-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ d08c9312:73efcc9f
2025-04-18 20:17:41
@ d08c9312:73efcc9f
2025-04-18 20:17:41https://youtu.be/qK7ffYzxiiQ
Resolvr was recently featured in The Institutes RiskStream Collaborative's educational video series on insurance digitization and cross-border payments. With over a century of history educating insurance professionals, The Institutes has established itself as the premier knowledge resource in risk management and insurance. And its RiskStream Collaborative non-profit serves as the industry's largest enterprise-level technology consortium focused on streamlining insurance processes through innovative solutions.
Resolvr's co-founders, Aaron Daniel and Dave Schwab, were joined by industry experts Lizzy Eisenberg from Lightspark and Austin Cornell from Zero Hash to discuss how Bitcoin and the Lightning Network are transforming global insurance payments operations.
Watch the video to learn how Resolvr is leveraging these real-time digital settlement networks to solve significant inefficiencies in today's insurance payment ecosystem - from the months-long settlement times that trap billions in value, to the manual reconciliation processes costing the industry nearly £1 billion annually at Lloyd's of London alone.
We're grateful to RiskStream Collaborative for showcasing these transformative technologies and emphasizing the importance of combining specialized insurance-native interfaces with powerful payment infrastructure to solve industry-specific challenges.
For more information about how Resolvr can help your organization streamline premium processing and payments, contact us today.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 7d33ba57:1b82db35
2025-03-27 08:55:21
@ 7d33ba57:1b82db35
2025-03-27 08:55:21L'Estartit is famous for its stunning beaches, the Medes Islands, and incredible diving opportunities. Once a small fishing village, it’s now a paradise for nature lovers, water sports enthusiasts, and those seeking a relaxing Mediterranean escape.
🏖️ Top Things to See & Do in L'Estartit
1️⃣ Medes Islands (Illes Medes) 🏝️
- A protected marine reserve, perfect for snorkeling and scuba diving.
- Explore sea caves, coral reefs, and diverse marine life.
- Take a glass-bottom boat tour to admire the underwater world without getting wet.
2️⃣ L'Estartit Beach 🏖️
- A long sandy beach with shallow waters, ideal for families.
- Great for swimming, sunbathing, and water sports like windsurfing and kayaking.
- Offers fantastic views of the Medes Islands.
3️⃣ Montgrí Massif & Castle 🏰
- Hike up to the Montgrí Castle for panoramic views of the Costa Brava.
- Trails through rocky landscapes and Mediterranean forests.
- A perfect spot for hiking, mountain biking, and photography.
4️⃣ Coastal Walking Route (Camí de Ronda) 🌊
- A breathtaking hiking trail along the cliffs, connecting L'Estartit with nearby beaches and coves.
- Discover hidden spots like Cala Pedrosa and Cala Ferriol.
5️⃣ Explore the Old Town & Port ⚓
- Wander through narrow streets with local shops and seafood restaurants.
- Visit the Sant Genís Church, a historic landmark in the town center.
- Enjoy a drink with a view at the marina.
6️⃣ Kayaking & Stand-Up Paddleboarding 🚣♂️
- Paddle along the coastline to explore caves, cliffs, and hidden coves.
- A great way to experience the natural beauty of the area.
🍽️ What to Eat in L'Estartit
- Suquet de Peix – Traditional Catalan fish stew 🐟
- Arroz a la Cassola – A savory rice dish with seafood 🍤
- Fideuà – Like paella, but made with short noodles instead of rice 🍜
- Calamars a la Planxa – Grilled squid with olive oil and garlic 🦑
- Crema Catalana – A classic Catalan dessert similar to crème brûlée 🍮
🚗 How to Get to L'Estartit
🚆 By Train: The nearest train station is Flaçà (30 min by car/taxi) with connections from Barcelona and Girona.
🚘 By Car: 1.5 hrs from Barcelona, 45 min from Girona, 1 hr from Figueres.
🚌 By Bus: Direct buses from Barcelona, Girona, and other Costa Brava towns.
✈️ By Air: The nearest airport is Girona-Costa Brava (GRO, 55 km).💡 Tips for Visiting L'Estartit
✅ Best time to visit? Late spring to early autumn (May–September) for warm weather 🌞
✅ Book diving tours in advance – Medes Islands are a top diving destination 🤿
✅ Hike early in the morning to avoid the heat & get the best views 🥾
✅ Visit in June for the Havaneres Festival, celebrating Catalan maritime music 🎶 -
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 000002de:c05780a7
2025-04-23 16:27:56
@ 000002de:c05780a7
2025-04-23 16:27:56Natalie Brunell had comedian T.J. Miller known for Silicon Valley on her show Coin Stories. I was kinda surprised. Not sure why but I recognized his voice because that's my brain I can forget a face but never a voice.
So what person that has fame also secretly is a bitcoiner. Not has the ETF or whatever but actually gets it and has for a while.
I think this is pretty widely believed that Mark Zuckerburg is a bitcoiner so that would be the person I'd list. No clue beyond that. There has to be quite a few well known people that also get bitcoin and just don't talk about it.
SO, who do you think is in the club?
originally posted at https://stacker.news/items/955179
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ e516ecb8:1be0b167
2025-04-23 15:25:16
@ e516ecb8:1be0b167
2025-04-23 15:25:16¡Muy bien, amigo! Vamos a sumergirnos en las profundidades arquetípicas de la psique humana para desentrañar esta noción, esta chispa de sabiduría que intentamos articular, porque, verás, no es una mera declaración trivial, no, no, es una verdad ontológica que reverbera a través de los eones, en los cimientos mismos del Ser.
Permíteme, si me lo permites, desplegar esta idea como si fuera un tapiz mitológico, tejido con los hilos del caos y el orden, porque eso es lo que hacemos cuando nos enfrentamos a la condición humana, ¿no es así? Nos esforzamos por dar sentido al cosmos, por encontrar un faro en la tormenta.
Ahora, consideremos esta proposición: la felicidad, esa efímera mariposa que revolotea en los márgenes de nuestra conciencia, no es, como podrías suponer ingenuamente, el summum bonum, el pináculo de la existencia. No, señor, no lo es. La felicidad es un estado fugaz, una sombra danzante en la caverna platónica, un destello momentáneo que se desvanece en cuanto intentas apresarlo. Es como tratar de agarrar el agua con las manos: cuanto más aprietas, más se escurre. Y aquí está el quid de la cuestión, la médula de la narrativa: perseguir la felicidad como si fuera el telos, el fin último de tu peregrinaje existencial, es una empresa quijotesca, una búsqueda condenada a la futilidad, porque la felicidad no es un destino; es un subproducto, un acompañante caprichoso que aparece y desaparece según los caprichos del destino. Pero entonces, ¿cuál es el antídoto? ¿Cuál es la brújula que orienta al alma en esta travesía a través del desierto de la modernidad? Aquí, amigo mío, es donde debemos invocar el espectro del propósito, esa fuerza titánica, ese Logos encarnado que nos llama a trascender la mera gratificación hedónica y a alinearnos con algo más grande, algo más profundo, algo que resuene con las estructuras arquetípicas que han guiado a la humanidad desde las fogatas de la prehistoria hasta los rascacielos de la posmodernidad. El propósito, verás, no es una abstracción frívola; es el eje alrededor del cual gira la rueda de la vida. Es la carga que eliges llevar voluntariamente, como el héroe mitológico que levanta el mundo sobre sus hombros, no porque sea fácil, sino porque es necesario.
Y no me malinterpretes, porque esto no es un juego de niños. Asumir un propósito es enfrentarte al dragón del caos, es mirar fijamente al abismo y decir: “No me doblegarás”. Es la disposición a soportar el sufrimiento —porque, créeme, el sufrimiento vendrá, tan seguro como el sol sale por el este— y transformarlo en algo redentor, algo que eleve tu existencia más allá de los confines de lo mundano. Porque, ¿qué es la vida sino una serie de tragedias potenciales, una danza perpetua al borde del precipicio? Y sin embargo, en esa danza, en esa lucha, encontramos significado. No es la ausencia de dolor lo que define una vida bien vivida, sino la valentía de avanzar a pesar de él, de construir orden a partir del caos, de erigir un templo de significado en medio de la entropía.
Así que, cuando decimos que la felicidad es pasajera y nuestro objetivo es perseguir un propósito, no estamos simplemente lanzando una frase al éter; estamos articulando una verdad que ha sido destilada a través de milenios de lucha humana, desde los mitos de Gilgamesh hasta las reflexiones de los estoicos, desde las catedrales góticas hasta las bibliotecas de la Ilustración. Es una invitación a reorientar tu brújula interna, a dejar de perseguir el espejismo de la felicidad y, en cambio, abrazar la carga gloriosa del propósito, porque en esa carga, en esa responsabilidad autoimpuesta, encuentras no solo significado, sino la posibilidad de trascendencia. Y eso, amigo mío, es la aventura más noble que un ser humano puede emprender.
-
 @ 7d33ba57:1b82db35
2025-03-26 09:22:57
@ 7d33ba57:1b82db35
2025-03-26 09:22:57Córdoba is a treasure trove of Moorish architecture, Roman heritage, and Andalusian charm. Once the capital of the Umayyad Caliphate, it’s home to stunning patios, atmospheric streets, and UNESCO-listed landmarks.
🏛️ Top Things to See & Do in Córdoba
1️⃣ La Mezquita-Catedral 🕌⛪
- Córdoba’s most iconic landmark, a UNESCO World Heritage Site.
- A breathtaking blend of Islamic arches and a Christian cathedral.
- Don’t miss the orange tree courtyard and bell tower views.
2️⃣ Alcázar de los Reyes Cristianos 🏰
- A medieval fortress with stunning gardens and Mudejar courtyards.
- Walk through Roman mosaics, ancient baths, and watchtowers.
3️⃣ Puente Romano & Calahorra Tower 🌉
- A historic Roman bridge over the Guadalquivir River.
- Great for sunset views with the Mezquita in the background.
- Visit the Calahorra Tower Museum for a look at Córdoba’s Islamic past.
4️⃣ Judería (Jewish Quarter) & Calleja de las Flores 🌺
- Wander through narrow, whitewashed streets lined with flowers.
- Visit the Córdoba Synagogue, one of Spain’s last remaining medieval synagogues.
- Stop by Calleja de las Flores, one of the most photogenic streets in Spain.
5️⃣ Palacio de Viana 🏡
- A 16th-century palace with 12 stunning courtyards filled with flowers.
- A must-visit during Córdoba’s Patio Festival (May).
6️⃣ Medina Azahara 🏛️
- The ruins of a 10th-century Moorish palace-city, 8 km from Córdoba.
- One of the greatest archaeological sites from Al-Andalus.
7️⃣ Plaza de la Corredera & Local Tapas 🍷
- A lively square with colorful buildings and traditional bars.
- Try local specialties like salmorejo (cold tomato soup) and flamenquín (breaded ham & cheese roll).
🍽️ What to Eat in Córdoba
- Salmorejo – A thick cold tomato soup, topped with ham and egg 🍅
- Flamenquín – A deep-fried pork roll stuffed with ham & cheese 🥩🧀
- Rabo de toro – Slow-cooked oxtail stew, a classic dish 🥘
- Berenjenas con miel – Fried eggplant drizzled with honey 🍆🍯
- Montilla-Moriles wine – A local sherry-like wine 🍷
🚗 How to Get to Córdoba
🚆 By Train: High-speed AVE trains from Madrid (1 hr 45 min), Seville (45 min), Málaga (1 hr)
🚘 By Car: 1.5 hrs from Seville, 2 hrs from Granada, 1 hr 40 min from Málaga
🚌 By Bus: Regular connections from major Andalusian cities
✈️ By Air: Closest airports are Seville (SVQ) or Málaga (AGP)💡 Tips for Visiting Córdoba
✅ Best time to visit? Spring (April–May) for mild weather & flower-filled patios 🌸
✅ Visit early morning or late afternoon to avoid the midday heat ☀️
✅ Book Mezquita tickets in advance to skip long queues 🎟️
✅ Try the local patios – Many houses open their courtyards for visitors 🏡 -
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 7d33ba57:1b82db35
2025-03-20 09:08:46
@ 7d33ba57:1b82db35
2025-03-20 09:08:46Puerto de las Nieves
Puerto de las Nieves is a picturesque seaside village on Gran Canaria’s northwestern coast, near Agaete. Known for its whitewashed houses, fresh seafood, and stunning coastal views, it’s the perfect place for arelaxing day by the ocean.
🌊 Top Things to Do in Puerto de las Nieves
1️⃣ Relax at Playa de las Nieves
A peaceful pebble beach with crystal-clear waters, perfect for swimming and sunbathing.
2️⃣ See the Dedo de Dios (God’s Finger) Rock Formation
This famous natural rock structure was partially destroyed by a storm in 2005, but the area remains a scenic spot.
3️⃣ Visit the Agaete Natural Pools (Las Salinas de Agaete)
Just a short walk away, these volcanic rock pools offer a natural and sheltered swimming experience.
4️⃣ Walk Along the Promenade
Enjoy a scenic stroll along the coastal promenade, lined with cafés, seafood restaurants, and local shops.
5️⃣ Take a Ferry to Tenerife
Puerto de las Nieves is the departure point for ferries to Santa Cruz de Tenerife, making it a great connection between the Canary Islands.
🍽️ What to Eat in Puerto de las Nieves
- Fresh seafood – Try the local grilled fish (pescado a la espalda) 🐟
- Papas arrugadas with mojo – A Canarian classic 🥔
- Pulpo a la gallega – Delicious Galician-style octopus 🐙
- Local wines – Agaete Valley is known for its unique volcanic wines 🍷
🚗 How to Get to Puerto de las Nieves
🚗 By Car: ~40 minutes from Las Palmas
🚌 By Bus: Direct routes from Las Palmas (Lines 103 & 105)💡 Tips for Visiting Puerto de las Nieves
✅ Best time to visit? Year-round, but sunsets here are especially magical 🌅
✅ Bring water shoes! The beach is pebbly, so they make swimming easier 👟
✅ Try a boat trip – Great for coastal views and dolphin watching 🚤 -
 @ 8f69ac99:4f92f5fd
2025-04-23 14:39:01
@ 8f69ac99:4f92f5fd
2025-04-23 14:39:01Dizem-nos que a inflação é necessária. Mas e se for, afinal, a raiz da disfunção económica que enfrentamos?
