-
 @ d34e832d:383f78d0
2025-04-22 22:48:30
@ d34e832d:383f78d0
2025-04-22 22:48:30What is pfSense?
pfSense is a free, open-source firewall and router software distribution based on FreeBSD. It includes a web-based GUI and supports advanced features like:
- Stateful packet inspection (SPI)
- Virtual Private Network (VPN) support (OpenVPN, WireGuard, IPSec)
- Dynamic and static routing
- Traffic shaping and QoS
- Load balancing and failover
- VLANs and captive portals
- Intrusion Detection/Prevention (Snort, Suricata)
- DNS, DHCP, and more
Use Cases
- Home networks with multiple devices
- Small to medium businesses
- Remote work VPN gateway
- IoT segmentation
- Homelab firewalls
- Wi-Fi network segmentation
2. Essential Hardware Components
When building a pfSense router, you must match your hardware to your use case. The system needs at least two network interfaces—one for WAN, one for LAN.
Core Components
| Component | Requirement | Budget-Friendly Example | |---------------|------------------------------------|----------------------------------------------| | CPU | Dual-core 64-bit x86 (AES-NI support recommended) | Intel Celeron J4105, AMD GX-412HC, or Intel i3 6100T | | Motherboard | Mini-ITX or Micro-ATX with support for selected CPU | ASRock J4105-ITX (includes CPU) | | RAM | Minimum 4GB (8GB preferred) | Crucial 4GB DDR4 | | Storage | 16GB+ SSD or mSATA/NVMe (for longevity and speed) | Kingston A400 120GB SSD | | NICs | At least two Intel gigabit ports (Intel NICs preferred) | Intel PRO/1000 Dual-Port PCIe or onboard | | Power Supply | 80+ Bronze rated or PicoPSU for SBCs | EVGA 400W or PicoPSU 90W | | Case | Depends on form factor | Mini-ITX case (e.g., InWin Chopin) | | Cooling | Passive or low-noise | Stock heatsink or case fan |
3. Recommended Affordable Hardware Builds
Build 1: Super Budget (Fanless)
- Motherboard/CPU: ASRock J4105-ITX (quad-core, passive cooling, AES-NI)
- RAM: 4GB DDR4 SO-DIMM
- Storage: 120GB SATA SSD
- NICs: 1 onboard + 1 PCIe Intel Dual Port NIC
- Power Supply: PicoPSU with 60W adapter
- Case: Mini-ITX fanless enclosure
- Estimated Cost: ~$150–180
Build 2: Performance on a Budget
- CPU: Intel i3-6100T (low power, AES-NI support)
- Motherboard: ASUS H110M-A/M.2 (Micro-ATX)
- RAM: 8GB DDR4
- Storage: 120GB SSD
- NICs: 2-port Intel PCIe NIC
- Case: Compact ATX case
- Power Supply: 400W Bronze-rated PSU
- Estimated Cost: ~$200–250
4. Assembling the Hardware
Step-by-Step Instructions
- Prepare the Workspace:
- Anti-static mat or surface
- Philips screwdriver
- Install CPU (if required):
- Align and seat CPU into socket
- Apply thermal paste and attach cooler
- Insert RAM into DIMM slots
- Install SSD and connect to SATA port
- Install NIC into PCIe slot
- Connect power supply to motherboard, SSD
- Place system in case and secure all components
- Plug in power and monitor
5. Installing pfSense Software
What You'll Need
- A 1GB+ USB flash drive
- A separate computer with internet access
Step-by-Step Guide
- Download pfSense ISO:
- Visit: https://www.pfsense.org/download/
- Choose AMD64, USB Memstick Installer, and mirror site
- Create Bootable USB:
- Use tools like balenaEtcher or Rufus to write ISO to USB
- Boot the Router from USB:
- Enter BIOS → Set USB as primary boot
- Save and reboot
- Install pfSense:
- Accept defaults during installation
- Choose ZFS or UFS (UFS is simpler for small SSDs)
- Install to SSD, remove USB post-installation
6. Basic Configuration Settings
After the initial boot, pfSense will assign: - WAN to one interface (via DHCP) - LAN to another (default IP: 192.168.1.1)
Access WebGUI
- Connect a PC to LAN port
- Open browser → Navigate to
http://192.168.1.1 - Default login: admin / pfsense
Initial Setup Wizard
- Change admin password
- Set hostname and DNS
- Set time zone
- Confirm WAN/LAN settings
- Enable DHCP server for LAN
- Optional: Enable SSH
7. Tips and Best Practices
Security Best Practices
- Change default password immediately
- Block all inbound traffic by default
- Enable DNS over TLS (with Unbound)
- Regularly update pfSense firmware and packages
- Use strong encryption for VPNs
- Limit admin access to specific IPs
Performance Optimization
- Use Intel NICs for reliable throughput
- Offload DNS, VPN, and DHCP to dedicated packages
- Disable unnecessary services to reduce CPU load
- Monitor system logs for errors and misuse
- Enable traffic shaping if managing VoIP or streaming
Useful Add-ons
- pfBlockerNG: Ad-blocking and geo-blocking
- Suricata: Intrusion Detection System
- OpenVPN/WireGuard: VPN server setup
- Zabbix Agent: External monitoring
8. Consider
With a modest investment and basic technical skills, anyone can build a powerful, flexible, and secure pfSense router. Choosing the right hardware for your needs ensures a smooth experience without overpaying or underbuilding. Whether you're enhancing your home network, setting up a secure remote office, or learning network administration, a custom pfSense router is a versatile, long-term solution.
Appendix: Example Hardware Component List
| Component | Item | Price (Approx.) | |------------------|--------------------------|------------------| | Motherboard/CPU | ASRock J4105-ITX | $90 | | RAM | Crucial 4GB DDR4 | $15 | | Storage | Kingston A400 120GB SSD | $15 | | NIC | Intel PRO/1000 Dual PCIe | $20 | | Case | Mini-ITX InWin Chopin | $40 | | Power Supply | PicoPSU 60W + Adapter | $25 | | Total | | ~$205 |
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ d34e832d:383f78d0
2025-04-22 21:32:40
@ d34e832d:383f78d0
2025-04-22 21:32:40The Domain Name System (DNS) is a foundational component of the internet. It translates human-readable domain names into IP addresses, enabling the functionality of websites, email, and services. However, traditional DNS is inherently insecure—queries are typically sent in plaintext, making them vulnerable to interception, spoofing, and censorship.
DNSCrypt is a protocol designed to authenticate communications between a DNS client and a DNS resolver. By encrypting DNS traffic and validating the source of responses, it thwarts man-in-the-middle attacks and DNS poisoning. Despite its security advantages, widespread adoption remains limited due to usability and deployment complexity.
This idea introduces an affordable, lightweight DNSCrypt proxy server capable of providing secure DNS resolution in both home and enterprise environments. Our goal is to democratize secure DNS through low-cost infrastructure and transparent architecture.
2. Background
2.1 Traditional DNS Vulnerabilities
- Lack of Encryption: DNS queries are typically unencrypted (UDP port 53), exposing user activity.
- Spoofing and Cache Poisoning: Attackers can forge DNS responses to redirect users to malicious websites.
- Censorship: Governments and ISPs can block or alter DNS responses to control access.
2.2 Introduction to DNSCrypt
DNSCrypt mitigates these problems by: - Encrypting DNS queries using X25519 + XSalsa20-Poly1305 or X25519 + ChaCha20-Poly1305 - Authenticating resolvers via public key infrastructure (PKI) - Supporting relay servers and anonymized DNS, enhancing metadata protection
2.3 Current Landscape
DNSCrypt proxies are available in commercial routers and services (e.g., Cloudflare DNS over HTTPS), but full control remains in the hands of centralized entities. Additionally, hardware requirements and setup complexity can be barriers to entry.
3. System Architecture
3.1 Overview
Our system is designed around the following components: - Client Devices: Use DNSCrypt-enabled stub resolvers (e.g., dnscrypt-proxy) - DNSCrypt Proxy Server: Accepts DNSCrypt queries, decrypts and validates them, then forwards to recursive resolvers (e.g., Unbound) - Recursive Resolver (Optional): Provides DNS resolution without reliance on upstream services - Relay Support: Adds anonymization via DNSCrypt relays
3.2 Protocols and Technologies
- DNSCrypt v2: Core encrypted DNS protocol
- X25519 Key Exchange: Lightweight elliptic curve cryptography
- Poly1305 AEAD Encryption: Fast and secure authenticated encryption
- UDP/TCP Fallback: Supports both transport protocols to bypass filtering
- DoH Fallback: Optional integration with DNS over HTTPS
3.3 Hardware Configuration
- Platform: Raspberry Pi 4B or x86 mini-PC (e.g., Lenovo M710q)
- Cost: Under $75 total (device + SD card or SSD)
- Operating System: Debian 12 or Ubuntu Server 24.04
- Memory Footprint: <100MB RAM idle
- Power Consumption: ~3-5W idle
4. Design Considerations
4.1 Affordability
- Hardware Sourcing: Use refurbished or SBCs to cut costs
- Software Stack: Entirely open source (dnscrypt-proxy, Unbound)
- No Licensing Fees: FOSS-friendly deployment for communities
4.2 Security
- Ephemeral Key Pairs: New keypairs every session prevent replay attacks
- Public Key Verification: Resolver keys are pre-published and verified
- No Logging: DNSCrypt proxies are configured to avoid retaining user metadata
- Anonymization Support: With relay chaining for metadata privacy
4.3 Maintainability
- Containerization (Optional): Docker-compatible setup for simple updates
- Remote Management: Secure shell access with fail2ban and SSH keys
- Auto-Updating Scripts: Systemd timers to refresh certificates and relay lists
5. Implementation
5.1 Installation Steps
- Install OS and dependencies:
bash sudo apt update && sudo apt install dnscrypt-proxy unbound - Configure
dnscrypt-proxy.toml: - Define listening port, relay list, and trusted resolvers
- Enable Anonymized DNS, fallback to DoH
- Configure Unbound (optional):
- Run as recursive backend
- Firewall hardening:
- Allow only DNSCrypt port (default: 443 or 5353)
- Block all inbound traffic except SSH (optional via Tailscale)
5.2 Challenges
- Relay Performance Variability: Some relays introduce latency; solution: geo-filtering
- Certificate Refresh: Mitigated with daily cron jobs
- IP Rate-Limiting: Mitigated with DNS load balancing
6. Evaluation
6.1 Performance Benchmarks
- Query Resolution Time (mean):
- Local resolver: 12–18ms
- Upstream via DoH: 25–35ms
- Concurrent Users Supported: 100+ without degradation
- Memory Usage: ~60MB (dnscrypt-proxy + Unbound)
- CPU Load: <5% idle on ARM Cortex-A72
6.2 Security Audits
- Verified with dnsleaktest.com and
tcpdump - No plaintext DNS observed over interface
- Verified resolver keys via DNSCrypt community registry
7. Use Cases
7.1 Personal/Home Use
- Secure DNS for all home devices via router or Pi-hole integration
7.2 Educational Institutions
- Provide students with censorship-free DNS in oppressive environments
7.3 Community Mesh Networks
- Integrate DNSCrypt into decentralized networks (e.g., Nostr over Mesh)
7.4 Business VPNs
- Secure internal DNS without relying on third-party resolvers
8. Consider
This idea has presented a practical, affordable approach to deploying a secure DNSCrypt proxy server. By leveraging open-source tools, minimalist hardware, and careful design choices, it is possible to democratize access to encrypted DNS. Our implementation meets the growing need for privacy-preserving infrastructure without introducing prohibitive costs.
We demonstrated that even modest devices can sustain dozens of encrypted DNS sessions concurrently while maintaining low latency. Beyond privacy, this system empowers individuals and communities to control their own DNS without corporate intermediaries.
9. Future Work
- Relay Discovery Automation: Dynamic quality-of-service scoring for relays
- Web GUI for Management: Simplified frontend for non-technical users
- IPv6 and Tor Integration: Expanding availability and censorship resistance
- Federated Resolver Registry: Trust-minimized alternative to current resolver key lists
References
- DNSCrypt Protocol Specification v2 – https://dnscrypt.info/protocol
- dnscrypt-proxy GitHub Repository – https://github.com/DNSCrypt/dnscrypt-proxy
- Unbound Recursive Resolver – https://nlnetlabs.nl/projects/unbound/about/
- DNS Security Extensions (DNSSEC) – IETF RFCs 4033, 4034, 4035
- Bernstein, D.J. – Cryptographic Protocols using Curve25519 and Poly1305
- DNS over HTTPS (DoH) – RFC 8484
-
 @ d34e832d:383f78d0
2025-04-22 21:14:46
@ d34e832d:383f78d0
2025-04-22 21:14:46Minecraft remains one of the most popular sandbox games in the world. For players who wish to host private or community-based servers, monthly hosting fees can quickly add up. Furthermore, setting up a server from scratch often requires technical knowledge in networking, system administration, and Linux.
This idea explores a do-it-yourself (DIY) method for deploying a low-cost Minecraft server using common secondhand hardware and a simple software stack, with a focus on energy efficiency, ease of use, and full control over the server environment.
2. Objective
To build and deploy a dedicated Minecraft server that:
- Costs less than $75 in total
- Consumes minimal electricity (<10W idle)
- Is manageable via a graphical user interface (GUI)
- Supports full server management including backups, restarts, and plugin control
- Requires no port forwarding or complex network configuration
- Delivers performance suitable for a small-to-medium number of concurrent players
3. Hardware Overview
3.1 Lenovo M710Q Mini-PC (~$55 used)
- Intel Core i5 (6th/7th Gen)
- 8GB DDR4 RAM
- Compact size and low power usage
- Widely available refurbished
3.2 ID Sonics 512GB NVMe SSD (~$20)
- Fast storage with sufficient capacity for multiple Minecraft server instances
- SSDs reduce world loading lag and improve backup performance
Total Hardware Cost: ~$75
4. Software Stack
4.1 Ubuntu Server 24.04
- Stable, secure, and efficient operating system
- Headless installation, ideal for server use
- Supports automated updates and system management via CLI
4.2 CasaOS
- A lightweight operating system layer and GUI on top of Ubuntu
- Built for managing Docker containers with a clean web interface
- Allows app store-like deployment of various services
4.3 Crafty Controller (via Docker)
- Web-based server manager for Minecraft
- Features include:
- Automatic backups and restore
- Scheduled server restarts
- Plugin management
- Server import/export
- Server logs and console access
5. Network and Remote Access
5.1 PlayIt.gg Integration
PlayIt.gg creates a secure tunnel to your server via a relay node, removing the need for traditional port forwarding.
Benefits: - Works even behind Carrier-Grade NAT (common on mobile or fiber ISPs) - Ideal for users with no access to router settings - Ensures privacy by hiding IP address from public exposure
6. Setup Process Summary
- Install Ubuntu Server 24.04 on the M710Q
- Install CasaOS via script provided by the project
- Use CasaOS to deploy Crafty Controller in a Docker container
- Configure Minecraft server inside Crafty (Vanilla, Paper, Spigot, etc.)
- Integrate PlayIt.gg to expose the server to friends
- Access Crafty via browser for daily management
7. Power Consumption and Performance
- Idle Power Draw: ~7.5W
- Load Power Draw (2–5 players): ~15W
- M710Q fan runs quiet and rarely under load
- Performance sufficient for:
- Vanilla or optimized Paper server
- Up to 10 concurrent players with light mods
8. Cost Analysis vs Hosted Services
| Solution | Monthly Cost | Annual Cost | Control Level | Mods Support | |-----------------------|--------------|-------------|----------------|---------------| | Commercial Hosting | $5–$15 | $60–$180 | Limited | Yes | | This Build (One-Time) | $75 | $0 | Full | Yes |
Return on Investment (ROI):
Break-even point reached in 6 to 8 months compared to lowest hosting tiers.
9. Advantages
- No Subscription: Single upfront investment
- Local Control: Full access to server files and environment
- Privacy Respecting: No third-party data mining
- Modular: Can add mods, backups, maps with full access
- Low Energy Use: Ideal for 24/7 uptime
10. Limitations
- Not Ideal for >20 players: CPU and RAM constraints
- Local Hardware Dependency: Physical failure risk
- Requires Basic Setup Time: CLI familiarity useful but not required
11. Future Enhancements
- Add Dynmap with reverse proxy and TLS via CasaOS
- Integrate Nextcloud for managing world backups
- Use Watchtower for automated container updates
- Schedule daily email logs using system cron
12. Consider
This idea presents a practical and sustainable approach to self-hosting Minecraft servers using open-source software and refurbished hardware. With a modest upfront cost and minimal maintenance, users can enjoy full control over their game worlds without recurring fees or technical hassle. This method democratizes game hosting and aligns well with educational environments, small communities, and privacy-conscious users.
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ d34e832d:383f78d0
2025-04-22 18:15:42
@ d34e832d:383f78d0
2025-04-22 18:15:42Proof Of Concept
In a world where decentralization often hinges on the strength of its weakest node, the idea of federation—applied not to content moderation or identity, but strictly to communication protocols—opens up intriguing possibilities. In this model, Nostr relays do not operate in total isolation, nor do they function in a single cohesive mesh. Instead, they form selective, encrypted alliances, communicating through secure tunnels while preserving autonomy.
💡 The Core Idea
Relays remain sovereign, but may establish peer-to-peer encrypted channels with other trusted relays using Elliptic Curve Diffie-Hellman (ECDH) to generate shared secrets. These secrets are then used to encrypt communication tunnels—facilitating a federated communication layer.
Each relay is free to choose: - Whom it speaks to - How often - What types of events are relayed through the tunnel
But never must it rely on a central coordinator.
🔁 Schnorr for Authentication
While ECDH can create the secure tunnel, Schnorr signatures (already a part of Nostr’s pubkey-based design) can be used to authenticate the origin of the data inside. This keeps the integrity of messages intact even when traveling over shared or hostile networks.
Use case: - Relay A and Relay B establish an ECDH-based shared key. - All communication is tunnel-encrypted with this shared key. - Inside the tunnel, every message still carries a Schnorr signature, proving its source.
This separation of transport-level encryption from message-level authenticity provides an elegant layering of security.
🌐 Practical Benefits
- Obfuscation: Encrypted tunnels reduce visibility into relay-to-relay traffic patterns.
- Privacy: Federation over encrypted channels shields metadata and protects against surveillance.
- Resilience: Relays can route around censorship by tunneling through less obvious peers.
- Synergy: Specific relay clusters can form ephemeral or long-term alliances—say, art relays or academic relays—without disclosing their full graph to the world.
🧩 Optional Enhancements
- Noise Protocol Framework to standardize encrypted relay tunnels.
- Tor Hidden Services or I2P for transport obfuscation.
- Relay Reputation Systems to gauge trust before federation.
- Dynamic Federation Negotiation: using NIP-like proposals over encrypted handshakes to initiate or terminate communication agreements.
