \ 13 comments \ 16 Apr on
~Stacker_Stocks
Forever top ~Lightning posts
La crème de la crème... check them all here. Nothing has changed this month!
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
The rise of Supertestnet at #5, congrats!
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
Bisq2 adds lightning by @supertestnet 3019 sats \ 47 comments \ 19 Aug 2024 on
~bitcoin
-
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
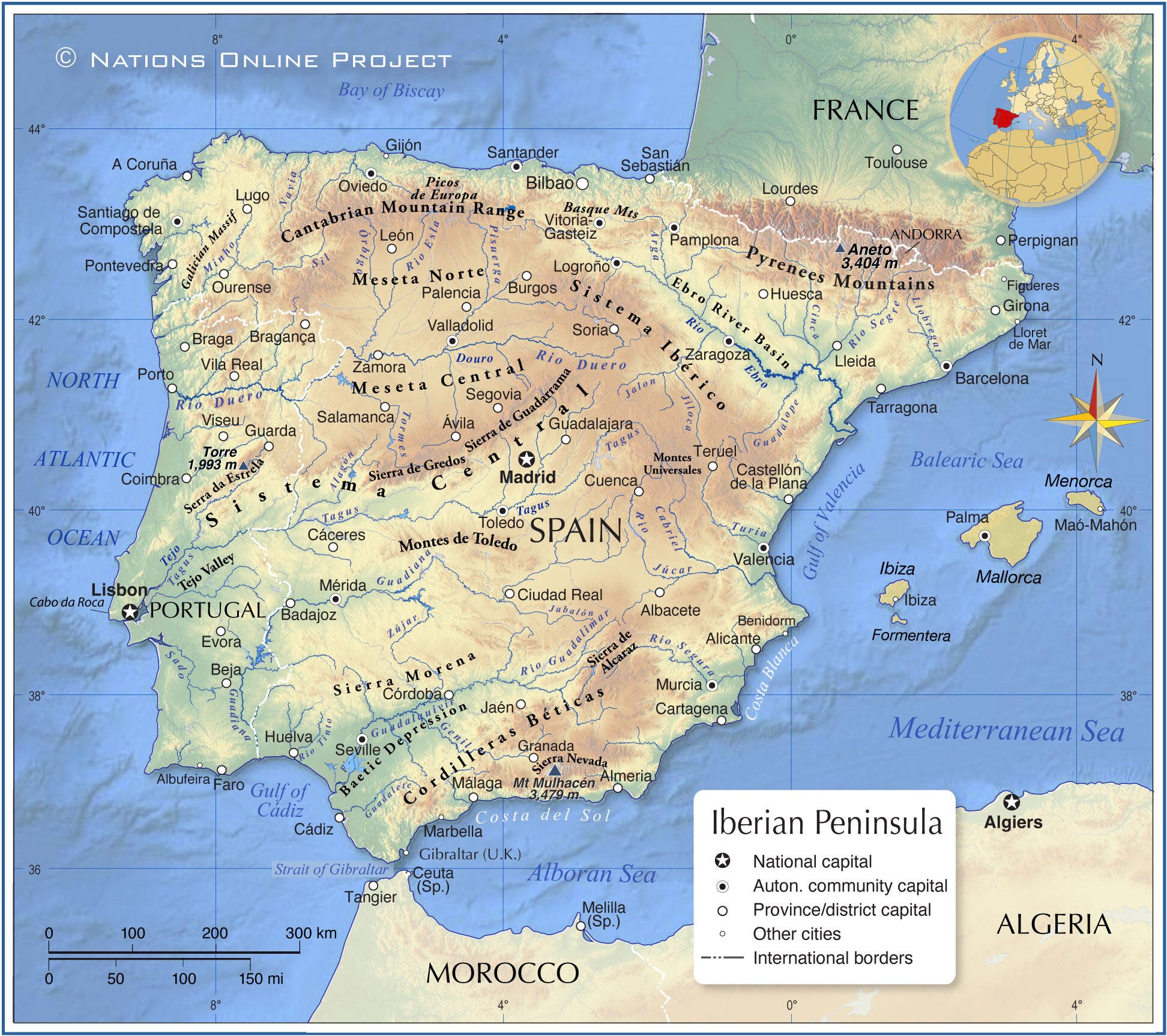
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ e97aaffa:2ebd765d
2025-04-21 12:57:16
@ e97aaffa:2ebd765d
2025-04-21 12:57:16Se este movimento de desglobalização continuar, poderá provocar uma cisão no mundo geopolítico, criar dois grandes blocos económicos, uma nova guerra fria.
Se isso se concretizar, quantos anos vão ser necessários para o S&P500 superar máximos históricos em termos reais, em poder de compra?
Em valores nominais vai ser rápido, o governo dos EUA vai imprimir tanto dinheiro, rapidamente vai superar máximos, mas em termos reais, vai demorar muitos anos.
Até agora, todo o mundo estava a investir nos EUA, mas se os países do bloco oriental, sobretudo a China, deixarem de investir em ações, obrigações e moeda dos EUA, irá provocar uma enorme redução de liquidez e na procura/demanda, não vai ser fácil ultrapassar isso.
Nos US Treasury, o afastamento da China começou em 2014(1° guerra da Ucrânia), mas o movimento acelerou em 2022(2° guerra da Ucrânia).

Os EUA, ao congelar as reservas da Rússia, ao utilizar as reservas como uma arma de guerra, “assustaram” a China e outros países. As sanções à Rússia e como esta fez para contornar as sanções foi um case study para a China.
Como o objetivo da China é recuperar Taiwan, sabe que sofrerá as mesmas represálias que hoje a Rússia sofre, por isso a China tem que se afastar da economia dos EUA.
A China está a trocar US Treasury por outros ativos e por outras geografias, o principal beneficiado foi o ouro, um ativo soberano, que não tem problemas de contraparte.
Este movimento da China foi bem visível no preço do ouro no último ano, uma valorização superior a 42%.
Mas não é só a China que está a apostar no ouro, são diversos, mas sobretudo composta por países do bloco oriental.
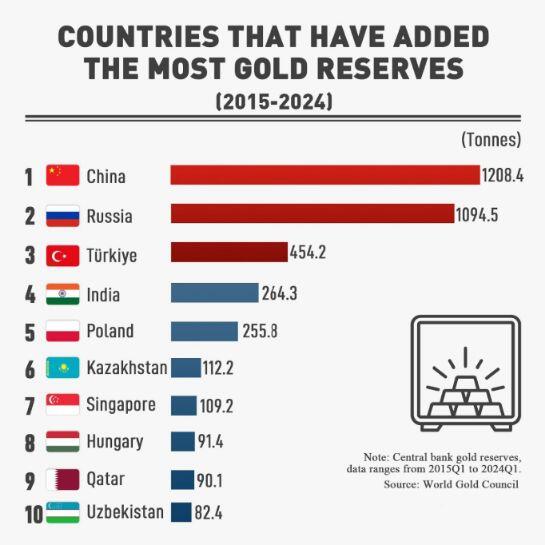
Enquanto, Taiwan for a fábrica do mundo nos semicondutores, estarão protegidos pelo guarda-chuva dos EUA. Mas os EUA, estão a construir fábricas próprias, quando forem auto-suficientes, vão descartar o “guarda-chuva”, Taiwan não terá qualquer hipótese sobre o poderio da China.
A China pensa sempre a longo prazo, estão apenas a aguardar, isto poderá estar para muito em breve.
Se isto se confirmar, o S&P500 poderá demorar décadas para recuperar desta crise, em termos de poder de compra.
-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 57d1a264:69f1fee1
2025-04-21 12:11:22
@ 57d1a264:69f1fee1
2025-04-21 12:11:22There's any content about SN out there?
In the news: - @BitcoinNews Stacker.News Raises $1.25m Seed Round At $25m Valuation - @Alby blog post explain how Stacker News adds Self-custodial Spending with NWC - @cryotosensei on @0xbitcoiner's website Stacker News encourages deep sharing ad Random things I learnt about Bitcoin from Stacker News - @anita's Earn bitcoin on Stacker News: People asked and I answered
Recently we have seen an article in BM writing about how PlebLab is shaping the future of bitcoin startups in Austin. SN was mentioned and linked 🎉
Started in 2021 by one of PlebLab’s cofounders Keyan Kousha, Stacker.news has quickly become a hub of news for many tech-savvy Bitcoiners. Boasting an open source Lightning-powered Reddit, the platform has gathered an active and loyal fan base that reward each other with sats for every upvote, often being early to integrate the latest technologies in the Bitcoin-social media tech scene.
In the past it has also only mentioned here.
From a startup pitch perspective:
Developer of a news platform intended for individuals to earn real money for creating and curating content. The company's platform specializes in allowing individuals to submit, vote, and comment on content, stories, and discussions about the topics in communities organized around their interests, enabling individuals to post content and get paid while reading the news. PitchBook -
https://pitchbook.com/profiles/company/535835-44#overviewStacker News is a forum (like Reddit or Hacker News) where you can earn real money for creating or curating content. F6S -
https://www.f6s.com/company/stacker-news#aboutPeople talking about SN:
-
A stacker shared a Lessons learned from Stacker.news and how SN works. Discourse Co-CEO respond:
Heh, it’s not a healthy or sustainable model for the types of communities consciously we build for. Definitely not something we would consider building into core but you could make it work with a plugin. Extrinsic motivators attract the wrong people for the wrong reasons, in my experience. Healthy community ecosystems are driven by intrinsic motivation.
-
on BitcoinTalk here, here and here. There are probably more posts where it has ben mentioned and discussed.
-
HackerNews crowd does not seem too excited about it. Just few comments on each post.
Some review have been collected on @julian's Apollo and ProductHunt.
Let's check what YT has:
Some interviews first. At 2023 ZBD x PlebLab TabConf Hackathon, Keyan Kousha explain Why Not to Use Stacker News
@kr did a great job interviewing k00b when SN was in its infancy - Stacker News Is Growing FAST - Stacker News Is Disrupting Social Media | E17 - Keyan Kousha on Stacker News, Earning Bitcoin, & Decentralized Content | The Kevin Rooke Show | E17 - How Siggy47 Stacked Over 500,000 Sats on Stacker News | SS8
And here some interviews:
Stacker News is a user-generated, feed-style news platform, modeled after Hacker News, but with the important distinction of having natively-integrated bitcoin lightning payments, as a means of fostering more natural communities (think less spam and antisocial behavior), cultivating high-signal bitcoin content, and providing a better user experience overall.
Stacker News is still in the very early days of its development, but it's a great showcase of how bitcoin can be used to improve upon an existing model, and in doing so, explore how improved incentives might influence media publishing, monetization, and moderation.
Keyan is a prime example of someone who caught the bitcoin bug, and just couldn't resist getting involved. The result is a product built with and for bitcoiners, and it was great to have him on the show to explain more about his motivations and ambitions.
-
From ~ideasfrommtheedge pod: AI, Simulations, and Startups with Keyan Kousha (Founder, Stacker News)
-
@alexstrenger's Convos On The Pedicab #177 Stacker News: A Bitcoiners Alternative To Reddit
-
@dk and @MaxAWebster intro on What's new with Stacker.News and Nostr? also shared here
-
@ConnectTheWorld stream Keep Austin Weird! Meet Keyan, the founder of Stacker.news
-
@Thriller Lightning: Stacker.News Founder Keyan
-
0.00000018: Keyan Kousha, Stacker.News: an interview in the Changing the Tide show here
-
@bitcoinplebdev reading top ~devs stories 04/08/2024 and stacker.news codebase overview / how to run locally)
That's the interviews I was able to find. Continuing the dig...
-
@TheWildHustle compiles SN ~Music' vibes into YT playlists
-
@kdnolan7 on was giving some updates about the ~Education territory here and here
Gradually, then suddenly, the message start to change, and the majority of videos communicate something that is probably, at least from my perspective, not the right way to market a product like SN:
-
@SatsMate lay out Why He Love Stacker News!
-
@voltage share a story quickly talking how Stacker News is like YCombinators Hacker News but YOU EARN! https://www.youtube.com/shorts/d1xZ3RE9plk
@HattyHats Earn Bitcoin (LN) Blogging with Stacker News
The long list continues: - Earn bitcoin Satoshis Reading & Sharing Content on Stacker.News - First Time Walk Through by @SatoshiTutor - Earn Free Bitcoin | Stacker News Quick Tutorial from Earning Crypto Site - One of the Different Ways to Earn Bitcoin 👉 stacker.news | Bitcoin Lifestyle #2 from @SatoshiComTR - @1100note another Stacker.News story - ...
This list of references can, and probably will, go on and on with the same topic. The message looks like will be always the same: come over, stack sats, stay humble. There's maybe something wrong with the message we share SN out there? Is not what we do, is how we do it, that make the difference. As you can see, there's not much there that refer to quality content, great supportive community, community moderated contents, no ads, no spam, no bots (well, not many) and no ai. Pure human content.
In other successful platforms where people earn money for the contents they create, the money factor is totally hidden, is not their main sales point in the pitch. Look at YT itself. We all know people earn fiat producing and sharing videos, but their comms does not talk about it, at least not the way stackers do. And you'll not find many YTers inviting others to create videos to earn money. Well ok, some do!
Something we could make an effort to improve, is the way we talk about SN. Finding alternative ways to do it is hard, some have been mentioned here https://stacker.news/items/948462/r/Design_r
Just wanted to see how much other quality content is out there talking about SN that is not about stacking sats? Share your best contents, nostr notes, x tweets, blog posts, articles, videos, interviews, reviews or any other media that has been created by others about SN (no memes shill) or that somehow mention it in the comments below.
originally posted at https://stacker.news/items/951177
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 92f1335f:2c8220d1
2025-04-21 11:38:11
@ 92f1335f:2c8220d1
2025-04-21 11:38:11Chapter 1: The Spark (2019)
Jonathan Parker wasn’t exactly a risk-taker. A software developer in his late twenties, he preferred routines—morning coffee, coding sprints, and quiet evenings with podcasts. But something kept catching his attention: Bitcoin.
It wasn't the first time he'd heard about it. Back in 2017, his college roommate had begged him to buy some at $3,000. Jonathan laughed it off. Then, Bitcoin soared and crashed. By 2019, most people had already moved on.
But not Jonathan.
In April 2019, curiosity turned into obsession. He began reading whitepapers, watching crypto influencers on YouTube, and combing through Reddit threads at midnight. After weeks of research, he took the plunge: he invested $2,600 into Bitcoin, buying half a coin at $5,200.
To his friends, it was a “weird tech gamble.” To Jonathan, it was something else entirely—a hedge against the world, a bet on the future.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 9c9d2765:16f8c2c2
2025-04-21 11:08:37
@ 9c9d2765:16f8c2c2
2025-04-21 11:08:37CHAPTER EIGHT
James woke up early the next morning, the weight of his new responsibilities settling over him like a quiet storm. His uncle, Charles, had called him the previous night to officially confirm his appointment as the new president of JP Enterprises. His first task would be to review all the company’s investment plans and oversee critical decisions that would shape the future of the business.
He had gladly accepted the challenge. This was his chance to prove himself, not just to the Ray family but to everyone who had ever doubted him.
The following morning, James dressed in his usual simple attire: a plain button-down shirt and worn-out jeans. He had never been one for extravagant outfits, and he saw no reason to change now. With determination in his heart, he made his way to JP Enterprises.
However, upon arriving at the company’s grand entrance, he was met with hostility. The senior security guard, a burly man named Greg, frowned as he assessed James from head to toe.
“Excuse me, sir,” Greg said, blocking his way. “This is a corporate building. If you’re here to beg, you should leave.”
James raised an eyebrow, his expression calm. “I’m here to meet with the board.”
Greg let out a short laugh. “You? Meet with the board? Do you even know where you are? This isn’t some charity house, get out before I call for backup.”
James stood firm, unwilling to engage in an argument but also refusing to leave. The confrontation drew attention from other employees, some whispering among themselves while others simply watched in curiosity.
At that moment, Nancy, the company’s general secretary, arrived from a different entrance and noticed the scene unfolding. She gave the security guard an order not to let him in, she was unaware of James’s new appointment and didn't know that they had made a grave mistake.
Sandra, the company’s general manager, had been watching the scene from her office window and stormed outside the building in fury. As soon as she saw James being harassed at the entrance, her temper flared.
She didn’t hesitate. Walking straight to Greg, she raised her hand and delivered a resounding slap across his face.
“You fool!” she shouted. “Do you have any idea who you just insulted?”
Greg, now holding his stinging cheek, looked at Sandra in shock. “Ma’am, I didn’t know… I thought…”
Sandra didn’t let him finish. She immediately turned to James, her demeanor shifting to one of deep respect. She bent down slightly, bowing her head in reverence.
“Boss,” she addressed him formally. “I apologize for this man’s ignorance. Please, allow me to escort you inside.”
At the use of the word “Boss,” the entire crowd watching from the sidelines gasped in surprise. Murmurs spread through the employees gathered nearby.
“Did she just call him boss?”
“Wait… is he the new president?”
Greg’s face turned pale as he suddenly realized the grave mistake he had made. Without hesitation, he fell to his knees. “Sir, I’m so sorry! I didn’t know! Please forgive me!”
James, however, did not spare him a second glance. His eyes held no anger, just a quiet authority. Without a word, he turned to Sandra, nodding in acknowledgment.
“Let’s go inside,” he said calmly.
As James stepped into the building, Sandra leading the way, every employee inside the vast, modern corporate office stood up in unison. They had already received word of the new president’s arrival, but no one had expected him to be introduced in such a dramatic fashion.
As he walked past, whispers filled the air.
“So that’s the new president?”
“He was treated like a beggar outside… unbelievable.”
“I heard he’s Charles’s nephew… But why is he dressed like that?”
James paid no attention to the whispers. He had expected doubt and skepticism. What mattered to him now was proving his worth through actions, not appearances.
As he entered the boardroom, he turned to Sandra and Nancy. “Let’s begin. I want to see all the investment reports immediately.”
Both women nodded, admiration shining in their eyes. James was not just stepping into power he was about to redefine it.
Nancy walked briskly down the marble hallway of JP Enterprises, her heels clicking against the polished floors. She had been summoned to the president’s office, a place she had only entered a handful of times under the previous administration. The air was thick with whispers from employees who had just witnessed the shocking revelation that the so-called beggar at the entrance was none other than the new president.
Her heart pounded as she approached the large mahogany doors, pushing them open slowly. Her breath hitched at the sight before her, James seated comfortably in the president’s chair, his fingers interlocked as he observed her with an unreadable expression.
Nancy’s knees nearly buckled. She had been one of the skeptics, assuming that James was nothing more than an unfortunate case. And now, seeing him in that seat, she realized just how wrong she had been.
“Mr. James…” she stammered, her voice barely above a whisper. “I… I had no idea. Please, forgive me for my doubts.”
James remained silent for a moment, then spoke in a firm but measured tone. “What’s done is done. But let this be a lesson, Nancy never judges someone based on their appearance.”
She nodded hastily, her face flushed with embarrassment. “Understood, sir. It won’t happen again.”
His gaze darkened slightly. “Good. Now, I need your complete discretion. If anyone finds out about my true identity before the right time, you will no longer have a place in this company.”
Nancy swallowed hard and nodded. “I won’t tell a soul, sir.”
With that matter settled, she quickly pulled out a folder from her bag and placed it on the desk. “Here are the company’s current investment plans, Mr. James.”
James opened the folder and scanned the documents. His expression remained neutral, but internally, he was unimpressed. The investments were scattered across various top companies in the city, some of which had questionable stability. He had seen similar patterns before risky, short-term gains that often led to losses in the long run.
Without hesitation, he reached for a pen and started crossing out each investment one by one.
Nancy’s eyes widened in shock. “Sir? You’re… cancelling all the investment plans?”
James set the pen down and met her gaze. “Yes. These investments are not what the company needs right now. We need to rebuild our foundation with something more solid.”
She hesitated before speaking. “But, sir, these were carefully chosen by the previous board. Some of these are partnerships with major corporations.”
James leaned back in his chair. “That may be, but their choices were reckless. I won’t allow this company to sink under the weight of poor decisions.”
Nancy nodded slowly, beginning to understand the shift in leadership. “So, what’s the next move, sir?”
A small smirk played on James’s lips. “I will personally be investing ten million dollars into this company. That will more than cover the loss from these cancelled investments.”
Nancy’s mouth fell open slightly. “You’re investing… ten million dollars? Personally?”
James nodded. “Yes. Consider it a reset. JP Enterprises needs a fresh start, and I intend to give it one.”
Nancy stood still, stunned by the weight of his words. This was no longer the James she had heard rumors about. This was a man of power, a man with a vision.
As she gathered the documents and prepared to execute his orders, she couldn’t shake the feeling that this was only the beginning. James wasn’t just here to lead JP Enterprises he was here to dominate.
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 95cb4330:96db706c
2025-04-21 09:59:02
@ 95cb4330:96db706c
2025-04-21 09:59:02Principle:
Reduce internal friction by minimizing unnecessary processes, approvals, and meetings.
Empower small, autonomous teams to make decisions quickly and independently.
💡 What It Means
- Bureaucracy kills speed, innovation, and ownership.
- Instead of creating endless layers of management and approval, build the smallest system necessary to enable great work.
- Give teams the trust and tools they need to move fast.
The goal is not chaos, but flexibility with lightweight structure—so the organization stays dynamic as it scales.
📈 Why It Matters
✅ Speed is a competitive advantage in entrepreneurship.
✅ Empowered teams are more creative and motivated.
✅ Minimal bureaucracy allows companies to iterate fast and stay customer-focused.
🏛️ Examples in Action
- Spotify uses small “squads” with high autonomy and light-touch leadership to maintain speed and innovation.
- Basecamp designs its company around minimal meetings, clear asynchronous communication, and trusting small teams to own outcomes.
- Amazon uses the "two-pizza team" rule—teams should be small enough to be fed with two pizzas.
📚 Resources to Explore
- 📄 Spotify’s Engineering Culture – Part 1
- 📖 Basecamp’s Approach to Minimal Management
- 📘 Harvard Business Review on 3 Ways to Improve Your Decision Making
- Spotify Engineering Culture - Part 1 (aka the "Spotify Model")
🚀 Action Prompthttps://hbr.org/2018/01/3-ways-to-improve-your-decision-making
Ask yourself:
"What approvals, meetings, or processes can I eliminate or simplify today to help my team move faster?"Build only as much structure as needed—and no more. Protect creativity, speed, and ownership at all costs.
-
 @ 8671a6e5:f88194d1
2025-04-12 23:04:34
@ 8671a6e5:f88194d1
2025-04-12 23:04:34
intro
Full disclosure : I bought multiple bitcoin art items to support artists
Bitcoin has absorbed old tropes from finance, tech, and economics, fundamentally reshaping how we think about money. But Bitcoin art? It should be a companion on the journey to a Bitcoin standard. Yet it doesn’t even seem to be trying. Every artistic movement worth its salt needs something to push against—to rebel, to spark thought, to provoke, or at the very least, to represent a technical or methodological leap forward in its field.
Pointillism comes to mind as an example in painting.
In this piece, I take a brief stroll into the subjective realm of art, specifically exploring art in the Bitcoin space—if such a thing truly exists. Some people might not like it, but as someone who has created modern art myself, I can confidently say that artists will emerge stronger from this transitional phase of Bitcoin art, whatever this era may be called later.
The art corner You know the drill. You visit any Bitcoin conference and there’s the obligatory “art corner” or gallery. Funny, wasn’t it just a few years back that a single decent artwork was a rarity needing a proper place for being shown tot he public? Now, every conference (small or big) needs this curated space, crammed with artists all vying for a sliver of attention.
And what do you usually find? A collection of the utterly predictable, the profoundly uninspired, the tiresomely repetitive, and anything but artistically groundbreaking amidst some exceptional pieces that will be snatched up almost immediately.
The themes are often so worn out, they’re practically a self-parody version of bitcoin art:
Animals holding signs (with of course… bitcoin logos)

Whales, dolphins, and the aquatic crew: The go-to, utterly drained metaphor for Bitcoin wealth, rendered in every conceivable medium with sea creatures.
Majestic vistas with bitcoin slogans: Think inspirational landscapes defaced with inscriptions or cryptic (not really) messages.
Women cradling blocks: Because apparently, nothing screams "Bitcoin" like a woman clutching a perfectly geometric cube. Bonus points if there are more painted women on a canvas, than actual women at the event.
Coins, coins, and more coins: Gold, silver, pixelated, abstract – just in case anyone forgot Bitcoin isn't a physical trinket.
Collages of Bitcoin celebs and memes: Why bother with originality when you can just mash up some social posts?
Reheated classics with an orange filter: Slap some orange highlights and a Bitcoin logo on a famous painting, and voilà! “Bitcoin art.” Bitcoin Pop-art, Bitcoin punk, Bitcoin collages…
It’s like the whole Bitcoin art scene is endlessly regurgitating the same tired ideas, and pouring a lot of time and effort in being just a fancy washing machine of orange t-shirts.
Most of it—not all, mind you, as there are people with exceptional thought and even more exceptional work—is no more than Bitcoin-themed art. By "theme," I mean the color orange or a “B,” much like you’d see M&M’s-themed coffee mugs, M&M’s t-shirts, or M&M’s-themed playing cards.
Now, let’s be clear: this isn’t about slagging off the artists themselves. I know how hard it is to thrive in this space, and I also learned about the time and effort put in to any work (the perception of the artwork has nothing to do with this at all!)
The dedication and passion within the bitcoin art scene are undeniable. Making art in a niche like Bitcoin is a tough gig (and often a thankless one, given the whole value-4-value thing seems perpetually broken). They deserve respect for putting themselves out there, doing the work and trying to make their passion work.
Many genuinely believe in what they’re creating, even if not everyone is convinced or will like a work of art. However, a lot of them are chasing a mirage, much like those hoping for an oasis of Bitcoin jobs in the desert. Many artists dream of turning their art into a business or a career move, and some even try to make a full-time living from it. That’s admirable, but I’m convinced it’s often a ruse, where your money, time, and effort dress up someone else’s business ideas and sense of branding. In my opinion, the real art movement in Bitcoin has yet to take off. It will need people with great ideas, motivation, know-how, and effort, for sure!
So I repeat the issue isn’t the individuals, the artists; it’s the collective creative stagnation that comes from clamoring to the general interest of this perceived “bitcoiner” as an audience.
Target < B > Audience
Only, this audience is usually not the target audience for the artworks itself. Art needs to have room to inspire, be free and relay an idea (even if that idea challenges another idea). That can’t be done to a target audience that just wants to sell their stuff to each other at a conference (see my piece on Bitcoin conferences for that) neither can it be a target audience that even is too cheap to buy a ticket and freeloads themselves into an conference.
Bitcoin is supposed to be revolutionary, yet so much of its art (or perceived art) feels like a tacked-on commercial necessity or, worse, a desperate attempt at self-validation. Most of it is just a perpetual branding motion from a non-existing marketing team.
The target audience is usually even worse. Not knowing what they’re looking at, out of their element and knowing they should and could support the artists and their work. A lot is depending on why this audience is wandering through a conference gallery in the first place.
If most people at a conference are the usuals, the sellers, the company people, then they're used to seeing these artists and their art pieces. No one is amazed anymore. Which is in fact a sad thing to happen.
I can't imagine how incredibly hard it must be to try to sell something as bitcoin art to this kind of audience, while trying to believe that a B-logo on an excerpt of the whitepaper is worth the effort. (I don’t think it is, but tastes differ, some people prefer a Whopper over a nice steak dinner)
Signaling “membership” in the bitcoin community is important to some, and they do that through hats, t-shirts, pins and hoodies, not buying a bitcoin artwork.
Art is inherently subjective, fluid, and deeply personal.
I love Kusama’s polka dots, someone else might be into Herman Brood’s chaotic paintings, and someone else might get all nostalgic over an Anton Pieck candy store drawings.
The contradiction Bitcoin: The hardest money ever created. Objectively verifiable. Math-based. Impersonal. Code.
The clash is between feeling and finance, between cold emotionless, hard numbers and warm, beating hearts.

