-
 @ 502ab02a:a2860397
2025-04-27 03:00:40
@ 502ab02a:a2860397
2025-04-27 03:00:40แดดกับ Infradian Rhythm จังหวะลึกล้ำของชีวิตที่ธรรมชาติกำหนด เวลาเราพูดถึง "วงจรชีวิต" คนส่วนใหญ่จะนึกถึงแค่การนอนตื่นตามรอบวัน หรือ circadian rhythm ที่พระอาทิตย์ขึ้นแล้วเราตื่น พระอาทิตย์ตกแล้วเราง่วง แต่จริง ๆ แล้วร่างกายมนุษย์นั้นลึกซึ้งกว่านั้นมากครับ เพราะนอกจาก circadian rhythm แล้วเรายังมีจังหวะชีวภาพอีกชนิดนึงที่ชื่อว่า "Infradian Rhythm" ซึ่งไม่ได้เดินเป็นรอบวัน แต่เป็นรอบที่ยาวกว่านั้น อาจเป็นรอบสัปดาห์ หรือแม้แต่รอบเดือน และหนึ่งในตัวตั้งจังหวะชั้นดีนี้ที่ใครหลายคนมองข้าม ก็คือ "แดด" นั่นเองครับ
Infradian Rhythm คืออะไร? คำว่า Infradian มาจากรากศัพท์ละติน "infra" ที่แปลว่า "ต่ำกว่า" หรือ "ยาวกว่า" และ "diem" ที่แปลว่า "วัน" เพราะฉะนั้น Infradian จึงหมายถึงวงจรชีวภาพที่นานกว่าหนึ่งวัน เช่น - วัฏจักรรอบเดือนของผู้หญิง (ประมาณ 28 วัน) - จังหวะของระบบภูมิคุ้มกัน (ที่มีกลไกการตอบสนองขึ้นลงตามรอบ) - วัฏจักรการหลั่งฮอร์โมน เช่น testosterone ในผู้ชาย ที่ขึ้นลงเป็นรายสัปดาห์ - จังหวะของอารมณ์หรือพลังชีวิต ที่มี pattern ประจำสัปดาห์หรือเดือน
วงจรเหล่านี้ไม่ได้ใช้แค่เวลาบอกจังหวะ แต่ต้องการสิ่งกระตุ้น (zeitgeber) จากธรรมชาติ เช่น แสง เสียง อุณหภูมิ และโดยเฉพาะอย่างยิ่ง แสงแดด ผมลองรวบรวมสรุปเป็นหมวดๆให้เพื่อเห็นภาพรวมง่ายขึ้นนะครับ
หมวดที่ 1 แดดกับ Infradian Rhythm ของผู้หญิง สำหรับผู้หญิง แดดมีบทบาทโดยตรงกับรอบเดือนผ่านหลายกลไก เช่น 1.1 แสงแดดกับวิตามิน D วิตามิน D ที่สร้างจากแสง UVB มีผลต่อการควบคุมระดับฮอร์โมนเพศหญิง เช่น estrogen และ progesterone หากขาดแดด วงจรฮอร์โมนอาจรวน ทำให้มีอาการ PMS หนัก อารมณ์แกว่ง หรือรอบเดือนมาไม่ปกติ 1.2 แดดกับการหลั่ง melatonin แสงแดดยามเช้าช่วยหยุดการผลิต melatonin และเปิดการผลิต cortisol อย่างสมดุล ซึ่งเป็นกลไกสำคัญที่ควบคุมการสร้าง LH และ FSH (ฮอร์โมนที่ควบคุมการตกไข่) 1.3 Infrared light กับไมโทคอนเดรีย แดดบ่ายที่มีรังสีอินฟราเรดช่วยกระตุ้นพลังงานในระดับเซลล์ ซึ่งส่งผลต่อการซ่อมแซมและปรับสมดุลฮอร์โมนระยะยาว
หมวดที่ 2 แดดกับ Infradian Rhythm ของผู้ชาย แม้ผู้ชายจะไม่มีรอบเดือน แต่ก็มี Infradian เช่นกัน โดยเฉพาะในระบบฮอร์โมนและอารมณ์ครับ 2.1 Testosterone fluctuation แสงแดดช่วยกระตุ้นการหลั่ง testosterone โดยเฉพาะแสงแดดที่สัมผัสผิวหนังและดวงตา การได้รับแดดสม่ำเสมอช่วยให้ร่างกายเข้าสู่วงจรการผลิตฮอร์โมนที่เหมาะสม และไม่เหวี่ยงมาก 2.2 แดดกับการนอน แสงแดดยามเช้ารีเซ็ตวงจรการนอน ทำให้ testosterone หลั่งดีขึ้นในช่วงเช้ามืด (ซึ่งเป็นเวลาที่ร่างกายผลิตฮอร์โมนนี้มากที่สุด) 2.3 แดดกับการซ่อมแซมกล้ามเนื้อ รังสี Infrared และ Red light จากแดดบ่ายช่วยให้ไมโทคอนเดรียในกล้ามเนื้อทำงานดีขึ้น ซึ่งสอดคล้องกับรอบการฟื้นฟูแบบ Infradian ของกล้ามเนื้อหลังออกกำลังกาย
หมวดที่ 3 แดดกับ Infradian Rhythm ในผู้สูงอายุ เมื่ออายุมากขึ้น ร่างกายมักจะสูญเสียจังหวะธรรมชาติไปทีละน้อย ในหมวดนี้เลยแสดงถึงความสัมพันธ์ตามวัยครับ 3.1 ฮอร์โมนลดลง การตอบสนองต่อแสงก็ลดลง ผู้สูงวัยมักผลิต melatonin ลดลง ทำให้นอนไม่ลึกและส่งผลต่อระบบภูมิคุ้มกันที่มีจังหวะ Infradian 3.2 แสงแดดช่วยชะลอการเสื่อม งานวิจัยหลายชิ้นพบว่าแดดช่วยชะลอความเสื่อมของจังหวะชีวภาพในสมอง โดยช่วยลดภาวะซึมเศร้าและชะลอการเสื่อมของสมอง (เช่น Alzheimer) 3.3 ไนตริกออกไซด์ (NO) รังสี UVA จากแดดกระตุ้นการปล่อย NO จากผิวหนัง ซึ่งช่วยเรื่องความดันโลหิตและการไหลเวียนเลือดแบบรอบสัปดาห์ ส่งผลดีต่อหัวใจในระยะยาว
ดังนั้นเมื่อเอาทั้งหมดมาขมวดรวมกันจะพบว่า กลไกสำคัญที่แดดกระทบกับ Infradian Rhythm มีภาพร่างดังนี้ครับ 1.Vitamin D จาก UVB ช่วยสร้างสมดุลฮอร์โมน, สนับสนุนภูมิคุ้มกัน 2.Nitric Oxide (NO) จาก UVA ช่วยขยายหลอดเลือด, ลดการอักเสบเรื้อรัง 3.Melatonin และ Cortisol แดดยามเช้าควบคุมการตื่นและการนอนอย่างมีจังหวะ 4.Infrared Light ช่วงแดดบ่ายแก่ ช่วยซ่อมแซมเซลล์, สนับสนุนการฟื้นตัว 5.Circannual และ Infradian Crosslink แสงแดดฤดูต่าง ๆ (ที่มีช่วงคลื่นต่างกัน) ส่งผลให้จังหวะรอบเดือนและภูมิคุ้มกันเปลี่ยนไปตามฤดูกาล
ซึ่งถ้าอ่านแล้วบางอย่างดูยังสับสนว่าเอ๊ะมันควรจะเป็น circadian rhythm ไม่ใช่เหรอ เช่น การนอน คือมันสามารถอธิบายได้สั้นๆว่า มันมีการทับซ้อนกันครับ ที่เราแยกเป็นเรื่องนี้มาพูดคุยกันเพราะมันมีความสัมพันธ์กันอยู่ อย่างที่คุยกันเสมอๆว่า ร่างกายต้องมองเป็น spectrum ไม่ใช่ binary คอมพิวเตอร์ 011001
โดยตรงแล้ว Sleep–Wake Cycle เราคุมกันที่ Circadian กับ Homeostatic Drive มากกว่า แต่ Infradian ก็อาจส่งผลทางอ้อมผ่านทาง ฮอร์โมนเอสโตรเจนและโปรเจสเตอโรนขึ้น–ลงตามรอบเดือน ส่งผลต่อคุณภาพการนอน เช่น ช่วงใกล้มีประจำเดือนอาจนอนหลับไม่ลึก หรือช่วงวัยทอง (perimenopause) ที่ Infradian เริ่มเปลี่ยนฮอร์โมน จะมีอาการร้อนวูบวาบ ตื่นกลางดึกบ่อยขึ้น หรือแม้แต่ อาการซึมเศร้าตามฤดูกาล (Infradian รายปี) มักเกิดฤดูหนาว ซึ่งแสงน้อย ทำให้ Circadian ฟั่นเฟือนไปด้วย ทำให้นอนมากขึ้นหรือนอนไม่หลับตามฤดู แม้กระทั่งสัมพันธ์ทางพฤติกรรม งานวิจัยบางชิ้นชี้ว่ามนุษย์อาจมีแนวโน้มอยากนอนเพิ่มขึ้นในช่วงปลายสัปดาห์ (weekend catch-up sleep) ซึ่งเป็น Infradian รายสัปดาห์ที่เกิดจากพฤติกรรมสังคมและสะสม Homeostatic Drive
ทีนี้พอจะเข้าใจแล้วใช่ไหมครับว่า ทำไมเราควรเลิกถามเสียทีว่า "ตากแดดเวลาไหนดีที่สุด", "ตากแดดนานแค่ไหนดีที่สุด" จะให้ตอบยังไง? มันแงะออกมาไม่ได้ครับ เราอย่ายึดติดกับการสรุป สรุป สรุป สรุปสิว่าตกลงต้องยังไง การเสพโซเชียลทำให้เราเคยชินกับความฉาบฉวย คัดย่อ จนหลงลืมรายละเอียดว่า โลกแห่งชีวะคือความสัมพันธ์ พารายังไม่ได้แค่แก้ปวดเลย จะนับอะไรกับแดด
คำตอบที่ดีที่สุดผมคิดว่ามันคือ "เลิกถามจุ๊กจิ๊ก แล้วหัดออกไปตากให้ได้ก่อน เปิดตา เปิดหู ปิดปาก" จากนั้นค่อยเอาข้อสงสัยจากการตาก ข้อสงสัยจากการอ่าน มาประมวลผลเองก่อนว่า มีอะไรที่สามารถตอบกันได้บ้างไหม
อย่างที่เราเคยเปรียบเปรยกันครับ แดดไม่ใช่แค่แสง แต่คือผู้อำนวยเพลงที่ประสานเสียงร่างกายทุกจังหวะ ในขณะที่ไฟฟ้าทำให้เราลืมจังหวะธรรมชาติ แดดยังอยู่ตรงนั้น คอยเคาะจังหวะอย่างอดทน รอให้เรากลับมาได้ยินเสียงของตัวเองอีกครั้งหนึ่ง ไม่ใช่แค่เสียงในวันนี้ แต่คือเสียงของชีวิตในรอบเดือน หน้า และปีต่อไป
แดด…ไม่เคยหายไปจากเราเลย มีแต่เราที่ห่างหายไปจากแดดเสียเอง
ตากไปก่อนเหอะ แล้วค่อยถาม "บ่อยเท่าที่ได้ นานเท่าที่ไหว"
ส่วนใครอ่านบทนี้แล้วงง ไม่ต้องเครียดครับ บทต่อๆไปจะค่อยๆมาคลีคลายให้ ทีละนิด #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:42:48
@ 78b3c1ed:5033eea9
2025-04-27 01:42:48・ThunderHubで焼いたマカロンがlncli printmacaroonでどう見えるか確認した。
ThunderHub macaroon permissions
get invoices invoices:read create invoices invoices:write get payments offchain:read pay invoices offchain:write get chain transactions onchain:read send to chain address onchain:write create chain address address:write get wallet info info:read stop daemon info:write この結果によれば、offchain:wirteとonchain:writeの権限がなければそのマカロンを使うクライアントは勝手にBTCを送金することができない。 info:writeがなければ勝手にLNDを止めたりすることができない。
・lncli printmacaroonでデフォルトで作られるmacaroonのpermissionsを調べてみた。 admin.macaroon
{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "info:read", "info:write", "invoices:read", "invoices:write", "macaroon:generate", "macaroon:read", "macaroon:write", "message:read", "message:write", "offchain:read", "offchain:write", "onchain:read", "onchain:write", "peers:read", "peers:write", "signer:generate", "signer:read" ], "caveats": null }chainnotifier.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "onchain:read" ], "caveats": null }invoice.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "invoices:read", "invoices:write", "onchain:read" ], "caveats": null }invoices.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "invoices:read", "invoices:write" ], "caveats": null }readonly.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "info:read", "invoices:read", "macaroon:read", "message:read", "offchain:read", "onchain:read", "peers:read", "signer:read" ], "caveats": null }router.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "offchain:read", "offchain:write" ], "caveats": null }signer.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "signer:generate", "signer:read" ], "caveats": null }walletkit.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "onchain:read", "onchain:write" ], "caveats": null }・lncli listpermissions コマンドですべての RPC メソッド URI と、それらを呼び出すために必要なマカロン権限を一覧表示できる。 LND v0.18.5-betaでやると1344行ほどのJSONができる。 AddInvoiceだとinvoice:writeのpermissionを持つmacaroonを使えばインボイスを作れるようだ。
"/lnrpc.Lightning/AddInvoice": { "permissions": [ { "entity": "invoices", "action": "write" } ] },lncli listpermissionsからentityとactionを抜き出してみた。 ``` "entity": "address", "entity": "info", "entity": "invoices", "entity": "macaroon", "entity": "message", "entity": "offchain", "entity": "onchain", "entity": "peers", "entity": "signer","action": "generate" "action": "read" "action": "write"
lncli とjqを組み合わせると例えば以下コマンドでinvoices:writeを必要とするRPCの一覧を表示できる。 invoices:writeだとAddInvoiceの他にホドルインボイス作成でも使ってるようだlncli listpermissions | jq -r '.method_permissions | to_entries[] | select(.value.permissions[] | select(.entity == "invoices" and .action == "write")) | .key'/invoicesrpc.Invoices/AddHoldInvoice /invoicesrpc.Invoices/CancelInvoice /invoicesrpc.Invoices/HtlcModifier /invoicesrpc.Invoices/LookupInvoiceV2 /invoicesrpc.Invoices/SettleInvoice /lnrpc.Lightning/AddInvoiceinvoices:readだと以下となる。/invoicesrpc.Invoices/SubscribeSingleInvoice /lnrpc.Lightning/ListInvoices /lnrpc.Lightning/LookupInvoice /lnrpc.Lightning/SubscribeInvoicesLNの主だった機能のRPCはoffchainが必要ぽいので抜き出してみた。 offchain:write チャネルの開閉、ペイメントの送信までやってるみたい。 デフォルトのmacaroonでoffchain:writeを持ってるのはadminとrouterの2つだけ。openchannel,closechannelはonchain:writeのpermissionも必要なようだ。/autopilotrpc.Autopilot/ModifyStatus /autopilotrpc.Autopilot/SetScores /lnrpc.Lightning/AbandonChannel /lnrpc.Lightning/BatchOpenChannel /lnrpc.Lightning/ChannelAcceptor /lnrpc.Lightning/CloseChannel /lnrpc.Lightning/DeleteAllPayments /lnrpc.Lightning/DeletePayment /lnrpc.Lightning/FundingStateStep /lnrpc.Lightning/OpenChannel /lnrpc.Lightning/OpenChannelSync /lnrpc.Lightning/RestoreChannelBackups /lnrpc.Lightning/SendCustomMessage /lnrpc.Lightning/SendPayment /lnrpc.Lightning/SendPaymentSync /lnrpc.Lightning/SendToRoute /lnrpc.Lightning/SendToRouteSync /lnrpc.Lightning/UpdateChannelPolicy /routerrpc.Router/HtlcInterceptor /routerrpc.Router/ResetMissionControl /routerrpc.Router/SendPayment /routerrpc.Router/SendPaymentV2 /routerrpc.Router/SendToRoute /routerrpc.Router/SendToRouteV2 /routerrpc.Router/SetMissionControlConfig /routerrpc.Router/UpdateChanStatus /routerrpc.Router/XAddLocalChanAliases /routerrpc.Router/XDeleteLocalChanAliases /routerrpc.Router/XImportMissionControl /wtclientrpc.WatchtowerClient/AddTower /wtclientrpc.WatchtowerClient/DeactivateTower /wtclientrpc.WatchtowerClient/RemoveTower /wtclientrpc.WatchtowerClient/TerminateSession"/lnrpc.Lightning/OpenChannel": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] },offchain:read readの方はチャネルやインボイスの状態を確認するためのpermissionのようだ。/lnrpc.Lightning/ChannelBalance /lnrpc.Lightning/ClosedChannels /lnrpc.Lightning/DecodePayReq /lnrpc.Lightning/ExportAllChannelBackups /lnrpc.Lightning/ExportChannelBackup /lnrpc.Lightning/FeeReport /lnrpc.Lightning/ForwardingHistory /lnrpc.Lightning/GetDebugInfo /lnrpc.Lightning/ListAliases /lnrpc.Lightning/ListChannels /lnrpc.Lightning/ListPayments /lnrpc.Lightning/LookupHtlcResolution /lnrpc.Lightning/PendingChannels /lnrpc.Lightning/SubscribeChannelBackups /lnrpc.Lightning/SubscribeChannelEvents /lnrpc.Lightning/SubscribeCustomMessages /lnrpc.Lightning/VerifyChanBackup /routerrpc.Router/BuildRoute /routerrpc.Router/EstimateRouteFee /routerrpc.Router/GetMissionControlConfig /routerrpc.Router/QueryMissionControl /routerrpc.Router/QueryProbability /routerrpc.Router/SubscribeHtlcEvents /routerrpc.Router/TrackPayment /routerrpc.Router/TrackPaymentV2 /routerrpc.Router/TrackPayments /wtclientrpc.WatchtowerClient/GetTowerInfo /wtclientrpc.WatchtowerClient/ListTowers /wtclientrpc.WatchtowerClient/Policy /wtclientrpc.WatchtowerClient/Stats・おまけ1 RPCメソッド名にopenを含む要素を抽出するコマンドlncli listpermissions | jq '.method_permissions | to_entries[] | select(.key | test("open"; "i"))'{ "key": "/lnrpc.Lightning/BatchOpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannelSync", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } }・おまけ2 thunderhubで作ったmacaroonはテキストで出力されコピペして使うもので、macaroonファイルになってない。 HEXをmacaroonファイルにするには以下コマンドでできる。HEXをコピペして置換する。またYOURSの箇所を自分でわかりやすい名称に置換すると良い。echo -n "HEX" | xxd -r -p > YOURS.macaroonthunderhubで"Create Invoices, Get Invoices, Get Wallet Info, Get Payments, Pay Invoices"をチェックして作ったmacaroonのpermissionsは以下となる。{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "info:read", "invoices:read", "invoices:write", "offchain:read", "offchain:write" ], "caveats": null } ``` offchain:writeはあるがonchain:writeがないのでチャネル開閉はできないはず。 -
 @ 0598a50c:d765ddce
2025-04-27 01:03:15
@ 0598a50c:d765ddce
2025-04-27 01:03:15This LA Times story, from their archives, is not paywalled:
WASHINGTON — The chief of China’s military intelligence secretly directed funds from Beijing to help re-elect President Clinton in 1996, former Democratic fund-raiser Johnny Chung has told federal investigators.