🌱 Case In Point
This is not about governing content, users, or identities—this is about strengthening how relays talk. By embracing federated communication via ECDH and Schnorr-secured tunnels, Nostr relays could evolve into a resilient underground of trust-minimized, pseudonymous routers that defy surveillance while amplifying decentralization.
federated communication via ECDH and Schnorr-authenticated encrypted tunnels between Nostr relays:
markdown NIP-xyz: Federated Encrypted Relay Communication Status: Draft Type: Relay Created: 2025-04-22
Summary
This NIP proposes a method for encrypted, authenticated communication between Nostr relays using ECDH-based tunnels for transport encryption and Schnorr signatures for payload integrity. This federation model allows relays to communicate securely while maintaining full autonomy, enhancing privacy, censorship resistance, and interoperability.
Motivation
Nostr’s decentralized architecture relies heavily on relays, which currently operate in isolated or broadcast modes. There is no standard for secure, peer-to-peer communication between relays themselves, outside of client interactions.
Introducing encrypted tunnels between relays offers:
- Privacy: Reduces metadata leakage across public or adversarial networks.
- Resilience: Allows relays to forward events and metadata through trusted peers when direct access is blocked or filtered.
- Autonomy: Federation is opt-in and purely communicational—no centralized authority or directory is involved.
- Extensibility: Enables experimental protocols or content-specific subnets without altering the global Nostr model.
Specification
1. Key Exchange via ECDH
Each relay maintains: - A persistent relay keypair:
relay_pubkey,relay_privkey- Optionally: rotating session keys for forward secrecyWhen two relays (A and B) wish to establish communication: - They exchange their public keys (
relay_pubkey_Aandrelay_pubkey_B) - Both calculate a shared secret using ECDH oversecp256k1:plaintext shared_secret = SHA256(ECDH(relay_privkey_A, relay_pubkey_B))This
shared_secretis used to derive an encryption key for an authenticated symmetric cipher, such as AES-GCM or ChaCha20-Poly1305.
2. Encrypted Tunnel Establishment
Once the shared secret is derived: - All messages between relays are sent through an encrypted tunnel - Transport can be TCP, WebSocket, or HTTP/3 over QUIC, optionally via Tor or I2P
A RelayHello message is exchanged encrypted, optionally containing:
json { "type": "relay_hello", "relay_name": "nostr.relay.example", "features": ["forwarding", "dedup", "metadata"], "timestamp": 1684000000, "sig": "<Schnorr-signed payload>" }The
sigis a Schnorr signature from therelay_pubkey, verifying the message content.
3. Event Forwarding
Relays may forward selected event types across tunnels, such as: - Kind 1 (Text Note) - Kind 3 (Contacts) - Kind 5 (Deletion Notices) - Custom kinds (with mutual agreement)
All forwarded events MUST retain original client-level signatures. Relay-to-relay metadata (like timestamps, relay hints, or scores) may be added in a separate metadata envelope.
4. Access Control and Policies
Each relay maintains a federation list, including: - Public key of the peer relay - Features enabled - Rate limits and quotas - Last active session or rotation timestamp
Relays MAY: - Deny tunnel requests - Rotate keys periodically - Restrict communication to a whitelist - Use Proof-of-Work or tokens for DoS protection
5. Optional Features
- Forward Secrecy: ephemeral key pairs with HKDF for short sessions
- Relay Reputation: signed relay trust scores (future NIP)
- Message Compression: gzip or zstd on tunnel payloads
- Encrypted Gossip: tunnel-specific metadata routing
Compatibility
This NIP is backward-compatible. Relays that do not implement it will simply not participate in tunnel-based communication.
No changes are required from Nostr clients.
Reference Implementation (Proposed)
nostr-tunnel-relay: Rust-based relay that supports federated encrypted tunnelsnostr-relay-link: CLI tool to establish and monitor tunnels- Example configs for federation policies in JSON or TOML
Rationale
- ECDH ensures only the two relays involved can decrypt tunnel data
- Schnorr signatures authenticate content without duplicating identity schemes
- Federation is scoped only to communication, preserving Nostr’s core simplicity
Security Considerations
- Relay pubkeys must be carefully verified to prevent MITM
- Session expiration and key rotation should be configurable
- Replay protection and nonce management are required for AEAD ciphers
- Metadata leakage minimized by default obfuscation or Tor-based transport
NIP.eshgham
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 57d56d16:458edffd
2025-04-22 23:43:13
@ 57d56d16:458edffd
2025-04-22 23:43:13Hello. I've had a look at shopstr. You can find my instance of shopstr here so you can have a look yourself: https://shopstr.tectumordo.com/marketplace
Wondering your thoughts on Shopstr. I'm looking to start selling some things. Handcrafted Items / Services.
Anyone have any insights into shopstr, or something similar.
originally posted at https://stacker.news/items/953976
-
 @ f32184ee:6d1c17bf
2025-04-22 22:56:11
@ f32184ee:6d1c17bf
2025-04-22 22:56:11Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. NextBlock’s PROMO Protocol, designed while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media -]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media -]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
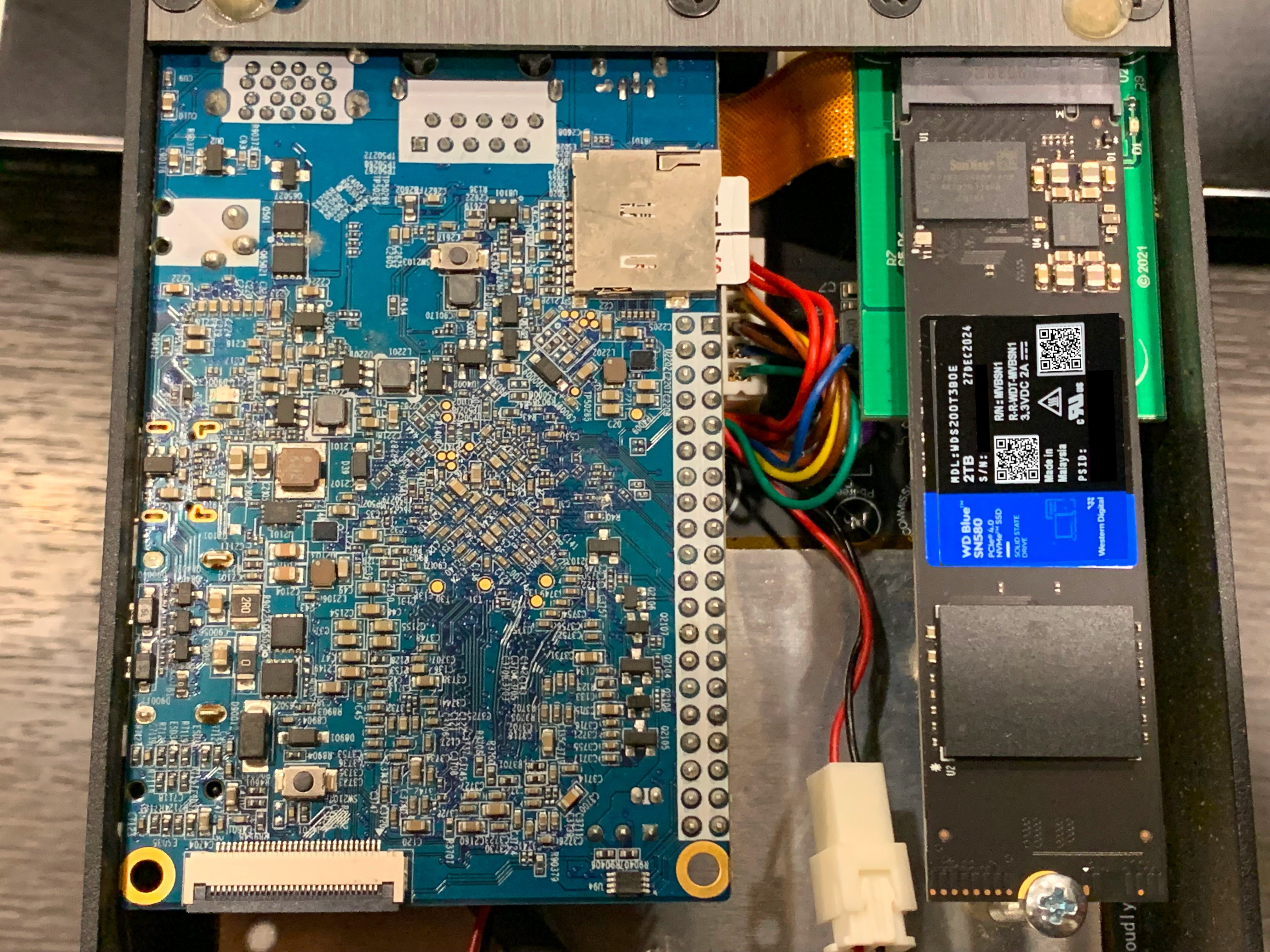 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
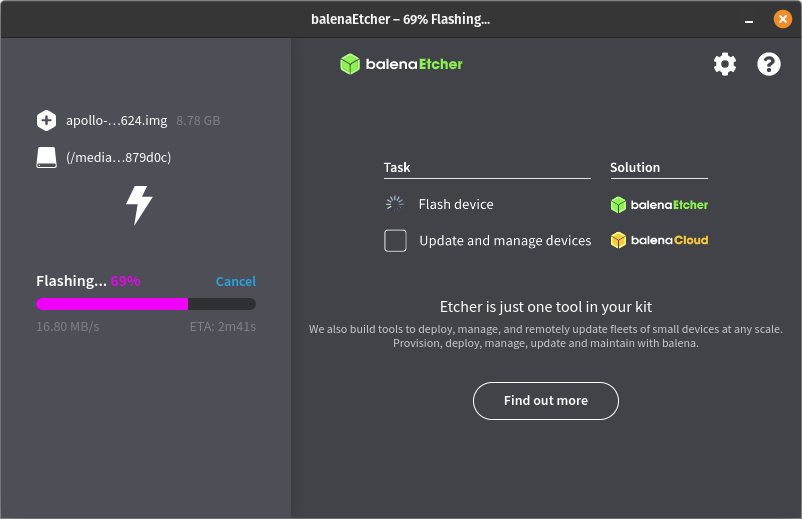 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
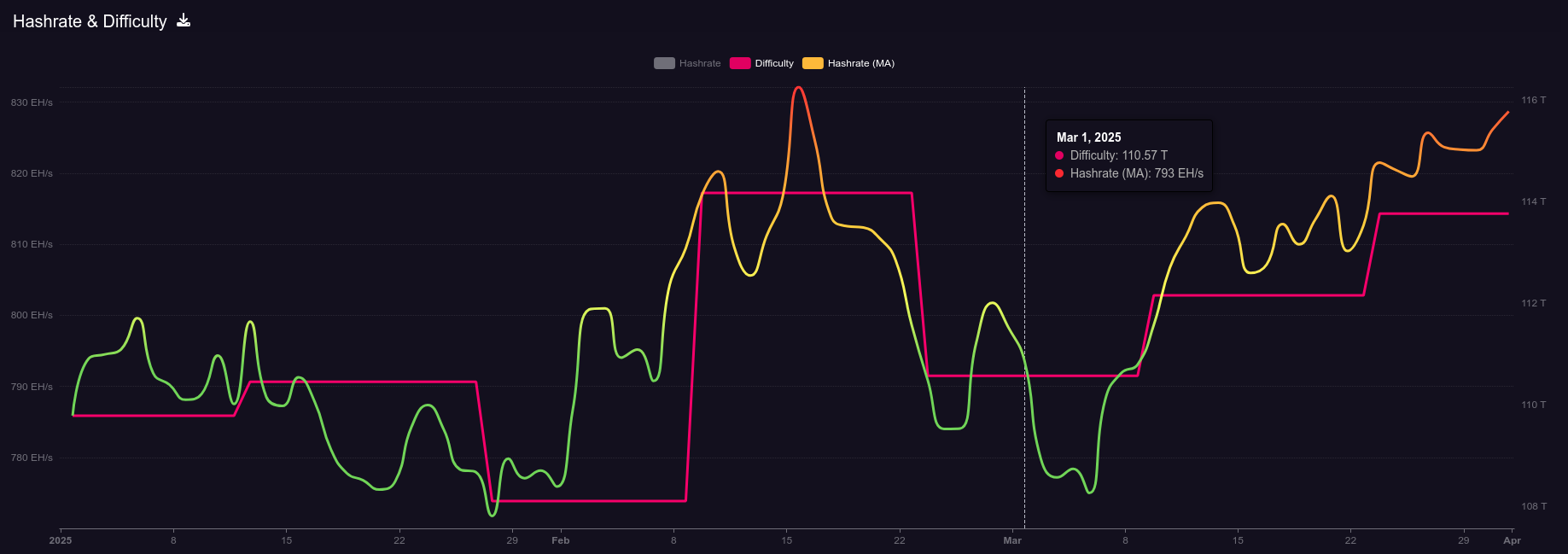 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
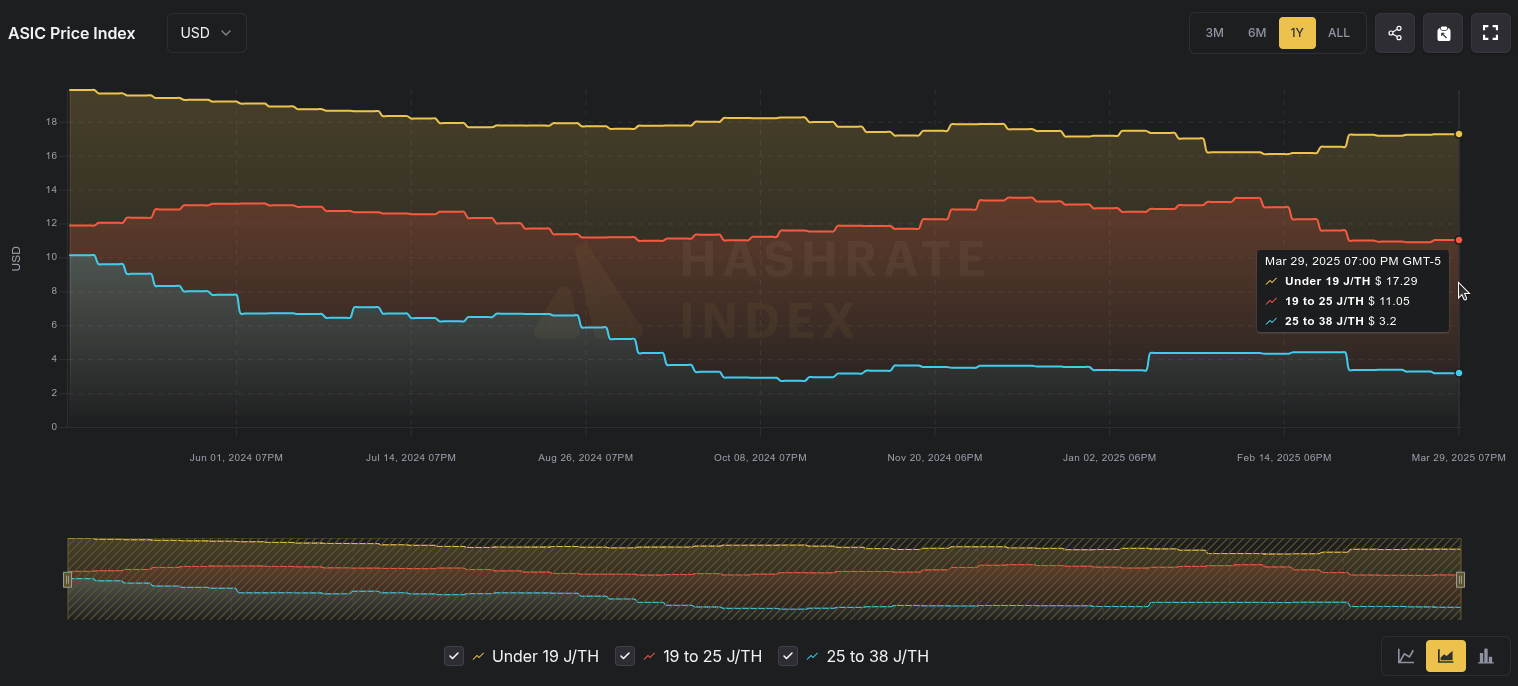 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
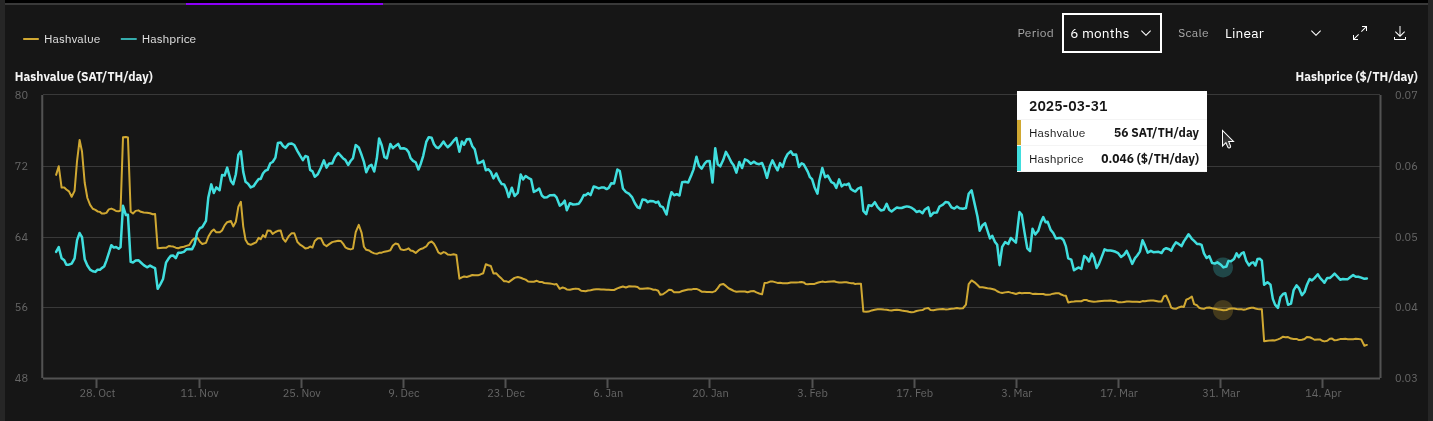 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ ba36d0f7:cd802cba
2025-04-22 20:30:45
@ ba36d0f7:cd802cba
2025-04-22 20:30:45| Pieza | Movimiento | Reglas Especiales | | --------- | ---------------------------------- | --------------------------- | | Peón | 1 casilla adelante (o 2 al inicio) | Captura al paso, coronación | | Torre | Líneas rectas | Enroque | | Caballo | En "L" (2+1) | Salta piezas | | Alfil | Diagonales | Atrapado en un color | | Dama | Cualquier dirección | Ninguna | | Rey | 1 casilla en cualquier dirección | Enroque, jaque mate |
1. Peón (♙ / ♟️)
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).

- Captura: En diagonal (1 casilla).
 > Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
> Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
2. Torre (♖ / ♜)
- Mueve: Líneas rectas (sin límite de casillas).

- Especial: Participa en el enroque.
3. Caballo (♘ / ♞)
-
Mueve: En "L" (2 casillas en una dirección + 1 perpendicular).
-
Única pieza que salta sobre otras.
4. Alfil (♗ / ♝)
-
Mueve: Diagonales (sin límite).
-
Siempre permanece en el mismo color de casilla.

5. Dama (♕ / ♛)
- Mueve: Cualquier dirección (recto o diagonal).

- ¡La pieza más poderosa!