A crença mainstream é clara: para estimular o crescimento, os governos devem poder desvalorizar a sua moeda — essencialmente, criar dinheiro do nada. Supostamente, isso incentiva o investimento, aumenta o consumo e permite responder a crises económicas. Esta narrativa foi repetida tantas vezes que se tornou quase um axioma — raramente questionado.
No centro desta visão está a lógica fiat-keynesiana: uma economia estável exige um banco central disposto a manipular o valor do dinheiro para alcançar certos objectivos políticos. Esta abordagem, inspirada por John Maynard Keynes, defende a intervenção estatal como forma de estabilizar a economia durante recessões. Na teoria, os investidores e consumidores beneficiam de taxas de juro artificiais e de maior poder de compra — um suposto ganho para todos.
Mas há outra perspectiva: a visão do dinheiro sólido (sound money, em inglês). Enraizada na escola austríaca e nos princípios da liberdade individual, esta defende que a manipulação monetária não é apenas desnecessária — é prejudicial. Uma moeda estável, não sujeita à depreciação arbitrária, é essencial para promover trocas voluntárias, empreendedorismo e crescimento económico genuíno.
Está na hora de desafiar esta sabedoria convencional. Ao longo dos próximos capítulos, vamos analisar os pressupostos errados que sustentam a lógica fiat-keynesiana e explorar os benefícios de um sistema baseado em dinheiro sólido — como Bitcoin. Vamos mostrar por que desvalorizar a moeda é moralmente questionável e economicamente prejudicial, e propor alternativas mais éticas e eficazes.
Este artigo (que surge em resposta ao "guru" Miguel Milhões) pretende iluminar as diferenças entre estas duas visões opostas e apresentar uma abordagem mais sólida e justa para a política económica — centrada na liberdade pessoal, na responsabilidade individual e na preservação de instituições financeiras saudáveis.
O Argumento Fiat: Por que Dizem que é Preciso Desvalorizar a Moeda
Este argumento parte geralmente de uma visão económica keynesiana e/ou estatista e assenta em duas ideias principais: o incentivo ao investimento e a necessidade de resposta a emergências.
Incentivo ao Investimento
Segundo os defensores do sistema fiat, se uma moeda como o ouro ou bitcoin valorizar ao longo do tempo, as pessoas tenderão a "acumular" essa riqueza em vez de investir em negócios produtivos. O receio é que, se guardar dinheiro se torna mais rentável do que investir, a economia entre em estagnação.
Esta ideia parte de uma visão simplista do comportamento humano. Na realidade, as pessoas tomam decisões financeiras com base em múltiplos factores. Embora seja verdade que activos valorizáveis são atractivos, isso não significa que os investimentos desapareçam. Pelo contrário, o surgimento de activos como bitcoin cria novas oportunidades de inovação e investimento.
Historicamente, houve crescimento económico em períodos de moeda sólida — como no padrão-ouro. Uma moeda estável e previsível pode incentivar o investimento, ao dar confiança nos retornos futuros.
Resposta a Emergências
A segunda tese é que os governos precisam de imprimir dinheiro rapidamente em tempos de crise — pandemias, guerras ou recessões. Esta capacidade de intervenção é vista como essencial para "salvar" a economia.
De acordo com economistas keynesianos, uma injecção rápida de liquidez pode estabilizar a economia e evitar colapsos sociais. No entanto, este argumento ignora vários pontos fundamentais:
- A política monetária não substitui a responsabilidade fiscal: A capacidade de imprimir dinheiro não torna automaticamente eficaz o estímulo económico.
- A inflação é uma consequência provável: A impressão de dinheiro pode levar a pressões inflacionistas, reduzindo o poder de compra dos consumidores e minando o próprio estímulo pretendido. Estamos agora a colher os "frutos" da impressão de dinheiro durante a pandemia.
- O timing é crítico: Intervenções mal cronometradas podem agravar a situação.
Veremos em seguida porque estes argumentos não se sustentam.
Rebatendo os Argumentos
O Investimento Não Morre num Sistema de Dinheiro Sólido
O argumento de que o dinheiro sólido mata o investimento falha em compreender a ligação entre poupança e capital. Num sistema sólido, a poupança não é apenas acumulação — é capital disponível para financiar novos projectos. Isso conduz a um crescimento mais sustentável, baseado na qualidade e não na especulação.
Em contraste, o sistema fiat, com crédito barato, gera bolhas e colapsos — como vimos em 2008 ou na bolha dot-com. Estes exemplos ilustram os perigos da especulação facilitada por políticas monetárias artificiais.
Já num sistema de dinheiro sólido, como o que cresce em torno de Bitcoin, vemos investimentos em mineração, startups, educação e arte. Os investidores continuam activos — mas fazem escolhas mais responsáveis e de longo prazo.
Imprimir Dinheiro Não Resolve Crises
A ideia de que imprimir dinheiro é essencial em tempos de crise parte de uma ilusão perigosa. A inflação que se segue reduz o poder de compra e afecta especialmente os mais pobres — é uma forma oculta de imposto.
Além disso, soluções descentralizadas — como os mercados, redes comunitárias e poupança — são frequentemente mais eficazes. A resposta à COVID-19 ilustra isso: grandes empresas foram salvas, mas pequenos negócios e famílias ficaram para trás. Os últimos receberam um amuse-bouche, enquanto os primeiros comeram o prato principal, sopa, sobremesa e ainda levaram os restos.
A verdade é que imprimir dinheiro não cria valor — apenas o redistribui injustamente. A verdadeira resiliência nasce de comunidades organizadas e de uma base económica saudável, não de decretos políticos.
Dois Mundos: Fiat vs. Dinheiro Sólido
| Dimensão | Sistema Fiat-Keynesiano | Sistema de Dinheiro Sólido | |----------|--------------------------|-----------------------------| | Investimento | Estimulado por crédito fácil, alimentando bolhas | Baseado em poupança real e oportunidades sustentáveis | | Resposta a crises | Centralizada, via impressão de moeda | Descentralizada, baseada em poupança e solidariedade | | Preferência temporal | Alta: foco no consumo imediato | Baixa: foco na poupança e no futuro | | Distribuição de riqueza | Favorece os próximos ao poder (Efeito Cantillon) | Benefícios da deflação são distribuídos de forma mais justa | | Fundamento moral | Coercivo e redistributivo | Voluntário e baseado na liberdade individual |
Estes contrastes mostram que a escolha entre os dois sistemas vai muito além da economia — é também uma questão ética.
Consequências de Cada Sistema
O Mundo Fiat
Num mundo dominado pelo sistema fiat, os ciclos de euforia e colapso são a norma. A desigualdade aumenta, com os mais próximos ao poder a lucrar com a inflação e a impressão de dinheiro. A poupança perde valor, e a autonomia financeira das pessoas diminui.
À medida que o Estado ganha mais controlo sobre a economia, os cidadãos perdem capacidade de escolha e dependem cada vez mais de apoios governamentais. Esta dependência destrói o espírito de iniciativa e promove o conformismo.
O resultado? Estagnação, conflitos sociais e perda de liberdade.
O Mundo com Dinheiro Sólido
Com uma moeda sólida, o crescimento é baseado em valor real. As pessoas poupam mais, investem melhor e tornam-se mais independentes financeiramente. As comunidades tornam-se mais resilientes, e a cooperação substitui a dependência estatal.
Benefícios chave:
- Poupança real: A moeda não perde valor, e a riqueza pode ser construída com estabilidade.
- Resiliência descentralizada: Apoio mútuo entre indivíduos e comunidades em tempos difíceis.
- Liberdade económica: Menor interferência política e mais espaço para inovação e iniciativa pessoal.
Conclusão
A desvalorização da moeda não é uma solução — é um problema. Os sistemas fiat estão desenhados para transferir riqueza e poder de forma opaca, perpetuando injustiças e instabilidade.
Por outro lado, o dinheiro sólido — como Bitcoin — oferece uma alternativa credível e ética. Promove liberdade, responsabilidade e transparência. Impede abusos de poder e expõe os verdadeiros custos da má governação.
Não precisamos de mais inflação — precisamos de mais integridade.
Está na hora de recuperarmos o controlo sobre a nossa vida financeira. De rejeitarmos os sistemas que nos empobrecem lentamente e de construirmos um futuro em que o dinheiro serve as pessoas — e não os interesses políticos.
O futuro do dinheiro pode e deve ser diferente. Juntos, podemos criar uma economia mais justa, livre e resiliente — onde a prosperidade é partilhada e a dignidade individual respeitada.
Photo by rc.xyz NFT gallery on Unsplash
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 7d33ba57:1b82db35
2025-04-23 13:51:02
@ 7d33ba57:1b82db35
2025-04-23 13:51:02You don’t need a fancy camera to dive into the miniature universe—your phone + a few tricks are all it takes! Macro photography with a smartphone can reveal incredible textures, patterns, insects, flowers, and everyday details most people miss. Here’s how to get the best out of it:
🔧 1. Use a Macro Lens Attachment (If Possible)
- Clip-on macro lenses are affordable and boost your phone's close-up power
- Look for 10x–20x lenses for best results
- Make sure it’s aligned perfectly with your phone’s lens
✨ 2. Get Really Close (but Not Too Close)
- Phones typically focus best at 2–5 cm in macro mode
- Slowly move your phone toward the subject until it comes into sharp focus
- If it blurs, back off slightly—tiny shifts matter a lot!
📸 3. Tap to Focus & Adjust Exposure
- Tap on your subject to lock focus
- Adjust brightness manually if your phone allows—slightly underexposed often looks better in macro
🌤️ 4. Use Natural Light or a Diffused Flash
- Soft natural light (like early morning or cloudy day) gives the best macro results
- Use white paper to bounce light or your hand to gently shade direct sun
- If using flash, try diffusing it with a tissue or tape for a softer effect
🧍♂️ 5. Steady Yourself
- Use both hands, brace against something, or use a tripod for stability
- Try your phone’s timer or remote shutter (via headphones or Bluetooth) to avoid shake
🧽 6. Clean Your Lens
- Macro shows everything—including dust and fingerprints
- Always wipe your lens gently before shooting
🌀 7. Explore Textures & Patterns
- Get creative with leaves, feathers, skin, fabrics, ice, fruit, rust, insects—anything with rich texture
- Look for symmetry, contrast, or repetition in tiny subjects
🧑🎨 8. Edit Smart
- Use apps like Snapseed, Lightroom Mobile, or your built-in editor
- Adjust sharpness, contrast, warmth, and cropping carefully
- Avoid over-sharpening—it can make things look unnatural
🎯 Bonus Tip: Try Manual Camera Apps
- Apps like Halide (iOS), ProCamera, or Camera+ 2 let you control ISO, shutter speed, and focus manually
- Great for getting extra precision
Macro phoneography is about patience and curiosity. Once you start noticing the tiny wonders around you, you’ll see the world a little differently.
-
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 7d33ba57:1b82db35
2025-04-23 12:54:11
@ 7d33ba57:1b82db35
2025-04-23 12:54:11Texel, the largest of the Dutch Wadden Islands, is a peaceful, windswept escape in the North Sea, known for its wide sandy beaches, unique landscapes, and laid-back island vibe. Just a short ferry ride from the mainland, Texel offers a perfect mix of nature, wildlife, local culture, and coastal relaxation.
🏖️ Top Things to Do on Texel
🚲 Cycle Across the Island
- With over 140 km of bike paths, cycling is the best way to explore
- Ride through dunes, forests, sheep pastures, and cute villages like De Koog and Oudeschild
🌾 Explore Dunes & Beaches
- Visit Dunes of Texel National Park—a coastal dream with rolling dunes, hiking trails, and wildflowers
- Relax on vast, quiet beaches perfect for swimming, kite flying, or just soaking up sea air
🐑 Texel Sheep & Local Farms
- Meet the island’s famous Texel sheep—known for their wool and adorable lambs
- Stop by local farms for cheese tastings, ice cream, or a farm tour
🐦 Spot Wildlife at De Slufter
- A unique salt marsh where tidal water flows in naturally
- Great for birdwatching—home to spoonbills, geese, and waders
- Beautiful walking trails with views over the dunes and out to sea
🐋 Ecomare Marine Center
- Learn about Texel’s marine life, see seals and seabirds, and explore interactive exhibits
- A hit for families and nature lovers alike
🍺 Taste Texel
- Try local specialties like Texels beer, lamb dishes, cranberry treats, and fresh seafood
- Cozy beach pavilions and harbor-side restaurants offer stunning sunset views
🚢 Getting to Texel
- Take the ferry from Den Helder (crossing time: ~20 minutes)
- Cars, bikes, and pedestrians all welcome
- Once on the island, biking or local buses make getting around easy
🏡 Where to Stay
- Choose from beachside hotels, charming B&Bs, cozy cabins, or campsites
- Many places offer serene views of dunes, fields, or sea
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 6ad3e2a3:c90b7740
2025-04-23 12:31:54
@ 6ad3e2a3:c90b7740
2025-04-23 12:31:54There’s an annoying trend on Twitter wherein the algorithm feeds you a lot of threads like “five keys to gaining wealth” or “10 mistakes to avoid in relationships” that list a bunch of hacks for some ostensibly desirable state of affairs which for you is presumably lacking. It’s not that the hacks are wrong per se, more that the medium is the message. Reading threads about hacks on social media is almost surely not the path toward whatever is promised by them.
. . .
I’ve tried a lot of health supplements over the years. These days creatine is trendy, and of course Vitamin D (which I still take.) I don’t know if this is helping me, though it surely helps me pass my blood tests with robust levels. The more I learn about health and nutrition, the less I’m sure of anything beyond a few basics. Yes, replacing processed food with real food, moving your body and getting some sun are almost certainly good, but it’s harder to know how particular interventions affect me.