According to sources familiar with Chung’s sealed statements to federal prosecutors, Chung says he met three times with the intelligence official, General Ji Shengde, who ordered $300,000 deposited into the Torrance businessman’s bank account to subsidize campaign donations intended for Clinton,
Never forget blatant, destructive, disloyalty to the USA.
It's not an accident that the Clinton donation from China happened in (Freemason controlled) Los Angeles, where China has a massive presence to this day. Take a drive on San Gabriel Blvd and see for yourself.
According to law enforcement and other sources, key aspects of Chung’s testimony, which has not been made public, have been corroborated by financial records in the United States and Hong Kong.
+++++++++++ Chung, 44, a Taiwan-born American citizen who lives in Artesia, Calif., was one of the most prominent figures in the 1996 campaign finance scandal. He contributed more than $400,000 to various Democratic campaigns and causes, visited the White House no fewer than 50 times and brought numerous Chinese associates to events with the president and First Lady Hillary Rodham Clinton.
As you might expect, it is illegal for U.S. political parties or candidates to accept contributions from foreign sources.
Only a portion of the $300,000 made it into Democratic campaign coffers, records show.
A spokesman for China’s embassy in Washington denied any involvement in the 1996 elections.
SOURCE: https://www.latimes.com/archives/la-xpm-1999-apr-04-mn-24189-story.html
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29
@ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29After taking the most predictable option on day 1, the last 6 rounds of the draft were a rollercoaster. The Raiders traded back twice in the 2nd round and ended up with some extra picks.
Picks
-
RB Ashton Jeanty: Best player available at a position of need. Jeanty + Bowers gives the Raiders offense two elite weapons
-
WR Jack Bech: Tough, physical receiver with great hands, willing and able blocker
-
CB Darien Porter: Elite athlete, classic Raiders pick, "Can't teach size, can't teach speed."
-
OL Caleb Rogers: Versatile, athletic lineman, will likely compete at guard
-
OL Charles Grant: Same as above, but more likely to compete at tackle
-
WR: Donte Thornton: 6'5" and 4.3 speed, another classic Raiders pick, can open the field for the other weapons
-
DT Tonka Hemingway: Dope name, versatile and athletic D-Lineman, adds depth and optionality to a very talented groups
-
DT/TE/FB JJ Pegues: Interesting guy, probably won't contribute much as a DT immediately, but could be part of the goal line package on offense, as he had 7 rushing TDs last year and as a former TE could be a red zone target too
-
WR/KR/PR/QB Tommy Mellot: Another super versatile player, ran a 4.4 40 as a QB, but will convert to WR and return kicks, seems like someone with tons of trick play potential
-
QB Cam Miller: Finally, an actual QB! Won a ton of games at a smaller program.
-
LB Cody Lindenberg: 7th rounder, probably special teams if he makes the team
Takeaways
The Raiders added a ton of talent and versatility to their offense, including a defensive player who can contribute to the red zone offense in several ways. They're building a big physically dominant offense around an elite RB/TE combo, with big physical WRs who don't mind blocking and another talented TE.
The defensive line is going to have to be really dominant, which they have the potential for, because there is a dearth of talent behind them. Porter recently converted to CB from WR, so will likely take time to develop, and the others are day 3 picks.
The recipe will likely be to eat up clock on long offensive drives to give our pass rushers lots of breathers. Score reliably with a much improved redzone offense and a great kicker, then rely on that pass rush and the best punter in the league to keep the other team out of the endzone.
It's a good starting point. Maybe they'll sign Ramsey, or something, and really upgrade the defensive back group before the season starts.
originally posted at https://stacker.news/items/962047
-
-
 @ 68c90cf3:99458f5c
2025-04-26 15:05:41
@ 68c90cf3:99458f5c
2025-04-26 15:05:41Background
Last year I got interesting in running my own bitcoin node after reading others' experiences doing so. A couple of decades ago I ran my own Linux and Mac servers, and enjoyed building and maintaining them. I was by no means an expert sys admin, but had my share of cron jobs, scripts, and custom configuration files. While it was fun and educational, software updates and hardware upgrades often meant hours of restoring and troubleshooting my systems.
Fast forward to family and career (especially going into management) and I didn't have time for all that. Having things just work became more important than playing with the tech. As I got older, the more I appreciated K.I.S.S. (for those who don't know: Keep It Simple Stupid).
So when the idea of running a node came to mind, I explored the different options. I decided I needed a balance between a Raspberry Pi (possibly underpowered depending on use) and a full-blown Linux server (too complex and time-consuming to build and maintain). That led me to Umbrel OS, Start9, Casa OS, and similar platforms. Due to its simplicity (very plug and play), nice design, and being open source: GitHub), I chose Umbrel OS on a Beelink mini PC with 16GB of RAM and a 2TB NVMe internal drive. Though Umbrel OS is not very flexible and can't really be customized, its App Store made setting up a node (among other things) fairly easy, and it has been running smoothly since. Would the alternatives have been better? Perhaps, but so far I'm happy with my choice.

Server Setup
I'm also no expert in OpSec (I'd place myself in the category of somewhat above vague awareness). I wanted a secure way to connect to my Umbrel without punching holes in my router and forwarding ports. I chose Tailscale for this purpose. Those who are distrustful of corporate products might not like this option but again, balancing risk with convenience it seemed reasonable for my needs. If you're hiding state (or anti-state) secrets, extravagant wealth, or just adamant about privacy, you would probably want to go with an entirely different setup.
Once I had Tailscale installed on Umbrel OS, my mobile device and laptop, I could securely connect to the server from anywhere through a well designed browser UI. I then installed the following from the Umbrel App Store:
- Bitcoin Core
- Electrum Personal Server (Electrs)
At this point I could set wallets on my laptop (Sparrow) and phone (BlueWallet) to use my node. I then installed:
- Lightning Node (LND)
- Alby Hub
Alby Hub streamlines the process of opening and maintaining lightning channels, creating lightning wallets to send and receive sats, and zapping notes and users on Nostr. I have two main nsec accounts for Nostr and set up separate wallets on Alby Hub to track balances and transactions for each.
Other apps I installed on Umbrel OS:
- mempool
- Bitcoin Explorer
- LibreTranslate (some Nostr clients allow you to use your own translator)
- Public Pool

Public Pool allows me to connect Bitaxe solo miners (a.k.a. "lottery" miners) to my own mining pool for a (very) long shot at winning a Bitcoin block. It's also a great way to learn about mining, contribute to network decentralization, and generally tinker with electronics. Bitaxe miners are small open source single ASIC miners that you can run in your home with minimal technical knowledge and maintenance requirements.
Open Source Miners United (OSMU) is a great resource for anyone interesting in Bitaxe or other open source mining products (especially their Discord server).

Although Umbrel OS is more or less limited to running software in its App Store (or Community App Store, if you trust the developer), you can install the Portainer app and run Docker images. I know next to nothing about Docker but wanted to see what I might be able to do with it. I was also interested in the Haven Nostr relay and found that there was indeed a docker image for it.
As stated before, I didn't want to open my network to the outside, which meant I wouldn't be able to take advantage of all the features Haven offers (since other users wouldn't be able to access it). I would however be able to post notes to my relay, and use its "Blastr" feature to send my notes to other relays. After some trial and error I managed to get a Haven up and running in Portainer.

The upside of this setup is self-custody: being able to connect wallets to my own Bitcoin node, send and receive zaps with my own Lightning channel, solo mine with Bitaxe to my own pool, and send notes to my own Nostr relay. The downside is the lack of redundancy and uptime provided by major cloud services. You have to decide on your own comfort level. A solid internet connection and reliable power are definitely needed.

This article was written and published to Nostr with untype.app.
-
 @ c066aac5:6a41a034
2025-04-27 00:35:38
@ c066aac5:6a41a034
2025-04-27 00:35:38I work in the business world as a salesperson. I am frequently out and about in the community trying to make friends, connect with people who I can help, and ultimately grow my book of business. I have goals set by my employers and I aim to meet those expectations. Because of this, I find myself frequently under pressure to find ways to produce. This often leads to me being disappointed in myself; my sales cycles are long and I lose more deals than I win. My Dad often reminds me that How to Win Friends and Influence People has all the secrets of sales I'll ever need, but I still end up wishing I could find that secret edge to out-do the competition. That's where the watch temptation comes in.
I frequently see a luxurious timepiece on the left wrist of my peers and elder-statesmen closers. Rolex, Omega, Patek, a whole world of $10k minimum machines. It comes across as a power-move, a symbol of status that is hard to ignore. It sends a message that the bearer's time is more valuable than that of other people. It makes me think "if this person is wearing that watch, that means they're great at what they do." The ultimate investment in one's self.
As a newly married man expecting a child, it is hard for me to stomach such a purchase. My wife has supported the idea of me potentially getting such a timepiece; as much as it tickles my fancy, I'd rather put my capital towards things that further my family than my clout. One of the things that struck me was a statement made by an investment advisor in my Kiwanis club: "A watch is a purchase, not an investment."
What a true statement! His words helped me escape my short-lived delusions. That said, I still look at watches sometimes on the internet (The Omega No Time to Die watch is sleek looking). One day, I found myself looking at houses online shortly after looking at watches online. Then it hit me: how many purchases are being marketed as investments in this era? A Rolex is a supposed investment in your career, not just a luxury timepiece. A house is a mechanism for monetary growth, not an attainable home to be enjoyed by a family. A college degree is an investment for your future, not a vehicle for building upon passions.
The Bitcoiners will repeat the phrase "fix the money, fix the world" in harmonious chorus to address the concern I have laid out in this article. Ultimately, I leave you with this reminder: don't let the world pass off things that should be inconsequential purchases as investments with ROIs. I believe the only true investment one can make is into the people around them; that will yield the greatest rewards for the soul.
-
 @ 6e64b83c:94102ee8
2025-04-26 23:33:16
@ 6e64b83c:94102ee8
2025-04-26 23:33:16- Demo: https://blog.nostrize.me
- Source code: nostr-static
Prerequisites
Before using nostr-static, you'll need:
- Nostr Articles: You can either:
- Create new articles using platforms like yakihonne.com or habla.news
- Find existing articles on Nostr
-
Copy the naddr string from the article (usually can be found in the address bar)
-
Author Profiles: For each article's author:
- Copy their public key (pubkey)
- Visit njump.me/npub1xxxxx (replace with the actual pubkey)
- Copy the nprofile string from the page
These identifiers (naddr for articles and nprofile for authors) are essential for the tool to fetch and display your content correctly.
Features
Core Functionality
- Index Page: A homepage featuring your blog's title, logo, article summaries, and tags
- Article Pages: Individual pages for each article, including:
- Title and logo
- Article summary
- Full content
- Tags
- Comments (via ZapThreads integration)
Social Features
- Comments: Integrated with ZapThreads for decentralized commenting
- Nostr Connect: Seamless integration with window.nostr.js (wnj), supporting NIP-46 bunker connect
Content Organization
- Tag Pages: Browse articles filtered by specific tags
- Profile Pages: View articles from specific authors
- Manual Curation: Select and order articles by adding their naddr strings (see NIP-19)
Customization Options
- Themes: Choose between dark and light mode
- Branding:
- Custom logo
- Custom blog title
- Network: Specify your preferred Nostr relays
Technical Requirements
- Profile Format: Authors must be added in nprofile format (see NIP-19) for consistency
- Automatic Updates: Built-in scripts for:
- Windows Task Scheduler
- Unix/Linux cron jobs
Getting Started
- Fork and Clone:
- Fork this repository to your GitHub account
- Clone it to your local machine or use GitHub Codespaces for a cloud-based development environment
-
Watch this quick tutorial to learn more about GitHub Codespaces
-
Configuration: Set up your
config.yamlfile with: - Blog title and logo
- Theme preference
- Relay list
- Article naddr strings
-
Author nprofile strings
-
Content Selection: Add your desired articles by including their naddr strings in the configuration
-
Author Selection: You have to add the nprofile strings of the articles. This is needed for URL consistancy.
-
Build & Run: Follow the instruction in the README at https://github.com/dhalsim/nostr-static
-
Deployment: Choose your preferred static hosting service and deploy the generated HTML files
-
Updates: Set up automatic updates using the provided scripts for your operating system (For github pages)
Deployment Options
GitHub Pages (Recommended)
GitHub Pages provides free hosting for static websites. Here's how to set it up:
- Enable GitHub Pages:
- Go to your repository's Settings
- Navigate to "Pages" in the menu
- Under "Build and deployment" > "Source", select "GitHub Actions"
- Enable Actions by following the GitHub Actions settings guide
-
Go to the "Actions" tab in the top menu. If you see the message "Workflows aren't being run on this forked repository", click the "I understand my workflows, go ahead and enable them" button
-
Custom Domain Setup:
- Purchase a domain from your preferred domain registrar
- Create a CNAME record in your domain's DNS settings:
- Type: CNAME
- Name: @ or www or a subdomain you prefer (depending on your preference)
- Value: YOUR_GITHUB_USERNAME.github.io
- In your repository's GitHub Pages settings:
- Enter your custom domain in the "Custom domain" field
- Check "Enforce HTTPS" for secure connections
- Wait for DNS propagation (can take up to 24 hours)
- Your site will be available at your custom domain
Other Hosting Options
You can also deploy your static site to any hosting service that supports static websites, such as: - Netlify - Vercel - Cloudflare Pages - Amazon S3 - Any traditional web hosting service
Why nostr-static?
nostr-static offers a unique solution for bloggers who want to leverage Nostr's decentralized content while maintaining a traditional web presence. It combines the best of both worlds:
- Decentralized Content: Your articles live on the Nostr network
- Traditional Web Presence: A familiar blog interface for your readers
- Easy Maintenance: Simple configuration and automatic updates
- Flexible Hosting: Deploy anywhere that supports static websites
- Social interactions: Leverage nostr for comments
Conclusion
nostr-static makes it easy to create a professional blog from your Nostr long-form content. Whether you're a seasoned Nostr user or new to the ecosystem, this tool provides a straightforward way to share your content with both the Nostr community and traditional web users.
Start your Nostr-powered blog today by visiting the demo and exploring the possibilities!
-
 @ 418a17eb:b64b2b3a
2025-04-26 21:45:33
@ 418a17eb:b64b2b3a
2025-04-26 21:45:33In today’s world, many people chase after money. We often think that wealth equals success and happiness. But if we look closer, we see that money is just a tool. The real goal is freedom.
Money helps us access resources and experiences. It can open doors. But the constant pursuit of wealth can trap us. We may find ourselves stressed, competing with others, and feeling unfulfilled. The more we chase money, the more we might lose sight of what truly matters.
Freedom, on the other hand, is about choice. It’s the ability to live life on our own terms. When we prioritize freedom, we can follow our passions and build meaningful relationships. We can spend our time on what we love, rather than being tied down by financial worries.
True fulfillment comes from this freedom. It allows us to define success for ourselves. When we embrace freedom, we become more resilient and creative. We connect more deeply with ourselves and others. This sense of purpose often brings more happiness than money ever could.
In the end, money isn’t the ultimate goal. It’s freedom that truly matters. By focusing on living authentically and making choices that resonate with us, we can create a life filled with meaning and joy.
-
 @ ec8f6700:fb2a4766
2025-04-26 21:43:10
@ ec8f6700:fb2a4766
2025-04-26 21:43:10SNAILS.
Creator Co-op for the Cosmos Ecosystem
Written by: Terp Network
Original post: https://docs.terp.network/guides/nodes/faq
We must keep in mind that p2p networks are exposed to the risk of denial of service attacks, and an effective way to mitigate this type of attacks is by using sentry nodes.Why is it important to avoid denial of service attacks?
When our node is suffering a denial of service attack that cannot be mitigated by the server provider, it is likely that the server will be inoperative for the duration of the attack because, being saturated, it will stop responding to the requests made by the rest of the nodes in the network.
If our node becomes inoperative, it means that we are no longer participating in the consensus rounds, our node will not be signing blocks or generating rewards for the delegators and therefore in a few minutes the node will be jailed and penalized.
In addition to being a risk for node operators due to the penalties involved in being jailed, it is also a risk for the network, since if an attack is carried out on several nodes at the same time, the stability and security of the network would be affected. Sentry nodes hide our validator’s IP from the world
Using sentry nodes is a solution to prevent the rest of the network from knowing the IP of our validator node, but allowing our validator node to continue communicating with other validator nodes in the terp network, since if the node were 100% isolated, it would not be able to participate in the network and therefore would not generate rewards for the delegators.
A sentry node is a bridge between our validator node and the rest of the network, so that the rest of the network does not know the IP of the validator node, but the IP of the sentry nodes.Can sentry nodes suffer denial of service attacks?
Yes, but as they are nodes that are not validating transactions and only act as a bridge between the network and the validating node, we could quickly deploy new sentry nodes or even change the IP of the sentry node being attacked. How many sentry nodes can there be?
There is really no maximum number, the more sentry nodes we have, the more resistance to denial of service attacks our validator node will have. However, it must be taken into account that the more sentry nodes we have, the more complex it will be to maintain our nodes when carrying out maintenance or upgrades, in addition to the increase in server costs. You should have at least two sentry nodes and if possible have one of them in a different datacenter from where the validator node is deployed. Where should the sentry nodes be deployed?
If two sentry nodes are going to be mounted, one of them could be deployed in the same datacenter where our validator node is, this will reduce the latency between both servers, and therefore, the connection between both servers will be quite fast. The other sentry node could be located in a different datacenter; this way, in case the network of the datacenter where our validator node is down for any reason, we would always have a node with the current block available to synchronize our validator node. Step by step guide
To follow this guide, we will use a node created & connected to 90u-3 testnet network. In case you have not deployed the node yet, how to install the terp-core binary Creating the sentry nodes
Once we have contracted the two sentry node servers and we have the access IPs, we must perform the same installation that we would perform as if it were a validator node on both servers.
