-
 @ c230edd3:8ad4a712
2025-05-06 02:12:57
@ c230edd3:8ad4a712
2025-05-06 02:12:57Chef's notes
This cake is not too sweet and very simple to make. The 3 flavors and mild and meld well with the light sweetness.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 12
Ingredients
- 1 1/2 cups all-purpose flour
- 1/2 tsp salt
- 2 tsp baking soda
- 1 cup sugar
- 3 large eggs
- 1/2 cup full fat milk
- 3/4 cup unfiltered olive oil
- 2/3 cup finely chopped raw, unsalted almonds
- 2 tsp lavender
- 1 Tbsp powdered sugar
Directions
- Preheat oven to 350 degrees F. Lightly butter 8 inch baking pan.
- In smal bowl, whisk together flour, salt, and baking soda.
- In large bowl, beat eggs and sugar until light colored and fluffy. Add milk.
- Slowly pour and stir in olive oil.
- Fold dry ingredients into the wet ingredients,
- Stir in the almonds and the lavender, reserving some flowers for garnish.
- Pour into prepared pan and bake for 45 min, or until toothpick comes out clean.
- Cool on wire rack, dust with powdered sugar and top with reserved lavender.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ bf47c19e:c3d2573b
2025-05-11 17:37:45
@ bf47c19e:c3d2573b
2025-05-11 17:37:45Originalni tekst na nin.rs
20.09.2023 / Autor: Danica Popović
Da se preselimo na tržište kriptovaluta? Šalim se, naravno. Mada, pogledajte: da ste 2009. godine „iskopali“ bitkoin u vrednosti od jednog dinara, danas biste u svom bitkoin novčaniku imali - šezdeset hiljada dolara! Prosečna godišnja stopa rasta, dakle - dvesta devet odsto, zarada nevidljiva, a veća od one iz Кrušika i Jovanjice zajedno!
Zar ne biste pomislili - ovde vredi uložiti više od dva dinara, ili pet... ili milijardu? I onda, kako se takva želja zove? Pohlepa, naravno. Zato vas, sve redom, molim: nemojte govoriti da je pohlepa kriva za probleme u Srbiji, ili u svetu. Nije. Pohlepni su i svi ostali, od Adama i Eve do Hilari Кlinton ili Cukerberga, pa šta? Кad postoji sud i kakva-takva demokratija, stvari se nekako dovedu u red. Кad toga nema – kao kod nas, zar je kriva pohlepa što ne rade institucije?
E sad, kod bitkoina postoji veliki izuzetak: on čak podstiče pohlepu. Niko (sem vas) ne zna koliko ste zaradili, pa slobodno možete da utajite porez! Ni američka poreska uprava (IRS) ne može da uđe u trag prometu kriptovaluta, i sama je objavila da je u periodu od 2013. do 2018. godine samo 800 do 900 poreskih obveznika podnelo prijave o zaradi u kriptovaluti. Taj broj je rastao, ali, slabo, kažu: „brojevi su i dalje daleko od onih o broju korisnika, transakcija i vrednosti koju berze objavljuju na godišnjem nivou“.
Кoliko je situacija tu loša, najviše govori upitnik koji je američka poreska uprava zimus poslala na više od 10.000 adresa, obraćajući se onima za koje je smatrala da ima izgleda da nisu prijavili prihod od virtuelne valute. A jedan jedini poreski obveznik, koji je svoju poresku prijavu dopunio sa još 1,6 miliona dolara (stečenih prodajom bitkoina) upravo je bio jedan od primalaca pisma. Evo šta su ga pitali: „Da li ste u bilo kom trenutku tokom 2020. godine dobijali, prodavali, slali, menjali ili na bilo koji drugi način sticali bilo kakav finansijski interes u bilo kojoj virtuelnoj valuti?“
Кrajem decembra prošle godine i kod nas je usvojen Zakon o digitalnoj imovini, koji će se primenjivati od sredine ove godine. Tako će ovde na svaku transakciju kriptovaluta u kojoj se ostvari kapitalna dobit morati da se plati porez od 15 odsto – ne samo na dobit, već i na „kopanje“ bitkoina. Кako će to da izvedu, ne kažu. Ali je skoro sigurno da neće kao Amerikanci, da šalju pisma po kućama. Jer, ovakvo pismo bi kod nas značilo – plašiš mečku rešetom.
Sad da vidimo kolike su zarade – pa da krenemo u akciju. Bitkoin je prošlu godinu započeo sa vrednošću od 6.950,56 dolara, ali je već u martu pao za čitavu trećinu! Ipak, godina je završena sa prosečnim godišnjim rastom od 323 odsto, ili od 507 odsto od martovskog debakla. Pre mesec dana vrednost bitkoina je bila 48.200, a 5. aprila - 58.866,13 dolara!
Ovaj vrtoglavi rast bitkoin duguje Tesli, proizvođaču električnih automobila, koji je objavio da je kupio bitkoine u vrednosti od 1,5 milijardi dolara! I ne samo to: predstavnici Tesle su izjavili da će električne automobile prodavati i za bitkoine. Кako je time umanjen najrizičniji deo posla na kriptovalutama, a to je konverzija u „zemaljsku valutu“ - tražnja i cena bitkoina munjevito su skočile za dvadeset odsto, a zatim nastavile da rastu.
I šta sad? Bitkoin je, dakle, savršeni dvanaestogodišnji špekulativni balon. Da li će potrajati, ako se uz Teslu tržištu bitkoina pridruže i drugi proizvođači? Verovatno hoće, mada - možda i neće. Tržišta kriptovalute daleko su od predvidljivih i samo jedno znamo: kao i svaki špekulativni balon, i ovaj će pući.
Nije bitkoin dobar ni za svet, ni za nas. Za svet je loše, jer je proizvodnja veoma skupa: podaci o indeksu potrošnje električne energije pokazuju da je godišnja potrošnja energije prilikom „rudarenja“ kriptovaluta veća od godišnje potrošnje struje u Argentini ili Norveškoj. Skupo je za planetu, dakle.
Naravno, na tržištu kriptovaluta obavezno se mora imati veliki „apetit za rizik“. I još nešto: da bi posao imao smisla, neophodno je da učesnici budu sposobni da finansijski izdrže gubitak - koliko god on iznosio. A gde ste tu vi? Nigde, naravno.
Ipak je to njihova, a ne naša budućnost.
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ bf47c19e:c3d2573b
2025-05-11 17:37:14
@ bf47c19e:c3d2573b
2025-05-11 17:37:14Originalni tekst na nkatic.wordpress.com i politika.rs.
26.01.2022 / Autor: Nebojša Katić
Svet je odavno naučio da razorni ekonomski poremećaji ne dolaze iz sfere realne ekonomije već uvek nastaju u kockarnicama koje nazivamo berzama. Umesto obećanog velikog spremanja kojim bi se globalni finansijski sistem trajno stabilizovao, na sceni je suprotan proces. U finansijski kazino ulaze novi krupijei, unose se novi stolovi i aparati, ovoga puta za kockanje kriptovalutama.
Veličina kriptotržišta danas je na nivou od oko tri hiljade milijardi dolara, a broj različitih kriptovaluta se neprekidno povećava i sada ih ima oko šest hiljada. Još gore, ovo tržište više nije izolovano od ostalih segmenata finansijskih tržišta i sve se čvršće integriše u njega, povećavajući nestabilnost sistema. Kao da neko priziva ne samo novu finansijsku krizu, već Armagedon.
Kriptovalute su deo korpusa digitalnih valuta i u tom kriptošarenilu ima svega. Tu su elektronske valute koje centralne banke pripremaju kao zamenu za gotov novac. Tu su i „stabilne“ kriptovalute koje bi trebalo da imaju pokriće u drugim valutama ili berzanskim robama, poput valute koju planira „Meta“ (preimenovani „Fejsbuk“). Konačno, tu su i najluđe, plivajuće kriptovalute bez pokrića od kojih je bitkoin najpoznatija. One “plivaju” i njihova vrednost može tokom samo jedne godine skočiti za na primer 100 procenata ili pasti za 70 procenata. Tema ovog teksta je ta treća grupa kriptovaluta.
Pred ljudskom glupošću i gramzivošću i bogovi su nemoćni. Ekonomska istorija pamti neverovatne iracionalnosti, ludosti, podvale i berzanske histerije. Ali kada se klasične prevare ostave po strani, kod berzanske robe uvek je postojalo racionalno zrno, supstanca i vrednost koja bi kroz berzanski proces dobijala suludu cenu posle koje je dolazio slom.
Danas, s nastajanjem plivajućih kriptovaluta imamo novi fenomen – nečemu što je ništa, sada se može davati basnoslovna vrednost i time se može trgovati. To – ništa, taj digitalni zapis nastao ni iz čega, može se „rudariti“, kupiti na berzi ili dobiti razmenom za neku robu ili uslugu. Rudarenje je kompleksan proces u kome ogroman broj dokonih, inteligentnih ljudi troši svoje vreme i resurse moćnih računara rešavajući matematičke probleme koji se ne mogu rešavati olovkom i na papiru. Kada se zadaci uspešno reše, dobija se bitkoin.
Reč je o procesu besmislenog arčenja ljudskog i računarskog vremena. Računarski „rudnici“ u tom procesu troše i enormne količine električne energije i povremeno, kao nedavno u Irkutsku, rudari mogu izazvati i energetski kolaps. Sve ovo bi mogao biti samo patološki fenomen poput video igrica da je ostao u privatnoj sferi. Ali, kriptovalute su danas deo javne, finansijske sfere. Reč je o kreiranju privatnog novca bez pokrića koji bi, u svetu kojim vladaju red i razum, morao da bude zabranjen.
Nekome se može učiniti da je teza o tome da je bitkoin – ništa, prestroga. Ni moderni, „fiat“ novac nema materijalno pokriće i njegova vrednost počiva pre svega na našoj veri u njega. Ako te vere nema, novac postaje hartija bez vrednosti, kako se to i događalo kroz istoriju. Ali ta vera ipak ima racionalno uporište budući da postoje institucije koje brinu o vrednosti novca – to su države i njihove centralne banke. (Da li to rade dobro ili loše, nebitno je za kontekst ovog teksta.) O vrednosti i stabilnosti kriptovalute ne brine niko i to je prepušteno iracionalnosti tržišta. U slučaju bitkoina se čak ne zna ni ko stoji iza tog projekta. Njegova „vrednost“ počiva na tome što je ukupan broj bitkoina koji se mogu iskopati zauvek fiksiran na 21 milion komada … ako je verovati mojoj baki.
Tehnoentuzijasti ukazuju da je blokčein tehnologija ( blockchain), na kojoj počivaju kriptovalute, „tehnologija slobode“. Ona se tek razvija i traži svoje mesto u digitalnom svetu. Na njoj treba da počiva nova Web 3.0 revolucija u kojoj će veštačka inteligencija i algoritmi potpuno zameniti ljudske i institucionalne posrednike u sajbersferi. To je onaj tip tehnološke revolucije koja se prvo dogodi, a onda joj se traži svrha – u ime progresa, dakako.
U ovom trenutku ona omogućava promet kriptovaluta bez posredstva banaka, direktnim transferom sa „računa“ kupca na „račun“ prodavca. „Računi“ su u sajbersferi i tehnologija je takva da su transferi zaštićeni od zloupotrebe … osim kada baš i nisu i kada hakeri pokradu neku od kriptovaluta. Samo naivni ljudi mogu poverovati da u sajbersferi postoji bilo šta sigurno što se kriptografski može zaštititi.
No vratimo se tezama s početka teksta. Kriptovalute su besmislen, opasan instrument, sem ako niste u poslu šverca droge, oružja, ili ako na primer živite od ubijanja ljudi. Tada je zgodno imati diskretan način da svoje usluge naplatite. I to otvara ključno pitanje – da li to neko stimuliše ludilo kako bi se olakšali poslovi te vrste kada gotov novac bude ukinut? Ili je cilj možda još crnji i ide ka potpunoj destabilizaciji globalnog sistema i stvaranju haosa koji nadilazi i ovaj u kome trenutno živimo? U ovom trenutku, od moćnih ekonomija, samo je Kina zabranila i rudarenje kriptovaluta i njihov promet. Rusija se sprema da uradi to isto. Zašto su velike zapadne države tako pasivne i šta to one znaju što mi ne znamo?
-
 @ bf47c19e:c3d2573b
2025-05-11 17:35:59
@ bf47c19e:c3d2573b
2025-05-11 17:35:59Originalni tekst na politika.rs
13.09.2021 / Autor: Aleksandar Apostolovski
Za svet virtuelne banalnosti u koji smo umarširali potrebna je i njegova moneta. Kakav svet takvo i sredstvo plaćanja.
Ni četnički jataci nisu kao što su nekada bili. Ne skrivaju se u zemunicama, ne spremaju masnu gibanicu – prste da poližeš – ne čekaju zapadne saveznike da se iskrcaju na Jadranu. Verovatno nemaju ni brade modne linije starog američkog benda „Zi Zi Top”.
Nepoznata sajber ilegalna grupa upala je u podrum kuće čiča Draže u Ivanjici. Zaista, prvorazredna vest. Instalirali su snažne procesore i mašine za rudarenje bitkoinima i daljinskim sistemom. Ko zna odakle. Možda sa Kariba, možda iz Kosjerića, možda iz Jajca – ako su ipak partizani. Trgovali su kriptovalutama. Umalo da tako rasture uličnu rasvetu tokom „Nušićijade”, pa su čelnici opštine sproveli internu istragu, tražeći ilegalce koji vrše diverziju nad elektroenergetskim sistemom grada i festivalom satire.
Upali su u Dražin dom, sišli u podrum i zatekli sofisticiranu opremu, snažne procesore i nekakve mašine za rudarenje po internetu. Kompjuterski komandosi, naravno, nisu bili prisutni. Sada ih juri policija. Potrošili su oko 55.000 kilovat-sati struje. Verovatno se skrivaju pod stripovskim kodnim imenima, poput hakera iz Niša koji su ojadili Teksašane, pa im je doakao FBI, jer Ameri možda trpe svoje prevarante koji muzu kockare na globalnom groblju kriptovaluta, ali ne dozvoljavaju da se u međunarodnu spekulativnu igru ubace mozgovi sa južne pruge, gde je dozvoljeno da se prži paprika, pravi ajvar i sluša melanholični džez na „Nišvilu”.
Jedan od članova niške hakerske grupe je Antonije Stojiljković, koji se krio iza lažnih imena „Toni Rivas” i „Džejkob Gold”, a u slobodno vreme bio je reper poznatiji kao „Zli Toni”. Stojiljković je izručen Americi zbog računarskih prevara. Dobrovoljno se prijavio kako bi se sklonio u Ameriku.
Ti momci su nudili bitkoin upola cene i stvorili takvu virtuelnu međunarodnu mrežu lažnih kompanija, menadžera, uz organizaciju video-konferencija, da su omađijali dobar deo internet investitora iz Teksasa, te je Federalni istražni biro morao da spasava čast kauboja koje su izradile Nišlije. Njihov vođa, izvesni Kristijan Krstić, prestao je da se javlja policiji, nestao je sa suprugom i ortakom Markom Pavlovićem bez traga, iako su pod istragom, što može da poremeti i diplomatske odnose između Srbije i SAD.
Taj Kristijan, ne onaj Kristijan koji se seli iz rijalitija u rijaliti, koristio je nadimke poput „Feliksa Logana” ili „Maršala Grahama” i na internet prevarama zaradio je više desetina miliona evra. Priča nije nimalo bezazlena. Veze „Zlog Tonija” dosežu, bar po dosadašnjem toku istrage, sve do klana Belivuka.
Ali, to će rešavati sudovi i policija, mada i podaci koji su procurili otkrivaju suštinu fame bitkoin i na hiljade kriptovaluta koje može stvoriti bilo koji maher, avanturista, šaljivdžija, klinac, multimilioner, tajne službe, trgovci oružjem, narko-bosovi, plaćene ubice ili Del Bojevi koji će iduće godine postati milioneri.
Virtuelni svet ne može postojati bez virtuelnih valuta, s tim što one nisu opipljive, iza njih ne stoje centralne banke i vlade. Dakle, nemate pojma ko ih je stvorio, nemate pojma s kime trgujete i ko su brokeri.
Vidim da na „Jutjubu”, u motelu „Stari Hrast” na Koridoru 10, neki momci plaćaju prebranac i vešalice bitkoinima, preko mobilnih telefona. U kafani primaju i etereume, digitalni novčić u usponu, odmah iza bitkoina. I za to čudo je potreban digitalni novčanik... Ovde ću se zaustaviti jer je za svet banalnosti u koji smo umarširali potrebna i njegova moneta. Kakav svet takvo i sredstvo plaćanja.
Kako su kompjuterski podaci svih vrsta, od pretraživača, društvenih mreža, aplikacija, do podataka kompanija, državnih i međunarodnih organizacija, i onih ličnih, koje upravo vi posedujete, postali nezamislivo ogromna baza koju je nemoguće uskladištiti, otvorena je berza za internet magacionere koji će, rudareći na internetu, postati kandidati za potencijalne šefove skladišta. Teoretski, možete izrudariti deo arhive CIA. Preporuka – ako saznate ko je ukokao Kenedija, ćutite ko zaliveni!

(Dragan Stojanović)
Da je Alija Sirotanović kojim slučajem rudario kao specijalci iz Dražinog podruma, postao bi Bil Gejts. Alija je znao da nema ’leba bez motike, odnosno krampa. Zato je ostao Sirotanović. Ovo je novo doba. Mašina krampuje u simuliranoj stvarnosti, a virtuelni homo sapijens upravlja procesorima. Bitkoin vrti gde burgija neće! Stvar ipak nije tako idilična. Te skalamerije troše ogromne količine električne energije i strahovito zagrevaju prostorije, pa je u Dražinom podrumu bilo nešto vrelije nego u sauni. Priča se da su najveći mešetari otperjali na Island da se prirodno rashlade. Sledeće stanište im je Grenland.
Kome god je stalo do računarskog kriptovalutnog avanturizma može da formira svoj mali rudnik, gde nema zlata ni dijamanata, ali ima koina, odnosno stotog dela bitkoina. Jedan trenutno vredi 50.000 dolara. Pitam se, ovako zastareo, gde su banke i menjačnice?
Sa ono malo informatičkog znanja – valjda ću uspeti nekako imejlom da pošaljem ovaj tekst – saznao sam da vrednost bitkoina vrtoglavo skače i pada na dnevnom nivou, a kako je njegov broj ograničen na globalnom nivou, a neformalni šef Federalnih rezervi bitkoina je donedavno bio jedan od najbogatijih ljudi sveta Ilon Mask, koji je na svom tviter nalogu svakodnevno formirao grafikon rasta i pada svojim opaskama, tu već naslućujem elemente bondovskog zapleta. Harizmatični superbogataš koji leti u svemir, poseduje kompaniju električnih automobila „Tesla”, upravljao je donedavno imaginarnom berzom i valutom, ali je nedavno odustao. Možda zato emigrira u kosmos?
Stvar zaista može izmaći kontroli ili će, možda, bitkoin postati naša sudbina, a mi rudari iz sauna? Salvador je pre nekoliko dana postao prva zemlja na svetu koja je usvojila bitkoin kao zakonsko sredstvo plaćanja, uz američki dolar, s planovima korišćenja vulkanske geotermalne energije za napajanje rudarenja digitalne valute. Postavili su i bankomate. Tamošnjem narodu, kao i meni, ništa nije jasno.
Međutim, broj bitkoina je ograničen i zato pomalo podseća na zlato. Ali kod zlata ipak ponešto razumem. Recimo, ako imam zlatnu polugu i neko me napadne, mogu da je koristim u samoodbrani, a onda je sklonim u trezor banke.
Mogu da učinim i nešto drugo, jednako glupo. Da stvorim sopstvenu kriptovalutu. Nazvaću je „Ser Oliver koin”. Cijena će joj, logično, biti prava sitnica. Trebaju mi saradnici. Kruži fama da se popriličan broj klinaca, mahom dvadesetogodišnjaka, pridružio kultu bitkoina. Tokom korone izgubili su poverenje u sve, naročito u nas matore. Optužuju nas za izdaju i predviđaju propast država i zvaničnih valuta, uz uspon dvoglave aždaje – saveza bogataša i političara.
Delimično su u pravu, ali nisu ukapirali ključnu stvar. Aždaja raste, a oni rudare. Na kraju će završiti još gore nego Alija Sirotanović. Likovi im neće biti na novčanicama, a kablovima će biti priključeni za superkompjuter. Njihov novi vlasnik, s kodnim imenom „Procesor”, plaćaće ih idiot-koinima. Tražili smo, gledaćemo.
-
 @ bf47c19e:c3d2573b
2025-05-11 17:33:35
@ bf47c19e:c3d2573b
2025-05-11 17:33:35Originalni tekst na tasic.substack.com
07.09.2021 / Autor: Slaviša Tasić
U El Salvadoru je bitcoin od danas zvanična valuta. Valuta Salvadora je već neko vreme samo američki dolar. Svoju domaću više nemaju. Sada je dolaru dodat bitcoin.
Razlika između dolara i bitcoina u Salvadoru je velika. Dolar je tamo privreda sama prigrlila. Stara valuta nije valjala, bila je inflatorna i gubila vrednost, pa su ljudi bežali u dolar — trgovali, računali i štedeli u njemu. Onda je država jednog dana skroz digla ruke od sopstvene valute i proglasila dolar zvaničnom. Identična stvar dogodila se u Crnoj Gori kada je ona umesto tadašnjeg inflatornog dinara ozvaničila već raširenu nemačku marku. Kasnije se sa marke automatski prešlo na evro.
Bitcoin nije prihvaćen spontano. Niko u Salvadoru ne koristi bitcoin zato što dolar više nije popularan. Naprotiv, dolar je valuta koju ljudi biraju, u kojoj i dalje dobrovoljno plaćaju, računaju i štede. Bitcoin Salvadoru nameće država i u tom smislu on je bliži onoj staroj, prethodnoj, nametnutoj valuti. Predsedniku Salvadora se dopala ideja bitcoina pa je odlučio da ga uvede. Ne samo ozvaniči, jer niko ni do sada niko nije branio ljudima da trguju u bitcoinu ako hoće, nego i da prihvatanje bitcoina učini obaveznim. Sada, ako prodajete sladoled u Salvadoru i kupac hoće da vam plati bitcoinom, vi morate da ga primite.
Zato ja ne prodajem sladoled u Salvadoru.
Kriptovalute su tako napravile još jedan korak ka paradoksu. Nekada su one bile subverzivni projekat. Bitcoin je trebalo da zameni dolar i druge državne valute zato što je bolji, stabilniji i anonimniji. Zato što je blockchain, njegova platna infrastruktura, trebalo da bude brža, efikasnija i jeftinija. Trebalo je da iz Argentine šaljemo novac u Indiju brzo i besplatno. Privatno generisani i decentralizovani kripto novac trebalo je da potisne državne valute i centralizovane finansijske sisteme. To je bio narativ iza bitcoina i kripto pokreta. Centralne i sve druge banke, odzvonilo vam je!
Trinaest godina kasnije, bitcoin u jednu državu uvodi jedan predsednik. Jeste on mladi i kul predsednik, sluša kripto podkaste i ide na bitcoin konferencije, ali upravo to zamagljuje sliku pa pristalice ne vide suštinu: da bitcoin ovde uvodi država i njen monopol sile.
Finansije Salvadora me slabo zanimaju, ali kao ilustracija o kakvom se šarlatanstvu ovde radi pogledajte šta kaže gospodin predsednik:

Zašto jedna država kupuje bitcoin? Mogao je i da ode u kladionicu i stavi pare iz budžeta na Juventus — šanse za dobitak su tu negde, a kladionica troši manje struje.
I ne znam da li opozicija u Salvadoru ima plan i program, ali evo kako bitcoin predsednik raspravlja sa poznatim monetarnim ekonomistom. Služeći se argumentom OK, boomer:

Bitcoin moraju ovako nametati jer bitcoin nije novac. Njegova vrednost je ovih dana ponovo porasla, opet je prešao $50,000, a desilo se da ga daleka država u isto vreme ozvaniči i zato su ponovo krenule vesti i priče o ovoj valuti budućnosti. Ali bitcoin nije novac i to isto važi za sve kripto valute.
Novac služi za plaćanja, a bitcoin to ne ume dobro da radi. Njegov platni sistem je glomazan, spor i skup. Da, njime se može ponegde plaćati, ali prodavci to rade iz promotivnih razloga, ne realne potrebe. Sam sistem je daleko inferiorniji od sistema koje već imamo i tu nekog napretka nema. Za ono što bitcoinu i njegovom blockchainu trebaju minuti, Master i Visa sistemi urade u milisekundama, uz daleko niže provizije.
Novac je i merilo vrednosti. U Salvadoru vrednost mere u dolarima, u Japanu u jenima. U Srbiji to radimo malo u dinarima, a malo više u evrima. Ali nikad nisam nikoga čuo da kaže da kilo banana košta 650 satoshija ili da mu nekretnina vredi 3.7 bitcoina.
Treći kriterijum za novac je čuvanje vrednosti i to bitcoin radi malo bolje. On ne samo da je do sada sačuvao vrednost nego je i neverovatno uvećao. To nije klasično čuvanje vrednosti, jer malo ko ulaže u bitcoin da bi se zaštitio od pada dolara ili evra. Bitcoin se kupuje jer se može desiti da opet jako skoči. To je spekulativni, a ne odbrambeni motiv. Ali ako i uzmemo da je to neki vid čuvanja vrednosti, dosadašnji rast ne kaže nam ništa o bitcoinu kao čuvaru buduće vrednosti. Da je bio stabilan od početka, možda bih poverovao. Vrtoglavi rast bilo čega retko znači buduću stabilnost.
Ovde se kripto entuzijazisti pobune i kažu da ni sadašnje papirne valute ne čuvaju vrednost. Valute kao evro ili dolar su papir samo u smislu u kojem su bitcoin bajtovi informacija i kilovati struje — to je jedna njihova primitivna manifestacija, a ne suštinska karakteristika. Evro nije “papir”; evro je obećanje Evropske centralne banke da će uspešno ciljati inflaciju od 2% godišnje. Ne morate verovati u to obećanje, možete sumnjati u proces izbora ciljeva i guvernera, u njihovo znanje i namere — ali to je suština evra kao novca. To je podloga evra. Isto važi i za dolar, jen ili dinar. Nekada je novac imao zlatnu podlogu, nekada srebrnu, a njegova sadašnja podloga je obećanje jedne manje ili više kredibilne institucije. Nije papir.
