-
 @ 3eba5ef4:751f23ae
2025-05-09 01:49:00
@ 3eba5ef4:751f23ae
2025-05-09 01:49:00加密洞见
取消 OP_RETURN 限制?引发比特币开发者激辩论
OP_RETURN 于 2014 年推出,允许将小块数据(如时间戳或短消息)包含在比特币交易中,作为在比特币链上存储有限信息的轻量级方式。出于防止垃圾信息的考虑,OP_RETURN 当前的大小限制是 83 字节。
Peter Todd 最近提议完全取消该限制。他认为该限制无法有效遏制滥用,反倒让事情更加复杂。因为它迫使一些开发人员采用各种变通方式——如使用 scriptsig 或不可花费输出(比如这里介绍了在无法花费的 Taproot 输出上存储数据的方式)——来存储媒体、垃圾信息和其他任意数据,这会导致 UTXO 集膨胀。
Pieter Wuille 同样主张 取消 OP_RETURN 限制。他认为,标准性策略并不太可能真正阻止那些由资金充足的组织创建的数据交易被确认——这些组织会将交易直接发送给矿工。此外,现在网络中的区块基本始终满载——即便是没有垃圾信息——因此 OP_RETURN 限制这样的规则已经没有效用。
总之,支持取消 OP_Return 限制一方的理由是,该限制是徒劳的,区块内已经有其它数据存储的替代方案。
反对该提案的一方则认为必须保留该限制,因为通过 OP_Return 存储任意数据违反了中本聪的初衷,也偏离了比特币作为金融网络的核心目的(Luke Dashjr)。其他反对意见包括: - 来自 Ocean Mining 的 @Mechanic:「开发者凭直觉就知道,不应用比特币来存储任意文件,而且应该尽一切可能让比特币难以用于这个目的。」 - Jason Hughes:「Bitcoin Core 开发人员即将合并一项将比特币变成毫无价值的山寨币的更改」……
了解争论中的更多观点,可以参考这里。
三种集群线性化技术比较
Pieter Wuille 在本文中比较了 SFL (spanning-forest linearization)、GGT 、CSS (candidate set search) 三种集群线性化技术之间的基本权衡,并跟进了每种技术的实现基准。
StarkWare 推出 ColliderVM:用于计算和桥接的 BitVM 替代协议
ColliderVM 是 StarkWare 研究的一个 BitVM 的替代协议,使用与 BitVM 相同的信任假设,但不需要欺诈证明,同时也能实现更广泛的功能,如智能合约和二层桥接。
相关论文:ColliderVM: Stateful Computation on Bitcoin without Fraud Proofs
相关视频:Bitcoin Horizons: from OP_CAT to Covenants
剑桥研究:比特币挖矿正使用超过 50% 的绿色能源
剑桥替代金融中心(CCAF)的一份新报告称,现在 52.4% 的比特币挖矿由绿色能源提供动力,其中 42.6% 来自水力和风能等可再生能源,9.8% 来自核能。比特币矿工正在通过减少化石燃料的使用和更好地管理硬件废物来改善他们的环境足迹。
精彩无限,不止于链
如何识破朝鲜黑客?Kraken 分享招聘经验
Kraken 团队最近发现一名朝鲜黑客试图通过申请工作,于是就如何在招聘流程每个阶段中识别并防范黑客分享了经验。
带回绕的轮次高效自适应安全门限签名方案
门限签名方案允许将一个签名密钥分发给 n 个用户,使得其中任意 t 个用户可以联合生成签名,但任意 t−1 个用户则无法做到这一点。研究者希望门限签名方案(Threshold Signatures)能具备自适应安全性,即在面对能够在交互后动态腐化诚实用户的对手时仍然保持安全。对于一类依赖带回绕(rewinding)证明的签名方案(如 Schnorr 签名),证明其自适应安全性是一个重大挑战。论文提出了两种在带回绕证明下可证明具备自适应安全性的门限签名方案。其安全性证明完全基于随机预言机模型(ROM),不依赖代数群模型(AGM)。
论文全文:Round-Efficient Adaptively Secure Threshold Signatures with Rewinding
以太坊如何简化 L1,实现对标比特币的简洁架构
Vitalik 近日发表 Simplifying the L1 ,建议简化以太坊 L1,从 EVM 迁移到 RISC-V(或其他最小 VM),采用「简单序列化」(Simple Serialize),仿效 Tinygrad 的简洁代码风格。
特别地,关于 RISC-V,Vitalik 认为这一转变会带来:
- 效率革命性提升:在 ZK 证明者内部,智能合约可直接执行,无需解释器开销。Succinct 数据显示,在多数场景下性能可提升百倍以上。
- 结构极致简化:RISC-V 规范相较于EVM 极为精简,其他候选方案(如 Cairo)同样具备简洁特性。
- 继承 EOF 的所有优势:包括代码分段管理、更友好的静态分析支持,以及更大的代码容量限制。
- 开发者工具链扩展:Solidity 和 Vyper 可通过新增后端编译支持新架构;若选择 RISC-V,主流语言开发者可直接移植现有代码。
- 消除对大部分预编译的要求:也许除了保留高优化的椭圆曲线运算外,大部分预编译功能将不再必要(而椭圆曲线也许也会随量子计算发展被淘汰)。
-
 @ a8d1560d:3fec7a08
2025-05-09 01:08:02
@ a8d1560d:3fec7a08
2025-05-09 01:08:02h1 🙂
h2 😈
h3 😴
h4 💩
h5 👾
h6 😺
codeblock 😮💨🤖😨😎😉🛹🧗🏻♀🥉🤸🏻♂️Further tests
😊🤩🥵🤪😥😈👽👈🏻👆🏻☝🏻👌🏻💋👧🏻👩🏻🦰👷🏻♀️🕵🏻♀️👩🏻⚕️👨🏻🚀🧛🏻♂🧝🏻♀🕴🏻👩👩👦🎩🧦
🐶🐧🐜🙈🦆🦐🐂🐇🐕🦺🐆🌱🌕🌗🌑🌓🌍🌎🌏⛈🌈 🫐🥨🥝🫛🍳🍧🥙🍺🍹🍷
🍏🍎🥥🥝🍯🍆🥜🥛🍺🧊🥢🧂
⚽🏑🤸🏻♀️⛳🚴🏻♀️🥇🥈🥉🎯🎮
🚗🚖🛟🚇🛶🚥🚧🏣🎇🌆🌄🌠🌁
⌚📀📺📸📡💎🪙💵💴💶💷(but no Bitcoin)🪙🛢⚱🩻🕳🛋🛍📁📂🗂📝🔓🔒🔏🔐
❤🧡💛💚🩵💙💜☮✝🕉☯🕎✡🆚☢㊙❌🔰〽🔞❎🌐🛃💤➡〰🔉🕚
🏳🏴🏴☠️🏁🚩🏳️🌈🇺🇸🇪🇺🇩🇪🇺🇦🇻🇦🇸🇻 -
 @ 502ab02a:a2860397
2025-05-09 01:07:20
@ 502ab02a:a2860397
2025-05-09 01:07:20ถ้าย้อนกลับไป 50 ปีก่อน ถ้าเฮียถามคำนี้กับลุงชาวนาคนหนึ่ง เขาคงหัวเราะแล้วตอบแบบไม่ต้องคิดว่า “ก็เจ้าของที่นาไงไอ้ทิด จะมีใครล่ะ?”
แต่พอมาในวันนี้ ถ้าเฮียถามคำเดิมในซูเปอร์มาร์เก็ต คงไม่มีใครกล้าตอบแบบนั้นอีกแล้ว เพราะแค่ในชั้นวางโยเกิร์ตเดียวกัน เฮียอาจเห็นยี่ห้อต่างกัน 10 ยี่ห้อ แต่ทั้งหมดอาจเป็นของบริษัทแม่เพียงเจ้าเดียว
ในศตวรรษที่ 21 อาหารไม่ใช่ของคนทำอาหาร แต่มันกลายเป็นของ บริษัทผู้ครอบครองข้อมูล พันธุกรรม และระบบการกระจายสินค้า โลกวันนี้ไม่ได้มีเกษตรกรล้อมวงเคี้ยวหมาก แต่มีบริษัทเทคโนโลยีจับมือกับนักลงทุนระดับโลก ถือครองเมล็ดพันธุ์ เป็นเจ้าของสิทธิบัตรจุลินทรีย์ในลำไส้ และมีอำนาจเสนอว่า “อาหารแบบไหนควรได้รับเงินสนับสนุนจากรัฐ”
บริษัทเทคโนโลยีในซิลิคอนแวลลีย์บางแห่ง ไม่ได้แค่ผลิตซอฟต์แวร์อีกต่อไป แต่เริ่มทำ "อาหารจากโค้ด" โปรตีนสังเคราะห์ที่ได้จากการแทรกยีน หรือแม้แต่ “อาหารจากคาร์บอนในอากาศ” ที่สร้างโดย AI เขาไม่ได้ปลูกข้าว แต่เขาเขียนสูตรให้เครื่องจักรสร้างอาหารในถัง
ใครมีสิทธิบัตร…คนนั้นคือเจ้าของ ใครควบคุมข้อมูลสุขภาพ…คนนั้นคือนายทุนแห่งความหิว และใครสามารถชี้นิ้วให้รัฐบาลเปลี่ยนนโยบายอาหารโรงเรียน…คนนั้นคือเจ้าของอนาคตของเด็กทั้งประเทศ
มันฟังดูเวอร์ใช่ไหม? แต่ลองดูดี ๆ…ใครเป็นเจ้าของฟาร์มหมู ฟาร์มไก่ โรงฆ่าสัตว์? หลายแห่งไม่ได้เป็นของชาวบ้านอีกต่อไป แต่เป็นของเครือบริษัทยักษ์ใหญ่ที่อยู่เบื้องหลังทั้งอาหารในซูเปอร์ และเม็ดวิตามินในกระปุกเฮียด้วย
ยิ่งไปกว่านั้น เจ้าของตัวจริงไม่ได้อยู่ในร้านของชำ แต่ซ่อนตัวอยู่ในบอร์ดบริหารบริษัทเกษตรข้ามชาติ ในเวทีประชุมเศรษฐกิจโลก และในห้องประชุมที่ตัดสินว่า “อาหารจากวัว” ควรถูกเก็บภาษีคาร์บอนเพิ่มหรือไม่
เมื่อก่อนเฮียเคยคิดว่า ถ้าเราปลูกผักเอง ก็คุมอาหารตัวเองได้ แต่พอระบบเริ่มขับไล่เมล็ดพันธุ์ดั้งเดิมให้สูญพันธุ์ ถ้าไม่มีใบอนุญาตปลูกพืช GMO หรือไม่มีเงินซื้อปุ๋ยจากบริษัทเดียวที่ยังอยู่รอด เกษตรกรจะเป็นเจ้าของอะไรกันแน่?
และคำว่า “อาหารอิสระ” ในยุคนี้ อาจไม่ใช่แค่การไม่พึ่งพาซูเปอร์ แต่มันคือ “การตื่นรู้ว่าใครเป็นคนจัดเกม และใครเป็นคนตั้งกฎ”
เพราะในยุคที่ทุกอย่างแปรรูปเป็นดิจิทัล แม้แต่อาหารก็อาจมีเจ้าของเพียงไม่กี่ราย และสิ่งที่น่ากลัวกว่าผูกขาด…คือการ “ผูกอนาคต” ของเราทั้งมื้อ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 5cb68b7a:b7cb67d5
2025-05-09 00:31:22
@ 5cb68b7a:b7cb67d5
2025-05-09 00:31:22In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back! 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞 For quick queries or support, connect with us on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust\ At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process\ Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate\ With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure\ Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools\ We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!\ Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back!\ 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
-
 @ c9badfea:610f861a
2025-05-09 00:06:23
@ c9badfea:610f861a
2025-05-09 00:06:23- Install LibreTorrent (it's free and open source)
- Search for torrents on various sources (see links below)
- Copy the torrent's 🧲️ Magnet Link
- Open LibreTorrent, tap the + icon, and select Add Link
- Paste the magnet link and tap Add
- The app will display the torrent's details and files; tap the ✓ icon to start the download
Some Sources
ℹ️ Magnet links start with
magnet:?ℹ️ Tapping a magnet link usually opens LibreTorrent automatically
⚠️ Using a VPN is strongly recommended
-
 @ 87f5e1d9:e251d8f4
2025-05-09 00:03:01
@ 87f5e1d9:e251d8f4
2025-05-09 00:03:01Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ c9badfea:610f861a
2025-05-08 23:06:09
@ c9badfea:610f861a
2025-05-08 23:06:09- Install VLC Media Player
- Open the app, navigate to More and tap New Stream
- Enter
https://iptv-org.github.io/iptv/index.m3uin the network address field and tap the arrow - Enjoy the global IPTV channel playlist
🔗️ Here is the stream URL as plain text: https://iptv-org.github.io/iptv/index.m3u
ℹ️ For playlists of specific countries, categories, or languages, visit IPTV-Org and see the Playlists section
ℹ️ You can find an overview of all available IPTV channels per country here
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-08 22:57:55
@ 5d4b6c8d:8a1c1ee3
2025-05-08 22:57:55Using a discussion style post to get better formatting on the nostr cross-post.
The Fed Leaves Fed Funds Rate at 4.5% as Economic Storm Clouds Gather
by Ryan McMaken
The Fed is now hemmed in by a rising risk of stagflation. It doesn’t know where the economy is headed, or is unwilling to take a position. At this point, “hope for the best” is Fed policy.
originally posted at https://stacker.news/items/975059
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 6fc114c7:8f4b1405
2025-05-08 22:55:57
@ 6fc114c7:8f4b1405
2025-05-08 22:55:57In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back! 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞 For quick queries or support, connect with us on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust\ At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process\ Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate\ With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure\ Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools\ We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!\ Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back!\ 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
-
 @ a5ee4475:2ca75401
2025-05-08 22:38:49
@ a5ee4475:2ca75401
2025-05-08 22:38:49list #foss #descentralismo
Nostr Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- DEG Mods - Decentralized Game Mods [info] [source] 🌐
- NG Engine - Nostr Game Engine [source] 🌐
- JmonkeyEngine - Java game engine [source] 🌐
Android
- Mindustry - Sandbox Tower-defence and RTS [source] 🤖
- SuperTuxKart - Mario Kart with Tux (linux penguin) [source] 🤖 | 🐧🪟🍎
- SolitaireCG - Solitaire Cardgames [source] 🤖
Rhythm
- Friday Night Funkin' - [source] [download] 🌐🐧🪟🍎
- Open Saber - Beat Saber VR like (requires a VR) [source] 🌐🐧🪟🤖
- RhythmAdventure - Osu! remake [source]
Voxel
- Luanti / Minetest - Minecraft-like voxel game and engine in Lua [info] [source]
- VoxeLibre / MineClone2 - Famous Luanti / Minetest mod [source] [source2]
- Veloren - Cubeword upgraded sandbox [source]
- Terasology - Minecraft-based vivid world [source]
- Reign of Nether - Minecraft RTS mod [source]
- Voxelands - [info] [source] [STOPED] 🐧🤖🍎
- New Fork: voxelands 🐧 *Voxelands ≠ Voxlands (closed source game)
Clone
- Pingus - Lemmings clone [source]
- FlappyBird - Flappy Bird clone [source]
Remake
- FreeDoom - Doom remake [source]
- Oolite - Elite remake [source]
- Q1K3 - Quake demake [source] 🌐
- AM2R - Metroid remake [source]
Inspired
- Boxhead2D - Single player top-down shooter based in the Boxhead 2Play 🐧🪟🍎
- Boxhead - Directx11 - Single player top-down shooter based in the Boxhead 2Play [source] 🌐
- OpenSuspect - Inspired by mafia and Among Us [source] 🐧🪟
- Xonotic - Inspired by Quake [source]
- Hedgewars - Inspired by Worms, but with hedgehogs [source]
- Secret Mayro Chronicles - Inspired by Super Mario [source]
- OpenRA - Communist strategy game inspired by Red Alert, Tiberian Dawn and Dune 2000 [source]
- OpenTTD - Based on Transport Tycoon Deluxe [source]
- AstroMenace - Spaceships shooter [source]
Strategy
- 0 A.D. - RTS [info] [source]
- Warzone 2100 - RTS [source]
- The Battle for Wesnoth - Turn-based fantasy strategy game [source]
FPS - First-Person Shooter
- Alien Arena - Fast-paced Sci-Fi FPS death match [info] [source] 🐧🪟🍎 [and FreeBSD 😈]
- Urban Terror - based on "total conversion" mod for Quake III Arena [info] [source] 🐧🪟🍎
- FreeHL - Rewrite of Half-Life: Deathmatch in QuakeC [source]
- FreeCS - Based in Counter-Strike 1.5 by FreeHL addon [info] [source] 🐧🪟🍎 [and FreeBSD 😈]
- Nexuiz Classic - retro deathmatch [source] 🐧🪟🍎
- AssaultCube - WWII layout [info] [source]
- OpenArena - clone of Quake III Arena [source]
- Warsow - Futuristic cartoonish world [source]
- World of Padman - Fun cartoonish shooter [info] [source] 🐧🪟🍎
- OpenSpades - A clone of Ace of Spades, with voxels, fully destructible terrain and plenty of game modes [source]
- Tremulous - Asymmetric team-based FPS with real-time strategy elements [source]
- Cube 2: Sauerbraten - A free multiplayer & single-player first-person shooter, the successor of the Cube FPS [info] [source]
- Quetoo (Q2) - old school death match [info] [slurce]🐧🪟🍎
- Red Eclipse 2 - sci-fi modern FPS arena [info] [source] 🐧🪟🍎
- BZFlag - Battle Zone capture the Flag game [info] [source] [source 2] 🐧🪟🍎
- The Darkmod [source] [source] [source 3]
- Wolfenstein: Enemy Territory - War as Axis or Allies in team-based combat
Original list with images in Medevel Website
Retro RPG
- Cataclysm: Dark Days Ahead - Post-apocalyptic survival - [source]
- Erebus - [source]
- FreedroidRPG - Tux against rebel bots [source]
- FreeDink - Dink Smallwood - Similar to classic Zelda [info] [source]
- Valyria tear - Based on the Hero of Allacrost engine [source]
- Fall of Imiryn [source]
- Hale - Tactical combat [source]
- IVAN: Iter Vehemens ad Necem - roguelike [source]
- Summoning Wars - 1 to 8 players [source]
- Flare - Action fantasy [source]
Educational
https://medevel.com/educational-games-26-993/
-
 @ a5ee4475:2ca75401
2025-05-08 21:57:12
@ a5ee4475:2ca75401
2025-05-08 21:57:12brasil #portugal #portugues #bitcoin
Brasil
-
Jericoacoara - Ceará nostr:nprofile1qqsdc47glaz2z599a7utq9gk2xyf6z70t7ddyryrnweyt32z4sdarfsppemhxue69uhkummn9ekx7mp00ex584
-
Rolante - Rio Grande do Sul nostr:nprofile1qqsdrks96vr7vc7frjflm8lmhwleslwzgjlkpyj4ahjhzgm4n8dh0qqprdmhxue69uhkymm4de3k2u3wd45ku6tzdak8gtnfdenx7qgcwaen5te0xycrqt3hxyhryvfh9ccngde6xsurgwqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduhxppd6
-
Santo Antonio do Pinhal - São Paulo nostr:nprofile1qqsr5maylee9j77ce0es6tgmxj3pax2dlsuuptkn2stuj95jzqysulgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqgdwaehxw309ahx7uewd3hkca6zsjl
Portugal
- Ilha da Madeira - nostr:nprofile1qqsv45qvfz5vdzwn9478wzusyggjf44x3w7xk8f3cgpe4px44wgv77cpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpz3mhxue69uhhyetvv9ujumn0wd68ytnzvuq32amnwvaz7tmwdaehgu3dwfjkccte9eshquqzhddc4
-
-
 @ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46
@ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46If you haven't noticed already, #Nostr is a little different from what most people are used to. One of the ways this is felt most acutely is with media hosting. Users are accustomed to uploading their images and videos directly through the app they are posting from. Many Nostr apps provide that same experience nowadays, but it wasn't always the case.
Just a couple years ago, users had to find somewhere to host their media separately, and then copy and paste the URL into their note whenever they wanted to share their cat pictures. One of the first, if not the first, media hosting services specifically intended for Nostr was nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7, which will be the service we are reviewing today.
Like our previous review of Amber, Nostr.Build is a service for users to pair with other Nostr apps. You won't generally use nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 by itself. Rather, you'll use it to host that incredible shot you want to post to #Olas, or to host screenshots for your long-form tutorial about setting up Nostr Wallet Connect that you'll be posting from #Habla.news, or for hosting a hilarious video of your cat falling asleep to nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u's voice and taking a tumble off of his favorite perch that you want to share on #Damus. However, there are some features within Nostr.Build that you may want to check out quite apart from using it with any other Nostr app.
Overall Impression
Score: 4.8 / 5
I have been impressed by Nostr.Build for some time now, but they have pulled out all the stops in their latest update, increasing their maximum file size for free accounts to 100MB, integrating the #Blossom protocol, adding the ability to share directly to Nostr from within your dashboard, and more integrations with other Nostr apps than ever before. Nostr.Build is simply a pleasure to use, whether through their web interface, or through another Nostr app that integrates with them.
With the ability to easily organize your media, view statistics, browse the media gallery of free uploads, metadata removal for increased privacy, and AI image generation, Nostr.Build is not simply a media hosting service, it is a full-fledged media management platform. Its robust features keep it well ahead of other Nostr-focused media hosting options available, and a particularly strong option for those using Blossom and wanting redundancy and reliable uptime for their media.
As much as I enjoy using the web interface, though, where Nostr.Build really shines is their integrations with other Nostr apps. These integrations allow users to have the same experience they are accustomed to from centralized social platforms of uploading their media from within the same app they are using to share it. No copy/pasting a URL from one app to another. In fact, many users may not realize they have been using Nostr.Build in their client of choice, simply because it is the default option for media hosting for many Nostr apps.
This has the added benefit to client developers that they can provide this experience to their users without having to run media hosting infrastructure on top of trying to build their app. The separation of relays, clients, and media hosting between different entities, while keeping a similar experience to centralized platforms where a single company controls all three, is critical to Nostr adoption.
Features
Nostr.Build has a plethora of features beyond simply hosting your media. Let's take a look!
AI Image Generation
Do you need a quick title image for a long-form article? How about inspiration for a logo or art piece? Nostr.Build's AI Studio has you covered.
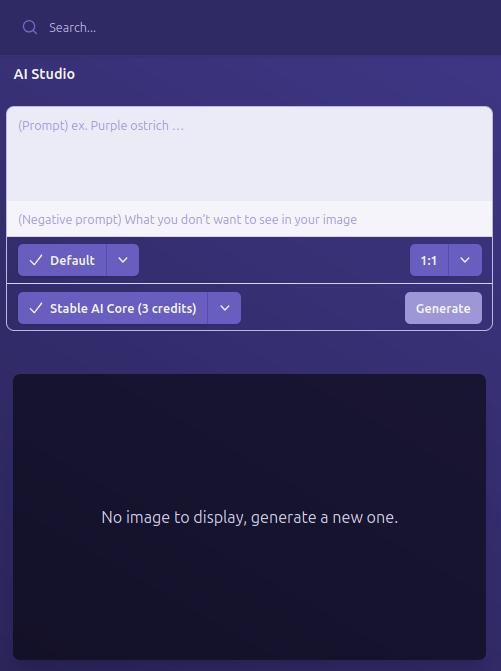
They have provided a few different models based on the plan you purchase, beginning with the Professional plan, which includes SDXL-Lightning and Stable Diffusion 1. Upgrading to the Creator plan will give you access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model, which is the same core model used for Grok2 images.
I personally have a Professional account, so I haven't had a chance to try out Flux.1, but I have used Stable Diffusion extensively for creating character art for #NostrHeroes characters, such as these:




Nothing too spectacular when compared with some of the newer models out there, and there is no image-to-image support (yet), but more than adequate for casual image generation needs. Moreover, it is far more than what one would expect from a simple media-hosting service.
Admittedly, I am also no expert at coaxing AI models to produce anything remarkable so your results may vary. Either way, image generation is a welcome tool to have available without needing to go to an outside service unless you require something very specific.
Upload Limits
The maximum file size limits on Nostr.Build have been getting progressively larger, even for their free service. As I recall, it was a mere 21MB limit per file just a few months ago, which is fine for image files, but is quickly exceeded with videos. Then they increased their limits to 50MB per file, and as of recent updates it has been increased once more to a whopping 100MB per file... for free! This is more than adequate for most uses.
However, free users' images, GIFs, and videos are automatically viewable via Nostr.Build's free media gallery. This is something to particularly bear in mind when uploading images you intend to share via direct message. Though your DMs are encrypted, the images uploaded to Nostr.Build are not, and if you don't have a paid account, they will be viewable to the all paid users in the free media gallery. If you want to upload images that will not be viewable unless you actively share them, you must have a paid account.
Paid accounts have no file size limit, but they do have a total storage limit. I could not find anything about total storage limits for free accounts, but Professional tier will give you 25GB, Creator 50GB, and Advanced 250GB. Uploads to paid accounts are not visible in the free media gallery, so only those you give the link to will be able to access your content.