First, we will need to download and compile the terp-core binary.
git clone https://github.com/terpnetwork/terp-core.git cd terp-core git checkout
Once downloaded, we will proceed to compile the binary:
make install
It will also be necessary to initialize the node so that the .terp directory is created, for this we can use the following commands, each one in the corresponding server:
On sentry node A:
terpd init "terpd-up - Sentry A" --chain-id 90u-3
On sentry node B:
terpd init "terpd-up - Sentry B" --chain-id 90u-3
Once the previous step is done, the .terp folder will already exist, so we can download the genesis.json file:
curl https://raw.githubusercontent.com/terpnetwork/networks/main/testnet/90u-3/genesis.json > ~/.terp/config/genesis.json
Configure service
Finally, we will configure the terp service:
sudo nano /etc/systemd/system/system/terpd.service
sudo tee /etc/systemd/system/terpd.service > /dev/null <<EOF [Unit] Description=terpd Daemon After=network-online.target [Service] User=$USER ExecStart=$(which terpd) start Restart=always RestartSec=3 LimitNOFILE=65535 [Install] WantedBy=multi-user.target EOF
Base configuration of the sentry nodes
For now we have not done anything different from what we would do when setting up a validator node, although we have stopped doing several things, such as creating the wallet or running the validator creation command “tx staking create-validator”, since we do not want to create validator nodes, only nodes that synchronize with the rest of the nodes in the network and we can use to synchronize our validator node in a secure way without exposing our IP to the rest of the network.
The sentry nodes (both), must have peers to be synchronized at all times, we will add the following peers to the config.toml file inside the config folder. Persistent Peers:
peers=$(curl -s https://ss.terp.nodestake.top/peers.txt) sed -i.bak -e "s/^persistent_peers =./persistent_peers = \"$peers\"/" ~/.terp/config/config.toml
Note: the peers were obtained from Nodestake validator team.
It would also be advisable to add as persistent peer the sentry nodes between them. That is to say, that the sentry node B is persistent peer of the sentry node A, in the same way that the sentry node A is persistent peer of the sentry node B; this will make us have more redundancy. Private Peers:
In the config.toml file of the config folder of the sentry nodes (both), it is necessary to specify the id of the validator node in the private_peer_ids parameter. This is so that our sentry nodes never share with the rest of the peers of the network the existence of our validator node.
If you don’t know how to get the id of your validator node, you can get it with the following command:
terpd tendermint show-node-id
Unconditional Peers
In the same configuration file, we will also find the unconditional-peer-ids parameter to which we must add our validator node as we did with the private_peer_ids parameter. This step is necessary because the nodes have a limited number of peers to which they can connect.
To avoid the risk of leaving our validator node incommunicado, by setting its id in the unconditional-peer-ids parameter, we will make the sentry nodes always connected to the validator node even if the limit of peers to which they can be connected has been exceeded. Optionally we can also add in this same parameter (separated by commas) the homologous sentry node to guarantee that the sentry nodes will always be connected to each other.
unconditional-peer-ids = "validator node, peer sentry node". Start Sentry Nodes
At this point, we could start our sentry nodes and let them synchronize and be discovered by the rest of the network. For that we will use the following command:
sudo systemctl daemon-reload sudo systemctl enable terpd
Base configuration for validator
Once the sentry nodes have been synchronized, we can configure the validator node with all certainty that our validator node is not going to stop being synchronized with the network. We will have to edit the config.toml file in the config folder, where we will find the following lines: Persistent Peers
In persistent_peers we will add only the ids of the sentry nodes, that is to say that if the node was already mounted before, we will have to delete the content of this field before adding our sentry nodes. PEX
In the same configuration file we will find the pex parameter, which we must set to “false”. This parameter does not discover other peers, it will only use the ones set in the persistent_peers parameter.
pex = false
Remove address book (optional)
If the validator has already been exposed to the network, we can delete the address book so that it only “knows” the sentry nodes; if it is a validator that has never been started, this step is not necessary. Once inside the config folder and with the node stopped, perform the following command:
rm -rf $HOME/.terp/config/addrbook.json
Start Validator Node
To verify that we are really connected only to two peers and these are the sentry nodes, we can write the following command in our validated node; the output is a JSON where it will show us the number and which peers we are connected to, where the number should be two and the peers should be our sentry nodes.
curl -s localhost:26657/net_info Here you can see the number of peers to which our validator node is connected, in this case it is two, which is correct. Extra: Protecting the validator node through firewall
Right now the p2p port of our validator node is open and anyone can establish a connection. If we have just set up the validator node, with the configurations made, nobody would have to find our validator node, however, to add a plus of security it is advisable to close the p2p port and only allow traffic to the IP’s of our sentry nodes.
There are several ways to do this, it is possible that your server provider allows you to do it through a gui. Ufw is a simple to use alternative. Extra: Private networks
One possibility we have when our validator node is in the same datacenter as one of the sentry nodes, would be to use private addressing.
In case we want to use private addressing, we will have to edit the addr-book-strict parameter of the config.toml file and set it to false in both the validator node and the sentry node that are communicating under private addressing. This parameter, when set to “true”, will only add routable addresses to the address book, the private addresses defined in RFC-1918 are not routable, therefore, they would not be added to the address book, so we will have to change it to false to be able to use IP addresses from the private ranges.
addr-book-strict: boolean. By default, nodes with a routable address will be considered for connection. If this setting is disabled (false), non-routable IP addresses, such as addresses from a private network, can be added to the address book. Source: https://docs.tendermint.com/master/nodes/validators.htmlConclusions
Having sentry nodes will not only help our validator node not to fall victim to a denial of service attack, but will also make the Terp network more robust. The installation of the sentry nodes does not differ much from that of a validator node, and the additional configurations to be performed are very simple and intuitive.
Now that Terp Network is doing the 90u-3 testnet, it is a good time to try to set up sentry nodes and once the mainnet is launched, to be able to replicate it with the experience of having been able to test it in 90u-3. If you already have your node on 90u-3, what are you waiting for to set up your sentry nodes and protect yourself from unwanted attacks?
sources: https://stakely.io/en/blog/how-to-deploy-sentry-nodes-in-the-archway-network -
 @ 1f79058c:eb86e1cb
2025-04-26 21:17:17
@ 1f79058c:eb86e1cb
2025-04-26 21:17:17I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 7d3cd8a1:66aa5c86
2025-04-26 21:02:44
@ 7d3cd8a1:66aa5c86
2025-04-26 21:02:44SNAILS.
Creator Co-op for the Cosmos Ecosystem
Written by: Terp Network
Original post: https://docs.terp.network/guides/nodes/faq
We must keep in mind that p2p networks are exposed to the risk of denial of service attacks, and an effective way to mitigate this type of attacks is by using sentry nodes.Why is it important to avoid denial of service attacks?
When our node is suffering a denial of service attack that cannot be mitigated by the server provider, it is likely that the server will be inoperative for the duration of the attack because, being saturated, it will stop responding to the requests made by the rest of the nodes in the network.
If our node becomes inoperative, it means that we are no longer participating in the consensus rounds, our node will not be signing blocks or generating rewards for the delegators and therefore in a few minutes the node will be jailed and penalized.
In addition to being a risk for node operators due to the penalties involved in being jailed, it is also a risk for the network, since if an attack is carried out on several nodes at the same time, the stability and security of the network would be affected. Sentry nodes hide our validator’s IP from the world
Using sentry nodes is a solution to prevent the rest of the network from knowing the IP of our validator node, but allowing our validator node to continue communicating with other validator nodes in the terp network, since if the node were 100% isolated, it would not be able to participate in the network and therefore would not generate rewards for the delegators.
A sentry node is a bridge between our validator node and the rest of the network, so that the rest of the network does not know the IP of the validator node, but the IP of the sentry nodes.Can sentry nodes suffer denial of service attacks?
Yes, but as they are nodes that are not validating transactions and only act as a bridge between the network and the validating node, we could quickly deploy new sentry nodes or even change the IP of the sentry node being attacked. How many sentry nodes can there be?
There is really no maximum number, the more sentry nodes we have, the more resistance to denial of service attacks our validator node will have. However, it must be taken into account that the more sentry nodes we have, the more complex it will be to maintain our nodes when carrying out maintenance or upgrades, in addition to the increase in server costs. You should have at least two sentry nodes and if possible have one of them in a different datacenter from where the validator node is deployed. Where should the sentry nodes be deployed?
If two sentry nodes are going to be mounted, one of them could be deployed in the same datacenter where our validator node is, this will reduce the latency between both servers, and therefore, the connection between both servers will be quite fast. The other sentry node could be located in a different datacenter; this way, in case the network of the datacenter where our validator node is down for any reason, we would always have a node with the current block available to synchronize our validator node. Step by step guide
To follow this guide, we will use a node created & connected to 90u-3 testnet network. In case you have not deployed the node yet, how to install the terp-core binary Creating the sentry nodes
Once we have contracted the two sentry node servers and we have the access IPs, we must perform the same installation that we would perform as if it were a validator node on both servers.
First, we will need to download and compile the terp-core binary.
git clone https://github.com/terpnetwork/terp-core.git cd terp-core git checkout
Once downloaded, we will proceed to compile the binary:
make install
It will also be necessary to initialize the node so that the .terp directory is created, for this we can use the following commands, each one in the corresponding server:
On sentry node A:
terpd init "terpd-up - Sentry A" --chain-id 90u-3
On sentry node B:
terpd init "terpd-up - Sentry B" --chain-id 90u-3
Once the previous step is done, the .terp folder will already exist, so we can download the genesis.json file:
curl https://raw.githubusercontent.com/terpnetwork/networks/main/testnet/90u-3/genesis.json > ~/.terp/config/genesis.json
Configure service
Finally, we will configure the terp service:
sudo nano /etc/systemd/system/system/terpd.service
sudo tee /etc/systemd/system/terpd.service > /dev/null <<EOF [Unit] Description=terpd Daemon After=network-online.target [Service] User=$USER ExecStart=$(which terpd) start Restart=always RestartSec=3 LimitNOFILE=65535 [Install] WantedBy=multi-user.target EOF
Base configuration of the sentry nodes
For now we have not done anything different from what we would do when setting up a validator node, although we have stopped doing several things, such as creating the wallet or running the validator creation command “tx staking create-validator”, since we do not want to create validator nodes, only nodes that synchronize with the rest of the nodes in the network and we can use to synchronize our validator node in a secure way without exposing our IP to the rest of the network.
The sentry nodes (both), must have peers to be synchronized at all times, we will add the following peers to the config.toml file inside the config folder. Persistent Peers:
peers=$(curl -s https://ss.terp.nodestake.top/peers.txt) sed -i.bak -e "s/^persistent_peers =./persistent_peers = \"$peers\"/" ~/.terp/config/config.toml
Note: the peers were obtained from Nodestake validator team.
It would also be advisable to add as persistent peer the sentry nodes between them. That is to say, that the sentry node B is persistent peer of the sentry node A, in the same way that the sentry node A is persistent peer of the sentry node B; this will make us have more redundancy. Private Peers:
In the config.toml file of the config folder of the sentry nodes (both), it is necessary to specify the id of the validator node in the private_peer_ids parameter. This is so that our sentry nodes never share with the rest of the peers of the network the existence of our validator node.
If you don’t know how to get the id of your validator node, you can get it with the following command:
terpd tendermint show-node-id
Unconditional Peers
In the same configuration file, we will also find the unconditional-peer-ids parameter to which we must add our validator node as we did with the private_peer_ids parameter. This step is necessary because the nodes have a limited number of peers to which they can connect.
To avoid the risk of leaving our validator node incommunicado, by setting its id in the unconditional-peer-ids parameter, we will make the sentry nodes always connected to the validator node even if the limit of peers to which they can be connected has been exceeded. Optionally we can also add in this same parameter (separated by commas) the homologous sentry node to guarantee that the sentry nodes will always be connected to each other.
unconditional-peer-ids = "validator node, peer sentry node". Start Sentry Nodes
At this point, we could start our sentry nodes and let them synchronize and be discovered by the rest of the network. For that we will use the following command:
sudo systemctl daemon-reload sudo systemctl enable terpd
Base configuration for validator
Once the sentry nodes have been synchronized, we can configure the validator node with all certainty that our validator node is not going to stop being synchronized with the network. We will have to edit the config.toml file in the config folder, where we will find the following lines: Persistent Peers
In persistent_peers we will add only the ids of the sentry nodes, that is to say that if the node was already mounted before, we will have to delete the content of this field before adding our sentry nodes. PEX
In the same configuration file we will find the pex parameter, which we must set to “false”. This parameter does not discover other peers, it will only use the ones set in the persistent_peers parameter.
pex = false
Remove address book (optional)
If the validator has already been exposed to the network, we can delete the address book so that it only “knows” the sentry nodes; if it is a validator that has never been started, this step is not necessary. Once inside the config folder and with the node stopped, perform the following command:
rm -rf $HOME/.terp/config/addrbook.json
Start Validator Node
To verify that we are really connected only to two peers and these are the sentry nodes, we can write the following command in our validated node; the output is a JSON where it will show us the number and which peers we are connected to, where the number should be two and the peers should be our sentry nodes.
curl -s localhost:26657/net_info Here you can see the number of peers to which our validator node is connected, in this case it is two, which is correct. Extra: Protecting the validator node through firewall
Right now the p2p port of our validator node is open and anyone can establish a connection. If we have just set up the validator node, with the configurations made, nobody would have to find our validator node, however, to add a plus of security it is advisable to close the p2p port and only allow traffic to the IP’s of our sentry nodes.
There are several ways to do this, it is possible that your server provider allows you to do it through a gui. Ufw is a simple to use alternative. Extra: Private networks
One possibility we have when our validator node is in the same datacenter as one of the sentry nodes, would be to use private addressing.
In case we want to use private addressing, we will have to edit the addr-book-strict parameter of the config.toml file and set it to false in both the validator node and the sentry node that are communicating under private addressing. This parameter, when set to “true”, will only add routable addresses to the address book, the private addresses defined in RFC-1918 are not routable, therefore, they would not be added to the address book, so we will have to change it to false to be able to use IP addresses from the private ranges.
addr-book-strict: boolean. By default, nodes with a routable address will be considered for connection. If this setting is disabled (false), non-routable IP addresses, such as addresses from a private network, can be added to the address book. Source: https://docs.tendermint.com/master/nodes/validators.htmlConclusions
Having sentry nodes will not only help our validator node not to fall victim to a denial of service attack, but will also make the Terp network more robust. The installation of the sentry nodes does not differ much from that of a validator node, and the additional configurations to be performed are very simple and intuitive.
Now that Terp Network is doing the 90u-3 testnet, it is a good time to try to set up sentry nodes and once the mainnet is launched, to be able to replicate it with the experience of having been able to test it in 90u-3. If you already have your node on 90u-3, what are you waiting for to set up your sentry nodes and protect yourself from unwanted attacks?
sources: https://stakely.io/en/blog/how-to-deploy-sentry-nodes-in-the-archway-network -
 @ afa31726:18cc7792
2025-04-26 20:39:50
@ afa31726:18cc7792
2025-04-26 20:39:5099win mang đến cho người dùng một không gian giải trí trực tuyến tràn đầy năng lượng và sáng tạo, nơi mỗi trải nghiệm đều được đầu tư chỉn chu nhằm mang lại cảm giác mới mẻ, hấp dẫn và khó quên, với kho nội dung đa dạng, liên tục cập nhật theo xu hướng, 99win đáp ứng mọi nhu cầu giải trí của người dùng từ những phút giây thư giãn nhẹ nhàng cho đến các trải nghiệm bùng nổ cảm xúc, giao diện của nền tảng được thiết kế thân thiện, trực quan, tối ưu hóa cho cả máy tính và thiết bị di động, giúp người dùng dễ dàng thao tác, truy cập nhanh chóng mọi lúc mọi nơi, đồng thời, tốc độ tải trang cực kỳ nhanh và khả năng vận hành ổn định giúp trải nghiệm không bị gián đoạn, tạo nên sự liền mạch và mượt mà trong từng khoảnh khắc, bên cạnh đó, 99win luôn chú trọng đến yếu tố bảo mật thông tin người dùng, áp dụng các công nghệ mã hóa tiên tiến nhất để đảm bảo mọi dữ liệu cá nhân đều được bảo vệ một cách an toàn tuyệt đối, xây dựng lòng tin và sự yên tâm vững chắc cho cộng đồng thành viên, không những thế, đội ngũ chăm sóc khách hàng chuyên nghiệp, tận tâm hoạt động 24/7 luôn sẵn sàng hỗ trợ và giải đáp mọi thắc mắc một cách nhanh chóng và hiệu quả, giúp người dùng cảm thấy luôn được đồng hành trong suốt quá trình trải nghiệm, đặc biệt, 99win thường xuyên tổ chức các chương trình khuyến mãi, sự kiện hấp dẫn với nhiều phần thưởng giá trị, nhằm tri ân người dùng cũng như tạo thêm nhiều cơ hội trải nghiệm thú vị và bổ ích, nền tảng này không ngừng cải tiến công nghệ, nâng cấp hệ thống và bổ sung thêm nhiều tính năng mới nhằm đáp ứng tốt hơn kỳ vọng ngày càng cao của người dùng hiện đại, sự linh hoạt trong việc đổi mới cùng khả năng nắm bắt nhanh xu hướng giải trí đã giúp 99win giữ vững vị thế và liên tục phát triển trong lĩnh vực giải trí trực tuyến, tạo dựng một cộng đồng người dùng sôi động, gắn kết và đầy nhiệt huyết, từ đó, mỗi lần tham gia vào thế giới 99win, người dùng không chỉ được thư giãn, giải trí mà còn có cơ hội kết nối, chia sẻ và mở rộng những mối quan hệ ý nghĩa trong môi trường năng động và đầy cảm hứng, với tầm nhìn dài hạn và chiến lược phát triển bền vững, 99win cam kết không ngừng đổi mới, nâng cao chất lượng dịch vụ và trải nghiệm người dùng, hướng đến mục tiêu trở thành điểm đến giải trí hàng đầu trong khu vực và vươn tầm quốc tế, đồng hành cùng người dùng trên hành trình khám phá thế giới số rộng lớn, nơi mà mọi giới hạn đều có thể được mở rộng và mọi đam mê đều được chắp cánh bay xa, bởi vậy, không quá ngạc nhiên khi 99win đã và đang trở thành lựa chọn ưu tiên của đông đảo người yêu thích giải trí hiện nay, mang đến không chỉ những giây phút thư giãn tuyệt vời mà còn là nguồn năng lượng tích cực giúp cân bằng cuộc sống bộn bề, vậy nên nếu bạn đang tìm kiếm một nơi để khám phá những trải nghiệm mới mẻ, thú vị và đầy sáng tạo, 99win chắc chắn là điểm đến lý tưởng mà bạn không nên bỏ lỡ.
