-
 @ 4fe4a528:3ff6bf06
2025-05-01 13:36:04
@ 4fe4a528:3ff6bf06
2025-05-01 13:36:04Bitcoin has emerged as a significant player in the financial markets, often drawing comparisons to traditional assets like stocks and gold. Historically, Bitcoin has shown a correlation with the S&P 500, reflecting the broader market trends. However, recent trends indicate a decoupling of Bitcoin from the S&P 500 and a growing correlation with gold. This essay explores the factors contributing to this shift and the implications for investors.
One of the primary reasons for Bitcoin's decoupling from the S&P 500 is the evolving perception of Bitcoin as a store of value rather than a speculative asset. As inflation concerns rise and central banks adopt expansive monetary policies, investors are increasingly looking for assets that can preserve value. Gold has long been regarded as a safe haven during economic uncertainty, and Bitcoin is increasingly being viewed in a similar light. This shift in perception has led to a growing correlation between Bitcoin and gold, as both assets are seen as hedges against inflation and currency devaluation.
Additionally, the increasing institutional adoption of Bitcoin has played a crucial role in its decoupling from traditional equities. Major corporations and institutional investors are now allocating a portion of their portfolios to Bitcoin, viewing it as a digital gold. This institutional interest has provided Bitcoin with a level of legitimacy and stability that was previously lacking, allowing it to operate independently of the stock market's fluctuations. As more institutional players enter the Bitcoin market, the asset's price movements may become less influenced by the broader economic conditions that affect the S&P 500.
Moreover, the unique characteristics of Bitcoin, such as its limited supply and decentralized nature, further differentiate it from traditional equities. Unlike stocks, which can be influenced by company performance and market sentiment, Bitcoin's value is driven by supply and demand dynamics within its own ecosystem. The halving events, which reduce the rate at which new Bitcoins are created, create scarcity and can lead to price appreciation independent of stock market trends.
In conclusion, the decoupling of Bitcoin from the S&P 500 and its coupling with gold can be attributed to a combination of factors, including a shift in perception towards Bitcoin as a store of value, increasing institutional adoption, and its unique characteristics as a digital asset. As investors seek alternatives to traditional assets in an uncertain economic landscape, Bitcoin's role as a hedge against inflation and currency devaluation is likely to strengthen. This evolving relationship between Bitcoin, gold, and traditional equities will continue to shape the investment landscape in the years to come.
Yesterday I fixed my neighbor's computer. He laughed at me for being into Bitcoin. We are still early.
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ e4950c93:1b99eccd
2025-05-02 09:36:09
@ e4950c93:1b99eccd
2025-05-02 09:36:09Tu as trouvé un produit naturel ? Partage-le ici en commentant cette page !
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations dont tu disposes. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ 99556507:a6cf5c08
2025-05-02 09:19:37
@ 99556507:a6cf5c08
2025-05-02 09:19:37El paradigma del trabajador común aceptado en nuestra era es trabajar duro durante 40 años por un salario para tener derecho a una jubilación los últimos 20 o con suerte 25 años de vida.
Pero ¿es ésto lo más rentable? ¿Hay otras alternativas?
Vamos a ponernos en la piel de un asalariado o un autónomo que ha cotizado durante 30 años por la base máxima y está a una década todavía de poder jubilarse. ¿Le conviene trabajar esa década para tener derecho a la pensión estatal? ¿O es una estafa?
Hagamos números: La cotización máxima del autónomo o la del empresario a cuenta del trabajador hoy en día es de 1.472€/mes, 12 pagas al año, o 17.664€/año. En 10 años, y considerando una inflación del 4% anual, pagará 202.075€ en cotizaciones sociales.
El cotizante que haya pagado esto durante toda su vida laboral tiene derecho a la jubilación máxima, que hoy es de 3.267€/ mes, 14 pagas al año, o 45.746,40€/año. Si pensamos que la esperanza de vida en España es de 83 años y se tiene derecho a la jubilación a los 67, significa que un pensionista medio recibirá la pensión durante 16 años. Pero vamos a a hacer las cuentas para Matusalén, el pensionista pesadilla para el gobierno y las aseguradoras, que llegará a cumplir los 92 años, recibiendo la pensión durante 25 años.
Asumamos que el gobierno, que necesita imperiosamente los votos de los 7 millones de pensionistas, seguirá revalorizando las pensiones con el IPC oficial, es decir, a una media del 4% anual.
Matusalén se jubilará a los 67 y recibirá a lo largo de sus 25 años de pensionista la cantidad de 1.905.000€(1), de los cuales tendrá que pagar alrededor de un 28% de impuestos.
[(1) 45.746,40*(1-1,0425)/(1-1.04)] = 1.905.150
Es decir, Matusalén pagará 202.000€ en total a lo largo de 10 años para recibir 1.905.000€ distribuidos durante los siguientes 25. Parece un buen negocio, ¿no?
Pero, y si Matusalén, que es una persona cabal y ahorradora, ha ido haciendo una hucha durante sus 30 años de vida laboral a razón de 1000€ al mes, de manera que ahora ya dispone de esos 202.075€ necesarios para pagar sus cotizaciones hasta la edad de jubilación, y además le sobran 160.000€ para sus gastos la próxima década, a razón de 16.000€/año, que deberían de ser suficiente para vivir, puesto que esta cantidad es justo el salario mínimo interprofesional actual. ¿Le merece la pena seguir trabajando o puede plantearse dejar de hacerlo y usar esos ahorros para pagar sus cotizaciones de los siguientes 10 años, y tener derecho a la jubilación cuando cumpla 67 años?
O ya puestos a hacer cuentas, dado que tiene un capital disponible de 202.000€ en el banco, ¿podría pensar en alguna inversión alternativa que revalorizara su dinero de manera que mejorase las prestaciones de su jubilación (los 1.905.000€ calculados antes)?
Aquí es donde sale a jugar la fórmula del interés compuesto: Cf = Ci * (1+Rn), donde: Cf: capital final (queremos llegar a 1.905.000€) Ci: capital inicial (los 202.075€ de Matu) R: tasa de interés anual (CAGR) n: numero de años de la inversión (10)
¿Qué crecimiento anual compuesto (CAGR) necesitaría Matu para obtener el total de lo que nos daría su pensión tras 25 años, pero en tan solo 10 años, de manera que pudiera disponer de todo ese capital incluso antes de jubilarse? Haciendo las cuentas, R = (Cf/Ci-1)(1/n) = 23.09 %
Por si has llegado hasta aquí pero te has perdido por el camino, acabamos de concluir que una persona que invierta hoy 202.075€ en un producto que rente un 23,09% anual, obtendrá 1.905.000€ en 10 años, el equivalente a toda su jubilación.
Pues esto parece incluso mejor que la alternativa anterior, ¿no? Pero claro, hay que encontrar un producto que garantice esta rentabilidad sostenida durante una década. ¿Qué podría ser? A esta alturas, si sigues por aquí, ya habrás podido intuir por dónde van los tiros. Lo único que ha garantizado esta revalorización hasta la fecha es #bitcoin.
Éste el el cuadro del CAGR de Bitcoin tabulado por años. Se lee de la siguiente manera: A finales de 2024, la columna "CAGR 2024" da el CAGR (rendimiento anual compuesto) para la diferencia de años entre 2024 y el año de la cifra que estemos mirando. Por ejemplo, el CAGR a 31/12/2024 de una inversión realizada el 31/12/2023, es decir de 1 año, es del 276,92%. Si la inversión se realizó el 31/12/2016, el CAGR 8 años después, a final de 2024, es del 78,22% ANUAL
(Ver imagen 1)
El tío Matusalén está buscando algo que le dé un mínimo del 23,09% anual, ¿recordáis?. Pues da igual cuándo haya invertido y cuánto tiempo mantenga la inversión. BTC siempre supera ese umbral, por mucho.
"Ya Manolito, pero estás mirando rendimientos desde finales de 2024, cuando Bitcoin hizo un precio máximo histórico. Esto no asegura que haya ocurrido esto cada año, ¿no?"
El siguiente cuadro muestra los CAGR calculados a finales de cada año, los últimos 6 años. Las cifras en verde corresponden a los rendimientos de inversiones mantenidas 10 años. No podemos ir más para atrás porque Bitcoin acaba de cumplir 16 años.
(ver imagen 2)
No es difícil comprobar que a 10 años vista, bitcoin siempre ha superado de largo esta tasa de crecimiento.
*Consideraciones fiscales ** La pensión máxima devenga impuestos sobre la base de rentas del trabajo a razón del 28% anual, mientras que las inversiones tributan a un máximo del 26% sobre la base de las rentas de capital, suponiendo que se recupere todo el mismo año. Si se distribuyen los rendimientos plurianualmente, ese 26% puede reducirse entono al 21%, suponiendo otro 7% anual de ventaja neta sobre la pensión. En el caso particular de Matusalén, los 45.746,40€ anuales de su pensión tributarían íntegros al 28%, por lo que los 1.905.150 se quedarían netos en 823.435,20€ al cabo de 25 años. Si hubiese optado por invertir los 202.075€ en Bitcoin, y suponiendo que la rentabilidad obtenida es solo la necesaria para conseguir los 1.905.150€, tributaría al 26% sobre la ganancia si decide convertirlos en € de una vez, es decir, pagaría 26%(1.905.150-202.075)=442,800€, con lo que le quedarían netos 1.462.350€. Si decide por el contrario vender solo bitcoins cada año por valor de 45,746€, y suponiendo que mantienen el mismo valor en € durante los 25 años, pagaría el 21% sobre la plusvalía, es decir 357.645€ a lo largo de los 25 años por lo que le habrá quedado neto 1.547.504€.
Resumiendo: Renta neta con la pensión estatal tras 25 años: 823.435€ Renta neta con el plan de inversión en bitcoin, con rescate en una vez, el año 0: 1.462.350€ Renta neta con el plan de inversión en bitcoin, con rescate a lo largo de 25 años: 1.547.504€
Hay que recordar que todo el ejercicio está realizado para el mejor caso del pensionista estatal, que vivirá muy por encima de la media. Cualquier número de años inferior mejorará la rentabilidad del plan de bitcoin respecto al estatal.
Conclusión: Al bueno de Matu más le vale comprar bitcoins hoy mismo con ese dinero ahorrado. No solamente no necesitará una pensión sino que lo más probable es que sus ahorros valgan 5 veces más que lo que conseguiría de pensionista, pero 25 años antes.
-
 @ 4fe4a528:3ff6bf06
2025-04-01 12:32:20
@ 4fe4a528:3ff6bf06
2025-04-01 12:32:20Ever since Mark Carney told the CEOs of the Canadian banks to freeze the truckers bank accounts there has been a growing acceptance that the money you have in a Canadian bank account isn’t yours; it belongs to Mark Carney. Now that there is another election in Canada we will decide who gets to prints the monies for us. There have been a lot of changes in the banking system since Mark Carney borrow money from China. Who is your master?
Banking changes that affected me today. 1. The Canadian Tire doesn’t accept Canadian cash to pay off your credit card. 2. You can’t use your Canadian Tire points unless you have your physical card in the store with you. 3. Some grocery and feed stores don’t accept bitcoin directly. SWIFT banking changes. 1. Stable Coins are a thing now. 2. Tether for outside the USA 3. Circle / XRP for inside the USA Let the best coin win. The bill should pass in the US senate by summer Bitcoin banking changes 1. More and more nodes are hosting friends and family via their LNURL accounts. 2. The USA now has bitcoin as an asset on their Strategic Reserve 3. Bitcoin Hashrate went from 550 EH/s to 990 EH/S in the last 12 months. I think the electrical usage has almost double also. 4. Tether brings USDT to Bitcoin’s Lightning Network, ushering in a New Era of Unstoppable Technology, now the world's largest stablecoin is part of the Lightning Network - Download the Joltz App today.
By my next news letter we should know who will be leading Canada. This is the current psychological warfare going on. 1. Push back against carbon taxes? You’re labeled a “climate denier.” 2. Stand up for provincial rights? You’re smeared as “anti-democratic.” 3. Question Carney’s globalist agenda? You’re branded an “extremist.”
Who do you think will be enforcing their will on Canadians in 28 days? Do you think Elections Canada will be keep the elections fair? I hope these articles help you on your hard money journey. Hopefully you can get what you want out of life - don’t sell your birthright. We are all in this together. Watch “The big Red Button” before May 1, 2025 (my next email)
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:42:53
@ 8f69ac99:4f92f5fd
2025-05-02 08:42:53O ADN (Alternativa Democrática Nacional) apresenta-se às eleições de 2025 com um programa orgulhosamente anti-sistema, culturalmente conservador e auto-descrito como “colocar os portugueses em primeiro lugar”. O seu programa soa a uma rutura radical com a política tradicional—misturando políticas familiares fortes, ceticismo em relação à moeda digital e retórica descentralizadora com prescrições morais rígidas e propostas de saneamento institucional.
Mas, sob a superfície, a visão de liberdade do partido é seletiva. O ADN defende a autonomia financeira, promove a transparência e propõe a redução da burocracia—mas também advoga a imposição estatal de normas culturais, o controlo do acesso a direitos e uma autoridade moral centralizada, levantando sérias dúvidas sobre a coerência na defesa da liberdade individual.
Os Pontos Positivos: Autonomia Financeira e Disciplina Institucional
Em algumas áreas, o ADN parece alinhar-se com princípios de liberdade económica e responsabilização institucional. Propõe:
- Acabar com o financiamento público dos partidos políticos, regalias dos deputados e as portas giratórias entre o jornalismo e o governo.
- Proteger o dinheiro físico e as criptomoedas descentralizadas da vigilância dos bancos centrais.
- Limitar despesas extraordinárias do Estado, reduzir a frota automóvel pública e combater as comissões bancárias abusivas.
Estas propostas respondem a preocupações reais com o excesso de poder estatal, a governação opaca e o controlo tecnocrático. Um Estado transparente e frugal, aliado a um sistema monetário baseado na troca voluntária, reflete instintos liberais genuínos.
As Contradições: Liberdade, Mas Só Para Alguns
O ADN promove valores como a liberdade, a família e a dignidade—mas impõe limites rígidos à forma como os indivíduos definem e expressam esses mesmos valores.
- O partido compromete-se a banir todo o conteúdo LGBT+ e a chamada “ideologia de género” do ensino público, a restringir os direitos de transição de género (especialmente para menores) e a revogar a legislação sobre aborto e eutanásia, mesmo quando baseada na escolha individual.
- Propõe ainda retirar o apoio estatal a organizações que defendem direitos ligados ao género ou identidade.
Aqui, a linha entre proteger as crianças e impor uma moral única torna-se difusa. O ADN não propõe apenas retirar a influência do Estado na educação—substitui-a por um filtro cultural rígido, imposto de cima. Ao fazê-lo, põe em risco a liberdade de consciência e a autoridade parental para quem não se conforma com a norma dominante.
Prioridade pelo Passaporte: Soberania à Custa da Igualdade de Acesso
O ADN defende de forma consistente a preferência por cidadãos portugueses no acesso à habitação pública, serviços sociais e apoios estatais. Embora popular, esta abordagem assume implicitamente que os bens públicos são privilégios, e não direitos ligados à contribuição individual ou necessidade.
Isto abre espaço para discriminação institucionalizada, independentemente do estatuto legal ou da participação fiscal. Uma sociedade verdadeiramente liberal assenta na igualdade perante a lei, e não na distribuição seletiva de benefícios com base na identidade.
Ceticismo Climático e Científico: Rejeição Sem Alternativa
O partido classifica a política climática como “fraude climática” e opõe-se à geoengenharia, embora defenda a energia nuclear e “mercados livres de energia”. No entanto, rejeitar por completo a intervenção climática—sem apresentar alternativas baseadas na inovação descentralizada—deixa um vazio onde poderia florescer uma verdadeira gestão ambiental voluntária e local.
Soluções ambientais baseadas na liberdade incluem conservação liderada por proprietários, precificação de carbono pelos mercados e autonomia energética local—não a negação dos riscos ou do consenso científico.
Referendos e Democracia Direta: Ferramentas Poderosas, Resultados Arriscados
O ADN propõe alargar o uso de referendos, contratos eleitorais vinculativos e maior consulta pública. Estas reformas descentralizam o poder no papel—mas sem salvaguardas constitucionais, correm o risco de se tornarem instrumentos de imposição da vontade da maioria, onde minorias impopulares ficam vulneráveis ao controlo plebiscitário.
Liberdade não é apenas “mais democracia”. É também proteger os direitos individuais contra abusos—tanto do Estado como da maioria.
Conclusão: A Liberdade Não Pode Ser Seletiva
O ADN promete soberania, transparência e responsabilidade—e, em algumas áreas, entrega. Mas o seu modelo mais abrangente impõe uma visão moral estreita, centraliza a autoridade cultural e define direitos com base na identidade e na tradição, em vez da universalidade.
Uma sociedade livre não protege apenas a tua família, a tua fé ou a tua moeda—protege também o direito do teu vizinho de viver de forma diferente.
Para quem procura verdadeira descentralização, associação voluntária e liberdade face à coerção—seja estatal ou cultural—é importante ponderar se a visão do ADN alarga a liberdade ou apenas transfere o controlo de Bruxelas para Lisboa, e de burocratas para vigilantes morais**.
Photo by Claudio Schwarz on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:35:48
@ 8f69ac99:4f92f5fd
2025-05-02 08:35:48O partido nacionalista Ergue-te apresenta uma crítica abrangente ao globalismo, ao multiculturalismo e às reformas sociais progressistas. O seu programa eleitoral para 2025 posiciona-se como uma defesa da “civilização portuguesa e europeia”, propondo o desmantelamento do enquadramento federal da UE, o regresso às leis de nacionalidade baseadas no ius sanguinis e a reversão de políticas que classifica como “ideologia de género” ou “suicídio cultural”.
Há que reconhecer ao Ergue-te a ênfase na soberania, na descentralização face a instituições supranacionais e na autodeterminação nacional—valores que ressoam com quem quer aproximar o poder das comunidades e afastá-lo de burocracias não eleitas. Mas o seu modelo de liberdade termina na fronteira nacional.
Uma vez resgatado o poder de Bruxelas, o programa do partido sugere que este seja centralizado em Lisboa—não para capacitar os cidadãos, mas para impor uma cultura nacional uniforme. O resultado não é descentralização, mas sim autoritarismo cultural sob uma bandeira nacionalista.
Descentralização da UE, Recentralização Interna
O Ergue-te rejeita o Tratado de Lisboa e defende uma confederação de nações europeias unidas apenas por acordos voluntários e revogáveis. Esta visão critica, com razão, a centralização crescente de poder na UE.
Contudo, embora o partido queira repelir o controlo externo, não demonstra o mesmo cepticismo em relação ao excesso de poder doméstico. Entre as suas propostas estão:
- Proibição da chamada “ideologia de género” em todas as escolas públicas.
- Revogação do casamento entre pessoas do mesmo sexo, da despenalização do aborto e das leis da eutanásia.
- Reintrodução de linguagem binária e baseada no sexo biológico na educação cívica.
- Fim do financiamento público a organizações que promovam valores “não tradicionais”.
Estas medidas substituem o domínio externo por uma moralidade estatal imposta internamente. A liberdade cultural não está mais protegida por ser legislada em Lisboa do que por ser decidida em Bruxelas.
Soberania sobre a Cidadania, Não Liberdade dentro dela
O Ergue-te propõe alterar a lei da nacionalidade portuguesa para um modelo baseado no sangue (ius sanguinis), limitando o acesso à cidadania a imigrantes e seus filhos, independentemente da sua integração ou contribuição para a sociedade.
Com esta proposta, o partido desvaloriza o princípio de que a cidadania deve assentar em direitos e responsabilidades individuais—e não em linhagem. A soberania torna-se assim um mecanismo de exclusão, e não uma base de participação cívica.
Ordem Moral pela Lei
Apresentada como uma defesa da “vida e da família”, a política social do partido visa anular décadas de liberalização legal. Defende:
- Fim do financiamento público ao aborto, salvo em situações médicas urgentes.
- Revogação da legislação sobre eutanásia.
- Anulação do casamento entre pessoas do mesmo sexo.
Embora apresentadas como salvaguarda da tradição, estas propostas implicam a codificação legal de uma visão moral única, à custa da autonomia pessoal e do pluralismo. A liberdade de escolher o próprio modelo familiar, as crenças ou decisões médicas é rejeitada em favor da conformidade imposta.
Imigração e Islão: Política Culturalmente Direccionada
O programa do Ergue-te opõe-se abertamente ao multiculturalismo e alerta para a “islamização da Europa”. Defende controles fronteiriços mais apertados e a prevenção da imigração não europeia, com o objectivo de preservar uma “homogeneidade cultural”.
Este discurso, envolto em retórica identitária, abre caminho para a punição colectiva e exclusão cultural. Confunde imigrantes com ideologias, negando-lhes a oportunidade de serem avaliados pelo seu mérito ou conduta. Assume ainda que a cultura nacional é estática e frágil—em vez de algo que as comunidades constroem e renegoceiam livremente.
Defesa e Política Externa: Um Duplo Critério
O partido apoia uma capacidade de defesa europeia, mas apenas como associação subordinada às forças armadas nacionais. Aponta a soberania militar como resposta a potências como os EUA ou a China—mas é vago quanto à forma como o nacionalismo militarizado promove a liberdade ou a paz.
A segurança não pode servir de pretexto para mobilização permanente nem para uma política fechada sobre si mesma. A verdadeira independência exige diplomacia, resiliência e abertura ao mundo—não apenas músculo militar.
Conclusão: A Liberdade Exige Mais do que uma Bandeira
O Ergue-te apresenta-se como defensor da soberania. Mas o seu programa sugere que a soberania pertence ao Estado, e não ao indivíduo. Combate a influência externa, mas convida à imposição interna. Diz defender a tradição, mas fá-lo por via da coerção, não do consentimento.
Uma política centrada na liberdade permite que as pessoas vivam de forma diferente, não apenas que resistam a Bruxelas. Dá espaço para que as famílias se formem nos seus próprios termos, para que os imigrantes se tornem vizinhos, e para que os cidadãos debatam em vez de obedecerem.
Na sua busca por ordem e identidade, o Ergue-te oferece controlo—não liberdade.
Photo by Claudio Schwarz on Unsplash
-
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:28:02
@ 8f69ac99:4f92f5fd
2025-05-02 08:28:02O partido Pessoas–Animais–Natureza (PAN) apresenta uma plataforma serena e voltada para o futuro nas legislativas de 2025—uma que combina consciência ecológica, bem-estar animal e reformas sociais progressistas com um surpreendente toque de pragmatismo económico. Da saúde mental ao salário mínimo, dos direitos dos animais à redução de emissões, o PAN aborda quase todas as áreas da política pública com um impulso moral unificador: proteger os vulneráveis—sejam humanos ou não.
Mas apesar da sua compaixão, o programa do PAN levanta uma questão central: pode uma sociedade expandir a liberdade confiando fortemente numa moralidade imposta pelo Estado e numa engenharia comportamental? Ou, mais directamente: quando a política pretende “fazer o bem”, quem decide o que isso significa—e até onde deve o Estado ir para o impor?
Acção Climática: Urgência de Cima para Baixo ou Autonomia Local?
A missão central do PAN é a acção climática. O partido opõe-se à exploração de combustíveis fósseis, defende uma transição total para as energias renováveis e apoia grandes investimentos no transporte público e na conservação da natureza.
Estes objectivos alinham-se com a resiliência a longo prazo—mas os métodos são quase exclusivamente liderados pelo Estado. Há pouca menção a instrumentos de mercado como o preço do carbono, a conservação baseada na propriedade privada ou a autonomia energética local. O plano parte do princípio de que o caminho é o controlo tecnocrático e o investimento centralizado.
Contudo, a liberdade prospera onde as soluções são descentralizadas, impulsionadas pela inovação privada, pela cooperação voluntária e pela experimentação de base. Ao manter o Estado no centro da reforma ecológica, o PAN corre o risco de reproduzir as mesmas estruturas de dependência que pretende ultrapassar.
Bem-Estar Animal: Uma Visão Ética com Ferramentas Coercivas
O PAN merece reconhecimento por ter trazido a protecção animal para o debate político nacional. O seu apelo à proibição da agropecuária industrial, à reforma legislativa e à integração da ética animal no ordenamento jurídico reflecte uma posição moral sincera.
Mas, novamente, o método escolhido é a proibição legal, e não a persuasão ou a evolução do mercado. O salto entre a preocupação ética e os mandatos de estilo de vida impostos—sobretudo por reguladores não eleitos—pode rapidamente resvalar para a coerção em vez da consciência. Uma sociedade livre deve acomodar visões diversas sobre alimentação, agricultura e ética, permitindo que os sinais do mercado e o discurso civil orientem os comportamentos, em vez de impor proibições generalizadas.
Política Social Progressista: Compaixão com Centralismo
O apoio do PAN à eutanásia, à reforma da saúde mental, às leis anti-discriminação e ao apoio à população idosa reflecte uma preocupação genuína com a inclusão social. O foco na saúde mental e no combate à solidão é particularmente humano.
No entanto, quase todas estas reformas são enquadradas como expansão de programas e mandatos estatais, em vez de iniciativas comunitárias, redes de entreajuda ou modelos de cuidado centrados na família. Há pouca ênfase em soluções voluntárias, parcerias com o sector privado ou iniciativas de base—apenas um apelo repetido, e repetitivo, a mais programas públicos, mais intervenção estatal e mais regulamentação.
Pragmatismo Económico: Uma Viragem Bem-Vinda (mas Incompleta)
Um dos elementos mais surpreendentes do PAN é a sua defesa da redução do IRC para 17% até 2028, da isenção de IVA em bens essenciais, e de benefícios fiscais para jovens trabalhadores. São raros sinais de liberalização económica—e revelam que o partido está atento às dificuldades causadas pela inflação e estagnação salarial.
Ainda assim, o PAN continua a assumir que o Estado deve ajustar comportamentos através de alavancas fiscais: incentivos, isenções, apoios dirigidos. A verdadeira liberdade económica implica simplificação fiscal, redução das distorções e confiança na ordem espontânea—não apenas redistribuir com um selo verde.
Independência Política: Aberto a Todos, Ligado a Todos?
O PAN afirma ser politicamente independente, colaborando com a esquerda e o centro consoante a convergência com a sua missão. Esta flexibilidade é louvável. No entanto, independência de alianças não equivale a independência de método. Ao longo do programa, o fio condutor é uma aposta na expansão institucional—e não na iniciativa pessoal.
Para um partido que defende a diversidade, há pouca margem para diversidade ideológica na forma como as pessoas vivem, trabalham e se relacionam com o mundo natural.
Conclusão: Ética sem Autoritarismo Seria Mais Forte
O PAN traz temas importantes para a mesa. A sua bússola ecológica e ética enriquece a democracia portuguesa. Mas a liberdade não pode ser usada apenas como instrumento para “boas causas”—deve ser um travão ao excesso de confiança do poder político motivado por causas.
Uma sociedade que cuida dos animais, do planeta e dos vulneráveis deve também confiar nos seus cidadãos para escolher como viver esses valores—em vez de os impor de cima.
No final, boas intenções não garantem liberdade. E a liberdade, quando bem defendida, alcança muitas vezes mais do que qualquer regulação poderia.
Photo by Claudio Schwarz on Unsplash
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 6be5cc06:5259daf0
2025-03-23 21:39:37
@ 6be5cc06:5259daf0
2025-03-23 21:39:37O conceito de Megablock propõe uma nova maneira de medir o tempo dentro do ecossistema Bitcoin. Assim como usamos décadas, séculos e milênios para medir períodos históricos na sociedade humana, o Bitcoin pode ser dividido em Megablocks, cada um representando 1 milhão de blocos minerados.
1. Introdução
O Bitcoin opera em um sistema baseado na mineração de blocos, onde um novo bloco é adicionado à blockchain (ou timechain) aproximadamente a cada 10 minutos. A contagem de tempo tradicional, baseada em calendários solares e lunares, não se aplica diretamente ao Bitcoin, que funciona de maneira independente das convenções temporais humanas.
A proposta do Megablock surge como uma alternativa para medir o progresso da rede Bitcoin, dividindo sua existência em unidades de 1 milhão de blocos, permitindo uma estruturação do tempo no contexto da blockchain. Entretanto, diferentemente de medidas fixas de tempo, como anos e séculos, o tempo de um Megablock futuro não pode ser previsto com exatidão, pois variações no hashrate e ajustes de dificuldade fazem com que o tempo real de mineração flutue ao longo dos anos.
2. Definição do Megablock
2.1 O que é um Megablock?
Um Megablock é uma unidade de tempo no Bitcoin definida por um ciclo de 1.000.000 de blocos minerados. Com a taxa de geração de blocos mantida em 10 minutos por bloco, podemos estimar:
1 Megablock ≈ 1.000.000×10 minutos = 10.000.000 minutos = 166.666,7 horas = 6.944,4 dias ≈ 19 anos
Entretanto, dados históricos mostram que a média real de tempo por bloco tem sido levemente inferior a 10 minutos. Ao analisar os últimos 800.000 blocos, percebemos que cada 100.000 blocos foram minerados, em média, 1 a 2 meses mais rápido do que o previsto. Com variações indo de 2 dias a 3 meses de diferença. Esse ajuste pode continuar mudando conforme o hashrate cresce ou desacelera
Isso significa que o Megablock não deve ser usado como uma métrica exata para previsões futuras baseadas no calendário humano, (apenas aproximações e estimativas) pois sua duração pode variar ao longo do tempo. No entanto, essa variação não compromete sua função como uma unidade de tempo já decorrido. O conceito de Megablock continua sendo uma referência sólida para estruturar períodos históricos dentro da blockchain do Bitcoin. Independentemente da velocidade futura da mineração, 1 milhão de blocos sempre será igual a 1 milhão de blocos.
2.2 Estrutura dos Megablocks ao longo da história do Bitcoin
| Megablock | Início (Bloco) | Fim (Bloco) | Ano Estimado (margem de erro: ±2 anos) | | ---------------- | ------------------ | --------------- | ------------------------------------------ | | 1º Megablock | 0 | 1.000.000 | 2009 ~ 2027 | | 2º Megablock | 1.000.001 | 2.000.000 | 2027 ~ 2045 | | 3º Megablock | 2.000.001 | 3.000.000 | 2045 ~ 2064 | | 4º Megablock | 3.000.001 | 4.000.000 | 2064 ~ 2082 | | 5º Megablock | 4.000.001 | 5.000.000 | 2082 ~ 2099 | | 6º Megablock | 5.000.001 | 6.000.000 | 2099 ~ 2117 | | 7º Megablock | 6.000.001 | 7.000.000 | 2117 ~ 2136 |
- Nota sobre o primeiro Megablock: Do Bloco Gênese (0) ao Bloco 1.000.000, serão minerados 1.000.001 blocos, pois o Bloco 0 também é contado. O milionésimo bloco será, na realidade, o de número 999.999. Nos Megablocks subsequentes, a contagem será exatamente de 1.000.000 de blocos cada.
O fornecimento de Bitcoin passará por 6 Megablocks completos antes de atingir seu total de 21 milhões de BTC, previsto para acontecer no Bloco 6.930.000 (7º Megablock), quando a última fração de BTC será minerada.
Se essa tendência da média de tempo por bloco ser ligeiramente inferior a 10 minutos continuar, o último bloco com recompensa pode ser minerado entre 2135 e 2138, antes da previsão original de 2140.
De qualquer forma, o Megablock não se limita ao fornecimento de novas moedas. O último bloco com emissão de BTC será o 6.930.000, mas a blockchain continuará existindo indefinidamente.
Após a última emissão, os mineradores não receberão mais novas moedas como recompensa de bloco, mas continuarão garantindo a segurança da rede apenas com as taxas de transação. Dessa forma, novos Megablocks continuarão a ser formados, mantendo o padrão de 1.000.000 de blocos por unidade de tempo.
Assim como o 1º Megablock marca a era inicial do Bitcoin com sua fase de emissão mais intensa, os Megablocks após o fim da emissão representarão uma nova era da rede, onde a segurança será mantida puramente por incentivos de taxas de transação. Isso reforça que o tempo no Bitcoin continua sendo medido em blocos, e não em moedas emitidas.
3. Benefícios do Conceito de Megablock
3.1 Estruturação do Tempo Já Decorrido
Os Megablocks permitem que os Bitcoiners analisem a evolução da rede com uma métrica clara e baseada no próprio protocolo, estruturando os períodos históricos do Bitcoin.
3.2 Comparação com Unidades Temporais Humanas
Assim como temos décadas, séculos e milênios, podemos organizar a história do Bitcoin com Megablocks, criando marcos temporais claros dentro da blockchain:
- 1 Megablock ≈ 17 a 19 anos (equivalente a uma “geração” no tempo humano)
- 210.000 blocos = ~4 anos (ciclo de halving do Bitcoin)
3.3 Aplicação na História do Bitcoin
Podemos usar Megablocks para marcar eventos históricos importantes da rede:
- O 1º Megablock (2009 ~ 2026/2028) engloba a criação do Bitcoin, os primeiros halvings e a adoção institucional.
- O 2º Megablock (2027 ~ 2044/2046) verá um Bitcoin muito mais escasso, possivelmente consolidado como reserva de valor global.
- O 3º Megablock (2045 ~ 2062/2064) pode ser uma era de hiperbitcoinização, onde a economia gira inteiramente em torno do BTC.
4. Conclusão
O Megablock é uma proposta baseada na matemática da rede para medir o tempo já decorrido no Bitcoin, dividindo sua história em unidades de 1 milhão de blocos minerados. Essa unidade de tempo permite que Bitcoiners acompanhem o desenvolvimento e registrem a história da rede de maneira organizada e independente dos ciclos arbitrários do calendário humano.
Estamos atualmente formando o Primeiro Megablock, assim como estamos vivendo e construindo a década de 2020 e o século XXI. Esse conceito pode se tornar uma métrica fundamental para o estudo da história do Bitcoin, reforçando a ideia de que no Bitcoin, o tempo é medido em blocos, não em relógios.
Você já imaginou como será o Bitcoin no 3º ou 4º Megablock?
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 57d1a264:69f1fee1
2025-05-02 06:17:05
@ 57d1a264:69f1fee1
2025-05-02 06:17:05Simple design
For as long as I remember, I’ve believed in simple design as a principle in my practice. It feels fundamental to me when I think about good design.
At the same time, I see many successful examples of complex products in the world. So I decided to ask, what value is simple design really providing me and my work?
Is it nostalgia?
I sometimes wonder if simple design is rooted in nostalgia. An example I like to use is:
Imagine yourself in the year 1981. You just purchased a brand new desk calculator. You are excited because you should be able to do any type of paperwork calculations you can imagine on it.
As you start to use it for the first time, it immediately prompts you to update its software. After using it for a few calculations, it asks you to fill out a survey about your experience. One day in the middle of adding up your checkbook, it interrupts you to tell you about a new leather-bound desk calendar the company just released. Sometimes in the middle of a complex calculation, the calculator will lag and crash. You have to restart it often to fix the issue.
I have a feeling that a person in 1981 would think this is a terrible calculator. They purchased the device to perform their calculations, nothing more. Why is it requiring so much more of their attention and effort?
Focus
I think simple design often refers to a focused product. A product that does a specific task can sometimes do that task really well. Products that try to do many things can offer a lot of value, but rarely do all the things well.
Some people prefer to use specific tools for specific tasks. Others prefer a wide variety of features.
I think the benefits of using fewer products are often a major reason complex products are successful. They may not be focused, they might be lower quality as a result, but people can use them for a wide variety of applications.
You can open a can of beans with a Swiss Army Knife — it will get the job done.
Art and subjectivity
Maybe simple design is valuable for intangible reasons. There is an art to simplicity. There is a beauty to simplicity.
A user can see more of the product's intentionality. The creator chose to leave certain features out. They decided what to include. The product likely exudes more vision and personality.
That might be unnoticed by some, but very valuable to others who care about craft. People who value the experience as much as the result.
Ease of use
I think a true benefit of simple design is the effect it has on ease of use. The less things there are to do in a product, the more obvious the things you can do become.
A simple product requires less of a user. That means a user can stay focused on their own needs and use the product in ways they define. They will encounter boundaries which limit them. These limitations could drive some away, but some might be engaged to find new and creative ways of working.
When to abandon simple design
I think the sad news is simple design is ultimately a limiting factor of a product's growth. I think there are many examples of this throughout the course of history (i.e. Ello vs Facebook, Rdio vs Spotify, Simplenote vs Notion, VSCO vs Instagram, Clear vs Things, Peach vs Twitter, etc). At the same time, I think 'simple design' does provide an entry point to successfully define what a product is.
The biggest challenge is continuing to evoke the benefits of simple design in an established product, while allowing a product to evolve and grow to meet its users' needs. That is a balancing act that very few products have ever achieved, but feels like an ideal that successful products should strive for.
One of Charlie Deets Writings
originally posted at https://stacker.news/items/969089
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 57d1a264:69f1fee1
2025-05-02 06:04:19
@ 57d1a264:69f1fee1
2025-05-02 06:04:19After being featured in the NY Times and WSJ, New York City officially opens a major addition to Central Park, the Davis Center at the Harlem Meer. Designed by architect Susan T Rodriguez in collaboration with Mitchell Giurgola, the renovation project replaces the old Lasker Rink and pool with a recreational facility that’s built directly into the landscape, restoring nature, reconnecting paths, and creating a year-round space for community activity. At the heart of the new design is a transformative water feature that shifts with the seasons, from a skating rink in winter to a lush green lawn in spring and fall and a pool in the summer.
The center’s new oval-shaped pool sits lower than the old one, surrounded by a gently sloped grassy berm. In winter, the pool becomes an ice-skating rink, making the site a destination in every season. A splash pad at the end of the water feature offers extra water play in the summer. By integrating the design into the natural shape of the land, the architects were able to open up the space around the pool and allow the landscape to flow around it, resulting in a setting that feels like it’s always been there.
Sustainability was a core part of the project. The building is expected to earn LEED Gold certification, thanks to features like passive ventilation, locally sourced stone and wood, energy-efficient systems, and a roof that absorbs rainwater. Bird-safe glass helps protect local wildlife, and recycled materials from the old building were reused during construction. Even more important, the new center supports free and low-cost programming year-round, including education, nature walks, community events, and recreation. It’s designed to welcome all kinds of visitors—from families and school groups to joggers, birdwatchers, and casual parkgoers.
Continue reading: https://www.designboom.com/architecture/giant-pool-new-york-central-park-new-davis-center-susan-t-rodriguez-mitchell-giurgola-04-24-2025/
originally posted at https://stacker.news/items/969086
-
 @ 97c70a44:ad98e322
2025-03-06 18:38:10
@ 97c70a44:ad98e322
2025-03-06 18:38:10When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specified a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
-
No auth, fully public - anyone can read/write to the group.
-
Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Triflector for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Triflector for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
Rooms have two modes - managed and unmanaged. Managed rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. This allows rooms to switch between managed and unmanaged modes without losing any content.Managed room names come from
kind 39000room meta events, but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access. Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
-
 @ 4fe4a528:3ff6bf06
2025-03-01 12:24:49
@ 4fe4a528:3ff6bf06
2025-03-01 12:24:49Technology adoption has been hard for a lot of people to understand. Tucker this week finally understood why gold became money. He finally understood that hard money drives out money that isn’t scarce. Still, most people don’t store their wealth in the hardest money ever made—Bitcoin.
Yes, Bitcoin went down 20-25% this week. How can the scarcest asset vary that much? Humans tend toward emotion—fear or greed. I am no exception, but if you have a plan or have been here before, you can control your emotion.
Let me illustrate. I installed a camera on the barn this week so I could save time checking on the cows. Lo and behold, the WiFi wasn’t strong enough, so I bought two outdoor access points. Whenever I would add them to the house, the WiFi mesh system would cause my internet to go down on the main computer. Fear of losing internet was causing me to consider taking a $100 write-off on my idea of saving time. Because I have solved networking issues before, I had the courage to be greedy and keep working at it. I know a lot of people would give up on technology and throw their cell phone in the snowbank - my neighbor does that. He usually comes back for it because he likes communication. Is a cell phone a feature or a bug? Answer… both.
What Satoshi solved 16 years ago was how to move 1s and 0s to different devices and keep them secure. What Vint Cerf solved 35 years ago was how to route 1s and 0s and have the packets arrive at the intended destination. Both Bitcoin and the Internet rely on people not throwing their cell phone in the snowbank.
This last drawdown in Bitcoin has given me hope that people will start to understand technology better and give up on Sol and Eth. Finally, people are realizing that printing digital coins doesn’t help people, just like printing Canadian dollars doesn’t help the average Canadian get ahead. It could be that Sam Bankman-Fried is in jail, but I think it has more to do with people starting to get comfortable with technology. https://youtu.be/fxWZO0FEQ1g
-
 @ 57d1a264:69f1fee1
2025-05-02 05:16:39
@ 57d1a264:69f1fee1
2025-05-02 05:16:39Large Language Models (LLMs) have transformed software engineering, but their application to physical engineering domains remains underexplored. This paper evaluates LLMs' capabilities in high-powered rocketry design through RocketBench, a benchmark connecting LLMs to high-fidelity rocket simulations. We test models on two increasingly complex design tasks: target altitude optimization and precision landing challenges. Our findings reveal that while state-of-the-art LLMs demonstrate strong baseline engineering knowledge, they struggle to iterate on their designs when given simulation results and ultimately plateau below human performance levels. However, when enhanced with reinforcement learning (RL), we show that a 7B parameter model outperforms both SoTA foundation models and human experts. This research demonstrates that RL-trained LLMs can serve as effective tools for complex engineering optimization, potentially transforming engineering domains beyond software development.
PDF: https://arxiv.org/pdf/2504.19394
Source: https://arxiv.org/abs/2504.19394
originally posted at https://stacker.news/items/969083
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 318ebaba:9a262eae
2025-05-02 04:57:05
@ 318ebaba:9a262eae
2025-05-02 04:57:05Dies ist ein Test
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 502ab02a:a2860397
2025-05-02 03:05:18
@ 502ab02a:a2860397
2025-05-02 03:05:18เราได้อ่านเรื่อง EVERY eggwhite ไปแล้วคิดว่าเขาจะหยุดแค่นี้ไหมครับ 555555 ไม่มีทางครับ การคืบคลานต้องมีต่อไป วันนี้จะมาในตอนที่ชื่อว่า
EVERY Egg ไข่ยุคใหม่ที่ไม่ต้องใช้แม่ไก่อีกต่อไป ลองนึกภาพ "ไข่เจียว" ที่ไม่มีแม่ไก่เกี่ยวข้องแม้แต่ขนไก่สักเส้น...ใช่เลยจ้ะ โลกตอนนี้ไปถึงจุดที่ ไข่ สามารถผลิตได้จาก “ยีสต์” ที่ถูกดัดแปลงพันธุกรรม เพื่อให้มันสร้าง “โปรตีนไข่” แบบเดียวกับในธรรมชาติ โดยไม่ต้องผ่านแม่ไก่ ไม่ต้องมีเปลือก และแน่นอน...ไม่มีเสียงขันตอนเช้าอีกต่อไป
ผู้เล่นที่น่าจับตาที่สุดคือบริษัท EVERY Company จาก Silicon Valley เจ้าเดิมที่เปิดตัวผลิตภัณฑ์ใหม่ในชื่อ EVERY Egg ซึ่งเป็น “ของเหลว” ที่หน้าตาเหมือนวิปไข่ไก่ แต่เบื้องหลังคือกระบวนการผลิตระดับไซไฟ! พวกเขาใช้เทคนิคที่เรียกว่า precision fermentation หรือ “การหมักแม่นยำ” เพื่อสั่งให้ยีสต์สร้างโปรตีน ovalbumin (โปรตีนหลักในไข่ขาว) และ lysozyme (สารฆ่าเชื้อแบคทีเรียตามธรรมชาติในไข่) ออกมา จากนั้นก็เอามาผสม เติมแต่ง แต่งกลิ่น เติมสี ใส่สารกันเสียเล็กน้อย...ปิ๊ง! ได้ไข่ที่ไม่มีไข่ ได้ใจประชาชนที่กินสารอาหารแบบคลั่งตัวเลข
จุดขายที่ EVERY Company ใช้ในการนำเสนอ EVERY Egg สลุตมาเป็นตับ ตับ ตับ แบบนี้ครับ 1. High quality egg protein ใช้โปรตีน ovalbumin ที่ได้จากกระบวนการ fermentation ด้วย precision fermentation จากยีสต์สายพันธุ์ Pichia pastoris ซึ่งเป็น โปรตีนหลักในไข่ขาวธรรมชาติและเคลมว่าให้คุณสมบัติเทียบเท่าหรือดีกว่าไข่จากไก่ในเรื่องโครงสร้างโปรตีนและการทำงานในอาหาร เช่น การตีขึ้นฟู (foaming) และการอิมัลซิไฟ คุณเอ๊ยยยย ฟลัฟฟลี่สุดๆ 555 2. No hens used เป็น selling point หลักที่สื่อสารหนักมากในเชิง “ไม่เบียดเบียนสัตว์” ดูมีคุณธรรม จึงถูกจัดเป็นมังสวิรัติ (vegan-friendly) แม้จะได้จากจุลินทรีย์ที่ออกแบบให้ผลิตโปรตีนที่เหมือนจากสัตว์ จุดนี้ล่อใจผู้บริโภควีแกนและกลุ่มที่ต่อต้านฟาร์มอุตสาหกรรมอย่างเต็มๆ พร้อมถวิลหา 3. No cholesterol ยังเป็นจุดขายหลักได้ตลอดกาลกับการครอบงำให้กลัวคอเลสเตอรอล เพราะผลิตจากจุลินทรีย์ ไม่ใช่จากสัตว์จริง ๆ จึงไม่มีคอเลสเตอรอลเลย ซึ่งเป็นข้อได้เปรียบเทียบกับไข่ไก่ที่มีคอเลสเตอรอลตามธรรมชาติ 4. No saturated fat พอๆกันครับ ยังเป็นจุดขู่จุดขายได้ตลอดกาลเช่นเดียวกับคอเลสเตอรอล โปรตีนที่ผลิตจากยีสต์ไม่มีไขมันอิ่มตัวเช่นเดียวกับผลิตภัณฑ์จากสัตว์จริง 5. No artificial flavors แหม่ พยายามสร้างภาพลักษณ์ว่าเป็น clean label ไม่ใช้แต่งกลิ่นหรือสารเติมแต่งรส (แม้จะเป็นผลิตภัณฑ์ที่ผ่านกระบวนการขั้นสูงมากก็ตาม) 6. No salmonella จุดที่คนโคตรกลัวเลยในไข่ สังเกตุไหมว่า จัดหนักจัดเน้นขยี้ความกลัวของคนได้ทุกจุด อย่างอันนี้เนื่องจากไม่มีสัตว์เข้ามาเกี่ยวข้องในการผลิต ทำให้โอกาสปนเปื้อนเชื้อซัลโมเนลลาที่พบบ่อยในไข่สดแทบเป็นศูนย์ เป็นจุดขายด้านความปลอดภัยอาหาร (food safety) ที่เขาเน้นมาก
เท่านี้ยังไม่พอครับ คำถามที่คนต้องสงสัยแน่นอนคือ ชนิดของกรดอมิโนหละครบไหม pain point ของชาววีแกน เนื่องจาก EVERY Company ใช้เทคนิค “Precision Fermentation” โดยใส่ยีนจากไก่ลงไปในยีสต์ เพื่อให้ผลิต ovalbumin ได้เหมือนในธรรมชาติ จึงทำให้โครงสร้างของกรดอะมิโนในโปรตีนนี้ เหมือนไข่จริงแทบ 100% โปรตีน ovalbumin ที่ใช้ผลิต เป็น primary protein จึงถือว่าเป็น โปรตีนมาตรฐาน (reference protein) ในทางโภชนาการ เพราะมี กรดอะมิโนจำเป็นทั้ง 9 ชนิด ในปริมาณที่เพียงพอ ได้แก่ Leucine, Lysine, Valine, Isoleucine, Threonine, Methionine, Phenylalanine, Tryptophan, Histidine
แต่... แม้จะมีกรดอะมิโนครบ ก็ยังมีเรื่องให้คิด โปรตีนนี้ ไม่มาจากธรรมชาติ โดยตรง แต่ผ่านการผลิตจากสิ่งมีชีวิตดัดแปลงพันธุกรรม (GMO yeast) ยังไม่มีข้อมูลชัดเจนเรื่อง bioavailability (การดูดซึม) เมื่อเทียบกับไข่จริง และที่สำคัญ คือการบริโภค “complete protein” ไม่ได้แปลว่า ปลอดภัยในระยะยาว ถ้าพื้นฐานมันคือ GMO จากแลปที่ไม่มีวิวัฒนาการร่วมกับมนุษย์ แน่นอนว่ามันยังต้องการ "ตลาดทดลอง" เพื่อทดลองและเก็บข้อมูลประกอบสินค้าในระยะเวลานึง เข้าใจไหม "หนูๆ"
คำถามคือ โปรตีนแท้...หรือแค่ “เลียนแบบ” EVERY Egg บอกว่าเขาสร้างโปรตีนเหมือนไข่เป๊ะชนิดที่ว่าเชฟชื่อดังยังแยกไม่ออก (ถ้าไม่ดูฉลาก) สามารถนำไปทอด ทำไข่คน ไข่เจียว โอ๊มเล็ต ได้เหมือนไข่จริงทุกประการ แถมยังไม่มีคอเลสเตอรอล ไม่มีไขมันอิ่มตัว มีแต่ “โปรตีนล้วนๆ” แบบคลีนๆ
แต่ตรงนี้แหละที่มันเริ่ม น่าสงสัย เพราะการไม่มีไขมันเลย มันก็คือการตัดเอา matrix ทางโภชนาการ ที่ธรรมชาติออกแบบมาให้เราย่อยง่าย ดูดซึมวิตามินได้ดี และช่วยให้เรารู้สึกอิ่มแบบธรรมชาติ ไข่แท้จากไก่ ไม่ใช่แค่แหล่งโปรตีน แต่มันคือ “ของขวัญจากธรรมชาติ” ที่มีทั้ง choline, lutein, zeaxanthin, วิตามิน A, D, E, B12, โอเมก้า-3, ไขมันดี และเลซิธิน อยู่ครบทุกอนู ช่วยทั้งสมอง ดวงตา และตับ
ในขณะที่ EVERY Egg คือ “ไข่ที่เราอยากให้มันเป็น” มากกว่า “ไข่ที่ธรรมชาติอยากให้เราได้กิน”
บริษัท The EVERY Company ได้ร่วมมือกับเชฟระดับสุดยอดมากมาย ซึ่งการร่วมมือครั้งนี้มีเป้าหมายเพื่อแสดงให้เห็นว่าโปรตีนไข่ที่ผลิตจากกระบวนการ precision fermentation ของ EVERY Egg สามารถตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศได้ เรามาดูตัวอย่างกันครับว่า มีที่ไหนบ้าง
-
Eleven Madison Park โดย เชฟ Daniel Humm (มิชลิน3 ดาว ที่นิวยอร์ก) EVERY Egg เปิดตัวครั้งแรกในปี 2023 ที่ร้าน Eleven Madison Park ซึ่งเป็นร้านอาหารระดับมิชลิน 3 ดาว ในนิวยอร์ก โดยเชฟ Daniel Humm ได้สร้างสรรค์เมนูพิเศษที่ใช้ EVERY Egg เป็นส่วนประกอบหลัก เช่น ออมเล็ต ค็อกเทล และของหวาน เพื่อแสดงถึงความสามารถของผลิตภัณฑ์นี้ในการตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศระดับ fine dining มิชลิน
-
Chantal Guillon (ร้านมาการองฝรั่งเศสในซานฟรานซิสโก) EVERY Company ได้ร่วมมือกับร้านขนม Chantal Guillon ในการผลิตมาการองที่ใช้ EVERY EggWhite™ ซึ่งเป็นโปรตีนไข่ขาวที่ผลิตจากกระบวนการ precision fermentation โดยไม่มีการใช้ไข่จากไก่เลย ผลิตภัณฑ์นี้ได้รับการยอมรับว่าให้รสชาติและเนื้อสัมผัสที่เทียบเท่ากับไข่ขาวธรรมชาติ
-
The Vegetarian Butcher เป็นแบรนด์ในเครือ Unilever ตามที่ได้เคยให้ข้อมูลไปแล้ว EVERY Company ได้จับมือกับ The Vegetarian Butcher ซึ่งเป็นแบรนด์อาหารมังสวิรัติในเครือ Unilever เพื่อพัฒนาและผลิตผลิตภัณฑ์ที่ใช้โปรตีนไข่จาก EVERY Egg โดยมีเป้าหมายในการลดการใช้สัตว์ในห่วงโซ่อาหารและส่งเสริมความยั่งยืนในอุตสาหกรรมอาหาร
-
Grupo Palacios ผู้ผลิต Spanish Omelet รายใหญ่ของโลก EVERY Company ได้ร่วมมือกับ Grupo Palacios ซึ่งเป็นผู้ผลิต Spanish Omelet รายใหญ่ของโลก โดยนำ EVERY Egg มาใช้ในผลิตภัณฑ์ของตน เพื่อเป็นทางเลือกที่ปลอดภัยและยั่งยืนต่อไข่ไก่ธรรมชาติ ซึ่งอาจมีปัญหาเรื่องการปนเปื้อนและความไม่แน่นอนในการผลิต
Fiat Egg บนเส้นทางเดียวกับ Fiat Food เฮียชวนให้มองภาพใหญ่เหมือนเวลาเรายืนอยู่บนดาดฟ้าแล้วมองลงไปที่ตลาด... ผลิตภัณฑ์อย่าง EVERY Egg ไม่ใช่แค่การสร้าง “ของใหม่” แต่มันคือการ เปลี่ยนแปลงพื้นฐานของอาหาร ด้วยแนวคิดแบบ “Fiat” เป๊ะ Fiat Food คืออาหารที่ไม่ได้เกิดจากธรรมชาติ แต่ถูก “กำหนดให้มีคุณค่า” โดยอุตสาหกรรม Fiat Money คือเงินที่ไม่ได้มีมูลค่าในตัวเอง แต่รัฐบาลบอกให้เรายอมรับมันเป็นเงิน
ในโลกนี้ ถ้า “ไข่” ไม่ต้องมาจากแม่ไก่ “นม” ไม่ต้องมาจากเต้า และ “เนื้อ” ไม่ต้องมาจากวัว แต่ใช้แค่สารเคมี + ยีสต์ + กราฟ + กลิ่นสังเคราะห์ = “ของกินได้” แล้วมันจะเหลือความเป็น อาหารแท้ (real food) อยู่อีกไหม?
เบื้องหลังที่เราควรถามให้ลึก แม้ว่า EVERY จะอ้างว่าโปรตีนจากยีสต์ของเขา “ปลอดภัยและยั่งยืน” แต่ยังไม่มีข้อมูลด้าน long-term health impact ยังไม่มีข้อมูลว่ายีสต์ GMO ที่ใช้ จะกระตุ้นภูมิแพ้หรือมีสารตกค้างหรือไม่ ยังไม่รู้ว่าสารแต่งกลิ่น รส และตัวพาอื่นๆ ที่ใส่ใน EVERY Egg จะส่งผลอะไรกับ microbiome หรือฮอร์โมนของเราในระยะยาว แต่นั่นก็คงมาพร้อมกับคำตอบหรูๆหล่อๆว่า "ขอให้มั่นใจในกระบวนการผลิตที่ทันสมัยและดีเยี่ยม" . . . ตามเคย
และที่น่าสนใจคือ...ผลิตภัณฑ์ EVERY Egg ยังไม่ได้รับการรับรอง GRAS (Generally Recognized As Safe) อย่างเป็นทางการจาก FDA จึงยังไม่สามารถวางจำหน่ายในร้านค้าปลีกทั่วไปได้ บริษัทกำลังร่วมมือกับบริษัทอาหารข้ามชาติในการเปิดตัวผลิตภัณฑ์ในปีนี้ แต่ยังไม่มีข้อมูลชัดเจนเกี่ยวกับการวางจำหน่ายในร้านค้าปลีกทั่วไป แต่ส่วนตัวเฮียคิดว่าไม่น่ากังวล น่าจะผ่านฉลุยแหละ 5555
ไข่สังเคราะห์ = ความหวัง? หรือกับดักในรูปของนวัตกรรม? เราคงไม่ปฏิเสธว่ามีหลายคนบนโลกที่แพ้ไข่จริง หรือห่วงใยเรื่องสวัสดิภาพสัตว์ รวมถึงต้องการความ "บริสุทธิ์" "สกัด" "เข้มข้น" แต่คำถามคือ...จะดีกว่าไหมถ้าเราหาทางผลิต ไข่จริงจากไก่ที่เลี้ยงแบบธรรมชาติ ในระบบ regenerative farming แทนที่จะพยายามสร้างโปรตีนปลอมขึ้นมาแข่ง? ทุกครั้งที่มีของใหม่ที่ดูดี สะอาด และ “คลีน” เฮียอยากให้ทุกคน ถามกลับในใจว่า “คลีน” แค่ในห้องแล็บ หรือ “คลีน” ในธรรมชาติจริงๆ?
สรุปแบบไม่ต้องตีลังกาคิดได้ว่า EVERY Egg คือก้าวใหม่ของเทคโนโลยีอาหารที่กำลังวิ่งไปข้างหน้าแบบไม่เหลียวหลัง แต่ในฐานะที่เฮียเชื่อใน real food, nutrient density และความฉลาดของธรรมชาติ เราอาจต้องเตือนใจไว้ว่า...การใช้ยีสต์ดัดแปลงพันธุกรรมมาผลิต “ไข่เทียม” ไม่ใช่ความผิด แต่ก็ไม่ใช่ความจำเป็นไหม เพราะแท้จริงแล้ว เรามี “ไข่” ที่สมบูรณ์แบบอยู่ในธรรมชาติแล้ว...แค่ไม่ควรปล่อยให้อุตสาหกรรมทำลายภาพลักษณ์ของมัน เพื่อขายของที่ “เหมือนไข่” แต่ไม่มีชีวิต
คำถามเดิมครับ วันนึงเมื่อถึงจุดที่คุณไม่ได้เลือก แล้วมันมีให้แค่นี้ วันนั้นจะทำอย่างไร วันแห่งความ "บริสุทธิ์" "สกัด" "เข้มข้น" ที่เราถวิลหา ??? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 3eba5ef4:751f23ae
2025-05-02 02:10:09
@ 3eba5ef4:751f23ae
2025-05-02 02:10:09加密洞见
secp256k1lab:一个不安全的 Python 库,如何让比特币更安全
一些比特币开发者长期以来一直认为应该有一个统一的、可重用的加密 BIP 参考 secp256k1 代码标准。Blockstream 研究团队发布了 secp256k1lab (GitHub Repo)—— 一个新的、故意不安全的 Python 库,用于原型开发、实验和 BIP 规范的制定。
该库并不用于生产的(因为没有常数时间防护,因此易受侧道攻击),但填补了一个空白:提供了一个干净且一致的 secp256k1 功能参考实现,包括 BIP-340 风格的 Schnorr 签名、ECDH 以及底层的域/群运算。该库的目标是:通过避免重复的、一次性的实现,让未来编写 BIP 变得更简单、更安全。对于 BIP 作者来说,这意味着更少的自定义代码和规范问题,以及一条更清晰的从原型到正式提案的路径。
使用基于时间的一次性密码(TOTP)在软件钱包中进行密码验证和访问控制
本文介绍了一种在比特币软件钱包中,使用基于区块的时间同步一次性密码(TOTP, Time-based One-Time Password)机制进行密码验证和钱包访问控制的方法。 与传统的 TOTP 系统不同,这种方法将区块链数据——特别是比特币的区块高度和区块哈希 ——同一个安全存储的加密信息结合,来生成一个动态变化的 6 位数验证码,具备以下安全属性:
-
双重保护:结合了设备持有性和基于区块链衍生的、基于时间的数据(blockchain-derived time-based data)。
-
抗重放攻击:验证码随每个新区块(约 10 分钟一个周期)更新。
-
最小攻击面:无需输入或复制密码短语。
-
硬件加密保护秘密信息:移动端应用的秘密信息存储在不可导出的安全硬件中。
比特币特征矩阵:跟踪比特币产品/服务的互操作性
Bitcoin Opentech 在此页汇集并跟踪比特币相关产品/服务的互操作性。
汇集各种比特币软分叉提案的网站
bitcoin.softforks.org 网站汇集了各种比特币软分叉提案,包含组件、实现原语等关键软分叉信息,以及使用该分叉的使用案例和用户等。
以太坊社区热议 RISC-V 替代 EVM,CKB-VM 经验倍受关注
Vitalik 近日在 Ethereum 的论坛上提出了将用 RISC‑V 代替 EVM 的设想,并提到 CKB-VM 的设计作为参考范例,引发了两个社区对 RISC-V 技术决策的关注和探讨。随着讨论的展开,CKB-VM 当年的设计考量又重新被提起,并吸引了更多人回顾和学习相关经验。CKB 是 Nervos Network 的 Layer 1 公链,其支持智能合约的 Cell 模型受比特币 UTXO 模型启发,并使用基于 RISC-V 的 CKB-VM 虚拟机,实现高效且支持多语言的合约执行。了解更多 CKB-VM 详情:
在 Ark 中集成 Taproot Assets 的概念验证
Ark Labs 分享了如何将 Taproot 资产集成到 Ark 的链下批处理层中:在 Ark 标准交易流程上,引入了 tVTXO(tokenized Virtual Transaction Output)——嵌入 Taproot 资产承诺的虚拟输出。tVTXO 的行为与任何其他 VTXO 一样,可在 Ark 的链下层花费,可预先签名以实现单边退出,但它包括两个关键附加功能:
-
资产承诺(Asset Commitments):使用 Taproot 的内部密钥和 TapTree 结构嵌入到 PkScript 中。
-
传输证明文件(Transfer Proof Files)是一条加密见证的确定性链,通过链下树跟踪资产的包含路径。这些证明可以通过链上元数据激活,从而退出 Taproot Asset 生态。
Erk:改进 Ark 协议,无需用户轮次交互
Erk 是 Ark 协议的一种新颖变体,引入了具有可重新绑定签名的「退款交易」(refund transactions),允许用户提前提供可应用于未来输出的签名。然后,服务器可以安全地刷新 VTXO,而无需用户在每一轮都处于联机状态。这解决了 Ark 的关键限制之一——要求用户在 VTXO 到期之前上线。
Erk 的另一个强大功能是「永久离线刷新」——用户可以按顺序批量预签名未来的刷新。通过 watchtower 监控协议,用户可以在资金保持安全的情况下无限期地保持离线状态。
Robosats:无 KYC 闪电网络 P2P 交易,支持人民币通过微信交易
RoboSats 是一个无 KYC 的开源闪电网络交易平台,使用LN Hodl invoices 最大限度地减少托管和信任要求。用户通过 Tor 浏览器操作,体验简单且交易费用低廉的 P2P 交易。
平台目前也支持通过微信进行人民币。
值得关注的几个闪电网络基础设施项目
OpenSats 的这篇文章重点关注闪电网络在基础设施上的推进,提到以下项目:
-
Lighting Splicing: 允许用户在不停机的情况下动态调整通道容量。通过消除关闭和重新打开通道的需要,Splicing 即减少了摩擦和成本,又简化了流动性管理。
-
Validating Lightning Signer (VLS): 通过将密钥存储和交易验证转移给外部签名者,来解决闪电网络传统的、将私钥直接存储在节点上用于交易签名的方式的风险,从而确保即使闪电节点遭到入侵,攻击者也无法访问或滥用私钥来窃取资金。
-
BLAST (Big Lightning Automated Simulation Tool): 目标是为闪电网络提供稳定的建模和仿真框架,为研究和开发人员和节点运营商提供更准确地反映真实网络状况的大规模测试环境。
-
Lampo: 提供了一个基于 Lightning 开发工具包(LDK)构建的模块化、社区驱动的开发工具和节点实现方案。
-
Lnprototest: 提供了一个基于 Python 的测试库,可帮助开发人员验证不同实现中的协议合规性,确保交叉兼容性并防止回归,以免影响实际用户。
Citrea 推出基于 BitVM 的信任最小化双向挂钩桥 Clementine
Rollup 项目 Citrea 在比特币测试网上部署了 Clementine Bridge,这是比特币测试网上第一个完整的 BitVM 桥设计。Clementine 桥是 Citrea 基于 BitVM 的信任最小化双向挂钩方案,核心组件包括:
-
比特币和 Citrea 的轻客户端证明
-
BitVM 中的零知识证明验证器
只要 BitVM 设置中的单个验证器是诚实的,Clementine 就会保持安全。这是对现有解决方案(开放和封闭联合)的重大改进。Clementine 桥的设计和 Citrea 的去信任轻客户端一起,最大限度减少了对 Citrea 双向挂钩的信任要求,且无需软分叉。
详情可参考 Clementine 白皮书,以及特征简介。
RISC-V 成为 BitVMX 验证系统最佳选择的五个关键原因
作为 BitVMX 的主要开发者的 Fairgate Labs 概述了 RISC-V 成为 BitVMX 验证系统最佳选择的五大关键:
-
开放且通用:RISC-V 作为标准,无 IP 障碍
-
成熟的工具支持:编译器和调试器的丰富生态系统
-
操作码简单
-
支持高级语言
-
支持通用验证
精彩无限,不止于链
违规却挡不住需求:深圳的 LuckyMiner 在争议中推动家用小型矿机普及
LuckyMiner 是一家深圳的比特币挖矿初创公司,它们生产家用迷你矿机正越来越受欢迎。LuckyMiner 模仿的主要对象是美国产的开源的小型矿机 Bitaxe。虽然开源,但 Bitaxe 适用于 CERN-OHL-S-2.0 规则,要求任何修改都需公开,而 LuckyMiner 并未遵循此规则。
这条推文的发帖人称跟 LuckyMiner 的创始人吃了饭,后者并不遮掩 LuckyMiner 违反了许可,并表示,除了零售的 LuckyMiner 之外,它们也为 B 端客户生产符合开源许可的 Bitaxes,并且同时仿造 braiins 的挖矿设备。
在对负担得起的家用采矿设备的需求不断增长的推动下,LuckyMiner 已经取得了成功。虽然存在争议,但低成本矿工的崛起表明草根阶层对比特币感兴趣,尤其是在亚洲努力应对日益增长的威权主义和金融压迫的时候。
反对销毁受易量子攻击的比特币
关于如何处理易受攻击的地址里的比特币,Jameson Lopp 在此前的文章中,表示它反对恢复这些代币,并主张原地销毁,以防止资金被量子计算的获胜者拿走。
而 UTXO Management 的 Guillaume Girard 在此反驳了 Lopp 的主张,出于以下考虑:
-
侵犯财产权:未经持有者同意就销毁这些币,违反了财产权原则。强制让这些币不可使用,破坏了比特币中对所有权和控制权的基本尊重
-
伦理问题:尽管销毁易受攻击的币是为了防止未来量子攻击者盗币,但实际上也会无差别地惩罚那些遗失钱包或不了解量子威胁的用户。这种做法在伦理上存在严重问题,因为不给用户自救的机会。
他提出了一些更具建设性的替代方案来取代销毁策略:
- Hourglass(沙漏机制):旨在减轻“没收式销毁”和“市场抛售”这两种方式带来的负面影响。它通过限制量子攻击事件可能引发的供应冲击,既不烧毁币,也不导致市场被抛压所淹没。
这一方案由 Hunter Beast 提出,试图成为“破坏性最小”的解决方案,目前正在开发者社区中接受评估。此外,Hunter Beast 也已经提出了 BIP 360,以引入抗量子密码学(PQC)并新增一种比特币地址类型。
让旧矿机继续发挥余热:边挖矿边供暖的未来可能
BitMEX 对 Heatbit Trio 比特币挖矿加热器做了测评。该产品本质上是一个旧矿机,配备有一个安静的风扇,适用于房间供暖。
作者表示 Heatbit 的商业模式很吸引人,结合挖矿机和加热器的领域也值得长期关注。因为从长远来看,部分由于摩尔定律的物理限制,ASIC 效率的提高速度将下降,因此 ASIC 可以经济地开采比特币更长的时间(如 10 年)。随着涉及的新风险技术的减少,生产成本也应该会下降。当这种情况发生到足够程度时,将比特币挖矿与加热设备相结合可能是有意义的,例如,游泳池、商用锅炉、住宅锅炉以及商用和住宅电加热系统。
开放、即时和无国界支付:稳定币未来
a16z 的该报告探讨了稳定币会如何颠覆全球支付行业,以及谁将从中受益最大等问题。
作者将稳定币的到来称为赚钱的「WhatsApp 时刻」,因为它使国际交易几乎免费、即时、开放。此外,文章指出只有两种稳定币是被认可的:法币或资产支持的稳定币,而 「策略支持的合成美元 」(Strategy-backed synthetic dollars, SBSD)并不被承认是可靠的价值储存或交换媒介。
-
-
 @ fd0bcf8c:521f98c0
2025-05-02 02:02:13
@ fd0bcf8c:521f98c0
2025-05-02 02:02:13Bitcoin
It stands alone. Immutable. Unyielding. It records without mercy. Each transaction cuts deep. Some carry wealth. Others just data. The debate rages on.
OP_RETURN
It divides us all. Bloat versus freedom. Money versus use. Simple versus complex.
Nodes
They bear heavy weight. Each byte costs something. Storage grows. Bandwidth drains. Money defenders stand guard.
"Our purpose is clear...Money serves one master." —Mises
Not art.
Not storage.
Not games.
The fee-payers
They disagree. "I paid. I belong." The miners take their cut. The highest fee wins. No questions asked. The protocol allows it.
"Accept what exists."—Marcus Aurelius
The chain is neutral. Always neutral.
What is a transaction?
None agree. Value transfer only? Or any valid data? The white paper speaks. "Electronic cash system." Yet code evolved. It grew teeth. It allows more now.
"Shitcoin"
Cuts both ways. A dangerous word. It keeps focus. It maintains unity. But it wounds creation. Makes builders desperate. They force ideas onto Bitcoin. They use OP_RETURN poorly. They bloat what needs no bloating. Seneca saw this coming...
"Fear makes suffering worse."
Innovation needs proper soil. Not forced transplants.
Money debates sharpen knives. Is Bitcoin gold? Is it currency? Mantras echo loudly.
"Digital gold."
_"Spend dollars, saving Bitcoin." _
"Never sell your Bitcoin."
Bitcoin becomes idol. Not tool. Mises would disapprove, "Money must move." Without exchange, it dies. If none spend, why fight bloat?
Rhetoric
It hurts us. "Shitcoin" closes minds. Forces square pegs round. Drives experiments home. To Bitcoin they return. Bearing misshapen plans.
"Knowledge exists in dispersion," Hayek warns.
Let ideas find homes. Let Bitcoin be Bitcoin.
Fees
They bring new problems. Users flee high costs. They seek cheaper chains. The wealthy still play games. They can afford the bloat. The poor cannot compete. The rich inscribe at will. Rothbard saw this trap, "Markets need equal rules."
Fee markets favor wealth. Always have. Always will.
Nodes must still run. Validators must validate. Decentralized. Resistant. Strong. The burden grows heavier. But principles matter most.
The battle
It continues. Hard words. Hard choices.
Bitcoin endures all. Money or platform? Gold or currency? The answers shift. The chain grows. Block by block. Byte by byte.
We need clearer words. Cleaner definitions. Less pride. More thought. Let Bitcoin be what it is. Not what we demand.
Bitcoin is human.
Not magical. Not divine. Fallible like its makers. A young experiment still. It could fail tomorrow.
"Nothing is too big to fail." —Satoshi
Our rhetoric needs maturity. Our definitions need clarity. Bitcoin needs humility. From all who touch the code.
-
 @ 3eba5ef4:751f23ae
2025-05-02 01:56:09
@ 3eba5ef4:751f23ae
2025-05-02 01:56:09Crypto Insights
secp256k1lab: An Insecure Python Library That Makes Bitcoin Safer
Some Bitcoin developers have long believed in the need for a unified, reusable cryptographic BIP reference standard for secp256k1. Blockstream Research has released secp256k1lab — an intentionally insecure new Python library designed for prototyping, experimentation, and BIP specifications.
This library is NOT intended for production use (it lacks constant-time protections and is thus vulnerable to side-channel attacks). However, it fills a gap by providing a clean and consistent reference implementation of secp256k1 functionality, including BIP-340 style Schnorr signatures, ECDH, and low-level field/group operations. Its goal: to make future BIP authoring simpler and more secure by avoiding redundant, one-off implementations. For BIP authors, this means less custom code, fewer specification bugs, and a clearer path from prototype to proposal.
Block-Based Time-Based One-Time Passwords for Secure Passphrase Validation in Bitcoin Wallets
This article introduces a method for passphrase validation and Bitcoin software wallet access control using a block-based time-based one-time password (TOTP) system.
Unlike traditional TOTP systems, this method uses blockchain data — specifically Bitcoin block height and block hash — combined with securely stored cryptographic secrets to generate a 6-digit dynamic verification code with the following security properties:
-
Two-Factor Protection: Combines device possession and blockchain-derived time-based data.
-
Replay Resistance: Codes change with every block (~10-min cycle).
-
Minimal Attack Surface: Passphrase never typed or copied.
-
Hardware-Backed Secrets: Mobile app secret stored in non-exportable secure hardware.
Bitcoin Feature Matrix: Tracking Interoperability of Bitcoin Products/Services
You can use this page on Bitcoin Opentech to track interoperability among Bitcoin products and services.
Tracking Bitcoin Soft Fork Proposals in One Place
bitcoin.softforks.org aggregates various Bitcoin soft fork proposals, including components, implementation primitives, use cases, and users.
Ethereum Community Explores Replacing EVM with RISC-V — Spotlight on CKB-VM Experience
Vitalik recently proposed the idea of replacing the EVM with RISC-V on the Ethereum forum, citing the design of CKB-VM as a reference. This has sparked active discussion in both communities around RISC-V as a technical direction. As the conversation deepens, the original design decisions behind CKB-VM have resurfaced, drawing renewed interest and encouraging more developers to study its architecture and lessons.
CKB is the Layer 1 blockchain of the Nervos Network. Its smart contract model, called the Cell model, is inspired by Bitcoin’s UTXO system. It uses the RISC-V–based CKB-VM to enable efficient and multi-language smart contract execution. Find more details in:
-
A Blockchain VM Built on RISC-V (The Birth of CKB-VM Part 1)
-
CKB-VM: Its Inspiration, Design, and Strengths (The Birth of CKB-VM, Part 2)
-
How to Have Fun with CKB-VM (The Birth of CKB-VM, Part 3)
Integrating Taproot Assets into Ark
Ark Labs shared their proof-of-concept of integrating Taproot Assets into the off-chain batching layer of Ark. They introduced tVTXOs (tokenized Virtual Transaction Outputs) — virtual outputs that embed Taproot Asset commitments.
tVTXOs behave like regular VTXOs, spendable off-chain and pre-signable for unilateral exits, but with two additional features:
-
Asset Commitments: Embedded in PkScript using Taproot’s internal key and TapTree structure.
-
Transfer Proof Files: A cryptographically linked, deterministic chain of off-chain proofs tracking asset inclusion. These can be activated via on-chain metadata to exit the Taproot Asset ecosystem.
Erk: An Ark Protocol Upgrade Removing User Round Interactions
Erk is a novel variant of the Ark protocol that introduces refund transactions with rebindable signatures. This allows users to pre-sign outputs that the server can safely refresh without needing the user to be online for each round — addressing one of Ark’s limitations.
Another feature of Erk is “perpetual offline refresh” — users can bulk pre-sign future refreshes. With watchtowers monitoring the protocol, users can stay offline indefinitely while their funds remain safe.
Robosats: No-KYC Lightning P2P Trading
RoboSats is an open-source, no-KYC Lightning P2P exchange using LN Hodl invoices to minimize custodial requirements and trust. Operated via the Tor browser, it offers a simple and low-fee user experience.
Find more in their GitHub repo and user guide.
Advancements in Lightning Infrastructure
OpenSats highlights several key Lightning infrastructure advancements:
-
Lightning Splicing: Allows dynamic channel capacity adjustment without downtime, simplifying liquidity management and reducing costs.
-
Validating Lightning Signer (VLS): Shifts key storage and transaction validation to an external signer. Even if a node is compromised, the attacker can’t access or misuse private keys.
-
BLAST (Big Lightning Automated Simulation Tool): Designed to provide a stable modeling and simulation framework of the Lightning Network for developers and node operators.
-
Lampo: A modular, community-driven development toolkit and node implementation built on Lightning Dev Kit (LDK).
-
Lnprototest: A Python-based testing library to help developers validate protocol adherence across different implementations.
Citrea Launches Clementine: A BitVM-Based Trust-Minimized 2-Way Peg Bridge
Rollup Citrea has deployed Clementine Bridge on Bitcoin testnet — the first fully BitVM-based bridge design on Bitcoin testnet. Clementine is Citrea’s trust-minimized, two-way peg solution powered by:
-
Bitcoin and Citrea’s light client proofs
-
Zero-knowledge proof verifier in BitVM
As long as one single verifier in the BitVM setup is honest, Clementine remains secure — a major improvement over existing approaches (e.g., open and closed federations). Paired with Citrea’s trustless light client, Clementine minimizes trust in Citrea’s bridge design and doesn’t require a soft fork.
Find more details in Clementine Whitepaper and Feature Overview.
Five Reasons RISC-V Is the Best Architecture for the BitVMX Proving System
Fairgate Labs, the main developers behind BitVMX, outlined five key reasons why RISC-V is the optimal choice for BitVMX:
-
Open and Universal: RISC-V as a standard with no IP barriers
-
Mature Tooling: A rich ecosystem of compilers and debuggers
-
Opcode Simplicity
-
High-Level Language Support
-
Universal Verification
Top Reads on Blockchain and Beyond
Demand Outpaces Licensing: LuckyMiner Drives Home Mining Boom Amid Controversy
LuckyMiner, a Bitcoin mining startup based in Shenzhen, China, is gaining traction with its mini miners. Their products are clones of the open-source Bitaxe miners from the U.S. However, Bitaxe is licensed under CERN-OHL-S-2.0, which requires all modifications to be open-sourced—something LuckyMiner has not complied with.
According to this post, LuckyMiner's founder openly admitted to violating the license and claimed that while their LuckyMiner devices for retail customers don’t comply with the open-source terms, they also produce fully license-compliant Bitaxes for business clients, while simultaneously cloning mining equipment from Braiins.
Against Burning Quantum-Vulnerable Bitcoins
Jameson Lopp has previously argued in favor of burning bitcoin in vulnerable addresses, to prevent funds from being taken by those who win the quantum computing race.
Guillaume Girard from UTXO Management disagrees, offering these counterpoints:
-
Property rights violation: Burning coins without the owner’s consent undermines the very principle of property rights. Forcing coins into unspendability erodes the core Bitcoin ethos of ownership and control.
-
Ethical concerns: While burning these coins may prevent quantum theft, it also punishes users who lost wallets or don’t understand the quantum threat—offering no chance for recovery.
Instead of burning, he proposes more constructive steps:
- Hourglass: Mitigates the downsides of both “confiscatory” and “liquidation” approaches – by limiting the potential supply shock of a quantum event, without burning coins or flooding markets.
This solution, proposed by Hunter Beast, aims to be the “least damaging” option and is currently under review by developers. Additionally, Hunter Beast has already proposed BIP 360 to bring Post-Quantum Cryptography (PQC) to Bitcoin with a new address type.
Old Miners, New Heat: Mining-as-Heating Might Just Work
BitMEX reviewed the Heatbit Trio—a Bitcoin miner repurposed into a room heater redesigned with a quiet fan.
The reviewer found the Heatbit concept commercially appealing and believes the heating-mining hybrid space is worth watching. The rate of improvement in ASIC efficiencies will decline (partly due to the limits of Moore’s Law), such that ASICs can economically mine Bitcoin for much longer—possibly up to 10 years. With fewer new technical risks, production costs should also drop. When that happens, integrating mining with heating systems may become practical.
Open, Instant, Borderless Payments: Stablecoins and Their Future
This a16z report explores how stablecoins are poised to change the global payments landscape—and who stands to benefit most.
The report sees stablecoins the "WhatsApp moment for money," enabling international transfers nearly free and instant. It also stresses that only two types of stablecoins are considered trustworthy: fiat-backed or asset-backed. The so-called Strategy-Backed Synthetic Dollars (SBSDs) are NOT considered to be a reliable store of value or medium of exchange.
-
-
 @ 16d11430:61640947
2025-02-09 00:12:22
@ 16d11430:61640947
2025-02-09 00:12:22Introduction: The Power of Focused Attention
In an age of distraction, power is not merely held through material wealth, authority, or control over others—it is built through focused attention. The human brain, a complex quantum-biological processor, constructs reality through perception. When harnessed correctly, focused attention allows individuals to transcend limitations, reshape their reality, and live free.
Power, then, is not external—it is a construct supported by the mind and created within the brain. Understanding how this works offers a path to transcendence, autonomy, and liberation from imposed limitations.
The Neuroscience of Focused Attention: Constructing Reality
The brain is a prediction engine, constantly processing information and filtering out irrelevant stimuli. Focused attention directs this process, acting as a spotlight that selects what becomes part of one's conscious experience. This is the fundamental mechanism behind cognitive power.
- Neuroplasticity: Building Power Through Repetition
The brain adapts to repeated stimuli through neuroplasticity. What one focuses on consistently rewires neural pathways, strengthening certain thoughts, beliefs, and abilities. Over time, this focus builds an internal structure of power—a network of ideas and perceptions that define one’s reality.
If one focuses on problems, they grow.
If one focuses on solutions, they appear.
If one focuses on fear, it shapes perception.
If one focuses on mastery, skills develop.
- The Quantum Mind: Attention as a Creative Force
Quantum physics suggests that observation influences reality. Just as subatomic particles behave differently when measured, focused attention may act as a force that shapes possibilities into tangible outcomes.
This aligns with the ancient concept that "energy flows where attention goes." What one attends to with intention can manifest as action, opportunity, and ultimately, freedom.
- The Reticular Activating System (RAS): Filtering Reality
The Reticular Activating System (RAS) in the brainstem acts as a gatekeeper for focus. It determines what information enters conscious awareness. When trained, it can filter out distractions and amplify pathways toward a desired goal.
Want to see opportunities? Program the RAS by setting clear intentions.
Want to break free from limiting beliefs? Train focus away from conditioned fears.
The Mind’s Role: Transcending Limitations
The mind is the interpreter of the brain’s electrical and biochemical activity. While the brain processes raw data, the mind provides meaning. This distinction is crucial because meaning determines how one experiences reality.
- Breaking Mental Chains: Rewriting Narratives
Most limitations are narratives—stories imposed by culture, society, or personal history. True power lies in rewriting these stories.
Instead of “I am trapped by my circumstances,” shift to “I create my own reality.”
Instead of “I need permission,” shift to “I give myself permission.”
By restructuring meaning, the mind can redefine the limits of what is possible.
- The Silence Paradox: Accessing Higher States
Silence, both literal and mental, creates space for higher-order thinking. Just as quantum tunneling allows subatomic particles to pass through barriers without energy loss, silence allows the mind to bypass noise and access deeper intelligence.
Meditation, stillness, and solitude amplify internal power.
The ability to not react is a form of control over external influence.
True mastery comes from detachment—engaging the world without being controlled by it.
Transcendence: Living Free Through Mental Autonomy
To transcend means to rise above imposed structures—whether societal, psychological, or energetic. The construct of power built through focused attention allows one to escape control mechanisms and live autonomously.
- Sovereignty of Mind: Owning One’s Thoughts
A free mind is one that chooses its inputs rather than being programmed by external forces. This requires:
Awareness of mental conditioning (social narratives, propaganda, biases)
Intentional thought selection (curating what enters the mental space)
Guarding attention fiercely (not allowing distraction to hijack focus)
- Detachment From Control Structures
Society operates on the principle of attention capture—through media, politics, and algorithms that direct thought patterns. Escaping these requires detachment.
Do not react emotionally to fear-based programming.
Cultivate independent thought by questioning imposed narratives.
Reduce external noise to amplify internal wisdom.
- The Flow State: Moving Beyond Constraints
When focus is refined to its highest degree, one enters flow state—a condition where action and awareness merge, and limitations dissolve.
In flow, work becomes effortless.
Creativity becomes boundless.
Freedom becomes not just a philosophy, but a lived experience.
Conclusion: The Mind as the Ultimate Key to Freedom
Power is not an external possession—it is the ability to direct one’s own focus. Through the interplay of brain function, cognitive attention, and mental discipline, one constructs personal sovereignty. The individual who masters focus, controls reality.
Freedom is not given. It is built—through attention, intention, and an unwavering commitment to mental autonomy.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 000002de:c05780a7
2025-05-01 23:17:11
@ 000002de:c05780a7
2025-05-01 23:17:11A lot of typing has been done comparing various right wing figures and people like Donald Trump and Elon Mush to Fascism and Nazism. It is frankly pretty absurd at this point. I'd be with them if they were just talking about these people being authoritarians. They clearly are in many ways. I'm not a fan.
But very little is said in a "non-partisan" way about the left. This is gonna be short and is meant to peak your curiosity to go and do some research for yourself.
The economist Milton Friedman famously said.
"After the fall of communism, everybody in the world agreed that socialism was a failure. Everybody in the world, more or less, agreed that capitalism was a success. And every capitalist country in the world apparently deduced from that what the West needed was more socialism."
This was said a long time ago and it is still the case. People espouse socialist ideas without even a concern about being called out for it. The same is NOT true of fascism or even traditional American patriotism.
But many of you may not realize just how deep the rot of socialism goes. Most people agree that the USSR committed terrible acts and was a failure. Before the creation of the USSR two socialists movements fought for power and control, the Bolsheviks and Mensheviks. The primary difference between the two groups was how to bring about socialism. The Bolsheviks led by Lenin favored a more radical revolutionary force led by a small group. The Mensheviks, led by Julius Martov, preferred a larger, more democratic rise to power. They supported a more gradual rise of socialism. In October of 1917 the Bolsheviks seized power in Russia in a bloody revolution.
Even to this day there are two different minds around how to bring about socialism. In the US the Menshevik approach is the one more popular. People like Bernie and AOC are this type of socialist. But make no mistake. They want to bring about a socialist utopian society. The type of system we have seen fail time and time again.
A few years ago I heard about another socialist movement and was frankly shocked that I had never heard about it before. In 1890 Britain a group of socialists formed an organization called the Fabian Society. The Fabians were/are socialists. But they believe in gradual incrementalism to bring about socialism. So what did the do you ask? They were at the center of the founding of the Labour party in the UK. Now, you might say. Big deal. But here's the weird thing. The Fabian Society's coat of arms was literally a wolf in sheep's clothing
They sought to bring about socialism covertly through democratic processes by presenting themselves as more moderate politicians. They have worked for decades to bring about socialism in the UK. If you don't count Margret Thatcher's era they've done a pretty great job. The UK is a mess.
So what does this have to do with May Day or Labor day for that matter? Well, socialists are at the center of every labor movement and celebrations like May day. Socialist ideas have been pumped into the government textbooks in the US for decades. Teachers are instructed in Universities full of believers in this wolf in sheep's clothing movement of democratic socialism.
Socialism leads to death and poverty. I'm not here to say that the US economy is the example for what the world should do. I'm a free market guy. We live in a corporatism led economy where the state partners with corporations to screw many in the US as well as the world. But I can tell you this. Socialism would be even worse.
The famous and infamous Russian anarchist Emma Goldman upon returning from her visit to the USSR was broken hearted. She had been a supporter of the revolution, but when she saw it with her own eyes she had a change of heart.
The compassion that seems to be a part of socialism is a lie. You can't institutionalize compassion. It has to come from the people, not a system. We should care for our brothers and sisters. But WE have to do it. We can't take from one group and give to another. We can't surrender our liberties to those that say they will take care of it for us. We have to do it. Capitalism is amoral. The free market is amoral. Both require us to be moral and show the way.
I hope this sparks your interest into looking into the history around socialist movements across the globe. I don't doubt that some have good motives, but the results are disastrous for the masses.
originally posted at https://stacker.news/items/968901
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ 2cb30c36:cc7ecec1
2025-05-01 21:52:50
@ 2cb30c36:cc7ecec1
2025-05-01 21:52:50Test
This is a test
-
 @ 63616fef:5e05fd6a
2025-05-01 21:26:58
@ 63616fef:5e05fd6a
2025-05-01 21:26:58How to achieve net zero:
1) Vastly reduce reliable electric generation 2) Optimize for unreliable, and intermittent power generation
Long form article posted via untype.app
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 9d92077c:38d27146
2025-01-20 20:46:31
@ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks.
—-
The Importance of Key Recovery on Nostr
One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation.
While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity.
—-
Proposed Solution: The Excalibur System
The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition.
1. Primary and Secure Keys
Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a
set_secure_keyevent.2. Key Transition Event
Upon detecting a compromise, the user activates the secure key by publishing a
key_transitionevent.This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata.
3. Social Graph Transition
Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data.
Followers are notified of the transition and encouraged to follow the secure key.
4. Unified Identity View
Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity.
Clients display a unified profile view, differentiating old and new events.
5. Seamless Transition for Existing Accounts
Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process.
6. Endless Security Chain
Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new
set_secure_keyevent.This ensures an endless chain of security, preventing future compromises from leaving users vulnerable.
Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently.
7. Insurance Model for Relays
Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations.
Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services.
This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network.
—-
Implementation Framework
Cryptographic Foundations
- The secure key must be pre-announced and linked to the primary key using a signed
set_secure_keyevent. - During key transition, the key_transition event includes a signature proving the association.
Relay Behavior
- Relays index the key_transition event and re-link historical data to the secure key.
- Events from the old key are tagged as "deprecated" but remain accessible.
Client Behavior
- Clients validate the
key_transitionevent and update social graphs automatically. - Followers are notified and prompted to follow the secure key.
- Profiles display both old and new events under a unified identity.
- Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly.
—-
Benefits of Excalibur
Resilience: Users can recover from key compromise without losing their digital identity or network.
Trust: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system.
Sustainability: The insurance premium model incentivizes relay adoption and ensures fair resource allocation.
User-Friendly: Automated transitions reduce the complexity for end users, making Nostr more accessible.
Adaptability: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability.
—-
Call to Action
The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality.
Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
- The secure key must be pre-announced and linked to the primary key using a signed
-
 @ 318ebaba:9a262eae
2025-05-01 21:07:55
@ 318ebaba:9a262eae
2025-05-01 21:07:55Fette Überschrift
So soll es sein.
kleine Überschrift
Save Draft
++und jetzt++
Publish
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ e8ed3798:67dd345a
2025-05-01 20:46:55
@ e8ed3798:67dd345a
2025-05-01 20:46:55test content
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6be5cc06:5259daf0
2025-01-18 02:11:43
@ 6be5cc06:5259daf0
2025-01-18 02:11:43- Not your keys, not your coins
Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos.
- HODL - Não venda
O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável.
- Stay humble - Não saia falando que você tem BTC
Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças.
- Don't trust, verify
No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações.
- Reject altcoins
As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente.
- Stack sats - DCA
Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado".
- Reject the ego
Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam.
- Keep learning
Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão.
- Help beginners
O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade.
- Don't push it
Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir.
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 318ebaba:9a262eae
2025-05-01 20:28:44
@ 318ebaba:9a262eae
2025-05-01 20:28:44Heute soll es funktionieren
-
 @ 2ed3596e:98b4cc78
2025-05-01 20:27:18
@ 2ed3596e:98b4cc78
2025-05-01 20:27:18The Bitcoin Well Affiliate program is here! You can earn a bitcoin bonus of 21% of revenue generated from transactions every time someone you refer transacts on our platform. Bitcoin Well Affiliates can also complete bounty tasks to earn sats, such as Bitcoin Well video tutorials. The Affiliate program is our way of aligning incentives with our mission to enable independence.
How to apply for the Bitcoin Well Affiliate program
The Affiliate program is big folks in and bitcoin or folks with a LOT of experience with bitcoin and self-custody wallets; the most important quality is a passion for orange-pilling!
Bitcoin Well Affiliates earn more than double our referral commission (21% of revenue generated from transactions), get a custom Bitcoin Well Affiliate webpage to help you get referrals and unlock bounty tasks for bonus sats. You can apply to join the Affiliate program by clicking here.
How to earn your Bitcoin Well Referral bonus
To refer a customer to Bitcoin Well, have them sign up using your Bitcoin Well referral link, this can be found in your Bitcoin Well account under Rewards > Referrals. Your referred customers also get a sign up bonus of 1,000 Bitcoin Well. You get 500 points for each referral, too.
Your personal referral link will be https://bitcoinwell.com/app/ref/YOUR_WELLTAG. A person can also be referred by typing in your welltag in the Referral Code field on the sign up page.
The best part? Sats are AUTOMATICALLY paid to your designated Lightning Wallet.