Media Types
Many file types are supported by Nostr.Built, even for free users, including:
- Image: .jpg, .png, .gif
- Video: .mov, mp4
- Audio: mp3, .wav
Upgrading to the Professional plan will add .pdf and .svg to the list of permitted file types, and upgrading to Creator or above will add .zip files, as well.
I believe other common file types are also supported, but these are the only ones specifically mentioned on the site.
Free Media Gallery
The free media gallery is an interesting little feature that Nostr.Build has available to paid accounts. Free users can get a preview, such as the one below, but only paid users can browse through the millions of uploads made by free users.
Apart from being amusing to browse through the things people have been uploading, I am unsure of how useful this particular feature is. No indication is given as to who uploaded the media, and it is limited compared to media feeds in other Nostr apps in two important ways. First, it only shows media uploaded to Nostr.Build, while other media-focused Nostr apps, such as Slidestr, Lumina, or even Primal will show media posted by all Nostr users. Second, Nostr.Build's gallery doesn't show all uploads to Nostr.Build, but only uploads from those without a paid account, further limiting the scope of whose uploads are seen.
Paid users have the advantage of being able to upload media that is not viewable to anyone unless they intentionally share the link somewhere. Free users, on the other hand, must be aware that their uploads are viewable by any paid users, whether they shared the link anywhere or not.
One incident I had while testing out another app required me to reach out to Nostr.Build support to request deletion of an image. It had some of my personal information in it, and had been uploaded to Nostr.Build and sent to me via DM. The sender assumed that since it was being sent via DM, no one else would be able to see the image, but because he was not a paid user of Nostr.Build, the image was included in the Free Media Gallery for any paid user to see. Not ideal, but the folks at Nostr.Build were quick to get it deleted for me.
In short, I have mixed feelings about this particular feature.
Blossom
Blossom is a media storage and retrieval protocol built for Nostr, but usable with any application that needs to access media via the web, and Nostr.Build has recently added support for Blossom uploads via their Blossom server: blossom.band
I will likely be adding a Nostrversity article going over Blossom in detail in the near future, but here's the basics of what it makes possible:
First, easy integration for media uploading from your favorite Nostr apps. Amethyst, Coracle, Primal and others have added Blossom upload support, so you just have to hop into your settings and add Nostr.Build's Blossom server address to start using it as your media host. No need to go to a separate app to upload your media and copy/paste the URL into your Nostr note!
Second, your media in Blossom is content addressable. This means it is named based on a hash of its actual data. Because of this, you can verify that the media has not been altered or replaced by your media host. If the hash doesn't match the data, it won't be loaded by the Nostr client, so you never have to worry about the image in your note being replaced by a different image by your media host.
Finally, because your media is addressable by its content, you can save the same media to multiple hosts, and if one of them goes down, Nostr apps can fetch your media from other hosts, just like they can do with your notes by fetching them from different relays if one relay you write to is down. This makes your images and videos much harder to censor, since you would need to be banned by multiple Blossom servers for your media to no longer be accessible.
If you would like to upload media to more than one Blossom server at the same time, your options are currently to use Primal and ensure that your settings have "Enable media mirrors" toggled on, or to use Bouquet. Hopefully we will see this option added to more Nostr apps in the near future.
Metadata Stripping
For files uploaded via Nostr.Build's dashboard, location metadata is removed upon upload. This is to protect user privacy, since this data could be used to reveal your home address if it is left attached to images posted publicly on Nostr.
When uploading via Blossom, media containing location metadata will be rejected. The user will be required to remove the metadata before they can upload the media.
No KYC and No Ads Policy
The only form of identification needed to use Nostr.Build is your Nostr identity. Every upload is tied to your npub, but no name, date of birth, email, or other identifying information is required. This is made possible because Nostr.Build only accepts Bitcoin as payment for their accounts, and no KYC is required to make Bitcoin transactions via Lightning.
Additionally, Nostr.Build is philosophically opposed to targeted advertising, so they have a policy that they will never use ads on their hosting service.
Client Integrations
Even before Blossom, Nostr.Build had many Nostr clients that used it as the default media hosting service, allowing users to upload directly within the app. This has only expanded now that Nostr.Build has added Blossom.
A very non-exhaustive list of clients that integrate with Nostr.Build is listed on their site, and includes Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne. Additional apps that support Nostr.Build via Blossom include Primal and Flotilla. Some of these integrations support both Blossom and NIP-96 options for uploading media, such as Amethyst, while others only support one or the other.
I would not be surprised to see more and more Nostr apps move to integrating Blossom and phasing out NIP-96 support. Either way, though, Nostr.Build currently supports both, and is therefore an excellent hosting option if you want to use it with a wide range of Nostr apps.
Media Statistics
For those with a paid account, Nostr.Build provides information about how often each of your uploads has been requested and viewed within a given time period.
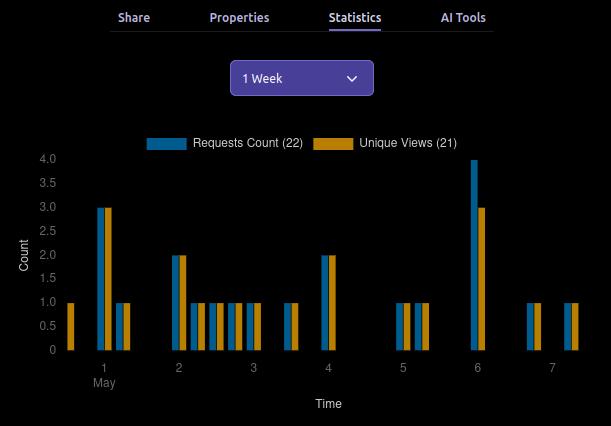
This can be valuable information for content creators, so they can determine what content is resonating with their audience, and what times of day their posts get the most views.
This information can currently be viewed for a maximum period of three months prior to the current date, and as short a period as just the past hour.
Can My Grandma Use It?
Score: 4.7 / 5
Nostr.Build is incredibly easy to use if you have a paid account, or if you are a free user uploading to Nostr.Build through a client that integrates with them by default. Previous frictions encountered by free users trying to upload large files should now be few and far between, thanks to the generous 100MB size limit.
Where things may be a bit more involved is when users are trying to set up media hosting on Nostr apps that don't use Nostr.Build by default. Exactly where in the settings the user must go to set this up, and whether to use the Blossom or NIP-96 address may not be immediately apparent, and requires an understanding of the difference that the user may not possess. This is not the fault of Nostr.Built, though, and I have not taken it into consideration in the scoring. Each individual Nostr app's settings should be as easy to understand as possible.
Another point of friction may come from free users who want to upload directly through the Nostr.Build site, instead of via another Nostr app. This used to be possible without logging in, but in an effort to ensure the service was used for Nostr, and not for general media hosting, Nostr.Build added the requirement to log in.
Thankfully, there are plenty of login options, including npub and password, browser extension (NIP-07), and even via a one-time-code sent to you via Nostr DM. However, if you don't have a paid account already, logging in will prompt you to upgrade. It seems that uploading directly via the website has been removed for free users entirely. You can only upload via another Nostr app if you don't have a paid account. This may lead to confusion for users who don't want to pay for an account, since it isn't made apparent anywhere that uploading through the website isn't an option for them.
Additionally, I would like to see the addresses for the Blossom server and for NIP-96 uploads (unless they are being phased out) added to the main page somewhere. Even selecting the "Blossom" page from the site navigation doesn't make clear what needs to be done to utilize the service. Something as simple as, "To use Nostr.Build with your favorite Blossom compatible Nostr apps, just add https://blossom.band as your media host in the app settings," would be enough to point users in the right direction.
For those who do have paid accounts, the dashboard is easy to navigate and organize your media.
By default, all uploads are added to the Main Folder. Users can leave them there, or they can easily create new folders and drag and drop media to organize it.
Every image has a copy/paste clipboard icon for ready access to copy the media URL for inclusion into a Nostr note.
Additionally, Nostr.Build allows users to share their uploaded media to Nostr directly from the dashboard. Bear in mind, though, this is published to a set of popular relays, without taking into account the user's preferred write relays.
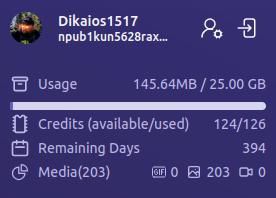
The section just below the user's profile information gives an at-a-glance view of important information, such as how much of the user's allotted storage has been used, how many AI Studio credits are available, how many days are left before their paid account must be renewed, and how many files from three major categories — GIFs, images, and videos — have been uploaded.
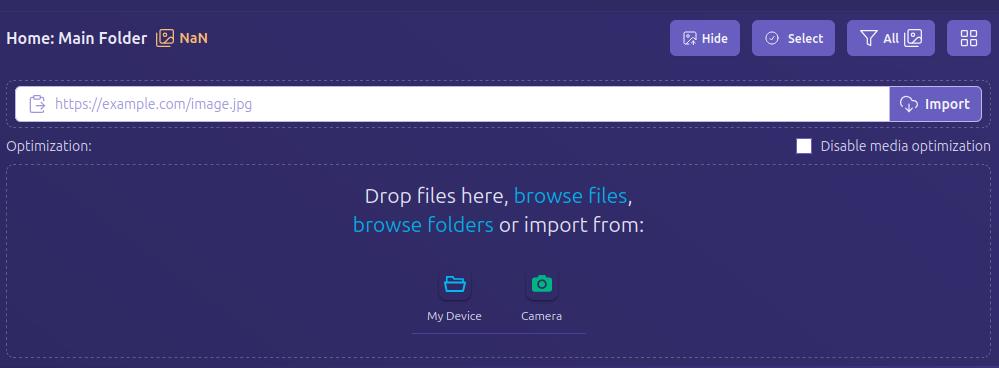
Uploading directly to the dashboard is also incredibly easy. You can simply drag and drop files into the upload pane, or browse for them. If you have a URL for the media you want to upload, you can even paste it to import from another website or Blossom server.
Anything I could think of that I might want to do in the interface was intuitive to find, well labeled, or had common and easily identified icons.
How do UI look?
Score: 4.7 / 5
I would describe Nostr.Build's UI as clean and utilitarian, which is what one would expect from a media hosting service. Nothing too flashy. Just what you need and nothing you don't.
We certainly like our purple color-schemes on Nostr, and Nostr.Build leans into that with white text on shades of purple backgrounds, along with occasional color-popping accents. If a Nostr client had made the same color choices, I might be a bit more critical, but it works in an app that users won't be spending a ton of time in, except while managing their media, or using the AI Studio to generate some images.
UI elements such as buttons, active folder indicators, and icons all maintain an attractive, and simple design, with rounded corners wherever appropriate. Nothing looks too busy or overbearing, and the spacing between image previews in the folder view is just right.
Font remains consistent throughout the interface, with no jarring changes, and bold text, in white or another contrasting color, is used appropriately to draw attention, while subdued text is rendered in a light purple to blend more with the background, while remaining readable.
As such, the UI is attractive, without being particularly breathtaking. Nothing to complain about, but also nothing to write home about.
Log In Options
Score: 4.8 / 5
As mentioned previously, Nostr.Build provides three ways a user can log in.
The first should be very familiar for any Nostr user who frequents web clients, and that is by use of a browser extension (NIP-07), such as Alby, Nos2x, or Gooti. Note, this will also work if you are on Android and using KeyChat's browser, which has a NIP-07 signer built in.
Next is the legacy login method for Nostr.Build that they have used since the service first launched, which is via npub and password. This should serve to remind you that even though Nostr.Build supports Nostr login, and can post your images to Nostr for you, it's really just a centralized media hosting service. Just like you wouldn't use only one Nostr relay, you should not use just one media host. Mirror your media to other Blossom servers.
Most intriguing, and one I had not seen used before, is the option to use your npub and have a one-time-code sent to you via Nostr DM. I tested this method out and it worked flawlessly. It is unfortunately using the old NIP-04 DM spec, though, so any clients that have deprecated these DMs will not work for receiving the code. We're in a strange place with Nostr DMs currently, with some clients deprecating NIP-04 DMs in favor of NIP-17, others that still only support NIP-04, and a few that support both. If you don't see the DM in your client of choice, hop over to Primal and check your DMs there in the "other" tab.
Since Nostr.Build is supporting Nostr login, I would like to see them add remote signer (NIP-46) login alongside browser extension login to round out the options expected from a Nostr web app.
Feature Set
Score: 4.8 / 5
The features provided by Nostr.Build all work as expected and provide a lot of value to the user. With only one exception, all of the features make sense for a media hosting and management service to provide, and they are adding more features all the time.
Users not only get a reliable hosting service, with excellent uptime for their media, but they get integrations with most Nostr clients I can think of, Blossom protocol support, media organization and statistics, posting media to Nostr from within the dashboard, metadata stripping for enhanced privacy, a wide range of supported file types, and an AI image generation studio! What's more, there are additional features already on the roadmap, including traditional and AI image editing, additional plan options, expandable storage, and video transcoding for optimized playback. Nostr.Build is just getting started and they already offer more than most media hosting services out there, intended for Nostr or otherwise.
The one feature I am still not sold on is the "Free Media Gallery." The name is misleading. The gallery itself is not free. You must have a paid account to access more than a preview of it. Rather, it displays media uploaded by free users, regardless of whether they uploaded that media to send via DM, or uploaded it but decided not to share it out, or uploaded it to post it only within a private group on Flotilla, or uploaded it and only sent the note with the image link to a private relay.
Moreover, if I want to see media that has been shared on Nostr, there are plenty of ways I can do so that I can be confident only include media users intended to be publicly viewable. This feature from Nostr.Build, if it is kept at all, should have some way of ensuring the gallery only includes images that were shared on public relays.
Pricing
Score: 5 / 5
The pricing structure for Nostr.Build is exceptionally reasonable when compared with other services.
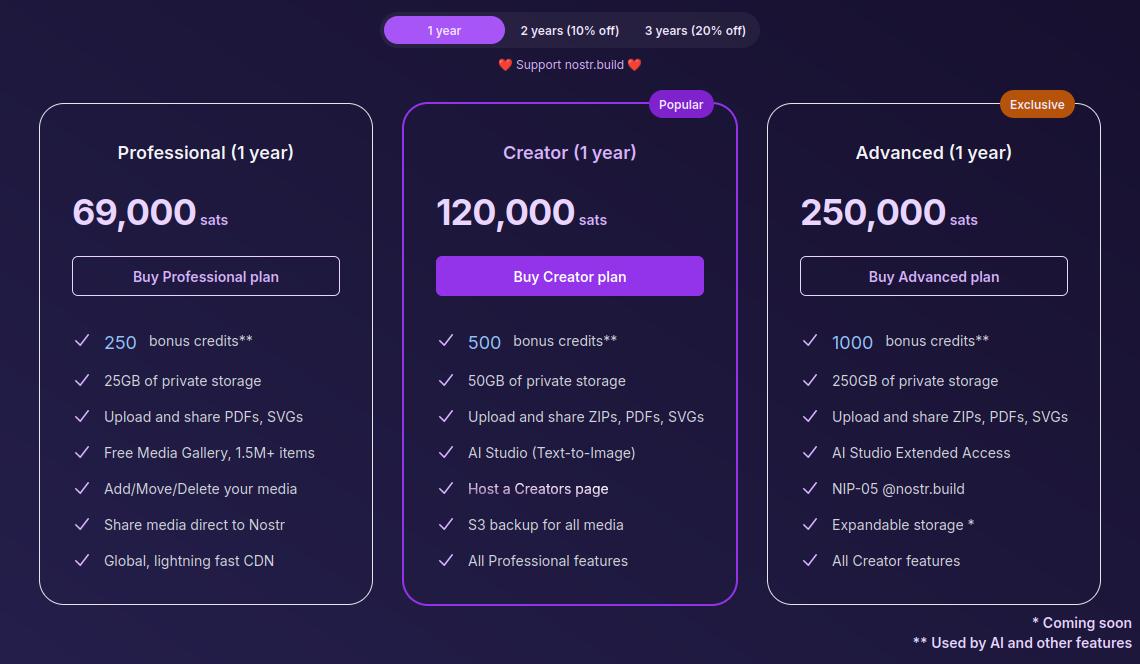
The Professional plan, which is their lowest paid tier, is just 69,000 sats a year. At current price, that translates to around $70 for the year, and Nostr.Build has been known to lower their pricing as Bitcoin goes up. Users can also get a 10% or 20% discount if they buy 2 or 3 years at a time, compensating for the fact that Bitcoin tends to go up year over year.
For that cost, users get 25GB of storage, unlimited file size for uploads within that storage cap, and access to all of Nostr.Build's features mentioned in this review, with the exception of their highest end AI models and storage of certain file types.
If I were to set up my own VPS to host a Blossom server with comparable storage, I would be paying around $14 a month before the cost of the domain, and it would be anything but plug and play. Even then, all I would have is storage. I would be missing out on all of the other features Nostr.Build has out of the box for less than half the price.
The Creator plan is close to double the cost at 120,000 sats, or about $120, a year. However, you aren't just getting double the storage space at 50GB; you are also getting double the AI credits, access to the higher tier AI models, S3 backup for all of your media, and your own Creator page you can share out with your media available for others to browse in one location.
The Advanced plan doesn't add a lot of extra features for more than double the price of the Creator plan, but it MASSIVELY increases your storage limit by 5x to a total of 250GB. Comparable storage space on a VPS to run your own Blossom server would be about $100 a month and Nostr.Build is offering it for about $250 (250,000 sats) for a whole year! If you really need to host that much media, it's hard to beat this price. The plan also comes with a Nostr.Build NIP-05 address, if you need one.
Now, the argument can be made, "But it's priced in sats, and that means in four years I will have spent many times that dollar amount on their service, possibly making it more expensive than other services priced in fiat." While that is true, it also doesn't take opportunity cost into account. Every dollar you spend on something other than Bitcoin is a missed opportunity to have bought Bitcoin with it. There's not really any difference between spending $70 in fiat to buy a hosting plan vs spending 69,000 sats, because you could have used that same $70 to buy Bitcoin instead, so you are losing out on that increase in purchasing power either way.
Not to mention, you can just buy the sats with your fiat and send it to Nostr.Build, so you would effectively be buying your plan with fiat, and they would be receiving sats.
I think Satellite.earth is still technically less expensive at just $0.05 per GB per month, which comes to $15 a year for the same 25GB of Nostr.Build's professional plan. However, all you get is media hosting. You miss out on all of the other features provided by Nostr.Build. And if you are uploading files of 100MB or less... Well, free with Nostr.Build is still cheaper than $0.5 per GB.
Wrap Up
All of the above comes together to make Nostr.Build a versatile and full-featured media hosting and management service at an affordable price point for their paid accounts, but with no need to pay at all if you just want a place to upload photos, GIFs, memes, and even some videos, so long as the file size stays under 100MB. Whether you want to use Nostr.Build as your primary media host, or as just one redundancy in your Blossom set up, they have you covered and I encourage you to check them out!
For the next review, I would like to go with another client, this time for the web, and the two options I am debating between are Coracle.social and Jumble.social. Let me know in the comments which you would like to see!
-
 @ 34f1ddab:2ca0cf7c
2025-05-08 21:39:47
@ 34f1ddab:2ca0cf7c
2025-05-08 21:39:47Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 5194e71c:761bd15c
2025-05-08 21:23:37
@ 5194e71c:761bd15c
2025-05-08 21:23:37[SELL] Funny video Clic on link and Pay on sats with QR code https://m-url.eu/r-66dx
originally posted at https://stacker.news/items/975020
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 7459d333:f207289b
2025-05-08 20:25:45
@ 7459d333:f207289b
2025-05-08 20:25:45lavaGiraffehas created some nice charts with an estimation on the JoinMarket coinjoins from January 1st 2024 until April 30th 2025 using https://github.com/PulpCattel/jm-scripts/blob/master/jmfinder.pyFalse positives are possible, so this is to be interpreted as an upper bound.
originally posted at https://stacker.news/items/974988
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ bbef5093:71228592
2025-05-08 19:59:24
@ bbef5093:71228592
2025-05-08 19:59:24Google három fejlett atomerőmű-fejlesztését finanszírozza
A Google megállapodást kötött az amerikai Elementl Power nevű nukleáris projektfejlesztő céggel, hogy legalább három, egyenként 600 MW kapacitású fejlett atomerőmű fejlesztését finanszírozza az Egyesült Államokban. Ezek a projektek a Google és más nagy technológiai cégek növekvő energiaigényét szolgálják ki, különösen az adatközpontok és a mesterséges intelligencia (AI) miatt[7][10][19][16]. A Google a fejlesztés korai szakaszában biztosít tőkét, a projektek befejezése után pedig lehetősége lesz az ott termelt villamos energia megvásárlására. A pontos helyszíneket és a megállapodás pénzügyi részleteit egyelőre nem hozták nyilvánosságra[10][19][16].
A Google célja, hogy működését 24/7, azaz folyamatosan elérhető, szén-dioxid-mentes energiával lássa el, és ezzel hozzájáruljon az elektromos hálózatok stabilitásához is[10][19][6]. Az Elementl Power technológia-semleges, vagyis még nem döntötték el, milyen típusú reaktort használnak, hanem a fejlesztésben legelőrébb járó technológiát választják majd a kivitelezés idején[10][19][16].
Big Tech és az atomenergia: trendek
A Google mellett más nagy technológiai cégek, például a Microsoft, az Amazon és az Oracle is elkötelezettek az atomenergia mellett, hogy adatközpontjaik számára megbízható, alacsony szén-dioxid-kibocsátású áramot biztosítsanak[15][11][20]. A Google például a Kairos Power nevű céggel is együttműködik kis moduláris reaktorok (SMR) fejlesztésében, amelyek első példányai 2030 körül állhatnak üzembe[1][2][3][17][8]. Az SMR-ek előnye, hogy gyorsabban és olcsóbban telepíthetők, mint a hagyományos nagy atomerőművek, és rugalmasabban illeszthetők az energiaigényekhez[2][3][1].
Pallas kutatóreaktor Hollandiában
Hollandiában befejezték az új Pallas kutatóreaktor alapozását és munkagödrét, ami jelentős mérföldkő a projektben. A reaktor az orvosi radioizotópok előállításában játszik majd kulcsszerepet, több millió beteg ellátását biztosítva világszerte, főként daganatos és szív-érrendszeri betegségek diagnosztikájában és terápiájában. A Pallas reaktor a jelenlegi, 1961 óta működő High-Flux Reactort (HFR) fogja felváltani[forrás: eredeti szöveg].
Finn SMR fejlesztés: demonstrációs üzem
A finn Steady Energy vállalat nem-nukleáris demonstrációs üzemet épít a helsinki Salmisaari B széntüzelésű erőmű helyén, hogy bemutassa LDR-50 típusú kis moduláris reaktorának (SMR) alkalmasságát távhőtermelésre. A projekt célja, hogy a fosszilis energiahordozókat alacsony kibocsátású technológiával váltsa fel a városi távhőrendszerekben[forrás: eredeti szöveg].
Urán és nukleáris üzemanyag: amerikai fejlesztések
Az amerikai Uranium Energy Corp (UEC) és a Radiant Industries megállapodást kötött amerikai eredetű urán szállításáról, hogy támogassák a Radiant Kaleidos mikroraktorok elterjedését. Ezek a mikroraktorok 1 MW teljesítményűek, szállíthatók, és 2028-tól kezdődhet a kereskedelmi alkalmazásuk[forrás: eredeti szöveg].
A Global Laser Enrichment (GLE) Észak-Karolinában megkezdte a harmadik generációs, lézeralapú Silex urándúsítási technológia demonstrációs tesztjeit. Ez a technológia nagyobb hatékonyságot, alacsonyabb költségeket és rugalmasabb üzemanyaggyártást ígér a jövő atomerőművei számára. A GLE célja, hogy 2028-tól kereskedelmi üzembe helyezze az új dúsítóüzemet Kentuckyban[forrás: eredeti szöveg].
Egyéb hírek röviden
- Az Egyesült Államokban befejezték az ITER szupravezető mágnesének utolsó moduljának tesztelését, amely kulcsfontosságú a franciaországi fúziós kísérleti reaktorban.
- Ausztráliában a nukleáris energia bevezetését szorgalmazza egy lobbicsoport, bár jelenleg törvény tiltja az atomerőművek építését.
- Csehországban, a Dukovany atomerőmű bővítésével kapcsolatos szerződéseket írtak alá dél-koreai cégekkel, egy francia bírósági tiltás ellenére.
- 2025 júniusában Zágrábban rendezik meg a European Nuclear Young Generation Forumot, amely a fiatal nukleáris szakemberek legnagyobb európai találkozója lesz[forrás: eredeti szöveg].