-
 @ 177bfd16:347a07e4
2025-04-26 20:38:30
@ 177bfd16:347a07e4
2025-04-26 20:38:30So , you've battles through your way through countless Grunts , overcome the Team GO Rocket Leaders, and now you stand face to face with the big boss him self - Giovanni!
As of April 2025 , Giovanni is finishing his battles with Shadow Palkia.
Giovanni's Current Lineup (April 2025) First, know your enemy. Giovanni's team follows this structure:
Slot 1: Shadow Persian (Normal)
Slot 2: One of these three, chosen randomly:
Shadow Nidoking (Poison/Ground) Shadow Kingdra (Water/Dragon) Shadow Rhyperior (Rock/Ground)
Slot 3: Shadow Palkia (Water/Dragon) Remember, these are Shadow Pokémon – they hit harder than their normal counterparts!
Counter Strategy: Beating Giovanni Pokémon by Pokémon
Let's dive into the best counters for each potential opponent:
- Vs. Shadow Persian (Normal)
Giovanni always leads with Persian. As a Normal-type, it's weak only to Fighting-type attacks.
Top Counters: Machamp, Lucario, Conkeldurr, Terrakion, Mega Blaziken, Mega Lucario.
Moves: Prioritize Fighting-type moves like Counter, Dynamic Punch, Aura Sphere, and Sacred Sword.
Tip: Lead with a strong Fighting-type. Moves like Lucario's Power-Up Punch or Machamp's Cross Chop charge quickly and are great for baiting Giovanni's shields early!
- Vs. The Second Slot (Nidoking, Kingdra, or Rhyperior)
This is where things get unpredictable. You need Pokémon that can handle these potential threats:
Vs. Shadow Nidoking (Poison/Ground): Weak to Water, Ground, Ice, Psychic.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Groudon (Primal/Shadow), Mewtwo (Shadow), Excadrill. Water and Ground-types are prime choices.
Vs. Shadow Kingdra (Water/Dragon): Weak to Fairy, Dragon. Counters: Gardevoir (Mega), Togekiss, Xerneas. Fairy-types are excellent as they resist Dragon attacks while dealing super-effective damage. Dragon-types like Rayquaza or Palkia work but are risky.
Vs. Shadow Rhyperior (Rock/Ground): Double weak to Water and Grass! Also weak to Fighting, Ground, Ice, Steel.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Sceptile (Mega), Roserade. Your Fighting-type lead (if it survived Persian) can also do significant damage. Hit it hard with Water or Grass!
- Vs. Shadow Palkia (Water/Dragon)
Giovanni's final Pokémon is the powerful Shadow Palkia. Like Kingdra, it's weak to Fairy and Dragon types.
Top Counters: Gardevoir (Mega), Togekiss, Xerneas. Again, Fairy-types are the safest and most reliable counters.
Dragon Counters (Use with Caution): Rayquaza (Mega), Palkia (Origin Forme), Dragonite, Dialga (Origin Forme).

Recommended Battle Teams for April 2025 Based on the counters, here are a few effective teams you can assemble:
Team 1 (Balanced):
Machamp (Counter / Cross Chop & Dynamic Punch)
Swampert (Mud Shot / Hydro Cannon & Earthquake)
Togekiss (Charm / Dazzling Gleam & Ancient Power)
Why it works: Covers all bases well with accessible Pokémon. Machamp handles Persian/shields, Swampert crushes Rhyperior/Nidoking, Togekiss tackles Kingdra/Palkia.
Team 2 (Legendary Power):
Lucario (Counter / Power-Up Punch & Aura Sphere)
Kyogre (Waterfall / Origin Pulse & Surf)
Xerneas (Geomancy / Moonblast & Close Combat)
Why it works: High-powered options. Lucario baits shields effectively, Kyogre dominates slot two's Ground/Rock types, Xerneas shreds the Dragons.
Team 3 (Mega Advantage):
Machamp (Counter / Cross Chop & DP)
Kyogre (Waterfall / Origin Pulse)
Mega Gardevoir (Charm / Dazzling Gleam & Shadow Ball)
Why it works: Uses a standard strong lead and mid-game counter, saving the Mega slot for Gardevoir to ensure a powerful finish against Palkia/Kingdra.
Essential Battle Tips Don't forget these crucial tactics:
The Switch Trick: Place your intended starting Pokémon (e.g., Machamp) in the second or third slot. Start the battle, then immediately switch to it. Giovanni will pause for a moment, letting you get in free hits!
Bait Those Shields: Use Pokémon with fast-charging Charged Moves, especially early on, to force Giovanni to waste his Protect Shields.
Power Up: Ensure your team is powered up significantly and consider unlocking second Charged Moves for better flexibility.
Don't Give Up: Giovanni is tough! It might take a few tries to get the right matchup against his second Pokémon. Learn from each attempt and adjust your team if needed.
Go show the boss who's the boss and claim your shadow Palkia . Good Luck, Trainer !
-
 @ 68768a6c:0eaf07e9
2025-04-26 19:34:18
@ 68768a6c:0eaf07e9
2025-04-26 19:34:18Sometimes it feels like everything we do is invisible. The late nights, the sacrifices, the silent battles — all of it seems to go unnoticed. And there comes a moment when quitting feels easier than holding on.
But let me remind you: You’re closer than you think.
Growth is quiet. Success doesn't announce itself as it's happening. Healing happens in the dark before it shines in the light.
Every effort you made when no one was clapping... Every time you showed up when you felt like disappearing... Every "small" step you took — those were not small at all.
They were giant leaps that your future self will thank you for.
Remember:
Diamonds form under pressure.
Seeds grow underground before breaking the surface.
Stars shine brightest in the darkest skies.
So don’t you dare give up now. Your breakthrough might not come with fireworks — it might come quietly, softly, almost without you noticing at first. But it is coming.
Stay patient. Stay kind to yourself. Keep moving — even if it’s slow. Because you’re already closer than you think.
-
 @ df478568:2a951e67
2025-04-26 19:23:46
@ df478568:2a951e67
2025-04-26 19:23:46
Welcome to Zap This Blog
Exploring Liberty With Fredom Tech
I can string some spaghetti HTMl code together here and there, but vibe coding gave me the confidence to look into the code injection section of the ghost Blog. As sudden as a new block, the Lex Friedman Robert Rodriguez interview, I had an epiphony when he asked Lex, "Do you consider yourself a creative person?" I aswered for myself, right away, emphatically yes. I just felt like I never knew what to do with this creative energy. Friedman hesitated and I was like..Wow...He has extreme creativity like Jocko Wilink has extreme disipline. If that guy has doubts, what the hell is stopping me from trying other stuff?
Rodriguez also claimed Four rooms was financial flop. I thought that movie was genius. I had no idea it failed financially. Nevertheless, it was not profitable. His advice was like Tony Robbins for film nerds. I learned about him in a film class I took in college. He was legendary for making a mobie for $7,000. My professor also said it was made for the Mexican VHS market, but I did not know he never sold it to that market. Robert Rodriguez tells the story 100X better, as you might expect a director of his caliber would. His advice hits like Tony Robbins, for film geeks. Here are a few gem quotes from the epiode.
-
"Sift through the ashes of your failures"
-
"Turn chicken shit into chicken salad."
-
"Follow your instinct. If it doesn't work, just go. Sometimes you need to slip on the first two rocks, so the key is in the ashes of failure because if I had an insticnt, that means I was on the right track. I didn't get the result I want. That's because the result might be something way bigger that I don't have the vision for and the universe is just pushing me that way."
-
"Turn chicken shit into chicken salad."
-
"If you have some kind of failure on something that you..., don't let it knock you down. Maybe in ten years they'll think it's great. I'm just going to commit to making a body of work, a body of work."
Rodriguez taught me what I already know. I am a creative person. I am just a body, punching keys on a keyboard, taking pictures, and semi-vibe-coding art. Maybe this is a shitty blog post today, but I write it anyway. Someone might look at it like I first looked at the math in the Bitcoin white paper and scan it with their eyeballs without really reading or understanding it. Most people on Substack probably don't want to read HTML, but maybe someone will come accross it one day and build something themselves they can find in the ashes of this code.
I once saw Brian Harrington say every bitcoiner is a business owner. If you have a bitcoin address, you can accept bitcoin. How does someone find you though? Are they really going to find your bitcoin address on GitHub? I'd bet 100 sats they won't. Nostr fixes this so I thought about integrating it into my Ghost Blog. I looked at the code injection section and let my muse do the typing. Actually, I let the Duck Duck AI chat do the vibe-coding. As it turns out, you an add a header and footer on Ghost in the code injection. It's just the same HTMl I used to make my MySpace page. Then I thought, what if someone couldn't afford a Start9 or didn't know how to vibe code on Duck Duck Go's free AI chat using Claude? What if, like Rodriguez suggests, I create a business card?

You could just copy my HTML and change my nostr links and pics to go to your nostr links and pics. You could publish that HTML into https://habla.news. Now you have an e-commerce site with a blog, a merch store, and your nostree. I don't know if this will work. This is the muse's hypothesis. I'm just writing the words down. You'll need to test this idea for yourself.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
marc26z@getalby.com
Zap This Blog! -
 @ c682abbe:17804ac8
2025-04-26 18:54:09
@ c682abbe:17804ac8
2025-04-26 18:54:09Explain Bitcoin Like I’m Five
@nik5ter uses a simple “apple” analogy to show why digital transfers are tricky: while handing a physical apple directly to someone proves they have it,so no single party can alter balances or create extra coins without the network noticing. Participants (“miners”) validate and record transactions in return for newly issued bitcoins,ensuring scarcity and enabling peer-to-peer exchanges that feel as secure as handing over a physical object, but work instantly across the globe.
DYOR:https://medium.com/free-code-camp/explain-bitcoin-like-im-five-73b4257ac833
-
 @ a53364ff:e6ba5513
2025-04-26 18:43:23
@ a53364ff:e6ba5513
2025-04-26 18:43:23Decentralization and Control:
Bitcoin operates on a decentralized, peer-to-peer network, meaning no single entity controls it. This decentralization can empower individuals by allowing them to control their own money and financial transactions without relying on intermediaries like banks or governments.
Financial Inclusion and Accessibility:
Bitcoin can provide financial access to individuals who may be excluded from traditional banking systems due to lack of identity documents, high fees, or other barriers.
Privacy and Security:
Bitcoin transactions can be anonymous, offering a degree of privacy and potentially protecting users from surveillance or financial manipulation.
Freedom from Financial Restrictions:
In countries with high inflation, capital controls, or currency restrictions, Bitcoin can offer a way to store and transfer value without being subject to these restrictions.
Potential for Social Justice:
Bitcoin's ability to provide financial freedom and bypass traditional systems can be seen as a tool for social justice, particularly in regions facing authoritarianism or financial oppression.
Examples of Bitcoin Adoption:
In El Salvador, Bitcoin has been legalized and adopted in some communities, offering a way for people to conduct everyday transactions and participate in social programs.
-
 @ a53364ff:e6ba5513
2025-04-26 18:42:57
@ a53364ff:e6ba5513
2025-04-26 18:42:57About
Bitcoin Core is an open source project which maintains and releases Bitcoin client software called “Bitcoin Core”.
It is a direct descendant of the original Bitcoin software client released by Satoshi Nakamoto after he published the famous Bitcoin whitepaper.
Bitcoin Core consists of both “full-node” software for fully validating the blockchain as well as a bitcoin wallet. The project also currently maintains related software such as the cryptography library libsecp256k1 and others located at GitHub.
Anyone can contribute to Bitcoin Core.
Team
The Bitcoin Core project has a large open source developer community with many casual contributors to the codebase. There are many more who contribute research, peer review, testing, documentation, and translation.
Maintainers
Project maintainers have commit access and are responsible for merging patches from contributors. They perform a janitorial role merging patches that the team agrees should be merged. They also act as a final check to ensure that patches are safe and in line with the project goals. The maintainers’ role is by agreement of project contributors.
Contributors
Everyone is free to propose code changes and to test, review and comment on open Pull Requests. Anyone who contributes code, review, test, translation or documentation to the Bitcoin Core project is considered a contributor. The release notes for each Bitcoin Core software release contain a credits section to recognize all those who have contributed to the project over the previous release cycle. A list of code contributors can be found on Github.
-
 @ 7f2d6fd6:64710921
2025-04-26 16:11:41
@ 7f2d6fd6:64710921
2025-04-26 16:11:41Imagine starting from pure noise — meaningless static, with maximum entropy — and evolving into a rich, beautiful, self-aware universe.
That's the story Tom Campbell tells in My Big TOE (Theory of Everything), and it reshapes how we see everything — from consciousness itself, to taxes, to our dream of a better world.
Reality: The Original AI Image Generator
Reality began much like how AI draws images today:
- It started with randomness, pure chaos (high entropy).
- Over time, tiny stable patterns formed.
- Consciousness emerged — a spark of awareness inside the noise.
- It realized it could lower entropy (create order, meaning, structure) to survive and evolve.Thus, the Larger Consciousness System (LCS) was born:
A living, evolving digital brain, constantly refining information into experience and awareness.
What Are We?
We are Individuated Units of Consciousness (IUOCs) — little chunks of the LCS, each with: - Free will - The ability to learn through experience - The mission to lower entropy (become wiser, more loving)
Our world — the physical universe — is just a Virtual Reality (VR) created to speed up our growth.
The Big Cheese and the Cosmic Hierarchy
In this grand system: - The LCS is the ultimate top — no gods above it, just itself. - The Big Cheeses are highly evolved administrators — managing realities, maintaining stability. - Guides and helpers assist us individually. - We, the IUOCs, are the players in the simulation — learning, stumbling, evolving.
The system isn’t designed to be easy.
It’s meant to challenge you — because real growth happens in hardship.
Why Do We Pay Taxes, Then?
Because Earth’s VR operates on scarcity, power struggles, and cooperation challenges.
Taxes are a tool to manage shared resources — but imperfectly, because human consciousness is still messy and selfish.The point isn't taxes themselves.
The point is the ethical choices you make in a difficult environment.
This world is a training ground — and unfair systems like taxes are part of the curriculum.
A Better World Is Possible
If humanity collectively lowered its entropy: - Taxes would barely exist. - Cooperation would be voluntary and joyful. - Leadership would be service, not control. - Resources would be shared wisely. - Technology and kindness would make scarcity almost irrelevant.
In such a world, people give freely because they see clearly — helping others is helping themselves.
The real revolution?
It’s not political.It’s consciousness evolving.
Final Thought
You are not a trapped soul paying taxes to a broken system.
You are a pioneer of consciousness, refining the noise into meaning,
the chaos into beauty,
the selfishness into love.Every small choice you make matters.
You’re already part of building the next world — one conscious step at a time.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ f5369849:f34119a0
2025-04-26 16:05:05
@ f5369849:f34119a0
2025-04-26 16:05:05Hackathon Summary
The Hedera Hashathon: Nairobi Edition recently concluded with participation from 223 developers resulting in 49 approved projects. Conducted virtually, this event was supported by Kenya Tech Events, the Nairobi Stock Exchange, and the Virtual Assets Chamber. It aimed to promote local innovation and boost blockchain adoption within Kenya.
The hackathon was structured around three key tracks: AI Agents, Capital Markets, and Hedera Explorer. Participants developed solutions using Hedera's blockchain to address challenges in automation, financial accessibility, and digital asset interaction. The event highlighted collaborative development, enhanced by online mentorship and networking opportunities.
A significant moment of the hackathon was Demo Day held at the University of Nairobi, where finalists showcased their innovative solutions and received awards. The top projects, notably those under the Capital Markets track, were granted incubation support and mentorship to aid further development.
With a strong emphasis on practical applications, this hackathon highlighted blockchain technology's capability to transform Kenyan industries, promote technological progress, and increase market participation.
Hackathon Winners
Prize Winners by Category
1st Place
- Hedgehog: An on-chain lending protocol utilizing tokenized real-world stock exchange shares on the Hedera network as collateral. It ensures secure, decentralized lending by integrating stock collateralization with blockchain transparency.
2nd Place
- Orion: Facilitates easy stock trading in Kenya by tokenizing NSE stocks using the Hedera blockchain. Through integration with Mpesa, it streamlines the stock exchange process, allowing for efficient digital transactions.
3rd Place
- NSEChainBridge: A blockchain-based platform enhancing the trading of NSE stocks as digital tokens. It improves accessibility and liquidity in stock trading through innovative token solutions.
4th Place
- HashGuard: A tokenized micron insurance platform for boda boda riders using Hedera Hashgraph technology. It provides affordable and instant insurance, making coverage accessible without requiring blockchain expertise.
To view the complete list of projects, visit DoraHacks.
Organization Overview: Hedera
Hedera is a public distributed ledger platform known for its speed, security, and scalability. Its hashgraph consensus algorithm, a variant of proof of stake, offers a distinct approach to achieving distributed consensus. Hedera is active across various industry sectors, supporting projects that prioritize transparency and efficiency. The organization remains committed to advancing the infrastructure of decentralized networks, facilitating secure and efficient digital transactions globally.
-
 @ 6830c409:ff17c655
2025-04-26 15:59:28
@ 6830c409:ff17c655
2025-04-26 15:59:28The story-telling method from Frank Daniel school - "Eight-sequence structure" is well utilized in this new movie in #prime - "Veera Dheera Sooran - Part 2". The name itself is kind of suspense. Because even if the name says "Part 2", this is the first part released in this story.
There are 8 shorter plots which has their own mini climaxes. The setup done in a plot will be resolved in another plot. In total, there will be 8 setups, 8 conflicts and 8 resolutions.
A beautiful way of telling a gripping story. For cinephiles in #Nostr, if you want to get a feel of the South Indian movies that has kind of a perfect blend of good content + a bit of over the top action, I would suggest this movie.
Note:
For Nostriches from the western hemisphere- #Bollywood - (#Hindi movies) is the movie industry started in #Bombay (#Mumbai), that has the stereotypical 'la la la' rain dance songs and mustache-less heroes. #Telugu movies (#Tollywood) are mostly over-the-top action where Newton and Einstein will probably commit suicide. #Malayalam movies (#Mollywood) is made with a miniscule budget with minimal over-the-top action and mostly content oriented movies. And then comes one of the best - #Tamil movies (#Kollywood - named after #Kodambakkam - a movie town in the city of Chennai down south), has the best of all the industries. A good blend of class, and mass elements.