Who is eligible to refer to Bitcoin Well?
The Bitcoin Well Affiliate program is available to anyone! However, our services are only available in Canada and the United States.
The Affiliate program includes referrals to business and High Net Worth Individuals that use our OTC desk.
How to hunt Affiliate bounty tasks and earn sats
Affiliates can hunt bounty tasks by making Bitcoin Well tutorials and uploading them to Youtube or X in exchange for sats.
Bounty tasks such as How to buy bitcoin (USA) on Bitcoin Well are a fantastic resource to generate referrals and boost traffic to your pages. Affiliate bounty tasks earn you 21,000-105,000 sats per video. \ \ Affiliate bounty tasks are only available to approved Bitcoin Well Affiliates. Read our Affiliate Bounty article for more details on submitting Affiliate bounties.
How does the Bitcoin Well referral program work?
The Bitcoin Well Affiliate and referral programs pay you automatically for your referral’s activities.
\ For example, today we have a 1.2% spread on standard portal transactions (buy, sell, pay bills). This means for every $100 someone spends on the platform we make $1.20, you’ll earn $0.24, automatically paid in sats. If they are using a Lite Account, with a 3% spread, you will earn $0.61 on that transaction, automatically paid in sats.
Referral bonuses don’t have an expiration date, cause we are all in bitcoin for the long haul!
The 21% revenue share for whales that end up purchasing through our OTC desk goes a long way, potentially in the thousands of referrals dollars per transaction. We do not place a cap on referral bonuses, so the bigger the whale, the bigger the referral bonus you earn!
How and when do I get paid?
Your referral bonuses are automatically paid out to the designated Lightning Wallet in your referral page. If you prefer, you can select a manual payout where you can withdraw your payouts at any time via LNURLw. \ \ OTC referral bonuses are processed around the middle of each month to your referral Lightning wallet.
What if I am not a fit for the Affiliate Program? Can I still earn from referrals?
Not everyone is the right fit for the Affiliate program, and that’s okay! Maintaining a far-reaching social presence is tough work. \ \ Thankfully, regular customers can still earn unlimited commissions from referrals at a 10% rate! This means for every $100 someone spends on the platform we make $1.20, you’ll earn $0.12, automatically paid in sats. The more your referrals transact, the more sats go to your Lightning wallet!
What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website!
-
 @ c0c42bba:a5feb7b5
2025-05-01 20:04:33
@ c0c42bba:a5feb7b5
2025-05-01 20:04:33Wisdom for the Fourth Decade
🔥
Turning 40 is like hitting the “I should really know better by now” milestone. It’s a time when you look back at your past self, shake your head, and chuckle (or cringe) at your youthful blunders.
Here are 15 truths you should embrace by this significant age, each one a guide to a more fulfilling, empowered life.
Leverage Is Key
Ever wonder why your colleague who seems to be on perpetual coffee breaks makes ten times more than you? It's not black magic. They have leverage—whether it's through technology, skills, or knowing how to delegate their way out of everything. Find your leverage and watch your value skyrocket.
Distraction: The Silent Killer
In our world of incessant notifications and cat videos, distraction is the enemy. It’s like having a mosquito in the room when you're trying to sleep. Cultivate a habit of deep work. Guard your attention like it's the last piece of cake at a party—fiercely.
Beware of Unqualified Advice
Taking advice from someone who hasn’t achieved what you want is like asking a cat for swimming lessons. Be selective with whose counsel you follow. Choose mentors who have walked the path and let their experiences be your map.
Own Your Life
Here’s the blunt truth: no one is coming to save you. Your problems, your life, are 100% your responsibility. Embrace this ownership. Empower yourself to be the hero of your own story. Don’t wait for a knight in shining armor—be your own rescue mission.
Action Over Self-Help Books
You don’t need to turn your living room into a self-help library. You need action. Self-discipline beats all the motivational quotes in the world. Commit to taking steps, however small, towards your goals. It's the doing, not just the knowing, that transforms dreams into reality.
The Power of Sales Skills
Unless your college degree is as specific as a neurosurgeon’s, your ticket to higher earnings in the next 90 days is learning sales. It’s a skill that opens doors, creates opportunities, and accelerates financial growth faster than you can say "commission."
No One Cares (In a Good Way)
Stop worrying about what others think—they’re too busy worrying about themselves. Take bold steps, make your moves, and create your chances. The world is too preoccupied with its own drama to scrutinize yours.
Collaborate with the Brilliant
When you meet someone smarter than you, don’t let your ego turn it into a competition. Collaborate with them. Two heads (especially two brilliant ones) are better than one, and together you can achieve remarkable things.
The Smoking Deception
Smoking has zero benefits. It’s like trying to improve your driving skills by riding a tricycle. If you want to sharpen your focus and enhance your thinking, ditch the habit. Your lungs—and your future self—will thank you.
Comfort: A Dangerous Addiction
Comfort is like quicksand. It feels nice until you’re stuck and can’t move. Regularly challenge yourself. Step out of your comfort zone because growth and fulfillment lie just beyond the boundaries of what feels easy.
Guard Your Privacy
Not everyone needs to know your life story, your plans, or what you had for breakfast. Maintain a sense of mystery. It’s not about being secretive; it’s about keeping some things just for yourself.
Alcohol: A Costly Vice
Alcohol impairs your judgment and lowers your inhibitions. It’s like paying someone to mess up your life. Avoid it. Clear thinking and control over your actions are priceless.
Keep Your Standards High
Don’t settle for less just because it’s available. High standards attract high-quality opportunities and people. Know your worth and hold out for what aligns with your values and goals.
Prioritize Your Chosen Family
The family you create is more important than the one you were born into. Nurture these relationships. They are your ride-or-die, your squad, your home team. Invest in them as they will be the cornerstone of your support system.
Take Nothing Personally
To save yourself from a myriad of mental burdens, learn not to take things personally. Most of the time, people’s actions are a reflection of their reality, not yours. This mindset shift will free you from unnecessary stress and emotional turmoil.
Embrace These Lessons -
 @ 1408bad0:4971f2ca
2025-05-01 19:55:37
@ 1408bad0:4971f2ca
2025-05-01 19:55:37Raised by Wolves is another sci-fi flick where Earth faces an extinction level event and lots of cool androids.
The series has some exciting action points showing a side of AI androids used as super weapons against humanity. If you were thinking to get an AI girlfriend, you might have a change of mind.
We see some pretty cool androids, but the awesome Necromancer is pretty spectacular and powerful and you wonder if anything can stop them. However, bizarrely, at times they are also apparently weak and despite their power, the religious group doesn't shy away from confrontation without any real weapons.
It would have been good if they had explored this side more and some of the advanced tech available like which gave the atheista super strength and speed to combat them.
The series has a feel like Foundation to it, but much less polished and maybe more negative and dreary at times. Instead of exploring exciting themes, it descends into mindless trivialities and bizarre gory rituals like killing a hideous pregnant animal and parading the dead baby corpse around.
They arrive on a mysterious but quite dreary planet and things start to set the scene.
The androids themselves are quite well played. The "Mother" is as expected in these woke times the strong and powerful one. The "Father" is the beta male serving her and the kids. It's all quite bizarre in a way.
When they first land they use some tech to make a base quickly and easily, but it disappoints how basic it all is. This is then compounded when the religious group arrive and instead of using modern tech to make a base as you might expect, instead turn into the Amish and make everything from wood. Oh yes, there are trees on this planet, but no really nice food.
The oddness continues and grows throughout the season as the androids become more human and spoiler alert , the most ridiculous storyline emerges as mother becomes pregnant and also really annoying. She starts attaching other bits and creatures to her to suck their blood out for her baby.
Despite all my criticisms, it has been an interesting first series but very disappointing in many ways compared to Foundation.
-
 @ fdd4dcaf:34a25ae0
2025-05-01 18:58:20
@ fdd4dcaf:34a25ae0
2025-05-01 18:58:20Cryptocurrency is a digital or virtual currency that uses cryptography for security and is decentralized, meaning it's not controlled by any government or financial institution.
Key Features 1. Decentralized: Cryptocurrencies operate independently of central banks and governments. 2. Digital: Cryptocurrencies exist only in electronic form. 3. Secure: Cryptocurrencies use advanced cryptography for secure transactions. 4. Limited supply: Most cryptocurrencies have a limited supply, which can help maintain their value.
Popular Cryptocurrencies 1. Bitcoin (BTC): The first and most well-known cryptocurrency. 2. Ethereum (ETH): A popular platform for decentralized applications (dApps). 3. Other altcoins: Litecoin, Ripple, Dogecoin, and many more.
Uses 1. Payments: Cryptocurrencies can be used for online transactions. 2. Investments: Some people invest in cryptocurrencies as a store of value or for potential growth. 3. Decentralized applications: Cryptocurrencies can power dApps and smart contracts.
Risks and Challenges 1. Volatility: Cryptocurrency prices can fluctuate rapidly. 2. Security risks: Cryptocurrency exchanges and wallets can be vulnerable to hacking. 3. Regulatory uncertainty: Cryptocurrency regulations vary by country and are subject to change.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 04ea4f83:210e1713
2025-05-01 18:22:24
@ 04ea4f83:210e1713
2025-05-01 18:22:2430. November 2022
Sehr geehrter Herr Bindseil und Herr Schaff von der Europäischen Zentralbank,
Ich schreibe Ihnen heute, am Tag der Veröffentlichung Ihres EZB-Blog-Berichts „Bitcoin's Last Stand", sowohl mit Belustigung als auch mit Bestürzung. Ich amüsiere mich darüber, wie albern und hilflos Sie beide erscheinen, indem Sie sich auf müde und längst widerlegte Erzählungen über Bitcoin und seine Nutzlosigkeit und Verschwendung stützen. Und ich bin beunruhigt, weil ich von zwei sehr gut ausgebildeten und etablierten Mitgliedern Ihres Fachgebiets eine viel differenziertere kritische Sichtweise auf den aufkeimenden Bitcoin und die Lightning Skalierungslösung erwartet hätte.
Sie haben sich mit Ihren dilettantischen Versuchen, Angst, Unsicherheit und Zweifel an einem globalen Open-Source-Kooperationsprojekt zu säen, das als ein ständig wachsendes Wertspeicher und -übertragungssystem für viele Millionen Menschen weltweit fungiert, wirklich einen Bärendienst erwiesen. Ein System, das jedes Jahr von mehr und mehr Menschen genutzt wird, da sie von seiner Effektivität und seinem Nutzen erfahren. Und ein System, das noch nie gehackt oder geknackt wurde, das funktioniert, um die „Banklosen" zu versorgen, besonders in den Ländern und Orten, wo sie von finsteren totalitären Regierungen schwer unterdrückt oder von der finanziell „entwickelten" Welt einfach im Stich gelassen wurden. In der Tat ist Bitcoin bereits gesetzliches Zahlungsmittel in El Salvador und der Zentralafrikanischen Republik, und erst gestern erhielt er in Brasilien den Status eines „Zahlungsmittels".
Es entbehrt nicht einer gewissen Ironie, wenn ich schreibe, dass Sie das Ziel so gründlich verfehlen, insbesondere weil die Bank- und Finanzsysteme, zu denen Sie gehören, für eine Energie- und Materialverschwendung verantwortlich sind, die um Größenordnungen größer ist als die Systeme und Ressourcen, die das Bitcoin-Netzwerk antreiben und erhalten. Ich bin mir sicher, dass Sie sich der revolutionären kohlenstoff- und treibhausgasreduzierenden Effekte bewusst sind, die Bitcoin-Mining-Anlagen haben, wenn sie neben Methan-emittierenden Mülldeponien und/oder Ölproduktionsanlagen angesiedelt sind. Und ich weiß, dass Sie auch gut über solar- und windbetriebene Bitcoin-Mining-Cluster informiert sind, die dabei helfen, Mikronetze in unterversorgten Gemeinden einzurichten.
Ich könnte noch weiter darüber sprechen, wie das Lightning-Netzwerk implementiert wird, um Überweisungszahlungen zu erleichtern sowie Finanztechnologie und Souveränität in Gemeinden in Laos und Afrika südlich der Sahara zu bringen. Aber lassen Sie mich zu dem Teil kommen, der einen gewöhnlichen Menschen wie mich einfach zutiefst traurig macht. Bitcoin ist, wie Sie sehr wohl wissen (trotz Ihrer dummen und veralteten Verleumdungen), ein technologisches Netzwerk, das nicht auf nationaler oder internationaler Verschuldung oder der Laune von Politikern basiert oder durch sie entwertet wird. Es ist ein System, das jenseits der Kontrolle einer einzelnen Person, eines Landes oder einer Gruppe von Ländern liegt. Wenn Bitcoin sprechen könnte (was er in der Tat ungefähr alle zehn Minuten tut, durch das elektro-mathematische Knistern und Summen des Wahrheitsfeuers), würde er diese Worte aussprechen:
„Über allen Völkern steht die Menschlichkeit".\ \ Als Bankiers der Europäischen Union, als Menschen von der Erde, als biologische Wesen, die denselben Gesetzen des Verfalls und der Krankheit unterliegen wie alle anderen Wesen, wäre es da nicht erfrischend für Sie beide, das Studium und die Teilnahme an einer Technologie zu begrüßen, die die Arbeit und die Bemühungen der sich abmühenden Menschen auf unserem Planeten bewahrt, anstatt sie zu entwerten? Wie die Bitcoin-Kollegin Alyse Killeen wiederholt gesagt hat: „Bitcoin ist FinTech für arme Menschen".
Ich bin dankbar für Ihre Aufmerksamkeit und hoffe, dass Sie über Bitcoin nachdenken und es gründlicher studieren werden.
Mit freundlichen Grüßen,
Cosmo Crixter
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
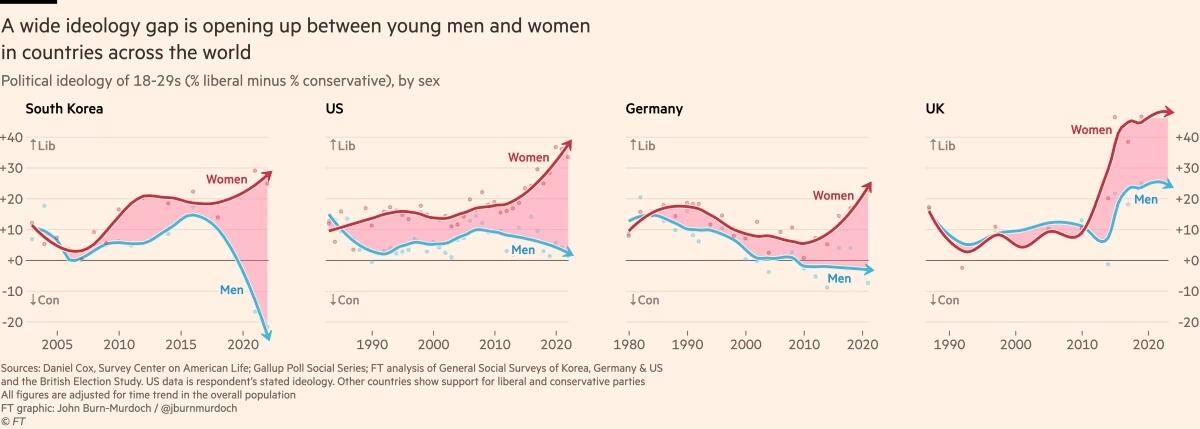
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ 36bedab2:524acad4
2024-12-26 23:23:37
@ 36bedab2:524acad4
2024-12-26 23:23:37404 Page Not Found
-
 @ 36bedab2:524acad4
2024-12-26 23:20:21
@ 36bedab2:524acad4
2024-12-26 23:20:21404 Page Not Found Error
-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ deba271e:36005655
2024-12-13 22:23:32
@ deba271e:36005655
2024-12-13 22:23:32Background
The free Alby account is going away by Jan 3rd 2025. With this users have options to switch to either self hosted Alby Hub or hosted Alby Hub for 21k sats per month (see https://albyhub.com/).
Unfortunatelly neither of these options work for me. - I'm currently traveling a lot without a single base home, so I can't just run some server "at home" and I want to be able to use it even when I'm in the midst of moving between locations. - 21k sats/month for Alby Hub is too steep just for using it for Nostr zaps. I'd pay more for the service than what I ever get in zaps. I'm happy to support projects, but the math just doesn't work out. - Running lightning node, etc in VPS is also prohibitively expensive for this usecase, but I may end up eventually doing this for other reasons. Getting VPS strong enough for self hosted node is around $80/month, but there are also options like https://nodana.io/ for $10/month. (Shill me better options if you have)
If there is a way to run a selft-custodial solution with these requirements (i.e. no "home" node, cheap for small amount zapping), let me know, otherwise this will do and we'll have to wait for BOLT12 in lnd.
Tutorial
So here's the plan - Get coinos.io account - Connect it with Amethyst via NWC - Install Alby Go to make it easier to use the account on the go
Here are the steps to do on your Android phone. iOS will be similar - Get Amethyst nostr app installed - Go to https://coinos.io/ , register new account and sign in. - On the main screen click on the settings gear icon and get the connection code
 - Reveal and copy the connection strings (tap on Copy)
- Open Amethyst and hold the lightning icon under any post
- Tap the "paste" button (see the screenshot)
- Reveal and copy the connection strings (tap on Copy)
- Open Amethyst and hold the lightning icon under any post
- Tap the "paste" button (see the screenshot)
 - Now click on Save and that's it
- Zapping should now work natively in Amethyst and it will use the hosted wallet
- Now click on Save and that's it
- Zapping should now work natively in Amethyst and it will use the hosted walletOptional - One extra thing you can do here is to install Alby Go (https://albygo.com/) and use the same "connection string" to connect it to your coinos.io account. This way you will have a mobile native wallet that's connected to this account (which makes it easier to pay with it, etc)
originally posted at https://stacker.news/items/808573
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ 6d8e2a24:5faaca4c
2024-12-02 09:03:49
@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.
What's your opinion, do you think Elon Musk is right by his statement?
-
 @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to buy bitcoin — opt out of inflation.
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-
 @ 36bedab2:524acad4
2024-11-24 23:17:58
@ 36bedab2:524acad4
2024-11-24 23:17:58A Lei de Gresham explica por que o Bitcoin é visto como um "bom dinheiro" e sua relevância no contexto econômico global.
- Bitcoin e a Lei de Gresham
O Bitcoin é um exemplo moderno da Lei de Gresham, mas funcionando de forma inversa em um ambiente onde não há obrigatoriedade de aceitação de moedas governamentais.
Bitcoin como "bom dinheiro":
Escassez e mineração: Bitcoin é escasso (máximo de 21 milhões) e sua criação exige esforço computacional significativo, semelhante à extração de ouro.
Proteção contra desvalorização: Ao contrário das moedas fiduciárias, que podem ser impressas sem limite, o Bitcoin tem regras rígidas que evitam inflação descontrolada.
Preferência pelo armazenamento: As pessoas preferem guardar Bitcoin como reserva de valor, em vez de gastá-lo, porque ele tende a valorizar com o tempo. Isso está alinhado com a Lei de Gresham: as pessoas gastam o "dinheiro ruim" (moedas fiduciárias inflacionárias) antes de gastar o "dinheiro bom" (Bitcoin).
- Bitcoin e a Geopolítica Monetária
O dólar norte-americano mantém seu status de moeda de reserva global, dando aos EUA a capacidade de imprimir dinheiro que outros países precisam usar.
Assim como o ouro, o Bitcoin é visto como uma ameaça ao sistema fiduciário liderado pelo dólar. Ele representa um "dinheiro bom" que não pode ser desvalorizado por decisões políticas.
A Lei de Gresham explica por que o Bitcoin é raramente gasto, mas amplamente guardado como uma reserva de valor. A sua ascensão reflete a insatisfação global com moedas fiduciárias inflacionárias, e ele é visto como uma esperança para o futuro financeiro, ao oferecer um sistema monetário independente, transparente e limitado.
O Bitcoin, como exemplo de "bom dinheiro", tem o potencial de mudar o sistema econômico global, libertando-o de governos que abusam de sua capacidade de emitir moedas descontroladamente.
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 6be5cc06:5259daf0
2024-11-12 03:11:11
@ 6be5cc06:5259daf0
2024-11-12 03:11:11Primeiramente, o que é mempool?
Abreviação de memory pool (ou "pool de memória") a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site mempool.emzy.de como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não a mempool do Bitcoin em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar VPN ou Tor ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
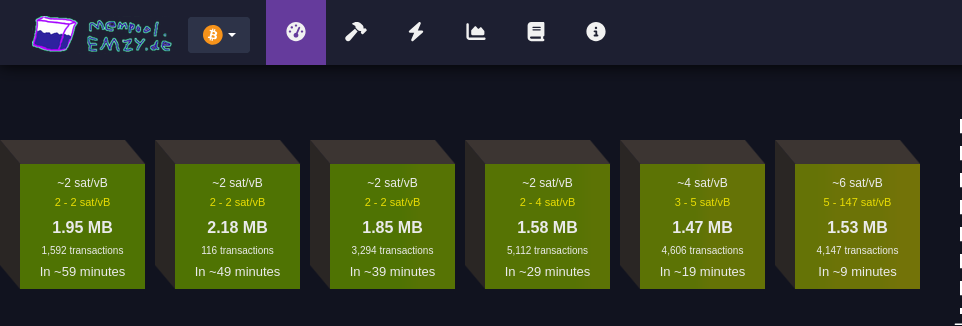
Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em entradas e saídas (inputs e outputs): * Entradas são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * Saídas representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
MB
Simplesmente o tamanho do bloco medido em megabytes :)
Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
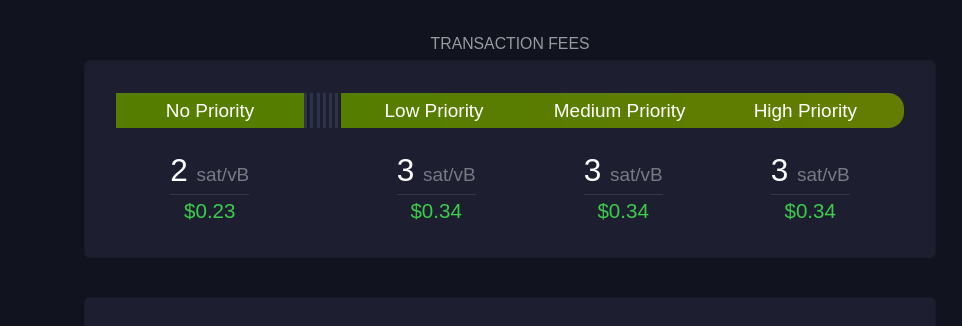 Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
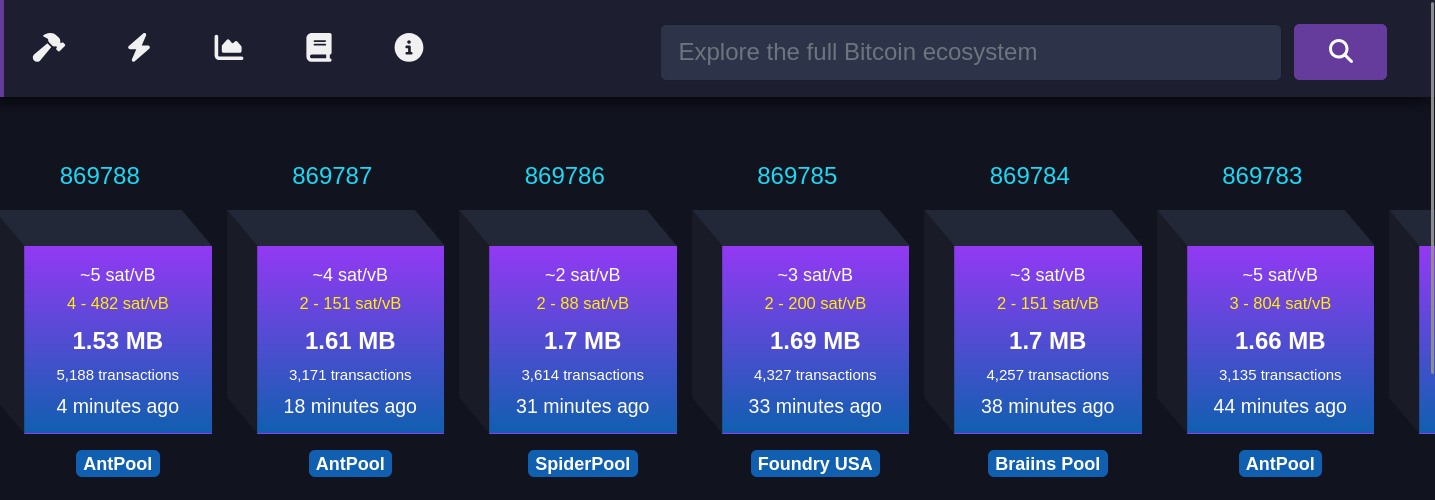 Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
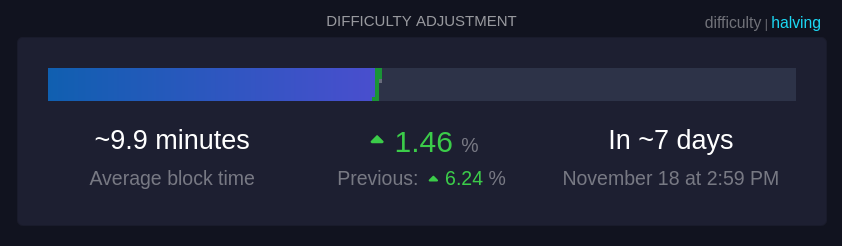 Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
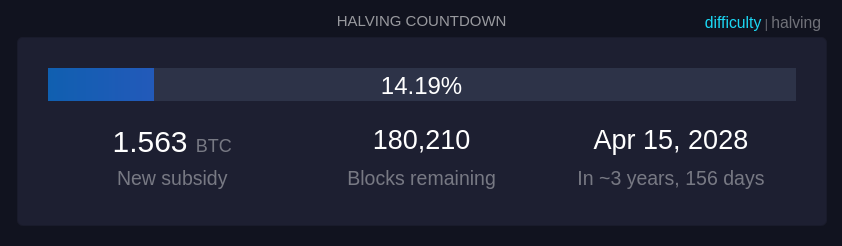 Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
 Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
Filtros (Consolidação, Coinjoin, Dados): Permite visualizar categorias específicas de transações: * Consolidação: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * Coinjoin: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * Dados: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
 Este gráfico exibe o número de transações recebidas ao longo do tempo.
Este gráfico exibe o número de transações recebidas ao longo do tempo. Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
 Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
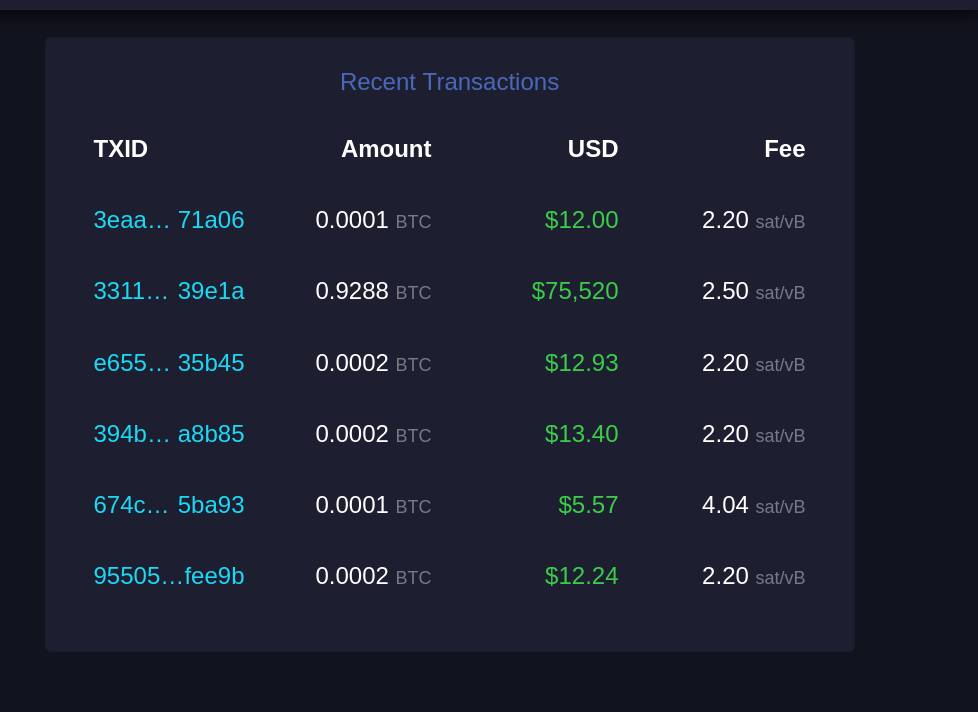 Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats! -
 @ 04ea4f83:210e1713
2025-05-01 18:21:07
@ 04ea4f83:210e1713
2025-05-01 18:21:07Erschienen in Citadel21 Vol. 18 | Veröffenlichung 21. Juli 2022\ Autor: FractalEncrypt\ Übersetzt von: Sinautoshi am 15.12.2022 - 767561