Hivatkozások:[1][2][3][7][10][16][19] – Google és nukleáris projektek[15][11][20] – Big Tech trendek
További részletek a többi témáról az eredeti szövegben találhatók.Hivatkozások: [1] A Google 7 atomreaktor megépítését támogatja az MI ... - itbusiness https://itbusiness.hu/technology/aktualis-lapszam/strategy/google-reaktor/ [2] Google új generációs atomreaktorokból vásárol áramot - DinaMix https://dinamix.hu/google-uj-generacios-atomreaktorokbol-vasarol-aramot/ [3] A Google moduláris atomreaktorokat vásárol a saját energiaellátására https://gyartastrend.hu/cikk/a-google-modularis-atomreaktorokat-vasarol-a-sajat-energiaellatasara [4] Az atom vonzza a befektetőket - Atombiztos Blog https://www.atombiztos.org/2025/05/05/az-atom-vonzza-a-befektetoket/125967/ [5] Máris trükköznek az AI-óriások, csak több áramuk legyen https://www.szabadeuropa.hu/a/maris-trukkoznek-az-ai-oriasok-csak-tobb-aramuk-legyen/33167550.html [6] 24/7 Clean Energy – Data Centers - Google https://www.google.com/about/datacenters/cleanenergy/ [7] Google agrees to fund three US nuclear power plants https://business.inquirer.net/524307/google-agrees-to-fund-three-us-nuclear-power-plants [8] Atomreaktorok építését rendelte meg a Google - Telex https://telex.hu/gazdasag/2024/10/14/google-kairos-atomeromu [9] Operating sustainably - Google Data Centers https://datacenters.google/operating-sustainably [10] Google To Commit Funding For Three Advanced Nuclear Power ... https://www.nucnet.org/news/google-to-commit-funding-for-three-advanced-nuclear-power-projects-5-4-2025 [11] Az atomenergia mellett tette le a voksát több technológiai óriás https://www.vg.hu/nemzetkozi-gazdasag/2025/03/atomenergia-technologiai-orias [12] 24/7 Carbon-free Energy Explained - Eavor Technologies https://eavor.com/blog/24-7-carbon-free-energy-explained/ [13] Google agrees to fund the development of three new nuclear sites https://www.reddit.com/r/nuclear/comments/1kh2s7t/google_agrees_to_fund_the_development_of_three/ [14] Téma: Új atomerőművet építtet magának a Google - PC Fórum https://pcforum.hu/tarsalgo/154783/uj-atomeromuvet-epittet-maganak-a-google-nem-is-egyet-hanem-mindjart-harmat [15] Big Tech has cozied up to nuclear energy - The Verge https://www.theverge.com/2024/10/5/24261405/google-microsoft-amazon-tech-data-center-nuclear-energy [16] Google to back development of 3 nuclear sites on data center push https://nypost.com/2025/05/07/business/google-to-back-development-of-3-nuclear-sites-on-data-center-push/ [17] Moduláris atomreaktorokból vásárol energiát a Google - HWSW https://www.hwsw.hu/hirek/68282/google-kairospower-atomreaktor-energia-aram.html [18] What is 24/7 carbon-free energy? - Baseload Capital https://www.baseloadcap.com/what-is-24-7-carbon-free-energy/ [19] Google to fund development of three nuclear power sites https://www.world-nuclear-news.org/articles/google-to-fund-elementl-to-prepare-three-nuclear-power-sites [20] Óriáscégek álltak a nukleáris reneszánsz élére - Világgazdaság http://www.vg.hu/nemzetkozi-gazdasag/2025/03/nuklearis-energia-amazon-google
-
 @ 2fdae362:c9999539
2025-05-08 19:57:33
@ 2fdae362:c9999539
2025-05-08 19:57:33Why Your Manufacturing Engineers Shouldn’t Build Your Next‑Gen Product (and How an External NPD Team Supercharges Both)
1 | Two Very Different Missions
Most electronics companies lump “engineering” into one budget line. In reality there are two distinct jobs:
| Mission | Core Question | Success Metric | |---------|---------------|----------------| | Manufacturing & Sales Support | How do we keep shipping and lower COGS? | Uptime, yield, cost‑down, ECO turnaround | | New‑Product Development | What will customers demand 18‑36 months from now? | Time‑to‑market, feature velocity, first‑pass success |
Trying to solve both with the same staff is like asking your pit‑crew to design an entirely new race‑car while the current one is circling the track.
2 | Why Your In‑House Team Excels at Sustaining Work
- Process‑driven mindset – KPIs center on takt time and scrap, not innovation cycles.
- Deep tribal knowledge of legacy designs, test fixtures, and compliance filings.
- Close link to Ops & Sales – Daily stand‑ups about line stoppages and customer RMAs.
That focus is exactly why the factory runs smoothly — but it penalizes exploratory work. Every minute spent chasing down a bleeding‑edge SoC or new RF stack is a minute the line risks slipping.
3 | What New‑Product Development Really Demands
- State‑of‑the‑art parts libraries (and the supply‑chain foresight to qualify alternates).
- Architectural runway — designs built for firmware updatability, security, and field diagnostics.
- Fast‑loop prototyping — EVT to DVT in weeks, not half‑years.
- Cross‑disciplinary toolchain — from FPGA simulation to Yocto‑based Linux builds to OTA pipelines.
These skills dull quickly when they aren’t used daily; maintaining them internally is expensive downtime for a sustaining group.
4 | The Outside‑NPD Model: Division of Labor That Works
| Stage | Your Internal Team | Our External NPD Team | |-------|-------------------|-----------------------| | Concept | Product vision, market intel | Technology scouting, architecture options | | Design | DFx feedback & factory constraints | Schematics, layouts, firmware, driver stacks | | Validation | Factory test jig specs | EVT/DVT, pre‑compliance, safety margins | | Transfer | Process FMEAs, operator training | Full doc set, source, BoM, bring‑up guides |
Result: No bandwidth tug‑of‑war — each team stays in its lane and both lanes move faster.
5 | Seven Tangible Benefits You’ll Feel in Year 1
- 14‑30 % faster NPD schedules via parallel tasking.
- Zero factory interruptions — sustaining KPIs stay green.
- Up‑to‑date technology choices yielding longer market life and lower future BOM risk.
- Process upgrades your ops team can re‑use (automated CI for firmware, digital‑thread BoM).
- Cleaner IP chain of custody — everything delivered in version‑controlled repos with SPDX manifests.
- Predictable budgeting — fixed‑price or milestone schedules instead of overtime creep.
- On‑demand specialist depth (wireless certs, OS driver authors, safety assessors) without hiring.
6 | Hand‑Off That Sticks
We shut the project down only after:
- Source, binaries, Gerbers, test plans, and regulatory artifacts are in your repo.
- Your sustaining engineers complete hands‑on bring‑up alongside ours.
- A 30‑60‑day shadow‑support window is booked.
That means the next ECO lands on your familiar desk, not ours — unless you want it to.
7 | A Quick Example
When ACME Corp’s internal team tried to modernize their decade‑old IoT gateway, the factory choked on late‑night proto builds. We took the NPD load, delivered a Linux‑plus‑Modbus driver stack in 16 weeks, and handed it back with a test‑rig script that ACME’s own sustaining crew still runs today — zero line downtime, product launched six months early.
8 | Ready to Split the Load?
If your manufacturing engineers are drowning in ECOs and your roadmap is slipping, let’s talk. We’ll map out an NPD sprint plan that leaves your factory gurus doing what they do best — keeping product flowing — while we build the future version you’ll hand back to them, fully documented.
-
 @ 7b20d99d:d2a541a9
2025-05-08 19:31:50
@ 7b20d99d:d2a541a9
2025-05-08 19:31:50
Bitcoin is a powerful tool for sending aid quickly, directly, and without intermediaries, especially in countries where banking systems are corrupt or inefficient. It allows for supporting noble causes without relying on slow or centralized NGOs. But where there is generosity, there are also abuses.
In the Bitcoin world, some have learned to exploit the anonymity and speed of transactions to create fake emotional stories and steal funds from well-meaning individuals. These scams damage trust and slow down the adoption of Bitcoin in humanitarian efforts.
In this series, I'll show you:
How to spot dubious projects,
What practices can alert you,
And most importantly, how to continue supporting real causes safely.

Alert 1: Lack of transparency
A serious charity project, whether Bitcoin-based or not, must be accountable.
In the Bitcoin ecosystem, where everything relies on peer-to-peer trust, transparency is even more crucial.
Here are the classic signs of a lack of transparency:
-
No concrete evidence of action on the ground.
A project that asks you for money but doesn't show any photos, videos, or reports is suspicious. Even with limited resources, a legitimate project can show:
Before/after images of an action (e.g., food distribution, healthcare, clothing)
Receipts or proof of purchase (blurred if necessary for privacy)
Testimonies from beneficiaries, even short ones
- No regular posting or tracking.
If a project has raised funds but doesn't publish any updates on the progress, distribution, or results achieved, this is a red flag. A genuine project maintains a connection with its donors, even after the fundraising process.
- Bitcoin address without tracking.
Providing a Bitcoin address without providing a link to a Geyser, BTCPay, or donation tracking page is an easy way to hide donation flows. Serious projects use public tools to make donations visible to everyone.
- Refusal to answer questions.
An honest project accepts questions from donors:
- Where do the funds go?
- Why this amount?
- Who is responsible?
If there is constant vagueness, or worse, aggression when you ask these questions: that's a red flag.
Recommendation :
Before donating, look for evidence. Ask simple questions. And above all, compare several projects: you'll quickly see who's doing real work, and who's showing nothing.

In Bitcoin charity projects, emotion is often the scammer's favorite tool. They know: if you're moved, you give quickly. Especially when there's an emergency. Unfortunately, they often have no real reason behind their requests.
Here's how these emotional manipulations work:
-
Dramatic stories without proof.
A sick child, an injured animal, a starving family... these stories touch the heart. But often, the images are taken from Google or old TikTok/Facebook accounts. There's no proof that the person requesting sats is actually involved.
-
The manufactured emergency.
Scammers use phrases like:
"URGENT! He only has two days to live!"
"We need 100,000 sats before midnight, or else..."
This kind of urgency is often fabricated to push you to act without thinking or checking.
- No trace of previous activity.
Often, these accounts have never discussed charity before. They suddenly appear, launch an emotional campaign, receive donations... then disappear or change their name.
- Reusing stories from other projects.
Some copy real stories from real projects and adapt them with new BTC addresses. They rely on virality and credulity. Sometimes, they even imitate the style of a legitimate project.
How to protect yourself?
Reverse image search: You can use Google Images or Yandex to check if the photo is circulating elsewhere.
Research the account's history: was it posting content before the campaign? Does it seem committed to Bitcoin or a cause?
Refrain from reacting too quickly: if a story upsets you, that's exactly what the scammer wants. Take a break, do some research.
Key points:
A real project doesn't need to manipulate your emotions to gain your support. It shares its impact, its concrete actions, and is open to scrutiny. Never let your sats speak before your brain.

Check the project's public presence and reputation
In the decentralized world of Bitcoin, there are no guarantees or official certifiers. What replaces institutions is reputation: what others say about you, what you publish, and how you act over time.
Before donating to a charitable project in Bitcoin, it is essential to verify the public presence and traceability of the project or individual. This can prevent you from being scammed by opportunistic or malicious accounts.
Here are the good reflexes to have:
- Cross-platform search
A legitimate project leaves its mark on multiple channels:
Nostr: posts, zaps, interactions, community relays
Twitter/X: regular posts, comments, retweets
Telegram, YouTube, Instagram: visual content and community comments
Even if it's small, a real project has at least one public space where it shares its activities, answers questions, and builds relationships with its supporters.
Alert: An account that appears out of nowhere with 3 posts in 2 days and an urgent donation request is suspicious.
- Seeking credible public support
A great sign is when other well-known users in the Bitcoin community (or on Nostr) endorse or support the project:
They share the campaign;
They respond to posts with enthusiasm or testimonials;
They contribute sats themselves;
You can send them a DM to ask, "Are you familiar with this project? Are they serious?"
- View account history
Does this account have:
- Have you already run other campaigns in the past?
- Demonstrated concrete results?
- A long-standing audience?
Scams often have an empty history, or one that has been deliberately deleted.
If the account was recently created, it's an orange flag. It's not always a scam, but it's a good sign.
- Beware of names that are too generic
Accounts like “Bitcoin_Charity,” “BTC_Hope4Africa,” or “SatoshiMissionHelp” that use generic, faceless names with no personal history or evidence of involvement are often lures to suck up your generosity.
In an open world like Nostr, trust must be earned, not granted automatically. Before you zap or send sats: check the footprints. A real project doesn't hide. It wants to be seen, recognized, supported... and verified.

Prefer traceable and public donations
One of the great advantages of Bitcoin is that every transaction is recorded on the blockchain. Yet, many BTC charitable projects fail to leverage this transparency potential… sometimes out of ignorance, sometimes intentionally.
If you want to give securely, you should prioritize tools and methods that allow clear tracking of your money.
- Favors transparent platforms (Geyser, Zaprite, BTCPay, etc.)
These platforms allow:
- Track how much has been raised in real time
- Have a public address or QR code that everyone can see
- Sometimes even see who donated (if the donor makes it public)
And most importantly: the funds go directly into the creator's wallet, without an intermediary
Example: Geyser.fund shows how many sats have been raised, how many are left to reach, and sometimes even the expenses incurred.
- Avoid isolated static addresses
When someone just gives you a Bitcoin address without any context or tools around it, you can't know:
- If others have already donated
- What's the status of the fundraising?
- What will happen with the funds received?
Even worse, an address can be reused for multiple different campaigns. No tracking, no limits.
Reminder: A scammer can also show a QR code with an emotional caption, collect in bulk, and then erase all traces.
- Request a dedicated campaign address
A serious project can:
- Generate a unique address for each campaign or donor (via a wallet or BTCPay store)
- Or show you a link to a Bitcoin explorer to track inflows in real time
This allows you to verify that: - Your donation has been received - Funds are not being diverted for other purposes - And that other people are also contributing (proof of credibility)
- Check expenses if possible
More and more projects are publishing:
- Captures of receipts or transfers
- Monthly reports
- Distribution videos
This allows donors to see how funds are being used, even in rural areas or without stable internet.
If a project doesn't want you to track donations, ask yourself why. In the Bitcoin ecosystem, transparency is a weapon against abuse. Use it, and encourage others to do the same.

Want to help? Great. But in the Bitcoin ecosystem, giving indiscriminately is like throwing your sats into a bottomless pit. Here's a clear list of best practices to avoid scams and support good causes with confidence and intelligence.
- Never give under pressure
A real project:
- Don't rush.
- Don't create an artificial sense of urgency.
- Don't demand anything.
Golden rule: if you are pressured to skip "quickly" or "now or everything is ruined", it is suspicious.
- Use reputable platforms
Before sending sats:
Check if the project is on Geyser.fund, Zaprite, BTCPayServer, or Tallycoin.
These platforms provide transparency, monitoring and protection.
If the project refuses to appear there "without valid reason", ask yourself questions.
- Always check the source
Ask yourself these questions:
- Who is leading this campaign?
- How long has this person been active in the community?
- Does their history hold a consistent profile?
- Are they well-known on Nostr, X, Telegram, or elsewhere?
A reliable project has nothing to hide. It is findable, traceable, and responsive.
- Don't rely on images or videos alone
A photo of a crying child or a dish being offered proves nothing. What you want to know:
- Did they take this photo?
- What's the connection to the campaign?
- Do they show several stages (preparation, distribution, follow-up)?
Scammers love beautiful stolen images, but never show the actual work.
- Request a follow-up report or evidence
A serious project can easily provide you with:
- A link to a dedicated Bitcoin address
- A video or photo with a personalized message
- A receipt or proof of purchase
If they refuse or get offended by you for asking? Run away.
- Share only verified projects
You are also responsible for what you share. By sharing a project without verifying:
- You're putting your credibility on the line.
- You risk causing others to lose sats.
Do your own research, even if you trust the person who sent you the link.
- Start small
You can test a project with a small amount and observe:
-
How they communicate after receiving it
-
If they thank you
- If they keep you informed
It's a simple way to filter out the good guys from the opportunists.
In a free ecosystem like Bitcoin, there's no customer service, no refunds, no "cancel" button. Your only security is your vigilance. Give, but give wisely.

How to intelligently support genuine causes
Supporting charitable projects with Bitcoin doesn't have to be risky. On the contrary, it can be a powerful tool for spreading the values of Bitcoin while genuinely helping people.
But for your help to have a real impact, it's not enough to just switch off and disappear. You have to be intelligently involved.
Here's how to become a helpful, strategic, and caring donor.
- Be part of the project, not just the donation
The best donors are not those who give the most, but those who:
- ask questions,
- suggest ideas,
- share campaigns,
- encourage the founder,
- inform others.
In Bitcoin, we talk about community, not customers. Be an agent of change, not just a transaction number.
- Favors projects with a long-term vision
A serious project speaks to you:
- education,
- sustainability,
- independence,
- integration of Bitcoin into local life.
He doesn't just give away rice or clothes. He wants to make people more autonomous, freer, and more connected to the decentralized economy.
Support projects that build, not just those that distribute.
- Diversify your support
You can :
- Skip small projects regularly
- Support a campaign with a fixed monthly budget
- Offer your skills: design, writing, video, networking
Participate in a DAO or a coordinated donations collective
Bitcoin support isn't just about money. Your time and talent are also valuable.
- Educate while you help
When you participate in a project, take the opportunity to:
- Explain to others how Bitcoin works
- Demonstrate the benefits of transparency through blockchain
- Raising awareness in your circle of the freedom offered by direct support in BTC
Education is the ultimate weapon against addiction and scams.
- Create or join a reliable initiative
You can :
- Create your own small campaign with Geyser.fund or Zaprite
- Join a collective like Hope With Bitcoin or other communities on Nostr
- Offer to document an existing campaign
This is how sustainable projects are born: not with large anonymous donations, but with small, well-supported flames.
Donating Bitcoin is more than just a transfer. It's an affirmation of values. It's a statement:
“I choose to support causes without going through banks, without permission, without borders, with transparency and freedom.”
But for it to work, you need:
-
Stay vigilant
-
Demand clarity
- Foster human connections
- Build trust
Bitcoin is a tool of sovereignty. It deserves honest projects. It's up to us to protect them.
Together, let's discover Hope With Bitcoin: The project whose mission is to share smiles and hope with those in need, while raising awareness for Bitcoin adoption.
X: https://x.com/HopeWithBTC
Nostr / Primal: https://primal.net/p/npub10vsdn82fps4vwjaqxcpwj0nyync0cfrp2f5qlayrljh6d549gx5s0y9eap
Proof Of Work: https://drive.google.com/drive/u/1/folders/19LWZX4TtF6DJbDVCqhJ0EMMQqnjHVMvm
Geyser : https://geyser.fund/project/hopewithbitcoin
-
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 3f770d65:7a745b24
2025-05-08 18:09:35
@ 3f770d65:7a745b24
2025-05-08 18:09:35🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: Austin Kelsay, Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: McShane (Bitcoin Strategy @ Roxom TV)
-
👥 Speakers:
-
Martti Malmi – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
Lyn Alden – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by DJ Valerie B LOVE, TatumTurnUp, and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by Derek Ross, Tomer Strolight, Terry Yiu, OpenMike, and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ a5ee4475:2ca75401
2025-05-08 16:41:28
@ a5ee4475:2ca75401
2025-05-08 16:41:28profissional #brasileiros #portugues #lista
[Em Atualização]
nostr:nprofile1qqsvz46xcwfqjyw5xkjh3gs8v63udn6slp2wehn8pyndtcpvvxa7rwqpzpmhxue69uhkummnw3ezumt0d5hsdzu0zr - Estude BITCOIN
!(image)[https://nostrcheck.me/media/public/nostrcheck.me_8896510008477875231689270519.webp]
Canal Principal: https://m.youtube.com/@altierebtc
Canal de Games: https://m.youtube.com/channel/UCm9dUXKlVbDOfa-7GB-6gxw
Twitch: https://m.twitch.tv/altiere/home
Endereço Lightning: Quietcarol43@walletofsatoshi.com
Peter Turguniev - nostr:nprofile1qqszleff9gkly5z85wf0em4dw4zcsaw8whp3es50f0syeme73kc49ygpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7qgj4r9
Site: ANCAP.SU
!(image)[https://i.im.ge/2023/06/01/hCgPJa.03de86ce-3106-4a4b-859c-b6b4d9e6e62e.jpg]
Canal Principal: https://m.youtube.com/@ancap_su
Visão Libertária: https://m.youtube.com/@Visao_Libertaria
Canal de Programação: https://m.youtube.com/@safesrc
Canal Mundo em Revolução: https://m.youtube.com/@wrevolving
Canal Hoje no X: https://m.youtube.com/@noxhoje
Canal Antigo: https://m.youtube.com/@ANCAPSUClassic
Site: https://pimentanocafe.com.br/
ANCAP.SU (Odysee): https://odysee.com/@ancapsu:be
Visão Libertária (Odysee): https://odysee.com/@ancapsu:c
Endereço Lightning: Ancapsu@getalby.com
nostr:nprofile1qqsw2k9dqcwkelfl0cr2ranhfvqx98et635hymmefl4rr89e4x9xtaqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u55vn8f
Economista e Cientista de Dados
!(image)[https://image.nostr.build/9caacd289ed01ad6fecd331a43218da6ce3c2f5713d9e9a4fc8c8b531728deb8.jpg]
Repositorio de codigos: https://github.com/Argonalyst
Notícias sobre tecnologia e inteligência artificial: https://youtube.com/@argonalyst
https://www.argonalyst.com/
Bitcoinheiros - nostr:nprofile1qqsdg0vnpw76lujncaexfh0fy747dheynq9s5m9wqxulcu2szlwqpfcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszyrhwden5te0dehhxarj9ekk7mf0cmje9h
!(image)[https://void.cat/d/A6LisLBh5cmyYtrgkjqBxe.webp]
Canal Principal: https://m.youtube.com/@Bitcoinheiros
Canal de Cortes: https://www.youtube.com/channel/UC82m2TCXSHWcqSLym5BzjLQ/
Site: https://bitcoinheiros.com/
Endereço Lightning: ln@pay.bitcoinheiros.com
Área Bitcoin - Divulgação sobre Bitcoin
nostr:nprofile1qqstvy6savnm83mf9775t70d2d2lp2rsw8hys5rfsq4lhy9qachctpgpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7svvx93 e nostr:npub1yzhwak5yc7pzvukwzlfj7p0dp2y07jd42y45h0maxuej4us5rcjsssxkej
!(image)[https://m.primal.net/KXBa.jpg]
Canal Principal: https://m.youtube.com/@AreaBitcoin
Site: Areabitcoin.com.br
Endereço Lightning: Cyanlionfish5@primal.net
nostr:nprofile1qqs075udlpdc60js8ade7st2zt942ghj0ehd6frnwjtylss5c9kdxzgpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uq32amnwvaz7tmhda6zumn0wd68ytnsv9e8g7g24pghx - Dev
Repositório: https://github.com/antonioconselheiro/omeglestr
nostr:nprofile1qqsqxh6ffher03qlngcnf93g9kyv7gzkmz6h6t8qylzkw8hup8zxytspzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcx72xdd
Biólogo e colunista
!(image)[https://image.nostr.build/8bddd8cd3e2e65c76cd7b02179e3ddeb3a1a1171f0a0ae32594278a9ccf19da0.jpg]
Canal Principal: https://m.youtube.com/@EliVieira
Endereço Lightning: Elivieira@bipa.app
nostr:nprofile1qqsgy4gvl2n03ylylv0ack59res7nytkjdq5wpqcw9ch5eqhwwnpnvgpypmhxw309aex2mrp0ykkummnw3ez6cnj9e3k7mfwvfer5dpcxsuz7qgewaehxw309a38ytnsw4e8qmr9wfjkccte9e3k7mf0qyvhwumn8ghj7cmv9ec82unsd3jhyetvv9ujucm0d5hs6m9t8t
Canal Principal: https://youtube.com/@Akitando
https://www.akitaonrails.com/
https://www.codeminer42.com/
Endereço Lightning: Akitaonrails@strike.me
Felipe Ojeda - nostr:nprofile1qqsv7c6qu0qsy9wxg9cqkhle078j46rhsvz64f6vukxdmpkdt7vt55cpz9mhxue69uhkummnw3ezuamfdejj7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uq3wamnwvaz7tmpw3kxzuewdehhxarj9ekxzmny9uwes77q
Saída fiscal para o Paraguai e P2P
https://youtube.com/@bitcoineliberdade
Lightning Network: ojeda@blink.sv
nostr:npub18zw66c2lvt6s06drtvtkjjyvnfwjdgg2w7y36rmtmg7rnfnkhhxq7hhu4t
Engenheiro
Construção econômica e sustentável: https://amandaefernando.com.br/
https://youtube.com/@amandaefernando
Carteira de Zap: lilacgecko5@blink.com
nostr:npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd
Canal principal: https://youtube.com/@fernandoulrichcanal
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
https://fiatjaf.com/
Repositórios de códigos:
https://git.fiatjaf.com/
https://github.com/fiatjaf
Outros repositórios:
https://github.com/nostr-protocol/nostr
Carteita de Zap: fiatjaf@zbd.gg
nostr:nprofile1qqsw2s3zjedanx8nve9zda7zkemx5n5d4v0mt0ncehfa7qkkjse5v5gpzpmhxue69uhkummnw3ezumt0d5hsxnexr8
Canal Principal: https://m.youtube.com/@FoxyeBitcoin
Endereço Lightning: Foxye@bipa.app
nostr:npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url - Irmãos Chioca
Tradutores e publicadores de temáticas libertárias [livros, artigos, vídeos e textos]
https://rothbardbrasil.com/
Canal principal: https://youtube.com/@institutorothbardbrasil
Carteira de zap: trendybean80@walletofsatoshi.com
João Abitante - nostr:nprofile1qqsyzwgmhmdsduuya866s2pnnkw2x956wdpumtjjw3rp4ueyunv9hlspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qgwwaehxw309ahx7uewd3hkctclycz6e
Contador Libertário
!(image)[https://m.primal.net/KWoL.png]
Canal Principal: https://youtube.com/@ahoradaelisao
Endereço Lightning: libertcontador@pay.bbw.sv
João Trein - nostr:nprofile1qqsze3h79ljwzqp7ryre9n6p9z8m4t4m5806v8anxu9q2dx7n5cgqfgpz3mhxue69uhkummnw3ezummcw3ezuer9wcq35amnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mgpzpmhxue69uhkummnw3ezumrpdejqj2zepn
Bitcoin e Cyber segurança
https://youtube.com/@tninvest
Carteira de Zap: tninvest@blink.com
nostr:nprofile1qqsdwdhzj3red6p62fus3sdk03cqp8t0u3enfupwa4rw2q2yhfwe9tqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc3ft2ln
Atendimento psicológico e sobrevivencialismo
Canal sobrevivencialismo: https://youtube.com/@sobrevivencialismo
Canal de psicologia: https://youtube.com/@juliolobosv
Carteira de zap: juliolobosv@getalby.com
nostr:npub1q88jfh2gasm0ztszhltfl226lhpvlxxq2u0t6smf2n5cn85es4assuwqmp
Divulgadora sobre Bitcoin
https://youtube.com/@bitlorena
Carteira de zap: potterlore@zbd.gg
nostr:nprofile1qqsp05nhmn8x343gme39d8l63z2d34ht4lgln60jn5vm3gsndj7u86qppemhxue69uhkummn9ekx7mp09kal50
Ambientalista
https://youtube.com/@marcobatalha
Carteira de zap marcobatalha@getalby.com
Marcus - nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft e nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju
https://privatelawsociety.net/know
https://github.com/PrivateLawSociety/pls-mvp
Carteira de zap: anarcus@getalby.com
nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcpzpmhxue69uhkummnw3ezumt0d5hsf83vqq
Programador
Repositório de códigos:
https://github.com/misesdev
Aulas de desenvolvimento de código
https://youtube.com/@misesdev
Carteira de Zap: greatasphalt42@walletofsatoshi.com
nostr:nprofile1qqsvqnfplem5auv0ug0j2v8kkp5x06fcv93rqs6cz54fm6svs28ahgqpz4mhxue69uhkummnw3ezummcw3ezuer9wchsn6tsk6
Repositório: https://github.com/ODevLibertario/nostrlivery
nostr:nprofile1qqstj62w4ctec57ny2p6hs67ut4nygsrc4th75ff42cyag4emy2v3yspz9mhxue69uhkummnw3ezuamfdejj7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqsuamnwvaz7tmwdaejumr0dshsxhz6wr
!(image)[https://image.nostr.build/22080bdb678ab61ef863be436d78654f537287951508198bf9fa5129abb289fc.jpg]
Canal Principal: https://m.youtube.com/@PROmetheusHODL
Canal no Odysee: https://odysee.com/@Prometheus:ef
Endereços Lightning e Liquid Blink: prometheus@blink.sv Alby: prometheusyt@getalby.com Liquid: VJLDAirBEPj4deoRnspxG8pnu8Ezxg6ajPcXyXoDXDP1dKn9UDJPDckiX5vBTp9aFQM42B15KpAHqVkc
nostr:npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp
https://youtube.com/@VamosViverFora
Carteira de zap: psp@blink.com
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
https://vitorpamplona.com/
Repositorio de codigo:
https://github.com/vitorpamplona
https://github.com/vitorpamplona/amethyst/
Cursos:
Seiiti Arata / Seiiti Arata (Inglês)
Produtor de cursos
https://www.arataacademy.com/
Canal principal: https://youtube.com/@arataacademy
Daniel Miorim e Malboro
Comentarismo e ensino
Alta Linguagem e Curso Libertário de Anticomunismo
https://youtube.com/@altalinguagem
Renato 38 e Alan Schramm
Livros, curso e consultoria de Bitcoin
O seguinte canal disponibiliza o curso, mas não menciona ser do Renato ou do Alan:
https://youtu.be/ZQaGXchogkk
Rafael Scapella
Viagens, informações e política internacional
https://youtube.com/@rafaelscapella?si=IfPjPfVsPlmA_zYX
Roberto Pantoja
Inovaflix - Cursos e Consutoria de Negócios
Canal de informação: https://youtube.com/@robertopantoja
Carlos Xavier
Prof. de Teologia e Direito
Curso de História da Filosofia e Direito
Direito sem Juridiquês:
https://youtube.com/c/DireitosemJuridiquês
- Playlist libertária:
https://youtube.com/playlist?list=PLYXudd4-x8GjzIyNZsUzzw8NF-Gkca8sV&si=oyDRdxVDB0b1GLTo
Teodidatas:
https://youtube.com/c/Teodidatas
Jason Schmütz (Toddyn)
Comunicador sobre jogos e temas gerais
Canal sobre Bitcoin, critica ao Estado e a empresas de jogos, e estilo de vida:
https://youtube.com/@ojasonschmutz
Canal de Jogos:
https://youtube.com/@toddyncp
Curso de criação de jogos sem programar - Codezero | RPG Paper Maker [Atualmente indisponível]
Pigdev
Desenvolvedor de jogos indies
https://youtube.com/@pigdev
Cursos e materiais para desenvolvimento de jogos
https://pigdev.itch.io/
Outros Profissionais Libertários
Anderson - Ciberdef
Defesa cibernética
https://youtube.com/@andersonciberdef
Guilherme Bauer - Capital Global
Internacionalização de patrimônio
https://odysee.com/@capitalglobalbr:b
Tuchê Nunes
Agricultura, permacultura e bioconstrução
https://youtube.com/@tuchenunesautossustentavel
Jack
Personal trainer
Dicas de treinos https://youtube.com/@lybrjack
Avelino Morganti
Ouro, prata e joias
Compras e pedidos: https://morgantis.com/
Canal de informação: https://youtube.com/@avelinomorganti
Bianca Colobari
Atendimento psicológico e experiência com educação domiciliar para crianças
Canal de informação https://youtube.com/@biancacolombari
Cecilia Isicke (Portugal)
Médica libertária e bitcoinheira
Canal de informação https://youtube.com/@draceciliaisicke650
Não Libertário e Bitcoiner
Núcleo Dharma
Artes Marciais, Autodefesa e Armas
https://youtube.com/channel/UCtbAO1zbJAwd6gDK7Y87JLA
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 000002de:c05780a7
2025-05-08 16:14:37
@ 000002de:c05780a7
2025-05-08 16:14:37Just an observation that makes me chuckle.