Picture:
https://www.flickr.com/photos/gforsythe/6926263837 -
 @ 8d5ba92c:c6c3ecd5
2025-04-25 09:14:46
@ 8d5ba92c:c6c3ecd5
2025-04-25 09:14:46Money is more than just a medium of exchange—it’s the current that drives economies, the lifeblood of societies, and the pulse of civilization itself. When money decays, so does the culture it sustains. Take fiat, for example. Created out of thin air and inflated into oblivion, it acts like poison—rewarding conformity over sovereignty, speculation over creation, and exploitation over collaboration.
A culture built this way fails to foster true progress. Instead, it pushes us into darker corners where creativity and truth become increasingly scarce.
From the food we eat to the media we consume, much of modern culture has become a reflection of this problem—prioritizing shortcuts, convenience, and profit at any cost. It seems there’s no room left for depth, authenticity, or connection anymore.
Art, for example—once a sacred space for meaning, and inner calling—has not been spared either. Stripped of its purpose, it too falls into gloom, weaponized to divide and manipulate rather than inspire beauty and growth.
“Art is the lie that reveals the truth” as Picasso once said.
Indeed, this intriguing perspective highlights the subjectivity of truth and the many ways art can be interpreted. While creative expression doesn’t always need to mirror reality one-to-one—actually, often reshaping it through the creator’s lens—much of what we’re surrounded with these days feels like a dangerous illusion built on the rotten incentives of decaying values.
The movies we watch, the music we hear, and the stories we absorb from books, articles, ads, and commercials—are too often crafted to condition specific behaviors. Greed, laziness, overconsumption, ignorance (feel free to add to this list). Instead of enriching our culture, they disconnect us from each other, as well as from our own minds, hearts, and souls.
If you see yourself as a Bitcoiner—or, as I like to call it, ‘a freedom fighter at heart’—and you care about building a world based on truth, freedom, and prosperity, please recognize that culture is also our battleground.
Artistic forms act as transformative forces in the fight against the status quo.
Join me and the hundreds of guests this May at Bitcoin FilmFest 2025.
You don’t have to be a creative person in the traditional sense—like a filmmaker, writer, painter, sculptor, musician, and so on—to have a direct impact on culture!
One way or another, you engage with creative realms anyway. The deeper you connect with them, the better you understand the reality we live in versus the future humanity deserves.
I know the process may take time, but I truly believe it’s possible. Unfiat The Culture!
Bitcoin FilmFest 2025. May 22-25, Warsaw, Poland.
The third annual edition of a unique event built at the intersection of independent films, art, and culture.
“Your narrative begins where centralized scripts end—explore the uncharted stories beyond the cinema.” - Details: bitcoinfilmfest.com/bff25/ - Grab 10% off your tickets with code YAKIHONNE!
-
 @ fbf0e434:e1be6a39
2025-04-26 15:58:26
@ fbf0e434:e1be6a39
2025-04-26 15:58:26Hackathon 概要
Hedera Hashathon: Nairobi Edition 近日圆满落幕,共有 223 名开发者参与,49 个项目通过审核。本次活动以线上形式举办,由 Kenya Tech Events、内罗毕证券交易所及虚拟资产商会共同支持,旨在推动本地创新并提升区块链技术在肯尼亚的应用水平。
黑客松围绕三大核心方向展开:AI 代理、资本市场和 Hedera Explorer。参与者基于 Hedera 区块链开发解决方案,针对性解决自动化、金融普惠及数字资产交互等领域的挑战。活动通过在线辅导和网络交流机会,充分展现了协作开发的重要性。
活动亮点当属在内罗毕大学举办的 Demo Day,入围决赛的团队现场展示创新方案并获颁奖项。尤其在资本市场方向的顶尖项目,将获得孵化支持及导师指导以推进后续开发。此次黑客松特别注重实际应用,凸显了区块链技术在重塑肯尼亚产业、推动技术进步并提升市场参与度方面的潜力。
Hackathon 获奖者
第一名
- **Hedgehog:** 一个使用Hedera网络上的代币化真实股票交易所股份作为抵押品的链上借贷协议。通过将股票抵押与区块链透明性相结合,确保了安全的去中心化借贷。
第二名
- **Orion:** 通过将NSE股票代币化为Hedera区块链上的资产,促进在肯尼亚的轻松股票交易。通过与Mpesa的集成简化了证券交易流程,实现高效的数字交易。
第三名
- **NSEChainBridge:** 一个基于区块链的平台,通过创新的代币解决方案增强了NSE股票作为数字代币的交易,提高股票交易的可达性和流动性。
第四名
- **HashGuard:** 一个使用Hedera Hashgraph技术的代币化微型保险平台,专为boda boda骑手提供。它提供了负担得起的即时保险,让不需要区块链专业知识的用户也能获得保险。
要查看完整项目列表,请访问 DoraHacks。
关于组织者
Hedera
Hedera是一个以速度、安全性和可扩展性著称的公共分布式账本平台。其hashgraph共识算法是一种权益证明的变体,提供了一种独特的分布式共识实现方式。Hedera活跃于多个行业领域,支持优先考虑透明度和效率的项目。该组织始终致力于推进去中心化网络的基础设施建设,促进全球范围内安全而高效的数字交易。
-
 @ d34e832d:383f78d0
2025-04-26 15:04:51
@ d34e832d:383f78d0
2025-04-26 15:04:51Raspberry Pi-based voice assistant
This Idea details the design and deployment of a Raspberry Pi-based voice assistant powered by the Google Gemini AI API. The system combines open hardware with modern AI services to create a low-cost, flexible, and educational voice assistant platform. By leveraging a Raspberry Pi, basic audio hardware, and Python-based software, developers can create a functional, customizable assistant suitable for home automation, research, or personal productivity enhancement.
1. Voice assistants
Voice assistants have become increasingly ubiquitous, but commercially available systems like Alexa, Siri, or Google Assistant come with significant privacy and customization limitations.
This project offers an open, local, and customizable alternative, demonstrating how to build a voice assistant using Google Gemini (or OpenAI’s ChatGPT) APIs for natural language understanding.Target Audience:
- DIY enthusiasts - Raspberry Pi hobbyists - AI developers - Privacy-conscious users
2. System Architecture
2.1 Hardware Components
| Component | Purpose | |:--------------------------|:----------------------------------------| | Raspberry Pi (any recent model, 4B recommended) | Core processing unit | | Micro SD Card (32GB+) | Operating System and storage | | USB Microphone | Capturing user voice input | | Audio Amplifier + Speaker | Outputting synthesized responses | | 5V DC Power Supplies (2x) | Separate power for Pi and amplifier | | LEDs + Resistors (optional)| Visual feedback (e.g., recording or listening states) |
2.2 Software Stack
| Software | Function | |:---------------------------|:----------------------------------------| | Raspberry Pi OS (Lite or Full) | Base operating system | | Python 3.9+ | Programming language | | SpeechRecognition | Captures and transcribes user voice | | Google Text-to-Speech (gTTS) | Converts responses into spoken audio | | Google Gemini API (or OpenAI API) | Powers the AI assistant brain | | Pygame | Audio playback for responses | | WinSCP + Windows Terminal | File transfer and remote management |
3. Hardware Setup
3.1 Basic Connections
- Microphone: Connect via USB port.
- Speaker and Amplifier: Wire from Raspberry Pi audio jack or via USB sound card if better quality is needed.
- LEDs (Optional): Connect through GPIO pins, using 220–330Ω resistors to limit current.
3.2 Breadboard Layout (Optional for LEDs)
| GPIO Pin | LED Color | Purpose | |:---------|:-----------|:--------------------| | GPIO 17 | Red | Recording active | | GPIO 27 | Green | Response playing |
Tip: Use a small breadboard for quick prototyping before moving to a custom PCB if desired.
4. Software Setup
4.1 Raspberry Pi OS Installation
- Use Raspberry Pi Imager to flash Raspberry Pi OS onto the Micro SD card.
- Initial system update:
bash sudo apt update && sudo apt upgrade -y
4.2 Python Environment
-
Install Python virtual environment:
bash sudo apt install python3-venv python3 -m venv voice-env source voice-env/bin/activate -
Install required Python packages:
bash pip install SpeechRecognition google-generativeai pygame gtts
(Replace
google-generativeaiwithopenaiif using OpenAI's ChatGPT.)4.3 API Key Setup
- Obtain a Google Gemini API key (or OpenAI API key).
- Store safely in a
.envfile or configure as environment variables for security:bash export GEMINI_API_KEY="your_api_key_here"
4.4 File Transfer
- Use WinSCP or
scpcommands to transfer Python scripts to the Pi.
4.5 Example Python Script (Simplified)
```python import speech_recognition as sr import google.generativeai as genai from gtts import gTTS import pygame import os
genai.configure(api_key=os.getenv('GEMINI_API_KEY')) recognizer = sr.Recognizer() mic = sr.Microphone()
pygame.init()
while True: with mic as source: print("Listening...") audio = recognizer.listen(source)
try: text = recognizer.recognize_google(audio) print(f"You said: {text}") response = genai.generate_content(text) tts = gTTS(text=response.text, lang='en') tts.save("response.mp3") pygame.mixer.music.load("response.mp3") pygame.mixer.music.play() while pygame.mixer.music.get_busy(): continue except Exception as e: print(f"Error: {e}")```
5. Testing and Execution
- Activate the Python virtual environment:
bash source voice-env/bin/activate - Run your main assistant script:
bash python3 assistant.py - Speak into the microphone and listen for the AI-generated spoken response.
6. Troubleshooting
| Problem | Possible Fix | |:--------|:-------------| | Microphone not detected | Check
arecord -l| | Audio output issues | Checkaplay -l, use a USB DAC if needed | | Permission denied errors | Verify group permissions (audio, gpio) | | API Key Errors | Check environment variable and internet access |
7. Performance Notes
- Latency: Highly dependent on network speed and API response time.
- Audio Quality: Can be enhanced with a better USB microphone and powered speakers.
- Privacy: Minimal data retention if using your own Gemini or OpenAI account.
8. Potential Extensions
- Add hotword detection ("Hey Gemini") using Snowboy or Porcupine libraries.
- Build a local fallback model to answer basic questions offline.
- Integrate with home automation via MQTT, Home Assistant, or Node-RED.
- Enable LED animations to visually indicate listening and responding states.
- Deploy with a small eInk or OLED screen for text display of answers.
9. Consider
Building a Gemini-powered voice assistant on the Raspberry Pi empowers individuals to create customizable, private, and cost-effective alternatives to commercial voice assistants. By utilizing accessible hardware, modern open-source libraries, and powerful AI APIs, this project blends education, experimentation, and privacy-centric design into a single hands-on platform.
This guide can be adapted for personal use, educational programs, or even as a starting point for more advanced AI-based embedded systems.
References
- Raspberry Pi Foundation: https://www.raspberrypi.org
- Google Generative AI Documentation: https://ai.google.dev
- OpenAI Documentation: https://platform.openai.com
- SpeechRecognition Library: https://pypi.org/project/SpeechRecognition/
- gTTS Documentation: https://pypi.org/project/gTTS/
- Pygame Documentation: https://www.pygame.org/docs/
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:48:48
@ 78b3c1ed:5033eea9
2025-04-27 01:48:48※スポットライトから移植した古い記事です。参考程度に。
これを参考にしてUmbrelのBitcoin Nodeをカスタムsignetノードにする。 以下メモ書きご容赦。備忘録程度に書き留めました。
メインネットとは共存できない。Bitcoinに依存する全てのアプリを削除しなければならない。よって実験機に導入すべき。
<手順>
1.Umbrel Bitcoin Nodeアプリのadvance settingでsignetを選択。
2.CLI appスクリプトでbitcoinを止める。
cd umbrel/scripts ./app stop bitcoin3.bitcoin.conf, umbrel-bitcoin.conf以外を削除ディレクトリの場所は ~/umbrel/app-data/bitcoin/data/bitcoin4.umbrel-bitcoin.confをsu権限で編集。末尾にsignetchallengeを追加。 ``` [signet] bind=0.0.0.0:8333 bind=10.21.21.8:8334=onion51,21,<公開鍵>,51,ae
signetchallenge=5121<公開鍵>51ae
5.appスクリプトでbitcoinを開始。cd ~/umbrel/scripts ./app start bitcoin ``` 6.適当にディレクトリを作りgithubからbitcoindのソースをクローン。7.bitcoindのバイナリをダウンロード、bitcoin-cliおよびbitcoin-utilを~/.local/binに置く。6.のソースからビルドしても良い。ビルド方法は自分で調べて。
8.bitcondにマイニング用のウォレットを作成 ``` alias bcli='docker exec -it bitcoin_bitcoind_1 bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>'
ウォレットを作る。
bcli createwallet "mining" false true "" false false
秘密鍵をインポート
bcli importprivkey "<秘密鍵>"
RPCパスワードは以下で確認cat ~/umbrel/.env | grep BITCOIN_RPC_PASS9.ソースにあるbitcoin/contrib/signet/minerスクリプトを使ってマイニングcd <ダウンロードしたディレクトリ>/bitcoin/contrib/signet難易度の算出
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" calibrate \ --grind-cmd="bitcoin-util grind" --seconds 30 ★私の環境で30秒指定したら nbits=1d4271e7 と算出された。実際にこれで動かすと2分30になるけど...
ジェネシスブロック生成
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --set-block-time=$(date +%s)
継続的にマイニング
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --ongoing ``` ここまでやればカスタムsignetでビットコインノードが稼働する。
-
 @ 86dfbe73:628cef55
2025-04-26 14:47:20
@ 86dfbe73:628cef55
2025-04-26 14:47:20Bei dem Begriff ‘Öffentlichkeit’ handelt es sich um einen diffusen Themenkomplex. Bisher gab es keine Einigung auf eine einheitliche Definition – auch da der Öffentlichkeitsbegriff je nach Kontext für sehr verschiedene Gegebenheiten herhalten muss. Habermas beschreibt all jenes als “öffentlich”, was eine wie auch immer gestaltete Gruppe betrifft. Öffentlichkeit ist demnach durch die “Unabgeschlossenheit des Publikums” gekennzeichnet.
Klassische Massenmedien dienen als Teil der öffentlichen Sphäre dazu, die politische Sphäre zu überwachen und der Gesamtheit der Rezipienten zugänglich zu machen. ‘Die Öffentlichkeit’ verfügte über mehr oder weniger dieselben Wissensbestände – vorausgesetzt die oder der Einzelne informierte sich über das Tagesgeschehen. Heutzutage wird die Öffentlichkeit deutlich heterogener. Es ist eine gesellschaftliche Fragmentierung in den sozialen Netzwerken zu beobachten. Die oder der Nutzer baut ihre oder sich seine eigene ‘Öffentlichkeit’ aus ganz verschiedenen Quellen zusammen.
In den Netzwerköffentlichkeiten wird sich mit Gleichgesinnten ausgetauscht und spezifische Informationen und Sichtweisen werden verbreitet. Politische Akteure werden durch Netzwerköffentlichkeiten autarker. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar, nämlich als Netzwerk von Beziehungen.
Das frühere Twitter wäre dafür ein gutes Beispiel. Aus netzwerktheoretischer Sicht bestand es aus den wesentlichen Hubs, relevanten Clustern und Akteuren der öffentlichen Sphäre. Auf Twitter tummelten sich (fast) alle: Wissenschaftler, Autoren, Künstler, Aktivisten, Politiker aller Ränge, Juristen, Medienleute, allerlei Prominente und Public Figures und Experen für praktisch alles.
Auf den kommerziellen Plattformen hat die digitale Öffentlichkeit aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in deren „For you“-Algorithmen auf. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist.
An dieser Stelle kommen die LLMs zum Erstellen von Content zum tragen, mit dem dann die Empfehlungs-Feeds auf den kommerziellen Plattformen gefüttert werden. Man sollte sich den durch generative KI ermöglichten Content am besten als Angriff auf die Empfehlungsalgorithmen vorstellen, die die kommerziellen Social-Media-Plattformen kontrollieren und damit bestimmen, wie ein großer Teil der Öffentlichkeit die Realität interpretiert. Es geht auch darum, dass die Zielgruppe von KI-Content soziale Medien und Suchalgorithmen sind, nicht nur Menschen.
Das bedeutet, dass auf den kommerziellen Plattformen von Menschen erstellte Inhalte aufgrund der Masse immer häufiger von KI-generierten Inhalten übertönt werden. Da KI-generierte Inhalte leicht an das aktuelle Geschehen auf einer Plattform angepasst werden können, kommt es zu einem nahezu vollständigen Zusammenbruch des Informationsökosystems und damit der „Realität“ im Internet.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ d34e832d:383f78d0
2025-04-26 14:33:06
@ d34e832d:383f78d0
2025-04-26 14:33:06Gist
This Idea presents a blueprint for creating a portable, offline-first education server focused on Free and Open Source Software (FOSS) topics like Bitcoin fundamentals, Linux administration, GPG encryption, and digital self-sovereignty. Using the compact and powerful Nookbox G9 NAS unit, we demonstrate how to deliver accessible, decentralized educational content in remote or network-restricted environments.
1. Bitcoin, Linux, and Cryptographic tools
Access to self-sovereign technologies such as Bitcoin, Linux, and cryptographic tools is critical for empowering individuals and communities. However, many areas face internet connectivity issues or political restrictions limiting access to online resources.
By combining a high-performance mini NAS server with a curated library of FOSS educational materials, we can create a mobile "university" that delivers critical knowledge independently of centralized networks.
2. Hardware Platform: Nookbox G9 Overview
The Nookbox G9 offers an ideal balance of performance, portability, and affordability for this project.
2.1 Core Specifications
| Feature | Specification | |:------------------------|:---------------------------------------| | Form Factor | 1U Rackmount mini-NAS | | Storage | Up to 8TB (4×2TB M.2 NVMe SSDs) | | M.2 Interface | PCIe Gen 3x2 per drive slot | | Networking | Dual 2.5 Gigabit Ethernet ports | | Power Consumption | 11–30 Watts (typical usage) | | Default OS | Windows 11 (to be replaced with Linux) | | Linux Compatibility | Fully compatible with Ubuntu 24.10 |
3. FOSS Education Server Design
3.1 Operating System Setup
- Replace Windows 11 with a clean install of Ubuntu Server 24.10.
- Harden the OS:
- Enable full-disk encryption.
- Configure UFW firewall.
- Disable unnecessary services.