„Hast du das Recht, deinen eigenen Verstand zu verändern? Hast du das Recht, deinen eigenen Computer zu verändern? Was sind deine Rechte, und was sind deine eigenen? Was sind die Grenzen der Gesellschaft und was sind die Grenzen des Einzelnen?" - Kevin Paul Herbert
Bitcoin und Psychedelika sind gleichzeitig die mächtigsten, aber am wenigsten verstandenen Technologien auf dem Planeten.
\ Sie ergänzen sich zu revolutionären Technologien, die für ein tiefgreifendes persönliches Wachstum genutzt werden können. Sie helfen uns, selbstbestimmte Grenzen in unserem Leben zu definieren, wenn es um die Frage geht, wer die Herrschaft über die Dinge hat, die wir denken, die Software, die wir benutzen, und die Handlungen, die wir ausführen. Sie können dazu genutzt werden, die Zukunft des Einzelnen und damit auch die der Welt zu gestalten. Viele nutzen diese Werkzeuge heute, um ein besseres, produktiveres Leben zu führen. Sowohl Psychedelika als auch Bitcoin bewirken einen Paradigmenwechsel bei den Nutzern. Das sind keine einfachen Veränderungen. Diese grundlegenden und dauerhaften Veränderungen können die Art und Weise, wie man mit der Welt interagiert, völlig verändern. Souveräne Menschen können sie nutzen, um auf messbare und unermessliche, materielle und immaterielle Weise zu großem Reichtum zu gelangen. Wie bei jedem Werkzeug gibt es auch hier Gefahren, aber der richtige Gebrauch in Verbindung mit Sinn und Verstand führt zu den besten Ergebnissen.
Wie bei allen Werkzeugen sind auch diese nicht für jeden geeignet.
\ Während sowohl Bitcoin als auch Psychedelika stark missverstanden werden, können diejenigen, die sich mit kontemplativen Studien beschäftigen, asymmetrische Gewinne erzielen. Fast niemand versteht vollständig, wie diese Dinge funktionieren, nicht einmal diejenigen, die sie regelmäßig besitzen oder nutzen. Ich kann das nicht genug betonen. Selbst Menschen mit Erfahrung haben Schwierigkeiten, das Ausmaß dieser Technologien vollständig zu erfassen. Jameson Lopp, einer der ersten Bitcoin-Entwickler, sagt: „Niemand versteht Bitcoin, und das ist auch gut so". Das Gleiche gilt für Psychedelika. Die Entscheidung, sich mit diesen Technologien zu beschäftigen, ist eine sehr persönliche Entscheidung, die man nicht auf die leichte Schulter nehmen sollte. Wenn du dir die Zeit nimmst, dich eingehend mit diesen Technologien zu befassen, gehörst du zu dem kleinen Prozentsatz der Bevölkerung, der sie verstehen möchte und davon profitieren kann. Jeder muss dies für sich selbst entscheiden, und das gilt hier mehr als anderswo - Wissen ist Macht.