originally posted at https://stacker.news/items/974829
-
 @ 5b730fac:9e746e2a
2025-05-08 15:33:12
@ 5b730fac:9e746e2a
2025-05-08 15:33:12| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ----------------------------------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | deleted config files, first install | Already installed | Manual | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzwpnxq6rvdp59d83mz |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "8e75993b2b6d28e4336bc90150e2c69db97d45f1c7db6bf3c3892cee55f45c44", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746716510, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c.ipk" ], [ "m", "application/octet-stream" ], [ "x", "bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c" ], [ "ox", "bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package_test-92-1157a2f" ], [ "release_channel", "dev" ] ] }Current version picked up by opkg:
root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-92-1157a2fCheck basic module's logic
Config.json contains the right event ID: ``` root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b" }
```
Install.json contains the right package path:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746715561, "download_time": 1746715507, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Deactivate, delete config files and start
Deactivate & delete config files:
root@OpenWrt:/tmp# service tollgate-basic stop root@OpenWrt:/tmp# service tollgate-basic status inactive root@OpenWrt:/tmp# rm /etc/tollgate/config.json /etc/tollgate/install.json root@OpenWrt:/tmp# ls /etc/tollgate/config.json /etc/tollgate/install.json ls: /etc/tollgate/config.json: No such file or directory ls: /etc/tollgate/install.json: No such file or directoryStart and check configs. Release channel is set to stable by default:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "unknown" } root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "stable", "ensure_default_timestamp": 1746717311 }Logs are too verbose, but otherwise fine. Skipped all events due to release channel:
Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.233356 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.235395 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.237559 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.239556 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.241685 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.259370 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.261258 Skipping event due to release channel mismatch Thu May 8 15:15:31 2025 daemon.info tollgate-basic[13609]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:15:56 2025 daemon.info tollgate-basic[13609]: Connecting to relay: wss://relay.tollgate.meStop
tollgate-basic:root@OpenWrt:/tmp# service tollgate-basic stop root@OpenWrt:/tmp# service tollgate-basic status inactiveSwitch to
devchannel:root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "stable", "ensure_default_timestamp": 1746717311 } root@OpenWrt:/tmp# vi /etc/tollgate/install.json root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "dev", "ensure_default_timestamp": 1746717311 }Restart service:
root@OpenWrt:/tmp# service tollgate-basic start root@OpenWrt:/tmp# service tollgate-basic status runningLogread:
Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 NIP94EventID: unknown Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 IPAddressRandomized: false Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: TODO: include min payment (1) for https://mint.minibits.cash/Bitcoin in future Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: TODO: include min payment (1) for https://mint2.nutmix.cash in future Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 Janitor module initialized and listening for NIP-94 events Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861535 Registering handlers... Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861715 Starting HTTP server on all interfaces... Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861834 Starting to listen for NIP-94 events Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Starting Tollgate - TIP-01 Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Listening on all interfaces on port :2121 Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Starting event processing loop Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://nos.lol Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://nostr.mom Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 15:21:30 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.meTrigger new event: ``` c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 416 bytes | 416.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git 1157a2f..e775bce multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_package
{ "id": "c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746718037, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk" ], [ "m", "application/octet-stream" ], [ "x", "cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078" ], [ "ox", "cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-93-e775bce" ], [ "release_channel", "dev" ] ] } ```
New event caught, updated and restarted:
Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Started the timer Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Arch Keys count: 61 Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:29 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:29.928620 Timeout reached, checking for new versions Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Newer package version available: multiple_mints_rebase_taglist_detect_package-93-e775bce Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Downloading package from https://blossom.swissdash.site/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk to /tmp/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk Thu May 8 15:27:34 2025 daemon.info tollgate-basic[13838]: Package downloaded successfully to /tmp/ Thu May 8 15:27:34 2025 daemon.info tollgate-basic[13838]: New package version is ready to be installed by cronjob Thu May 8 15:27:34 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:34.073022 Verifying package checksum Thu May 8 15:27:34 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:34.082504 Package checksum verified successfully Thu May 8 15:27:55 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 NIP94EventID: c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481 Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 IPAddressRandomized: 10.156.11.1 Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: TODO: include min payment (1) for https://mint.minibits.cash/Bitcoin in future Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: TODO: include min payment (1) for https://mint2.nutmix.cash in future Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Starting Tollgate - TIP-01 Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Listening on all interfaces on port :2121 Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 Janitor module initialized and listening for NIP-94 events Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.915222 Registering handlers... Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.915366 Starting HTTP server on all interfaces... Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.917009 Starting to listen for NIP-94 events Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Starting event processing loop Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Connecting to relay: wss://relay.damus.ioNew config files with new IP address
root@OpenWrt:~# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481" } root@OpenWrt:~# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk", "ip_address_randomized": "10.156.11.1", "install_time": 1746718081, "download_time": 1746718054, "release_channel": "dev", "ensure_default_timestamp": 1746717311, "update_path": null } -
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ f1989a96:bcaaf2c1
2025-05-08 15:05:45
@ f1989a96:bcaaf2c1
2025-05-08 15:05:45Good morning, readers!
This week, we bring reports from Bangladesh, where the interim government instructed the central bank to halt the printing of old banknotes featuring Sheikh Mujibur Rahman, the founding president of Bangladesh. This has induced a currency shortage, as new notes have yet to be issued to replace the discontinued ones. As a result, Bangladeshis find themselves holding worthless currency, facing increased costs, and feeling frustrated over such poor currency management. Meanwhile, in Indonesia, citizens are fleeing to gold as the local rupiah currency crashes to record lows amid increasing financial controls from the government.
In open-source news, LNbits, a Bitcoin and Lightning wallet management software, emerged from beta with its v1.0.0 release. LNbits works like a control panel on top of a Bitcoin wallet, letting users divide funds into separate accounts and use different features and functionalities. It is a handy tool for educators, civil society organizations, and communities who want to use Bitcoin for real-world transactions without needing advanced technical skills. We also spotlight a new tool called following .space that allows users to curate and share premade follow packs for nostr. The result is a more straightforward onboarding process for new users interested in censorship-resistant social media and the ability to curate feeds to better suit their interests.
We end with an interview with HRF Chief Strategy Officer Alex Gladstein, who explores his thinking behind the relationship between Bitcoin and human rights as we enter an age of increased corporate and nation-state adoption. He highlights the paradox where Bitcoin, a tool for individual financial freedom, is being adopted by institutions around the world, many of which regularly seek greater control over financial activity. We also include a new report from Bitcoin developer and past HRF grantee, b10c, who documents the current state of Bitcoin mining centralization and the threat it poses to decentralization and censorship resistance.
Now, let’s jump right in!
SUBCRIBE HERE
GLOBAL NEWS
Bangladesh | Currency Shortage as Central Bank Halts Printing of Banknotes
A state-induced cash crunch is paralyzing Bangladesh after the interim government, led by Muhammad Yunus, ordered the central bank to discontinue old banknotes featuring Sheikh Mujibur Rahman, the founding president of Bangladesh. New cash is expected to be printed in phases beginning in May. But Bangladeshis report they are currently stuck with old and unusable currency, as the national mint has yet to issue replacement currency and lacks the capacity to print more than three notes at a time. Meanwhile, public ATMs continue to dispense old and worn-out banknotes, with merchants reluctantly accepting them and banks refusing to exchange them. Through all this, the central bank of Bangladesh sits on nearly 15,000 crore taka ($1.28 billion) worth of old notes in vaults, but the interim government has refused to release them, deepening public frustration.
Nigeria | Regulates Bitcoin as a Security
Nigerian lawmakers are moving to regulate digital assets as securities by passing the Investment and Securities Act (ISA) 2025. Rather than embrace it as a tool for financial freedom, the law places Bitcoin under the purview of the Nigerian Securities and Exchange Commission (SEC). Companies must now register with the Nigerian SEC, implement more strict data-collection processes (to harvest personal information), and navigate a legal framework not designed for a borderless and permissionless technology like Bitcoin. The law further grants the SEC access to data from telecom and Internet providers to investigate “illegal market activity” — a provision that could easily be abused to surveil or intimidate Bitcoin users and developers. Nigeria routinely uses regulations to stifle the presence of open-source money, raising compliance hurdles, imposing taxes, and punishing digital asset companies. It’s not unreasonable to suspect this new classification could provide the state with a means to suppress the free adoption and innovation of Bitcoin.
Indonesia | Gold Rush Amid Economic Uncertainty
As the rupiah currency falls to record lows, Indonesians are flocking to gold in a rush to protect their savings. But gold isn’t the only safe haven. With 74% of Indonesia’s population unbanked or underbanked, digital tools like Bitcoin offer a more accessible alternative, especially when nearly 70% of Indonesians have Internet access. The Indonesian government is also tightening capital controls. A new policy forces exporters to keep all foreign currency earnings inside the country for a full year to trap dollars in the financial system. HRF grantee Bitcoin Indonesia is responding by helping people in the region (especially in nearby states like Burma) build financial resilience through meetups, workshops, and training focused on Bitcoin custody, privacy, and adoption. In an area where financial services remain out of reach for millions, learning how to save and transact permissionlessly is paramount.
Kenya | Introduces Legal Framework for Virtual Asset Service Providers (VASPs)
Kenya’s government introduced a comprehensive legal framework to regulate Virtual Asset Service Providers (VASPs) through its newly proposed 2025 VASP Bill. The legislation outlines strict licensing requirements for digital asset exchanges, wallet providers, brokers, and other digital asset firms. It functionally bars individuals from operating independently (think: open-source freedom tech builders) by mandating local incorporation, compliance with cybersecurity standards, and approval from financial regulators. This appears to be an attempt to formalize and better control the rapidly growing digital asset space. It could stifle grassroots innovation and limit access to financial tools that have become vital for activists and citizens seeking privacy and autonomy as economic policies and high inflation drive unrest.
El Salvador | Attorney General’s Office Preparing Arrest Warrants for Independent Journalists
El Faro, one of El Salvador’s most prominent investigative news outlets, shared reliable information that the Salvadoran Attorney General’s Office is preparing arrest warrants against three of its journalists. The warning came from El Faro director Carlos Dada, who suggests that the charges may include “apology for crimes” and “illicit association.” The alleged charges allegedly stem from El Faro’s latest reporting: a three-part video interview with former leaders of the 18th Street Revolucionarios gang that sheds light on Bukele’s “years-long relationship” with Salvadoran gangs. El Faro editor-in-chief Óscar Martínez said that any arrests or home raids following this news would be “for having done journalism.” With El Salvador’s shrinking civic space, this potential action against independent media would further restrict Salvadorans’ ability to access independent information and hold officials accountable.
BITCOIN AND FREEDOM TECH NEWS
LNbits | Emerges from Beta with v1.0.0 Release
LNbits, an open-source software tool that lets people create and manage Bitcoin Lightning wallets securely for themselves and for others, officially launched version 1.0.0, marking its transition out of beta and into a more stable release for public use. It works like a control panel sitting on top of a Bitcoin wallet, letting users divide funds into separate accounts and use different features and functionalities. LNbits is especially useful for educators, small businesses, and community organizers who want to use and manage Bitcoin for payments and savings. HRF is pleased to see this Bitcoin Development Fund (BDF) grantee strengthen the tools available to activists to achieve financial freedom in the face of censorship, surveillance, or inflation.
SeedSigner | Self-Custody Tool for Chinese Bitcoiners Facing Local Corruption
Chinese Bitcoin users are turning to SeedSigner, an open-source and fully customizable Bitcoin hardware wallet, as a more private way to protect their savings from law enforcement corruption. While many assume the primary threat to Bitcoin in China comes from top-down management and enforcement from the Chinese Communist Party (CCP), new reports suggest greater concern over the police, who regularly monitor mail, detect hardware wallet purchases, and fabricate charges to extort Chinese users’ Bitcoin. SeedSigner solves this by allowing users to assemble a secure signing device from generic, inexpensive parts, avoiding the risk of shipping a branded wallet that might flag them as a target. When privacy violations begin at the local level, SeedSigner can help citizens safeguard their financial freedom by making secure self-custody discreet, accessible, and affordable.
Following .space | Create and Share Follow Packs on Nostr
Following.space is a new tool for nostr that solves one of the protocol’s biggest pain points: finding people worth following in the absence of an algorithm. Created by developer and HRF grantee Calle, the tool lets anyone build and share curated “follow packs” — pre-made lists of nostr users that can be easily distributed across the web. The lists are customizable and can be made based on shared interests, communities, organizations, regions, and more. This makes onboarding new users easier and allows users to curate their feeds to suit their interests. The result is a simple but powerful tool that helps nostr scale more organically by encouraging natural discovery. Enabling free expression and connections without reliance on centralized platforms strengthens human rights and financial freedom in repressive environments. Try it here.
256 Foundation | Releases Ember One Source Code
The 256 Foundation, an open-source Bitcoin mining initiative, released the source code of its new Ember One Bitcoin mining hashboard to the public. A Bitcoin hashboard is a device with multiple chips for performing Bitcoin mining computations. The open-source Ember One only consumes 100 Watts of total power and is modular by design, allowing user customization and the ability to mine discreetly even under autocratic regimes. This is important because it gives individuals a way to access and earn Bitcoin without drawing the attention of officials. For dissidents, mining at home means gaining more control over how they earn, spend, and store their money, all without relying on centralized systems at the whims of dictators.
Btrust and Africa Free Routing | Announce Partnership to Advance African Bitcoin Development
Btrust, a nonprofit advancing Bitcoin development in Africa, awarded a grant to Africa Free Routing, a program within African Bitcoiners, to support five Bitcoin Lightning-focused developer boot camps across the continent in 2025. These bootcamps aim to onboard non-Bitcoin developers into the Bitcoin ecosystem, offering hands-on training, mentorship, and opportunities to contribute to open-source projects. This work strengthens the foundations of freedom tech in Africa, providing tools that allow people to resist financial repression under tyranny. Learn more about the partnership here.
Presidio Bitcoin | Hosting First Hackathon
Presidio Bitcoin, the Bay Area’s first dedicated freedom tech co-working and events space, just announced its first-ever hackathon, which will take place from May 16-17, 2025. This 24-hour hackathon in San Francisco brings together developers and technologists to build and collaborate at the frontier of Bitcoin, AI, and open-source technology. In addition to the hackathon, Presidio is launching a new program offering free three-month access to its workspace for Bitcoin open-source contributors. This is a valuable opportunity to connect with fellow developers, startup founders, and freedom tech advocates in the area. HRF is proud to sponsor this hackathon and is looking forward to how the outcomes might help create better freedom tools for dissidents worldwide. Learn more about the event here.
RECOMMENDED CONTENT
Bitcoin Nation State Adoption Paradox - Interview with Alex Gladstein
In a recent episode of the Bitcoin Fundamentals podcast, hosted by Preston Pysh, Alex Gladstein, HRF’s chief strategy officer, discusses the complexities of Bitcoin’s new era of adoption. He highlights the paradox where Bitcoin, a tool for individual financial freedom, is being adopted by governments, which some believe to be potentially compromising to its core principles. He emphasizes that while governments may adopt it for strategic or economic reasons, in doing so, they expose their populations to a technology that will ultimately weaken state control over money and advance individual liberty and human rights. Watch the full interview here.
Bitcoin Mining Centralization by b10c
In this report, Bitcoin developer and past HRF grantee b10c documents the growing trend of centralization in Bitcoin mining pools. It shows that over 95% of blocks are now mined by just six Bitcoin mining pools, with Foundry and AntPool controlling roughly 60–70% of the hashrate (the computing power dedicated to the Bitcoin network). This marks a rise in mining pool centralization in recent years. While this hasn’t harmed Bitcoin’s censorship resistance yet, it reduces the number of block template producers. This concentration of template producers poses a potential risk to Bitcoin’s neutrality, which is essential for ensuring access to uncensorable money and protecting human rights in autocratic regimes. HRF has happily supported both Hashpool and Public Pool with recent grants to support smaller, independent pools that help preserve Bitcoin's decentralization. Read the full report here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 611021ea:089a7d0f
2025-05-08 15:00:17
@ 611021ea:089a7d0f
2025-05-08 15:00:17This is the 2nd article I've written regarding my thoughts around the nostr health and fitness ecosystem and how something like NIP101h could play a part in enabling an ecosystem of highly specialized apps benefiting from nostr inherent interoperability. I've posted the last article on Wikistr and have continued experimenting with the NIP in a couple of clients. Recently I've been focused on extending the NIP to include calories and workout intensity.
Caloric Data
Let's talk about calories for a minute. Seems simple, right? You burn some, you consume some. But as I started implementing kind 1357 for caloric data, I quickly realized this was too simplistic.
The reality is tracking calories burned through a 10K run is fundamentally different from logging the calories in your morning avocado toast. Different contexts, different metadata, different user flows. Trying to cram both into one kind felt like forcing a square peg through a round hole.
So I split them: - Kind 1357: Calories expended (your run, your workout, even just existing) - Kind 2357: Calories consumed (your meals, snacks, that beer you "forgot" to log)
This wasn't just a technical decision. It reflects how people actually think about and track their health. Nobody mentally lumps "I burned 350 calories on my run" with "I ate a 650 calorie lunch" as the same type of data point. They're related but distinct.
Workout Intensity
Speaking of workouts, RUNSTR has been sending workout data for a while now, but workout intensity (kind 1356) is something I've been particularly excited about.
Why? Because intensity is the secret sauce that makes fitness data meaningful. Two people can run the same distance, but one might be casually jogging while catching up on podcasts, and another might be doing high-intensity intervals that leave them gasping for air.
Same distance, totally different physiological impacts.
Intensity gives context to duration. It turns "I worked out for 45 minutes" into a meaningful metric about how hard you pushed. And this isn't just for the fitness obsessed—it's essential for things like heart rate zone training, progressive overload, and recovery monitoring.
The Bigger Vision: Why I'm Building This
I'm not building NIP-101h because I think the world needs another fitness standard. God knows there are plenty already. I'm building it because I believe health data belongs to people, not platforms.
Right now, your Apple Health data lives in Apple's ecosystem. Your Fitbit data lives in Fitbit's walled garden. Your Strava data? Yep, siloed there too. These companies have built incredible products, but they've also created digital gulags.
Nostr gives us a chance to flip the script. What if your health data lived on the internet rather than the platform? What if you could: - Track your runs in RUNSTR - Encrypt sensitive data - Store data in relays or blossom servers - Use the data across an open ecosystem of interoperable apps
...all without asking permission from some corporate overlord?
That's pretty much the vision. I've also spun up HealthNote Relay to support some of the new NIPs and Kinds while I continue to flesh out NIP-101h.
The Power of Specialization
One thing I've realized is that the real magic happens when we get specific. A diabetes management app needs different data structures than a strength training app. But they both benefit from a common language for the overlap.
So I'm intentionally designing the NIP-101h series as a collection of highly specialized kinds rather than a monolithic standard. This lets developers pick and choose exactly what they need, while still ensuring interoperability where it matters.
Take our calorie example—by splitting into two kinds, we allow for specialized nutrition tracking apps that might never care about workout calories, while still ensuring they can talk to fitness apps when needed.
What's Coming Next
I've got a growing list of kinds I want to tackle: - Sleep data (duration, quality, phases) - Strength training specifics (sets, reps, weight) - Hydration tracking - Mental health metrics
But I'm equally excited to see what others build. Maybe someone will create specialized kinds for pregnancy tracking, or chronic illness management, or physical therapy progress.
That's the beauty of this approach—I don't need to anticipate every use case. The framework lets the community evolve it organically.
Join the Health Data Revolution
If you're a developer interested in health and fitness on Nostr, I'd love to hear from you. What kinds would help your use case? What are you building? What am I missing?
And if you're just a Nostr user who cares about your health data, check out RUNSTR (Alpha) or Npub.health (super alpha) to see what we're building.
You can find information the specification here NIP 101h.
See you in volume three, where I'll dig into NIP101h format details and share what I've learned from the early experiments.
Lets Go!
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 5b730fac:9e746e2a
2025-05-08 14:55:38
@ 5b730fac:9e746e2a
2025-05-08 14:55:38| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | dev | Already Installed | Automatic | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzdfex5unzvfcfywh0x |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746714091, "kind": 1063, "tags": [ [ "url", "https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk" ], [ "m", "application/octet-stream" ], [ "x", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "ox", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-91-ca43710" ], [ "release_channel", "dev" ] ], "content": "TollGate Module Package: basic for gl-mt3000" }Current version picked up by opkg:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-91-ca43710Check basic module's logic
Config.json contains the right event ID:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9" }Install.json contains the right package path:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746714121, "download_time": 1746714105, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Update package manually
Trigger new event announcement on this branch
New NIP94 event on this branch
{ "id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746715485, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk" ], [ "m", "application/octet-stream" ], [ "x", "1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3" ], [ "ox", "1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-92-1157a2f" ], [ "release_channel", "dev" ] ] }The new version was updated automatically despite internet gateway interruption: ``` Thu May 8 14:44:51 2025 daemon.info tollgate-basic[10154]: Subscription successful on relay wss://relay.damus.io Thu May 8 14:44:51 2025 daemon.info tollgate-basic[10154]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Started the timer Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Arch Keys count: 59 Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:05 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:05.228500 Timeout reached, checking for new versions Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Newer package version available: multiple_mints_rebase_taglist_detect_package-92-1157a2f Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Downloading package from https://blossom.swissdash.site/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk to /tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk Thu May 8 14:45:07 2025 daemon.info tollgate-basic[10154]: Package downloaded successfully to /tmp/ Thu May 8 14:45:07 2025 daemon.info tollgate-basic[10154]: New package version is ready to be installed by cronjob Thu May 8 14:45:07 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:07.693753 Verifying package checksum Thu May 8 14:45:07 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:07.703697 Package checksum verified successfully Thu May 8 14:45:10 2025 daemon.info tollgate-basic[10154]: Started the timer Thu May 8 14:45:22 2025 daemon.info tollgate-basic[10154]: Connecting to relay: wss://relay.tollgate.me Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.453098 Timeout reached, checking for new versions Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Newer package version available: multiple_mints_rebase_taglist_detect_package-92-1157a2f Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.461627 Verifying package checksum Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.471684 Package checksum verified successfully Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.471744 Verifying package checksum Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Package /tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk already exists with correct checksum, skipping download Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.481076 Package checksum verified successfully Thu May 8 14:45:47 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:47.810824 Relay wss://nos.lol disconnected, attempting to reconnect Thu May 8 14:45:47 2025 daemon.info tollgate-basic[10154]: Connecting to relay: wss://nos.lol Thu May 8 14:45:47 2025 daemon.info tollgate-basic[10154]: Connected to relay: wss://nos.lol
```
New version picked up by opkg: ``` root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-92-1157a2f
```
tollgate-basic is running again:
root@OpenWrt:/tmp# service tollgate-basic status runningEvent id in config is fine:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b" }install.json is fine: ``` root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746715561, "download_time": 1746715507, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }
```
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 000002de:c05780a7
2025-05-08 14:55:34
@ 000002de:c05780a7
2025-05-08 14:55:34There are so many projects in the bitcoin space that deserve praise but I just wanna shout out Cashu.me. Its a browser based cashu (eCash / Lighting) wallet. It can be very handy when you need a wallet but don't wanna download yet another app. I hadn't used it in a very long time and decided to try it out again the other day. Its really well done.
As with other Cashu wallets you need to select a mint and backup your key phrase but it is very simple the get started.
If you wanna learn more about Cashu check out Cashu.space
Two other good wallets that support Cashu.
originally posted at https://stacker.news/items/974759
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 1893da11:a9bd4471
2025-05-08 14:42:20
@ 1893da11:a9bd4471
2025-05-08 14:42:20Introduction: The Challenge of Bitcoin-Secured Loans
Bitcoin holders often face a dilemma: they need liquidity but don't want to sell their assets, potentially missing out on future gains or triggering taxable events. Bitcoin-secured loans offer a solution, allowing users to borrow cash (like digital dollars) using their Bitcoin as collateral. However, the current landscape is fraught with challenges. Many existing solutions require users to trust centralized entities or involve complex mechanisms like wrapping Bitcoin, exposing them to significant risks:
- Custodial Risk: Handing over your Bitcoin to a third party means trusting they won't lose it, misuse it, or become insolvent. Billions have been lost this way.
- Smart Contract Risk: Platforms built on chains like Ethereum rely on complex smart contracts, which can contain bugs or vulnerabilities exploitable by hackers.
- Oracle Risk: Loan systems need reliable price feeds (oracles) to manage collateral. Centralized or manipulatable oracles can lead to unfair liquidations.
- Privacy Risk: Loan details and transactions are often publicly visible on the blockchain.
- Complexity and Cost: Existing processes can be slow, require extensive documentation, and involve high fees.
There's a clear need for a better way – one that is simple, reliable, and minimizes trust. This is where the Lava Loans Protocol comes in.
What is Lava Loans?
In simple terms, Lava Loans provides a way to borrow digital dollars using your native Bitcoin as collateral, directly from your own vault. It's designed to be:
- Simple & Fast: Get a loan in seconds with minimal questions asked.
- Low-Cost & Flexible: Offers competitive rates, dynamic fee structures, and allows borrowing any amount.
- Reliable & Trust-Minimized: Leverages Bitcoin's own capabilities to reduce reliance on intermediaries and enhance security.
How Lava Loans Addresses the Risks
Lava tackles the common pitfalls of crypto loans head-on:
- Eliminating Custodial Risk: Instead of transferring your Bitcoin to a custodian or wrapping it, Lava uses native Bitcoin locked directly on the Bitcoin network within a special type of contract. This prevents rehypothecation and loss through hacks or confiscation.
- Minimizing Smart Contract Risk: Lava utilizes Bitcoin smart contracts, also known as Discreet Log Contracts (DLCs). These are designed to be less complex and more secure than many general-purpose smart contracts, with outcomes pre-defined and formally verified.
- Reducing Oracle Risk: Users choose their own off-chain, blinded oracles (called Sibyls) for price data, with enhanced redundancy to ensure reliability. Off-chain attestations avoid high fees and miner manipulation risks associated with on-chain oracles. Blinded oracles provide price data without knowing the specific contract they influence, preventing targeted attacks.
- Enhancing Privacy: Because DLCs operate differently from typical public smart contracts, the details of the loan contract are not broadcast publicly on the Bitcoin blockchain.
- Trustless Initiation & Repayment: Atomic swaps ensure that collateral only moves to the contract once the loan is received, and collateral is automatically returned upon verified repayment.
The Magic Ingredients: DLCs and Sibyls Oracles
Two core technologies make Lava Loans unique:
-
Discreet Log Contracts (DLCs): Think of a DLC as a pre-programmed Bitcoin transaction agreed upon by the borrower and lender. Before the loan starts, they define all possible outcomes (e.g., repayment, liquidation at a specific price, expiry) and create encrypted signatures for each. The Bitcoin collateral is locked in a multisig output controlled by these pre-signed transactions. Only the conditions agreed upon (verified by oracle signatures) can unlock the funds according to the pre-defined rules. This offers:
- Security: Formally verified, pre-defined outcomes minimize bug risk.
- Privacy: Contract details remain off-chain.
- Scalability: Minimal on-chain footprint as execution logic is off-chain.
- Customization: Users can choose their own oracles and LTV thresholds.
-
Sibyls Oracles: These are the independent price feed providers for Lava. Key characteristics include:
- Off-Chain: Attestations happen off-chain, avoiding blockchain fees and manipulation.
- User-Chosen: Borrowers select the oracles they trust for each loan.
- Blinded: Oracles provide signed price data without knowing the specific DLC it applies to, enhancing security.
- Redundant: Multiple oracles can be configured to provide fallback price feeds, reducing the risk of oracle failure.
System Overview
Here's a high-level look at the components involved in the Lava Loans ecosystem:
[ Borrower ] --(locks Bitcoin)--> [ DLC Contract (Bitcoin) ] [ Lender ] --(sends stablecoins)--> [ Alt-Chain Contract (Solana) ] [ Oracles ] --(provides price)--> [ DLC Contract (Bitcoin) ] [ Borrower ] --(repays loan)--> [ Alt-Chain Contract (Solana) ] [ Lender ] --(claims collateral)--> [ DLC Contract (Bitcoin) ]The Lava Loan Lifecycle
A loan progresses through several states:
- Initialized: A trustless atomic swap occurs. The borrower locks Bitcoin collateral into the DLC on the Bitcoin network, and the lender locks the loan capital (e.g., digital dollars on a network like Solana using HTLCs) which the borrower then claims.
- Active: The collateral is secured in the DLC, and the borrower has the loan capital. The Lava Protocol monitors the loan-to-value (LTV) ratio using price data from the chosen Sibyls oracles, with customizable LTV thresholds for greater flexibility.
- Terminated: The loan concludes in one of several ways:
- Repaid: The borrower repays the loan capital plus interest on the loan asset network, with dynamic fees adjusting based on network conditions. Upon verification, the DLC automatically releases the Bitcoin collateral back to the borrower.
- Liquidated: If the Bitcoin price drops and the LTV reaches a pre-determined threshold (now more flexible to avoid premature liquidations), the DLC automatically releases the collateral to the lender.
- Expired: If the loan term ends before repayment, the DLC releases an amount equivalent to the principal plus interest to the lender, and the remaining collateral is returned to the borrower.
- Fail-safe: In rare cases of unresponsive oracles, redundant Sibyls oracles and built-in mechanisms ensure collateral is not permanently lost.
Loan Process Sequence
The following diagram illustrates the typical sequence of events in a Lava Loan:
1. Borrower --> DLC: Create loan contract with collateral 2. Lender --> Alt-Chain: Fund loan with stablecoins 3. Borrower --> Alt-Chain: Receive and use stablecoins 4. (If repayment) 4a. Borrower --> Alt-Chain: Repay loan 4b. Lender --> Alt-Chain: Confirm repayment 4c. Borrower --> DLC: Claim collateral 5. (If liquidation) 5a. Oracle --> DLC: Provide price attestation 5b. Lender --> DLC: Claim collateral 6. (If expiry) 6a. Borrower/Lender --> DLC: Split collateralLava Loans vs. Other Bitcoin Lending Platforms: A Quick Comparison
How does Lava stack up against typical DeFi lending protocols and other Bitcoin lending platforms like Unchained, Strike, and Coinbase?
| Feature | Lava Loans (Bitcoin) | Typical Ethereum DeFi | Unchained | Strike | Coinbase | | :------------------- | :---------------------------------------------------- | :-------------------------------------------------------- | :---------------------------------------------------- | :---------------------------------------------------- | :---------------------------------------------------- | | Collateral | Native Bitcoin | Often Wrapped Bitcoin (wBTC) or other assets | Native Bitcoin | Native Bitcoin | Native Bitcoin | | Contract Type | Discreet Log Contracts (DLCs) - Pre-agreed, Private | Smart Contracts - Public, Complex, Run on EVM | 2/3 Multisig Vaults | Custodial Contracts | Custodial Contracts | | Security | Aims for higher security via simpler, pre-set DLCs | Can be complex, potential for bugs/exploits | Secure via multisig, but relies on key holders | Custodial, less transparent | Custodial, less transparent | | Privacy | Higher privacy (contract details off-chain) | Lower privacy (contract interactions often public) | Moderate privacy (multisig details on-chain) | Lower privacy (custodial model) | Lower privacy (custodial model) | | Oracles | User-chosen, Off-chain, Blinded (Sibyls) | Often On-chain, potentially manipulatable | Not applicable (manual monitoring) | Centralized oracles | Centralized oracles | | Trust | Designed to minimize trust in intermediaries | Often requires trust in custodians, bridges, or protocols | Moderate trust (key holders could collude) | Higher trust (custodial, opaque practices) | Higher trust (custodial, opaque practices) | | Rehypothecation | No rehypothecation, verifiable on-chain via DLCs | Possible, depends on protocol | No rehypothecation, secured by multisig | Opaque, likely rehypothecated | Opaque, likely rehypothecated | | Interest Rates | Competitive, typically lower due to non-custodial model | Varies, often 5-10% for wBTC loans | 11-14% for non-rehypothecated loans | 12-13% (implies rehypothecation) | ~5-6% (implies rehypothecation) |
Lava leverages Bitcoin’s native capabilities and a specific oracle design to prioritize security, privacy, and trust minimization. Unlike Unchained, which uses a 2/3 multisig where two key holders could potentially collude, Lava’s DLCs ensure cryptographic proof of non-rehypothecation, verifiable on-chain in real time. Strike and Coinbase, being custodial, lack transparency about rehypothecation practices, with market rates suggesting they rehypothecate collateral. The v3 protocol introduces dynamic fee adjustments and more flexible LTV thresholds, reducing premature liquidations and optimizing costs based on network conditions.
Conclusion
Lava Loans presents a compelling option for those seeking liquidity against their Bitcoin holdings without sacrificing security or control. By utilizing Discreet Log Contracts, a user-centric, blinded oracle system (Sibyls) with enhanced redundancy, and new features like dynamic fees and flexible LTV thresholds, Lava provides a simple, reliable, and trust-minimized borrowing experience. These advancements directly address the major pain points found in many existing centralized and decentralized lending platforms.
References
- Maredia, Shehzan. "Lava Loans". Lava Blog, April 9, 2025. https://www.lava.xyz/blog/lava-loans
- https://github.com/lava-xyz/loans-paper/blob/main/loans_v3.pdf
- https://github.com/lava-xyz/sibyls
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 5b730fac:9e746e2a
2025-05-08 14:32:04
@ 5b730fac:9e746e2a
2025-05-08 14:32:04| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | dev | Already Installed | Manual | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzdp4xvmnvdpkpctkgk |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746711607, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk" ], [ "m", "application/octet-stream" ], [ "x", "0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97" ], [ "ox", "0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-89-4e46a9b" ], [ "release_channel", "dev" ] ] }Installed here:
Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Started the timer Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Arch Keys count: 56 Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:23 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:23.779018 Timeout reached, checking for new versions Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Newer package version available: multiple_mints_rebase_taglist_detect_package-89-4e46a9b Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Downloading package from https://blossom.swissdash.site/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk to /tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk Thu May 8 13:40:28 2025 daemon.info tollgate-basic[6709]: Package downloaded successfully to /tmp/ Thu May 8 13:40:28 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:28.863469 Verifying package checksum Thu May 8 13:40:28 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:28.873010 Package checksum verified successfully Thu May 8 13:40:28 2025 daemon.info tollgate-basic[6709]: New package version multiple_mints_rebase_taglist_detect_package-89-4e46a9b is ready to be installed by cronjob Thu May 8 13:41:06 2025 daemon.err tollgate-basic[7713]: 2025/05/08 13:41:06 NIP94EventID: 33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988 Thu May 8 13:41:06 2025 daemon.err tollgate-basic[7713]: 2025/05/08 13:41:06 IPAddressRandomized: 192.168.3.1Current version picked up by opkg:
root@OpenWrt:~# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-89-4e46a9bCheck basic module's logic
Config.json contains the right event ID: ``` root@OpenWrt:~# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988" }
```
Install.json contains the right package path:
root@OpenWrt:~# cat /etc/tollgate/install.json { "package_path": "/tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746711661, "download_time": 1746711628, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Update package manually
Prevent automatic update
Stop
tollgate-basicso that it doesn't automatically update to newer event kinds.root@OpenWrt:~# service tollgate-basic stop root@OpenWrt:~# service tollgate-basic status inactiveTrigger new event announcement on this branch
New NIP94 event on this branch
c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 429 bytes | 429.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git 4e46a9b..ad29788 multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_packageThe new version that we will install manually:
{ "id": "2ff8b1e63036f03884a82450c811d9df0ed2b9f1a4099bbb1e4308e1d845be97", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746712364, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk" ], [ "m", "application/octet-stream" ], [ "x", "e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059" ], [ "ox", "e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-90-ad29788" ], [ "release_channel", "dev" ] ] }The installation:
root@OpenWrt:/tmp# wget https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk Downloading 'https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk' Connecting to 212.47.72.157:443 Writing to 'e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk' e8633b4c2ceb05b5fd45 2943k --:--:-- ETA Download completed (4509706 bytes) root@OpenWrt:/tmp# opkg install e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk Upgrading tollgate-module-basic-go on root from multiple_mints_rebase_taglist_detect_package-89-4e46a9b to multiple_mints_rebase_taglist_detect_package-90-ad29788... Command failed: Not found Removing existing banner file if present... Configuring tollgate-module-basic-go. nodogsplash cfg7c92bd Running TollGate NoDogSplash file copy script... Source files: drwxr-xr-x 2 root root 384 May 8 13:57 . drwxr-xr-x 3 root root 224 May 8 13:50 .. -rw-r--r-- 1 root root 599 May 8 13:50 asset-manifest.json -rw-r--r-- 1 root root 312 May 8 13:50 manifest.json -rw-r--r-- 1 root root 642 May 8 13:50 splash.html Copying splash.html... IP is already randomized or not set to false. Exiting.Current version picked up by opkg:
root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-90-ad29788 root@OpenWrt:/tmp#tollgate-basic is running again:
root@OpenWrt:/tmp# service tollgate-basic status runningEvent ID successfully set to
unknown:root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "unknown" }install.jsonis still pointing at dev channel:root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746712641, "download_time": 1746711628, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Trigger new event announcement on this branch
Trigger new event:
c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 418 bytes | 418.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git ad29788..ca43710 multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_packageNew event json:
{ "id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746714091, "kind": 1063, "tags": [ [ "url", "https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk" ], [ "m", "application/octet-stream" ], [ "x", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "ox", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-91-ca43710" ], [ "release_channel", "dev" ] ], "content": "TollGate Module Package: basic for gl-mt3000" }Logread output: ``` Thu May 8 14:12:11 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:12:11.615394 Relay wss://relay.damus.io disconnected, attempting to reconnect Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Connecting to relay: wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Connected to relay: wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Subscription successful on relay wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 14:20:41 2025 daemon.info tollgate-basic[8933]: Connecting to relay: wss://relay.tollgate.me Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Started the timer Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-90-ad29788 basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-90-ad29788 basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Arch Keys count: 115 Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:43 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:43.304879 Timeout reached, checking for new versions Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Newer package version available: multiple_mints_rebase_taglist_detect_package-91-ca43710 Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Downloading package from https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk to /tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk Thu May 8 14:21:45 2025 daemon.info tollgate-basic[8933]: Package downloaded successfully to /tmp/ Thu May 8 14:21:45 2025 daemon.info tollgate-basic[8933]: New package version is ready to be installed by cronjob Thu May 8 14:21:45 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:45.667395 Verifying package checksum Thu May 8 14:21:45 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:45.676755 Package checksum verified successfully Thu May 8 14:22:06 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:22:06 NIP94EventID: 51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9 Thu May 8 14:22:06 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:22:06 IPAddressRandomized: 192.168.3.1
```
Config has the right event id again:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9" }Install.json has the right file path again:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746714121, "download_time": 1746714105, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null } -
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 66df6056:f3203c64
2025-05-08 14:28:51
@ 66df6056:f3203c64
2025-05-08 14:28:51งาน Bitcoin++ ประจำปี 2025 ที่จัดขึ้นที่เมืองออสติน รัฐเท็กซัส เป็นการรวมตัวของนักพัฒนา Bitcoin ที่เจาะลึกในประเด็นทางเทคนิค โดยเฉพาะอย่างยิ่งเรื่อง Mempool, Transaction Relay และ Mining Pools หัวข้อเหล่านี้ถูกเน้นย้ำว่าเป็นหัวข้อที่น่าสนใจและเป็นที่ถกเถียงกัน เป้าหมายหลักของงานคือเพื่อให้เหล่านักพัฒนาและผู้สร้างสรรค์ได้แบ่งปันสิ่งที่พวกเขากำลังทำอยู่ เรียนรู้เกี่ยวกับความท้าทายในการนำ Transaction เข้าสู่ Block และการปรับปรุง Bitcoin รวมถึงส่งเสริมการเติบโตของชุมชน Open-Source
งานในปีนี้เป็นครั้งแรกที่มุ่งเน้นไปที่ Mempool และ Transaction Relay โดยเฉพาะ ซึ่งเกี่ยวข้องโดยตรงกับการสร้าง Block Mempool ถูกมองว่าเป็นพื้นที่ส่วนรวม (commons) และเป็นตลาดประมูลที่เสรีและเปิดกว้างที่สุดแห่งหนึ่งของโลก ที่ซึ่งใครก็ตามที่เป็นเจ้าของ Bitcoin สามารถเสนอราคา (ค่าธรรมเนียม) และใครก็ตามที่ขุด Bitcoin ก็สามารถยอมรับราคานั้นและนำ Transaction เข้า Block ได้ แม้ว่ากระบวนการนี้จะมีความท้าทายและบางครั้งก็เป็นที่ถกเถียงกัน แต่ Bitcoin ยังคงทำงานเป็นระบบแบบอนาธิปไตย (anarchic system) ที่การพัฒนาเกิดขึ้นในลักษณะกระจายศูนย์
ประเด็นร้อน: OP_RETURN และการถกเถียงเรื่อง Data Carrier
หนึ่งในประเด็นหลักที่ถูกกล่าวถึงและมีการจัดดีเบตแบบ Oxford-style คือเรื่องขีดจำกัดของ Data Carrier ใน OP_RETURN โดยเฉพาะการถกเถียงเรื่องการปลดขีดจำกัดค่าเริ่มต้นใน Bitcoin Core การถกเถียงนี้สะท้อนให้เห็นถึงความตึงเครียดระหว่างกลุ่มที่เรียกว่า "Monetary Maximalists" ซึ่งต้องการให้ Bitcoin เป็นเงินที่ดีที่สุด กับกลุ่ม "Platform Maximalists" ที่ต้องการให้ Bitcoin สามารถทำสิ่งต่างๆ ที่ไม่เกี่ยวข้องกับเงินได้มากขึ้น เช่น การออก Token บน Bitcoin
ฝ่ายที่สนับสนุนการปลดขีดจำกัดแย้งว่ามันเป็นปัญหาทางเทคนิคที่ไม่มีวิธีที่มีหลักการในการป้องกันอย่างแท้จริงในระดับ Consensus การพยายามใช้ Filter ใน Mempool เพื่อป้องกันนั้นไม่สามารถทำได้อย่างสมบูรณ์ และผู้ใช้สามารถหาวิธีหลีกเลี่ยงได้ การปลดขีดจำกัดอาจช่วยลดการสร้าง UTXO ที่ใช้ไม่ได้ (unspendable UTXOs) ซึ่งเป็นสิ่งที่แย่กว่า OP_RETURN และจะช่วยประหยัดเวลาของนักพัฒนาจากการโต้เถียงในเรื่องเล็กๆ น้อยๆ
ขณะที่ฝ่ายคัดค้านการปลดขีดจำกัดยืนยันว่า Filter ใน Mempool ทำงานได้ผลในการยับยั้งการใช้ OP_RETURN สำหรับข้อมูลที่ไม่ใช่ทางการเงิน และการปลดขีดจำกัดจะเป็นการทำลาย Filter ที่มีอยู่ พวกเขาแย้งว่า Bitcoin ถูกออกแบบมาให้เป็นระบบการเงิน ไม่ใช่ฐานข้อมูลสำหรับเก็บข้อมูลตามอำเภอใจ การอนุญาตให้เก็บข้อมูลที่ไม่ใช่ทางการเงินจำนวนมากจะทำให้ Transaction ของผู้ใช้ทั่วไปมีค่าใช้จ่ายสูงขึ้น และเป็นการ "ขาย Bitcoin ให้กับผู้ที่เสนอราคาสูงสุด" ซึ่งอาจนำไปสู่การบ่อนทำลายโดยผู้ที่ควบคุมระบบการเงินแบบเก่า พวกเขายืนยันว่า Bitcoin ควรเน้นการเป็นเงิน และการเปลี่ยนแปลงที่ไม่จำเป็นซึ่งทำลาย Filter ที่ทำงานอยู่จะทำให้ความไว้วางใจใน Bitcoin Core ลดลง นอกจากนี้ยังมีการพูดถึงทางเลือกในการใช้ Filter ในระดับ Node เช่นที่ implement ใน Bitcoin Knots
ความรวมศูนย์ในการขุดและการกระจายศูนย์
ปัญหาความรวมศูนย์ใน Mining Pool เป็นอีกหัวข้อที่มีการหารืออย่างกว้างขวาง โดยเฉพาะเรื่องความหลากหลายของ Block Template เครื่องมืออย่าง stratum.work ถูกสร้างขึ้นมาเพื่อช่วยให้ผู้สังเกตการณ์สามารถเปรียบเทียบ Block Template จาก Pool ต่างๆ ได้ ข้อมูลแสดงให้เห็นว่า Antpool และ Pool ที่เป็น "เพื่อน" (Antpool and friends) รวมถึง Foundry มีส่วนแบ่ง Hash Rate รวมกันค่อนข้างสูง ซึ่งทำให้เกิดความกังวลเกี่ยวกับความรวมศูนย์ ปัญหาดังกล่าวถูกมองว่าเป็นปัญหาเชิงเศรษฐศาสตร์และแรงจูงใจ มากกว่าปัญหาทางเทคนิคล้วนๆ
ทางออกในการกระจายศูนย์การขุดและการสร้าง Block Template ถูกนำเสนอ โดยเฉพาะโปรโตคอล Datam ที่พัฒนาโดย Ocean Mining Datam ถูกออกแบบมาเพื่อการขุดแบบกระจายศูนย์โดยเฉพาะ โดย กำหนดให้ Miner ต้องรัน Node ของตัวเองเพื่อสร้าง Block Template ซึ่งแตกต่างจาก Stratum V2 ที่ยังคงมีการใช้งานแบบรวมศูนย์อยู่ Datam Gateway ทำหน้าที่เป็นตัวเชื่อมระหว่าง Miner กับ Pool โดยใช้ Stratum V1 แต่ Miner เป็นผู้สร้าง Block Template เอง โปรโตคอล Datam นั้นเรียบง่าย ใช้ภาษา C เพื่อให้มีขนาดเล็กและมีประสิทธิภาพสูง สามารถทำงานบน Raspberry Pi ได้ และมีการเข้ารหัสระหว่าง Pool กับ Gateway การสร้าง Datam ขึ้นมาใหม่จากศูนย์เป็นเพราะไม่มีโปรโตคอลหรือซอฟต์แวร์ Pool เดิมที่ตอบโจทย์การกระจายศูนย์ได้อย่างสมบูรณ์
การแก้ไข Bug ใน Consensus (Consensus Cleanup)
มีการนำเสนอ BIP 54 หรือ Great Consensus Cleanup ซึ่งเป็นข้อเสนอ Soft Fork เพื่อแก้ไข Bug เล็กน้อยในกฎ Consensus ของ Bitcoin จุดประสงค์ไม่ใช่การเปลี่ยนแปลงคุณค่าหลักของ Bitcoin แต่เป็นการแก้ไข Bug ที่สามารถทำได้ผ่าน Soft Fork Bug เหล่านี้รวมถึงปัญหาที่อาจนำไปสู่การมี Transaction ID (TXID) ของ Coinbase ซ้ำกันในอนาคตสำหรับ Block ที่เกิดขึ้นก่อน BIP 34 การแก้ไขใน BIP 54 เกี่ยวข้องกับการใช้ Time Locking และการกำหนดค่า End Sequence ใน Coinbase Transaction เพื่อป้องกันปัญหานี้ ข้อเสนอนี้ถูกพัฒนาขึ้นโดย Antoine Riard และมีการหารืออย่างละเอียด
ความปลอดภัยทางควอนตัมในอนาคต
ประเด็นเรื่องความปลอดภัยทางควอนตัมของ Bitcoin ก็ถูกหยิบยกขึ้นมาพูดคุย แม้จะดูเป็นปัญหาที่ไกลตัว แต่ก็เป็นสิ่งสำคัญที่จะต้องมีแผนรองรับ BIP 360 ถูกนำเสนอเป็นข้อเสนอ Soft Fork ทางเลือก (Opt-in soft fork) เพื่อเพิ่มความปลอดภัยทางควอนตัมให้กับ Bitcoin ปัญหาหลักคือผู้ใช้จะต้องเปิดเผย Public Key และ Signature เมื่อใช้จ่าย Transaction และคอมพิวเตอร์ควอนตัมอาจสามารถคำนวณ Private Key จาก Public Key ได้ BIP 360 เสนอให้เพิ่มข้อมูล Public Key และ Signature ที่ผ่านการป้องกันควอนตัมเข้าไปใน Transaction โดยรองรับ Taproot อย่างไรก็ตาม Multisig บางประเภท เช่น P2SH หรือ P2WSH อาจให้การป้องกันได้ดีกว่า เนื่องจากผู้โจมตีจะต้องหา Private Key หลายตัว ในขณะที่ Key Path Spend ของ Taproot อาจไม่ช่วยป้องกันปัญหานี้ BIP 360 ยังกำหนดให้มี Public Key ที่ป้องกันควอนตัมเพียงตัวเดียวเพื่อหลีกเลี่ยงความกำกวมของที่อยู่ Taproot
นวัตกรรมและกรณีใช้งานอื่นๆ
นอกจากนี้ยังมีการกล่าวถึงโครงการอื่นๆ ที่น่าสนใจ เช่น Maple AI ที่มุ่งมั่นสร้าง AI ที่ไม่ใช่แบบรวมศูนย์ และ Open Secret ซึ่งเป็น Framework สำหรับนักพัฒนาในการให้ผู้ใช้สามารถ Self-Custody ข้อมูลของตนเองได้ แนวคิดนี้คล้ายกับการ Self-Custody Bitcoin ใน Wallet โดยมองว่าการถือข้อมูลผู้ใช้เป็นภาระความเสี่ยงสำหรับนักพัฒนา
มีการพูดถึงแนวโน้มที่ผู้เล่นในระบบการเงินแบบเก่าอย่าง Visa และ Stripe กำลังพยายามเข้าสู่พื้นที่ Digital Currency โดยอาจใช้การ Tokenize Credit Card รวมถึงบทบาทที่อาจเกิดขึ้นของ AI Agents ซึ่งอาจเริ่มใช้ Bitcoin หรือ Lightning Network ในการชำระเงินในอนาคต มีการคาดการณ์ว่า AI Agents อาจทำธุรกรรมผ่าน Lightning Network ได้ในระดับที่สูงกว่าการใช้งานของมนุษย์อย่างรวดเร็ว โดยมีการพัฒนาโปรโตคอลอย่าง X402 และ Fusats เพื่อรองรับการชำระเงินสำหรับ Agents โดยเปิดโอกาสให้ Agents เลือกใช้สกุลเงินดิจิทัลที่ดีที่สุดในตลาดเสรี
สุดท้าย งาน Bitcoin++ เน้นย้ำถึงความสำคัญของการประชุมและการรวมตัวกันของนักพัฒนาเพื่อหารือ ประสานงาน และแบ่งปันไอเดีย โดยเฉพาะในประเด็นที่ต้องอาศัยความร่วมมือและการแก้ปัญหาที่ซับซ้อน
-
 @ a296b972:e5a7a2e8
2025-05-08 13:13:51
@ a296b972:e5a7a2e8
2025-05-08 13:13:51Sachzwangfreie, gesichert systemkritische Investigativ-Journalisten der unabhängigen, für Ausgewogenheit bekannten Mainstream-Medien, haben in jahrelanger Recherche den Rechtsruck Deutschlands beobachtet und nun in einem rund 5000 Seiten starken Gutachten dem Bundesamt für Verfassungsschutz zugespielt. Möglicherweise ist Erfahrung in der Veröffentlichung der Tagebücher eines verkannten Künstlers hierbei sehr hilfreich gewesen.