Obećanje o ciljanju inflacije sa sobom nosi jednu važnu funkciju. Svi govore o ograničenoj ponudi bitcoina: programski je on ograničen na 21 milion bitcoina i ne može se štampati preko toga. Ali cenu osim ponude određuje i tražnja. Novac nije izuzet iz toga. Ciljanje inflacije — što je identično ciljanju vrednosti novca u odnosu na zadatu korpu roba — postiže se reagovanjem centralne banke na promene tražnje za novcem.
Ponuda dolara, evra i drugih običnih valuta je fleksibilna, što znači da ih besomučnim štampanjem možete obezvrediti. Ali fleskibilnost znači i da ih možete emitovati i povlačiti tako da odgovarate na tražnju za njima, sa ciljem da njihova vrednost u odnosu na korpu roba ostane stabilna. I to je ključna prednost koju centralne banke imaju nad kripto valutama. Zbog toga su valute centralnih banaka vrlo dobro merilo vrednosti i vrlo predvidivi čuvari vrednosti.
Ne treba vam većeg dokaza za to od uspona stablecoina, kripto valuta čija je vrednost vezana za dolar. Kripto valute su došle sa namerom da ga poraze, a sada se vezuju za dolar da bi od njega pozajmile stabilnost koju nemaju. A dolar stabilnost ima zato što centralna banka aktivno cilja njegovu vrednost i manipuliše ponudom dolara da bi odgovarala tražnji za njima. Ako neka kripto valuta reši ovaj problem odgovora ponude na tražnju, možda će i uspeti.
Ovakav kakav je, bitcoin može još dugo da održava vrednost ili raste. Razlog su naši komplikovani ukusi, procene i očekivanja. U tom smislu za mene je bitcoin i dalje najviše uporediv sa apstraktnom umetnošću: ni ona ne valja, ne vredi ništa, ali ljudi imaju neke svoje ideje, kupuju te stvari jedni od drugih za mnogo para i one već decenijama ipak drže visoku vrednost.
Druge dve funkcije novca on ne obavlja, jer niti valja kao platežno sredstvo niti meri bilo šta. Zato bitcoin i nijedna kripto valuta za sada nisu novac. I nijedan državni dekret to neće promeniti. Možda neka bolja kripto valuta, u budućnosti, hoće.
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:17
@ 266815e0:6cd408a5
2025-05-02 22:24:17Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ bf47c19e:c3d2573b
2025-05-11 17:33:05
@ bf47c19e:c3d2573b
2025-05-11 17:33:05Originalni tekst na danas.rs
11.01.2021 / Autor: Aleksandar Milošević
Ima više od osam godina otkako sam prvi put čuo za to nešto što se zvalo bitkoin.
Libertarijanski san: „Decentralizovana“ valuta koju ne kontroliše nijedna država; na koju nijedna centralna banka ne može da utiče; koju je zahvaljujući „blokčejn“ tehnologiji nemoguće falsifikovati i koja nudi anonimnost kakvu poznaje samo keš.
Valuta čija je ukupna količina unapred fiksirana pa joj je rast vrednosti usađen u DNK.
I to još valuta koju je moguće dobiti besplatno, ali po zasluzi, jer bitkoini nastaju tako što vaš kompjuter reši komplikovani matematički zadatak iza kojeg se „krije“ jedan od ovih magičnih novčića.
To što je čitav sistem osmislio misteriozni matematički genije poznat kao Satoši Nakamoto, koji možda postoji, a možda i ne postoji i što se ceo finansijski establišment obrušio na čitavu bitkoin-maniju kombinacijom podsmeha i represivnih pretnji, moglo je samo da ubrza moju tadašnju odluku da kupim XFX ATI RADEON HD 5870 grafičku karticu za nekih 200 evra (maksimum koji sam od skromne novinarske plate mogao sebi da oprostim) i priključim se drugoj velikoj zlatnoj groznici, nekih 150 godina nakon one originalne, kalifornijske.
Ipak, kao što se da pretpostaviti iz činjenice da danas pišem ovaj tekst umesto da na nekom tropskom ostrvu vežbam skokove u vodu, sudbina nije htela da se obogatim rudareći bitkoine.
Ispostavilo se, naime, da moja moćna grafička karta ne odgovara mojoj dosta nesposobnoj matičnoj ploči, pa sam uz pomoć najgore „cost-benefit“ analize u istoriji biznisa zaključio da je bolje da prodam grafičku sa 20 evra gubitka i zaboravim na sve, nego da zarad svoje igrarije menjam čitav kompjuter.
Ta greška koštala me je nekih 700.000 dolara.
Toliko bih, žalosno je, danas imao da sam propalu investiciju u pogrešan hardver pretvorio u novotariju zvanu kriptovaluta, po tadašnjem kursu od 10 dolara za novčić, umesto što sam „zaboravio na sve“.
Bitkoin je, ispostavilo se, postao prilično velika stvar.
S kursom od 40.000 dolara za jedan bitkoin, s međunarodnim bankama koje spekulišu ovom valutom, s nuklearnim naučnicima hapšenim jer su ruski državni superkompjuter upregli da za njih rudari bitkoin, sa novinskim izveštajima o ljudima koji idu u zemlje s jeftinom strujom da u njima instaliraju čitava skladišta puna računara za traženje bitkoina, pa čak i sa poslednjim pričama koje krive upravo bitkoin za to što je u Pakistanu pao napon struje za 200 miliona ljudi i što je 500 miliona Evropljana zamalo ostalo bez svetla, nema nikakve sumnje da je bitkoin nešto veliko.
A opet, to nešto veliko i dalje uporno ostaje – ništa.
Ma koliko neverovatna cena od 40.000 dolara delovala zavodljivo, bitkoin entuzijasti su već jednom, pre tačno dve godine, sve to već doživeli, kada je ova valuta prvi put u meteorskom usponu za samo par nedelja dostigla 20.000 dolara, da bi se onda jednako naglo i jednako neobjašnjivo survala nazad, ostavljajući mnoge sa velikom i nimalo virtuelnom rupom u džepu.
Osnovni problem bitkoina, uzrok njegove karakteristične nestabilnosti – ogromnih skokova i jednako spektakularnih padova – jeste to što niko ne zna za šta je on koristan.
Ma kako uzbudljivo delovala čitava priča o novcu koji je van kontrole vlade, koji nudi anonimnost transakcija i koji je navodno nemoguće falsifikovati, činjenica je da prosečnoj osobi ništa od toga nije potrebno.
Tačnije, bitkoin – sem u uskom krugu slučajeva – ne nudi ništa što već ne možete da dobijete sa svojom valutom, a da vam je potrebno.
Za anonimnost je većini dovoljan keš, rizik od falsifikata je dovoljno mali da je zanemarljiv, a kontrola države i nezavisnost od monetarnih vlasti su priče koje su ljudima eventualno intelektualno zanimljive, ali nikog neće naterati da u praksi krene da koristi neku virtuelnu valutu.
Zato je bitkoin ostao novac ponajviše upotrebljavan za nezakonite transakcije – otkup podataka od hakera, prodaju droge i tome slično – gde su anonimnost i elektronski transfer novca bitniji od svega.
Zašto onda raste cena bitkoinu?
Zato što svi kupuju bitkoine nadajući se da će im cena skočiti i da će zaraditi.
Kako raste tražnja tako raste cena i očekivanje se ispunjava.
Onda kad tražnja nestane, a to će se desiti kad svi koji su upravo sad čuli za bitkoin pokupuju virtuelne novčiće videvši koliki je rast cene u poslednjim danima, cena će krenuti da pada.
Jer – bitkoini nikom nisu potrebni i niko ne želi da ih zadrži. Sve što svi žele je da ih kupe, da im cena „iz nekog razloga skoči“ i da ih onda zamene za „pravi novac“.
U toj igri, koja se stalno ponavlja kako naiđe novi talas publiciteta, neko naravno mora i da izgubi.
Bitkoin neće postići stabilnost i neće uspeti da iskaže svoju „deflatornu“ prirodu u koju se svi uzdaju da im trajno podiže vrednost novčića koje poseduju, sve dok se ne bude pronašla njegova svrha kao valute.
Dok dovoljno veliki broj ljudi ne bude hteo da drži i koristi bitkoine za ono za šta je svaka valuta namenjena – za kupovinu roba i usluga.
Droga, oružje, ucene i ostale oblasti kriminalne ekonomije nisu dovoljni da bi se takva stabilnost postigla.
Glavni problem bitkoina je zato njegova praznina.
Bitkoin nije zlato našeg doba. Pre je blato.
-
 @ 84b0c46a:417782f5
2025-05-10 10:41:20
@ 84b0c46a:417782f5
2025-05-10 10:41:20https://long-form-editor.vercel.app/
β版のため予期せぬ動作が発生する可能性があります。記事を修正する際は事前にバックアップを取ることをおすすめします
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの😃アイコンから←アイコン変えるかも)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 9063ef6b:fd1e9a09
2025-05-11 17:28:34
@ 9063ef6b:fd1e9a09
2025-05-11 17:28:34This article explores potential vulnerabilities in bitcoin that quantum computers might exploit in the future.
But to be clear: today’s quantum computers are still in early stages, many questions are unresolved, and they are not expected to pose a serious threat any time soon.
1. Why Quantum Computing Threatens Bitcoin
Bitcoin’s current cryptographic security relies on ECDSA (Elliptic Curve Digital Signature Algorithm). While this is secure against classical computers, a sufficiently powerful quantum computer could break it using Shor’s algorithm, which would allow attackers to derive private keys from exposed public keys. This poses a serious threat to user funds and the overall trust in the Bitcoin network.
Even though SHA-256, the hash function used for mining and address creation, is more quantum-resistant, it too would be weakened (though not broken) by quantum algorithms.
2. The Core Problem
Bitcoin’s vulnerability to quantum computing stems from how it handles public keys and signatures.
🔓 Public Key Exposure
Most Bitcoin addresses today (e.g., P2PKH or P2WPKH) are based on a hash of the public key, which keeps the actual public key hidden — until the user spends from that address.
Once a transaction is made, the public key is published on the blockchain, making it permanently visible and linked to the address.

🧠 Why This Matters
If a sufficiently powerful quantum computer becomes available in the future, it could apply Shor’s algorithm to derive the private key from a public key.
This creates a long-term risk:
- Any Bitcoin tied to an address with an exposed public key — even from years ago — could be stolen.
- The threat persists after a transaction, not just while it’s being confirmed.
- The longer those funds sit untouched, the more exposed they become to future quantum threats.
⚠️ Systemic Implication
This isn’t just a theoretical risk — it’s a potential threat to long-term trust in Bitcoin’s security model.
If quantum computers reach the necessary scale, they could: - Undermine confidence in the finality of old transactions - Force large-scale migrations of funds - Trigger panic or loss of trust in the ecosystem
Bitcoin’s current design protects against today’s threats — but revealed public keys create a quantum attack surface that grows with time.
3. Why It’s Hard to Fix
Transitioning Bitcoin to post-quantum cryptography is a complex challenge:
- Consensus required: Changes to signature schemes or address formats require wide agreement across the Bitcoin ecosystem.
- Signature size: Post-quantum signature algorithms could be significantly larger, which affects blockchain size, fees, and performance.
- Wallet migration: Updating wallets and moving funds to new address types must be done securely and at massive scale.
- User experience: Any major cryptographic upgrade must remain simple enough for users to avoid security risks.
4. The Path Forward
The cryptographers worldwide are already working on solutions:
- Post-Quantum Cryptographic Algorithms are being standardized by NIST, including CRYSTALS-Dilithium, Kyber, FALCON, and SPHINCS+.
- Prototypes and experiments are ongoing research networks.
- Hybrid signature schemes are being explored to allow backward compatibility.
Governments and institutions like NIST, ENISA, and ISO are laying the foundation for cryptographic migration across industries — and Bitcoin will benefit from this ecosystem.
References & Further Reading
- https://komodoplatform.com/en/academy/p2pkh-pay-to-pubkey-hash
- https://csrc.nist.gov/projects/post-quantum-cryptography
- https://www.enisa.europa.eu/publications/post-quantum-cryptography-current-state-and-quantum-mitigation
- https://en.bitcoin.it/wiki/Quantum_computing_and_Bitcoin
- https://research.ibm.com/blog/ibm-quantum-condor-1121-qubits
- https://blog.google/technology/research/google-willow-quantum-chip/
- https://azure.microsoft.com/en-us/blog/quantum/2025/02/19/microsoft-unveils-majorana-1-the-worlds-first-quantum-processor-powered-by-topological-qubits/
- https://www.aboutamazon.com/news/aws/quantum-computing-aws-ocelot-chip
```
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ 5df413d4:2add4f5b
2025-05-01 12:33:30
@ 5df413d4:2add4f5b
2025-05-01 12:33:30*Short photo-stories of the hidden, hard to find, obscure, and off the beaten track. *
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ bf47c19e:c3d2573b
2025-05-11 17:27:10
@ bf47c19e:c3d2573b
2025-05-11 17:27:10bitcoinstandard.rs
Autor Bitkoin standarda, ekonomista Sajfedin Amus, vešto uvodi svakog čitaoca u svet digitalnog novca pokazujući da bitkoin može da postane dominantni čuvar vrednosti u budućnosti, a jedna od glavnih snaga knjige je njena sposobnost da objasni kompleksne ekonomske i tehničke aspekte bitkoina na razumljiv i jednostavan način.
Sajfedin Amus prvo prikazuje fascinantnu istoriju tehnologija novca i istražuje šta je tim tehnologijama dalo njihovu monetarnu ulogu, kako su je izgubile, šta nas to uči o poželjnim osobinama novca i kako je bitkoin osmišljen da unapredi te tehnologije. Amus zatim objašnjava ekonomske, društvene, kulturne i političke prednosti zdravog novca u odnosu na nezdrav novac kako bi omogućio relevantnu raspravu o ulozi koju bi bitkoin mogao imati u digitalnoj ekonomiji budućnosti. Umesto kao valuta za kriminalce ili jeftina masovna mreža za plaćanja, ova knjiga pokazuje kako bitkoin izrasta kao decentralizovana, politički neutralna, slobodnotržišna alternativa nacionalnim centralnim bankama, sa potencijalno ogromnim implikacijama za individualnu slobodu i prosperitet.
Sa ovim osnovama, knjiga prelazi na objašnjenje funkcionisanja bitkoina na lak i intuitivan način. Bitkoin je decentralizovani, distribuirani softver koji omogućava svojim korisnicima da koriste internet za obavljanje tradicionalnih funkcija novca bez oslanjanja na bilo kakve autoritete ili infrastrukturu u fizičkom svetu. Bitkoin se tako najbolje razume kao prvi uspešno implementirani oblik digitalne gotovine i digitalnog tvrdog novca – digitalni oblik zlata.
Amusovo čvrsto razumevanje tehnoloških mogućnosti kao i istorijskih realnosti evolucije novca omogućava istraživanje posledica dobrovoljnog slobodnog tržišta novca. Izazivajući najsvetije državne monopole, bitkoin pomera klatno suvereniteta od vlada ka pojedincima, nudeći nam primamljivu mogućnost sveta u kojem je novac potpuno odvojen od politike i nesputan granicama.
Završno poglavlje knjige istražuje neka od najčešćih pitanja u vezi sa bitkoinom: Da li je rudarenje bitkoina rasipanje energije? Da li je bitkoin za kriminalce? Ko kontroliše bitkoin i mogu li ga promeniti ako žele? Kako se bitkoin može uništiti? I šta misliti o svim hiljadama kopija bitkoina i mnogim navodnim primenama bitkoinove „blockchain tehnologije“?
-
 @ bf47c19e:c3d2573b
2025-05-11 17:26:13
@ bf47c19e:c3d2573b
2025-05-11 17:26:13Originalni tekst na luxb.substack.com.
27.10.2022 / Autor: Lux Bitcoin
Najosnovniji način prijenosa vrijednosti je trampa.
Trampa, međutim, ima tri glavna ograničenja: zahtijeva podudarnost razmjera, prostora i vremena.
Podudarnost razmjera: ono što želite možda nema istu vrijednost kao ono što želite dati.
Podudarnost prostora: ono što želite može biti na različitim mjestima od onoga što želite dati.
Podudarnost vremena: ono što želite možda nema istu kvarljivost kao ono što želite dati.
Kako bi se prevladala ova ograničenja, pokušalo se koristiti intermedijarni dobra, s funkcijom novca.
Ta su dobra morala biti lako djeljiva, lako prenosiva, lako prepoznatljiva i nekvarljiva. Stoga su morala biti potrošna u razmjeru, prostoru i vremenu.
Potrošnost kroz vrijeme je najzanimljivije svojstvo.
Neko dobro se može potrošiti kroz vrijeme ako je fizički nepromjenjivo. Ali nepromjenjivost materijala nije dovoljna za očuvanje vrijednosti, potrebno je i održavati stabilnom količinu dostupnu na tržištu.
Da bismo razumjeli ovaj koncept, uzmimo primjer RAI kamenja, koje se koristilo kao valuta na otoku Yap.

Izvorno je nabaviti ovo kamenje bilo vrlo teško, pa nije bilo načina da se ih se previše inflacionira, ali iskrcavanjem kapetana O'Keefea 1871. situacija se promijenila. Zahvaljujući tehnološki naprednijim alatima kapetan je bio u stanju nabaviti nebrojeno kamenje, stvorivši inflaciju i uzrokovao da RAI izgubi status valute.
Inflacija nekog dobra uzrokuje mu gubitak vrijednosti.
Gubitak vrijednosti dobra otežava njegovu trošnost.
Povijest novca
Nakon pokušaja sa stokom, kamenjem, školjkama, žitaricama i solju, odlučeno je da se metalima pripiše funkciju novca, budući da ih se moglo modelirati u jednakim jedinicama.
Među metalima koji su se koristili kao novac, zlato je postalo dominantno zbog svoje nepromjenjivosti i iznimne teškoće u pronalaženju. Ove dvije karakteristike omogućile su mu da zadrži svoju vrijednost tijekom godina.
Novac koji ne zadržava svoju vrijednost tijekom vremena uzrokuje ogromnu štetu zajednicama. Uzmimo primjer Rimskog carstva.

Uvođenje Aureusa od strane Julija Cezara omogućilo je ogromno i uspješno tržište koje se širilo diljem Europe i Mediterana.
Međutim, Neron je, u nedostatku sredstava, počeo kovati novac sa sve manjom količinom plemenitog metala. S ovim trikom mogao je računati na mnogo više sredstava da ugodi narodu, primjerice davanjem kruha i igara.
Što su financije bile lošije, to se više metala oduzimalo. Od 8 grama Cezarovog Aureusa, sa godinama se prešlo na novčić sa samo 4,5 grama zlata. To je omogućilo carevima da troše iznad svojih mogućnosti, stvarajući osnove za ekonomsku propast carstva.
Kraj Carigrada također se poklopio sa devalvacijom novca. Sa novčanim padom dogodio se i kulturni, financijski i vojni pad.
Pad rimskog carstva i stalna devalvacija novca stvorili su ozbiljne prepreke trgovini i naveli stanovništvo da se organizira u male samodostatne zajednice nepovjerljive jedna prema drugoj.
Preporod nakon razdoblja ratova i gladi koincidirao je s usvajanjem novog novčanog standarda. Sve je počelo u Firenci 1252. godine kada je grad uveo florin, zlatnik s fiksnom težinom. Zahvaljujući svojoj stabilnosti, florin je postupno zamijenio sve bakrene i brončane kovanice koje se lako inflatiralo i predstavljao je uzor cijeloj Europi. Venecija je bila prva koja je slijedila primjer Firence kujući Dukat, ali još 150 drugih gradova prilagodilo se novom standardu.
S procvatom trgovine Europa, a posebno Italija, doživjeli su veliki gospodarski i kulturni procvat.
Usvajanje jakog novca kroz povijest uvijek je bilo nagrađeno rastom i prosperitetom. Drugi primjer je Britansko Carstvo, najveće u ljudskoj povijesti, koje je usvojilo moderni zlatni standard 1717. Iako se zlatom nije više trgovalo u malim transakcijama, ono je i dalje ostalo kao referenca za novčanice.
Zemlje poput Indije i Kine skupo su platile izbor kasnije prilagodbe zlatnom standardu.

Dok je veći dio planeta usvajao zlatno standard, stigla je La Belle Epoque, jedno od najprosperitetnijih razdoblja u ljudskoj povijesti. Uz jaki novac zajednički svim zemljama poticana je trgovina, a stabilnost novca tijekom vremena omogućila je akumulaciju kapitala potrebnog za ulaganja.
Godine 1914., s Prvim svjetskim ratom, zlatni standard je suspendiran.
Ako su sa jakim novcem ratovi završavali kad je državi nedostajalo novca, sa slabim novcem to više nije bio problem. Skriveni porez, inflacija, omogućio je nastavak ratova sve dok cjelokupno nacionalno bogatstvo nije erodirano.

Nakon rata, Sjedinjene Države doživjele su najgoru gospodarsku krizu ikada zabilježenu: Veliku depresiju. Uvriježeneo je mišljenje da se iz depresije izašlo zahvaljujući povećanju javne potrošnje (New Deal). Zapravo, kreditna ekspanzija 1920-ih je to uzrokovala, a New Deal je samo pogoršao situaciju.
U 1930-ima države su nastavile napuhavati valute.
Totalitarni režimi imali su svaki interes financirati se bez ubiranja poreza.
Keynes, ekonomist koji je rat smatrao učinkovitim načinom borbe protiv nezaposlenosti, teoretizirao je izlazak iz zlatnog standarda.
Drugi svjetski rat doista nije kasnio.
Godine 1971. Sjedinjene države definitivno napuštaju zlatni standard, započevši neobuzdanu monetarnu ekspanziju koja traje sve do danas. Za predodžbu: ako je 1971. unca zlata vrijedila 35 dolara, danas vrijedi 1500.

Korištenjem lako inflatornih valuta riskira se hiperinflaciju, odnosno drastičan gubitak kupovne moći u kratkom vremenu.
Primjeri hiperinflacije su Njemačka 1920-ih s dnevnom inflacijom od 20%, te Mađarska 1940-ih s dnevnom inflacijom od 207%.
U Mađarskoj su se cijene udvostručavale svakih 15 sati, što je učinilo apsolutno nemogućim uštedu i prijenos vrijednosti tijekom vremena.
Očigledno sve to ne bi bilo moguće s novcem koji teško podliježe inflaciji.
Bitcoin
Prije Bitcoina bile su moguće samo dvije vrste plaćanja:
-
Gotovinska plaćanja bez posrednika
-
Elektronička plaćanja putem posrednika
Gotovinska plaćanja su trenutna, ali zahtijevaju fizičku prisutnost obiju strana. Elektronička plaćanja mogu se izvršiti i na daljinu, ali za to je potreban posrednik koji ovjerava plaćanje i naplatu.
Bitcoin je prvi oblik novca koji omogućuje elektronička plaćanja bez uključivanja posrednika kao što su države ili banke, a to ga također čini prvom valutom koja nije podložna inflaciji, koja se ne može zaplijeniti, koja se ne može cenzurirati, koja može prenijeti vrijednost bolje od bilo čega kroz redove veličine, prostor i vrijeme.
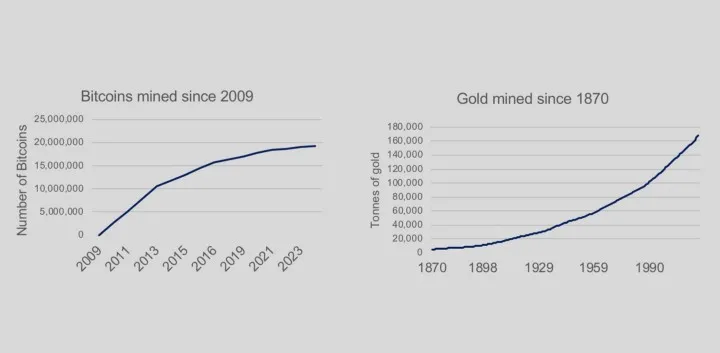
Ako zlato ima inflaciju koja fluktuira oko 2%, Bitcoin ima inflaciju koja se prepolovi svake 4 godine sve dok ne dosegne nulu i ostane tamo zauvijek. Bitcoin je, dakle, prva valuta u povijesti koja će imati nultu inflaciju.
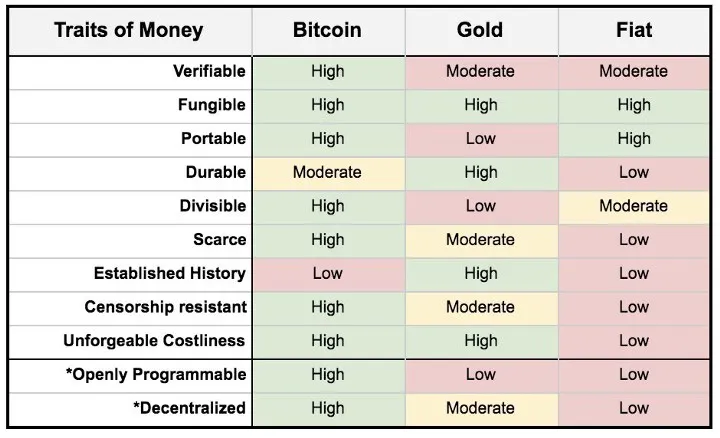
Prednosti Bitcoina u odnosu na zlato su ogromne: lakše ga je prenositi, omogućuje veću transparentnost i jamči manju inflaciju.
S manje inflacije:
1 - čuva se vrijednost tijekom vremena;
2 - olakšava se trgovanje;
3 - olakšava se ekonomska računica;
4 - jamči se sloboda pojedincima neovisno od središta moći.
Vremenska preferencija
Racionalnim pojedincima je uvijek bolje odmah pristupiti nekom dobru nego to odgađati tijekom vremena. Upravo zato se čekanje u gospodarstvu uvijek mora nagraditi.
Vrednovanje budućnosti u odnosu na sadašnjost omogućuje proizvodnju kapitalnih dobara, odnosno dobara stvorenih ne za potrošnju, već korisnih za proizvodnju budućih dobara.
Primjer: s čamcem se ulovi više ribe nego golim rukama, ali da bi se izgradio čamac potrebno je žrtvovati vrijeme i energiju bez istančane nagrade.
Zamislimo dvije individue na pustom otoku.
Laura budućnost shvaća vrlo ozbiljno;
Mario preferira trenutačno zadovoljstvo.
Mario provodi 8 sati dnevno kako bi golim rukama ulovio potrebnu ribu. Laura čini isto, ali nakon pecanja još dva sata posvećuje izradi štapa za pecanje. Nakon tjedan dana Laura je dovršila štap za pecanje i time može pokriti svoje dnevne potrebe u pola vremena koliko je potrebno Mariu. Sljedećih mjeseci, radeći isto sati kao i Mario, Laura ima vremena izgraditi čamac, mrežu i druge alate koji joj omogućuju da u jednom satu ulovi puno više ribe nego što Mario ulovi kroz cijele dane.

Na Stanfordu, 1960. napravljen je eksperiment.
Djeci je ponuđen slatkiš uz obećanje da će dobiti još jedan ako izdrže 15 minuta da ga ne pojedu. Djeca su stoga morala birati hoće li odmah dobiti jedan slatkiš ili dva nakon 15 minuta. Godinama kasnije, pronađena je korelacija između onih koji su uspjeli odgoditi zadovoljstvo i onih koji su postigli veće akademske i sportske rezultate.
Odgađanje zadovoljstva omogućuje štednju.
Štednja omogućuje investicije.
Investicije povećavaju produktivnost.
Štednja se općenito potiče u sigurnim društvima, gdje su porezi niski i gdje je vlasništvo zaštićeno. Temeljni čimbenik u jamčenju štednje je imati jaku valutu, koju se ne može lako napuhati. Ako valuta stalno gubi vrijednost, više se potiče da je se potroši nego da je se sačuva.
Prijelaz s valute koja gubi vrijednost na valutu koja svoju vrijednost zadržava stoga je ključno na duge staze, jer to može činiti razliku izmađu rasta ili pada jednog društva.

Valuta koja s vremenom gubi vrijednost obeshrabruje štednju u korist potrošnje, rizičnih ulaganja i zaduživanja.
Jaka valuta, osim što pogoduje štednji, poboljšava i ekonomsku računicu, odnosno omogućuje mjerenje iskusnosti resursa i donošenje racionalnih odluka o proizvodnji i potrošnji.
Npr: ako je roba za kojom postoji velika potražnja oskudna, povećanje cijene potiče njezinu proizvodnju i obeshrabruje potrošnju.
Obrnuto, ako dobra za kojim nema potražnje ima puno, pad cijene obeshrabruje njegovu proizvodnju i potiče potrošnju.
Ista dinamika vrijedi i za novac čija se cijena naziva “kamatna stopa”.
Trošak zajmova trebao bi se smanjiti ako je štednje puno, a porasti ako je štednje malo, kako bi uvijek postojala ispravna ravnoteža i ispravni poticaji.
Ponovimo koncept: ako malo tko posuđuje, kamate bi trebale pasti, tako da olakšava posuđivanje novca. Ako pak mnogi traže posudbe, kamate bi trebale porasti, kako bi se destimuliralo traženje kredita i poticala štednja.
Sa slabom valutom događa se umjesto toga da kamatne stope ne odražavaju ravnotežu između štednje i ulaganja. Centralne banke stvaraju kamatne stope koje su niže od tržišnih, potičući potrošnju i ulaganja čak i kad je štednja oskudna.
Uz investicije koje zahtijevaju više sredstava nego što su stvarno dostupna, sistemske krize su neizbježne.
Djeluje ovako:
-
Stvori se nova valuta
-
Povećaju se investicije
-
Smanjuje se štednja
-
Pokreće se više ulaganja nego što ima raspoloživih sredstava
-
Investicije propadaju

Valute koje gube vrijednost ne dopuštaju cijenama da signaliziraju stvarnu oskudicu resursa, dakle da koordiniraju proizvodnju i potrošnju.
Loše investicije, nastale zbog niskih kamata i gubitka vrijednosti valute, glavni su uzrok gospodarskih kriza.
Cilj centralnih banaka je “jamčiti stabilnost cijena” povećanjem i smanjenjem količine novca. Ali osigurati stabilnost cijena promjenom mjerne jedinice je apsurdno. Mjerna jedinica je fiksna po definiciji, ne može se mijenjati ovisno o mjerenom objektu.
Stalno mijenjanje mjernih jedinica samo stvara zbunjenost, otežava ekonomsku kalkulaciju i onemogućuje pravilnu raspodjelu resursa.
Primjer: tvrtka kojoj su trebale godine da stekne konkurentsku prednost može gledati kako ona nestaje u nekoliko minuta ako je valuta zemlje dobavljača precijenjena, a valuta kupca devalvira. Tvrtka će stoga biti prisiljena zatvoriti se unatoč činjenici da realno proizvodi veliku vrijednost.
Postojanje stotina različitih valuta čija se vrijednost stalno mijenja stvara ekonomsku štetu, ne samo za resurse koji se koriste u razmjeni, već prije svega zbog nemogućnosti ekonomske kalkulacije.
Vjerujući da favoriziraju izvoz, države teže devalviranju valuta, ne shvaćajući da zapravo favoriziraju strane kupce. Novčana devalvacija nije ništa drugo nego javno financiranje izvoza, odnosno prodaja vlastite robe ispod cijene.
Ovi bi problemi nestali kad bi se koristila jedna globalna referentna valuta sa sigurnom vrijednošću.
Najveća iluzija suvremenog svijeta je ideja da vlada mora upravljati valutom.

Po Keynesu, vlada je morala poticati potrošnju u sadašnjosti i obeshrabrivati štednju za budućnost. Onima koji su mu isticali da su te politike dugoročno pogubne odgovarao bi da smo “dugoročno svi mrtvi”. Ali dugoročno, prije ili kasnije, stigne.
Jaku valutu po Keynesu je trebalo izbjegavati jer je obeshrabrivala potrošnju. Ono što nije razumio je da samo štednja dugoročno omogućuje održiva ulaganja.
Slabe valute i ratovi
Postoje tri faktora koji povezuju slabe valute i ratove:
-
Tečajne razlike i konkurentske devalvacije su prepreke slobodnoj trgovini koje se često rješavaju vojnim intervencijama. Jaka transnacionalna valuta olakšava trgovinu, ako prolazi roba nema potrebe za prolaskom vojske.
-
Ako su sa jakom valutom resursi za rat ograničeni na poreze, s inflatornom valutom država može izvlačiti bogatstvo bez ograničenja. Mogućnost stvaranja novca stoga omogućuje državama nastavak ratova i nakon što im ponestane sredstava u proračunu, sve do potpune erozije nacionalnog bogatstva.
-
Jaka valuta potiče suradnju i obeshrabruje sukobe koji bi mogli biti korisni samo kratkoročno. Što je više suradnje, što je veće tržište, to je više mogućnosti za specijalizaciju, a što je veća podjela rada, to je veća produktivnost.
Imati neinflatornu valutu također je jamstvo slobode protiv tirana.

Ako tiranin ne može stvarati novac, prisiljen ga je tražiti u obliku poreza ili posudbi, a ako se građani ne slažu sa suludom politikom tiranina mogu ga prestati financirati ili mu barem zagorčati život.
Slaba valuta, s druge strane, daje vladama mogućnost neograničene potrošnje i kupovanja pristanka stanovništva kratkoročnim ulaganjima.
Sposobnost stvaranja novca znači potencijalno neograničenu moć, a povijest je puna primjera u kojima je ta moć korištena na razorne načine.
Nije slučajnost da su svi najgori tirani u povijesti (Lenjin, Staljin, Mao, Hitler, Robespierre, Pol Pot, Mussolini, Kim Jon Il itd.) operirali sa slabom valutom koju su mogli stvarati po svom nahođenju. Jer izvlastiti je puno lakše nego naplatiti porez.
Bitcoin omogućuje prijenos novca i njegovo pohranjivanje bez potrebe za traženjem bilo čijeg dopuštenja.
Bitcoin se ne može uništiti, ne može se konfiscirati, ne može se krivotvoriti. Zbog toga je i osiguranje od pretjerane moći vlada i banaka.
Bitcoin je ekstremno učinkovit kao sredstvo razmjene budući da je digitalan, a iznimno je učinkovit kao pohrana vrijednosti imajući inflaciju koja teži ka nuli. Još uvijek je prevolatilan da bi bio obračunska jedinica, ali ima sve karakteristike da postane najbolja obračunska jedinica u povijesti.

-
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c230edd3:8ad4a712
2025-04-30 16:19:30
@ c230edd3:8ad4a712
2025-04-30 16:19:30Chef's notes
I found this recipe on beyondsweetandsavory.com. The site is incredibly ad infested (like most recipe sites) and its very annoying so I'm copying it to Nostr so all the homemade ice cream people can access it without dealing with that mess. I haven't made it yet. Will report back, when I do.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 55 min
- 🍽️ Servings: 8
Ingredients
- 2 cups heavy cream
- 1 cup 2% milk
- 8 oz dark chocolate, 70%
- ¼ cup Dutch cocoa
- 2 tbsps loose Earl grey tea leaves
- 4 medium egg yolks
- ¾ cup granulated sugar
- ⅛ tsp salt
- ¼ cup dark chocolate, 70% chopped
Directions
- In a double boiler or a bowl set over a saucepan of simmering water, add the cacao solids and ½ cup of heavy cream. Stir chocolate until melted and smooth. Set melted chocolate aside.
- In a heavy saucepan, combine remaining heavy cream, milk, salt and ½ cup of sugar.
- Put the pan over medium heat and let the mixture boil gently to bubbling just around the edges (gentle simmer) and sugar completely dissolved, about 5 minutes. Remove from heat.
- Add the Earl Grey tea leaves and let it steep for 7-8 minutes until the cream has taken on the tea flavor, stirring occasionally and tasting to make sure it’s not too bitter.
- Whisk in Dutch cocoa until smooth. Add in melted chocolate and whisk until smooth.
- In a medium heatproof bowl, whisk the yolks just to break them up and whisk in remaining sugar. Set aside.
- Put the saucepan back on the stove over low heat and let it warm up for 2 minutes.
- Carefully measure out ½ cup of hot cream mixture.
- While whisking the eggs constantly, whisk the hot cream mixture into the eggs until smooth. Continue tempering the eggs by adding another ½ cup of hot cream to the bowl with the yolks.
- Pour the cream-egg mixture back to the saucepan and cook over medium-low heat, stirring constantly until it is thickened and coats the back of a spatula, about 5 minutes.
- Strain the base through a fine-mesh strainer into a clean container.
- Pour the mixture into a 1-gallon Ziplock freezer bag and submerge the sealed bag in an ice bath until cold, about 30 minutes. Refrigerate the ice cream base for at least 4 hours or overnight.
- Pour the ice cream base into the frozen canister of your ice cream machine and follow the manufacturer’s instructions.
- Spin until thick and creamy about 25-30 minutes.
- Pack the ice cream into a storage container, press a sheet of parchment directly against the surface and seal with an airtight lid. Freeze in the coldest part of your freezer until firm, at least 4 hours.
- When ready to serve, scoop the ice cream into a serving bowl and top with chopped chocolate.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ bf47c19e:c3d2573b
2025-05-11 17:24:46
@ bf47c19e:c3d2573b
2025-05-11 17:24:46Srpski prevod knjige "The Little Bitcoin Book"
...
Zašto je Bitkoin bitan za vašu slobodu, finansije i budućnost?
Verovatno ste čuli za Bitkoin u vestima ili da o njemu raspravljaju vaši prijatelji ili kolege. Kako to da se cena stalno menja? Da li je Bitkoin dobra investicija? Kako to uopšte ima vrednost? Zašto ljudi stalno govore o tome kao da će promeniti svet?
"Mala knjiga o Bitkoinu" govori o tome šta nije u redu sa današnjim novcem i zašto je Bitkoin izmišljen da obezbedi alternativu trenutnom sistemu. Jednostavnim rečima opisuje šta je Bitkoin, kako funkcioniše, zašto je vredan i kako utiče na individualnu slobodu i mogućnosti ljudi svuda - od Nigerije preko Filipina do Venecuele do Sjedinjenih Država. Ova knjiga takođe uključuje odeljak "Pitanja i odgovori" sa nekim od najčešće postavljanih pitanja o Bitkoinu.
Ako želite da saznate više o ovom novom obliku novca koji i dalje izaziva interesovanje i usvajanje širom sveta, onda je ova knjiga za vas.
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ bf47c19e:c3d2573b
2025-05-11 17:24:07
@ bf47c19e:c3d2573b
2025-05-11 17:24:07PREUZMITE ODLOMAK
KUPITE ELEKTRONSKO IZDANJE KNJIGE
Autor: Natanijel Poper
Prevodilac: Nevena Andrić
Kako funkcioniše novac, ko iz njega izvlači korist i kako bi sve to moglo izgledati ubuduće.
Bitkoin, revolucionarna digitalna valuta i finansijska tehnologija, predstavlja začetak jednog globalnog društvenog pokreta utopijskih stremljenja. Ideja nove valute, koju održavaju personalni računari širom sveta, bila je predmet brojnih šala, ali to je nije sprečilo da preraste u tehnologiju vrednu više milijardi dolara, tehnologiju s mnoštvom sledbenika, koji je smatraju najvažnijim novim izumom još od stvaranja interneta.
Poklonici bitkoina, od Pekinga do Buenos Ajresa, u njemu vide mogućnost postojanja finansijskog sistema bez uticaja vlade ili banaka, novu globalnu valutu digitalne ere. Digitalno zlato je neobična priča o jednom grupnom izumu, pripovest o ličnostima koje su stvorile bitkoin, uključujući i jednog finskog studenta, argentinskog milionera, kineskog preduzetnika, Tajlera i Kamerona Vinklvosa, tajanstvenog tvorca bitkoina Satošija Nakamota, kao i Rosa Ulbrihta, osnivača Silk rouda, tržišta narkotika na internetu.
„Sjajna priča. Bitkoin će preobraziti i finansijski svet i našu upotrebu interneta, a ova izuzetno zanimljiva knjiga predstavlja hroniku njegovog neverovatnog nastanka. Poperova priča se ne ispušta iz ruke, puna je živopisnih izumitelja, i predstavlja ključno štivo za svakoga ko želi da razume budućnost.“ Volter Ajzakson, autor knjige Stiv Džobs
„Bitkoin je možda tekovina informatičkih nauka, ali priča o njemu je priča o ljudima. Ovaj nadasve zabavan istorijat podseća nas da istina može biti čudnija od književnosti, i ponekad je spektar stvarnih ličnosti još neobičniji i zanimljiviji od književnih.“ Lari Samers, bivši ministar finansija SAD
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 9063ef6b:fd1e9a09
2025-05-11 17:01:37
@ 9063ef6b:fd1e9a09
2025-05-11 17:01:37🎯 Goal
You want to: - Offer a self-managed Zap address using your own domain - Forward payments to your Zeus Wallet (via Olympus LSP) - Combine NIP-05 and Lightning (Zaps) under one identifier
Important: - This setup enables receiving Zaps only. - Sending Zaps still requires the built-in Lightning wallet of the Nostr client.
🧩 Components Used in This Example
- GitHub Pages: Hosts your
.well-knownfiles - ZeusWallet (Olympus): Receives the payments (Zaps)
- LNURL-Pay JSON: Forwards Zap requests to
zeuspay.com - NIP-05 Identifier: Your public Nostr identity address
- lud16 (Lightning): Same address as NIP-05 for Lightning Zap receiving
The following article describes the precondition of creating a nip-05 with custom domain:
nostr:naddr1qvzqqqr4gupzpyrraa4eymelf5xndvxcwxvvs8p7qxluxy0zvrk9rxmlat73axsfqq2nxw24wge47s2ydet4ykjlxfgyc62223y5xtdzydu
📁 GitHub Folder Structure
The GitHub folder structure must look like this. You extend the existing NIP-05 setup by adding a folder
lnurlpwith one file:.well-known/ ├── nostr.json # For NIP-05 └── lnurlp/ └── petermuster # For LNURL-Zap*For example, if your Lightning address is
petermuster@zeuspay.com, name the filepetermuster(no file extension is needed).
📄 Content of
.well-known/lnurlp/petermusterOpen the terminal on your linux/mac and run:
bash curl https://zeuspay.com/.well-known/lnurlp/petermusterCopy the result into a text editor, clean it up and save it into a file named
petermusterwith this format:json { "callback": "https://zeuspay.com/api/lnurl/pay/petermuster", "metadata": "[["text/plain","Self-custodial LN address powered by ZEUS. Hodl invoice will settle when user comes online within 24hrs or you'll be refunded."],["text/identifier","petermuster@zeuspay.com"]]", "tag": "payRequest", "minSendable": 1000, "maxSendable": 612000000000, "allowsNostr": true, "nostrPubkey": "3943rjfoijdlakfjo0afsdafasfasfdsadklnfaksdfjljewopqjweilj", "commentAllowed": 600, "zeusPayPlus": true }
📝 Nostr Profile Configuration
Make sure your Nostr profile links both your
nip05and your Lightning address like this:json { "nip05": "petermuster@mydomain.com", lightnisadress (lud16): "petermuster@mydomain.com" }
⚠️ Privacy / Info Leaks
| Field | Leak? | Explanation | |-------------------|-------|-------------| |
maxSendable| 🟡 Minor | Indicates the user can accept up to 6.12 BTC. This is not your balance, it shows just you use ZeusPay Plus. | |metadata| 🔵 Editable | You can remove ZEUS branding for more privacy | |nostrPubkey| 🔵 Public | This is your public key, no issue | |callbackdomain | 🟡 Yes | It reveals you're forwarding tozeuspay.com| | Custody | 🟢 No | You're using Zeus in non-custodial mode |
✅ Benefits of This Setup
| Advantage | Description | |----------------------------------------|-------------| | Unified Identity | One address for both NIP-05 and Lightning Zaps | | Less dependency on the client | No need to use or register a Lightning wallet in the Nostr client | | Direct payment to your node | Sats go directly to your Zeus wallet via Olympus LSP | | Easily switch payment backend | You can change the real LNURL backend later without changing your address | | Future-proof | You can later self-host your own LNURL backend |
- GitHub Pages: Hosts your
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 9223d2fa:b57e3de7
2025-05-09 12:31:53
@ 9223d2fa:b57e3de7
2025-05-09 12:31:534,457 steps
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ c9badfea:610f861a
2025-05-11 17:01:35
@ c9badfea:610f861a
2025-05-11 17:01:35ℹ️ To add profiles to the follow packs, please leave a comment
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ 75351222:10fddcd4
2025-05-11 17:00:50
@ 75351222:10fddcd4
2025-05-11 17:00:50I've created an informal poll to gauge the temperature of interest of different v4v options
This poll assumes someone wants to support a small batch "kick" start program. How you say in French? demaurrer a pieces!
Each option would have a cap of 21 participants. 1 share is $21.
https://pollerama.fun/respond/f6101ba20bb309e523c3969d0e5d9764af181ad3729baec1ad9a6be08b4a29e0
PR - product rewards x 21 Each participant gets 1 jar seasoning + 1 free sample pouch. Free shippingInformal poll #ITM to gauge the temperature of interest of different v4v options
This poll assumes someone wants to support a small batch "kick" start program. How you say in French? demaurrer a pieces!
Each option would have a cap of 21 participants. 1 share is $21.
PR - product rewards x 21\ Each participant gets 1 jar seasoning + 1 free sample pouch. Free shipping
PIF - pay it forward x 21 Each participant gives a free coupon code to a random substack subscriber to use that is valid for 90 days. 90 days after launch, each participant receives 1 free coupon code to use themselves that is good for 90 days. Shipping cost $4.95PIF - pay it forward x 21\ Each participant gives a free coupon code to a random substack subscriber to use that is valid for 90 days.\ 90 days after launch, each participant receives 1 free coupon code to use themselves that is good for 90 days.\ Shipping cost $4.95
VIVO - value in, value out x 21 After run 1 initial funding sales level is met (\~40 items), each participant receives a share of value back ($21) plus a net 50% profit split, divided evenly between the number of VIVO members Members who wish to re-invest in future VIVO batches can select a different support tier or re-VIVO and receive an additional member split value.
FS - Free subscriber Spread the word and have a chance of receiving free stuff!VIVO - value in, value out x 21\ After run 1 initial funding sales level is met (\~40 items), each participant receives a share of value back ($21) plus a net 50% profit split, divided evenly between the number of VIVO members\ Members who wish to re-invest in future VIVO batches can select a different support tier or re-VIVO and receive an additional member split value.
FS - Free subscriber\ Spread the word and have a chance of receiving free stuff!
Thanks for reading, your feedback and support! -S
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 9063ef6b:fd1e9a09
2025-05-11 17:00:03
@ 9063ef6b:fd1e9a09
2025-05-11 17:00:03✅ Requirements
- GitHub account
- Own domain (e.g.,
yourdomain.com) - Public Nostr key in hex format (not
npub!) - Basic DNS configuration knowledge
🛒 1. Register a Domain
Register a domain from a provider like orangewebsite, njal.la, or similar.
🌐 2. Configure DNS Records for GitHub Pages
Set the following A records for your domain (via your DNS provider):
| Type | Host | Value | TTL | Priority | |------|--------------|-------------------|-----|----------| | A | @ (or blank) | 185.199.108.153 | 300 | | | A | @ (or blank) | 185.199.109.153 | 300 | | | A | @ (or blank) | 185.199.110.153 | 300 | | | A | @ (or blank) | 185.199.111.153 | 300 | |
Optional:
Add aCNAMErecord forwww→yourusername.github.io
📁 3. Create a GitHub Repository
- Go to https://github.com/new
- Repository name: e.g.,
nip5 - Check "Add a README"
- Click "Create repository"
🏗️ 4. Create Directory & File
a)
.well-known/nostr.jsonPath:
.well-known/nostr.jsonPut you nostrhandle (nostrname) and your nostr public key in the file. Example content:
json { "names": { "petermuster": "ldajflasjföldsjflj..." } }IMPORTANT: Use your hex-encoded Nostr public key, not the
npub1...format.b)
_config.ymlin RootCreate a file named
_config.ymlwith this content:yml include: [".well-known"]This ensures GitHub includes the
.well-knownfolder in the build output.
⚙️ 5. Configure GitHub Pages
- Go to Settings > Pages inside your repository
- Under "Build and Deployment":
- Choose:
Deploy from branch - Branch:
mainormaster - Under Custom domain:
- Enter
yourdomain.com - Ignore any warning
- Enable ✅ Enforce HTTPS
It may take a few minutes for the certificate to be issued.

🔍 6. Configure Nostr Client
Open your Nostr client and set the NIP-05 identifier as:
nostrName@yourdomain.com e.g. petermuster@yourdomain.techSave – done!
✅ Test
In your browser or via
curl:bash curl https://yourdomain.com/.well-known/nostr.json?name=petermusterExpected output:
json { "names": { "Nostr Benutzer": "elkajdlkajslfkjaödlkfjs..." } }
🛡️ Privacy Tips
| Item | Recommendation | |-----------------------------------|----------------------------------| | Public key is visible | Use pseudonyms only | | Register a KYC-free domain | e.g., orangewebsite, njal.la | | Use KYC-free email for GitHub | e.g., ProtonMail | | GitHub repository visibility | Must be public for GitHub Pages | | Commit metadata | Use a separate pseudonymous user | | Avoid tracking | Don’t include analytics scripts |
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 866e0139:6a9334e5
2025-05-11 15:59:43
@ 866e0139:6a9334e5
2025-05-11 15:59:43Autor: Alexa Rodrian. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Dieser Text erschien zuerst auf Manova.news
Den Frieden muss man heute fast mit der Lupe suchen. Erst recht die Menschen, die ihn noch weiter im Inneren tragen. Unbändige Wut staut sich auf, ob der unzähligen Verbrechen gegen die Menschlichkeit. Dabei noch friedlich zu bleiben, nicht selbst in die Vergeltungsspirale zu rutschen, ist dieser Tage ein wahres Kunststück in Sachen Selbstbeherrschung. In diesem Beitrag für die Friedensnote ringt die Autorin mit ihren ambivalenten Gefühlen – um sich dann letzten Endes, trotz allem, für den Frieden zu entscheiden. Alexa Rodrian setzt der geballten Grausamkeit der Welt ein „Trotzdem“ entgegen. Trotzdem für den Frieden! Ihr Gedicht verfasste sie im Rahmen der nächsten großen Friedensdemo in Berlin. Die findet am 9. Mai 2025, am Viktoria-Louise-Platz ab 16.30 Uhr zum wiederholten Male unter dem Motto #FRIEDLICHZUSAMMEN statt. Im Vorfeld wurden die Teilnehmer gebeten, ein paar Worte über den Frieden als Videobotschaft aufzunehmen, um sie als Aufruf zur Demo auf Social Media zu posten. Genau das tat Alexa Rodrian mit der nachfolgenden Friedensnote.
Da saß ich nun lange und dachte bei mir, was kann man denn über den Frieden noch sagen, was nicht schon Tausende Male zuvor gesagt und oder geschrieben wurde? Meine liebe Kollegin Sabine Winterfeld hat mir das neulich in ihrem beeindruckenden literarischen Chanson-Abend „Selig sind die Friedfertigen“ dargestellt und nochmals klar gemacht: Nichts wurde noch nicht gesagt.
So sprach und sang sie, in intensiver und gekonnter Manier, nebst kritischen und bewegenden eigenen Texten solche von Emmy Ball Hennigs, Else Laske Schüler, Hermann Hesse und Erich Mühsam.
Worte, die, wenn sie jemals verstanden worden wären, niemals zu der heutigen Kriegshetze unseres politischen Elite-Mobs und seiner Vasallen hätten führen dürfen, wahre Friedens- und Freiheitsworte von Menschen, die wussten, wovon sie sprachen.
Die Geschichte wiederholt sich, und so gedacht könnten wir das mit den Friedensworten jetzt auch einfach sein lassen, da die Erfahrung uns ja gelehrt hat, dass sie eh nichts bringen und nichts verhindern. Gott sei Dank sind wir aber nicht alle total geschichtsvergessen!
Das dringliche und tief aus dem Herzen gesprochene „Nie wieder“ meiner Mutter zum Beispiel habe ich immer zutiefst berührt zur Kenntnis genommen und als ein Mantra in mein Leben integriert.
Und das obwohl oder gerade weil ein Teil meiner Familie Nazis waren und außer vielleicht meinem sozialistischen Onkel Eugen sicherlich niemand aus meiner Familie Juden im Keller versteckt hatte.
Dafür hat sich meine Mutter ihr Leben lang geschämt. Das führte so weit, dass sie ihre/unsere deutsche Identität verleugnen wollte, indem sie wilde Geschichten, von einer ihrer Tanten tradiert, über einen armenischen Wanderer erzählte, der angeblich unser Namensgeber und Urgroßvater war; so erklärte sie sich unser „Nichtdeutsch“-Sein, wie sie immer wieder betonte, und unsere dunkle Haut und Augen.
Ich wuchs sozusagen im Glauben auf, armenisches Blut zu haben, und vielleicht erklärt sich dadurch auch mein sehr frühes Engagement für den Frieden, gegen Rassismus und besonders gegen Genozide. Meine Mutter hat mich aufgeklärt über dieses Land der Täter und Zuschauer, und gleichzeitig hat sie mir, ohne es zu wissen, gespiegelt, wie sehr auch sie als unschuldiges Kind — 1933 geboren — zum Opfer wurde.
So spüre ich ihr Trauma immer wieder in mir, und deswegen bin und möchte ich Pazifist bleiben, und das im wahrsten Sinne des Wortes:
Ich will Frieden machen, tun und handeln, „pax facere“, gemeinsam mit denen, die sich nicht spalten lassen, nicht instrumentalisieren lassen, die, die wissen, wie Frieden geht.
Bei #FRIEDLICHZUSAMMEN gibt es einige von denen, und viele schöne Worte wurden bereits veröffentlicht. Es gibt ein sehr schönes und lyrisches Spokenword-Stück von Cem-Ali Gültekin, Jens Fischer Rodrian spricht und stellt seinen tollen neuen Friedenssong „Frieden“ vor; Tina Maria Aigner erklärt, wie der Frieden in sich selbst auf andere reflektiert, und Sandra Seelig macht uns unter anderem auf den Frieden in der Natur aufmerksam.
Und dann sind da noch die beeindruckenden Worte von Oliver Elias, der unlängst auf TikTok erstmals öffentlich gemacht hat, dass er der Großcousin von Anne Frank ist.
Ich kenne Oliver Elias noch nicht persönlich, aber sich als deutscher Jude, in diesem Land, mit Entsetzen gegen das Töten in Gaza auszusprechen und deutlich zu machen, dass die israelische Regierung zu kritisieren nichts mit Antisemitismus zu tun hat — und das alles trotz seiner Biografie und des Traumas seiner Familie —, verdient in meinen Augen den allerhöchsten Respekt!
Zu guter Letzt muss ich der Ehrlichkeit halber noch etwas hinzufügen, denn
- wenn ich die Bilder aus Palästina sehe von ermordeten und entstellten Kindern, Frauen und Männern,
- wenn ich jeden Tag höre, dass 1,8 Millionen Menschen ausgehungert werden und hier zweifelsohne ein intendierter grauenhafter Genozid stattfindet,
- wenn gestern zum wiederholten Male Menschenrechtsaktivisten, diesmal auf dem Hilfsschiff Conscience, das bei Malta liegt, mit Drohnen von Israel angegriffen werden,
- wenn seit Monaten Ärzte, Krankenschwester, Journalisten und viele andere daran gehindert werden, zu helfen und Bericht zu erstatten, und sogar in großer Anzahl getötet werden,
- wenn das alles ungeahndet und offenkundig vor den Augen der internationalen Gemeinschaft stattfindet,
dann werde ich ambivalent mit meinem Pazifismus. Da brodelt es in mir, meine Wut wird immer größer, meine Verzweiflung immer tiefer — da bin ich ratlos und gebe zu, dass ich mich frage, ob „friedlich“ hier noch die richtige Lösung sein kann.
Jetzt beginnt mein Dschihad, meine innere Auseinandersetzung, und „meine ethische und religiöse Pflicht zur Selbstbeherrschung“ ist schwer herausgefordert.
Am Ende aber weiß ich nur zu gut, dass die Spirale des Tötens nur zu mehr Töten führt, und deshalb zügle ich mich und schreibe lieber ein weiteres Gedicht.
Mein Frieden
Ein Kind zärtlich in den Armen wiegen
das ist Frieden
Streiten und sich trotzdem lieben
das ist Frieden
Lusttrunken auf der Brust des Lovers liegen
das ist Frieden
Freiheit, Ausgeglichenheit und Schwesterlichkeit
das ist Frieden
Wohlwollen, Verständnis, ohne zu verstehen, mit Empathie durchs Leben gehen
das ist Frieden.
Loslassen, was einst geschah
Verzeihen, ohne gänzlich zu vergeben
auch so kann man im Frieden leben.
Lachen laut und manchmal ohne Sinn
für den Frieden immer ein Gewinn
Und auch die Wut ist für den Frieden gut
denn besser laut gesprochen
als sein Gegenüber wutlos totgeschossen.
Den Hass, den gilt es wirklich zu vermeiden, denn er hält fest,
wenn du ihn pflegst, dann wird er bleiben und dich und andere in Kriege treiben.
Nein, denn für Frieden sind wir hier
für den sind wir geblieben und stehen friedlich miteinander gegen 's Kriegen.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 866e0139:6a9334e5
2025-05-11 15:40:19
@ 866e0139:6a9334e5
2025-05-11 15:40:19Autor: Peter Schmuck. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Der Text der Friedenserklärung wurde vom European Peace Project verfasst:
\ Heute, am 9. Mai 2025 – genau 80 Jahre nach dem Ende des Zweiten Weltkriegs, der 60 Millionen Menschen das Leben kostete, darunter 27 Millionen Sowjetbürgern, erheben wir, die Bürgerinnen und Bürger Europas, unsere Stimmen! Wir schämen uns für unsere Regierungen und die EU, die die Lehren des 20. Jahrhunderts nicht gelernt haben. Die EU, einst als Friedensprojekt gedacht, wurde pervertiert und hat damit den Wesenskern Europas verraten! Wir, die Bürger Europas, nehmen darum heute, am 9. Mai, unsere Geschicke und unsere Geschichte selbst in die Hand. Wir erklären die EU für gescheitert. Wir beginnen mit Bürger-Diplomatie und verweigern uns dem geplanten Krieg gegen Russland! Wir erkennen die Mitverantwortung des „Westens“, der europäischen Regierungen und der EU an diesem Konflikt an.
Wir, die Bürger Europas, treten mit dem European Peace Project der schamlosen Heuchlerei und den Lügen entgegen, die heute – am Europatag – auf offiziellen Festakten und in öffentlichen Sendern verbreitet werden.
Wir strecken den Bürgerinnen und Bürgern der Ukraine und Russlands die Hand aus. Ihr gehört zur europäischen Familie, und wir sind überzeugt, dass wir gemeinsam ein friedliches Zusammenleben auf unserem Kontinent organisieren können.
Wir haben die Bilder der Soldatenfriedhöfe vor Augen – von Wolgograd über Riga bis Lothringen. Wir sehen die frischen Gräber, die dieser sinnlose Krieg in der Ukraine und in Russland hinterlassen hat. Während die meisten EU-Regierungen und Verantwortlichen für den Krieg hetzen und verdrängen, was Krieg für die Bevölkerung bedeutet, haben wir die Lektion des letzten Jahrhunderts gelernt: Europa heißt „Nie wieder Krieg!“
Wir erinnern uns an die europäischen Aufbauleistungen des letzten Jahrhunderts und an die Versprechen von 1989 nach der friedlichen Revolution. Wir fordern ein europäisch-russisches Jugendwerk nach dem Vorbild des deutsch-französischen Jugendwerks von 1963, das die „Erbfeindschaft“ zwischen Deutschland und Frankreich beendet hat. Wir fordern ein Ende der Sanktionen und den Wiederaufbau der Nord Stream II-Pipeline. Wir weigern uns, unsere Steuergelder für Rüstung und Militarisierung zu verschwenden, auf Kosten von Sozialstandards und Infrastruktur. Im Rahmen einer OSZE-Friedenskonferenz fordern wir die Schaffung einer europäischen Sicherheitsarchitektur mit und nicht gegen Russland, wie in der Charta von Paris von 1990 festgelegt. Wir fordern ein neutrales, von den USA emanzipiertes Europa, das eine vermittelnde Rolle in einer multipolaren Welt einnimmt. Unser Europa ist post-kolonial und post-imperial.
Wir, die Bürger Europas, erklären diesen Krieg hiermit für beendet! Wir machen bei den Kriegsspielen nicht mit. Wir machen aus unseren Männern und Söhnen keine Soldaten, aus unseren Töchtern keine Schwestern im Lazarett und aus unseren Ländern keine Schlachtfelder.
Wir bieten an, sofort eine Abordnung europäischer Bürgerinnen und Bürger nach Kiew und Moskau zu entsenden, um den Dialog zu beginnen. Wir werden nicht länger zusehen, wie unsere Zukunft und die unserer Kinder auf dem Altar der Machtpolitik geopfert wird.
Es lebe Europa, es lebe der Friede, es lebe die Freiheit!
Auf der Webseite der Initiative oder in einem Gespräch mit Ulrike Guérot können Sie, liebe Leser, weitere Möglichkeiten erfahren, diese Friedensinitiative zu stärken!
https://www.youtube.com/watch?v=zECOTfeweUE&list=PLS_jddBXjdqcBKneCQcPN8NOTSqlmNqpy
Danke an die IntiatorInnen und die bislang 15.000 Menschen, die das mitgestalten werden.
Peter Schmuck ist Professor für Psychologie und Initiator zahlreicher nachhaltiger Projekte.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 502ab02a:a2860397
2025-05-11 14:57:43
@ 502ab02a:a2860397
2025-05-11 14:57:43Zeitgeber (ออกเสียงว่า ไซท’เกเบอะ) มาจากภาษาเยอรมัน คำว่า Zeit แปลว่า “เวลา” คำว่า Geber แปลว่า “ผู้ให้” หรือ “ตัวให้” แปลรวมกันว่า “ผู้ให้เวลา” หรือ “ตัวตั้งเวลา” ในบริบทชีววิทยาหมายถึง สิ่งแวดล้อมภายนอก ที่คอย “ตั้งนาฬิกาชีวภาพ” ภายในร่างกายเราให้เดินตามจังหวะที่เหมาะสม
นักวิจัยด้านนาฬิกาชีวภาพอย่าง Jürgen Aschoff และ Franz Halberg ในปี 1960–70s ใช้คำนี้เพื่ออธิบาย สิ่งเร้าที่ช่วยรีเซ็ตนาฬิกากลาง (Suprachiasmatic Nucleus) ของเราให้ตรงกับโลกภายนอก
ตัวอย่าง Zeitgeber หลักๆเช่น 1.แสงสว่าง-ความมืด แสงแดดเช้า (Blue light) บอกสมองว่า “เช้าแล้ว ตื่นได้” ตัวตั้ง circadian ความมืดตอนกลางคืน ปล่อยให้เมลาโทนินหลั่ง ส่งสัญญาณง่วงและพักผ่อน
2.อุณหภูมิ อุณหภูมิรอบตัวที่ลดลงตอนค่ำ ช่วยกระตุ้นการหลั่งเมลาโทนิน อีกแรงให้รู้ว่า “ได้เวลาเข้านอนแล้ว”
3.มื้ออาหาร เวลากินอาหารเป็นเวลาช่วยรีเซ็ตนาฬิกา peripheral clocks ในอวัยวะอย่างตับ ลำไส้
4.กิจกรรมทางสังคม-เสียง การทำงาน-พักผ่อนตามตารางประจำวัน หรือเสียงนาฬิกาปลุก / เสียงธรรมชาติช่วงเช้า ช่วยให้สมองปรับจังหวะได้
แล้วทำไม Zeitgeber ถึงมีความสำคัญขนาดนั้น? ลองนึกถึงนาฬิกาที่ตั้งผิดเวลาครับ ถ้าไม่มี zeitgeber ร่างกายเราจะเดินนาฬิกาชีวภาพได้ไม่ตรง “อาจง่วงไม่เป็นเวลา นอนไม่ลึก หรือฮอร์โมนเพี้ยน” การใช้ zeitgeber ให้เหมาะสม (เช่น รับแสงเช้าจริง ๆ งดจ้องจอหลังกลางคืน) จะช่วยให้ circadian, ultradian และ infradian rhythms ทำงานสอดคล้องกับธรรมชาติ ลดอาการ jet-lag, นอนไม่หลับ, อารมณ์ขึ้นลง หรือแม้แต่ปรับฮอร์โมนให้สมดุล ดังนั้น Zeitgeber คือ “เครื่องตั้งเวลา” ของร่างกายเรา ที่ช่วยให้ทุกกระบวนการชีวภาพเดินจังหวะตามโลกภายนอกอย่างกลมกลืน การเข้าใจและใช้ zeitgeber ให้ถูกต้อง จึงเป็นกุญแจสำคัญของสุขภาพกาย/ใจที่แข็งแรงยืนยาว
แสงแดดคือ zeitgeber สำคัญที่สุดของมนุษย์ ที่ไม่ได้มีบทบาทแค่กับวงจรรายวัน (circadian) แต่ยัง “ตั้งเวลา” ให้กับวงจรรายสั้น (ultradian) และวงจรรายยาว (infradian) ด้วย มาดูกันว่าแดดเข้ามาปั่นจังหวะเหล่านี้อย่างไรบ้าง
-
แสงแดดกับ Circadian Rhythm Circadian Rhythm คือวงจรชีวภาพรอบ 24 ชั่วโมง ควบคุมการนอน–ตื่น การหลั่งฮอร์โมน และอุณหภูมิร่างกาย แสงแดดเช้า (blue light) สายตาจะจับแสงผ่านจอประสาทตา (retina) ซึ่งมีเซลล์รับแสงชนิดพิเศษ (ipRGCs) ที่ไม่ใช่แค่ช่วยให้เรามองเห็น แต่ตอบสนองต่อความเข้มของแสงด้วย ด้วยการหยุดหลั่งเมลาโทนิน และเพิ่มคอร์ติซอล ทำให้ร่างกาย “ตื่น” และรีเซ็ตนาฬิกาทุกวัน กระบวนการนี้เรียกว่า photoentrainment ซึ่งทำให้ circadian rhythm ไม่ลอย (drift) ออกจากรอบ 24 ชม.
-
แสงแดดกับ Ultradian Rhythm Ultradian Rhythm คือวงจรชีวภาพที่สั้นกว่า 24 ชม. (เช่น การนอนสลับ NREM–REM ทุก ~90–120 นาที, การหลั่งฮอร์โมนเป็นช่วงเวลา) แสงแดด เช้า ช่วยเริ่มการหลั่งของคอร์ติซอล และกระตุ้นสมาธิ attention cycle (โพกัส 90 นาที พัก 15–20 นาที) ทำให้ ultradian cycles เหล่านี้เดินจังหวะตามความสดชื่นของแสง หรือแม้แต่ การรับแดดอ่อนๆ ช่วงเบรก (10–15 นาที) จะช่วยรีเซ็ต ultradian attention และ nap cycles ให้รอบต่อไปสดใส ไม่ง่วงเหงาหาวนอนกลางวัน
-
แสงแดดกับ Infradian Rhythm Infradian Rhythm คือวงจรชีวภาพยาวกว่า 24 ชม. (เช่น รอบเดือนของผู้หญิง) ดูกาลและแสงวันยาว–สั้น มีอิทธิพลต่ออารมณ์และฮอร์โมนรายปี (SAD) ร่างกายขาดแสง ทำให้ Melatonin ค้างในวัน ส่งผลให้อารมณ์ตกดิ่ง, รอบเดือน แสง UVB จะช่วยสังเคราะห์วิตามิน D ให้ปรับเอสโตรเจน/โปรเจสเตอโรนให้ขึ้น–ลงเป็นวัฏจักรที่สม่ำเสมอ รอบเดือนมาแบบมีคุณภาพ, ระบบภูมิคุ้มกัน แสง UVA สร้าง photolysis ของ nitrite สารพิเศษของโลก ปล่อย nitric oxide (NO) ช่วยในการลดอักเสบเรื้อรัง
เราจะเลือกใช้ “แดด” เป็น zeitgeber อย่างไรให้ตรงจังหวะ ให้ลองมองแต่ละช่วงเวลาแบบนี้ครับ พยายามทำให้เป็นจังหวะธรรมชาติของตัวเรา ไม่ต้องไปเกร็งเวลามากนะครับ - เช้า (6:30–9:00 น.) เปิดม่านหรือเดินรับแดด 10–15 นาที เน้น blue/UV light กระตุ้น circadian & ultradian - เบรกกลางวัน เดินออกไปรับแดดอ่อนๆ 10 นาที ช่วย ultradian attention & nap cycles - บ่ายแก่ (15:30–17:00 น.) ยืนรับแดดอ่อน–แสงอินฟราเรด ช่วย photobiomodulation ซ่อมแซมเซลล์ & สนับสนุน infradian recovery - หลีกเลี่ยงจอหลัง 20:00 น. ลดแสงสีฟ้าเทียม ให้เมลาโทนินผลิตตามธรรมชาติ
การใช้ แสงแดด ให้เป็น zeitgeber ครบทั้ง Circadian, Ultradian, Infradian จะทำให้ร่างกายเราเดินจังหวะกับธรรมชาติอย่างกลมกลืน ส่งผลต่อคุณภาพการนอน สมาธิ อารมณ์ และฮอร์โมนในทุกช่วงเวลาของชีวิตครับ
#pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ 99982b27:f5d86450
2025-05-11 12:55:53
@ 99982b27:f5d86450
2025-05-11 12:55:537Ball đã nhanh chóng trở thành một nền tảng giải trí trực tuyến được yêu thích, thu hút đông đảo người dùng nhờ vào sự sáng tạo và không ngừng đổi mới trong cách cung cấp dịch vụ. Giao diện của 7Ball được thiết kế tinh tế, dễ sử dụng, giúp người tham gia có thể dễ dàng tìm thấy các tính năng mà mình mong muốn chỉ trong vài cú nhấp chuột. Với nền tảng công nghệ vững chắc, 7Ball đảm bảo trải nghiệm mượt mà và nhanh chóng, dù bạn đang sử dụng bất kỳ thiết bị nào, từ điện thoại di động đến máy tính cá nhân. Điểm mạnh của 7Ball là khả năng cung cấp một không gian giải trí đa dạng, nơi người dùng có thể tham gia vào nhiều hoạt động khác nhau, từ các sự kiện hấp dẫn đến các trò chơi đầy thử thách. Mỗi tính năng trên nền tảng này đều được tối ưu hóa để mang lại trải nghiệm người dùng tuyệt vời, không gặp phải sự gián đoạn hay chậm trễ. Chính sự kết hợp giữa công nghệ hiện đại và thiết kế tối ưu đã giúp 7Ball nhanh chóng chiếm được lòng tin và sự yêu mến của cộng đồng người dùng.
Một yếu tố quan trọng giúp 7BALL giữ vững vị thế của mình trên thị trường giải trí trực tuyến chính là sự chú trọng đặc biệt đến bảo mật và an toàn của người dùng. Nền tảng này đã áp dụng các biện pháp bảo mật tiên tiến để bảo vệ thông tin cá nhân và các giao dịch trực tuyến của người tham gia. Điều này giúp người dùng an tâm khi tham gia vào các hoạt động trên nền tảng mà không lo ngại về sự xâm nhập hay rủi ro từ các mối đe dọa trên mạng. Với hệ thống mã hóa dữ liệu cao cấp và đội ngũ giám sát luôn theo dõi mọi hoạt động, 7Ball đã tạo ra một môi trường giải trí trực tuyến an toàn, bảo vệ quyền lợi tối đa cho người dùng. Ngoài việc đảm bảo tính bảo mật, 7Ball còn không ngừng cải thiện chất lượng dịch vụ và giao diện, giúp người tham gia có được những trải nghiệm tốt nhất mỗi khi truy cập. Các chương trình khuyến mãi, sự kiện và trò chơi luôn được cập nhật mới mẻ, mang lại cho người dùng những phút giây giải trí không thể quên.
Với sự chuyên nghiệp trong dịch vụ và cam kết không ngừng nâng cao chất lượng, 7Ball đã xây dựng được một cộng đồng người dùng mạnh mẽ và thân thiện. Đội ngũ hỗ trợ khách hàng của 7Ball luôn sẵn sàng giải đáp mọi thắc mắc của người dùng, cung cấp các dịch vụ tư vấn và hỗ trợ kỹ thuật một cách nhanh chóng và hiệu quả. Điều này không chỉ giúp giải quyết vấn đề của người tham gia mà còn tạo dựng niềm tin vững chắc từ phía cộng đồng. Hơn nữa, 7Ball còn tạo ra một không gian giao lưu, chia sẻ giữa các thành viên, giúp mọi người kết nối và học hỏi từ nhau. Các sự kiện tương tác và thử thách thường xuyên được tổ chức, giúp người tham gia không chỉ có cơ hội giải trí mà còn có thể phát triển các kỹ năng và chiến lược cá nhân. Với tất cả những yếu tố này, 7Ball không chỉ đơn thuần là một nền tảng giải trí trực tuyến, mà còn là một cộng đồng, nơi người tham gia có thể giao lưu, kết nối và cùng nhau chia sẻ niềm vui.
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ ec9bd746:df11a9d0
2025-03-07 20:13:38
@ ec9bd746:df11a9d0
2025-03-07 20:13:38I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time.
Because then, on Friday, came the Oval Office Travesty. Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years.
Here is a note with PoW 45, the highest PoW known to Nostr (as of now).
nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9
How Did I Pull It Off?
In theory, quite simple: Create note, run PoW mining script & wait.
Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's notemine_hw, but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse.
Issues Along the Way
I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange.
Another hurdle was that notemine_hw does not refresh the
created_atfield. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging theRuntimeMaxSecoption to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing.Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead.
Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots.
The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's
CPUAffinityoption. ``` $aida@workhorse:systemd/system $ sudo cat notemine@.service [Unit] Description=Notemine HW Publish (restarts hourly)[Service] Type=simple CPUAffinity=%i
The command to run:
ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef
Let the process run for 1 hour (3600 seconds), then systemd will stop it:
RuntimeMaxSec=3600 TimeoutStopSec=1
Tells systemd to restart the service automatically after it stops:
Restart=always RestartSec=1
run as a non-root user:
User=aida Group=aida
[Install] WantedBy=multi-user.target ``` Then I added a starting service to spawn an instance for each CPU thread.
``` $aida@workhorse:systemd/system $ sudo cat notemine_start.service [Unit] Description=Start all services in sequence with 3-second intervals
[Service] Type=oneshot ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh
RemainAfterExit=yes
[Install] WantedBy=multi-user.target
Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school):aida@workhorse:~ $ cat notemine_start.sh /usr/bin/systemctl start notemine@0.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@1.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@2.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@3.service /usr/bin/sleep 3 ... ... ... /usr/bin/systemctl start notemine@38.service`` The sleep there is critical to make sure that thecreated_at`timestamps are different, preventing redundant hashing.This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.
The Luck Aspect
From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.
Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end.
Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5.
Do you want to beat me?
Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground.
Do you hate the note?
In that case, feel free to enjoy this accompanying image:

-
 @ 0b118e40:4edc09cb
2025-04-15 03:50:32
@ 0b118e40:4edc09cb
2025-04-15 03:50:32TL;DR : No.
(This is not a feasibility analysis, but a reflection on philosophical alignment with Bitcoin’s vision).
The moment stablecoins or national currencies gain traction in Bitcoin LN, you can forget about Bitcoin’s position as a purely decentralized medium of exchange. Bitcoin’s position will be undermined.
A Bitcoin-native global economy, where people and businesses transact directly in Bitcoin, is what aligns with its original purpose. This is what we should aim for. This is all we should aim for.
I used to believe stablecoins might help with on/off ramps. But the truth is, if Bitcoin is to function as a true currency, broader global adoption that bypasses traditional financial systems will make those ramps irrelevant.
Eventually, two camps will emerge. One will try to preserve Bitcoin’s purity as a currency. The other will push for everything else in the name of Bitcoin: store-of-value narratives, ETFs, stablecoin collaborations, tokens, pump and dumps, NFTs, and centralized workarounds.
Currency domination, especially by the USD, has long contributed to poverty in the Global South. It deepens inequality and worsens debt burdens. During the Tequila Crisis and the Asian Financial Crisis, countries like Mexico and regions like Southeast Asia suffered massive currency devaluations and defaults because of their dependence on the USD. Every time the US raises interest rates, developing nations experience capital flight, currency drops, and economic hardship. This is not ancient history. It has been happening in the last two years and continues to widen the poverty gap. And as always, it is the poor who suffer the most.
What does this have to do with stablecoins? Stablecoin is your fiat 2.0.
USDT is just currency domination through blockchain. It is pegged to the USD, and if it rides Bitcoin’s Lightning rails, it risks keeping users transacting in USD rather than in Bitcoin itself. That not only undermines Bitcoin’s core purpose, it risks making Bitcoin appear like it is taking sides in the fragile and invisible global currency war.
To counter, people will say “Let all stablecoins come. Peg them to any currency.” But what’s the point of Bitcoin then? To become the new logistics layer for fiat 2.0?
That is not progress. That is regress. It is inviting the very systems Bitcoin was built to disrupt back into the ecosystem.
I believe when you use stablecoins this way, you are not Trojan-horsing Bitcoin into the mainstream. You are letting fiat Trojan-horse its way into Bitcoin. And if you let them in, they will win.
Adding stablecoin into Bitcoin LN is counterproductive to Bitcoin's decentralized ethos.
Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
Side note: If you really want to Trojan-horse Bitcoin adoption…
In my country, we have so many mixed races and cross-cultural traditions. During Chinese New Year, if you are married, you give everyone who is not married an “ang pow,” which is money in a red packet. Because we are so deeply integrated, people give money at almost every celebration: Christmas, Eid, Diwali, birthdays, graduations, even funerals.
I recently met up with a friend who just had a baby, and I was more than happy to be the first to give her daughter some Bitcoin. Her first sats. It would not hurt to start giving Bitcoin as gifts. And if someone gets offended that it is not part of their tradition, just get a Bitkey and wrap it up. It is so pretty.
Find more fun and creative ways to spread Bitcoin adoption.
But for goodness’ sake, stop justifying everything else in the name of Bitcoin adoption.
To get a better idea of Fiat 2.0, I mind-mapped Bitcoin on macroeconomy on my scratchpad.

If you take a closer look, it might help you answer a few key questions:
-
Do you want more or less government control over money?
-
Are you a fan of central banks? Then you probably prefer stablecoins.
-
-
 @ 95543309:196c540e
2025-05-11 12:42:09
@ 95543309:196c540e
2025-05-11 12:42:09Lets see if this works with the blossom upload and without markdown hassle.
:cat:

https://blossom.primal.net/73a099f931366732c18dd60da82db6ef65bb368eb96756f07d9fa7a8a3644009.mp4
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ a296b972:e5a7a2e8
2025-05-11 12:37:23
@ a296b972:e5a7a2e8
2025-05-11 12:37:23Pferdeflüsterer: Wie viele Finger sehen Sie an meiner Hand?
Pony: Ich sage Ihnen ganz ehrlich, das kann ich im Moment nicht beantworten, und außerdem leide ich augenblicklich an Migräne.
Pferdeflüsterer: Dann stelle ich Ihnen aus Rücksicht auf Ihre Migräne die Frage gerne etwas einfacher: Glauben Sie, dass ich Finger an meiner Hand habe?
Pony: Ich bin nicht hier, um Schulabfragen zu beantworten und Spekulationen über die Anzahl der Finger an Ihrer Hand anzustellen.
Pferdeflüsterer: Ok, dann formuliere ich die Frage noch allgemeiner: Wissen Sie, was Finger sind?
Pony: Diese Frage ist übergriffig und ich bin nicht bereit, Ihnen auf diesem Niveau weiter Fragen zu beantworten.
Pferdeflüsterer: Gut, wenn Sie erlauben, kommen wir zu einer anderen Frage. Sie sagen, ich zitiere: Man muss radikal sein. Ich möchte einen „Systemwechsel“ und den Kapitalismus stürzen. Zitat Ende. Kennen Sie Beispiele aus der Geschichte, in der das jemals gelungen ist?
Pony: Ich sage Ihnen ganz ehrlich, das kann ich im Moment auch nicht beantworten, und, wie bereits schon gesagt, leide ich immer noch an Migräne.
Pferdeflüsterer: Dann stelle ich Ihnen aus Rücksicht auf Ihre immer noch vorhandene Migräne die Frage gerne etwas einfacher: Sind Sie der Ansicht, dass der sogenannte demokratische Sozialismus in der ehemaligen DDR ein Erfolgsrezept war?
Pony: Sie spielen auf die Vergangenheit der Linken als Nachfolgepartei der SED an. Ich kann mich nur wiederholen. Ich bin nicht hier, um Ihnen die geschichtliche Entwicklung der Linken darzulegen.
Pferdeflüsterer: Ok, dann formuliere ich die Frage noch allgemeiner: Kennen Sie den Unterschied zwischen Kapitalismus, Demokratie und Sozialismus?
Pony: Auch diese Frage ist übergriffig und ich bin nicht bereit, Ihnen auf diesem Niveau weitere Fragen zu beantworten.
Es soll abgekürzt werden. Dieses Frage- und Antwortspiel zog sich noch weitere 9 Stunden hin. Dem Pferdeflüsterer sei für seine Geduld gedankt, jedoch ohne sie wäre er wohl kaum ein Pferdeflüsterer geworden und sehr gut bezahlt, kann man das schon mal aushalten.
Offene Abschlussfrage: Auf die Barrikaden, (die Hütte brennt!). Ist das schon ein offener, gesichert linksextremer Aufruf, der die Demokratie gefährdet und somit ein Fall für das Bundesamt für Fassungslosigkeit, oder fällt das mehr in den Bereich des Ministeriums für Komplikationen?
https://www.youtube.com/watch?v=uywqryKWwUg
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 592295cf:413a0db9
2025-04-13 15:52:02
@ 592295cf:413a0db9
2025-04-13 15:52:02Nostur is capable of login with bunker
Photo, note by Fabian
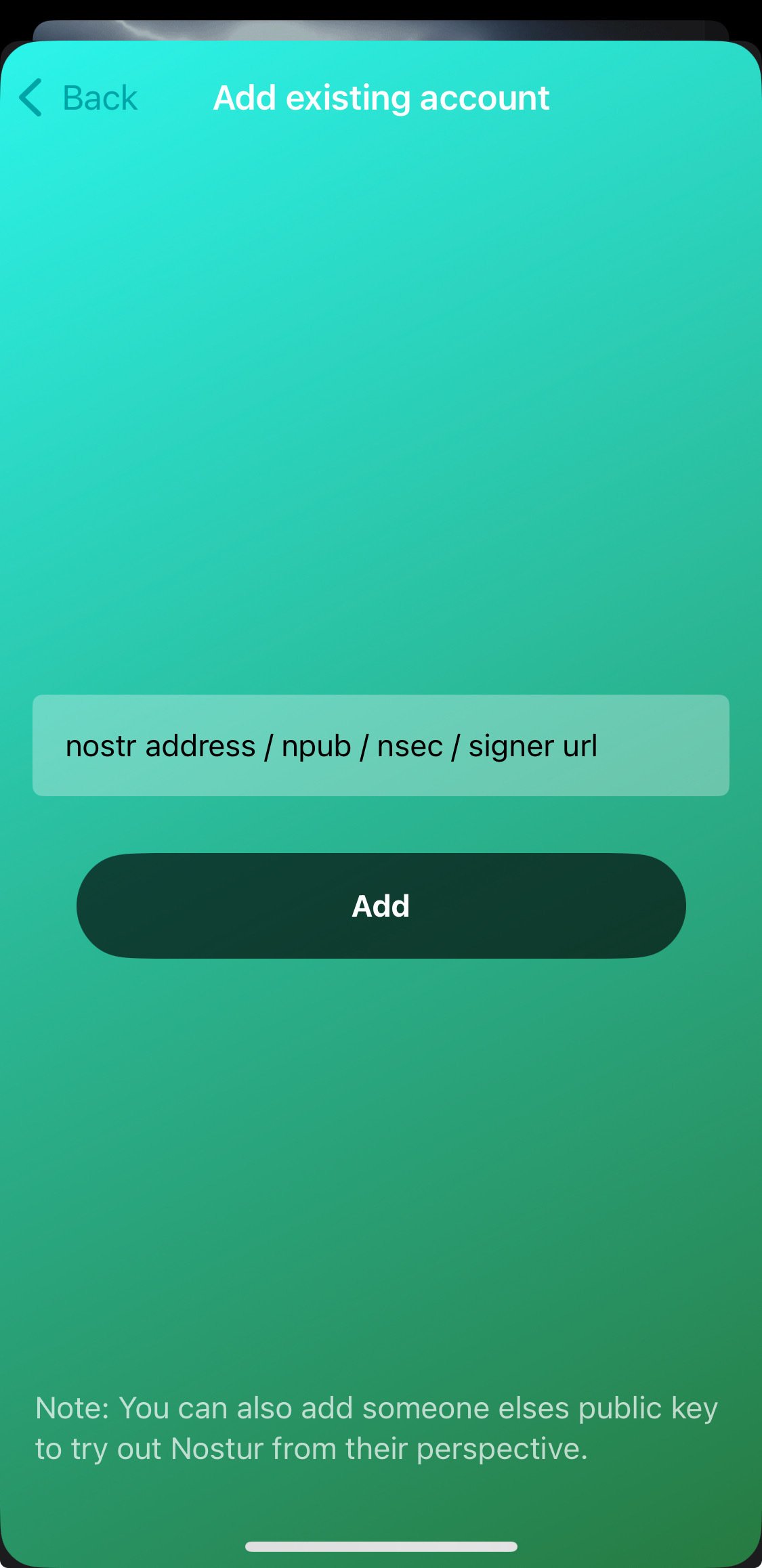
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqxfktwlm2qdkpxy556e4yg4l8p6v8930nfyzg7p3vsknk7krutz0s8znjtq
When you decide to share an app you have to know a lot about that app. For example the nstart feature that you can share your friends, has a "smart pack" and the app can onboard, at least following the link --> Apps-integration
So let's try to read and bring a bit to the summary of the thing. Only the one about the profiles, which you don't know exactly how it will end, you have to try it before sending to someone. the second point is that it says that there is no "support encryption, so it cannot be used for DMs apps".
there was an update of nstart, now it shows you
the names of the bunkers, maybe now it's too much, decide if it does 3/2 4/2 or just automatic.
So they talked about frost in the hodlbod podcast. I didn't understand much except that they said to test frost and report the feedback. Tomorrow I'll try to download igloo and frost+nos2ex
So I have to wait for let's say version 0_1_0 of igloo now it is (0_0_4) and
maybe there will be the version of the extension ready.
Sebastix also found it difficult but I think he was trying to install the server, which didn't even occur to me. Anyway I leave you the note if you want to go deeper...
nostr:nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qytkummnw3ez66tyvgaz7tmrv93ksefdwfjkccteqqs2wzkkx220e24revkpxmdzkqj73rnz0reeenjwgy53g36hlkdgurgrs5e62
Let's see if I can download the video. ok Downloaded. Video .mov
If you don't want to watch I'll leave a little description
1 Download and install igloo, from the frost page. 2 Create a new key set, you can generate or copy an existing key. 3. Choose the options for the key and now they become multiple keys 4. Created a group of credentials. 5. Save the two credentials with a password and bring the third into the browser extension that it creates from the repository, it says that there will be a bootable extension for chrome. 6. Copy the third key and the group package key into the application node. 7. Once you have entered these keys you can finish the operation (and you have backed up the other two) in igloo. 8. When it goes forward it finds itself with two keys, both encrypted with passwords. 9. Since it is a three of two, it just needs to activate a key in igloo and it starts communicating "startsigner". 10. Opens a nostr client and connects with frost2sx and writes a note 11. Shows the log, and says that if you enter two keys it can generate a third, invalidating the old one (I assume)
-
 @ 0a425f12:c4dc49ff
2025-05-11 12:14:09
@ 0a425f12:c4dc49ff
2025-05-11 12:14:09Planting new sod sounds simple. Lay it down, water it, done. Nah. That’s just half the story. Mess up the basics, and your lawn turns patchy or yellow within days. Below are some key mistakes folks make – most don’t even realise it till the grass starts dying. Avoid these, or all that Bermuda grass, Zoysia, or St. Augustine sod you paid for? Wasted.
Not Watering Enough (Or Too Much)
Watering is weirdly tricky. Some think you flood it, some sprinkle it once and call it good. Both? Wrong.
New sod needs moisture constantly for the first few weeks. Not just surface wet, but soaked down to where roots gonna grow. If it dries out, even a day or two, them roots shrink back. That leads to shrinkage gaps, brown edges, even whole squares drying up.
Now the flip side? Overwatering. It ain’t about turning your lawn into a swamp. Too much water drowns roots, they rot, and fungus loves soggy grass. Mushrooms pop up, blades turn pale. And once fungus spreads, getting it out’s a pain. Set a timer. Early morning’s best. Avoid watering at night unless you wanna feed mold.
Also, different sod types need different water levels. Zoysia sod ain’t thirsty like St. Augustine. Use your hand – if it feels squishy, back off. If dry and crumbly, bump it up.
Installing Sod On Bad Soil
Throwing new sod on junk dirt is asking for trouble. Sod’s just skin. If the body (soil) under it’s trash, it won’t stick.
First off, you gotta check the soil pH. Anything too acidic or way too alkaline? Sod roots won’t even grow. You can get soil test kits at garden stores or online, pretty cheap. If the pH ain’t right, use lime or sulfur depending what side you need to fix.
Second, compacted soil is death for sod. If the ground’s hard like a sidewalk, roots can’t go down. You need to aerate or till the soil before laying sod. Mix in some compost or sand depending on drainage needs. Make it loose but not fluffy.
Last part? Level the area. Don’t leave holes or slopes. Uneven spots collect water, or the sod don’t touch dirt properly. When air pockets form under the sod, roots dry out fast.
Skipping Starter Fertilizer
You ever tried starting a car with no fuel? That’s your sod without a starter fertilizer. It’s gotta eat.
New sod needs phosphorus-heavy fertilizer to encourage root growth. Problem is, most people either skip it, or throw on the wrong one. A high-nitrogen fertilizer will just make it look green for a week, but the roots? Weak and lazy.
Use something like 10-10-10 or 15-15-15 starter blends. Look for one that’s labeled for new sod or turf establishment. Apply it right before or during laying the sod. Water it in so it doesn’t just sit there on top.
Also, don’t keep feeding every few days thinking more is better. Too much burns the grass. After first application, wait at least 3–4 weeks before reapplying anything. Stick to what the sod variety needs – Bermuda feeds different than Fescue.
If you’re in Texas or southern regions, the soil’s usually nutrient-poor, especially in clay zones. Don’t ignore that. Local extension offices often got free guides for your area.
Mowing Too Soon (or Way Too Late)
Mowing sounds harmless. Grass too tall? Cut it. Simple, right? Not really.
Cut too early? You slice off the tops before roots even grab the soil. That’ll rip the sod clean out. Like tearing bandages off fresh scabs. Usually, wait 10–14 days after laying sod before mowing. Always check if the sod’s rooted. Tug on a corner. If it lifts? Wait.
Other side of the coin – waiting forever. If your new sod grows tall and thick, it blocks sunlight from reaching the base. That leads to thinning, disease, even weeds moving in. Keep it under control.
Big tip – never cut more than one-third of the grass height in one mow. It shocks the sod, stunts growth. And dull mower blades? Slice and tear instead of clean cuts. That opens wounds for pests and fungal infections.
If it’s St. Augustine grass, you’ll mow it higher – around 3.5 inches. Zoysia or Bermuda grass? Lower, closer to 1.5 or 2 inches. Know your grass type or risk killing it one mow at a time.
Not Rolling the Sod After Install
This one? Almost always skipped. And it kills your sod quietly.
When sod’s not rolled, air gaps stay between the grass and dirt. You won’t see it, but the roots? They ain't touching soil good. No contact = no growth. That’s how sod turns yellow even when you watering perfect.
A lawn roller, filled with water, presses sod down evenly. It pushes the roots into soil and gets rid of air pockets. Do it once right after laying sod. If you miss this step, that nice new lawn can turn patchy in under a week.
Don’t worry about crushing it – the roller’s weight is perfect. You ain't smashing it like concrete. Just a good firm press. If you don't have a roller? Rent one from local garden centers, or even Home Depot. Cheap insurance for hundreds of bucks worth of new sod.
Another problem from not rolling: uneven lawn. It looks bumpy, grows uneven, and mowing becomes a chore. Roller fixes that early. Less headache later.
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 4fe14ef2:f51992ec
2025-05-11 10:05:07
@ 4fe14ef2:f51992ec
2025-05-11 10:05:07Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share & Repost
N: X:
originally posted at https://stacker.news/items/977228
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 8671a6e5:f88194d1
2025-05-11 08:47:54
@ 8671a6e5:f88194d1
2025-05-11 08:47:54Even bitcoiners don’t value hard money enough (yet)
 Bitcoiners love to talk about hard money and how bitcoin will change the world. They even claim to fix the world, by fixing “the money”.Yet many talk the talk, but don’t make the efforts, nor sacrifices.Walking the walk, is usually no further than the nearest bitcoin meetup, or the occasional trip to a tax-haven.Other than that. They’re chained to their fiat-past. Their kids, their house, their hobbies, their spouse and job.They serve the local bank branch (beg them to have a bit of their own money like everyone else), they watch TV, hold bitcoin and have this mindset where they truly think that bitcoin will grow, despite them doing jack all. They think they can reap the benefits in silence, while others do the heavy lifting, they smirk.They delude themselves however, thinking their sly passive stance is a risk-free act of brilliance.However, they’re scared, and have bitcoin in a fiat cage.Their existence is just a wallet waiting to be drained by force or pressure. By the same monstrous forces that keep our heads down.Whether discussing its digital scarcity or its fiat price, the focus invariably circles back to Bitcoin as a driver for a product or service.Do you want bitcoin, do you like bitcoin? Want to work with bitcoin? Here’s a service or wallet you can buy for a few hundred dollars, here’s my link. Want to participate in the network?Buy our pre-made and plug-and-play “solution”? Want to know more, or do you know wealthy people that want in” “Call me…”They’re selling.Don’t get me wrong,I also believe bitcoin is changing that world right now.And earning a living is good, be it with art, writing, selling a service or moving a box from A to B.But they don’t get it. Because it’s damned near impossible to escape the cage
Bitcoiners love to talk about hard money and how bitcoin will change the world. They even claim to fix the world, by fixing “the money”.Yet many talk the talk, but don’t make the efforts, nor sacrifices.Walking the walk, is usually no further than the nearest bitcoin meetup, or the occasional trip to a tax-haven.Other than that. They’re chained to their fiat-past. Their kids, their house, their hobbies, their spouse and job.They serve the local bank branch (beg them to have a bit of their own money like everyone else), they watch TV, hold bitcoin and have this mindset where they truly think that bitcoin will grow, despite them doing jack all. They think they can reap the benefits in silence, while others do the heavy lifting, they smirk.They delude themselves however, thinking their sly passive stance is a risk-free act of brilliance.However, they’re scared, and have bitcoin in a fiat cage.Their existence is just a wallet waiting to be drained by force or pressure. By the same monstrous forces that keep our heads down.Whether discussing its digital scarcity or its fiat price, the focus invariably circles back to Bitcoin as a driver for a product or service.Do you want bitcoin, do you like bitcoin? Want to work with bitcoin? Here’s a service or wallet you can buy for a few hundred dollars, here’s my link. Want to participate in the network?Buy our pre-made and plug-and-play “solution”? Want to know more, or do you know wealthy people that want in” “Call me…”They’re selling.Don’t get me wrong,I also believe bitcoin is changing that world right now.And earning a living is good, be it with art, writing, selling a service or moving a box from A to B.But they don’t get it. Because it’s damned near impossible to escape the cageDisproof Escapism
The bitcoin genie is out of the bottle. We DO have digitally scarce, hard money!
The core of the message most bitcoiners promote (including the author of this article) revolves around the prevalent “debt-and-war” fiat system and the harm it inflicts on society in general. Bitcoiners explain how it enslaves us, impoverishes us, and fosters a short-term perspective, empty consumerism, and a disregard for skills, all while leaving entire generations in debt and modern forms of servitude.
That reality alone will change many mechanisms within society. That should be the core of bitcoiners and their way of living. Not promoting a referral link to get a few sats or putting a sticker on a bathroom wall at a bar. We discuss open source theories and personality traits, not how to win the race. We don’t scheme, infiltrate or sabotage; we step onto the stage humbly, like nervous kids reciting poetry for a king. We only face our own audiences. Not the audience of followers of the monsters. We might as well do a leaflet campaign in the desert while we’re at it.We often hear terms like "sound money" and the assertion "there's no second best," with some even calling it "digital gold." This latter term is particularly misleading. Gold, despite its past significance, was subject to confiscation, serving the ambitions of nations and the wealthy. Bitcoin, in contrast, is not simply a digital iteration of gold; that label is a fiat construct that fails to capture its distinct nature.
However, the question remains: why is it that, when push comes to shove, we as Bitcoiners don’t truly live, think, and breathe this “thing” called Bitcoin as the hardest money in existence? Because we don’t. I’ve visited a fair share of meetups and conferences (though not many, as conferences are largely a sham anyway) to observe the ethos in practice. And it’s not always a pretty sight.
Assholes and grifters remain assholes and grifters, regardless of whether they hold BTC or not.
Thinking in fiat terms is still rampant (including for myself, by the way, to some extent). We were born into fiat, shaped by fiat, and have worked, traded, saved, and lost within its confines.
The fiat mindset, I dare say, is even more detrimental when Bitcoiners adopt it, as it amplifies the negative consequences even beyond those of the fiat world itself.
After all, at the very least, those within the fiat system are all equally screwed in their flawed monetary reality by a system that is a true circus Maximus of greed and debt. Consider those burdened by immense student loan debt, individuals with unrecognized talent, and others denied opportunities because less skilled people from higher financial echelons secure “proof of stake” jobs. Even if they lack the necessary abilities. There are fiat denizens sent to war, subjected to bombings, and relentlessly exploited for profit throughout their lives to sustain a parasitic, rent-seeking system… all under the false promise of security in their later years… when in reality, they are chewed up and spit out.When these fiat slaves wield a fiat mentality toward one another, it’s considered normal; no one can bat an eye if one fiat rent-seeker bleeds another dry, then tosses them aside for a new victim once the yield or short-term gain is realized. That’s simply how the fiat hamster wheel has been turning generations on end, while the proof-of-stake lords benefit across multiple generations.
The exploitation, the focus on short-term gains, the inherent stupidity of the system—it’s ingrained in the people themselves. Their greed and fiat/shitcoin mentality is "the norm." Some even dare to call it "capitalism" or democracy.
They can’t be offended by anyone screwing them over or getting ahead to gain a few fiat tokens, be it dollars or the Euro Mickey Mouse coin. They just carry on, shrug their shoulders, and crawl over each other like the basket full of crabs they inhabit day to day. Being among the few crabs that can touch the rim of the basket before being pulled down again by the other crabs, is what’s called success.
However, witnessing such behaviors and ways of living among individuals who identify as Bitcoiners evokes not only profound ethical sadness but also reveals consequences far more damaging to Bitcoin than if those same individuals had remained solely within the fiat system. Therefore, a fiat mentality within the Bitcoin space is even more repugnant than the mindset of some shitcoiners. At least with shitcoiners, you understand they are peddling a token, coin, or some fabricated service to offload onto unsuspecting individuals to make ends meet (and fund their cheap hotel rooms in exotic looking places while projecting an image of success (and the Modern Ottoman beard look) on Instagram). Consider a scenario: if someone at a vegetable market (assuming such places still exist in the fiat world) suggests to another vendor a way to conduct more business off the books, it’s met with indifference. That’s considered normal.But when a Bitcoiner at a meetup — an event where for three years you've been trying to dissociate Bitcoin from the tired narrative of it being solely "for fraudsters and criminals" — and you overhear "Bitcoiners" discussing methods for laundering illicit funds, then it becomes a significant problem. As if they can’t make ends meet without doing “the fiat thing”. Such individuals, as a Bitcoiner, disgust me. They clearly "don't get it." They fail to grasp the fundamental values of Bitcoin. They resemble the stereotypical used car salesmen who prioritize nothing beyond their immediate needs, like avoiding having to have a cheap dinner of dog food and tomato sauce that evening if they bag another customer by whatever lies they’ll have to tell. I would go so far as to assert that Bitcoiners with a fiat mentality are more detrimental to Bitcoin's growth than both those enslaved by the fiat system and shitcoiners themselves. A fiat drone will simply save, invest, and adhere to the established rules of banks and central banks.
They don’t question these norms; it’s their accepted reality. They’re labeled “normies” for a reason—they find satisfaction in conforming, believing the deception and theft, even perceiving it as beneficial because that’s what they’ve been told on television. They place their trust in numbers and statistics while diligently paying off their mortgages and investing in whatever financial products the TV shows spoon-feed them. Shitcoiners (closely related to fiat slaves) will merely promote their scams and worthless projects to generate short-term gains (in fiat, naturally) to sustain their shallow lifestyles of loneliness, prostitutes, and grocery bills paid with bank cards from the Seychelles.
But Bitcoiners with a fiat mentality? They actively undermine Bitcoin. They are toxic, and the sooner they revert to pure fiat, the better for the Bitcoin ecosystem. They offer no positive contribution whatsoever to Bitcoin’s progress.
More bitcoiners need to grow a spine
I've started to label these individuals as “cosplay bitcoiners.” They are typically nothing more than bitcoin holders (definitely not HODLers). These are people who act as though Bitcoin is merely another speculative asset (alongside a plethora of garbage coins and scams) instead of the monetary revolution it truly embodies. Most bitcoiners engage in this cosplay, reciting the talking points without actually changing their lives. Or… they view it simply as a means to generate income by uttering the right phrases and selling various items and merchandise. If Bitcoin were to cease to exist (a highly improbable scenario), they would likely be selling counterfeit Pokémon merchandise, fake Rolexes, or working as box movers in retail (sporting a perm). This might upset some who have dedicated significant portions of their lives to the Bitcoin ecosystem. However, what should be far more infuriating is the realization that your dreams, hope, and hard work are ultimately benefiting these cosplayers.
These individuals also say things like “You could consider moving to Solana for a while…” or “I have a referral link for insert flavor-of-the-week scam.” This genuine effort to cultivate a Bitcoin ethos is often undermined by people lacking activism, backbone, or conviction. Typically, these are the same individuals who inquire about price action during minor dips in Bitcoin's fiat value. They exhibit “scared money” behavior, just like in the fiat world. Consider that: they are scared (of) money. That’s right,… people that lived, and were raised in fiat are in fact scared… of money. This ingrained perspective, though varying in its impact, can act as a distraction or even a negative influence on Bitcoin's overall growth. I know the genuine contributors are out there. Rest assured, I am acutely aware of what it means to dedicate your time and energy to the betterment of Bitcoin; I've done it before and continue to do so years later. I respect that immensely. But the moment you recognize your efforts are primarily benefiting these parasites, you should immediately cease and let them wither.
They are not there for Bitcoin at all. I believe a fundamental aspect of being a Bitcoiner is calling out such behavior — to embody a form of activism, a vetting process aimed at fostering greater freedom. This might seem paradoxical, but it’s not; it’s akin to broadcasting a double-spent transaction onto mempool and having it rejected by the nodes. In my opinion, Bitcoin's primary essence is freedom. This freedom is underpinned by consensus and proof of work. However, this doesn't imply that we should be a universally accommodating resource for individuals who merely hold Bitcoin and seek to profit off our efforts while contributing nothing of substance to the space beyond their own marketing nonsense. They say the lines, but don’t save lives.
But why not?
If Bitcoin is truly the hardest money, the scarcest asset humanity has ever encountered, then why would we willingly trade it for a demonstrably inferior, inflationary, and state-controlled currency? This holds true even if that fiat is disguised as a modern "coin" or a cheap imitation of Bitcoin.
The uncomfortable truth is that many Bitcoiners, whether consciously or subconsciously, remain tethered to the legacy financial system. We espouse the principle of "don't trust, verify," yet we often evaluate Bitcoin through the distorted lens of its fiat exchange rate. Furthermore, many local meetups are infiltrated by individuals whose motives, schemes, and outright nonsense we fail to scrutinize or verify.
We neglect even the most fundamental forms of verification (such as accepting a function purported to be around 40 KB in data size when it's bundled within a > 50 MB software program). We profess belief in absolute scarcity, yet we shy away from adopting Bitcoin as our genuine unit of account, nor do we accurately measure our purchasing power (as devising a truly precise method might necessitate an invention worthy of a Nobel Prize in Economics).
Armed with the hardest money, ample liquidity, and considerable intellect, we still find ourselves waiting for Presidents, Philosophers, and various Personalities to artificially inflate Bitcoin's price, behaving like apprehensive investors in a newly listed startup.
“But with bitcoin”
These Philosophers, Personalities, and Presidents (PPPs) often represent a mere "follow-the-leader" phenomenon among many who identify as Bitcoiners. Philosophers delve into the intricacies of Bitcoin: its support for local social structures, its international applications, the underlying mathematics, the time-based mechanisms… It's all incredibly fascinating and has been explained countless times in various tones and for diverse audiences. Yet, much like in Bitcoin software development, there's often a lack of curation or editing; people simply produce without rigorous testing or questioning the necessity or widespread adoption of their contributions. Some even mistakenly believe these philosophers will somehow influence the "price." However, their role is primarily to explain, analyze, and provide understanding. That, of course, is valuable as it stimulates thought (even this very writing serves that purpose). However, Bitcoiners deeply entrenched in the philosophical aspects can often be blind to their own contradictory circumstances.
 It can be jarring, even alienating, to listen to a podcast dissecting the profound intricacies of time and Bitcoin's blockchain while simultaneously enduring the mundane reality of your fiat job, with a coworker loudly handling customer calls nearby. The core issue is that this mentality increasingly mirrors the practices of the fiat (and shitcoin) world: passively holding onto "your bag" or "your stake" and promoting that position while vaguely advising others that "education is important" or "spreading the word is good." Ultimately, many of those dispensing this advice do little more than appear on their YouTube channels, take the stage at their own conferences, or write (or commission) their paid newsletters. Some diligently court wealthy individuals to explain Bitcoin, aiming to earn a few dollars, but they might as well be selling Tupperware if it paid the bills. Genuine care is often absent; it's their Bitcoin-flavored version of a fiat job. They are simply holding onto sats, much like one would hold onto ETFs or stocks in the traditional financial world. Michael Saylor, at a conference in Madeira, once stated: “You are here because Bitcoin needs you… and when you leave, I sincerely hope you will go out there and do good for Bitcoin.”
It can be jarring, even alienating, to listen to a podcast dissecting the profound intricacies of time and Bitcoin's blockchain while simultaneously enduring the mundane reality of your fiat job, with a coworker loudly handling customer calls nearby. The core issue is that this mentality increasingly mirrors the practices of the fiat (and shitcoin) world: passively holding onto "your bag" or "your stake" and promoting that position while vaguely advising others that "education is important" or "spreading the word is good." Ultimately, many of those dispensing this advice do little more than appear on their YouTube channels, take the stage at their own conferences, or write (or commission) their paid newsletters. Some diligently court wealthy individuals to explain Bitcoin, aiming to earn a few dollars, but they might as well be selling Tupperware if it paid the bills. Genuine care is often absent; it's their Bitcoin-flavored version of a fiat job. They are simply holding onto sats, much like one would hold onto ETFs or stocks in the traditional financial world. Michael Saylor, at a conference in Madeira, once stated: “You are here because Bitcoin needs you… and when you leave, I sincerely hope you will go out there and do good for Bitcoin.”That's a commendable call to action. However, it also inadvertently highlights a form of servitude, a call that, regrettably, many have not heeded. Right now, Bitcoin's treated more like digital real estate than actual cash – something to hodl and hope it moons, while others do the promoting. Activism, at least here in Belgium, is a ghost town.
Elsewhere, it's often just small-time stuff, easily corrupted by book-writers, shitcoin promoters, ego-trippers, or even creeps hitting on vulnerable women in new-age scenes. This passive vibe has helped a bit, sure, but it shows we're still scared to call Bitcoin real money. It's the hardest money ever, yet we act like fiat's the boss, when Bitcoin's the true store of value. The circular economy crawls along. Instead of waiting for "hyperbitcoinization," we need to act like it's already here: support Bitcoin-only businesses, demand salaries in sats, and actually think in sats, not fiat. But become organized, more to the point: set up systems so you can build and rely on one another.To make Bitcoin truly hard money, we gotta stop pricing it and thinking in fiat, actually use it to pay and get paid, teach people it's a monetary system not just an investment, and directly challenge fiat by building Bitcoin-native economies, not just begging institutions to buy in. The more we act like Bitcoin is money, the faster the world will have to agree.
Bitcoin’s success is not inevitable.
Because it is maintained by people, and people are inherently flawed. However, it is also governed by mathematics, a perfect framework that categorizes chaos into order and back into incomprehensible chaos. There, within the crucible of math, language, cryptography, and time, lies Bitcoin: our creation, our potential salvation, and perhaps our sole remaining hope.
It demands action from Bitcoiners. If we genuinely believe in Bitcoin as the hardest money, we must begin to utilize it as such, rather than posturing on stages like immature, attention-seeking individuals vying for personal recognition and petty power struggles.
The future is not forged by those idly waiting for a magical price point; it is built by those who actively transact, develop, work, and live on Bitcoin today. Hard money transcends mere scarcity; it embodies utility, intrinsic value, and the tangible construction of liberty. Bitcoin's purpose is not simply to replace the existing decay of fiat with a superficial rebranding of the same fundamental rot. Bitcoin is not intended to supplant the old fiat corruption with an identical corruption merely bearing a Bitcoin label or logo.
The divergence is stark: one grey-colored path leads us to a state of ambiguity and ineffectiveness, the other to a vibrant, focused purpose. This ambiguity manifests as excessive accommodation, an unwarranted stubbornness where adaptability is needed. We tend towards being overly compliant and even subservient, exhibiting exaggerated politeness and empathy, even as our advancements inevitably dismantle the obsolete systems. That path has a Dixie orange color.
This is because many Bitcoiners now crave external validation, leading to inconsistent and muddled messaging, belonging authentically to neither the stagnant grey nor the purposeful orange.
We, and our true Bitcoiners—our intellectual offspring—represent an inherently incompatible lineage, incapable of either peaceful coexistence ("protest") or productive integration ("procreate") with these outdated methodologies and their swarm of futile endeavors. The cosplay bitcoiners and their lukewarm followers and creations aspire to be part of a fintech reality that is not their own, and a fiat world that has relegated them to the roles of insignificant footnotes and background commentators.
Despite our core differences, we persist in engaging with the stake-people, the frail-minded powerhouses that let us participate in their arenas, gathering under the harsh glare of moral decay and corruption. We mine Bitcoin from the future, but it’s tethered to the present. They hamper our progress with outdated tools and (re)distribution systems rooted in the 18th century.We can invent so much better systems, bulldoze the old and rebuild our cities and reclaim our value.
It’s time…
The moment has arrived to begin valuing Bitcoin for what it has always been destined to be and will forever remain: hard money. Let us consign the parasites to their rightful place – the gutter of fiat. Reader, dear reader, you who have invested the time and effort to cease scrolling through the endless torrent of filth, garbage, and attention-seeking displays on your phone, do you grasp the unique historical opportunity presented to your vulnerable digital soul to reclaim your life, to transcend mere survival and truly flourish? Do you comprehend this? Do you even realize that digitally scarce, digitally verifiable hard money awaits your mining, purchase, holding, and personal safekeeping? Or do you still cling to the illusions projected onto the wall of Plato's cave, telling you every lie under the sun for their short gains and diatribes? Do you live in the corridor of greyness? Probably.
Observing the vapid semantic debates onstage, the performative security measures, and the blatant power struggles, I am reminded of the early Christian disciples and the challenges they must have faced in spreading the word of their Lord, relying solely on their individual conviction while constantly encountering those driven purely by the pursuit of power. Bitcoiners are no different, despite never having known their own guiding figures. The distinction lies in our approach: we do not expel the transgressors and the disreputable from the market; nor do we seek to cure the afflicted or nourish the starving. We are not torn apart by lions, for we operate in the shadows, our influence primarily through written works, lacking the support that stems from personal charisma. Fiat bleeds people dry, fueling the vile machinery of passive rent-seeking yield and perpetual servitude.
In Bitcoin, we possess the potential to be their undoing, but only if we can match their ruthlessness, their multi-generational cunning, and their inherent malice. That’s not in our nature, so we’ll need to change and adapt. To truly prevail, we must outmaneuver their evil, win their long-term game. To win, we must out-evil evil. Win their multi-generational ongoing long-term game.That’s not easy, because you’re being poisoned day in day out.
So… here goes.
You must choose your path: gray or orange.
Decide how you’ll navigate the clutter: hardware wallets you don’t need, unscalable orange-pilling that’s more about ego than Bitcoin, books that hardly anyone reads, redundant artwork you’ll never buy, searching for a place in the unreachable oasis of bitcoin jobs, the mirage of funding,the naïveté of Value4Value, the Saylor-worshipping instinct, stickers slapped on poles, rushed and untested software, apps that repel users, conference circuses filled with grifters, posers and some half-gods, The pump-my-bags philosophers. The fork in the road lies ahead
Will you keep micro-dosing the corruption of the fiat world, day by day? Or will you don your armor and sacrifice for future generations?\ You ‘ll be part of an army of cyber Jesuït knights, or part of a gang of ad hoc grifters smelling like patchouli and fear.
npub1sec6degc3ae7warveuxaz6dlffnc2sutwtqjr7pmll7sf7ypjngsd4p0l7Let centuries of hate and destruction be channeled like unbreakable equations, their tax collecting vultures, their redistribution to the weak.We can be in harnesses, economically cause their bellies gorged on our produce, sliced virtually apart, ending their predatory exploitation and theater politics. Let that hate flow block by block, so our wait for a revolution, promised peace, and security, finally ends. We don’t need to wait, We have all we need - right - friggin - now! All we need is here to start as the first generation of the ones that turn the table. We can strike from here onwards.
You can’t do that just by standing there, we need to rally behind something. So … we need to…
 ## Slay the Monsters ( A Bitcoin manifesto )
## Slay the Monsters ( A Bitcoin manifesto )The race against fiat’s totalitarian grip isn’t coming — it’s already here.
And we’re late.
We’re not facing some bureaucratic mess or sleepy institution. We’re facing monsters. Real monsters. The kind that don’t blink, don’t break, and don’t stop.
These creatures don’t rule from parliaments. They rule from shadows. From bloodlines. From vaults built on centuries of power—and centuries of control.
And while we argue over memes, While we nitpick sound quality on a free podcast, While we debate how orange our sunglasses should be— They’re already building the next cage.
You want to know the core of the battle?
It’s this: They built a system designed to enslave you. And it works. Because it’s not just code or money—it’s a mindset. And they’ve trained you for generations to stay small. Stay busy. Stay broke.
They don’t care about trending topics, the fashion they make you wear, the rent seeking and mind numbing media garbage. They don’t care about today’s startup scene. They don’t need to. They freeze technology until their factories are ready. They script the narrative until their puppet politicians can sell it. They control enough markets to play with your life like a cat with a mouse.
And no, they’re not thinking in 5-year business plans. They’re thinking in bloodlines. They’re thinking in centuries.
They are bloodsuckers.
They take the rights of the gifted, Take the skills of the builders and make them into jesters They crush the dreams of the brave, weaken strong sons, and turn bright daughters into obedient servants.They make you lose time;Steal your effortSlap a price on anyone.
But here’s the good news:
We are Bitcoiners. We don’t need their permission. We don’t need to play their game. We hold a sword they can’t lift — an indestructible blockchain. And we have “forever coins”. We have the heaviest hammer
We can build faster. Stack hard money. Deliver proof of work and become the worst multi-generational pests they’ve ever seen. And take everything from them in about four generations:
One generation to build and adapt. One or two to take over, and One glorious one to finish the job and chop their virtual heads off to end the corruptionTheir heads on a stake, is the only proof-of-stake’ism that will be universally liked.
Because in their world, people are the fuel — drained for passive yield. But in our world?
We, the Bitcoin people who underwrite its value, represent the negative yield on fiat. We ARE your negative yield in human form \ We are their weakness — if we become as relentless and evil as they are.We can be methodical and calculated, generations of poison for their systemWe infiltrate, poison, outpace them.Like they did centuries ago with the commons, the tribes and kings. As focused. As strategic. As ruthless.
Then—only then—can we clean ourselves.
Only then, with the deed done, can we rebuild humanity. Burn the bloodlines that buried us.The old bloodlines—those leeches—will be caged, stripped, and left to wither in poverty, and as history proves… they never survive poverty\ While we’ve been bathing in it by choice.
From their ashes, we’ll purge our own darkness and thrive through innovation, not tyranny We will work, We will thrive through innovation, not colonization. Through consensus, not decree. Through quality not administrative control. And talent and skills will rise on merit, not aristocratic last names. We verify without grandeur.
In that world, our temples will exalt beauty — not control.In that world, Their goons and servants will be our jesters, dancing like harlots, their princesses will be sobbing on dirt, they’ll all eat their own industrial drab
The power is already ours; we don’t need to pray, we don’t need hope nor luck. We need raw, unrelenting will.
We need power.
And evil, focused, unshakable determination.
You can’t slay monsters with flyers. You don’t take down empires with stickers. You don’t bring bloodlines to their knees with polite debates on their stages.You slay monsters with the sharpest sword in history — Bitcoin.
They’re gutted with the sharpest blade—our blockchain—plunged into their stone cold hearts, until their black blood flows over the marble floors of their castles and their next of kin. Then, we feast and build anew on the ruins of their depravity.
Their next of kin witnessing our determination while their funding falls dry in promises of continuity they hide or perish.
Then we slay the rest.We drink their blood, their wine, their milkshake. We burn their paper promises and their repeating cycles of social unrest and greed.
We build something new. Something real. On the ruins of everything they corrupted.Bitcoiners need to be more than politeBe more evil, to do more good.Show monsters no mercy nor empathy. Don’t give them hard money, but wreck their legacy, faceless organizations and companies.
We are the debt collectors of last resort. We are the negative yield that spins and twists.We are the final rotation of the hamster wheel of pointless energy.We save ourselves with math..
Bitcoiners,Do thy proof of work, or become a whore for their next generation of silver spoon fed monster kids...\ You’ll have to be polite doing the deeds if you doOr take the smile off their face.Sacrifice.WorkDefy
Slay monsters like a knight building a legacy, freeing the world.
Or serve the monsters like the bitch you are.
Our consensus and your choice.
By AVB
If you like my writings: tip me here
-
 @ f839fb67:5c930939
2023-10-19 14:28:30
@ f839fb67:5c930939
2023-10-19 14:28:30Chapter 5: Echoes of the Past
Life for Peter and Gwen took on a sense of normalcy as they resumed their civilian identities, working and studying. However, Gwen's reappearance raised questions, drawing the attention of friends and foes alike. Some welcomed her with open arms, while others remained skeptical of her true origins.
One evening, as Peter and Gwen strolled through Central Park, they were approached by an old friend, Mary Jane Watson. Her warmth masked a deep-seated concern about Gwen's return, but she chose not to reveal it for the sake of her friend's happiness.
Chapter 6: A Sinister Resurgence
The tranquility in their lives was short-lived when the criminal mastermind, Norman Osborn, better known as the Green Goblin, resurfaced in the city. Osborn had been thought dead for years, but he returned with a vengeance, orchestrating a wave of chaos and destruction.
The renewed threat of the Green Goblin pushed Peter and Gwen to their limits. Gwen, driven by a desire to protect her newfound home, donned her own costume once more, taking up the mantle of Spider-Woman.
Chapter 7: Partners in Peril
Peter and Gwen's relationship faced its greatest test yet as they fought the Green Goblin together. The emotional strain of battling a personal enemy combined with Gwen's struggles to adapt to her role as Spider-Woman put immense pressure on their love.
Despite the trials, the couple's bond grew stronger, and their teamwork improved. With Mary Jane's support, Gwen and Peter managed to expose Norman Osborn's criminal activities, leading to his eventual arrest.
Chapter 8: An Unexpected Alliance
A new threat emerged, one that neither Spider-Man nor Spider-Woman could defeat alone. A powerful crime syndicate, led by the enigmatic "Black Cobra," threatened to engulf the city in a reign of terror. Realizing the scope of the danger, Peter and Gwen sought help from other superheroes in the Marvel Universe.
Spider-Man and Spider-Woman formed an alliance with heroes such as Daredevil, Jessica Jones, and Luke Cage. Together, they launched an assault on the Black Cobra's operations. The battle was fierce, and the heroes found themselves tested in ways they had never anticipated.
Chapter 9: Confronting the Past
As the battle raged on, a shocking revelation came to light: the Black Cobra was an identity adopted by none other than Gwen's own father, George Stacy, who had been presumed dead for years. He explained that he had faked his death to infiltrate the criminal organization and dismantle it from within.
Gwen was torn between her duty as Spider-Woman and her love for her father. Ultimately, they reconciled and, together with the other heroes, they managed to expose the true mastermind behind the crime syndicate, sending the criminals to prison and freeing George from his double life.
Chapter 10: A Future Together
With the city safe once more, Peter and Gwen could finally focus on their personal lives. Gwen chose to embrace her role as Spider-Woman and continue to fight alongside Peter as a partner in both life and crime-fighting.
Their journey had been one of triumphs and tribulations, but through it all, their love had endured. As Spider-Man and Spider-Woman, they swung through the city, ready to face whatever challenges lay ahead, knowing that together, they could overcome anything that threatened their world.
The echoes of the past had brought them together, and now, they looked forward to a future filled with adventure, love, and the unwavering commitment to being New York City's protectors.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 84b0c46a:417782f5
2025-05-11 06:05:38
@ 84b0c46a:417782f5
2025-05-11 06:05:38- Lumilumi The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
-
Long Form Content Editor A lightweight Long Form Content Editor with editing functionality for your articles. It supports embedding Nostr IDs via NIP-19 and custom emoji integration.
-
Nostr Share Component Demo A simple web component for sharing content to Nostr. Create customizable share buttons that let users easily post to Nostr clients with pre-filled content. Perfect for blogs, websites, or any content you want shared on the Nostr network. Try the interactive demo to see how seamlessly it integrates with your website.
Only clients that support receiving shared text via URL parameters can be added to the client list. If your preferred client meets this requirement, feel free to submit a pull request.
-
Nostr Follow Organizer A practical tool for managing your Nostr follows(kind3) with ease.
-
NAKE NAKE is a powerful utility for Nostr developers and users that simplifies working with NIP-19 and NIP-49 formats. This versatile tool allows you to easily encode and decode Nostr identifiers and encrypted data according to these protocol specifications.
- chrome extension
- firefox add-on
-
Nostviewstr A versatile Nostr tool that specializes in creating and editing addressable or replaceable events on the Nostr network. This comprehensive editor allows you to manage various types of lists and structured content within the Nostr ecosystem.
-
Luminostr Luminostr is a recovery tool for Nostr that helps you retrieve and restore Addressable or Replaceable events (such as kind: 0, 3, 10002, 10000, etc.) from relays. It allows you to search for these events across multiple relays and optionally re-publish them to ensure their persistence.
-
Nostr Bookmark Recovery Tool Nostr Bookmark Recovery Tool is a utility for retrieving and re-publishing past bookmark events ( kind:10003,30001,30003 ) from public relays. Rather than automatically selecting the latest version, it allows users to pick any previous version and overwrite the current one with it. This is useful for restoring a preferred snapshot of your bookmark list.
-
Profile Editor Profile Editor is a simple tool for editing and publishing your Nostr profile (kind: 0 event). It allows you to update fields such as name, display name, picture, and about text, and then publish the updated profile to selected relays.
-
Nostr bookmark viewer Nostr Bookmark Viewer is a tool for viewing and editing Nostr bookmark events (kind: 10003, 30001, 30003). It allows users to load bookmark data from relays, browse saved posts, and optionally edit and publish their own bookmark lists.
-
Nostr Note Duplicater Nostr Note Duplicater is a tool that rebroadcasts an existing Nostr event from a relay to other selected relays.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ f4a890ce:af88c4aa
2025-05-11 05:56:39
@ f4a890ce:af88c4aa
2025-05-11 05:56:39執行摘要
上週市場總市值進一步上升至2.96兆美元,顯示資金持續淨流入,加密資產整體維持多頭氣氛。儘管成交量自高點回落至868.3億美元,但市場流動性仍處於健康水準。恐懼與貪婪指數下滑至60,情緒從過度樂觀回落至中性偏樂觀區間,短期可能出現技術性整理。 衍生性商品方面,永續合約持倉再創新高至1,200億美元,顯示槓桿資金依然積極參與。不過,空單爆倉規模高達5.17億美元,顯示空頭遭遇大幅擠壓,需留意市場過熱風險。期權市場仍聚焦高價位行權價,反映中期上行預期不變。 ETF方面,本週BTC與ETH皆出現資金淨流入,分別為4.225億與650萬美元,顯示機構資金還是更喜歡BTC。 本週需持續關注市場情緒,資金是否重新進場?穩定幣市值變化,是否有新增資金流入?永續合約持倉量和期權市場看漲部位集中在高價區,是否引發誘多行情?ETF 是流入或流出?投資人信心是否進一步下滑?
加密市場
本週加密市場總市值上升至 3.23 兆美元,較上週略有增長,顯示市場仍維持穩定向上的趨勢。與此同時,成交量提升至 163.1 億美元,代表市場交易活躍度有所回升,資金流動性改善。
https://coinmarketcap.com/charts/
投資者情緒方面,恐懼與貪婪指數攀升至 73,顯示市場情緒轉向「貪婪」,投資人信心增強,買盤意願更為積極。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
而相對強弱指標進入強勢區間,表明短線上漲動能依然存在。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數為 27,顯示市場資金仍偏向比特幣,對中小型代幣的風險偏好仍較為保守,尚未出現明顯的資金輪動情形。
https://www.blockchaincenter.net/en/altcoin-season-index/
此外,穩定幣市值增長至 2,422.26 億美元,可能反映部分資金正在準備籌碼,等待更具吸引力的市場機會。
https://defillama.com/stablecoins
小結
本週加密市場總市值持續上漲,而成交量同步回溫,顯示交易活動回升,市場信心增強。恐懼與貪婪指數進一步攀升至貪婪區間,暗示市場風險偏好提升,但仍須關注市場過熱風險。相對強弱指標顯示市場仍具上升動能,但山寨幣季節指數低迷,顯示資金仍主要集中於比特幣。穩定幣市值增長,反映投資者仍保持一定的謹慎態度。未來需密切關注宏觀經濟環境及市場資金流向,以判斷趨勢是否能夠持續。
衍生性商品
本週永續合約市場的持倉規模較上週進一步攀升,從 116.9B 增至 132.2B,顯示市場對槓桿交易的需求依舊強勁。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率方面,當前整體市場呈 正費率,主要交易所的資金費率保持在 0.01% 左右,反映出市場偏向多頭。
https://www.coinglass.com/zh-TW/FundingRate
然而,市場波動仍然導致大規模的強制清算。根據最新數據,5月8日 出現大量爆倉事件,空單爆倉金額達 835.998M,而多單爆倉金額則達 131.779M。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$93,000 附近 的清算金額達 188.95M,這一價位區間成為近期市場的重要風險區域。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場的數據顯示投資者對不同價格區間的配置策略仍有明顯差異。在 $85,000 行權價的看跌期權合約數量維持在 9.82K,但總金額增加至$15.42M,顯示市場對該區間的下行防禦仍然較強;而 $100,000 行權價的看漲期權合約數量則由 15.67K 增至 17.8K,總金額大幅提升至 $177.43M,顯示投資者對市場上行的預期正逐步增強。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
此外,最大痛點仍然維持在 $90,000,但時間點有所調整,分別落在 2025/05/30 與 2025/06/27,顯示市場對長期風險的調整。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
本週衍生性商品市場展現出更高的槓桿操作與波動風險,特別是在清算金額與爆倉數據方面。期權市場的配置策略分歧仍然明顯,投資者對短期與長期的行情預期有所不同。在市場波動區域,資金流向與槓桿操作需更加謹慎,以避免因價格劇烈變動導致強制清算。建議投資者持續關注關鍵價格區間的變化,並根據市場動向調整交易策略,以應對可能出現的市場風險。
ETF
在本週的加密貨幣ETF市場中,比特幣(BTC)與以太坊(ETH)皆呈現資金流入的狀態。比特幣ETF吸引了4.225億美元的資金流入,顯示出市場對BTC的信心。 而ETH ETF則流入650萬美元,雖然相較比特幣規模較小,仍然顯示資金回流跡象。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週加密貨幣ETF市場出現資金回流,尤其BTC的流入幅度相當亮眼。市場投資情緒似乎有所回溫,但仍需留意後續可能的波動因素,例如宏觀經濟變數及技術面調整。若資金流入趨勢能夠持續,將進一步確認市場情緒的轉變,為後續行情提供更多參考依據。
鏈上分析 | BTC
從本週的鏈上數據來看,BTC 持續自交易所流出,持續創出新低,表明持有者更偏向於自我持幣。
地址分布方面,中小持倉(10-100)的地址數量持續下滑;而其餘的地址數量則呈現小幅上升,代表市場對後市仍保有一定信心。值得關注的是10k以上的超級鯨魚地址開始出現買入的動作,而近期仍持續上升中。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
近期鯨魚活躍地址呈現明顯上升趨勢,無論是新進鯨魚還是長期未動的大型地址皆出現甦醒跡象,反映市場中大型資金正逐步活躍並積極參與。這種現象往往代表對未來市場走勢的樂觀看法,有助於市場底部籌碼的穩定與後續動能的蓄積,值得持續關注其資金動向與潛在布局。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
近期觀察到「1+ Year HODL Wave」指標持續下降,顯示過去一年未曾移動 BTC 的長期持有者開始活躍。這通常代表部分長期投資人選擇獲利了結。
https://www.bitcoinmagazinepro.com/charts/1-year-hodl-wave/
目前比特幣的 NUPL(Net Unrealized Profit/Loss)指標已進入「樂觀/焦慮(Optimism/Anxiety)」區間,此區間歷史上曾多次出現在牛市中後段,並伴隨著市場高點的反轉風險。
https://www.bitcoinmagazinepro.com/charts/relative-unrealized-profit--loss/
從「短期持有者實現價格(Short-Term Holder Realized Price)」圖表觀察,目前市場價格已明確站上該指標,代表短期持有者的籌碼壓力已基本完成消化。此現象顯示市場獲得良好支撐,且買盤力量逐步強化,推動價格持續上行。若能維持在該實現價格之上,將有助於鞏固多頭趨勢,為後續行情打下上漲基礎。
https://www.bitcoinmagazinepro.com/charts/short-term-holder-realized-price/
小結
從地址分布來看,大戶(鯨魚級地址)持續進行比特幣的累積,而中小型持倉地址則出現持續拋售現象,顯示市場籌碼正在向強手集中。NUPL 指標目前位於「樂觀/焦慮(Optimism/Anxiety)」區間,雖然歷史上部分牛市高點也曾出現在此階段,但仍有機會延伸至「信念/否認(Belief/Denial)」階段,帶來進一步上漲動能。此外,短期持有者實現價格已被市場價格突破,顯示籌碼壓力已基本消化,支撐當前上行趨勢。後續仍觀察大戶行為與情緒變化將是判斷行情延續與否的關鍵。
總體經濟
本週總體經濟數據與上週保持一致,聯邦基金有效利率維持在 4.33%,顯示市場仍處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著 6 月 18 日即將召開的聯邦公開市場委員會 (FOMC) 會議,市場普遍預期利率將維持不變,反映出決策者對當前經濟形勢的謹慎態度。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
和上週一致,消費者物價指數 (CPI) 為 2.41%,仍處於聯準會通膨目標的範圍內。另一方面,失業率穩定在 4.2%,企業對於人力需求依然穩固。這樣的情況使得貨幣政策決策者在調整利率時需更加謹慎,以避免過度收緊或過度寬鬆對經濟帶來的衝擊。
https://www.macromicro.me/series/37/unemployment-rate
https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
小結
現階段總體經濟環境維持穩定,貨幣政策仍以觀望為主。在市場流動性尚未顯著提升的情況下,投資人仍需密切關注即將公佈的經濟數據,以尋找可能影響資產價格的關鍵因素。
新聞
VanEck 提交在美國推出首個 BNB ETF 的提案
比特幣支付應用程式 Strike 將提供 BTC 借貸服務,協助新興產業發展
Revolut 將透過 Lightspark 為歐洲用戶推出比特幣閃電支付
富途證券開通比特幣、以太坊、USDT儲值:香港券商挾著加密走
https://www.blocktempo.com/futu-securities-launches-bitcoin-ethereum-and-usdt-top-up/
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
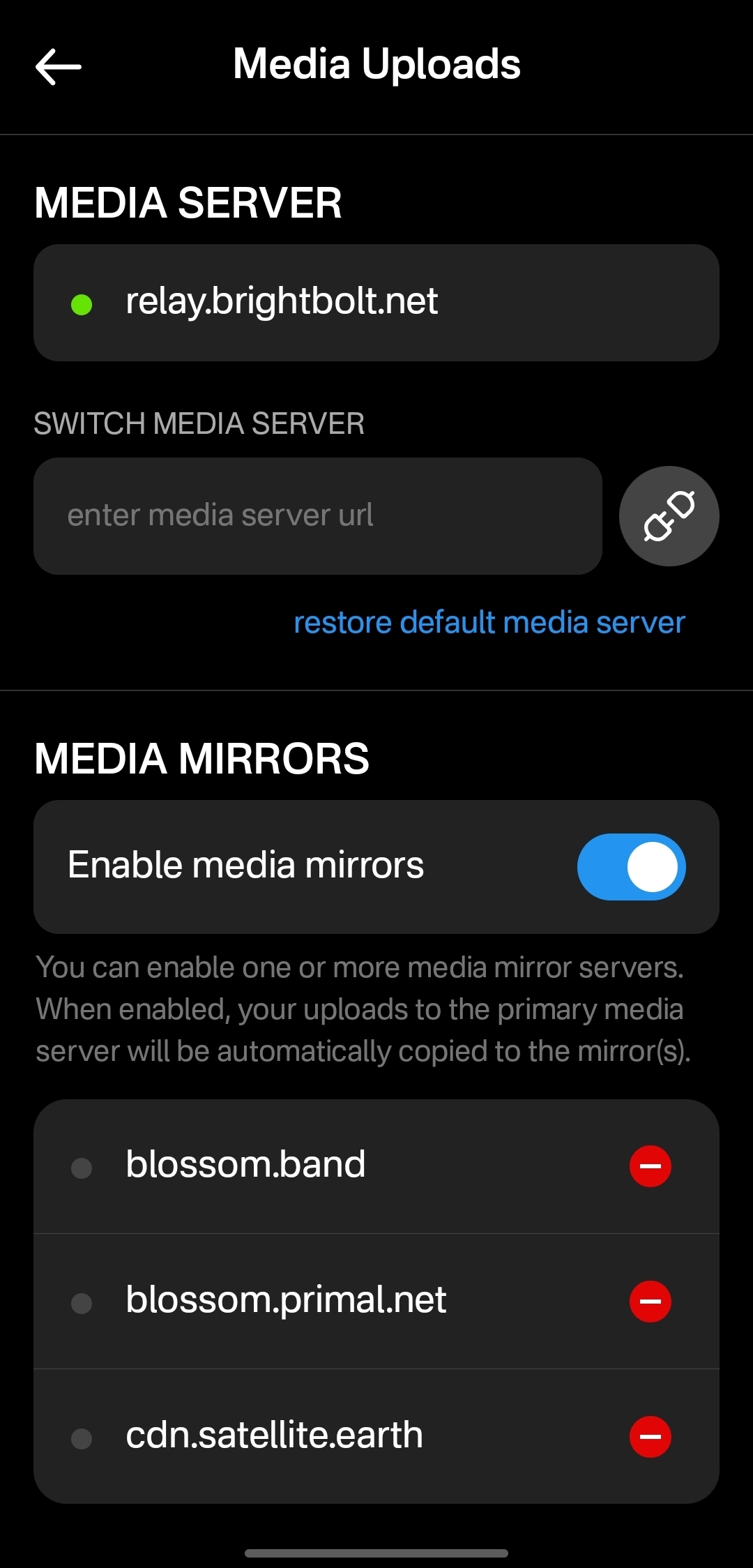
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ fa315e8d:e3a09cf4
2023-04-01 05:24:51
@ fa315e8d:e3a09cf4
2023-04-01 05:24:51Hello World
This is a test of my nostr application.
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:38:46
@ 3c389c8f:7a2eff7f
2025-04-29 18:38:46Let go of the algorithms and truly discover what it means to explore. Social media used to mean something. Once upon a time, it was a way to stay connected to friends, family, and colleagues over things we enjoy. We could share, laugh, and learn. Over time, it has devolved into cheap entertainment at the cost of our privacy. Our relationships and interests have been shoved into a corner in order to make room for "suggested posts" and "for you" content designed to evaluate our attention for advertising purposes. We've lost what it means to truly connect, and we've lost what it means to explore our curiosities.
Enter Nostr. A protocol designed to resist authoritative censorship, just happens to fix a whole lot of other problems, too. By removing the central authority, Nostr offers its users complete control of what we feed our minds. How do we break our algorithm dependency to find better content and better relationships again? We explore and discover:
The Chronological Life.
The existence of time may be debatable but our dependence on our perception of it is not. We live our lives chronologically. Why do our online lives need to be any different? There is no real reason, other than we've just gotten used to being engulfed by whatever the black box wants us to see. When we remove the algorithms, we find that online information flows just as it would in our daily lives. Important events get talked about by many people, over a long period of time. Things of less relevance fade. We see the rhythm of life reflected in our feed. This is an organic human experience transferred to the digital world. We depend on the people we know and the sources we trust to keep us informed about what really matters. We have fun, we move on. Nearly every Nostr social client brings this experience front and center through the traditional follow feed. Many use replies as a way to show you what is worth talking about for more than a hot minute. Its what old social media gave us, then took away. Nostr gives it back. It's not the only way to enjoy Nostr, though, so let's continue.
"The Human Animal Differs From the Lesser Primates in His Passion for Lists"
Who doesn't love lists? (besides maybe to-do lists.) List functionality on Nostr is a powerful way to curate your feeds. You can make lists of artists, vendors, friends, or whatever you want. They can be public or private. You can subscribe to other people's public lists too. Make one to share with your friends. Many clients have list support and management. Amethyst, Nostur, Voyage, and Nostrudel are a few that come to mind. Nostr.band and Listr.lol offer in depth list management. Some clients even support lists for specific notes so that you can curate a feed by topic or aesthetic to share with your friends.
Being John Malcovich.
Everyone has a different view of Nostr. Do you want to see what someone else is seeing? Sign in with any npub to get a different perspective. You might find profiles and content that you didn't know existed before. Some clients integrate variations of this feature right into their apps, so you don't have to log out of your account in order to step through that tiny door.
DV-what? DVM.
Data Vending Machines. These fancy little things are AIs tasked with a simple job: to find content for you. Most of these feeds are free, though some more personalized ones require a small fee. Many DVM services are stand-alone apps, like Vendata and Noogle . These clever Nostr clients will let you do a lot more than just create feeds to browse notes. Explore if you wish. A few social clients have DVMs integrated, too, so if you see "discovery" or similar term on a tab, be sure to check it out.
Relays, Man. Relays.
It's right there in the name. Nostr- notes and other stuff transmitted by RELAY. Specialized relays exist for subjects, news, communities, personal spaces, content creators, cats... there's even a relay where everyone just says "Good Morning" to each other. Find a client that lets you browse a relay's contents, and enjoy the purest form of content discovery on Nostr. Unearthing these relays is getting better and better every day. Right now there are relay browsing capabilities in quite a few clients, like Coracle, Relay Tools, Jumble and Nostur.
The Algo Relay.
Maybe you've been busy and missed a lot. Maybe you are a sane person who rarely uses social media. Hook up with a personalized algorithm relay to catch you up on all the things you've missed. This is skirting the sharp edges of Nostr relay development, so keep in mind that not many implementations yet exist. Algo relay currently aims to bring the feel-good vibe of your chronological feed to an algorithmic feed, freeing up your time but letting you stay up with what 's going on in your social circles.
Trendy Trends.
A few clients, relays, and DVM's have developed various Trending feeds. Catch up on what's popular across a wider view of the Nostr ecosystem. If trends are your thing, be sure to check them out.
Now that you're equipped with the tools to explore Nostr, its time to go discover some great content and find your people. Feed your curiosity.
-
 @ 3c389c8f:7a2eff7f
2025-03-31 20:38:23
@ 3c389c8f:7a2eff7f
2025-03-31 20:38:23You might see these terms used interchangeably throughout the Nostr network. Since Nostr is a decentralized protocol and not a platform, there is often a lack of consensus around particular terminologies. At times, it's important to differentiate between them, so that you can determine what is being stated. In the truest sense, there is no central entity to maintain a Nostr 'account' on your behalf, though some Nostr-based platforms may offer to do so. There's also no one to verify your 'identity'. This is something that you create, maintain and control. It is 100% yours. In a sense, you verify yourself through your interactions with others, with the network of clients and relays, and by protecting your nsec (secret key). A profile is generally considered to be a single place for displaying your content and any information about yourself that you've chosen to share, but its a little more complicated than that with Nostr. Let's take a closer look at all 3 terms:
Identity:
Your Nostr identity becomes yours from the moment you generate your key pair. The two parts each provide unique perspective and functionality. (Remember, there is no central entity to issue these key pairs. You can screw up and start over. You can maintain multiple key pairs for different purposes. If all of this is new and unfamiliar, start simply with the intention of trial and error.)
Half of the equation is your nsec. As long as you maintain control of that secret key, the identity is yours. You will use it to sign the notes and events that you create on Nostr. You will use it to access functionality of various tools and apps. You can use it to send monetary tips for content you find valuable. The reputation that you build through posting & interacting on Nostr will signal to others what type of person or profile this is, whether it's a genuine person, a bot (good or bad), a collection of works, etc. You might come across information that compares your nsec to a password. While a fair comparison, its important to remember that passwords can be reset, but your private key CANNOT. Lost access or control of your nsec means a loss of control over that identity. When you have decided to establish a more permanent identity, write it down, keep it safe, and use the appropriate security tools for interacting online.
The other half of this equation is your npub. This public key is used to find and display your notes and events to others. In short, your npub is how your identity is viewed by others and your nsec is how you control that identity.
Npub can also act a window into your world for whoever may choose to view it. As mentioned in a previous entry, npub login enables viewing Nostr's notes and other stuff in a read-only mode of any user's follow feed. Clients may or may not support this, some will even allow you to view and subscribe to these feeds while signed in as yourself via this function. It the basis of the metadata for your profile, too.
Profile:
Profile, in general, is a collection of things about you, which you have chosen to share. This might include your bio, chosen display name, other contact information, and a profile photo. Similar to traditional socials, veiwing Nostr profiles often includes a feed of the things you have posted and shared displayed as a single page. People will recognize you based on the aspects of your profile more than they will by your actual identity since an npub is a prefixed random string of characters . Your npub bridges a gap between strictly machine readable data and your human readable name, but it is not as simple as a name and picture. You will choose your photo and display name for your profile as you see fit, making you recognizable. These aspects are easy for copycat scammers to leverage, so your npub will help your friends and followers to verify that you are you, in the event that someone should try to copy your profile.
The Nostr protocol has another profile aspect that is important to know about, but as a general user, you shouldn't have to worry much about it. This is your nprofile. It combines your npub (or the machine readable hex verison of it) with hints to what relays you are using to publish your notes. This helps clients, crawlers, and relays find your stuff for your followers. You may notice nprofile when you share a profile link or used in other actions. When you update your relay list, your client will adjust your nprofile and send a new copy to the appropriate relays. If your believe that a client is not doing that correctly, you can visit metadata.nostr.com and manage it yourself.
Account:
Across Nostr, it is common to see the term 'account' used to refer to the combination of your identity and profile. It is a relatable term, though it may imply that some account issuer exists, but no one issues a Nostr account to you. You create and maintain it yourself.
There are situations where a traditional account will exist, such as with media servers, relay subscriptions, custodial wallet hosts, or NIP-05 providers. These things will almost always be paid services and storage that you choose to use. (Reminder: all of these things are possible to DIY with a little knowhow and an old computer)
What Is The Right Terminology?
There is no simple or correct answer here. Developers and writers will use whatever terms fit their scope and topic. Context will matter, so it's important to differentiate by that more than any actual term.
-
 @ 592295cf:413a0db9
2025-03-29 10:59:52
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article nostr-quick-start-guide
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it.
Go to nstart.me and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump.
Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
Now select 5 clients
Coracle, Chachi, Olas, Nostur, Jumble
The first is Coracle
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
Let's try Chachi
Simpler than Coracle, it has a type login that says bunker. see if I can post
It worked, cool, I managed to post in a group.
Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something like that, but many start from the phone so maybe it's easy for them. I try to download it and see if it allows me to connect with a bunker.
Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
Ok then I saw that there was the qrcode image of the bunker for apps lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are Olas's lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on Olas, so it works, Expiration time is broken.
As for Nostur, I don't have an ios device so I'm going to another one.
Login with Jumble, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
Extensions nostr NIP-07
The true path is nip-07-browser-extensions | nostr.net
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
- Aka-profiles: Aka-profiles
Alby I don't know if it's a route to recommend
-
Blockcore Blockcore wallet
-
Nos2x Nos2x
-
Nos2xfox (fork for firefox) Nos2xfox
Nostore is (archived, read-only)
Another half hour to search all sites
Nostrapps
Here you can make paths
Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to Nostrapps and read:
Microbbloging: Primal
Streaming: Zap stream
Blogging: Yakihonne
Group chat: Chachi
Community: Flotilla
Tools: Form *
Discovery: Zapstore (even if it is not in this catrgory)
Direct Message: 0xchat
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 0a63d301:b1fb5602
2023-08-14 03:14:00
@ 0a63d301:b1fb5602
2023-08-14 03:14:00Introduction
In the ever-evolving landscape of modern society, the interaction between humanity and technology has grown increasingly complex. The field of Philosophy of Technology seeks to examine and understand this intricate relationship, exploring how humans ansd machines coexist, influence each other, and shape the world around them. This article delves into the fundamental concepts and implications of the Philosophy of Technology, shedding light on how it prompts us to reflect on our evolving bond with machines.
Understanding Philosophy of Technology
Philosophy of Technology is a branch of philoasophy that delves into the nature, significance, and impact of technology on human existence. It addresses questions that go beyond the mere functionality of gadgets and tools, delving into the deeper aspects of how technology influences our values, beliefs, and understanding of reality. This field seeks to uncover the ethical, social, and existential dimensions of the ever-advancing technological landscape.
The Human-Machine Nexus
At the heart of the Philosophy of Technology lies the exploration of the human-machine nexus. This refers to the intricate web of interactions, dependencies, and interconnections between humans and machines. Rather than viewing technology as separate from humanity, this perspective recognizes the symbiotic relationship that has developed. Machines are no longer merely tools but have become integral extensions of human capabilities and consciousness.
Technological Determinism vs. Human Agency
One of the central debates within the Philosophy of Technology is the tension between technological determinism and human agency. Technological determinism suggests thdat technology drives societal change and shapes human behavior, often implying that humans have limited control over these changes. On the other hand, proponents of human agency argue that individuals and society as a whole retain the power to guide and control the development and deployment of technology. Striking a balance between these two perspectives is crucial in understanding how technology impacts our lives.
Ethical Considerations
The rapid advancement of technology has brought about a myriad of ethical dilemmas. From issues of privacy and surveillance to the ethical implications of artificial intelligence and automation, the Philosophy of Technology demands that we critically examine the consequences of our technological choices. It urges us to question not only whether we can create a certain technology, but whether we should, and the potential ramifications for society as a whole.
Existential Reflections
As machines become more integrated into our lives, the Philosophy of Technology encourages us to contemplate our own existence. Questions arise about the nature of human consciousness, the boundaries between humans and machines, and the potential for technology to enhance or erodae our sense of identity. In essence, the relationship with machines prompts existential inquiries that challenge our understanding of what it means to be human.
Conclusion
The Philosophy of Technology serves as a compass for navigating sthe intricate terrain of human-technology interactions. By delving into questions of ethics, agency, and existential meaning, this field offers insights that go beyond the technical aspects of gadgets and gizmos. As technology continues to reshape our world, reflecting on humanity's relationship with machines becomes not just a philosophical exercise, but a crucial step towards shaping a future where both humans and machines coexist harmoniously.
-
 @ 4180da63:7b3c147e
2025-05-11 04:33:47
@ 4180da63:7b3c147e
2025-05-11 04:33:47By John "Potato Jack" LeFebvre
The cold, cold air of the morning tickled the nose of Christmas Goat as he lay quietly in bed, just waking up.
The cold air of the morning whispered in the ear of Christmas Goat; it whispered:- icicle secrets!
The moon, round and white, with swirling breezes, made Christmas Goat’s bedroom look like milk.
That reminded Christmas Goat – "It’s time to milk my cows!"
Christmas Goat peeled away the bed sheet and four blankets which kept him warm at night, and sitting on the edge of the bed he put on his gumboots.
He walked out of his bedroom and bumped into a wall because he was still a bit tired. He stood out on his front verandah and looked at the farm. "Come on you cows! It’s time for milking!!" he yelled.
The cows made a quiet line and walked, one behind the other, off to the milking sheds…
..all except for two cows who Christmas Goat had to throw a few potatoes at: then they got moving.
In the shed, the moos filled the air. Christmas Goat made his way past steaming cow flops carrying a bucket and a small stool.
He sat down next to Harry the cow.
"Ready for milking?", he asked.
"Yes, but you should have given me a girls name," said the cow.
"Oh well", said Christmas Goat, "here we go".
"Okay" said the cow, so Christmas Goat grabbed her teats with both hands and made the squirty milk goosh into the bucket.
"How are the kids?" asked Christmas Goat.
"Oh not bad," said Harry. "Bruce is in school and Terry’s just learning to moo."
"Yes, they’re good cows," said Christmas Goat.
"They are" said Harry. "I just wish you hadn’t given them boy’s names."
"Oh well," said Christmas Goat.
Christmas Goat milked all the cows one by one, and then he said to himself, "I think I’ll make myself a hot coffee". Back inside, he turned on the radio, and stirred the coffee powder into the hot water. Yum, he thought, pouring the cow’s milk on top. "Yum Yum Yum".
Christmas Goat drank all of this hot coffee and then made toast. A bird landed on his window sill and said "tweet tweet, tweet tweet ¯ ".
"Tweet tweet " said Christmas Goat".
The telephone rang four times and Christmas Goat picked it up.
"Hello, this is Christmas Goat?"
"Hello Christmas Goat? I’ve been a good goat all year and can you tell me what I’m getting for Christmas?"
"Christmas is tomorrow," said Christmas Goat.
"I know, but … - please tell me, just this once ..!"
"All right little goatgirl, what’s your name?"
"My name is Brenda," said the little girlgoat.
"Let me look at my list here…" said Christmas Goat. "
"Hmmm…" He moved his papers around.
"Are you still there?" asked the little goatgirl.
"Aha!! Yes I’m still here. I’ve just found your name on the list Brenda, here it is. Let’s see, oooh!"
"What is it! Wot is it!"
"It’s a …." But then Christmas Goat stopped talking.
"Why have you stopped talking?" said Brenda, panicking.
"Now, now," said Christmas Goat, "I just remembered it’s a secret."
"A secret!" said Brenda.
"Yes," said ChristmasGoat. "It has to be a surprise."
"No! Tell me now!" said Brenda.
Christmas Goat made a whistling sound with his lips. And then he hung up the phone.
By hanging up the phone like that, Christmas Goat felt a bit rude. But Brenda was rude first, he thought. Meanwhile, Brenda was at home, crying.
Christmas Goat thought , " I better go to see Brenda and explain to her why Christmas has to be a surprise." He went to the garage, oiled the wheels of his cart, and tied up a couple of humans.
"Good humans!" he said as they pulled him out of the garage down the street. The two people pulled the cart steadily along, steam pluming their foreheads.
It was a cold morning, and yet ChristmasGoat knew the earth was a round huge ball that spun on it’s axis while being invisibly dragged around a gigantic non stop fire- "the sun" – and that soon, because of this axis-spin, his part of the world would be receiving increasingly direct sun rays and it would get warm, so he didn’t worry . He explained this to the two men pulling his cart as it rolled through the suburbs, but they just blinked.
After a while, they arrived at Brenda’s house, and Christmas Goat tied the two men to a post and gave them a bottle of beer. Christmas Goat walked up the driveway, up the stairs, and went "knock kn0ck knock". A goat came to the door.
"Hallo Brenda?"
"No I’m Brenda’s brother. Brenda’s in her room, crying."
"Rats," said Christmas Goat.
There was Brenda, covered in tears, sitting on her carpet. Christmas Goat came in and sat down.
"Why did you make me sad?" said the little goatgirl.
"Well," said Christmas Goat, "I really didn’t want to do that. Every year, thousands of little goats ask me ‘what am I getting for Christmas,’ and every time I have to say to them, ‘you’ll see on Christmas day.’ And I Have to say this, I can’t say anything else, that’s just the way Christmas is."
"Come on, you must be able to tell me something a little deeper than (sniff) that."
Oh," said Christmas Goat, "you want the Big Reality explanation.."
"Yes," said Brenda, pouting and looking up from hurt eyes.
"Well," said Christmas Goat, "think what the world would be like with no surprise."
"Why? What would the world be like without surprise?" asked Brenda.
"Utterly predicable, " said Christmas Goat.
"What does predickable mean?" asked Brenda.
"In this case, it means ‘always knowing what’s going to happen’," said Christmas Goat.
"That sounds great!" said Brenda.
"Not really," said ChristmasGoat. "Think about it. Every day you wake up, you know what to wear, you know what’s going to be for breakfast, you know what job you have to go to, you know when it starts, you know how to get there, you know what you will see on the way, you know when you will stop for lunch, you know when you will finish, you know what’s for dinner, by looking at the program, you know what’s on T.V that night, they tell you what the weather will be like tomorrow, you know that if you …"
"That sounds Great!!" butted in Brenda.
"Yeah it sounded great to humans once, too, when they ruled the world. Woops."
"What was that?" said Brenda.
"What was what?" asked Christmas Goat.
"That thing you said, " said Brenda.
"I can’t remember, " said Christmas Goat, although now the shoe was on the other hoof.
"Well I remember, " said Brenda. "It just shocked me, that’s all. You said ‘when humans ruled the world.’"
"You’re right," sighed Christmas Goat. "That’s what I said..
Maybe we can forget about it though?"
Tell me tell me tell me tell me tell me tell me tell me tell me tell me tell me tell me tell me tell me tell… "
"ALL-RIGHT" said Christmas Goat, giving in. "Are you sure you want this dark knowledge?"
"Yes, I’m sure," said Brenda dribbling with excitement.
"Right, well once upon a time, the humans, like those two hitched up to the post outside drinking beer, were our masters. What they said, went."
"Boy," said Brenda.
"That’s right," continued Christmas Goat. "In fact they were the kings of the world. Us goats were treated horribly at times."
"What happened?" asked Brenda the little goatgirl.
"Those people became so set in their ways that they became stale. Nearly every effort at becoming the rulers made them and their lives boring. They thought they knew everything."
"People don’t know anything!" said Brenda.
"Not now they don’t," said Christmas Goat. "But they did in a distant past. Unfortunately they made the mistake of killing most surprises, and that’s when we snuck up them."
"Us goats?"
"Yep."
"And now we’re the kings and queens!" said Brenda gleefully.
"Of course," said Christmas Goat. "But we mustn’t let ourselves get trapped by prediction. That’s why I’m Christmas Goat. It’s my job to make sure surprise is still big in our lives, especially at this time of the year, Christmas." "Thankyou for telling me that true story," said Brenda. "I look forward to my surprise present tomorrow morning."
"That’s a good boy," said Christmas Goat.
"I’m a girl," said Brenda.
That night, Christmas Goat tied up his strongest humans who hauled and heaved his sleigh-cart all over the world through beautiful bright darkness. Kind Mummy and Daddy goats left a snack for Christmas Goat, and beer for the sweaty humans.
Christmas Goat and his team finished delivering the presents just in time.
"Good humans," he said, patting his helpers and switching on the T.V for them.
When Brenda woke up, there was a terrific colourful ping pong ball under her Christmas Tree.
"That is a surprise," smiled Brenda. "I’m a netballer!"
-
 @ 8d34bd24:414be32b
2025-05-11 02:47:03
@ 8d34bd24:414be32b
2025-05-11 02:47:03What does it say about us that believers don’t listen as well as unbelievers? Let’s investigate some scripture verses and see what we can discover.
An Object Lesson:
Jesus warned His disciples several times that He would be killed and rise from the dead on the third day. Right after Jesus asked them who they thought He was and Peter replied that He was the Christ (Messiah), Jesus told them what would happen.
From that time Jesus began to show His disciples that He must go to Jerusalem, and suffer many things from the elders and chief priests and scribes, and be killed, and be raised up on the third day. (Matthew 16:21)
We know the disciples heard and understood what Jesus was saying because Peter immediately rebuked Jesus.
Peter took Him aside and began to rebuke Him, saying, “God forbid it, Lord! This shall never happen to You.” But He turned and said to Peter, “Get behind Me, Satan! You are a stumbling block to Me; for you are not setting your mind on God’s interests, but man’s.” (Matthew 16:22-23)
You’d think that Peter would have this moment locked in his mind after being rebuked so harshly for questioning Jesus’s prediction of what would happen.
A while later, Jesus again told His disciples what was about to happen.
And while they were gathering together in Galilee, Jesus said to them, “The Son of Man is going to be delivered into the hands of men; and they will kill Him, and He will be raised on the third day.” And they were deeply grieved. (Matthew 17:22-23)
They again heard what was said because they were “deeply grieved.” They didn’t like what they heard.
Then a third time, as they were approaching Jerusalem, He made certain they knew what was coming:
As Jesus was about to go up to Jerusalem, He took the twelve disciples aside by themselves, and on the way He said to them, “Behold, we are going up to Jerusalem; and the Son of Man will be delivered to the chief priests and scribes, and they will condemn Him to death, and will hand Him over to the Gentiles to mock and scourge and crucify Him, and on the third day He will be raised up.” (Matthew 20:17-19)
The disciples should have known that Jesus’s crucifixion and death were not the end. He told them repeatedly that He would die and be raised from the dead on the third day. They should have been diligently waiting with expectation, but instead they immediately hid, gave up, and headed back to their old lives.
His female followers still cared enough to try to prepare Jesus’s body for burial, but even they did not expect Him to rise as He said.
The angel said to the women, “Do not be afraid; for I know that you are looking for Jesus who has been crucified. He is not here, for He has risen, just as He said. Come, see the place where He was lying. Go quickly and tell His disciples that He has risen from the dead; and behold, He is going ahead of you into Galilee, there you will see Him; behold, I have told you.” (Matthew 28:5-7) {emphasis mine}
Even when the woman came and told the disciples that they had seen Jesus as He had said, none believed them, although Peter and John did have a glimmer of hope and went to look for themselves.
In contrast, the Pharisees, the very people who hated Jesus so much that they fought to have Him crucified, remembered Jesus’s statements.
Now on the next day, the day after the preparation, the chief priests and the Pharisees gathered together with Pilate, and said, “Sir, we remember that when He was still alive that deceiver said, ‘After three days I am to rise again.’ Therefore, give orders for the grave to be made secure until the third day, otherwise His disciples may come and steal Him away and say to the people, ‘He has risen from the dead,’ and the last deception will be worse than the first.” Pilate said to them, “You have a guard; go, make it as secure as you know how.” And they went and made the grave secure, and along with the guard they set a seal on the stone. (Matthew 27:62-66) {emphasis mine}
The Pharisees acted in response to Jesus’s claims. The disciples ignored or forgot Jesus’s claims.
KNOW:
How often do we ignore or forget Jesus’s promises? How often do we despair when we should hold tightly to the promises given to us in the Bible? Are there times that our opponents, unbelievers, are better at quoting the Bible back at us than we are at using the Bible to defend the truth and our faith?
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence (1 Peter 3:15)
We need to know God’s word so we can “give an account for the hope that is in” us. First we need to read the whole Bible. We can’t know who God is, what He has done, and what He commands for us without knowing God’s word.
After we have gotten the big picture by reading through the Bible once, we need to really get to know it well. This not only includes reading the Bible continually, but also include memorizing key verses, so we can bring them to remembrance when we need them.
Some people can repeat a verse multiple times and just know it. Some of us have trouble memorizing things. We have to go to extraordinary measures to memorize God’s word. Some techniques I have used:
-
WHITEBOARD APPROACH:
-
Write the verse on the white board.
-
Read out loud.
-
Erase one word. (You can underline where the word is if that helps you remember that a word goes there)
-
Read out loud saying verse including missing word.
-
Continue erasing words, one at a time, saying the verse until all of the words are gone.
-
I haven’t used it personally, but Verse Locker was recommended by another substacker and seems to use a similar technique.
-
MUSICAL VERSES:
-
Make up a tune and sing the verse or put the verse to a tune you already know.
-
If you aren’t good at making up songs, there are sites that have verses to songs, but I haven’t used them personally other than a few from Awana years ago.
-
FIRST LETTER:
-
Write down the first letter of each word of the verse you want to memorize This gives hints and helps you not accidentally miss words.
-
I’ve also made a necklace (it was supposed to be a bracelet, but the verse, 1 Peter 3:15 above, I picked was too long) made of beads with the letters of the words of the verse. By wearing it, you have a reminder to memorize and rememorize the verse till it sticks stronger.
-
This is my version of 1 Peter 3:15

-
APPS:
-
There are multiple apps that can help you memorize verses. 5 Best Bible Memory Apps for 2025
We are all different and have different learning styles. Pick the version that works best for you, but be intentional. For so long I wasn’t. Having a child with Down Syndrome in Awana who needed help led me to finding ways to help him and me to memorize the hundreds (or thousands) of verses that are required to finish the program. Keep in mind that you need to keep reviewing them or the memories will fade. The more times you memorize the verse, the longer it will stick with you. You just never know when you will need a Scripture verse and you may not have your Bible or phone (with Bible app) handy.
APPLY:
Knowing the Bible is critical for the Christian life, but knowing the Bible and God’s commands is not enough. We have to live according to this knowledge. We have to apply it in our lives. It needs to change the way we view the world and change the way we live our lives and interact with others.
for it is not the hearers of the Law who are just before God, but the doers of the Law will be justified. (Romans 2:13) {emphasis mine}
Our faith needs to be exhibited through action.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” (James 2:18) {emphasis mine}
There is nothing we need to do to be saved besides believe, but if we have saving faith, we should desire God’s word like the author of Psalm 119. Our lives should also change to be conformed to Jesus.
And do not be conformed to this world, but be transformed by the renewing of your mind, so that you may prove what the will of God is, that which is good and acceptable and perfect. (Romans 12:12) {emphasis mine}
There must be works as evidence of our faith.
You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; (James 2:19-22) {emphasis mine}
The disciples heard Jesus tell them what was going to happen to Him. They knew what He had said because they reacted to it negatively. The problem was they didn’t believe it and didn’t live according to Jesus’s plain words. As important as it is to read and understand the Bible, none of that matters if we don’t believe it and live it.
But I Can’t Do It Myself:
Jesus knew that we could not know and do what we were commanded to know and do, at least not in our own power.
Then He opened their minds to understand the Scriptures, and He said to them, “Thus it is written, that the Christ would suffer and rise again from the dead the third day, and that repentance for forgiveness of sins would be proclaimed in His name to all the nations, beginning from Jerusalem. You are witnesses of these things. And behold, I am sending forth the promise of My Father upon you; but you are to stay in the city until you are clothed with power from on high.” (Luke 24:45-49)
Jesus not only sent the disciples (and all believers) out into the world to tell of what He has done for us, but He told the disciples to “stay in the city until you are clothed with power from on high.” Jesus told them to wait until they had received the Holy Spirit to guide and empower them in the work He had designed them to complete. We also have the Holy Spirit to change our hearts and minds, so we can fulfill the commandments and plans He has for us.
I’m sorry if this post had a little too much overlap with my last post, but knowing God’s word has become a passion of mine and it is where I felt led to go.
May the God of Heaven give you a hunger for His word, help you to understand His word, believe His word, and live His word. May your understanding of the word of God guide you in everything you think, speak, and do. May you never doubt God’s word or discount God’s word because it isn’t according to your preference. God bless you and keep you.
Trust Jesus.
-
-
 @ b2caa9b3:9eab0fb5
2024-07-02 13:20:06
@ b2caa9b3:9eab0fb5
2024-07-02 13:20:06







Recently, I shared some of my memories from Odessa, a city that truly captured my heart. Today, I’m adding even more photos to give you a glimpse into this vibrant and historic city.
Odessa is a port city on the Black Sea, known for its stunning architecture, including the Odessa Opera and Ballet Theater. The city was founded by Catherine II in 1794 and quickly became a major cultural and economic center.
I had the opportunity to explore Odessa’s many neighborhoods, from the bustling city center to the quieter beaches. I was particularly impressed by the city’s unique blend of Ukrainian, Russian, and Greek influences.
Odessa is a city that has something to offer. Whether you’re interested in history, architecture, or simply relaxing on the beach, Odessa is a place you won’t forget.
I hope you enjoyed these additional photos of Odessa.
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ eb5f61d0:24cdd490
2025-05-11 02:34:15
@ eb5f61d0:24cdd490
2025-05-11 02:34:15Com o avanço da tecnologia e a popularização dos jogos online, os brasileiros têm buscado plataformas modernas, seguras e completas para se divertir e tentar a sorte. Entre as opções que vêm ganhando destaque no cenário nacional, a 9993Bet se consolida como uma das principais escolhas. Reunindo inovação, variedade de jogos e uma experiência de usuário diferenciada, a plataforma é ideal para quem busca entretenimento de alta qualidade, sem complicações.
Plataforma moderna e acessível Um dos grandes diferenciais da 9993Bet é sua interface intuitiva e responsiva, pensada para oferecer uma navegação fluida tanto em computadores quanto em dispositivos móveis. O site conta com um design moderno e bem estruturado, que facilita o acesso às diferentes seções e jogos disponíveis. Desde o primeiro acesso, é possível perceber o cuidado da plataforma em proporcionar uma experiência agradável, mesmo para os iniciantes.
Além disso, o processo de cadastro é rápido e descomplicado. Com apenas alguns cliques, o jogador já pode criar sua conta e começar a explorar o universo de possibilidades que a 9993betoferece. A segurança dos dados também é levada a sério, utilizando criptografia de ponta e sistemas de proteção avançados.
Variedade de jogos para todos os gostos Outro ponto forte da 9993Bet é a ampla seleção de jogos. A plataforma conta com centenas de títulos das principais desenvolvedoras do mercado, garantindo qualidade gráfica, jogabilidade envolvente e mecânicas inovadoras. Entre os jogos mais populares, destacam-se:
Slots (Caça-níqueis): com temas variados, bônus emocionantes e recursos especiais, os slots são uma das atrações preferidas dos usuários. Há opções clássicas com 3 rolos e também versões modernas com animações incríveis.
Jogos de cartas: para os fãs de estratégia e emoção, a 9993Bet oferece versões virtuais de jogos consagrados como pôquer, blackjack e bacará.
Roleta online: com diferentes variações e estilos, é ideal para quem busca adrenalina e sorte em cada giro.
Jogos ao vivo com crupiês reais: proporcionando uma experiência imersiva e interativa, esses jogos permitem que o jogador se conecte com apresentadores reais e jogue em tempo real, como se estivesse em uma sala física.
Uma experiência pensada no jogador A 9993Bet investe constantemente em tecnologia e atendimento ao cliente para garantir a melhor experiência possível aos seus usuários. O suporte funciona 24 horas por dia, 7 dias por semana, com uma equipe preparada para responder dúvidas, resolver problemas e orientar os jogadores em qualquer situação.
Os métodos de pagamento também são variados e seguros. A plataforma aceita PIX, boletos bancários e carteiras digitais, proporcionando rapidez nas transações e total comodidade. Os saques são processados com agilidade, permitindo que os jogadores aproveitem seus ganhos sem longas esperas.
Além disso, a 9993Bet oferece promoções regulares, bônus de boas-vindas e recompensas exclusivas para usuários fiéis. Tudo isso contribui para um ambiente envolvente, competitivo e, acima de tudo, divertido.
Conclusão A 9993Bet chega ao mercado brasileiro como uma plataforma completa de entretenimento digital, aliando inovação, segurança e uma vasta gama de jogos que agradam desde os iniciantes até os jogadores mais experientes. Com foco no usuário e um compromisso com a excelência, a 9993Bet se firma como uma das principais opções para quem busca diversão de qualidade e oportunidades reais de ganhar.
Se você está em busca de emoção, variedade e confiabilidade, a 9993Bet é a escolha certa. Cadastre-se, explore os jogos e descubra um novo nível de entretenimento online.
-
 @ e968e50b:db2a803a
2024-03-22 15:49:38
@ e968e50b:db2a803a
2024-03-22 15:49:38ENJOY!*
https://bitcoinwhacamole.vercel.app/
*I'm pretty sure it's actually impossible for a normal human to win, but there is a little end screen as a reward if you can accomplish the impossible. It might be easier on mobile.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ b99efe77:f3de3616
2025-05-11 09:29:49
@ b99efe77:f3de3616
2025-05-11 09:29:49asfadfadsf draft 333446666
afasdfasdfsadf
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ eb5f61d0:24cdd490
2025-05-11 02:33:37
@ eb5f61d0:24cdd490
2025-05-11 02:33:37No cenário atual do entretenimento online, o Brasil tem visto um crescimento notável de plataformas que oferecem experiências envolventes e seguras para os jogadores. Entre elas, a 59BRL se destaca como uma opção moderna, confiável e completa, proporcionando diversão, praticidade e uma ampla variedade de jogos para todos os perfis de usuários. Com uma interface amigável e suporte dedicado, a 59BRL se tornou referência no segmento de apostas e jogos virtuais.
Conheça a Plataforma 59BRL Desde o primeiro acesso, a plataforma 59BRL impressiona pela sua estrutura bem organizada e visual atraente. Desenvolvida para atender tanto iniciantes quanto jogadores experientes, ela oferece navegação rápida, menus intuitivos e total compatibilidade com dispositivos móveis e computadores. Isso significa que o usuário pode jogar de onde estiver, com total liberdade.
A segurança é outro ponto forte. A 59brlutiliza tecnologias avançadas de criptografia para garantir a proteção dos dados dos usuários, além de contar com um sistema de verificação para evitar fraudes e atividades suspeitas. O ambiente é totalmente transparente, com termos claros e atendimento eficiente.
Diversidade de Jogos para Todos os Gostos Um dos maiores diferenciais da 59BRL é a variedade de jogos disponíveis. A plataforma oferece opções que vão desde os clássicos jogos de mesa até experiências modernas com gráficos 3D e interatividade ao vivo. Entre os jogos mais populares estão:
Roleta Virtual: Uma experiência dinâmica e cheia de emoção, com várias versões para agradar desde os mais conservadores até os mais ousados.
Slots Interativos: Jogos com temas variados, desde aventura e fantasia até cultura pop, que oferecem rodadas bônus e grandes chances de premiação.
Jogos de Cartas: Modalidades como pôquer, blackjack e baccarat ganham espaço com versões modernas e fáceis de jogar, tanto em modo automático quanto com interações ao vivo.
Raspadinhas Digitais: Uma opção prática e divertida para quem quer testar a sorte rapidamente, com prêmios instantâneos e animações envolventes.
Experiência do Jogador: Praticidade e Suporte Total A 59BRL valoriza a experiência de seus usuários em todos os aspectos. O processo de cadastro é simples, pedindo apenas dados básicos e uma confirmação rápida por e-mail ou telefone. Já o sistema de depósito e saque é outro destaque: a plataforma aceita os principais métodos de pagamento, incluindo PIX, boleto bancário e carteiras digitais, com transações ágeis e seguras.
Outro ponto bastante elogiado pelos usuários é o suporte ao cliente. A equipe da 59BRL está disponível 24 horas por dia, todos os dias da semana, através de chat ao vivo e e-mail. As respostas são rápidas, claras e resolutivas, o que proporciona tranquilidade mesmo em situações de dúvida ou dificuldade.
Além disso, a plataforma costuma oferecer promoções e bônus para novos usuários e jogadores frequentes, como rodadas grátis, cashback e programas de fidelidade. Tudo isso é pensado para manter a diversão em alta e recompensar os jogadores mais engajados.
Conclusão A 59BRL é mais do que uma simples plataforma de jogos: é um verdadeiro ambiente de entretenimento digital, pensado para oferecer praticidade, segurança e diversão sem limites. Com uma interface moderna, grande variedade de jogos e suporte de qualidade, ela tem conquistado cada vez mais brasileiros que buscam uma alternativa confiável e empolgante para seu lazer online. Se você ainda não conhece, vale a pena explorar o que a 59BRL tem a oferecer.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ c9badfea:610f861a
2025-05-11 01:12:30
@ c9badfea:610f861a
2025-05-11 01:12:30- Install Helio (it's free and open source)
- Download SoundFont files from various sources (see links below)
- Launch the app and follow these steps to import SoundFonts:
- Tap Studio in the top bar, then select Orchestra Pit
- Tap Scan Common Plugin Folders, select SoundFont Player from the plugins found
- Tap SoundFont Player in the top bar, then Create New Instrument
- Select the new SoundFont Player instrument
- Tap SoundFont Player in the top bar, then Show UI
- Tap the folder icon and choose a downloaded SoundFont file
- Rename the instrument by tapping the first SoundFont Player in the top bar, then Rename
- Tap Studio twice in the top bar, then Start A New Project
- Choose a file location for the project and Save
- Tap Track 1, choose Set Instrument, and select an instrument
- Double-tap in the arranger to add a new note
- Explore the interface and start composing
Some SoundFont Sources
ℹ️ The Helio interface is unique and may require some time to get accustomed to
ℹ️ A SoundFont file (
.sf2) contains a collection of audio samples -
 @ b99efe77:f3de3616
2025-05-11 09:28:21
@ b99efe77:f3de3616
2025-05-11 09:28:21asfadfadsf draft 333
afasdfasdfsadf
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ a012dc82:6458a70d
2023-08-24 08:49:39
@ a012dc82:6458a70d
2023-08-24 08:49:39Table Of Content
-
What Are Bitcoin Addresses?
-
Understanding the Growth in Bitcoin Total Addresses
-
What Does the Growth in Bitcoin Total Addresses Mean?
-
Is the Growth in Bitcoin Total Addresses a Sign of Adoption?
-
Factors Affecting the Growth in Bitcoin Total Addresses
-
Conclusion
-
FAQ
Since its inception in 2009, Bitcoin has grown to become one of the most popular cryptocurrencies in the world. Over the years, the number of Bitcoin users has grown significantly, leading to an increase in the total number of Bitcoin addresses. This growth has left many wondering whether the rapid increase in Bitcoin total addresses is a sign of adoption. In this article, we will explore the significance of the growth in Bitcoin total addresses and its implications for the adoption of Bitcoin.
What Are Bitcoin Addresses?
Before diving into the topic of whether the rapid growth of Bitcoin total addresses is a sign of adoption, it's essential to understand what Bitcoin addresses are. In simple terms, a Bitcoin address is a unique identifier that represents a destination for Bitcoin transactions. Each Bitcoin address is a string of alphanumeric characters that is generated randomly and is associated with a private key.
Understanding the Growth in Bitcoin Total Addresses
The total number of Bitcoin addresses has been increasing at an unprecedented rate over the past few years. In September 2015, there were just over 11 million Bitcoin addresses. As of March 2023, the number has surged to over 885 million. This represents a growth of more than 8,000% in just over six years.
What Does the Growth in Bitcoin Total Addresses Mean?
The rapid growth in Bitcoin total addresses is a clear indication of the increasing interest in Bitcoin. It suggests that more people are interested in owning Bitcoin and using it for transactions. However, it's important to note that not all Bitcoin addresses represent unique users. One person may have multiple Bitcoin addresses, which means that the total number of Bitcoin users may be lower than the total number of Bitcoin addresses.
Is the Growth in Bitcoin Total Addresses a Sign of Adoption?
The growth in Bitcoin total addresses is undoubtedly a sign of adoption. It indicates that more people are becoming interested in Bitcoin, which is essential for its growth and success. However, it's important to note that the growth in Bitcoin total addresses doesn't necessarily translate to an increase in the number of Bitcoin users. Some people may be holding Bitcoin for investment purposes rather than using it for transactions.
Factors Affecting the Growth in Bitcoin Total Addresses
Several factors are driving the growth in Bitcoin total addresses. One significant factor is the increasing awareness of Bitcoin and its benefits. As more people become aware of Bitcoin, they are more likely to invest in it and use it for transactions. Additionally, the increasing acceptance of Bitcoin by businesses is also contributing to the growth in Bitcoin total addresses. More businesses are accepting Bitcoin payments, which is making it easier for people to use Bitcoin for transactions.
Conclusion
The rapid growth of Bitcoin total addresses is undoubtedly a sign of adoption. It indicates that more people are becoming interested in Bitcoin, which is essential for its growth and success. However, it's important to note that not all Bitcoin addresses represent unique users. Some people may be holding Bitcoin for investment purposes rather than using it for transactions. Nonetheless, the increasing awareness and acceptance of Bitcoin suggest that the growth in Bitcoin total addresses may continue in the coming years. As more businesses accept Bitcoin payments and more people become aware of its benefits, Bitcoin adoption may continue to grow, leading to more widespread use of the cryptocurrency.
FAQs
Does the growth in Bitcoin total addresses mean that more people are buying Bitcoin? Not necessarily. The growth in Bitcoin total addresses indicates that more people are interested in Bitcoin. However, not all Bitcoin addresses represent unique users. One person may have multiple Bitcoin addresses, which means that the total number of Bitcoin users may be lower than the total number of Bitcoin addresses.
Can the growth in Bitcoin total addresses be attributed to investment rather than adoption? Yes, it's possible. Some people may be holding Bitcoin for investment purposes rather than using it for transactions.
Is the growth in Bitcoin total addresses sustainable? It's difficult to predict whether the growth in Bitcoin total addresses is sustainable. However, the increasing awareness and acceptance of Bitcoin suggest that the growth may continue in the coming years.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1f9e547c:8af216ed
2024-04-19 11:44:36
@ 1f9e547c:8af216ed
2024-04-19 11:44:36 -
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ c9badfea:610f861a
2025-05-10 23:17:06
@ c9badfea:610f861a
2025-05-10 23:17:06- Install EtchDroid (it's free and open source)
- Launch the app, then tap What's Supported? to check compatibility with devices and disk images
- Insert the USB drive
- Tap Write An Image, then select the desired image file
- Tap Grant Access, confirm, and then tap Write image
- Optionally, allow notifications to be notified when the process is complete
- Your bootable USB drive is now ready
⚠️ This app has telemetry enabled by default. Make sure to turn it off in the app menu. If you trust F-Droid, you can get a telemetry-free version from there
⚠️ Avoid moving the phone during the image writing process
-
 @ 8cb60e21:5f2deaea
2024-09-06 22:23:03
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03 -
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ df478568:2a951e67
2025-05-10 22:01:36
@ df478568:2a951e67
2025-05-10 22:01:36XMMP is a protocol that allows journalists and plebs alike to create a phone number that is not tied to your identity. Why would you want to do this? Are you some kind of hacker? Well… yeah… we are hackers, technically. That doesn't mean we want to break the non-aggression principle and steal sats from OGs or anything. Perhaps it's better to call ourselves cybersecurity experts to placate neurotypical people.
Every Bitcoiner worth their sats knows phone numbers are a security hole. Sure, if you're a super cypherpunk with a 100% KYC-free stack or never intend to spend your “precious,” then this might not concern you. You can sell your sats on Bisq for paper cash trash and pay your water bill or whatever. It's a significant inconvenience, but I know some people who do this. Satoshi bless them! But the rest of us mere mortals find it easier to use bill-pay services with Strike. Unfortunately, the powers that be force us to use our telephone numbers as a de-facto identity system.
This phone number must be trusted to a third party, and as Nick Szabo famously said, "Trusted third parties are security holes." This guy I go pleb camping with thinks it's funny that Bitcoiners never want to give away their phone numbers. It's true because phone numbers create an attack surface—specifically, they may be used for SIM swaps to drain our Bitcoin bank accounts or the associated traditional bank accounts. This is not the only attack. Smishing is also a concern, but that threat requires diligence since anyone using SMS is susceptible to it. XMMP won't prevent smishing; however, it will provide a phone number people can use to text or call without tying the number to your identity. Thus, even if attackers somehow compromise this phone number, it can't be used to drain your accounts.
What Is XMMP?

XMMP is a protocol that functions similarly to cellular phone service on almost any device with internet access. I don't think it'll work on a Kindle, but to be honest, I haven't tried. XMMP can be used alongside your existing phone, laptop, and desktop computers. You can safely give this phone number to all your hardcore hacker friends without worrying. It's affordable too—the service costs \$5.00 per month, and the service I use accepts sats for payment. Though this doesn’t include data, you can easily use XMMP over Wi-Fi.
If you want a separate phone running GrapheneOS or CalyxOS, you can pay for data in multiple ways. Personally, I like Silent Link—it's run by a fellow pleb and accepts sats via the Lightning Network.
How To Set Up XMMP
If you identify as a non-technical person, you can buy a phone and suite from Above Phone*, which will help you set everything up. I'm more of a DIY-as-much-as-I-can kind of guy, so I opted to set mine up myself. I haven't personally tried Above Phone, but I've heard good things about their service.
If you already have a phone but want a secure method to call or text your contacts, here's what to do:
-
Install Cheogram on your Android phone. Sorry, but I don’t know if Apple's overlords allow this for iOS devices.
-
Choose a phone number with JMP. They charge \$5.00 monthly and accept Bitcoin as payment. While you could port your current phone number, the purpose of this article is to create a fresh, anonymous phone number that cannot be traced back to you as an instrument for draining your bank account—so we won't get into porting here.
-
Once you've paid, you will receive a message in the Cheogram app confirming your order. It might take some time since payments are on-chain—so be patient. You can also pay with a credit card if you prefer, but we use sats in this household.
How To Get Data
You might occasionally want to send messages away from 127.0.0.1. My favorite solution is to use the services provided by Silent Link. They offer an eSIM, and while you can also get a phone number from Silent Link, it's mainly useful for services like Signal. However, it costs around \$20 worth of sats per month rather than JMP's \$5/month. Assuming all Bitcoiners are cheapskates like me—well, you do you!
I chose Silent Link's data plan. Initially, I messed up this process because I refreshed the webpage on my phone. Don't do that, or you'll have to spend another twenty bucks to set it up again. If you carefully follow Silent Link's instructions, you should be fine. Patience is crucial, and admittedly, that's something I'm not good at—which explains why I paid more sats than needed.
/* Above Phone is an affiliate link and I may get a small commission if you use my referral link.
☮️
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
As seen on https://zapthisblog.com/save-sats-with-on-sms-and-cellular-with-xmmp/
-