Einführung
\ Es gibt erstaunlich viele Beziehungen zwischen Bitcoin und Psychedelika, die sich auf vielen verschiedenen Ebenen ergeben. Diese Ähnlichkeiten führen zu einer tiefer gehenden Frage:
Sind Bitcoin und Psychedelika Werkzeuge der Selbstsouveränität, weil sie diese Ähnlichkeiten haben, oder sind sie ähnlich, weil sie Werkzeuge der Selbstsouveränität sind?
Um die Antwort zu finden, müssen wir die beiden Werkzeuge einzeln und in Kombination untersuchen. In diesem Artikel gehen wir auf die vielen Ebenen der Übereinstimmung zwischen diesen Technologien ein und ich möchte dich ermutigen, tiefer eizusteigen, wenn dein Interesse geweckt ist. Diese Kaninchenlöcher gehen tief.
Wie bei Bitcoin ist der LSD- und Psilocybin-Quellcode in verschiedenen Implementierungen frei verfügbar. Die Schöpfer von LSD und Bitcoin haben Anleitungen veröffentlicht, damit jeder auf der ganzen Welt die jeweiligen Tools lesen, verstehen und nutzen kann. Jeder kann das LSD-Patent mit den genauen Schritten zur Synthese von reinem LSD frei lesen, und jeder kann den Bitcoin-Quellcode frei lesen und seine eigene Software von Grund auf erstellen. Jeder kann an jedem Ort seine eigene Implementierung erstellen und sich einem bereits weltweit vernetzten Netzwerk von Gleichgesinnten anschließen. Die Werkzeuge sind weithin verfügbar und können von interessierten Bastlern zu Hause aus einer erstaunlichen Anzahl von Standardteilen hergestellt werden. Wenn sie erst einmal installiert sind, kann eine vorsichtige und aufmerksame Person diese Werkzeuge mit großem Nutzen einsetzen. Eine unvorsichtige Nutzung wird schnell und entschieden bestraft, und die Nutzer müssen sich selbst verbessern, nachdem sie ihre Lektion auf die harte Tour gelernt haben. Konsequenzen sind ein fester Bestandteil von Systemen, die Verantwortung verlangen.
Der ehrliche Forscher wird in Bezug auf diese beiden Technologien von Desinformationen geplagt. Bei den Psychedelika gibt es eine endlose Reihe von falschen Behauptungen. Sie reichen von „Chromosomenschäden, die zu missgebildeten Babys führen" bis hin zu „du springst aus dem Fenster und glaubst, du kannst fliegen" oder sogar, dass du „von einer einzigen Dosis dauerhaft verrückt werden kannst". Es gibt auch eine endlose Reihe von falschen Behauptungen über Bitcoin, von staatlichen Eingriffen über den Verbrauch von mehr Energie als Land X bis hin zum Kochen der Ozeane oder „es ist eine langsame, veraltete Technologie". Deshalb müssen unerschrockene Reisende ihre Bullshit-Detektoren schärfen und Experten in Sachen Recherche und logischem Denken werden.
Die Wahrheit ist, dass die Propagandamauern rund um Bitcoin und Psychedelika errichtet wurden, um die Menschen davon abzulenken, sich selbst zu versorgen. Nachgiebige Menschen, die keine Fragen stellen, sind viel leichter zu kontrollieren als Menschen, die für ihre Freiheit eintreten. Ein Großteil der Anti-Psychedelika- und Anti-Bitcoin-Propaganda kommt direkt von der Regierung. Die Fehlinformationen werden in einen Mantel der Seriosität gehüllt und durchdringen schnell die Gesellschaft. Wenn du Medien oder Inhalte konsumierst, schau dir immer die Quelle an. Wer stellt diese Informationen zur Verfügung und zu welchem Zweck? Achte immer auf die Beweggründe und Anreize. Benutze die „Brille des Skeptikers", wenn du diese Instrumente untersuchst. Glaube keiner Behauptung (auch nicht meiner), ohne sie zu belegen und zu dokumentieren. Vertraue nicht, sondern überprüfe.
Während sowohl Psychedelika als auch Bitcoin in den Mainstream-Medien als gefährlich, schädlich und geradezu böse verteufelt wurden, möchte ich hier dafür plädieren, dass diese Dinge gesund sind, gute Familienwerte vermitteln und mächtige Werkzeuge sind, um uns selbst und unsere Beziehungen zu anderen und der Welt zu verändern.
Auch wenn Bitcoin und Psychedelika wertvolle Werkzeuge sein können, sind sie kein Gegenmittel für falsches Denken. Während einige Nutzer diese Werkzeuge nutzen können, um zu handlungsrelevanten Erkenntnissen zu gelangen, sind nicht alle Nutzer so erfolgreich. Diejenigen, die sich von falschem Denken leiten lassen, können sich in den Seitengassen von Shitcoinerei, New-Age-Zauberkram und anderen logischen Irrtümern wiederfinden. Anstatt diese Wege als destruktiv zu erkennen, gaukeln sie sich vor, etwas Revolutionäres entdeckt zu haben. Es ist wichtig, dass du dein bestes Urteilsvermögen einsetzt und eine skeptische Haltung bewahrst, wenn du dich im Leben im Allgemeinen und mit diesen Tools im Besonderen bewegst.
Die Vorteile, die eine bessere Integration dieser Technologien in die moderne Gesellschaft mit sich bringt, sind enorm und könnten die Zukunft der Menschheit auf tiefgreifende Weise verändern.
Bitcoin ermöglicht eine vernetzte Welt mit einer einzigen Währung. Wie die Verwendung einer einzigen Sprache bringt er uns mit einem fließenden und dynamischen globalen Zusammenhalt zusammen. Handel, Reisen, Umzüge, Steuern und Währungsumrechnung. All das wird durch eine bescheidene Technologie vereinfacht, die für alle zugänglich ist.
Für Psychedelika kann die Integration viele Wege gehen. Der hoffnungsvollste ist jedoch der, bei dem die Menschen legalen Zugang zu bekannten Molekülen in bekannter Reinheit und mit verlässlichen Informationen über deren sichere Verwendung haben. Die Schaffung von sicheren Räumen für den Konsum von Psychedelika (wie die temporären autonomen Zonen von Hakim Bey) und ihre Verknüpfung mit psychedelischen Krisenzentren, die an lokalen Universitäten untergebracht sind, würde es der Gesellschaft ermöglichen, von beiden Seiten der psychedelischen Erfahrung zu profitieren. Die Kreativität und Fantasie der autonomen Räume und die Heilung und Transformation, die durch die Betreuung von Menschen in einer psychedelischen Krise möglich sind, haben ein grenzenloses Potenzial. Dieses sorgfältige Erfahrungsmanagement würde dem Nutzer, den Betreuern und der Gesellschaft insgesamt zugute kommen. Die durchdachte Integration dieser beiden Technologien in die moderne Gesellschaft hat das Potenzial, sowohl dem Einzelnen als auch der globalen Gemeinschaft Vorteile zu bringen.
Bildgebende Studien des Gehirns unter Einfluss von LSD und Psilocybin geben interessante Hinweise darauf, dass Psychedelika die Gehirnaktivität erhöhen und neue Bahnen und Verbindungen im gesamten Gehirn aktivieren. Wenn das mit dem Einzelnen passiert, stell dir vor, was mit dem Makrokosmos der Zivilisation passiert.
Jeder Weg birgt Gefahren, und es gibt kein Patentrezept. Wir haben die Werkzeuge; sie mit Geschick, Integrität und Zielstrebigkeit einzusetzen, ist eine Entscheidung. Das Werkzeug wird die Arbeit nicht für dich erledigen. Das ist der Proof of Work-Gedanke in Aktion.
Ein Hinweis zu den hier erwähnten psychedelischen Substanzen: Es gibt zwar viele psychedelische Verbindungen, aber in diesem Artikel konzentriere ich mich auf LSD und Psilocybin. LSD ist zwar das am weitesten verbreitete Psychedelikum, aber es kann eine zentralisierende Wirkung auf die Chemiker haben, die es herstellen. Es bildet sich eine natürliche Vertriebspyramide mit dem Chemiker an der Spitze, den Groß- und Einzelhändlern und schließlich den Endverbrauchern, die die Basis der Pyramide bilden. Diese Pyramide entsteht, weil ein einziges Gramm LSD 10.000 Dosen enthält. Die LSD-Synthese ist für begeisterte Forscher nicht unerreichbar, aber für den „Normalbürger" nicht so leicht zugänglich wie der Anbau von Pilzen. Pilze der Gattung Psilocybe sind viel dezentraler, weil sie ein Werkzeug sind, das von fast jedem und überall auf dem Planeten eingesetzt werden kann. Es wird kein Händler benötigt, nur du, etwas Erde und ein paar Sporen.
Zusammensetzung der Leserschaft
\ Ich gehe davon aus, dass dieser Artikel von Personen mit unterschiedlichem Verständnis für die behandelten Themen gelesen wird. Ich gehe davon aus, dass die Leser in eine der folgenden vier Kategorien fallen;
- Bitcoiner, die Erfahrung mit Psychedelika haben
- Bitcoiners, die keine Erfahrung mit Psychedelika haben
- Menschen mit psychedelischer Erfahrung, die Bitcoin nicht benutzen
- Menschen, die weder mit dem einen noch mit dem anderen Erfahrung haben
Während sich der größte Teil dieses Artikels auf die Vergleiche und Gemeinsamkeiten zwischen Bitcoin und Psychedelika konzentriert, gehen die folgenden kurzen Abschnitte auf jeden einzelnen ein. Für diejenigen, die damit nicht vertraut sind, beschreibe ich kurz, warum ich beide für ein wichtiges Instrument der Selbstbestimmung halte. Sowohl Bitcoin als auch Psychedelika sind Gegenstand von wilden Fehlinformationskampagnen, auf die wir später noch genauer eingehen werden. Ich erwähne das jetzt nur, um darauf hinzuweisen, dass die allgemein zugänglichen Medien zu beiden Themen verwirrend und in vielerlei Hinsicht irreführend sind, wenn du nur ein oberflächliches Verständnis von beiden Themen hast. Man muss sich eingehend mit dem Thema befassen, um den ganzen Schwachsinn zu durchschauen.
Für diejenigen, die noch keine Erfahrung mit Psychedelika haben oder diese nicht kennen
\ LSD und Psilocybin gehören zu den mächtigsten Werkzeugen für die Selbsterkundung, die heute verfügbar sind. Sie sind außerdem ungiftig und nicht gewohnheitsbildend, obwohl sie auch Gefahren bergen. Sie geben dir einen Zugang zu dir selbst, den du auf keine andere Weise erreichen kannst. Kein noch so großer Yoga- oder Meditationstrip kann dir einen LSD-Trip bescheren. Sie gehören zu den sichersten Moleküle auf dem Planeten. Vergleiche zum Beispiel NULL Todesfälle durch LSD und Magic Mushrooms mit über 3.000 Todesfällen pro Jahr durch etwas, das als sicher gilt, wie Aspirin.
Die Bedeutung von Psychedelika als Mittel zur menschlichen Selbsterforschung kann gar nicht hoch genug eingeschätzt werden. Steve Jobs beschrieb die Einnahme von LSD als eines der wichtigsten Dinge in seinem Leben.
"Die Einnahme von LSD war eine tiefgreifende Erfahrung, eines der wichtigsten Dinge in meinem Leben. Es stärkte meinen Sinn für das, was wichtig war - großartige Dinge zu schaffen und sie in den Strom der Geschichte und des menschlichen Bewusstseins einzubringen, so gut ich konnte." - Steve Jobs

\ Roland Griffiths Arbeit an der Johns Hopkins University zeigt, dass Psilocybin Depressionen und Angstzustände bei Patienten mit lebensbedrohlichen Krebserkrankungen erheblich und nachhaltig verringert.
„Das hat mich wie ein Schlag ins Gesicht getroffen. Die Vorstellung, dass Menschen Psilocybin einnehmen und sich ihr Leben innerhalb weniger Stunden komplett verändert. Nicht nur positive Veränderungen von Einstellungen, Verhaltensweisen und Überzeugungen, sondern eine grundlegende psychologische Veränderung an einem Nachmittag. Selbst einige Jahre nach den Experimenten berichten 75 % der Freiwilligen, dass ihre einzige Psilocybin-Dosis eine der bedeutsamsten Erfahrungen ihres Lebens war, wenn nicht sogar DIE bedeutsamste Erfahrung überhaupt."\ - Brian Muraresku

Für alle, die neu sind oder keine Erfahrung mit Bitcoin haben
\ Bitcoin ist eine Null-zu-Eins-Erfindung, die den Regierungen der Welt die Macht entzieht und sie an Einzelpersonen zurückgibt. Es ist eine nie wieder zu wiederholende Entdeckung, die seit einem Jahrzehnt das Leben verändert. Es ist Geld, das durch Mathematik gestützt wird, nicht durch die Versprechen von Politikern.
Hast du dich jemals gefragt, ob Geld für die menschliche Entwicklung und das Wachstum wichtig ist? Wie haben verschiedene Formen von Geld den Verlauf der menschlichen Geschichte verändert? Geld wird gegen die Zeit der Menschen getauscht. Unsere Lebenszeit ist endlich. Eine unendliche Ressource zu verwenden, um für eine endliche Ressource zu bezahlen, ist von Natur aus ungerecht. Im Geld ist Lebensenergie gespeichert.
Das Geld, das wir heute verwenden, ist als Fiat-Geld bekannt, „Geld per Dekret". Mit anderen Worten: „Geld, weil wir es sagen". Fiat-Geld verliert mit der Zeit an Wert, was als „Inflationsrate" bezeichnet wird. Geld, das mit der Zeit an Wert verliert, ist Zeitdiebstahl. Es stiehlt den Wert, für den du bereits gearbeitet und deine Zeit und Energie investiert hast, um ihn zu verdienen. Bitcoin ist Geld, das im Laufe der Zeit nie an Wert verliert. Seine elegante mathematische Ausschüttung ist vorprogrammiert und unveränderlich.
„Du kannst beim Fiat-Standard bleiben, bei dem einige Leute kostenlos unbegrenzt neue Geldeinheiten produzieren können, nur du nicht. Oder du kannst dich für den Bitcoin-Standard entscheiden, bei dem niemand das tun darf, auch du nicht."- Ross Stevens

\ Auch wenn ich keine begutachteten Studien vorweisen kann, habe ich als persönliche Anekdote eine Unterströmung der Selbstverwirklichung bemerkt, die sich stark durch die Bitcoin-Kultur zieht. Viele setzen sich für eine Rückbesinnung auf das Landleben ein, für eine gesunde Ernährung (indem sie schlechte Lebensmittel wie Samenöle und künstliches Fleisch weglassen und sich vermehrt mit minimal oder gar nicht verarbeiteten natürlichen Lebensmitteln ernähren), für Sport, Kunst, Familie und Wellness.
Ich glaube, dass das persönliche Wachstum der Bitcoiner die Ethik widerspiegelt, die im Bitcoin-Netzwerk selbst einprogrammiert ist. Hier sind zwei Beispiele;
Proof of Work - Bitcoinern ist klar, dass ohne Handeln kein Wert geschaffen werden kann. Das gilt für fast jeden Aspekt des Lebens. Um die Vorteile zu erhalten, muss man die Arbeit machen.
Vertraue nicht, sondern verifiziere (Don't Trust, Verify) - der Aspekt des Verifizierens und nicht nur des Akzeptierens jeder angebotenen Version der Wahrheit ist heute wichtiger denn je.
Es gibt noch viel mehr, aber ich hoffe, dass dieser kurze Überblick einen Einblick gibt, warum diese beiden Technologien meiner Meinung nach komplementär und diskussionswürdig sind.
Werkzeuge der Selbstbestimmung
\ Wenn ich sage, dass Bitcoin und Psychedelika Werkzeuge der Selbstbestimmung sind, dann will ich damit sagen, dass es sich um Werkzeuge handelt, die jedem von uns heute zur Verfügung stehen und die wir nutzen können, um unsere eigenen Antworten auf Fragen wie diese zu definieren, zu formen und zu gestalten:
- Was bedeutet es, ein freies und souveränes Individuum zu sein?
- Was darf der Staat regeln?
- Was sind deine Rechte, und was ist dein Eigentum?
- sind die Grenzen der Gesellschaft und
- was sind die Grenzen des Individuums?
- Hast du das Recht, deine eigene Meinung zu ändern?
- Hast du das Recht, deinen eigenen Computer zu verändern?
Unsere Antworten auf Fragen wie diese bestimmen den Verlauf unseres Lebens. Wir können diese Werkzeuge nutzen, um tiefer in unseren Geist und Körper zu blicken oder an die Grenzen des Verständnisses zu gelangen. Der zielstrebige Mensch kann diese Erkenntnisse nutzen, um ein erfolgreicheres Leben zu führen.
Bitcoin ist ein Werkzeug der Information. LSD ist ein Mittel der Erfahrung und der Vorstellungskraft.
Die grünen Rechtecke aus Fiat-Papier haben einen Wert, weil der Staat das sagt. Bitcoin ist das Gegengift zum Fiat-Geld. Vieles andere auf dieser Welt wird uns per Dekret aufgezwungen. Bitcoin hilft dir, Fiat-Geld aus deinem Leben zu entfernen. Psychedelika helfen dir, Fiat-Geld aus deinem Geist und Körper zu entfernen. Zusammen geben sie dir die Macht, in deiner Souveränität aufrecht zu stehen und die ultimative Herrschaft über dein inneres und äußeres Leben zu erlangen.
Es sind Werkzeuge, die wir zu Hause für unseren persönlichen Gebrauch nutzen können und die niemandem schaden. Psychedelika, manchmal auch Entheogene genannt, wecken ein Gefühl für das Göttliche im Inneren. Sie geben den Nutzern direkten Zugang zu mystischen Zuständen, ohne dass Dritte wie organisierte Religionen, Schriften oder Doktrinen dazwischengeschaltet werden müssen. Bitcoin bietet den Nutzern Zugang zu Geld, das durch Mathematik gestützt wird und nicht durch die Versprechen von Ökonomen, Banken oder Politikern. Die Nutzer sind nicht gezwungen, Vermittler zwischen sich und die direkte Erfahrung der Realität zu stellen. Sie sind nicht gezwungen, sich von jemand anderem sagen zu lassen, „wie es ist" oder „wie es sich anfühlt". Sie können es selbst erleben.
Bei Bitcoin haben alle Nutzer die Möglichkeit, einen vollständigen Knotenpunkt (Full-Node) zu betreiben, und damit direkten Zugang zu einem weltweit vernetzten Finanznetzwerk ohne Vermitter oder Zensur. Bei Psychedelika erhalten die Nutzer einen direkten, unvermittelten Zugang zu ihren eigenen vernetzten neuronalen Netzwerken. Es gibt auch global vernetzte soziale Netzwerke, die entstehen, um beide Technologien zu verbreiten, zu diskutieren und zu nutzen, oft in Kombination. Das sind Peer-to-Peer-Netzwerke ohne Anführer, ohne Verantwortliche und ohne Angestellte. Alle Nutzer sind gleichberechtigt.
Die Verwendung von Bitcoin und Psychedelika eröffnet das Verständnis für die Verflechtung verschiedener Disziplinen und Technologien. Politik, Technik, Wirtschaft, Chemie, Psychologie, Spieltheorie, Soziologie und Philosophie sind nur einige der Bereiche, die zusammenkommen, um unser Verständnis für diese Werkzeuge und ihre optimale Nutzung zu verbessern.
Viele Nutzerinnen und Nutzer von Bitcoin und Psychedelika haben festgestellt, dass der Weg zu einem tieferen Verständnis in einer breiten Palette von Themen liegt. Die Kombination des durch Bildung gewonnenen Wissens mit den Erkenntnissen, die wir durch die Nutzung dieser Technologien gewinnen, bringt mehr Tiefe und Verständnis in unser Leben.
„Bitcoin ist amoralisch und absolut neutral gegenüber der Frage, ob du dem Netzwerk beitrittst oder nicht", sagt Mark Maraia. Ich würde das noch erweitern und sagen, dass LSD amoralisch und absolut neutral ist. Die extremen Erfahrungen sind auf deine persönliche Körperchemie, deine Einstellung und das gesamte Wissen und die Erfahrung deines Lebens zurückzuführen. Wir sind die Variablen, Bitcoin und LSD sind die Konstanten. Du bekommst das heraus, was du hineinbringst.
Ich habe viele Bitcoiner gesehen, die in Kaninchenlöcher geraten sind, die zu bedeutenden Veränderungen in ihrem Leben führen. Wie sie essen, arbeiten, Sport treiben, Medien konsumieren und vieles mehr, ändert sich. Tiefgreifende Veränderungen, die sie oft dem Bitcoin und dem Grundsatzdenken zuschreiben. Diese Lebensveränderungen haben wenig oder gar nichts mit Wirtschaft, Geld oder Finanzen zu tun.
Nutzer von Psychedelika machen ähnliche Veränderungen in ihrem Lebensstil durch, die ihren Umgang mit der Welt tiefgreifend verändern. Diese Veränderungen können sich auf die gleiche Weise wie beim Bitcoin manifestieren: Sie verändern die Art und Weise, wie Menschen essen, arbeiten, Sport treiben, Medien konsumieren, miteinander interagieren, usw. Diese bedeutenden Veränderungen im Leben wären ohne den direkten Einsatz einer oder beider der in diesem Artikel besprochenen Technologien vielleicht nie verwirklicht worden.
Wie jedes Werkzeug kann auch dieses missbraucht werden und die Nutzer auf den falschen Weg führen. Wir werden in Kürze mehr über die naiven Irregeleiteten, die Affinitätsbetrüger, die Angreifer und die ganz schlechten Akteure sprechen, die diese Technologien nutzen, und darüber, wie das alles abläuft.
Die Kombination von Bitcoin und Psychedelika

Während jede dieser Technologien für sich genommen lebensverändernd sein kann, eröffnet ihre Kombination einzigartige Möglichkeiten für den Einzelnen und die Menschheit als Ganzes. Bitcoin und Psychedelika sind wie Musikinstrumente, die jeweils mit ihrer eigenen, einzigartigen Frequenz schwingen. Jedes Instrument kann für sich allein ein Lied spielen, aber zusammen vervielfachen sich die symphonischen Möglichkeiten exponentiell. Wenn sie zusammen gespielt werden, schwingen die Frequenzen der Instrumente nahtlos mit und verwandeln sich für immer in tiefere, reichere Lieder.
In meinem eigenen Leben schreibe ich den Psychedelika einen direkten Einfluss auf die Kunst zu, die ich mache. Ohne Psychedelika hätte ich vielleicht Kunst in irgendeiner Form geschaffen, aber sie sähe nicht so aus und wäre nicht von denselben Designentscheidungen und Motivationen geprägt. Mein gesamtes Kunstportfolio ist ein direktes und eindeutiges Ergebnis der intensiven persönlichen Beschäftigung mit revolutionären psychedelischen Technologien wie LSD und Bitcoin. Ich habe Bitcoin durch eine Kombination aus Kunst, Psychedelika und natürlich Bitcoin kennengelernt. Früher habe ich LSD Blotter Art Designs gemacht, Kunst, die in winzige Quadrate perforiert und dann von den Chemikern mit LSD getränkt wurde. Ich habe auch das LSD-Mandala entworfen, das die soziale Geschichte, die Chemie und die Geheimnisse der LSD-Verteilung in einem grafischen Kodex verschlüsselt.
Ein anonymer Bitcoiner aus Brasilien fragte mich 2015, ob ich Bitcoin für meine Kunst nehmen würde, da es für ihn der einfachste Weg sei, internationale Transaktionen durchzuführen. Ich hatte zwar von Bitcoin gehört, wusste aber nicht, wie ich sie annehmen sollte. Ich sagte ihm: „Klar, aber du musst mir sagen, wie ich das einrichten soll". Dieser anonyme Fremde half mir, meine erste Bitcoin-Brieftasche einzurichten, schickte mir 3,1 Bitcoin für meine Kunst und verschwand dann prompt wieder im Internet, ohne dass ich je wieder von ihm gehört hätte. Ich vergaß Bitcoin, aber ein paar weitere „Berührungspunkte" mit Bitcoin im Laufe der Jahre waren wie eine Reihe von Neonpfeilen, die auf eine wichtige Botschaft des Universums hinwiesen.
Im Dezember 2017 machte ich meine erste Bitcoin-Kunst. Dieser Themenwechsel war für mich sehr wichtig, da ich meine Kunst als eine Methode betrachte, meine Botschaft in die Welt zu tragen. Wenn ich mich auf etwas einlasse, nimmt es mein ganzes Leben in Beschlag. Psychedelika waren über ein Jahrzehnt lang mein Thema gewesen, daher war dieser Wechsel für mich von großer Bedeutung.
Ich ließ mich schnell auf den Mist ein und glaubte etwa anderthalb Jahre lang lächerliche Dinge wie „Ethereum ist die Zukunft der Kunst" und andere ebenso zweifelhafte Dinge. Aber wie ich schon sagte, wenn ich mich für etwas interessiere, bin ich davon eingenommen. Ich untersuche es so gründlich, wie ich kann.
Ich fing an, NFTs zu untersuchen, lernte, wie sie kodiert sind und wie sie funktionieren, und je mehr ich lernte, desto desillusionierter wurde ich. Durch die Verwendung einer Reihe von Shitcoins in Kombination mit Psychedelika erkannte ich schnell, dass ich auf dem falschen Weg war. Ich konnte auch den richtigen Weg klar erkennen. Der eine Weg führt mich in die Dunkelheit und Zerstörung, zu Lügen und Betrug, der andere führt zu Wahrheit und Stabilität. Mein Weg ist Bitcoin, einzig und alleine. Ich kann mich nicht länger von den falschen Versprechungen und der Sackgasse in der Müllhalde der Shitcoinerei ablenken lassen.
Es gab eine harte Grenze, eine Schwelle, und ich habe sie im Juni 2019 überschritten. Während ich an einem Hackathon-Projekt für die Bitcoin-Konferenz 2019 arbeitete, machte ich eine psychedelische Erfahrung, die mir einen Strich durch die Rechnung machte. Während ich an einem (wirklich kitschigen) „Super-Bowl-Werbespot für Bitcoin" arbeitete, traf mich der Entschluss auf einmal; ich loggte mich in die Börse ein und tauschte alle meine Shitcoins gegen Bitcoin. Und meine Kunst sollte von nun an nur noch in Bitcoin gemacht werden.
Im folgenden Monat flog ich nach San Francisco zur Bitcoin 2019 Konferenz. An jenem Freitag während der Konferenz hörte ich, wie jemand die Uhr und den kalenderähnlichen Charakter von Bitcoin erwähnte. Ich nahm an diesem Abend LSD und ging zu einem Bitcoin-Entwicklertreffen, das nur wenige Blocks von meinem Hotel entfernt stattfand. Nachdem ich einen ganzen Tag und Abend LSD und Bitcoin-Inhalte konsumiert hatte, verbrachte ich die Nacht damit, die allerersten Konzeptentwürfe für die Bitcoin Full Node Skulptur zu skizzieren. In den nächsten sieben Monaten arbeitete ich unermüdlich, mied Freunde, Fernsehen, Twitter und Schlaf, um immer mehr zu schaffen.

Dabei verband ich Bitcoin und Psychedelika direkt mit dem Wunsch, ein Kunstwerk zu schaffen, das Bitcoin über Zeit, Raum, Geist und die Menschen, die das Netzwerk bilden, abbildet. Dieser Prozess erstreckte sich über die gesamten sieben Monate und ich habe in dieser Zeit LSD auf unterschiedliche Weise eingesetzt. Ich fand es in zwei Bereichen besonders hilfreich:
- Für ganzheitliches, übergreifendes Denken. Um die Visionen zu erhalten und festzuhalten, die ich von der Idee in die Form bringen wollte. Das sind in der Regel höhere Dosen, und ich arbeite während dieser Erfahrung nicht an der Kunst. Ich überdenke das Projekt in meinem Kopf und beobachte, wie es entsteht. Ich mache mir Notizen und mache einfache Skizzen, ohne Druck, halte alles fest.
- Für das Arbeiten in einem Flow-Zustand. Hier hast du direkten Zugang zum kreativen Fluss, während du an der Kunst arbeitest. Die Zeit löst sich auf, und alles fällt weg. Du und der kreative Prozess brennt im Einklang. In diesen Phasen kann eine fantastische Menge an Arbeit in kurzer Zeit erledigt werden.
Beides miteinander zu verbinden, bedeutet nicht immer, dass man beides zur gleichen Zeit braucht. Ich habe ein Sprichwort: „Erschaffe high, bearbeite nüchtern". Bringe deine Ideen, Fähigkeiten und Leidenschaften in die psychedelische Erfahrung ein und konzentriere all das auf eine bestimmte Mission, ein Ziel. Nutze diese rohe, ungeschliffene Inspiration und forme sie mit einem ruhigen Geist. Den Nutzen aus jedem dieser Zustände zu ziehen, war entscheidend für die Erstellung der Bitcoin Full Node Skulptur.
Während des Prozesses lernte ich viel über Bitcoin und seine Funktionsweise, indem ich versuchte, es visuell zu beschreiben. Man kann nicht beschreiben, was man nicht versteht. Ich habe auch viele Erkenntnisse gewonnen, indem ich verschiedene Aspekte von Bitcoin visualisiert habe. Ich konnte sehen, wie wichtige Teile auf neue Weise zusammenpassen, und mein Verständnis vertiefte sich durch die Fähigkeit, Konzepte geometrisch zu visualisieren.
Jede Reise besteht aus drei Teilen, die jeweils ein paar Stunden dauern. Der Aufschwung, der Höhepunkt und der Abschwung. Jede oder alle (oder keine) dieser Phasen kann für die Kreativität genutzt werden. Wenn die Intensität des Trips nachlässt, ist die Phase des Ausklingens für mich eine äußerst produktive Phase.
Ich erzähle dir von einer meiner Methoden, um LSD für deine Kreativität zu nutzen, wobei ich mir bewusst bin, dass das, was für mich funktioniert, für dich vielleicht nicht funktioniert. Die Methode ist sehr einfach. Sie setzt voraus, dass du gutes LSD in einer bekannten Dosierung auf dem Papier hast. (Und du weißt zuverlässig, wie stark eine Dosis auf dich wirkt).
- Schneide dein LSD je nach Potenz in 3er oder 4er Stücke. Du willst, dass diese Menge ausreicht, um etwas zu spüren. Es sollte keine Dosis unterhalb der Wahrnehmungsschwelle sein.
- Beginne damit, ein Viertel einer Standarddosis zu nehmen. Manchmal reicht das schon aus, dann kannst du hier aufhören.
- Nachdem du 60 Minuten gewartet hast, nimmst du eine weitere Vierteldosis. Du kannst weiterhin jede Stunde eine viertel Dosis einnehmen. Ich habe keine feste Grenze dafür gefunden, wie lange das so weitergehen kann.
- Konzentriere dich bei dieser Erfahrung auf ein bestimmtes Projekt oder Problem.
- Lege eine Zeit und einen Ort fest, an dem du nicht gestört oder abgelenkt wirst.
- Halte alle Werkzeuge bereit, die du brauchst.
Indem du die Dosis über die Zeit verteilst, vermeidest du die Intensität einer krachenden LSD-Welle, die dich auf einmal trifft. Indem du die Dosis verteilst, wird es einfacher, in den psychedelischen Raum zu gelangen und sich darin zurechtzufinden. Es gibt weniger Rucke zwischen dem normalen Wachbewusstsein und der LSD-Gedankenwelt, weil das eine leicht in das andere überzugehen scheint. Außerdem wird die Intensität des Erlebnisses insgesamt abgeschwächt, während es gleichzeitig verlängert wird und leichter zu bewältigen ist.
Auf einer tieferen Ebene werden Psychedelika und Informatik schon seit Jahrzehnten kombiniert, und ich habe viele faszinierende Beispiele gefunden, wie Menschen dies erfolgreich tun.
Ein Computerprogrammierer auf Reddit scheint eine ähnliche Technik zu verwenden, wie ich sie oben beschrieben habe.
„Du kannst auch versuchen zu programmieren, während du auf einer leichteren Dosis bist. Das kann eine ziemlich erstaunliche Erfahrung sein, denn du kannst mit einem Bruchteil eines Tabs trippen und programmieren. Wenn du das machst, nimm dir ein Problem vor, mit dem du anfängst, bevor du trippst, aber hab keine Angst davor, den Gang komplett zu wechseln und etwas völlig anderes, verrücktes und wunderbares zu machen." -u/tosler
\ Wenn du ein Psychedelikum nimmst und über ein Thema nachdenkst, auf das du neugierig bist, kann das zu neuen und neuartigen Ideen und Lösungen führen. Als z. B. der Nobelpreisträger Kary Mullis die PCR erfand, schrieb er die Nobelpreis-Idee direkt seinen Erfahrungen mit LSD zu.
„Hätte ich die PCR erfunden, wenn ich kein LSD genommen hätte? Das bezweifle ich ernsthaft... Ich könnte auf einem DNA-Molekül sitzen und den Polymeren zusehen, wie sie vorbeiziehen. Das habe ich zum Teil auf psychedelischen Drogen gelernt." - Kary Mullis

\ Ein weiteres hervorragendes Beispiel für eine wissenschaftliche Studie über die kreativitätsfördernden Eigenschaften der Kombination von psychedelischen Drogen mit bestimmten Interessens- oder Forschungsgebieten stammt aus einer Studie, die vor der Illegalisierung von LSD durchgeführt wurde. Das ist deshalb wichtig, weil LSD in der Öffentlichkeit noch nicht mit dem negativen Stigma der „Illegalität" oder „Unmoral" behaftet war, da es keine Gesetze gegen den Konsum von LSD gab.
An der Studie nahmen 27 Personen teil, „darunter Ingenieure, Physiker, Mathematiker, Architekten, ein Möbeldesigner und ein Werbegrafiker. Die Probanden wurden angewiesen, ein oder mehrere Probleme auszuwählen, die eine kreative Lösung erforderten und an denen sie wochen- oder monatelang gearbeitet hatten, ohne eine zufriedenstellende Lösung finden zu können."
Und jetzt kommt der Clou: Noch Monate nachdem die Wirkung nachgelassen hatte, blieben die Teilnehmer standhaft: LSD hatte ihnen absolut geholfen, ihre komplexen, scheinbar unlösbaren Probleme zu lösen. Und die Einrichtung stimmte zu.
Kurz nach ihren LSD-Erfahrungen brachten die 27 Männer eine Reihe von Innovationen auf den Weg, die weithin Anerkennung fanden, darunter:
- ein mathematisches Theorem für NOR-Gatter-Schaltungen
- ein konzeptionelles Modell für ein Photon
- eine Vorrichtung zur Strahlsteuerung eines linearen Elektronenbeschleunigers
- ein neues Design für das Vibrationsmikrotom
- eine technische Verbesserung des Magnetbandrekorders
- Entwürfe für eine private Residenz und einen Kunsthandwerker-Einkaufsplatz
- ein Experiment für eine Raumsonde zur Messung der Sonneneigenschaften
Da LSD illegal ist, werden wir vielleicht nie erfahren, wie viele Entdeckungen und Erfindungen das direkte Ergebnis der Kombination von Psychedelika mit der Leidenschaft und den Fähigkeiten eines Menschen sind. Viele Berufstätige hatten und haben immer noch zu viel Angst vor beruflichen oder gesellschaftlichen Konsequenzen aufgrund ihres Konsums von Psychedelika. Glücklicherweise schweigen nicht alle zu diesem Thema. Dennis Wier, ein Computerprogrammierer, hat diese Geschichte erzählt:
"So habe ich 1975 LSD-25 für ein komplexes Programmierprojekt verwendet. Ich arbeitete in New York an der Entwicklung eines Compilers für eine Anwendungssprache namens "MARLAN". An einem bestimmten Punkt des Projekts konnte ich keinen Überblick über die Funktionsweise des gesamten Systems gewinnen. Es war wirklich zu viel für mein Gehirn, all die subtilen Aspekte und Verarbeitungsnuancen im Blick zu behalten, um einen Überblick über die Verarbeitung und das Design zu bekommen. Nachdem ich einige Wochen lang mit diesem Problem gekämpft hatte, beschloss ich, ein wenig Säure zu verwenden, um zu sehen, ob dies einen Durchbruch bringen würde.\ \ Ich nahm nur fünfundsiebzig Mikrogramm, weil ich kein Interesse daran hatte, zu trippen, denn ich hatte ein bestimmtes, begrenztes und eindeutiges Ziel für den Gebrauch von LSD. Während ich durch das LSD stimuliert wurde, konnte ich mir das gesamte System gleichzeitig vor Augen führen. Ich verbrachte einige Zeit damit, mir verschiedene Aspekte des Compilers, der Sprache und der Verarbeitung vor Augen zu führen. Unter dem Einfluss von LSD entdeckte ich drei oder vier Ungereimtheiten im Design und machte mir Notizen, um sie später zu überprüfen.\ \ Nachdem alle Änderungen vorgenommen worden waren, konnte ich die Programmierung dieses riesigen Systems erfolgreich abschließen. Die von mir vorgenommenen Änderungen verringerten künftige Fehler bei der Programmänderung und trugen zur Eleganz des Entwurfs bei. Das System war ein kommerzieller Erfolg für meinen Arbeitgeber und wurde von ihm viele Jahre lang genutzt. Obwohl die Verwendung von LSD eine wichtige Komponente für den Erfolg des Systems war, wusste außer mir niemand von seiner Verwendung."
\ Bill Atkinson, der Erfinder von HyperCard, gab zum ersten Mal öffentlich bekannt, dass die gesamte Idee für seine Softwareerfindung auf einem LSD-Trip entstand, den er bei 1:03:45 in diesem Video anschaulich beschreibt.
„Ich will nicht behaupten, dass jeder Softwareentwickler auf der Welt LSD nehmen sollte, aber bei mir hat es funktioniert." -Bill Atkinson