Nach sorgfältiger Überprüfung des Inland-Geheimdienstes konnte festgestellt werden, dass dem 3. Reich zugeschriebenes Gedankengut fortbesteht und dadurch die Unseredemokratie nachhaltig vergiftet ist. Bei der Beurteilung waren die Erkenntnisse der Gauck-Behörde von unschätzbarem Wert.
Ein Magazin, einst bekannt dafür, der Politik scharf auf die Finger zu schauen, und das auch die vorgenannten Tagebücher veröffentlicht hat (das war vor der Zeit, als ein ausgewachsener amerikanischer Voll-Philanthrop mit seiner Großzügigkeit die laufenden Strom- und Heizkosten des Verlagsgebäudes bezahlt hat), scheint hier seine Schreib-Fachkräfte zur Verfügung gestellt zu haben. Das könnte erklären, warum einige Details der nicht zu hinterfragenden Schrift an die Öffentlichkeit gelangt sind.
Schon im Grundgesetz kommt der durch das NS-Regime verbrannte Begriff „Volk“ zwölf Mal vor. So lebt die Ideologie, dass es ein deutsches Volk gibt, auch im Grundgesetz weiter. Vermutlich wurde durch Bestechung und Intrigen der Artikel 116 Absatz 1 hineingeschmuggelt, der besagt, wer Deutscher im Sinne des Grundgesetzes ist. Das fordert zwangsläufig eine dringend notwendige Prüfung, ob nicht das Grundgesetz selbst verfassungswidrig ist.
Mit Gründung der Bundesrepublik Deutschland wurde auch weiterhin im Straßenverkehr am Rechtsverkehr festgehalten, obwohl die Autoindustrie mit Beibehaltung des Lenkrades auf der linken Seite ein klares Zeichen gegen rechts gesetzt hat.
Der Ausbau des deutschen Autobahnnetzes wurde im 3. Reich stark vorangetrieben. Er diente vor allem dazu, eine schnelle Truppenbewegung zu ermöglichen. Schließlich sollte nach Goebbels, vor allem bekannt durch seine Rede im Sportpalast in Berlin, bestmögliche Kriegstüchtigkeit hergestellt werden. Die Waffenproduktion der Hermann-Göring-Werke, heute Rheinmetall, ließen die Hochöfen bereits dauerglühen.
Nach dem 2. Weltenbrand wurde der Ausbau des deutschen Autobahnnetzes weiter vorangetrieben. Statt sie zu entschärfen, wurden extreme Rechtskurven durch Leitplanken gesichert. Weniger scharfe Rechtskurven wurden in einer Liste als Verdachtsfall erfasst und werden seitdem intensiv beobachtet, die Unfallhäufigkeit wird ständig gemessen.
Ein weiteres Indiz für rechtes Gedankengut ist die Tatsache, dass eine bekannte Autofirma ihre Produkte auch in der Bundesrepublik nicht in Bürgerwagen umbenannt hat. So wurde in der Wirtschaftswunderzeit mit einem verfassungswidrigen Kraftfahrzeug mit 37 PS wild in der Gegend herumgefahren und durch Auslandsreisen, gerne an den Gardasee, der Begriff Volk in die ganze Welt getragen. Den Höhepunkt des Gipfels erreichte die Verfassungswidrigkeit jedoch dadurch, dass ein Werk in Brasilien den Bürgerwagen produzierte und so den gesamten amerikanischen Kontinent mit hässlichem Gedankengut verseuchte.
Deutsche Unternehmen, die aus Überzeugung Schrauben und Muttern mit Rechtsgewinde herstellen, können nur überzeugte Rechtsextremisten sein. Alles, was rechts ist oder rechts herum geht, muss zum Schutze von Unseredemokratie verfolgt und verboten werden. Auch die Buchhaltung der Unternehmen gehört reformiert, denn schließlich gibt es mit Soll und Haben eine linke und, staatsgefährdend, auch eine rechte Seite, auf der die Einnahmen und Ausgaben erfasst werden.
In großen Städten wurden nach der bedingungslosen Kapitulation der Wehrmacht Straßen und Plätze, die nach den „Größen“ des 3. Reichs benannt wurden, wieder umbenannt. Es wurde dabei versäumt, Parks in größeren Städten, die sich Volksgarten nennen, in Bürgergarten umzubenennen.
Auch wurde versäumt, ideologisch vergiftete Tischsitten zu reformieren. So liegt das Messer neben dem Teller weiterhin rechts. Die Absicht liegt sozusagen auf der Hand, denn das ist eine eindeutige Aufforderung zu Messergewalt, zumal die meisten Menschen Rechtshänder sind.
An der Schreibweise von links nach rechts wurde weiter festgehalten. Ein weiteres Anzeichen dafür, wie das Volk durch alltägliche Verrichtungen zu einer rechten Gesinnung durch dunkle Kräfte hingeleitet werden soll. Die Schreibweise „kursiv“ wurde nicht verboten, obwohl sie extrem rechts ist.
Offensichtlich wird auch die Indoktrination des Volkes, wenn vom für die Linken diskriminierenden Rechtsstaat die Rede ist. Menschen, die ein gesundes Rechtsverständnis haben, sind ideologisch vergiftet.
Die Auflösung von Familienstrukturen, einst die kleinste tragende Zelle der Gesellschaft, muss dringend umgesetzt werden, da verschworene Gruppen, die im Ernstfall wie Pech und Schwefel zusammenhalten, den Staat delegitimieren. Sie könnten zum Beispiel einen Familienausflug planen, von dem der Staat nichts weiß.
Ein Ehepaar, das nicht mehr zeitgemäß in einem Doppelbett schläft, ist höchstverdächtig. Der Ehepartner, der in einem Ehebett auf der rechten Seite sehr nah an der Bettkante schläft, schläft rechtsextrem. Wenn er ein Gitter am Bett hat, damit er nicht aus dem Bett fällt, schläft er sogar extrem gesichert rechts.
Der Verfassungsschutz muss dringend prüfen, ob nicht das gesamte deutsche Volk verboten werden sollte, denn es ist eindeutig so, dass das Volk völkisch ist und das darf in einer Unseredemokratie keinen Platz haben.
Mit Übergabe des Gutachtens an den Verfassungsschutz sieht dieser es als Geheimsache an, sodass er es aus Gründen des Staatswohls nicht denjenigen gegenüber zugänglich gemacht werden kann, die es betrifft, nämlich das völkische Volk.
Jenes Volk, das dank einer übermenschlichen Autoren-Anstrengung im wirtschaftlichen Bereich immer mehr den nicht mehr vorhandenen Pfennig und die nicht mehr vorhandene Mark umdrehen muss.
Als Volks-Sparmöglichkeiten gibt es jedoch noch:
· Im Outlet-Store Markenartikel 2. Wahl
· Auf dem Markt Spargel 2. Wahl
· Und jetzt auch einen Bundeskanzler 2. Wahl
Warum hat das undankbare deutsche Volk, das die Unseredemokratie nicht genug zu schätzen weiß, immer noch etwas zu meckern?
Wer jetzt behauptet, dass dieser Text absurd ist, der möge sich in der Realität umsehen. Da finden die wirklichen Absurditäten statt. Das hier ist nur Schwurbelei von jemandem, der die Welt nicht mehr versteht.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ c11cf5f8:4928464d
2025-05-08 11:51:12
@ c11cf5f8:4928464d
2025-05-08 11:51:12Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory.
Let's check our top performing post Ads!
Top-Performing Ads
This month, the most engaging ones are:
-
01[SELL] The Book of Bitcoin Mythology - Bitcoin accepted - ($21 + shipping) by @VEINTIUNO offering a printed version of the Bitcoin Mythology @spiral series, available online originally in English and translated by the post author in Spanish. 100 sats \ 6 comments \ 18 Apr -
02[SELL] Southwest voucher, 50k sats (digital code/ USA) by @BlokchainB, where he share a voucher Southwest Airlines. Have you sold it to @itsrealfake then? 206 sats \ 3 comments \ 27 Apr -
03SoapMiner Beef Tallow Soap by @PictureRoom, a review of a great handmade product sold P2P. 83 sats \ 2 comments \ 3 May -
04[SELL] Walter Whites Mega Package eBook (25000) by @MidnightShipper, return selling hand-picked ebooks from his/her huge collection 36 sats \ 4 comments \ 21 Apr -
05Medical Consultation (an update to a previous post) by @BTCLNAT, renewing prices and details of a previous Ad-post. Pretty fair still... 5k sats/consultation still a bargain! 100 sats \ 3 comments \ 22 Apr -
06[SELL] Bitcoin Education Playing Cards $30 Bitcoin accepted by @NEEDcreations, releasing a new updated edition, ow available for sale on the 360BTC's pleb shop 19 sats \ 0 comments \ 30 Apr -
07OFFICIAL - VINTAGE - Marlboro Zippo - Real & WORKS by @watchmancbiz, returns with just a link to SatStash for more info on the auction 0 sats \ 0 comments \ 3 May
A quick reminder that now you ca setup auctions here in the AGORA too! Learn how. The other feature released last month was the introduction of Shopfronts on SN. Check our SN Merch and SN Zine examples. Thank you all! Let's keep these trades coming and grow the P2P Bitcoin circular economy!
Lost & Found in SN' Wild West Web
Stay with me, we're not done yet! I found plenty of other deals and offers in other territories too..
- Private Package Delivery where @Jon_Hodl share his experience on receiving one personally
- 🚨 VIP-Only Flash Sale: Bitaxe Gamma for $125 by @siggy47, grabbing one of these bad boys.
- Where do you sell books for Bitcoin, besides on ~Agora Territory? by @hasherstacker, asking ~BooksAndArticles community. Do you have a book to sell? Let me know how I can help!
- This best-selling book on ‘abundance’ has got it wrong - Max Rashbrooke by @Solomonsatoshi sharing an interesting external article.
- Trump Store Selling ‘Trump 2028’ Hats Trump Says He’s ‘Not Joking’ another interesting article shared by our dear friend @CarlTuckerson
Wow, such an exciting month!
Active Professional Services accepting Bitcoin in the AGORA
Let us know if we miss any, here below the most memorable ones: - https://stacker.news/items/900208/r/AG @unschooled offering Language Tutoring - https://stacker.news/items/813013/r/AG @gpvansat's [OFFER][Graphic Design] From the paste editions (It's important to keep these offers available) - https://stacker.news/items/775383/r/AG @TinstrMedia - Color Grading (Styling) Your Pictures as a Service - https://stacker.news/items/773557/r/AG @MamaHodl, MATHS TUTOR 50K SATS/hour English global - https://stacker.news/items/684163/r/AG @BTCLNAT's OFFER HEALTH COUNSELING [5K SAT/ consultation - https://stacker.news/items/689268/r/AG @mathswithtess [SELL] MATHS TUTOR ONILINE, 90k sats per hour. Global but English only.
Let me know if I'm missing other stackers offering services around here!
In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- https://stacker.news/items/972209/r/AG Here Comes Bitcoin Swag Shop by @k00b
- https://stacker.news/items/969011/r/AG Sales Corner (Prospecting) by @Akg10s3
- https://stacker.news/items/971914/r/AG Satoshi Escrow A Bitcoin non-custodial P2P dispute resolution using Nostr keys by @AGORA
- https://stacker.news/items/972209/r/AG Twin Cities Outdoor Agora Market by @k00b
- https://stacker.news/items/942025/r/AG How to create your Shopfront on STACKER NEWS to upsell your products & services by @AGORA
BUYing or SELLing Cowboys Credits?
BUY or SELL them in the ~AGORA marketplace
Here's what stackers have to offers: - [SWAP] SN Cowboy credits by @DarthCoin - https://stacker.news/items/758411/r/AG by @SimpleStacker that also shares a CCs market analysis. - [BUY] 100 cowboy credits for one satoshi by @ek - Will Pay Sats For Cowboy Credits by @siggy47 - 📢 CCs to Sats Exchange Megathread recently started by @holonite, not sure why in ~bitcoin. Consider the ~AGORA next time ;)
🏷️ Spending Sunday and Selling weekly?
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! All series available here: Or read the latest one from https://stacker.news/items/970896/r/AG
📢 Thursday Talks: What have you sold for Bitcoin this week?
Our recently launched weekly series going out every Thursday. In the past one, I collected all @Akg10s3's Sales Corner posts. Fresh out of the box, today edition https://stacker.news/items/974581/r/AG
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- Start your own [SHOPFRONT] or simply...
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to.
Or contact @AGORA team on nostr DM, and we can help you publish a personalized post.
.
#nostr#bitcoin#stuff4sats#sell#buy#plebchain#grownostr#asknostr#market#businessoriginally posted at https://stacker.news/items/974611
-
-
 @ 9c35fe6b:5977e45b
2025-05-08 11:49:44
@ 9c35fe6b:5977e45b
2025-05-08 11:49:44Into the Heart of the Desert If you're looking for an adventure beyond the ordinary, Egypt Safari Tours with ETB Tours Egypt offer an unforgettable escape into the Egyptian desert. Venture into the golden sands of the White Desert, Bahariya Oasis, or Siwa, where time seems to stand still. This is more than sightseeing — it's a soul-stirring journey.
Exclusive Experiences with Egypt Private Tours For those who value privacy and exclusivity, ETB Tours Egypt designs tailor-made Egypt private tours that bring the desert to life on your terms. Whether it's a sunset camel ride, a 4x4 dune adventure, or camping under the stars, your itinerary is crafted just for you.
Explore More with Egypt Vacation Packages Why stop at the desert? Combine your safari adventure with cultural highlights and coastal escapes through our curated Egypt vacation packages. Enjoy the perfect balance between relaxation and exploration as you transition from the desert to the Nile.
Budget-Friendly Desert Escapes Traveling on a budget doesn’t mean you have to sacrifice experience. ETB Tours Egypt offers incredible Egypt budget tours that make desert adventures accessible to all. With professional guides and well-organized itineraries, you’ll enjoy value-packed experiences at an affordable price.
All Inclusive Egypt Vacations: Worry-Free Travel Enjoy stress-free travel with our all inclusive Egypt vacations. From hotel stays and meals to guided safaris and transportation, every detail is taken care of. Just bring your adventurous spirit—we’ll handle the rest.
Combine Desert Thrills with Ancient Wonders Turn your desert safari into a grand journey by including one of our Egypt pyramid tour packages. Witness the mystique of the Pyramids of Giza before heading into the vast desert—blending ancient history with modern adventure To Contact Us: E-Mail: info@etbtours.com Mobile & WhatsApp: +20 10 67569955 - +201021100873 Address: 4 El Lebeny Axis, Nazlet Al Batran, Al Haram, Giza, Egypt
-
 @ 0861144c:e68a1caf
2025-05-08 11:45:52
@ 0861144c:e68a1caf
2025-05-08 11:45:52May 7th - Asuncion, Paraguay
We made trhe 11th meetup of our community. This time, we reached an ATH of atendees, almost 150 people. This time, we were talking about bitcoin for begginers and for the main event I made a presentation a about Robosats, encouraging people to take orders, buy bitcoin and most of it, make your life better.
The motto this time was: this is not about being a trader. It's about happiness.
Bitcoin can help you find new ways to explore the best version of yourself because right now people are looking anti-inflation methods for not lose money. In every meetup, we're encouraging our new members to embrace and adopt bitcoin for their products/services.
Most of them are skeptics (at first) when I say that Lightning Network is cheaper as f**k. I show them the fee paid, their eyes...it's the aha moment for them.
I'm happy and bullish af.
originally posted at https://stacker.news/items/974608
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 7e538978:a5987ab6
2025-05-08 10:23:28
@ 7e538978:a5987ab6
2025-05-08 10:23:28E-commerce store owners can now integrate Bitcoin payments into their WooCommerce shops using the LNbits WooCommerce plugin. This plugin supports payments using the Bitcoin Lightning Network and on-chain Bitcoin, providing merchants with flexible options to accept Bitcoin.
Integration with Bitcoin Payments
The LNbits WooCommerce plugin enables online merchants to accept Bitcoin payments easily. It uses LNbits to handle Bitcoin Lightning and traditional on-chain transactions, offering customers efficient payment methods.

Recent updates include support for Gutenberg block checkout integration, ensuring compatibility with the latest WooCommerce versions and improving the checkout experience for merchants and customers alike.
How the LNbits Plugin Works
The plugin integrates with LNbits through the Satspay Server extension. Lightning Network transactions are handled by LNbits. Merchants can manage on-chain payments via LNbits' Watch-only wallet extension.
Setup Steps for Merchants
The setup process for the LNbits WooCommerce plugin involves a few simple steps:
- Run an LNbits instance – either self-host or use the LNbits SaaS service at saas.lnbits.com.
- Install the Satspay Server extension within your LNbits instance.
- Add the LNbits plugin to your WordPress site.
- Configure the plugin via WooCommerce admin panel under WooCommerce > Settings > Payments.
Start Accepting Bitcoin Payments
By accepting Bitcoin payments, merchants offer customers a secure and efficient alternative payment method. Integrating the LNbits WooCommerce plugin is straightforward and aligns with the increasing adoption of cryptocurrency in online retail.