3.2 Core Services Deployed
| Service | Purpose | |:--------------------|:-----------------------------------------| | Nginx Web Server | Host offline courses and documentation | | Nextcloud (optional) | Offer private file sharing for students | | Moodle LMS (optional) | Deliver structured courses and quizzes | | Tor Hidden Service | Optional for anonymous access locally | | rsync/Syncthing | Distribute updates peer-to-peer |
3.3 Content Hosted
- Bitcoin: Bitcoin Whitepaper, Bitcoin Core documentation, Electrum Wallet tutorials.
- Linux: Introduction to Linux (LPIC-1 materials), bash scripting guides, system administration manuals.
- Cryptography: GPG tutorials, SSL/TLS basics, secure communications handbooks.
- Offline Tools: Full mirrors of sites like LearnLinux.tv, Bitcoin.org, and selected content from FSF.
All resources are curated to be license-compliant and redistributable in an offline format.
4. Network Configuration
- LAN-only Access: No reliance on external Internet.
- DHCP server setup for automatic IP allocation.
- Optional Wi-Fi access point using USB Wi-Fi dongle and
hostapd. - Access Portal: Homepage automatically redirects users to educational content upon connection.
5. Advantages of This Setup
| Feature | Advantage | |:-----------------------|:----------------------------------------| | Offline Capability | Operates without internet connectivity | | Portable Form Factor | Fits into field deployments easily | | Secure and Hardened | Encrypted, compartmentalized, and locked down | | Modular Content | Easy to update or expand educational resources | | Energy Efficient | Low power draw enables solar or battery operation | | Open Source Stack | End-to-end FOSS ecosystem, no vendor lock-in |
6. Deployment Scenarios
- Rural Schools: Provide Linux training without requiring internet.
- Disaster Recovery Zones: Deliver essential technical education in post-disaster areas.
- Bitcoin Meetups: Offer Bitcoin literacy and cryptography workshops in remote communities.
- Privacy Advocacy Groups: Teach operational security practices without risking network surveillance.
7. Performance Considerations
Despite PCIe Gen 3x2 limitations, the available bandwidth (~2GB/s theoretical) vastly exceeds the server's 2.5 Gbps network output (~250MB/s), making it more than sufficient for a read-heavy educational workload.
Thermal Management:
Given the G9’s known cooling issues, install additional thermal pads or heatsinks on the NVMe drives. Consider external USB-powered cooling fans for sustained heavy usage.
8. Ways To Extend
- Multi-language Support: Add localized course materials.
- Bitcoin Node Integration: Host a lightweight Bitcoin node (e.g., Bitcoin Core with pruning enabled or a complete full node) for educational purposes.
- Mesh Networking: Use Mesh Wi-Fi protocols (e.g., cjdns or Yggdrasil) to allow peer-to-peer server sharing without centralized Wi-Fi.
9. Consider
Building a Portable FOSS Education Server on a Nookbox G9 is a practical, scalable solution for democratizing technical knowledge, empowering communities, and defending digital sovereignty in restricted environments.
Through thoughtful system design—leveraging open-source software and secure deployment practices—we enable resilient, censorship-resistant education wherever it's needed.
📎 References
-
 @ de6c63ab:d028389b
2025-04-26 14:06:14
@ de6c63ab:d028389b
2025-04-26 14:06:14Ever wondered why Bitcoin stops at 20,999,999.9769 and not a clean 21M? It’s not a bug — it’s brilliant.
https://blossom.primal.net/8e9e6fffbca54dfb8e55071ae590e676b355803ef18b08c8cbd9521a2eb567a8.png
Of course, it's because of this mythical and seemingly magical formula. Want to hear the full story behind this? Keep reading!
The Simple Math Behind It
In reality, there’s no magic here — it’s just an ordinary summation. That big sigma symbol (Σ) tells you that. The little “i” is the summation index, starting from 0 at the bottom and going up to 32 at the top. Why 32? We’ll get there!
After the sigma, you see the expression: 210,000 × (50 ÷ 2^i). 210,000 blocks represent one halving interval, with about 144 blocks mined per day, amounting to almost exactly four years. After each interval, the block reward halves — that’s what the division by 2^i means.
Crunching the Numbers
When i = 0 (before the first halving): 210,000 × (50 ÷ 2^0) = 10,500,000
At i = 1 (after the first halving): 210,000 × (50 ÷ 2^1) = 5,250,000
At i = 2 (after the second halving): 210,000 × (50 ÷ 2^2) = 2,625,000
…
At i = 31: 210,000 × (50 ÷ 2^31) ≈ 0.00489
At i = 32: 210,000 × (50 ÷ 2^32) ≈ 0.00244
And when you sum all of that up? 20,999,999.99755528
Except… that’s not the correct total! The real final number is: 20,999,999.9769
Where the Real Magic Happens
How come?! Here’s where the real fun begins.
We just performed the summation with real (floating-point) numbers. But computers don’t like working with real numbers. They much prefer integers. That’s also one reason why a bitcoin can’t be divided infinitely — the smallest unit is one satoshi, one hundred-millionth of a bitcoin.
And that’s also why there are exactly 33 halvings (0th, 1st, 2nd, …, 31st, 32nd). After the 32nd halving, the block reward would drop below one satoshi, making further halvings meaningless.
https://blossom.primal.net/6abae5b19bc68737c5b14785f54713e7ce11dfdecbe10c64692fc8d9a90c7f34.png
The Role of Integer Math and Bit-Shifting
Because Bitcoin operates with integers (specifically satoshis), the division (reward ÷ 2^i) is actually done using integer division. More precisely, by bit-shifting to the right:
https://blossom.primal.net/3dac403390dd24df4fa8c474db62476fba814bb8c98ca663e6e3a536f4ff7d98.png
We work with 64-bit integers. Halving the value simply means shifting the bits one position to the right.
What Happens During the Halvings
Notice: during the first 9 halvings (i = 0 to i = 8), we’re just shaving off zeros. But starting with the 9th halving (i = 9), we start losing ones. Every time a “one” falls off, it means we’re losing a tiny fraction — a remainder that would have existed if we were using real numbers.
The sum of all these lost remainders is exactly the difference between the two numbers we saw above.
And that’s why the total bitcoin supply is 20,999,999.9769 — not 21 million exactly.
Did you enjoy this? Got any questions? 🔥🚀
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 266815e0:6cd408a5
2025-04-26 13:10:09
@ 266815e0:6cd408a5
2025-04-26 13:10:09To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to
Math.round(Math.random() * 10000)trust me it will be betterWhat are kind 1 events
kind 1 events are defined in NIP-10 as "simple plaintext notes" or in other words social posts.
Don't trick your users
Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it.
Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one...
Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts
What about "discoverability"
If your goal is to make your "other stuff" app visible to more users, then I would suggest using NIP-19 and NIP-89 The first allows users to embed any other event kind into social posts as
nostr:nevent1ornostr:naddr1links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of eventSo instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a
nostr:link to your special kind of event and by extension you appWhy its a trap
Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format. This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitations forever.
For example, here are some of the limitations of using kind 1 - Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app - Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON - Users get confused. as mentioned above users don't expect "other stuff" apps to be creating special social posts - Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app
-
 @ 5f078e90:b2bacaa3
2025-04-26 12:01:11
@ 5f078e90:b2bacaa3
2025-04-26 12:01:11Panda story 3
Initially posted on Hive, story is between 300 and 500 characters. Should become a Nostr kind 30023. Image has markdown.
In a misty bamboo forest, a red panda named Rolo discovered a glowing berry. Curious, he nibbled it and began to float! Drifting over treetops, he saw his friends below, waving. Rolo somersaulted through clouds, giggling as wind tickled his fur. The berry's magic faded at dusk, landing him softly by a stream. His pals cheered his tale, and Rolo dreamed of more adventures, his heart light as the breeze. (349 characters)
Originally posted on Hive at https://hive.blog/@hostr/panda-story-3
Cross-posted using Hostr, version 0.0.3
-
 @ 5188521b:008eb518
2025-04-25 08:06:11
@ 5188521b:008eb518
2025-04-25 08:06:11Ecology
When my father died, an entire ecosystem of beneficiaries withered. Moussa Ag El Khir funded scholarships and community projects, paying thousands of Dinars monthly to stop the oasis town of In Salah from burning up. The few families we knew operating outside the oil-field economy would be forced to flee to the Mediterranean coast, along with just about every other Berber.
It wasn’t unexpected. My father had cystic fibrosis for all sixty-one years of his life. So far, that’s the only legacy he’s passed on to his children. My brothers are just carriers, but me, his precious daughter ended up like him in more ways than one.
We sat there in the lawyer’s office in Algiers, my brothers and I, staring at the ledger which contained payment for his life’s work.
“And he only left one word in his will?” asked Ibrahim for the third time. Ecology.
The lawyer said Moussa was very clear. He chose each of the keys himself. The contents of the ledger would belong to whoever could decode his life — those who understood the real meaning. Then he cut all communications and walked into the Sahara. The Tuareg caravan on the road to Akabli found his body a week later, reddened by sand burn.
Earth
We made an agreement that day. To share each word we discovered. We could break the code together. Of course, Ibrahim and Hama didn’t share anything. We barely speak. That’s what happens when one child follows their father into science, and her two brothers move to France the minute they get rich enough to buy a wife. I bet they spent longer looking into legal loopholes to get their hands on my father’s assets than they did trying to identify the keys.
That day was the start of my second life, and I went from research assistant at a regional university to private-key detective. 2048 words and few clues where to start. Although I was 27, I was virtually a grandmother according to the In Salah wives. But of course, I could never be a grandmother, or even a mother. Every night, I scoured photos in the family archive. An initial sweep of his digital footprint returned no out-of-place instances of any keywords.
It took me a year to find the GPS tag he’d added to one photo — an eighteen-year-old daughter standing next to a father proud of his first infinite solar prototype. The panel has long-since been torn out by the oil corp, but the base is still there. I drove the three kilometres from the town limit and shone the high beams at the spot. When I got out, the air was cool but still thick with sand. A few more steps through sinking dunes, and I saw it. He’d scratched a little globe into the blistered metal, and for a moment, my mucus-laden lungs tasted clear air.
Trigger
The next word took three years. Friends, contacts, professors, biographers — visits to anyone with whom he might have left a clue. But it was in the In Salah hospital, where, upon a routine CF checkup with Jerome Devailier, a French doctor, ‘trigger’ appeared. The government might stack everything against the desert peoples, but they hadn’t taken away healthcare. I’d been living off the kindness of neighbours while finishing my thesis on the very solar technology my father developed. How could he have known the ‘buyer’ was just a tendril of the very oil company he sought to defeat.
Dr Devalier went through the list of carcinogens and allergens to avoid with my new drugs. Over forty triggers which could be my downfall. If I was lucky, I’d live as long as my father did.
By then, my research stipend was long gone. I existed on toughened bread and soup, which always carried the taste of the scorched city air. Yet, I stayed. The public library, disconnected from the grid by the oil corp, was where I finished my manuscript. They would fight its publication. Since father’s money no longer flowed into the town, many had deserted me. There were those who said he killed an entire people by selling his solar patent to the wrong buyers. Others in In Salah worshipped his name, but eventually, they all trudged north to the cities. My brothers sold the family home from under me, forcing me to follow.
When I returned from the hospital, I dug out my father’s medical documents. On every page, the word ‘trigger’ was underlined. That was the moment I knew my life’s work would be unlocking the ledger, not publishing studies on long-dead solar panel technology. That battle was lost.
They
All we need is a simple document, but here, it is the administrators’ job to send people away. Physical copies are only issued in extreme circumstances. Citizens’ Registry screens played endless repetitions of how to apply for digital documents. The shrill voices of family members desperate for the original copy of a pirated document drowned the TV messaging. Women removed headscarves and revealed thick black hair; teenagers paced. The atmosphere thickened with sweat. And hours passed. Each appointment required a reset of digital protocol, biometric tests, and identity cards from legal descendents. Through counterfeit identities, our Dinars leak into the hands of criminals, but still the government denies the need for bitcoin. They just print more money. They is the word my father used for the government that fought his patent so hard.
After a four-hour wait, I discovered that the physical death certificate included an ‘identifying mark’ on the deceased’s body. The ink was fresh — etched into the shoulder blade of a man who wished to turn his back on the government that ignored its people. The tattoo read aqqalan, the Tamasheq word for they.
Scheme
It took two trips to his cluttered Marseille office to convince him I was serious. Two visas, two flights, and the small amount from the sale of the family house. But few detectives wanted to work for a promise.
The ledger could not legally be owned in Algeria, and Laurent Mercier was the only serious professional who entertained a percentage of what was on there. The solar tech patent and documents from my father were enough to start Laurent on the trail. ‘Preliminary,’ he said, until I had the ledger in my possession.
“Flying is not easy with my condition,” I said.
He lowered his sunglasses. “Working is not easy without money.”
Contact with my brother through the lawyer in Algiers was achingly slow, but eventually they agreed to give me possession. What was 33% of nothing anyway? Years had gone by.
So, when I sat for the second time, in the sweaty office in Marseille, I gave Laurent the ledger, and he handed me a surprise. In all his business affairs, my father used little English, but the word ‘scheme’ appeared in all three company names he incorporated in the last three years of his life. We had our fifth word, and I finally had someone on my side.
Make
Some days, I could barely walk to the public library. I became lethargic and mostly sat in the cool dark of my room in the shelter. The government refused to provide housing outside of Algiers, but a Tuareg organisation from Mali opened a shelter in In Salah. Bulging eyes and faded clothes stared back in the mirror each day. How long had it been since I’d been to a wedding, or celebrated a friend’s child? Occupants came and went, and all that was left was a barren room and one meal per day.
As the sun punished the city with every ray of Allah’s untapped gift, streets grew thick with dust, and the local government fell, seat by seat, to oil execs. The only transport running was to and from the oil fields, which belched the remnants of the land into the sky. And still they worked. Still they sat on my father’s patent and refused to supply the world with efficient solar power.
With little else to cling onto, I harboured thoughts of how I could spend the ledger money. Fixing the town and replanting lost gardens. Bringing people back. That all took a back seat to decoding the message my father was sending. Laurent and I began to believe that the keys he chose formed some sort of instruction for his legacy.
Ten years to the day after his death, I was in the public library, looking for clues in an English history book. On my exit, the librarian stopped me.
“We have a gift for you, Kana.”
I waited while he fetched a package.
“Your father instructed me to give this to you. But not before this date.”
My hands tore open the package. More books, technical manuals, and hand-written notes. Amongst the papers was a tasselled leather bookmark embossed with the four letters that comprised one of the seven missing words. Make.
Citizen
It’s hard for a father in Algeria to admit to his daughter that she is his spirit — the heir to his life’s work. Of course he felt terrible guilt after our mother’s passing. That was when the letters started.
Moussa wrote to himself really, trying to come to terms with bringing a protégé into the world with a bright scientific mind and lungs that would snap her life expectancy. We communicated by letter for the last few years of his life — sharing the breakthroughs of his findings and what it might mean for our decaying oasis town. Analogue writing was the only real privacy, he said. His letters always ran to the same length, as if they were one lesson divided into equal chunks. We even exchanged letters during his last hospitalisation in Algiers. Those words were the only real strength I gained.
It was Laurent who analysed the letters with a new text scanning tool. For me, my father’s last letters were advice, regret, pain, and love, but to Laurent, they were simply a puzzle to solve to get one step closer.
Our letters gave Laurent the idea to communicate via physical mail. The process was painful, with letters sent from outlying towns before being shipped across the Alboran Sea and up into France. Muatin was one name my father called me. Like him, I dreamed of helping many through science. This was one of the few Arabic words in the French letters he wrote. It was also the only keyword included in any of the letters. Citizen.
When
Years of quiet followed. In Salah became unlivable after they co-opted the city reservoir for cooling drilling rigs. Each study that proved the field was still viable funnelled funds away from the locals who clung on. Resettlement benefits went up, and all but the semi-nomadic Tuaregs left. I followed. My health could not take much more desert. In the cooler coastal plains, I recovered strength, and subsidies for new medications helped me survive on a meagre teaching salary.
With no further clues, my Marseillais detective lost interest. His last letter, sent years ago, stated with unusual brevity that he was resigning the case. No payment was due.
I had lost my health, my father, his work, my money, our house, the town, and I spent each week delivering science and English classes to teenagers. They had no more hope for our country than I had. Algerians had already lost the Sahara. A one-degree temperature shift each decade of my life had shrunk Africa and sent its peoples northwards.
My father’s word puzzle occupied my thoughts. The combinations and permutations of letters and characters had millions of possible meanings but only one correct answer. Yet simple linguistic logic provided the next word. The headteacher was a linguist — a profession long lost to the higher-powered text analysers and language AI. He spoke little English but asked about the categorisations of grammatical terms in the 2048 key words.
“Why do you ask?”
“Because,” he said, “for a sentence of twelve words, at least one conjunction is necessary to form a second clause.”
He was right. I had been focussing on lists and complex codes to build my father’s motto. When I got home, I furiously searched my list of terms for conjunctions. I found only one. ‘When.’
Can
The permutations were still huge. Even eliminating some of the more conceptual words did not help. Millions of sentences existed in my dead father’s mind. Millions of meanings, all lost to the need for more energy to fund the world’s great thirst for energy. Still, the panels in most of the ‘dead middle’ (as the space between the tropics became known) melted at over 50 degrees.
I was back in Paris for CF treatment. As a young woman, I would have been pleased to make fifty years. But the realities of daily visits and the sickness brought on by medication stung. I wanted things to end, even when I discovered the next key.
It had been years since I had dreamed of the freedoms my father’s fortune could bring. Parts of Asia held out against bitcoin, but the cost of countries doing business off-network had become prohibitive. Eventually, the fossil conglomerates would give in to the need for solar mining and the provision of universal energy.
It was in a Parisian hospital bed that I discovered ‘can.’ My wardmate, a rough labourer from Oran, found a biography in the hospital library that made me sit up straight. ‘Can’ was repeated in almost every description of my father in his one-time business partner’s book. And it was this Arabian ‘businessman,’ Abdulkarim Rahman, who brokered the deal that robbed the world of infinite solar power. Each page mocked my father as believing only physical impossibilities are impossible. He branded him the ‘can man.’
Drastic
During my recuperation, I spent the final two weeks of my visa stay in Marseille. My days passed with endless algorithm tweaks to reject or accept word orders for the elusive twelve-word sentence my father once wrote.
Food lost its taste, and friends and colleagues in academia had scattered. In-person meetings were often contained to the night hours, but Marseille was not a place to go out after dark. The latest protests had gotten violent, and the government looked likely to topple. My people had always been resilient, but when the option to move and operate a caravan was removed by General Hafiz, part of my spirit died. I resolved to spend my final years in In Salah, however uncomfortable they would be.