\ 1987 revolutionierte Apple die Art und Weise, wie Menschen mit ihren Computern interagieren, indem es HyperCard kostenlos zu jedem verkauften PC lieferte. Das Programm wurde dafür gelobt, „die Möglichkeiten der Computerprogrammierung und des Datenbankdesigns in die Hände von Nicht-Programmierern zu legen". Es wurde zu einem der ersten Werkzeuge für das elektronische Publizieren. HyperCard selbst war ein Werkzeug zur Selbstbestimmung, das von einem Programmierer entwickelt wurde, der zwei andere Werkzeuge zur Selbstbestimmung nutzte. Das ist eine sehr interessante Situation, in der die Werkzeuge neue Werkzeuge hervorbringen, die von den Menschen, die sie benutzen, hergestellt werden, und die neuen Werkzeuge sind auf dasselbe Ziel ausgerichtet wie die ursprünglichen Werkzeuge - die Erhöhung der Selbstsouveränität.
Ich möchte ein letztes Beispiel für einen Computerprogrammierer anführen, der LSD und dezentrale Netzwerke für sein Streben nach Selbstbestimmung nutzte. Kevin Paul Herbert, ein autodidaktischer Computerprogrammierer und Softwaredesigner, der Software entwickelt hat, die heute auf Millionen von Internet-Routern weltweit läuft, gab 2008 dieses Interview.
"Psychedelika sind besonders hilfreich bei der Entwicklung neuer Computertechnologien. Sie müssen etwas an der internen Kommunikation in meinem Gehirn verändern. Was auch immer mein innerer Prozess ist, der mich Probleme lösen lässt, er funktioniert anders, oder vielleicht werden andere Teile meines Gehirns benutzt. Wenn ich auf LSD bin und etwas höre, das reiner Rhythmus ist, versetzt mich das in eine andere Welt und in einen anderen Gehirnzustand, in dem ich aufgehört habe zu denken und angefangen habe zu wissen." - Kevin Paul Herbert
\ Ein letztes Zitat von Kevin Herbert geht wirklich auf die tiefgreifenden Fragen ein, die den selbstbestimmten Technologien zugrunde liegen. Vergiss nicht, dass er über all das bereits 2008 nachgedacht hat.
"Was steht für unsere Freiheit? Was steht dafür, was die Regierung regulieren darf und aus welchem Grund?
Wohin uns das führt, hängt davon ab, ob wir bereit sind, ein Modell zu akzeptieren, in dem die Dinge offen sind - einschließlich unseres eigenen Verstandes - oder ein Modell, in dem die Dinge geschlossen sind - einschließlich unseres eigenen Verstandes und der Dinge, über die wir nachdenken können, sowie der Chemikalien, die wir einsetzen können, um unser Denken zu beeinflussen." - Kevin Paul Herbert
\ Sei dir bewusst, dass diese Erfahrungen durch den Lebensweg des Einzelnen geprägt sind. Je mehr du weißt und je mehr Fähigkeiten du hast, desto mehr werden sie den Inhalt deiner psychedelischen Erfahrungen beeinflussen. Was auch immer dein Interesse, deine Leidenschaft oder dein Handwerk ist, wenn du diese Technologien nutzt, um deine Kreationen zu beeinflussen, werden sie sich zweifellos verändern und weiterentwickeln. Auf welche Weise, kann ich nicht sagen - das liegt an dir.
Ich glaube, wir alle sind in der Lage, Meisterwerke zu schaffen. Ein Automechaniker kann so gut sein, dass man ihn für einen Künstler hält. Das Gleiche gilt für einen Koch, einen Anwalt oder einen Lehrer - alle diese Berufe können bis zu einem gewissen Grad meisterhaft ausgeübt werden. Finde deine Leidenschaft, folge ihr und schaffe deine Meisterwerke.
Ich glaube, dass wir mit diesen Werkzeugen der Selbstbestimmung als Individuen wachsen können und die Möglichkeit haben, die Welt um uns herum auf tiefgreifende Weise zu beeinflussen.
Ursprungsgeschichten
\ Ein mysteriöser Cypherpunk hat an Halloween 2008 anonym ein White Paper in einem obskuren Kryptografieforum veröffentlicht. Er oder sie bleibt lange genug dabei, um das revolutionärste Geldsystem der Welt in seinen Kinderschuhen zu halten, und verschwindet dann wieder. Es wird viel darüber diskutiert, ob Satoshi eine Person oder viele ist, männlich oder weiblich, lebendig oder tot. Alles ist von Geheimnissen umhüllt.
Auch die Ursprünge der Psychedelika sind umstritten. Terence McKenna verbreitete die „Stoned-Ape-Theorie", nach der sich gedankenlose Affen durch den Konsum von psychedelischen Pilzen auf dem afrikanischen Kontinent zu Menschen entwickelten. Ob das stimmt oder nicht, die Ursprünge dieser Beziehung gehen zweifellos auf eine Zeit vor der aufgezeichneten Geschichte zurück.
Noch mysteriöser ist die Entstehungsgeschichte von LSD. Die berühmte „Bicycle Day"-Geschichte ist höchstwahrscheinlich eine Erfindung. Eine gründliche Untersuchung der Behauptungen in dieser Geschichte führt zwangsläufig zu dem Schluss, dass die Dinge unmöglich zusammenpassen. Wir sollen glauben, dass eine Kaskade von „Unfällen" zu der unerwarteten Entdeckung der stärksten Substanz geführt hat, die der Menschheit bekannt ist.
Vertraue nicht, überprüfe. Ohne dich zu weit in dieses Kaninchenloch zu führen, stelle ich dir diese Präsentation des LSD-Chemikers Dave Nichols von der Mind States-Konferenz 2004 zur Verfügung, und du kannst hier anfangen zu deine eigenen Nachforschungen azustellen (DYOR). Dr. Nichols ist in seinen Schlussfolgerungen weitaus freundlicher als ich, und ich habe einen separaten Artikel, in dem ich die wahre Geschichte hinter dem Bicycle Day noch viel ausführlicher darstelle. Die Ursprünge von LSD und Bitcoin sind auf ähnliche Weise von Geheimnissen und Legenden umwoben.
Es gibt drei unterschiedliche Versionen in der Entstehungsgeschichte von Bitcoin und LSD:
- Was tatsächlich geschah
- Was uns erzählt wird
- Vollständige Erfindungen und Fehlinformationen über das, was passiert ist
Wie auch immer sie ursprünglich entstanden sind, die unumstößliche Tatsache ihrer Existenz zwingt uns heute dazu, uns damit auseinanderzusetzen, was diese Technologien für jeden Einzelnen von uns und für das weltweite Kollektiv bedeuten.
Der Schöpfer und die Geheimdienste
\ Auch wenn sie umstritten sind, gibt es angebliche Verbindungen zwischen Satoshi Nakamoto und Albert Hoffman, den Schöpfern von Bitcoin und LSD, und Geheimdiensten mit drei Buchstaben wie der CIA und der NSA. Bei Satoshi gibt es sowohl Behauptungen, dass er wegen der CIA in die Bitcoin-Gemeinschaft kam, als auch, dass er sie verließ. Bekanntlich verschwand er ein für alle Mal, als der Bitcoin-Entwickler Gavin Andreson beschloss, sich mit der CIA zu treffen, um sie über Bitcoin aufzuklären. Die NSA hat den SHA-256-Algorithmus entwickelt, der in Bitcoin verwendet wird, was zu weiteren Satoshi-Verschwörungstheorien führt.
Es gibt auch Behauptungen, dass Albert Hofmann, der Erfinder von LSD, ein Mitarbeiter der CIA war oder wurde und mit dem St. Anthony Brand in Port Saint Esprit, Frankreich, im Jahr 1951 in Verbindung gebracht wurde. Es gibt noch viele weitere Behauptungen über Verbindungen der Geheimdienste zu den Erfindern von LSD und Bitcoin, die mehr oder weniger glaubwürdig sind. Diese Behauptungen sind zwar unterhaltsam, können aber in den meisten Fällen weder bewiesen noch widerlegt werden, so dass uns eine rationale Untersuchung nur bedingt weiterbringt.
Die frühe Revolution durch Computer
\ Eine unbestreitbare Verbindung zieht sich durch die einzelnen Revolutionen des Computers, der Psychedelika, der Kryptografie und des Bitcoin. Sie alle sind in einem komplexen Geflecht der Selbstverwirklichung miteinander verbunden. Es ist erstaunlich, dass die frühe Computer-, die öffentliche Kryptografie- und die psychedelische Revolution alle auf denselben Ort und dieselbe Zeit zurückgehen.
Die Zeit von Anfang der 1950er Jahre bis 1965 wurde in der San Francisco Bay Area in Kalifornien zu einem Sammelbecken für selbstgebaute Computer, Mathematiker und LSD. In der Zeit von 1966 bis 1976 wurden sowohl LSD als auch der Personal Computer zu Werkzeugen der Revolution und des persönlichen Wachstums. Um den Verbindungen zwischen LSD und Bitcoin auf die Spur zu kommen, müssen wir in diese Zeit zurückgehen und die Fäden zurückverfolgen, die einen Wandteppich der Transformation durch diese beiden Gemeinschaften webten und sie für immer verbanden.
Da LSD in Kalifornien erst 1966 verboten wurde, gab es einen Zeitraum von über einem Jahrzehnt, in dem Informatik und psychedelische Wissenschaft in akademischen Kreisen nebeneinander existierten.
Zwischen 1950 und Mitte der 1960er Jahre wurden mehr als tausend klinische Abhandlungen, mehrere Dutzend Bücher und sechs internationale Konferenzen über die Therapie mit psychedelischen Drogen veröffentlicht. Diese Geschichte aus dieser Zeit verbindet das frühe Informatikpublikum mit dem frühen Gebrauch von LSD in der Bay Area:
„Von 1961 bis 1965 führte die in der Bay Area ansässige International Foundation for Advanced Study mehr als 350 Menschen zu Forschungszwecken auf LSD-Trips. Einige von ihnen waren wichtige Pioniere in der Entwicklung der Computertechnik, wie z.B. Doug Engelbart, der Vater der Computermaus."
LSD wurde in vielen führenden Computerfirmen der 1950er und 60er Jahre eingesetzt, vom Systemdesign bis hin zum Entwurf von Computerschaltkreisen:
„Einige der frühen Computeringenieure verließen sich beim Entwurf von Schaltkreisen auf LSD, vor allem in den Jahren, bevor sie auf Computern entworfen werden konnten, denn „man musste in der Lage sein, sich eine schwindelerregende Komplexität in drei Dimensionen vorzustellen und alles im Kopf zu behalten. Und sie fanden heraus, dass LSD dabei helfen konnte."
Timothy Leary, Harvard-Professor und bekannter Psychedeliker, wurde zu einem ausgesprochenen Befürworter der Macht des Computers als Werkzeug für persönliches Wachstum. Er sah den PC als eine Technologie an, die den Geist auf ähnliche Weise öffnen kann wie das LSD.
„Der PC ist das LSD der 1990er Jahre". -Timothy Leary

LSD war im Silicon Valley der 1960er Jahre allgegenwärtig. Informatiker, Programmierer und Designer aller großen Unternehmen waren daran beteiligt. Diese Geschichte aus dem Wired Magazine geht auf die Verbindungen zwischen Psychedelika, dem Internet und den Grateful Dead ein. Auch wenn diese Geschichte 25 Jahre vor der Geburt von Bitcoin spielt, klingt der folgende Absatz sehr nach Bitcoin:
„Ein Teil der Magie dieser Transaktion besteht darin, dass es gelungen ist, nützliche Inhalte über Jahrzehnte hinweg über das Netzwerk zu teilen. Aber eine andere, noch erstaunlichere Tatsache ist die Widerstandsfähigkeit der Daten, die von Maschine zu Maschine mit einer Art Lebenskraft weitergegeben wurden. Irgendetwas in ihnen machte sie selbstreplizierend und lebendig, etwas, das darum bettelte, kopiert und geteilt, angehört und gesungen zu werden."
Wir können sehen, dass die Anfänge der Computer- und der psychedelischen Revolutionen beide auf diesen konzentrierten Knotenpunkt von Ort und Zeit zurückgehen. Diese Flüsse scheinen in dieselben Meere zu fließen und denselben Quellen zu entspringen. Es gibt Überschneidungen zwischen den scheinbar getrennten Subkulturen, die sich in den frühen Computer- und Psychedelik-Gemeinschaften gebildet haben. Viele Denker, Autoren, Wissenschaftler und Forscher der damaligen Zeit kamen durch soziale Umstände oder durch ihre Berufe in engen Kontakt.
Der Weg von der Entwicklung von Kontrollinstrumenten für Unternehmen hin zur Entwicklung von Instrumenten für Menschen, die sich der Kontrolle widersetzen, hat sich über Jahrzehnte vollzogen.
\ Wir alle sind Nutznießer der Arbeit psychedelischer Informatikerinnen und Informatiker aus einer nicht allzu fernen Vergangenheit.
Wir haben diese klare Verbindung zwischen der psychedelischen und der Computer-Revolution gesehen und können nun auch die öffentliche Kryptografie-Revolution direkt mit beiden in Verbindung bringen. Die Kryptografie war ein streng gehütetes Geheimnis der staatlichen Geheimdienste, bis Whitfield Diffie und Martin Hellman das geheime Wissen aus der Versenkung holten und es dem Normalbürger zugänglich machten.
Diese Frechheit blieb nicht ohne Folgen. Die Regierung versuchte, die Verschlüsselung zu verbieten, indem sie sie als Kriegsmunition einstufte und das Schreiben und Veröffentlichen von kryptografischem Code illegal machte. Die Verwendung von Kryptografie wäre das Gleiche wie ein Waffenhändler zu sein. Dies führte zu den Verschlüsselungskriegen in den 1980er und 1990er Jahren.
Auch hier befinden wir uns wieder in dieser punktgenauen Verknüpfung von Zeit und Ort. Der Held unserer Geschichte tritt in die Schlacht ein und verändert den Lauf der Menschheitsgeschichte für immer. 1965, nachdem er das MIT verlassen hatte, bekam Whit Diffie dank seiner Kenntnisse über Psychedelika einen Job und reiste 1969 (du hast es erraten) in die San Francisco Bay Area.
1975 veröffentlichte er seine Arbeit zur Public-Private-Key-Kryptografie, die die Grundlage für das gesamte Bitcoin-System bildet.
\ John Markoff beschreibt diese psychedelische Verbindung in seinem Buch „What the Dormouse Said: How the Sixties Counterculture Shaped the Personal Computer Industry":
"Diffies Bewerbungsgespräch bei der MITRE Corporation fand mit einem angesehenen Mathematiker und Softwareentwickler namens Roland Silver statt, der sein Mentor wurde. Es war ein ungewöhnliches Vorstellungsgespräch, wenn man bedenkt, dass es sich um einen Militärdienstleister handelte. Es fand in Silvers Haus statt, und fast das gesamte Gespräch drehte sich um psychedelische Drogen: wie man sie zubereitet, wo man sie bekommt usw. Diffie hat mit Bravour bestanden."
Diffie war auch ein großer Verfechter der persönlichen Freiheit und Selbstbestimmung. Als er erfuhr, dass die Geheimdienste der Regierung Wissen über kryptografische Mathematik versteckten, wird er mit den Worten zitiert
"Kryptografie ist für die menschliche Privatsphäre unerlässlich! Vielleicht sollten leidenschaftliche Forscher/innen im öffentlichen Sektor versuchen, das Thema zu befreien. Wenn wir uns anstrengen, könnten wir eine Menge von diesem Material wiederentdecken."- Whitfield Diffie

Nachdem Whitfield und Hellmann ihre bahnbrechende Arbeit über die Kryptografie mit öffentlich-privaten Schlüsseln veröffentlicht hatten, fragte ein anderer Forscher aus der Bay Area an, ob sie an einer Zusammenarbeit interessiert seien. Es handelte sich um Ralph Merkle, den Erfinder einer weiteren wichtigen Technologie, die Bitcoin zugrunde liegt: des Merkle-Baums.
Während eines sehr kurzen Moments in der Geschichte leuchtet dieses sehr kleine geografische Gebiet wie ein magisches Ei, das Technologien des Wandels und der Hoffnung hervorgebracht hat.
\ Die tief verwobenen Verbindungen zwischen der Entstehung der Revolutionen der Psychedelika, des Personal Computing und der Kryptografie sind wirklich bemerkenswert. Diese drei Wissenschaften konvergieren in den nächsten Jahrzehnten in Ausdrucksformen der Selbstsouveränität durch digitale Privatsphäre, digitales Geld und digitale Philosophie, die durch „Cypherpunks, die Code schreiben" verwirklicht werden.
Bevor wir uns den historischen Verbindungen zuwenden, wäre ich nachlässig, wenn ich nicht Ross Ulbricht und Silk Road erwähnen würde. Einer der sichtbarsten Aspekte der frühen Bitcoin-Geschichte war die Beziehung zwischen Online-Peer-to-Peer-Marktplätzen, Bitcoin und Psychedelika. Im Jahr 2011 wurde die Welt mit einer neuen Art von „Drogenmarkt" konfrontiert. Dieser neue Online-Marktplatz bot sowohl den Käufern als auch den Verkäufern einzigartige Vorteile.
Viele wissen es nicht, aber Ross baute seine eigenen psychedelischen Pilze an, die das allererste Produkt auf der Silk Road-Website sein sollten. Bevor es etwas anderes gab, gab es Bitcoin und Psilocybe cubensis. Abgesehen von Lazlo's Pizza sind psychedelische Pilze also wohl einer der ersten aufgezeichneten Peer-to-Peer-Tauschgeschäfte von Bitcoin gegen Waren/Dienstleistungen. Auch wenn es einige Papierhandtücher, Tassen und andere banale und vergessene Gegenstände gibt, ist die Verbindung zwischen der Online/P2P/Psychedelic/Cypherpunk-Community unbestreitbar.
Interessanterweise war der erste Ort, an dem Ross für die Silk Road warb, das psychedelische Pilz-Online-Forum The Shroomery, unter dem Benutzernamen "altoid". Du kannst seinen einzigen Beitrag hier nachlesen.
Die Ebene der Umsetzung
\ Die nächste Ebene, auf der man nach interessanten Parallelen suchen kann, ist die einfachste Ebene der Grundlagen der einzelnen Implementierungen. Bitcoin ist ein Protokoll, ein Satz von Regeln, Anweisungen und Parametern, und es gibt verschiedene Implementierungen von Bitcoin, die mit dem Protokoll kompatibel sind. Die Implementierungen sind die Software, die du ausführst und die es dir ermöglicht, mit dem Netzwerk zu interagieren. Obwohl es eine Standard-„Referenzimplementierung" von Bitcoin gibt, haben die Nutzer die völlige Freiheit, verschiedene Programmiersprachen, Funktionen und Architekturen zu verwenden, um mit demselben Bitcoin-Netzwerk zu interagieren wie alle anderen.
Die meisten Bitcoin-Nutzer schätzen zwar die Möglichkeit, dies zu tun, aber werden wir werden eigene Bitcoin-Implementierung nicht von Grund auf programmieren. Wir werden aus den vielen verfügbaren Implementierungen wählen und entscheiden, ob wir Open-Source- oder Closed-Source-Code verwenden.
Dieses Thema ist zu umfangreich für diesen Artikel, aber ich bin der festen Überzeugung, dass man Bitcoin niemals mit Closed-Source-Code verwenden sollte. Wenn du dich für Open-Source-Code entscheidest, kannst du die Software anhand ihres Quellcodes sowohl überprüfen als auch kompilieren.
Hier gibt es eine Menge Nuancen. Auf dieser Ebene können die „Werkzeuge" von Bitcoin so austauschbar sein wie das Auto, das du fährst, und der Endnutzer hat fast die gleiche Auswahl. Diese Wahl ist wichtig und sollte gut überlegt sein. Das Auto, das du fährst, ist vielleicht an den meisten Tagen unbedeutend, aber eines Tages könnte es aufgrund bestimmter Eigenschaften deine Familie retten.
Wichtig ist, dass unabhängig von der Implementierung, für die sich ein Nutzer entscheidet, die Möglichkeit, seinen eigenen Knotenpunkt zu betreiben, der demokratisierende und wohl auch wichtigste Faktor ist. Jeder sollte in der Lage sein, seinen eigenen Knotenpunkt zu betreiben und dabei Zwischenhändler und Unsicherheiten auszuschalten.
Ein Bitcoin-Knoten ist eine Quelle der Wahrheit - eine vollständige Geschichte von der Gegenwart bis zurück zur Genesis. Indem du deinen eigenen Knotenpunkt betreibst, erhältst du deine eigene direkte Quelle der Wahrheit, die nicht von Banken, Politikern oder Priestern vermittelt wird. Für Bitcoin bedeutet dies, dass die Nutzer mit Sicherheit wissen können, dass ihre eigenen Transaktionen gültig und echt sind - ohne einen Goldbarren einschmelzen zu müssen, um das zu überprüfen, was teure Ausrüstung und Zeit kostet. Wenn der Bitcoin in meiner Wallet ankommt, weiß ich, dass er zu 100% echt ist. Er ist nicht gefälscht und nicht entwertet. Es ist reiner, unverfälschter Bitcoin.
Bei psychedelischen Drogen kannst du sie selbst anbauen, synthetisieren und/oder extrahieren, ohne dass du Zwischenhändler brauchst oder dir Sorgen über Reinheit, Gewicht oder falsche Identifizierung machen musst.
Psychedelika ermöglichen es dir, wie Sama Katharo es formulierte: „dich mit deinem eigenen inneren Knotenpunkt zu verbinden". Die Software der komplexesten und am dichtesten verzweigten Verarbeitungsmaschine, die der Mensch kennt: dein Gehirn. Du kannst sie nutzen, um deine eigene Quelle der inneren Wahrheit zu destillieren. Du kannst die riesigen Gedankenwelten in deinem Kopf erforschen, ohne dass sich ein Psychiater oder eine andere „vertrauenswürdige dritte Partei" einmischen oder ihren Bezugsrahmen auf dich projizieren muss. Psychedelika geben dir die Schlüssel zu deinem eigenen inneren Palast.
Psychedelika gibt es, genau wie Bitcoin, in vielen verschiedenen Varianten, z. B. LSD, MDMA, Psilocybin, DMT, Meskalin oder Cannabis. Es gab auch einen Boom von experimentellen psychedelischen „Forschungschemikalien", die sich über die Darknet-Märkte (und damit auch über Bitcoin) verbreitet haben. Und obwohl der Betrieb eines großen psychedelischen Labors außerhalb der Möglichkeiten und Wünsche der meisten Menschen liegt, können fast alle Erwachsenen die Kontrolle über ihren psychedelischen Weg übernehmen und ihre eigenen Pilze, Kakteen und Cannabis anbauen. Dies kann in verschiedenen Ländern unterschiedliche rechtliche Konsequenzen haben, und jeder Nutzer muss entsprechend entscheiden.
Der Weg zum eigenen Anbau von psychedelischen Drogen ist eine heroische Suche nach Selbsterkenntnis, Vorbereitung, Wachstum und Geduld. Sich die Zeit zu nehmen, um die richtigen Materialien zu verstehen, zu kultivieren, zu pflegen und hervorzubringen, hat unermessliche Vorteile. Diese Vorbereitung und Kontemplation gibt dem Suchenden die Kontrolle darüber, was in unserem Körper passiert.
Auf dem Weg des Bitcoiners, der versucht, seine Zukunft in der Schuldenspirale zu kontrollieren, die sich um uns herum abspielt, gibt es eine ähnliche Heldentat.
Learning by Doing
\ Sowohl bei Bitcoin als auch bei Psychedelika ist es wichtig, dass du sie tatsächlich BENUTZEN kannst, bevor du sie richtig verstehen kannst. Du kannst ein Buch darüber lesen, wie sie funktionieren, was sie bewirken und wie man sie richtig einsetzt, aber dein Verständnis ist unvollständig, solange du sie nicht persönlich erlebt hast. Keine noch so gute Vorbereitung oder Lektüre kann dich auf den weltbewegenden Wirbelsturm vorbereiten, der das Herzstück der psychedelischen Erfahrung ist. Keine noch so gute Lektüre kann dich auf das Gefühl vorbereiten, das du bekommst, wenn du Bitcoin verschickst - eine kostspielige und unumkehrbare Aktion.
Je mehr du sie benutzt, desto besser wirst du mit ihnen vertraut. Je vertrauter du wirst, desto tiefer kannst du in die Erfahrung eintauchen. Das ist Weisheit, die aus Erfahrung entsteht, nicht Wissen, das man durch Lesen erlangt.
"Ein tiefes Verständnis von Bitcoin zu erlangen, ist wie ein tiefer psychedelischer Trip. Denn alles scheint sich um dieses Ideal herum auf unerwartete und ziemlich radikale Weise zu verändern, weil du die Dinge jetzt auf eine ganz andere Art und Weise siehst, als du sie ursprünglich zu sehen glaubtest." - Eric Cason
Endgültigkeit
\ Sowohl bei Psychedelika als auch bei Bitcoin gibt es einen Punkt an dem es keine Rückkehr mehr gibt. Wenn du eine Bitcoin-Transaktion abschickst, kannst du sie nicht mehr zurücknehmen. Sobald du auf „Senden" klickst und das Netzwerk die Transaktion bestätigt, kann keine deiner Handlungen mehr verhindern, dass der Bitcoin sich einmal bewegt. Wenn du dir einen Schuss LSD auf die Zunge legst oder ein paar Gramm Pilze isst, bist du für die nächsten Stunden an diese Erfahrung gebunden. Es gibt kein STRG+Z, keine Wiederholung oder Rückerstattung. Es gibt keinen Ausweg außer dem Durchgang.
Es gibt eine Schwelle, nach deren Überschreiten nichts mehr so ist, wie es einmal war. Diese Endgültigkeit gibt dem Benutzer eine Pause, um seine Handlungen zu überdenken. Ein Fehler oder Fehltritt hat hier unmittelbare Konsequenzen, daher ist es klug und umsichtig, vorsichtig vorzugehen. Es ist von größter Bedeutung, dass du deine Entscheidungen bei der Nutzung dieser Technologien sorgfältig triffst. Mit der Übung kommt die Vertrautheit. Und mit der Vertrautheit kommt das Vertrauen. Diese Technologien fördern bewusstes Handeln und führen zu Überzeugung, wenn sie mit Sorgfalt und Respekt eingesetzt werden.
Die Erlebnisse
\ Die Erfahrungen mit Psychedelika und Bitcoin bringen uns zu denselben grundlegenden Fragen über das Menschsein und die Interaktion mit dem Universum um uns herum.
- Was ist Zeit?
- Was ist Geld?
- Was ist real?
- Was ist Sprache?
- Was ist Arbeit?
- Was ist Energie?
- Ist der Einsatz von Energie gut oder schlecht?
- Wo gehöre ich zu meinen Mitmenschen?
Warum bringen uns diese beiden unterschiedlichen Technologien zu denselben grundlegenden Fragen über die Realität und das Menschsein? Warum inspirieren sie uns dazu, die großen Fragen zu stellen?
Das Konzept der Zeit ist auf mehreren Ebenen tief mit Bitcoin und Psychedelika verwoben. Bitcoin hat die Zeitmessung neu definiert, und die Folgen davon müssen erst noch verstanden werden. Die menschliche Erfahrung von Zeit ist variabel. Wir interpretieren die Zeit durch eine Linse anderer Wahrnehmungen (wenn du Spaß hast, scheint die Zeit schnell zu vergehen, während es dir, wenn du verzweifelt auf etwas wartest, vorkommen kann, als sei jede Sekunde eine Ewigkeit).
Dies wird durch Psychedelika noch verstärkt, da das Konzept der Zeit dehnbar und amorph wird und Neuartigkeit und Zufälligkeit mit der alltäglichen Erfahrung der Zeit wie ein Spiegelbild spielen. Vergleiche dies mit den Blockzeiten von Bitcoin. Blocks sollen alle 10 Minuten kommen, aber manchmal sind sie schneller, manchmal langsamer. Wie die Wellen im Ozean bewegt sich jeder Tick der Bitcoin-Uhr in seinem eigenen Rhythmus, ist aber endlos, wie die Zeit selbst.
Sowohl Bitcoin als auch Psychedelika haben ihren eigenen inneren Zeitrhythmus, der durch den Rhythmus der Uhr nicht beeinflusst oder verändert wird.
Integration: Unerfahrener vs. erfahrener Gebrauch
\ Bei Bitcoin und Psychedelika gibt es ein Spektrum an Vertrautheit, das direkt mit der Zeit und der Arbeit korreliert, die der Nutzer in das Erlernen und die Nutzung der Technologien investiert. Dieses Spektrum reicht von unerfahrenen bis hin zu erfahrenen Nutzern. Die Vorteile beider Technologien können am besten von erfahrenen Nutzern genutzt werden. Menschen, die in der Lage sind, die Erkenntnisse aus ihren Erfahrungen zu nutzen und sie erfolgreich auf ihr Leben anzuwenden, profitieren am meisten.
Diese Fähigkeit, Erkenntnisse zu erkennen, zu nutzen und in die Tat umzusetzen, würde ich als fortgeschrittene Nutzung von Psychedelika bezeichnen. Viele Menschen, die Psychedelika einnehmen, gelangen zu tiefgreifenden Einsichten, die eine große persönliche Bedeutung haben. Wenn die Wirkung nachlässt, setzen unerfahrene Nutzer diese Erkenntnisse jedoch nicht in die Tat um.
Vorteile, Entdeckungen und Erfindungen können sich in einem Funken der Inspiration manifestieren, nur um wenige Augenblicke später wieder vergessen und für immer verloren zu sein. Manche Nutzer erleben nach einer psychedelischen Erfahrung Veränderungen, aber die sind nur von kurzer Dauer. Sie gewinnen Einsichten und nehmen Veränderungen vor, aber wie viele Neujahrsvorsätze verschwinden diese schnell in der Entropie. Die Veränderungen halten ein paar Wochen, vielleicht einen Monat an, aber schon bald fallen die Nutzer wieder in die Routine des Alltags zurück und schlechte Gewohnheiten, die erkannt und angegangen wurden, kehren zurück.
Die Rückkehr des Alltäglichen und das Aufzwingen der Welt auf unsere Gewohnheiten kann eine mächtige Kraft sein. Psychedelische Drogen und die Erkenntnisse aus den ersten Prinzipien des Bitcoin-Denkens können mächtig sein, müssen aber verstärkt werden. Diese Verstärkung kann in Form von direktem Handeln, tiefem Studium oder Willenskraft erfolgen, aber ich glaube, dass es auch wichtig ist, zur Quelle der Erfahrung zurückzukehren.
Für Bitcoin bedeutet das, Podcasts zu hören, zu lernen, zu programmieren, zu bauen und zu teilen. Bei psychedelischen Drogen bedeutet das, dass du die psychedelische Erfahrung in regelmäßigen Abständen wiederholen musst. Es gibt kein Patentrezept. Du würdest nicht erwarten, dass eine einzige Dosis Aspirin ein Leben lang Schmerzen lindert, und mit Psychedelika ist es genauso. Sie wirken eine Zeit lang, sollten aber nur bei Bedarf verabreicht werden.
Es ist von größter Bedeutung, die während einer psychedelischen Erfahrung gelernten Lektionen oder gewonnenen Erkenntnisse richtig zu verarbeiten. Wenn du während der Erfahrung etwas Wertvolles bekommst, behandle es wie jeden anderen Gegenstand von großem Wert. Du wirst nicht bei jedem Erlebnis Einsichten oder Lebenslektionen erhalten, und das ist in Ordnung. Aber es ist gut, darauf vorbereitet zu sein, wenn sie auftauchen, damit du ihren Wert für dein Leben maximieren kannst.
Selbstvertrauen aufbauen
\ Sowohl Bitcoin als auch Psychedelika können ein tiefes inneres Vertrauen aufbauen. Psychedelische Drogen können sehr herausfordernd sein. Die psychedelische Erfahrung kann in gewisser Weise mit einer Initiation verglichen werden. Manche Menschen erleben auf Psychedelika eine Tod-Wiedergeburt-Erfahrung, und es gibt keine lebensbejahendere Erfahrung als die eines Nahtods.
Psychedelika können auch sehr beängstigend sein, wenn sie ohne die nötige Vorsicht und den nötigen Respekt eingesetzt werden. Aber selbst die furchterregendsten Erfahrungen bringen uns nicht um, und das gibt uns ein Gefühl der Ermächtigung. Auch ohne das Drama des Egotods oder eine beängstigende psychedelische Erfahrung würden viele Menschen einen Teil ihrer psychedelischen Erfahrung als „herausfordernd" bezeichnen. Diese tiefgreifenden inneren Herausforderungen zu durchlaufen, kann das Selbstvertrauen enorm stärken.
Die psychedelische Erfahrung ist auch eine moderne Analogie zu einer inneren „Heldensuche". Sie wird nicht auf die leichte Schulter genommen und ist ein Weg mit großen persönlichen Herausforderungen und Dramen. Die Suche kann zu einer direkten göttlichen, mystischen Erfahrung führen, zu einem Schatz, bevor der Held nach Hause zurückkehrt.
Bitcoin schafft auch ein Vertrauen, das man nur durch Erfahrung gewinnen kann. Diejenigen, die sich seit mehr als einem Jahr mit Bitcoin beschäftigen, sind auf zahlreiche Medienartikel gestoßen, die laut und stolz verkündeten: „Bitcoin ist tot!" Mehr als 450 dieser Artikel wurden in den letzten zehn Jahren veröffentlicht, doch Bitcoin stirbt nie. Er ist einer nicht enden wollenden Flut von technologischen, politischen und ideologischen Angriffen ausgesetzt, aber im Durchschnitt wird alle 10 Minuten ein neuer Bitcoin-Block im Netzwerk erzeugt. Die Uhr tickt weiter. Diese Widerstandsfähigkeit schafft Vertrauen bei den Bitcoinern, und dieses Vertrauen wächst und vertieft sich mit der Zeit.
Auswirkungen auf langfristiges Denken und Planen
\ Das Konzept der „Zeitpräferenz", das von Saifedean Ammous populär gemacht wurde, basiert auf den Entscheidungen, die wir alle treffen, und ihrem Verhältnis zur Zeit. Willst du einen Bitcoin heute oder zehn im nächsten Jahr?
Es gibt zwei Arten von Zeitpräferenzen: hohe und niedrige. Das Denken mit hoher Zeitpräferenz optimiert für die unmittelbare Zukunft (heute, morgen), während das Denken mit niedriger Zeitpräferenz für die lange Zukunft (Jahre, Jahrzehnte, Generationen) optimiert. Das Denken in niedrigen Zeitpräferenzen ist ein Luxus, den sich diejenigen leisten, die ihre unmittelbare Zukunft gesichert haben. Man kann nicht für die Zukunft planen, wenn man nicht weiß, woher die nächste Mahlzeit kommt oder wo man die Nacht verbringen wird.
Zum Denken mit geringen Zeitpräferenzen gehört das Sparen für die Zukunft und die Sicherung des persönlichen Wohlstands durch große persönliche Verantwortung und Bildung. Diejenigen, die in Bitcoin sparen und sie langfristig halten, stellen fest, dass ihr Vermögen um Größenordnungen zunimmt. Niemand hat jemals Bitcoin gekauft, sie vier Jahre lang gehalten und dann Geld verloren. Niemals. Das passiert einfach nicht. Wenn du sie kurzfristig kaufst, kann alles Mögliche passieren, und höchstwahrscheinlich wirst du dein Geld verlieren. Kaufe, halte, sammle und gib sparsam aus.
Diese Lehren aus dem Bitcoin beginnen das Leben der Nutzer zu durchdringen, und schon bald wird diese Art des Denkens auf alle Aspekte des Lebens angewendet. Die Nutzer bilden sich in verwandten Disziplinen weiter, treiben Sport und ernähren sich gesünder, weil sie nun optimistischer in die Zukunft blicken.
Eine düstere Zukunft, die einst voller Ungewissheit war, wird durch persönliches Handeln in eine Vision der Hoffnung verwandelt, und das ist unbeschreiblich ermutigend.
Es kommt niemand, um dich zu retten. Du musst der Held auf dieser Reise sein.
Psychedelika wirken sich sowohl auf das Denken in niedrigen als auch in hohen Phasen aus und sind für jeden Menschen zutiefst individuell. Ich finde, dass Psychedelika als persönliches Barometer genutzt werden können - ein Werkzeug, um den Verlauf meiner Zukunft vorherzusagen. Indem wir die Vergangenheit nutzen, um aus einzigartigen und unverwirklichten Perspektiven in die Zukunft zu blicken, können wir dieses Werkzeug nutzen, um Pläne für persönliches Wachstum zu entwerfen. Indem ich mich außerhalb meiner alltäglichen Erfahrungen bewege, kann ich mich aus einem ganz neuen Blickwinkel betrachten.
Viele von uns können schnell die Fehler anderer sehen, aber nicht die eigenen? Psychedelika ermöglichen uns einen Perspektivwechsel, der es uns erlaubt, uns selbst und unser Leben aus einem neuen Blickwinkel zu betrachten, in dem wir Fehler, die wir ignoriert, übersehen oder unterdrückt haben, leicht und klar erkennen können.
Ich kann das Ziel und den Weg dorthin sehen. Ich kann sehen, was für mich richtig ist, und ich kann auch andere Wege sehen, die ich einschlagen könnte und wo sie mich in die Irre führen könnten. Die wahre Kraft der Psychedelika besteht darin, diese Einsichten zu erkennen und konsequent danach zu handeln. Viele Menschen nehmen Psychedelika und haben eine großartige Vision, stecken dann aber zwei Wochen später in denselben persönlichen und emotionalen Furchen fest, in denen sie vor der Erfahrung steckten. Das liegt daran, dass es fast keine guten Informationen über die richtige Integration psychedelischer Erfahrungen gibt. Deine beste Lehrerin oder dein bester Lehrer ist es, die Arbeit zu machen, aufmerksam zu sein, sich entsprechend anzupassen und die Ergebnisse zu beobachten. Tatsache ist, dass viele Menschen durch den Konsum von Bitcoin und/oder Psychedelika langfristige positive Veränderungen in ihrem Leben bewirken.
Die Wirkung von Psychedelika findet nicht nur im Kopf statt. Die Wissenschaft hat gezeigt, dass diese Moleküle die Struktur unseres Gehirns physisch verändern. Dieses Bild zeigt, wie Psychedelika das Wachstum von Gehirnzellen fördern und neue Nervenbahnen im Gehirn bilden können. Du denkst anders, weil du anders bist.
Altcoins, Forschungschemikalien und Schadensminimierung
\ Sowohl bei Bitcoin als auch bei Psychedelika gibt es räuberische „Hochstapler" und Affinitätsbetrüger, die auftauchen, um die Gemeinschaft auszunutzen. In beiden Kulturen gibt es eine unehrliche Bevölkerung, die von der Förderung dieser Betrügereien profitiert, und eine ehrliche Bevölkerung, die als Immunsystem fungiert, um diese Gifte zu identifizieren, zu entlarven und zu vertreiben. Bei Bitcoin gibt es eine aktive Kultur, die den Affinitätsbetrug schnell, laut und nachdrücklich aufdeckt. In der Psychedelik gibt es eine ähnliche Kultur, die „Schadensminimierung" genannt wird und in der lautstarke Mitglieder die größere Gemeinschaft vor den Angriffen der schlechten Akteure schützen.
Es gibt eine ganze Galaxie von „Altcoins", die behaupten, dass sie aus dem einen oder anderen Grund besser sind als Bitcoin. Einige der Altcoin-Projekte mögen legitime Experimente mit digitalen Vermögenswerten sein, aber die große Mehrheit sind gefährliche Betrüger, die versuchen, dein Geld durch falsche Versprechungen und technisches Geschwätz zu stehlen.
Diese Altcoins nehmen viele Formen an: Defi, Proof-of-Stake, algorithmische Stablecoins, NFTs und viele andere Worthülsen, die bei näherer Betrachtung nicht das sind, wofür sie werben. Viele dieser Projekte und Altcoins behaupten, sie seien „dezentralisiert", während sie in Wirklichkeit direkte zentralisierende Faktoren verbergen, die den gesamten Sinn des Projekts zunichte machen. In Bitcoin haben wir einen umgangssprachlichen Ausdruck für diese Nicht-Bitcoin-Krypto-Vermögenswerte: Shitcoins.
"Es gibt Bitcoin und es gibt Shitcoin."- Kongressabgeordneter Warren Davidson