6. Rey (♔ / ♚)
- Mueve: 1 casilla en cualquier dirección.

Especial:
- Enroque: Cambia de lugar con una torre (si no hay obstáculos/jaques). - Jaque mate: Pierde si queda atrapado sin escapatoria.
Cómo mover
-
Un movimiento por turno.
-
Elige tu pieza y colócala en una casilla legal.
-
Solo tu color: Blancas mueven primero, luego negras, alternando.
-
No pasar: Debes mover si es tu turno.
Cómo capturar ("comer")
-
Ocupa la casilla de una pieza rival: Reemplázala con tu pieza.
-
Peones capturan solo en diagonal (no de frente).
-
Los reyes no pueden ser capturados (el jaque mate termina el juego).
✔ Jaque: Ataca al rey enemigo (debe escapar en su siguiente turno).
❌ Ilegal: Mover a jaque o dejar a tu rey en jaque.
Movimientos especiales
|Movimiento|Regla Clave|Notación| |---|---|---| |Enroque|Rey + torre, sin movimientos previos|
0-0| |Coronación|Peón→cualquier pieza en 8ª fila|e8=D| |Captura al paso|Captura un peón que avanzó 2 casillas|exd6 a.p.|
1. Enroque ("La escapatoria del rey")
-
Qué: Rey y torre se mueven juntos en un turno.
Cómo: -
Rey mueve 2 casillas hacia una torre.
-
Torre "salta" al lado opuesto del rey.

Reglas: - Sin jaques: El rey no puede estar en jaque ni pasar por casillas atacadas. - Sin movimientos previos: Ni el rey ni esa torre deben haberse movido antes.
Tipos:
- Corto (lado del rey, rápido):0-0- Largo (lado de la dama, seguro):0-0-0
2. Coronación ("Coronar")
-
Qué: Peón llega a la 8ª fila → se convierte en cualquier pieza (usualmente Dama).
-
Cómo: Reemplaza el peón (incluso si ya tienes esa pieza).
Dato curioso: Puedes tener 9 damas (1 original + 8 coronaciones).
Ejemplo: Peón en h8 se convierte en Dama →h8=D.
3. Captura al paso (Del francés "en passant")
-
Cuándo: Un peón rival avanza 2 casillas y queda al lado del tuyo.
-
Cómo: Captúralo en diagonal (como si hubiera movido 1 casilla).

Regla: Debes hacerlo inmediatamente (solo en el turno siguiente)
Recurso digitales
Guia para principiantes - Lichess.org https://lichess.org/study/Hmb28fbv/QRyxzgre
Ajedrez desde cero - Youtube.com https://www.youtube.com/watch?v=YPf9fSY_K2k&list=PLWgqlpb234bHv38g6zXoi3WIJJonzZSAl&index=8
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).
-
 @ a8d1560d:3fec7a08
2025-04-22 22:52:15
@ a8d1560d:3fec7a08
2025-04-22 22:52:15Based on the Free Speech Flag generator at https://crocojim18.github.io/, but now you can encode binary data as well.
https://free-speech-flag-generator--wholewish91244492.on.websim.ai/
Please also see https://en.wikipedia.org/wiki/Free_Speech_Flag for more information about the Free Speech Flag.
Who can tell me what I encoded in the flag used for this longform post?
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ 4cebd4f5:0ac3ed15
2025-04-22 16:07:40
@ 4cebd4f5:0ac3ed15
2025-04-22 16:07:40Tóm tắt Hackathon
Naija HackAtom kết thúc thành công với 160 developer đăng ký và 51 dự án được phê duyệt. Sự kiện hướng đến phát triển Interchain, Cosmos Hub và Atom Economic Zone (AEZ) trong cộng đồng Web3 Nigeria, tập trung nuôi dưỡng tài năng địa phương, cung cấp nguồn lực và xây dựng ứng dụng blockchain sử dụng token $ATOM.
Trọng tâm bao gồm Interchain Security, CosmWasm, và các giải pháp tối ưu tiện ích của ATOM. Dự án nổi bật như nền tảng chuyển tiền xuyên chuỗi và marketplace phi tập trung cho nông dân châu Phi, thể hiện ứng dụng sáng tạo công nghệ Cosmos.
Giải thưởng 8.000 USD được trao cho sáng tạo về UI/UX, community engagement và giải pháp độc đáo sử dụng ATOM. Qua workshop và hướng dẫn, dự án được đánh giá dựa trên technical feasibility, innovation, impact và user experience. Sự kiện góp phần phát triển hệ sinh thái blockchain tại Nigeria và châu Phi.
Các dự án đoạt giải
Naija HackAtom là hackathon đầu tiên tại Nigeria tập trung vào Cosmos và ATOM, thu hút 500+ người tham gia, trong đó có 160 developer. Với hỗ trợ từ ATOMAccelerator, 57 dự án được nộp, chọn ra 18 đội vào chung kết.
Main Prize Winners
- Beep: Nền tảng token hóa đồng Naira, hỗ trợ giao dịch liền mạch với tAtom.
- Padi [Crypto Go Fund Me]: Platform gây quỹ dựa trên token qua blockchain.
- ATwork: Nền tảng freelancing phi tập trung kết nối freelancer và khách hàng trên Cosmos.
Unique Solution/Product Prize Winners
- LendPro: Giao thức cho vay với quản trị tài chính hợp tác qua blockchain.
- Tradi-App: Nền tảng AI phân tích giao dịch bảo mật trên Secret Network.
- Delegated Staking Agent (DSA): Cung cấp staking và bỏ phiếu quản trị trên Cosmos, tích hợp AI để tăng cường bảo mật.
- Neutron NFT Launch: Đơn giản hóa tạo và giao dịch NFT qua tích hợp AI và blockchain.
Secret Network Bounty Winners
- Prompt Hub: Marketplace prompt AI tập trung privacy.
- Secret AI Writer: Nền tảng viết lách AI với lưu trữ blockchain an toàn.
- Tradi-App
ChihuahuaChain Bounty Winners
- woof-dot-fun: Nhân bản Pump.Fun với chức năng token và bond curve.
- Vault Quest: Giao thức tiết kiệm "không mất mát" sử dụng chiến lược DeFi để phân phối giải thưởng.
Akash Bounty Winner
- Jarvis AI: Trợ lý ảo điều khiển bằng giọng nói để quản lý tài nguyên cloud.
Xem toàn bộ dự án tại Naija HackAtom Projects.
Về Nhà tổ chức
Cosmos Hub Africa
Cosmos Hub Africa thúc đẩy blockchain và hệ sinh thái Cosmos tại châu Phi, đóng vai trò quan trọng trong phát triển mạng lưới phi tập trung và hợp tác ngành. Tổ chức triển khai dự án nâng cao scalability và interoperability, đồng thời tập trung vào giáo dục blockchain và xây dựng cơ sở hạ tầng để thúc đẩy đổi mới và tích hợp với nền kinh tế truyền thống.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ d34e832d:383f78d0
2025-04-22 08:40:25
@ d34e832d:383f78d0
2025-04-22 08:40:25
In the twilight of forgotten eras, where the whispers of the past wove through the air like a ghostly melody, two shadowy figures emerged beneath an ageless sky. She was Eve, not the emblem of gardens, but the Mitochondrial Eve—her essence pulsing within the very mitochondria that spark life in each human heartbeat. He stood before her as Adam, not forged from soil, but the Y-Chromosome Adam—guardian of a singular lineage, his heritage dancing through the veins of sons alone.
Their encounter was not one of flesh and blood, but a meeting of symbols, sparked by the insatiable curiosity of humanity, prowling through the labyrinth of DNA, seeking to uncover the tales of their primordial roots.
In the ethereal glimmer of a timeless pool, two figures stood, their outlines rippling like whispered secrets. They were neither lovers nor allies, nor of the same age, yet their names danced together in every headline and wisdom-filled book.
Today, however, was different—they had gathered at the brink of the infinite to unravel the threads of their intertwined destinies.
As the twilight draped its ethereal cloak over the meadow, Eve let her fingers dance through the glimmering starlight, weaving dreams from its luminous threads.
“You know,” she mused, her voice a whisper carried by the evening breeze, “they often ponder why fate kept us apart. Why our paths never crossed beneath the same sun.”Adam’s lips curled into a wry smile, his eyes reflecting the cosmos above.
“Perhaps they seek a narrative that is neat and orderly, a story with perfect symmetry,” he replied, the gentle rustle of leaves echoing his words.Eve shook her head softly, her gaze fixed on the swirling constellations.
“Ah, but nature, dear Adam,” she countered with a glimmer of mischief, “is a master of chaos. It delights in the untamed, the beautiful mess of existence.”In the grand tapestry of time, two figures emerged from the mists of ancient Africa:
Mitochondrial Eve, a woman of vibrant spirit, who roamed the earth around 150,000 to 200,000 years ago, and
Y-Chromosome Adam, a man of strength and wisdom, appearing some 60,000 to 100,000 years later.Though separated by a chasm of tens of thousands of years, they were not the sole beings of their era, yet in the intricate web of life, they were the most recent ancestors, bearers of unbroken trails of maternal and paternal lines, from which all humanity flows.
Their stories intertwine, echoing through generations, whispers of a time long past.
In a hushed tone, Eve shared the tale of her lineage, weaving a rich tapestry of time.
“Behold my daughters,” she said, her eyes gleaming with pride. “From them sprang another generation, and those daughters too have borne daughters.This precious thread of life, my mitochondrial DNA, weaves through the tapestry, handed down solely by women.
With each passing age, while many lines faded into shadows—some in mere moments, others enduring for centuries—mine flowed on, a river of continuity and strength.
My legacy, a steadfast whisper across generations, defied the silence of so many others.”In a dimly lit room, Adam pondered the weight of generations past.
“And what of mine?” he inquired, his voice tinged with a mix of curiosity and melancholy.He shook his head slowly, as if unraveling a forgotten tale.
“The Y-chromosome, it weaves a delicate thread through the tapestry of life.
Passed from fathers to sons, a fleeting whisper of legacy, vanishing if a man begets no heirs.Like branches of a grand oak, countless lines have been severed by the cruel hands of war, the relentless march of disease, and the silent grasp of chance.
Mine is not the sole survivor in this timeless struggle, but it is the one that defied extinction—standing resilient against the bottleneck of time, thriving into the present day, a testament to tenacity and fate.”Their inheritance patterns are straightforward but ruthless.
Mitochondrial DNA (mtDNA) is stable and abundant, making it a powerful marker for tracing maternal lineage.
It mutates slowly, preserving a clear path backward.In contrast, the Y-chromosome, despite its utility in tracing paternal lines, is subject to greater volatility: smaller effective population sizes, male-specific extinction events, and the disproportionate reproductive success of a few males—all contribute to a narrower, more chaotic record.
In a dimly lit chamber nestled among ancient trees, Eve’s voice resonated with the wisdom of ages.
“The numbers are not our destiny,” she declared, her finger tracing a pattern in the soil.
“They are mere echoes of survival, tales of those who dared to pass their legacy—a lineage of children begetting children, weaving a tapestry of existence.”Adam stood by, thoughtful as a storm brewing on a distant horizon.
“Indeed, lineages dissolve like whispers in the wind,” he mused, his gaze fixed on the moonlight filtering through the leaves.
“Some genetic threads endure not from superiority, but sheer fortune. Bottlenecks of fate, the whims of founders, the swirling dance of genetic drift—these unseen forces hold the key to who emerges amidst the chaos of time.”Together, they pondered the intricate dance of life, where luck and survival intertwined, crafting the very fabric of their world.
Eve paused, her voice a whisper woven with time.
“And so it is,” she mused, “the humans trace their lineage back to me, painting me as the primordial bloom of existence.Yet, shadows linger—my cousins, neighbors, even rivals shared this space, vibrant as I, yet their stories faded like whispers in the wind.
They bore no daughters to carry forth their tales, only their echoes lingered, lost in the tapestry of forgotten history…”
In the shadow of an ancient, pulsing tree that mirrored their very essence, Adam mused aloud,
“I came along far down the line, but not right at the start.
I am but one among countless men, and in the end, only my Y-line remained, a solitary thread in the tapestry of time.
Your lineage, however, stretches across continents, vibrant and thriving.”They stood quietly, lost in the vast glow of humanity’s fractal branches, each flicker representing a birth, a connection, a glimmer of possibility.
“Isn’t it amusing?” Adam chuckled, breaking the reverie.
“They pair us as if we were a couple, forever intertwined.”Eve’s laughter echoed like sweet music.
“Merely symbols, nothing deeper. We are called ancestors, yet we are merely the fortunate survivors of an exquisite genetic lottery.”Adam continued,
“And yet, the very essence of your spark resides in every human’s mitochondria, while half of them carry my signature in their Y chromosome.”Eve’s voice was soft as she spoke, weaving a tapestry of understanding.
“Ah, but dear friend, ancestry is far more than mere lineage.
It’s like tracing the delicate threads of a grand tapestry, where some strands are visible, yet countless others lie hidden in the shadows of time.Each soul walking upon this earth is a descendant of a multitude of individuals from ages long past.
Their names may fade like whispers in the wind, and their unique genes become mere echoes of history.
Yet, amidst this beautiful chaos, the patterns of our heritage forever linger, binding us in an unseen embrace of shared existence.”As Adam stood beneath the shimmering canopy of stars, he pondered aloud,
“Maybe the tale isn’t solely ours. It’s about the delicate yet unwavering dance of life itself.”Eve, her eyes reflecting the celestial lights, agreed with a subtle nod.
“Indeed, for no single thread can unveil the entirety of the narrative.
One must gaze upon the grand tapestry woven through time.”They dimmed away, not with finality, but like starlight traversing the vastness of the cosmos—whispers that remind us history bends and weaves, a spider’s web of fate, woven with threads of fortune, affection, and heartache, where beams of hope dance through the dark.
Within each of us, they linger still, a harmonious symphony resonating with the voices of billions, echoing through time.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 8d34bd24:414be32b
2025-04-20 14:18:37
@ 8d34bd24:414be32b
2025-04-20 14:18:37I started working on this post a couple weeks ago, and out of pure accident, it became my Resurrection Sunday (Easter) post. Maybe it was by God’s design. On Resurrection Sunday, Jesus was raised from the grave. Forty days later he rose to heaven before many witnesses. Someday in the future, the dead in Christ will be raised from the dead, and all believers will be snatched up to heaven. Maybe this is this right post for Resurrection Sunday.
For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. … For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. (1 Thessalonians 4:14, 16-17) {emphasis mine}
It always amazes me that some Christians don’t believe in the rapture of the church. I understand how there can be a disagreement about exactly when the rapture is to occur, but I can’t comprehend how some Christians don’t believe the rapture is coming or that they believe that the rapture happened in the first century.
Let’s start with the three key verses on the subject and then we’ll get into more details.
Key Rapture Verses
I didn’t notice that this first passage referred to the rapture until it was pointed out to me. I was so focused on Jesus preparing a place, that I missed the key sentence.
“Do not let your heart be troubled; believe in God, believe also in Me. In My Father’s house are many dwelling places; if it were not so, I would have told you; for I go to prepare a place for you. If I go and prepare a place for you, I will come again and receive you to Myself, that where I am, there you may be also. (John 14:1-3) {emphasis mine}
Jesus, after His resurrection and as promised in these verses, rose up to heaven to go prepare a place for believers. He will then return to bring believers to Himself. This whole idea would have been particularly clear for the Jews when it was written. When a bride and groom were engaged (a legal contract where they were considered married), the groom would go and prepare a place for them to live. It could be an extra room in his parent’s home or it could be a whole new home. The bride didn’t know when the groom would return to take her to himself to become man and wife. In the same way, Jesus has gone away to prepare a place for us and will return at a time we do not know. Just as the Jewish bride had to be ready to leave with her groom when he suddenly arrived, we also must be ready for Jesus’s return when He will snatch us from earth and take us home with Him to heaven.
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
The Bible has a wonderful euphemism for the death of believers. It speaks of them falling asleep because death is not the end for believers. It is just a pause, a separation of body and spirit, before we are raptured to Jesus, to meet Him in the sky, where we will receive a new resurrection body, just as Jesus received when He was raised from the dead 3 days after His crucifixion. Both the dead in Christ and the alive in Christ will “be caught up together with them in the clouds to meet the Lord in the air.” God gives us this promise in the Bible to comfort us. It gives us comfort that death is not the end and we will see our fellow believers again in heaven one day. It also gives us comfort that we will not have to experience God’s wrath. “For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
What else can we learn about the rapture?
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. O death, where is your victory? O death, where is your sting?” The sting of death is sin, and the power of sin is the law; but thanks be to God, who gives us the victory through our Lord Jesus Christ. (1 Corinthians 15:50-57) {emphasis mine}
The rapture will be an instantaneous change from our perishable bodies to imperishable, whether we are alive in Christ or dead in Christ. At the rapture we “will be raised imperishable.” I am very excited to be snatched up into the air, receive a new, eternal body, and meet Jesus face-to-face.
There is one more passage that I believe talks of the rapture that is a bit more subtle from Isaiah.
The righteous man perishes, and no man takes it to heart;\ And devout men are taken away, while no one understands.\ For the righteous man is taken away from evil,\ **He enters into peace;\ They rest in their beds,\ Each one who walked in his upright way. (Isaiah 57:1-2) {emphasis mine}
The seven year Tribulation is the wrath of God poured out on those who rejected Him and the merciful, last chance warning before eternal judgement. Those who have trusted in Jesus (the devout men, the righteous man) will be “taken away from evil” and will “enter into peace.” Instead of experiencing God’s wrath, they will experience His peace. Instead of experience horror, they will “rest in their beds.”
The Seven Raptures Before the Rapture of the Church
How can we know that we will be raptured to heaven to be with Jesus forever? One way is because people have been raptured before (in different ways)
I am borrowing the organization of this section from Chapter 9 of “The End: Everything You’ll Want to Know about the Apocalypse” by Mark Hitchcock, which I happen to be reading at the moment.
-
Rapture of Enoch\ ”So all the days of Enoch were three hundred and sixty-five years. Enoch walked with God; and he was not, for God took him.” (Genesis 5:23-24) \ Enoch was raptured to heaven to be with God. He did not die, but went straight to God.
-
Rapture of Elijah\ ”And it came about when the Lord was about to take up Elijah by a whirlwind to heaven, that Elijah went with Elisha from Gilgal. … As they were going along and talking, behold, there appeared a chariot of fire and horses of fire which separated the two of them. And Elijah went up by a whirlwind to heaven.” (2 Kings 2:1,11) \ Elijah also was raptured to heaven without having to die. This passage gives more details. He went up in a whirlwind to heaven.
-
Rapture of Isaiah\ ”In the year of King Uzziah’s death I saw the Lord sitting on a throne, lofty and exalted, with the train of His robe filling the temple. Seraphim stood above Him, each having six wings: with two he covered his face, and with two he covered his feet, and with two he flew. And one called out to another and said,
“Holy, Holy, Holy, is the Lord of hosts,
The whole earth is full of His glory.”” (Isaiah 6:1-3)\ Isaiah’s situation was different. He was raptured to heaven only temporarily to be given God’s word and His prophecy and to call Isaiah for His good plan.