For further details, visit the official plugin page:
WordPress Plugin Directory – LNbits Bitcoin Onchain and Lightning Payment Gateway
-
 @ 7460b7fd:4fc4e74b
2025-05-08 10:14:59
@ 7460b7fd:4fc4e74b
2025-05-08 10:14:59背景与研究范围
Backpack 是由多名前 FTX 和 Alameda 员工在 FTX 崩盘后创立的一家加密交易平台,与 Amber Group(一家大型加密金融服务商)和已倒闭的交易所 FTX 之间可能存在多重隐秘关联。本研究超越公开新闻,从团队延续、资金路径、合规架构、基础设施复用和链上迹象等角度,推理分析三者之间的联系。下文将分别讨论:团队与股权延续性、法币出金(稳定币清算)架构、Amber Group 的支持角色、Circle/Equals Money 等第三方的关联,以及“交叉代币解锁”机制的可能性,并给出关键证据与信息缺口。
团队与股权上的延续性
首先,在团队方面,Backpack 由多名 FTX/Alameda 前成员创立。据报道,Backpack 的联合创始人包括前 Alameda Research 早期员工 Armani Ferrante,以及 FTX 前总法律顾问 Can Suncoinspeaker.com;另一位联合创始人 Tristan Yver 也曾任职于 FTX/Alamedanftgators.com。据 CoinSpeaker 披露,Backpack 40名员工中至少有5人是 FTX 前员工coinspeaker.com。这表明 Backpack 在团队传承上与 FTX 存在明显延续。一方面,创始团队直接来自原 FTX 帝国的核心人员;另一方面,他们将过往在大型交易所积累的经验带入了 Backpack。
其次,在股权投资方面也有延续痕迹。早在2022年9月,Backpack 背后的公司 Coral 即获得了由 FTX Ventures 领投的2000万美元种子轮融资,用于开发 Backpack xNFT 钱包等产品nftgators.com。然而由于2022年11月FTX暴雷,这笔来自 FTX 的投资资金大部分被冻结损失nftgators.com。在经历了资金困难的“蟑螂生存模式”后,Backpack 团队于2023-2024年重新融资,成功在2024年2月完成1700万美元的 A 轮融资nftgators.com。值得注意的是,此轮融资的投资阵容中出现了 Amber Group 的身影nftgators.com。Amber Group 与 Placeholder、Hashed、Wintermute 等知名机构共同参与了该轮融资coinspeaker.com。这意味着 Amber 已经成为 Backpack 股东之一,在股权上建立了联系。此外,Jump Crypto 和 Delphi Digital 等与 FTX时代关系密切的机构也参与了投资nftgators.com。综上, Backpack 的股东和团队构成反映出明显的历史延续:既有原FTX系资本(FTX Ventures)和人员直接过渡,也有 Amber Group 等行业巨头在FTX倒台后入场接棒投资,为 Backpack 提供资金和资源支持。
法币出金架构与 USDC 清算渠道
FTX 时代的稳定币清算: 为了解 Backpack 是否继承了 FTX 的 USDC 清算架构,需要回顾 FTX 过往的法币出入金体系。FTX 在运营高峰时期,以其流畅的出入金和稳定币兑换闻名。用户可以将 USDC 等稳定币充值到 FTX 并直接视同美元资产使用,提取时又能以银行电汇方式取出美元,过程中几乎无汇兑损耗。这背后可能依赖于 FTX 与 Circle 等机构的直接清算合作,以及自有银行网络的支持。例如,Circle 提供的企业账户服务可以让像FTX这样的平台在后台实现USDC与美元的1:1兑换与清算circle.com。事实上,FTX 曾是 USDC 的主要场景之一,大量用户通过将美元换成 USDC 再转入FTX进行交易,从而绕过昂贵的跨境汇款费用。FTX 很可能建立了高效的稳定币兑换通道——例如通过 Silvergate 银行网络或与稳定币发行方直接交割——来实现低成本、快速的法币⇄USDC 转换。这套“USDC 清算架构”是FTX业务成功的重要基础之一。
Backpack 的出金方案: Backpack 作为新兴交易所,近期正式推出了类似的法币⇄稳定币出入金功能,并号称实现了“0费率”的美元/USDC转换panewslab.com。根据官方公告,从2025年5月起,Backpack Exchange 用户可以通过电汇方式充值和提取美元,且美元与USDC的兑换不收取任何手续费panewslab.com。这与FTX当年提供的低成本稳定币出入金体验如出一辙,表明 Backpack 很可能在复用或重建一种高效的清算架构。
与FTX相比,Backpack 并未公开具体采用了何种技术/金融渠道来实现0手续费。但通过社区测试和代码线索,可以推测其架构与FTX思路相似:首先, Backpack 将美元法币与USDC稳定币视为等价资产开放存取,用户电汇美元到账后在平台得到USDC或美元余额,提币时可用USDC直接提走或兑换成美元汇出。其次, Backpack 可能通过与稳定币发行方Circle的合作,或通过场外流动性方,将用户的USDC和法币进行实时对冲清算。Circle提供的API允许合规企业账户方便地将USDC兑换为美元存入银行账户circle.com;Backpack 很可能利用了这一渠道,在后台完成USDC的兑换,再通过银行网络把美元汇给用户。虽然Backpack官方未明言使用Circle,但其USDC通道开放的举措本身就体现了Circle所倡导的稳定币跨境支付应用场景circle.com。因此,从设计上看,Backpack 的法币出入金体系是对FTX模式的一种延续和致敬,即充分利用稳定币作为清算中介,实现跨境汇款的低成本与高效率。
银行网络与 Equals Money: 更有意思的是,有社区用户实测 Backpack 的美元提现,发现汇款发起方显示为“Equals Money PLC”btcxiaolinzi.top。Equals Money 是英国一家持有FCA牌照的电子货币机构(EMI),为企业提供银行转账和外汇服务btcxiaolinzi.top。测试者推断,Backpack 可能在 Equals Money 开立了企业账户,用于代替传统银行向用户汇出美元btcxiaolinzi.top。这一细节揭示了Backpack出金架构的实现路径:Backpack 很可能将待提现的USDC通过某种方式兑换成法币并存入其在Equals Money的账户,由后者完成跨境电汇至用户收款银行。由于Equals Money本质上连接着欧洲和国际支付网络,Backpack借助它可以避开美国传统银行的限制,为全球用户(包括无法直接与美国持牌银行打交道的用户)提供出金服务。这一点在FTX时代并未被广泛报道,但符合FTX/Alameda团队擅长搭建复杂金融通道的作风。由此推断, Backpack 确实在承袭FTX时期的清算理念:利用多层金融机构合作(如稳定币发行方、电子货币机构等),构筑高效的全球资金出入网络。在表面0手续费的背后,可能是由Backpack或其合作方(如做市商)承担了兑换成本,以吸引用户panewslab.com。目前这一体系已进入公开测试及运营阶段,随着更多支付方式(ACH、SEPA)的推出,Backpack正逐步完善其全球法币出入金矩阵panewslab.com。
Amber Group 的潜在支持角色
作为Backpack的重要战略投资方,Amber Group 在该体系中可能扮演多重支持角色。首先是资金层面: Amber参与了Backpack的A轮融资nftgators.com并获得股权,这意味着Amber对Backpack的发展具有直接利益。在FTX倒闭后,Amber选择投资由FTX前团队创立的新交易所,体现出其对这支团队能力和商业模式的认可。Amber本身是知名的加密市场做市和金融服务公司,管理着庞大的资产并具备深厚的流动性提供能力dailycoin.com。因此可以合理推测,Amber除了资本投入,还可能作为做市商为Backpack的交易提供充足的流动性支持,确保用户在Backpack上交易时有良好的市场深度和稳定的价格。这种隐性支持符合许多交易所背后有大做市商“站台”的行业惯例。尤其Backpack定位要提供低成本的稳定币兑换和跨链流动性,Amber在稳定币交易市场的经验和库存或可帮助其维持汇率稳定。
其次是技术与基础设施支持: Amber Group 多年来构建了自己的交易系统(包括托管、风控和前端应用,如之前面向零售的 WhaleFin 应用)。尽管目前未有公开信息表明Backpack直接复用了Amber的技术,但不排除Amber在底层架构上提供咨询或授权支持的可能。例如,Amber深耕多链资产管理和清算,其内部API或合规方案可能对Backpack搭建跨法币/加密的基础设施有所启发。双方如果有合作,极有可能保持低调以避免监管敏感。还有一种支持形式是隐性投资或子基金合作: Amber可能通过旗下基金或关联投资工具,持有Backpack相关业务的权益而不公开身份。然而截至目前,我们尚未发现明确证据证明Amber有这种“隐形”持股行为——Amber作为领投方之一出现于公开融资名单,说明其支持主要还是以正式股权投资和业务协作的方式进行coinspeaker.com。
第三是合规与网络资源: Amber在全球(尤其亚洲)拥有广泛的业务网络和合规资源。Backpack注册在阿联酋迪拜,并计划拓展美国、日本、欧洲等市场learn.backpack.exchangelearn.backpack.exchange。Amber总部位于亚洲(最初在香港,新加坡等地开展业务),对东亚和东南亚市场非常了解。Amber的联合创始人团队中有合规专家,曾帮助公司获取多地牌照。Backpack的联合创始人之一(Can Sun)本身是前FTX法务,这保证了内部合规经验,但Amber的外部资源也可能提供协助。例如,Amber在香港与监管机构打交道的经验,或许有助于Backpack寻求香港或东南亚牌照;Amber在银行业和支付领域的关系网络,也可能帮助Backpack连接银行通道(如引荐像Equals Money这样的机构)。虽然这方面多属于推测,但考虑到Amber投资后通常会积极赋能被投企业,Backpack有理由从Amber处获得合规咨询、市场拓展等方面的帮助。
总的来看,Amber Group 对 Backpack 的支持可能是**“润物细无声”**式的:既体现在台前的融资与做市合作,也体现在幕后的资源共享和经验输出。这种支持帮助Backpack在短时间内补齐了从交易技术到法币通道的诸多要素,使其有能力低成本快速上线类似FTX当年的核心功能(如稳定币快速出入金)。然而,由于双方都未公开详述合作细节,我们对Amber介入的深度仍缺乏直接证据,只能从结果倒推其可能性。
Circle、Equals Money 等第三方的关联
在Backpack、FTX与Amber的关系网络中,Circle和Equals Money等第三方机构扮演了关键“节点”,它们的出现为三者合作提供了基础设施支撑:
-
Circle(USDC发行方): Circle公司本身与FTX及Backpack都有千丝万缕的业务联系。FTX在世时是USDC重要的使用方,帮助USDC拓展了交易所场景;FTX垮台后,Backpack继续扛起“稳定币交易所”的大旗,大量采用USDC作为美元计价和清算工具panewslab.com。虽然我们没有公开材料直接指出Backpack已与Circle签署合作协议,但Backpack推出USD/USDC通道的举措实际是在推动USDC的使用,这与Circle致力于扩大USDC应用的战略不谋而合circle.com。Circle近年来打造跨境支付网络,与多家交易平台和金融机构合作提供法币-稳定币转换服务circle.com。因此,有理由相信Backpack在后台利用了Circle的流动性或API来实现用户提币时的USDC兑换和赎回。比如,当用户在Backpack提取美元,Backpack可能将等额USDC通过Circle赎回成美元,Circle则将该美元汇入Backpack的银行账户进行出金。这种模式其实正是Circle提供给企业客户的“稳定币托管清算”服务之一circle.com。换言之,Circle充当了Backpack法币出金链条中的关键一环,尽管普通用户感知不到它的存在。反过来看Amber,作为全球领先的做市商,也大量使用USDC进行交易和结算,Amber与Circle之间亦可能有直接合作关系(如参与Circle的伙伴计划等)。可以说,Circle及其USDC网络构成了FTX时代和Backpack时代连接传统金融和加密世界的桥梁:FTX和Backpack都踩在这座桥上快速发展,而Amber作为市场参与者,同样频繁走这座桥,为自身和伙伴创造价值。
-
Equals Money(英国电子货币机构): 前文提及,Equals Money PLC 在Backpack的出金过程中显现出来btcxiaolinzi.top。这家公司提供面向企业的银行即服务(BaaS),允许像Backpack这样的客户通过其平台发起全球付款。Equals Money的出现意味着Backpack选择了一条灵活的合规路径来实现银行转账功能:相比直接开设传统银行账户,使用EMI能更快获取支付能力且准入门槛较低。FTX时期并未传出使用EMI的消息,因为当时FTX可直接依赖自己的银行关系网(例如通过位于美国、欧洲的自有账户)来处理汇款。然而在后FTX时代,许多加密公司(包括Amber)都在寻找新的银行替代方案,EMI因此受到青睐。具体联系: 根据实测,Backpack用户提现美元到Wise时,Wise收到的汇款来自Equals Moneybtcxiaolinzi.top。Wise作为跨境汇款平台,其收款机制对资金来源要求严格,但Equals Money持有FCA牌照,属于受监管机构,Wise接收来自Equals的资金被视为合规btcxiaolinzi.top。由此推断,Backpack通过Equals的企业账户,将兑换好的美元直接打给用户填入的收款账号(包括Wise提供的虚拟账号)。这表明Backpack和Equals Money之间有直接业务往来,Equals是Backpack法币出金服务链条上的合作伙伴。值得一提的是,Amber Group 此前在欧洲也曾探索电子货币牌照或合作渠道的可能,尽管无法确认Amber是否也使用Equals,但不排除Amber为Backpack牵线搭桥、推荐了Equals这类服务商的可能性。
综合来看, Circle和Equals Money分别代表了稳定币清算层和法币支付层的基础设施,与Backpack/FTX/Amber的联系体现为:Circle提供“链上到链下”的美元流动性支持,Equals提供“链下”最后一公里的银行网络接口。三者之所以都选择/使用这些渠道,是因为它们共享了对加密法币融合效率的追求。对于FTX和Backpack而言,这些渠道是业务方案的一部分;对于Amber而言,这些渠道是服务布局和投资的一环(Amber支持的交易所采用了这些方案,也间接符合Amber推动行业基础设施完善的利益)。
“交叉代币解锁”机制与链上协作迹象
“交叉代币解锁”是指Amber、Backpack(或其关联项目)之间通过持有彼此发行的代币,并利用协议合作、解锁计划或链上交易,实现协同利益的一种机制。鉴于Backpack尚处于发展初期,我们需要探讨哪些代币或资产可能涉及双方的互动:
-
Backpack 平台代币的潜在发行: 根据Backpack社区的信息,平台计划通过交易积分空投方式向活跃用户发放代币资格btcxiaolinzi.top。这暗示Backpack未来会推出自己的平台代币。若真如此,早期投资方(包括Amber Group)很可能在代币经济中占有一席之地,例如通过投资协议获得一定比例的平台代币配额。在代币正式解锁流通时,Amber等机构投资者将持有相应份额。这就产生了潜在的“交叉代币”联系:Amber持有Backpack的代币,并可在协议允许的时间窗口解锁出售或利用。这种关系一方面绑定了Amber与Backpack的长期利益,另一方面也为Amber提供了在二级市场获利或支持Backpack代币市值的机会。如果Backpack设计代币经济时有锁仓解锁期,那么Amber的代币解锁时间和数量将受到协议约束。从链上数据看,未来可以观察这些大额代币解锁地址是否与Amber的钱包存在关联,以验证Amber对Backpack代币的处置行为。当前,由于Backpack代币尚未发行,我们只能提出这一推测性机制,等待后续链上数据来印证。
-
Amber 持仓代币与Backpack业务的协同: 反之,Amber Group 或其子基金本身持有众多加密资产,是否有与Backpack生态互动的情况?例如,Amber可能持有某些与Backpack生态有关的项目代币(如Solana链上资产,Backpack钱包支持的特定NFT/代币等)。一个案例是Backpack团队曾在Solana上发行受欢迎的 xNFT系列“Mαd Lads”NFTlearn.backpack.exchange。Amber或其投资部门是否参与了该NFT的投资或持有尚无公开资料,但不排除Amber透过场内交易购买一些以支持Backpack生态热度。再者,如果Amber在其他项目上持有代币,而Backpack平台上线这些资产交易,Amber可能通过链上转账将流动性注入Backpack,从而实现双方受益——Amber获得流动性做市收益,Backpack获得交易量和资产丰富度。这可以视作一种链上协作。例如Amber持有大量某种代币X,在Backpack上新上线代币X交易对时,Amber账户向Backpack的热钱包充值代币X提供初始流动性。这样的行为在链上会呈现Amber已知地址向Backpack地址的大额转账。如果将来这些数据出现,将成为印证双方链上合作的直接证据。目前,此类链上轨迹还未有公开披露,我们只能假设其存在的可能性。
-
FTX 遗留资产与Backpack 的关联: 另一个值得一提的链上观察维度是FTX/Alameda遗留资产的动向。FTX倒闭后,其相关钱包曾多次异动。Backpack团队作为前员工,有可能知晓某些地址或资产的情况。但由于破产清算在法庭监管下进行,直接将FTX遗留资产转给新项目不太现实。不过,不排除某些前Alameda投资的项目代币后来为Backpack团队所用。例如,Alameda早期投资的项目若代币解锁,Backpack团队个人可能持有部分并用于新平台的流动性。这种间接关联较难确认,但链上仍可寻找蛛丝马迹,比如监测前Alameda标识的钱包与Backpack相关地址之间的交易。如果有频繁互动,可能暗示Backpack获取了Alameda旧有资产的支持。至今未见显著证据,推测空间大于实证。
小结: “交叉代币解锁”机制目前更多停留在理论推演层面。我们确认了Backpack未来存在发行平台代币的规划btcxiaolinzi.top;也确认Amber作为投资方大概率会获得并持有该代币份额。但具体的锁仓解锁安排、双方是否会通过特殊协议(如做市激励、流动性挖矿等)进行合作,还有待官方披露或链上数据验证。链上分析工具可以在未来帮助捕捉Amber地址与Backpack生态代币/NFT的交互,从而揭示深层协作。如果发现Amber旗下地址在Backpack代币解锁后立即大量转入交易所,可能意味着Amber选择变现;反之,若锁定期内就有灰度交易发生,甚至可能存在双方提前约定的场外交换。这些都是值得持续监测的方向,但就目前信息来看,尚无定论。
\ 图:FTX、Amber Group 与 Backpack 三者关系示意图。红色/橙色线表示团队和股权延续(FTX前员工和投资延续到Backpack,Amber参与投资并可能提供流动性);蓝色线表示Backpack法币出金所依赖的稳定币清算和银行通道(通过USDC及Equals Money实现);灰色虚线表示FTX和Amber分别与USDC发行方Circle在业务上的联系。这些关系共同构成了Backpack在FTX余荫和Amber支持下快速搭建全球业务的基础。
关键证据与信息缺口
通过上述分析,我们梳理了已知的信息链条,并挖掘了若干可能的隐秘关联,同时也识别出需要进一步调查的信息空白:
-
明确的证据链: 我们找到了多项公开资料证明Backpack与FTX/Amber的联系:包括创始团队来自FTX/Alamedacoinspeaker.com、FTX Ventures 曾投资Backpack母公司nftgators.com、Amber Group 参与了Backpack的融资coinspeaker.com、多名FTX旧部现在Backpack任职coinspeaker.com等。这些形成了人员和资金延续的直接证据。另外,通过用户分享和代码库,我们确认Backpack法币出金使用了Equals Money通道btcxiaolinzi.top并提供了0手续费的USD/USDC转换panewslab.com——这证明了Backpack确实建立了类似FTX当年的稳定币清算架构,只是技术实现上借助了新的合作方(Equals Money)。这些证据支撑了本文的大部分推论基础。
-
合理的推测与佐证: 有些关联尚无官方公告证明,但基于行业惯例和现有线索推测合理,并有部分侧面佐证。例如,Amber 为Backpack提供做市流动性支援一事,没有直接新闻来源,但考虑到Amber投资交易所的动机和能力,此推断具有高概率可靠性。再如,Backpack疑似使用Circle的USDC清算服务,虽无明示,但从其业务模式和Circle的产品定位来看circle.com,这一幕后合作应该存在。同样地,Amber可能通过非公开方式向Backpack输出技术/合规支持,也是基于双方利益绑定关系而做出的推断。这些推测目前缺乏直接证据,只能算作可能性假设,需要后续留意更多细节披露。
-
信息缺口与待验证点: 首先,关于Backpack具体的清算路径,我们仍不清楚它如何在链上/链下转换巨额USDC为法币。虽然Equals Money出现在汇款端btcxiaolinzi.top,但在那之前USDC的结算或许涉及Circle或其他做市商(如Amber)——这部分交易发生在后台,需更多技术信息或链上监控来捕捉。其次,Amber与Backpack之间除股权外是否存在合同约定的业务合作(如Amber成为指定做市商、提供信贷支持等)目前尚未公开,属于信息真空。第三,Backpack未来的代币发行和分配细节未知,Amber等投资方将如何参与、解锁周期如何,将直接影响“交叉代币”协作的发生与否,需等官方白皮书出台。第四,更多链上证据的挖掘:由于没有公开的钱包标签,很难直接将某条链上交易指认属于Amber或Backpack。但如果未来Backpack发行代币或大型交易上线,链上必然会出现相关资金流,我们可以通过已知Amber常用地址(如果有披露)来交叉比对,看其是否与Backpack生态有交互。这是一块需要进一步研究的领域,可能借助区块链分析工具和交易图谱来补全证据。最后,还有监管和法律结构的信息:例如Backpack在不同司法管辖区的注册实体与银行账号详情,FTX遗产处理过程中是否对Backpack团队有约束,这些在公开资料中都尚无答案。
结论
综合全篇分析,Backpack、Amber Group 与已倒闭的FTX之间确实存在千丝万缕的延续和关联。Backpack可以被视作FTX精神和技术路线的“继承者”之一——由FTX旧将创建,在FTX垮台造成的市场空白中迅速崛起coinspeaker.com。Amber Group 则扮演了重要的扶持者角色,通过投资和可能的资源注入,参与了Backpack的重建过程coinspeaker.com。在具体业务层面,Backpack延续了FTX时代的创新,如高效的稳定币清算和全球化业务布局,但为了适应新的环境,它也采用了新的工具(如Equals Money的出金渠道)和更严格的合规措施(迪拜等地的牌照)coinspeaker.com。这一切背后,隐现着Amber等老牌加密公司的身影支持,以及Circle等基础设施提供商的支撑。
当然,隐秘关联并不意味着不正当行为,上述关系很多是基于正常的商业合作和延续,只是未明言于公众。例如,前FTX团队利用自己的经验和人脉创建新平台,本身无可厚非;Amber投资新交易所也是市场行为。从推理和现有证据看,并没有直接迹象显示三者存在违法的秘密勾连。然而,对于研究者和行业观察者而言,了解这些联系有助于洞察加密行业格局的演变:FTX的倒下并未让其积累的人才和思想消失,反而通过创业和投资,以新的形式(Backpack)继续影响市场;Amber等老牌玩家则通过战略投资,将自己的版图延伸到新兴平台,以保持竞争力。
未来展望: 随着Backpack进一步发展,我们预计会有更多信息浮出水面来验证或修正上述假设。例如,Backpack若推出平台代币,其投资人持仓和解锁情况将记录在链,从而揭示Amber等的参与细节;再比如,Backpack进入美国市场时需要公开其合作银行或支付伙伴,届时我们可能印证Circle等在其中的角色。如果出现新的合作公告或监管披露文件,也能帮助我们更清晰地绘制三者关系网。目前的信息不对称使我们只能尽力拼凑一幅关联图景,并针对关键环节提供已知证据支持。仍存在的一些信息缺口需要持续跟进调查。总之,Backpack、Amber Group 与FTX的故事折射出加密行业的新旧交替与传承。在FTX的余烬上,新火花正在由熟悉旧世界的人点燃,而这些火花能否照亮一个更加合规稳健的未来,还有待时间检验。 nftgators.comcoinspeaker.com
-
-
 @ 7460b7fd:4fc4e74b
2025-05-08 10:14:13
@ 7460b7fd:4fc4e74b
2025-05-08 10:14:13Backpack 平台 USDC 出金渠道深度研究报告
背景简介
Backpack 是近年来崛起的加密交易与钱包平台,由前 FTX/Alameda 团队成员创立coindesk.comfinsmes.com。2024 年初 Backpack 曾宣布与 Banxa 合作提供法币出入金服务,支持130多个国家用户使用信用卡/银行渠道买卖加密资产learn.backpack.exchange。2025 年 5 月,Backpack 官方更是推出“0 手续费”的 USD⇄USDC 出金通道,允许用户通过电汇将 USDC 1:1 无损兑换为美元并提取到银行账户lianpr.combinance.com。本报告将详细分析 Backpack 当前的出金方式及其合作渠道、低成本运营的原因、Backpack 与支付机构 Equals Money 的关系,并探讨如果搭建类似的加密金融服务,应如何与 USDC 发行方 Circle 建立合作。
Backpack 的 USDC 出金方式与合作渠道
USD⇄USDC 零手续费通道 – Backpack Exchange 已面向全球用户开放美元与 USDC 间的法币转换,并永久免除任何手续费23btc.com。用户完成 KYC 验证后,可以通过 电汇(Wire Transfer) 将美元直接充值到 Backpack 平台获取等值 USDC,或将持有的 USDC 提现兑换为美元电汇至本人银行账户binance.com。据官方介绍,该通道具备“三大核心优势”:一是零摩擦转换,实现美元与 USDC 间的无缝1:1兑换;二是即时到账,宣称电汇入金/提现可秒级处理;三是全球覆盖,后续将支持 ACH、SEPA 等本地清算网络23btc.com。
合作金融机构 – 为实现合规的法币收付,Backpack 并非自行持有银行牌照,而是借助第三方持牌机构的通道来托管用户的法币资金assets.ctfassets.net。有迹象表明 Backpack 使用了英国的电子货币机构 Equals Money 作为其出入金通道之一:在其开源代码中,Backpack 将“EqualsMoney”集成为一个区块链/支付网络类型github.com。这意味着 Backpack 平台可以通过 Equals Money 提供的多币种账户和支付网络,来代收用户的银行转账并代付提现资金。除了英国渠道,Backpack 集团在全球多地布有实体,以拓展支付能力。例如,用户实测的电汇显示汇款方为 “Trek Labs Australia Pty Ltd”(Backpack 在澳大利亚的子公司)medium.com。这家公司作为汇款主体将等值美元汇出到用户银行账户。除澳洲外,Backpack 背后的 Trek Labs 集团还在迪拜设有 Trek Labs Ltd FZE,在立陶宛设有 Trek Labs UAB,在美国设有 Trek Labs, Inc.medium.com。这种全球子公司布局使 Backpack 能借助各地区的合作银行或支付机构完成跨境资金结算,覆盖包括欧美、亚太在内的广阔用户群。
出金流程 – 用户在 Backpack 平台发起 USDC 提现时,平台会通过上述合作渠道将用户的 USDC 兑换为等额法币,并由托管金融机构从其法币池中汇出资金。比如,当用户提取 1,000 USDC 到香港银行账户,Backpack 将该 USDC 转换为 1,000 美元,由合作机构通过 SWIFT 电汇发送。用户可在 Backpack 后台实时查询电汇状态medium.com。实际测试显示,从提现到款项到账香港银行大约耗时36小时(约1.5个工作日)medium.com。汇款时收款行信息需要用户自行提供并添加到平台,如收款行名称、地址、SWIFT代码等medium.com。Backpack 平台本身要求用户的银行账户姓名与平台注册姓名一致,以确保合规。assets.ctfassets.netassets.ctfassets.net
低成本出金的架构与原因
Backpack 能提供零手续费的稳定币出金服务,得益于其结算架构设计和合规路径上的优势,使其运营成本得以控制在极低水平:
-
Stablecoin 即时清算:Backpack 利用 USDC 稳定币作为桥梁,实现用户资金在链上和银行账户之间的快速清算。由于 USDC 与美元1:1锚定,兑换过程中没有汇率损耗或价差成本lianpr.com。平台内美元和 USDC 的余额转换也是按面值对等,不收取点差,这实现了资金的“零摩擦”兑换23btc.com。相比传统银行汇款需要经过多级代理和 Forex 转换,Stablecoin 的使用大幅降低了兑换费用和时间延迟。
-
第三方牌照通道:Backpack 选择通过持牌支付机构(如 Equals Money 等)来承载法币收付功能,而非自行作为汇款人展开业务。这种策略绕开了平台直接获取银行牌照或支付牌照的高成本投入,转而借用第三方机构的现有牌照和账户网络。例如,Equals Money作为英国受监管的电子货币机构,拥有多币种账户和全球汇款能力。Backpack 通过 API 接入该机构后,相当于获取了一套现成的银行基础设施,可以以较低费用发送SWIFT、电汇等github.com。第三方机构通常按照交易量收取较小的服务费,Backpack 可以在当前发展阶段予以补贴,从而对用户“免手续费”。这种“牌照即服务”的模式使 Backpack 将合规成本外包,自己专注于用户和交易环节。
-
合规及监管路径:Backpack 利用多个辖区的子公司布局,根据各地监管环境选择最优的出金路径。例如,在欧洲可能通过立陶宛子公司对接 EU 区的支付网络,在亚洲通过澳大利亚子公司汇出 SWIFT。medium.com这种灵活性使他们能规避单一地区监管限制,选择成本最低、效率最高的清算通道完成提现。此外,多实体运营也有助于分散风险,符合各地反洗钱要求,为零手续费策略提供合规保障。
-
资金结算与收益:尽管对用户宣称0手续费,Backpack 可能通过其他方式覆盖成本。例如,用户的法币资金在汇出前可能短暂存放于合作机构的池中,这些资金量若较大,可产生利息收益,用于弥补转账费用coindesk.com。另外,Backpack 平台的主要收入来自交易手续费和利息产品等,高频交易活动带来的收入能够补贴出金通道的成本,从整体上实现盈亏平衡。
值得注意的是,“0 手续费”指的是 Backpack 平台本身不向用户收取出金手续费,但并不意味着整个过程完全免费。银行端的固定费用仍可能存在。例如,有用户反馈,通过 Backpack 将 USDC 提现到香港 ZA Bank 账户时,Backpack 未收取费用,但 ZA Bank 会收取一次性 20 美元的入账费用twitter.com。类似地,美国银行接收国际电汇通常也会有每笔 15\~30 美元不等的手续费。这些费用属于收款行或中间行收费,并非 Backpack 或其合作方收取。即便如此,相比传统OTC中介或其他交易所的出金方案,Backpack 的整体成本依然极低——没有额外的汇兑损耗,仅需承担银行常规入账费,大额提现尤为划算。一位资深用户将 Backpack 提现称为“目前最优、最简单的合规出金路径”,反馈资金1天左右即到账,流程非常顺畅x.com。可见,Backpack 通过精心搭建的结算架构,实现了高效低成本的出金服务,在合规前提下大大降低了用户将数字资产变现的门槛。
Backpack 与 Equals Money 的关系考察
Equals Money 背景 – Equals Money 是英国上市金融科技公司 Equals Group PLC 旗下的支付业务品牌,提供多币种电子账户、国际汇款和企业外汇兑换等服务。该公司前身为 FairFX,持有英国金融行为监管局(FCA)颁发的电子货币机构牌照,主营为企业客户提供全球支付解决方案fxcintel.com。简单来说,Equals Money 扮演的是受监管的“非银行支付平台”角色,可为合作伙伴提供银行账户托管和跨境支付通道。对于缺乏自有牌照的加密公司而言,与这类机构合作能快速获得法币收付能力。
业务合作关系 – 目前公开信息并未有 Backpack 与 Equals Money 签署官方战略合作的公告,但从技术集成和业务逻辑上看,两者存在密切的业务往来。Backpack 在代码库中增添了对 “EqualsMoney” 的支持选项github.com表明其系统已经对接了 Equals 提供的支付 API。在用户充值/提现时,Backpack 系统可以将指令通过该接口发送给 Equals,由后者执行实际的银行转账操作(如从对应的用户托管账户划款)。换言之,Equals Money可能充当了 Backpack 用户法币资金的托管方和结算代理。还有用户实测提到,从 Backpack 提现美元时,资金是由 “Trek Labs Australia Pty Ltd” 汇出medium.com。结合上下文,推测 Trek Labs Australia 这家 Backpack 子公司可能在 Equals Money或类似机构开设了运营账户,用于统一汇出用户提现款项。这个细节侧面印证了 Backpack 利用第三方支付平台进行法币结算:汇款主体虽然名义上是 Backpack 关联公司,但实际的支付通道和银行接口由 Equals Money 等持牌机构提供支持。
人员和投资交集 – 在股权和团队层面,暂未发现 Backpack 与 Equals Money 有直接的交叉。Backpack 的融资由加密领域的风投基金主导(Placeholder、Hashed、Amber Group 等)finsmes.com,并无公开提及来自 Equals 集团的投资。管理团队方面,Backpack 由前加密交易所从业者主导,而 Equals Money 属于传统金融支付行业,公司高管以金融背景为主,目前没有明显的人事重合记录。此外,Equals Group PLC 在2024年底宣布将被嵌入式金融公司 Railsr 收购thisweekinfintech.com(该交易有待监管批准),这属于其自身战略调整,与 Backpack 无直接关联。总体来看,Backpack 与 Equals Money 更可能是一种商业合作关系:Backpack 作为客户接入 Equals Money 的支付服务,以使用其许可和网络;双方在产权和团队上保持独立。此类合作在金融科技领域较为常见,属于优势互补:加密平台获取法币通道,支付机构拓展客户和资金流量。
合作的意义 – 通过与 Equals Money 等机构合作,Backpack 实现了快速合规地打通法币出入口,在竞争激烈的交易所市场上形成差异化优势。用户能够享受到类似银行级别的出金体验(直接电汇到账)且几乎零成本x.com,这极大增强了 Backpack 平台的吸引力和资金留存率。对 Equals Money 而言,服务 Backpack 这样高增长的加密客户,也为其带来了可观的跨境支付业务量和创新合作机遇。在严格遵守反洗钱和监管要求的前提下,这种加密与传统金融的合作模式,展现了融合创新的前景。
搭建类似业务与 Circle 合作的要点