\ Eine ganze Galaxie von psychedelischen Molekülen aus dem Frankenstein'schen Zeitalter findet ihren Weg aus skizzenhaften Laboren in Übersee auf die globalen psychedelischen Märkte. Dinge wie 2C-I, DOB, aMT, 25i-NBOMe, Bromo-Dragonfly und JWH-018 sind nur einige der chemischen Substanzen, die derzeit auf dem Weltmarkt erhältlich sind.
Weil diese Chemikalien so selten sind, gibt es nur sehr wenige Daten über ihr Sicherheitsprofil. Skrupellose Dealer kaufen diese billigen Imitate und verkaufen sie als LSD, MDMA oder Meskalin an ahnungslose Kunden. 25i-NBOME wird oft fälschlicherweise als LSD verkauft, aber diese Substanz ist hochgiftig und hat schon mehrere Konsumenten getötet, im Gegensatz zu LSD, das noch nie jemanden getötet hat.
Ich habe ein paar Blotter zur Schadensminimierung erstellt, um diese betrügerische Technik zu bekämpfen. Dies ist ein Beispiel dafür, dass der Aktivismus zur Schadensbegrenzung Parallelen zum „toxischen Bitcoin-Maximalismus" aufweist.
Obwohl es in beiden Gemeinschaften überall Betrüger gibt, ist nicht jeder, der sich mit Altcoins oder Forschungschemikalien beschäftigt, unehrlich oder darauf aus, dir zu schaden. Viele erforschen ernsthaft die Vorzüge und Fallstricke dieser unbekannten Wege, und ich habe nichts dagegen, dass sie das tun. Diese Menschen sind nicht gefährlich für die Gemeinschaft, sondern meist nur für sich selbst.
Auch wenn ich glaube, dass sie fehlgeleitet sind, schaden ihre ehrlichen Erkundungen niemandem. Manche Menschen investieren einen großen Teil ihres Lebens in die Erkundung dieser Pfade und finden vielleicht nie den Weg hinaus. Ich denke jedoch, dass dies für die meisten ein Übergangsstadium ist, in dem sie die Konsequenzen ihres falschen Denkens erfahren und sich selbst korrigieren.
Wenn die Selbsterkundung zur Anpreisung wird, haben wir eine Grenze überschritten. Ich habe etwas dagegen, wenn Menschen falsche Behauptungen aufstellen, die für jeden, der ihnen zuhört, gefährliche Folgen haben, vor allem, wenn sie das nur tun, weil sie davon profitieren.
Sowohl bei Bitcoin als auch bei Psychedelika gibt es ausgetretene Pfade, die zuverlässig und vorhersehbar sind. Andere Wege sind weniger ausgetreten oder sogar unbekannt und bergen neue und einzigartige Gefahren. Die klassischen Psychedelika wie LSD, Pilze, DMT, Meskalin und Cannabis sind gut befahrene, gut dokumentierte und entsprechend gekennzeichnete Wege. Das bedeutet, dass Millionen von Menschen diese Substanzen über Jahrzehnte oder sogar Jahrhunderte hinweg konsumiert haben. Aufgrund ihrer weit verbreiteten, langfristigen Verwendung wissen wir viel über ihre Sicherheit, Wirksamkeit und Dosierung. Diese Psychedelika sind in einer Vielzahl von Umgebungen unglaublich sicher.
Bitcoin ist auch ein weit verbreiteter Weg. Er hat Millionen von Nutzern und ist seit über einem Jahrzehnt in der Praxis erprobt. Bitcoin winkt jeden Tag mit einem Billionen-Dollar-Preis für jeden, der ihn knacken kann, doch niemand hat es je geschafft. Das Gegenteil ist in der Welt der Nicht-Bitcoin-Kryptowährungen der Fall. Fast wöchentlich gibt es einen neuen Defi- oder Smart-Contract-Exploit oder Hack. Der Sommer 2022 hat uns auch gezeigt, wie gefährlich es ist, Dritten zu vertrauen und ein Gegenparteirisiko einzugehen.
Die wichtigste Erkenntnis aus diesem Abschnitt, wenn nicht sogar aus dem ganzen Artikel, ist, dass man sich in der Welt der "Kryptowährungen" auf Bitcoin konzentrieren sollte, wie auf LSD und Psilocybin in der Welt der Psychedelika.\ \ Es gibt viele Ablenkungen und falsche Wege, die dich in die Irre führen. Fallen Sie nicht darauf herein. Sowohl Psychedelika als auch Bitcoin zeigen uns, dass Zeit unser wertvollstes Gut ist. Wenn du den Fokus verlierst, ist es leicht, von der Mission abzuweichen und dich ablenken zu lassen. Wenn du deine Aufmerksamkeit und Energie fokussierst, verbringst du mehr Zeit auf Wegen, die tiefgreifende und messbare Vorteile für dein Leben haben können. Du kannst nicht gewinnen, wenn du nicht spielst. Ablenkungen halten dich komplett vom Spielfeld fern.
Es gibt kein "Wundermittel" gegen falsches Denken
\ Viele Nutzer von Psychedelika glauben, dass sich alles innerhalb eines Nachmittags ändern würde, wenn alle Menschen auf der Welt LSD nehmen würden. Bei Bitcoin gibt es den Spruch „Bitcoin repariert dies", der besagt, dass Bitcoin auf magische Weise fast jedes Problem auf der Welt lösen kann. Meiner Erfahrung nach gibt es leider kein Patentrezept für falsches Denken.
Bitcoin hält die Shitcoinerei nicht auf. Psychedelische Drogen machen dich nicht automatisch zu einem guten Menschen.
Nur weil du dich für Bitcoin interessierst, heißt das nicht, dass du gegen Fiat-Denken oder Shitcoinerei immun bist. Und nur weil du Psychedelika nimmst, heißt das nicht, dass du nicht in einem Labyrinth aus fantastischem Denken landest. Es bedeutet auch nicht, dass du deine psychedelischen Erkenntnisse erfolgreich in dein Leben integrieren wirst.
Als ich mit Bitcoin anfing, hatte ich keine Ahnung von der riesigen Welt der Kryptowährungen. Ich dachte, Bitcoin sei die einzige digitale Währung. Ich fand schnell heraus, dass es über tausend verschiedene „Altcoins" gibt. Ich begann zu recherchieren, aber die verfügbaren Quellen waren nicht zuverlässig. Ich sah immer wieder Altcoin-Promoter, die sagten: „Bitcoin ist eine alte, veraltete Technologie", „Bitcoin ist langsam und teuer" und „dieser neue Coin behebt all das".
Noch wichtiger ist, dass diese Betrüger von dem Wunschtraum leben, dass diese neue Münze das gleiche Wachstum wie Bitcoin erfährt und möglicherweise den Nutzen und den Preis von Bitcoin übertrifft. Oft kosten diese Münzen nur ein paar Cent pro Stück, so dass die Verlockung, ein paar Cent in Zehntausende zu verwandeln, wie ein Sirenengesang auf unsere Gier wirkt.
Ich bin darauf hereingefallen und habe über ein Jahr lang auf die harte (und teure) Tour gelernt, dass ich meine Zeit und mein Geld mit einem Haufen Shitcoins verschwendet habe. Das war eine wertvolle, aber teure Lektion. Ich habe sie mir zu Herzen genommen und konzentriere mich jetzt ausschließlich auf Bitcoin. Das hat mein Leben in vielerlei Hinsicht verändert und dafür bin ich für immer dankbar.
Das spricht dafür, dass einige von uns die Dinge auf die harte Tour lernen müssen. Man kann keine Einsicht gewinnen, ohne die Erfahrung gemacht zu haben, Zeit, Energie und Geld zu verlieren. Für manche sind das die Kosten für das Schulgeld. Ich hoffe, dass du aus meinen Fehlern lernen kannst. Ich kann dir empfehlen, die Twitter-Seite von @CoinFessions zu besuchen, wenn du aus den Fehlern anderer lernen willst. Heute bin ich sehr schnell dabei, meine Zeit und Aufmerksamkeit auf meine spezielle Mission zu konzentrieren und so viele Ablenkungen auszuschließen, wie ich abwehren kann.
Hüte dich vor der „Touristen"-Kultur
\ Bezahlte Krypto-Tradinganalyse-Gruppenleitern und Ayahuasca-Schamanen sollten mit größter Skepsis betrachtet werden. In fast allen Fällen sollte man diese Leute meiden. Das gilt auch für Ayahuasca-Tourismus, psychedelische Exerzitien, medizinisch unterstützte psychedelische Behandlungen und jede Situation, in der du deine Souveränität, deinen Platz und dein Umfeld an andere abgibst.
Ich möchte nicht beobachtet, angeleitet oder angesungen werden oder die Protokolle, Glaubenssätze oder Rituale anderer auf mich projiziert bekommen, während ich mich in einem psychedelischen Zustand befinde. Ich möchte die Kontrolle über meine eigene Erfahrung haben und diese Verantwortung nicht an eine vertrauenswürdige dritte Person abgeben. Das Gleiche gilt für das Vertrauen in einen YouTube-Krypto-Trader, der finanzielle Entscheidungen trifft, die mich und meine Familie betreffen. Das wird nicht passieren.
Wenn du irgendwo im Urlaub bist, wissen wir alle, dass es eine „Touristenversion" und eine „echte Version" der Orte gibt, die wir besuchen. Es gibt den Strand, an den du gereist bist, mit dem herrlichen Sand, der Sonne und dem Himmel, und dann gibt es den Laden, der versucht, dir T-Shirts, Muscheln, Schlüsselanhänger und eine Fahrt im Kleinbus zu verkaufen, um die örtlichen Sehenswürdigkeiten zu sehen.
Geh an den Strand und halte dich von den Touristenläden fern. In jeder Kultur gibt es Elemente, die "wahr und rein" für die Ideologien der Bewegung sind. Es gibt aber auch räuberische Mitläufer, die nach Gelegenheiten suchen, die Unwissenheit der Neuankömmlinge über die Feinheiten auszunutzen.
In der Bitcoin-Kultur gibt es das Konzept des „Orangewashings", mit dem man sich als Bitcoiner ausgibt, aber in Wirklichkeit ist man ein Shitcoiner oder Betrüger, der nur so tut, als ob er so tut, als ob er so tut und so redet. Andere machen sich gar nicht erst die Mühe des Orangenwaschens und verkünden stolz, dass Bitcoin alt, langsam, Boomer-Tech und eindeutig minderwertiger als ihre neueste Version ihres Schlangenöls ist.
In der psychedelischen Kultur gibt es immer mehr Menschen, die dein Geld gerne annehmen, um dir im Gegenzug psychedelische Dienstleistungen, Moleküle und sogar Investmentaktien anzubieten. Manche haben tiefere und dunklere Beweggründe für deinen Geist und Körper. Ich würde dir raten, dich von all diesen Angeboten fernzuhalten oder sie zumindest mit großer Skepsis zu betrachten. Ich sage nicht, dass alle Erscheinungsformen dieser Aspekte der Kulturen von Natur aus schädlich sind, sondern dass man immer die Anreize im Auge behalten muss. Wenn du dich auf einen Rückzugsort, einen „Schamanen", einen psychedelischen Arzt oder eine Fachkraft einlässt, dann recherchiere ausgiebig über die Person/das Unternehmen.
Nimm dir die Zeit, eine authentische Kultur zu suchen. Pflege das Echte und lehne das Gefälschte ab.\ \ Du wirst um ein Vielfaches belohnt werden, und zwar auf unvorhersehbare Weise.
Alchemie
\ Ich möchte auf die Verbindung zum alten alchemistischen Wunsch eingehen, Blei in Gold zu verwandeln. Mit Bitcoin verwandeln wir die Fiat-Strukturen der Welt in einen digitalen, kryptografischen Schatz, der sich überall auf der Welt hin teleportieren kann. Dies geschieht wie ein Zauberspruch, indem man bestimmte Wörter in der richtigen Reihenfolge verwendet. Wenn du den Code ausführst, funktioniert er. Indem wir die richtigen Wörter in der richtigen Reihenfolge verwenden, können wir die Welt wesentlich verändern.
Das sind nicht nur Veränderungen in unseren Köpfen. Es sind Veränderungen, die andere sehen, fühlen und unabhängig überprüfen können. Der richtige Computercode kann eine Zugbrücke anheben oder alle Ampeln in der Stadt in perfektem Timing ändern, damit die Autofahrer sicher über die Straßen kommen. Bitcoiner sind Magier und Zauberer, die Computercode statt Zauberbücher benutzen. Psychedelische Chemiker sind Zauberer, die ihre Zaubersprüche in der Sprache der Atome sprechen. Wie Buchstaben, die Wörter in einem Code oder einem Zauberspruch bilden, werden Atome zu Molekülen angeordnet.
Psychedelika verwandeln das fiktive Denken und Leben in neue Perspektiven und mystische Erfahrungen. Pilze sind wie die Alchemisten der Natur - sie verwandeln tote und verfallende Materie, also buchstäblichen Müll, in psychedelische Pilze, eine der elegantesten Erscheinungsformen der Natur.
Bitcoin kann auch Abfall in Schätze umwandeln. Gestrandete Energie, einst eine Last, wird durch Bitcoin in eine digitale Goldmine verwandelt. Bitcoin kann sogar unsere Mülldeponien in wertvolle Bitcoin-Minen verwandeln und so Müll in Schätze verwandeln. Der alchemistische Traum wird wahr, und zwar auf eine Weise, die sich unsere Vorfahren nie hätten vorstellen können.
Die alte Wissenschaft und Chemie der Alchemie findet im digitalen Zeitalter eine neue Form. Wenn du diese Werkzeuge studierst und anwendest, kannst du dein Leben und die Welt um dich herum wirklich und dauerhaft verändern.
"Es handelt sich eindeutig um eine Krise von zwei Dingen: des Bewusstseins und der Konditionierung. Wir haben die technologische Macht, die technischen Fähigkeiten, um unseren Planeten zu retten, Krankheiten zu heilen, die Hungernden zu ernähren und Kriege zu beenden. Aber es fehlt uns an der intellektuellen Vision, an der Fähigkeit, unsere Meinung zu ändern. Wir müssen uns von 10.000 Jahren schlechten Verhaltens befreien. Und das ist nicht einfach." - Terence McKenna
\ ⚡ Unglaublich, du hast den Artikel bis zum Ende gelesen und ich hoffe du konntest etwas Mitnehmen für deine persönliche Reise aus diesem Text.\ \ ⚡ Vielen Dank für deine Aufmerksamkeit. Wenn dir die kostenfreie Übersetzung dieses Artikels gefallen hat, würde ich mich über ein paar Satoshi auf Value for Value Basis freuen.
-
 @ 36bedab2:524acad4
2024-11-10 21:37:52
@ 36bedab2:524acad4
2024-11-10 21:37:521. Power ON
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
2. BIOS (Basic Input/Output System)
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o MBR ou a partição EFI para dar continuidade ao processo de boot.
3. Master Boot Record (MBR) ou EFI Partition
- O MBR (Master Boot Record) ou a partição EFI (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o boot loader e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o boot loader, que é responsável por carregar o sistema operacional.
4. Boot Loader (e.g., GRUB)
- O Boot Loader (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o kernel do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
5. Kernel
- O kernel é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
6. Initial RAM disk - initramfs
- O initramfs é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
7. /sbin/init (parent process)
- Após o kernel inicializar o sistema, ele chama o processo /sbin/init, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o systemd, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
8. Command Shell using getty
- Getty é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
9. Graphical User Interface (X Window ou Wayland)
- Finalmente, o sistema carrega a interface gráfica usando o X Window System (X11) ou o Wayland (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
Como esses processos se intercalam?
- Hardware ligado → BIOS/UEFI realiza verificações básicas.
- BIOS/UEFI encontra o dispositivo de boot e carrega o MBR ou partição EFI.
- MBR/EFI localiza e executa o boot loader (GRUB).
- GRUB permite que o usuário escolha o sistema operacional e carrega o kernel do Linux.
- Kernel inicializa o sistema, configurando os recursos de hardware e carregando o initramfs.
- Initramfs fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
- Kernel chama o processo /sbin/init (ou systemd), que inicia todos os serviços e processos do sistema.
- Init executa o getty para configurar o terminal de login.
- Getty chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-
 @ bcea2b98:7ccef3c9
2024-11-09 17:01:32
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-
 @ 04ea4f83:210e1713
2025-05-01 18:18:36
@ 04ea4f83:210e1713
2025-05-01 18:18:36Digitales Geld ist nur Text, die ganze Zeit
Bei digitalem Geld geht es im Grunde nur um Zahlen in einem Hauptbuch. Die ganze Zeit über sind es die Zahlen, auf die es ankommt. Lange Zahlen sind einfach nur Zeichenketten im PC und diese werden als Nachrichten in einem Netzwerk, das durch Regeln gebildet wird, an gleichwertige Peers gesendet - das ist Bitcoin, das mit einem einzigartigen dezentralen Zeitstempel-Algorithmus kombiniert wird, der durch die Unfälschbarkeit von Energie gesichert ist. Das Ergebnis ist ein Bargeldnetzwerk mit einem festen, vorprogrammierten Zeitplan für die Geldschöpfung, das den ersten absolut knappen digitalen Inhabervermögenswert schafft.\ \ Diese revolutionären Ideen werden bleiben, genauso wie das Feuer, das Rad, die Elektrizität, das Smartphone, das Internet oder die Zahl Null. Technologie entwickelt sich weiter und was machen lebende Organismen? Sie können mutieren, genau wie Viren, und das hat mich zu dem Schluss gebracht, dass es auch in dieser Hinsicht eine Verbindung gibt und das obwohl Gigi bereits einige der vielen Facetten von Bitcoin beschrieben hat. Für mich ist die Grundlage die Abstraktion, dass Bitcoin nur die Summe aller Menschen ist, die Satoshis besitzen oder anderweitig mit dem Bitcoin-Netzwerk interagieren.\ \ Die Technologien werden in einem bestimmten Tempo angenommen. Allerdings gibt es immer frühe oder späte Entdecker von neuer Technologie. Aber was passiert, wenn es zu einer ernsthaften Bedrohung wird, wenn hartes Geld nicht adoptiert wird? Was passiert, wenn die Geschwindigkeit der Preiszunahme so hoch wird, dass es unmöglich ist, jemanden zu finden, der Satoshi in Fiat tauschen möchte? Was passiert, wenn die Hyperbitcoinisierung morgen beginnt? Was wäre, wenn es eine UpSideProtection™️ gäbe, die diesen Prozess noch mehr beschleunigt und dir Bitcoin zu einem Bruchteil seines wahren Wertes sichert?\ \ Wir alle wünschen uns einen sicheren Übergang, um den Krieg aufgrund einer scheiternden Dollar-Hegemonie zu vermeiden, und tatsächlich gibt es ein Rennen, um den Krieg zu vermeiden. Mein größtes Geschenk ist die Zeit, die ich ich investiere, und die monetäre Energie, die ich in Bitcoin spare, und da ich schon eine Weile dabei bin, sehe ich, dass meine Mitstreiter die gleiche Mission verfolgen. Aber das ist NICHT genug. Wir müssen skalieren. Schneller.\ \ Das Erstaunen über den Kurzfilm der große Widerstand hat mich zu dem Schluss gebracht, dass wir alle Werkzeuge und Informationen in Form von Lehrern, Podcasts, Büchern und aufklärenden Videos bereits haben. Der Vorteil einer festen Geldmenge wird aber noch nicht von einer kritischen Masse verstanden, sondern nur von einer intoleranten Minderheit. Diese Minderheit wächst von Tag zu Tag. Ihre Inkarnationen sind die DCA-Armee, die Hodler der letzten Instanz, die unbeirrten Stacker, die Cyberhornets, die Memefactory™️ und Mitglieder der 21 Gruppe auf der ganzen Welt.\ \ Wir Bitcoiner sind räumlich getrennt, aber nicht in der Zeit. Getrennt in der Sprache, aber nicht in der Mission. Vereint müssen wir uns zu Wort melden, aufklären und Bitcoin wie einen Virus verbreiten.\ \ Niemand entscheidet, was Bitcoin für dich ist - dieser Virus des Geistes verfestigt sich in unbestechlichen Zahlen, die zu einer wachsenden Zahl an UTXOs in den Geldbörsen führen, nicht in negativen gesundheitlichen Auswirkungen. Bitcoin ist der Virus der Schuldenindustrie, der Virus, der im 21. Jahrhundert zur größten Definanzialisierung und Auflösung des Kredits führen wird. Da wir noch nicht in einer hyperbitcoinisierten Welt leben, müssen wir den Virus effektiver machen. Bitcoin muss mutieren, aber es ist nicht Bitcoin, der tatsächlich mutiert, sondern die Menschen, die ihn benutzen. Sie werden zu toxischen Maximalisten, die den Virus noch stärker verbreiten und alle Shitcoiner während ihrer Anwesenheit geistig infizieren oder argumentativ töten.\ \ Ich habe mich gefragt, wie wir eine Milliarde Menschen dazu ausbilden und überzeugen können, Bitcoin freiwillig zu nutzen und darin zu sparen, so dass sie Bitcoin als primäres Mittel zur Speicherung und Übermittlung von Werten in Raum und Zeit nutzen? Die Hyperbitcoinisierung braucht nur eine einzige, starke positive Rückkopplungsschleife um wirklich in Gang zu kommen, und diese Rückkopplung gibt es bereits, aber nicht in den Köpfen aller. Ab einer bestimmten Schwelle wird die Schwerkraft von Bitcoins gehärteten monetären Eigenschaften einfach zu hoch sein, als dass die Spieltheorie nicht zu dieser Rückkopplung führen würde, vor allem da Bitcoin im Jahr 2024 Gold in Punkto Knappheit übertrifft.\ \ Die Verbreitung der Idee einer festen dezentralen Geldmenge, die der Macht zentraler Kräfte entzogen ist, ist der Virus. Der Weg, das Spiel zu spielen, ist, Stacker zu stapeln, und Stacker stapeln Sats, wodurch die Geldmenge noch dezentralisierter wird und ein Verbot noch absurder wird. Sats sind endlich und unser Spiel ist es auch. Allein eine bestimmte Anzahl von einfachen Leuten, den Plebs, kann den Preis auf 1.000.000 EURO treiben.\ \ Letztendlich wird sich die Welt an das neue Gleichgewicht der Macht zugunsten des Individuums anpassen. Diese Idee in die Köpfe der Massen zu bringen, ist die wichtigste Aufgabe für 2023, die in das nächste Halving Mitte 2024 führt.\ \ Wir müssen unseren Reproduktionswert erhöhen, um die Akzeptanz zu steigern. Die Verwendung von Bitcoin als Zahlungsmittel und eine Kreislaufwirtschaft ist wichtig. Bildung ist wichtig. Apps und Anwendungsfälle sind wichtig. Die Kaufkraft, d.h. die Moskau Zeit, die sich in Richtung Mitternacht (00:00) bewegt, spielt eine Rolle, und all dies hängt zusammen.\ \ Aber wie genau können Plebs eine Milliarde Menschen überzeugen?\ \ Wie genau hat das Corona-Virus eine Milliarde Menschen infiziert?\ \ Peer-to-Peer.\ \ Erhebe deine Stimme, wer auch immer du bist, sprich über Bitcoin, werde aktiv und BUIDL oder lass uns einfach Spaß daran haben, arm zu bleiben und es genießen, jeden Tag bestohlen zu werden.\ \ Lass uns Yellow mehr Freizeit schenken und Bitcoin bis 100k+ aufkaufen und uns damit ins Stackheaven befördern.
"Don't stop believin' HODL on to that feelin' "
Der Rest wird in die unumstößliche Geschichte der Timechain eingraviert.
„Unter dieser Maske gibt es mehr als nur Fleisch. Unter dieser Maske ist eine Idee. Und Ideen sind kugelsicher." Alan Moore, V wie Vendetta

⚡
Danke für deine Aufmerksamkeit .\ \ #GetShortFiat und #GetOnZero\ \ Es ist immer noch 60 Uhr. Sei weise und stapele unbeirrt. Man kann die Mathematik und Physik nicht austricksen.\ \ Wenn der Post dir Motivation zum Stapeln von Sats oder dem Stapeln von Stackern gemacht hat, freue ich mich, wenn du mir auch etwas beim Stapeln hilfst!
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 4fe4a528:3ff6bf06
2024-11-01 13:30:30
@ 4fe4a528:3ff6bf06
2024-11-01 13:30:30Buy Bitcoin "Opt out of inflation" Lyn Alden’s https://www.lynalden.com/october-2024-newsletter/ is better than this monthly https://amendt.substack.com/p/buy-bitcoin. She explains, better than I can, why bitcoin is still inexpensive. From my perspective, the reason bitcoin is getting more and more valuable is because it is almost my birthday and people know I would enjoy bitcoin as a birthday present. Ok maybe I am not the central figure in this bitcoin saga, but for some reason bitcoin goes up on my birthday. So, I would like to take this opportunity to thank you for causing this commodity to increase in value during my birthday. That was a joke!
I don’t think it is because you want to send me bitcoin that that is the only reason why bitcoin is climbing. Mind you the price action in bitcoin could be because the big boys (with money) have bought https://docs.google.com/spreadsheets/d/1EZPpEA_aaZSwOTM90KpbLYfPJWqq31vOS1HhXNfkUmQ. Yes Lyn explains why the smart money (rich guys) are now putting their money into bitcoin. It has a lot to do with scarcity — only 1.223921×10¹⁴ sats left and Metcafe’s law.
Metcalfe's Law states that the value of a network is proportional to the square of the number of users in the network
We are now back to 60% bitcoin dominance which is saying a lot when there is 2.4 million competing digital assets. With One bitcoin now over 100,000 Canadian dollars that says a lot of people think it is money. Go ahead and spend a dollar and get yourself 1000 sats just in case it catches on. My whole beef prices are now https://www.pricedinbitcoin21.com/chart/livestock/LC1. On the rail beef is only 4500 sats / lb — the same price as a dozen of eggs. Also, if you need a place to stay, https://airbtc.online/properties/one-bedroom-suite-in-the-country/. Finally people in Canada can live only on bitcoin. Justin Trudeau said on March 12, 2023 Buy Bitcoin, https://cdn.satellite.earth/eef0f82150494810cacb622bd203cf8dea19b094cea940932e43d5a21b05c56a.mp4 Bitcoin is now up over 100% since then.
Happy Birthday to https://v.nostr.build/ivyiPSnv7HfuECFE.mp4
-
 @ a9434ee1:d5c885be
2024-10-29 20:46:24
@ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...)
Design System
Check it out here.
This is by no means finished and will be continually updated and completed as we go along.Project description
Check it out here nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda
This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki.
Explanatory videos
This list of videos will also be continually updated and completed as we go along:
-
Chat as the universal interface
https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov -
Your Nostr Dashboard
https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov -
Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov
-
Design entered the Chat
https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov -
Targeted publication & The blurry edges of interoperable communities
https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov -
Travel Back
https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
-
-
 @ 9017cf6a:3d8a7adb
2024-10-27 21:46:06
@ 9017cf6a:3d8a7adb
2024-10-27 21:46:06Ricardo Nunes (MDB) é eleito prefeito de São Paulo
O prefeito de São Paulo, Ricardo Nunes (MDB), conquistou sua reeleição neste domingo (27) e agora terá mais quatro anos para administrar a maior cidade do Brasil.
Apoiado por Jair Bolsonaro (https://www.conexaopolitica.com.br/tag/jair-bolsonaro/) e pelo PL (https://www.conexaopolitica.com.br/tag/pl/), que indicou seu vice na chapa, o emedebista foi confirmado como o vencedor do segundo turno disputado contra o esquerdista Guilherme Boulos (PSOL).
Nunes assumiu a prefeitura da capital paulista em 2021, após a morte de Bruno Covas (PSDB), de quem era vice na chapa eleita em 2020. Aos 56 anos, ele agora terá um mandato completo para gerenciar a principal metrópole da América do Sul.
Comments: https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/#respond
https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/
-
 @ 4ba8e86d:89d32de4
2024-10-24 23:20:51
@ 4ba8e86d:89d32de4
2024-10-24 23:20:51VeraCrupt foi lançado em 2013 como um fork do projeto TrueCrypt descontinuado. Desde então, o VeraCrypt tem passado por diversas atualizações e melhorias de segurança, incluindo a correção de problemas identificados por auditorias de código do TrueCrypt. O VeraCrypt inclui implementações otimizadas de funções criptográficas de hash e cifras, o que aumenta o desempenho em CPUs modernas. O software permite criar e gerenciar volumes criptografados em computadores ou dispositivos de armazenamento externo, com suporte para vários algoritmos de criptografia e recursos adicionais, como proteção contra ataques de keylogger e ocultação de volumes , tem opção de segurança robusta para proteger seus dados.
Quando você cria um volume criptografado no VeraCrypt, o software cria um arquivo virtual que funciona como um disco rígido criptografado. Esse arquivo é montado como uma unidade lógica no seu sistema operacional e pode ser acessado como qualquer outro disco rígido.
Antes que você possa acessar o volume criptografado, você precisa fornecer a senha correta. A senha é usada para desbloquear o arquivo virtual criptografado e permitir que o sistema operacional acesse o conteúdo. O VeraCrypt suporta vários algoritmos de criptografia, incluindo AES, Serpent e Twofish, que podem ser selecionados pelo usuário ao criar o volume criptografado.
O VeraCrypt também oferece recursos adicionais de segurança, como proteção contra keyloggers, que podem registrar as teclas digitadas no teclado para capturar senhas. Ele faz isso fornecendo uma interface virtual para digitar senhas, o que impede que os keyloggers capturem a senha real. O VeraCrypt também permite ocultar volumes criptografados dentro de outros volumes criptografados, o que fornece uma camada adicional de segurança.
O veracrypt proteger informações confidenciais armazenadas em dispositivos de armazenamento, como discos rígidos, unidades flash USB e cartões de memória, contra acesso não autorizado. Se um usuário estiver executando o Tails a partir de uma unidade flash USB, e o disco rígido estiver criptografado com o VeraCrypt, o Tails não terá acesso ao conteúdo do disco rígido, a menos que o usuário monte o volume criptografado do VeraCrypt e forneça a senha correta.
No entanto, é importante lembrar que a criptografia do disco rígido por si só não garante a segurança completa do sistema. Os usuários também devem tomar outras medidas de segurança, como manter o sistema operacional e o software atualizados, usar senhas fortes e não compartilhá-las com ninguém, e tomar cuidado com o acesso físico ao computador ou dispositivo de armazenamento externo.
https://veracrypt.fr
https://github.com/veracrypt/VeraCrypt/
-
 @ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52
@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52Tldr
- Nostr relays help users post and read notes on the network
- Relay operators have launched a variety of relays for you to use
- You too can launch your own relay for any reason you like
- Launching your own relay gives you a lot of power in how you use Nostr
- Many relay softwares exist for you to use
- I launched a personal relay using HAVEN relay software on my VPS
- I am now more in control of saving notes, cutting spam, and protecting my privacy
- My personal relay is now hosted at relay.rodbishop.nz
What are Nostr Relays Anyway?
When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators.
Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these.
Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set.
It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to:
- Power your own client
- Support your community
- Run a for-profit relay business
- Relay a certain a type of content you need
- Back up your own notes, decrease spam, or increase privacy
- Curate your own social feed with your own algorithm
Relay instances available to connect with
Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with.
A few sites try to collate which relays are in operation, like nostr.info and xport.top and sesseor's relay list . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time.
Broadly speaking, relays might be available for different users to use in different ways:
- A relay where anyone can post, like relay.damus.io
- A paid relay where anyone can post after payment, to cut spam, like nostr.wine
- A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like nostrelites.org
- A speciality relay where a particular community can post, like nostr.com.au for #austriches (Australians)
- A relay where anyone can post just specific content, like purplepag.es for user profiles only
- A team relay for your company or organisation only
- A personal relay for your own personal use
Nostr.Band shows which of these available relays are most popular, such as relay.damus.io and nos.lol and eden.nostr.land
Relay softwares for you to launch your own
You may decide to launch you own relays, and if you do there are many different relay softwares to choose from:
- Simple, like Bucket (<100 lines of code)
- Widely used, like Nostream (top ranked on Github)
- Customisable, like Khatru (a framework for customised relays)
- Specialised, like HAVEN or Team Relay (for personal or teams relays, based on Khartu)
You can run these on your own server, or local machine, or phone or with a third-party host.
Aljaz provides a great resource with 45+ relay softwares to choose from.
In summary, at a high level,
- Anyone can connect to any of the relay instances that are available for them to use
- Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like
Reasons to Run Your Own Relay
As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power.
For my own journey down the #nostr rabbit hole, I was looking for a relay to:
- back up my notes
- decrease spam
- increase my privacy
- learn skills I could later use for running a community or team or paid relay
Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online.
Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam.
Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private.
For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures.
To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one.
The outbox model
Mike Dilger proposed the outbox model (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes.
Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs.
Outbox Relay (also called Home Relay)
- This relay is for notes you have written, so that everyone knows where to find your notes
- In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it
- An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach
Inbox Relay (also called Public Relay)
- This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments
- In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it
- An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note
Chat Relay (also called Direct Message Relay)
- This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private
- In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it
- An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust
Private Relay
- This relay is for your private use only, so that you can store private drafts or thoughts
- Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all)
- In a set up where you are running your own, it gives you true privacy for these notes
In summary as a user
- I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network
- I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network
- I can have private direct message conversations with others in my chat relay.
- I can save private notes in my private relay
For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features.
HAVEN as a personal relay
I decided to go with HAVEN relay software.
HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust.
HAVEN is written by Utxo the Webmaster . It is based upon the Khatru relay framework by Fiatjaf
Setting up HAVEN as a Personal Relay
I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker.
- I have a cheap VPS which currently runs Albyhub and Phoneixd with Docker,
- My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but Sebastix published a fork with Docker support.
To get HAVEN up and running in Docker on your VPS:
- Clone and configure HAVEN with the right variables
- Launch it in Docker on your VPS
- Check the URLs and logs to see your HAVEN running
- Configure a subdomain to point to the VPS
- Configure the VPS to reverse proxy to the Docker port
- Configure the relays in your favourite Nostr client
- Post a note to your outbox and see if it blasts!
Running HAVEN
I cloned Sebastix fork to start.
git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd havenThe software sets up all environment variables in the
.envfile, and comes with an.env.examplefile. Duplicate and rename the file to.env. Within the.envfile you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required:- Replace all instances of the default user npub with your own (for me,
npub1r0d8...) - Change the default relay URL to your own (for me,
relay.rodbishop.nz) - Replace all instances of the default name in the relay names (for me, "Rod's ...")
- Replace all instances of the default profile image with your own
To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See
relays_blastr.example.jsonandrelays_import.example.json. To use these features simply duplicate and rename these files torelays_blastr.jsonandrelays_import.jsonrespectively. Within these files you can specify the public relays of your choice. I simply used the default list.There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it.
To launch the relay run Docker Compose.
docker-compose up -d docker logs haven-relayThen you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages.
The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows.
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keysYour browser should show you have four relays in operation, for example as follows.
your_IP_address:3355(your outbox or home relay)your_IP_address:3355/private(your private relay)your_IP_address:3355/chat(your direct message relay)your_IP_address:3355/inbox(your inbox relay)
That's it. Your relay is online.
Connecting HAVEN
Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together.
Configure DNS
First, configure your domain. At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caserelay.rodbishop.nz
Your subdomain now points to your server.
Configure reverse proxy
Next, you need to redirect traffic from your subdomain to your relay at port
3355.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx.
For my method, my steps were as follows:
- Add configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.rodbishop.nzsubdomain - Add the Caddy Docker network to the HAVEN
docker-compose.ymlto make it be part of the Caddy network
For the addition to the
Caddyfile, I used as follows:relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }For the addition to the
docker-compose.yml, I used as follows:``` networks: - caddy # Added this line to services to connect to the Caddy network
networks: caddy: external: true # Added this to section specify the Caddy network ```
Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at
relay.your_domain_name.com. For my set up, this wasrelay.rodbishop.nz.Connecting your Nostr client
Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN.
- In the sidebar, select Relays
- For "Public Outbox/Home Relays" enter
relay.your_domain_name.com - For "Public Inbox Relays" enter
relay.your_domain_name.com/inbox - For "DM Inbox Relays" enter
relay.your_domain_name.com/chat - For "Private Home Relays" enter
relay.your_domain_name.com/private - Click Save to broadcast your new relays to the Nostr network.
Your new relay configuration is now live.
Testing your relay
Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post.
- Create a test note, and then before you post it, edit your relays using the icon at the top
- Turn off all relays except your own outbox relay, and post the note
- Access your HAVEN docker logs with
docker logs haven-relayand see if there is a log to indicate if the note was received and blasted to other public relays - Copy the
neventof the note, and attempt to find it in another client
If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn).
2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inboxThat's it. If you followed this successfully your personal relay is up and running.
What I did wrong so you don't have to
My first relay was too public
This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down.
Unfamiliar with Go language
I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here.
I failed a few times due to a messy folder
After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue.
Trouble with Nostr.wine
I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows
CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users'It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings.
Failed to create web of trust graph
When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam).
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keysI never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again".
Failed to run --import function
HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows:
panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailableI have yet to work out the solution for this, and will update this note when I do so!
What's Next?
Over the past four blogs I have
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these?
- Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain
- Experiment with different signers like Amber and Nsec.app and NFC cards
- Set up a paid relay for #austriches (Australians and Kiwis on Nostr)
- Set up a team relay to experiment with Nostr for business or community projects
- Or something else ... ?
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
Pura vida Nostr.
-
 @ 4ba8e86d:89d32de4
2024-10-17 22:26:20
@ 4ba8e86d:89d32de4
2024-10-17 22:26:20Ele oferece a opção de utilizar autenticação de dois fatores para aumentar ainda mais a segurança. O aplicativo foi desenvolvido em 2016 pelo americano Mo Bitar para oferecer um lugar seguro para armazenar informações pessoais sem a preocupação de que seus dados sejam coletados ou expostos a terceiros.
O Standard Notes é um cofre de aço para seus dados mais confidenciais, que protege suas anotações e arquivos com criptografia de ponta a ponta líder do setor e auditada 4x. Armazene com segurança todos os seus dados confidenciais em um só lugar e acesse-os de todos os seus dispositivos, com a certeza de que seus dados estarão sempre protegidos pelos mais altos padrões de segurança.
Ao contrário de outros serviços de anotações, o Standard Notes apresenta medidas de segurança avançadas e controles de privacidade que protegem seus dados contra hacks, violações de dados, acesso do governo e até mesmo acesso de funcionários. Ele defende a privacidade dos usuários e apresenta políticas revisadas por pares e auditáveis.
O Standard Notes utiliza criptografia de ponta a ponta para proteger todos os dados, que são criptografados sempre que tocam um disco, como em seus servidores ou no dispositivo do usuário. Auditorias independentes são realizadas periodicamente em sua criptografia, aplicativo e código do servidor para garantir que os dados estejam protegidos. O código aberto do Standard Notes permite que os usuários tenham clareza sobre como seus dados estão sendo tratados em cada etapa do caminho. Ele não coleta ou armazena informações do usuário, como endereço IP ou agente do usuário, para proteger a privacidade.
-
Acesse a F-droid ou Google Play Store em seu dispositivo Android.
-
siga as instruções para criar uma conta ou fazer login em uma conta existente.
-
Comece a criar suas notas e armazenar outras informações importantes com a tranquilidade de que seus dados estão seguros e protegidos.
https://github.com/standardnotes
-
-
 @ 04ea4f83:210e1713
2025-05-01 18:12:30
@ 04ea4f83:210e1713
2025-05-01 18:12:30Was ist ein Meme?
Bevor wir uns in die Materie vertiefen, sollten wir einen genaueren Blick auf die Begriffe werfen, mit denen wir es zu tun haben. Laut dem American Heritage Dictionary of the English Language ist ein Meme „eine Einheit kultureller Informationen, wie z. B. eine kulturelle Praxis oder Idee, die verbal oder durch wiederholte Handlungen von einem Geist zum anderen übertragen wird".
Der Begriff wurde von Richard Dawkins in seinem 1976 erschienenen Buch geprägt und ist eine Anspielung auf das Wort "Gen", die Einheit der biologischen Information, die sexuell von einem Organismus auf einen anderen übertragen wird.
Dawkins erkannte, dass kulturelle Informationen ähnlich wie biologische Informationen sind und sich genauso verbreiten und mutieren, wenn auch auf einer höheren Abstraktionsebene. Genau wie bei biologischen Informationen ist der ultimative Test für kulturelle Informationen das Überleben, und genau wie biologische Informationen müssen sie für die Umwelt geeignet sein, um sich zu verbreiten und am Leben zu gehalten zu werden.
Manche Ideen funktionieren einfach nicht, wenn sie fehl am Platz sind oder die Zeit nicht reif für sie ist. Sie werden schnell sterben, genau wie der sprichwörtliche Fisch auf dem Trockenen. Andere Memes funktionieren vielleicht eine Zeit lang, verblassen aber langsam durch allmähliche Veränderungen in der Umwelt oder brechen plötzlich durch die von ihnen ausgelösten destruktiven Rückkopplungsschleifen zusammen. Wie Gene verbreiten sich Meme langfristig nur dann, wenn sie für den Organismus und seine Umwelt von Nutzen sind.
„In der Wissenschaft der Ökologie lernt man, dass der Mensch nicht ein Organismus in einer Umwelt ist, sondern eine Organismus-Umwelt-Beziehung. Das heißt, ein einheitlicher Bereich des Verhaltens. Wenn man das Verhalten eines Organismus sorgfältig beschreibt, kann man das nicht tun, ohne gleichzeitig das Verhalten der Umwelt zu beschreiben... [...] Der Organismus ist nicht die Marionette der Umwelt, die von ihr herumgeschubst wird. Umgekehrt ist auch die Umwelt nicht die Marionette des Organismus, die vom Organismus herumgeschubst wird. Die Beziehung zwischen ihnen ist, um es mit John Deweys Worten zu sagen, transaktional."\ \ Alan Watts
Was hat das mit Bitcoin zu tun? Nun, du musst dich fragen, wie das Bitcoin-Netzwerk zustande kommt, und wenn du das tust, wirst du feststellen, dass Bitcoin sich nicht allzu sehr von den oben erwähnten Memen und Genen unterscheidet. Bitcoin ist ein instanziierter Computercode, ein digitaler Organismus, der die Menschheit dafür bezahlt, ihn am Leben zu erhalten, wie Ralph Merkle es so treffend formulierte. Die kumulative Arbeit, die in Bitcoins Timechain eingebettet ist, ist das, was Bitcoin real macht und was ihn von gewöhnlicher Information unterscheidet. Und von gewöhnlichen Computerprogrammen, was das betrifft. Genauso wie es einen Unterschied zwischen dir selbst und einem Ausdruck deiner DNA gibt, gibt es einen Unterschied zwischen dem Bitcoin-Code - den Memes, die er sich zu Nutze macht - und der realen Instanziierung von Bitcoin.
Das Bitcoin-Netzwerk instanziiert und validiert sich selbst alle 10 Minuten, Block für Block, wie ein Uhrwerk. Diese Blöcke sind die Informationseinheit, die übertragen wird, und ja, genau wie bei den Memen ist diese Information eine kulturelle Information. Die Tatsache, dass diese Information elektronisch übertragen wird, spielt keine Rolle; sie verkörpert immer noch den Kern der Bitcoin-Kultur, die Seele des Netzwerks. Und genau wie Memes wird diese Information durch wiederholte Aktionen von einem Knotenpunkt zum anderen übertragen. Und davor, von einem Geist zum anderen.
Im ökologischen Sinne handeln wir alle mit Bitcoin, und Bitcoin handelt mit uns. Wenn du von Bitcoin gehört hast, wenn du das Meme „21 Millionen" kennst, dann hat Bitcoin mit dir Geschäfte gemacht. Lange bevor du deine erste Bitcoin-Transaktion gemacht haben.
Memes und ihre Umgebung
Bitcoin sind Menschen, wenn es darauf ankommt. Ja, es ist Software, aber die Menschen müssen die Software ausführen und, was noch wichtiger ist, selbst entscheiden, was Bitcoin ist. Es gibt keine Autorität, wenn es um Bitcoin geht. So muss jeder für sich selbst herausfinden, was Bitcoin ist, und aus der Überschneidung der verschiedenen Standpunkte ergibt sich ein Konsens. Dies ist ein ständiger Prozess, denn es geht nicht nur darum, was Bitcoin derzeit ist, sondern auch darum, was Bitcoin sein könnte. Was Bitcoin sein sollte. Genau darum ging es im Blocksize War. Ein Kampf um die Seele von Bitcoin. Eine Meinungsverschiedenheit über die Zukunft und den ultimativen Zweck von Bitcoin. Ein Unterschied im memetischen Material, der letztendlich zu einer Spaltung des Protokolls führte, was wiederum zu einer Spaltung des Netzwerks und einer Spaltung der Kultur führte.
Aber auch ohne eine Spaltung, selbst wenn ein Konsens besteht, ist die Frage „was Bitcoin ist" nicht eindeutig zu beantworten.
Für dich mag das Lightning Network nicht wichtig sein, und es steht dir frei, eine Vor-SegWit-Version von Bitcoin zu betreiben. Für jemand anderen sind Dickbutts und Fürze auf der Blockchain vielleicht nicht wichtig, und er könnte sich entscheiden, eine Vor-Taproot-Version von Bitcoin zu verwenden (oder eine Version zu verwenden, die Ordnungszahlen (Ordinals) nicht respektiert). Bitcoin ist abwärtskompatibel, und Upgrades sind optional, gerade weil es keine Autorität gibt, die etwas vorschreibt.
So funktioniert Bitcoin, und so wird es immer funktionieren, weshalb Memes wichtig sind und warum es eigentlich durchweg Memes sind.
Um Bitcoin zu nutzen, muss man sich freiwillig entscheiden. Man muss zuerst von der Idee überzeugt werden, von der Idee, Sats zu akzeptieren, damit Fiat fallen zu lassen und Bitcoin zu erwerben. Erst wenn man davon überzeugt ist, dass elektronisches Bargeld mit einer (absolut) festen Menge nützlich sein könnte, wird man es akzeptieren oder damit sparen.
Das Meme „21 Millionen" kommt zuerst, und nachdem unsere Gehirne ausreichend von der Idee infiziert wurden, werden wir deshalb die Software starten, die die 21 Millionen ins Leben rufen.
Natürlich kommen manche Leute - ich glaube, die meisten - auf Umwegen zum Bitcoin. Du denkst, dass es sich um einen spekulativen Vermögenswert handelt, etwas, das existiert, um mehr Dollar zu verdienen, d. h. um mehr Papiergeld zu verdienen. Oder du entdeckst ihn über Online-Glücksspiele oder andere Wege, und auf diese Weise kommen sie zu ihren ersten Sätzen. Aber selbst wenn du auf Umwegen zu Bitcoin kommst, selbst wenn Bitcoin vor deiner Haustür ankommt, ohne dass du verstehst, womit du es zu tun hast, musst du lernen, Bitcoin selbstbestimmt zu nutzen, oder du wirst es nicht schaffen.
Bitcoin auf eine selbstsouveräne Art und Weise zu nutzen, bedeutet, dass du die Memes von Bitcoin absorbieren musst. Zum Beispiel musst du die „21 Millionen" übernehmen und ihnen zustimmen, sonst hast du keinen Bitcoin, sondern einen Shitcoin in den Händen. Bitcoin am Laufen zu halten bedeutet, Bitcoin auszuleben, was wiederum bedeutet, seine eigenen Schlüssel zu besitzen, seinen eigenen Knoten zu betreiben und den zentralen Konsensparametern zuzustimmen, die Bitcoin zu Bitcoin machen.