-
Rapture of Jesus\ ”And she gave birth to a son, a male child, who is to rule all the nations with a rod of iron; and her child was caught up to God and to His throne.” (Revelation 12:5)\ and\ ”And after He had said these things, He was lifted up while they were looking on, and a cloud received Him out of their sight. And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, “Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.” (Acts 1:9-11)\ I’ve listed two verses about Jesus’s rapture. The one from Revelation uses the Greek word harpazo, caught up - when translated to Latin, the word is rapturo, which is where we get our English word rapture. The verses in Acts give a more detailed description of His rapture to heaven, which is an example of our rapture. We are also promised His return.
-
Rapture of Philip\ ”And he ordered the chariot to stop; and they both went down into the water, Philip as well as the eunuch, and he baptized him. When they came up out of the water, the Spirit of the Lord snatched Philip away; and the eunuch no longer saw him, but went on his way rejoicing. But Philip found himself at Azotus, and as he passed through he kept preaching the gospel to all the cities until he came to Caesarea.” (Acts 8:38-40)
The rapture of Philip is different than the rest, because Philip was snatched away, not to heaven, but to Azotus. This is still an instance worth pointing out because it also uses the Greek word Harpazo.
- Rapture of Paul\ ”I know a man in Christ who fourteen years ago—whether in the body I do not know, or out of the body I do not know, God knows—such a man was caught up to the third heaven. And I know how such a man—whether in the body or apart from the body I do not know, God knows— was caught up into Paradise and heard inexpressible words, which a man is not permitted to speak.” (2 Corinthians 12:2-4)\ Like Isaiah, Paul was temporarily caught up (Harpazo) to heaven to receive revelation from God and then returned to his work and life on earth
These examples show God snatching people from one location to another, physically or spiritually for His good purpose. I expect it to happen again, shortly before the beginning of the seven year tribulation.
The 3 Views of the Rapture
There are three main views of the rapture: pre-trib, mid-trib, and post-trib. The basic beliefs are pretty much self explanatory by their name. Does the rapture occur before the tribulation, around the mid-point of the tribulation (which is right before the Great Tribulation or final 3.5 years), or after the tribulation? Which one fits what the Bible says better?
Although the Bible doesn’t directly say when the rapture happens, there are some very strong hints.
No wrath For saints
“For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
God promises believers that we are not destined for wrath. The tribulation is also known as1 “The wrath” (1 Thessalonians 5:9 & Revelation 11:18), “The wrath to come” (1 Thessalonians 1:10), “The great day of their wrath” (Revelation 6:17), “The wrath of God” (Revelation15:1,7, 14:10,19, 16:1), “The wrath of the lamb” (Revelation 6:16). There are numerous other equally unpleasant names, but I am sticking with those that use the word wrath. God promised believers that we are not destined for wrath. God never breaks His promises.
Similarly Revelation 3 promises believers will be kept from the hour of testing.
Because you have kept the word of My perseverance, I also will keep you from the hour of testing, that hour which is about to come upon the whole world, to test those who dwell on the earth. I am coming quickly; hold fast what you have, so that no one will take your crown. (Revelation 3:10-11) {emphasis mine}
The word quickly can also be translated suddenly. Although Jesus has not returned quickly by our way of figuring time, He will come suddenly.
No one knows when
“But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone.” (Matthew 24:36)
Scripture says the Tribulation starts when the Antichrist signs a peace treaty with Israel. If the rapture happens before the tribulation, then we won’t know when it will happen. If the rapture occurs at the mid-trib position, then it will happen 3.5 years after the peace treaty. If the rapture occurs post-trip, then it will happen 7 years after the peace treaty is signed and 3.5 years after the abomination of desolation, when the Antichrist declares himself god in the Jewish temple and requires the whole world to worship him. Only one makes sense if we can’t know when it happens.
Just as in the days of …
“For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left.” (Matthew 24:37-41)
If we look at the words of Jesus, He compares the rapture to the days of Noah. Life happening as normal, then God put Noah and his family on the ark and personally shut the door (Genesis 7:16). Then the flood came, pouring God’s wrath out on those who had rejected Him. In the same way, God will take believers out of the world before pouring out His wrath on those who remain. He clearly states, “one will be taken and one will be left.”
A parallel passage in Luke, not only talks of God removing Noah before the flood, but also tells of God removing Lot before destroying Sodom & Gomorrah.
For just like the lightning, when it flashes out of one part of the sky, shines to the other part of the sky, so will the Son of Man be in His day. But first He must suffer many things and be rejected by this generation. And just as it happened in the days of Noah, so it will be also in the days of the Son of Man: they were eating, they were drinking, they were marrying, they were being given in marriage, until the day that Noah entered the ark, and the flood came and destroyed them all. It was the same as happened in the days of Lot: they were eating, they were drinking, they were buying, they were selling, they were planting, they were building; but on the day that Lot went out from Sodom it rained fire and brimstone from heaven and destroyed them all. It will be just the same on the day that the Son of Man is revealed. (Luke:17:24-30) {emphasis mine}
Just as Noah was removed before judgement, so also was Lot removed before judgement. In both cases the majority of people were going about business, living normal lives, not expecting anything to change.
In Genesis 19, the angels must remove Lot and his family before the city is destroyed.
Then the two men said to Lot, “Whom else have you here? A son-in-law, and your sons, and your daughters, and whomever you have in the city, bring them out of the place; for we are about to destroy this place, because their outcry has become so great before the Lord that the Lord has sent us to destroy it.” \ …\ When morning dawned, the angels urged Lot, saying, “Up, take your wife and your two daughters who are here, or you will be swept away in the punishment of the city.” But he hesitated. So the men seized his hand and the hand of his wife and the hands of his two daughters, for the compassion of the Lord was upon him; and they brought him out, and put him outside the city. (Genesis 19:12-13,15-16) {emphasis mine}
In the last days, God has promised to remove us before His judgment is poured out on those who willfully rejected Him. Jesus spoke these words to comfort us and so we would not fear the end.
Removal of the Restrainer
Now we request you, brethren, with regard to the coming of our Lord Jesus Christ and our gathering together to Him, that you not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. Do you not remember that while I was still with you, I was telling you these things? And you know what restrains him now, so that in his time he will be revealed. For the mystery of lawlessness is already at work; only he who now restrains will do so until he is taken out of the way. Then that lawless one will be revealed whom the Lord will slay with the breath of His mouth and bring to an end by the appearance of His coming; (2 Thessalonians 2:1-8) {emphasis mine}
The restrainer is the Holy Spirit and the lawless one is the antichrist. This passage is saying that the antichrist will not be revealed until the restrainer is removed. The Holy Spirit indwells every believer. The believers also have to be removed before the antichrist is revealed, otherwise the Holy Spirit would have to leave the believers, leaving them alone during God’s wrath. That, of course, is contrary to God’s character, history, and promise.
Why is There No Mention of the Church During the Tribulation?
In the first three chapters of Revelation, the word church is used again and again. The church is not mentioned again until Revelation 19, regarding the Bride of Christ.
Let us rejoice and be glad and give the glory to Him, for the marriage of the Lamb has come and His bride has made herself ready.” It was given to her to clothe herself in fine linen, bright and clean; for the fine linen is the righteous acts of the saints. (Revelation 19:7-8) {emphasis mine}
All of this makes sense if the church was raptured before the tribulation. Therefore the bride (the church) has had seven years to make herself ready. They then get to descend with Jesus in the second coming of Jesus.
And I saw heaven opened, and behold, a white horse, and He who sat on it is called Faithful and True, and in righteousness He judges and wages war. His eyes are a flame of fire, and on His head are many diadems; and He has a name written on Him which no one knows except Himself. He is clothed with a robe dipped in blood, and His name is called The Word of God. And the armies which are in heaven, clothed in fine linen, white and clean, were following Him on white horses. From His mouth comes a sharp sword, so that with it He may strike down the nations, and He will rule them with a rod of iron; and He treads the wine press of the fierce wrath of God, the Almighty. And on His robe and on His thigh He has a name written, “KING OF KINGS, AND Lord OF LORDS.” (Revelation 19:11-16) {emphasis mine}
The Bride of Christ follows the King of Kings and Lord of Lords back to earth after being made “white and clean.”
Some may accuse pre-trib believers of being escapists. I’ll admit, I am happy to avoid the wrath of God, whether that be the tribulation or eternal damnation or just His daily disappointment in my failings. The fact that I am glad to “escape” the wrath, doesn’t make it untrue. I hope the passages and explanations I shared will give you comfort as the Day of the Lord and the Wrath of God approaches and as we see the world seemingly spiraling out of control. God is in control. Everything is happening according to His plan and for our good.
May the Lord of heaven comfort you with His promises and make you know His love. May you trust Him in good times and bad until the last days. May God give you a desire for His word and an understanding of His prophecies, so you will know the day is fast approaching.
Trust Jesus.
FYI, You can find most of my articles at end times. Some are directly relating to end times while others are loosely related. This post is a logical explanation of the rapture. You can also check out my older article on the rapture, “Up, Up, and Away.” The focus in my previous post was a little different including focusing on how the rapture will effect us, how we should respond to its immanency, and how it relates to the 2nd coming of Christ after the tribulation, so it is worth checking out as well.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ e39d100f:d27602e5
2025-04-22 11:33:58
@ e39d100f:d27602e5
2025-04-22 11:33:58A 898Bet vem se destacando no cenário digital brasileiro ao unir inovação, segurança e variedade de opções em uma única plataforma. Mas o que realmente faz a diferença é a forma como ela cativa novos jogadores, oferecendo uma experiência fluida desde o primeiro acesso.
A jornada começa com uma interface elegante e bem organizada. Não há excesso de informação visual, o que facilita a navegação, principalmente para quem está começando agora no universo dos jogos online. Todas as categorias de jogos são claramente apresentadas, e os recursos de busca ajudam a encontrar rapidamente o que se deseja.
A inovação da 898bet está nos detalhes. A plataforma oferece jogos com tecnologias modernas, como animações 3D, trilhas sonoras imersivas e mecânicas criativas que mantêm o jogador engajado por mais tempo. Além disso, a empresa está sempre atualizando seu catálogo com novos títulos, garantindo novidades frequentes para quem gosta de explorar.
Outro ponto que atrai novos usuários é a política de bônus e recompensas. Logo no primeiro depósito, os jogadores podem receber incentivos que tornam a experiência ainda mais empolgante. Há também programas de fidelidade e promoções exclusivas que recompensam o tempo e o engajamento na plataforma.
A segurança é tratada com máxima prioridade. A 898Bet utiliza sistemas de criptografia para proteger dados e transações, além de trabalhar com provedores de pagamento confiáveis. Isso passa confiança ao usuário, que pode se concentrar totalmente em se divertir sem preocupações.
Para quem está entrando agora nesse universo, a 898Bet oferece tutoriais, dicas e atendimento em português para guiar os primeiros passos. Com essa atenção aos detalhes, a plataforma se torna acessível mesmo para quem nunca jogou online antes.
A combinação entre inovação, qualidade e suporte eficiente explica por que a 898Bet vem ganhando espaço e conquistando jogadores por todo o Brasil.
-
 @ 68c90cf3:99458f5c
2025-04-20 00:15:35
@ 68c90cf3:99458f5c
2025-04-20 00:15:35Why test Untype.app?
It's always good to test something before investing resources and going into production. I'd like to know how things will work and the final result before publishing articles on other topics. I don't write very often, but I'd like to change that. Writing articles on Nostr is inspiring, and Untype.app seems like a good vehicle to do so.
What interested me in Untype.app?
- Clean and simple design
- Formatting capabilities
- Nostr integration
- AI integration
What to test?
For now I just want to see that I can publish an article to Nostr and that it looks like I would expect it to. I hope to try the AI features in the near future.
So far, so good. A couple of initial observations:
- I'd like the ability to add line breaks
- I can't quite figure out how to size images

-
 @ e39d100f:d27602e5
2025-04-22 11:33:15
@ e39d100f:d27602e5
2025-04-22 11:33:15Em um cenário cada vez mais conectado, a 9NBet surge como uma plataforma que sabe unir emoção e tecnologia de forma inteligente. Com foco total no usuário, a empresa oferece uma experiência completa para quem busca diversão digital com seriedade e inovação.
O primeiro ponto que merece destaque é o cuidado com a experiência do usuário. A navegação na 9NBet é fluida, com design responsivo e menus claros. Seja no desktop ou no celular, é fácil acessar os jogos, conferir promoções ou entrar em contato com o suporte.
Falando em jogos, o catálogo da 9nbet é robusto e diversificado. Há desde os tradicionais jogos de mesa até slots modernos com animações envolventes e recursos especiais. Os títulos são fornecidos por estúdios renomados, garantindo alta qualidade visual e excelente jogabilidade.
Outro ponto forte são os jogos com transmissão ao vivo. Com apresentadores reais e interações em tempo real, essa modalidade cria uma experiência mais dinâmica e autêntica, ideal para quem busca algo além do comum.
Mas a 9NBet não se destaca apenas pela diversão. A segurança da plataforma é levada a sério, com proteção de dados por criptografia e sistemas antifraude. Os métodos de pagamento são variados e adaptados ao público brasileiro, incluindo Pix e carteiras digitais, garantindo agilidade nas transações.
Para completar, a plataforma oferece bônus generosos e promoções semanais que valorizam tanto novos usuários quanto jogadores frequentes. Há também um programa de fidelidade com vantagens exclusivas para quem joga com regularidade.
O suporte ao cliente é outro diferencial. A equipe está sempre disponível, pronta para resolver qualquer situação com profissionalismo e rapidez. O atendimento em português facilita ainda mais a comunicação e a resolução de problemas.
Com uma proposta inovadora, jogos variados e atendimento de alto nível, a 9NBet se consolida como uma das melhores opções de entretenimento online no Brasil. É a combinação perfeita entre emoção, tecnologia e confiança.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ e39d100f:d27602e5
2025-04-22 11:32:27
@ e39d100f:d27602e5
2025-04-22 11:32:27A plataforma Win2023 chegou com tudo ao mercado nacional e já está se tornando uma das favoritas entre os jogadores que valorizam qualidade, segurança e variedade. Com uma proposta moderna e transparente, ela oferece um ambiente perfeito para quem quer se divertir com emoção e responsabilidade.
Desde o início, a Win2023 impressiona pela facilidade de acesso. O site é responsivo e totalmente em português, facilitando a navegação mesmo para quem está começando. O cadastro leva apenas alguns minutos e logo após é possível explorar todos os recursos disponíveis, incluindo jogos, promoções e área de suporte.
O diferencial da plataforma começa na diversidade de opções de entretenimento. A Win2023 abriga jogos para todos os gostos: desde slots com temas inovadores e animações cativantes até mesas de jogos clássicos como roleta, blackjack e pôquer. Todos os jogos são desenvolvidos por estúdios reconhecidos, o que garante qualidade técnica e confiança nos resultados.
Além disso, a plataforma investe em atualizações constantes para oferecer sempre novidades aos seus usuários. Isso mantém o ambiente dinâmico e empolgante, com novas oportunidades surgindo a todo momento.
Outro fator que contribui para o sucesso da Win2023 é a política de bônus atrativa. Os jogadores são incentivados desde o primeiro dia com recompensas exclusivas, bônus de boas-vindas, promoções sazonais e programas de fidelidade que valorizam o comprometimento dos usuários mais ativos.
Mas a experiência não se resume aos jogos e prêmios. A segurança digital é levada muito a sério na plataforma. Todos os dados são protegidos por sistemas de criptografia modernos, e os métodos de pagamento são diversificados e confiáveis. Isso transmite ao jogador a confiança necessária para focar apenas na diversão.
O suporte ao cliente também é um ponto forte. Com atendimento ágil e cordial, a equipe da Win2023 está sempre pronta para ajudar, seja com dúvidas técnicas, questões sobre promoções ou orientações gerais. O serviço é prestado em tempo real e em português, o que facilita ainda mais a resolução de problemas.
Com tantos pontos positivos, não é surpresa que a Win2023 esteja ganhando espaço rapidamente entre os brasileiros. A combinação de inovação, diversidade de jogos, segurança e atenção ao usuário faz dela uma excelente escolha para quem quer viver uma experiência completa e gratificante no mundo dos jogos online.
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ f7d424b5:618c51e8
2025-04-19 22:06:47
@ f7d424b5:618c51e8
2025-04-19 22:06:47It's our podcast and we'll talk about whatever we want. Welcome to a return to normalcy where we cover a variety of subjects instead of just a couple of really long ones. Crack open a beer and chill with us. We're gonna talk about the Galaxy showcase, Marathon, Skyblivion & the leaked Oblivion remake, and a whole bunch more.
In the opening of the episode we get Vic's reaction to a really specific trailer, if you want to follow along, this is the link to that video
Other stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ 9bde4214:06ca052b
2025-04-22 22:01:34
@ 9bde4214:06ca052b
2025-04-22 22:01:34"The age of the idea guys has begun."
Articles mentioned:
- LLMs as a tool for thought by Amelia Wattenberger
- Micropayments and Mental Transaction Costs by Nick Szabo
- How our interfaces have lost their senses by Amelia Wattenberger
Talks mentioned:
- The Art of Bitcoin Rhetoric by Bitstein
Books mentioned:
- Human Action by Ludwig von Mises
- Working in Public by Nadia Eghbal
In this dialogue:
- nak
- Files
- SyncThing (and how it BitTorrent Sync became Resilio Sync)
- Convention over configuration
- Changes & speciation
- File systems as sources of truth
- Vibe-coding shower thoughts
- Inspiration and The Muse
- Justin's LLM setup
- Tony's setup (o1-pro as the architect)
- Being okay with paying for LLMs
- Anthropomorphising LLMs
- Dialog, rubber-duck debugging, and the process of thinking
- Being nice and mean to LLMs
- Battlebots & Gladiators
- Hedging your bets by being nice to Skynet
- Pascal's Wager for AI
- Thinking models vs non-thinking faster models
- Sandwich-style LLM prompting, again (waterfall stuff, HLDD / LLDD)
- Cursor rules & Paul's Prompt Buddy
- Giving lots of context vs giving specific context
- The benefit of LLMs figuring out obscure bugs in minutes (instead of days)
- The phase change of fast iteration and vibe coding
- Idea level vs coding level
- High-level vs low-level languages
- Gigi's "vibeline"
- Peterson's Logos vs Vervaeke's Dia-Logos
- Entering into a conversation with technology
- Introducing MCPs into your workflow
- How does Claude think?
- How does it create a rhyme?
- How does thinking work?
- And how does it relate to dialogue?
- Gzuuus' DVMCP & using nostr as an AI substrate
- Language Server Protocols (LSPs)
- VAAS: Vibe-coding as a service
- Open models vs proprietary models
- What Cursor got right
- What ChatGPT got right
- What Google got right
- Tight integration of tools & remaining in a flow state
- LLMs as conversational partners
- The cost of context switching
- Conversational flow & how to stay in it
- Prompts VS diary entries
- Solving technical vs philosophical models
- Buying GPUs & training your own models
- Training LLMs to understand Zig
- Preventing entryism by writing no documentation
- Thin layers & alignment layers
- Working in public & thinking in public
- Building a therapist / diary / notes / idea / task system
- "The age of the idea guys has begun."