Maybe some of them work in the short term then lose their effect, Maybe some work better for particular phenotypes, but not for mine. Maybe my timing in the day is off, or I’m not combining them correctly for my lifestyle and circumstances. The body is a complex system, and complex systems are characterized by having unpredictable outputs given changes to initial conditions (inputs).
. . .
I started getting into Padel recently — a mini-tennis-like game where you can hit the ball off the back walls. I’d much rather chase a ball around for exercise than run or work out, and there’s a social aspect I enjoy. (By “social aspect”, I don’t really mean getting to know the people with whom I’m playing, but just the incidental interactions you get during the game, joking about it, for example, when you nearly impale someone at the net with a hard forehand.)
A few months ago, I was playing with some friends, and I was a little off. It’s embarrassing to play poorly at a sport, especially when (as is always the case in Padel) you have a doubles partner you’re letting down. Normally I’d be excoriating myself for my poor play, coaching myself to bend my knees more, not go for winners so much. But that day, I was tired — for some reason I hadn’t slept well — and I didn’t have the energy for much internal monologue. I just mishit a few balls, felt stupid about it and kept playing.
After a few games, my fortunes reversed. I was hitting the ball cleanly, smashing winners, rarely making errors. My partner and I started winning games and then sets. I was enjoying myself. In the midst of it I remember hitting an easy ball into the net and reflexively wanting to self-coach again. I wondered, “What tips did I give to right the ship when I had been playing poorly at the outset?” I racked my brain as I waited for the serve and realized, to my surprise, there had been none. The turnaround in my play was not due to self-coaching but its absence. I had started playing better because my mind had finally shut the fuck up for once.
Now when I’m not playing well, I resist, to the extent I’m capable, the urge to meddle. I intend to be more mind-less. Not so much telling the interior coach to shut up but not buying into the premise there is a problem to be solved at all. The coach isn’t just ignored, he’s fired. And he’s not just fired, his role was obsoleted.
You blew the point, you’re embarrassed about it and there’s nothing that needs to be done about it. Or that you started coaching yourself like a fool and made things worse. No matter how much you are doing the wrong thing nothing needs to be done about any of it whatsoever. There is always another ball coming across the net that needs to be struck until the game is over.
. . .
Most of the hacks, habits and heuristics we pick up to manage our lives only serve as yet more inputs in unfathomably complex systems whose outputs rarely track as we’d like. There are some basic ones that are now obvious to everyone like not injecting yourself with heroin (or mRNA boosters), but for the most part we just create more baggage for ourselves which justifies ever more hacks. It’s like taking medication for one problem that causes side effects, and then you need another medicine for that side effect, rinse and repeat, ad infinitum.
But this process can be reverse-engineered too. For every heuristic you drop, the problem it was put into place to solve re-emerges and has a chance to be observed. Observing won’t solve it, it’ll just bring it into the fold, give the complex system of which it is a part a chance to achieve an equilibrium with respect to it on its own.
You might still be embarrassed when you mishit the ball, but embarrassment is not a problem. And if embarrassment is not a problem, then mishitting a ball isn’t that bad. And if mishitting a ball isn’t that bad, then maybe you’re not worrying about what happens if you botch the next shot, instead fixing your attention on the ball. And so you disappear a little bit into the game, and it’s more fun as a result.
I honestly wish there were a hack for this — being more mindless — but I don’t know of any. And in any event, hack Substacks won’t get you any farther than hack Twitter threads.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 7d33ba57:1b82db35
2025-04-23 11:40:24
@ 7d33ba57:1b82db35
2025-04-23 11:40:24Perched on the northern coast of Poland, Gdańsk is a stunning port city with a unique blend of Hanseatic charm, maritime heritage, and resilience through centuries of dramatic history. With its colorful façades, cobbled streets, and strong cultural identity, Gdańsk is one of Poland’s most compelling cities—perfect for history buffs, architecture lovers, and coastal wanderers.
🏛️ What to See & Do in Gdańsk
🌈 Stroll Down Długi Targ (Long Market)
- The heart of Gdańsk’s Old Town, lined with beautifully restored colorful merchant houses
- Admire the Neptune Fountain, Artus Court, and the grand Main Town Hall
⚓ The Crane (Żuraw) & Motława River
- Gdańsk’s medieval port crane is an iconic symbol of its maritime past
- Walk along the Motława River promenade, with boats, cafés, and views of historic granaries
⛪ St. Mary’s Church (Bazylika Mariacka)
- One of the largest brick churches in the world
- Climb the tower for panoramic views of the city and harbor
🕊️ Learn Gdańsk’s Layers of History
🏰 Westerplatte
- The site where World War II began in 1939
- A powerful memorial and museum amid coastal nature
🛠️ European Solidarity Centre
- A striking modern museum dedicated to the Solidarity movement that helped end communism in Poland
- Insightful, moving, and highly interactive
🏖️ Relax by the Baltic Sea
- Head to Brzeźno Beach or nearby Sopot for golden sands, seaside promenades, and beach cafés
- In summer, the Baltic vibes are strong—swimming, sunsets, and pier strolls

🍽️ Tastes of Gdańsk
- Try pierogi, fresh Baltic fish, golden smoked cheese, and żurek soup
- Visit a local milk bar or enjoy a craft beer at one of Gdańsk’s buzzing breweries
- Don’t miss the amber jewelry shops—Gdańsk is known as the Amber Capital of the World
🚆 Getting There
- Easily reached by train or plane from Warsaw and other major European cities
- Compact city center—walkable and scenic
-
 @ 7d33ba57:1b82db35
2025-04-23 10:28:49
@ 7d33ba57:1b82db35
2025-04-23 10:28:49Lake Bled is straight out of a storybook—an emerald alpine lake with a tiny island crowned by a church, surrounded by forested hills and overlooked by a clifftop castle. Just an hour from Ljubljana, this Slovenian gem is perfect for romantic getaways, outdoor adventures, or a peaceful escape into nature.
🌊 Top Things to Do in Bled
🛶 Bled Island & Church of the Assumption
- Take a traditional pletna boat or rent a rowboat to reach the only natural island in Slovenia
- Ring the church bell and make a wish—it’s a local tradition!
- Enjoy serene lake views from the island’s stone steps
🏰 Bled Castle (Blejski Grad)
- Perched on a cliff 130 meters above the lake
- Explore the medieval halls, museum, and wine cellar
- The terrace views? Absolutely unforgettable—especially at sunset
🚶♂️ Walk or Cycle the Lakeside Path
- A 6 km flat path circles the lake—perfect for a leisurely stroll or bike ride
- Stop for lakeside cafés, photo ops, or a quick swim in summer
🌄 Outdoor Adventures Beyond the Lake
- Hike to Mala Osojnica Viewpoint for the most iconic panoramic view of Lake Bled
- Go paddleboarding, kayaking, or swimming in warmer months
- Nearby Vintgar Gorge offers a stunning wooden path through a narrow, turquoise canyon
🍰 Try the Famous Bled Cream Cake (Kremšnita)
- A must-try dessert with layers of vanilla custard, cream, and crispy pastry
- Best enjoyed with a coffee on a terrace overlooking the lake

🏡 Where to Stay
- Lakeside hotels, cozy guesthouses, or charming Alpine-style B&Bs
- Some even offer views of the lake, castle, or Triglav National Park
🚗 Getting There
- Around 1 hour from Ljubljana by car, bus, or train
- Easy to combine with stops like Lake Bohinj or Triglav National Park
-
 @ fbf0e434:e1be6a39
2025-04-23 08:42:22
@ fbf0e434:e1be6a39
2025-04-23 08:42:22Hackathon 概要
Naija HackAtom 圆满落幕。此次活动共有 160 名开发者注册参与,成功展示 51 个通过审核的项目。该黑客马拉松旨在推动尼日利亚 Web3 社区内 Interchain、Cosmos Hub 和 Atom 经济区(AEZ)的发展,主要目标是培养本土人才、提供资源支持,并开发基于 $ATOM 代币的区块链应用。
活动聚焦 Interchain 安全性、Atom 经济区、CosmWasm 以及 ATOM 的具体发展等关键领域。其中,跨链汇款平台、面向非洲农民的去中心化市场等项目尤为亮眼,充分展现了 Cosmos 技术的创新应用潜力。
本次黑客马拉松设立了 10000 美元的奖金池,用于奖励在 UI/UX 设计、社区参与度及 Atom 创新应用方案等方面表现突出的项目。在系列研讨会与公开教程的辅助下,参赛者提交的项目从技术可行性、创新性、社会影响力和用户体验等维度进行评审。活动凭借广泛的参与度与丰富的创新成果,有力推动了尼日利亚乃至整个非洲区块链生态的发展。
Hackathon 获奖者
Naija HackAtom 作为尼日利亚首个以 Cosmos 和 ATOM 为核心的黑客马拉松,吸引了超 500 人参与,其中开发者达 160 名。在 ATOMAccelerator 的支持下,活动共收到 57 个项目提交,最终 18 个项目脱颖而出,入围决赛。
主奖项获奖者
- Beep: 一个用于Naira代币化的平台,促进了与tAtom无缝交易和交换。
- Padi [Crypto Go Fund Me]: 一个基于区块链的平台,用于进行代币驱动的筹款活动。
- ATwork: 一个去中心化的自由职业平台,通过Cosmos区块链增强自由职业者与客户之间的合作。
独特解决方案/产品奖项获奖者
- LendPro: 一个借贷协议,通过区块链促进合作金融治理。
- Tradi-App: 一个在Secret Network上的隐私AI交易分析平台,提供市场见解。
- Delegated Staking Agent(DSA): 提供Cosmos生态系统中的质押和治理投票,具有AI增强的安全性能。
- Neutron NFT Launch: 通过整合AI、区块链和NFT技术简化NFT的创建和交易。
Secret Network 赏金获奖者
- Prompt Hub: 一个专注隐私、AI生成提示的市场,带有集成功能。
- Delegated Staking Agent(DSA)
- Secret AI Writer: 一个AI写作平台,提供安全的区块链存储和隐私中心的内容生成。
- Tradi-App
ChihuahuaChain 赏金获奖者
- Neutron NFT Launch
- woof-dot-fun: 一个复制Pump.Fun的项目,具有代币和债券曲线功能。
- Vault Quest: 一个无损奖品储蓄协议,利用DeFi策略进行基于收益的奖品分配。
Akash 赏金获奖者
- Jarvis AI: 一个语音激活的助手,旨在高效的云资源管理。
有关Naija HackAtom期间提交的所有项目的完整列表,请访问这里。
关于组织者
Cosmos Hub Africa
Cosmos Hub Africa专注于在非洲推广区块链技术和Cosmos生态系统。该组织在去中心化网络开发和区块链行业内的协作方面发挥着重要作用。其贡献包括提高平台之间可扩展性和互操作性的项目。目前,Cosmos Hub Africa致力于推进该地区的区块链教育和基础设施,旨在促进与传统经济和金融系统的创新和整合。
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 21335073:a244b1ad
2025-03-18 14:23:35
@ 21335073:a244b1ad
2025-03-18 14:23:35Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ fd06f542:8d6d54cd
2025-04-23 07:51:30
@ fd06f542:8d6d54cd
2025-04-23 07:51:30- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
- 第九章、NIP-09: Event Deletion Request
- 第十章、NIP-10: Text Notes and Threads
- 第十一章、NIP-11: Relay Information Document
- 第十二章、NIP-13: Proof of Work
- 第十三章、NIP-14: Subject tag in text events
- 第十四章、NIP-15: Nostr Marketplace (for resilient marketplaces)
- 第十五章、NIP-17: Private Direct Messages
- 第十六章、NIP-18: Reposts
- 第十七章、NIP-19: bech32-encoded entities
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ da0b9bc3:4e30a4a9
2025-04-23 07:50:49
@ da0b9bc3:4e30a4a9
2025-04-23 07:50:49Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/954269
-
 @ 2b24a1fa:17750f64
2025-04-23 06:53:15
@ 2b24a1fa:17750f64
2025-04-23 06:53:15„Immer wieder ist jetzt“ übertitelt unsere Sprecherin Sabrina Khalil ihren Text, den sie für die Friedensnoten geschrieben hat. Das gleichnamige Gedicht hat Jens Fischer Rodrian vertont.
Sprecher des Textes: Ulrich Allroggen
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ fd06f542:8d6d54cd
2025-04-23 06:39:15
@ fd06f542:8d6d54cd
2025-04-23 06:39:15有时候写点日志,可以 记录一点琐碎的事情。
! 也许这就是 这就是 这个blog存在的原因吧。
如何将docsify 变成一个渲染blog的 工具
我用了很多办法,但是关键点还是这个 方法。 无须配置 window.$docsify ={} ```js $: if (blogItem) {
compiledContent = window.__current_docsify_compiler__.compile(blogItem.content); }```
直接用内容的 功能转换。
但是渲染的时候要注意:
html <article class="markdown-section" id="main"> {@html compiledContent} </article>内容要加上这个外框,这个问题我调试了一天在知道...原来是少了他,导致缺少很多东西。
如何上传背景图片?
- 一定要点击 封面图区域的空白处, 让 编辑框失去焦点。
- 再 把鼠标放在 虚线封面图区域,就可以ctrl+v 粘贴截图了。
其他使用事项,我想起来再写吧。
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ 8d34bd24:414be32b
2025-04-23 03:52:15
@ 8d34bd24:414be32b
2025-04-23 03:52:15I started writing a series on the signs of the End Times and how they align with what we are seeing in the world today. There are some major concerns with predicting the end times, so I decided I should insert a short post on “Can we know when the end times are coming?” Like many principles in the Bible, it takes looking at seemingly contradictory verses to reach the truth.
This Generation
Before I get into “Can we know?” I want to address one point that some will bring up against a future Rapture, Tribulation, and Millennium.
Truly I say to you, this generation will not pass away until all these things take place. (Matthew 24:34) {emphasis mine}
What generation is Jesus talking about. Most Christians that don’t believe in a future Rapture, Tribulation, and Millennium will point to this verse to support their point of view. The important question is, “What is Jesus referring to with the words ‘this generation’?”