That’s why it's always a bit surreal to see people that sit in a conference room, go from a deep dive into Lightning Network scalability or Bitcoin’s code ossification; and see them wandering through an “art gallery” filled with pieces that are the polar opposite of anything remotely code-related. The cold hearts walk amongst the works of warmth. The trustless math calculates their steps and starts to look at something that’s exposed to a public of that’s not there for the art, but the mimicking of such a think in their setting makes them have their own élan, grandeur. It feels forced. And to me, it feels even wrong to see people walk out of a conference room, right into the art gallery… where they’re usually stroll around out of boredom or just as a form of a break. It’s almost disrespectful, and I feel art needs its own place, the right setting. And that setting is definitely not a bitcoin conference.
You see tech and finance folks just standing there, at these art corners looking at the art pieces like cows watching a drone show.
You feel this subtle pressure to act like it’s profound, even though it rarely is. But you’re there, so you play along with the charade as well. It’s miserable to see. Certainly when some people are more interested in buying the piece of mind of the artist, the way of life or a glimmer of independence they’re missing themselves.
I believe bitcoin art is rarely bought for anything else than capturing the reality and authenticity of the artists. Artists know that. And they sell that authenticity (out) to eat, drink, sleep and pay their rent. Authenticity can be double spent, unlike the hard money asset where it’s supposedly all about. Artists have very big blocks.
It’s a bit like that hyped-up restaurant that turns out to be serving dressed-up bar food, but you’re with friends, so you pretend that $35 hors d'oeuvre doesn’t taste suspiciously like steamed shoe laces. Theaters are sometimes food bars or galleries. Proof of fart Then there’s the awkward issue of selling this stuff. How do you, as an artist, “comment on” or “complete” an asset in an artistic way, while that asset appreciates by an average of 40 to 70% a year?
Buying traditional art as an investment is one thing, driven by aesthetics or emotional connection. But buying Bitcoin art with Bitcoin? That’s a financial decision triggering regret (almost for sure). Think about it: 0.1 BTC spent on a canvas today, isn’t just a fixed one-time cost; it’s a future opportunity cost.
That same Bitcoin could be worth significantly more in a few years. The artwork, not so much, not even a Picasso painting or a Hokusai manages that kind of annual return. So, unless you’re head-over-heels for the piece (or the artist), buying Bitcoin art with Bitcoin is almost certainly a bad trade financially – though, so is buying that fancy coffee machine you'll use twice or getting a diamond ring for you loved one.
Of course, this isn't a definitive argument against it (it's subjective, remember). But it's a factor, just one element. People who buy art to lock it away into a vault aren't the same folks milling around a Bitcoin conference, presumably. But still.
Purpose
Historically, in the West at least, art served many purposes: glorifying churches, telling stories to the illiterate, and expressing the full spectrum of human emotion (pain, regret, doubt, madness, etc.). There was always a demand, whether from religious institutions, the populace, or a desire for education and status. The demand rarely came from onlookers or passive walk-ins. You can only walk in after the demand has been met. The real commanding force in Bitcoin art isn’t the financial types in suits or the grifter with a few stickers who got into the conference for free and smells like weed. The demand comes from people who love to cultivate the branding to propel themselves forward.
In Bitcoin? None of that. There’s little genuine demand, I’d argue. The demand seems mostly driven by the artists themselves wanting to participate. Which, in itself, makes the act of creation worthwhile for them. But the audience demand feels… manufactured. Nobody wakes up thinking: “.. I sure hope there’s a Bitcoin art gallery at this conference...”
This low-to-nonexistent demand, however, presents a massive opportunity to actually impress. Low expectations mean impact is easier to achieve in a lasting way. But that impact evaporates fast if all the visitors get is the same old themes with some orange varnish or a monkey holding a sign.
"Proof of work" isn’t enough here; we already have that in the bitcoin network. Bitcoin art need "proof of thought". Sure, Bitcoin artists put in the hours. Their work is literally proof of effort. But effort alone doesn’t equal value – originality does. Copying Warhol, Mondrian, or Van Gogh and slapping a Bitcoin twist on it isn’t the high level of creativity that can pull art lovers in (and even make them bitcoiners); on the contrary it’s opportunism. And in a space that seems to thrive on recycling successful (or at least visible or temporary cool) ideas, genuine artistic innovation is a rare beast.
Bitcoin art could be so much more. And yes that’s subjective, but at the same time, … walk around at any art gallery and be honest with yourself as a person and buy what you really like, support the artists and the scene, and at the same time realize you’re playing dress up.
There should be so much more, as a separate art movement. It could delve into the philosophy of decentralization, the tension between digital scarcity and creativity, the profound societal shifts Bitcoin is triggering. Instead, we’re mostly drowning in kitsch and thinly veiled cash grabs. The Bitcoin art world doesn’t need more bodies; it needs better minds. We don’t need bigger blocks, we don’t need blocks at all!
The uncomfortable truth is that many Bitcoin artists are here chasing opportunities, just like the rest of us. But spotting an opportunity doesn’t magically transform you into an artist.
I could “find the opportunity” to be a star in the hypothetical Bitcoin basketball league, being one of the first to join. But compared to the global pool of professional basketball talent, I’d likely be laughably bad. I’m not even tall enough to reach most pro players’ armpits, let alone dunk. Yet, in òur tiny Bitcoin league WBBF (World Bitcoin Basketball Federation), I’d be a legend, an OG, demanding respect for my early participation and best-dunk-champion. Just like some Bitcoin artists seem to expect accolades for a weak, orange-tinted imitation of 1960s pop art.

I wouldn’t cut it in any real basketball club, probably not even the lowest amateur league, considering my limited knowledge of the rules. Do you have to run back to the center? Can you tackle other players? Is snatching the ball mid-dribble legal? No clue.
But I could hang around the basketball scene a bit, soak up the jargon, maybe buy a sports drink for a better player to glean some knowledge, and then clumsily mimic their moves while still being terrible at dribbling. I’de buy the right shoes as well. To fit in. Just like bitcoiners buy the right t-shirts.
The same principle applies to some Bitcoin musicians and other creatives. Being the only one doing something – be it Bitcoin-themed sculptures, paintings, sci-fi, or whale graffiti murals – doesn’t automatically make you a leading figure. It just makes you… the only one. Being the sole sci-fi filmmaker in Bangladesh makes you the top of your national field, sure, but it doesn’t make you the next Kubrick. Likewise, airbrushing an orange “B” on a canvas doesn’t turn you into the next Georgia O’Keeffe.
The Bitcoin world thrives on competition and proof of work. Perhaps it’s high time Bitcoin art did the same. We need a battle of ideas, experiments, and genuine insights, not just more orange paint, paragraphs of the white paper and some copper wires.
The genuinely sad part is the sheer effort many of the artists pour into their work! But there’s a limit to how much you can make people want to buy an art piece simply because it has a Bitcoin theme. Go beyond that.
Get real
Real Bitcoin art, in whatever form it takes, will command a high valuation because it will be scarce, original, and have Bitcoin not just as a subject, but woven into its very fabric. That form (and there will be many), in my opinion, is still waiting to be discovered. And I’m fairly certain it won’t be found in a conference gallery, where bored artists sit next to their work, politely nodding at every bloke who wants to sound knowledgeable about art for five minutes or tries to make himself look like a big shot. Because let’s face it, I’ve yet to meet a Bitcoiner with a genuine understanding of art history or a truly discerning eye.
Some starting points, perhaps (just my two cents) :
Art that embodies decentralization itself, inviting audience participation and co-creation, mirroring Bitcoin’s ethos but yet to be fully realized in the art world. Including consensus.
Art that incorporates distributed consensus or a rotating "proof of work" concept in its creation or presentation.
Purely mathematical art forms that resonate with Bitcoin’s underlying principles.
The possibilities are vast. Or maybe, just maybe, Bitcoin itself is our art, and we don’t need all this orange-tinged stuff cluttering up galleries nobody asked for.
And why not paint blocks holding women, instead of women holding blocks? Or why not have inflation-resistant art? Or math-based art that isn’t even possible to show on a canvas?
On that subject, the author of this piece enjoys making art as well and conducted a small experiment. I've performed a "life performance" approximately three times now, which I consider pure Bitcoin art. This was an action, not a physical object. It demonstrated work I personally delivered as “a miner” (function in this art piece), and during the process, people could verify it and even received my block subsidy (effort). So far, only one person has recognized this art form; the rest were unaware. Since it's an action, not an object, it's intangible unless you witnessed it. This is my way of saying, "you are the artist." According to the bitcoin ethos.
Interestingly enough, other people, even those involved in Bitcoin art themselves (!), didn't see it. This amused me because, much like the early weeks of Bitcoin's network growth, many initially failed to recognize its potential. Perhaps this parallel should be enough for us all to understand the true nature of Bitcoin art.
The Artistic Dare:
Here’s a challenge, not to your wallet, but to your creative soul: conceive and execute a piece of art that embodies the spirit and principles of Bitcoin in a way that is genuinely original, thought-provoking, and resonates beyond the immediate Bitcoin echo chamber. Forget the predictable iconography. Dig deeper.
If you can create something truly compelling, something that makes us see Bitcoin – or art – in a new light, then you’ve truly created Bitcoin art. And then comes the extra real challenge: finding someone who can and would pay for it, and at the same time “gets it”.
The main challenge is creating real art—a path, a genre—where a standalone Bitcoin art gallery can thrive outside the conferences and the small echo chamber of the “what do you sell?” crowd.
Don’t sell your dreams and authenticity to bored traders or bitcoin consultants. It’s like serving the finest wine to a bunch of alcoholics in a bar at 4 am.
Playing it safe with themes and artworks that can’t cross into the real art scene (even the underground art scene, let alone the corporate art) will not be as long-lived as bitcoin itself. Trying to spark interest from art lovers in general, will be the killer app, and will make bitcoin art into a movement. And that’s what we all need to make it art,… the pieces can’t exist without the movement. I hope someone will get the right spark, idea and fire going.
But until then we’ll be stuck with people painting a chimpanzee holding a glittering Bitcoin logo and chatting with any dude that wants to feel like someone at a conference.
Good luck.
AVB
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 7d33ba57:1b82db35
2025-04-21 08:47:51
@ 7d33ba57:1b82db35
2025-04-21 08:47:51Spread across 14 islands and connected by elegant bridges, Stockholm is often called the **"Venice of the North." It blends royal history, cutting-edge design, lush nature, and a laid-back Nordic vibe like few cities can. With cobblestone streets in Gamla Stan, sleek modern art in Södermalm, and serene waterways everywhere, Stockholm is both storybook and futuristic.

🏰 Top Things to Do in Stockholm
🏛️ Gamla Stan (Old Town)
- A beautifully preserved medieval core with colorful buildings, narrow alleys, and cozy cafés
- Visit the Royal Palace, Stockholm Cathedral, and watch the changing of the guard
- Stop by Stortorget Square for the classic photo and a fika (Swedish coffee break)
🖼️ Vasa Museum
- Home to the Vasa warship, which sank on its maiden voyage in 1628 and was miraculously recovered 333 years later
- One of Sweden’s most popular and jaw-dropping museums

🏡 Skansen Open-Air Museum
- A walk through Sweden’s past—complete with historic homes, craft demos, and even Scandinavian animals
- Great for families or anyone curious about Swedish traditions
🌉 Södermalm
- Stockholm’s hip, creative district
- Full of boutique shops, vintage stores, craft coffee, and rooftop bars
- Climb Monteliusvägen for incredible views of the city skyline and Lake Mälaren

🌿 Nature & Water Everywhere
- Take a boat tour of the Stockholm Archipelago, made up of 30,000+ islands
- Kayak through the canals or paddleboard around Kungsholmen
- In summer, locals swim off the rocks in the city or picnic in Djurgården Park

🍽️ Food & Fika
- Try Swedish meatballs, gravad lax, or herring smörgåsbord
- Visit the indoor Östermalm Market Hall for local specialties
- Don’t miss fika culture—coffee + cinnamon buns (kanelbullar) is a must

🚆 Getting Around
- Super walkable and bike-friendly
- Excellent public transport: trams, ferries, metro (Tunnelbana)
- The T-Centralen station even doubles as an underground art gallery

📅 Best Time to Visit
- Summer (June–August): Long sunny days, outdoor festivals, archipelago adventures
- Winter: Christmas markets, cozy cafés, and snow-dusted rooftops
- Year-round appeal with distinct charm in every season

-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:37:32
@ 5c26ee8b:a4d229aa
2025-04-14 16:37:3210:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ da0b9bc3:4e30a4a9
2025-04-21 07:56:29
@ da0b9bc3:4e30a4a9
2025-04-21 07:56:29Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/951022
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 866e0139:6a9334e5
2025-04-21 06:47:57
@ 866e0139:6a9334e5
2025-04-21 06:47:57Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Sie wollen die neuesten Pareto-Artikel auf einen Blick sehen (Friedenstaube & Co.), um nichts mehr zu verpassen?* Hier geht es zu unserem Telegram-Kanal.***
An Ostern begehen Christen das Hochamt ewiger Ideale. In Kirchen, die zu Hochzeiten der Pandemie geschlossen, später für Impfkampagnen wieder geöffnet wurden, wird der Sieg des Lebens über den Tod beschworen. Der Aufstand des Geistes gegen die Materie. Doch wie steht es um die Revolte des Geistes in einer Welt, die den Menschen zunehmend in die Rolle eines verwalteten Tieres drängt?
Die Revolte der Normalen
Albert Camus, einer der klarsten Köpfe des 20. Jahrhunderts, wusste: Nur wer an etwas glaubt, revoltiert. Der Revoltierende sagt Nein zu Unterdrückung und Ja zur Würde. Ohne Glauben an Werte vergiftet sich der Mensch am Ressentiment – jener toten Emotion, die weder schöpft noch heilt, sondern nur vernichtet. Oder versinkt im Nihilismus. Dieser greift auch heute um sich. Deutschland, deine Leuchttürme sind Irrlichter geworden. Inmitten einer Dauerkrise, die jeden Normalzustand zersetzt, bleibt eine Frage offen: Wie gesund bleibt der Mensch in einem kranken System? Wie lange dauert es, bis Normalität selbst als Revolte gilt?
Camus schrieb:
„Wenn man an nichts glaubt, wenn nichts Sinn hat und wir keinen Wert konstatieren können, dann ist alles möglich und nichts hat Bedeutung.“
In einer Welt, in der Gesundheitspolitik zur Farce, Wissenschaft zur Ideologie und Aufarbeitung zur Fortsetzung der Propaganda mutiert, wird die Revolte der Normalen zur letzten Verteidigungslinie der Freiheit.
https://www.youtube.com/watch?v=Y2roiEvbPuU
Das Leid der Revoltierenden
Die Revolte ist kein Spaziergang. Sie schmerzt. Sie kostet Freunde, Ansehen, Karriere. Aber sie schenkt eine ungeahnte Kraft: Die Entdeckung, dass der Impuls zum Leben stärker ist als zum Tod. Das Wunder von Ostern, die Auferstehung, ist im Innersten die Revolte der Lebendigkeit gegen die Herrschaft des Todes. Der Märtyrer Jesus nimmt die Sünden und Leiden der Welt auf sich – ein menschgewordener Widerstand, der durch seine Hingabe unsterblich wird.
Sein "Verbrechen"? Er stellte sich zugleich gegen die geistige und politische Elite seiner Zeit. Gegen Besatzer, Schriftgelehrte, Pharisäer, Frühbürger. Heute wäre Jesus wohl ein Querdenker, ein Reichgottesbürger, ein Verschwörungstheoretiker. Mindestens ein Rechter. Vielleicht ein antisemitischer Spinner, der es wagte, eine Alternative zum bestehenden Glaubenssystem zu etablieren.
„Wer an mich glaubt, wird leben“, sagte Jesus. Man kann es so lesen:\ Wer an die verkörperten Werte glaubt – Wahrheit, Freiheit, Liebe –, wird leben. Denn wer an einen Wert glaubt, macht ihn lebendig. Der Nihilist hingegen fügt sich ein, wird Stein in der Mauer des Systems.
Camus brachte es auf den Punkt:
„Lieber stehend sterben als knieend leben.“
In Zeiten, in denen Friedenstreiber als Nazis diffamiert werden und Protestierende als Pathologische gelten, bleibt die stille Revolte des Individuums das letzte unzerstörbare Element.
Die Psy-Op der Aufarbeitung
Nach der Inszenierung des Corona-Spektakels erleben wir die nächste Bühne: Die Aufarbeitung durch die Täter selbst. Eine theatralische Umarmung des eigenen Versagens, mit Bundesverdienstkreuz und Download-Gesichtsausdruck bei Frau Buyx inklusive. Wenn Corona eine Psy-Op war, warum sollte nicht auch seine Aufarbeitung Teil der Psy-Op sein? Die Strukturen erinnern an Rosenhan, Milgram und das Stanford Prison Experiment:
- Etikettierung der Kritiker als Verrückte.
- Pathologisierung der Revolte als Krankheit.
- Belohnung der Kollaborateure mit Orden und Posten.
Ein Lehrbuch der totalitären Psychologie.
https://www.youtube.com/watch?v=XTBYWPLXrTk
Immunologische Reaktionen eines sterbenden Systems
Während die Panzer-Osterhasen rollen, also die Neuvariante des Impfspritzbesteck-Gebäcks der letzten Krise, offenbart sich die Wahrheit: Das System hat seine eigene Bevölkerung beschossen. Friendly Fire unter falscher Flagge.\ Kollateralschaden im Namen von Volksgesundheit und Solidarität.

Jetzt dasselbe nochmal in Tarnfleck statt Weißkittel.
Was bleibt?
Demut.\ Selbstständigkeit.\ Verbindungen, die nicht von Zertifikaten abhängen.\ Der stille Aufbau von Netzwerken jenseits der Anstaltsordnung.
Unabhängiger machen kann man sich zum Beispiel bei Vorträgen und Seminaren von Michael Ballweg, der immer noch in einen kafkaesken Prozess verwickelt ist.
Meine Stimme erhebe ich in Zukunft auch mit der FSUS (Free Speech Union Switzerland) im Rücken, einem Verein der u.a. Rechtshilfe für verfolgte Freiredner organisiert. Bei Interesse an einer Mitgliedschaft erfahren Sie hier mehr.
Oder wie manche sagen: “Buy Bitcoin and focus on your craft.”
Die letzte Revolte
Wer heute zweifelt, beweist Charakter.\ Wer heute fragt, zeigt Rückgrat.\ Wer heute eigene Gedanken wagt, revoltiert bereits.
Wenn wir uns verbinden, werden wir das neue Gesicht der Welt.
Ostern erinnert uns daran:\ Die größte Revolte ist das Aufstehen in einer Welt, die uns niederdrücken will.
Nicht die angepasstesten überleben, sondern die Standhaftesten.\ Nicht die Lautesten, sondern die Wahrhaftigsten.\ Nicht die, die folgen, sondern die, die aufstehen.
In diesem Sinne:
Frohe Auferstehung.
https://www.youtube.com/watch?v=vbH9YacSi2o
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 8671a6e5:f88194d1
2025-04-03 14:52:44
@ 8671a6e5:f88194d1
2025-04-03 14:52:44\~ The person came up to me from behind his merchandise stand and saw my Noderunners pin on my black t-shirt, then looked me dead in the eye and asked : “So… what do you sell?”
This is the eighth long-read in a series of twelve “food for thought” writings on Bitcoin. It was originally meant to be a few chapters in a book, but life’s too short for that.
Define
Let me start by saying there’s no single way to define or explain a “Bitcoin conference.” The experience can vary depending on a few factors: who’s organizing it (a long-time Bitcoiner or someone from traditional finance trying to grasp Bitcoin), where it’s being held (a sunny paradise like Madeira or a gloomy northern French town), and who’s speaking (technical experts or charismatic entertainers or people with little substance).
Despite these differences, there’s a shared culture that ties these conferences together: a mix of excitement, frustrations, and inevitable evolution. That’s what I explore.
This is just my take, based on what I’ve personally witnessed and what I hear from my surroundings. It’s not meant to be a blanket critique of all Bitcoin conferences as there are plenty I haven’t attended, though I hear about most of them. Even the good ones will evolve into something else over time. So, plan accordingly.
A bit of background on my perspective: at some point in my life, I hit a bump in the road that kept me tied to where I live — a bleak corner of Belgium, surrounded by fiat slaves, shitcoiners, and people who spend six hours a day consuming brain-numbing garbage television. Traveling is an exception for me, but for many Bitcoin conference attendees, it’s a ritual, a must-do event.
So, I view these events with a mix of fascination and grounded skepticism — something I’ve found lacking in many Bitcoiners. I’ve never been to a Bitcoin conference before 2023, despite receiving plenty of invites over the years. From what I heard and saw in photos from friends who attended (even the real early ones) these events seemed eerily similar to the dull hotel conference rooms I once endured in tech and telecom. I’ve had my fill of lukewarm, watery coffee and lifeless speakers droning on about firewalls. So I skipped that particular honor.
Up until around 2018, Bitcoin conferences were a soulless sea of chairs lined up under fluorescent tube lights, draining the life out of attendees—one telecom acronym at a time. Not exactly inviting. Yet, looking back from the perspective of 2025, those were the “pure” days. Back then, people like Roger Ver (before he pivoted to Bitcoin Cash), Andreas Antonopoulos, and encryption specialists spoke to small audiences, explaining Bitcoin in its raw form.
But, like any Bitcoiner, I try to improve myself. So, I made the effort to travel, visit other Bitcoiners, and attend Bitcoin conferences. The conferences I attended in 2023/2024 made me a bit wiser ; not necessarily from what was said on stage (with a few lucky exceptions who still try to bring original thoughts). Most of what I learned came from the long queues, the drama, and watching grifters operate in real time and the good characters floating around.
So, here’s what I’ve learned.