Mit der Zeit wird ein horizontaler Meme-Transfer stattfinden. Bitcoin wird auf dich abfärben. Du wirst nicht nur den Ideen ausgesetzt sein, die in Bitcoin eingebettet sind; nein, du wirst ein Teil davon sein und das Meme leben, indem du die Satoshi Tag für Tag und Block für Block hältst.
Oder du wirst es nicht. Wenn du mit den Ideen, die in den Konsensparametern von Bitcoin eingebettet sind, nicht einverstanden sind, hast du zwei Möglichkeiten: Du kannst dich abspalten oder unter dem Bitcoin Derangement Syndrom leiden. Man kann sich natürlich auch an die Umwelt anpassen und in Symbiose mit ihr leben, was bedeutet, sich mit dem in Bitcoin eingebetteten memetischen Material zu arrangieren - es zu akzeptieren und ihm langsam zuzustimmen.
Wenn man die zuvor skizzierte ökologische Sichtweise anwendet, bilden Bitcoin und die Bitcoiner selbst den Organismus-Umwelt und beeinflussen sich gegenseitig in 10-Minuten-Intervallen. Das Knifflige daran ist, dass Bitcoin sowohl Organismus als auch Umwelt ist, genau wie wir selbst. Das Bitcoin-Meme lebt in unseren Gehirnen und unsere Vorstellung davon, was Bitcoin ist - und was es sein sollte - ändert sich mit der Zeit. Die ökonomische Erweiterung von uns - unsere Sats - leben in der Umgebung, die Bitcoin ist, eine Umgebung, die wir individuell und kollektiv hervorbringen.
Wir formen unsere Werkzeuge, und unsere Werkzeuge formen uns. Und wir benutzen unsere Werkzeuge, um unsere Umwelt zu formen, die natürlich auch uns formt. Kultur ist das Ergebnis dieser gegenseitigen Beeinflussung, und was ist Kultur anderes als eine Vielzahl von Memen?
Bei Bitcoin haben wir es mit einem unglaublichen meinungsbildenden Werkzeug zu tun, das eng mit uns verwoben ist. Ein Werkzeug, das ein Umfeld schafft, das lächerlich schwer zu ändern ist. Ich würde sogar so weit gehen zu sagen, dass einige Aspekte dieser seltsamen Meme-Werkzeug-Organismus-Umwelt-Schleife unmöglich zu ändern sind, da dies die Identität von Bitcoin und Bitcoinern gleichermaßen zerstören würde.
Für mich wird Bitcoin immer durch 21ismus definiert werden, auch wenn ich der letzte Mensch wäre, der an dieses Meme glauben würde. Anstelle dessen würde ich lieber auf dem Hügel von 21 Millionen sterben - allein und in Armut, mit dem Node in der Hand und zwölf Worten in meinem Kopf - als einer Erhöhung des Bitcoin-Angebots um 1 % zuzustimmen. (Buchvorschlag: Mandibles)
Es gibt diejenigen, die diese unveränderliche Umgebung akzeptieren, und diejenigen, die sie ablehnen, was natürlich zu einer Spaltung der Kultur führt.
Kulturelle Spaltungen
Wir erleben zweifelsohne eine Art Kulturkrieg. Links gegen Rechts, Rot gegen Schwarz, Based gegen Woke, Blue Bird gegen Purple Bird und Furries gegen normale Menschen. Es ist schwer, die Bruchlinien auszumachen, die diesem Krieg zugrunde liegen. Einige glauben, dass es auf Individualismus gegen Kollektivismus hinausläuft. Andere sehen es als Kapitalismus vs. Marxismus, selbstregulierende Ordnung vs. zentrale Planung. Wieder andere spekulieren, dass dieses Chaos mit dem Rückgang des religiösen Glaubens zusammenhängt, der eine Folge der nietzscheanischen Ermordung Gottes ist.
Alle diese Gründe mögen zutreffend oder teilweise zutreffend sein, aber für mich als Bitcoiner - als jemand, der die Graphen des "WTF geschah 1971" viele Male bestaunt hat - ist es schwer, etwas anderes als den Notstand des Fiat-Geldes als den Hauptgrund für das Chaos, das wir erleben, zu benennen. Für mich scheint es offensichtlich, dass diese verrückten Zeiten ein Ergebnis des Fiat-Geldsystems und der wirtschaftlichen sowie memetischen Konsequenzen sind, die es mit sich bringt. Es ist ein System, das völlig von der Realität abgekoppelt ist, ein künstliches und hochpolitisches Umfeld, das, ob wir es erkennen oder nicht, das wirtschaftliche Betriebssystem unserer Welt ist. Für mich lässt sich die Bruchlinie der Gesellschaft am besten als „Bitcoin vs. Fiat" zusammenfassen.
Seit 50 Jahren leben wir die Idee des Fiat-Geldes aus. Das Meme, dass die Art des Basisgeldes keine Rolle spielt, die hartnäckige Überzeugung, dass „wir es uns selbst schulden". Wir scheinen zu glauben, dass unsere kollektive Zukunft ein magischer goldener Topf ist - scheinbar ohne Boden -, aus dem wir uns immer und immer wieder etwas leihen können.
Ich glaube, dass wir uns in der Endphase des großen Fiat-Experiments befinden. Einmal mehr haben die arroganten Könige dieser Welt beschlossen, Gott zu spielen und sich in Kräfte einzumischen, die größer sind als sie, größer als wir. Wieder einmal müssen wir feststellen, dass das Drucken von Geld keinen wirklichen Wert schafft. Einmal mehr wird sich die Gesellschaft wandeln oder ganz zusammenbrechen, wie es in Ägypten, Rom und in vielen anderen Kulturen vor der unseren geschah. Und einmal mehr wird sich die Natur durchsetzen, indem sie Verwüstung anrichtet und alles ausrottet, was nicht mit ihr übereinstimmt. Seien es Ideen oder anderes.
„Als es nun an Geld gebrach im Lande Ägypten und in Kanaan, kamen alle Ägypter zu Josef und sprachen: Schaffe uns Brot! Warum lässt du uns vor dir sterben? Denn das Geld ist zu Ende."\ \ Mose 47:15
Diesmal ist das Fiat-Experiment jedoch nicht lokal begrenzt. Es ist nicht das Geld eines einzelnen Landes, das versagt, sondern das Meme des Fiat-Geldes selbst.
Geld drucken vs. das Geld in Ordnung bringen
Die Erkenntnis der Bedeutung des Geldes sowie der moralischen und kulturellen Implikationen der Natur des Geldes - und der Ethik der Geldproduktion - hat mein Weltbild unwiderruflich verändert. Als ich erkannte, dass Gelddrucken nichts anderes als eine Umverteilung von Reichtum ist und dass eine zentral geplante Umverteilung von Reichtum eine unmögliche Aufgabe ist - nicht nur rechnerisch, sondern auch moralisch -, dämmerte mir, dass Konfiszierung durch Inflation und andere Formen der unfreiwilligen Umverteilung nichts anderes ist als Diebstahl auf Umwegen. Das Fiat-System ist ein System der Sklaverei, und nein, das ist keine Übertreibung.
Aber hier ist die gute Nachricht: Bitcoin schafft hier Abhilfe.

Das ist unsere Meme-Welt, alle anderen leben nur darin.
Es gibt eine bestimmte Ethik, die in Bitcoin eingebettet ist, und es ist diese Ethik, die den Grundstein für die Meme bildet, die wir entstehen und sich verbreiten sehen. Wenn ich es in einem Satz zusammenfassen müsste, dann wäre es dieser: „Du sollst nicht stehlen." Wenn ich es in einer Zahl zusammenfassen müsste, dann wäre es natürlich 21 Millionen.
Die Motivation hinter der Erschaffung von Bitcoin ist zweifelsohne politisch, wie „Kanzlerin am Rande der zweiten Bankenrettung" und verschiedene Kommentare von Satoshi zeigen. So stimmte Satoshi zwar der Aussage zu, dass „sie in der Kryptographie keine Lösung für politische Probleme finden werden", aber er erwähnte auch, dass „wir eine wichtige Schlacht im Wettrüsten gewinnen und ein neues Territorium der Freiheit gewinnen können". Man beachte die Worte, die in dieser Aussage verwendet werden: ein Gebiet (Umfeld) der Freiheit (im Gegensatz zur Sklaverei).
Ich würde argumentieren, dass „eine große Schlacht gewinnen" eine Untertreibung ist, und ich würde auch argumentieren, dass die ursprüngliche Behauptung falsch ist, aber ich werde darauf zurückkommen.
Doch auch ohne diese Kommentare, selbst wenn die in den Genesis-Block eingebettete Botschaft „ooga chaka ooga ooga ooga chaka" lauten würde, wäre Bitcoin immer noch politisch. Ja, das daraus resultierende System ist unpolitisch, genau wie der Sonnenaufgang unpolitisch ist, aber der Akt der Schaffung von bitcoin ist ein politischer Akt. Er ist eine Aussage, eine Manifestation bestimmter Ideen, von Qualitätsmemes.
Vergleiche die in Bitcoin eingebettete Ethik (festes Angebot, keine erzwungene Umverteilung, kein kostenloses Mittagessen, keine Rettungsaktionen) mit der Ethik des Fiat-Geldes (endloses Angebot, zentral geplante Umverteilung, Rettungsaktionen für Freunde, alles ist erfunden) - oder, noch drastischer, mit der „Ethik" der Shitcoins, die nur Fiat-Geld auf Steroiden ist (jeder kann sein eigenes Geld drucken, nichts ist wichtig, Rugpulls sind lustig und Dickbutts sind im Grunde die Mona Lisa).
Ist es eine Überraschung, dass die Kultur rund um diese Phänomene so unterschiedlich ist? Oder ist „du wirst nichts besitzen und du wirst glücklich sein" einfach eine Folge des Mems, das Fiat-Geld ist? Ist der kulturelle Unterschied zwischen Bitcoinern und Shitcoinern ein natürliches Ergebnis der Meme, die in den verschiedenen Organismus-Umgebungen eingebettet sind und von diesen hervorgebracht werden?
Im Klartext bedeutet das Meme des Fiat-Geldes - die Idee, dass wir Geld aus dem Nichts erschaffen können und sollten - einfach zu sagen: „Ich weiß besser als der Markt, wie man Geld verteilt", was bedeutet, dass ich besser als alle anderen weiß, was gut und was schlecht ist, was wertvoll ist und was nicht, was notwendig und was überflüssig ist.
Die Frage, die das Fiat-System beantwortet, ist die folgende: Wer darf Geld fälschen und wie viel? Und wer darf Zugang zu Geld haben, und wer nicht? Die Antwort ist politisch und wird mit Gewalt durchgesetzt.
Das Bitcoin-System beantwortet dieselben Fragen, und die Antworten sind ebenso einfach wie ethisch: Niemand darf Geld fälschen, und jeder kann darauf zugreifen. Keine Ausnahmen.
Dies sind zwei sehr unterschiedliche Ideen, zwei sehr unterschiedliche Memes. Die eine wird im Fiat-System umgesetzt, die andere im Bitcoin-System. Das eine bricht aus den Nähten, das andere tuckert vor sich hin und wächst wirtschaftlich, rechnerisch und memetisch - alle 10 Minuten.
Bitcoin vs. Gold
Wenn es darum geht, die Grundursache vieler unserer Übel zu identifizieren, hatten die Goldanhänger (größtenteils) die richtige Idee. Aber sie hatten keine Möglichkeit, ihre Ideen auf sinnvolle und effektive Weise umzusetzen, die in der vernetzten Welt des 21. Das Meme des „gesunden Geldes" ist das richtige Mem, aber ohne eine Möglichkeit, dieses Meme effizient umzusetzen, hat das Meme keine Möglichkeit, sich in der Bevölkerung zu verbreiten.
So sieht es aus, liebe Goldfresser: Wir werden nicht zu einem Goldstandard zurückkehren. Gold hat in der Vergangenheit versagt, und es würde auch in der Zukunft versagen. Die Nützlichkeit des „Goldstandard"- Memes ist zu einem Ende gekommen. Das Überbleibsel seiner glorreichen Vergangenheit wird nur noch in der Linguistik zu finden sein.
„Warum", fragst du dich? Nun, zunächst einmal verbietet der physische Körper des Goldes die Teleportation, d. h. die elektronische Übertragung von Gold. Er verbietet die Unsichtbarkeit, d. h. die plausible Abstreitbarkeit des Besitzes. Bitcoin kann sofort teleportiert und perfekt versteckt werden. Man kann ihn im Kopf behalten, und niemand kann wissen, ob man Bitcoin tatsächlich besitzt oder nicht. Gold wird allein aus logistischen Gründen immer in Tresoren zentralisiert sein. Bitcoin muss das nicht sein. Gold wird sich immer mit einer bestimmten Rate aufblähen, da eine unbekannte Menge noch unter der Erde (und im Weltraum) liegt. Die Menge, die sich über der Erde befindet, ist ebenfalls unbekannt, da der weltweite Goldvorrat nicht einfach überprüft werden kann.
Im Gegensatz dazu ist Bitcoin absolut knapp und perfekt überprüfbar. Alle 10 Minuten wird der Gesamtvorrat an Bitcoin geprüft. Alle 10 Minuten wird der Emissionsplan überprüft. Alle 10 Minuten werden Milliarden von Sats endgültig und elektronisch, d.h. mit Lichtgeschwindigkeit, abgerechnet. Eine echte, physische Abrechnung. Global und sofort, ohne große Kosten oder Reibungsverluste. Alle 10 Minuten.

Das Gold-Meme wird sich noch eine Weile halten, und das ist auch gut so. Die Menschen sind nostalgisch, besonders wenn sie in ihren Gewohnheiten verhaftet sind. Wie bei wissenschaftlichen Revolutionen wird sich die monetäre Revolution, die derzeit im Gange ist, wahrscheinlich langsam verbreiten: eine Beerdigung nach der anderen.
Ich glaube jedoch, dass Bitcoin die Macht hat, die Köpfe und Herzen der Menschen sehr schnell zu gewinnen, wenn diese Köpfe offen oder kulturell angepasst genug sind; oder wenn die Veränderung in ihrem Umfeld drastisch genug ist.
Politik vs. Kultur
Kehren wir zu der Behauptung zurück, dass "du in der Kryptographie keine Lösung für politische Probleme finden werden". Ich habe bereits erwähnt, dass ich dem nicht zustimme, und hier ist der Grund. Politik ist der Kultur nachgelagert, und Kryptographie im Allgemeinen (und Bitcoin im Besonderen) verändert die Kultur.
Das sollte jedem außer dem blindesten Beobachter des Bitcoin-Bereichs sonnenklar sein. Die Kultur rund um Bitcoin ist durchdrungen von Verantwortung und Selbsteigentum („besitze deine eigenen Schlüssel" & „nicht deine Schlüssel, nicht dein Bitcoin"), Verifizierung und Schlussfolgerungen aus ersten Prinzipien ("vertraue nicht, verifiziere"), langfristigem Denken und Sparen für die Zukunft ("bleibe bescheiden, staple Sats"), sowie einem Fokus auf harte Arbeit, Integrität, Wahrheit und sichtbare Ergebnisse ("Proof-of-work, der Arbeitsnachweis").
Satoshi erkannte in wahrer Cypherpunk-Manier, dass Memes implementiert werden müssen, um sich möglichst effizient zu verbreiten, weshalb er sich hinsetzte und den Code schrieb. Es war auch der erste Test für die Tauglichkeit seiner Ideen, wie er in einem seiner vielen Forenbeiträge erwähnte: „Ich musste den ganzen Code schreiben, bevor ich mich selbst davon überzeugen konnte, dass ich jedes Problem lösen kann, und dann habe ich das Whitepaper geschrieben."
Das ist der Arbeitsnachweis, genau da. Das ist Anti-Fiat. Nicht nur darüber reden, sondern es auch tun. Mit gutem Beispiel vorangehen. Nicht nur über die Ideen spekulieren, die man im Kopf hat, die Memes, die man in der Welt verbreitet sehen möchte, sondern sie auch umsetzen. Das heißt, sie an der Realität zu messen.
„Lass deine Memes keine Träume sein."
Satoshi (paraphrasiert)
Ist es eine Überraschung, dass sich Bitcoin in den Bereichen „gesunde Ernährung", „gesunde Landwirtschaft", „freie Meinungsäußerung und Menschenrechte ausbreitet? Dass Bitcoin schnell und einfach von Menschen verstanden wird, die buchstäblich nahe am Boden sind, verbunden mit der grundlegenden Realität der Dinge? Ist es eine Überraschung, dass Bitcoin von denjenigen genutzt und verstanden wird, die es am meisten brauchen? Von denjenigen, die in Ländern leben, in denen das Geld versagt? Von denjenigen, die vom Fiat-System abgelehnt werden?
Das sollte keine Überraschung sein. Einige Kulturen haben eine natürliche Überschneidung mit der Bitcoin-Kultur, und es sind diese Kulturen, die Bitcoin zuerst annehmen werden. Frühe Beispiele sind die Cypherpunk-Kultur sowie die Kulturen rund um die österreichische Wirtschaft, den Libertarismus und das muslimische Finanzwesen. Wenn diese Kulturen Bitcoin annehmen, wird Bitcoin seinerseits diese Kulturen annehmen und dich beeinflussen. Ein für beide Seiten vorteilhafter Einfluss, wie er für alles, was langfristig überlebt, erforderlich ist, und wie er für die Symbiose, die die Natur darstellt, Standard ist. Der Organismus und das Umfeld, das durch die orangefarbene Münze und ihre Besitzer geschaffen wird, will überleben. Bitcoin: das egoistische Meme.
Natürlich gibt es auch Fiat-Meme. Es ist das, was unsere Kultur in den letzten 50 Jahren geprägt hat: „Fake it till you make it" und „YOLO" kommen mir in den Sinn, was interessanterweise die moderne Version der keynesianischen Idee ist, dass wir auf lange Sicht alle tot sind. Ist es verwunderlich, dass ein Umfeld, das durch falsches Geld geschaffen wurde, zu falschem Essen, falschen Körpern, falscher Gesundheit, falscher Medizin, falschen Beziehungen, falschen Experten und falschen Menschen führt?
Diejenigen, die an der Spitze der Fiat-Pyramide sitzen, sprechen von „nutzlosen Essern" und versuchen uns davon zu überzeugen, dass wir nichts besitzen müssen, aber trotzdem glücklich sein werden. Man muss sich über den Slogan wundern: „Du wirst nichts besitzen und du wirst glücklich sein".
„Du wirst ein glücklicher kleiner Sklave sein", heißt es in diesem Meme. Jemand hat beschlossen, dass Glück das ultimative Ziel ist, das es zu erreichen gilt, und du (und nur du) weißt, wie du es für dich erreichen können.

„Glück"
Als ob Glück das eigentliche Ziel wäre, das A und O, der Grund für unsere Existenz. Was ist mit dem Streben nach etwas Sinnvollem, etwas, das schwer ist, etwas, das Opfer erfordert, das Schmerz und Leid mit sich bringt?
\ „Jeder Mensch ist glücklich, bis das Glück plötzlich ein Ziel ist."
Oder was ist mit der Aussage von Lagarde, dass „wir glücklicher sein sollten, einen Arbeitsplatz zu haben, als dass unsere Ersparnisse geschützt sind?" Das ist Ausdruck eines bestimmten Memes, das sich in ihrem Kopf festgesetzt hat, des Mems, dass Arbeitsplatzsicherheit die meisten anderen Bedürfnisse übertrumpft und dass normale Menschen kein Vermögen anhäufen müssen. Schlimmer noch: Es suggeriert, dass es völlig in Ordnung ist, das zu stehlen, was normale Menschen durch fleißige Arbeit im Laufe ihres Lebens angespart haben.

Wir sollte glücklicher sein einen Job zu haben als das unsere Erparnisse geschützt werden. Christine Largarde Präsidentin der ECB, Oktober 2019
Es gibt einen Grund, warum wir vom „Rattenrennen" oder dem „Hamsterrad" sprechen und warum dieser Teil unserer Kultur in Kunst und Film so stark kritisiert wird. Um Tyler Durden zu zitieren: „Die Werbung bringt uns dazu, Autos und Klamotten zu jagen, Jobs zu machen, die wir hassen, damit wir Scheiß kaufen können, den wir nicht brauchen. Wir sind die mittleren Kinder der Geschichte, Mann. Wir haben keinen Sinn und keinen Platz. Wir haben keinen Großen Krieg. Keine Weltwirtschaftskrise. Unser großer Krieg ist ein spiritueller Krieg... unsere große Depression ist unser Leben. Wir sind alle durch das Fernsehen in dem Glauben erzogen worden, dass wir eines Tages alle Millionäre, Filmgötter und Rockstars sein werden. Aber das werden wir nicht. Und wir lernen diese Tatsache langsam kennen. Und wir sind sehr, sehr wütend."
Ich glaube jedoch nicht, dass die Menschen wütend sind. Ich glaube, dass die meisten Menschen deprimiert und nihilistisch sind. Sie sehen keinen Ausweg, sie sind hoffnungslos und haben sich mit ihrer Position im System abgefunden - ob bewusst oder unbewusst.
Nichts zeigt die Plackerei des Fiat-Rattenrennens besser als der kurze Animationsfilm „Happiness", der eine visuelle Reise durch die unerbittliche Suche des Menschen nach Erfüllung in der modernen Welt darstellt. Er setzt in Bilder um, was viele Menschen nicht in Worte fassen können. Hilflosigkeit, Sucht, Hoffnungslosigkeit. Eine Krise des Selbst, eine Krise des Sinns. Das Fehlen einer hoffnungsvollen Vision für die Zukunft.
„Ehrlich gesagt, ist es ziemlich deprimierend", so ein 44-jähriger Arbeiter, der allein im Wald festsitzt. „Ich habe versucht, einen Gedanken zu formulieren, ihn auszudrücken, ohne zusammenzubrechen und zu weinen. Aber ich bin mir nicht sicher, ob ich ihn weitergeben kann, ohne zu weinen."
„Mein Problem, einer der Gründe, warum ich hierher kommen wollte, war also, dass ich versuchen wollte, über den neuen Aspekt meines Lebens nachzudenken. Mit anderen Worten: nach den Kindern."
„Ein Mensch kann eine Menge Dinge ertragen, für jemanden, den er liebt. Die gleichen Dinge nur für sich selbst zu ertragen, ist nicht so einfach. Ich bin Elektriker. Man könnte meinen, das sei nicht so schwer, aber es sind viele sich wiederholende Aufgaben. Ich weiß, dass jeder seine eigene Arbeit hat, ich weiß, dass das einfach der Lauf der Welt ist. Aber für mich ist der Gedanke, dass ich weitere 15 Jahre meines Lebens damit verbringen muss, auf die Wochenenden zu warten, einfach eine Qual. Einfach nur die banale Qual des Ganzen..."
Schau dir bei Möglichkeit diesen Clip an. Es ist eine Sache, über das Meme des Rattenrennens zu theoretisieren; es ist eine andere Sache, einem erwachsenen Mann zuzusehen, der weinend zusammenbricht, nachdem er über sein Leben, das System, in das er eingebettet ist, und die Zukunft, die dieses System für ihn bereithält, nachgedacht hat. Nachdem er sich die Tränen weggewischt hat, spekuliert er darüber, was der Grund für seine depressive Stimmung sein könnte: „An diesem Ort kenne ich die Regeln. Es ist das Leben außerhalb dieses Ortes, das mich zum Weinen bringt."
Das ist es, nicht wahr? Regeln und Regeländerungen. Wenn du jemanden zutiefst deprimieren wollen, änderst du die Regeln, und zwar häufig. Zwingen du sie, etwas Sinnloses zu tun. Ändere die Regeln willkürlich. Das ist es, was die Menschen wirklich demoralisiert: in einem System willkürlicher Regeländerungen gefangen zu sein. Keine Hoffnung auf Stabilität und kein Ausweg.

Der Dritte Weltkrieg wird ein Guerilla-Informationskrieg sein, bei dem es keine Trennung zwischen militärischer und ziviler Beteiligung gibt. - Marshall McLuhan
Das Meme ist die Nachricht.
"Weißt du, jetzt habe ich es endlich verstanden. Über den Unterschied zwischen einem echten Krieg und einem globalen Guerillakrieg. Denn was wir jetzt haben, ist kein konventioneller Krieg mit scharfen Waffen. Mit militärischer Ehre, militärischen Rängen, militärischer Aktivität... Das ist ein Kulturkrieg. Wir haben die Unruhen. Wir haben die Unordnung. Und jetzt weiß ich wirklich, wie das funktioniert. Wenn die Unruhen vorbei sind, kann man nicht mehr sagen: „Ich habe mit Stolz gedient. Es spielt keine Rolle, auf welcher Seite man steht. Denn die Unruhen sind ein Krieg gegen den Stolz. Es ist ein Krieg gegen die Moral der Menschen. Man kann dem Feind nicht als Gleicher gegenübertreten. Jeder lebt im Schatten. Es ist immer verdeckt. Es ist immer gefälscht. Er ist immer erfunden. Und es kann keine Geschichte darüber geschrieben werden, weil alles abgeschottet ist."\ \ Bruce Sterling
Für die Geldpolitik gibt es im Fiat-System keine Regeln. „Die Regeln sind erfunden, und die Punkte sind egal", um Drew Carey zu zitieren. Die Realität hat Regeln, und wenn ein Fiat-System erst einmal aus dem Ruder gelaufen ist, dann ist es die Realität, die die Konsequenzen zieht, nicht das Fiat-System selbst.
Das Fiat-System ist kaputt; sein Geld ist wertlos; seine Kultur ist deprimiert und hoffnungslos. Wenn die Politik der Kultur nachgelagert ist, ist es dann eine Überraschung, dass unsere Politik größtenteils eine Clownshow ist, die nur auf Äußerlichkeiten und kurzfristige Ziele ausgerichtet ist? Wo gibt es Hoffnung in der hoffnungslosen Welt des fiat everything? Kaputte Ideen führen zu kaputten Umgebungen, die wiederum zu kaputten Organismen führen. Ist der Mensch erst einmal kaputt, wird er nicht in der Lage sein, seine Umwelt auf eine für alle Seiten vorteilhafte Weise zu verändern. Ganz im Gegenteil. Er wird in einer Abwärtsspirale aus Verzweiflung und Zerstörung feststecken und versuchen, „um jeden Preis" zu tun, was nötig ist.
Ohne Bitcoin sind die Aussichten für unsere Zukunft düster. Ohne Bitcoin hast du zwei Möglichkeiten: die schwarze Pille des Pessimismus oder das Soma des Nihilismus.
Es gibt einen Grund, warum die Leute sagen, dass Bitcoin Hoffnung ist.
Schwarze Pille vs. Orange Pille
Bitcoin ist Hoffnung, weil die Regeln von Bitcoin bekannt und stabil sind. Das Bitcoin-System ist wahnsinnig zuverlässig, funktioniert wie ein Uhrwerk, mit Regeln, die bekannt und in Stein gemeißelt sind. Es ist eine Umgebung mit eisenharten Zwängen, die ohne Herrscher durchgesetzt werden.
Es ist nicht nur das Gegenteil des Fiat-Systems, sondern auch sein Gegengift. Es ist nicht nur ein Rettungsboot, in das jeder einsteigen kann, der in Not ist, sondern auch ein Heilmittel, das Sinn und Optimismus gibt, wo es vorher keinen gab.
Es ist leicht, depressiv zu werden, wenn man die Übel des Fiat-Systems erkannt hat. Viele Bitcoiner, die heute von Optimismus erfüllt sind, waren hoffnungslos und fatalistisch, bevor sie die orangefarbene Pille schluckten. Viele Menschen sind es immer noch, Lionel Shriver und die meisten Goldfresser eingeschlossen.
Aber man muss bereit sein. Man kann sich nur selbst eine orangefarbene Pille geben, wie man sagt. Niemand kann dir Bitcoin aufzwingen.
Du müsstest eine Erleuchtung haben, dieselbe Erleuchtung wie unser 44-jähriger Elektriker im Wald, der über sein Leben nachdenkt. Kurz nach seinem Zusammenbruch und seinem Monolog darüber, dass er im Rattenrennen feststeckt, kommt er zu einer plötzlichen Erkenntnis: „Ich muss etwas ändern. Es ist nicht die Welt, die sich ändern muss. Es bin ich, der sich ändern muss. Es ist meine Einstellung zum Leben."
Ja. Was für ein Chad.
Das ist buchstäblich die Funktionsweise von Bitcoin.
Fiat Denkweise vs. Bitcoin Denkweise
\ Das Fiat-System wird nicht einfach verschwinden, und es wird auch nicht still und leise verschwinden. Zu viele Menschen sind immer noch mit dem Gedanken an leicht verdientes Geld infiziert, arbeiten in Scheißjobs und führen ein Fiat-Leben. Der Tod des Fiat-Organismus ist jedoch unausweichlich. Er ist selbstzerstörerisch, und wie alle Tiere, die in die Enge getrieben werden und am Rande des Todes stehen, wird er in einem letzten Versuch, das Unvermeidliche zu verhindern, um sich schlagen.

Piggies von artdesignbysf
„Unser großer Krieg ist ein spiritueller Krieg", wie Tyler Durden es so treffend formulierte. Und wir sind mittendrin in diesem Krieg.
Mit jedem Tag wird es offensichtlicher, dass dies ein geistiger Krieg ist. Ein Zusammenprall von Ideen, ein Kampf der unterschiedlichen Weltanschauungen.
Selbst der letzte Boss von Bitcoin, Augustin Carstens, weiß, dass dies ein Krieg ist. Warum sonst würde er, die Verkörperung des Fiat-Standards, im Fernsehen auftreten und Folgendes sagen?
„Vor ein paar Jahren wurden Kryptowährungen als Alternative zu Papiergeld dargestellt. Ich denke, diese Schlacht ist gewonnen. Eine Technologie macht noch kein vertrauenswürdiges Geld."
Augustin Carstens
Wenn wir uns nicht in einem memetischen Krieg befänden, warum wäre es dann notwendig zu erklären, dass eine Schlacht gewonnen wurde?
Wenn wir uns nicht mitten in einem spirituellen Krieg befinden würden, warum würde Christine Lagarde, eine Person, die wegen Fahrlässigkeit und Missbrauchs öffentlicher Gelder verurteilt wurde - eine Person, die jetzt Präsidentin der Europäischen Zentralbank ist - öffentlich erklären, dass wir Bitcoin auf globaler Ebene regulieren müssen, denn „wenn es einen Ausweg gibt, wird dieser Ausweg genutzt werden?"
Warum würde Stephen Lynch behaupten, dass Bitcoin „auf Null gehen wird, wenn wir ein CBDC entwickeln, das den vollen Glauben und Kredit der Vereinigten Staaten hinter sich hat?"
Warum würde Neel Kashkari, verrückt wie er ist, vor eine Kamera treten, um das Mem zu verbreiten, dass „es unendlich viel Bargeld in der Federal Reserve gibt", in der Hoffnung, dass diese Aussage das Vertrauen in das zusammenbrechende Fiat-System stärken würde?

Es ist fast unmöglich, sich diese Interviews anzusehen, ohne den Kopf zu schütteln. Glauben diese Menschen wirklich, was sie sagen? Ist es Böswilligkeit oder ist es Unwissenheit? Oder ist es einfach ein Auswuchs der verzerrten Weltsicht des Fiat-Verstandes? Sind diese Menschen nicht mehr zu retten, oder könnte Bitcoin sie sogar demütigen und sie auf den Pfad der Verantwortung und der Finanzdisziplin bringen?
Wie auch immer die Antwort lauten mag, die bloße Existenz von Bitcoin ist eine Beleidigung für ihr Denken, oder für jedes Fiat-Denken, was das betrifft. Bitcoin setzt die Idee außer Kraft, dass Geld vom Staat geschaffen werden muss. Seine Architektur sagt: „Jeder sollte Zugang zum Geldsystem haben". Sein Design sagt: „Wir sehen, was ihr getan habt, Fiat-Leute, und wir werden dem ein Ende setzen."
„Die Existenz von Bitcoin ist eine Beleidigung für den Fiat-Verstand."
\ Es ist ironisch, dass das, was die meisten Fiat-Leute zuerst sehen, die Schlachtrufe der Bitcoiner sind, die „HODL!" schreien und „wir werden euch obsolet machen" von den Dächern schreien. Du übersiehst die tiefere Wahrheit dieser Memes, die Tatsache, dass diese Meme der tiefen Überzeugung entspringen, dass ein mathematisch und thermodynamisch gesundes System einem politischen System vorzuziehen ist. Sie hören weder das Brummen der ASICs, noch achten sie auf die gültigen Blöcke, die unaufhörlich eintreffen. Alle 10 Minuten wird leise geflüstert: „Du sollst nicht stehlen."
Das laute und prahlerische Oberflächenphänomen lässt sich leicht ins Lächerliche ziehen und abtun. Der zutiefst technische, wirtschaftliche und spieltheoretische Organismus, der die 21 Millionen zustande bringt, nicht so sehr. Beide sind im Wachstum begriffen. Beide sind miteinander verwoben. Das eine kann ohne das andere nicht existieren.
Fiat-Selbst vs. Bitcoin-Selbst
\ Beim ersten Kontakt wird der Bitcoin von den meisten abgetan. In einer Welt, die vom Fiat-Standard beherrscht wird, sind die meisten Menschen nicht in der Lage, die orangefarbene Münze zu verstehen, wenn sie zum ersten Mal über sie stolpern. Ich denke, man kann mit Sicherheit sagen, dass die meisten Bitcoiner es nicht sofort „verstanden" haben. Ich habe es anfangs sicherlich nicht verstanden.
Die Reise vieler Bitcoiner lässt sich wie folgt zusammenfassen:
- Was zum Teufel ist das?
- Was zum Teufel ist das?
- Was zur Hölle?
- Die Scheiße?
- Scheiße...
- All in.
Der Prozess des Verstehens und der Annahme von Bitcoin ist der Prozess des Verlassens deines Fiat-Selbst hinter sich. Man muss die Fiat-Memes aus dem Kopf bekommen und die Bitcoin-Memes hineinlassen. Du musst dein Fiat-Selbst ausbrennen und dein Bitcoin-Selbst aufbauen. Tag für Tag, Aktion für Aktion, Block für Block.
Indem du am System der Fiat-Schuldensklaverei teilnimmst, verstärkst du das Meme der sofortigen Befriedigung, der Diskontierung der Zukunft für die Gegenwart, des falschen Geldes und des kurzfristigen Denkens. Indem du am Bitcoin-System teilnimmst, stärkst du das Mem des gesunden Geldes, des unelastischen Angebots, des langfristigen Denkens, der Verantwortung und der unveräußerlichen Eigentumsrechte.
„Man kann die Revolution nicht kaufen. Man kann die Revolution nicht machen. Du kannst nur die Revolution sein. Sie ist in deinem Geist, oder sie ist nirgendwo." - Ursula K. Le Guin
Verstehe mich nicht falsch. Es ist nichts falsch daran, in den Fiat-Minen zu arbeiten und bescheiden Sats zu stapeln. Es ist eines der wichtigsten Dinge, die du tun kannst. Das Stapeln von Sats gibt dir Freiheit, Kontrolle und Selbstständigkeit. Es ermöglicht dir, sich in eine Position der Stabilität und Stärke zu manövrieren, und ehe du dich versiehst, wird der einfache Akt des demütigen Stapelns und der Liebe zu deinem zukünftigen dich selbst verändern.
Der wahre Kampf ist ein persönlicher Kampf. Den Drang zu unterdrücken, etwas umsonst haben zu wollen. Die Gewohnheit der sofortigen Befriedigung aufzugeben und eine Kultur des langfristigen Denkens aufzubauen. Ablehnung von impulsiven Ausgaben, Akzeptanz von Opfern und Einschränkungen.
Die Beziehung zwischen Ihnen und der Welt ist transaktional, wie John Dewey uns lehrte. Nicht nur unsere physischen Körper sind an unsere physische Umgebung gebunden, sondern wir sind auch über die ebenso reale wirtschaftliche Umgebung, an der wir uns beteiligen, miteinander verbunden. Und mit jedem Dollar, den wir ausgeben, und jedem Satoshi, den wir sparen, erschaffen wir unsere Zukunft.
Es gibt eine Weggabelung. Das Schild auf der einen Seite sagt: „Du wirst nichts besitzen und du wirst glücklich sein". Das Schild auf der anderen Seite sagt: „Du wirst Bitcoin besitzen und du wirst die beste Version deiner selbst sein."