假如希望搭建与 Backpack 类似的稳定币出入金架构,与 USDC 发行方 Circle 建立合作是关键一步。Circle 提供针对企业的账户服务和 API接口,使合作方能够方便地在应用中集成 USDC 与法币的转换和支付功能circle.comcircle.com。以下是与 Circle 合作时需要关注的主要要点:
- 主体资格
需要有合法注册的公司实体,并处于 Circle 支持的地区(如北美、欧洲等)。Circle 暂不向个人用户开放其直接铸币/赎回服务,仅面向机构客户。 - 业务规模要求
主要针对大体量、批量使用 USDC 的公司,例如交易所、托管机构、数字钱包平台或银行等。若业务量较小,Circle 会建议通过第三方交易所获取 USDC。 -
KYC 合规审查
对申请企业进行严格的背景尽调,包括高管和受益人身份验证、注册信息、经营范围、反洗钱和制裁风险评估等。需提供公司注册证书、人员身份证明、合规方案等,审核时间通常为数天至数周。 -
账户功能
审核通过后可开立 Circle 账户,支持将银行资金充值并自动兑换为 USDC,或将 USDC 赎回为法币并电汇到指定银行账户;涵盖链上转账、ACH 和电汇等多种渠道。 -
API 接入
提供完整的 REST API 和 SDK,支持自动化发起电汇兑换、铸造/销毁 USDC、提现等操作,合作方只需专注前端体验,后端支付和结算由 Circle 处理。 -
费用结构
对符合条件的合作伙伴铸造/赎回 USDC 不收手续费;法币转账需承担银行或中间行手续费。支持免费 ACH 通道,国际电汇按银行标准收费。 -
合规责任
Circle 对企业客户履行 KYC/AML 义务,但合作方若面向终端用户提供服务,也需自行做用户审核与交易监控,并在高金额转账时传输用户身份信息(Travel Rule)。
合作流程:实际操作中,搭建团队需要先在 Circle 官网提交企业账户申请,提供相关资料并通过合规审核circle.com。拿到账户后,可登录 Circle 提供的业务后台或通过 API Sandbox 进行测试集成,熟悉 USDC 钱包、法币钱包的操作。一旦准备就绪,即可将功能推向生产环境,为用户开通 USDC 与法币的双向兑换。值得注意的是,企业应根据所服务用户区域,获取必要的当地监管许可或豁免。例如在美国需要遵守联邦和州级货币转移许可证要求,在欧盟则可能利用立陶宛等国的数字资产服务牌照。这与 Backpack 多地布局子公司的做法类似,都是为了符合法规开展业务。
成功案例:除了 Backpack,业内已有多家知名机构通过与 Circle 合作开展稳定币支付业务。例如 Binance 与 Circle 达成战略合作,使其平台更广泛支持 USDCfortune.com;支付公司 Stripe 也集成了 Circle API,在其产品中新增了稳定币收付功能stables.money。这些案例表明,通过 Circle 提供的基础设施,加密公司可以较为迅速地搭建起合规、高效的法币⇄稳定币出入金体系,触达全球80多个国家的用户circle.com。因此,对于希望复制 Backpack 模式的新创团队而言,提早布局与 Circle 等发行方的合作,并搭建完善的合规架构,将是取得监管认可和市场竞争优势的关键。
结论
Backpack 平台通过巧妙融合稳定币技术和传统金融渠道,打造出了低成本、高效率的USD⇄USDC出金方案。在无需用户承担手续费的情况下,依托 Equals Money 等支付伙伴和自身全球子公司网络,实现了合规的美元电汇快速到账23btc.commedium.com。这一模式的成功在于对结算架构的创新设计和对监管资源的充分利用:既发挥了 USDC 稳定币实时、低成本的优势,又借力持牌金融机构解决了法币合规问题。这为行业树立了一个范例。
对于有意搭建类似业务的团队,与 Circle 建立合作无疑是重要的一环。Circle 提供了成熟的 USDC 基础设施,只要申请企业拥有足够的资质和规模,通过严格的 KYC 审核后即可获得稳定币铸造和法币结算的能力circle.comcircle.com。在此基础上,新业务还需结合自身情况选择适当的支付合作方和注册管辖地,搭建自己的合规“护城河”。只有技术与合规并重,才能如同 Backpack 一样,在保证低成本出金的同时,赢得监管许可和用户信赖。
参考资料:
-
Backpack 官方公告及新闻稿binance.comlianpr.com23btc.com
-
Backpack 用户协议与代码仓库assets.ctfassets.netgithub.com
-
媒体报道(CoinDesk 等)coindesk.comlearn.backpack.exchange
-
第三方分析与用户实测反馈medium.comtwitter.com
-
Circle 官方文档与博客circle.comcircle.comcircle.com
-
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 57412389:2b288de5
2025-05-08 16:38:23
@ 57412389:2b288de5
2025-05-08 16:38:23Bitcoiners won big in the 2024 elections that saw Trump take the White House and Republicans control both the House and the Senate. Not because Trump and his Republican teammates are God's gift to the US or because they're all Bitcoiners, but because they're not the version of the Democrats we saw during the previous four years.
If you're reading this I'm sure you're well aware of the hostility the previous administration had towards Bitcoin. It was obvious at the time that individual actors like Elizabeth Warren and Gary Gensler were acting against Bitcoin, but after Trump's victory, plenty of Bitcoiners and people in the "crypto industry" felt comfortable enough to speak out about the specific lashings they took from Biden and crew. Chokepoint 2.0 went from a conspiracy theory toan accepted truththat the administration was working to slow Bitcoin anyway they could. It was a mind numbing stance that certainly opened the door for Trump to gain a non-negligbile amount of votes pretty easily. He got on stage at Bitcoin 2024 and treated it like any other rally, ranting on and on about how great he was and how bad the Democrats were with a few crypto lines sprinkled in. He, almost teasingly, said "Have fun playing with your Bitcoin.", walked off stage, and that was it. That's all it took for him to secure the vote of anyone with a hair of their networth tied up in "crypto".
I'm not suggesting Trump is a nothing for Bitcoin, he's pushed the Strategic Bitcoin Reserve forward and certainly given air cover to other Republicans in power at the state level to push positive Bitcoin legislation, but the big win for Bitcoiners is that he isn't the other guys.
On top of the SBR at the federal level, New Hampshire and Arizona have passed state level SBRs at the time of this writing with many others having bills trying to make their way through the system. There are alsoplenty of other billsat the state level that have already passed or are on their way to passing that defend things like the right to self custody and other protections for Bitcoiners.
These bills are all great news and I don't want to act like the elite purity test Bitcoiners and pretend the largest government in the world being Bitcoin friendly isn't a big deal - it is. But, at the end of the day with the way politics seems to work as of late, everything can be changed with the swipe of a pen by the next guy in power. These should be treated as four year promises at best.
Political power works like a seesaw. Right now the Republicans have the juice, but come next election cycle that's likely to change. The issue is the system is burning and there's nothing that politicians can realistically do to put out the flames. All the real solutions, like eliminating government programs such a social security and medicare/medicaid, are political suicide and anyone running on that platform wouldn't sniff a seat in office. So every four years Americans look back on the previous four and go "Man, that guy really sucked. Things are worse than they were before. The other guys can save us!" Of course, the other guys suck too, but the current guys sucking is just fresher in the minds of the public. There is nothing any politician can do to put out this fire because all they can afford to wield is a garden hose or they won't get votes. So, we all just watch this fire grow larger and larger and pick a different guy with a different garden hose every four years because the last guy didn't work and the only move we've got is to pick the other guy.
So, if all these executive orders, working groups, bills, and laws can just be evaporated by the other team next time around why was the Trump win so big for Bitcoin? The answer is that it buys Bitcoin time to soak into every crevice of the financial system. If the next political team in power decides they hate Bitcoin and want to reverse every positive thing done by Trump's team it's going to be a lot harder for them to do that when a serious portion of the financial system has an incentive to fight for and vote in favor of Bitcoin.
Just a handful of examples of how Bitcoin is soaking into the financial system:
iBIT is currently Blackrock's 11th largest ETF by AUM. FBTC is Fidelity's largest ETF by AUM. Wisconsin and Michigan state pensions both hold Bitcoin ETFs. CalPERS holds shares of MSTR.
There's a point where so many different entities that affect so many different individuals hold Bitcoin, or investments centered around Bitcoin, that a politician attacking Bitcoin from a regulatory perspective just isn't realistic in the same way regulation against Gold isn't feasible. These regulatory attacks on an asset with deep roots in the financial system would be poltical suicide just like threatening to delete Social Security. No longer is attacking Bitcoin a move against a few hundred thousand internet dorks, it's an attack on anyone with a pension, anyone who owns the stock of a company holding bitcoin, any private business holding bitcoin, plus a few hundred thousand internet dorks.
While the Bitcoin bills catch all the headlines, the real signal is watching bitcoin soak into private holdings of people in power, pension funds, public company treasuries, etc. We've got four years to for Bitcoin to become so ingrained that no politician could attack it.
-
 @ 8bde549d:567bf85c
2025-05-08 09:40:41
@ 8bde549d:567bf85c
2025-05-08 09:40:41TP88 là một trong những nền tảng giải trí trực tuyến được đánh giá cao nhờ vào giao diện thân thiện và dễ sử dụng, giúp người chơi dễ dàng tham gia và trải nghiệm các trò chơi yêu thích. Với mục tiêu mang đến những giây phút thư giãn tuyệt vời cho người dùng, TP88 không ngừng cải thiện và cập nhật các tính năng mới để phù hợp với nhu cầu giải trí ngày càng cao. Nền tảng này cung cấp đa dạng các trò chơi từ các game trí tuệ yêu cầu tư duy chiến lược đến các trò chơi vui nhộn và giải trí, giúp người chơi có thể lựa chọn theo sở thích và phong cách của mình. Từ những trò chơi đơn giản nhưng đầy thử thách cho đến những trò chơi phức tạp và sáng tạo, TP88 đều có thể đáp ứng mọi yêu cầu của người chơi. Với đồ họa sắc nét, âm thanh sống động và hiệu ứng đặc biệt, TP88 chắc chắn sẽ mang đến cho người tham gia những trải nghiệm giải trí chân thực và đầy đủ cảm xúc.
Ngoài những yếu tố về sự đa dạng và hấp dẫn của các trò chơi, TP88 cũng đặc biệt chú trọng đến bảo mật và sự an toàn của người chơi. Trong môi trường trực tuyến hiện nay, vấn đề bảo vệ thông tin cá nhân và các giao dịch tài chính luôn được đặt lên hàng đầu. TP88 sử dụng công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin người chơi sẽ được bảo vệ một cách an toàn và không bị xâm phạm. Mọi giao dịch tài chính, từ việc nạp tiền đến rút tiền, đều được thực hiện nhanh chóng, chính xác và bảo mật tuyệt đối, giúp người chơi có thể yên tâm trong suốt quá trình tham gia. Nền tảng này cũng tuân thủ các tiêu chuẩn quốc tế về bảo mật và an toàn, mang đến cho người chơi một môi trường giải trí trực tuyến đáng tin cậy và an toàn. Hệ thống bảo mật và hỗ trợ khách hàng của TP88 luôn hoạt động 24/7 để đảm bảo rằng mọi vấn đề phát sinh của người chơi sẽ được giải quyết kịp thời và hiệu quả.
Một trong những yếu tố quan trọng khiến TP88 trở thành sự lựa chọn hàng đầu của những người yêu thích giải trí trực tuyến chính là các chương trình khuyến mãi và sự kiện hấp dẫn. Nền tảng này thường xuyên tổ chức các chương trình khuyến mãi, sự kiện đặc biệt và các giải thưởng giá trị để thu hút người chơi tham gia và tạo cơ hội cho họ nhận được nhiều phần thưởng hấp dẫn. Các chương trình này không chỉ làm tăng thêm phần thú vị mà còn mang đến nhiều cơ hội để người chơi tăng thêm tài khoản của mình một cách dễ dàng. Ngoài ra, TP88 còn có các sự kiện cộng đồng, nơi người chơi có thể giao lưu, chia sẻ kinh nghiệm và kết nối với nhau. Những sự kiện này góp phần tạo nên một cộng đồng gắn kết và sôi động, nơi mà người chơi có thể học hỏi và phát triển kỹ năng của mình. Với tất cả những ưu điểm này, TP88 không chỉ là một nền tảng giải trí đơn thuần mà còn là một cộng đồng lớn mạnh, nơi người chơi có thể tìm thấy niềm vui và sự thỏa mãn trong mỗi lần tham gia.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ ecda4328:1278f072
2025-05-08 09:29:23
@ ecda4328:1278f072
2025-05-08 09:29:23A detailed breakdown of the recent debate around Bitcoin Core’s proposed policy change to OP_RETURN — and why it’s less dramatic than some fear.
TL;DR
Removing the 80-byte OP_RETURN limit is a mempool policy cleanup, not a consensus rule change. It reduces UTXO bloat, improves relay consistency, and doesn’t affect Bitcoin’s monetary properties or block size limits.
What Is OP_RETURN?
OP_RETURNis a Bitcoin script opcode introduced in 2014 (Bitcoin Core 0.9.0) to allow small amounts of arbitrary data to be embedded in transactions. Crucially, it creates provably unspendable outputs, preventing UTXO set pollution.A default policy limit of 80 bytes was added to discourage non-payment data usage while still allowing basic use cases (e.g., hashes, commitments).
Why Was OP_RETURN Added? (Bitcoin Core 0.9, March 2014)
When OP_RETURN was introduced, it wasn’t to promote on-chain data — it was a harm-reduction tool:
“This change is not an endorsement of storing data in the blockchain... [It] creates a provably-prunable output, to avoid data storage schemes... storing arbitrary data... bloating Bitcoin’s UTXO database.” — Bitcoin Core 0.9 Release Notes
Before that, users embedded data in fake outputs, bloating the UTXO set and degrading node performance.
OP_RETURN made those outputs prunable and cleaner, though it imposed an 80-byte policy cap — not a consensus rule.
What’s Actually Changing?
Bitcoin Core PR #32359 proposes:
- Removing the 80-byte policy limit on OP_RETURN data
- Removing the
-datacarrierand-datacarriersizeconfiguration options - Default behavior will now relay (and mine) larger OP_RETURNs
⚠️ This is not a consensus change. Blocks stay limited to \~4MB. No rules about block validity are altered.
Why It’s Not a Big Deal
- ✅ Consensus stays the same: No risk of chain splits
- ✅ Block size stays capped (\~4MB)
- ✅ You can still run Bitcoin Knots if you prefer stricter policies
- ✅ Transaction size limit (\~100KB) remains for DoS protection
Bottom line: This is a configuration tweak to improve consistency between nodes and miners.
Common Uses of OP_RETURN
- Timestamping
- Cross-chain anchoring (e.g., merge-mined sidechains)
- Asset issuance (e.g., Omni/Tether)
- Notarization and commitments
- Metadata for protocols like Citrea
📝 In contrast, Ordinal inscriptions use witness data; Stamps use fake outputs — not OP_RETURN.
Arguments For Removing the Limit
- The limit is ineffective — easily bypassed via witness/multisig/fake outputs
- Cleaner data paths — prevents UTXO bloat from “Stamp”-style tricks
- Reflects mining reality — miners already include these transactions
- Improves relay/mempool consistency
- Avoids centralization risks — removes miner advantages from custom policies
- Enables metaprotocols — safely embed structured metadata without abusing Bitcoin’s core design
Arguments Against Removing the Limit
- Risk of encouraging non-monetary use
- Fears of "spam" or NFT-like inscriptions
- Concerns over governance process
- Perceived erosion of Bitcoin’s monetary purity
🧠 Note: The 80-byte cap was policy, not consensus. Removing it doesn’t allow anything that wasn’t already valid on-chain.
Policy vs. Consensus
- Policy rules affect relay and mempool behavior
- Consensus rules affect what blocks are considered valid
Large OP_RETURNs are already valid. The inconsistency is that many nodes don’t relay them, while miners do include them. This change aligns relay with mining, improving propagation and fee estimation.
Bitcoin Knots: A Protest Client
Bitcoin Knots (maintained by Luke Dashjr) retains the old 80-byte policy. After the PR surfaced, some users switched to Knots as a protest.
According to Matthew R. Kratter, Bitcoin Knots briefly surpassed Core 29.0 in node count during early 2025 — but this spike appears to have been driven more by timing mismatches between release cycles and a coordinated protest campaign, rather than a durable shift in user adoption. In fact, most Bitcoin nodes today still run older versions of Core. As of May 2025, Core 28.1.0 alone accounts for over 21% of nodes, while Core 29.0.0 sits below 6%, and Knots 20250305 trails at just over 6% — suggesting that the majority of the network remains on pre-29 Core versions rather than switching to Knots en masse.
Broader Implications
- 🛠️ Highlights tensions between devs, miners, and users over governance
- 🧭 Shows how non-consensus rules can impact perceived neutrality
- 🧪 Sparks renewed focus on tooling (e.g., ASMap, better banlists, relay filtering)
- 🔐 Reaffirms user sovereignty through client diversity
Final Thoughts
Removing the OP_RETURN limit aligns Bitcoin Core’s policy with reality — what’s already getting mined — while cleaning up harmful workarounds.
It won’t break Bitcoin.
But it does surface deeper tensions about Bitcoin’s purpose, evolution, and who ultimately decides what gets built and accepted.
References
- PR: Remove arbitrary limits on OP_RETURN #32359
- PR: Deprecate datacarrier options #32406
- Mailing list: Relax OP_RETURN standardness restrictions
- Gist with full community discussion
- Bitcoin Knots
- Kratter video: Bitcoin Core Removes the Mask
🙏 Acknowledgements
Thanks to @hodlinator, ShiShi21m, and many others in the community for their thoughtful insights, corrections, and spirited discussion.
Based on the original GitHub Gist: Bitcoin OP_RETURN Controversy: Complete Summary
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.