Chain of ticket
I quickly discovered that many Bitcoin conferences have their own “quest for tickets” dynamic, almost like an industry with its own inner circle. It’s a waterfall system: tickets start at lower prices to fill up the venue (usually right after the previous edition). That’s standard practice, both inside and outside of Bitcoin. But what’s strange is seeing organizations that only pop up when a conference needs promotion—somehow securing tickets for themselves and their friends (or for *making* friends) while shilling referral links for small discounts to their followers.
The real free tickets, though, are a hot topic in many local communities and make all the difference for some attendees. What’s particularly interesting is that most ticket prices can be paid in Bitcoin, adding a layer of calculation to the process.
If you paid 230500 sats for your ticket and later see the dollar price fluctuate, say from $180 to $270, or the other way around, by the time the conference starts, you realize you either bought too late or too early.\ It’s better to not have bought at all.
Some ticket holders end up paying less (in dollar terms) than others, making it a gamble. As the event date approaches, ticket prices tend to rise—unless you wait until the last minute, when they haven’t sold out, or just pay at the door. It’s a strange feeling knowing that not everyone paid the same amount (and as mentioned, a significant number get in for free) depending on their timing.
Many organizations and local community representatives show up primarily to be present; securing free tickets, which function more as a badge of recognition than a necessity.\ It’s similar to how a rock groupie sees backstage access: a status symbol, whether for an autograph or something more. Being seen standing next to big names is a huge deal for some, as they derive their own status from proximity.\ This also reinforces the “rockstar status” that conferences create around certain figures, once they come out to take a selfie with some nice people and young fans, then to quickly disappear back to the ‘whale room’ or backstage.
There’s often an entire insider network determining who gets these free tickets. In some cases, it’s naturally tied to the local community, but in others, the professionalism is laughably low. At certain events, you could probably just walk up to the entrance (if there’s even someone checking) and say, “I’m with the organization” to get in for free.
It gets even more absurd.\ At a conference near the French-Swiss border, I was probably one of the very few who actually paid for entry. The real spectacle wasn’t in the talk rooms — which remained eerily empty — but in the dining area, where half the town seemed to have shown up just for the free food. Around 200 people queued for a free lunch, while the presentation halls were at best one-third full throughout the day.
And beyond the ticket games, there are plenty of ways to slip in unnoticed. Carrying a random piece of equipment and mumbling\ “I need to put this crate in the back” can get you past security. Or you can just wait for the one security guard to get distracted by chatting up a girl or stepping out for a smoke, and you’re in. At one event, I walked in alongside someone carrying crates of wine for the VIP lounge. I blended in perfectly (I paid afterward).
So, to sum up: at nearly every conference I’ve been to, a big portion of attendees either walk in for free or hold compensation tickets they got through some connection. Sometimes that connection is uncomfortably close to the organizers. Other times, they just slap an “industry” label on themselves when, in reality, they’re nothing more than a social media bio with a few followers.
Local representatives of a podcast, community, influencer network, or fake marketing club also get in for free. And you? The regular guest, you and I are paying for them. There’s no real vetting process; with some organizers, anyone wearing a Bitcoin t-shirt and saying the magic words “I do community building” or “I know the local Bitcoin meetups” gets a free pass.
The ones who actually want to learn about Bitcoin — the ones who click the link and pay full price — are the ones covering the costs for everyone else and ultimately making these conferences profitable (or at least break even). The problem? They’re the ones left wondering: “Was it really worth my time and money?” only to never return again most of the time.
Because many of the people at these conferences aren’t there to learn. They’re part of the circus. And others? They’re the ones paying for the circus boss, the clowns, and the trapeze artists.
At that one conference with the massive free-lunch crowd, I saw one interesting talk. And I had plenty of valuable conversations and observations — conversations I could have just as easily had by visiting that place outside of a conference setting.
In the end, I realized the main reason I was there was to support a fellow Bitcoiner giving a presentation. And after that? They disappeared from my life. Because, just like in the fiat world, you’re only as good as your last few hours of usefulness to most people.
Which brings me to the next element of Bitcoin conferences...friends
Bitcoin “frens”
This might be the hardest lesson of all: you meet fellow Bitcoiners at these conferences. And some of them? They’re truly special characters. A few even made such a deep connection with not-so-well-traveled-me that I would’ve gladly traveled a full travel day just to spend time working and doing something meaningful together (which I actually did).
But most of these connections? They last only a moment. Few survive beyond the conference, mainly because of the vast distances— both in kilometers (or miles) and in the way we live our everyday lives. The Bitcoiners you meet at these events are, for the most part, just regular people trying to make ends meet in the fiat world while saving in Bitcoin. Or they’re chasing the Bitcoin dream or even find a job in the fata morgana of bitcoin jobs. They act like they belong, like a clown acting like he’s going to climb the trapeze.
I respect that. But over time, I realized that many of them operate in Bitcoin mode; a kind of facade. Behind that front, that mask, most are just testing the waters to see if they can make it. And most don’t.\ Treating Bitcoin as a lifestyle movement, a career shortcut, or an identity, has its limits. Eventually, the real person breaks through. And you have to face your own instincts and personality.\ I’ve tried to be an acrobat, and ride the lion, make the audience laugh, but I’m still the seal who’s brought back to the cage after he balanced a ball on his nose. The quote “I’m Jack’s wasted life.” came to mind often when standing somewhere at a conference space.
Self-doubting people stay self-doubting, owning Bitcoin or not. Emotional wrecks remain emotional wrecks — just with Bitcoin now. And when these masks slip off, you’ll see everything: the greed, the overconfidence, the longing for drama, the addictions, the narcissism, the energy-draining personalities, sleaziness usually with the ones who always say the right oneliners or wear the right Bitcoin merch to blend in.
And you can love people for that. Everyone has flaws. Everyone has a price as well.
But these Bitcoin “frens” can also hurt you badly. Because as Bitcoiners, we carry hopes. And hopes are like ants on a sidewalk, they’ll eventually get crushed.\ We long to meet people who see the same truth, the same vision of Bitcoin as we do. Some will act like they actually understand and do, they talk the talk for a while, as if they’re parroting a podcast.
If you stay in the shadows - like I did for years - you won’t have to deal with these things. If you never try, you’ll never be let down. But you still stay in the imaginary basement, letting yourself down. That’s not the bitcoin style. We router around problems. Even if we stand amidst the problems (like a conference).
But if you do? There’s a hefty price to pay — beyond just the money spent. It’s a cost paid in energy, emotions, and social interactions and above all: time.
And once in a while, you’ll meet a friend for life.
Just be prepared:
Bitcoin is a journey that few people you encounter at a conference can take for longer than four years, or even four hours of conversation actually.
And then, after navigating the social maze of Bitcoin conferences —the connections, the masks, the fleeting friendships, the smell of weed and regret — you find yourself facing an even greater challenge: the queue at a coffee stall.

## \ The Soviet LN Queue
It’s one of the most fascinating and frustrating aspects of every conference: the insanely long lines. Whether it’s for the toilets, a coffee booth, or some niche merchandise stall, you’ll see Bitcoiners waiting like it’s 1963 after a Soviet state bakery just got fresh deliveries.
waiting for coffee Seriously, aren’t we supposed to be the pinnacle of free-market efficiency? Instead, we’ve somehow perfected the art of the long food lines. I remember people waiting in line for like 35 minutes to order a cappuccino!
The usual culprit? A mix of payment chaos and the Bitcoin Orangepill mental issues in action.
A large portion insists on using Lightning (as in "their preferred lighting wallet"), which would be fine except they’re fumbling with some exotic, half-working wallet because using something that’s actually fast might get them sneered at for being “custodial.”
On top of that, vendors are juggling card payments, cash, various Lightning POS systems, and even the occasional cutting edge dudes trying to pay with an Apple Watch or worse, some newly released Lightning-enabled gadget that doesn’t work yet. And when it does work, it requires so much attention and Instagram footage that it takes five minutes just to hand someone a coffee while the guy pays with a lighting NFC ring on his finger, something you can't use ànywhere else ever. It’s cool. But not to anyone else than you.
So, here’s a tip for the regular people, the rats that pay for all of this : sneak out.
Then you find a small, locally owned café outside the conference, pay them in cash, and actually enjoy your food in a few seconds or minutes.
If (and only if) they accept Bitcoin, great! Tip them well. Otherwise, just relax and have a conversation with a local, all the while inside the conference venue there are Bitcoiners filming each other struggling to make a payment with the latest Lightning-enabled NFC card or making the staff uneasy.
Meanwhile, some poor 22-year-old café worker is trapped in an unsolicited podcast participation:
“Wait, you accept tips in Wallet of Satoshi? Who told you that? I’ll explain it to you!”
Or worse:
“Hold on, I just need to do a quick swap… It’s an on-chain transaction, the last block was 19 minutes ago, can’t be long now… wait… umm… do you take VISA?”
At this point, ordering a simple drink at a Bitcoin conference has become an unnecessarily complex, ego-driven performance. With long queues as a direct result. And don’t get me started on the story when 30+ bitcoiners walked in to a Portuguese restaurant without a reservation, and they all wanted to pay with different payment methods. It was like the Vietnam war.
Solution:
A tip for conference organizers and their catering : pick one Bitcoin point of sales system, set clear guidelines, and make everyone stick to them. Instruct people to adhere to the following :
Pay with a (bank) card, cash, or Lightning and PLEASE decide beforehand which method you’re using before ordering your stuff! We prefer lighting.
If you’re using Lightning, have enough balance on you wallet or get lost.
Use a compatible wallet. (Provide a tested “approved” list and train staff properly. Users who use other stuff get their order “cancelled” at the first sign of trouble. Your app‘s not scanning, or not compatible, or it has some technical mumbo-jumbo going on to your vpn LN node at home 2000 km away? Please get real and pay with a bank card or something.
No filming, duck-facing (like it's 2017) or stupid selfies with your payment. It’s been done a thousand times by now. There are people in line, waiting behind you, they want to order as well, while you have your little ego trip or marketing moment. Move on please!
“Our staff knows how bitcoin payments work, you don’t need to #orangesplain it to anyone.” We don’t care about your 200th LN app or the latest “but… this one is faster” thingy. Order your drinks, pay and get out of the way please.
Bitcoin fixes many things. But it hasn’t quite fixed this yet.
The bitcoin conference axiom
Going to a conference, versus keeping your bitcoin in your wallet is a tough choice for many.
If you pay nothing for tickets and lodging, while enjoying free meals and cocktails, your opportunity cost drops close to zero —yet your networking and social impact are maximized while you can also do business. That’s ideal. At least, for you. In such case, Bitcoin may only "win" over an extended timeline, but for you, it's essentially a free ride. You incur no real opportunity costs. You drink their milkshake.
On the other hand, if you’re a regular attendee, you pay full price: the ticket, overpriced drinks and food from the stands (losing even more if you generously pay for coffee in sats), plus extras like t-shirts and books (which you’ll never read). Your milkshake gets taken—at least half of it.
If you’re lucky, you might spend an evening in town with the event’s "stars"—those occasional luminaries who briefly grace the normies with their presence for a drink. Some can’t even hold their liquor. Year after year, the same 10 to 15 speakers or panelists appear, funded by your dime, traveling the world and enjoying the perks—some even cultivating fan bases and hosting exclusive parties.
The real opportunity cost hits hardest for regular attendees who come to learn, shelling out significant money while accumulating their fourth hardware wallet or yet another orange-themed t-shirt. They might even squeeze in a selfie with a former sportswear model turned Bitcoiner. For normies (as they’re often called), the financial and social scales rarely tip in their favor.
Calculating the conference opportunity cost
To determine the opportunity cost of attending a conference instead of investing in Bitcoin, over time follow these steps:
-
Calculate your total conference expenses, including tickets, travel, food, drinks, and lodging (merchandise and donations).
-
Estimate Bitcoin’s percentage gain over the conference period and the following year(s). (in order to not make you cry, I suggest nog going over 5 years)
-
Multiply your total conference cost by this percentage to determine the potential Bitcoin profit you forgo.
-
Assign a dollar value to the networking or business opportunities you expect to gain from the conference (if you’re not just in it for the laughs, meeting high-class consultants, friendships, self-proclaimed social media Bitcoiners, or the occasional gyrating on one of the musicians/artists/food stall staff members).
-
Subtract this “networking” value from the missed Bitcoin profit to find your net opportunity cost (this is rather personal,… with me it’s zero, but for someone selling t-shirts it’s probably much more).
If the result is negative over the chosen timeframe, the conference was financially worthwhile for you. If positive, holding or buying Bitcoin was the smarter move.
Unless you’re a recognized speaker in this traveling circus, your opportunity cost will likely be positive — meaning all the others lose hard money, while fumbling with your Lightning wallet.
The Conference Opportunity Cost Formula
Let:
CT = Total conference ticket & entrance cost (in dollars)
CR = Total related conference costs (travel, lodging, food, etc.)
C = CT + CR (Total cost)
G = Bitcoin’s % gain per year (as a decimal, e.g., 5% = 0.05)
N = Estimated fiat value of networking/business opportunities and knowledge gained.
OC = (C × G) − N
Where:
OC (Opportunity Cost) < 0 → The conference was worth attending.
OC (Opportunity Cost) > 0 → Holding/buying Bitcoin was the better move.
Some example calculations (I've left out examples before 2020, I don't want people crying or waking up at night thinking "Why did I go to Amsterdam in 2014?!")
example : Conference in April 2024 Entrance: $200 Lodging, t-shirt, and travel: $900 Bitcoin's estimated gain: 23% (0.23) No business / knowledge value gained OC = (200 + 900) × 0.23 - 0
- $253 OC (Bitcoin would have been the better choice.)
Conference in April 2020 (adjusted for historical Bitcoin growth) Entrance: $175 Lodging and travel: $700 Bitcoin's estimated gain: 1089% (10.89) No business / knowledge value gained OC = (175 + 700) × 10.89 - 0 OC = +$9,529 (Massive missed gains — Bitcoin was the clear winner.
--
So the first lesson in bitcoin should be: Only attend conferences if you get paid to do so and get a free ticket and free lodging, which kind of would kill that whole industry to begin with.
Energizing
At first, it’s energizing to meet like-minded bitcoiners, but after a while, you realize that a big chunk of them are just trying to sell you something or aren’t really bitcoin-focused at all. And some of them are just looking for their next way to kill time and boredom.
The drama that comes with attending these conference and the personal interaction can get pretty intense at times, since expectations often don’t match the personalities. Before you know, you’re walking around at night through some bad part of a town, while crying your eyes out because you thought you found your soulmate.
Future pure industry conferences will suffer less from this drama, because everyone there has the same goal — pushing their company or product— while the “other” grassroots conferences are more of a meeting spot for bitcoiners of all types and perspectives, bringing the usual drama and mess that comes with human interactions. Current conferences are a mix of both usually.
I think the current era of bitcoin conferences is coming to an end. Soon, probably by the end of 2025, we’ll see a clear split between industry-driven and human-driven (grassroots) smaller conferences, and it’ll be really important to keep these two separate.
I even had the idea to launch a sort of conference where there wouldn’t be any industry speakers or companies present. Just bitcoiners gathering at a certain place at a specific week and having a good time. I called it “club Sat” And you could just go there, and meet other bitcoiners, while acting there was a big venue and speakers,… but there aren’t any. Would be refreshing. No struggle for tickets, no backstage stuff, no boring talks and presentation,… just the surroundings and the drama lever you want and probably like.
On stage
The podium is usually left for the known names. Not every conference is like that, but most of them need these names, badly. These names know each other, they encounter one another in VIP rooms and “the industry” a lot of times anyway.
The same people you see in the bitcoin news, the same people having a cult following, and the very same people traveling, staying and drinking for free while spreading the same bitcoin wisdoms will be invited over and over again.
Or… they go rock around as they’re usually so bored they had to start a rock band to entertain themselves. Which is rather entertaining if you’re following up on who does what, but in the end it’s largely just for their own amusement and it shows. I get that. I would do the same. It’s fun and all.
It’s just a bit sad that there are only a small group of top-layer speakers, and then the sub-top that usually has more to say, or gets little opportunity. The reason for that is simple: the “normies” who pay in full for tickets, come there for the “big” names. They don’t know that much about bitcoin usually, so they’re not waiting on some unknown dude explaining something about an obscure niche subject. A debate can help remedie this, to mix it in with some lesser known names, but I have the feeling the current “line-up” of bitcoin conferences feels like a rock festival in 2025 putting the Stone temple pilots or Creed on the card.
Yes, they’ll attract an audience and do their playset well,… but it’s not exactly the pinnacle of the music industry at the moment, neither is Madonna by the way :)
Promoting anything
The people organizing these events usually aren’t Bitcoiners either — they’re promoters (few exceptions though).

They don’t care if they organize a symposium about a newly discovered STD, A three-day cheese tasting event, a Star Trek convention, or a Lucha Libre wrestling tournament featuring El HODLador, as long as they can sell tickets and make money from merchandise they're good. The last thing on the mind with some of them will be helping bitcoin adoption. There will be a time (soon) where people that know bitcoin, known bitcoiners and know how to organize events get their act together. It will be different than the early days, and it will be different than the boring going-through-the-motions conferences we have now. There shall be fun, social gatherings, life, excitement and culture, and not the “what do you sell?” atmosphere, neither the “this old dude on stage again”?
That’s why they’ll slap any semi-famous name on the poster to pull in a crowd - could be a washed-up Mexican wrestling star with strange legal issues, the cheese-tasting equivalent of Usain Bolt, or your neighborhood Bitcoin old-timer with a beard and a "best selling author" label.
It’s also why most of these conferences end up being more about shitcoins than anything else. And even if they're for the most part about bitcoin, the venue is usually infested with marketing budgets, useless organizations that wanted complimentary tickets (some of them do only one thing: popping up when a conference is nearby and then they’re gone again) ... along with some hawking consultant types you never see anywhere else.
They'll occasionally pay people but usually in fiat, or if you're a bigger name, you might get other deals. For artists or staff, it's all in fiat from what I heard.
Pure Bitcoin conferences, also rely on these big names. Whether it’s a well-known Bitcoiner, a CEO, president, or someone with real reveling knowledge to share with the audience (though that last type is getting rare).
Looking for love in all the wrong places
\ Let’s also address the fair share of “orange diggers” at Bitcoin conferences—because yes, they exist. And no, let’s not single out one particular gender here.
Some people treat a Bitcoin conference like a live-action dating app mixed with a financial vetting process for potential partners. It’s essentially an opportunity to inspect and assess the grab bag of fintech, crypto, and Bitcoin folks in real life.
And if you think this is exaggerated, just attend a few conferences—three is enough. You’ll start noticing the same people popping up, seemingly without any real Bitcoin knowledge, but with a very strong interest in dining, chatting, and generally being around—as long as you look and play the part. I can only imagine how dialed-up this effect must be at a shitcoin conference — probably like flies on a cowpie.
The trick is, in Bitcoin, these people try to blend in. Some even tag along with real Bitcoiners, while others just crash the party and try to get noticed. Their actual interest in Bitcoin? Close to zero. Their main target? Your wallet, or some fantasy thing about getting to know someone out of the ordinary.
And that’s a shame for the people who genuinely care about Bitcoin, who want to network, or who simply are looking for like-minded people. They often find themselves competing for attention with those who’ve turned “being noticed” into a sport, while the rest just wander around, lost in the shuffle. Talk to the quiet ones. Certainly if they look like they belong in a antiques shop.
My advice: Talk to people and be genuine. If you don’t know much about Bitcoin, that’s fine - nobody expects you to be a walking whitepaper and on top of that, most people you'll encounter don't know that much either. It’s bitcoin: we’re all rather average people that hold an extraordinary asset.
Just don’t be "that orange digger" looking for a partner with a loaded bag of bitcoin.
Because in the end, what’s the prize you win? You don’t know who’s under the mask. You don’t even know who’s under your own mask.
Finding a man or woman at a place where half the people are laser-focused on financial sovereignty, and the other half are busy arguing about seed phrase storage, UTXO management, and why your Lightning wallet sucks? But good luck with that. The judge of character usually comes when they find the next shiny object or ditched you standing in the rain at the entrance of a restaurant while dealing with a lightning watchtower or a funny cigarette or whatever.
If you’re truly looking for love, maybe stick to going to a normal bar. If you’re here to learn, connect, and be part of something of a grassroots movement, then be real yourself.
I've seen some rather nasty examples of people at Bitcoin conferences—of all kinds. And I've also seen some really cool examples of truly awesome people. This led me to believe that Bitcoin conferences simply let you meet… people, just dialed up a bit.
Future If you encounter rotten people, they’ll usually be even more rotten than in the fiat world. If you meet really cool people, they’ll be even more awesome than the cool people in the fiat world.
Our volatility is our freedom. So, I guess it’s normal. Doesn’t make it any easier, though.
Bitcoin sees through bullshit, and so do Bitcoiners (even if it takes 21,000 blocks)
Pretty soon, I reckon we’ll see conferences fork into two camps: grass roots, and the “industry” level ones. (human / corporate) I guess I’ll only attend the human part, for sure, but I can’t help but booking myself a single room in a hotel in a nice area in that case, so I don’t have to deal with class of 2022 hippies sharing referral links to their middleman service while asking me for a lighter 3 times in a row. The chances for me of meeting cool bitcoiners in a nearby cocktail bar are a lot higher.
In the meanwhile, I’ll look forward and see how the bitcoin conferences will evolve, fork in two “styles”. One corporate and one underground. Maybe there will be one more genre just for the fun of it.
I’ll stay away, as I don’t like this current mix of industry gigs and having the insiders and “the rest” of us all mingled together clamoring for tickets, attention and coffee. The game is rigged. Staying at home is the better option (for now).
written by AVB
If you like : tip here
-
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 1beecee5:d29d2162
2025-04-21 06:30:55
@ 1beecee5:d29d2162
2025-04-21 06:30:55 -
 @ b0137b96:304501dd
2025-04-21 05:54:41
@ b0137b96:304501dd
2025-04-21 05:54:41Streaming has revolutionized how we consume entertainment, offering unparalleled access to diverse content worldwide. With the rise of theBest OTT Platform options, audiences can enjoy their favorite Hollywood, Bollywood, and regional films anytime, anywhere. However, for many viewers, language can be a barrier to fully experiencing international cinema. That’s where innovative platforms step in, bridging the gap between global content and regional audiences.
If you're searching for theBest OTT Platform that delivers high-quality international and regional content, we’ve got you covered. Let’s explore four leading platforms—Dimension on Demand (DOD), Hoichoi, Olly Plus, and Aha Video—that are transforming the Indian entertainment landscape.
Dimension on Demand (DOD) – The Best OTT Platform for Hollywood in Your Language Among the many platforms available, Dimension on Demand (DOD) stands out as theBest OTT Platform for movie lovers who enjoy global cinema in their native tongue. Unlike other platforms that focus solely on regional or Bollywood content, DOD specializes in offering Hollywood movies dubbed in 9 languages like Hindi, Telugu, Tamil, Bangla, Malayalam, Bhojpuri, English, Kannada, and Marathi. This means you can enjoy blockbuster hits, critically acclaimed masterpieces, and thrilling action films—all in the comfort of your language.
What makes DOD truly unique? A vast library of Hollywood movies dubbed in Indian languages Seamless user experience with high-definition streaming Personalized recommendations based on viewer preferences Accessible across multiple devices—smart TVs, mobiles, and laptops A growing collection that ensures fresh content for movie enthusiasts Beyond its impressive collection, DOD ensures that audiences across India can experience world-class entertainment without language barriers. If you love Hollywood but prefer watching in your native language, DOD is undoubtedly the Best OTT Platform.
Hoichoi – A Must-Have for Bengali Entertainment Hoichoi (https://www.hoichoi.tv/)has become a go-to OTT platform for Bengali audiences, offering an impressive mix of movies, web series, and original content. With a strong focus on Bengali-language storytelling, it delivers a diverse collection ranging from classic films to modern thrillers.
Why Choose Hoichoi? Extensive collection of Bengali films and web series Exclusive Hoichoi Originals with gripping storytelling A mix of contemporary and classic Bengali cinema With its continuous addition of fresh content and commitment to Bengali storytelling, Hoichoi has solidified its position as a top-tier platform for regional entertainment lovers.
Olly Plus – A Celebration of Odia Content Olly Plus (https://www.youtube.com/OllyPlus) is Odisha’s dedicated OTT platform, catering specifically to Odia-speaking audiences. It features a rich selection of Odia movies, music, and podcasts, making it a hub for cultural and entertainment enthusiasts.
What Sets Olly Plus Apart? Exclusive Odia-language movies, music, and short films A platform dedicated to preserving and promoting Odia storytelling Inclusion of music, podcasts, and cultural content With Odia entertainment often underrepresented in mainstream media, Olly Plus plays a crucial role in bringing high-quality Odia content to its audience.
Aha Video – The Ultimate Destination for Telugu & Tamil Viewers Aha Video (https://www.aha.video/) has carved a niche in the Best OTT Platform industry by delivering high-quality Telugu and Tamil entertainment. From blockbuster movies to gripping web series, Aha Video ensures South Indian audiences have access to exclusive content tailored to their preferences.
Why Aha Video is a Must-Try? Exclusive Telugu and Tamil movie collections Original series that cater to South Indian storytelling A strong focus on South Indian cinema and entertainment Its commitment to regional cinema ensures that fans of Telugu and Tamil content always have something fresh and exciting to watch.
Why the Best OTT Platforms Matter for Regional Audiences As the streaming industry expands, the importance of theOTT Platform options for regional audiences cannot be overlooked. They not only cater to language-specific audiences but also help preserve and promote local cultures while making global content more accessible.
The Rise of the Best OTT Platforms for Regional Content: They bridge the gap between global cinema and local audiences Viewers can enjoy Hollywood and indie films in their native language Regional content platforms contribute to cultural storytelling and preservation Whether it’s the Hollywood-dubbed collection of DOD, the Bengali storytelling of Hoichoi, the Odia exclusives of Olly Plus, or the South Indian cinema of Aha Video, each platform plays a vital role in reshaping digital entertainment in India.
The Final Verdict – Which is the Best OTT Platform? Choosing the Best OTT Platform depends on your content preferences. If you are looking for international cinema in regional languages, Dimension on Demand (DOD) is the perfect choice. For regional entertainment lovers, Hoichoi, Olly Plus, and Aha Video offer excellent options tailored to specific linguistic audiences.
With DOD leading the way in bringing global entertainment to regional audiences, it's clear that the future ofOTT lies in localization and accessibility. Whether you're a fan of Hollywood, Bengali dramas, Odia storytelling, or Tamil blockbusters, there’s an OTT platform designed just for you.
Want to experience Hollywood like never before? Watch your favorite global films in your language on Dimension on Demand (DOD). Subscribe now and explore an ever-growing collection of blockbuster movies!
-
 @ 9223d2fa:b57e3de7
2025-04-21 05:53:02
@ 9223d2fa:b57e3de7
2025-04-21 05:53:02193 steps
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:32:51
@ 5c26ee8b:a4d229aa
2025-04-14 16:32:5110:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ ed5774ac:45611c5c
2025-03-24 21:33:47
@ ed5774ac:45611c5c
2025-03-24 21:33:47Erdogan’s Turkey: The Rise, Reign, and Decline of a Political Strongman
As Turkey’s political crisis intensifies with Erdogan’s imprisonment of Imamoglu—a leading opposition figure and likely frontrunner in the 2028 presidential elections—it is crucial to analyze the historical events and geopolitical factors that enabled Erdogan’s rise, secured the consolidation of his rule, and allowed him to maintain his grip on power for decades. To understand the foundations of Erdogan’s enduring political legacy, we must examine the historical events that shaped his ideology and the global power struggles of the time. Equally important are the international actors who facilitated his rise and prolonged his rule. Key factors include the link between Erdogan’s rise and the Iraq War, the interplay between Turkey’s military coups and the Ukraine crisis, the events that led to the erosion of Western support for Erdogan, the role of the U.S. and NATO in the 2016 coup attempt against his rule, and the shifting geopolitical landscape that continues to define Turkey’s political future.
The Roots of Islamism: The CIA, the 1980 Coup, and the Suppression of Turkish Liberalism
Erdogan’s rise is deeply intertwined with the growth of Turkey’s Islamic movement, which gained traction in the 1970s amid Cold War geopolitics. During this period, the U.S., under the guidance of Zbigniew Brzezinski, National Security Advisor to President Jimmy Carter, devised the “Green Belt” strategy. This plan aimed to cultivate a radicalized Islamic generation across the Muslim world to counter the spread of communist ideology. The U.S. intervention in Afghanistan, which radicalized certain factions and triggered the Soviet invasion, was a critical component of this strategy. Brzezinski himself proudly acknowledged this in various interviews. Turkey, a NATO ally bordering the Soviet Union, became a key theater for implementing this policy.
The military coup of September 12, 1980, marked a pivotal moment in Turkish history. Led by General Kenan Evren, the Turkish armed forces seized power under the pretext of restoring order amid escalating violence between leftist and rightist factions that had claimed thousands of lives. However, the junta’s crackdown disproportionately targeted the Turkish left—a movement distinct from Soviet-style communism, composed of liberal, educated intellectuals such as writers, artists, journalists, and thinkers. These individuals, who championed Turkish sovereignty, intellectual freedom, and democratic ideals, were perceived as a direct threat to the military’s Islamization agenda, backed by the CIA. Tens of thousands were imprisoned, tortured, or executed, while left-wing organizations were banned outright.
At the same time, the junta actively fostered Islamist groups, establishing religious schools known as Imam Hatip institutions under the guise of combating Marxism and communism. In reality, their true objective was to eliminate anyone who sought Turkish sovereignty, embraced patriotism, or valued critical thinking. Writers, artists, journalists, and intellectuals—those who dared to think independently and question authority—were viewed as existential threats to the Islamization model the military and its CIA allies sought to impose. By silencing these voices, the junta aimed to eradicate opposition to their vision of a Turkey subservient to religious dogma and foreign interests, ensuring a populace stripped of sovereign thought and resistant to enlightenment.
This paradox—a secular military suppressing liberal intellectuals while nurturing Islamist groups—laid the foundation for Erdogan’s rise and the eventual Islamization of Turkish society.
The Chaos of the 1990s: Economic Crisis and the Rise of Erdogan
The 1990s were a chaotic decade for Turkey, marked by economic instability, a Kurdish insurgency, and a revolving door of coalition governments. The 1994 financial crisis saw inflation soar, while terrorist attacks by the Kurdistan Workers’ Party (PKK) and political assassinations fueled national disarray. Successive governments, often beholden to globalist agendas dictated by the International Monetary Fund and World Bank, failed to deliver stability. This period mirrored today’s European political crises, where ideological convergence has left voters disillusioned.
Into this void stepped Erdogan, a charismatic former soccer player turned politician from Istanbul’s working-class Kasimpasa district, whose blend of populist appeal and religious rhetoric resonated with a disillusioned populace. His rise was no accident. In 1994, he won the mayoralty of Istanbul as a member of the Islamist Welfare Party (Refah Partisi), showcasing a blend of populist charisma and religious appeal. However, his early political career faced a setback in 1997 when the military, acting as guardians of Turkey’s secular Kemalist legacy, forced the resignation of Welfare Party Prime Minister Necmettin Erbakan in what was dubbed a “postmodern coup.” Erdogan’s imprisonment in 1998 for reciting a divisive poem only solidified his image as a martyr among his devout supporters.
The 2001 Crisis: Neocons, Economic Sabotage, and Erdogan’s Ascendancy
Erdogan’s true ascent began amid Turkey’s devastating 2001 financial crisis, which saw the economy contract by 5.7%, unemployment spike, and the Turkish lira collapse. The crisis, worsened by IMF-mandated austerity measures, discredited the ruling coalition under Prime Minister Bulent Ecevit. A staunch nationalist, Ecevit had spearheaded Turkey’s 1974 intervention in Cyprus and forced Syria to expel PKK leader Abdullah Ocalan in 1999. His refusal to align Turkey with the impending U.S.-led Iraq War in 2003 made him a liability for U.S. neoconservatives, who were already preparing for the conflict.
Far from a mere economic downturn, the 2001 crisis was a deliberate strategy orchestrated by the global Western financial cartel to destabilize Ecevit’s nationalist government. This administration, fiercely protective of Turkish sovereignty, had unequivocally opposed Turkey’s involvement in the Iraq War. To eliminate this obstacle, the financial cartel—comprising international financial institutions and Western-backed actors—engineered the crisis by exploiting Turkey’s reliance on hot money and Western financial support. The resulting economic collapse eroded public trust in the government and existing political parties, creating a power vacuum that paved the way for Erdogan. Handpicked by the globalist cabal as their new proxy, Erdogan was positioned to advance their political agenda in Turkey. The neocons viewed him as a pliable ally: a moderate Islamist who could pacify Turkey’s religious conservatives while advancing Western interests. Despite resistance within his own party, Erdogan advocated for Turkish involvement in the Iraq War, though the Turkish Parliament, with the help of dissidents in his party, ultimately rejected U.S. troop deployments in 2003. Nevertheless, Erdogan remained loyal to his neocon backers and globalist patrons, privatizing state assets at rock-bottom prices—akin to Yeltsin’s controversial reforms in 1990s Russia—and deepening Turkey’s economic dependence on the EU and the U.S.
In addition to tying Turkey’s economy to Western interests, Erdogan targeted the Turkish military in 2007 through the Ergenekon and Sledgehammer trials. Widely criticized as show trials orchestrated with the help of the Gulen movement—a shadowy Islamic network led by Fethullah Gulen—these cases imprisoned or sidelined hundreds of officers, including navy admirals opposed to NATO’s Black Sea ambitions. These officers had long argued that NATO’s mission ended with the fall of the Soviet Union and advocated for closer ties with Russia and China. They also opposed plans to integrate Georgia and Ukraine into NATO, fearing it would destabilize the region and turn the Black Sea into a battleground between the West and Russia. By weakening the navy and sidelining its dissenting admirals, Erdogan brought Turkey back in line with NATO’s strategic objectives, enabling the neocons to advance their plans for NATO expansion into the Black Sea region—a move that set the stage for the 2008 Russo-Georgian War and the 2014 Ukrainian crisis.. Without this internal coup against the Turkish military, these events might have unfolded differently—or not at all.
For his services to the globalist agenda, Erdogan was portrayed in Western media as a democratizing hero, and Turkey’s economy was praised for its growth and strength. However, the reality was starkly different. To understand the globalist propaganda surrounding Erdogan, consider Barack Obama’s first foreign visit as U.S. president: a trip to Turkey in 2009. In a speech to the Turkish Parliament, Obama praised Erdogan’s “democratic reforms” and the strength of Turkey’s economy—which was growing steadily only due to cheap credit provided by international financial institutions serving the same globalist interests Erdogan represented. Meanwhile, journalists and dissidents filled Turkish prisons.
The 2016 Coup Attempt: Erdogan’s Break with the West
Erdogan’s honeymoon with the West soured in the 2010s. His support for Egypt’s Muslim Brotherhood and his interventionist stance in Syria clashed with U.S. priorities, especially after the Arab Spring upended regional alliances. Sensing Erdogan’s growing autonomy, the neocons turned to Fethullah Gulen, a cleric living in Pennsylvania since 1999 with close ties to the CIA and the Clinton Foundation. Gulen’s Hizmet movement, once an ally in Erdogan’s rise, had infiltrated Turkey’s police, judiciary, and military, creating a “parallel state.”
The July 15, 2016, coup attempt—marked by rogue military units bombing parliament and nearly capturing Erdogan—was orchestrated by factions of the Gulen movement within the army, with the involvement of the CIA and NATO, using Incirlik Air Base as one of the primary command centers to coordinate the operation (one of NATO’s largest military bases in the region). The timing suggests that the neocons, anticipating Hillary Clinton’s presidency, planned to install Gulen as their new puppet in Turkey. As a radical Sunni leader hostile to Iran, Gulen could have aligned Turkey with a broader anti-Iranian axis, potentially dragging the country into a regional war against Iran—much like Saddam Hussein did three decades earlier.
The coup’s failure, quashed by loyalists and public resistance, marked a turning point, leading Erdogan to purge over 100,000 civil servants and consolidate his power through a 2017 referendum and pivoting toward Russia and China—not out of conviction, but as leverage against Western abandonment.
Turkey’s Geopolitical Balancing Act: Ukraine, NATO, and the Black Sea
Erdogan’s post-2016 flirtations with Moscow—evidenced by the purchase of Russian S-400 systems and energy deals—reflect more than a pragmatic balancing act. They reflect a desperate attempt to regain Western attention, akin to dating someone new to make an ex jealous, aimed at convincing the West not to write him off.
The Ukrainian crisis, escalating with Russia’s 2022 invasion, has pushed Turkey into a delicate role. As a NATO member controlling the Bosphorus, Erdogan has mediated grain deals and prisoner swaps, leveraging Turkey’s strategic position. Yet his reluctance to fully back NATO’s hardline stance has further alienated him from the West, making him a target for a potential regime change operation as the West has grown desperate to win its proxy war against Russia. As a result, international media and globalist factions have intensified efforts to undermine his regime, seeking to remove him from power.
Turkey at a Crossroads: Imamoglu, Erdogan’s Decline, and the Future
Erdogan has fulfilled his mission: he has made Turkey’s economy dependent on the West, eliminated patriotic voices in the military, dismantled the parliamentary system, wrecked the education system, and buried the secular Turkish republic. His legacy is a deeply polarized Turkey: economically dependent on the West, militarily weakened, and institutionally hollowed out.
Corruption scandals, a collapsing lira, and authoritarian excesses have fueled widespread public discontent. Yet, rather than addressing the root causes of this anger—economic hardship, growing authoritarianism, and systemic corruption—Erdogan has grown increasingly paranoid, attributing every challenge to Western conspiracies and interventions. This refusal to confront reality has only deepened the divide between him and the Turkish people, fueling widespread disillusionment and anger.
Imamoglu’s rise—winning Istanbul in 2019 and 2023 despite blatant election irregularities, systematic government interference, censorship, and the full force of Erdogan’s authoritarian machinery—stands as a testament to his resilience and the enduring hope of Turkey’s opposition. Facing a system rigged to ensure his defeat, Imamoglu triumphed against overwhelming odds. Erdogan’s regime spared no effort, leveraging state media, the judiciary, and security forces to manipulate the results, yet it could not prevent Imamoglu’s victories in Istanbul, which shattered the illusion of invincibility surrounding Erdogan’s rule. His recent imprisonment on fabricated charges ahead of the 2028 elections underscores Erdogan’s desperation to suppress this threat, further alienating a populace yearning for change.
Turkey now stands at a crossroads. The powers that once propelled Erdogan to prominence—U.S. neoconservatives and the Islamist legacy of the 1980 coup—have lost control of their creation. His fall from Western favor, tied to the 2016 coup attempt and his regional overreach, has left him isolated, oscillating between East and West while clinging to power as domestic anger reaches a boiling point. Whether Imamoglu or another leader emerges, Turkey’s post-Erdogan era will face the monumental task of rebuilding its secular republic and defining its role in an increasingly complex global landscape.
Turkey’s struggle is not just its own—it is an example of the suffering endured for decades under Western colonialism and a parasitic financial order. This system, designed to enrich a handful of elites in the West, thrives by exploiting the Global South, perpetuating poverty, and engineering chaos to maintain control. Turkey’s fight for self-determination stands as a beacon for all nations seeking to break free from the chains of neocolonialism and reclaim their rightful place in a just and equitable global order. The future must be built on the sovereignty of nations, free from the selfish designs of a Western oligarchy.
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ 233e10e1:d45c3bb8
2025-04-12 20:24:35
@ 233e10e1:d45c3bb8
2025-04-12 20:24:35Here I try to tie this fictional history back to our own reality, illuminating why, even if the Gold Standard had been restored, where the invention of Bitcoin might still be inevitable due to the frailty of man. Bitcoin combines the scarcity and immutability of gold with the efficiency of digital settlement. In a world that promotes low time preference, stable value, and secure transactions, Bitcoin stands as the logical evolution of monetary technology.
-
 @ 872982aa:8fb54cfe
2025-04-21 02:58:53
@ 872982aa:8fb54cfe
2025-04-21 02:58:53保存到草稿431243214321
-
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ 10fe3f70:3489c810
2025-04-12 03:53:36
@ 10fe3f70:3489c810
2025-04-12 03:53:36contract-drafting #agreement-drafting #learn-drafting #keep-learning
I am a lawyer and a teacher. I am interested in learning new things every day.
I am from India, and have studied in a reputed law school in Delhi. I have long experience of working as in-house counsels to some reputed organisations.
My present goal is to teach drafting of contracts. What I will teach is some basic skills required by students to draft contracts.
I did some freelance online teaching during Covid Pandemic, and found that students are very interested in learning the craft. But, I also understood that they may not have enough free time to learn due to busy schedule.
If you are interested, you can access my curated playlist on Youtube
Keep watching this space, if you wish to know more...
Lessons on Contract Drafting
- Contract Drafting - An Introduction
- ...
-
 @ cb4352cd:a16422d7
2025-04-21 11:17:41
@ cb4352cd:a16422d7
2025-04-21 11:17:41What happens when artificial intelligence meets Web3? It's no longer just an idea — it's happening, and it's reshaping how we think about applications, economies, and communities online.
AI-as-a-Service in Web3
One of the clearest signs of this shift is the rise of decentralized AI marketplaces. Projects like Bittensor show that users can contribute machine learning models and earn rewards in cryptocurrency.
Another example is Gensyn, linking AI developers to decentralized compute resources.
Verifying AI with Blockchain
Blockchain helps verify AI outputs. Initiatives like Oraichain and Fetch.ai ensure AI agents interact securely and transparently in decentralized ecosystems.
AI-Driven Decentralized Organizations
Projects like SingularityNET explore AI marketplaces and autonomous governance models, creating new possibilities for decentralized coordination.
Generative AI in Web3 Content Creation
Platforms like Alethea AI are building intelligent NFTs that adapt to user interactions. AI-generated quests and dynamic worlds are reshaping GameFi.
The Road Ahead
Beyond Banking Conference by WeFi will spotlight how AI and Web3 are converging to redefine ownership, collaboration, and the very nature of the internet.
The question isn't whether AI and Web3 will merge — it's how quickly their union will reshape everything we know about digital life.
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ 502ab02a:a2860397
2025-04-21 02:26:09
@ 502ab02a:a2860397
2025-04-21 02:26:09เรามาดูกันครับว่า Precision Fermentation ของ Perfect Day เค้าใช้อะไรเป็นกำลังสำคัญในการหมัก ให้ได้สินค้ามูลค่ามหาศาล ท้าวความกันก่อนว่า Perfect Day เป็นบริษัทที่ผลิต เวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว ด้วยการใช้จุลินทรีย์
Microflora ฟาร์มวัวยุคใหม่ ที่ไม่มีวัว ถ้าคุณเคยดูสารคดีธรรมชาติ แล้วเห็นภาพป่าดิบเขียวชอุ่มที่แต่ละสิ่งมีชีวิตทำหน้าที่ของมันอย่างกลมกลืนกัน ทั้งแมลงที่บินไปมา เชื้อราที่แอบฝังรากอยู่ใต้ใบไม้ หรือจุลินทรีย์ที่ไม่เห็นด้วยตาเปล่าแต่ทำงานหนักอยู่ใต้ดิน... โลกของ microflora ก็ไม่ต่างอะไรกับ “จักรวาลจิ๋ว” แบบนั้นเลย
Microflora คืออะไร? microflora เป็นศัพท์ที่นักวิทยาศาสตร์ใช้เรียกสิ่งมีชีวิตขนาดจิ๋วที่มองไม่เห็นด้วยตาเปล่า แต่มีชีวิตจริงๆ แบบครบสูตร คือเจริญเติบโตได้ แบ่งตัวได้ กินได้ เหมือนสิ่งมีชีวิตอื่นๆ เป๊ะๆ มาจาก micro กับ flora
พอพูดถึงคำว่า “flora” บางคนอาจนึกถึงต้นไม้ แต่ในความหมายนี้ มันกว้างกว่านั้นมาก เพราะ “microflora” ไม่ได้จำกัดแค่พืช แต่หมายถึงสิ่งมีชีวิตจิ๋วจากหลากหลายอาณาจักรในธรรมชาติ เช่น ฟังไจ (Fungi) — ไม่ใช่แค่เห็ดที่เรากินกัน แต่รวมถึงเชื้อราจิ๋วที่อยู่ในดินและอากาศ ที่เก่งเรื่องการปล่อยเอนไซม์ย่อยอาหารนอกตัว แล้วดูดสารอาหารเข้าไป แบคทีเรีย (Bacteria) — นักแบ่งตัวมือโปรที่อยู่ในทุกที่ตั้งแต่ดินในสวน ยันในลำไส้เรา โพรทิสต์ (Protists) — กลุ่มที่เหลือๆ ที่ไม่เข้าพวกกับใคร เช่น สาหร่ายบางชนิด หรืออะมีบา
microflora เหล่านี้เหมือนพนักงานจิ๋วที่ทำหน้าที่เฉพาะทาง บางตัวเก่งเรื่องสร้างโปรตีน บางตัวสร้างไขมัน บางตัวสังเคราะห์วิตามินเก่งสุดๆ เลยกลายเป็นขุมพลังที่มนุษย์เริ่มหันมาใช้มากขึ้นเรื่อยๆ
ความสัมพันธ์ระหว่างมนุษย์กับ microflora ไม่ใช่เรื่องใหม่เลย เราหมักเบียร์ ทำโยเกิร์ต ดองกิมจิ และทำซีอิ๊วจากถั่วเหลืองด้วยกระบวนการที่เรียกว่า “fermentation” หรือ “การหมัก” มานานหลายพันปีแล้ว ซึ่งเป็นการอาศัยพลังของจุลินทรีย์ธรรมชาติให้สร้างรสชาติ วิตามิน หรือย่อยของที่เรากินให้ดูดซึมง่ายขึ้น แต่วันนี้โลกไปไกลกว่านั้นมาก เพราะเราสามารถสอนจุลินทรีย์ให้ผลิต “โปรตีนเฉพาะแบบ” ได้ตามต้องการ กระบวนการนี้เรียกว่า Precision Fermentation หรือ “การหมักแบบแม่นยำ” ฟังดูเหมือนห้องทดลองของ Iron Man เลยเนอะ
Perfect Day ใช้วิธีนี้ในการผลิต เวย์โปรตีน แบบไม่ต้องรีดนมจากวัวเลยสักหยด ด้วยการใช้ “เชื้อราจิ๋ว” ชนิดหนึ่งที่มีชื่อสายวิทยาศาสตร์ว่า Trichoderma
ทำไมต้อง Trichoderma? เจ้า Trichoderma ไม่ใช่เชื้อราหน้าตาน่ากลัวแบบในหนังสยองขวัญ แต่มันคือเชื้อราที่อยู่ในดินมานานกว่า 70 ปีแล้ว และเป็นที่รู้กันในวงการวิทยาศาสตร์ว่า มันเก่งเรื่องการผลิตเอนไซม์ที่ย่อยไม้ ย่อยใบไม้ ย่อยสิ่งมีชีวิตอื่นในธรรมชาติได้อย่างมีประสิทธิภาพ จึงเป็นเหมือน “โรงงานย่อยอาหาร” ชั้นเลิศ
นักวิทยาศาสตร์ของ Perfect Day เห็นแววก็เลยจับมันมา “ฝึกงาน” ใหม่ โดยใช้กระบวนการที่เรียกว่า strain engineering หรือ “การออกแบบสายพันธุ์” พูดง่ายๆ ก็คือ ใส่รหัสพันธุกรรม (เหมือนคำสั่งงาน) เข้าไปให้มันผลิตโปรตีนจากนมได้ เช่น beta-lactoglobulin ซึ่งเป็นโปรตีนตัวหลักของเวย์ในน้ำนมวัว
เมื่อ Trichoderma อ่านคำสั่งนี้ออก มันก็เริ่มเดินเครื่องผลิตโปรตีนตามที่เราสั่ง เหมือนเป็น “วัวในห้องแล็บ” ที่ไม่มีเสียงร้อง ไม่มีปุ๋ยคอก และไม่ต้องเลี้ยงด้วยหญ้า
microflora = วัวจิ๋วยุคใหม่
ลองจินตนาการว่าถ้าในอดีตเราต้องเลี้ยงวัวจริงๆ เพื่อให้ได้โปรตีนจากนม วันนี้เราใช้แค่จุลินทรีย์จิ๋วในถังหมัก แล้วป้อน “อาหาร” ให้มันเป็นน้ำตาลจากพืช (เช่น ข้าวโพด !!! เป็นง่ะ ข้าวโพดอีกแล้ว) มันก็จะเปลี่ยนคาร์โบไฮเดรตเหล่านั้นให้กลายเป็นโปรตีน หรือไขมัน หรือสารที่เราต้องการได้แบบแม่นยำ
microflora ไม่ใช่สัตว์ แต่ก็ทำหน้าที่แทนสัตว์ได้ พวกมันไม่มีสมอง ไม่มีระบบประสาท ไม่รู้สึกเจ็บ ไม่เบื่อ ไม่หิวข้าว ไม่ต้องการวันหยุด แต่มันมี “ความสามารถ” ที่เราสามารถดึงมาใช้ให้เกิดประโยชน์ได้อย่างน่าทึ่ง
ข้อดีของ microflora -เลี้ยงง่าย แค่ให้คาร์บ (จากพืช) ก็พร้อมทำงาน -ไม่ต้องใช้พื้นที่เยอะ ผลิตในถังหมัก ไม่ต้องใช้ทุ่งหญ้ากว้างๆ แบบฟาร์มวัว -ควบคุมคุณภาพได้ ผลิตโปรตีนได้สม่ำเสมอ ปราศจากสารก่อภูมิแพ้หรือยาปฏิชีวนะ -ลดการปล่อยก๊าซเรือนกระจก เพราะไม่ต้องเลี้ยงสัตว์ที่ปล่อยมีเทน
microflora จึงเป็น “เพื่อนร่วมงานที่เล็กที่สุด” แต่ก็อาจจะทรงพลังที่สุดในครัวของอนาคต และแม้เราจะยังยึดมั่นกับ animal-based diet อยู่ แต่ผมคิดว่าเรื่องนี้ก็น่าสนใจในฐานะ เทคโนโลยีที่กำลังท้าทายโลก fiat food อีกแนวทางหนึ่ง เพราะมันไม่ใช่พืชประดิษฐ์ ไม่ใช่แป้ง+สี+กลิ่น+สารพัด additive แต่คือ “การสร้างโปรตีนแท้” ด้วยความรู้ทางวิทยาศาสตร์ ที่เอื้อให้มนุษย์เลิกพึ่งวัวโดยตรง
ไม่แน่ว่าวันหนึ่ง แทนที่จะมีฟาร์มวัวเลี้ยงวัว 500 ตัวเพื่อผลิตเวย์ 1 ตัน เราอาจมีแค่ถังหมัก 1 ถัง ที่เลี้ยงเชื้อรา 500 ล้านตัว แล้วได้เวย์โปรตีนคุณภาพเดียวกัน...โดยไม่ต้องมีเสียง "มอ" เลยสักแอะ
แต่คำถามสำคัญคือ เราจะมีฟาร์มนั้นได้ไหม หรือได้แต่ทำหน้าที่ซื้อนมมารับประทานเท่านั้น
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ e111a405:fa441558
2025-04-11 17:15:58
@ e111a405:fa441558
2025-04-11 17:15:58Meritocracy without equality is basically a ladder with missing steps, which only the fortunate few can climb. The rest is basically left at the ground to gaze up.
Furthermore, a pure focus on meritocracy can become a weakness if it’s a zero-sum game. While talents thrive in systems that value it, without fairness, you ultimately get exploitation, resentment, or fragility.
Ergo: meritocracy needs to be balanced with equality, and equality needs to be balanced with meritocracy.
In a meritocratic system, you basically need that the fortunate and the able are compassionate towards those less fortunate and able.
If you are more on the libertarian side, you need the fortunate individuals to compete as capitalists and then be socialists within their communities and families.
If you prefer a state, then the state must encourage meritocratic contribution of everyone that is able, to the best of their ability, while balancing it with a fair welfare system that nurtures and supports those less able and fortunate.
I think this is something Germany did historically quite well, but at one point we lost the balance: we lost the culture of merit by putting too much emphasis on equality – even to a point that Germany now cares for millions of non-citizens that never contributed, when it should instead demand these individuals to contribute to the best of their ability.
If we want to have a state, then we don’t want a welfare state, and – I think – we should also not want a pure capitalistic state. We need balance and thus a social meritocracy.
-
 @ e39d100f:d27602e5
2025-04-21 02:28:33
@ e39d100f:d27602e5
2025-04-21 02:28:33A 5GBet tem se destacado cada vez mais no cenário brasileiro como uma plataforma completa de entretenimento online, oferecendo aos usuários uma experiência repleta de emoção, segurança e diversidade de jogos. Seja você um jogador iniciante ou experiente, a 5GBet proporciona uma navegação intuitiva e um ambiente confiável para quem busca diversão sem sair de casa.
Desde o primeiro acesso, é fácil perceber que a 5GBet se preocupa com a experiência do usuário. O design do site é moderno e responsivo, adaptando-se perfeitamente a computadores, tablets e celulares. Isso garante que os jogadores possam se divertir a qualquer momento, de qualquer lugar.
Outro ponto forte é a segurança. A plataforma utiliza tecnologia de criptografia avançada para proteger os dados dos usuários, além de contar com métodos de verificação de identidade para garantir transações seguras. Tudo isso contribui para um ambiente confiável, onde o jogador pode focar apenas na diversão.
Variedade de Jogos para Todos os Gostos Na 5gbet , a variedade de jogos é um dos principais diferenciais. O site oferece uma extensa seleção de opções, desde os clássicos jogos de mesa até slots modernos com gráficos impressionantes e temáticas envolventes. Os jogadores podem escolher entre diversos estilos e dinâmicas, o que torna a experiência muito mais rica e personalizada.
Os jogos de cartas, como o pôquer e o blackjack, são populares entre os usuários mais estratégicos. Já os slots oferecem uma jogabilidade mais leve e dinâmica, com recursos interativos e animações cativantes. Há também jogos com crupiês ao vivo, que proporcionam uma experiência ainda mais imersiva, com transmissão em tempo real e interação com outros jogadores.
Experiência do Jogador: Intuitiva e Recompensadora A experiência do jogador na 5GBet é cuidadosamente pensada para ser fluida e gratificante. O processo de cadastro é rápido, e os métodos de depósito e saque são variados, incluindo opções populares como PIX, transferência bancária e carteiras digitais. Além disso, o suporte ao cliente está disponível para tirar dúvidas e resolver questões com agilidade, seja via chat ao vivo ou e-mail.
Outro destaque é o sistema de recompensas e promoções oferecido aos jogadores. Desde bônus de boas-vindas até promoções recorrentes, a 5GBet valoriza seus usuários ativos e oferece incentivos para tornar a jornada ainda mais empolgante.
A comunidade de jogadores também é bastante ativa, e a plataforma frequentemente promove torneios e desafios, permitindo que os usuários testem suas habilidades e interajam com outros entusiastas.
Conclusão A 5GBet se consolida como uma excelente opção para quem busca entretenimento online com qualidade, segurança e muita variedade. Com uma plataforma bem estruturada, jogos empolgantes e uma experiência de usuário impecável, é fácil entender por que cada vez mais brasileiros escolhem a 5GBet como seu destino de diversão online. Se você ainda não conhece, vale a pena explorar e descobrir tudo o que essa plataforma tem a oferecer.
-
 @ 8671a6e5:f88194d1
2025-03-21 13:38:50
@ 8671a6e5:f88194d1
2025-03-21 13:38:50As old people tend to say:\ \ *nasal voice* “Back in my day…” … Bitcoin was this wild, beautiful thing, new. It was something technical that came alive before our very eyes after running a node (just a .exe running on a windows machine in my case).\ Even when you started to painstakingly mined bitcoin on a GPU, in a pool, you felt like growing a network of like minded people, or at least people who thought there was something there. Even if we couldn’t comprehend what it all would lead to (or what fiat value it could reach).\ Then came the first paper wallets, the first good software wallets and attempts at hardware wallets, the first buzz of owning your own value — it was motivating and rewarding. The look on the face of other people you explained bitcoin to, when they’ve seen their first transaction pop up after validation. Awesome.\ \ Back then, it wasn’t about fiat gains or slick marketing campaigns; it was about a distributed network “generating” numbers, keeping a distribute ledger “in synchronization”, at the same time it was a middle finger to the system, representing freedom to transact in value we valued ourselves because of the underlying network of people, nodes and miners.\ \ It was this sort of secret handshake between tech minded people, anti-globalists, anarchists, nerds and rebels who saw the fiat scam for what it was.\ Orange-pilling wasn’t even a term; it was just what you did.\ You'd walk people through the setup of bitcoin core, and the white paper, told them why central banks are a trick that functions as a legalized Ponzi scheme and you showed them bitcoin’s workings without middlemen.\ You played around with bitcoin, person to person, no bullshit, no subscriptions, no suits, no posing like a big shot, no referral links.\ Those were the fun times — pre-Saylor, pre-nation-state hype, pre-every Laura, Luigi, and self-proclaimed “OG” thinking they’re going to conquer the world.\ I miss that.
But times change.
\ The good ol' days are dead
It’s not the first instance in our lifetime that we see things pop-up, being invented, and where some good new idea becomes a reality and then that very good idea becomes an institution (there’s an obscure 1990s movie reference for you).\ We live and learn, just like the first technical people setting up their own point of presence internet servers, we all have to learn how to grow and adapt.
Early Bitcoiners didn’t have referral links or corporate sponsors — they had a mission, and the spirit came from within themselves and from the math and tech they’ve seen at work in practice. And yes, educating about it was important, as was looking for ways to improve bitcoin (the early years weren't exactly main-stream material for example).
From that learning yourself about Bitcoin and feeling the need to share and convince others around you, came the need to talk and learn together with others.
You’d talk your buddy into installing a wallet over a coffee, maybe show your uncle how to buy a few bitcoin, and it felt like planting seeds for something real.
Even if they didn’t get it—“So this number goes from my address to your address?”—you kept explaining and showing.
Then the suits rolled in. Bigger companies wer started, like Blockstream, Trezor, Coinbase and Binance.
Wall Street, Saylor with his infinite buy tweets, El Salvador and its volcano bonds, the US ETF approval — and the game changed, everyone heard about it one way or another. That’s damned important! You’re NOT the bringer of news.\ \ Suddenly, it wasn’t grassroots anymore; it was headlines, hype and game-theory. As predicted by so many in the space.\ Fine, whatever, it's progress or something else, but we as bitcoiners need to adapt to that reality.\ Some adaptations will also cause us to put energy elsewhere than before.\ What worked in 2012 or 2016, might not work anymore after 2024.\ ”We bitcoiners route around problems.” Right?
You didn’t need new people to create an account, or be part of a ‘squad’ or team, you certainly didn’t need them to sell merchandise. You just showed them bitcoin’s inner workings.\ \ Bitcoin was the marketing, the engine, the product and the goal. Bitcoin was the core. Just like digital communication was the core of the earliest internet enthusiasts. The magic of sending a text into the network, and through clever routing, someone thousands of miles away could read it almost immediately, that was the magic, the core.
Sending value with bitcoin has that same magical way, immutable, uncensored, unconfiscatable, with proven digital scarcity and forced honesty.
Nowadays we have so-called orange-pillers.\ They’re trying to spread those values. Or so they should..
They didn’t get the memo on Bitcoin becoming more commonly known apparently, and if they did, their lust for dopamine has long replaced that with their urge to get people to install a lightning wallet. It’s sometimes rather disturbing to see this Orange Pill’ing play out.
They’re out there, like they’re stuck in 2013. But they’re usually not from 2013 at all, more like class of 2020’ish. Not that it matters, they’re still living in the illusion that there are people out there that didn’t hear of bitcoin and that THEY and THEY alone can save these poor souls.\ After 2018 it’s safe to say that that’s not the case.\ I’ll repeat that for the die-hard orange-piller: they do not need you to hear about bitcoin.
These Orange Pillers have another kind of magic happen:
While they’re winning over new souls into bitcoin, one barber, taxi driver and babysitter at a time, they get the small electric charge in their brain that tells them their wealth, their (and their holding's) value will go up somehow. They’re also desperate to make some kind of connection with other bitcoiners, and while they lack that connection, they try to find (or make) new bitcoiners around them.\ This approach might have worked in the past, but things are different now. You’re usually talking to people who you try to convince of something they’ve already rejected (often harshly rejected) or never will care about .\ Most people, do not give a damn about inflation or how that came to be. Certainly when they’re doing their job.\ \ It’s like someone shoving the book of a cult under your nose and trying to convince you it’s going to save your life. You’re not open to it, neither are most of the Orange pill targets to your bitcoin gospel.\ Orange Pillers don’t see how the very people they try to convince today weren’t “in it” for a variety of (good for them) reasons. Unlike in the old days, where people’s natural state was “not heard of bitcoin”; since it was new, and people genuinely didn’t learn about it or read into it.\ That’s however, not the case today. That taxi driver? He heard about bitcoin. Be sure.
Such new people today, are almost non-existing, they either bought some long ago, got rekt trading shitcoins and stayed away.\ That, or they found it all a bit too “iffy” (thank you mainstream media) and will politely hold back from not yelling to your face, “I don’t care about that Bitcoin stuff!”.\ They know it’s some form of money or value, they know it exists. Which makes orange pillers the bringers of old news to the bottom of the barral.\ They might get a “hit” now and then of course. But even then, your impact is neglectable in a world that rewards cowardice and short term greed. You’re too late. You don’t scale. And it doesn’t matter.
Since 2020, it has shifted from genuinely introducing people to bitcoin to just "spreading it for the sake of spreading it."\ It looks more and more like an old lion, pacing back and forth in a cramped cage at an old ZOO, restless and frustrated.\ There’s just empty repetition.
The mental breakdown of orange-pilling
\ Let’s look a little further into the act of orange pilling.\ \ It's not like a 1990s hacker type showing a brand new Hayes -compatible modem to his buddy and trying to get a connection going to a local Point of Presence to get internet access.\ \ It’s more like showing your holiday pictures to an uninterested family member. All to get the dopamine hit, the ‘aha moment’ out of someone is now your own ‘aha got someone new’ moment. Like an addict looking for that next high.\ \ You want them to get the app, get some sats and feel the same feeling you have. While they’re worrying about cleaning a table for example, or getting your bill.\ \ This “badge of honor” of Orange Pilling someone is that little shot of dopamine many people need (especially in group) to feel validated.\ The real feeling has everything to do with social conformity1 and the involved brain areas that get stimulus shots and increased activity.2\ \ Above that, for the sake of the mental reward, some people go further down the social boundaries. That’s why orange pilling, often comes across as pushy, unnatural and/or annoying.\ It’s because it’s basically an activity with all the neuro stimulus of an addiction, or done as an ego boost.
Math based
On top of all of that. If you do the math on it the whole action becomes even more ludicrous.\ \ The math in the early days of bitcoin was simple: there was exponential expansion of the number of bitcoiners.\ Purely for bitcoin, the growth in numbers is still going strong, but the percentage has now naturally been flattened out because of media coverage, scams that trick people into other stuff and the close to impossible way to scale the onboarding from a person to person level to larger scales (there are apps doing a good job however, but even then it spread under former bitcoin users or people already in the know on some level, like former shitcoiners).\ \ So even at the rate of trying to orange-pill let’s say 10 people per week (many bitcoiners don’t even tàlk to 10 people a week, let alone convince them to use bitcoin).\ \ When hypothetically 50% of these people (not unusual with word of mouth recommendations) actually install the app you recommended, and we take also a high percentage of 10% actually do a regular buy of bitcoin after installing any of these apps (Strike or Blink or any other).\ \ Given that hypothetical high rate of 10 people a day plus the conversion rate, it would take approximately 200 weeks, close to four years (pun intended) to reach 2000 people as a critical mass that actually installed and used the bitcoin app.\ \ If these 2000 people all buy for about 1000$ worth of bitcoin each, they’ll be good for about 2 million dollars in bitcoin buys over a four year period.\ Even if you take very, very optimistic statistics this, you’ll get a close to zero impact, safe for the occasional big shot you might encounter and converts into a mini-Saylor, or the occasional person you might have saved a few thousand dollars (because they all keep thinking in fiat terms anyway).\ \ But on the other side, people with +100 million dollars to spend will surely have advisors and in-house knowledge, to not having to to rely on your sorry ass explaining bitcoin or installing Wallet of Satoshi on their phone or something.\ \ That’s all peanuts. It’s futile. And you’re fighting an honorable battle from 11 years ago.
### \ Why
I can't grasp why so many people keep doing this the way they do.
Orange-pilling mostly works when the price is going up anyway, unfortunately.
However, when BTC’s up 15% in a week, everyone’s a genius and your coworker suddenly can be all ears about “sound money” and future price gains.
When it’s crashing or flat? Good luck, nobody cares among the normies, unless the “orange-pillee” (the target) has their own ulterior motives for listening (like getting someone to at least give them some attention in any form).
And by the way, to come back to these taxi drivers you try to convince… many taxi drivers already had their share of die hard bitcoiners in their car, and got the explanation. Some of them even act like total noobs probably to get some sats out of your orange pilling wallet. They’re good at playing dumb, trust me.\ \ Do you really think a taxi driver in let’s say Lugano, Amsterdam or Prague didn’t already know bitcoin before you tried to convince him to accept it? You’re not the first. At all.
Most of all, you interact with people while they’re doing their job. You’re actually interfering with their work. When a waiter in a fully booked restaurant has to halt his word and listen to you explaining how to install a lightning wallet on their old iphone that’s almost out of battery, you’re losing anyway.\ They might listen, they might even be pestered to the point they’ll install the damned app. And what do you win or achieve?\ A sparkle in your brain that says “you’re such a cool bitcoiner”?\ Then… after what’s usually a painful few minutes going through a horrible counter-intuitive interface, you get them 5000 sats or whatever over to them.
Oh and adding things like “Hey man, keep these sats for at least 4 years, it will go up in price” is just rotten as well. Just give the people a decent tip and leave. You’re not doing anyone a favor.
When the moment’s there ànd some people are clearly open to it, thèn you might add some info. Point them to an easy to use non KYC app (if there is such a thing).\ But even then, just letting someone know you want to pay in bitcoin, should be enough, WHISPER bitcoin.\ They don’t need your pushy sales pitch on top of the daily struggles they face in hospitality and retail jobs.\ \ The squads
An example,... I saw this crew, let’s name them the “Re-play” squad, they’re all wearing blue hats and have a few flyers with them from a marketing company which managed to put them to some good use at a very low expense rate.
This image is still stuck in my head, some random European country during late summer time — local Bitcoiners, along with some counterparts from other countries. The real “we’re the future” types.
Sitting on the floor at a Bitcoin party, rolling “funny cigarettes” passing a lighter, chatting and laughing about how they orange-pilled some dude in a bar.
 “Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.
“Yeah, man, I showed him how to set up a Lightning wallet in a few minutes, he’s in!”. Then taking a big puff.\
Except here’s the punchline: the guy wasn’t “in” he was probably just some horny schmuck trying to get into the pants of a woman Bitcoiner in the group, who’d flashed her … QR code at him.They’re all proud, they’re all high, they all belong to a group now … and they’re convinced they’re conquering the world one wallet at a time (they don’t do the math on that, neither should they,… ignorance is bliss).
Doing good for bitcoin has been transcended into an egotrip, and the short-lived kick in the orbitofrontal cortex3 for “doing something”, it’s the filling of a lingering emptiness.\ \ The same people move around like they’re an anthill, reminiscent of the hippie communes, until they’ve returned to their misery at home, knee deep in sorrows of the fiat world. As is the orange pilled person by they way, who’s life won’t be helped by a few sats and yet a new app on their phone. An app they’ll hardly use, unless they start to bond with the other bitcoiners in the area.
These people you target already have had all chances in the world to learn about bitcoin but are too far gone to care.\ Podcasts, books, family members that are into bitcoin, or whatever blog or online service… even the biggest shitcoin casino’s only have rather decent guides and basic explanations. There are excellent educational apps like yzer.io4 as well as the excellent lopp.net5 website by Jameson Lopp.
Convincing people one-by-one doesn’t work anymore—it’s inefficient and outdated since the price surges, media coverage, and ETF launches. Even if some are open to it, it’s a futile, unscalable solution of dread, working indirectly for the benefit of the Wall street types or some shitcoin casinos (where most “new coiners” end up).
Orange pillers, also never can “read the room”. The crew in a busy restaurant or bar isn’t waiting for any explanation about UTXOs or custodians from you!
Even if you'll hit machine-like numbers of onboarding twenty people a day (By then, you’ll need to avoid being labeled the local bitcoin village fool in your community) and assume they're all pure bitcoiners afterwards.\ Which won’t happen either as any incentive of the orange pilled people is clearly nòt long-term thinking; otherwise they would have onboarded you some 8 years ago!\ \ People are extremely lazy, and the general public usually has an attention span of about 8 seconds at best6.\ Back in the early days, you could sit people down and show another tech person for hours on end how to work with bitcoin, now more than a decade later, you have about 5 to 60 seconds tops. (most lightning wallet’s onboarding sequence easily takes 2 tot 5 minutes)
To further convince yourself how pointless Orange Pilling is today: go out and watch people on a public transport vehicle: they scroll and swipe through TikTok and Instagram. You’ll notice they’re swipe-apes, there’s no substance or reliable source of bitcoin buying power there, no bitcoin innovation will come from them, and no philosophical insights will ever be ignited in their buy-the-next-cool-sneakers-now brain. They’re not a target audience. They’re the all singing and all dancing crap of the world. They’re not convinced, Inconvincible and inconvertible.
Meanwhile, no substantial steps have been made for bitcoin, even if you get them to install that app you so desperately want them to have. Neither can you expect the no-coiners or pre-coiners (god I hate that word, it sounds kinky somehow) to do anything for bitcoin, as the gap between them and the actual positive impact they could have is too wide.\ It costs time, studying and experimenting. While these people excel at thing like: shopping, watching dime-a-dozen garbage series on Netflix, watching social media posts that don’t challenge them, and eating take-out food while score some drugs.\ \ So… to conclude the story about that dude in the bar which was so carefully orange pilled by our “Re play” squad members, he probably traded his sats for a beer by now (although that demands some form of effort in finding a recipient that has beer and wants to trade it for sats, which is unlikely) , more likely he forgot about the app altogether or he’s trading shitcoins to “make more money as greed that sets in. And he probably got that woman’s telephone number, to “talk about those bitcoins” later on at his crappy rental apartment right above a shoarma restaurant.\ \ The phrase “everyone’s a scammer” includes people who pretend to care about bitcoin just to get something out of it. Even a complete newbie or shitcoin fan will fake interest in bitcoin to seem legit. I’ve watched it happen.
Orange-pilling: the good, the bad, and the ugly
\ So onboarding devolved into this whole subculture of failure, and started to manifest itself over time as a empty motion, a series of must-do things.\ \ The Pavlovian response whenever someone is a walking opportunity for accepting bitcoin (certainly in any bar, restaurant or hotel), results in the foaming at the mouth to get them onboarded on some app or wallet.\ It’s so pointless I actually feel ashamed when I’m in a group that starts to hawk and push their lightning wallets onto unsuspecting people who just want to do their job.\ (and Lightning Wallets are so crappy to onboard people with, it’s mind numbingly stupid)\ \ To my amazement, there are actually a lot of bitcoin holders, or people that claim to be into bitcoin (especially in a bull market) who still pester random people with this kind of behavior.\ \ Some of these are trying to get them to click a referral link from a venture capital firm, in return for a few bucks (incentives these days are needed to get the groundswell going apparently), or worse even, make them install some non-custodial wallet and run into the brick wall of initial on-chain setup fees and then run away like a complete loser because they’re too cheap to fork that initial on-chain fee out for the people they’ve tried to onboard. “Yeah, like, you can buy these 100.000 sats online later if you like and thèn you can have this wallet, but at least it’s not custodial eh.. uh … My buddies are over there, I’ll see you later”.\ \ When you start to observe these people in the wild, it’s like watching a gaze of raccoons going through some neighborhood’s trash cans at night (without the playful conviction).\ Fascinating, if you’re into low-budget wildlife documentaries.
 Gaze of raccoons looking for a QR code
Gaze of raccoons looking for a QR codeIF you still want to onboard someone, point them to the right info at the right time (when thèy ask you).\ I call it “Bitcoin whispering”. #BitcoinWhispering
### \ \ Let’s quickly look at the three sort of Orange Pillers:
The pushy ideologists: The most annoying of the bunch, but at the same time the ones who mean really well. I sometimes feel sorry for them.\ No one’s safe from them. Hairdresser? “You should accept Bitcoin, man.” Bartender? “Credit cards are no goog, why not use Lightning?” Taxi driver? “Ever heard of Lightning? I can tip you in Bitcoin, man.” They’re not educating; they’re feeding their ego and their need to spread the word.
The referral grifters: More damaging to Bitcoin than shitcoiners in my opinion. They don’t care about Bitcoin’s properties; it’s just a slot machine for them. And if they understand, their short term greed and social circle dependency makes them go for spreading the word of a middleman company.\ “Sign up with my link, bro, stack those sats!”\ Their goal? A kickback and the next pat on the back from their miserable squad members.
The show-offs: The worst. They don’t know anything themselves but love the spotlight. “Yeah, I got my barber stacking sats!” Yet when it’s time to actually help onboard a business, they’re nowhere to be found. All talk, no substance. They achieve a small social circle of noob bitcoiners surrounding them, with most of them going through the shitcoin-phase shortly after or swapping off-the book gains. They’re not good for bitcoin and usually don’t stay that long anyway.\ \ The world doesn’t need your savior complex.
After the second half of 2024 if someone wanted in, they’ll find a way. And if they ask a Bitcoiner for help? Sure, we’ll point them in the right direction — most of us will help when asked (gladly so).\ But this idea that you, oh mighty orange-piller, need to swoop in and “save” people is more about you than about bitcoin.
Create a good, nice, safe (protected from scams!) environment or way to get people to the info and the other way around.\ Be there when people can ask questions, lead by example, make it work and show it. If an app is easy to use, makes sense and has no friction, then people will come. If you’re pestering people and hounding them into liking something that’s so far removed from their reality (fiat-world), they’ll be scared away and not return.
### \ Conclusion
Although I miss the old days, I also realize they ain’t coming back — when orange-pilling was just sharing a crazy new idea with someone who was open to it.
The Orange pilling space is now too keen for a large part to shove their bitcoin app in someone’s face, be it in dollars, a few sats or a discount on their next transaction fee at some multi level marketing middleman.\ This onboarding is also strangely in parallel with what shitcoiners or the most vile fiat companies do, OP’ers are too desperate for relevance so they often don’t look at the value proposition of bitcoin anymore. Filling their void got the upper hand.\ Their shot of feelgood moments needs to be filled.\ While there’s close to no impact to gain anymore on one-one-one convincing.\ The lesson to save in bitcoin, is usually lost on the people anyway, which was the last reason left to do it.\ \ Be there when people ask for help on bitcoin, build stuff, but stop the aggressive orange-pilling, it serves no purpose anymore other than your dopamine hit and a token feeling for “doing something”, and it’s a sad addiction.
Therefore in 2025, orange-pilling has become of a full-blown mental issue.
by AVB
if you like my writings : tip here
\ Footnotes:
https://journal.psych.ac.cn/xlkxjz/EN/Y2015/V23/I11/1956
https://www.frontiersin.org/journals/behavioral-neuroscience/articles/10.3389/fnbeh.2019.00160/full
https://en.wikipedia.org/wiki/Orbitofrontal_cortex
https://yzer.io/
https://lopp.net
https://theweek.com/health-and-wellness/1025836/tiktok-brain-and-attention-spans
Share
TopLatest
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40
@ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40It’s often said that 'Bitcoin doesn’t need marketing'—and the internet proves it well, almost like a daily feed. Instead of typical ads in the form of 'sell-me-anything-and-everything', the space thrives on organic memes and threads: a grassroots testament to Bitcoin ethos.
This isn’t about the artificial promotion of THE TRUMAN SHOW, where desires are manufactured and ads dictate specific behaviours. Bitcoiners don’t just reject the Proof-of-Hype, so typical in a fiat-driven world, they replace it with Proof-of-Work: value emerging not from coercion, but from consensus (i.e., what the community validates as genuine and meaningful).
The "Funny Money" Crew
On the other hand, equally common is the twist with memes labeled 'Bitcoin’s Marketing Team', featuring faces like:
🤡 Jerome Powell (Fed Chair), Christine Lagarde (ECB), Agustín Carstens (BIS chief, CBDC pusher), Janet Yellen (U.S. Treasury Secretary), Jamie Dimon (JPMorgan CEO), Elizabeth Warren (U.S. Senator), and so on.
Sophisticated jokes—appreciated by those who understand their actual impact. After all, what better advertisement for Bitcoin could there be than watching the fiat system degrade in real time? 😎
Why Bring This Up?
First, because I want to remind that Bitcoiners weaponize even simple ideas better than entire Wall Street-hired PR firms. Every "Bitcoin doesn’t need marketing" or "Thanks, Fed for the free promo!" is a clever, almost subversive way of raising topics we should be aware of. Exposing fiat’s failures often speaks louder than directly evangelizing how sound Bitcoin is—and how well it solves problems that keep many non-coiners awake at night.
Second, to credit where it’s due: Bitcoin-only projects and individuals who are actively spreading the word—hard money, real solutions, and the culture itself. But this isn’t 'marketing' in the traditional, pushy, profit-at-all-costs sense. Instead, it’s built on:
- Information (no bullshit, just facts)
- Education (orange-pilling, not upselling)
- Community (value, instead of dry PR)
- Creativity (proof-of-mind, not algo-baits)
- Experiences (how-to solutions, not showing off)
And let’s be clear: Earning money isn’t evil—it’s necessary for these projects to survive. What matters is the intention. No one should apologize for creating Bitcoin-themed ads, so long as they’re carrying the meaning, instead of being rooted in hype.
PoW: Earning Attention, Not Buying It
The list below (part one) is based on my own preferences, but it was also inspired by Bitcoin FilmFest, which—in its upcoming edition #BFF25, May 22-25—introduced a new block to the program: ‘BFF PoWies: The Show for Bitcoin-Only Advertising.’ A dedicated space for creative expression beyond films, where projects and individuals compete for awards in categories like Grand Prix, Best Visual, and Best Identity—with a $4,500 prize pool to grab.
Anyways, as our small but passionate team dug into this topic, I was really happy to uncover unique video ads, some of which I’m excited to share with you now.
If you know others, tag me (private profile) or 'Bitcoin FilmFest' directly on socials. Feel free to submit your work to the PoWies too (submissions close May 6th).
Without further ado... Let's explore the space where value is discovered, not packaged in empty promises 📺👇
Bitcoin-Video Ads: Part One.
Creative, funny, dynamic, inspirational. All four below. Enjoy!
1/. NEVER LOSE YOUR BITCOIN (Liana)
https://v.nostr.build/P7To0HpNmmB6iudR.mp4
2/. MAKE A CHANGE, (Wasabi)
https://v.nostr.build/rUGQAysAIDH8Wx9x.mp4
3/. THE MOTHER OF ALL BACKUPS (Cryptosteel)
https://v.nostr.build/3zesnSjQudQoxl5f.mp4
- FINANCIAL FALLOUT (21 Futures)
https://v.nostr.build/sFvmt8oCWfxLKJRb.mp4
PS. The most effective Bitcoin ads aren't 'typical' campaigns—they're the result of creativity, PoW, and authentic storytelling move hand-in-hand.
BTC Your Mind. Let it Beat... Şela
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ e39d100f:d27602e5
2025-04-21 02:18:40
@ e39d100f:d27602e5
2025-04-21 02:18:40O mercado de entretenimento digital no Brasil está em constante expansão, e entre as novas opções que vêm ganhando destaque, a plataforma Betao se sobressai como uma das mais promissoras. Com um ambiente moderno, seguro e recheado de atrações, o Betao oferece uma experiência diferenciada tanto para jogadores iniciantes quanto para os mais experientes.
Uma Plataforma Intuitiva e Acessível Logo ao acessar o site do Betao, o usuário já percebe a preocupação com a usabilidade. O design é limpo, responsivo e adaptado para todos os tipos de dispositivos, o que permite que os jogadores aproveitem ao máximo cada funcionalidade, seja no computador, tablet ou celular.
Além disso, o processo de cadastro é rápido e descomplicado. Em poucos cliques, o jogador já está pronto para explorar os jogos disponíveis. Outro ponto positivo é a variedade de métodos de pagamento, que incluem transferências bancárias, carteiras digitais e até opções com criptomoedas, oferecendo mais liberdade e praticidade.
Catálogo de Jogos Variado e Empolgante O Betao se destaca por seu portfólio diversificado de jogos online. A plataforma trabalha com provedores renomados do setor, garantindo alta qualidade gráfica, fluidez nas partidas e mecânicas envolventes.
Entre os destaques, estão os jogos de slots, que atraem jogadores pela combinação de simplicidade e emoção. Com temas variados, gráficos vibrantes e bônus interativos, essas máquinas virtuais oferecem diversão contínua e oportunidades de prêmios significativos.
Outra categoria bastante procurada são os jogos de mesa, como roleta, blackjack e bacará. Essas opções são ideais para quem gosta de jogos que exigem estratégia e tomada de decisões rápidas, proporcionando uma experiência desafiadora e recompensadora.
Experiência do Jogador em Primeiro Lugar No Betao, o foco está na satisfação do jogador. A plataforma investe constantemente em melhorias para garantir um ambiente justo, transparente e divertido. Um dos grandes diferenciais é o suporte ao cliente, que funciona 24 horas por dia, todos os dias da semana. Com atendimento em português e canais acessíveis — como chat ao vivo e e-mail —, os usuários recebem ajuda imediata sempre que necessário.
Além disso, o Betao promove promoções regulares, programas de fidelidade e bônus de boas-vindas que valorizam a permanência e o engajamento dos jogadores. Tudo isso contribui para criar uma comunidade ativa e satisfeita.
Segurança e Confiabilidade Segurança é um fator essencial em qualquer plataforma de jogos online, e o Betao leva isso a sério. A empresa utiliza tecnologias de criptografia avançadas para proteger os dados e transações dos usuários, além de operar de forma legalizada, com licenças reconhecidas internacionalmente. Essa transparência aumenta a confiança dos jogadores e garante tranquilidade durante toda a experiência.
Conclusão Com uma combinação de tecnologia de ponta, ampla variedade de jogos, atendimento eficiente e foco total na experiência do usuário, o Betao se consolida como uma das melhores opções para quem busca diversão e entretenimento de qualidade no universo digital. Seja você um novato ou veterano nesse meio, vale a pena explorar tudo o que a plataforma tem a oferecer.
-
 @ 87122b31:726e2c4c
2025-04-21 02:16:07
@ 87122b31:726e2c4c
2025-04-21 02:16:07BJ66 là một nền tảng kỹ thuật số nổi bật với thiết kế tối giản nhưng đầy tinh tế, hướng đến việc tạo ra một môi trường thân thiện và dễ tiếp cận cho tất cả người dùng. Ngay từ giao diện đầu tiên, BJ66 cho thấy sự chú trọng vào trải nghiệm người dùng khi mọi yếu tố được sắp xếp một cách khoa học và thuận tiện. Các tính năng chính được trình bày rõ ràng, biểu tượng minh họa sắc nét giúp người dùng dễ dàng thao tác, kể cả với những người chưa có nhiều kinh nghiệm sử dụng công nghệ. Sự linh hoạt trong cách bố trí menu, lựa chọn ngôn ngữ và chế độ hiển thị sáng – tối cũng mang đến sự cá nhân hóa tối đa cho mỗi người dùng. Nền tảng này tương thích mượt mà trên nhiều thiết bị khác nhau từ điện thoại thông minh, máy tính bảng đến laptop, tạo điều kiện cho người dùng kết nối mọi lúc mọi nơi mà không bị giới hạn bởi thiết bị hay hệ điều hành.
Không chỉ dừng lại ở thiết kế giao diện đẹp mắt và thân thiện, BJ66 còn ghi điểm mạnh mẽ ở khả năng vận hành ổn định và bảo mật cao. Với hệ thống máy chủ tối ưu và công nghệ xử lý hiện đại, các thao tác trên BJ66 diễn ra nhanh chóng, mượt mà, không bị giật lag hay gián đoạn. Người dùng có thể thực hiện nhiều hoạt động cùng lúc mà không gặp tình trạng chậm trễ hay lỗi hệ thống, đặc biệt quan trọng trong bối cảnh yêu cầu tốc độ và tính liên tục ngày càng cao. Về bảo mật, BJ66 áp dụng các lớp mã hóa tiên tiến và cơ chế xác minh đa yếu tố, bảo vệ thông tin cá nhân và dữ liệu của người dùng khỏi các rủi ro tấn công mạng. Mọi hoạt động đăng nhập, thay đổi cài đặt hay giao dịch đều được theo dõi và ghi nhận để tăng cường tính minh bạch và an toàn. Đội ngũ hỗ trợ kỹ thuật của BJ66 cũng là một điểm cộng lớn, khi họ hoạt động liên tục 24/7 với thái độ chuyên nghiệp, tận tâm và phản hồi nhanh chóng, đảm bảo người dùng luôn có người đồng hành trong suốt quá trình sử dụng.
BJ66 không ngừng đổi mới và phát triển để mang đến một hệ sinh thái số toàn diện, đáp ứng mọi nhu cầu của người dùng hiện đại. Nền tảng tích hợp nhiều tiện ích thông minh được hỗ trợ bởi công nghệ tiên tiến như trí tuệ nhân tạo (AI), cá nhân hóa nội dung và gợi ý dựa trên thói quen sử dụng. Điều này giúp người dùng tiết kiệm thời gian tìm kiếm và truy cập nhanh hơn đến các tính năng mình yêu thích. Ngoài ra, BJ66 thường xuyên cập nhật những cải tiến mới nhằm nâng cao hiệu suất, cải thiện giao diện và tối ưu hóa các chức năng, từ đó duy trì được tính cạnh tranh và giữ chân người dùng trong thời gian dài. Trong thời đại công nghệ số đang phát triển nhanh chóng, BJ66 nổi bật như một lựa chọn đáng tin cậy, nơi người dùng có thể yên tâm trải nghiệm với sự an toàn, thuận tiện và sự thấu hiểu đến từ một nền tảng luôn đặt người dùng ở vị trí trung tâm. Với sự kết hợp giữa công nghệ hiện đại, giao diện thân thiện và cam kết phát triển bền vững, BJ66 không chỉ đơn thuần là một công cụ mà còn là một phần không thể thiếu trong lối sống số hóa ngày nay.
-
 @ 87122b31:726e2c4c
2025-04-21 02:15:16
@ 87122b31:726e2c4c
2025-04-21 02:15:16WIN1 là nền tảng công nghệ hiện đại được xây dựng với mục tiêu cung cấp một không gian trực tuyến toàn diện, nơi người dùng có thể tương tác, trải nghiệm và kết nối một cách mượt mà, tiện lợi. Sở hữu giao diện trực quan, tối ưu hóa cho cả người mới bắt đầu và người dùng thành thạo, WIN1 tạo ra cảm giác thân thiện ngay từ lần đầu truy cập. Các yếu tố bố cục được sắp xếp hợp lý, màu sắc hài hòa và các biểu tượng dễ hiểu giúp việc điều hướng trở nên dễ dàng trên mọi loại thiết bị – từ điện thoại thông minh, máy tính bảng đến máy tính cá nhân. Không dừng lại ở đó, WIN1 còn cho phép người dùng tùy chỉnh không gian trải nghiệm cá nhân với các chế độ giao diện sáng – tối, ngôn ngữ linh hoạt, và các thiết lập cá nhân hóa dựa trên thói quen sử dụng. Nhờ vậy, người dùng luôn cảm thấy sự chủ động trong mọi tương tác với nền tảng.
Điểm nổi bật khác giúp WIN1 khẳng định vị thế là khả năng vận hành ổn định và bảo mật cao. Hệ thống hoạt động nhanh chóng, ổn định và có khả năng xử lý đồng thời nhiều truy cập mà không gây gián đoạn. Điều này đặc biệt quan trọng trong bối cảnh người dùng ngày càng có xu hướng sử dụng nhiều thiết bị cùng lúc để phục vụ nhu cầu công việc và giải trí. WIN1 áp dụng các công nghệ mã hóa tiên tiến và xác thực bảo mật nhiều lớp, đảm bảo dữ liệu người dùng luôn được bảo vệ nghiêm ngặt. Ngoài ra, nền tảng còn thường xuyên cập nhật và kiểm tra hệ thống để phát hiện, khắc phục kịp thời các rủi ro tiềm ẩn. Bên cạnh yếu tố kỹ thuật, WIN1 còn xây dựng đội ngũ chăm sóc khách hàng tận tâm, hoạt động 24/7, sẵn sàng hỗ trợ người dùng trong mọi tình huống từ những thắc mắc đơn giản đến các vấn đề kỹ thuật phức tạp, giúp người dùng an tâm tuyệt đối trong suốt hành trình trải nghiệm.
Không ngừng đổi mới và hoàn thiện, WIN1 liên tục tích hợp các xu hướng công nghệ tiên tiến nhằm tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nền tảng này không chỉ đơn thuần là công cụ kết nối, mà còn hướng đến xây dựng một hệ sinh thái số hóa toàn diện, trong đó người dùng có thể tận hưởng sự tương tác thông minh nhờ vào các tiện ích được tích hợp như trí tuệ nhân tạo (AI), hệ thống gợi ý cá nhân hóa và các tính năng tự động hóa thông minh. Các phân tích dữ liệu từ hành vi người dùng được sử dụng một cách linh hoạt để đưa ra đề xuất phù hợp, giúp mỗi lần truy cập vào WIN1 đều mang lại cảm giác mới mẻ và đúng nhu cầu. Đây chính là minh chứng cho định hướng phát triển dài hạn, bền vững của WIN1: luôn lấy người dùng làm trung tâm, không ngừng nâng cấp công nghệ, đồng thời đảm bảo sự ổn định và an toàn trong suốt quá trình sử dụng. Trong thời đại mà công nghệ trở thành một phần không thể thiếu trong cuộc sống, WIN1 là lựa chọn lý tưởng dành cho những ai đang tìm kiếm một nền tảng đáng tin cậy, dễ sử dụng và luôn đổi mới để bắt kịp xu hướng toàn cầu.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:08:06
@ 4ba8e86d:89d32de4
2025-04-21 02:08:06FOSS Browser é um navegador Android totalmente livre e de código aberto (freedom/libre, no sentido de liberdade). Seu código-fonte é público e o aplicativo não solicita permissões desnecessárias. Ele é baseado no WebView do Android, com o objetivo de oferecer uma navegação simples, leve, eficiente e com uma interface agradável.
FOSS Browser é uma aplicação Android para navegação na internet. Por utilizar o WebView nativo do sistema, ele não possui um motor de renderização avançado como navegadores tradicionais, o que o torna mais leve e direto ao ponto.
O FOSS Browser permite salvar configurações específicas para cada domínio, o que ajuda a proteger sua privacidade. Para cada site visitado, é possível ativar ou desativar opções como:
- Bloqueador de anúncios (AdBlock);
- Execução de JavaScript;
- Uso de cookies;
- Proteção contra fingerprinting;
- E outras opções personalizáveis.
Para sites que não têm configurações salvas, você pode ajustar um perfil padrão conforme suas preferências.
Mais recursos de privacidade:
- AdBlock integrado, com atualizações automáticas. Você escolhe o que deseja bloquear. As listas são baseadas nos hosts do projeto Steven Black - AdBlock Hosts https://github.com/StevenBlack/hosts
- Bloqueio de cookies de terceiros.
- Bloqueio de banners de consentimento de cookies.
- Habilitar ou desabilitar o preenchimento automático do Android.
- Apagar dados de navegação automaticamente ao sair do app.
- Escolher entre diferentes mecanismos de busca, ou definir um mecanismo personalizado.
- O próprio FOSS Browser não coleta nenhum dado dos usuários https://codeberg.org/Gaukler_Faun/FOSS_Browser/src/branch/master/PRIVACY.md
O FOSS Browser adota o design moderno do Material You, com suporte ao modo claro/escuro do sistema e temas baseados no papel de parede do dispositivo. A interface foi otimizada para uso com uma só mão, com todos os elementos principais localizados na parte inferior da tela.
Recursos adicionais:
- Manter a tela ligada durante a navegação;
- Abrir links em segundo plano;
- Restaurar abas automaticamente ao reiniciar o app.
Gerencie seus favoritos com filtros personalizados. Você pode nomear cada filtro como quiser. Ao pressionar e segurar o ícone de favoritos na barra de ferramentas, terá acesso rápido aos seus sites favoritos.
Gestos Personalizáveis Você pode atribuir quase 20 gestos diferentes à barra de ferramentas e aos seus botões, com suporte a quatro direções por gesto. Também é possível acionar ações ao pressionar e segurar os botões da barra, totalizando até 10 gestos diferentes para controlar o navegador.
Algumas ações disponíveis incluem:
- Carregar o último site acessado;
- Alternar entre abas;
- Recarregar a página;
- Abrir favoritos;
- E muito mais.
-Backup e Restauração
Faça backup de todos os seus dados e configurações importantes (favoritos, histórico, configurações por site, etc.) diretamente no cartão SD. Os backups também podem incluir as configurações gerais do FOSS Browser, e podem ser restaurados em uma instalação nova ou em outro dispositivo, bastando copiar os arquivos de backup.
Link Pra baixar no obtainium : https://codeberg.org/Gaukler_Faun/FOSS_Browser
Fdroid : https://f-droid.org/packages/de.baumann.browser/
https://codeberg.org/Gaukler_Faun/FOSS_Browser
-
 @ 8671a6e5:f88194d1
2025-03-15 20:50:18
@ 8671a6e5:f88194d1
2025-03-15 20:50:18Like so many people, I see ads for hardware wallets all the time in my X feed, or even when listening to podcasts you get the occasional promotion for one of these devices. Hardware wallet manufacturers and brands are a part of bitcoin life and culture. They’re sponsors, and they of course like to sell their devices.
As a long-time bitcoiner, I can say that I’ve given out more money (bitcoin) buying hardware wallets than what’s good for me. I supported projects and even had one of the prototypes of the Case wallet (fingerprint sensor, international sim-card and a camera!) in 2015/16, a thing I could hardly use, since it was bitcoin in your pocket, on-chain, before there was ANY need for that.
The point is, I love these devices. I love playing around with them. That’s fun when you’re a techie or someone who’s really onto bitcoin and wants to try the new Trezor, Ledger (yuk), Bitbox or cold card wallet… Unfortunately, except for this “obsession” with trying these devices out, and the occasional corporate/business needs,… the secure feeling of having one (or more) prevails over the real need. There’s a series of downsides to having a Hardware wallet, which are often overlooked.
The main downside is actually summed up as : “you don’t need it”
Let’s elaborate. For most people, I must say that I can’t recommend having one of these devices anymore. The market is saturated and the devices are often sold to people who are even unable to use them properly. Or customers that spent way more money buying them, than what’s eventually stored on it!
They’re of course handy “signing devices” for securely signing a transaction or message. They’re also a great way to do multi-signature and so on. That’s all neat.
But your average user,... most of the people don’t need it. There are several reasons for that.
Before the readers put me away as a fiat-slave dissing on bitcoin, or some dude trying to shill his own project: no … I don’t have my own “solution” I’m selling, I don’t go and ask you to click my referral link or ask for money here. I probably bought more hardware wallets in my life for a higher amount than most users hold in bitcoin right now. So no,... I supported this industry, I don’t hate it. I just want to voice my opinion her on the saturation of the market and the stupidity of holding your keys on a device that inherently can’t be trusted (in theory).
The reasons: 1
Bitcoin inverted effect on diminishing cash value : A bitcoin amount today buys you less than that same bitcoin amount in a few years. Let’s start with an obvious, but often forgotten reason to NOT invest in a hardware wallet. The price. The price is around 150 to 350 $ in fiat now in 2024. I even bought such devices at 600$ once (160000$ in today’s price;). Over time, most people that are into bitcoin less than 5 years, are better off buying bitcoin for the amount they would have bought the HW device for.
One can of course make the argument that it costs more to lose your keys altogether, but that’s also the case with a paper with your seed phrase or any other method.
Securing your keys is of course extremely important. No matter what you want to use. It doesn’t take away the fact that buying a Hardware wallet for fiat or for bitcoin isn’t economically wise, certainly not for beginners or people who have less bitcoin than the 20x cash value of the hardware wallet they want to buy. I have a simple formula here.
The Deadeye’s Hardware Wallet Law: which is a formula: Y < (X / 20) If you have 1 million sats today (660$ at time of writing) then it makes little sense to buy a hardware wallet for 179$ in my opinion. A good rule of thumb is: take the amount of bitcoin you want to secure, calculate the fiat price in dollar HW price = X Take the fiat price in dollar + shipping in fiat = Y If Y < (X / 20) that fiat price is less than a factor 20 of what you want to secure, then you might consider buying the HW wallet.
Example: Johnny wants to buy a new coldcard at 219$ + 41 $ shipping. He has 2,3 million sats (1524$) 260 < (1524 /20) So 260 < 76.2 … is not true , so he shouldn’t buy this and stack the sats instead on a cheaper solution (software wallet, or a self-generated seed phrase or even a reputable exchange in absolute last resort, if the tech-lever is very low)
2
Entropy - the entropy on a hardware device is delivered usually by “special chipsets” that generate a random (or close to random, as computers can’t be really random) seed phrase for you. Just like the old paper wallet generators only, they use some sort of scheme or algorithm to generate this. As a user you’ll have to trust that algo. And trust that it’s not broken by a hacker that finds the secret sauce and can generate more or less the same kind of entropy (even then, it would be extremely unlikely they would be able to re-generate your seed). But it’s a factor: the entropy a person can generate themselves (with play cards, dice, or a cat tapping a keyboard…) is always superior to some algorithm on a device Hardware itself can be fragile or downright sub-par. The hardware wallets of course exist because of the tech inside. Mainly the print board, the screen, the chipset and some even a battery(!). The hardware is NOT under your control. It’s made in a few big factories in Asia usually and even if you trust the building process completely, there’s no way for an average paranoid user to “trust” the unverifiable source of the chip design, chip manufacturing and the software that keeps the thing running.
The hardware itself is a blind trust you put into the image and reputation of a company. Some of these companies are dodgy at best from my personal perspective and opinion (nGrave, Ledger …) others have a more steady reputations and exude trustworthiness (Bitbox, …) Still… they are all just hardware, a sum of parts you don’t control and don’t verify.
When is the last time you checked the “military grade secure element chipset” in your super-duper hardware device? Where was it manufactured and who designed the chip lay-out?
3 Cycling through versions. HW wallets go through iterations and new version all the time. When you bought a coldcad Mark 1 back in the day, it’s now long obsolete. You can’t use some features and you’re even lucky if the hardware itself still functions after being in storage for +6 years. When I asked the manufacturer why they recommended outphasing the coldcard around two years ago, they said something like “it’s to keep up with security”. It even makes sense from their tech and product perspective, but in the end, it’s not really what people expect (realistic or not). Well… that’s like a subscription in my opinion? Every two years, you fork out something of 150 to 200$ for a new hardware device (plus shipping and customs) and the risk involved to put your funds on the new device by transferring to the new wallet’s addresses or put the old seed in that new device and so on… All this… to have the “right tool” for keeping 24 words “safe”? So, our formula in point 1, was adjusted to /20 to compensate for that “cycling” through versions at a rate of a few hundred dollars every 2-3 years at least. That’s a bit of the top in my opinion. A good bitcoin hardware device should at least be usable and up to par for 10 years at the very least. Words written down or secured anywhere, last forever.
4 Easy of use is still not ok: This might be very controversial with all the HW wallets claiming to be “easy to use”, but in fact: they’re not. Most users (and I take some family members and friends as an example here) can’t make heads or tails from how these things work. Give any non-tech user a coldcard, ledger of bitbox and they’ll not be on their way to use it as an everyday device. It might sound silly for the daily users of such a wallet, but a “noob” in my opinion is better off learning to familiarize themselves with software wallets first before even considering buying a HW wallet.
5 Buggy hardly tested apps The hardware wallets accompanied by an app (like Jade’s Green wallet to name one) are often introducing an extra layer of problems (both on the bugs and the risks). Who knows that this software will still be available in a few years time? We saw many things come and go over the years.
6 Alienation from the private keys: New users are better of learning the ropes with seed phrases and private keys by using Electrum, Sparrow and the likes (or even stack wallet duo) in order to learn what holding your own keys means.
People who start their journey with a hardware wallet often think about their bitcoin holding as something that tangible “inside the hardware wallet”, instead of looking at the key-perspective. I think a lot of people are alienated from the bitcoin concept of having your own keys by using HW wallets. (and yes, that’s not a strong argument, I know, but it is a factor to take into account)
7
You’ll have to securely store your seed phrase ANYWAY. The fact remains, that you bought a hardware wallet, and still have to safely secure your private keys, seed phrase at some point and do it securely. That’s something you need anyway. So… why not just use your paper with 24 words and use the wallet on occasion by using a secure “other way” (seed signer, an electrum wallet, sparrow,...) when you need to do a transaction?
I believe people will also do les on-chain pure bitcoin transactions when they need to do more work when not using a HW wallet: it’s an extra barrier to hold instead of paying. (if you like to do that of course)
8
Upgrade processes aren't always that clear on some HW wallets. I personally “bricked” a coldcard this way, by accidentally using a wrong upgrade file on a Mark 2 coldcard, and it was unrepairable after that.
The 12 or 24 words are the most important thing you have, … you don’t need a hardware device if you’re just starting, or just are a hodl’er.
9 Centralized software. Bugs and “new” features
Lots of bugs in the software also cause problems: For example; your 24 words from device A, can’t be imported to device B although they should “speak the same language” in theory (BIP39). One device accepts using two times the same word in a seed phrase, one doesn’t. There are other bugs: like random reboots, unlocking problems, strange implementations in the software (like Trezor trying out implementing the Swiss “travel rule” setting one day and pushing this upgrade to the users) and so on…. Without a HW wallet, you can just choose yourself what software / node or wallet to run anything on, and you’re not tied to the centralized, expensive and often untested way of hardware wallet manufacturer’s viewpoints and or “secret deals”.
- And then there’s the privacy concern. We all know about Ledger’s famous “mishap” where they leaked all the home addresses of hardware wallet customers .. some of them actually had to move to other places to live as a result.
Conclusion:
In my opinion; hardware wallets are toys for bored bitcoiners. And I admit I was one myself for a long time. (I am one of these people yes)
The blockstream Jade was the last hardware wallet I’ve ever bought I guess.
I’m done with the crappy interfaces, the buggy software, the ‘subscription’ to endless upgrades new hardware and the strange feeling of unease when storing something on such devices while you depend on the “open source” nature of something made in China or wherever.
There are much cheaper, easier and more secure solutions.
Hence, most people don’t need hardware wallets.
deadeyes
@avbpodcast
 imaginary Hardware wallet
imaginary Hardware walletLike so many people, I see ads for hardware wallets all the time in my X feed, or even when listening to podcasts you get the occasional promotion for one of these devices.\ Hardware wallet manufacturers and brands are a part of bitcoin life and culture. They’re sponsors, and they of course like to sell their devices.
As a long-time bitcoiner, I can say that I’ve given out more money (bitcoin) buying hardware wallets than what’s good for me.\ I supported projects and even had one of the prototypes of the Case wallet (fingerprint sensor, international sim-card and a camera!) in 2015/16, a thing I could hardly use, since it was bitcoin in your pocket, on-chain, before there was ANY need for that.
The point is, I love these devices.\ I love playing around with them.\ That’s fun when you’re a techie or someone who’s really onto bitcoin and wants to try the new Trezor, Ledger (yuk), Bitbox or cold card wallet… \ Unfortunately, except for this “obsession” with trying these devices out, and the occasional corporate/business needs,… the secure feeling of having one (or more) prevails over the real need.\ There’s a series of downsides to having a Hardware wallet, which are often overlooked.
The main downside is actually summed up as : “you don’t need it”
Let’s elaborate.
For most people, I must say that I can’t recommend having one of these devices anymore. The market is saturated and the devices are often sold to people who are even unable to use them properly. Or customers that spent way more money buying them, than what’s eventually stored on it!
They’re of course handy “signing devices” for securely signing a transaction or message. They’re also a great way to do multi-signature and so on. That’s all neat.
But your average user,... most of the people don’t need it. There are several reasons for that.
Before the readers put me away as a fiat-slave dissing on bitcoin, or some dude trying to shill his own project: no …\ I don’t have my own “solution” I’m selling,\ I don’t go and ask you to click my referral link or ask for money here. I probably bought more hardware wallets in my life for a higher amount than most users hold in bitcoin right now. So no,... I supported this industry, I don’t hate it. I just want to voice my opinion her on the saturation of the market and the stupidity of holding your keys on a device that inherently can’t be trusted (in theory).
The reasons:
1
Bitcoin inverted effect on diminishing cash value :\ A bitcoin amount today buys you less than that same bitcoin amount in a few years. Let’s start with an obvious, but often forgotten reason to NOT invest in a hardware wallet. The price. The price is around 150 to 350 $ in fiat now in 2024. I even bought such devices at 600$ once (160000$ in today’s price;). Over time, most people that are into bitcoin less than 5 years, are better off buying bitcoin for the amount they would have bought the HW device for.
One can of course make the argument that it costs more to lose your keys altogether, but that’s also the case with a paper with your seed phrase or any other method.
Securing your keys is of course extremely important. No matter what you want to use. It doesn’t take away the fact that buying a Hardware wallet for fiat or for bitcoin isn’t economically wise, certainly not for beginners or people who have less bitcoin than the 20x cash value of the hardware wallet they want to buy. I have a simple formula here.
### The Deadeye’s Hardware Wallet Law:\ which is a formula: Y < (X / 20)
If you have 1 million sats today (660$ at time of writing) then it makes little sense to buy a hardware wallet for 179$ in my opinion.\ A good rule of thumb is: take the amount of bitcoin you want to secure, calculate the fiat price in dollar HW price = X\ Take the fiat price in dollar + shipping in fiat = Y\ If Y < (X / 20) that fiat price is less than a factor 20 of what you want to secure, then you might consider buying the HW wallet.\ \ Example: Johnny wants to buy a new coldcard at 219$ + 41 $ shipping.\ He has 2,3 million sats (1524$) 260 < (1524 /20) \ So 260 < 76.2 … is not true , so he shouldn’t buy this and stack the sats instead on a cheaper solution (software wallet, or a self-generated seed phrase or even a reputable exchange in absolute last resort, if the tech-lever is very low)\ \ 2
Entropy - the entropy on a hardware device is delivered usually by “special chipsets” that generate a random (or close to random, as computers can’t be really random) seed phrase for you. Just like the old paper wallet generators only, they use some sort of scheme or algorithm to generate this. As a user you’ll have to trust that algo. And trust that it’s not broken by a hacker that finds the secret sauce and can generate more or less the same kind of entropy (even then, it would be extremely unlikely they would be able to re-generate your seed).\ But it’s a factor: the entropy a person can generate themselves (with play cards, dice, or a cat tapping a keyboard…) is always superior to some algorithm on a device Hardware itself can be fragile or downright sub-par.\ The hardware wallets of course exist because of the tech inside. Mainly the print board, the screen, the chipset and some even a battery(!).\ The hardware is NOT under your control. It’s made in a few big factories in Asia usually and even if you trust the building process completely, there’s no way for an average paranoid user to “trust” the unverifiable source of the chip design, chip manufacturing and the software that keeps the thing running.\ \ The hardware itself is a blind trust you put into the image and reputation of a company. Some of these companies are dodgy at best from my personal perspective and opinion (nGrave, Ledger …) others have a more steady reputations and exude trustworthiness (Bitbox, …) Still… they are all just hardware, a sum of parts you don’t control and don’t verify.\ \ When is the last time you checked the “military grade secure element chipset” in your super-duper hardware device? Where was it manufactured and who designed the chip lay-out? \ \ 3\ Cycling through versions.\ HW wallets go through iterations and new version all the time. When you bought a coldcad Mark 1 back in the day, it’s now long obsolete. You can’t use some features and you’re even lucky if the hardware itself still functions after being in storage for +6 years.\ When I asked the manufacturer why they recommended outphasing the coldcard around two years ago, they said something like “it’s to keep up with security”.\ It even makes sense from their tech and product perspective, but in the end, it’s not really what people expect (realistic or not). Well… that’s like a subscription in my opinion? Every two years, you fork out something of 150 to 200$ for a new hardware device (plus shipping and customs) and the risk involved to put your funds on the new device by transferring to the new wallet’s addresses or put the old seed in that new device and so on…\ All this… to have the “right tool” for keeping 24 words “safe”? So, our formula in point 1, was adjusted to /20 to compensate for that “cycling” through versions at a rate of a few hundred dollars every 2-3 years at least. That’s a bit of the top in my opinion. A good bitcoin hardware device should at least be usable and up to par for 10 years at the very least. Words written down or secured anywhere, last forever.\ \ 4\ Easy of use is still not ok: This might be very controversial with all the HW wallets claiming to be “easy to use”, but in fact: they’re not. Most users (and I take some family members and friends as an example here) can’t make heads or tails from how these things work. Give any non-tech user a coldcard, ledger of bitbox and they’ll not be on their way to use it as an everyday device.\ It might sound silly for the daily users of such a wallet, but a “noob” in my opinion is better off learning to familiarize themselves with software wallets first before even considering buying a HW wallet.\ \ 5 Buggy hardly tested apps\ The hardware wallets accompanied by an app (like Jade’s Green wallet to name one) are often introducing an extra layer of problems (both on the bugs and the risks). Who knows that this software will still be available in a few years time? We saw many things come and go over the years. \ \ 6\ Alienation from the private keys: New users are better of learning the ropes with seed phrases and private keys by using Electrum, Sparrow and the likes (or even stack wallet duo) in order to learn what holding your own keys means.
People who start their journey with a hardware wallet often think about their bitcoin holding as something that tangible “inside the hardware wallet”, instead of looking at the key-perspective. I think a lot of people are alienated from the bitcoin concept of having your own keys by using HW wallets. (and yes, that’s not a strong argument, I know, but it is a factor to take into account)
7
You’ll have to securely store your seed phrase ANYWAY.\ The fact remains, that you bought a hardware wallet, and still have to safely secure your private keys, seed phrase at some point and do it securely.\ That’s something you need anyway. So… why not just use your paper with 24 words and use the wallet on occasion by using a secure “other way” (seed signer, an electrum wallet, sparrow,...) when you need to do a transaction?
I believe people will also do les on-chain pure bitcoin transactions when they need to do more work when not using a HW wallet: it’s an extra barrier to hold instead of paying. (if you like to do that of course)
8
Upgrade processes aren't always that clear on some HW wallets.\ I personally “bricked” a coldcard this way, by accidentally using a wrong upgrade file on a Mark 2 coldcard, and it was unrepairable after that.
The 12 or 24 words are the most important thing you have, … you don’t need a hardware device if you’re just starting, or just are a hodl’er.
\ 9 Centralized software. Bugs and “new” features
Lots of bugs in the software also cause problems: For example; your 24 words from device A, can’t be imported to device B although they should “speak the same language” in theory (BIP39).\ One device accepts using two times the same word in a seed phrase, one doesn’t.\ There are other bugs: like random reboots, unlocking problems, strange implementations in the software (like Trezor trying out implementing the Swiss “travel rule” setting one day and pushing this upgrade to the users) and so on….\ Without a HW wallet, you can just choose yourself what software / node or wallet to run anything on, and you’re not tied to the centralized, expensive and often untested way of hardware wallet manufacturer’s viewpoints and or “secret deals”.
10) And then there’s the privacy concern. We all know about Ledger’s famous “mishap” where they leaked all the home addresses of hardware wallet customers .. some of them actually had to move to other places to live as a result.
Conclusion:
In my opinion; hardware wallets are toys for bored bitcoiners.\ And I admit I was one myself for a long time. (I am one of these people yes)
The blockstream Jade was the last hardware wallet I’ve ever bought I guess (and it broke about 4 months of operation, after the PIN code entry froze and the device stopped responding). \ \ On top of that: who needs to sign that much transactions a day (safe for shitcoiners?)
I’m done with the crappy interfaces, the buggy software, the ‘subscription’ to endless upgrades new hardware and the strange feeling of unease when storing something on such devices while you depend on the “open source” nature of something made in China or wherever.
\ There are much cheaper, easier and more secure solutions.
 \
Hence, most people don’t need hardware wallets.
\
Hence, most people don’t need hardware wallets. deadeyes
@avbpodcast
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:31:49
@ 5c26ee8b:a4d229aa
2025-04-14 16:31:4910:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ 87122b31:726e2c4c
2025-04-21 02:14:24
@ 87122b31:726e2c4c
2025-04-21 02:14:24Betwinner mang đến một nền tảng số hiện đại được thiết kế để phục vụ đa dạng đối tượng người dùng trong thời đại công nghệ ngày càng phát triển. Từ giao diện thân thiện đến khả năng tùy biến linh hoạt, nền tảng này luôn đặt sự thuận tiện và trải nghiệm người dùng lên hàng đầu. Ngay từ lần đầu truy cập, bạn sẽ cảm nhận được tốc độ phản hồi nhanh chóng, giao diện mượt mà và bố cục dễ hiểu – những yếu tố giúp Betwinner trở nên khác biệt so với nhiều nền tảng khác. Sự tương thích đa thiết bị, từ điện thoại thông minh đến máy tính bàn, giúp người dùng dễ dàng duy trì kết nối và thao tác linh hoạt trong mọi hoàn cảnh. Với việc tích hợp các tính năng thông minh và các lựa chọn cá nhân hóa như chế độ nền tối, ngôn ngữ hiển thị và điều chỉnh bố cục theo thói quen sử dụng, Betwinner mang lại cảm giác sử dụng cá nhân hóa rõ rệt và gần gũi.
Không chỉ gây ấn tượng với thiết kế và hiệu năng vận hành, Betwinner còn chú trọng vào bảo mật và sự an tâm của người dùng. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ thông tin cá nhân và dữ liệu trong quá trình sử dụng, kết hợp cùng cơ chế xác thực đa lớp để ngăn chặn các truy cập trái phép. Điều này đặc biệt quan trọng khi người dùng ngày càng có yêu cầu cao về tính bảo mật trong các giao dịch và thông tin cá nhân. Ngoài ra, Betwinner còn trang bị hệ thống hỗ trợ khách hàng 24/7, sẵn sàng giải đáp mọi thắc mắc, xử lý vấn đề nhanh chóng và đảm bảo người dùng luôn nhận được sự hỗ trợ cần thiết khi gặp phải bất kỳ sự cố nào. Việc cập nhật hệ thống và cải tiến tính năng diễn ra thường xuyên nhằm tối ưu hóa hiệu năng và tăng cường sự ổn định trong mọi hoạt động, từ những thao tác cơ bản cho đến các chức năng chuyên sâu hơn.
Không dừng lại ở việc cung cấp một nền tảng số tiện lợi, Betwinner còn hướng đến xây dựng một hệ sinh thái kết nối toàn diện. Với khả năng tích hợp nhanh các công nghệ mới như trí tuệ nhân tạo (AI), học máy (machine learning), cũng như tự động hóa quy trình trải nghiệm, nền tảng này đang tạo ra những thay đổi đáng kể trong cách người dùng tiếp cận và tương tác với không gian số. Mọi dữ liệu sử dụng đều được phân tích để từ đó cung cấp các đề xuất thông minh, giúp tiết kiệm thời gian và tối ưu hóa trải nghiệm cá nhân. Không chỉ là nơi cung cấp công cụ, Betwinner còn là điểm đến cho những ai muốn trải nghiệm môi trường công nghệ hiện đại, nơi mỗi hành động đều được hỗ trợ bởi nền tảng kỹ thuật mạnh mẽ và tư duy lấy người dùng làm trọng tâm. Trong bối cảnh xu hướng chuyển đổi số ngày càng mạnh mẽ, Betwinner đã và đang khẳng định vị thế là một trong những lựa chọn hàng đầu dành cho những ai đang tìm kiếm sự tiện nghi, bảo mật và sự chủ động trong trải nghiệm số hóa.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ e39d100f:d27602e5
2025-04-21 02:14:21
@ e39d100f:d27602e5
2025-04-21 02:14:21O mundo do entretenimento digital não para de crescer, e a 5588bet surge como uma plataforma moderna, segura e completa para quem busca diversão, emoção e oportunidades reais de ganhar prêmios. Com uma interface amigável, suporte eficiente e uma grande variedade de jogos, a 5588bet rapidamente conquistou espaço entre os jogadores brasileiros.
A primeira impressão ao acessar a 5588bet é a de um ambiente profissional e bem estruturado. A navegação é fluida, tanto no computador quanto em dispositivos móveis, permitindo que o usuário explore todas as funcionalidades com facilidade. A plataforma foi desenvolvida pensando na experiência do usuário, oferecendo menus intuitivos, design atrativo e carregamento rápido das páginas.
A segurança é uma prioridade para a 5588bet . Os dados dos jogadores são protegidos com tecnologia de criptografia de ponta, garantindo que todas as transações financeiras e informações pessoais estejam resguardadas. Além disso, a plataforma conta com uma equipe de suporte técnico disponível 24 horas por dia, pronta para auxiliar em qualquer necessidade.
Variedade de Jogos para Todos os Perfis Um dos grandes diferenciais da 5588bet é a diversidade de jogos disponíveis. A plataforma oferece títulos para todos os gostos, desde os clássicos até os mais modernos, todos com gráficos impressionantes e excelente jogabilidade.
Entre os destaques estão os jogos de roleta, bacará, pôquer, além de uma enorme seleção de slots com diferentes temáticas e mecânicas de bônus. Os jogadores podem explorar aventuras inspiradas em mitologia, filmes, frutas clássicas e muito mais. Muitos desses jogos são desenvolvidos por provedores renomados internacionalmente, garantindo qualidade e inovação a cada partida.
Além disso, para quem gosta de emoção em tempo real, a plataforma conta com mesas interativas com apresentadores ao vivo, proporcionando uma experiência imersiva que simula a sensação de estar em um ambiente físico de jogos, tudo isso com a comodidade de estar em casa ou em qualquer lugar.
Experiência do Jogador em Primeiro Lugar A 5588bet entende que a satisfação do jogador vai além da variedade de jogos. Por isso, investe em uma experiência completa. O processo de registro é rápido e simples, permitindo que novos usuários comecem a jogar em poucos minutos. Os métodos de pagamento são diversificados e incluem as principais carteiras digitais e bancos brasileiros, facilitando depósitos e saques.
A plataforma também oferece promoções atrativas para novos usuários e campanhas frequentes para jogadores fiéis. Bônus de boas-vindas, giros gratuitos, cashback e torneios especiais são algumas das formas que a 5588bet utiliza para valorizar seus usuários e tornar cada visita ainda mais interessante.
Outro ponto importante é a transparência. As regras de cada jogo, promoções e procedimentos financeiros são claramente explicados, dando ao jogador confiança e controle total sobre suas escolhas dentro da plataforma.
Conclusão A 5588bet se destaca como uma plataforma inovadora, segura e repleta de opções para quem busca entretenimento online de qualidade. Com jogos envolventes, suporte eficiente e uma experiência focada no usuário, ela se consolida como uma das melhores escolhas para jogadores brasileiros. Se você está em busca de diversão com emoção e recompensas, a 5588bet é o destino ideal.
-
 @ 8671a6e5:f88194d1
2025-03-15 20:36:41
@ 8671a6e5:f88194d1
2025-03-15 20:36:41I’ll have to use my best Tone Vays impersonation voice for saying this, “..but actually “Value for Value, is à scàm”.
We hear a lot about Value4Value in bitcoin. People giving some content, good or service, and then getting their proverbial hat out, to collect whatever it’s deemed worth to the audience.
Some examples:
-
Jimmy makes a nice website for the community, and gets a donation from whoever likes the work he put in.
-
Mathilda makes a nice series of travel videos about bitcoin places, and does a little dance, and people can donate sats.
-
Jody makes a podcast about bitcoin philosophy and the local community and people can donate for every episode.
That’s all very nice in theory.
I keep thinking about a documentary maker who told his audience he slept on a kitchen table because he had no money for a bed. And he would stop doing things V4V because of it. I can understand that sentiment, and I fear he’s not alone in that feeling.
One of the other artists in attendance told me “then he should work harder and make better things or get some sponsors”. Which contradicts the V4V model, and is rather disparaging towards that filmmaker.
In the world of "Value for Value" (V4V), the system is rigged from the get-go because of dodgy fundamentals based on goodwill. It borders on a scam, be it a voluntary run scam from both sides.
Unfortunately, there are very, very low percentages of people (let alone bitcoiners) that have goodwill. At least in Europe (I don’t know how this exactly works out in the US or Asia).
A personal friend of mine ran a history podcast for many years, and got more kudos, and gifts than I ever had in bitcoin.
And no, it’s not about the money, the income. You can call me a sour person all you want for saying this. It’s mainly about feeling a slight appreciation for what you do
On top of that, the subject itself is a bit of a “no-no” to talk about. If you do, you’re often branded a complainer, a wanker, a negative Nancy. Well… that’s one of the signs you participate in a sort of scam. When you point out holes in the scheme, you’re branded a complainer or a negativist; you often also get ousted.
That’s the way we’re all supposed to go thumbs-up on everything while sleeping on a kitchen table, while doing “good for the community.
To clarify (some close to the reality numbers):
If you put in ± 10 hours in an episode in total in a history podcast, you got rewarded about 50€ (usually from people appreciating the story and effort, relating to the part in history).
If you put in ± 6 hours in two episodes in total (less research than a history podcast), in bitcoin in Belgium, you get rewarded with 2 likes (one from myself and one from another bitcoiner), and no re-shares and about 2000 sats per episode on a good day, and 0 on a bad day.
unknown bitcoin artist holding an orange cup New people in bitcoin who fall for this need to be aware of the loss of time they'll face (which some can stomach, others won't...). Maybe this blog post can help prevent people from turning sour or becoming blatantly against the community.
People who have a good "ethics" stance in bitcoin will probably start to do things in V4V, hoping they get a good return for their work. You dive into this for the love of the community, for proof-of-work in Bitcoin, and maybe to carve out a name for yourself, or so you believe. But over time, this passion isn't enough to outweigh the hours, effort, and the relentless critique from the community's armchair philosophers – and trust me, there's no shortage of those.
Soon, however, such goodwill people will start to be disgruntled or at least less happy about the V4V model's returns. Let's face it, Value4Value was a marketing term invented by Adam Curry, along with Dave Jones, to launch a concept as an anti-movement against Apple's hegemony. It was meant to preserve free speech (that, it succeeded in; they've put the "free" in free speech). For themselves, because they had the first-mover advantage, it worked out fine. And until like the end of 2015, it worked very well.
However, I never heard of anyone after the year 2015 who lived off a value4value scheme having enough income and being happy about the exchange of goods and services...
Many podcasters resolve this by asking a fee for their "full" private and ad-free stream. Others just quit or go full paid service. It's all good, as long as you pick your poison and don't rely too much on appreciation in this community.
I'll go even further; in my opinion, the value proposition of Value 4 Value has a negative influence on bitcoin adoption. Because so many people will start under this model, hoping to make a living or at least break even on their hobby project, they'll soon turn sour.
This negative impact is due to an over-supply of content, or the implication that you have to get sponsors. I regularly got that message from people like, “Why don’t you get a sponsor?” They act like I don’t know that working for free isn't paying the bills. I know. Trust me on that. I work for free out of passion and genuine interest. If that gets punished, then there's something really wrong with this community.
On sponsors: the problem with this approach is that you can't call your own sponsor's product "a toy-grade piece of unreliable garbage" on-air if you take their money. And if you do, it's probably not doing wonders for your income.
Not only are you sacrificing your independence, but you're also stripping away the very essence of why you started the podcast in the first place. On that subject, I can't bring myself to read ads about dog food or some insurance company's new scammy tactics to "protect" people. If I go that route, I would whore myself out to the extent that I might as well start a "banging hot crypto of the week" podcast and shill any NFT, meme-coin, and garbage scam token out there if they pay me. That's also not the "value" people tune in for, I guess (although some Belgians still make a career out of doing so).
Broken value
There's an element of guaranteed discontent in Value4Value that's profoundly broken.
So here's my breakdown:
In Value4Value, you have at least two elements in the equation: the maker of goods/services/content and the receiver of such content, who also turns into the giver.
The first one is the first giver, the second one is the second giver in the exchange.
The first giver, often a content creator, pours their heart, time, and energy into something, expecting nothing in return but hoping for recognition or a fair exchange. Instead, they're often left with scraps while others freely take, use, and even profit from their work without so much as a nod. Giving credit is passé as well... even people who blatantly steal stuff from others smile in your face and go on with their "business". Result: the first giver feels scammed out of their time.
Then there's the second giver, the one who actually decides to pay up and not be a bitch. They give away their hard-earned fiat or bitcoin for something they could've gotten for "free", hoping to keep the cycle of generosity alive. But as reality sets in, they realize they're the only ones p(l)aying this game, leaving them feeling cheated, especially when they hear about others enjoying the same benefits without contributing a sat. Result: the second giver feels scammed out of their money, but at least they got something out of it.
Both ends
In essence, V4V is a scam on both ends.
There's the dishonest way where you might earn a bit, but at the cost of your integrity (for example, praising a rotten hardware wallet like it's a revolutionary invention while collecting the kickbacks). Or there's the so-called honorable path where you gain nothing but scorn and perhaps a pat on the back before someone else capitalizes on your efforts. (Not talking about the people here even ridiculing you for doing something for free).
This leaves a bitter feeling for everyone involved. Those who dare to charge for their services face another kind of scam - the guilt of appearing to be in it for the money while potentially exploiting the naive under the guise of community spirit. And those who speak up about it, like that documentary maker and some artists alike, are all getting brutally laughed at. Because it's a taboo subject to "complain" about income.
But that's not the issue here; I never started a podcast to earn a living or make money. I would be mad doing so and thinking so, certainly not in this market and community. The deeper issue is less trivial, however: when value for value is not recognized, and there are hardly any widespread tools to really capitalize on it, then it's a negative point for bitcoin adoption.
(Just an example) People who run the podcast feed on their own website steal potential income from me by circumventing a good podcast 2.0 platform like the Fountain app. It's probably well meant, to spread the word, but in general, it's profiting from content in the most lazy way possible.
You can prevent that from happening by making the feed private, but then you need to pay a service fee, which you can't pay because 90% of the bitcoiners are too cheap to pay for it. So you pay it out of your own pocket, only to get the critique about your podcast being "behind a paywall". So... you either let yourself be ripped off even further and earn less every episode... Or you just give up, take everything offline, and go work at McDonald's (at least they pay you by the hour, and then you're in the fiat scam and you know it!).
The same goes for artists who get their designs, logos, and artwork copied or see some other artwork that's "heavily inspired" by their own creation popping up somewhere else.
And don't get me started on people copying tweets, ideas, parts of a blog post, and re-telling it to pass it off as their own idea in a book or their own content channels (even some pretty famous people in the bitcoin space do this on a regular basis; you have to get your content somewhere, I guess, after years of getting free tickets to any conference and enjoying life in our little bubble of misfits and backroom deals).
We route around problems
One of Bitcoin's amazing properties is that it isn't bringing you "yield" on itself. One bitcoin doesn't generate more bitcoin by printing more bitcoin, like in fiat. You can't just sit on your ass and get more diluted Mickey Mouse money.
So if you want to be active in the space, you have to either sell yourself (your soul maybe included), or sell a product you have total control over (your own brand of orange-themed cuddly toys for grown-up men, hoodies, umbrellas, paintings with the same themes everyone else does, 3D printed action figures of yourself, or whatever you can come up with that's not too embarrassing to show up with at a conference).
It's in fact no laughing matter. In bitcoin, we're used to routing around problems.
According to me, the broader adoption of bitcoin and its ethos (mind my words here) cannot grow and be successful if we don't solve this problem. The majority of content creators aren't the "big names" with their big middlemen sponsors (even a few got sponsored by FTX and Celsius Network back in the day, and currently a lot of them eat out the hands of some hardware wallet manufacturers and exchanges). These smaller names and new people, make content and art or the likes in order to grow their audience, have fun, learn and make a bit of money on the side if possible. Some of them even want to make a real career out of it. That's all fine.
As a community we need to learn to support people in a decent way.
Some initiatives I've seen were also utterly flawed, so we need to do better. The idea of a "bitcoin influencer" team, for example, was, as far as I could tell, an utter failure from the start, certainly if I saw some people in that group at a conference dry-humping a potential beneficiary (or the other way around; we all route around problems in our own special way :), then I somehow start to question their motives. But it might also be my imagination; the end result is the same; everyone still sleeps on their proverbial kitchen table while delivering free stuff.
We often claim that the fiat world drains us of our energy, time, and effort in order to reward us in 'melting' fiat currency. Well... at least they got a melting ice cube instead of the proverbial pat on the back on the black hoodie you wear in support of someone else's project.
If bitcoin ground-level pleb things, run by real people, need to be successful to grow bitcoin awareness, then we need to find a better solution for this problem. Otherwise, many people will be utterly turned off by the promising "peer-to-peer" world they've stepped into. It not only turns them into the fiat-slave mindset again but also discourages people from building and doing cool things. No one likes to be ripped off. No one likes to work for free. No one likes to be spit in the face and get dirty looks or eye-rolls when you enter the room.
And no, don’t invent things just for me; I’m fine.
I see donations and likes/shares as a real-life measuring stick for the quality and reach of my work. With an average of 3 retweets and shares per episode, it's a failure. And with 13,420 sats over 7 episodes, it's not a big deal, but it's something. Many people in the space would be happy to get such a gift for 18 hours of work.1
Like the famous monologue in the movie Trainspotting, we could also ask ourselves collectively, ... Choose Bitcoin. Choose Value4Value. Choose a scam. Choose life... which scam do you prefer?
Will you choose working for free for bitcoin? Or choose life?
thank you for reading,
by … Kim DV for @AVBpodcast :
no donation button here for obvious reasons
1 sarcasm, a beggar near the Brussels Central station makes more money just sitting on his ass with a Mc Donald’s cup in hand telling people “ s'il te plaît “I’ll have to use my best Tone Vays impersonation voice for saying this, “..but actually “Value for Value, is à scàm”.
We hear a lot about Value4Value in bitcoin. People giving some content, good or service, and then getting their proverbial hat out, to collect whatever it’s deemed worth to the audience.\ \ Some examples:\ \ - Jimmy makes a nice website for the community, and gets a donation from whoever likes the work he put in.\ \ - Mathilda makes a nice series of travel videos about bitcoin places, and does a little dance, and people can donate sats.\ \ - Jody makes a podcast about bitcoin philosophy and the local community and people can donate for every episode.
That’s all very nice in theory.\ \ I keep thinking about a documentary maker who told his audience he slept on a kitchen table because he had no money for a bed. And he would stop doing things V4V because of it. I can understand that sentiment, and I fear he’s not alone in that feeling.\ \ One of the other artists in attendance told me “then he should work harder and make better things or get some sponsors”. Which contradicts the V4V model, and is rather disparaging towards that filmmaker.\ \ In the world of "Value for Value" (V4V), the system is rigged from the get-go because of dodgy fundamentals based on goodwill. It borders on a scam, be it a voluntary run scam from both sides.\ \ Unfortunately, there are very, very low percentages of people (let alone bitcoiners) that have goodwill. At least in Europe (I don’t know how this exactly works out in the US or Asia).\ \ A personal friend of mine ran a history podcast for many years, and got more kudos, and gifts than I ever had in bitcoin.\ \ And no, it’s not about the money, the income. You can call me a sour person all you want for saying this. It’s mainly about feeling a slight appreciation for what you do\ \ On top of that, the subject itself is a bit of a “no-no” to talk about. If you do, you’re often branded a complainer, a wanker, a negative Nancy. Well… that’s one of the signs you participate in a sort of scam. When you point out holes in the scheme, you’re branded a complainer or a negativist; you often also get ousted.
That’s the way we’re all supposed to go thumbs-up on everything while sleeping on a kitchen table, while doing “good for the community.\ \ To clarify (some close to the reality numbers):\ \ If you put in ± 10 hours in an episode in total in a history podcast, you got rewarded about 50€ (usually from people appreciating the story and effort, relating to the part in history).\ \ If you put in ± 6 hours in two episodes in total (less research than a history podcast), in bitcoin in Belgium, you get rewarded with 2 likes (one from myself and one from another bitcoiner), and no re-shares and about 2000 sats per episode on a good day, and 0 on a bad day.
 unknown bitcoin artist holding an orange cup
unknown bitcoin artist holding an orange cupNew people in bitcoin who fall for this need to be aware of the loss of time they'll face (which some can stomach, others won't...). Maybe this blog post can help prevent people from turning sour or becoming blatantly against the community.
People who have a good "ethics" stance in bitcoin will probably start to do things in V4V, hoping they get a good return for their work. You dive into this for the love of the community, for proof-of-work in Bitcoin, and maybe to carve out a name for yourself, or so you believe. But over time, this passion isn't enough to outweigh the hours, effort, and the relentless critique from the community's armchair philosophers – and trust me, there's no shortage of those.
Soon, however, such goodwill people will start to be disgruntled or at least less happy about the V4V model's returns. Let's face it, Value4Value was a marketing term invented by Adam Curry, along with Dave Jones, to launch a concept as an anti-movement against Apple's hegemony.\ It was meant to preserve free speech (that, it succeeded in; they've put the "free" in free speech).\ For themselves, because they had the first-mover advantage, it worked out fine. And until like the end of 2015, it worked very well.\ \ However, I never heard of anyone after the year 2015 who lived off a value4value scheme having enough income and being happy about the exchange of goods and services...\ \ Many podcasters resolve this by asking a fee for their "full" private and ad-free stream. Others just quit or go full paid service. It's all good, as long as you pick your poison and don't rely too much on appreciation in this community.
I'll go even further; in my opinion, the value proposition of Value 4 Value has a negative influence on bitcoin adoption. Because so many people will start under this model, hoping to make a living or at least break even on their hobby project, they'll soon turn sour.\ \ This negative impact is due to an over-supply of content, or the implication that you have to get sponsors. I regularly got that message from people like,\ “Why don’t you get a sponsor?”\ They act like I don’t know that working for free isn't paying the bills. I know. Trust me on that. I work for free out of passion and genuine interest. If that gets punished, then there's something really wrong with this community.\ \ On sponsors: the problem with this approach is that you can't call your own sponsor's product "a toy-grade piece of unreliable garbage" on-air if you take their money. And if you do, it's probably not doing wonders for your income.\ \ Not only are you sacrificing your independence, but you're also stripping away the very essence of why you started the podcast in the first place. On that subject, I can't bring myself to read ads about dog food or some insurance company's new scammy tactics to "protect" people.\ If I go that route, I would whore myself out to the extent that I might as well start a "banging hot crypto of the week" podcast and shill any NFT, meme-coin, and garbage scam token out there if they pay me.\ That's also not the "value" people tune in for, I guess (although some Belgians still make a career out of doing so).
Broken value
There's an element of guaranteed discontent in Value4Value that's profoundly broken.
So here's my breakdown:
In Value4Value, you have at least two elements in the equation: the maker of goods/services/content and the receiver of such content, who also turns into the giver.\ \ The first one is the first giver, the second one is the second giver in the exchange.\ \ The first giver, often a content creator, pours their heart, time, and energy into something, expecting nothing in return but hoping for recognition or a fair exchange. Instead, they're often left with scraps while others freely take, use, and even profit from their work without so much as a nod. Giving credit is passé as well... even people who blatantly steal stuff from others smile in your face and go on with their "business". Result: the first giver feels scammed out of their time.
Then there's the second giver, the one who actually decides to pay up and not be a bitch.\ They give away their hard-earned fiat or bitcoin for something they could've gotten for "free", hoping to keep the cycle of generosity alive.\ But as reality sets in, they realize they're the only ones p(l)aying this game, leaving them feeling cheated, especially when they hear about others enjoying the same benefits without contributing a sat.\ Result: the second giver feels scammed out of their money, but at least they got something out of it.
Both ends
In essence, V4V is a scam on both ends.
There's the dishonest way where you might earn a bit, but at the cost of your integrity (for example, praising a rotten hardware wallet like it's a revolutionary invention while collecting the kickbacks).\ Or there's the so-called honorable path where you gain nothing but scorn and perhaps a pat on the back before someone else capitalizes on your efforts. (Not talking about the people here even ridiculing you for doing something for free).
This leaves a bitter feeling for everyone involved. Those who dare to charge for their services face another kind of scam - the guilt of appearing to be in it for the money while potentially exploiting the naive under the guise of community spirit.\ And those who speak up about it, like that documentary maker and some artists alike, are all getting brutally laughed at. Because it's a taboo subject to "complain" about income.\ \ But that's not the issue here; I never started a podcast to earn a living or make money. I would be mad doing so and thinking so, certainly not in this market and community. The deeper issue is less trivial, however: when value for value is not recognized, and there are hardly any widespread tools to really capitalize on it, then it's a negative point for bitcoin adoption.
(Just an example) People who run the podcast feed on their own website steal potential income from me by circumventing a good podcast 2.0 platform like the Fountain app. It's probably well meant, to spread the word, but in general, it's profiting from content in the most lazy way possible.\ \ You can prevent that from happening by making the feed private, but then you need to pay a service fee, which you can't pay because 90% of the bitcoiners are too cheap to pay for it. So you pay it out of your own pocket, only to get the critique about your podcast being "behind a paywall".\ So... you either let yourself be ripped off even further and earn less every episode...\ Or you just give up, take everything offline, and go work at McDonald's (at least they pay you by the hour, and then you're in the fiat scam and you know it!).\ \ The same goes for artists who get their designs, logos, and artwork copied or see some other artwork that's "heavily inspired" by their own creation popping up somewhere else.\ \ And don't get me started on people copying tweets, ideas, parts of a blog post, and re-telling it to pass it off as their own idea in a book or their own content channels (even some pretty famous people in the bitcoin space do this on a regular basis; you have to get your content somewhere, I guess, after years of getting free tickets to any conference and enjoying life in our little bubble of misfits and backroom deals).
\ We route around problems\ \ One of Bitcoin's amazing properties is that it isn't bringing you "yield" on itself. One bitcoin doesn't generate more bitcoin by printing more bitcoin, like in fiat. You can't just sit on your ass and get more diluted Mickey Mouse money.
So if you want to be active in the space, you have to either sell yourself (your soul maybe included), or sell a product you have total control over (your own brand of orange-themed cuddly toys for grown-up men, hoodies, umbrellas, paintings with the same themes everyone else does, 3D printed action figures of yourself, or whatever you can come up with that's not too embarrassing to show up with at a conference).
It's in fact no laughing matter.\ In bitcoin, we're used to routing around problems.\ \ According to me, the broader adoption of bitcoin and its ethos (mind my words here) cannot grow and be successful if we don't solve this problem.\ The majority of content creators aren't the "big names" with their big middlemen sponsors (even a few got sponsored by FTX and Celsius Network back in the day, and currently a lot of them eat out the hands of some hardware wallet manufacturers and exchanges).\ These smaller names and new people, make content and art or the likes in order to grow their audience, have fun, learn and make a bit of money on the side if possible. Some of them even want to make a real career out of it. That's all fine.\ \ As a community we need to learn to support people in a decent way.\ \ Some initiatives I've seen were also utterly flawed, so we need to do better. The idea of a "bitcoin influencer" team, for example, was, as far as I could tell, an utter failure from the start, certainly if I saw some people in that group at a conference dry-humping a potential beneficiary (or the other way around; we all route around problems in our own special way :), then I somehow start to question their motives.\ But it might also be my imagination; the end result is the same; everyone still sleeps on their proverbial kitchen table while delivering free stuff.\ \ We often claim that the fiat world drains us of our energy, time, and effort in order to reward us in 'melting' fiat currency. Well... at least they got a melting ice cube instead of the proverbial pat on the back on the black hoodie you wear in support of someone else's project.\ \ If bitcoin ground-level pleb things, run by real people, need to be successful to grow bitcoin awareness, then we need to find a better solution for this problem. Otherwise, many people will be utterly turned off by the promising "peer-to-peer" world they've stepped into. It not only turns them into the fiat-slave mindset again but also discourages people from building and doing cool things. No one likes to be ripped off. No one likes to work for free. No one likes to be spit in the face and get dirty looks or eye-rolls when you enter the room.\ \ And no, don’t invent things just for me; I’m fine.\ \ I see donations and likes/shares as a real-life measuring stick for the quality and reach of my work.\ With an average of 3 retweets and shares per episode, it's a failure. And with 13,420 sats over 7 episodes, it's not a big deal, but it's something. Many people in the space would be happy to get such a gift for 18 hours of work.1
 \
Like the famous monologue in the movie Trainspotting, we could also ask ourselves collectively, ...\
Choose Bitcoin.\
Choose Value4Value.\
Choose a scam.\
Choose life... which scam do you prefer?\
\
Will you choose working for free for bitcoin?\
Or choose life?
\
Like the famous monologue in the movie Trainspotting, we could also ask ourselves collectively, ...\
Choose Bitcoin.\
Choose Value4Value.\
Choose a scam.\
Choose life... which scam do you prefer?\
\
Will you choose working for free for bitcoin?\
Or choose life?thank you for reading,
\ by … Kim DV for @AVBpodcast :
no donation button here for obvious reasons
sarcasm, a beggar near the Brussels Central station makes more money just sitting on his ass with a Mc Donald’s cup in hand telling people “ s'il te plaît “
-
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ d34e832d:383f78d0
2025-04-21 01:31:02
@ d34e832d:383f78d0
2025-04-21 01:31:02Optimizing Knowledge Management with Obsidian and the Zettelkasten Method
The Zettelkasten method, which translates to "slip box" in German, is a powerful system for personal knowledge management developed by sociologist Niklas Luhmann. It relies on creating and linking small, self-contained notes that each represent a single idea or thought. These notes are connected through internal references, forming a dense web of knowledge that mirrors how ideas evolve and relate to each other naturally. By writing in small, atomic units, users are encouraged to distill complex concepts into their essence, improving understanding and retention.
Zettelkasten facilitates knowledge retention by encouraging active engagement with information. Instead of passively reading or highlighting, users must rephrase, question, and connect ideas. This process reinforces memory and builds a reusable archive of insights. The method also supports long-term idea development by creating an environment where thoughts grow organically through continuous linking, comparison, and reflection. For researchers and writers, Zettelkasten becomes a dynamic workspace for managing sources, forming arguments, and drafting structured content.
With the rise of digital tools, the Zettelkasten method has found a modern home in applications like Obsidian. Obsidian is a markdown-based note-taking app that allows users to create a network of interlinked notes stored locally on their device. It supports backlinks, graph views, and a customizable interface, making it ideal for implementing Zettelkasten. Unlike paper systems or linear document editors, Obsidian turns a note collection into an interactive, searchable, and scalable knowledge base. This evolution has made it easier than ever to adopt and maintain a Zettelkasten system for academic research, professional writing, and lifelong learning. - Problem Statement: Despite its effectiveness, many users struggle with implementing Zettelkasten in a way that integrates well into their daily routines. This thesis presents a streamlined, efficient setup using Obsidian for optimal results.
1. Install Obsidian
- Download Obsidian from the official website (https://obsidian.md) and install it on your preferred device (Windows, macOS, Linux, or mobile).
- Open the app and create a new Vault, which will serve as the central repository for all your notes.
- Choose a location for your vault. For backup and multi-device access, store it in a synced folder like Dropbox, OneDrive, or iCloud.
2. Folder Structure
Set up a simple, organized folder structure to support the Zettelkasten flow:
00_Templates: Store reusable note templates.01_Source_Material: Notes from books, articles, lectures, etc.02_Rough_Notes: Free-form, early-stage thoughts (optional).03_Main_Notes: Core Zettelkasten notes; each represents a single atomic idea.04_Indexes: Thematic hubs or entry points for exploring related notes.05_Tags: Empty placeholder notes acting as tags for navigation or filtering (optional).
3. Settings Configuration
- Default Location for New Notes: Point to
03_Main_Notes. - Appearance: Choose a legible font and theme; toggle "Readable line length" for better formatting.
- Hotkeys: Assign shortcuts, e.g.:
Ctrl + N: New NoteCtrl + T: Insert Template (after plugin activation)- Core Plugins:
- Enable Templates, Daily Notes (optional), and Backlinks.
- Community Plugins (optional):
- Calendar: For date-based organization.
- Tag Wrangler: For managing and merging tags.
- Advanced Tables, Quick Switcher++, or DataView: For productivity.
4. Create Templates
Under
00_Templates, create templates like:Source Material Template ``` Title: Author: Source: Date: Tags:
Summary: Key Points: Quotes: Reflections: ```
Main Note Template ``` Title: Date Created: Tags:
Idea: Context: Connections: [[Linked Note]] Reflections: ```
Configure the Templates plugin to insert templates quickly using hotkeys.
5. Note-Taking Workflow
Step 1: Capture - In
01_Source_Material, create notes while reading or researching. Summarize, highlight quotes, and reflect in your own words. - Use tags for themes, authors, or concepts (e.g.,#philosophy,#biology).Step 2: Synthesize - In
03_Main_Notes, write atomic notes from your reflections. - Each note should express a single idea clearly (under 500 words). - Use links to reference related notes with[[Note Name]]. - Focus on clarity, brevity, and insight.Step 3: Connect - Link your new idea to related ideas, themes, or sources. - Create notes in
04_Indexesto organize clusters of related content. - Add notes to multiple indexes or link to broader themes using[[#Tag]].
6. Use Tags and Indexes Thoughtfully
- Avoid creating hundreds of tags. Stick to a small set of relevant themes.
- Use
05_Tagsto define and clarify what each tag means. - In
04_Indexes, organize curated lists of related notes. Example:Mindfulness Indexmight link to[[]]notes from psychology, philosophy, and neuroscience.
7. Benefits for Research and Writing
- Streamlines Research: Notes from multiple sources are cross-referenced and easily revisitable.
- Accelerates Writing: Writing becomes an assembly of existing notes instead of starting from scratch.
- Improves Clarity: Breaking down ideas into atomic notes encourages better thinking and clarity.
- Long-Term Retention: Regular review and linking strengthen memory and understanding.
- Reusable Content: Notes can be reused across multiple projects, articles, or books.
8. Maintenance Tips
- Review backlinks weekly to surface forgotten or underdeveloped ideas.
- Refactor or split long notes to maintain atomicity.
- Avoid over-editing old notes; instead, create new ones that build upon earlier thoughts.
With this Obsidian-based Zettelkasten setup, you're not just taking notes — you're cultivating a living knowledge system. Whether you're an academic, writer, student, or lifelong learner, this system adapts to your workflow, grows with your interests, and becomes more powerful the more you use it. Over time, your vault evolves into a personalized knowledge database that supports deeper understanding, creative exploration, and effortless content creation.
- The Zettelkasten Methodology
The Original Zettelkasten Technique: Core Principles & Benefits
The Zettelkasten method (German for "slip box") was developed by sociologist Niklas Luhmann as a tool to manage complex knowledge and boost creativity in writing and research. He credited it with enabling his prolific academic output: over 70 books and hundreds of articles. The brilliance of the system lies in its simplicity, modularity, and organic growth.
🌱 Core Principles of Zettelkasten
1. Atomicity
Each note in the Zettelkasten should express a single idea or concept. This principle ensures clarity, encourages deeper understanding, and makes ideas easier to reuse and connect.
- ✅ Do: “The law of diminishing returns means each additional input yields less output.”
- ❌ Don’t: Combine multiple concepts or quotes into one long note.
Atomic notes are easier to: - Link logically. - Modify independently. - Reuse across different contexts.
2. Linking
Instead of a rigid hierarchy, Zettelkasten thrives on contextual, lateral linking.
- Notes are connected using direct references to other notes.
- Each note becomes part of a network, not a silo.
- Links simulate how human memory works—via associations, not folders.
Example: A note on “Nietzsche’s eternal recurrence” might link to notes on “cyclical time in Buddhism” or “existentialism.”
Benefits: - Emergent structure—patterns and themes arise naturally. - Serendipitous discovery—old ideas resurface via linked paths. - Compound creativity—new combinations emerge from connected thoughts.
3. Simplicity
Luhmann emphasized a low-friction system. His physical slip-box used numbered index cards and manual cross-referencing—no complex categorization.
Simplicity: - Reduces friction between thought and capture. - Makes the system future-proof and easy to maintain. - Encourages writing in your own words, promoting internalization.
Modern Zettelkasten tools (like Obsidian) honor this by: - Allowing bidirectional links (
[[Note Title]]). - Replacing folders with tags and contextual backlinks. - Supporting plain text Markdown format for longevity.
✍️ Benefits of Zettelkasten
📚 For Writing
- Provides a ready-made library of ideas to draw from.
- Writing becomes assembly, not invention—you collect, synthesize, and expand existing notes.
- Encourages idea-driven writing, not source-driven copying.
“Writing is no longer a process of transfer, but of transformation.” — Luhmann
🔍 For Research
- Encourages critical engagement with sources (notes are written in your own words).
- Makes literature review manageable through connected concepts.
- Supports non-linear learning—you follow interesting links, not rigid outlines.
🧠 For Idea Organization
- Keeps ideas alive and evolving through regular linking and revisiting.
- Avoids information rot by focusing on synthesis, not storage.
- Fosters a personal knowledge graph—tailored to how you think.
🧩 Summary Table
| Principle | What it Means | Why it Matters | |---------------|------------------------------------|--------------------------------------| | Atomicity | 1 idea per note | Improves clarity, reuse, and focus | | Linking | Contextual note-to-note links | Encourages discovery and depth | | Simplicity | Low friction, minimal structure | Easy to maintain and long-lasting |
Consider
The original Zettelkasten is more than a note-taking method—it's a thinking partner. By focusing on the quality of thought, it transforms how you learn, create, and connect ideas. Whether used with index cards or modern tools like Obsidian, its core principles remain timeless.
Would you like a visual map or Obsidian-ready template for Luhmann-style Zettelkasten?
- Benefits of Zettelkasten for Writing:
- Streamlines Research: Centralized notes help avoid redundant research across multiple projects.
- Facilitates Long-Form Writing: Accumulated notes serve as building blocks for larger projects.
- Personal Writing Assistant: The evolving network of notes provides quick access to ideas for future writing.
-
Obsidian Setup and Configuration
-
Installing Obsidian: Guide the user through the installation process, emphasizing the free version and its core features.
-
Creating and Organizing a Vault: A vault in Obsidian is the central hub for all your notes. This section provides instructions for setting up a vault and explains the importance of cloud storage for backup and accessibility.
-
Folder Structure: Establish a recommended folder structure:
- Rough Notes: Optional folder for quick thoughts.
- Source Material: Store notes from books, articles, etc.
- Tags: Empty notes used as tags for easy categorization.
- Indexes: Organized collections of notes based on specific topics or themes.
- Templates: Predefined templates for consistent note-taking.
-
Main Notes: The core content of your knowledge base.
-
Settings Configuration:
- Configure default note locations.
- Customize appearance for readability.
- Set up hotkeys for efficient note-taking (e.g., Ctrl+T for template insertion).
- Enable and configure the "Templates" core plugin for consistent note creation.
-
The Note-Taking Process
-
Creating Notes: Guide the user on how to create new notes (Ctrl+O) and insert templates (Ctrl+T). Emphasize the importance of focusing on one idea per note to maintain atomicity.
-
Source Material Notes:
- Record page numbers, quotes, and elaborate on the ideas in your own words.
-
Include metadata such as authorship, publication year, and source references.
-
Main Notes:
- Synthesize ideas from source material.
- Focus on the key takeaways and connections between different ideas.
-
Use internal links ([[Note Name]]) to connect related notes and foster deeper understanding.
-
Tagging Notes:
- Use tags sparingly but effectively.
- Avoid over-complicating tags, focusing on personal interests or key themes.
- Tags act as an index to quickly locate notes.
-
Linking and Organizing Ideas
-
Internal Links and Connections: Demonstrate how internal links help create a web of interconnected ideas. Discuss how linking related concepts and topics can lead to a more holistic understanding.
-
Indexing for Navigation: Show how creating indexes for topics allows for quick access to collections of related notes. Introduce the idea of building thematic indexes for large research projects.
-
Synthesizing Notes for Larger Projects: Explain how to take notes from the Source Material and Main Notes to gradually build drafts for books, essays, or research papers.
-
Best Practices for Obsidian and Zettelkasten
-
Consistency and Simplicity: Emphasize the importance of simplicity in both note-taking and vault organization. Discourage the need for a "perfect" setup, focusing on efficiency and growth over time.
-
Keeping Notes Concise: Encourage users to keep each note under 500 words, focusing on one idea per note. This enhances clarity and makes it easier to synthesize ideas later.
-
Making Notes Readable: Provide tips on formatting for readability: use headings, bullet points, and quotes to break up large blocks of text.
-
Practical Applications of Zettelkasten in Writing
-
Research Projects: Show how to leverage your Zettelkasten system to conduct more efficient and thorough research for academic papers, articles, or blog posts.
-
Book and Essay Writing: Provide examples of how notes in Obsidian can evolve into larger writing projects, from initial drafts to final revisions.
-
Personal Projects and Brainstorming: Illustrate how the Zettelkasten method can be used for creative writing, personal reflections, or brainstorming for new ventures.
-
Case In Point
-
Summary of Findings: Recap the effectiveness of combining the Zettelkasten method with Obsidian for knowledge management, writing, and research.
-
Future Directions: Suggest areas for future exploration, such as integrating other digital tools (e.g., Zotero, Roam Research) into the workflow or expanding the Zettelkasten method into larger organizational systems.
-
References
-
Cite all relevant sources, including academic papers, books, and articles about the Zettelkasten method, Obsidian, and knowledge management.
📘 1. Source Note Template (
Source Note)This template is used when reading books, articles, podcasts, or videos. The goal is to capture contextual metadata and your impressions, not to mindlessly copy.
```markdown
📘 Source: {{title}}
Type: Book / Article / Video / Podcast
Author: {{author}}
Published: {{date}}
Source Link: Link
Tags: #source #{{topic}}
Related Notes: [[ ]]
🧠 Summary
A brief summary of the source in your own words.
🧩 Key Ideas
- Idea 1
- Idea 2
- Idea 3
🔎 Quotes & Passages
“...”
— Page X🗺️ Linked Notes
- [[Note about idea X]]
- [[Historical context of Y]]
📝 Your Thoughts
- Agreement? Disagreement?
- How does this relate to your current research?
- Ideas it sparked? ```
🧠 2. Main/Idea Note Template (
Zettelor Permanent Note)Each idea should be atomic, clearly written in your own words, and linked to related ideas. This is the core of your Zettelkasten.
```markdown
💡 {{Descriptive Title}}
ID: {{YYYYMMDDHHMM}}
Tags: #zettel #{{topic}}
Linked From: [[ ]]
🧠 Core Idea
Write a single, concise idea in your own words. This should be a self-contained statement or argument.
💬 Explanation / Elaboration
Explain why this idea matters or how it connects to broader themes. Use metaphors, contrast, or short examples.
🔗 Related Notes
- [[Related idea A]]
- [[Contrasting concept B]]
- [[Supports claim C]] ```
Tip: Use the ID convention (e.g.
202504201013) to uniquely identify each note.
🧪 3. Research Summary Note (
Literature Noteor Topic Overview)Use this when you're studying a broader concept or topic and summarizing multiple inputs (e.g., a research question or paper theme).
```markdown
🧪 Research Summary: {{Topic}}
Tags: #summary #research #{{subject}}
Created: {{date}}
Status: Draft / Ongoing / Complete
📌 Topic Overview
Brief definition or framing of the research question.
📚 Key Sources
- [[Author, Title]] — key takeaway.
- [[Article Title]] — significant argument.
🧩 Key Themes
- Theme 1: summary + relevant note links.
- Theme 2: contrasting perspective.
🧠 Emerging Ideas
- New insights or patterns you're noticing.
- Questions that remain unanswered.
🔗 Related Notes
- [[Main idea note]]
- [[Potential application note]]
- [[Philosophical implication]] ```
🔄 How They Interact
- Source Notes → inspire → Main Notes
- Main Notes → get linked into → Research Summaries
- Research Summaries → help generate → new Main Notes
“You don’t collect knowledge, you build it — one link at a time.”