Die Wahl liegt bei dir.
Bitcoin hat die Macht, die beste Version von sich selbst hervorzubringen, weil die Anreize von Bitcoin auf gegenseitige Verbesserung ausgerichtet sind. Auf individueller Ebene erfordert der Besitz von Bitcoin eine Änderung der Zeitpräferenz und der Verantwortung. Der Besitz impliziert, dass man seine eigenen Schlüssel besitzt. Wenn du das nicht tun, besitzts du keine Bitcoin, sondern Schuldscheine. Es bedeutet auch, dass du deinen eigenen Knotenpunkt betreiben, um zu überprüfen, ob du tatsächlich Bitcoin besitzen. Wenn man das nicht tut, vertraut man auf das Wort eines anderen, verlässt sich auf seine Sicht von Bitcoin, seine Weltsicht und darauf, dass er einen nicht anlügt.
Darüber hinaus bedeutet der fortgesetzte Besitz von Bitcoin, dass man die Verantwortung übernimmt, einen Wert für die Gesellschaft zu schaffen. Geld tut nichts anderes, als zu zirkulieren, also musst etwas leisten, das andere Menschen als wertvoll empfinden. Wenn du das nicht tust, wirst du bald keine Bitcoin mehr haben. Die Natur wird dich dazu zwingen, dich von deinen Sats zu trennen, denn jeder - auch du - muss essen.
„Beschäftige dich mit dem Sinn des Lebens, wirf leere Hoffnungen beiseite, engagiere dich für deine eigene Rettung - wenn du dich überhaupt um dich selbst kümmerst - und tue es, solange du kannst."\ \ Marcus Aurelius
Der Bitcoin-Weg ist kein einfacher Weg, aber ein erfüllender. Er ist erfüllend, weil du die Regeln kennst, du kennst die Konsequenzen, und du hast die Verantwortung. Es ist ein Weg, der es dir erlaubt, dein Leben so zu gestalten, wie du es für richtig hältst, aber du musstes auch selbst gestalten. Es ist ein Weg, der es dir ermöglicht, sich vor Übergriffen und Diebstahl zu schützen, und der langfristige Sicherheit und Stabilität bietet. Aber du musst ihn gehen. Du musst mitmachen. Du musst ihn ausleben.
Du musst dein Fiat-Selbst ausbrennen und die einfachen Antworten, die Abkürzungen und den Scheinwert hinter dir lassen. Du musst etwas Reales anbieten, jemand Reales sein und im Falle des Scheiterns die realen Konsequenzen tragen.
Die Grenze zwischen Gut und Böse verläuft nicht nur in jedermanns Herzen, sondern auch die Grenze zwischen Fiat und Bitcoin verläuft ebenfalls in jedermanns Herzen. Es geht nicht um „wir gegen sie". Es geht um unser Fiat-Selbst gegen unser Bitcoin-Selbst. Persönliche Verantwortung vs. vorsätzliche Ignoranz. Systemische Fragilität vs. langfristige Stabilität. Mit jeder Handlung triffst du eine Entscheidung, und du hast keine andere Wahl als zu handeln.
Es gibt eine Weggabelung, und jeder Einzelne von uns muss sich entscheiden, welchen Weg er einschlagen will. Den scheinbar bequemen Weg, den die Machthaber vorgeben, oder den Bitcoin-Weg: hart, steinig, mit Höhen und Tiefen, ohne Sicherheitsnetze und ohne Rettungsaktionen. Es ist kein einfacher Weg, aber es ist ein schöner Weg. Ein Weg, der Geduld, Verantwortung und Disziplin lehrt. Ein Weg, der dich demütig macht. Ein sinnvoller Weg. Ein Weg, den zu gehen sich lohnt.
Früher war es ein einsamer Weg, aber das ist er nicht mehr. Früher war es ein verrückter Weg. Heute ist der Weg zu mehr Freiheit der verrückte Weg. Es ist ein langer Weg, ein täglicher Kampf. Und niemand außer dir kann diesen Weg gehen. Ich würde dir gerne sagen, dass ich dich auf dem Gipfel treffe, aber ich fürchte, es gibt keinen Gipfel. Ich treffe dich stattdessen auf dem Weg.

Gigi ist ein professioneller Shitposter und Meme-Kenner. Er ist vor kurzem aus der woken Höllenlandschaft der Vogel-App in das lila gelobte Land des Straußen-Protokolls umgezogen. Wenn er nicht gerade Shitposting betreibt, ist er meistens damit beschäftigt, ein Bitcoin-Genießer zu sein und seine Pflaumen im Glanz der orangefarbenen Münze zu baden. Du kannst ihn herbeirufen, indem du seinem npub in den Kartenschlitz eines stillgelegten Geldautomaten flüsterst:
npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
-
 @ 04ea4f83:210e1713
2025-05-01 17:59:51
@ 04ea4f83:210e1713
2025-05-01 17:59:51In nicht allzu vielen Jahren wird die Zahl der Bitcoiner in den Vereinigten Staaten von Amerika zehn Millionen überschreiten. Wenn wir diesen Meilenstein erreichen, ist das Spiel vorbei: Bitcoin gewinnt.
Mein Lieblingsautor und -denker, Nassim Nicholas Taleb, schrieb in seinem Buch Skin in the Game über "die unnachgiebige Minderheit". Das Konzept funktioniert folgendermaßen: Auf fast allen verpackten Lebensmitteln, die in den USA verkauft werden, ist außen ein kleines U in einem Kreis aufgedruckt. Nur sehr wenige US-Bürger benötigen die durch dieses U gekennzeichnete Koscher-Zertifizierung, aber für die Lebensmittelhersteller ist es einfacher, nicht für jedes Produkt zwei separate Versionen zu produzieren, so dass sie im Allgemeinen alles koscher machen. Nach Taleb gilt die Regel: „Ein koscherer Esser wird niemals nicht-koschere Lebensmittel essen, aber einem nicht-koscheren Esser ist es nicht verboten, koscher zu essen."
„Bei den meisten beobachteten komplexen Systemen liegt der Anteil der Minderheit, der erforderlich ist, um die Bevölkerung von ihrer unnachgiebigen Meinung abzubringen, in der Größenordnung von 3 bis 4%. Bei einer US-Bevölkerung von 325 Millionen sind 3% 10 Millionen." - Nassim Nicholas Taleb
Ein Fintech-Fonds, der seit 2012 im Bitcoin-Bereich tätig ist, hat kürzlich eine intensive Analyse durchgeführt, die zur besten Schätzung des Bitcoin-Besitzes geführt hat, die ich kenne. Nur 7 Millionen Menschen weltweit haben einen Wert von 100 Dollar oder mehr im Bitcoin-Protokoll gespeichert. Um die Zahlen zu runden, nehmen wir an, dass die Hälfte dieser Menschen in den USA lebt und dass ein Siebtel von ihnen einen höheren Wert als $2500 in BTC speichert. Das sind gerade einmal 500.000 US-Bürger mit einer bedeutenden Menge an Bitcoin. Und wie viel Prozent davon verstehen und interessieren sich tatsächlich so sehr für Bitcoin, dass sie dafür kämpfen würden? Lass uns großzügig sein und sagen wir 20%.
Es gibt ungefähr 100.000 Bitcoiner in den Vereinigten Staaten. Das bedeutet, dass wir eine 100-fache Steigerung benötigen, um das Niveau einer "unnachgiebigen Minderheit" zu erreichen. Das ist der Grund, warum die Akzeptanz alle anderen Prioritäten für Bitcoin dominiert.
„Bitcoiner haben bereits so viele potentielle Angriffsvektoren ausgeschaltet und so viel FUD gehandhabt, dass es nicht mehr viel Abwärtsrisiko für Bitcoin gibt." - Cory Klippsten
Ein weiteres Konzept, auf das sich Taleb in den fünf Bänden seines Incerto bezieht, ist: Schütze dich vor dem Abwärtsrisiko. Bitcoiner haben bereits so viele potentielle Angriffsvektoren ausgeschaltet und so viel FUD gehandhabt, dass es nicht mehr viel Abwärtsrisiko für Bitcoin gibt. Aber es gibt ein gewisses Risiko, egal ob man es mit unter 1%, unter 10% oder mehr beziffert. Und der bei weitem bedrohlichste Angriffsvektor wäre meiner Meinung nach eine konzertierte Aktion der US-Regierung auf vielen Ebenen, die versucht, Bitcoin auszurotten, um die Hegemonie des Dollars auf der ganzen Welt zu erhalten.
Um es klar zu sagen: Bitcoin würde selbst den konzertiertesten und bösartigsten Angriff der US-Regierung überleben. Er könnte sogar gedeihen, im Stil von Antifragile (ein weiteres Buch von Taleb), mit Menschen auf der ganzen Welt, die massenhaft Sats kaufen, wenn sie sehen, wie der frühere Hegemon ausschlägt. Es könnte aber auch anders kommen, mit einem massiven Rückgang der Netzwerkaktivität und des gespeicherten Wertes, mit Tausenden von Menschenleben, die irreparabel gestört werden, und mit einer Verzögerung unserer leuchtend orangenen Zukunft um Jahrzehnte oder länger.
Das ist für mich nicht hinnehmbar. Deshalb habe ich mein Leben der Rekrutierung der anderen 99% unserer unnachgiebigen Bitcoiner-Minderheit hier in den Vereinigten Staaten gewidmet. Es gibt bereits 100.000 von uns. Helfe mit, die anderen 9,9 Millionen zu rekrutieren.
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ 318ebaba:9a262eae
2025-05-01 17:34:40
@ 318ebaba:9a262eae
2025-05-01 17:34:40Longform ohne Überschrift
bold
italic
++underline++
~~durchgestrichen~~
- der Editor ist gut
- wirklich spitze
ein Zitat zweite Zeile
--- drei Bindestriche
code bloggsGanz lang Mehrere Zeilen| Head | Head | | --- | --- | | Data | Data |
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 4ba8e86d:89d32de4
2024-10-08 15:50:58
@ 4ba8e86d:89d32de4
2024-10-08 15:50:58Ele foi desenvolvido pela Beowulf Blockchain, uma empresa que é conhecida por suas soluções seguras e confiáveis de blockchain e criptografia.
A autenticação em duas etapas é um processo que adiciona uma camada extra de segurança ao login em uma conta online. Em vez de depender apenas de uma senha, o 2FA exige uma segunda forma de autenticação, geralmente um código enviado para um dispositivo móvel ou gerado por um aplicativo. Isso ajuda a garantir que apenas o proprietário da conta possa acessá-la.
A história do Aegis Authenticator remonta ao início dos anos 2000, quando a autenticação em duas etapas começou a ser amplamente adotada para proteger contas online. Desde então, houve vários casos de violação de segurança em grandes empresas, incluindo Yahoo, Equifax e Marriott, que expuseram informações pessoais de milhões de usuários. Como resultado, a segurança online se tornou uma preocupação crescente para indivíduos e empresas em todo o mundo.
O Aegis Authenticator funciona gerando códigos de autenticação em tempo real que mudam a cada 30 segundos. Esses códigos são usados em conjunto com uma senha para acessar uma conta online. O aplicativo suporta a autenticação com base em tempo e também com base em contagem, o que significa que ele pode ser usado com serviços que suportam ambas as opções.
O Aegis Authenticator possui recursos de backup e sincronização em nuvem para garantir que os usuários possam acessar suas contas em outros dispositivos, mesmo que o dispositivo original seja perdido ou roubado. O aplicativo utiliza criptografia de ponta a ponta para proteger as informações do usuário em trânsito e armazenadas na nuvem.
O Aegis Authenticator resolve vários problemas de segurança online, incluindo a prevenção de ataques de phishing e o aumento da segurança em contas com senhas fracas. Os códigos gerados pelo aplicativo são válidos apenas por um curto período de tempo, o que dificulta a utilização de um código roubado por um atacante. Além disso, o aplicativo é capaz de detectar automaticamente tentativas de phishing e alertar o usuário.
-
Baixe o aplicativo na loja de aplicativos do seu dispositivo móvel. https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis
-
Abra o aplicativo e clique em "Adicionar conta".
-
Selecione o serviço para o qual deseja configurar a autenticação em duas etapas.
-
Siga as instruções do serviço para vincular sua conta ao Aegis Authenticator. Isso pode envolver digitalizar um código QR com a câmera do seu dispositivo ou inserir um código de configuração manualmente.
-
O aplicativo irá gerar um código de autenticação em tempo real para sua conta, que muda a cada 30 segundos. Use esse código em conjunto com sua senha para acessar sua conta.
Com esses passos simples, você pode usar o Aegis Authenticator para proteger suas contas online e aumentar sua segurança digital Um próximo Passo seria adquirir um Yubico.
https://void.cat/d/KzX75b9AwikAGHiywPb3Su.webp
-
-
 @ 4ba8e86d:89d32de4
2024-10-07 23:19:19
@ 4ba8e86d:89d32de4
2024-10-07 23:19:19O Orbot é um aplicativo de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários da Internet. Ele funciona como um front-end para o Tor, permitindo que os usuários se conectem à rede Tor e usem serviços online de forma anônima e segura.
O Tor é uma rede de computadores que foi desenvolvida originalmente pelo governo dos Estados Unidos para proteger a privacidade dos usuários da Internet e permitir a comunicação segura de informações confidenciais. O Tor funciona usando um sistema de "onion routing" (roteamento de cebola), que envolve o encapsulamento de dados em várias camadas de criptografia antes de serem transmitidos através da rede.
O Orbot é um componente do Guardian Project, uma iniciativa que visa desenvolver tecnologia segura e anônima para ativistas de direitos humanos, jornalistas e outros usuários que precisam de privacidade online. O aplicativo é distribuído sob a Licença Pública Geral do GNU, o que significa que é totalmente gratuito e de código aberto.
O Orbot foi lançado pela primeira vez em 2008, como parte do projeto Tor, uma rede descentralizada de anonimização de tráfego que ajuda a proteger a privacidade dos usuários na internet. A ideia por trás do Orbot era fornecer uma maneira fácil para usuários móveis de acessar a rede Tor e proteger suas comunicações enquanto estavam em movimento. A primeira versão do Orbot foi lançada para o sistema operacional Android, e desde então, tem sido amplamente adotada por usuários preocupados com a privacidade.
O aplicativo inclui um proxy HTTP que permite conectar navegadores da web e outros aplicativos cliente HTTP na interface Tor SOCKS. Isso significa que todos os seus dados são criptografados e encaminhados através da rede Tor antes de serem transmitidos para o servidor de destino, tornando extremamente difícil para qualquer pessoa interceptar ou monitorar suas atividades online.
Além de fornecer anonimato e segurança aos usuários, o Orbot também pode ser usado para acessar conteúdo restrito por região. Por exemplo, se você está em um país que censura determinados sites ou serviços online, o Orbot pode ajudá-lo a acessar esse conteúdo de forma segura e anônima.
Os principais recursos do Orbot incluem a conexão segura à rede Tor, o acesso a serviços online restritos, o proxy HTTP, o código aberto e a facilidade de uso. Esses recursos tornam o Orbot uma ferramenta valiosa para usuários preocupados com a privacidade que desejam se comunicar e navegar na Internet de forma segura e anônima.
O Orbot é um aplicativo gratuito e de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários
Aqui está um passo a passo para instalar o Orbot em seu dispositivo Android:
-
Acesse a F-droid ou Google Play Store em seu dispositivo Android.
-
Selecione a opção "Iniciar" para iniciar a conexão com a rede Tor. Aguarde até que a conexão seja estabelecida. Isso pode levar alguns minutos, dependendo da velocidade de sua conexão com a internet.
- Depois que a conexão for estabelecida, você poderá navegar na internet de forma anônima e segura usando o Tor.
Lembre-se de que o uso do Tor não garante anonimato completo e pode ser necessário seguir outras medidas de segurança para proteger sua privacidade na internet. Além disso, o Orbot é apenas uma parte do ecossistema de segurança e privacidade e pode ser necessário utilizar outras ferramentas para garantir a segurança online.
https://github.com/guardianproject/orbot/stargazers
-
-
 @ bec0c9d3:c4e9cd29
2024-10-06 14:07:27
@ bec0c9d3:c4e9cd29
2024-10-06 14:07:27Hello, Free People!
Last weeks we were very productive. Our team has reached a higher level. Ideas, designs, workflow - you name it.
All of this to deliver you the best experience in the space. Where Open Source and Cypherpunk Ethos lead the way.
2140 COLLECTIVE alongside with CyphermunkHouse is proud to announce that Ours (Yours) festival will take place in LONDON / UK.
During Halloween/BitcoinWhitepaper weekend.
29.OCT - 03.NOV 2024
Please check BITCOIN CULTURE FESTIVAL '24 AGENDAPage for more updated info !
All of this will not be possible without YOU.If you want to join our crew, share some ideas, help, anything - feel free to contact us using the application forms, ready - waiting on the main page.
Forms are dedicated to Volunteers and Artists that can drop an Art for Phisical Gallery There will be also an Online auction that will display your art worldwide. Bitcoin pay only).
We are also prepered forms for #nostr panel speakers who want to present any #nostr project, freedom tools, etc. ART Panel Art, music, culture - stuff around our values, Bitcoin, and freedom, during friday and saturday events.
If you wanna share you bitcoin story to isnpire otheres we invite you to visit us on free #TootingMarket Day where we preper Open Mic. Let us know. On the market, which has already onboarded 20 Bitcoin merchants with food, drink, and veggy stalls, in beautiful London City.
Please check out forms - maybe you will be the one, inspired enough to share your knowledge , ideas , and spirit.
All tribes are welcome. . We will prepare space for you!
Also, if you believe in our ethos and mission and think it would be okay for you to support us, feel free to check our Sponsorship Packages. HERE
Any help is well appreciated!
As like a Cypherpunk's Movement, we truly respect our guests' privacy. Therefore, making pictures or video recordings will not be allowed during our events.

We will organize accreditation for professional photographers, so all good memories will be well documented.
We hope you will understand our values and respect this rule as well. #PrivacyMatters

To make a long story short. We are waiting for you in London. Be prepared for an Atomic Vibe Experience .
Be a part of the Peacefull Revolution. Remmember It always starts from YOU.
Subscribe to our newsletter on our page to stay informed and up-to-date. Help us spread the word by sharing the link using the share button.
Follow us also on all socials: NOSTREE.me - NOSTR LinkTree INSTAGRAM TWETTER - X YOUTUBE
LINKS
OUR PARNERS / SPONSORS

Hashtags
ArtGallery
ArtPanel
2140wtf
2140army
CyphermunkHouse
art
artstr
nostrart
craft
culture
music
bitcoin
nostr
TootingMarket
NostrLDN
NostrLondon
Foodst
Foodstrlondon
foodstrLDN
yakihonne
-
 @ 4d41a7cb:7d3633cc
2025-05-01 17:13:17
@ 4d41a7cb:7d3633cc
2025-05-01 17:13:17Did you know that Federal Reserve Notes (FRNs), commonly known as "us dollars" are broken contracts? In fact FRNs started as dollar IOUs and then the Federal Reserve (a private corporation) defaulted on its debts and made the U.S citizens pay the bill: effectively stealing the privately owned gold.
The United States Dollar
It is not that the dollar was "backed by gold" as it is commonly said. The dollar was primally a measure of weight of silver and then a measure of weight of gold. Let see a little history about the U.S dollar.
What does the constitution says?
Article I, Section 8:
This section grants Congress the power "to coin money, regulate the value thereof, and of foreign coin, and fix the standard of weights and measures."
Article I, Section 10:
"No State shall... make any Thing but gold and silver Coin a Tender in Payment of Debts."
The United States government, by decree, created the dollar as measure of weight defined by the Coinage Act of 1792 as 371.25 grains (24 grams) of silver.
The 1794 silver dollar, known as the "Flowing Hair dollar," was the first silver dollar coin produced by the United States Mint. This was the original dollar! The were minted in $1, $0,5.
 In 1795 the United States minted its first gold coins under the Coinage Act of 1792, which introduced the following denominations: $2,5, $5 and $10. The silver to gold ratio was fixed at 1:15, meaning 15 ounces of silver was the equivalent to one ounce of gold.
In 1795 the United States minted its first gold coins under the Coinage Act of 1792, which introduced the following denominations: $2,5, $5 and $10. The silver to gold ratio was fixed at 1:15, meaning 15 ounces of silver was the equivalent to one ounce of gold.Individuals could bring silver bullion to the U.S. Mint and have it coined into legal tender.
 ## Coinage acts
## Coinage actsThe Coinage Act of 1834 adjusted the gold-to-silver ratio to 16:1 and and the weight of the gold coins because gold was undervalue and encouraging the melting and exporting of American gold.
The coinage act of 1837 defined the silver dollar as containing 412.5 grains of standard silver (90% silver and 10% copper) and it reinforced the legal tender status of these coins, ensuring their acceptance for all debts, public and private.
The Coinage Act of 1849 specifically addressed the introduction of new gold denominations in response to the California Gold Rush, which significantly increased gold supplies in the United States. The Act authorized the minting of a $1 gold coin, the smallest gold denomination ever issued by the United States. The Act also authorized the creation of the $20 gold coin, known as the Double Eagle.
The gold dollar coin contained 23.22 grains of pure gold or 1.505grams or 0.0484 troy ounces.
 The Double Eagle contained 464.4 grains of pure gold or 30.093 grams, 0.968 troy ounces.
The Double Eagle contained 464.4 grains of pure gold or 30.093 grams, 0.968 troy ounces. The coinage act of 1857 sought to establish a uniform domestic currency and reduce reliance on foreign coins, demonetizing every foreign coins as legal tender. This was also the beginning of the Flying Eagle cent, which was smaller in diameter and composed of 88% copper and 12% nickel. This centralized more the coinage in the U.S.
The coinage act of 1857 sought to establish a uniform domestic currency and reduce reliance on foreign coins, demonetizing every foreign coins as legal tender. This was also the beginning of the Flying Eagle cent, which was smaller in diameter and composed of 88% copper and 12% nickel. This centralized more the coinage in the U.S.U.S Gold certificates
The Act of March 3, 1863, officially known as the National Bank Act, was a significant piece of legislation during the American Civil War aimed at creating a national banking system and establishing a uniform national currency.
This legislation allowed the U.S. Treasury to issue gold certificates, which served as a form of paper currency backed by gold. The introduction of gold certificates was primarily intended to facilitate transactions involving gold without the need for the physical transfer of the metal.
This was primary for large size comercial transactions or payments among banks.
1865 Series
 "It is hereby certified that one hundred dollars have been deposited with the assistant treasurer of the U.S in New York payable in GOLD at his office in the xxx New York "
"It is hereby certified that one hundred dollars have been deposited with the assistant treasurer of the U.S in New York payable in GOLD at his office in the xxx New York "The coinage act of 1873 also known as the "crime of 1873" was the intent to demonetize silver by ceasing the minting of silver dollars which meant that citizens could no longer bring silver to the mint to be coined into legal tender. By stopping the production of silver dollars, the Act implicitly placed the U.S. on a gold standard, where gold, not silver, was the primary basis for currency. This had lasting economic effects, particularly on farmers and silver miners who preferred bimetallism (the use of both gold and silver as standards).
The Act was controversial, particularly in western and rural areas where silver was a significant economic factor. Many believed that the Act was passed to benefit creditors and large financial interests by adopting a gold standard, which tended to deflate prices and increase the value of money.
The coinage act of 1878, The Act mandated the U.S. Treasury to purchase a specified amount of silver each month, between two million and four million dollars worth, and to mint it into silver dollars. This marked a partial return to the use of silver as currency through the coinage of the standard silver dollar. The Act allowed for the issuance of silver certificates, which could be used as currency in place of actual silver coins, thus easing the circulation of silver-backed currency.
The Bland-Allison Act was passed against a backdrop of economic depression and agrarian unrest. It represented a compromise between advocates of the gold standard and those wishing to return to bimetallism.
1882 series
 The 30 years of economic and political discourse between bimetallism supporters and gold only advocates finally ended in the 1900.
The 30 years of economic and political discourse between bimetallism supporters and gold only advocates finally ended in the 1900.The Gold Standard Act of 1900
The Gold Standard Act of 1900 formalized the monetary system of the United States by establishing gold as the sole standard for redeeming paper money and effectively ending the bimetallic standard. It established that the gold dollar would be the standard unit of value, equating the dollar to 25.8 grains of gold at a purity of 90%. Silver certificates and silver coins remained in circulation but without the backing of free and unlimited coinage.
Let's remember that the dollar was still a measure of gold. The certificates where government IOUs for that gold that was deposited in the treasury of the United States.
1907 series of gold certificates:

## The Federal Reserve Act of 1913
The Federal Reserva Act of 1913 created a monopoly over the issuance of the American paper currency. This marked the privatization of the currency and a centralization of power like never before. More about this in another article.
But essentially the secret agenda of banksters was to issue IOUs without any restriction and make the United State Government responsible to redeem this paper currency for gold. And I will show you exactly how. Alfred Owen Crozier wrote a book in 1912 one year before the bill was passed analyzing and opposing it and made this same argument.
Federal Reserve Notes
A paper contract, a promissory note, an "I owe you x amount"
This paper currency issued by this private central bank were dollar IOUs contracts or promissory notes.
According to Black's law dictionary a Federal Reserve note is: The paper currency in circulation in the United States. The notes are issued by the Federal Reserve Banks, are effectively non-interest-bearing promissory notes payable to bearer on demand, and are issued in denominations of $1, $5, $10, $20, $50, $100, $500, $1000, $5,000 and $10,000.
NON INTERES BEARING PROMISSORY NOTES.
A promissory note is a written, unconditional promise made by one party (the maker) to pay a definite sum of money to another party (the payee) or bearer, either on demand or at a specified future date. It is essentially a financial instrument representing a formal commitment to settle a specified monetary obligation.
Key Characteristics of a Promissory Note:
- Written Instrument: The promise to pay must be documented in writing.
- Unconditional Promise: The promise to pay cannot be contingent on any external factors or conditions.
- Definite Sum: The amount to be paid must be clearly specified and agreed upon in the note.
- Payee: The note must designate the person or entity to whom the payment is to be made either explicitly or implicitly by specifying it as payable "to bearer".
- Payable on Demand or at a Specific Time: The promissory note should indicate whether the payment is due upon demand by the payee or at a specific future date as agreed by the involved parties.
Promissory notes are commonly used in various financial transactions, including loans, business financing, and real estate deals, as they formalize the commitment to pay and can be enforced as a legal contract if necessary.
The Federal Reserve (FED) issued paper contract promising to be redeemable in gold. Most people never saw or understood the contract. Most never read it because the Fed cleverly hid the contract on the front of the bill by dividing it into five separate lines of text with a very different typeface for each line and placing the president's picture right in the middle. They even used the old lawyer's trick of hiding the most important text in small print.
Over time, the terms and conditions of the contract were watered down until they eventually became literally a promissory note for nothing. But let's analice how they did this step by step...
FEDERAL RESERVE NOTES: 1914 SERIES
 Content of the contract:
Content of the contract:Federal reserve note
The United States of America will pay to the bearer on demand: FIFTY DOLLARS
Authorized by federal reserve act of December 23, 1913
This note is receivable by all national and member banks and federal reserve banks and for all taxes, customs and other public dues. It is redeemable in gold on demand at the treasury department of the United States in the city of Washington district of Columbia or in gold or lawful money at any federal reserve bank.
So if a dollar was 20.67 per ounce, $50 could be exchanged for about 2.42 ounces of gold.
FEDERAL RESERVE NOTES :1918 SERIES
Content of the contract:
Federal reserve note
The United States of America will pay to the bearer on demand: Ten thousand dollars
Authorized by federal reserve act of December 23, 1913, as amended by act of September 26, 1918
This note is receivable by all national and member banks and federal reserve banks and for all taxes, customs and other public dues. It is redeemable in gold on demand at the treasury department of the United States in the city of Washington district of Columbia or in gold or lawful money at any federal reserve bank.
So if a dollar was 20.67 per ounce, $10,000 could be exchanged for 484.29ounces of gold.
Series of 1928
The great imitation
In 1928 the U.S government issued a new series of gold certificates payable to the bearer on demand.
 The same year the Federal Reserve issued it's own promissory notes copying the us government gold certificate's design:
The same year the Federal Reserve issued it's own promissory notes copying the us government gold certificate's design:Content of the contract:
Federal reserve note
The United States of America
will pay to the bearer on demand: One hundred dollars
Reedemable in gold on demand at the United States treasury, or in gold or lawful money, at any federal reserve bank.
So if a dollar was 20.67 per ounce, $100 could be exchanged for 4.84 ounces of gold.
Here's all the denominations issued by the Federal Reserve back then:
 This instrument was the facilitator of the Great depression, the inflation and deflation of the paper currency: as Thomas Jefferson warned long time ago:
This instrument was the facilitator of the Great depression, the inflation and deflation of the paper currency: as Thomas Jefferson warned long time ago:“If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.”
THE CONFISCATION OF GOLD
The end of the dollar and the replacement of gold and gold certificates by Federal Reserve Notes worthless paper currency.
Executive Order 6102, issued on April 5, 1933, by President Franklin D. Roosevelt, forced everyone to exchange their gold and gold certificates for federal reserve notes at $20,67 FEDERAL RESERVE NOTES per ounce.
THIS WAS THE END OF THE DOLLAR. THE END OF THE GOLD STANDARD. THE END OF THE CONSTITUTIONAL REPUBLIC FORM OF GOVERNMENT. THE END OF FREEDOM. THE ABANDONMENT OF THE CONSTITUTIONAL PRINCIPLES.
The Gold Reserve Act of 1934
This act further devalued the "gold content of the FRNs" and ended the redemption of gold certificates for gold coins. One ounce of gold was now "35 FRNs" in theory but this was not entirely true.
Lets analice the evolution of the Federal Reserve Notes.
 Content of the contract:
Content of the contract:Federal reserve note
The United States of America
will pay to the bearer on demand: One hundred dollars
THIS NOTE IS LEGAL TENDER FOR ALL DEBTS, PUBLIC AND PRIVATE AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY, OR AT ANY FEDERAL RESERVE BANK.
So if a dollar was 20.67 per ounce, $100 could be exchanged for one hundred dollars of Lawful money?
They eliminated the gold clause from the contract. This contract is a lie, what is this redeemable for? U.S treasuries? Different denominations of FRNs? They changed the definition of lawful money. This was never money this was a broken contract and it gets obvious in the next series...
1963 Series
This series look like they did photoshop on the "payable to the bearer on demand" part that was below franklin in previous series.
Content of the contract now was
Federal reserve note
The United States of America
THIS NOTE IS LEGAL TENDER FOR ALL DEBTS, PUBLIC AND PRIVATE.
ONE HUNDRED DOLLARS
Conclusion
Between 1913 and 1928 the dollar was gradually replaced by Federal Reserve Notes until in 1934 the gold standard was definitively abandoned. From that time the Federal Reserve Note became the "new legal tender money" replacing the dollar and slowly replacing silver coins too until in 1965 silver was definitively abandoned.
IT IS NOT THAT THE DOLLAR WAS “BACKED” BY SILVER OR GOLD.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins can be “money” in America. Since gold and silver coinage was heavy and inconvenient for a lot of transactions, they were stored in banks and a claim check was issued as a money substitute. People traded their coupons as money or “currency.” Currency is not money, but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution for the united States of America to issue currency of any kind, but only lawful money – gold and silver coin.
It is essential that we comprehend the distinction between real money and paper money substitute. One cannot get rich by accumulating money substitutes; one can only get deeper into debt. We the People no longer have any “money.” Most Americans have not been paid any “money” for a very long time, perhaps not in their entire life. Now do you comprehend why you feel broke? Now do you understand why you are “bankrupt” along with the rest of the country?
-
 @ 318ebaba:9a262eae
2025-05-01 17:11:41
@ 318ebaba:9a262eae
2025-05-01 17:11:41Flycat is nice 1. Handy 2. Smooth
-
 @ 4ba8e86d:89d32de4
2024-10-05 22:04:32
@ 4ba8e86d:89d32de4
2024-10-05 22:04:32Como funciona o PGP.
O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://nostrcheck.me/media/public/nostrcheck.me_5922365650718442651699905288.webp
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional.
https://nostrcheck.me/media/public/nostrcheck.me_1563316185075842071699905520.webp
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações.
https://nostrcheck.me/media/public/nostrcheck.me_6137622541655550851699909180.webp
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.
https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp
Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
https://nostrcheck.me/media/public/nostrcheck.me_4033165715613998201699910446.webp
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
https://nostrcheck.me/media/public/nostrcheck.me_2943209062439984111699910538.webp
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp
Figura 1-8. Anatomia de um certificado PGP
Distribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp
Figura 1-9. Um certificado PGP
Formato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
https://nostrcheck.me/media/public/nostrcheck.me_4125576093727079591699911294.webp
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
https://nostrcheck.me/media/public/nostrcheck.me_4681914789296468891699911522.webp
Figura 1-11. Confiança direta
Confiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
https://nostrcheck.me/media/public/nostrcheck.me_2764578291212045251699911580.webp
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
https://nostrcheck.me/media/public/nostrcheck.me_5284734693832771181699911783.webp
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 2ed3596e:98b4cc78
2025-05-01 17:01:26
@ 2ed3596e:98b4cc78
2025-05-01 17:01:26Our bounty program rewards Bitcoin Well Affiliates for making tutorials and Bitcoin Well walkthroughs. Make a video within our guidelines, share your post URLs (Youtube and X) and get paid over per video.
Each month we’ll have new bounty tasks with different tutorials available for you to make and earn sats. Click here to submit a Bitcoin Well bounty.
Bounty tasks and requirements for May 2025
For the month of May, the following bounty tasks will be available to approved Bitcoin Well Affiliates:
-
Buy bitcoin on-chain (Canada) – 63,000 sats
-
Requirements:
-
Buy walkthrough process: homescreen → buy page → e-transfer Q&A explained → review order → on-chain delivery explanation
-
Voice over guiding through each step
-
Mention OTC for Large purchases over $100k. Mention and include booking link in video description
-
Include affiliate webpage/referral link in video description
-
Uploaded to youtube and X/Nostr
-
-
Buy bitcoin via Lightning (USA) – 63,000 sats
-
Requirements:
-
Buy walkthrough process: homescreen → buy page → order form → bank funding and rate lock → order delivery expectations → confirm order
-
Voice over guiding through each step
-
Mention OTC for Large purchases over $100k. Mention and include booking link in video description
-
Include affiliate webpage/referral link in video description
-
Uploaded to youtube and X/Nostr
-
-
Pay bills on-chain (Canada) – 42,000 sats
-
Requirements:
-
Bill pay walkthrough process: homescreen → bill page → add a bill → bill pay order form → explain static bill pay address → confirm and review order → time to fulfill
-
Voice over guiding through each step
-
Include affiliate webpage/referral link in video description
-
Uploaded to youtube and X/Nostr
-
-
Recurring bitcoin buy (USA) – 105,000 sats
-
Requirements:
-
Recurring Buy walkthrough process: homescreen → buy page → order form → funding → date and frequency selection → order delivery expectations → confirm order
-
Voice over guiding through each step
-
Mention OTC for Large purchases over $100k. Mention and include booking link in video description
-
Include affiliate webpage/referral link in video description
-
Uploaded to youtube and X/Nostr
-
Please note that all requirements must be satisfied for a video to earn its bounty. Any questions about Bitcoin Well products details or bounty requirements can be directed to Konrad, Community Manager @ Bitcoin Well: k.fitz@bitcoinwell.com
Completed your bounty content and ready to earn your sats? Submit your bounty tasks here.
-
-
 @ 79dff8f8:946764e3
2025-05-01 16:48:55
@ 79dff8f8:946764e3
2025-05-01 16:48:55Hello world
-
 @ e968e50b:db2a803a
2025-05-01 16:46:13
@ e968e50b:db2a803a
2025-05-01 16:46:13Hey, are you familiar those scammy sites that will pay you to review companies? The line goes something like, "work from home and review products." Of course, the person is reviewing something online that they might not otherwise care about. When I look for reviews of a company, I'm almost always going to peer to peer type services.
Let's pause for a second for a seeming non-sequitur. Long story short, phone provider that I left has been charging me for an iPad that I accidentally didn't take off the plan. That's not the problem. The problem is that they made it IMPOSSIBLE to cancel this service, including going into a brick and mortar store. I'll spare you the details, but it took more than a full days work to get this thing cancelled. It was obvious that I wasn't even using the service, and it still cost me over a hundred bucks to square up after wasting so much of my life trying to get this thing cancelled on my account that supposedly didn't exist anymore.
Why is this relevant? I'm about to absolutely carpet bomb this company with bad reviews. They legitimately put significantly more work into trying to continue to charge me for this service I didn't want, didn't need, and didn't use, than they ever did trying to give me good service as a customer. When I started looking around online, I found a positive review I did about a flooring company two years ago...and wow! This review had so many great reviews. Beyond being amusingly recursive, it's real bad news for this phone company. I'm like a reviewing celebrity on this medium.
So...it occurred to me, what about a Trustpilot, BBB, or Angie's List type service that is fused with the sn news model? Put some skin in the game to review and put some skin in the game to endorse that review. stacker.reviews maybe?
Obviously, downzapping might not make sense there. Any company with a bad review could really hide their dirty laundry. But if they wanted to boost their good posts, plenty of safety mechanisms might make that costly (percentage of zaps going to website and boosts favored by numbers of zaps). I almost thought a review territory might make sense, but something like this would obviously need to be organized differently than a bulletin board.
I can imagine this being a good way to onboard people to bitcoin. Imagine it:
Wait, I can get some of these satoshi things for shouting to the rooftops about that plumber that saved my family's house?!? Hold my beer.
Wait, I can actually invest in this great review that warns people about that electrician?!?! Hold my warm beer.
idk Just a thought. I'm probably not the first person to think of this. Does it already exist? I got a humdinger of a harangue for it if so.
originally posted at https://stacker.news/items/968624
-
 @ 4ba8e86d:89d32de4
2024-10-05 21:04:30
@ 4ba8e86d:89d32de4
2024-10-05 21:04:30Em vez de compartilhar seu endereço de email real com serviços e sites que você usa, você pode criar um endereço de email temporário usando o Simplelogin. Esse endereço temporário é exclusivo para cada serviço ou site, permitindo que você gerencie sua caixa de entrada e reduza a quantidade de spam e emails não solicitados que você recebe.
O Simplelogin foi fundado em 2019 por dois desenvolvedores franceses, Nicolas Grenié e Anthony Castellanos, com o objetivo de oferecer aos usuários uma maneira fácil de criar endereços de e-mail descartáveis para proteger sua privacidade e segurança online.Em 2022, a empresa se juntou à família ProtonMail, uma empresa suíça conhecida por seus serviços de e-mail seguros e criptografados, permitindo que a Simplelogin expandisse seus recursos de segurança e privacidade, além de oferecer uma integração perfeita com o ProtonMail.
O SimpleLogin resolve vários problemas relacionados à privacidade e segurança online, incluindo:
-
Proteção da privacidade do seu endereço de e-mail: o SimpleLogin permite que você crie endereços de e-mail descartáveis que podem ser usados para se inscrever em sites ou serviços sem divulgar seu endereço de e-mail principal. Isso ajuda a reduzir a quantidade de spam e e-mails indesejados na sua caixa de entrada.
-
Proteção contra ataques de phishing: o SimpleLogin impede que os hackers obtenham seu endereço de e-mail real, reduzindo assim as chances de ser alvo de ataques de phishing.
-
Acesso seguro aos seus e-mails: o SimpleLogin oferece autenticação de dois fatores e suporte a PGP, garantindo que seus e-mails sejam protegidos contra invasões e leituras não autorizadas.
-
Maior controle sobre sua privacidade: o SimpleLogin permite que você crie e gerencie vários endereços de e-mail, controlando assim quais sites e serviços têm acesso ao seu endereço de e-mail principal. Além disso, o SimpleLogin permite que você exclua facilmente os endereços de e-mail descartáveis quando não precisar mais deles.
Alguns motivos pra usar SimpleLogin https://nostr.build/i/a243a8f7ebafa3e3f8c6f3942c69ce03315aaed70394deb4e31af50f82d098f5.jpg
-
Privacidade: O SimpleLogin protege sua privacidade online, permitindo que você crie endereços de e-mail descartáveis que não estão vinculados ao seu endereço de e-mail principal. Isso ajuda a reduzir o spam e a quantidade de e-mails indesejados que você recebe.
-
Segurança: O SimpleLogin oferece recursos de segurança avançados, como autenticação de dois fatores e suporte a PGP, ajudando a proteger seus e-mails de invasões e leituras não autorizadas.
-
Controle: O SimpleLogin permite que você crie e gerencie facilmente vários endereços de e-mail, controlando quais sites e serviços têm acesso ao seu endereço de e-mail principal.
-
Simplicidade: O SimpleLogin é fácil de usar e pode ser configurado em questão de minutos, sem a necessidade de conhecimentos técnicos avançados.
-
Integração com outros serviços: O SimpleLogin se integra facilmente com outros serviços, como o ProtonMail, permitindo que você gerencie todos os seus e-mails em um só lugar.
O Simplelogin é uma ferramenta essencial para manter sua privacidade e segurança online. Com a criação e gerenciamento de endereços de e-mail descartáveis exclusivos para cada site ou serviço que você utiliza, você pode reduzir significativamente a quantidade de spam e e-mails não solicitados em sua caixa de entrada. Além disso, o Simplelogin fornece uma proteção extra contra ataques de phishing e garante que seus e-mails sejam acessados de forma segura. Experimente o Simplelogin hoje mesmo e proteja sua privacidade e segurança online de maneira fácil e eficaz.
https://simplelogin.io/
https://github.com/simple-login/app
-