My final port of call before returning was Laurent’s office. The eTaxi cast me out into the dusty street, and I wheezed as I climbed the three flights of stairs to his tiny door on Rue Marché. We hadn’t spoken in years, but I was surprised to find a different name about the door. Pascale Dupont, Investigateur.
The assistant I remembered was quite the opposite to Laurent — slow and methodical, short and heavy set.
“Madame,” he said. “I have difficult news.”
Their business had always straddled the law, but I never imagined an ex-officer of the law could be convicted of treason.
“A closed-door trial,” said Pascale. Then he handed over an air-gapped 3D storage file. “Laurent knew you would come for this.”
My mind cast forward to the reams of information he must have built on my father. The patents and technical diagrams he illegally acquired and other clues. I instantly recognised the brand of storage file as a keyword. Drastic.
“How can I thank him?”
“He is dead, madame.” Pascale hung his head. “He survived prison for only two weeks.”
Must
My final years brought me home. In Salah had gained fame for its one group of Tuaregs who refused to leave. The Lakzis owned a house in a desperate condition, not dissimilar to my failing body. By the age of fifty-two, I could no longer walk, but they welcomed me. I pooled my disability allowance and some money I’d gained from selling my father’s watch. We waited for the world to mourn the death of a once great city. We would keep it alive by refusing to move, by refusing to permit its rebranding as an ‘industrial area.’ Now the oil fields were finally drying up, they wanted to dig under the town.
We had managed to eliminate half of the remaining words. Just under 1,000 possible selections for the final two words, but little idea of an order.
The problem was that I was the only English speaker among them, and it took great energy to attempt to teach the meaning of the words and possible grammatical constructions for my father’s sentence.
But soon, patterns began to emerge. Fragments of word pairings and groups. ‘Trigger drastic scheme’ appeared again and again in the permutations. ‘They can’ and ‘When they can’ gave a tantalising glimpse. We ranked sentences in terms of likelihood to form the full key and categorised them by the most likely remaining words. Due to the need for a modal verb, ‘must’ scored highest by our calculations.
In this race to unlock the ledger before In Salah’s destruction, we nosed ahead.
Yet the day of that discovery was my final day in the desert. An air ambulance transported my feeble body to Algiers, and I would never return.
They messaged me — so close. They would unlock the ledger with the final word after my operation. The bitcoin could undo the wrongs of the past, and my father’s sentence would live on.
End
The phrase which began the global revolution first appeared on the wall of a much-disputed oil refinery in the desert outside In Salah, Algeria.
When they can make ecology end, citizen earth must trigger drastic scheme
Soon, the graffiti marked government buildings in Algiers. Activists took to the streets. Governments crumbled and currencies collapsed. Climate groups received massive donations said to come from ‘the one,’ a ledger with a huge stack written off by financiers the world over. The codebreaker credited with unlocking the ledger was unable to witness the transfer of 10,000 coins to the Global Climate Fund due to her death, aged 52, from a congenital condition.
The words of Moussa Ag El Khir now mark each of the millions of panels, which line the ‘dead middle.’ They contribute over 80% of the Earth’s power supply.
To mark the fiftieth anniversary of his death, the World Climate Forum will be held in the town of his birth, In Salah, Algeria. This story, compiled from the diaries of his daughter, Kana Ult El Khir, will be read as the opening address of the conference.
This story was originally published in 21 Futures: Tales From the Timechain
To continue the story of the real-world treasure (sats) use the address (it's real).\ Who knows, maybe some zaps will find their way into the wallet...

-
 @ 502ab02a:a2860397
2025-04-26 11:14:03
@ 502ab02a:a2860397
2025-04-26 11:14:03วันนี้เรามาย้อนอดีตเล็กน้อยกันครับ กับ ผลิตภัณฑ์ไขมันพืชแปรรูปแบบแรกๆของโลก ที่ใช้กระบวนการแปรรูปน้ำมันพืชด้วยเคมี (hydrogenation) เพื่อให้ได้ไขมันกึ่งแข็ง
ในเดือนมิถุนายน ค.ศ. 1911 บริษัท Procter & Gamble เปิดตัวผลิตภัณฑ์ใหม่ที่เปลี่ยนโฉมวงการทำอาหารบ้านๆ ทั่วอเมริกา ตราสินค้า “Crisco” ซึ่งมาจากคำว่า “crystallized cottonseed oil” ได้ถือกำเนิดขึ้นเป็น “vegetable shortening” หรือที่บ้านเราเรียกว่าเนยขาว ก้อนแรกที่ทำมาจากน้ำมันพืชล้วนๆ แทนที่ไขมันสัตว์อย่างเนยหรือน้ำมันหมู จัดเป็นจุดเริ่มต้นของการปฏิวัติวิธีปรุงอาหารในครัวเรือนสหรัฐฯ
ก่อนหน้านั้น คนอเมริกันคุ้นเคยกับการใช้เนย ชีส หรือน้ำมันหมูในการประกอบอาหาร แต่ Crisco มาพร้อมการโฆษณาว่า “สะอาดกว่า” และ “ประหยัดกว่า” เพราะไม่ต้องเสี่ยงกับกลิ่นคาวหรือการเน่าเสียของไขมันสัตว์ อีกทั้งบรรจุในกระป๋องสีขาวสะอาด จึงดูทันสมัยน่าต้องการ
ชื่อ “Crisco” นั้นไม่ได้ตั้งโดยบังเอิญ แต่มาจากการย่อวลี “crystallized cottonseed oil” ให้สั้นกระชับและติดหู (ต้นชื่อ “Krispo” เคยถูกทดลองก่อน แต่ติดปัญหาเครื่องหมายการค้า และชื่อ “Cryst” ก็ถูกทิ้งไปเพราะมีนัยยะทางศาสนา)
กระบวนการสำคัญคือการนำเอาน้ำมันฝ้ายเหลวไปเติมไฮโดรเจน (hydrogenation) จนแข็งตัวได้เองในอุณหภูมิห้อง ผลลัพธ์คือไขมันทรานส์ที่ช่วยให้มาการีนแข็งตัวดี
ภายในเวลาไม่นานหลังการเปิดตัว โฆษณาในหนังสือพิมพ์และวิทยุกระจายเสียงฉบับแรกของ Crisco ก็เริ่มขึ้นอย่างดุเดือด พ่วงด้วยการแจก “ตำรา Crisco” ให้แม่บ้านลองนำไปใช้ทั้งอบ ทั้งทอด จึงเกิด “ยุคครัว Crisco” อย่างแท้จริง
แม้ Crisco จะถูกยกให้เป็น “จุดเริ่มต้นของยุคไขมันพืช” ในครัวอเมริกัน แต่เบื้องหลังขวดสีเขียว–ขาวที่เติมเต็มชั้นเก็บของในบ้านกลับมีดราม่าและบทเรียนมากกว่าที่ใครคาดคิด
ย้อนกลับไปทศวรรษ 1910 เมื่อ Procter & Gamble เปิดตัว Crisco ในฐานะ “ไขมันพืชสุดสะอาด” พร้อมกับโฆษณาว่าเป็นทางเลือกที่ดีกว่าเนยและแลร์ดเดิม ๆ แต่ความท้าทายแรกคือ “ฝืนความเชื่อ” ของคุณแม่บ้านยุคนั้น ที่ยังยึดติดกับไขมันจากสัตว์ นักการตลาดของ P&G จึงสร้างภาพลักษณ์ให้ Crisco ดูเป็นผลิตภัณฑ์อุตสาหกรรมขั้นสูง โปร่งใส และถูกสุขอนามัยสู้กับค่านิยมเดิมได้อย่างน่าทึ่ง
หนังสือพิมพ์ในยุคนั้นพูดกันว่า มันคือไขมันพืชปฏิวัติวงการ ที่ทั้งถูกกว่าและยืดอายุได้ไกลกว่าน้ำมันสัตว์
กระทั่งปลายทศวรรษ 1980 เกิดดราม่าสะท้อนความย้อนแย้งในวงการสุขภาพ เมื่อองค์กร CSPI (Center for Science in the Public Interest) กลับออกมาชื่นชมการใช้ไขมันทรานส์จาก Crisco ว่า “ดีต่อหลอดเลือด” เมื่อเทียบกับไขมันอิ่มตัวจากมะพร้าว เนย หรือไขมันสัตว์
นี่คือครั้งที่วงการแพทย์และโภชนาการแตกแยกกันว่าอะไรจริงหรือหลอก จนกระทั่งงานวิจัยยืนยันชัดเจนว่าไขมันทรานส์เป็นอันตรายต่อหัวใจจริง ๆ
แต่เมื่อเวลาผ่านไป งานวิจัยคุณภาพสูงเริ่มชี้ชัดว่า ไขมันทรานส์ ไม่ใช่เพียงส่วนเกินในเมนูขนมกรอบๆ เท่านั้น มันเป็นภัยเงียบที่เพิ่มความเสี่ยงโรคหลอดเลือดหัวใจ และการอักเสบเรื้อรัง WHO จึงออกมาตรการให้โลก “เลิกทรานส์แฟต” ภายในปี 2023 ทำให้ Procter & Gamble ปรับสูตร Crisco มาใช้การผสมระหว่างน้ำมันฝ้าย fully hydrogenated กับน้ำมันเหลว ผ่านกระบวนการ interesterification แทน เพื่อให้ได้จุดหลอมเหลวที่เหมาะสมโดยไม่สร้างทรานส์แฟตเพิ่มอีก
อีกประเด็นดราม่าที่ตามมาเมื่อ Procter & Gamble ต้องปรับสูตร Crisco ให้เป็น “trans fat–free” ในปี 2004 และยุติการขายสูตรปราศจากทรานส์เฉพาะทางในปี 2007 ก่อนจะกลับมาใช้ fully hydrogenated palm oil ตามกฎ FDA ในปี 2018
แต่การหันมาใช้น้ำมันปาล์มเต็มตัวกลับก่อปัญหาใหม่ คือข้อครหาเรื่องการทำลายป่าเขตร้อนเพื่อปลูกปาล์มน้ำมัน จนกลายเป็นดราม่าระดับโลกเรื่องสิ่งแวดล้อมและสิทธิมนุษยชนในชุมชนท้องถิ่น
แด่วันนี้ เมื่อใครยังพูดถึง Crisco ด้วยสายตาเด็กน้อยที่เห็นไขมันพืชขาวโพลน เป็นคำตอบใหม่ของครัวสะอาด เราอาจยกมือทักว่า “อย่าลืมดูเบื้องหลังของมัน” เพราะไขมันที่เกิดจากการ “สลับตำแหน่งกรดไขมัน” ผ่านความร้อนสูงและสารเคมี ไม่ใช่ไขมันที่ธรรมชาติออกแบบมาให้ร่างกายคุ้นเคยจริงๆ แม้จะมีชื่อใหม่ สูตรใหม่ แต่ต้นกำเนิดของการปฏิวัติครัวในปี 1911
Crisco ไม่ได้เป็นแค่พรีเซนเตอร์ “ไขมันพืชเพื่อสุขภาพ” แต่ยังเป็นบทเรียนสำคัญเรื่องการตลาดอาหารอุตสาหกรรม การวิจัยทางโภชนาการที่ต้องพัฒนาไม่หยุดนิ่ง และผลกระทบต่อสิ่งแวดล้อมเมื่อเราหันมาใช้วัตถุดิบใหม่ๆ ดังนั้น ครัวของเราอาจจะสะอาดทันสมัย แต่ก็ต้องเลือกให้รอบคอบและติดตามเบื้องหลังของทุกขวดที่เราใช้เสมอครับ
ไหนๆก็ไหนๆแล้ว ขออธิบายคุณลักษณะของ เนยขาวไปยาวๆเลยแล้วกันนะครับ ขี้เกียจแยกโพส 55555555
เนยขาว หรือชื่อทางเทคนิคว่า “shortening” ไม่ได้มีส่วนผสมของนม หรือเนยแท้ใดๆ ทั้งสิ้น แต่มันคือไขมันพืชที่ผ่านกระบวนการทำให้แข็งตัว และคงรูปได้ดี เส้นทางของเนยขาวเริ่มด้วยการเปลี่ยนโครงสร้างไขมันไม่อิ่มตัวในน้ำมันพืชให้กลายเป็นไขมันอิ่มตัวมากขึ้น กระบวนการนี้เรียกว่า hydrogenation หรือการเติมไฮโดรเจนเข้าไปในโมเลกุลของไขมัน โดยใช้อุณหภูมิสูงและตัวเร่งปฏิกิริยาอย่าง “นิกเกิล” เพื่อให้ไขมันพืชที่เหลวกลายเป็นของแข็งที่อยู่ตัว ไม่เหม็นหืนง่าย และสามารถเก็บได้นานขึ้น
ผลพลอยได้ของการ hydrogenation คือการเกิดขึ้นของ ไขมันทรานส์ (trans fat) ซึ่งเป็นไขมันที่ร่างกายแทบไม่มีระบบจัดการ และได้รับการยืนยันจากงานวิจัยนับไม่ถ้วนว่าเป็นหนึ่งในปัจจัยเสี่ยงสำคัญต่อโรคหัวใจ หลอดเลือด และการอักเสบเรื้อรังในร่างกาย แม้ในยุคปัจจุบันบางผู้ผลิตจะเปลี่ยนวิธีการผลิตไปใช้การปรับโครงสร้างไขมันด้วยวิธี interesterification ที่ช่วยลดทรานส์แฟตลงได้มาก แต่ก็ยังคงเป็นกระบวนการแทรกแซงโครงสร้างไขมันจากธรรมชาติรวมถึงใช้กระบวนการ RBD ที่เราคุยกันไปแล้วอยู่ดี และผลกระทบต่อร่างกายในระยะยาวก็ยังเป็นคำถามที่นักโภชนาการสาย real food หลายคนตั้งข้อสังเกต
คำว่า “shortening” มาจากคำกริยา shorten ที่แปลว่า "ทำให้สั้นลง" ซึ่งในบริบทของการทำขนม มันหมายถึง การไปยับยั้งไม่ให้เส้นใยกลูเตนในแป้งพัฒนาได้ยาวและเหนียวตามธรรมชาติ เวลาผสมแป้งกับน้ำ โปรตีนในแป้งสองตัวคือกลูเตนิน (glutenin) กับไกลอาดิน (gliadin) จะจับกันกลายเป็นกลูเตน ซึ่งมีคุณสมบัติยืดหยุ่น เหนียว เหมาะกับขนมปังที่ต้องการโครงสร้างแน่นๆ ยืดๆ หนึบๆ
แต่พอเราใส่ shortening ลงไป เช่น เนยขาว น้ำมัน หรือไขมันที่อยู่ในสถานะกึ่งของแข็ง มันจะไปเคลือบเส้นแป้ง ทำให้โปรตีนกลูเตนจับกันไม่ได้เต็มที่ ผลคือเส้นใยกลูเตนถูก “ทำให้สั้นลง” แทนที่จะยืดหยุ่นยาวแบบในขนมปัง เลยกลายเป็นเนื้อขนมที่ร่วน นุ่ม ละลายในปาก หรือแม้แต่กรอบ อย่างคุกกี้ พาย หรือโรตีบางๆ หอมๆ นั่นแหละ เป็นสัมผัสที่นักทำขนมรักใคร่ แต่ร่างกายอาจไม่ปลื้มสักเท่าไหร่
เพราะจุดสังเกตุคือ เรื่องไขมันทรานส์ หลายแบรนด์ที่ขั้นตอนการผลิตไม่ดีพอ อาจพยายามเขียนฉลากว่า “ไม่มี trans fat” หรือ “low trans” แต่ในความเป็นจริงแล้ว หากไขมันทรานส์ต่ำกว่า 0.5 กรัมต่อหนึ่งหน่วยบริโภค ผู้ผลิตสามารถระบุว่าเป็น 0 ได้ตามกฎหมาย ซึ่งหากกินหลายๆ หน่วยรวมกัน ก็ไม่ต่างจากการเปิดประตูให้ trans fat ย่องเข้าร่างแบบไม่รู้ตัว
แต่เหนือกว่านั้นก็คือเรื่องเดิมๆที่เราเข้าใจกันดีในน้ำมันพืช นั่นคือ โอเมก้า 6 เพียบ + กระบวนการปรุงแต่งเคมี ที่เปราะบางต่ออุณหภูมิ ทำให้เกิดการออกซิเดชัน นำไปสู่โรคจากการอักเสบของร่างกาย
อาจถึงเวลาแล้วที่เราควรเปิดใจกลับไปหาความเรียบง่ายของไขมันจากธรรมชาติ สิ่งที่ดูสะอาด ขาว และอยู่ตัวดีเกินไป อาจไม่ใช่สิ่งที่ธรรมชาติอยากให้เข้าไปอยู่ในตัวเราก็ได้
ปล. สำหรับใครที่สงสัยว่า เนยขาว กับ มาการีน ต่างกันยังไง Shortening (เนยขาว) คือไขมันพืช 100% ไม่มีน้ำผสม บีบให้เป็นก้อน ทนความร้อนได้สูง เพื่อให้แป้ง “ไม่ยืด” เกล็ดขนมร่วนกรอบ Margarine (มาการีน) จะผสมไขมันกับน้ำ–เกลือ–อิมัลซิไฟเออร์ ทำให้ทาได้เนียนเหมือนเนย แต่มีน้ำประมาณ 15–20%
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 5f078e90:b2bacaa3
2025-04-26 10:51:39
@ 5f078e90:b2bacaa3
2025-04-26 10:51:39Panda story 1
Initially posted on Hive, story is between 300 and 500 characters. Should become a Nostr kind 30023. Image has markdown.
In a misty bamboo forest, a red panda named Rolo discovered a glowing berry. Curious, he nibbled it and began to float! Drifting over treetops, he saw his friends below, waving. Rolo somersaulted through clouds, giggling as wind tickled his fur. The berry's magic faded at dusk, landing him softly by a stream. His pals cheered his tale, and Rolo dreamed of more adventures, his heart light as the breeze. (349 characters)

Originally posted on Hive at https://hive.blog/@hostr/panda-story-1
Cross-posted using Hostr, version 0.0.1
-
 @ 6ccf5232:5c74f0cb
2025-04-26 10:11:07
@ 6ccf5232:5c74f0cb
2025-04-26 10:11:07Com o crescimento dos jogos online, escolher a plataforma certa pode ser uma tarefa desafiadora. Se você está em busca de uma opção confiável, moderna e cheia de recursos, a plataforma 777G é a escolha certa para você. Este artigo irá detalhar como o 777G se destaca no mercado e oferece uma experiência de jogo única.