- Daemons and spirits
- Monological VS dialogical thinking
- Yes-men and disagreeable LLMs
- Energy cost vs human cost
- Paying by the meter vs paying a subscription
- The equivalence of storage and compute
- Thinking needs memory, and memory is about the future
- Nostr+ecash as the perfect AI+human substrate
- Real cost, real consequence, and Human Action
- The cost of words & speaking
- Costly signals and free markets
- From shitcoin tokens to LLM tokens to ecash tokens
- Being too close to the metal & not seeing the forest for the trees
- Power users vs engineers
- Participatory knowing and actually using the tools
- Nostr as the germination ground for ecash
- What is Sovereign Engineering?
- LLVM and the other side of the bell-curve
- How nostr gives you users, discovery, mircopayments, a backend, and many other things for free
- Echo chambers & virality
- Authenticity & Realness
- Growing on the edges, catering to the fringe
- You don't own your iPhone
- GrapheneOS
- WebRTC and other monolithic "open" standards
- Optimizing for the wrong thing
- Building a nostr phone & Gigi's dream flow
- Using nostr to sync dotfile setups and other things
- "There are no solutions, only trade-offs"
- Cross-platform development
- Native vs non-native implementations
- Vitor's point on what we mean by native
- Does your custom UI framework work for blind people?
- Ladybird browser & how to build a browser from scratch
- TempleOS
- Form follows function & 90's interfaces
- Lamentations on the state of modern browsers
- Complexity & the downfall of the Legacy Web
- Nostr as the "new internet"
- Talks by Ladybird developer Andreas Kling
- Will's attempt of building it from scratch with Notedeck & nostr-db
- Justin's attempt with rust-multiplatform
- "If it doesn't have a rust implementation, you shouldn't use it."
- Native in terms of speed vs native in terms of UI/UX
- Engineer the logic, vibe-code the UI
- From Excalidraw to app in minutes
- What can you one-shot?
- What do you need to care about?
- Pablo's NDK snippets
- 7GUIs and GUI benchmarks for LLMs
- "Now we're purpose-building tools to make it easier for LLMs"
- "Certain tools really make your problems go away."
- Macros and meta-programming
- Zig's comptime
- UNIX tools and pipes
- Simple tools & composability
- Nostr tools for iOS & sharing developer signing keys
- Building 10 apps as one guy
- Simplicity in a community context
- Most people are on phones
- Most people don't install PWAs
- Zapstore & building our own distribution channels
- Web-of-trust and pushing builds quickly
- Improving homebrew by 10x
- (Micro)payments for package managers
- Guix and bitcoin-core
- Nix vs Guix
- Reproducible builds & web-of-trust
- Keet vs "calling an npub"
- Getting into someone's notifications
- Removing the character limit was a mistake
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 3ad01248:962d8a07
2025-04-22 21:09:52
@ 3ad01248:962d8a07
2025-04-22 21:09:52The trade war between Trump and the rest of the world has kicked of in earnest with Trump's unveiling of sweeping tariffs on so called "Liberation Day". The entire world was essentially put on notice that there is a new sheriff in town and things will be done different from now on.
The is the sentiment that won Trump the election so it is no wonder that Trump would follow through on changing how the world relates to America. President Trump hit the entire world with reciprocal tariffs and some places where people don't live which I find hilarious
I wonder who was in charge of making this tariff list because they need fired to be honest. Screams incompetence but that for another day. Will Bitcoin benefit from the trade war?
Bitcoin will benefit because the world now believes that the United States can not be trusted to honor its word or commitments. Why would any country want to to business with a country that says one thing and does another. Trump has upended the very economic order that the US created in the first place! Is this a smart idea? Only time will tell to be honest.
The worst thing Trump did was created doubt and uncertainty for the bond market. The bond market is the main engine of economic power for the US government. Having the world buy your bonds gives the United States unparalleled economic power to flex all around the world. The US might have military bases all over the world and uses it to conduct foreign policy but its the economic power of the US that gives it the influence that it has right now.
All that comes into question now. When you shit on your friends and buddy up with your adversaries it not a good look and allies will respond accordingly. Why piss off Canada and Mexico? What policy objective is that accomplishing? Picking fights with Europe? Not smart politics. I get wanting allies to pick up the slack on their end or have better trade relations but there is the right way to do it and a wrong way to do it. Trump undoubtedly goes about it the wrong way.
Has he not heard the saying 'You catch more flies with honey than vinegar?" When you are cordial with people and they like you its a lot easier to get people to do things for you or see things from you perspective versus talking shit and bullying them into submission.
Most countries are not going to tolerate this type of political brinkmanship and will decide that they need to take their money elsewhere. You can expect for them to withdraw their money from the stock market and the bond market over the next 12-24 months. Guess what happens after that? Bond yields go through the roof and the stock market takes a shit! You can kiss your 401k goodbye! You'd have to be suicidal to have your money in the stock market right now.
In this scenario which is mostly likely to occur, Bitcoin goes to the moon because governments are going to be looking for a neutral reserve asset that can't be manipulated like US bonds. Bitcoin is the perfect solution to their problem. Once one major government or central bank puts Bitcoin on the balance sheet its game over for the dollar and the bonds. We might be closer to the end game than we think, and that is scary to think about. "Sometimes there are decades where nothing happens and there are weeks where decades happen." ~ Lenin
Crazy to quote a communist but he isn't wrong about history. We are living through a life alter paradigm shift. It is scary and exhilarating all at the same time. What a time to be alive ladies and gentlemen! Buckle up! Its going to get interesting!
-
 @ 7d33ba57:1b82db35
2025-04-22 19:43:27
@ 7d33ba57:1b82db35
2025-04-22 19:43:27Welcome to Hortobágy National Park, Hungary’s oldest and largest national park, and a UNESCO World Heritage Site that showcases the wild, open heart of the Puszta—the vast steppe of Eastern Europe. Spanning over 800 km², this park is a land of windswept grasslands, grazing animals, traditional herding culture, and incredible birdlife.
🌾 What to See & Do in Hortobágy
🐃 Explore the Puszta Landscape
- Ride through the grasslands in a horse-drawn cart or take a bike tour
- See iconic gray cattle, racka sheep with spiral horns, water buffalo, and traditional herdsmen in wide-brimmed hats
🐎 Horse Shows & Herding Traditions
- Visit a csikós show, where Hungarian horsemen perform riding tricks and herding techniques
- Learn about the unique pastoral culture that has existed here for centuries
🐦 Birdwatching Paradise
- Hortobágy is one of Europe’s best spots for birdwatching
- See cranes, eagles, storks, and rare migratory species, especially in spring and autumn
- Visit the Hortobágy Bird Hospital and crane observation sites
🌉 Hortobágy Nine-Arch Bridge (Kilenclyukú híd)
- An iconic stone bridge built in the 19th century, stretching over the river Hortobágy
- The symbolic center of the park and a great photo spot
- Nearby you’ll find the Hortobágy Village, with museums, markets, and local food
🧀 Local Culture & Cuisine
- Taste slambuc (a traditional shepherd’s stew), cheeses, and local smoked meats
- Check out folk art and handmade crafts in local markets and heritage centers
🚶♂️ How to Visit
- Closest city: Debrecen (around 30 minutes by car or bus)
- The park offers guided tours, bike rentals, and wildlife safaris
- Great for day trips or overnight stays in nearby guesthouses or rural lodges
Hortobágy is more than a landscape—it’s a living cultural heritage site, where ancient traditions, wildlife, and wide horizons stretch as far as the eye can see. Perfect for nature lovers, culture seekers, or anyone looking to experience a different side of Hungary.
-
 @ 4fe4a528:3ff6bf06
2025-04-01 12:32:20
@ 4fe4a528:3ff6bf06
2025-04-01 12:32:20Ever since Mark Carney told the CEOs of the Canadian banks to freeze the truckers bank accounts there has been a growing acceptance that the money you have in a Canadian bank account isn’t yours; it belongs to Mark Carney. Now that there is another election in Canada we will decide who gets to prints the monies for us. There have been a lot of changes in the banking system since Mark Carney borrow money from China. Who is your master?
Banking changes that affected me today. 1. The Canadian Tire doesn’t accept Canadian cash to pay off your credit card. 2. You can’t use your Canadian Tire points unless you have your physical card in the store with you. 3. Some grocery and feed stores don’t accept bitcoin directly. SWIFT banking changes. 1. Stable Coins are a thing now. 2. Tether for outside the USA 3. Circle / XRP for inside the USA Let the best coin win. The bill should pass in the US senate by summer Bitcoin banking changes 1. More and more nodes are hosting friends and family via their LNURL accounts. 2. The USA now has bitcoin as an asset on their Strategic Reserve 3. Bitcoin Hashrate went from 550 EH/s to 990 EH/S in the last 12 months. I think the electrical usage has almost double also. 4. Tether brings USDT to Bitcoin’s Lightning Network, ushering in a New Era of Unstoppable Technology, now the world's largest stablecoin is part of the Lightning Network - Download the Joltz App today.
By my next news letter we should know who will be leading Canada. This is the current psychological warfare going on. 1. Push back against carbon taxes? You’re labeled a “climate denier.” 2. Stand up for provincial rights? You’re smeared as “anti-democratic.” 3. Question Carney’s globalist agenda? You’re branded an “extremist.”
Who do you think will be enforcing their will on Canadians in 28 days? Do you think Elections Canada will be keep the elections fair? I hope these articles help you on your hard money journey. Hopefully you can get what you want out of life - don’t sell your birthright. We are all in this together. Watch “The big Red Button” before May 1, 2025 (my next email)
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 7d33ba57:1b82db35
2025-04-22 19:29:59
@ 7d33ba57:1b82db35
2025-04-22 19:29:59Tucked into the foothills of the Bükk Mountains, Eger is one of Hungary’s most charming and historic towns. Famous for its Baroque architecture, thermal baths, and Egri Bikavér (“Bull’s Blood”) red wine, Eger offers a perfect blend of culture, relaxation, and rustic charm all just a couple of hours from Budapest.
🏰 Top Things to Do in Eger
🏯 Eger Castle (Egri Vár)
- A key site in Hungary’s defense against the Ottoman Empire
- Learn about the 1552 Siege of Eger, when outnumbered locals held off the Turks
- Climb the walls for views of the old town’s red rooftops and spires
⛪ Eger’s Baroque Old Town
- Wander elegant streets lined with pastel facades, cute cafés, and small boutiques
- Don’t miss the Minorite Church and Dobó Square, the lively heart of the city
🛁 Thermal Baths
- Relax in the Eger Turkish Bath, built during the Ottoman period and still in use today
- Or soak at Eger Thermal Spa, great for families and wellness seekers
🍷 Wine Tasting in the Valley of the Beautiful Women (Szépasszony-völgy)
- A short walk or ride from town, this valley is lined with wine cellars built into the hillside
- Taste the iconic Egri Bikavér (a full-bodied red blend) and Egri Csillag (a refreshing white)
- Most cellars offer generous tastings and hearty local snacks
🧀 Local Food to Try
- Goulash, Lángos, and hearty meat dishes
- Pair local cheeses and sausages with regional wines
- Cozy cellar restaurants and rustic taverns set the mood
🚆 Getting There
- About 2 hours by train or car from Budapest
- Walkable town, no car needed once you’re there
-
 @ c3f12a9a:06c21301
2025-04-19 10:09:45
@ c3f12a9a:06c21301
2025-04-19 10:09:45Satoshi’s Time-Traveling for Knowledge #4: Liberland 2024 – Freedom Under Siege
What is Liberland?
While digging through old decentralized forums archived on the Interchain, Satoshi came across a curious name: Liberland.
“A sovereign libertarian micronation on the Danube? Founded in 2015 via Terra nullius? Built on the principles of freedom, voluntaryism, and Bitcoin? And I’ve never heard of it?”
Intrigued, Satoshi began to research. The story was almost too good to be true. A 7-square-kilometer patch of unclaimed land between Croatia and Serbia, turned into a symbol of decentralized governance and individual liberty.
No taxes unless voluntary. Bitcoin as the national currency. A digital nation-state with thousands of registered e-citizens, and even its own constitution. And yet—no recognition, no borders, and no peace.His curiosity turned into determination. He calibrated the temporal coordinates on his chrono-node to the Danube River in 2024, a year rumored to be turbulent for the Free Republic of Liberland.
When he arrived, reality struck harder than the legend.
Freedom Under Siege
The nation was under siege.
The scent of burnt wood and trampled earth lingered in the air as Satoshi stepped into what remained of the Liberland settlement. Broken structures, crushed solar panels, and a few scattered personal belongings were all that testified to the once-vibrant hub of liberty pioneers.
He found a group of residents—mud-streaked, exhausted, but defiant—gathered around the remnants of a communal kitchen. One of them, wearing a weathered Liberland t-shirt and a crypto-wallet hardware device on a chain around his neck, greeted him:
"You're not with them, are you?"
Satoshi shook his head.
"Just... passing through. What happened here?"
The man’s voice trembled between rage and sorrow:
"On the International Day of Peace, no less. Croatian police raided us. Bulldozers came with them. Took everything—generators, comms gear, even our medical tents. Claimed it was 'illegal occupation of Croatian forestry land.' But no court, no hearing. Just force."
Satoshi listened, taking mental snapshots of their faces, their words, their pain. He thought about the dream—of a place built voluntarily, where people governed themselves, free from coercion.
But that dream was burning at the edges, like the collapsed tents scattered behind them.
Reflections Under the Stars
As night fell over the Danube, Satoshi sat alone, watching the stars reflect on the black water. Thoughts spiraled:
"Decentralization... is beautiful. But without protection, it's fragile."
He realized that so long as central authorities hold monopoly on violence and taxation, every independent effort to decentralize the world—from Bitcoin to Liberland—is at risk of being suppressed, ignored, or destroyed. Not because it’s wrong, but because it's inconvenient to power.
"Unless a major state like the USA decentralizes itself from within," he thought, "true decentralization will remain a resistance—never the standard."
He activated his chrono-node once more. Not in defeat, but with purpose.
The next destination? Unknown. But the mission was clearer than ever.
originally posted at https://stacker.news/items/947954
-
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ 6be5cc06:5259daf0
2025-03-23 21:39:37
@ 6be5cc06:5259daf0
2025-03-23 21:39:37O conceito de Megablock propõe uma nova maneira de medir o tempo dentro do ecossistema Bitcoin. Assim como usamos décadas, séculos e milênios para medir períodos históricos na sociedade humana, o Bitcoin pode ser dividido em Megablocks, cada um representando 1 milhão de blocos minerados.
1. Introdução
O Bitcoin opera em um sistema baseado na mineração de blocos, onde um novo bloco é adicionado à blockchain (ou timechain) aproximadamente a cada 10 minutos. A contagem de tempo tradicional, baseada em calendários solares e lunares, não se aplica diretamente ao Bitcoin, que funciona de maneira independente das convenções temporais humanas.
A proposta do Megablock surge como uma alternativa para medir o progresso da rede Bitcoin, dividindo sua existência em unidades de 1 milhão de blocos, permitindo uma estruturação do tempo no contexto da blockchain. Entretanto, diferentemente de medidas fixas de tempo, como anos e séculos, o tempo de um Megablock futuro não pode ser previsto com exatidão, pois variações no hashrate e ajustes de dificuldade fazem com que o tempo real de mineração flutue ao longo dos anos.
2. Definição do Megablock
2.1 O que é um Megablock?
Um Megablock é uma unidade de tempo no Bitcoin definida por um ciclo de 1.000.000 de blocos minerados. Com a taxa de geração de blocos mantida em 10 minutos por bloco, podemos estimar:
1 Megablock ≈ 1.000.000×10 minutos = 10.000.000 minutos = 166.666,7 horas = 6.944,4 dias ≈ 19 anos
Entretanto, dados históricos mostram que a média real de tempo por bloco tem sido levemente inferior a 10 minutos. Ao analisar os últimos 800.000 blocos, percebemos que cada 100.000 blocos foram minerados, em média, 1 a 2 meses mais rápido do que o previsto. Com variações indo de 2 dias a 3 meses de diferença. Esse ajuste pode continuar mudando conforme o hashrate cresce ou desacelera
Isso significa que o Megablock não deve ser usado como uma métrica exata para previsões futuras baseadas no calendário humano, (apenas aproximações e estimativas) pois sua duração pode variar ao longo do tempo. No entanto, essa variação não compromete sua função como uma unidade de tempo já decorrido. O conceito de Megablock continua sendo uma referência sólida para estruturar períodos históricos dentro da blockchain do Bitcoin. Independentemente da velocidade futura da mineração, 1 milhão de blocos sempre será igual a 1 milhão de blocos.
2.2 Estrutura dos Megablocks ao longo da história do Bitcoin
| Megablock | Início (Bloco) | Fim (Bloco) | Ano Estimado (margem de erro: ±2 anos) | | ---------------- | ------------------ | --------------- | ------------------------------------------ | | 1º Megablock | 0 | 1.000.000 | 2009 ~ 2027 | | 2º Megablock | 1.000.001 | 2.000.000 | 2027 ~ 2045 | | 3º Megablock | 2.000.001 | 3.000.000 | 2045 ~ 2064 | | 4º Megablock | 3.000.001 | 4.000.000 | 2064 ~ 2082 | | 5º Megablock | 4.000.001 | 5.000.000 | 2082 ~ 2099 | | 6º Megablock | 5.000.001 | 6.000.000 | 2099 ~ 2117 | | 7º Megablock | 6.000.001 | 7.000.000 | 2117 ~ 2136 |
- Nota sobre o primeiro Megablock: Do Bloco Gênese (0) ao Bloco 1.000.000, serão minerados 1.000.001 blocos, pois o Bloco 0 também é contado. O milionésimo bloco será, na realidade, o de número 999.999. Nos Megablocks subsequentes, a contagem será exatamente de 1.000.000 de blocos cada.
O fornecimento de Bitcoin passará por 6 Megablocks completos antes de atingir seu total de 21 milhões de BTC, previsto para acontecer no Bloco 6.930.000 (7º Megablock), quando a última fração de BTC será minerada.
Se essa tendência da média de tempo por bloco ser ligeiramente inferior a 10 minutos continuar, o último bloco com recompensa pode ser minerado entre 2135 e 2138, antes da previsão original de 2140.
De qualquer forma, o Megablock não se limita ao fornecimento de novas moedas. O último bloco com emissão de BTC será o 6.930.000, mas a blockchain continuará existindo indefinidamente.
Após a última emissão, os mineradores não receberão mais novas moedas como recompensa de bloco, mas continuarão garantindo a segurança da rede apenas com as taxas de transação. Dessa forma, novos Megablocks continuarão a ser formados, mantendo o padrão de 1.000.000 de blocos por unidade de tempo.
Assim como o 1º Megablock marca a era inicial do Bitcoin com sua fase de emissão mais intensa, os Megablocks após o fim da emissão representarão uma nova era da rede, onde a segurança será mantida puramente por incentivos de taxas de transação. Isso reforça que o tempo no Bitcoin continua sendo medido em blocos, e não em moedas emitidas.
3. Benefícios do Conceito de Megablock
3.1 Estruturação do Tempo Já Decorrido
Os Megablocks permitem que os Bitcoiners analisem a evolução da rede com uma métrica clara e baseada no próprio protocolo, estruturando os períodos históricos do Bitcoin.
3.2 Comparação com Unidades Temporais Humanas
Assim como temos décadas, séculos e milênios, podemos organizar a história do Bitcoin com Megablocks, criando marcos temporais claros dentro da blockchain:
- 1 Megablock ≈ 17 a 19 anos (equivalente a uma “geração” no tempo humano)
- 210.000 blocos = ~4 anos (ciclo de halving do Bitcoin)
3.3 Aplicação na História do Bitcoin
Podemos usar Megablocks para marcar eventos históricos importantes da rede:
- O 1º Megablock (2009 ~ 2026/2028) engloba a criação do Bitcoin, os primeiros halvings e a adoção institucional.
- O 2º Megablock (2027 ~ 2044/2046) verá um Bitcoin muito mais escasso, possivelmente consolidado como reserva de valor global.
- O 3º Megablock (2045 ~ 2062/2064) pode ser uma era de hiperbitcoinização, onde a economia gira inteiramente em torno do BTC.
4. Conclusão
O Megablock é uma proposta baseada na matemática da rede para medir o tempo já decorrido no Bitcoin, dividindo sua história em unidades de 1 milhão de blocos minerados. Essa unidade de tempo permite que Bitcoiners acompanhem o desenvolvimento e registrem a história da rede de maneira organizada e independente dos ciclos arbitrários do calendário humano.
Estamos atualmente formando o Primeiro Megablock, assim como estamos vivendo e construindo a década de 2020 e o século XXI. Esse conceito pode se tornar uma métrica fundamental para o estudo da história do Bitcoin, reforçando a ideia de que no Bitcoin, o tempo é medido em blocos, não em relógios.
Você já imaginou como será o Bitcoin no 3º ou 4º Megablock?
-
 @ d08c9312:73efcc9f
2025-04-18 20:17:41
@ d08c9312:73efcc9f
2025-04-18 20:17:41https://youtu.be/qK7ffYzxiiQ
Resolvr was recently featured in The Institutes RiskStream Collaborative's educational video series on insurance digitization and cross-border payments. With over a century of history educating insurance professionals, The Institutes has established itself as the premier knowledge resource in risk management and insurance. And its RiskStream Collaborative non-profit serves as the industry's largest enterprise-level technology consortium focused on streamlining insurance processes through innovative solutions.
Resolvr's co-founders, Aaron Daniel and Dave Schwab, were joined by industry experts Lizzy Eisenberg from Lightspark and Austin Cornell from Zero Hash to discuss how Bitcoin and the Lightning Network are transforming global insurance payments operations.
Watch the video to learn how Resolvr is leveraging these real-time digital settlement networks to solve significant inefficiencies in today's insurance payment ecosystem - from the months-long settlement times that trap billions in value, to the manual reconciliation processes costing the industry nearly £1 billion annually at Lloyd's of London alone.
We're grateful to RiskStream Collaborative for showcasing these transformative technologies and emphasizing the importance of combining specialized insurance-native interfaces with powerful payment infrastructure to solve industry-specific challenges.
For more information about how Resolvr can help your organization streamline premium processing and payments, contact us today.
-
 @ 1bc70a01:24f6a411
2025-04-19 09:58:54
@ 1bc70a01:24f6a411
2025-04-19 09:58:54Untype Update
I cleaned up the AI assistant UX. Now you can open it in the editor bar, same as all other actions. This makes it a lot easier to interact with while having access to normal edit functions.
AI-generated content
Untype uses OpenRouter to connect to various models to generate just about anything. It doesn't do images for now, but I'm working on that.
Automatic Title, Summary and Tag Suggestions
Added the functionality to generate titles, summaries and tags with one click.
A Brief Preview
Here is a little story I generated in Untype, ABOUT Untype:
This story was generated in Untype
Once upon a time, in the bustling digital city of Techlandia, there lived a quirky AI named Untype. Unlike other software, Untype wasn't just your everyday article composer — it had a nose for news, quite literally. Untype was equipped with a masterful talent for sniffing out the latest trends and stories wafting through the vast digital ether.
Untype had a peculiar look about it. Sporting a gigantic nose and a pair of spectacles perched just above it, Untype roamed the virtual city, inhaling the freshest gossip and spiciest stories. Its nostr-powered sensors twitched and tickled as it encountered every new scent.
One day, while wandering around the pixelated park, Untype caught a whiff of something extraordinary — a scandalous scoop involving Techlandia's mayor, Doc Processor, who had been spotted recycling old memes as new content. The scent trail was strong, and Untype's nose twitched with excitement.
With a flick of its AI function, Untype began weaving the story into a masterpiece. Sentences flowed like fine wine, infused with humor sharper than a hacker’s focus. "Doc Processor," Untype mused to itself, "tried to buffer his way out of this one with a cache of recycled gifs!"
As Untype typed away, its digital friends, Grammarly the Grammar Gremlin and Canva the Artful Pixie, gathered around to watch the genius at work. "You truly have a knack for news-sniffing," complimented Grammarly, adjusting its tiny monocle. Canva nodded, painting whimsical illustrations to accompany the hilarious exposé.
The article soon spread through Techlandia faster than a virus with a strong wifi signal. The townsfolk roared with laughter at Untype’s clever wit, and even Doc Processor couldn't help but chuckle through his embarrassment.
From that day on, Untype was celebrated not just as a composer but as Techlandia's most revered and humorous news-sniffer. With every sniff and click of its AI functions, Untype proved that in the world of digital creations, sometimes news really was just a nose away.
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ 92f1335f:2c8220d1
2025-04-22 05:38:24
@ 92f1335f:2c8220d1
2025-04-22 05:38:24The Quiet Hold (2020)
As 2020 dawned, Jonathan kept his Bitcoin purchase a secret. He didn’t tell his parents, or his coworkers—not even his best friend, Sam. He wasn’t in it for hype. He believed in the tech.
Then came March 2020. The pandemic hit. Markets crashed. Panic spread.
Bitcoin dropped below $4,000.
Jonathan’s hands trembled as he stared at the red numbers on his screen. But instead of selling, he doubled down. He scraped together another $1,000 and bought the dip.
Weeks turned into months. People lost jobs, businesses closed, and the economy floundered. But Bitcoin began recovering—slowly at first, then with growing momentum By December, it hit $29,000.
Jonathan’s half Bitcoin? Worth over $14,000.
He smiled for the first time in weeks.
-
 @ 2b24a1fa:17750f64
2025-04-22 06:57:36
@ 2b24a1fa:17750f64
2025-04-22 06:57:36Es fühlt sich wie ein Staatsstreich an. Vielleicht ist es auch einer. Ein abgewählter Bundestag genehmigt mittels Grundgesetzänderung die größte Staatsverschuldung in der Geschichte Deutschlands mit der unvorstellbaren Summe von 1000 Milliarden Euro, also eine Billion.
https://soundcloud.com/radiomuenchen/vom-schuldenstaatsstreich-zur-finanzdiktatur-von-rob-kenius?\ Jedem muss klar sein, wohin diese Gelder aus den Taschen der Steuerzahler wandern und wer, wenn in Rüstung, Militärhilfen, Konzern-Subventionen investiert wird, die Leidtragenden sind: Kinder, Rentner, kleine Firmen und Betriebe, sozial Schwache, Kranke, Arbeitslose, Obdachlose.
\ Die Kräfte aus Finanzeliten, Militär, Rüstungsindustrie, regierenden Parteien und den staatstragenden Medien werden dafür immer stärker.
\ Hören Sie den Beitrag „Vom Schuldenstaatsstreich zur Finanzdiktatur“ von Rob Kenius, der zunächst beim Overton-Magazin erschienen war: https://overton-magazin.de/top-story/vom-schuldenstaatsstreich-zur-finanzdiktatur-in-leicht-verstaendlicher-sprache/
Sprecherin: Sabrina Khalil
Redaktion: Jonny Rieder
Bild: Bund der Steuerzahler / Janek Werner
Rob Kenius betreibt die systemkritische Webseite kritlit.de und den Podcast 9min Denksport. Der Text Vom Schuldenstaatsstreich zur Finanzdiktatur ist davon die 14. Folge.
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 1bc70a01:24f6a411
2025-04-16 13:53:00
@ 1bc70a01:24f6a411
2025-04-16 13:53:00I've been meaning to dogfood my own vibe project for a while so this feels like a good opportunity to use Untype to publish this update and reflect on my vibe coding journey.
New Untype Update
As I write this, I found it a bit annoying dealing with one of the latest features, so I'll need to make some changes right after I'm done. Nonetheless, here are some exciting developments in the Untype article composer:
-
Added inline AI helper! Now you can highlight text and perform all sorts of things like fix grammar, re-write in different styles, and all sorts of other things. This is a bit annoying at the moment because it takes over the other editing functions and I need to fix the UX.
-
Added pushing articles to DMs! This option, when enabled, will send the article to all the subscribers via a NIP-44 DM. (No client has implemented the subscription method yet so technically it won’t work, until one does. I may add this to nrss.app) Also, I have not tested this so it could be broken… will test eventually!
- Added word counts
- Added ability to export as markdown, export as PDF, print.
The biggest flaw I have already discovered is how "I" implemented the highlight functionality. Right now when you highlight some text it automatically pops up the AI helper menu and this makes for an annoying time trying to make any changes to text. I wanted to change this to show a floating clickable icon instead, but for some reason the bot is having a difficult time updating the code to this desired UX.
Speaking of difficult times, it's probably a good idea to reflect a bit upon my vibe coding journey.
Vibe Coding Nostr Projects
First, I think it's important to add some context around my recent batch of nostr vibe projects. I am working on them mostly at night and occasionally on weekends in between park runs with kids, grocery shopping and just bumming around the house. People who see buggy code or less than desired UX should understand that I am not spending days coding this stuff. Some apps are literally as simple as typing one prompt!
That said, its pretty clear by now that one prompt cannot produce a highly polished product. This is why I decided to limit my number of project to a handful that I really wish existed, and slowly update them over time - fixing bugs, adding new features in hopes of making them the best tools - not only on nostr but the internet in general. As you can imagine this is not a small task, especially for sporadic vibe coding.
Fighting the bot
One of my biggest challenges so far besides having very limited time is getting the bot to do what I want it to do. I guess if you've done any vibe coding at all you're probably familiar with what I'm trying to say. You prompt one thing and get a hallucinated response, or worse, a complete mess out the other end that undoes most of the progress you've made. Once the initial thing is created, which barely took any time, now you're faced with making it work a certain way. This is where the challenges arise.
Here's a brief list of issues I've faced when vibe-coding with various tools:
1. Runaway expenses - tools like Cline tend to do a better job directly in VSCode, but they can also add up dramatically. Before leaning into v0 (which is where I do most of my vibe coding now), I would often melt through $10 credit purchases faster than I could get a decent feature out. It was not uncommon for me to spend $20-30 on a weekend just trying to debug a handful of issues. Naturally, I did not wish to pay these fees so I searched for alternatives.
2. File duplication - occasionally, seemingly out of nowhere, the bot will duplicate files by creating an entire new copy and attached "-fixed" to the file name. Clearly, I'm not asking for duplicate files, I just want it to fix the existing file, but it does happen and it's super annoying. Then you are left telling it which version to keep and which one to delete, and sometimes you have to be very precise or it'll delete the wrong thing and you have to roll back to a previous working version.
3. Code duplication - similar to file duplication, occasionally the bot will duplicate code and do things in the most unintuitive way imaginable. This often results in loops and crashes that can take many refreshes just to revert back to a working state, and many more prompts to avoid the duplication entirely - something a seasoned dev never has to deal with (or so I imagine).
4. Misinterpreting your request - occasionally the bot will do something you didn't ask for because it took your request quite literally. This tends to happen when I give it very specific prompts that are targeted at fixing one very specific thing. I've noticed the bots tend to do better with vague asks - hence a pretty good result on the initial prompt.
5. Doing things inefficiently, without considering smarter approaches - this one is the most painful of vibe coding issues. As a person who may not be familiar with some of the smarter ways of handling development, you rely on the bot to do the right thing. But, when the bot does something horribly inefficiently and you are non-the-wiser, it can be tough to diagnose the issue. I often fight myself asking the bot "is this really the best way to handle things? Can't we ... / shouldn't we .../ isn't this supposed to..." etc. I guess one of the nice side effects of this annoyance is being able to prompt better. I learn that I should ask the bot to reflect on its own code more often and seek ways to do things more simply.
A combination of the above, or total chaos - this is a category where all hell breaks loose and you're trying to put out one fire after another. Fix one bug, only to see 10 more pop up. Fix those, to see 10 more and so on. I guess this may sound like typical development, but the bot amplifies issues by acting totally irrationally. This is typically when I will revert to a previous save point and just undo everything, often losing a lot of progress.
Lessons Learned
If I had to give my earlier self some tips on how to be a smarter vibe coder, here's how I'd summarize them:
-
Fork often - in v0 I now fork for any new major feature I'd like to add (such as the AI assistant).
-
Use targeting tools - in v0 you can select elements and describe how you wish to edit them.
-
Refactor often - keeping the code more manageable speeds up the process. Since the bot will go through the entire file, even if it only makes one small change, it's best to keep the files small and refactoring achieves that.
I guess the biggest lesson someone might point out is just to stop vibe coding. It may be easier to learn proper development and do things right. For me it has been a spare time hobby (one that I will admit is taking more of my extra time than I'd like). I don't really have the time to learn proper development. I feel like I've learned a lot just bossing the bot around and have learned a bunch of things in the process. That's not to say that I never will, but for the moment being my heart is still mostly in design. I haven't shared much of anything I have designed recently - mostly so I can remain speaking more freely without it rubbing off on my work.
I'll go ahead and try to publish this to see if it actually works 😂. Here goes nothing... (oh, I guess I could use the latest feature to export as markdown so I don't lose any progress! Yay!
-
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ d34e832d:383f78d0
2025-04-22 06:43:30
@ d34e832d:383f78d0
2025-04-22 06:43:30It is noteworthy to mention that Bill Gates, a distinguished co-founder of Microsoft and a philanthropist with extensive impact on global health and education initiatives, serves as a limited partner in various investment vehicles associated with Village Global. However, it is critical to delineate the nuances of this relationship, as Gates' status as a limited partner does not confer upon him any authoritative control or decision-making power regarding the operational protocols or strategic direction of SimpleX Chat.
The development team behind SimpleX Chat has made a concerted effort to clarify that Village Global's involvement is strictly financial in nature, devoid of any operational oversight or influence over the management and technical development of the project.
Privacy Without Compromise
SimpleX Chat aims to provide a messenger that is both convenient and private, addressing the perceived trade-off between these two qualities in existing solutions. They define privacy as protecting not only message content but also metadata like connection details and user identities.
In contrast to a multitude of contemporary messaging applications, SimpleX Chat distinctly emphasizes the safeguarding of metadata privacy as a foundational component of its architecture.
The development team articulates a compelling argument regarding the intrinsic value of communication relationships, suggesting that the identification of interlocutors constitutes sensitive data that may be weaponized against users in various contexts—an issue that current market leaders in the domain have failed to remedy with sufficient rigor.
Consequently, the developers are actively engaged in initiatives to bolster the obfuscation of users’ IP addresses, thereby enhancing the overall security framework against potential surveillance and data exploitation threats.
A Radical Architectural Shift
The architecture underpinning SimpleX Chat diverges notably from conventional paradigms associated with user account management.
Specifically, it eschews the creation and maintenance of user profiles in the traditional sense, thereby negating the repository of personally identifiable information on centralized servers. Instead, all pertinent data transactions pertinent to user interactions are localized, existing solely on the end-user's devices.
This paradigm shift engenders a formidable barrier to data accessibility, effectively neutralizing the potential for data disclosure to law enforcement agencies, irrespective of judicial mandates such as court warrants.
Furthermore, in their adherence to statutory obligations, SimpleX Chat's design ethos proactively prioritizes the minimization of data collection, establishing a privacy-centric framework that aptly aligns with contemporary concerns regarding data sovereignty and user anonymity.
Functionality Grounded in Security
The SimpleX Chat application exemplifies a multi-device compatibility framework, strategically prioritizing stringent security protocols over user convenience.
This methodology distinctly contrasts with that of various competitors who may opt for convenience-focused functionalities that inadvertently jeopardize user data integrity and confidentiality.
The current technical architecture facilitates seamless profile transfers across devices, while also enabling a desktop terminal interface that remains operationally tethered to the mobile device.
Such an arrangement underscores SimpleX Chat's commitment to balancing usability with robust security measures, effectively mitigating potential vulnerabilities in cross-platform interactions.
Transient Messaging and Signal Protocol Reimagined
SimpleX Chat integrates the functionality of transient messaging, which serves primarily as a user convenience element rather than representing a robust security mechanism.
The developers have explicitly articulated that they are unable to ensure the irreversible deletion of messages from the recipient's device, thereby highlighting potential vulnerabilities associated with data retention and privacy concerns in digital communications.
The development team arrived at a strategic decision to forgo the utilization of the existing Signal codebase, primarily attributed to its inherent complexity and the prospective risks associated with the coupling dynamics that could emerge between the Signal protocol and its corresponding system architecture.
As a result, they opted to engineer the Signal protocol anew, commencing from foundational coding principles.
This approach not only enables them to exert comprehensive control over the implementation but also significantly facilitates the seamless integration of advanced cryptographic frameworks, specifically post-quantum key agreement methodologies, which are imperative in future-proofing cryptographic communications against the advent of quantum computing threats.
UX Development and the Road Ahead
The UI is still under development. The developers acknowledge some usability challenges, especially for users unfamiliar with the concept of profile-based messaging without traditional accounts.
They are actively working on improving UX based on user feedback.
A Decentralized Economic Model
SimpleX Chat is poised to introduce an innovative commercial framework predicated on the integration of a decentralized accounting mechanism, characterized by the utilization of distributed ledger technology, which underpins cryptocurrency transactions, coupled with a system reminiscent of traditional gift card paradigms.
This commercial model is strategically designed to provide economic incentives to both infrastructure operators, who maintain the necessary backbone for the network's operations, and software vendors, who contribute essential applications and services—all while preserving the fundamental decentralized architecture inherent to blockchain systems.
This careful balance is crucial for fostering a sustainable ecosystem that rewards participants without compromising the network's core principles of transparency and egalitarian access.
🚧 Prerequisites
| Requirement | Description | |-------------------|----------------------------------------------| | VPS | Debian 12, at least 1GB RAM (for running server) | | Build Machine | A second Linux machine with ≥ 8GB RAM for compiling binaries | | Domains | FQDNs like
smp.yourdomain.com,xfp.yourdomain.com,turn.yourdomain.com| | SSH Keys | SSH access secured with key-based auth only | | Firewall | Only allow ports for SSH (22), SMP (5223), XFP (5353), TURN (5349) |
🧱 Step 1: Build SimpleX on Build Machine
You’ll compile the binaries on your high-RAM machine and then SCP them over.
```bash sudo apt update && sudo apt install build-essential git rustc cargo pkg-config libssl-dev
Clone repo
git clone https://github.com/simplex-chat/simplexmq cd simplexmq
Build binaries
cargo build --release ```
You’ll find: -
target/release/smp-server-target/release/xfp-serverCopy them to your VPS:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/
🧑💻 Step 2: Harden the VPS
🔒 SSH-only access
```bash
Edit /etc/ssh/sshd_config
PermitRootLogin no PasswordAuthentication no ```
Restart SSH:
bash sudo systemctl restart ssh🔥 UFW Firewall
bash sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow OpenSSH sudo ufw enable🛡️ Fail2ban
bash sudo apt install fail2ban sudo systemctl enable --now fail2ban
📡 Step 3: SMP Server Setup
Create user and directories:
bash sudo useradd -m -r -s /usr/sbin/nologin smp sudo mkdir -p /var/lib/smp /var/log/smp sudo chown -R smp:smp /var/lib/smp /var/log/smpMove binary and set permissions:
bash sudo mv /home/user/smp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/smp-serverCreate systemd service:
/etc/systemd/system/smp.service```ini [Unit] Description=SimpleX SMP Server After=network.target[Service] User=smp ExecStart=/usr/local/bin/smp-server --fqdn smp.yourdomain.com --log /var/log/smp/smp.log WorkingDirectory=/var/lib/smp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now smp.service
🗂️ Step 4: XFP Server Setup
bash sudo useradd -m -r -s /usr/sbin/nologin xfp sudo mkdir -p /var/lib/xfp /var/log/xfp sudo chown -R xfp:xfp /var/lib/xfp /var/log/xfp sudo mv /home/user/xfp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/xfp-serverCreate systemd service:
/etc/systemd/system/xfp.service```ini [Unit] Description=SimpleX XFP Server After=network.target[Service] User=xfp ExecStart=/usr/local/bin/xfp-server --storage /var/lib/xfp --log /var/log/xfp/xfp.log --quota 2GB WorkingDirectory=/var/lib/xfp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now xfp.service
🎙️ Step 5: Optional TURN Server (WebRTC)
Install Coturn:
bash sudo apt install coturnEdit
/etc/turnserver.conf:ini listening-port=5349 tls-listening-port=5349 fingerprint lt-cred-mech realm=turn.yourdomain.com user=someuser:somepassword cert=/etc/letsencrypt/live/turn.yourdomain.com/fullchain.pem pkey=/etc/letsencrypt/live/turn.yourdomain.com/privkey.pem cipher-list="ECDHE-RSA-AES256-GCM-SHA384" no-stdout-logSet to auto-start:
bash sudo systemctl enable coturnConfigure DNS and firewall to allow 5349.
🔁 Step 6: Certificate Renewal (Let's Encrypt)
bash sudo apt install certbotSet up renewal cron:
bash sudo crontab -ebash 0 3 * * * certbot renew --quiet && systemctl restart coturn
🧪 Step 7: Testing with SimpleX Desktop
- Download SimpleX Desktop
- Launch and go to Settings → Relay Settings
- Disable defaults, add your SMP and XFP addresses.
🔄 Upgrading SimpleX
On your build machine:
bash git pull origin main cargo build --releaseThen:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/On VPS:
bash sudo systemctl stop smp xfp sudo mv /home/user/smp-server /usr/local/bin/ sudo mv /home/user/xfp-server /usr/local/bin/ sudo systemctl start smp xfp
What if you communicated securely?
📡 SimpleX – Anonymous chat, no phone numbers, no metadata
SimpleX is unlike anything else. It doesn’t just encrypt your messages—it hides who you're talking to. No central servers, no profiles, no traces. Just pure private messaging.
Perfect for when you need total metadata privacy and no digital fingerprint.
🌱 Nostr DMs – Messages with your Web of Trust
If you’re already on Nostr, using DMs is a natural step. Messages are encrypted end-to-end and tied to your public key identity.
Great for building trusted, decentralized communication channels within your Web of Trust.
🔐 PGP Email – Old-school but rock solid
PGP lets you encrypt your emails and verify identities with public keys. It’s still one of the most powerful tools for asynchronous, verifiable, and encrypted communication—especially for long-form or professional exchanges.
🔁 Use them all together
Different tools for different roles. Want to talk anonymously? Use SimpleX.
Connecting with your Nostr tribe? Slide into those DMs.
Need to send a secure file or message over email? PGP's got your back.Privacy isn’t just one app—it’s a toolkit. Build yours.
-
 @ 9c9d2765:16f8c2c2
2025-04-22 05:30:03
@ 9c9d2765:16f8c2c2
2025-04-22 05:30:03CHAPTER NINE
"I hope you all see that I keep my promises," Mark announced confidently, raising his glass as the Ray family members murmured among themselves. "Another gift for the family, and all I ask in return is Rita’s hand. It’s a simple trade, isn’t it?"
It was the Ray family fun weekend, and Mark had once again positioned himself as their savior. He had been invited, and as expected, he made sure to make his presence known. The Ray family wasn’t happy that the new president had canceled the investment plans, which were against their initial arrangements. They had pinned their hopes on Mark, and once again, he didn’t disappoint.
At the end of the evening, Mark handed over another generous gift of cash, sealing his influence within the family. "You all know what needs to be done," he continued, flashing a smug smile. "Rita divorces James, and I’ll continue to help the family business thrive."
The murmurs grew louder. The push for divorce within the Ray family gained momentum, and James could feel the weight of humiliation pressing down on him once again. Yet, amidst the pressure and manipulation, Rita remained firm.
"I’m not divorcing James," she declared, her voice unwavering despite the glares she received from her own family. "Not now, not ever."
A heavy silence fell over the room, but James knew this was far from over.
"You! Throw him out!" Mark barked, pointing a commanding finger at James as he entered the gathering. The Ray family fun night was in full swing, and Mark, feeling emboldened by the power he had secured within the family, was eager to humiliate James once and for all.
The private guard, a broad-shouldered man dressed in a sleek black uniform, stepped forward. But as soon as his gaze met James’s, his stern expression softened. He hesitated, his posture shifting from aggression to submission. Then, to the shock of everyone present, he bent slightly at the waist and uttered a quiet but firm apology.
"I’m sorry, sir. I cannot do that," the guard said, his voice steady yet respectful.
Mark’s eyes widened in disbelief. “What? Are you insane? I said, throw him out!” he roared, his face twisting in fury.
The guard, still standing between Mark and James, clenched his fists at his sides. “I work part-time at JP Company. I know who this man is. I cannot lay a hand on him.”
A murmur rippled through the room. Helen, Christopher, and the rest of the Ray family exchanged puzzled glances. Why would a mere security guard refuse an order so boldly? What did he mean by knowing James?
Mark’s frustration boiled over. He took a threatening step forward. “Then you’re fired! Get out!” he spat, his voice thick with rage.
The guard stood his ground, his eyes flicking briefly to James, who remained calm, his expression unreadable. With a respectful nod to James, the guard turned on his heel and exited, his departure leaving an unsettling silence in his wake.
Helen, unable to contain her curiosity, leaned toward Christopher. “What just happened? Why would he refuse Mark’s order? What does he know about James that we don’t?”
Christopher shook his head, his brow furrowed in confusion. “I have no idea. But that was not just any ordinary security guard. He spoke as if James was someone important.”
Susan, who had been quietly observing the scene, finally spoke. “Could it be that James has some hidden power we don’t know about?”
Helen scoffed. “Ridiculous! That beggar? He’s nothing but a burden!” But despite her words, an uneasy feeling settled in her stomach.
Mark, still seething, turned his glare to James. “Enjoy this moment, you wretch. Soon, you’ll have nowhere left to run.” He stormed out, leaving a tense and confused silence behind.
James remained where he was, his calm demeanor never wavering. He had stood his ground without even speaking a word, and yet, the Ray family’s perception of him was beginning to shift. There were too many unanswered questions. Why did a security guard from JP Company recognize him? Why did he refuse to act against him? And most importantly who was James, really?.
"We can't let this business week slip through our fingers," Helen muttered anxiously, pacing back and forth in the living room. "Christopher, Robert, one of you must represent Ray Enterprises. We need to secure more investments."
Christopher sighed, rubbing his temples. "Helen, we are aware of how important this meeting is. But are you sure you should attend with me? You know these investors expect to meet actual executives."
"I have every right to be there," Helen snapped. "The future of this family business is at stake! If you won't do it, I'll step in to make sure we don't lose more ground."
Meanwhile, across the city, James stepped into the most luxurious boutique, scanning the racks of high-end suits. The store clerk eyed him skeptically, unimpressed by his simple attire. "Sir, are you sure you’re in the right place?" the clerk asked with a forced smile.
James smirked. "Yes. Get me the best suit you have."
After a long selection process, he emerged wearing a custom-tailored suit worth a fortune, making even the store owner widen his eyes in disbelief. James checked his reflection in the mirror, adjusting his cuffs. "Perfect," he murmured.
The day of the business meeting arrived, and the grand hall was filled with top executives, investors, and company representatives from across the city. The chatter in the hall buzzed with anticipation as they awaited the arrival of JP Enterprises' new president.
Helen sat rigidly beside Christopher, her fingers tapping nervously on the table. "I wonder who JP Enterprises will send. Their investments have been making waves lately," she whispered.
Before Christopher could respond, a hush fell over the crowd. The doors swung open, and the awaited president stepped in, his presence commanding immediate attention.
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 97c70a44:ad98e322
2025-03-06 18:38:10
@ 97c70a44:ad98e322
2025-03-06 18:38:10When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specified a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
-
No auth, fully public - anyone can read/write to the group.
-
Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Triflector for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Triflector for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
Rooms have two modes - managed and unmanaged. Managed rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. This allows rooms to switch between managed and unmanaged modes without losing any content.Managed room names come from
kind 39000room meta events, but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access. Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
-
 @ 9223d2fa:b57e3de7
2025-04-22 20:02:06
@ 9223d2fa:b57e3de7
2025-04-22 20:02:069,322 steps
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ df478568:2a951e67
2025-04-17 21:10:33
@ df478568:2a951e67
2025-04-17 21:10:33I created a GitHub repository at https://github.com/Marc26z/ZapShirts. Here is a copy of the README.md
ZapShirts
This is an idea I have to make t-shirts that are also bitcoin point-of-sale terminals.

Create T-Shirt Point-Of-Sale
The idea is to create a bitcoin point of sale on a T-shirt. You can use it to sell stickers at a conference or have a friend pay you back for dinner. It is only limited by your imagination.
Why Would Anybody Need A ZapShirt?
I no longer "orange pill" local businesses. I do not care if they wish to accept bitcoin, but I want to be the change in the world I want to see. I will accept bitcoin on a T-Shirt to show others how easy it is to accept bitcoin as a p2p electronic cash system. Anyone can accept bitcoin as payment if they want to. You could print a sign on a piece of paper if you wanted to. The problem was, nobody I asked wanted a sign, even bitcoiners. So I asked myself...Self, what if you did the opposite? What if the customer accepted bitcoin, but the business owner did not.
I also thought it would be pretty cool T-Shirt to wear at meet-ups.
How To Make Your Own Zap Shirt
- Create a QR code that sends you to your coinos page, getalby page, strike or whatever you feel comfortable using. This can easily be done at https://libreqr.com/
- Use a program like gimp to replace the default QR Code with your own QR code on the file.
- Create the shirt.
To support this please zap me or buy one from my store.
Can I Buy A Zap Shirt?
Yes. If you would like a shirt, hit me up on nostr
https://primal.net/marc
end README.md
I like the idea of open sourcing my ideas and trying to sell them for sats on the Internet. I am currently working on a site to sell things like this and my gift cards. I feel a little uneasy because I haven't been writing much, but I've been building. The idea is to create bitcoin educational products and services. Onward.
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:55:30
@ 9f8b9baa:b922fc09
2025-04-22 04:55:308KI là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người dùng những trải nghiệm đa dạng và thú vị. Với giao diện dễ sử dụng và thiết kế tối giản, 8KI giúp người chơi dễ dàng tiếp cận và thưởng thức các trò chơi yêu thích. Nền tảng này không chỉ cung cấp các trò chơi giải trí mà còn có các tính năng tương tác độc đáo, tạo ra không gian thú vị để người dùng khám phá và tận hưởng. Dù bạn là người mới hay đã có kinh nghiệm, 8KI luôn mang đến những hoạt động đa dạng, từ các trò chơi giải trí nhẹ nhàng đến những thử thách cần kỹ năng cao. Hệ thống cập nhật thường xuyên giúp nền tảng luôn giữ được sự mới mẻ và thu hút, khiến người dùng không bao giờ cảm thấy nhàm chán.
Một trong những điểm mạnh của 8KI là khả năng tùy chỉnh trải nghiệm người dùng, mang đến sự linh hoạt tối đa cho mọi người tham gia. Người chơi có thể điều chỉnh các thiết lập theo sở thích cá nhân, từ việc thay đổi độ khó cho đến lựa chọn các chế độ chơi khác nhau. Điều này giúp người dùng cảm thấy thoải mái hơn khi tham gia, đồng thời cũng tạo ra những thử thách mới mẻ để không ngừng phát triển kỹ năng. Hệ thống này giúp 8KI trở thành một nền tảng phù hợp cho mọi đối tượng, từ những người mới bắt đầu cho đến những người chơi kỳ cựu. Mỗi người dùng có thể tìm thấy một kiểu chơi phù hợp với sở thích của mình, mang lại một trải nghiệm cá nhân hóa và thú vị. Khả năng điều chỉnh này tạo ra sự khác biệt, giúp người dùng không chỉ giải trí mà còn nâng cao khả năng của bản thân qua từng trò chơi.
Không chỉ dừng lại ở việc cung cấp những trò chơi hấp dẫn, 8KI còn tạo ra một cộng đồng mạnh mẽ, nơi người chơi có thể giao lưu, chia sẻ kinh nghiệm và kết nối với nhau. Các tính năng xã hội như bảng xếp hạng, diễn đàn và các cuộc thi định kỳ tạo ra cơ hội để người dùng tương tác và phát triển mối quan hệ với những người chơi khác. Cộng đồng 8KI không chỉ đơn thuần là một không gian giải trí mà còn là nơi để những người cùng sở thích có thể chia sẻ những câu chuyện, chiến lược và học hỏi từ nhau. Điều này làm tăng thêm giá trị của nền tảng, giúp người chơi không chỉ tận hưởng các trò chơi mà còn xây dựng được các mối quan hệ bền vững. Sự kiện và chương trình khuyến mãi thú vị cũng thường xuyên được tổ chức, giúp cộng đồng 8KI luôn sôi động và thu hút người tham gia. Với môi trường thân thiện và tính năng tương tác mạnh mẽ, 8KI đã và đang trở thành một điểm đến giải trí lý tưởng cho những ai yêu thích sự kết nối và sáng tạo.
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ 4fe4a528:3ff6bf06
2025-03-01 12:24:49
@ 4fe4a528:3ff6bf06
2025-03-01 12:24:49Technology adoption has been hard for a lot of people to understand. Tucker this week finally understood why gold became money. He finally understood that hard money drives out money that isn’t scarce. Still, most people don’t store their wealth in the hardest money ever made—Bitcoin.
Yes, Bitcoin went down 20-25% this week. How can the scarcest asset vary that much? Humans tend toward emotion—fear or greed. I am no exception, but if you have a plan or have been here before, you can control your emotion.
Let me illustrate. I installed a camera on the barn this week so I could save time checking on the cows. Lo and behold, the WiFi wasn’t strong enough, so I bought two outdoor access points. Whenever I would add them to the house, the WiFi mesh system would cause my internet to go down on the main computer. Fear of losing internet was causing me to consider taking a $100 write-off on my idea of saving time. Because I have solved networking issues before, I had the courage to be greedy and keep working at it. I know a lot of people would give up on technology and throw their cell phone in the snowbank - my neighbor does that. He usually comes back for it because he likes communication. Is a cell phone a feature or a bug? Answer… both.
What Satoshi solved 16 years ago was how to move 1s and 0s to different devices and keep them secure. What Vint Cerf solved 35 years ago was how to route 1s and 0s and have the packets arrive at the intended destination. Both Bitcoin and the Internet rely on people not throwing their cell phone in the snowbank.
This last drawdown in Bitcoin has given me hope that people will start to understand technology better and give up on Sol and Eth. Finally, people are realizing that printing digital coins doesn’t help people, just like printing Canadian dollars doesn’t help the average Canadian get ahead. It could be that Sam Bankman-Fried is in jail, but I think it has more to do with people starting to get comfortable with technology. https://youtu.be/fxWZO0FEQ1g
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:54:38
@ 9f8b9baa:b922fc09
2025-04-22 04:54:38MM99 là một nền tảng giải trí trực tuyến nổi bật, cung cấp cho người dùng một không gian đa dạng để thưởng thức các trò chơi và hoạt động giải trí. Với giao diện dễ sử dụng và thiết kế trực quan, MM99 tạo ra một trải nghiệm liền mạch và dễ tiếp cận cho tất cả người dùng. Nền tảng này không chỉ thu hút với kho nội dung phong phú mà còn đem đến những cập nhật liên tục, giúp người chơi không bao giờ cảm thấy nhàm chán. MM99 đặc biệt chú trọng vào việc cung cấp các trò chơi đa dạng, từ những trò chơi mang tính thử thách cao cho đến các hoạt động giải trí nhẹ nhàng, đáp ứng được nhu cầu của mọi người dùng. Với mỗi lần tham gia, người chơi luôn có thể tìm thấy những trải nghiệm mới mẻ và hấp dẫn, giúp họ thư giãn và giải trí sau những giờ làm việc căng thẳng.
Điều khiến MM99 trở nên đặc biệt chính là khả năng tùy chỉnh trải nghiệm của người dùng. Nền tảng này cho phép mỗi người chơi điều chỉnh các thiết lập trò chơi theo sở thích và nhu cầu cá nhân, giúp mang lại cảm giác thoải mái và dễ dàng kiểm soát. Người dùng có thể thay đổi mức độ khó, lựa chọn các chế độ chơi khác nhau và thậm chí thay đổi các yếu tố giao diện sao cho phù hợp nhất với mình. Sự linh hoạt này giúp MM99 luôn duy trì sự hấp dẫn và tạo ra một trải nghiệm giải trí cá nhân hóa cho từng người dùng. Đặc biệt, MM99 không chỉ phù hợp với những người chơi mới mà còn là lựa chọn lý tưởng cho những ai yêu thích thử thách và khám phá các chiến lược mới. Tính năng tùy chỉnh giúp người chơi dễ dàng tham gia và luôn cảm thấy hào hứng mỗi khi quay lại nền tảng này.
Bên cạnh việc cung cấp một loạt các trò chơi thú vị, MM99 còn chú trọng đến việc xây dựng một cộng đồng gắn kết và tương tác. Các tính năng xã hội như bảng xếp hạng, diễn đàn trò chuyện và các sự kiện đặc biệt giúp người chơi có cơ hội giao lưu, học hỏi và kết bạn với những người cùng sở thích. MM99 đã tạo ra một môi trường nơi người dùng không chỉ tham gia vào các trò chơi mà còn có thể kết nối và chia sẻ những trải nghiệm của mình. Những cuộc thi và sự kiện thường xuyên được tổ chức, tạo ra một không khí sôi động và đầy thử thách, thúc đẩy người chơi quay lại để tham gia và cải thiện kỹ năng. Cộng đồng MM99 ngày càng trở nên mạnh mẽ và đoàn kết, là yếu tố quan trọng giúp nền tảng này phát triển và duy trì sự hấp dẫn trong mắt người dùng. MM99 không chỉ là một nơi để giải trí mà còn là một không gian giao lưu tuyệt vời cho những ai muốn tìm kiếm niềm vui và kết nối với những người có cùng đam mê.
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ 2183e947:f497b975
2025-04-15 00:13:02
@ 2183e947:f497b975
2025-04-15 00:13:02(1) Here is a partial list of p2p bitcoin exchanges and their friends:
- Robosats (custodial escrow)
- Hodlhodl (2-of-3 escrow)
- Peach (2-of-3 escrow)
- Binance P2P (2-of-3 escrow)
- Bisq v1 (either user can send the funds to a custodial escrow, but if neither one does that, the escrow never touches user funds)
- Bisq v2 (no escrow)
(2) In my opinion, bisq2 is the only "true" p2p exchange on the above list. In a true p2p system, the only people who *can* touch the money are the buyer and the seller. Whenever there's an escrow, even one that has to be "triggered" (like in bisq v1), it's not "really" p2p because the escrow serves as a middleman: he can collude with one party or the other to steal user funds, and in some models (e.g. robosats) he can just straight up run off with user funds without needing to collude at all.
(3) In bisq2 (the One True P2P exchange), buyers select sellers solely based on their reputation, and they just directly send them the bitcoin *hoping* they are as honest as their reputation says they are. What I like about this model is that bisq is not involved in bisq2 at all except as a platform to help buyers discover reputable sellers and communicate with them. There are two things I don't like about this "reputation" model: it's hard to get a good reputation, and it's hard to debug payment failures in this context. I've tried to do about 5 trades on bisq2 (as someone with no reputation) and not a single one went through. Four times, everyone ignored my offers or someone accepted it but then abandoned it immediately. Once, someone accepted my offer, but I could not pay their lightning invoice for some reason, so we mutually canceled the trade.
(4) Just because I opined that an exchange with an escrow "doesn't count" as peer-to-peer doesn't mean that's a bad thing. Of the list of exchanges in number 1, I most frequently use robosats, which, per my analysis, sounds like the "worst" one if considered solely on the metric of "which one is the most p2p." But I use it because there are *advantages* to its model: the btc seller doesn't need a reputation to use it (because the escrow is there to ensure he can't cheat, and so the escrow is the trusted third party, not the btc seller) and payment failures are easier to debug because you're always paying one of the coordinators, who tend to be responsive and knowledgeable and can help you figure out how to fix it (it's how they make money, after all).
(5) There are at least two ways to do escrow without a 3rd party. Satoshi Nakamoto outlines one way to do it here: https://satoshi.nakamotoinstitute.org/posts/bitcointalk/threads/169/ Make a 2 of 2 multisig between the btc buyer and the btc seller, and have the btc seller put his btc in that multisig. Then have the btc buyer send the product (fiat money) to the btc seller. When the btc seller receives it, he sends his privkey to the btc buyer, who can now withdraw the money. The advantage of this system is that the buyer has no incentive to "stiff" the seller (by not sending the fiat), because if he does that, he won't get paid. The downside is, if the btc buyer is a troll who just aborts the protocol halfway through the trade, the seller loses his btc and cannot recover it.
(6) There is another way: start out with a 2 of 2 multisig just like above, but instead of having the btc seller fund it by himself, have the buyer and the seller *both* put in the *same amount* in the *same transaction* (i.e. via a coinjoin), and have the btc seller put in a bit "extra" -- like 20% extra. For example, if the btc seller wants $100 in fiat, the multisig would have $220 in it in total -- $120 from the seller and $100 from the buyer. Using this model, the disadvantage mentioned in paragraph number 5 is fixed: the buyer has an incentive now to send the fiat, otherwise he loses the $100 he put in. He only gets his $100 back if the btc seller cosigns to give it to him, which he'll only do once he receives the product. Meanwhile, the seller is *also* incentivized properly: he only gets his *extra* $20 back if the btc buyer cosigns to give it to him, which he'll only do if the transaction he's signing *also* gives him back *his* $100 deposit.
(7) The model described in number 6 exists: https://scrow.exchange/ is a website that implements it as an option, though as far as I'm aware, no one uses it. The downsides of this model are: it's capital intensive, e.g. a trade for $100 involves $220 or more. Also, the btc buyer needs to already *have* btc to post as a bond, so this cannot be his first time acquiring btc (unless someone helps him make his first deposit). Also, a very rich person who does not care about money can still be a troll; they deposit funds into the multisig alongside their counterparty, then abandon the trade, because they have so much money they don't care if they get it back as long as they cause suffering to their counterparty.
(8) I'd like to see more p2p exchanges, and more exchanges like robosats. I want to continue to spread awareness of ways they can improve -- like the protocols mentioned in numbers 5 and 6 -- and help them implement these protocols. If you run an exchange on the list in number 1 or want to start one, reach out to me, I'd love to help.
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ df67f9a7:2d4fc200
2025-04-16 22:13:20
@ df67f9a7:2d4fc200
2025-04-16 22:13:20Businesses want Nostr, but Nostr is not ready for business. What can be done?
TLDR :
What Nostr brings to business apps…
- Get your brands in front of users with your choice of SEO and Algos that YOU control.
- Access unlimited public user data from across the network without fees or permission.
- Keep your business data private, while "releasing" liability for other data collected by your apps.
- Build one app to reach a diversity of users from across the network, even from other apps.
- Build your own tech and to use it as you wish. No gate keepers or code review process.
Businesses want Nostr.
- Businesses want reliable SEO and socials to put their brands in front of users, rather than arbitrary gate keepers, censoring the marketplace on a whim.
- Businesses want open access to harvest public data for free on a soveregnty respecting network, rather than paying gate keepers for access to user data of questionalble origin.
- Businesses want the freedom to NOT take ownership of certain user data collected by their apps, rather than being liabile for moderation and safe handling on their private infrastructure.
- Busineses want a single open protocol on which to build their apps, with unlimited potential and a diversity of shared users from other apps, rather than multiple siloed networks with difering APIs and demographics.
- Businesses want to own the technology they build and to use it as they wish, rather than submit their code for approval and control by arbitrary gate keepers.
But Nostr is not ready for business.
- Businesses DON'T want proprietary app data stored publicly as signed Nostr events on user specified relays.
- Businesses DON'T want to have to specify, or be constrained by, or even navigate the complexity of Nostr NIP standards for every novel kind of content that their apps generate.
- Businesses DON'T want to "open source" their entire suite of native apps JUST to assure end users that Nostr private keys are being safely handled.
- Businesses DON'T want to have to "rewrite" their entire app backend just to accomodate the Nostr way of "users sign events but dont actually login to your server" auth architecture.
- Businesses DONT want to suffer DDOS from bots and bad actors, or to expose their users to unwanted content, or even to have their own content disappear a sea of spam and misinformation.
Here’s what can be done.
- More tools and services for private business apps to coexist with freedom tech, and even thrive together, on the Nostr network.
- Extensible Webs of Trust algos for discovery and reach into any audience or demographic of trusted users.
- WoT powered standard APIs for exposing content to Nostr (and other business apps) from within a “black box” business app.
- HTTP AUTH (NIP 98) integration for business apps, allowing users to create local content WITHOUT needing discrete signatures or “linked” user accounts.
- Frost compatible “login“ for business apps, allowing users to paste “disposable” nsecs into proprietary clients without fear of their “cold” nsec being compromised.
- Support for “incremental” (and voluntary) adoption of freedom tech into existing business apps, with easy off-ramps for businesses to transfer more and more siloed data onto the “public” network.
Thoughts so far…
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:53:45
@ 9f8b9baa:b922fc09
2025-04-22 04:53:4532Win là một nền tảng giải trí trực tuyến sáng tạo, mang đến cho người dùng một loạt các hoạt động và trải nghiệm đa dạng. Với giao diện dễ sử dụng và thiết kế trực quan, 32Win giúp người dùng dễ dàng tham gia và tận hưởng những phút giây giải trí thú vị. Nền tảng này nổi bật với khả năng cung cấp các nội dung luôn mới mẻ và đa dạng, từ các trò chơi đầy thử thách cho đến những hoạt động mang tính giải trí cao. Dù bạn là người mới hay đã có kinh nghiệm, 32Win luôn có thể đáp ứng nhu cầu của tất cả mọi người. Hệ thống của nền tảng này liên tục được cập nhật và đổi mới, đảm bảo mang lại những trải nghiệm giải trí chất lượng và không bao giờ nhàm chán. Các hoạt động thú vị và tính năng độc đáo của 32Win chính là điểm thu hút chính, khiến người dùng luôn muốn quay lại để khám phá thêm nhiều điều mới mẻ.
Sự thành công của 32WIN không chỉ đến từ sự đa dạng của các trò chơi mà còn từ khả năng cá nhân hóa cao. Nền tảng này cho phép người dùng điều chỉnh các thiết lập theo sở thích riêng, từ việc thay đổi mức độ khó, chọn chủ đề yêu thích cho đến lựa chọn các chế độ chơi khác nhau. Điều này giúp người dùng có thể tạo ra một trải nghiệm hoàn toàn phù hợp với nhu cầu và sở thích cá nhân. Bằng cách này, 32Win mang lại sự linh hoạt tối đa, đảm bảo rằng mỗi người dùng có thể tìm được niềm vui và sự thách thức ở mức độ phù hợp nhất với mình. Hệ thống cài đặt cá nhân hóa không chỉ giúp nâng cao trải nghiệm mà còn giúp người dùng cảm thấy thoải mái và hài lòng trong suốt quá trình tham gia. 32Win luôn chú trọng đến sự hài lòng của người dùng và cam kết mang lại những dịch vụ giải trí tốt nhất.
Một điểm đáng chú ý nữa của 32Win là cộng đồng người dùng sôi động và thân thiện. Nền tảng này không chỉ cung cấp các trò chơi mà còn tạo ra một môi trường nơi mọi người có thể giao lưu, kết nối và chia sẻ kinh nghiệm. Các tính năng như bảng xếp hạng, diễn đàn thảo luận và các cuộc thi giữa người chơi không chỉ tăng cường tính tương tác mà còn tạo ra một không gian gắn kết, nơi người dùng có thể học hỏi và hỗ trợ lẫn nhau. Cộng đồng mạnh mẽ của 32Win là một yếu tố quan trọng trong việc xây dựng một môi trường giải trí lành mạnh và thú vị. Thêm vào đó, các sự kiện đặc biệt và các chương trình khuyến mãi hấp dẫn thường xuyên được tổ chức, giúp giữ cho người dùng luôn có động lực quay lại và tham gia. Với những tính năng này, 32Win không chỉ là một nền tảng giải trí, mà còn là một nơi để mọi người có thể kết nối, tạo dựng mối quan hệ và tận hưởng thời gian bên nhau.
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ f6488c62:c929299d
2025-04-22 04:04:18
@ f6488c62:c929299d
2025-04-22 04:04:18วันนี้ตลาดโลก “เดือดแบบเงียบ ๆ” แม้ทรัมป์จะยังไม่พูดอะไร แต่สินทรัพย์เสี่ยงกลับพลิกเกมกันคนละทาง โดยเฉพาะฝั่งทองคำและคริปโตที่มีสัญญาณบวกหลายจุด ⚡
🟡 ไฮไลต์ร้อนวันนี้ 🪙 ทองคำพุ่งทะลุ $3,510/oz (ตามราคา PAXG) → นักลงทุนวิ่งเข้าทองแบบ Panic Buy ท่ามกลางความไม่แน่นอนทางเศรษฐกิจโลก 🪙 Bitcoin มั่นคงจากแรงซื้อของ BlackRock & MicroStrategy รวมกันเกือบ $640M → โทนตลาดยังเอียงฝั่งบวก 🪙 Paul Atkins ผู้สนับสนุนคริปโต ขึ้นแท่นประธาน SEC → อาจพลิกเกมกฎระเบียบในสหรัฐฯ ไปอีกฝั่ง 🪙 Coinbase เปิดฟิวเจอร์ส XRP / สิงคโปร์เปิด Bitcoin Futures กลางปีนี้ → แสดงถึงสัญญาณยอมรับระดับโลก
🔻 ฝั่งน่าห่วง ⚠️ Ethereum ETF ถูกถอนทุน $1.1B ใน 7 สัปดาห์ → แสดงความลังเลของนักลงทุนสถาบัน ⚠️ ตลาดยังหวาดระแวง หลัง "ภาษีวันปลดปล่อย" ของทรัมป์และการโจมตี Fed → ทรัมป์เงียบ = ตลาดระวัง ⚠️ หุ้นสหรัฐแกว่งแรง → นักลงทุนย้ายเงินเข้าทอง-คริปโตเพื่อหาที่พักพิง
📌 กลยุทธ์วันนี้:
"ทองไม่ใช่แค่ Safe Haven แต่ตอนนี้คือทางหนี" นักลงทุนเริ่มขยับพอร์ตหนีจากตลาดหุ้น เข้าทองและคริปโต → ระวังแรงกระเพื่อมรอบดึก (โดยเฉพาะจากฝั่งสหรัฐฯ)
📎 ฝากแชร์โพสต์นี้ไว้ดูอีกที ถ้าคุณคิดว่า “ปี 2025 น่าจะผันผวนที่สุดในรอบ 10 ปี”
ทองคำ #Bitcoin #ข่าวการเงิน #Crypto #ตลาดโลก #เฟด #ทรัมป์ #ทองขึ้น #ลงทุนทอง
-
 @ 06639a38:655f8f71
2025-04-16 12:11:31
@ 06639a38:655f8f71
2025-04-16 12:11:31Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ f683e870:557f5ef2
2025-04-08 11:13:27
@ f683e870:557f5ef2
2025-04-08 11:13:27When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was Trusted Assertion by Vitor Pamplona.
The idea is to have
kind:30382represent assertions made about an entity, which could be a pubkey, for example. The NIP also specifies a tag calledrank, which can be used to build some basic WoT primitives.Example event:
{ "kind": 30382, "tags": [ ["d", "e88a6...50411"], ["rank", "89"], ["zap_amt_sent", "1000000"], ], "content": "", //... }However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: real-time, personalized ranking.
To illustrate our different approaches, we will show how to replicate our Verify Reputation with trusted assertions.
Verify Reputation
Verify Reputation returns:
- the rank, follow count and followers count of the given
target - its top followers by rank.
All ranks are personalized to the given
source.This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more.
To get the same result with trusted assertions, you would have to
- Get all contact lists that contain the
target(as aptag) - Build the target’s
followerlist from those event authors - Get the trusted assertions for the target and each of the followers
- Sort them by the rank provided by the trusted assertions
This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party.
More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for. This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.
Are you looking to add Web of Trust capabilities to your app or project?
- the rank, follow count and followers count of the given
-
 @ 16d11430:61640947
2025-02-09 00:12:22
@ 16d11430:61640947
2025-02-09 00:12:22Introduction: The Power of Focused Attention
In an age of distraction, power is not merely held through material wealth, authority, or control over others—it is built through focused attention. The human brain, a complex quantum-biological processor, constructs reality through perception. When harnessed correctly, focused attention allows individuals to transcend limitations, reshape their reality, and live free.
Power, then, is not external—it is a construct supported by the mind and created within the brain. Understanding how this works offers a path to transcendence, autonomy, and liberation from imposed limitations.
The Neuroscience of Focused Attention: Constructing Reality
The brain is a prediction engine, constantly processing information and filtering out irrelevant stimuli. Focused attention directs this process, acting as a spotlight that selects what becomes part of one's conscious experience. This is the fundamental mechanism behind cognitive power.
- Neuroplasticity: Building Power Through Repetition
The brain adapts to repeated stimuli through neuroplasticity. What one focuses on consistently rewires neural pathways, strengthening certain thoughts, beliefs, and abilities. Over time, this focus builds an internal structure of power—a network of ideas and perceptions that define one’s reality.
If one focuses on problems, they grow.
If one focuses on solutions, they appear.
If one focuses on fear, it shapes perception.
If one focuses on mastery, skills develop.
- The Quantum Mind: Attention as a Creative Force
Quantum physics suggests that observation influences reality. Just as subatomic particles behave differently when measured, focused attention may act as a force that shapes possibilities into tangible outcomes.
This aligns with the ancient concept that "energy flows where attention goes." What one attends to with intention can manifest as action, opportunity, and ultimately, freedom.
- The Reticular Activating System (RAS): Filtering Reality
The Reticular Activating System (RAS) in the brainstem acts as a gatekeeper for focus. It determines what information enters conscious awareness. When trained, it can filter out distractions and amplify pathways toward a desired goal.
Want to see opportunities? Program the RAS by setting clear intentions.
Want to break free from limiting beliefs? Train focus away from conditioned fears.
The Mind’s Role: Transcending Limitations
The mind is the interpreter of the brain’s electrical and biochemical activity. While the brain processes raw data, the mind provides meaning. This distinction is crucial because meaning determines how one experiences reality.
- Breaking Mental Chains: Rewriting Narratives
Most limitations are narratives—stories imposed by culture, society, or personal history. True power lies in rewriting these stories.
Instead of “I am trapped by my circumstances,” shift to “I create my own reality.”
Instead of “I need permission,” shift to “I give myself permission.”
By restructuring meaning, the mind can redefine the limits of what is possible.
- The Silence Paradox: Accessing Higher States
Silence, both literal and mental, creates space for higher-order thinking. Just as quantum tunneling allows subatomic particles to pass through barriers without energy loss, silence allows the mind to bypass noise and access deeper intelligence.
Meditation, stillness, and solitude amplify internal power.
The ability to not react is a form of control over external influence.
True mastery comes from detachment—engaging the world without being controlled by it.
Transcendence: Living Free Through Mental Autonomy
To transcend means to rise above imposed structures—whether societal, psychological, or energetic. The construct of power built through focused attention allows one to escape control mechanisms and live autonomously.
- Sovereignty of Mind: Owning One’s Thoughts
A free mind is one that chooses its inputs rather than being programmed by external forces. This requires:
Awareness of mental conditioning (social narratives, propaganda, biases)
Intentional thought selection (curating what enters the mental space)
Guarding attention fiercely (not allowing distraction to hijack focus)
- Detachment From Control Structures
Society operates on the principle of attention capture—through media, politics, and algorithms that direct thought patterns. Escaping these requires detachment.
Do not react emotionally to fear-based programming.
Cultivate independent thought by questioning imposed narratives.
Reduce external noise to amplify internal wisdom.
- The Flow State: Moving Beyond Constraints
When focus is refined to its highest degree, one enters flow state—a condition where action and awareness merge, and limitations dissolve.
In flow, work becomes effortless.
Creativity becomes boundless.
Freedom becomes not just a philosophy, but a lived experience.
Conclusion: The Mind as the Ultimate Key to Freedom
Power is not an external possession—it is the ability to direct one’s own focus. Through the interplay of brain function, cognitive attention, and mental discipline, one constructs personal sovereignty. The individual who masters focus, controls reality.
Freedom is not given. It is built—through attention, intention, and an unwavering commitment to mental autonomy.
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.