Is it referring to the people He was talking to at that time? If so, since that generation died long ago, then Jesus’s predictions must have been fulfilled almost 2 millennia ago. The problem with this interpretation is that nothing resembling these predictions happened during that initial generation. You have to really twist His words to try to support that they were fulfilled. Also, John wrote in Revelation about future fulfillment. By that time, John was the last of the apostles still alive and that whole generation was pretty much gone.
If “this generation” doesn’t refer to the people Jesus was speaking to personally in that moment, then to whom does it refer? The verses immediately preceding talk about the signs that will occur right before the end times. If you take “this generation” to mean the people who saw the signs Jesus predicted, then everything suddenly makes sense. It also parallel’s Paul’s statement of consolation to those who thought they had been left behind,**
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
Some believers thought things were happening in their lifetime, but Paul gave them comfort that no believer would miss the end times rapture.
No One Knows
Truly I say to you, this generation will not pass away until all these things take place. Heaven and earth will pass away, but My words will not pass away.
But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone. For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left. (Matthew 24:34-41) {emphasis mine}
This verse very explicitly says that no one, not even angels or Jesus, knows the exact day or hour of His coming.
So when they had come together, they were asking Him, saying, “Lord, is it at this time You are restoring the kingdom to Israel?” He said to them, “It is not for you to know times or epochs which the Father has fixed by His own authority; but you will receive power when the Holy Spirit has come upon you; and you shall be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:6-8)
In this verse Jesus again says that they cannot know the time of His return, but based on context, He is explaining that this generation needs to focus on sharing the Gospel with world and not primarily on the kingdom. Is this Jesus’s way of telling them that they would not be alive to see His return, but they would be responsible for “sharing the Gospel even to the remotest part of the earth?”
Therefore we do know that predicting the exact date of His return is a fool’s errand and should not be attempted, but does this mean we can’t know when it is fast approaching?
We Should Know
There is an opposing passage, though.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
In this passage, Jesus reprimands the Pharisees and Sadducees because, although they can rightly read the signs of the weather, they were unable to know and understand the prophecies of His first coming. Especially as the religious leaders, they should’ve been able to determine that Jesus’s coming was imminent and that He was fulfilling the prophetic Scriptures.
In Luke, when Jesus is discussing His second coming with His disciples, He tells this parable:
Then He told them a parable: “Behold the fig tree and all the trees; as soon as they put forth leaves, you see it and know for yourselves that summer is now near. So you also, when you see these things happening, recognize that the kingdom of God is near. (Luke 21:29-31) {emphasis mine}
Jesus would not have given this parable if there were not signs of His coming that we can recognize.
We are expected to know the Scriptures and to study them looking for the signs of His second coming. We can’t know the hour or the day, but we can know that the time is fast approaching. We shouldn’t set dates, but we should search anxiously for the signs of His coming. We shouldn’t be like the scoffers that question His literal fulfillment of His promises:
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:3-9) {emphasis mine}
One thing is certain, we are closer to Jesus’s second coming than we have ever been and must be ready as we see the day approaching.
May the God of heaven give you a desire and urgency to share the Gospel with all those around you and to grow your faith, knowledge, and relationship with Him, so you can finish the race well, with no regrets. May the knowledge that Jesus could be coming soon give you an eternal perspective on life, so you put more of your time into things of eternal consequence and don’t get overwhelmed with things of the world which are here today and then are gone.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
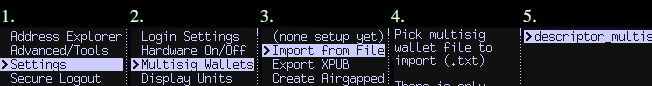
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
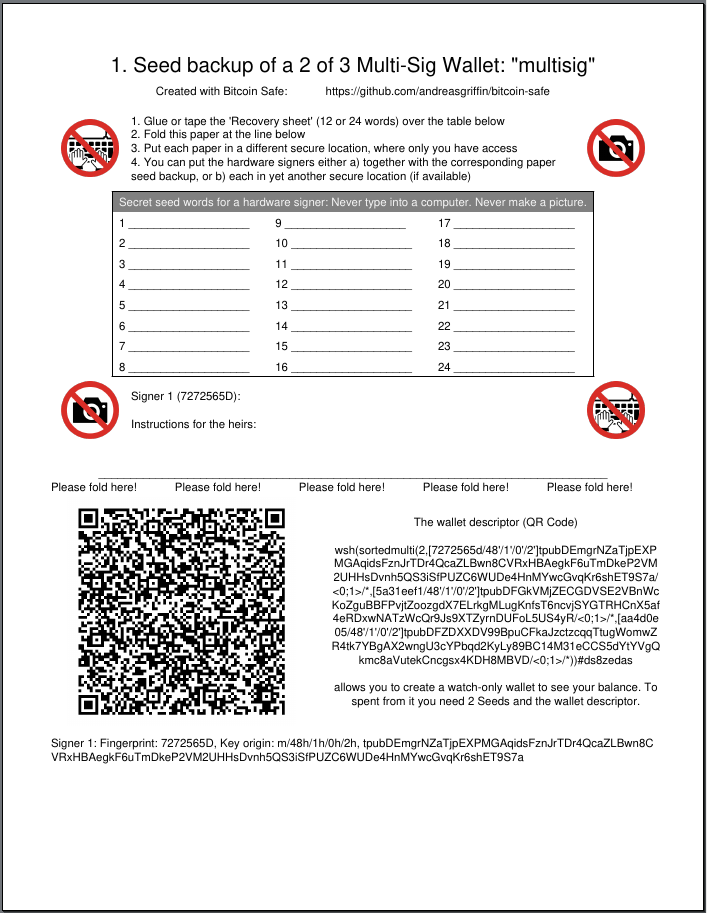
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
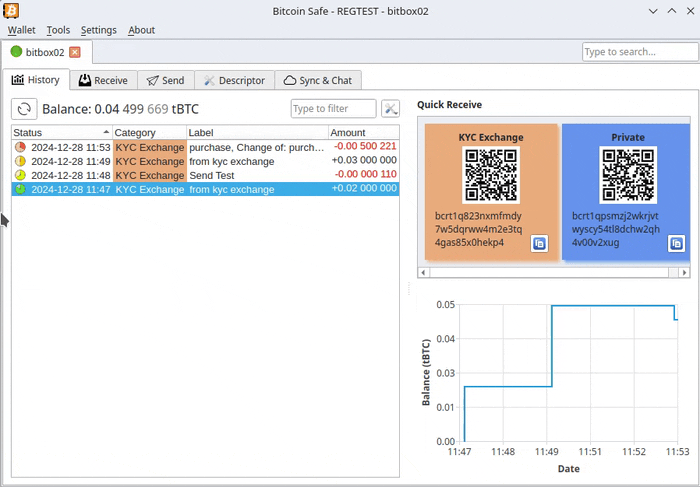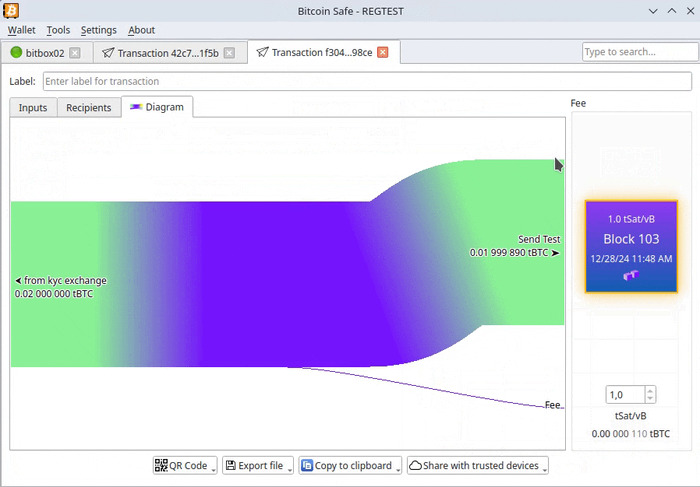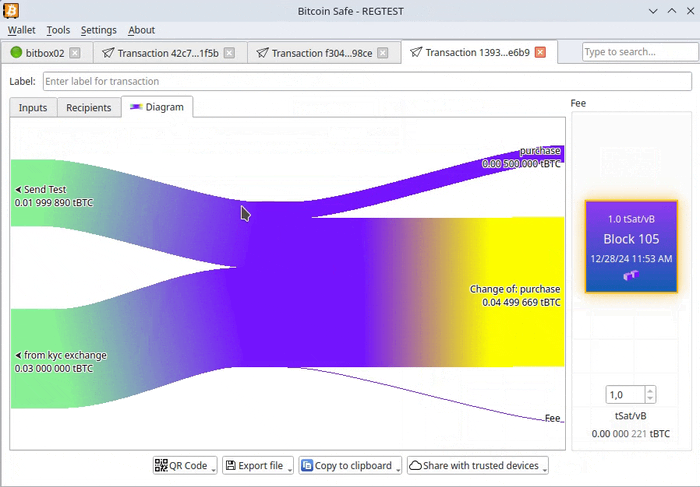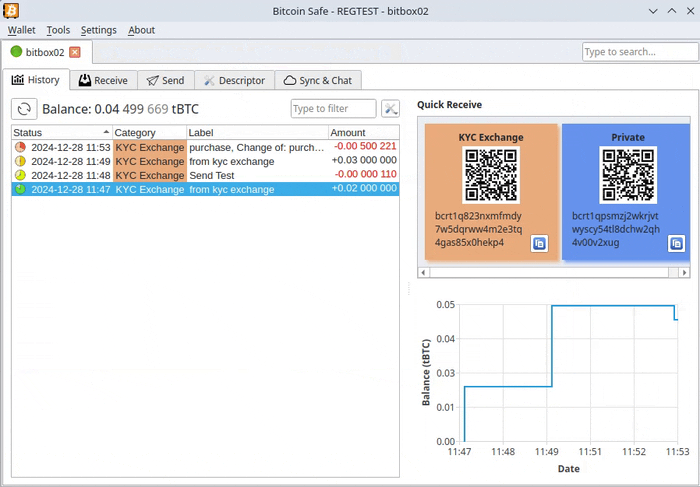
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
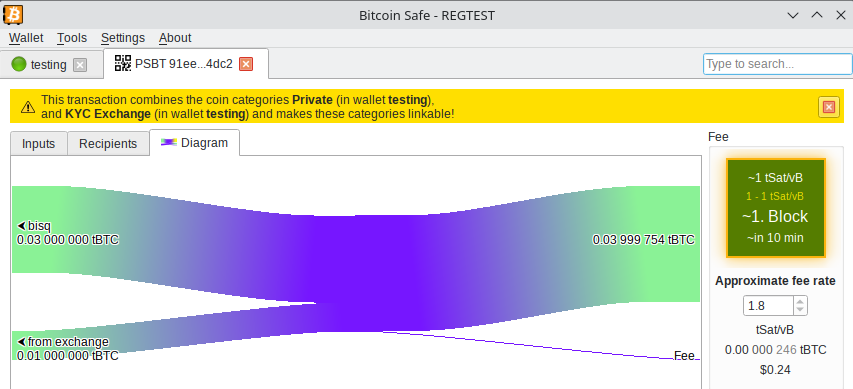
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
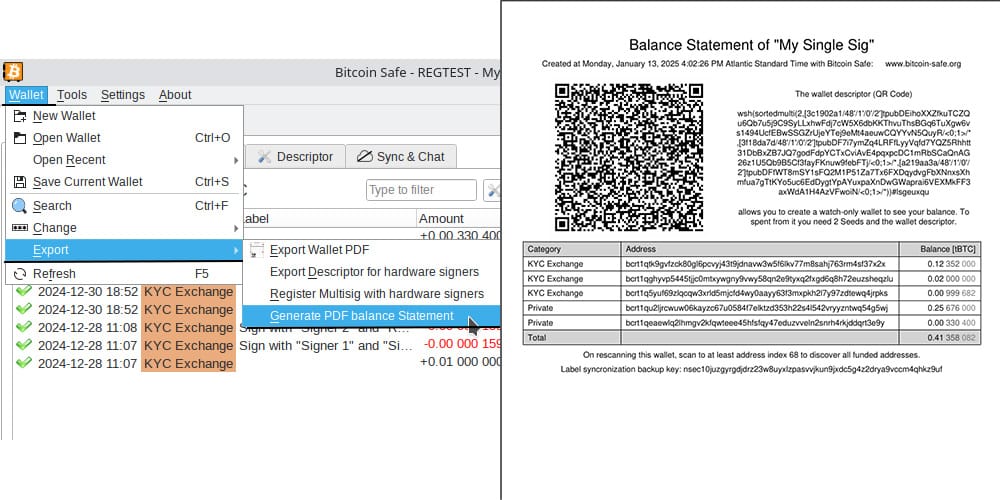
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
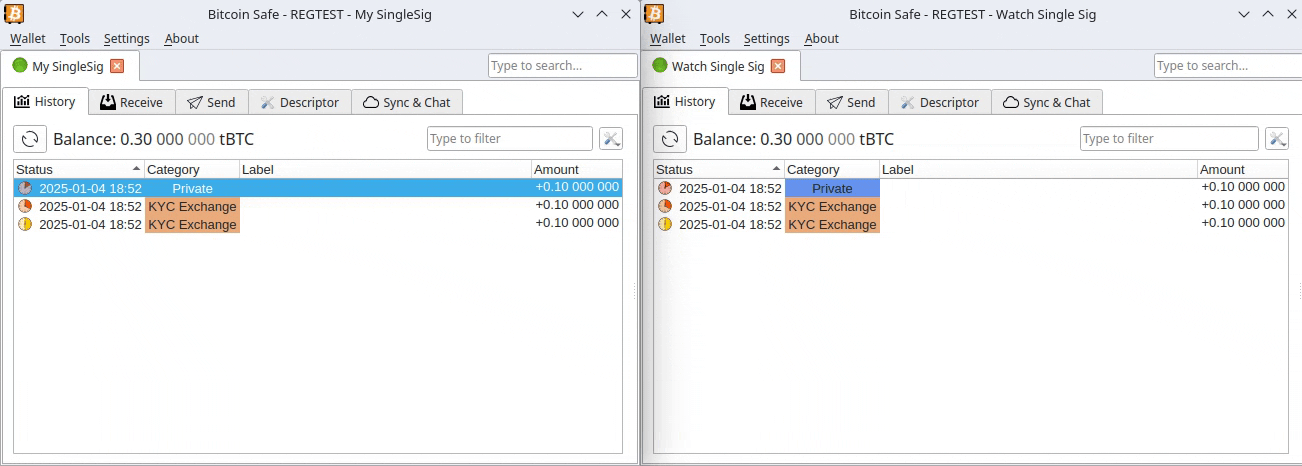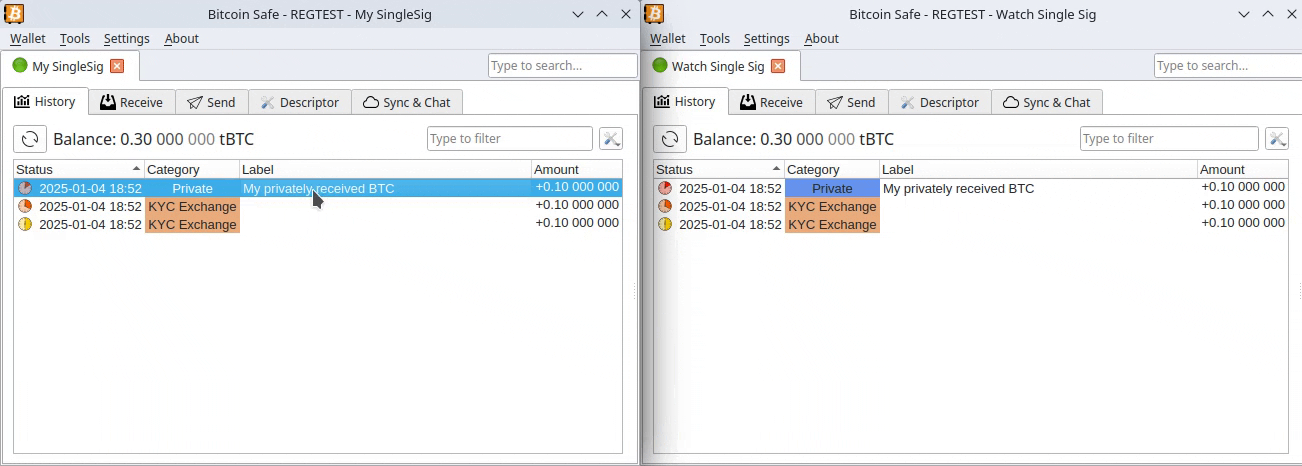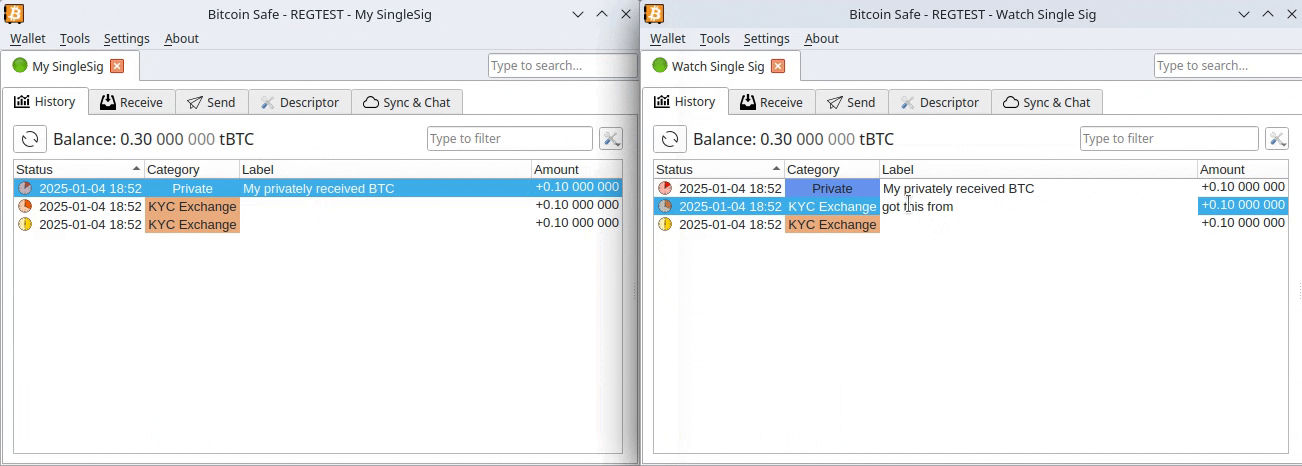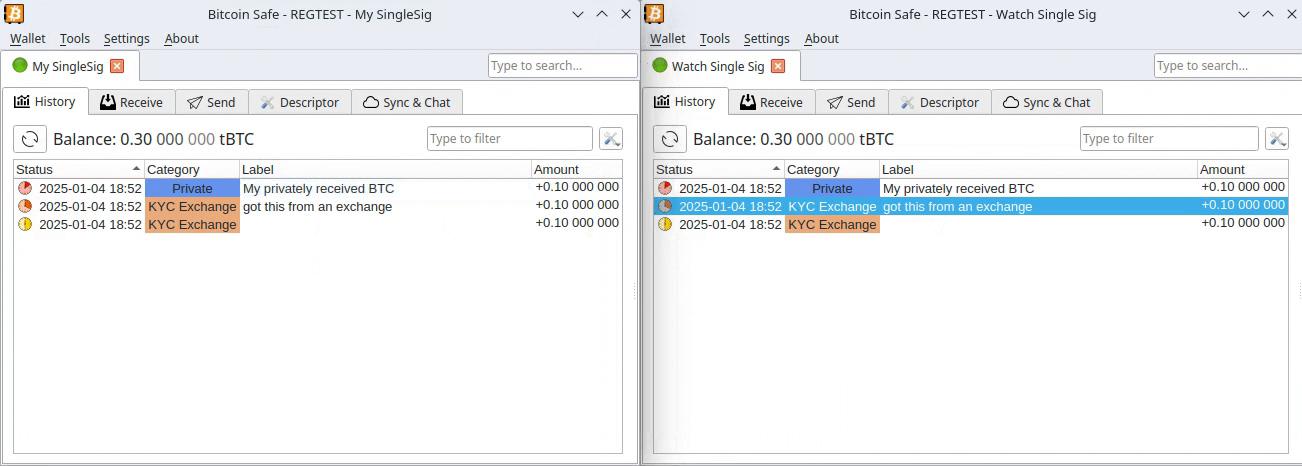
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 06639a38:655f8f71
2025-03-17 15:13:22
@ 06639a38:655f8f71
2025-03-17 15:13:22- My PR#100 for
sirn-se/websocket-phpgot merged and was released in version 3.2.3 - Closed issue #83, reviewed and merged PR#84 for integrating NIP-04 and NIP-44
- Closed issue #85 and merged PR#86 with Event object verification
1.6.0release https://github.com/nostrver-se/nostr-php/releases/tag/1.6.0
Planned for week 12:
- Integrate NIP-19
- My PR#100 for
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
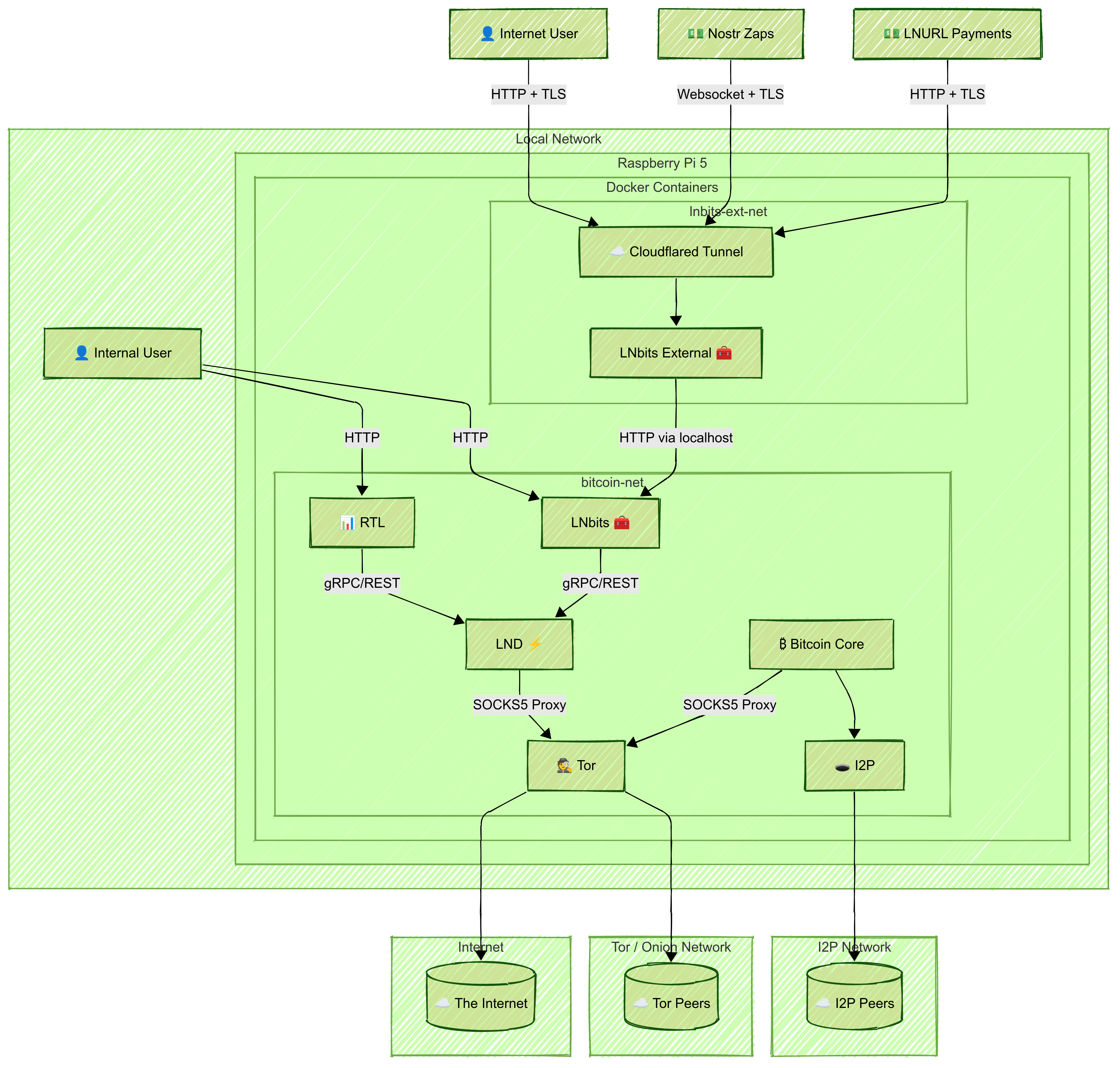
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 06639a38:655f8f71
2025-03-17 14:55:18
@ 06639a38:655f8f71
2025-03-17 14:55:18https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir has started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL as
dtag so it can be used as a unique identifier for every client - Use the content field for the description
- Use the
atag for an addressable event following NIP-01:["a", "39700:pubkey_of_author:", recommended_relay_url_optional]
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ b8a9df82:6ab5cbbd
2025-03-15 00:48:58
@ b8a9df82:6ab5cbbd
2025-03-15 00:48:58There are places in the world where history lingers in the air, where the past and present collide in an explosion of color, sound, and raw emotion.
Comuna 13 is one of them.
The people here are absolutely amazing. I have never experienced such kindness and warmth in Europe or the US as I have here in Medellín.
The generosity is overwhelming—not because they expect anything in return, but simply because they embody a culture of pure love and openness. Colombia, so far, has been one of the best countries I have ever visited—tremendously underestimated. My family and friends were worried about me before I came, fearing I’d be drugged or something bad would happen. But the reality? It has been nothing short of incredible.
Traveling the world, seeing and experiencing different cultures and people, is a blessing—a gift I will be forever grateful for. This is exactly what I always dreamed of: to explore the world with great company, immersing myself in new places, and soaking it all in.
But let me tell you a story that’s touching me deeply as I sit here in Medellín, watching kids play baseball.
They laugh, they run, they chase the ball through the narrow streets, between the colorful murals that stretch up the walls of Comuna 13. It’s an interesting choice of location for a baseball court because you get the sense that the entire community—every house, every window—can see what’s happening. There is an atmosphere of ease and peace, a stark contrast to what this place once was.
When @Rainier turned to me and asked, "Do you know what this place used to be?"
I had a slight idea but was too afraid to speak it out loud—because if it were true, it would be too brutal to believe.
When he told me, I was speechless.
This lively baseball field, these bright murals, this explosion of art and culture—this was once an execution site. A place where people were shot, their deaths meant to serve as a warning to the entire community. Here, in the very spot where children now laugh and play, people once lost their lives in fear and silence. Their deaths were not hidden; they were made into a spectacle, a method of control. The community was forced to watch, powerless, as violence reigned over their homes.
And now? Now it is alive.
Operation Orion, October 16, 2002
Comuna 13 has seen transformation like few places in the world. In 2002, during Operation Orion, the Colombian military launched a brutal crackdown on guerrilla groups controlling the area. Helicopters hovered over the steep hills, gunfire echoed through the streets, and civilians were caught in the crossfire. The operation was meant to rid the area of crime, but it came at a devastating cost. Many innocent people disappeared, never to be seen again. Families were torn apart, and the scars of violence ran deep.
"No matter how broken some parts of the world may seem, there will always be an opportunity for change." – Iván González
And yet, here I stand today, in the middle of what feels like a festival of life. The walls tell stories through vibrant graffiti, each piece echoing the voices of resilience and resistance. The air vibrates with reggaeton and hip-hop beats, the smell of street food drifts through the alleyways, and people—locals and tourists alike—move together in the rhythm of the city’s rebirth.
Yes, it’s touristy. But it’s also real. It’s people painting their past into something beautiful. It’s a man with a cat wearing sunglasses casually walking by. It’s kids laughing in the streets that once ran red with fear. It’s hope.
This is Comuna 13. A place once infamous for death, now bursting with life.
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 3197ad60:7a122b95
2025-03-14 20:00:01
@ 3197ad60:7a122b95
2025-03-14 20:00:01I’m working on my portfolio. I will take it with me to the Children’s Book Fair in Bologna, to stand in very long queues, hoping to show it to some people in the publishing industry.
Preparing a portfolio could be a moment of celebration of all the work I have done and want to share with the world. Wouldn’t that be wonderful?
Instead, it slowly and quietly became a litany of the “could”s and “should”s and “must ”s: I could include all the work that’s even remotely relevant, I should probably showcase a range of skills, and therefore I must create a bunch of completely new work to appeal to every possible audience.
Maybe I need a range of deep, magical forest backgrounds, or a unicorn flying over a London night sky, or a coral reef with jellyfish playing poker, painted in very bright colours. Just to show that I can.

Well, that quickly became a downward spiral of stress-induced ideas for illustrations I don’t have time to make. Even though I enjoyed the work I was doing, in that mindset, no matter what I do, it’s never enough.
And then, lo and behold, I looked through my sketchbook. I was looking for something specific, a texture or a colour from a sketch that I’ve done. I opened one sketchbook looking for it, then another one, then one more.
There was so much work looking back at me wherever I turned. After all, I’ve been drawing daily since last July, sometimes from life, sometimes from imagination. Inevitably, I created a lot of work: paintings, drawings, sketches, and finished illustrations. Only looking through my work did I realise that I will always feel the push to make more work for my portfolio; because my style keeps evolving, I’m able to draw more and better with every step. But is the work I’ve done so far, enough to show where I am as an illustrator? Hell yeah.
Many cliches come to mind (because they’re true!) but my favourite is: don’t compare yourself to others, only compare to yourself from the past.
This is the third year of me going to Bologna for the fair, and the first time I will bring a portfolio with me. That means whatever I do is already 100% more than what I’ve done before. That’s a much better way to think about it.
Chill, Martyna, you’ve got this.
Thanks for reading.
x

-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ 6ad08392:ea301584
2025-03-14 19:03:20
@ 6ad08392:ea301584
2025-03-14 19:03:20In 2024, I was high as a kite on Nostr hopium and optimism. Early that year, my co-founder and I figured that we could use Nostr as a way to validate ambassadors on “Destination Bitcoin” - the germ of a travel app idea we had at the time that would turn into Satlantis. After some more digging and thinking, we realised that Nostr’s open social graph would be of major benefit, and in exploring that design space, the fuller idea of Satlantis formed: a new kind of social network for travel.
 ###### ^^2 slides from the original idea here
###### ^^2 slides from the original idea hereI still remember the call I had with @pablof7z in January. I was in Dubai pitching the AI idea I was working on at the time, but all I could think and talk about was Satlantis and Nostr.
That conversation made me bullish AF. I came back from the trip convinced we’d struck gold. I pivoted the old company, re-organised the team and booked us for the Sovereign Engineering cohort in Madeira. We put together a whole product roadmap, go to market strategy and cap raise around the use of Nostr. We were going to be the ‘next big Nostr app’.
A couple of events followed in which I announced this all to the world: Bitcoin Atlantis in March and BTC Prague in June being the two main ones. The feedback was incredible. So we doubled down. After being the major financial backer for the Nostr Booth in Prague, I decided to help organise the Nostr Booth initiative and back it financially for a series of Latin American conferences in November. I was convinced this was the biggest thing since bitcoin, so much so that I spent over $50,000 in 2024 on Nostr marketing initiatives. I was certainly high on something.
Sobering up
It’s March 2025 and I’ve sobered up. I now look at Nostr through a different lens. A more pragmatic one. I see Nostr as a tool, as an entrepreneur - who’s more interested in solving a problem, than fixating on the tool(s) being used - should.
A couple things changed for me. One was the sub-standard product we released in November. I was so focused on being a Nostr evangelist that I put our product second. Coupled with the extra technical debt we took on at Satlantis by making everything Nostr native, our product was crap. We traded usability & product stability for Nostr purism & evangelism.
We built a whole suite of features using native event kinds (location kinds, calendar kinds, etc) that we thought other Nostr apps would also use and therefore be interoperable. Turns out no serious players were doing any of that, so we spent a bunch of time over-engineering for no benefit 😂
The other wake up call for me was the Twitter ban in Brazil. Being one of the largest markets for Twitter, I really thought it would have a material impact on global Nostr adoption. When basically nothing happened, I began to question things.
Combined, these experiences helped sober me up and I come down from my high. I was reading “the cold start problem” by Andrew Chen (ex-Uber) at the time and doing a deep dive on network effects. I came to the following realisation:
Nostr’s network effect is going to take WAY longer than we all anticipated initially. This is going to be a long grind. And unlike bitcoin, winning is not inevitable. Bitcoin solves a much more important problem, and it’s the ONLY option. Nostr solves an important problem yes, but it’s far from the only approach. It’s just the implementation arguably in the lead right now.
This sobering up led us to take a different approach with Nostr. We now view it as another tool in the tech-stack, no different to the use of React Native on mobile or AWS for infrastructure. Nostr is something to use if it makes the product better, or avoid if it makes the product and user experience worse. I will share more on this below, including our simple decision making framework. I’ll also present a few more potentially unpopular opinions about Nostr. Four in total actually:
- Nostr is a tool, not a revolution
- Nostr doesn’t solve the multiple social accounts problem
- Nostr is not for censorship resistance
- Grants come with a price
Let’s begin…
Nostr is a tool, not a revolution
Nostr is full of Bitcoiners, and as much as we like to think we’re immune from shiny object syndrome, we are, somewhere deep down afflicted by it like other humans. That’s normal & fine. But…while Bitcoiners have successfully suppressed this desire when it comes to shitcoins, it lies dormant, yearning for the least shitcoin-like thing to emerge which we can throw our guiltless support behind.
That thing arrived and it’s called Nostr.
As a result, we’ve come to project the same kind of purity and maximalism onto it as we do with Bitcoin, because it shares some attributes and it’s clearly not a grift.
The trouble is, in doing so, we’ve put it in the same class as Bitcoin - which is an error.
Nostr is important and in its own small way, revolutionary, but it pales in comparison to Bitcoin’s importance. Think of it this way: If Bitcoin fails, civilisation is fucked. If Nostr fails, we’ll engineer another rich-identity protocol. There is no need for the kind of immaculate conception and path dependence that was necessary for Bitcoin whose genesis and success has been a once in a civilisation event. Equivocating Nostr and Bitcoin to the degree that it has been, is a significant category error. Nostr may ‘win’ or it may just be an experiment on the path to something better. And that’s ok !
I don’t say this to piss anyone off, to piss on Nostr or to piss on myself. I say it because I’d prefer Nostr not remain a place where a few thousand people speak to each other about how cool Nostr is. That’s cute in the short term, but in the grand scheme of things, it’s a waste of a great tool that can make a significant corner of the Internet great again.
By removing the emotional charge and hopium from our relationship to Nostr, we can take a more sober, objective view of it (and hopefully use it more effectively).
Instead of making everything about Nostr (the tool), we can go back to doing what great product people and businesses do: make everything about the customer.
Nobody’s going around marketing their app as a “react native product” - and while I understand that’s a false equivalent in the sense that Nostr is a protocol, while react is a framework - the reality is that it DOES NOT MATTER.
For 99.9999% of the world, what matters is the hole, not the drill. Maybe 1000 people on Earth REALLY care that something is built on Nostr, but for everyone else, what matters is what the app or product does and the problem it solves. Realigning our focus in this way, and looking at not only Nostr, but also Bitcoin as a tool in the toolkit, has transformed the way we’re building.
This inspired an essay I wrote a couple weeks ago called “As Nostr as Possible”. It covers our updated approach to using and building WITH Nostr (not just ‘on’ it). You can find that here:
https://futuresocial.substack.com/p/as-nostr-as-possible-anap
If you’re too busy to read it, don’t fret. The entire theory can be summarised by the diagram below. This is how we now decide what to make Nostr-native, and what to just build on our own. And - as stated in the ANAP essay - that doesn’t mean we’ll never make certain features Nostr-native. If the argument is that Nostr is not going anywhere, then we can always come back to that feature and Nostr-fy it later when resources and protocol stability permit.
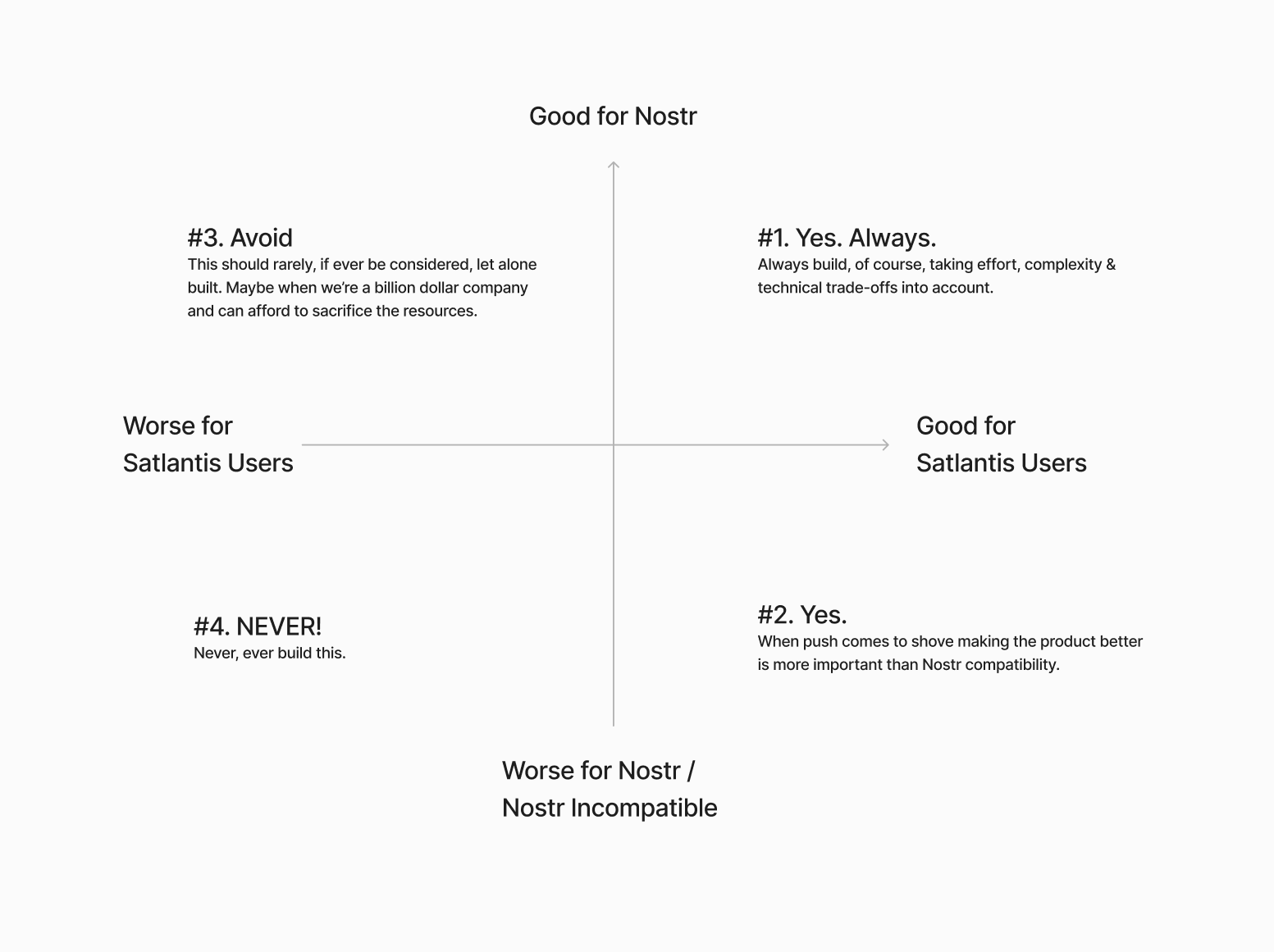
Next…
The Nostr all in one approach is not all “positive”
Having one account accessible via many different apps might not be as positive as we initially thought.

If you have one unified presence online, across all of your socials, and you’re posting the same thing everywhere, then yes - being able to post content in one place and it being broadcast everywhere, is great. There’s a reason why people literally PAY for products like Hypefury, Buffer and Hootsuite (aside from scheduling).
BUT…..This is not always the case.
I’ve spoken to hundreds of creators and many have flagged this as a bug not a feature because they tend to have a different audience on different platforms and speak to them differently depending on the platform. We all know this. How you present yourself on LinkedIn is very different to how you do it on Instagram or X.
The story of Weishu (Tencent’s version of TikTok) comes to mind here. Tencent’s WeChat login worked against them because people didn’t want their social graph following them around. Users actually wanted freedom from their existing family & friends, so they chose Douyin (Chinese TikTok) instead.
Perhaps this is more relevant to something like WeChat because the social graph following you around is more personal, but we saw something similar with Instagram and Facebook. Despite over a decade of ownership, Facebook still keeps the social graphs separated.
All this to say that while having a different strategy & approach on different social apps is annoying, it allows users to tap into different markets because each silo has its own ‘flavour’. The people who just post the same thing everywhere are low-quality content creators anyway. The ones who actually care, are using each platform differently.
The ironic part here is that this is arguably more ‘decentralised’ than the protocol approach because these siloes form a ‘marketplace of communities’ which are all somewhat different.
We need to find a smart way of doing this with Nostr. Some way of catering to the appropriate audience where it matters most. Perhaps this will be handled by clients, or by relays. One solution I’ve heard from people in the Nostr space is to just ‘spin up another nPub’ for your different audience. While I have no problem with people doing that - I have multiple nPubs myself - it’s clearly NOT a solution to the underlying problem here.
We’re experimenting with something. Whether it’s a good idea or not remains to be seen. Satlantis users will be able to curate their profiles and remove (hide / delete) content on our app. We’ll implement this in two stages:
Stage 1: Simple\ In the first iteration, we will not broadcast a delete request to relays. This means users can get a nicely curated profile page on Satlantis, but keep a record of their full profile elsewhere on other clients / relays.
Stage 2: More complex\ Later on, we’ll try to give people an option to “delete on Satlantis only” or “delete everywhere”. The difference here is more control for the user. Whether we get this far remains to be seen. We’ll need to experiment with the UX and see whether this is something people really want.
I’m sure neither of these solutions are ‘ideal’ - but they’re what we’re going to try until we have more time & resources to think this through more.
Next…
Nostr is not for Censorship Resistance
I’m sorry to say, but this ship has sailed. At least for now. Maybe it’s a problem again in the future, but who knows when, and if it will ever be a big enough factor anyway.
The truth is, while WE all know that Nostr is superior because it’s a protocol, people do NOT care enough. They are more interested in what’s written ON the box, not what’s necessarily inside the box. 99% of people don’t know wtf a protocol is in the first place - let alone why it matters for censorship resistance to happen at that level, or more importantly, why they should trust Nostr to deliver on that promise.
Furthermore, the few people who did care about “free speech” are now placated enough with Rumble for Video, X for short form and Substack for long form. With Meta now paying lip-service to the movement, it’s game over for this narrative - at least for the foreseeable future.
 The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded.
The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded.For the normies who never cared, they still don’t care - or they found their way to the anti-platforms, like Threads, BlueSky or Pornhub.
The small minority of us still here on Nostr…are well…still here. Which is great, but if the goal is to grow the network effect here and bring in more people, then we need to find a new angle. Something more compelling than “your account won’t be deleted.”
I’m not 100% sure what that is. My instinct is that a “network of interoperable applications”, that don’t necessarily or explicitly brand themselves as Nostr, but have it under the hood is the right direction. I think the open social graph and using it in novel ways is compelling. Trouble is, this needs more really well-built and novel apps for non-sovereignty minded people (especially content creators) and people who don’t necessarily care about the reasons Nostr was first built. Also requires us to move beyond just building clones of what already exists.
We’ve been trying to do this Satlantis thing for almost a year now and it’s coming along - albeit WAY slower than I would’ve liked. We’re experimenting our way into a whole new category of product. Something different to what exists today. We’ve made a whole bunch of mistakes and at times I feel like a LARP considering the state of non-delivery.
BUT…what’s on the horizon is very special, and I think that all of the pain, effort and heartache along the way will be 100% worth it. We are going to deliver a killer product that people love, that solves a whole host of travel-related problems and has Nostr under the hood (where nobody, except those who care, will know).
Grants come with a price
This one is less of an opinion and more of an observation. Not sure it really belongs in this essay, but I’ll make a small mention just as food for thought,
Grants are a double-edged sword.
I’m super grateful that OpenSats, et al, are supporting the protocol, and I don’t envy the job they have in trying to decipher what to support and what not to depending on what’s of benefit to the network versus what’s an end user product.
That being said, is the Nostr ecosystem too grant-dependent? This is not a criticism, but a question. Perhaps this is the right thing to do because of how young Nostr is. But I just can’t help but feel like there’s something a-miss.
Grants put the focus on Nostr, instead of the product or customer. Which is fine, if the work the grant covers is for Nostr protocol development or tooling. But when grants subsidise the development of end user products, it ties the builder / grant recipient to Nostr in a way that can misalign them to the customer’s needs. It’s a bit like getting a government grant to build something. Who’s the real customer??
Grants can therefore create an almost communist-like detachment from the market and false economic incentive. To reference the Nostr decision framework I showed you earlier, when you’ve been given a grant, you are focusing more on the X axis, not the Y. This is a trade-off, and all trade-offs have consequences.
Could grants be the reason Nostr is so full of hobbyists and experimental products, instead of serious products? Or is that just a function of how ambitious and early Nostr is?
I don’t know.
Nostr certainly needs better toolkits, SDKs, and infrastructure upon which app and product developers can build. I just hope the grant money finds its way there, and that it yields these tools. Otherwise app developers like us, won’t stick around and build on Nostr. We’ll swap it out with a better tool.
To be clear, this is not me pissing on Nostr or the Grantors. Jack, OpenSats and everyone who’s supported Nostr are incredible. I’m just asking the question.
Final thing I’ll leave this section with is a thought experiment: Would Nostr survive if OpenSats disappeared tomorrow?
Something to think about….
Coda
If you read this far, thank you. There’s a bunch here to digest, and like I said earlier - this not about shitting on Nostr. It is just an enquiry mixed with a little classic Svetski-Sacred-Cow-Slaying.
I want to see Nostr succeed. Not only because I think it’s good for the world, but also because I think it is the best option. Which is why we’ve invested so much in it (something I’ll cover in an upcoming article: “Why we chose to build on Nostr”). I’m firmly of the belief that this is the right toolkit for an internet-native identity and open social graph. What I’m not so sure about is the echo chamber it’s become and the cult-like relationship people have with it.
I look forward to being witch-hunted and burnt at the stake by the Nostr purists for my heresy and blaspheming. I also look forward to some productive discussions as a result of reading this.
Thankyou for your attention.
Until next time.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 378562cd:a6fc6773
2025-03-14 17:36:17
@ 378562cd:a6fc6773
2025-03-14 17:36:17In a world where the glow of screens has become the only light that shines bright, it's easy to get lost in the endless expanse of the digital universe. But what if we told you that there's a world beyond the confines of the internet, a world where the air is sweet with the scent of possibility, and the sound of human connection echoes through the streets? A world where the simple act of receiving a handwritten note or a card in the mail can transport you to a bygone era of wonder and enchantment.
Imagine a life where the only sound you hear is the gentle hum of conversation, the rustle of leaves, or the soft lapping of waves against the shore. A life where the only light that shines bright is the warm glow of a sunset, or the soft beam of a candle flickering in the evening breeze. A life where time stands still, and the only clock that matters is the one that ticks away in the silence of your own heart.
This is what it was like to live in the 1990s, a time before the internet and social media dominated our lives. A time when we 'old-folks' grew up in. A time when people actually talked to each other, face-to-face, without the need for a screen. A time when community was built on shared experiences, and relationships were nurtured through genuine human interaction. A time when the world was a vast and mysterious tapestry, waiting to be explored and discovered.
The Liberating Joy of Unplugged Living
Living without the constant distraction of the internet has its benefits, but it's more than that – it's a journey into the heart of human connection. You'll find that you're more present in the moment, more engaged with the people around you, and more connected to your own thoughts and feelings. You'll also find that you're more creative, more productive, and more at peace.
But it's not just about the benefits – it's about the joy of experiencing life in a different way. Imagine being able to focus on a book, a puzzle, or a craft without the constant temptation to check your phone. Imagine being able to enjoy a meal, a walk, or a conversation without the distraction of notifications. Imagine being able to savor the simple pleasures of life, like the taste of a freshly brewed cup of coffee, or the feel of warm sand between your toes. Imagine going to the restroom and not having a tempting beep or music playing from your pants.
Finding Community in the Real World
So, how do you find community and connection in a world without social media? It's easier than you think. Try joining a local club or group that aligns with your interests. Attend community events, like farmers' markets, concerts, or street fairs. Volunteer for a cause you care about, and meet like-minded people along the way. You can also try more low-key activities, like playing a sport, joining a book club, or taking a cooking class. The key is to find activities that bring you joy and help you connect with others in a meaningful way. And as you do, you'll find that the world is full of people who are just as eager to connect, to share, and to experience life together.
A World of Possibility
Living without the internet may seem daunting, but it's not as scary as it sounds. In fact, it can be incredibly liberating. By unplugging from the matrix and reconnecting with the world around you, you'll find a sense of freedom and joy that you may have forgotten existed. You'll discover a world of possibility, a world where anything can happen, and where the only limit is your own imagination.
So, take a step back, put down your phone, and experience life in all its beauty and complexity. Take a deep breath, and let the fresh air fill your lungs. Listen to the sound of your own heartbeat, and let the rhythm of the world guide you on your journey. Go outside and close your eyes. Can you feel the warmth from the sun or does the wind tingle your skin? Can you hear a bird or two or twenty? What else do you hear? You might notice that the longer you listen, sitting still with your eyes closed, the more sounds you will be able to hear. It quite inviting if you only give it a try.
In the end, life isn’t meant to be lived through a screen—it’s meant to be felt, experienced, and shared in the real world. The laughter of a friend, the quiet hum of nature, the warmth of a handwritten letter—these are the things that make life rich. So, take a break from the endless scroll, step outside, and rediscover what it means to truly live. The world is still out there, waiting for you to notice it.
-
 @ f18571e7:9da08ff4
2025-03-14 16:43:03
@ f18571e7:9da08ff4
2025-03-14 16:43:03Gostaria de dar-te as boas vindas à essa rede social descentralizada e sem censura. Creio eu que já tenha ouvido falar sobre o que ela é e como funciona parcialmente, caso não, existem dois sites (ao meu conhecimento) com boas informações, se chamam nostr.com e nostr.how, mas darei mais à frente uma explicação básica.
E já te dou um aviso: você precisa saber ler!
Aqui irei tentar ajuntar o máximo de informações que conseguir para que não falte nada para você, e o que faltar, quero que você saiba como pesquisar. Cada parte de como funciona, como acessar, como criar, etc.
Usarei como padrão neste artigo o #Amethyst, pois é o melhor e mais completo client para android, mas muitas das configurações nele podem ser visualizadas em outros clients. E para começar, vamos ver o que são clients.
Clients
Chamamos de clients (ou clientes em português) aqueles sites ou apps que dão acesso ao protocolo Nostr. Assim como para acessar à internet existem vários browsers (ou navegadores), para acessar o Nostr também existem vários clients, cada um voltado a um foco específico.
Amethyst
O melhor e mais completo client para #android, nele você pode ter acesso de tudo um pouco. Lives, comunidades, chats, "vídeos curtos", hashtags, notas populares, e muito mais.
Na versão da Play Store, existe uma funcionalidade de tradução usando o Google tradutor. https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
Em outras lojas de apps e no repositório Github, o apk não possui essa função. https://github.com/vitorpamplona/amethyst
Aqui tem um tutorial do Amethyst: nostr:nevent1qqsgqll63rw7nfn8ltszwx9k6cvycm7uw56e6rjty6lpwy4n9g7pe5qpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqqqqs7yma4t
Outros Clients
Aqui algumas pessoas expondo suas opiniões sobre certos clients: nostr:nevent1qqsdnrqszc2juykv6l2gnfmvhn2durt703ecvvakvmyfpgxju3q2grspzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqghvkced nostr:nevent1qqsvqahwnljqcz3s3t5zjwyad5f67f7xc49lexu7vq5s2fxxskegv4spzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzeykzw2 Eu mesmo gosto do Amethyst para android e iris.to para web no PC.
Recomendo à você dar uma olhada nesse site: nostrapps.comEle possui todos os clients atuais do Nostr, com uma descrição e links direcionais para você.
Nostr
Agora que você já sabe mais sobre os #clients, você pode acessar o Nostr segundo seu interesse de interface. Vamos ver o que uma IA nos diz sobre o Nostr:
"O #Nostr é um protocolo descentralizado e open source que permite a criação de redes sociais e outros aplicativos sem a necessidade de um servidor central. O nome é um acrônimo para Notes and Other Stuff Transmitted by Relays (Notas e Outras Coisas Transmitidas por Relays). Ele foi projetado para ser resistente à censura, oferecendo uma alternativa às plataformas tradicionais, onde os usuários têm controle total sobre seus dados.
Para que serve?\ O Nostr serve como base para aplicações descentralizadas, como redes sociais, sistemas de pagamento instantâneo em Bitcoin (usando a rede Lightning) e interações diretas entre criadores e consumidores de conteúdo. Ele promove a liberdade de expressão e a privacidade, sem exigir informações pessoais como nome, e-mail ou número de telefone para criar uma conta.
Como funciona?\ O protocolo utiliza dois componentes principais: clientes e relays. Os clientes são aplicações que os usuários usam para interagir com a rede, enquanto os relays são servidores que armazenam e transmitem mensagens. Cada usuário tem uma chave criptográfica única, que garante a autenticidade e a integridade das mensagens. Os relays são independentes, o que significa que, se um relay for bloqueado ou cair, os usuários podem continuar se conectando através de outros.
Em resumo, o Nostr é uma revolução na forma como nos conectamos online, oferecendo liberdade, privacidade e controle aos usuários."
-Perplexity AI
Se você chegou aqui, é porque ouviu em algum lugar ou de alguém, algo parecido com isso. O Nostr é algo moldável, você consegue fazer dele o que quiser, e por aqui você vai encontrar muitas dessas pessoas que o moldam (idealizadores, programadores e desenvolvedores).
Cuide de sua NSEC
Sua Nsec é a chave privada para acesso ao seu perfil, quem a possuir poderá realizar qualquer alteração que queira, comentar, publicar posts e assim por diante. Você deve guardar essa Nsec como se fosse a seed phrase ou chave privada de sua carteira cripto.
Existem alguns modos de guardar e criptografar sua Nsec:
Sem Criptografia
Primeiro de tudo, fique ciente de onde está a sua nsec no client em que acessa o Nostr!
No Amethyst
- Abra o menu de opções
- Selecione "Copia de segurança"
- Clique em "copiar minha chave secreta" Sua nsec será copiada para a àrea de transferência de seu teclado.
Depois de copiar sua nsec, as melhores recomendações que tenho para passar são:
1. Amber
Guarde sua nsec no #Amber, um app assinador de eventos que guarda sua nsec sob criptografia. Após isso, use o mesmo para acessar qualquer client ou site e gerenciar as permissões de cada um. nostr:nevent1qqsvppyfxm87uegv9fpw56akm8e8jlaksxhc6vvlu5s3cmkmz9e0x8cpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqztzjvrd
2. Nos2x-fox
Coloque sua nsec no #Nos2x-fox, um gerenciador de permissões para navegadores a partir do #Firefox. https://addons.mozilla.org/en-US/firefox/addon/nos2x-fox/ E para navegadores da base #chromium existe o #Nos2x do mesmo desenvolvedor. https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
3. Gerenciador de Senhas
Essa é a recomendação mais arriscada, você ainda terá de usar o copiar e colar de sua nsec para acessar o Nostr, a não ser que seu gerenciador reconheça o campo de preenchimento da nsec. Mesmo assim, existem dois gerenciadores que indico; o #Bitwarden e #KeePassDX:
Bitwarden (online)
Play Store: https://play.google.com/store/apps/details?id=com.x8bit.bitwarden Github: https://github.com/bitwarden/mobile
KeePassDX (offline)
Play Store: https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free Github: https://github.com/Kunzisoft/KeePassDX
Com Criptografia
Se tiver interesse em criptografar sua chave, o formato nativo aceito pelos clients é o ncryptsec. O #ncryptsec é uma criptografia por senha (a grosso modo), onde para ser capaz de usá-la nos clients, somente em conjunto com a senha usada na criptografia, fora isso, você não tem acesso. Você consegue encriptar sua nsec e hex para ncryptsec por meios como os abaixo:
1. Amethyst (nsec)
Existe uma função nativa no Amethyst abaixo da opção "copiar chave secreta" onde é só adicionar a sua senha e será criada uma ncryptsec para copiar. Guarde essa nsec encriptada + senha de descriptação em um lugar seguro.
2. Amber (nsec)
No Amber, existe uma função capaz de encriptar sua nsec.
Ao entrar no Amber
- Selecione a engrenagem na parte inferior da tela
- Selecione "backup keys"
- E rolando para baixo existe um campo para digitar sua senha para encriptação da nsec, digite sua senha e copie a ncryptsec. Guarde-as em um lugar seguro.
3. Nostr-Tools (hex)
Foi-me dito que essa ferramenta também encripta o formato nsec, mas eu não consegui fazê-lo, então deixarei para o formato hex. Compile essa ferramenta em seu pc e siga as instruções. Sua chave Hex será encriptada. https://github.com/nbd-wtf/nostr-tools/blob/master/nip49.ts Guarde-as em um lugar seguro.
Relays e Servidores
Relays
Os #Relays (ou relés) são essenciais para receber e enviar informações no Nostr, veja abaixo algumas definições e como utilizar: nostr:nevent1qqsw85k097m8rh5cgqm8glndhnv8lqsm3ajywgkp04mju9je3xje3hcpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqqqqzxvc0le No exemplo é usado o Orbot no Amethyst, você pode escolher usar essa opção, mas houve uma atualização do Amethyst desde a criação deste post, onde foi adicionada a função de "Tor interno".
No Amethyst
- Deslize a tela da esquerda pra direita
- Selecione "Opções de Privacidade"
- Na opção "Motor Tor Ativo" selecione "Interno"
- Para melhor privacidade, na opção "Predefinições Tor/Privacidade" selecione "Privacidade Completa" Todo conteúdo e informação que receber do Nostr passará através da rede Tor, além de que é possível visualizar conteúdos publicados no Nostr exclusivos da rede #Tor com essa configuração. Lembrando que este método é mais veloz que usar o Orbot.
Aqui estão alguns relays Tor: nostr:nevent1qqsqe96a8630tdmcsh759ct8grfsdh0ckma8juamc97c53xvura3etqpxpmhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtmhwden5te0vdhkyunpve6k6cfwvdhk6tmjv4kxz7gzyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgmxr5jk
Servidores de Mídia
Os servidores de mídia são os responsáveis por armazenar seus vídeos e fotos postados no Nostr. No Amethyst já existem alguns por padrão: https://image.nostr.build/8e75323bb428c1e5ef06e37453f56bc3deecd38492a593174c7d141cac1c2677.jpg Mas se você quiser, pode adicionar mais: nostr:nevent1qqster6rm55vy3geqauzzwrm50xwvs2gwa4l27ta2tc65xhpum2pfzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgv2za2r Fique atento aos limites e regras de cada servidor de mídia. nostr:nevent1qqsq3qchucw49wfu2c4wpsung93ffzg4ktt4uuygnjcs5pldf5alr9c3hsgjr
E aqui vai uma #curiosidade: Caso queira postar uma foto ou vídeo que já postou antes, copie o ID da nota em que ela está e cole no novo post, ou então o URL da mídia. Você pode perceber que após upar uma mídia no Nostr, isso se torna uma URL, sempre que usar essa mesma URL, essa mídia irá aparecer.
Lightning e Zaps
Se você chegou aqui por meio de bitcoinheiros, já deve saber que por aqui, usamos a #Lightning para enviar zaps. Mas o que são zaps?
Zaps são nada mais do que satoshis enviados no Nostr. Um exemplo, eu criei esse artigo, pessoas que querem me apoiar ou agradecer por tal, me enviam alguma quantia em sats, dizemos que essa pessoa me mandou um #zap.
Agora posso falar mais sobre a lightning no Nostr.
Para enviar zaps para usuários no Nostr, você precisa de uma carteira lightning. E a carteira que recomendo criarem para isso é através da #Coinos. Na Coinos, você não precisa criar carteiras com seed phrases nem canais lightning, ela é uma carteira custodial, ou seja, a seed phrase está de posse da Coinos. Basta você acessar coinos.io e criar uma conta com username e senha, você pode configurar um e-mail de resgate, código 2FA, e senha para movimentação de fundos. Se quiser, aqui está o app da Coinos, ainda em fase de testes, mas a maior parte do usual funciona perfeitamente. nostr:nevent1qqspndmkhq2dpfjs5tv7mezz57fqrkmlklp4wrn3vlma93cr57q5xlqpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q7xzhreevjvzyvuy48mjn7qlx55q2dktk3xm0lnlpehxvl8dq3l6qxpqqqqqqzp4vkne (o app está disponível na #zapstore, baixe a loja para ter acesso) O legal da coinos é que você pode criar um endereço lightning com o nome que você escolher, o meu por exemplo é componente08@coinos.io, basta criar sua conta e poderá enviar e receber zaps no mesmo instante.
Mas para receber de fato um zap usando o Nostr, você precisa configurar seu endereço lightning no seu perfil. Crie sua conta e copie seu endereço lightning.
No Amethyst
- Clique na sua imagem de perfil
- Selecione "Perfil"
- Aperte o botão com um lápis
- Em "Endereço LN" e "LN URL" cole seu endereço lightning Pronto! Agora as pessoas podem te enviar zaps através de suas publicações.
Antes de enviar zaps, configure seus valores no client.
No Amethyst
- Aperte e segure no raio de qualquer publicação
- No campo "novo valor em sats" digite um valor desejado
- Aperte o "x" nos valores que deseja excluir
- Clique em "Salvar"
Agora, você pode clicar no raio e escolher um valor, ao escolher você será direcionado para a sua carteira, confirme a transação e seu zap foi realizado!
Existe outro meio de enviar zaps que é através do #NWC (Nostr Wallet Connect). Siga os mesmos passos do Yakihonne no Amethyst na aba do raio que acessamos anteriormente. nostr:nevent1qqsxrkufrhpxpfe9yty90s8dnal89qz39zrv78ugmg5z2qvyteckfkqpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgrw73ux O NWC dá ao client ou app, a permissão de gerenciar sua carteira. Isso te permite enviar zaps sem sair do client ou precisar entrar no app da carteira.
Existem muitas outras carteiras lightning por aí, então além da coinos, deixarei o link de outras duas que utilizo.
WOS (Wallet of Satoshi)
Somente Play Store: https://play.google.com/store/apps/details?id=com.livingroomofsatoshi.wallet
Minibits
Play Store: https://play.google.com/store/apps/details?id=com.minibits_wallet Github: https://github.com/minibits-cash/minibits_wallet
Comunidades
Em uma #comunidade é possível encontrar respostas para suas perguntas, artigos e postagens de seu interesse, links úteis e tutoriais para burlar sistemas, documentos e estudos sem censura, etc. Aqui está um exemplo: nostr:nevent1qqs8qztlq26hhstz9yz2tn02gglzdvl5xhkpzhnpuh8v65mjldtdjlqpzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgldlvdq Esse usuário recorrentemente atualiza a lista de comunidades brasileiras no Nostr, recomendo seguir o perfil para se manter atualizado caso tenha interesse: nostr:nevent1qqsxkusgt02pmz6mda4emjlnjjyd4y9pa73ux02dcry8vk3wp85aq9cpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgqq5zn5 Aqui vão algumas #curiosidades para usuários mais avançados: nostr:nevent1qqs246x86gw4zfp70wg65rjklf909n6nppwm0xx6mssl6jgznw4nkjcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkt83q Existem alguns clients que podem criar e gerenciar comunidades, caso você não encontrou nada de seu interesse e quer criar uma, os mais populares são:
Satellite.earth e noStrudel.ninja
Chats
Os #chats são espaços voltados a interação por meio de mensagens, aqui estão alguns: nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqqqqpgdaghw Para contatar uma pessoa no privado:
No Amethyst
- Clique no perfil da pessoa
- Clique no ícone de mensagem
- Envie uma mensagem
Caso queira criar um chat, siga os passos:
No Amethyst
- Clique no ícone de mensagens
- Clique no ícone de "+"
- Serão exibidas duas opções; "privado" e "público", escolha privado para um grupo de poucas pessoas e público para qualquer que quiser entrar.
- Adicione as especificações necessárias e seu chat será criado.
Seguidores
Existe uma #ferramenta capaz de identificar quais usuários que você segue estão inativos, ou publicam pouco e a longos hiatos: nostr:nevent1qqsqqqyhmkqz6x5yrsctcufxhsseh3vtku26thawl68z7klwvcyqyzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgmfzr67
Mais do Nostr
Existem muitas outras coisas para se explorar no Nostr, e é possível que daqui a uns meses, essas configurações e dicas estejam obsoletas. Explorem e aprendam mais sobre esse protocolo.
Abaixo estão mais algumas coisas que gostaria de compartilhar:
Muitos clients não possuem um sistema de #notificações, isso por conta da natureza #descentralizada dos apps, e para não ceder ao Google para isso, optaram por não ter notificações. O Amethyst por exemplo, só possui notificações ativas para quando você receber zaps. Mas esse problema foi resolvido com o #Pokey: nostr:nevent1qqsyw0m8wkwvzsanwufh6kmu3fkkjsu3x6jxxwxst5fxu3yld7q84cspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqz4d5hj5
Aqui está um post sobre uma #loja de #apps voltada a apps do Nostr: nostr:nevent1qqsrk55p927srd30ukas79qzhlwhm5ls9l07g548y288s5u29najzrqpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg85l2mtv4kuxdg36gal3ypymjchvckmypt0kk9qayd9wn5yc5z4zqpsgqqqqqqskv0pek
Alguns RSS para quem gosta de notícias: nostr:nevent1qqsxctkju0pesrupvwfvzfr8wy3hgqag6r8v4228awgyf2x9htjqa7qpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzn4acev
Algumas pessoas famosas que estão por aqui: nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqprwcjan
Alguns Nostr clients e outras coisas: nostr:nevent1qqsgx5snqdl2ujxhug5qkmmgkqn5ej6vhwpu4usfz03gt4n24qcfcwspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqp3pf6y2
Outros posts interessantes: nostr:nevent1qqsp6vf8pp6l97ctzq2wp30nfc9eupnu2ytsauyxalp8fe8dda6dvdgpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkju3h nostr:nevent1qqs0faflxswn5rg8fe9q3202en927my6kupcf08lt26ry3cg3xuuy3gpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgsyrpkh nostr:nevent1qqspx9t3qfnsuzafxxuc5hyha9n5ul5v97uz57hfac9xdtvk5eygqggpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qa5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqxpqqqqqqzctx6uf
Funcionalidades do Amethyst
• Reações (noStrudel também aceita)
nostr:nevent1qqst57p0pzw3vsx3n8g7eaa0dlx3kp5ys9rw3t367q5ewhdyw0kd2rspzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyz36wgs59y6smv4etwgrygja4pwa69vj53hww0hd0wa38vtu5clzzqcyqqqqqqgpje0yu
• Markdown
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpekll6f
Espero ter dado alguma direção pela qual seguir por aqui, se tiver dúvidas, pode comentar aqui abaixo e responderemos com o melhor que pudermos. Olhem alguns dos comentários abaixo, terão posts que os veteranos consideram importantes.
Aos veteranos, comentem abaixo caso tenha faltado algo, e complementem aos novatos, grato!
Mais uma vez, seja bem-vindo ao Nostr!
nóspossuímosaweb #awebénostr
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ 6a6be47b:3e74e3e1
2025-03-14 11:48:03
@ 6a6be47b:3e74e3e1
2025-03-14 11:48:03Hi frens! The other day, I was thinking about doing some spring cleaning. Even though I try to keep things tidy and organized at home 🏠, a little boost never hurts. So, I made a list and decided to post it here. Yay! 🎉
The basics 🛋️ Dust furniture and surfaces 🍴Clean appliances and countertops
🧼 Clean mirror, toilet, shower and sink
🧹 Sweep and mop hard floors 🛏️ Change bedsheets
🪄Vacuum 🪟Clean windows 🪴 Water plants or repot them if neededFull throttle 👚 Donate, recycle or upcycle items 📄 Sort thourgh documents 🧽 Clean fridge 📦 Store seasonal items in labeled boxes 🧽 Clean air filters
You can add as much as you want and do as much as you think is necesary. I just wrote the most important ones that came to mind. ✏️ And of course, here's the list so you can fill it as you wish!
🪄If you can, go ahead and support my artwork! Zaps, likes, reposts – things like that really help us artists keep creating.
✨This amazing community at Nostr has been more than I could express, and so I thank you! Hope you like this little design! 🌈
💌 PS Don't you fret my frens, I have a couple of things in the making I can't wait to show you! 🎉 Stay tuned!
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.












