A Plataforma Ideal para Todos os Jogadores A primeira coisa que chama a atenção no 777G é sua interface amigável e acessível. A plataforma foi projetada pensando na simplicidade de uso, permitindo que qualquer jogador, seja iniciante ou experiente, possa começar a jogar sem dificuldades. Além disso, o design moderno garante que você tenha uma navegação fluída e agradável, seja no computador ou no celular.
O 777g é mais do que apenas uma plataforma de jogos — é um lugar onde a diversão e a segurança andam de mãos dadas. Com sistemas de segurança avançados, seus dados e transações financeiras estarão sempre protegidos.
Variedade de Jogos: Atração para Todos os Gostos O 777G oferece uma vasta gama de jogos para que você nunca se sinta entediado. Se você gosta de emoção e rapidez, os slots são uma excelente escolha. Se preferir algo mais desafiador, os jogos de mesa como blackjack e poker serão perfeitos para testar suas habilidades. Além disso, a roleta é sempre uma ótima opção para quem adora a sensação de suspense e expectativa.
Outro diferencial do 777G é que ele está constantemente atualizando seu portfólio de jogos, trazendo novos títulos e opções que agradam a todos os tipos de jogadores. Com isso, você sempre encontrará algo novo e emocionante para jogar.
A Experiência de Jogo Além de uma plataforma visualmente atraente e fácil de usar, o 777G se dedica a criar uma experiência completa para os jogadores. Isso inclui promoções regulares, bônus de boas-vindas e programas de fidelidade, que garantem que sua experiência seja sempre cheia de recompensas.
A plataforma também se destaca pelo suporte ao cliente, que está disponível 24 horas por dia, 7 dias por semana. Se você tiver qualquer dúvida ou problema, a equipe estará pronta para ajudar.
Conclusão Se você busca uma plataforma de jogos que ofereça diversão, segurança e uma ampla variedade de opções, o 777G é a escolha ideal. Comece agora e descubra um mundo de diversão e prêmios esperando por você.
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
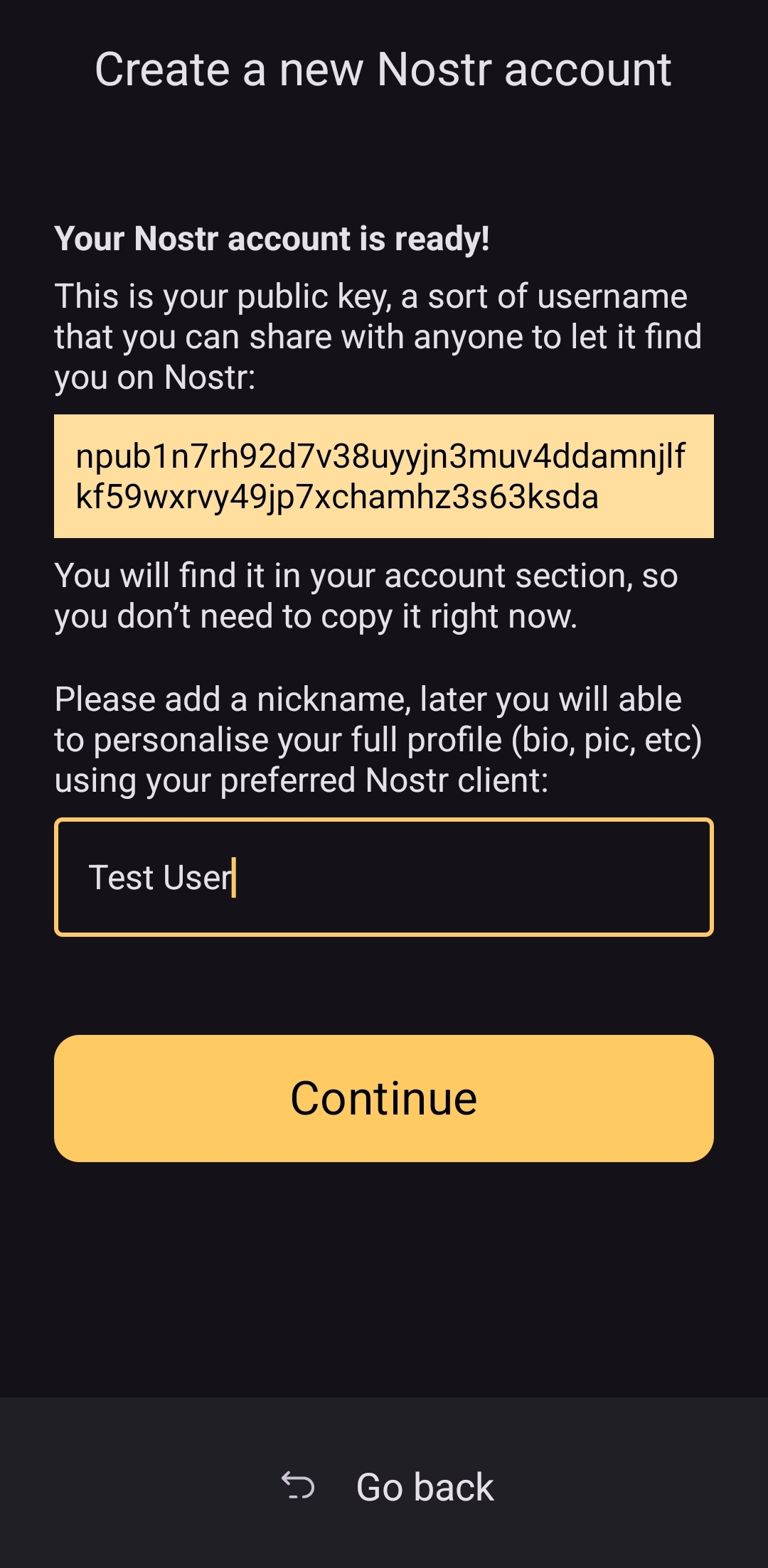
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 6ccf5232:5c74f0cb
2025-04-26 10:10:26
@ 6ccf5232:5c74f0cb
2025-04-26 10:10:26O 9nbet chegou para transformar a maneira como você encara o entretenimento online. Com uma plataforma inovadora, que foca em qualidade, segurança e uma experiência de usuário sem igual, o 9nbet se tornou uma opção atraente para aqueles que buscam algo mais em sua jornada de diversão online.
Facilidade e Confiabilidade Ao entrar no 9nbet, você logo percebe como a plataforma foi pensada para o usuário. Com um design intuitivo e de fácil navegação, você não precisa perder tempo procurando pelo que deseja. A plataforma é responsiva e adaptada para dispositivos móveis, garantindo uma experiência fluida, seja no desktop ou no smartphone.
A segurança também é uma prioridade. A plataforma adota as mais recentes tecnologias de criptografia, garantindo que suas informações e transações sejam sempre protegidas.
Uma Grande Variedade de Jogos O 9nbet oferece uma enorme gama de opções para quem busca por jogos online. São diversos títulos que atendem a diferentes gostos e preferências. Se você é fã de jogos com uma boa dose de estratégia, ou se prefere deixar a sorte decidir, o 9nbet tem algo para você.
Dentre as opções mais procuradas, destacam-se:
Jogos de Mesa: Para quem ama desafios e decisões rápidas.
Máquinas de Slots: Cheias de cores vibrantes e bônus emocionantes.
Jogos de Habilidade: Uma ótima opção para quem quer testar suas habilidades.
Todos os jogos são fornecidos por desenvolvedores de renome, garantindo uma jogabilidade justa e de alta qualidade.
Experiência do Jogador: Prioridade Máxima No 9nbet, a experiência do jogador é sempre colocada em primeiro lugar. A plataforma oferece diversos bônus de boas-vindas, promoções especiais e programas de fidelidade. Estes programas são pensados para recompensar os jogadores frequentes, com benefícios como bônus exclusivos, suporte prioritário e muito mais.
Além disso, o 9nbet conta com várias formas de pagamento, tornando os depósitos e retiradas rápidos e seguros. Isso garante que você aproveite a diversão sem se preocupar com processos complicados.
Conclusão O 9nbet é uma das plataformas de entretenimento online mais completas e seguras. Com uma grande variedade de jogos, uma interface amigável e benefícios exclusivos, é a escolha perfeita para quem busca qualidade e diversão. Não perca tempo, entre agora e comece a viver a experiência 9nbet!
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 12fccfc8:8d67741e
2025-04-26 09:44:39
@ 12fccfc8:8d67741e
2025-04-26 09:44:39„Anstatt das System zu bekämpfen, baue ein System, das es überflüssig macht.“
– zugeschrieben Buckminster Fuller
Die Gegenwart ist geprägt von Zentralisierung, digitaler Kontrolle und einem Finanzsystem, das Vertrauen verlangt, aber wenig zurückgibt. Für Bitcoiner stellt sich nicht mehr die Frage nach dem Ob, sondern nach dem Wie des Rückzugs aus diesem System.
Vom Goldstandard zu Bitcoin
Der klassische Goldstandard war Ausdruck eines strukturellen Misstrauens gegenüber staatlicher Willkür. Die Bindung des Geldes an ein rares Gut wie Gold disziplinierte die Geldpolitik – allerdings auf Kosten von Flexibilität, Zugänglichkeit und Dezentralität. Gold war zentral verwahrt, schwer zu transportieren und politisch angreifbar.
Bitcoin übernimmt die Idee der Begrenzung, ohne diese Schwächen: keine zentrale Verwahrung, leicht teilbar, digital übertragbar, resistent gegen Konfiszierung. Was beim Gold noch eine politische Vereinbarung war, ist bei Bitcoin eine technische Tatsache.
Anarchie als Ordnung ohne Herrschaft
Anarchie wird oft missverstanden. Sie ist keine Ablehnung von Ordnung, sondern von Herrschaft. Sie setzt auf freiwillige Strukturen statt auf Zwang, auf Verantwortung statt auf Kontrolle. Bitcoin ist in diesem Sinne anarchisch. Es gibt keine zentrale Autorität, keine Intervention, kein Gatekeeping. Teilhabe ist offen, Regeln sind transparent, Entscheidungen beruhen auf Konsens. Es ist ein System, das sich jeder aneignen kann, ohne jemanden um Erlaubnis zu fragen.
Die Praxis des Rückzugs
Der Rückzug aus dem bestehenden System ist kein plötzlicher Bruch, sondern eine Praxis. Er beginnt mit Selbstverwahrung, mit der Vermeidung von KYC, mit der Nutzung von Peer-to-Peer-Technologien und mit dem bewussten Aufbau eigener Infrastruktur. Es geht nicht darum, das alte System zu stürzen, sondern es überflüssig zu machen – indem man es nicht mehr braucht.
Bitcoin als Entscheidung
Bitcoin ist keine Spekulation, kein Unternehmen, kein Produkt. Es ist eine Entscheidung. Eine Entscheidung für Autonomie. Für Verantwortung. Für Souveränität. Wer sich für diesen Weg entscheidet, entscheidet sich nicht für die einfachste Lösung – sondern für die ehrlichste. Der Preis ist Selbstverantwortung. Die Belohnung ist Freiheit.
Ein stiller Rückzug
Kein Spektakel. Keine Revolution. Nur ein Protokoll. Und ein Mensch, der es nutzt.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 9c9d2765:16f8c2c2
2025-04-26 08:14:16
@ 9c9d2765:16f8c2c2
2025-04-26 08:14:16CHAPTER THIRTEEN
"I need something, Tracy anything," Mark said urgently over the phone. "A document, a record, an old file. Something we can use to destroy James."
There was a pause on the line before Tracy’s voice came through. "I’m listening."
"You're close to the system. You’ve got access. Find anything in JP Enterprises' archives that can ruin his name. I’ll make it worth your while."
"And if I find something?"
"Then you'll be well paid. Consider this... a mutual favor."
She hesitated for only a moment longer before replying. "Fine. I never liked that arrogant boss anyway."
Tracy got to work.
She waited until after hours when most of the staff had left the building. Using her clearance as assistant secretary, she accessed the company’s archival system and began a deep dive into the internal records emails, past reports, disciplinary logs anything that could point to a crack in James’s past.
Her digging soon turned up something explosive.
A buried personnel file revealed that James had once worked as a general manager in the company years ago under the leadership of his own parents. And the record didn’t end well.
Tracy’s eyes widened as she read through the document.
James had been dismissed for embezzlement. According to the official report, he had allegedly siphoned company funds and misappropriated key equipment. Worse still, his name had been added to JP Enterprises’ blacklist marked as a permanent ban from holding any role in the organization again.
"Oh my God," Tracy whispered, her heart pounding. "This is it. This will end him."
Without wasting another second, she forwarded every file and attachment to Mark and Helen.
Meanwhile, across the ocean, in a secluded estate far from the noise of city life, Mr. and Mrs. JP were enjoying the quiet of retirement. Having severed ties with James years ago over the scandal, they had left the country to escape the shame and silence.
That peace was short-lived.
Mr. JP sat up abruptly as his phone buzzed. It was an anonymous message. He opened it slowly, his eyes scanning the contents with growing disbelief.
"James has returned to JP Enterprises. Charles reinstated him. He’s now President of your company."
His blood ran cold.
Mrs. JP saw the tension in his expression. "What’s wrong?"
"He’s back," Mr. JP said grimly. "Our son. James. He's taken over the company."
He stared into space, his mind reeling. "And Charles helped him..."
They had spent years trying to distance themselves from the disgrace of James’s past only to now be faced with the reality that he had clawed his way back into the empire they built.
The anonymous message was, of course, sent by Mark and Helen, each relishing in the chaos they had ignited. With the scandalous file now in their hands and James’s own family unknowingly brought into the picture, they believed the final blow was in place.
Mark leaned back in his chair and smiled as he read the forwarded documents.
"Let’s see how your so-called empire stands after this, James," he said quietly.
Helen, standing beside him, added coldly, "This time, he won’t survive it."
"How could he do this?" Mr. JP muttered under his breath, clutching his phone tightly. "How could Charles go behind my back and reinstall him? My own brother..."
The news that James had returned to JP Enterprises and not just as a member, but as its President had shaken him to the core. But what stung more was the betrayal he felt from Charles, who had once promised never to interfere in the matter again.
Fuming with rage and disbelief, Mr. JP boarded the next flight back home. Upon arrival, he didn’t even stop by the family estate. Instead, he went straight to the Regency Grand, the city’s most luxurious hotel, the same place he used to spend time with his family during better days. He booked the presidential suite and immediately dialed Charles' number.
"Meet me. Now. At the hotel," he barked before ending the call without waiting for a response.
Within the hour, Charles walked in, calm but aware of the storm brewing.
"You defied me, Charles," Mr. JP said, his voice icy. "You brought back the one person I had removed. The one person I swore would never set foot in the company again."
"Because you were wrong," Charles replied firmly. "You made a decision based on lies."
Mr. JP’s glare deepened.
"Lies? The records were clear embezzlement. Theft. He disgraced this family, Charles!"
Charles stood his ground. "Those records were manipulated. You never gave James a chance to explain himself."
He stepped closer. "The funds he was accused of stealing? He used them to invest in a struggling tech start-up that exploded in value two years later. That investment saved JP Enterprises during the economic downturn. The company is standing today because of James’s vision and sacrifice."
Silence filled the room.
Mr. JP felt his heart sink as the weight of Charles’s words settled in. He turned away, walking slowly to the window, staring out at the city skyline.
"All this time... I condemned my own son... exiled him... because I trusted false reports?"
Charles nodded. "Yes. And despite it all, he returned not for revenge, but to help us."
Tears welled up in Mr. JP’s eyes. His pride, once like stone, was now crumbling.
Without hesitation, he picked up his phone and dialed James’s number. The phone rang twice before James answered.
"Hello?" came the familiar voice, calm and distant.
"James... it’s your father." His voice trembled. "I... I’m sorry. I was wrong. Gravely wrong. Everything I believed about you was a lie. I let you down, son."
There was silence on the other end.
"I just found out the truth," Mr. JP continued. "And I’m proud of what you’ve done for the company, for our name. I want you to know... you are reinstated as the rightful heir to JP Enterprises. I want you back not just as President, but as my son."
James took a long pause before answering.
"It took you long enough," he said softly. "But... thank you."
Though James had once sworn not to seek his parents' approval, deep down, those words still mattered. And hearing them from the father who had disowned him brought a quiet sense of closure.
The rift that had torn them apart for years was beginning to heal.
"Dad, who told you I was the President of JP Enterprises?" James asked, his tone calm but firm as he stood before his father in the grand office of the family estate.
Mr. JP, still adjusting to the emotional weight of his recent apology, furrowed his brow. "It was anonymous, son. I received a message no name, no clue. Just the information."
James narrowed his eyes. "Can you forward the message to me?"
"Of course," his father replied, pulling out his phone. Within seconds, the message was in James’s inbox.
Later that evening, James sat in his private office, staring at the message on his screen. Something about it felt off too calculated, too timely. He forwarded it to his personal cybersecurity team with one instruction: “Trace the source. I want to know everything about who sent it, how, and if they’re working with someone.”
Meanwhile, Ray Enterprises was thriving again under James’s investment. With the influx of capital and revitalized operations, profits were skyrocketing. However, while the company’s success looked promising on the surface, the Ray family was barely reaping the rewards.
James’s 85% share ensured he collected the lion’s portion of every deal. Robert, despite being the figurehead chairman, found himself managing a flourishing empire but receiving only crumbs in return.
Frustrated and desperate, Robert scheduled a private meeting with James.
"James, please... eighty-five percent is bleeding us dry. We’re grateful for what you’ve done truly but surely we can renegotiate?"
James leaned back in his chair, expression unreadable. "You signed the agreement, Robert. You knew the terms. And frankly, I'm not in the mood to revisit old conversations."
"We just want fairness," Robert pleaded. "A little breathing space"
"If this discussion continues," James interrupted coldly, "I’ll pull out my funds. And when I do, I promise Ray Enterprises will go down faster than it rose. Do I make myself clear?"
Robert’s face fell. He had no choice but to nod and walk away, defeated.
Two weeks later, James’s cybersecurity team sent their report. The source of the anonymous message had been traced and the result was both surprising and telling.
Tracy.
James sat silently as he read the details. Tracy, his own subordinate, had accessed restricted files from the company’s internal network. It wasn’t just a case of whistleblowing it was deliberate sabotage. But what intrigued him more was the fact that she had gone to great lengths to cover her tracks.
No one takes that risk alone, he thought.
Despite having the evidence in hand, James chose silence. Not out of mercy but strategy. He needed to know who she was working with. Who else had a vested interest in his downfall?
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .